Digital Forensics Mobile Device Data Extraction. Crime Scene/Digital and Multimedia Division
|
|
|
- Coleen Haynes
- 5 years ago
- Views:
Transcription
1 Mobile Device Data Extraction
2 12. MOBILE DEVICE DATA EXTRACTION PROCEDURE Purpose The purpose of this procedure is to extract data from mobile devices and/or removable media utilizing the most appropriate examination tool Scope This procedure describes an overview of the steps taken by DFL examiners in extracting data from various types of mobile devices submitted for examination Equipment Forensic workstation Appropriate examination tool for mobile devices (software and/or hardware) Forensic storage drive/flash drive for data storage Shielding enclosure (Faraday device) Digital camera Overview Mobile devices are designed to communicate with cellular networks, but also may be capable of connecting wirelessly to other devices via Wi-Fi, Bluetooth, or infrared connections. Allowing a device to receive a signal from a network or wireless connection can result in a change in the data contained on the internal memory of the device. Remote wiping is also a concern While powered on, cellular devices are always attempting to establish asynchronous communication with cell towers or other wireless channels to enable the devices to perform as designed. Therefore, mobile devices should be powered OFF when submitted for examination. If, during processing and/or transportation, it is necessary to power on the mobile device, the device should not be allowed to connect to surrounding networks. The device should be placed into airplane mode if possible. Faraday enclosures are utilized to prevent external connectivity if airplane mode is not enabled Mobile devices are produced by a variety of manufacturers, each utilizing their own unique operating system, version or implementation of an operating system, applications, data storage services, peripherals, and file structure systems. Due to this, it may be necessary to utilize several different acquisition tools in order to extract and document the desired data from a mobile device. Qualified examiners determine the best acquisition tool(s) to be utilized to conduct an examination. Uncontrolled When Printed Page 2 of 5
3 Mobile devices often contain removable storage devices such as media cards. These removable devices are processed via normal computer forensic imaging procedures. See Physical and Logical Imaging Procedures section for processing instructions Procedure The examiner should visually examine and photograph the mobile device and document the following: (Examiners should ensure that the camera is securely mounted before photographing evidence) Appearance Condition Presence of any removable digital storage devices (e.g., integrated circuit cards, flash memory, etc.) Identifying information (e.g., manufacturer, model number, etc.) Unusual markings and defects It is preferred to do this prior to the imaging process, but circumstances may dictate doing so after the image extraction is completed. All steps, where applicable, must be documented If the target device is submitted in a powered-on state, place the device into airplane mode, if possible If powered off, place the device into a shielded enclosure, power on, and place into airplane mode, if airplane mode is supported If this is not supported, examination shall be performed inside the shielded enclosure Attach the device with appropriate connectors for data extraction The tools that are appropriate for the examination of a mobile device will be determined by factors such as the examination request, the type of mobile device to be examined, and the presence of any external storage capabilities A communication channel must be established between the evidence device and the examination machine. The device must be detected successfully before the examiner may proceed with an automated examination It may be necessary to utilize various acquisition methods in order to extract as much data as possible If the evidence device cannot be successfully connected to an examination machine, but the device contents are accessible by visual examination, the requested evidence may be documented manually by photographing the content of individual screens If evidence is visually observed on the device, but automated software extraction does not support the specific task to extract that visual evidence, Uncontrolled When Printed Page 3 of 5
4 then those specific screens may be photographed to supplement the automated extraction report Manual examination will be used when a data connection cannot be established with the device or the electronic extraction does not retrieve information that is visible by interacting with the evidence manually. In these instances, examiners shall work in consultation with the requesting agency to photograph or video requested data that can be seen on the device through manual examination. An effort will be made by the examiner to document the requested data as completely as possible with the understanding that some data, due to limitations of the phone's operating system or physical condition of the device, may not be completely documented Analyze the device and resident data to identify and recover specific data that addresses the customer extraction request. Document the details of the analysis Discrepancies noted during the examination must be documented in the case record The following information if applicable, should be documented in the case record: Shielding method(s) employed Hardware(s) and software(s) (include version) used for the extraction. Record if the imaging fails and/or other recovered data discrepancies. Devices that are not supported by software may have the display content photographed through manual extraction, as described above The forensic copy and work product may be exported to the forensic server into an appropriately labeled case folder structure for temporary backup purposes. See F-SAN storage procedure section for further details QC Verifications After processing mobile devices, examiners shall always verify the accuracy of the data extracted from the device where possible: The examiner shall ensure that the identified and recovered data is an accurate depiction of what is on the submitted mobile target device through visual comparison. This comparison may be accomplished by randomly picking extracted data and comparing it to the data displayed in the mobile device. Another way to confirm an accurate data extraction is to verify that the mobile device has the same phone number from the SIM card (and/or serial #/IMEI) Limitations It may not be possible to bypass securities to obtain information from a mobile device or to utilize forensic examination software to successfully connect to the device to obtain Uncontrolled When Printed Page 4 of 5
5 intelligible, stored data. Furthermore, the device may be physically damaged, preventing connection and/or manual review of device content Currently there is no forensic product that acquires or parses all electronically stored information from every type of mobile device. Multiple forensic products and/or manual preservation (photography, video recording and/or transcription) may be necessary to document the information observed on the mobile device s display, where possible Forensic examination devices or software may not identify or recover all electronically stored information on all devices. This limitation can be identified through a manual review of identified and recovered data, unless a visual review is not possible (password lock, damaged screen, etc.) There is no HASH verification required for cell phone and portable device imaging due to the volatile nature of memory storage and due to the fact that communication channels must be established between the forensic examination device and mobile device. Therefore, some writing to the device is required to access the internal memory. Uncontrolled When Printed Page 5 of 5
This version has been archived. Find the current version at on the Current Documents page. Archived Version. Capture of Live Systems
 Scientific Working Group on Digital Evidence Capture of Live Systems Disclaimer: As a condition to the use of this document and the information contained therein, the SWGDE requests notification by e-mail
Scientific Working Group on Digital Evidence Capture of Live Systems Disclaimer: As a condition to the use of this document and the information contained therein, the SWGDE requests notification by e-mail
Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014
 Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014 INTRODUCTION The field of computer forensics has long been centered on traditional media like hard drives.
Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014 INTRODUCTION The field of computer forensics has long been centered on traditional media like hard drives.
Digital Forensics Validation, Performance Verification And Quality Control Checks. Crime Scene/Digital and Multimedia Division
 Validation, Performance Verification And Quality Control Checks 5. VALIDATION, PERFORMANCE VERIFICATION AND QUALITY CONTROL CHECKS 5.1. Purpose 5.1.1. The purpose of this procedure is to establish guidelines
Validation, Performance Verification And Quality Control Checks 5. VALIDATION, PERFORMANCE VERIFICATION AND QUALITY CONTROL CHECKS 5.1. Purpose 5.1.1. The purpose of this procedure is to establish guidelines
MOBILE DEVICE FORENSICS
 MOBILE DEVICE FORENSICS Smart phones and other handheld electronics have become an important part of our everyday lives and the ever changing technology is making these devices a major source of digital
MOBILE DEVICE FORENSICS Smart phones and other handheld electronics have become an important part of our everyday lives and the ever changing technology is making these devices a major source of digital
Digital Cameras. An evaluation of the collection, preservation and evaluation of data collected from digital
 Ronald Prine CSC 589 - Digital Forensics New Mexico Institute of Mining and Technology October 17, 2006 Digital Cameras Executive Summary An evaluation of the collection, preservation and evaluation of
Ronald Prine CSC 589 - Digital Forensics New Mexico Institute of Mining and Technology October 17, 2006 Digital Cameras Executive Summary An evaluation of the collection, preservation and evaluation of
Identity Theft Prevention Policy
 Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Android Forensics. Presented By: Mohamed Khaled. Thanks to: Ibrahim Mosaad Mohamed Shawky
 Android Forensics Presented By: Mohamed Khaled Thanks to: Ibrahim Mosaad Mohamed Shawky Agenda Mobile Forensic Process Different Mobile Forensic Scenario Acquisition Guide Challenges of Android Forensics
Android Forensics Presented By: Mohamed Khaled Thanks to: Ibrahim Mosaad Mohamed Shawky Agenda Mobile Forensic Process Different Mobile Forensic Scenario Acquisition Guide Challenges of Android Forensics
SSDD and SSDF Handset seizure Paraben * Seizure test SE K850, SE Xperia
 SSDD and SSDF Handset seizure Paraben * Seizure test SE K850, SE Xperia Small Scale Digital Device (SSDD) SSDD definition A Small Scale Digital Device is any of a variety of small form factor devices utilizing
SSDD and SSDF Handset seizure Paraben * Seizure test SE K850, SE Xperia Small Scale Digital Device (SSDD) SSDD definition A Small Scale Digital Device is any of a variety of small form factor devices utilizing
ELECTRONIC DEVICES ACCEPTABLE USE POLICY
 U.S. DEPARTMENT OF ENERGY NATIONAL NUCLEAR SECURITY ADMINISTRATION NEVADA FIELD OFFICE Approved: 12-15-2014 ELECTRONIC DEVICES ACCEPTABLE USE POLICY 1 Legend and Definitions: Symbol or Phrase Meaning The
U.S. DEPARTMENT OF ENERGY NATIONAL NUCLEAR SECURITY ADMINISTRATION NEVADA FIELD OFFICE Approved: 12-15-2014 ELECTRONIC DEVICES ACCEPTABLE USE POLICY 1 Legend and Definitions: Symbol or Phrase Meaning The
Scientific Working Group on Digital Evidence
 SWGDE Best Practices for Mobile Device Evidence Collection & Preservation, The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period
SWGDE Best Practices for Mobile Device Evidence Collection & Preservation, The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period
Incident Response Data Acquisition Guidelines for Investigation Purposes 1
 Incident Response Data Acquisition Guidelines for Investigation Purposes 1 1 Target Audience This document is aimed at general IT staff that may be in the position of being required to take action in response
Incident Response Data Acquisition Guidelines for Investigation Purposes 1 1 Target Audience This document is aimed at general IT staff that may be in the position of being required to take action in response
OXYGEN SOFTWARE OXYGEN FORENSIC KIT
 OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
OXYGEN SOFTWARE OXYGEN FORENSIC KIT
 OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
10 th National Investigations Symposium
 10 th National Investigations Symposium AVOIDING FORENSIC PITFALLS First Responders Guide to Preserving Electronic Evidence 6 November 2014 Bronwyn Barker Electronic Evidence Specialist Investigation 5
10 th National Investigations Symposium AVOIDING FORENSIC PITFALLS First Responders Guide to Preserving Electronic Evidence 6 November 2014 Bronwyn Barker Electronic Evidence Specialist Investigation 5
OXYGEN SOFTWARE OXYGEN FORENSIC KIT
 OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
OXYGEN SOFTWARE OXYGEN FORENSIC KIT Oxygen Forensic Kit complete out-of-the-box solution When to start? Immediately! Oxygen Forensic Kit is a complete set you can quickly use right out of the box. It does
Intro. This program can retrieve messages, call logs, pictures, contacts, apps, calendar events, s, passwords, deleted data, and much more.
 FAQ Intro Thank you for purchasing MOBILedit Forensic Express. This tool preforms mobile phone content extractions and is used by professionals in law enforcement, military as well as the corporate and
FAQ Intro Thank you for purchasing MOBILedit Forensic Express. This tool preforms mobile phone content extractions and is used by professionals in law enforcement, military as well as the corporate and
<Criminal Justice Agency Name> Personally Owned Device Policy. Allowed Personally Owned Device Policy
 Policy Title: Effective Date: Revision Date: Approval(s): LASO: CSO: Agency Head: Allowed Personally Owned Device Policy Every 2 years or as needed Purpose: A personally owned information system or device
Policy Title: Effective Date: Revision Date: Approval(s): LASO: CSO: Agency Head: Allowed Personally Owned Device Policy Every 2 years or as needed Purpose: A personally owned information system or device
IDENTITY THEFT PREVENTION PROGRAM
 IDENTITY THEFT PREVENTION PROGRAM COLDWELL BANKER-D ANN HARPER REALTY PROPERTY MANAGEMENT JULY 1, 2013 COLDWELL BANKER-D ANN HARPER REALTY PROPERTY MANAGEMENT, located in SAN ANTONIO, TX 78258 developed
IDENTITY THEFT PREVENTION PROGRAM COLDWELL BANKER-D ANN HARPER REALTY PROPERTY MANAGEMENT JULY 1, 2013 COLDWELL BANKER-D ANN HARPER REALTY PROPERTY MANAGEMENT, located in SAN ANTONIO, TX 78258 developed
HotSpot USER MANUAL. twitter.com/vortexcellular facebook.com/vortexcellular instagram.com/vortexcellular
 HotSpot USER MANUAL www.vortexcellular.com twitter.com/vortexcellular facebook.com/vortexcellular instagram.com/vortexcellular 1 Contents Quick User Guide... 2 1. Power On/Off... 2 2. Turn On /Off Screen...
HotSpot USER MANUAL www.vortexcellular.com twitter.com/vortexcellular facebook.com/vortexcellular instagram.com/vortexcellular 1 Contents Quick User Guide... 2 1. Power On/Off... 2 2. Turn On /Off Screen...
Guide to Computer Forensics and Investigations Fourth Edition. Chapter 2 Understanding Computer Investigations
 Guide to Computer Forensics and Investigations Fourth Edition Chapter 2 Understanding Computer Investigations Objectives Explain how to prepare a computer investigation Apply a systematic approach to an
Guide to Computer Forensics and Investigations Fourth Edition Chapter 2 Understanding Computer Investigations Objectives Explain how to prepare a computer investigation Apply a systematic approach to an
Manual Version: V1.02. User Manual Guard Viewer
 Manual Version: V1.02 User Manual Guard Viewer Notice The contents of this document are subject to change without prior notice. Updates will be added to the new version of this manual. We will readily
Manual Version: V1.02 User Manual Guard Viewer Notice The contents of this document are subject to change without prior notice. Updates will be added to the new version of this manual. We will readily
ANALYSIS AND VALIDATION
 UNIT V ANALYSIS AND VALIDATION Validating Forensics Objectives Determine what data to analyze in a computer forensics investigation Explain tools used to validate data Explain common data-hiding techniques
UNIT V ANALYSIS AND VALIDATION Validating Forensics Objectives Determine what data to analyze in a computer forensics investigation Explain tools used to validate data Explain common data-hiding techniques
TomTom GPS Device Forensics
 TomTom GPS Device Forensics Written by Ben LeMere & Andy Sayers For more information visit GPSForensics.org blemere@gpsforensics.org asayers@gpsforensics.org Introduction: The sales of portable navigation
TomTom GPS Device Forensics Written by Ben LeMere & Andy Sayers For more information visit GPSForensics.org blemere@gpsforensics.org asayers@gpsforensics.org Introduction: The sales of portable navigation
Airplane mode Android app application Back key bandwidth
 1G First-generation analog wireless telephone technology. 2G Second-generation wireless technology, the first digital generation and the first to include data services. 3G Third-generation wireless telephone
1G First-generation analog wireless telephone technology. 2G Second-generation wireless technology, the first digital generation and the first to include data services. 3G Third-generation wireless telephone
Remote Device Mounting Service
 HOW TO USE REMOTE DEVICE MOUNTING SERVICES The Remote Data Mounting Services (RDMS) lets you acquire live evidence from active and remote network computers. You can gather many types of active information
HOW TO USE REMOTE DEVICE MOUNTING SERVICES The Remote Data Mounting Services (RDMS) lets you acquire live evidence from active and remote network computers. You can gather many types of active information
Operating System Specification Mac OS X Snow Leopard (10.6.0) or higher and Windows XP (SP3) or higher
 BlackLight is a multi-platform forensic analysis tool that allows examiners to quickly and intuitively analyze digital forensic media. BlackLight is capable of analyzing data from Mac OS X computers, ios
BlackLight is a multi-platform forensic analysis tool that allows examiners to quickly and intuitively analyze digital forensic media. BlackLight is capable of analyzing data from Mac OS X computers, ios
Certified Digital Forensics Examiner
 Certified Digital Forensics Examiner ACCREDITATIONS EXAM INFORMATION The Certified Digital Forensics Examiner exam is taken online through Mile2 s Assessment and Certification System ( MACS ), which is
Certified Digital Forensics Examiner ACCREDITATIONS EXAM INFORMATION The Certified Digital Forensics Examiner exam is taken online through Mile2 s Assessment and Certification System ( MACS ), which is
DIGITAL CITIZEN TABLET FUNDAMENTALS
 DIGITAL CITIZEN TABLET FUNDAMENTALS Syllabus Version 1.0 Purpose This document details the syllabus for the Digital Citizen Tablet Fundamentals module. The syllabus describes, through learning outcomes,
DIGITAL CITIZEN TABLET FUNDAMENTALS Syllabus Version 1.0 Purpose This document details the syllabus for the Digital Citizen Tablet Fundamentals module. The syllabus describes, through learning outcomes,
GEORGIA DEPARTMENT OF CORRECTIONS Standard Operating Procedures
 GEORGIA DEPARTMENT OF CORRECTIONS Standard Operating Procedures Support Services Telecommunications Subject: Wireless Devices Revises Previous Authority: Page 1 of 5 Owens/Smith I. POLICY: A. To provide
GEORGIA DEPARTMENT OF CORRECTIONS Standard Operating Procedures Support Services Telecommunications Subject: Wireless Devices Revises Previous Authority: Page 1 of 5 Owens/Smith I. POLICY: A. To provide
Introduction to. Digital Forensics. Digital Forensics VEHICLE SOLUTIONS!
 Introduction to DIGITAL FORENSICS The use of digital devices in everyday life continues to increase as people integrate technology into their lives. It is estimated that as of 2010, there were over 5 billion
Introduction to DIGITAL FORENSICS The use of digital devices in everyday life continues to increase as people integrate technology into their lives. It is estimated that as of 2010, there were over 5 billion
Computer Forensics: Investigating Data and Image Files, 2nd Edition. Chapter 3 Forensic Investigations Using EnCase
 Computer Forensics: Investigating Data and Image Files, 2nd Edition Chapter 3 Forensic Investigations Using EnCase Objectives After completing this chapter, you should be able to: Understand evidence files
Computer Forensics: Investigating Data and Image Files, 2nd Edition Chapter 3 Forensic Investigations Using EnCase Objectives After completing this chapter, you should be able to: Understand evidence files
2. PLEASE CHECK AND COMPLETE THE FOLLOWING: 3. PLEASE SELECT THE FOLLOWING FOR YOUR BETA EXAM: 4. METHOD OF PAYMENT AWS USE ONLY
 8669 NW 36 St, #130, Miami, FL 33166-6672 (800) 443-9353, ext. 273 Fax: (305) 443-6445 CRWT (Certified Resistance Welding Technician) EXAM APPLICATION BETA TEST LAST NAME FIRST NAME MI ADDRESS APT NO.
8669 NW 36 St, #130, Miami, FL 33166-6672 (800) 443-9353, ext. 273 Fax: (305) 443-6445 CRWT (Certified Resistance Welding Technician) EXAM APPLICATION BETA TEST LAST NAME FIRST NAME MI ADDRESS APT NO.
Vendor: ECCouncil. Exam Code: EC Exam Name: Computer Hacking Forensic Investigator Exam. Version: Demo
 Vendor: ECCouncil Exam Code: EC1-349 Exam Name: Computer Hacking Forensic Investigator Exam Version: Demo QUESTION 1 What is the First Step required in preparing a computer for forensics investigation?
Vendor: ECCouncil Exam Code: EC1-349 Exam Name: Computer Hacking Forensic Investigator Exam Version: Demo QUESTION 1 What is the First Step required in preparing a computer for forensics investigation?
Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI)
 Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI) Duration: 5 days You Will Learn How To Understand how perimeter defenses work Scan and attack you own networks, without actually harming
Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI) Duration: 5 days You Will Learn How To Understand how perimeter defenses work Scan and attack you own networks, without actually harming
APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE
 APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE William Stallings F.1 TCP/IP LAYERS... 2 F.2 TCP AND UDP... 4 F.3 OPERATION OF TCP/IP... 6 F.4 TCP/IP APPLICATIONS... 10 Copyright 2014 Supplement to Computer
APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE William Stallings F.1 TCP/IP LAYERS... 2 F.2 TCP AND UDP... 4 F.3 OPERATION OF TCP/IP... 6 F.4 TCP/IP APPLICATIONS... 10 Copyright 2014 Supplement to Computer
Standards and Competencies ITS 1.0 Perform maintenance on systems and components
 Skill Performance This portion of the contest will be a series of modules through which each contestant will rotate on a fixed time schedule to troubleshoot or complete tasks with client, server, or end
Skill Performance This portion of the contest will be a series of modules through which each contestant will rotate on a fixed time schedule to troubleshoot or complete tasks with client, server, or end
Paraben s DS 7.5 Release Notes
 Paraben s DS 7.5 Release Notes Welcome to Paraben s DS Mobile Forensic Solution! DS is designed to allow investigators to acquire the data contained on mobile phones, smartphones, tablets, GPS, and PDA
Paraben s DS 7.5 Release Notes Welcome to Paraben s DS Mobile Forensic Solution! DS is designed to allow investigators to acquire the data contained on mobile phones, smartphones, tablets, GPS, and PDA
CompTIA A+ Certification: Labs. Course Outline. CompTIA A+ Certification: Labs. 07 Dec
 Course Outline CompTIA A+ Certification: 220-902 Labs 07 Dec 2018 Contents 1. Expert Instructor-Led Training 2. ADA Compliant & JAWS Compatible Platform 3. State of the Art Educator Tools 4. Award Winning
Course Outline CompTIA A+ Certification: 220-902 Labs 07 Dec 2018 Contents 1. Expert Instructor-Led Training 2. ADA Compliant & JAWS Compatible Platform 3. State of the Art Educator Tools 4. Award Winning
Guide for Minimum Qualifications and Training for a Forensic
 Guide for Minimum Qualifications and Training for a Forensic Footwear and/or Tire Tread Examiner 1. Scope 1.1 This Guide describes the minimum qualifications and training for a forensic footwear and/or
Guide for Minimum Qualifications and Training for a Forensic Footwear and/or Tire Tread Examiner 1. Scope 1.1 This Guide describes the minimum qualifications and training for a forensic footwear and/or
Video and Audio Recordings Video and audio recordings of activities continue to
 Chapter 3 Video and Audio Recordings Video and audio recordings of activities continue to become prevalent in investigations of criminal activity. Recordings include surveillance tapes recordings of criminal
Chapter 3 Video and Audio Recordings Video and audio recordings of activities continue to become prevalent in investigations of criminal activity. Recordings include surveillance tapes recordings of criminal
Mobile Forensics. Luis Rivera, Michael Zanchelli, Julio Poblete. Capstone: System Security IASP-470. Dr. John Yoon. Due 30 April, 2018
 1 Mobile Forensics Luis Rivera, Michael Zanchelli, Julio Poblete Capstone: System Security IASP-470 Dr. John Yoon Due 30 April, 2018 2 Abstract Cell Phones have become an essential part of any person s
1 Mobile Forensics Luis Rivera, Michael Zanchelli, Julio Poblete Capstone: System Security IASP-470 Dr. John Yoon Due 30 April, 2018 2 Abstract Cell Phones have become an essential part of any person s
VIEVU Solution App User Guide
 VIEVU Solution App User Guide INTRODUCTION VIEVU Solution is the next generation, fully-hosted, cloud evidence management system. This guide describes how to operate the VIEVU Solution. Additional support
VIEVU Solution App User Guide INTRODUCTION VIEVU Solution is the next generation, fully-hosted, cloud evidence management system. This guide describes how to operate the VIEVU Solution. Additional support
Digital Forensics. Also known as. General definition: Computer forensics or network forensics
 TEL2813/IS2621 Security Management James Joshi Associate Professor Lecture 3 Jan 29, 2014 Introduction ti to Digital Forensics Digital Forensics Also known as Computer forensics or network forensics General
TEL2813/IS2621 Security Management James Joshi Associate Professor Lecture 3 Jan 29, 2014 Introduction ti to Digital Forensics Digital Forensics Also known as Computer forensics or network forensics General
Source: https://articles.forensicfocus.com/2018/03/02/evidence-acquisition-using-accessdata-ftk-imager/
 by Chirath De Alwis Source: https://articles.forensicfocus.com/2018/03/02/evidence-acquisition-using-accessdata-ftk-imager/ Forensic Toolkit or FTK is a computer forensics software product made by AccessData.
by Chirath De Alwis Source: https://articles.forensicfocus.com/2018/03/02/evidence-acquisition-using-accessdata-ftk-imager/ Forensic Toolkit or FTK is a computer forensics software product made by AccessData.
Reviewing the Results of the Forensic Analysis
 CYBERSECURITY FORENSICS WORKSHOP Reviewing the Results of the Forensic Analysis Ian M Dowdeswell Incident Manager, Q-CERT 2 CYBERSECURITY FORENSICS WORKSHOP Caveats This is not an actual crime it has been
CYBERSECURITY FORENSICS WORKSHOP Reviewing the Results of the Forensic Analysis Ian M Dowdeswell Incident Manager, Q-CERT 2 CYBERSECURITY FORENSICS WORKSHOP Caveats This is not an actual crime it has been
Android Forensics: Simplifying Cell Phone Examinations
 Android Forensics: Simplifying Cell Phone Examinations Jeff Lessard, Gary Kessler 2010 Presented By: Manaf Bin Yahya Outlines Introduction Mobile Forensics Physical analysis Logical analysis CelleBrite
Android Forensics: Simplifying Cell Phone Examinations Jeff Lessard, Gary Kessler 2010 Presented By: Manaf Bin Yahya Outlines Introduction Mobile Forensics Physical analysis Logical analysis CelleBrite
COMP116 Final Project. Shuyan Guo Advisor: Ming Chow
 Digital Forensics with ios Devices COMP116 Final Project Shuyan Guo Shuyan.guo@tufts.edu Advisor: Ming Chow Abstract This project focuses on ios device forensics. The study provides a general overview
Digital Forensics with ios Devices COMP116 Final Project Shuyan Guo Shuyan.guo@tufts.edu Advisor: Ming Chow Abstract This project focuses on ios device forensics. The study provides a general overview
+Cam Quick Start Guide
 CAUTION RISK OF ELECTRIC SHOCK DO NOT OPEN CAUTION TO REDUCE THE RISK OF ELECTRIC SHOCK, DO NOT REMOVE COVER (OR BACK). NO USER SERVICEABLE PARTS INSIDE, REFER SERVICING TO QUALIFIED SERVICE PERSONNEL.
CAUTION RISK OF ELECTRIC SHOCK DO NOT OPEN CAUTION TO REDUCE THE RISK OF ELECTRIC SHOCK, DO NOT REMOVE COVER (OR BACK). NO USER SERVICEABLE PARTS INSIDE, REFER SERVICING TO QUALIFIED SERVICE PERSONNEL.
Department of Public Health O F S A N F R A N C I S C O
 PAGE 1 of 9 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
PAGE 1 of 9 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
Certified Digital Forensics Examiner
 Certified Digital Forensics Examiner Course Title: Certified Digital Forensics Examiner Duration: 5 days Class Format Options: Instructor-led classroom Live Online Training Prerequisites: A minimum of
Certified Digital Forensics Examiner Course Title: Certified Digital Forensics Examiner Duration: 5 days Class Format Options: Instructor-led classroom Live Online Training Prerequisites: A minimum of
Quick Start Guide. Paraben s SIM Card Seizure. For Authorized Distribution Only. For use with Microsoft Windows XP/Vista/7
 For Authorized Distribution Only Quick Start Guide Paraben s SIM Card Seizure For use with Microsoft Windows XP/Vista/7 Paraben s SIM Card Seizure Getting Started Guide Contact Information Product Support
For Authorized Distribution Only Quick Start Guide Paraben s SIM Card Seizure For use with Microsoft Windows XP/Vista/7 Paraben s SIM Card Seizure Getting Started Guide Contact Information Product Support
Petroleum giant in the Gulf pilot module for a RF-based PERIMETER INTRUDER TRACKING SYSTEM
 Petroleum giant in the Gulf pilot module for a RF-based PERIMETER INTRUDER TRACKING SYSTEM Monitors remote installations without security manpower Long distance RF detection and alert over 360 degrees
Petroleum giant in the Gulf pilot module for a RF-based PERIMETER INTRUDER TRACKING SYSTEM Monitors remote installations without security manpower Long distance RF detection and alert over 360 degrees
Contact Information. Contact Center Operating Hours. Other Contact Information. Contact Monday through Thursday Friday
 Contact Information Contact Center Operating Hours Contact Monday through Thursday Friday Phone: 1.801.796.0944 8 AM 5 PM Eastern Time 8 AM 3 PM Eastern Time Online chat: http://support.paraben.com 10
Contact Information Contact Center Operating Hours Contact Monday through Thursday Friday Phone: 1.801.796.0944 8 AM 5 PM Eastern Time 8 AM 3 PM Eastern Time Online chat: http://support.paraben.com 10
The Use of Technology to Enhance Investigation
 The Use of Technology to Enhance Investigation Of High Profile Corruption Cases. Centre for Socio-Legal Studies Objectives By the end of this keynote, participants will be knowledgeable on: 1. Open Source
The Use of Technology to Enhance Investigation Of High Profile Corruption Cases. Centre for Socio-Legal Studies Objectives By the end of this keynote, participants will be knowledgeable on: 1. Open Source
Collect Data, Photos, and GPS Coordinates with a Handheld Windows Tablet ARM Tablet Data Collector, Licensed as TDCx Add-In
 Collect Data, Photos, and GPS Coordinates with a Handheld Windows Tablet ARM Tablet Data Collector, Licensed as TDCx Add-In Available from Gylling Data Management, Inc. and GDM Representatives January
Collect Data, Photos, and GPS Coordinates with a Handheld Windows Tablet ARM Tablet Data Collector, Licensed as TDCx Add-In Available from Gylling Data Management, Inc. and GDM Representatives January
KillTest 䊾 䞣 催 ࢭ ད ᅌ㖦䊛 ᅌ㖦䊛 NZZV ]]] QORRZKYZ TKZ ϔᑈܡ䊏 ᮄ ࢭ
![KillTest 䊾 䞣 催 ࢭ ད ᅌ㖦䊛 ᅌ㖦䊛 NZZV ]]] QORRZKYZ TKZ ϔᑈܡ䊏 ᮄ ࢭ KillTest 䊾 䞣 催 ࢭ ད ᅌ㖦䊛 ᅌ㖦䊛 NZZV ]]] QORRZKYZ TKZ ϔᑈܡ䊏 ᮄ ࢭ](/thumbs/85/91514352.jpg) KillTest Exam : 312-49v8 Title : ECCouncil Computer Hacking Forensic Investigator (V8) Version : Demo 1 / 6 1.What is the First Step required in preparing a computer for forensics investigation? A. Do
KillTest Exam : 312-49v8 Title : ECCouncil Computer Hacking Forensic Investigator (V8) Version : Demo 1 / 6 1.What is the First Step required in preparing a computer for forensics investigation? A. Do
Information Security Incident Response Plan
 Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
How to connect to a Wi-Fi or Wireless Network
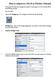 How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
Hashing Techniques for Mobile Device Forensics
 SMALL SCALE DIGITAL DEVICE FORENSICS JOURNAL, VOL. 3, NO. 1, JUNE 2009 ISSN# 1941-6164 1 Hashing Techniques for Mobile Device Forensics Shira Danker Rick Ayers Richard P. Mislan Abstract- Previous research
SMALL SCALE DIGITAL DEVICE FORENSICS JOURNAL, VOL. 3, NO. 1, JUNE 2009 ISSN# 1941-6164 1 Hashing Techniques for Mobile Device Forensics Shira Danker Rick Ayers Richard P. Mislan Abstract- Previous research
SimplySNAP Quick Install Guide
 SimplySNAP Quick Install Guide The instructions in this guide provide a basic overview for quickly getting results from a SimplySNAP lighting solution. They are intended to get you up and running quickly,
SimplySNAP Quick Install Guide The instructions in this guide provide a basic overview for quickly getting results from a SimplySNAP lighting solution. They are intended to get you up and running quickly,
Product Key. Installing the SIM Cards. Top
 QUICK START GUIDE Product Key 2 Top 3 4 5 6 1 Power Button 2 Earphone Connector 3 Front-Facing Camera 4 Speaker 5 Ambient Light Sensor 6 LED Indicator 7 Microphone 8 Menu 9 Home 10 Back 11 USB Connector
QUICK START GUIDE Product Key 2 Top 3 4 5 6 1 Power Button 2 Earphone Connector 3 Front-Facing Camera 4 Speaker 5 Ambient Light Sensor 6 LED Indicator 7 Microphone 8 Menu 9 Home 10 Back 11 USB Connector
ipad Settings Turn on icloud Backup Go to Settings, icloud. From here you can choose what items you want to have backed up.
 ipad Settings Make Passcode Complex for More Security A four digit passcode isn t as secure as a longer string of characters and numbers. To change this go to Settings and tap on Touch ID & Passcode. To
ipad Settings Make Passcode Complex for More Security A four digit passcode isn t as secure as a longer string of characters and numbers. To change this go to Settings and tap on Touch ID & Passcode. To
MODULAR CIRCUIT MONITORING SYSTEM
 MODULAR CIRCUIT MONITORING SYSTEM Contact Anord Mardix (USA) Inc. 3930 Technology Court Sandston, VA 23150 Email: us.sales@anordmardix.com Call: +1 800 228 4689 www.linkedin.com/company/anordmardix www.twitter.com/anordmardix
MODULAR CIRCUIT MONITORING SYSTEM Contact Anord Mardix (USA) Inc. 3930 Technology Court Sandston, VA 23150 Email: us.sales@anordmardix.com Call: +1 800 228 4689 www.linkedin.com/company/anordmardix www.twitter.com/anordmardix
Presenter Name. Date
 Presenter Name Date Smartphone Forensics! Henry E. Saint-Fleur Antenna NFC microchip Presenter Name Date Smartphone Forensics Background Henry Saint-Fleur! Background! Computer Science / Network Administration
Presenter Name Date Smartphone Forensics! Henry E. Saint-Fleur Antenna NFC microchip Presenter Name Date Smartphone Forensics Background Henry Saint-Fleur! Background! Computer Science / Network Administration
Chapter 9 Introduction to Networks
 Chapter 9 Introduction to Networks 9.1 Uses of a network Networks are used in many situations. We can see networks in places like offices, airports and factories. In fact we use networks in many situations
Chapter 9 Introduction to Networks 9.1 Uses of a network Networks are used in many situations. We can see networks in places like offices, airports and factories. In fact we use networks in many situations
Technical Procedure for the SAFIS/AFIT
 Technical Procedure for the SAFIS/AFIT 1.0 Purpose - This procedure describes how to operate the State Automated Fingerprint Identification System/Advanced Fingerprint Identification Technology (SAFIS/AFIT).
Technical Procedure for the SAFIS/AFIT 1.0 Purpose - This procedure describes how to operate the State Automated Fingerprint Identification System/Advanced Fingerprint Identification Technology (SAFIS/AFIT).
Running head: FTK IMAGER 1
 Running head: FTK IMAGER 1 FTK Imager Jean-Raymond Ducasse CSOL-590 June 26, 2017 Thomas Plunkett FTK IMAGER 2 FTK Imager Outline Process for Adding Individual Files & Folders as Evidence Items Although
Running head: FTK IMAGER 1 FTK Imager Jean-Raymond Ducasse CSOL-590 June 26, 2017 Thomas Plunkett FTK IMAGER 2 FTK Imager Outline Process for Adding Individual Files & Folders as Evidence Items Although
Cellebrite Digital Forensics for Legal Professionals (CDFL)
 Global forensic training Course description Level Intermediate Length Two days (14 hours) Training Track Investigative The two-day Cellebrite Digital Forensics for Legal Professionals course is designed
Global forensic training Course description Level Intermediate Length Two days (14 hours) Training Track Investigative The two-day Cellebrite Digital Forensics for Legal Professionals course is designed
Macintosh Forensic Survival Course
 Macintosh Forensic Survival Course Duration: 5 days/level Date: On demand Venue: On demand Language: English Seat availability: On demand (recommended no more than 12) Learning Objectives: Macintosh Forensic
Macintosh Forensic Survival Course Duration: 5 days/level Date: On demand Venue: On demand Language: English Seat availability: On demand (recommended no more than 12) Learning Objectives: Macintosh Forensic
ALTERNATIVE CHARGE CONTROL SYSTEM FOR MERCHANDISE DISPLAY SECURITY SYSTEM
 Technical Disclosure Commons InVue Defensive Publications Defensive Publications Series August 11, 2017 ALTERNATIVE CHARGE CONTROL SYSTEM FOR MERCHANDISE DISPLAY SECURITY SYSTEM InVue Security Products
Technical Disclosure Commons InVue Defensive Publications Defensive Publications Series August 11, 2017 ALTERNATIVE CHARGE CONTROL SYSTEM FOR MERCHANDISE DISPLAY SECURITY SYSTEM InVue Security Products
COURSE OUTLINE AND SCHEDULE: ASSIGNMENTS ARE DUE EACH MONDAY WEDNESDAY JANUARY Computing Overview
 COURSE OUTLINE AND SCHEDULE: ASSIGNMENTS ARE DUE EACH MONDAY WEDNESDAY JANUARY 22 1.0 Computing Overview 1.1 Course Introduction 1.1.1 PC Pro and A+ Certification (9:03) 1.2 Using the Simulator 1.2.1 Using
COURSE OUTLINE AND SCHEDULE: ASSIGNMENTS ARE DUE EACH MONDAY WEDNESDAY JANUARY 22 1.0 Computing Overview 1.1 Course Introduction 1.1.1 PC Pro and A+ Certification (9:03) 1.2 Using the Simulator 1.2.1 Using
CounterACT Afaria MDM Plugin
 Version 1.7.0 and Above Table of Contents About Afaria MDM Service Integration... 4 About This Plugin... 4 How It Works... 5 Continuous Query Refresh... 5 Offsite Device Management... 6 Supported Devices...
Version 1.7.0 and Above Table of Contents About Afaria MDM Service Integration... 4 About This Plugin... 4 How It Works... 5 Continuous Query Refresh... 5 Offsite Device Management... 6 Supported Devices...
CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE
 UDC 343.3/.7:340.6 Pregledni rad CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE American University in Bosnia & Herzegovina, BOSNIA & HERZEGOVINA, e-mail: edita.bajramovic@gmail.com
UDC 343.3/.7:340.6 Pregledni rad CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE American University in Bosnia & Herzegovina, BOSNIA & HERZEGOVINA, e-mail: edita.bajramovic@gmail.com
GUIDANCE ON ACCESSING THE HOUSTON METRO SECURE FTP SITE FOR DOCUMENT MANAGEMENT
 GUIDANCE ON ACCESSING THE HOUSTON METRO SECURE FTP SITE FOR DOCUMENT MANAGEMENT Documents associated with the 5307, 5337, 5339 grant programs will be stored and retrieved using Houston METRO's Secure FTP
GUIDANCE ON ACCESSING THE HOUSTON METRO SECURE FTP SITE FOR DOCUMENT MANAGEMENT Documents associated with the 5307, 5337, 5339 grant programs will be stored and retrieved using Houston METRO's Secure FTP
Product Specification SpeedAlert 18 Radar Message Sign
 SpeedAlert Radar Message Sign SpeedAlert 18 (SA18): 18 x 28 full matrix (SpeedAlert 24 (SA24) 24 x 60 full matrix also available See separate SpeedAlert 24 Spec Sheet) Size and Weight without battery 30
SpeedAlert Radar Message Sign SpeedAlert 18 (SA18): 18 x 28 full matrix (SpeedAlert 24 (SA24) 24 x 60 full matrix also available See separate SpeedAlert 24 Spec Sheet) Size and Weight without battery 30
NVR 3 Workstation for Mac OS
 NVR 3 Workstation for Mac OS User s Manual For Version 3.0.09 2015/01/27 About This Manual Target Audience This manual is intended for End Users who actually execute security tasks such as monitoring activities,
NVR 3 Workstation for Mac OS User s Manual For Version 3.0.09 2015/01/27 About This Manual Target Audience This manual is intended for End Users who actually execute security tasks such as monitoring activities,
Scientific Working Group on Digital Evidence
 SWGDE Best Practices for Digital & Multimedia Evidence Video Acquisition from The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period
SWGDE Best Practices for Digital & Multimedia Evidence Video Acquisition from The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period
Scientific Working Group on Digital Evidence
 Disclaimer: As a condition to the use of this document and the information contained therein, the SWGDE requests notification by e-mail before or contemporaneous to the introduction of this document, or
Disclaimer: As a condition to the use of this document and the information contained therein, the SWGDE requests notification by e-mail before or contemporaneous to the introduction of this document, or
Scepter III. Data Collector. Getting Started Guide. Champion Instruments,LLC
 Scepter III TM Data Collector Getting Started Guide 1. Physical Appearance GPS Antenna Earpiece Touch Panel Function Keys Camera Key Power Key Reset Button Microphone Front Mini USB socket Back Strap Holder
Scepter III TM Data Collector Getting Started Guide 1. Physical Appearance GPS Antenna Earpiece Touch Panel Function Keys Camera Key Power Key Reset Button Microphone Front Mini USB socket Back Strap Holder
CompTIA IT Fundamentals V5 (Course & Lab) Course Outline. CompTIA IT Fundamentals V5 (Course & Lab) 24 Jan
 Course Outline CompTIA IT Fundamentals V5 (Course & Lab) 24 Jan 2019 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert Instructor-Led
Course Outline CompTIA IT Fundamentals V5 (Course & Lab) 24 Jan 2019 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert Instructor-Led
MOBILedit Forensic Express
 MOBILedit Forensic Express All-in-one phone forensic tool from pioneers in the field MOBILedit Forensic Express is a phone and cloud extractor, data analyzer and report generator all in one solution. A
MOBILedit Forensic Express All-in-one phone forensic tool from pioneers in the field MOBILedit Forensic Express is a phone and cloud extractor, data analyzer and report generator all in one solution. A
Scientific Working Group on Digital Evidence
 The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period of 60 days. SWGDE encourages stakeholder participation in the preparation
The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period of 60 days. SWGDE encourages stakeholder participation in the preparation
This guide describes features that are common to most models. Some features may not be available on your tablet.
 User Guide Copyright 2014 Hewlett-Packard Development Company, L.P. Bluetooth is a trademark owned by its proprietor and used by Hewlett-Packard Company under license. Google, Google Now, Google Play,
User Guide Copyright 2014 Hewlett-Packard Development Company, L.P. Bluetooth is a trademark owned by its proprietor and used by Hewlett-Packard Company under license. Google, Google Now, Google Play,
One of the primary features of 5-Star Students is the ability to capture and store attendance data during school events.
 Conducting Events This guide will assist you with planning and conducting events using 5-Star Students Determine which events you ll track using 5-Star Students Understand requirements and options for
Conducting Events This guide will assist you with planning and conducting events using 5-Star Students Determine which events you ll track using 5-Star Students Understand requirements and options for
FAST Installation (PMRS) Box Contents
 FAST Installation (PMRS) Box Contents PMRS Unit Video/Power Adapter GPS Antenna 5V Charger u USB Cable 12V 5V Car Adapter PTZ+GPIO Cable Voice splitter GSM Antenna (Optional) LAN Cable Required Items SIM
FAST Installation (PMRS) Box Contents PMRS Unit Video/Power Adapter GPS Antenna 5V Charger u USB Cable 12V 5V Car Adapter PTZ+GPIO Cable Voice splitter GSM Antenna (Optional) LAN Cable Required Items SIM
SHIELD RADAR SPEED DISPLAY
 PRODUCT SPECIFICATIONS: SHIELD RADAR SPEED DISPLAY Shield Speed Display 3 units to cover any application Shield 12 or 12B: 12 x 6 digits, 112 LED/digit Shield 15 or 15B: 15 x 8 digits, 140 LED/digit SpeedAlert
PRODUCT SPECIFICATIONS: SHIELD RADAR SPEED DISPLAY Shield Speed Display 3 units to cover any application Shield 12 or 12B: 12 x 6 digits, 112 LED/digit Shield 15 or 15B: 15 x 8 digits, 140 LED/digit SpeedAlert
Information Security Incident Response Plan
 Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
IP Network Camera J2ME (Java) Application
 IP Network Camera J2ME (Java) Application Revision 1.0 User Manual Information provided in this manual was made as accurate as possible. If there are discrepancies among the manuals in different languages,
IP Network Camera J2ME (Java) Application Revision 1.0 User Manual Information provided in this manual was made as accurate as possible. If there are discrepancies among the manuals in different languages,
ForeScout Extended Module for VMware AirWatch MDM
 ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
Cable Testing Management System (CTMS) User Manual. Approved for Public - Unlimited Distribution
 Cable Testing Management System (CTMS) User Manual Table of Contents TABLE OF CONTENTS... 2 INTRODUCTION... 3 USING THE CABLE TESTING USER MANUAL... 3 HARDWARE AND CONNECTIONS... 3 IMPORT/EXPORT TOOL...
Cable Testing Management System (CTMS) User Manual Table of Contents TABLE OF CONTENTS... 2 INTRODUCTION... 3 USING THE CABLE TESTING USER MANUAL... 3 HARDWARE AND CONNECTIONS... 3 IMPORT/EXPORT TOOL...
NEO 4.5. User Manual
 1 NEO 4.5 User Manual Table of Contents Safety Information... 3 Appearance and Key Function... 4 Introduction... 5 Call Functions... 6 Contacts... 7 Messaging... 8 Internet Browser... 9 Bluetooth & Wi-Fi...
1 NEO 4.5 User Manual Table of Contents Safety Information... 3 Appearance and Key Function... 4 Introduction... 5 Call Functions... 6 Contacts... 7 Messaging... 8 Internet Browser... 9 Bluetooth & Wi-Fi...
CIS Business Computer Forensics and Incident Response. Lab Protocol 03: Acquisition
 CIS 8630 Business Computer Forensics and Incident Response Lab Protocol 03: Acquisition Purpose: Ensure every student has experienced imaging digital storage media, hashing digital media, transferring
CIS 8630 Business Computer Forensics and Incident Response Lab Protocol 03: Acquisition Purpose: Ensure every student has experienced imaging digital storage media, hashing digital media, transferring
Test Results for Mobile Device Acquisition Tool: Zdziarski s Method
 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 Test Results for Mobile Device Acquisition Tool: Zdziarski s Method October 2010 37 38 38 October 2010
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 Test Results for Mobile Device Acquisition Tool: Zdziarski s Method October 2010 37 38 38 October 2010
Connection Guide (for KeyMission 80)
 Connection Guide (for KeyMission 80) Table of Contents Installing the SnapBridge app... 2 Connecting the Camera and a Smart Device... 3 Image Upload and Remote Photography... 7 Troubleshooting... 9 This
Connection Guide (for KeyMission 80) Table of Contents Installing the SnapBridge app... 2 Connecting the Camera and a Smart Device... 3 Image Upload and Remote Photography... 7 Troubleshooting... 9 This
Connection Guide (for COOLPIX)
 Connection Guide (for COOLPIX) This document describes the procedure for using the SnapBridge app (Version 2.0) to establish a wireless connection between a supported camera and smart device. When you
Connection Guide (for COOLPIX) This document describes the procedure for using the SnapBridge app (Version 2.0) to establish a wireless connection between a supported camera and smart device. When you
Installing and Configuring The Edge (Server)
 Table of Contents Best Practices... 2 Obtaining the Software... 2 Software Installation... 2 Configuring the Server... 5 Operational Reminders... 6 11 October 2016 TIP-2014-021 1 Best Practices If you
Table of Contents Best Practices... 2 Obtaining the Software... 2 Software Installation... 2 Configuring the Server... 5 Operational Reminders... 6 11 October 2016 TIP-2014-021 1 Best Practices If you
Forensic Video Analysis The Ocean Systems OMNIVORE
 Forensic Video Analysis The Ocean Systems OMNIVORE Its great when a company listens and learns from users of a product in order to develop something new. dcoder was, and still is, the forensic screen capture
Forensic Video Analysis The Ocean Systems OMNIVORE Its great when a company listens and learns from users of a product in order to develop something new. dcoder was, and still is, the forensic screen capture
Upgrading the Cisco ONS CL to Release 7.0
 This document explains how to upgrade Cisco ONS 15310-CL Cisco Transport Controller (CTC) software from Release 5.x or Release 6.x to Release 7.0.x, or from Release 7.0.x to a later maintenance release
This document explains how to upgrade Cisco ONS 15310-CL Cisco Transport Controller (CTC) software from Release 5.x or Release 6.x to Release 7.0.x, or from Release 7.0.x to a later maintenance release
BC Taxi Camera Rule. Legislation Section 28(2)(a) of the Passenger Transportation Act states:
 Effective May 31, 2017 Purposes 1. Enable taxicab licensees in British Columbia to use taxi cameras for driver and passenger safety. 2. Establish privacy safeguards. 3. Establish standards and requirements
Effective May 31, 2017 Purposes 1. Enable taxicab licensees in British Columbia to use taxi cameras for driver and passenger safety. 2. Establish privacy safeguards. 3. Establish standards and requirements
ECCouncil Computer Hacking Forensic Investigator (V8)
 ECCouncil 312-49v8 ECCouncil Computer Hacking Forensic Investigator (V8) Version: 9.0 QUESTION NO: 1 ECCouncil 312-49v8 Exam What is the First Step required in preparing a computer for forensics investigation?
ECCouncil 312-49v8 ECCouncil Computer Hacking Forensic Investigator (V8) Version: 9.0 QUESTION NO: 1 ECCouncil 312-49v8 Exam What is the First Step required in preparing a computer for forensics investigation?
