How to scan DVWA with Kali Sparta
|
|
|
- Ross Jordan
- 5 years ago
- Views:
Transcription
1 How to scan DVWA with Kali Sparta Introduction The motivation for this paper is to show the user how to quickly get Sparta operational and scanning the DVWA running on a local instance. SPARTA is a python GUI application that simplifies network infrastructure penetration testing by aiding the penetration tester in the scanning and enumeration phase. It allows the tester to save time by having point-and-click access to their toolkit and by displaying all tool output in a convenient way. If less time is spent setting up commands and tools, more time can be spent focusing on analysing results. -- tools.kali.org/information-gathering/sparta Requirements If you see the following $ symbol on a command line to execute, what that means is that the command is executed as a regular user, i.e. the Ubuntu user. Ignore the leading $ and execute the rest of the command. $ command to execute as a regular user If you see a command line lead with the # symbol, then that means that the command is executed as the root user. This implies you need to elevate to the root user before running the command, e.g. with: sudo su root. # command to execute as the root user VirtualBox Go to: and download VirtualBox. The author is running on Ubuntu 17.04, so following to this URL: For Ubuntu, double click on the.deb file, i.e. virtualbox-5.2_ ubuntu-zesty_amd64.deb, and install VirtualBox on your local workstation. Clean VirtualBox Networking Run these two commands from a Terminal: VBoxManage list natnetworks VBoxManage list dhcpservers Output: NetworkName: NAT IP: Network: /24 IPv6 Enabled: No IPv6 Prefix: fd17:625c:f037:a88b::/64 DHCP Enabled: Yes Enabled: Yes loopback mappings (ipv4)
2 =2 NetworkName: NAT IP: NetworkMask: loweripaddress: upperipaddress: Enabled: Yes NetworkName: HostInterfaceNetworking-vboxnet0 IP: NetworkMask: loweripaddress: upperipaddress: Enabled: Yes NetworkName: HostInterfaceNetworking-vboxnet1 IP: NetworkMask: loweripaddress: upperipaddress: Enabled: No Now, delete ALL of the pre-installed VirtualBox networks (one at a time following the syntax below): VBoxManage natnetwork remove --netname <NetworkName_from_above> VBoxManage natnetwork remove --netname NAT # repeat as many times as necessary to delete all of them. VBoxManage dhcpserver remove --netname <DHCP_Server_NetworkName_from_above> VBoxManage dhcpserver remove --netname NAT # repeat as many times as necessary to delete all of them. Add VirtualBox Networking Now, add the new VirtualBox networks so the Kali Linux guides work. VBoxManage natnetwork add \ --netname NAT \ --network " /24" \ --enable --dhcp on VBoxManage dhcpserver add \ --netname NAT \ --ip \ --lowerip \ --upperip \ --netmask \ --enable VBoxManage hostonlyif create VBoxManage hostonlyif ipconfig vboxnet0 \ --ip \ --netmask VBoxManage dhcpserver add \ --ifname vboxnet0 \ --ip \ --lowerip \ --upperip \ --netmask VBoxManage dhcpserver modify \ --ifname vboxnet0 \ --enable
3 Vagrant Go to: follow the appropriate link to your OS and 32 or 64 bit version representing your local workstation. Download. For Ubuntu, double click on the.deb file, i.e. vagrant_2.0.1_x86_64.deb, and install Vagrant on your local system. Kali Linux The author highly recommends to create a directory structure that is easy to navigate and find your code. As an example, you could use something similar to: ${HOME/Source_Code/Education/vagrant-machines/kali-linux-vm/ Go ahead and make this structure with the following command (inside a Terminal): $ mkdir p ${HOME/Source_Code/Education/vagrant-machines/kali-linux-vm/ Inside of the kali-linux-vm directory, populate a new file with the exact name, Vagrantfile. Case matters, uppercase the V. Vagrantfile: # -*- mode: ruby -*- # vi: set ft=ruby : # Vagrantfile API/syntax version. VAGRANTFILE_API_VERSION = "2" Vagrant.configure(VAGRANTFILE_API_VERSION) do config config.vm.box = "Sliim/kali amd64" config.vm.box_version = "1" # For Linux systems with the Wireless network, uncomment the line: config.vm.network "public_network", bridge: "wlo1", auto_config: true # For macbook/osx systems, uncomment the line: #config.vm.network "public_network", bridge: "en0: Wi-Fi (AirPort)", auto_config: true config.vm.hostname = "kali-linux-vagrant" config.vm.provider "virtualbox" do vb vb.memory = "4096" vb.cpus = "3" vb.gui = true vb.customize ["modifyvm", :id, "--cpuexecutioncap", "95"] vb.customize ["modifyvm", :id, "--vram", "32"] vb.customize ["modifyvm", :id, "--accelerate3d", "on"] vb.customize ["modifyvm", :id, "--ostype", "Debian_64"] vb.customize ["modifyvm", :id, "--boot1", "dvd"] vb.customize ["modifyvm", :id, "--boot2", "disk"] vb.customize ["modifyvm", :id, "--audio", "none"] vb.customize ["modifyvm", :id, "--clipboard", "hosttoguest"] vb.customize ["modifyvm", :id, "--draganddrop", "hosttoguest"] vb.customize ["modifyvm", :id, "--paravirtprovider", "kvm"] end end
4 Save and write this file. From a Terminal, change directory to: $ cd ${HOME/Source_Code/Education/vagrant-machines/kali-linux-vm/ Then run (inside the directory kali-linux-vm): $ vagrant up This will download the appropriate image and start the virtual machine. Once running, through the VirtuaBox GUI, login as root. Password is toor, root backwards. Edit the following file: /etc/ssh/sshd_config And change the line: #PermitRootLogin prothibit-password To: PermitRootLogin yes Then restart the ssh daemon: # kill HUP $(pgrep sshd) Notice, you are on a Bridged adapter, this will open the instance to allow root to ssh in with the most unsecure password in the world. Only make this change (allowing root to login via SSH) if you require root SSH access. You can change the root user s password, which is highly recommended. Damn Vulnerable Web Application (DVWA) Go ahead and make this structure with the following command (inside a Terminal): $ mkdir p ${HOME/Source_Code/Education/vagrant-machines/dvwa-linux-vm/ Inside of the dvwa-linux-vm directory, populate a new file with the exact name, Vagrantfile. Case matters, uppercase the V. Vagrantfile: # # setup local instance of Damn Vulnerable Web Application (DVWA): # # Vagrantfile API/syntax version. Don't touch unless you know what you're doing! VAGRANTFILE_API_VERSION = "2" Vagrant.configure(VAGRANTFILE_API_VERSION) do config # For Linux systems with the Wireless network, uncomment the line: config.vm.network "public_network", bridge: "wlo1", auto_config: true # For macbook/osx systems, uncomment the line: #config.vm.network "public_network", bridge: "en0: Wi-Fi (AirPort)", auto_config: true
5 # uncomment the next line for Macbook/OSx systems, wireless : # config.vm.network "public_network", bridge: "en0: Wi-Fi (AirPort)", auto_config: true config.vm.provision :shell, path: "bootstrap.sh" config.vm.hostname = "dvwa" config.vm.provider "virtualbox" do vb vb.memory = "1024" vb.cpus = "2" vb.gui = false vb.customize ["modifyvm", :id, "--cpuexecutioncap", "95"] vb.customize ["modifyvm", :id, "--vram", "32"] vb.customize ["modifyvm", :id, "--accelerate3d", "on"] vb.customize ["modifyvm", :id, "--ostype", "Ubuntu_64"] vb.customize ["modifyvm", :id, "--boot1", "dvd"] vb.customize ["modifyvm", :id, "--boot2", "disk"] vb.customize ["modifyvm", :id, "--audio", "none"] vb.customize ["modifyvm", :id, "--clipboard", "hosttoguest"] vb.customize ["modifyvm", :id, "--draganddrop", "hosttoguest"] vb.customize ["modifyvm", :id, "--paravirtprovider", "kvm"] end end Save and write this file. Inside of the dvwa-linux-vm directory, populate a new file with the exact name, bootstrap.sh. Case matters, all lowercase. bootstrap.sh (include the shebang in your file, the #!/usr/bin/env bash): #!/usr/bin/env bash PHP_FPM_PATH_INI='/etc/php/7.0/fpm/php.ini' PHP_FPM_POOL_CONF='/etc/php/7.0/fpm/pool.d/ MYSQL_ROOT_PW='Assword12345' MYSQL_dvwa_user='dvwa_root' MYSQL_dvwa_password='sunshine' DVWA_admin_password='admin' recaptcha_public_key='u8392ihj32kl8hujalkshuil32' recaptcha_private_key='89ry lih32ilj32' install_base() { add-apt-repository -y ppa:nginx/stable sudo apt-get update sudo apt-get dist-upgrade -y sudo apt-get install -y nginx mariadb-server mariadb-client php php-common php-cgi php-fpm php-gd php-cli php-pear php-mcrypt php-mysql php-gd git vim config_mysql(){ mysqladmin -u root password "${MYSQL_ROOT_PW" # Config the mysql config file for root so it doesn't prompt for password. # Also sets pw in plain text for easy access. # Don't forget to change the password here!! cat <<EOF > /root/.my.cnf [client] user="root" password="${mysql_root_pw" EOF mysql -BNe "drop database if exists dvwa;" mysql -BNe "CREATE DATABASE dvwa;" mysql -BNe "GRANT ALL ON *.* TO '"${MYSQL_dvwa_user"'@'localhost' IDENTIFIED BY '"${MYSQL_dvwa_password"';" service mysql restart
6 config_php(){ ##Config PHP FPM INI to disable some security settings sed -i 's/^;cgi.fix_pathinfo.*$/cgi.fix_pathinfo = 0/g' ${PHP_FPM_PATH_INI sed -i 's/allow_url_include = Off/allow_url_include = On/g' ${PHP_FPM_PATH_INI sed -i 's/allow_url_fopen = Off/allow_url_fopen = On/g' ${PHP_FPM_PATH_INI sed -i 's/safe_mode = On/safe_mode = Off/g' ${PHP_FPM_PATH_INI echo "magic_quotes_gpc = Off" >> ${PHP_FPM_PATH_INI sed -i 's/display_errors = Off/display_errors = On/g' ${PHP_FPM_PATH_INI ##explicitly set pool options (these are defaults in ubuntu so i'm commenting them out. If they are not defaults for you try uncommenting these #sed -i 's/^;security.limit_extensions.*$/security.limit_extensions =.php.php3.php4.php5.php7/g' /etc/php/7.0/fpm/pool.d/ #sed -i 's/^listen.owner.*$/listen.owner = www-data/g' /etc/php/7.0/fpm/pool.d/ #sed -i 's/^listen.group.*$/listen.group = www-data/g' /etc/php/7.0/fpm/pool.d/ #sed -i 's/^;listen.mode.*$/listen.mode = 0660/g' /etc/php/7.0/fpm/pool.d/ systemctl restart php7.0-fpm config_nginx(){ cat << 'EOF' > /etc/nginx/sites-enabled/default server { listen 80; root /var/www/html; index index.php index.html index.htm; #server_name localhost location "/" { index index.php index.html index.htm; #try_files $uri $uri/ =404; EOF location ~ \.php$ { include /etc/nginx/fastcgi_params; fastcgi_pass unix:/var/run/php/php7.0-fpm.sock; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $request_filename; systemctl restart nginx install_dvwa(){ if [[! -d "/var/www/html" ]]; then mkdir -p /var/www; ln -s /usr/share/nginx/html /var/www/html; chown -R www-data. /var/www/html; fi cd /var/www/html rm -rf /var/www/html/.[!.]* rm -rf /var/www/html/* git clone chown -R www-data../ cp config/config.inc.php.dist config/config.inc.php ### chmod uploads and log file to be writable by nobody
7 chmod 777./hackable/uploads/ chmod 777./external/phpids/0.6/lib/IDS/tmp/phpids_log.txt ## change the values in the config to match our setup (these are what you need to update! sed -i '/db_user/ s/root/'${mysql_dvwa_user'/' /var/www/html/config/config.inc.php sed -i '/db_password/ /var/www/html/config/config.inc.php sed -i "/recaptcha_public_key/ s/''/'"${recaptcha_public_key"'/" /var/www/html/config/config.inc.php sed -i "/recaptcha_private_key/ s/''/'"${recaptcha_private_key"'/" /var/www/html/config/config.inc.php update_mysql_user_pws(){ ## The mysql passwords are set via /usr/share/nginx/html/dvwa/includes/dbms/mysql.php. # If you edit this every time they are reset it will reset to those. # Otherwise you can do a sql update statement to update them all (they are just md5's of the string. # The issue is the users table doesn't get created until you click that button T_T to init. #mysql -BNe "UPDATE dvwa.users SET password = md5('your_mysql_pw_here') WHERE user = 'admin';" #mysql -BNe "UPDATE dvwa.users SET password = md5('your_mysql_pw_here') WHERE user = 'gordonb';" #mysql -BNe "UPDATE dvwa.users SET password = md5('your_mysql_pw_here') WHERE user = '1337';" #mysql -BNe "UPDATE dvwa.users SET password = md5('your_mysql_pw_here') WHERE user = 'pablo';" #mysql -BNe "UPDATE dvwa.users SET password = md5('your_mysql_pw_here') WHERE user = 'smithy';" sed -i '/admin/ s/password/'${dvwa_admin_password'/g' /var/www/html/dvwa/includes/dbms/mysql.php sed -i '/gordonb/ s/abc123/'${dvwa_admin_password'/g' /var/www/html/dvwa/includes/dbms/mysql.php sed -i '/1337/ s/charley/'${dvwa_admin_password'/g' /var/www/html/dvwa/includes/dbms/mysql.php sed -i '/pablo/ s/letmein/'${dvwa_admin_password'/g' /var/www/html/dvwa/includes/dbms/mysql.php sed -i '/smithy/ s/password/'${dvwa_admin_password'/g' /var/www/html/dvwa/includes/dbms/mysql.php install_base config_mysql install_dvwa update_mysql_user_pws config_php config_nginx Save and write this file. From a Terminal, change directory to: $ cd ${HOME/Source_Code/Education/vagrant-machines/dvwa-linux-vm/ Then run (inside the directory dvwa-linux-vm): $ vagrant up You will need the IP address from the new DVWA virtual machine. Login with: $ vagrant ssh Then run: $ ip a
8 Choose the second network adapter, it should look like: ip a 1: lo: <LOOPBACK,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN group default qlen 1 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet /8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 02:53:17:3c:de:80 brd ff:ff:ff:ff:ff:ff inet /24 brd scope global enp0s3 valid_lft forever preferred_lft forever inet6 fe80::53:17ff:fe3c:de80/64 scope link valid_lft forever preferred_lft forever 3: enp0s8: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link/ether 08:00:27:f0:77:2d brd ff:ff:ff:ff:ff:ff inet /24 brd scope global enp0s8 valid_lft forever preferred_lft forever inet6 fe80::a00:27ff:fef0:772d/64 scope link valid_lft forever preferred_lft forever The author s home wireless network uses /24 as the network range. Therefore, the adapter, enp0s8 is what he is looking for. The IP to use as a target is Write down your value. Sparta (Kali Linux version, Beta) First launch both Vagrant boxes for Kali-Linux and DVWA. Then log into Kali-Linux with username: root and password:toor.
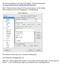
9 Next, from the upper menu, Application, open and go to 01 Information Gathering, and select Sparta. Some
10 Above, in Hosts, click where it says, Click here, which will bring up the above box, type in your target IP or range. Here we want to target single instance. Then click on Add to Scope button. Above, we see TCP ports 22 and 80 open. Right-Click on the line with port 80, then select Send to Brute.
11 Uncheck the box with Exit on first valid, then change the method from http-head to http-get. Now change the radio buttons to Username list and Password list. The author recommends using the same lists as from the previous lab utilizing Hydra with Kali Linux. Now click on Run. Above, we see the scan in progress with results of username and password combinations that worked. On an older laptop, this will take a very long time to finish the brute force attack. However, on a newer MacBook, model a1398, the same exact scan took less than 2 minutes to complete, using the same password_list.txt file. You can right click in the log on any line and instruct the command to be killed.
12 Conclusion By following this guide, the user has installed VirtualBox, Vagrant, Kali-Linux, DVWA and ran a successful attack with Sparta against DVWA. All isolated on the local system. What s beautiful about Sparta is that it is a wrapper for nmap, hydra, nikto and many other tools. Features (from their homepage): Run nmap from SPARTA or import nmap XML output. Transparent staged nmap: get results quickly and achieve thorough coverage. Configurable context menu for each service. You can configure what to run on discovered services. Any tool that can be run from a terminal, can be run from SPARTA. You can run any script or tool on a service across all the hosts in scope, just with a click of the mouse. Define automated tasks for services (ie. Run nikto on every HTTP service, or sslscan on every ssl service). Default credentials check for most common services. Of course, this can also be configured to run automatically. Identify password reuse on the tested infrastructure. If any usernames/passwords are found by Hydra they are stored in internal wordlists which can then be used on other targets in the same network (breaking news: sysadmins reuse passwords). Ability to mark hosts that you have already worked on so that you don t waste time looking at them again. Website screenshot taker so that you don t waste time on less interesting web servers. Sparta goes through and simplifies the coordination between these various tools and makes it easy to get to the later stage of having working credentials to get into the remote target. Make sure you use this tool with complete knowledge of the target you are attacking and the written legal permission to use this tool on any networks other than isolated on your laptop. You ve been warned.
How to perform a security assessment with Paros Proxy using Kali Linux
 How to perform a security assessment with Paros Proxy using Kali Linux Introduction Paros Proxy is a security and vulnerability testing tool. Paros can be used to spider/crawl an entire site (URL), and
How to perform a security assessment with Paros Proxy using Kali Linux Introduction Paros Proxy is a security and vulnerability testing tool. Paros can be used to spider/crawl an entire site (URL), and
How to scan DVWA with the Free edition of Burp Suite
 How to scan DVWA with the Free edition of Burp Suite Introduction The motivation behind this paper is to have a working reference model for scanning any site with the free edition of Burp Suite. I am using
How to scan DVWA with the Free edition of Burp Suite Introduction The motivation behind this paper is to have a working reference model for scanning any site with the free edition of Burp Suite. I am using
How to scan web sites with Faraday IDE on Kali Linux
 How to scan web sites with Faraday IDE on Kali Linux Introduction The motivation for this paper is to show the user how to quickly get Kali Linux up and running, along with Damn Vulnerable Web Application
How to scan web sites with Faraday IDE on Kali Linux Introduction The motivation for this paper is to show the user how to quickly get Kali Linux up and running, along with Damn Vulnerable Web Application
How to securely deploy Elasticsearch 6 with TLS certificates from Puppet 6.
 How to securely deploy Elasticsearch 6 with TLS certificates from Puppet 6. Introduction The motivation for this paper is to guide the reader through the accurate steps to quickly deploy Elasticsearch
How to securely deploy Elasticsearch 6 with TLS certificates from Puppet 6. Introduction The motivation for this paper is to guide the reader through the accurate steps to quickly deploy Elasticsearch
How to securely isolate Damn Vulnerable Linux with VirtualBox
 How to securely isolate Damn Vulnerable Linux with VirtualBox Motivation I have this vision of going through and testing software inside of a closed lab that allows me to understand exploits and vulnerabilities
How to securely isolate Damn Vulnerable Linux with VirtualBox Motivation I have this vision of going through and testing software inside of a closed lab that allows me to understand exploits and vulnerabilities
OpenFlow Configuration Lab
 APNIC SDN Workshop Lab OpenFlow Configuration Lab Objective: As part of this hands-on module, you will be installing the Mininet network emulator on your PC. You will then configure a standalone OpenFlow
APNIC SDN Workshop Lab OpenFlow Configuration Lab Objective: As part of this hands-on module, you will be installing the Mininet network emulator on your PC. You will then configure a standalone OpenFlow
Module 2 OpenFlow Configuration Lab
 APNIC SDN Workshop Lab Module 2 OpenFlow Configuration Lab Objective: As part of this hands-on module, you will be installing the Mininet network emulator on your PC. You will then configure a standalone
APNIC SDN Workshop Lab Module 2 OpenFlow Configuration Lab Objective: As part of this hands-on module, you will be installing the Mininet network emulator on your PC. You will then configure a standalone
Safari O Reilly CLASS PREPARATION
 CLASS PREPARATION Building Distributed Pipelines for Data Science Using Kafka, Spark, and Cassandra Table of contents Environment 1 Prerequisites 1 Import the Virtual Machine 3 If you are stuck in Virtual
CLASS PREPARATION Building Distributed Pipelines for Data Science Using Kafka, Spark, and Cassandra Table of contents Environment 1 Prerequisites 1 Import the Virtual Machine 3 If you are stuck in Virtual
Installing and Using Docker Toolbox for Mac OSX and Windows
 Installing and Using Docker Toolbox for Mac OSX and Windows One of the most compelling reasons to run Docker on your local machine is the speed at which you can deploy and build lab environments. As a
Installing and Using Docker Toolbox for Mac OSX and Windows One of the most compelling reasons to run Docker on your local machine is the speed at which you can deploy and build lab environments. As a
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability.
 CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
Quick Start Guide for Vmware. Version 2.5 Vmware vsphere Instance
 Quick Start Guide for Vmware Version 2.5 Vmware vsphere Instance CONTENTS 1. Introduction 1.1 Running Gemini appliance on Vmware vsphere 1.1.1 Supported Versions 1.1.2 System Requirement 1.1.3 Note on
Quick Start Guide for Vmware Version 2.5 Vmware vsphere Instance CONTENTS 1. Introduction 1.1 Running Gemini appliance on Vmware vsphere 1.1.1 Supported Versions 1.1.2 System Requirement 1.1.3 Note on
Seccomp, network and namespaces. Francesco Tornieri <francesco.tornieri AT kiratech.it>
 Seccomp, network and namespaces Francesco Tornieri VM vs Container 2 Namespaces ecc 3 Namespaces ecc man namespaces: A namespaces wraps a global system resource in a
Seccomp, network and namespaces Francesco Tornieri VM vs Container 2 Namespaces ecc 3 Namespaces ecc man namespaces: A namespaces wraps a global system resource in a
We want to install putty, an ssh client on the laptops. In the web browser goto:
 We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
L.A.M.P. Stack Part I
 L.A.M.P. Stack Part I By George Beatty and Matt Frantz This lab will cover the basic installation and some configuration of a LAMP stack on a Ubuntu virtual box. Students will download and install the
L.A.M.P. Stack Part I By George Beatty and Matt Frantz This lab will cover the basic installation and some configuration of a LAMP stack on a Ubuntu virtual box. Students will download and install the
How To Start Mysql Using Linux Command Line Client In Ubuntu
 How To Start Mysql Using Linux Command Line Client In Ubuntu Step One: Install MySQL Client On Debian, Ubuntu or Linux Mint: Before you start typing commands at the MySQL prompt, remember that each In
How To Start Mysql Using Linux Command Line Client In Ubuntu Step One: Install MySQL Client On Debian, Ubuntu or Linux Mint: Before you start typing commands at the MySQL prompt, remember that each In
TELE3119 Trusted Networks Lab 1(a),(b) Sniffing wireless traffic
 TELE3119 Trusted Networks Lab 1(a),(b) Sniffing wireless traffic [10 points, Due Week 5] Part (a) Objective: The objective of this exercise is to setup an infrastructure for capturing the network traffic
TELE3119 Trusted Networks Lab 1(a),(b) Sniffing wireless traffic [10 points, Due Week 5] Part (a) Objective: The objective of this exercise is to setup an infrastructure for capturing the network traffic
CS 410/510: Web Security X1: Labs Setup WFP1, WFP2, and Kali VMs on Google Cloud
 CS 410/510: Web Security X1: Labs Setup WFP1, WFP2, and Kali VMs on Google Cloud Go to Google Cloud Console => Compute Engine => VM instances => Create Instance For the Boot Disk, click "Change", then
CS 410/510: Web Security X1: Labs Setup WFP1, WFP2, and Kali VMs on Google Cloud Go to Google Cloud Console => Compute Engine => VM instances => Create Instance For the Boot Disk, click "Change", then
OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE. In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses:
 OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE VirtualBox Install VirtualBox In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses: 192.168.1.2/24 192.168.2.2/24 192.168.3.2/24
OPENSTACK CLOUD RUNNING IN A VIRTUAL MACHINE VirtualBox Install VirtualBox In Preferences, add 3 Host-only Ethernet Adapters with the following IP Addresses: 192.168.1.2/24 192.168.2.2/24 192.168.3.2/24
Docker Networking: From One to Many. Don Mills
 Docker Networking: From One to Many Don Mills What we are going to talk about Overview of traditional Docker networking Some demonstrations Questions New Docker features Some more demonstrations Questions
Docker Networking: From One to Many Don Mills What we are going to talk about Overview of traditional Docker networking Some demonstrations Questions New Docker features Some more demonstrations Questions
Communication protocols and services
 This chapter describes various protocols and that may be enabled on Modberry. SSH Connection SSH service is started up on boot and already preinstalled and configured. You may access your device through
This chapter describes various protocols and that may be enabled on Modberry. SSH Connection SSH service is started up on boot and already preinstalled and configured. You may access your device through
Setting up a virtual testbed for ESGF
 Setting up a virtual testbed for ESGF Author: Prashanth Dwarakanath, NSC, Sweden Version: 1.04 October 23, 2018 i 1 About this document............................... 1 2 Prerequisites....................................
Setting up a virtual testbed for ESGF Author: Prashanth Dwarakanath, NSC, Sweden Version: 1.04 October 23, 2018 i 1 About this document............................... 1 2 Prerequisites....................................
Red Hat Satellite 6.2
 Red Hat Satellite 6.2 Provisioning Guide A guide to provisioning physical and virtual hosts on Red Hat Satellite Servers. Edition 1.0 Last Updated: 2018-05-01 Red Hat Satellite 6.2 Provisioning Guide
Red Hat Satellite 6.2 Provisioning Guide A guide to provisioning physical and virtual hosts on Red Hat Satellite Servers. Edition 1.0 Last Updated: 2018-05-01 Red Hat Satellite 6.2 Provisioning Guide
TangeloHub Documentation
 TangeloHub Documentation Release None Kitware, Inc. September 21, 2015 Contents 1 User s Guide 3 1.1 Managing Data.............................................. 3 1.2 Running an Analysis...........................................
TangeloHub Documentation Release None Kitware, Inc. September 21, 2015 Contents 1 User s Guide 3 1.1 Managing Data.............................................. 3 1.2 Running an Analysis...........................................
Installing MediaWiki using VirtualBox
 Installing MediaWiki using VirtualBox Install VirtualBox with your package manager or download it from the https://www.virtualbox.org/ website and follow the installation instructions. Load an Image For
Installing MediaWiki using VirtualBox Install VirtualBox with your package manager or download it from the https://www.virtualbox.org/ website and follow the installation instructions. Load an Image For
Automatic Creation of a Virtual Network with VBoxManage [1]
![Automatic Creation of a Virtual Network with VBoxManage [1] Automatic Creation of a Virtual Network with VBoxManage [1]](/thumbs/78/77924363.jpg) Automatic Creation of a Virtual Network with V... 1 Automatic Creation of a Virtual Network with VBoxManage [1] Submitted by Steve [2] on Wed, 18/09/2013-5:46pm I am using VirtualBox to create multiple
Automatic Creation of a Virtual Network with V... 1 Automatic Creation of a Virtual Network with VBoxManage [1] Submitted by Steve [2] on Wed, 18/09/2013-5:46pm I am using VirtualBox to create multiple
1. Download the latest version of the Kali Linux 64 bit ISO image:
 Ronny Bull Pen Testing Talk Pre-Lab: Virtual Machine Setup Lab Objectives: Configure VirtualBox to support Kali Linux LiveCD and Metasploitable 2 Configure Virtualbox networking to support both NAT Network
Ronny Bull Pen Testing Talk Pre-Lab: Virtual Machine Setup Lab Objectives: Configure VirtualBox to support Kali Linux LiveCD and Metasploitable 2 Configure Virtualbox networking to support both NAT Network
installing Linux Paul Cobbaut
 installing Linux Paul Cobbaut installing Linux Paul Cobbaut lt-2.0 Publication date Wed 12 Nov 2014 03:59:02 PM CET Table of Contents 1. installing Debian 8... 1 1.1. Debian... 2 1.2. Downloading... 2
installing Linux Paul Cobbaut installing Linux Paul Cobbaut lt-2.0 Publication date Wed 12 Nov 2014 03:59:02 PM CET Table of Contents 1. installing Debian 8... 1 1.1. Debian... 2 1.2. Downloading... 2
Ubuntu Set Static Ip Address Command Line
 Ubuntu 10.04 Set Static Ip Address Command Line Check to see if everything works, Mount at startup, Automounter, Static Mounts These have to be IP addresses because of a limitation in portmap (it doesn't
Ubuntu 10.04 Set Static Ip Address Command Line Check to see if everything works, Mount at startup, Automounter, Static Mounts These have to be IP addresses because of a limitation in portmap (it doesn't
Deploy and Secure an Internet Facing Application with the Barracuda Web Application Firewall in Amazon Web Services
 Deploy and Secure an Internet Facing Application with the in Amazon Web In this lab, you will deploy an unsecure web application into Amazon Web (AWS), and then secure the application using the. To create
Deploy and Secure an Internet Facing Application with the in Amazon Web In this lab, you will deploy an unsecure web application into Amazon Web (AWS), and then secure the application using the. To create
Installing PHP on Windows 10 Bash and Starting a Local Server
 Installing PHP on Windows 10 Bash and Starting a Local Server Bash on Ubuntu/Windows is a way to use a command line to run all kinds of programs (including git!). But we ll want a Bash terminal to run
Installing PHP on Windows 10 Bash and Starting a Local Server Bash on Ubuntu/Windows is a way to use a command line to run all kinds of programs (including git!). But we ll want a Bash terminal to run
Software Installation Manual
 Software Installation Manual LEMA Course Scheduling System Team 12 Name Primary Role Secondary Role David Wiggins Project Manager Developer Aakash Shah Prototyper Developer Kushalpreet Kaur Developer Developer
Software Installation Manual LEMA Course Scheduling System Team 12 Name Primary Role Secondary Role David Wiggins Project Manager Developer Aakash Shah Prototyper Developer Kushalpreet Kaur Developer Developer
Experimenting Internetworking using Linux Virtual Machines Part I
 Experimenting Internetworking using Linux Virtual Machines Part I Hui Chen Previous Release on October 27, 2014 Lastly revised on November 4, 2015 Revision: Copyright c 2016. Hui Chen
Experimenting Internetworking using Linux Virtual Machines Part I Hui Chen Previous Release on October 27, 2014 Lastly revised on November 4, 2015 Revision: Copyright c 2016. Hui Chen
Red Hat Satellite 6.3
 Red Hat Satellite 6.3 Provisioning Guide A guide to provisioning physical and virtual hosts on Red Hat Satellite Servers. Edition 1.0 Last Updated: 2018-09-06 Red Hat Satellite 6.3 Provisioning Guide
Red Hat Satellite 6.3 Provisioning Guide A guide to provisioning physical and virtual hosts on Red Hat Satellite Servers. Edition 1.0 Last Updated: 2018-09-06 Red Hat Satellite 6.3 Provisioning Guide
Infrastructure at your Service. Oracle over Docker. Oracle over Docker
 Infrastructure at your Service. Infrastructure at your Service. About me David Hueber COO Principal Consultant Mobile +41 79 963 43 68 david-.hueber@dbi-services.com www.dbi-services.com Page 2 18.11.2015
Infrastructure at your Service. Infrastructure at your Service. About me David Hueber COO Principal Consultant Mobile +41 79 963 43 68 david-.hueber@dbi-services.com www.dbi-services.com Page 2 18.11.2015
Contents in Detail. Acknowledgments
 Acknowledgments xix Introduction What s in This Book... xxii What Is Ethical Hacking?... xxiii Penetration Testing... xxiii Military and Espionage... xxiii Why Hackers Use Linux... xxiv Linux Is Open Source....
Acknowledgments xix Introduction What s in This Book... xxii What Is Ethical Hacking?... xxiii Penetration Testing... xxiii Military and Espionage... xxiii Why Hackers Use Linux... xxiv Linux Is Open Source....
Linux Systems Administration Getting Started with Linux
 Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Stand-by server iprotect 8.03
 Stand-by server iprotect 8.03 o Functional Description o Implementation Guide lines o Cold- and Warm stand-by o Automatic fail-over Publication May, 2016 Keyprocessor BV Paasheuvelweg 20 1105BJ Amsterdam
Stand-by server iprotect 8.03 o Functional Description o Implementation Guide lines o Cold- and Warm stand-by o Automatic fail-over Publication May, 2016 Keyprocessor BV Paasheuvelweg 20 1105BJ Amsterdam
TELE3119 Trusted Networks Lab 1 (a), (b) Sniffing wireless traffic
 TELE3119 Trusted Networks Lab 1 (a), (b) Sniffing wireless traffic [10 points, Due Week 5] Part (a) Objective: The objective of this exercise is to setup an infrastructure for capturing the network traffic
TELE3119 Trusted Networks Lab 1 (a), (b) Sniffing wireless traffic [10 points, Due Week 5] Part (a) Objective: The objective of this exercise is to setup an infrastructure for capturing the network traffic
The instructions in this document are applicable to personal computers running the following Operating Systems:
 Preliminary Notes The instructions in this document are applicable to personal computers running the following Operating Systems: Microsoft Windows from version 7 up to 10 Apple Mac OS X from versions
Preliminary Notes The instructions in this document are applicable to personal computers running the following Operating Systems: Microsoft Windows from version 7 up to 10 Apple Mac OS X from versions
Installation Manual InfraManage.NET Installation Instructions for Ubuntu
 Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Bitnami Ruby for Huawei Enterprise Cloud
 Bitnami Ruby for Huawei Enterprise Cloud Description Bitnami Ruby Stack provides a complete development environment for Ruby on Rails that can be deployed in one click. It includes most popular components
Bitnami Ruby for Huawei Enterprise Cloud Description Bitnami Ruby Stack provides a complete development environment for Ruby on Rails that can be deployed in one click. It includes most popular components
Kollaborate Server. Installation Guide
 1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house on your own server and storage.
1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house on your own server and storage.
Downloading and installing Db2 Developer Community Edition on Ubuntu Linux Roger E. Sanders Yujing Ke Published on October 24, 2018
 Downloading and installing Db2 Developer Community Edition on Ubuntu Linux Roger E. Sanders Yujing Ke Published on October 24, 2018 This guide will help you download and install IBM Db2 software, Data
Downloading and installing Db2 Developer Community Edition on Ubuntu Linux Roger E. Sanders Yujing Ke Published on October 24, 2018 This guide will help you download and install IBM Db2 software, Data
About Backup and Restore, on page 1 Supported Backup and Restore Procedures, on page 3
 About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
Bitnami MariaDB for Huawei Enterprise Cloud
 Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
gosint Documentation Release Cisco CSIRT
 gosint Documentation Release 0.0.1 Cisco CSIRT Nov 20, 2017 Contents 1 Installation 3 1.1 Quick Installation............................................ 3 1.2 Manual Installation............................................
gosint Documentation Release 0.0.1 Cisco CSIRT Nov 20, 2017 Contents 1 Installation 3 1.1 Quick Installation............................................ 3 1.2 Manual Installation............................................
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades Q2
 Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Verteego VDS Documentation
 Verteego VDS Documentation Release 1.0 Verteego May 31, 2017 Installation 1 Getting started 3 2 Ansible 5 2.1 1. Install Ansible............................................. 5 2.2 2. Clone installation
Verteego VDS Documentation Release 1.0 Verteego May 31, 2017 Installation 1 Getting started 3 2 Ansible 5 2.1 1. Install Ansible............................................. 5 2.2 2. Clone installation
Cumulus VX for a POC in pre-sales. Using Cumulus VX to create a virtual POC environment.
 Cumulus VX for a POC in pre-sales Using Cumulus VX to create a virtual POC environment. Contents Contents Cumulus VX in pre-sales engagement Introduction Cumulus VX in a POC Intended Audience Installation
Cumulus VX for a POC in pre-sales Using Cumulus VX to create a virtual POC environment. Contents Contents Cumulus VX in pre-sales engagement Introduction Cumulus VX in a POC Intended Audience Installation
Linux Essentials Objectives Topics:
 Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Linux Essentials Linux Essentials is a professional development certificate program that covers basic knowledge for those working and studying Open Source and various distributions of Linux. Exam Objectives
Infoblox Kubernetes1.0.0 IPAM Plugin
 2h DEPLOYMENT GUIDE Infoblox Kubernetes1.0.0 IPAM Plugin NIOS version 8.X August 2018 2018 Infoblox Inc. All rights reserved. Infoblox Kubernetes 1.0.0 IPAM Deployment Guide August 2018 Page 1 of 18 Overview...
2h DEPLOYMENT GUIDE Infoblox Kubernetes1.0.0 IPAM Plugin NIOS version 8.X August 2018 2018 Infoblox Inc. All rights reserved. Infoblox Kubernetes 1.0.0 IPAM Deployment Guide August 2018 Page 1 of 18 Overview...
Siemens PLM Software. HEEDS MDO Setting up a Windows-to- Linux Compute Resource.
 Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Siemens PLM Software HEEDS MDO 2018.04 Setting up a Windows-to- Linux Compute Resource www.redcedartech.com. Contents Introduction 1 On Remote Machine B 2 Installing the SSH Server 2 Configuring the SSH
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide
 Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide Oded Nahum Principal Systems Engineer PLUMgrid EMEA November 2014 Page 1 Page 2 Table of Contents Table
Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide Oded Nahum Principal Systems Engineer PLUMgrid EMEA November 2014 Page 1 Page 2 Table of Contents Table
Table of Contents. Table of Contents License server installation guide - Linux. Download SCL
 Table of Contents Table of Contents License server installation guide - Linux Download SCL Download Synopsys Installer Install SCL - RHEL and CentOS Install SCL - Debian and Ubuntu Customizing the License
Table of Contents Table of Contents License server installation guide - Linux Download SCL Download Synopsys Installer Install SCL - RHEL and CentOS Install SCL - Debian and Ubuntu Customizing the License
CyberP3i Hands-on Lab Series
 CyberP3i Hands-on Lab Series Lab Series using NETLAB Designer: Dr. Lixin Wang, Associate Professor Hands-On Lab for Application Attacks The NDG Security+ Pod Topology Is Used 1. Introduction In this lab,
CyberP3i Hands-on Lab Series Lab Series using NETLAB Designer: Dr. Lixin Wang, Associate Professor Hands-On Lab for Application Attacks The NDG Security+ Pod Topology Is Used 1. Introduction In this lab,
OpenStack Havana All-in-One lab on VMware Workstation
 OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
OpenStack Havana All-in-One lab on VMware Workstation With all of the popularity of OpenStack in general, and specifically with my other posts on deploying the Rackspace Private Cloud lab on VMware Workstation,
HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS
 HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS How To Securely Configure a Linux Host to Run Containers To run containers securely, one must go through a multitude of steps to ensure that a)
HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS How To Securely Configure a Linux Host to Run Containers To run containers securely, one must go through a multitude of steps to ensure that a)
ViMP 2.0. Installation Guide. Verfasser: ViMP GmbH
 ViMP 2.0 Installation Guide Verfasser: ViMP GmbH Table of contents About this document... 3 Prerequisites... 4 Preparing the server... 5 Apache2... 5 PHP... 5 MySQL... 5 Transcoding... 6 Configuration...
ViMP 2.0 Installation Guide Verfasser: ViMP GmbH Table of contents About this document... 3 Prerequisites... 4 Preparing the server... 5 Apache2... 5 PHP... 5 MySQL... 5 Transcoding... 6 Configuration...
Bitnami MySQL for Huawei Enterprise Cloud
 Bitnami MySQL for Huawei Enterprise Cloud Description MySQL is a fast, reliable, scalable, and easy to use open-source relational database system. MySQL Server is intended for mission-critical, heavy-load
Bitnami MySQL for Huawei Enterprise Cloud Description MySQL is a fast, reliable, scalable, and easy to use open-source relational database system. MySQL Server is intended for mission-critical, heavy-load
Observium Enable your new virtual host 4
 Observium Contents 1 Introduction 1 1.1 Goals................................. 1 1.2 Notes................................. 1 2 Observium installation 2 2.1 1. Installation based on offical instructions.............
Observium Contents 1 Introduction 1 1.1 Goals................................. 1 1.2 Notes................................. 1 2 Observium installation 2 2.1 1. Installation based on offical instructions.............
Install latest version of Roundcube (Webmail) on CentOS 7
 Install latest version of Roundcube (Webmail) on CentOS 7 by Pradeep Kumar Published December 14, 2015 Updated August 3, 2017 Roundcube is a web browser based mail client & also known as webmail. It provides
Install latest version of Roundcube (Webmail) on CentOS 7 by Pradeep Kumar Published December 14, 2015 Updated August 3, 2017 Roundcube is a web browser based mail client & also known as webmail. It provides
CIS 76 VLab Pod Setup
 CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
User Guide Infoblox IPAM Driver for Docker. Version 1.1
 User Guide Infoblox IPAM Driver for Docker Version 1.1 Copyright Statements 2017, Infoblox Inc. All rights reserved. The contents of this document may not be copied or duplicated in any form, in whole
User Guide Infoblox IPAM Driver for Docker Version 1.1 Copyright Statements 2017, Infoblox Inc. All rights reserved. The contents of this document may not be copied or duplicated in any form, in whole
Manually Password Protect Directories Apache Ubuntu
 Manually Password Protect Directories Apache Ubuntu Apache can be configured to force users to login before being Password protection can be useful for securing a directory that planning to edit them manually,
Manually Password Protect Directories Apache Ubuntu Apache can be configured to force users to login before being Password protection can be useful for securing a directory that planning to edit them manually,
#Uncomment the second line to enable any form of FTP write command. #write_enable=yes
 Installing and configuring Apache 2 in Linux Please note that dashes (-) are used to indicate what you should type, they should not be included in the command. Install Linux on an old desktop, dual core
Installing and configuring Apache 2 in Linux Please note that dashes (-) are used to indicate what you should type, they should not be included in the command. Install Linux on an old desktop, dual core
SETTING UP 3 WORDPRESS SITES ON APACHE AND UBUNTU BY RAMI
 SETTING UP 3 WORDPRESS SITES ON APACHE AND UBUNTU 14.04 BY RAMI SETTING UP 3 WORDPRESS SITES ON APACHE SERVER AND UBUNTU 14.04 THE SET UP This may be a little rough in some places because not all the terms
SETTING UP 3 WORDPRESS SITES ON APACHE AND UBUNTU 14.04 BY RAMI SETTING UP 3 WORDPRESS SITES ON APACHE SERVER AND UBUNTU 14.04 THE SET UP This may be a little rough in some places because not all the terms
Configuring a Standalone VCL Environment using VMware Server 2.0
 Configuring a Standalone VCL Environment using VMware Server 2.0 DISCLAIMER! This document provides instuctions for configuring a standalone VCL environment running on a single computer which is able to
Configuring a Standalone VCL Environment using VMware Server 2.0 DISCLAIMER! This document provides instuctions for configuring a standalone VCL environment running on a single computer which is able to
Using RANCID. Contents. 1 Introduction Goals Notes Install rancid Add alias Configure rancid...
 Using RANCID Contents 1 Introduction 2 1.1 Goals................................. 2 1.2 Notes................................. 2 2 Install rancid 2 2.1 Add alias............................... 3 2.2 Configure
Using RANCID Contents 1 Introduction 2 1.1 Goals................................. 2 1.2 Notes................................. 2 2 Install rancid 2 2.1 Add alias............................... 3 2.2 Configure
Setting up a LAMP server
 Setting up a LAMP server What is a LAMP? Duh. Actually, we re interested in... Linux, Apache, Mysql, and PHP A pretty standard web server setup Not the only technology options! Linux Pick any! Common choices
Setting up a LAMP server What is a LAMP? Duh. Actually, we re interested in... Linux, Apache, Mysql, and PHP A pretty standard web server setup Not the only technology options! Linux Pick any! Common choices
Computer Security Coursework Exercise CW1 Web Server and Application Security
 Computer Security Coursework Exercise CW1 Web Server and Application Security In this coursework exercise we will guide you through an attack against a vulnerable machine. You will take the role of Mallet
Computer Security Coursework Exercise CW1 Web Server and Application Security In this coursework exercise we will guide you through an attack against a vulnerable machine. You will take the role of Mallet
Bitnami Pimcore for Huawei Enterprise Cloud
 Bitnami Pimcore for Huawei Enterprise Cloud Description Pimcore is the open source platform for managing digital experiences. It is the consolidated platform for web content management, product information
Bitnami Pimcore for Huawei Enterprise Cloud Description Pimcore is the open source platform for managing digital experiences. It is the consolidated platform for web content management, product information
My installation at Maple Park Development Corp.
 My installation at Maple Park Development Corp. U-verse ADSL (6 MB) (2) Grandstream HT702 VOIP adaptors (4) Hardwired PCs (or devices) (1) WRT54G (as a hub) 3-6 wireless guests/other @99.26.133.45 (Dynamic)
My installation at Maple Park Development Corp. U-verse ADSL (6 MB) (2) Grandstream HT702 VOIP adaptors (4) Hardwired PCs (or devices) (1) WRT54G (as a hub) 3-6 wireless guests/other @99.26.133.45 (Dynamic)
Software Transfer Document. SensUs Digital. Valedictorian. Version July 6, 2017
 Valedictorian Software Transfer Document Version 1.0.0 Project team J.M.A. Boender 0978526 R. Coonen 0902230 R.A.T. van Dijk 0864724 H.R. Galioulline 0927184 B.A.M. van Geffen 0892070 A.A.W.M. de Kroon
Valedictorian Software Transfer Document Version 1.0.0 Project team J.M.A. Boender 0978526 R. Coonen 0902230 R.A.T. van Dijk 0864724 H.R. Galioulline 0927184 B.A.M. van Geffen 0892070 A.A.W.M. de Kroon
Parallel Programming Pre-Assignment. Setting up the Software Environment
 Parallel Programming Pre-Assignment Setting up the Software Environment Authors: B. Wilkinson and C. Ferner. Modification date: Aug 21, 2014 (Minor correction Aug 27, 2014.) Software The purpose of this
Parallel Programming Pre-Assignment Setting up the Software Environment Authors: B. Wilkinson and C. Ferner. Modification date: Aug 21, 2014 (Minor correction Aug 27, 2014.) Software The purpose of this
Lab 0: Intro to running Jupyter Notebook on a Raspberry Pi
 Lab 0: Intro to running Jupyter Notebook on a Raspberry Pi Nick Antipa, Li-Hao Yeh, based on labs by Jon Tamir and Frank Ong January 24, 2018 This lab will walk you through setting up your Raspberry Pi
Lab 0: Intro to running Jupyter Notebook on a Raspberry Pi Nick Antipa, Li-Hao Yeh, based on labs by Jon Tamir and Frank Ong January 24, 2018 This lab will walk you through setting up your Raspberry Pi
Patch Server for Jamf Pro Documentation
 Patch Server for Jamf Pro Documentation Release 0.8.2 Bryson Tyrrell Jun 06, 2018 Contents 1 Change History 3 2 Using Patch Starter Script 7 3 Troubleshooting 9 4 Testing the Patch Server 11 5 Running
Patch Server for Jamf Pro Documentation Release 0.8.2 Bryson Tyrrell Jun 06, 2018 Contents 1 Change History 3 2 Using Patch Starter Script 7 3 Troubleshooting 9 4 Testing the Patch Server 11 5 Running
CDX REPORT TEAM #8 JACOB CHAPMAN SNEHESH THALAPANENI DEVISHA SRIVASTAVA
 CDX REPORT TEAM #8 JACOB CHAPMAN SNEHESH THALAPANENI DEVISHA SRIVASTAVA SANJAY ALEX KALLA HOSTING We installed Open VPN daemon, which can be used to securely link two or more private networks using an
CDX REPORT TEAM #8 JACOB CHAPMAN SNEHESH THALAPANENI DEVISHA SRIVASTAVA SANJAY ALEX KALLA HOSTING We installed Open VPN daemon, which can be used to securely link two or more private networks using an
Installation Instructions for Xorcom TwinStar Plus Servers
 Document version: 1.0 Overview Installation Instructions for Xorcom TwinStar Plus Servers This document describes the configuration process which must be performed at the customer site for pre-configured
Document version: 1.0 Overview Installation Instructions for Xorcom TwinStar Plus Servers This document describes the configuration process which must be performed at the customer site for pre-configured
Introduction. What is Linux? What is the difference between a client and a server?
 Linux Kung Fu Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and open-source operating system distributions
Linux Kung Fu Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and open-source operating system distributions
Linux Systems Security. Logging and Network Monitoring NETS1028 Fall 2016
 Linux Systems Security Logging and Network Monitoring NETS1028 Fall 2016 Monitoring Monitoring can take many forms, from passive periodic inspection to realtime intrusion detection For this unit, we will
Linux Systems Security Logging and Network Monitoring NETS1028 Fall 2016 Monitoring Monitoring can take many forms, from passive periodic inspection to realtime intrusion detection For this unit, we will
Buzztouch Server 2.0 with Amazon EC2
 Buzztouch Server 2.0 with Amazon EC2 This is for those that want a step by step instructions on how to prepare an Amazon's EC2 instance for the Buzztouch server. This document only covers the amazon EC2
Buzztouch Server 2.0 with Amazon EC2 This is for those that want a step by step instructions on how to prepare an Amazon's EC2 instance for the Buzztouch server. This document only covers the amazon EC2
Virtual Machine. Release 1.0. Howard Chivers
 Virtual Machine Release 1.0 Howard Chivers Feb 21, 2017 CONTENTS 1 Getting Started 2 1.1 The Virtual Machine.................................... 2 1.2 Exercise Documentation..................................
Virtual Machine Release 1.0 Howard Chivers Feb 21, 2017 CONTENTS 1 Getting Started 2 1.1 The Virtual Machine.................................... 2 1.2 Exercise Documentation..................................
Below are the steps to install Orangescrum Self Hosted version of Cloud Edition in Ubuntu Server Last Updated: OCT 18, 2018
 Below are the steps to install Orangescrum Self Hosted version of Cloud Edition in Ubuntu Server Last Updated: OCT 18, 2018 Step 1 Download the Orangescrum Self Hosted version of CloudEdition Extract the
Below are the steps to install Orangescrum Self Hosted version of Cloud Edition in Ubuntu Server Last Updated: OCT 18, 2018 Step 1 Download the Orangescrum Self Hosted version of CloudEdition Extract the
VIRTUAL GPU LICENSE SERVER VERSION , , AND 5.1.0
 VIRTUAL GPU LICENSE SERVER VERSION 2018.10, 2018.06, AND 5.1.0 DU-07754-001 _v7.0 through 7.2 March 2019 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server...
VIRTUAL GPU LICENSE SERVER VERSION 2018.10, 2018.06, AND 5.1.0 DU-07754-001 _v7.0 through 7.2 March 2019 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server...
Linux Kung Fu. Stephen James UBNetDef, Spring 2017
 Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
Git Command Line Tool Is Not Installed
 Git Command Line Tool Is Not Installed Make Sure It Is Accessible On Y Error: "git" command line tool is not installed: make sure it is accessible on y I have installed git tool. even in git bash its showing
Git Command Line Tool Is Not Installed Make Sure It Is Accessible On Y Error: "git" command line tool is not installed: make sure it is accessible on y I have installed git tool. even in git bash its showing
INTRODUCTION. To avoid the PHP7 conflicts use this OS image: STEP 1 - Parts List:
 INTRODUCTION These are enhanced instruction set to install RaspberryPints on a Raspberry Pi 2 Model B with use of an AlaMode card and Flow Meters from AdaFruit.com. I started with instruction set here:
INTRODUCTION These are enhanced instruction set to install RaspberryPints on a Raspberry Pi 2 Model B with use of an AlaMode card and Flow Meters from AdaFruit.com. I started with instruction set here:
Apache Manual Install Ubuntu Php Mysql. Phpmyadmin No >>>CLICK HERE<<<
 Apache Manual Install Ubuntu Php Mysql Phpmyadmin No Ubuntu 14.10 LAMP server tutorial with Apache 2, PHP 5 and MySQL (MariaDB) Additionally, I will install phpmyadmin to make MySQL administration easier.
Apache Manual Install Ubuntu Php Mysql Phpmyadmin No Ubuntu 14.10 LAMP server tutorial with Apache 2, PHP 5 and MySQL (MariaDB) Additionally, I will install phpmyadmin to make MySQL administration easier.
TROUBLESHOOTING GUIDE. HYCU Data Protection for Nutanix
 TROUBLESHOOTING GUIDE HYCU Data Protection for Nutanix Version: 3.0.0 Product release date: April 2018 Document release date: April 2018 Legal notices Copyright notice 2017 2018 HYCU. All rights reserved.
TROUBLESHOOTING GUIDE HYCU Data Protection for Nutanix Version: 3.0.0 Product release date: April 2018 Document release date: April 2018 Legal notices Copyright notice 2017 2018 HYCU. All rights reserved.
USING NGC WITH GOOGLE CLOUD PLATFORM
 USING NGC WITH GOOGLE CLOUD PLATFORM DU-08962-001 _v02 April 2018 Setup Guide TABLE OF CONTENTS Chapter 1. Introduction to... 1 Chapter 2. Deploying an NVIDIA GPU Cloud Image from the GCP Console...3 2.1.
USING NGC WITH GOOGLE CLOUD PLATFORM DU-08962-001 _v02 April 2018 Setup Guide TABLE OF CONTENTS Chapter 1. Introduction to... 1 Chapter 2. Deploying an NVIDIA GPU Cloud Image from the GCP Console...3 2.1.
Jackson State University Department of Computer Science CSC / Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
Openvpn Client Do Not Change Default Gateway
 Openvpn Client Do Not Change Default Gateway I currently have a router using OpenVPN in client mode to connect to a host Is it possible to make OpenVPN the default gateway for everyone connected So what
Openvpn Client Do Not Change Default Gateway I currently have a router using OpenVPN in client mode to connect to a host Is it possible to make OpenVPN the default gateway for everyone connected So what
= Session-(1.4) Preparing the Workstation for the Lab / OS Installation = Session-(1.4) Preparing the Workstation for the Lab / OS Installation
 = Session-(1.4) Preparing the Workstation for the Lab / OS Installation = Session-(1.4) Preparing the Workstation for the Lab / OS Installation (1.4.1) Hardware Recommendation. (1.4.2) Operating System
= Session-(1.4) Preparing the Workstation for the Lab / OS Installation = Session-(1.4) Preparing the Workstation for the Lab / OS Installation (1.4.1) Hardware Recommendation. (1.4.2) Operating System
Install some base packages. I recommend following this guide as root on a new VPS or using sudo su, it will make running setup just a touch easier.
 Nagios 4 on Ubuntu 16 Install some base packages. I recommend following this guide as root on a new VPS or using sudo su, it will make running setup just a touch easier. apt-get install php-gd build-essential
Nagios 4 on Ubuntu 16 Install some base packages. I recommend following this guide as root on a new VPS or using sudo su, it will make running setup just a touch easier. apt-get install php-gd build-essential
LAB #7 Linux Tutorial
 Gathering information: LAB #7 Linux Tutorial Find the password file on a Linux box Scenario You have access to a Linux computer. You must find the password file on the computer. Objective Get a listing
Gathering information: LAB #7 Linux Tutorial Find the password file on a Linux box Scenario You have access to a Linux computer. You must find the password file on the computer. Objective Get a listing
Downloading and installing Db2 Developer Community Edition on Red Hat Enterprise Linux Roger E. Sanders Yujing Ke Published on October 24, 2018
 Downloading and installing Db2 Developer Community Edition on Red Hat Enterprise Linux Roger E. Sanders Yujing Ke Published on October 24, 2018 This guide will help you download and install IBM Db2 software,
Downloading and installing Db2 Developer Community Edition on Red Hat Enterprise Linux Roger E. Sanders Yujing Ke Published on October 24, 2018 This guide will help you download and install IBM Db2 software,
Platform Migrator Technical Report TR
 Platform Migrator Technical Report TR2018-990 Munir Contractor mmc691@nyu.edu Christophe Pradal christophe.pradal@inria.fr Dennis Shasha shasha@cs.nyu.edu May 12, 2018 CONTENTS: 1 Abstract 4 2 Platform
Platform Migrator Technical Report TR2018-990 Munir Contractor mmc691@nyu.edu Christophe Pradal christophe.pradal@inria.fr Dennis Shasha shasha@cs.nyu.edu May 12, 2018 CONTENTS: 1 Abstract 4 2 Platform
CS 143A. Principles of Operating Systems. Instructor : Prof. Anton Burtsev
 CS 143A Principles of Operating Systems Instructor : Prof. Anton Burtsev (aburtsev@uci.edu) Assistants : Junjie Shen junjies1@uci.edu Vikram Narayanan narayav1@uci.edu Biswadip Maity (Deep) Email : maityb@uci.edu
CS 143A Principles of Operating Systems Instructor : Prof. Anton Burtsev (aburtsev@uci.edu) Assistants : Junjie Shen junjies1@uci.edu Vikram Narayanan narayav1@uci.edu Biswadip Maity (Deep) Email : maityb@uci.edu
Installing FreePBX 13 on Debian 8.1
 Installing FreePBX 13 on Debian 8.1 READ FIRST Manual installations of FreePBX is considered an EXPERTS ONLY exercise. This method of installation is enough to get CORE functionality of FreePBX. Non-commercial
Installing FreePBX 13 on Debian 8.1 READ FIRST Manual installations of FreePBX is considered an EXPERTS ONLY exercise. This method of installation is enough to get CORE functionality of FreePBX. Non-commercial
