Server virtualiza,on and security. CSCI 470: Web Science Keith Vertanen
|
|
|
- Lisa Glenn
- 5 years ago
- Views:
Transcription
1 Server virtualiza,on and security CSCI 470: Web Science Keith Vertanen
2 Mo*va*on Virtualiza*on Overview Setup process (DigitalOcean) Securing a new Ubuntu VM So<ware patching Access control Firewall setup Monitoring Tes*ng 2
3 hcp:// records- in- montana- hacked- compromises- personal- data- of million- people.htm 3
4 hcp:// m/graphics/2014- data- breaches/ 4
5 5
6 6
7 7
8 Virtual machine (VM) Virtualiza*on Isolated so<ware container with OS and app Separate and independent Many can run simultaneously on a single computer hcp:// basics/how- virtualiza*on- works 8
9 Crea*ng VM Step 1: Signup, verify , credit card details Step 2: Configure desired resources, physical loca*on, features, ini*al account access 9
10 Crea*ng VM Step 1: Signup, verify , credit card details Step 2: Configure desired resources, physical loca*on, features, ini*al account access 10
11 Crea*ng VM Step 1: Signup, verify , credit card details Step 2: Configure desired resources, physical loca*on, features, ini*al account access Step 3: Wait 1 minute 11
12 Crea*ng VM Step 1: Signup, verify , credit card details Step 2: Configure desired resources, physical loca*on, features, ini*al account access Step 3: Wait 1 minute Step 4: Change ed root password to something hard to guess 12
13 Grab lunch, and then % more /var/log/auth.log Jan 13 12:44:47 kvertanen sshd[1002]: Server listening on port Jan 13 13:49:32 kvertanen sshd[1371]: reverse mapping checking getaddrinfo for huzhou.ctc.mx.fund123.cn [ ] failed - POSSIBLE BREAK- IN ATTEMPT! Jan 13 13:49:33 kvertanen sshd[1371]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost= user=root Jan 13 13:49:35 kvertanen sshd[1371]: Failed password for root from port ssh2 Jan 13 13:49:46 kvertanen sshd[1371]: message repeated 5 times: [ Failed password for root from port ssh2] Jan 13 13:49:46 kvertanen sshd[1371]: Disconnecting: Too many authentication failures for root [preauth] Jan 13 13:49:46 kvertanen sshd[1371]: PAM 5 more authentication failures; logname= uid=0 euid=0 tty=ssh ruser= rhost= user=root Jan 13 13:49:46 kvertanen sshd[1371]: PAM service(sshd) ignoring max retries; 6 > 3 Jan 13 13:49:47 kvertanen sshd[1373]: error: Could not load host key: /etc/ssh/ssh_host_ed25519_key Jan 13 13:49:48 kvertanen sshd[1373]: reverse mapping checking getaddrinfo for huzhou.ctc.mx.fund123.cn [ ] failed - POSSIBLE BREAK- IN ATTEMPT! Jan 13 13:49:49 kvertanen sshd[1373]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost= user=root Jan 13 13:49:51 kvertanen sshd[1373]: Failed password for root from port ssh2 Jan 13 13:49:53 kvertanen sshd[1375]: error: Could not load host key: /etc/ssh/ssh_host_ed25519_key Jan 13 13:50:03 kvertanen sshd[1373]: message repeated 5 times: [ Failed password for root from port ssh2] Jan 13 13:50:03 kvertanen sshd[1373]: Disconnecting: Too many authentication failures for root [preauth] Jan 13 13:50:03 kvertanen sshd[1373]: PAM 5 more authentication failures; logname= uid=0 euid=0 tty=ssh ruser= rhost= user=root Jan 13 13:50:03 kvertanen sshd[1373]: PAM service(sshd) ignoring max retries; 6 > 3 Jan 13 13:50:03 kvertanen sshd[1377]: error: Could not load host key: /etc/ssh/ssh_host_ed25519_key Jan 13 13:50:05 kvertanen sshd[1377]: reverse mapping checking getaddrinfo for huzhou.ctc.mx.fund123.cn [ ] failed - POSSIBLE BREAK- IN ATTEMPT! Jan 13 13:50:05 kvertanen sshd[1377]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost= user=root Jan 13 13:50:07 kvertanen sshd[1377]: Failed password for root from port ssh2 Jan 13 13:50:11 kvertanen sshd[1375]: reverse mapping checking getaddrinfo for huzhou.ctc.mx.fund123.cn [ ] failed - POSSIBLE BREAK- IN ATTEMPT! Jan 13 13:50:11 kvertanen sshd[1375]: pam_unix(sshd:auth): authentication failure; logname= uid=0 eu 13
14 % sudo nmap Starting Nmap 6.40 ( ) at :50 MST Nmap scan report for Host is up (0.094s latency). Not shown: 995 closed ports PORT STATE SERVICE 22/tcp open ssh 135/tcp filtered msrpc 139/tcp filtered netbios- ssn 445/tcp filtered microsoft- ds 593/tcp filtered http- rpc- epmap 0: Ini*al vulnerability tes*ng Run nmap to scan for open ports on the VM Nmap done: 1 IP address (1 host up) scanned in seconds 14
15 % apt- get update Ign trusty InRelease... Fetched 2,533 kb in 4s (625 kb/s) Reading package lists... Done % apt- get install fail2ban Reading package lists... Done Building dependency tree Reading state information... Done... The following NEW packages will be installed: fail2ban python- pyinotify whois 0 upgraded, 3 newly installed, 0 to remove and 3 not upgraded. Need to get 184 kb of archives. After this operation, 927 kb of additional disk space will be used. Do you want to continue? [Y/n] Y... % more /var/log/fail2ban.log :33:46,613 fail2ban.jail : INFO Jail 'ssh' started :09:40,229 fail2ban.actions: WARNING [ssh] Ban :19:40,969 fail2ban.actions: WARNING [ssh] Unban : Securing SSH Threat: Unauthorized logins Mi*ga*on: Install fail2ban Create non- obvious username with sudo privileges Only allow login from non- obvious username Disable root login Move SSH from port 22 to another port below 1024 Switch to public/private key authen*ca*on 15
16 % adduser kvertanen Adding user `kvertanen'... Adding new group `kvertanen' (1000)... Adding new user `kvertanen' (1000) with group `kvertanen'... Creating home directory `/home/kvertanen'... Copying files from `/etc/skel'... Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully Changing the user information for kvertanen Enter the new value, or press ENTER for the default Full Name []: Room Number []: Work Phone []: Home Phone []: Other []: Is the information correct? [Y/n] Y % visudo Add new user by duplica*ng root reference: root ALL=(ALL:ALL) ALL kvertanen ALL=(ALL:ALL) ALL 1: Securing SSH Threat: Unauthorized logins Mi*ga*on: Install fail2ban Create non- obvious username with sudo privileges Only allow login from non- obvious username Disable root login Move SSH from port 22 to another port below 1024 Switch to public/private key authen*ca*on 16
17 % nano /etc/ssh/sshd_config Restrict to given user (op*onally, specific IP address AllowUsers kvertanen Disable login using root username: PermitRootLogin no Move to different port, e.g. 587 (but below 1024 so as to require root privileges to start): Port 587 Restart SSH server: % service ssh restart Test in new terminal window: % ssh - p 587kvertanen@ kvertanen@ s password: Welcome to Ubuntu... % ssh - p 587root@ kvertanen@ s password: Permission denied, please try again. % ssh kvertanen@ ssh: connect to host port 22: Connection refused 1: Securing SSH Threat: Unauthorized logins Mi*ga*on: Install fail2ban Create non- obvious username with sudo privileges Only allow login from non- obvious username Disable root login Move SSH from port 22 to another port below 1024 Switch to public/private key authen*ca*on 17
18 Prepare loca*on on VM for public keys (as the non- root user): % ssh - p 587 kvertanen@ kvertanen@ s password: Welcome to Ubuntu... % mkdir /home/kvertanen/.ssh % chmod 700 /home/kvertanen/.ssh 1: Securing SSH Threat: Unauthorized logins Mi*ga*on: Install fail2ban Create a public/private key pair on local client (e.g. on ka*e): % ssh- keygen - t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/staff/ vertanen/.ssh/id_rsa): id_digital Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in id_digital. Your public key has been saved in id_digital.pub.... % ls - l id_digital* - rw vertanen staff 1675 Jan 13 13:34 id_digital - rw- r- - r- - 1 vertanen staff 396 Jan 13 13:34 id_digital.pub Create non- obvious username with sudo privileges Only allow login from non- obvious username Disable root login id_digital = your private RSA key (keep somewhere safe) id_digital.pub = your public RSA key (goes on server in ~/.ssh/authorized_keys) Move SSH from port 22 to another port below 1024 Switch to public/private key authen,ca,on 18
19 Copy public key from client onto VM: % cat./id_digital.pub ssh - p 587kvertanen@ "cat >> ~/.ssh/authorized_keys" kvertanen@ s password: Test out logging in using private key: % ssh - p i id_digital kvertanen@ Welcome to Ubuntu... Prevent password- based logins: % nano /etc/ssh/sshd_config PasswordAuthentication No Restart SSH server: % service ssh restart 1: Securing SSH Threat: Unauthorized logins Mi*ga*on: Install fail2ban Create non- obvious username with sudo privileges Only allow login from non- obvious username Disable root login Move SSH from port 22 to another port below 1024 Switch to public/private key authen,ca,on 19
20 % apt- get update Ign trusty InRelease... Get:18 trusty- security/main Translation- en [97.0 kb] Hit trusty- security/universe Translation- en Fetched 2,533 kb in 4s (625 kb/s) Reading package lists... Done % apt- get upgrade Reading package lists... Done... 5 upgraded, 0 newly installed, 0 to remove and 3 not upgraded. Need to get 1,538 kb of archives. After this operation, 8,192 B disk space will be freed. Do you want to continue? [Y/n] Y Get:1 trusty- updates/main libssl1.0.0 amd f- 1ubuntu2. 8 [826 kb]... Fetched 1,538 kb in 0s (3,314 kb/s) Preconfiguring packages... (Reading database files and directories currently installed.) Unpacking libssl1.0.0:amd64 (1.0.1f- 1ubuntu2.8) over (1.0.1f- 1ubuntu2.7) : Securing so<ware Threat: Exploit of known so<ware vulnerabili*es Mi*ga*on: Make sure you are star,ng with up- to- date soiware Configure automa*c security updates Verify automa*c updates are working 20
21 % apt- get install unattended- upgrades Edit /etc/apt/apt.conf.d/50unattended- upgrades Change to include unacended- upgrades: Unattended- Upgrade::Allowed- Origins { "Ubuntu precise- security"; // "Ubuntu precise- updates"; }; Edit /etc/apt/apt.conf.d/10periodic Change to: APT::Periodic::Update- Package- Lists "1"; APT::Periodic::Download- Upgradeable- Packages "1"; APT::Periodic::AutocleanInterval "7"; APT::Periodic::Unattended- Upgrade "1"; 2: Securing so<ware Threat: Exploit of known so<ware vulnerabili*es Mi*ga*on: Make sure you are star*ng with up- to- date so<ware Configure automa,c security updates Verify automa*c updates are working (a<er a day) 21
22 % more /var/log/unattended- upgrades/unattended- upgrades.log :57:40,315 INFO Initial blacklisted packages: :57:40,315 INFO Starting unattended upgrades script :57:40,315 INFO Allowed origins are: ['o=ubuntu,a=trusty- security'] :57:49,592 INFO Packages that will be upgraded: liboxideqt- qmlplugin linux- generic linux- headers- generic li nux- image- generic oxideqt- codecs- extra :57:49,592 INFO Writing dpkg log to '/var/log/unattended- upgrades/unattended- upgrades- dpkg_ _07:57 : log' :58:44,956 INFO All upgrades installed :54:41,448 INFO Initial blacklisted packages: :54:41,449 INFO Starting unattended upgrades script :54:41,449 INFO Allowed origins are: ['o=ubuntu,a=trusty- security'] :54:53,582 INFO Packages that will be upgraded: libssl1.0.0 linux- generic linux- generic- lts- saucy linux- gen eric- lts- trusty linux- headers- generic linux- headers- generic- lts- saucy linux- headers- generic- lts- trusty linux- image- gener ic linux- image- generic- lts- saucy linux- image- generic- lts- trusty linux- libc- dev openssl :54:53,583 INFO Writing dpkg log to '/var/log/unattended- upgrades/unattended- upgrades- dpkg_ _07:54 : log' :55:50,474 INFO All upgrades installed 2: Securing so<ware Threat: Exploit of known so<ware vulnerabili*es Mi*ga*on: Make sure you are star*ng with up- to- date so<ware Configure automa*c security updates Verify automa,c updates are working (aier a day) 22
23 Add needed ports (at a minimum port that SSH is on): % ufw allow 587 % ufw enable Command may disrupt existing ssh connections. Proceed with operation (y n)? y Firewall is active and enabled on system startup % ufw status Status: active To Action From ALLOW Anywhere 587 (v6) ALLOW Anywhere (v6) 3: Securing network Threat: Exploits on other (unneeded) network services Mi*ga*on: Use a soiware firewall, open only needed ports Verify ports are closed using Nmap: % sudo nmap Starting Nmap 6.40 ( ) Nmap scan report for Host is up (0.55s latency). Not shown: 999 filtered ports PORT STATE SERVICE 587/tcp open fw1- secureremote Nmap done: 1 IP address (1 host up) scanned in seconds 23
24 Further securing Intrusion Detec*on System (IDS) Monitors for suspicious ac*vi*es Network- based Packets on the network Host- based Monitor logs, files Send out warnings via , etc. 24
25 Further securing Hardening specific applica*ons: Apache (web server) PHP (server- side scrip*ng) MySQL (database) 25
26 Virtualiza*on Summary Your own server in 60 seconds Securing a new VM: Lock down ability to login Keep so<ware up to date Use a firewall Install intrusion detec*on system(s) Harden installed apps (e.g. Apache, MySQL) 26
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
SmartCash SmartNode Setup Guide V1.2 Windows 10 13/01/2018 By (Jazz) yoyomonkey Page 1
 SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2. Windows 10. Date: 13/01/2018. By (Jazz) yoyomonkey
 SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
SmartCash SmartNode Setup Guide v1.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at the casual
HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS
 HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS How To Securely Configure a Linux Host to Run Containers To run containers securely, one must go through a multitude of steps to ensure that a)
HOW TO SECURELY CONFIGURE A LINUX HOST TO RUN CONTAINERS How To Securely Configure a Linux Host to Run Containers To run containers securely, one must go through a multitude of steps to ensure that a)
ssh and handson Matsuzaki maz Yoshinobu 1
 ssh and handson Matsuzaki maz Yoshinobu maz@iij.ad.jp 1 Secure Shell (ssh) Replacement for unsecure tools/protocols rsh and telnet Usually listen on tcp/22 Whole communication is encrypted
ssh and handson Matsuzaki maz Yoshinobu maz@iij.ad.jp 1 Secure Shell (ssh) Replacement for unsecure tools/protocols rsh and telnet Usually listen on tcp/22 Whole communication is encrypted
UNIT 10 Ubuntu Security
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 10 Ubuntu Security Learning Objectives Participants will understand how to configure major components of Linux/Ubuntu Account
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 10 Ubuntu Security Learning Objectives Participants will understand how to configure major components of Linux/Ubuntu Account
BUILD LINUX LEARNING LAB FOR FREE
 HOW TO BUILD LINUX LEARNING LAB FOR FREE Proudly Presented by: LearnLinux.ca Learn Linux - kickstart your IT career Table of Contents 1. What is Linux? 2. VMware Workstation Player Download 3. VMware Workstation
HOW TO BUILD LINUX LEARNING LAB FOR FREE Proudly Presented by: LearnLinux.ca Learn Linux - kickstart your IT career Table of Contents 1. What is Linux? 2. VMware Workstation Player Download 3. VMware Workstation
Linux Systems Security. Access Control and Authentication NETS1028 Fall 2016
 Linux Systems Security Access Control and Authentication NETS1028 Fall 2016 Access Control Authenticating users is the act of trying to verify that a user is who they claim to be We generally rely on the
Linux Systems Security Access Control and Authentication NETS1028 Fall 2016 Access Control Authenticating users is the act of trying to verify that a user is who they claim to be We generally rely on the
FEPS. SSH Access with Two-Factor Authentication. RSA Key-pairs
 FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
FEPS SSH Access with Two-Factor Authentication RSA Key-pairs access.eps.surrey.ac.uk Contents: Introduction - 3 RSA Key-pairs - 3 Where can I use my RSA Key-Pair? - 3 Step 1 Prepare to generate your RSA
This guide assumes that you are setting up a masternode for the first time. You will need:
 KRT MN Guide Setting up a masternode requires a basic understanding of Linux and blockchain technology, as well as the ability to follow instructions closely. It also requires regular maintenance and careful
KRT MN Guide Setting up a masternode requires a basic understanding of Linux and blockchain technology, as well as the ability to follow instructions closely. It also requires regular maintenance and careful
SCRIV NETWORK COLD WALLET MASTERNODE SETUP GUIDE DETAILED
 SCRIV NETWORK MASTERNODE SETUP GUIDE COLD WALLET DETAILED March, 2018 Table of Contents Requirements for running SCRIV cold wallet masternode on Linux VPS: 3 Setup Linux-based VPS... 3 1. Install SCRIV
SCRIV NETWORK MASTERNODE SETUP GUIDE COLD WALLET DETAILED March, 2018 Table of Contents Requirements for running SCRIV cold wallet masternode on Linux VPS: 3 Setup Linux-based VPS... 3 1. Install SCRIV
Windows Subsystem for Linux Guide Documentation
 Windows Subsystem for Linux Guide Documentation Release Kenneth Reitz Aug 30, 2017 Contents: 1 Background on WSL (Windows Subsystem for Linux) 3 1.1 What is WSL?..............................................
Windows Subsystem for Linux Guide Documentation Release Kenneth Reitz Aug 30, 2017 Contents: 1 Background on WSL (Windows Subsystem for Linux) 3 1.1 What is WSL?..............................................
Expedition. Hardening Guide Version Palo Alto Networks, Inc.
 Expedition Hardening Guide Version 1.0 1 Palo Alto Networks, Inc. www.paloaltonetworks.com 2018 Palo Alto Networks, Inc. Palo Alto Networks is a registered trademark of Palo Alto Networks. You can find
Expedition Hardening Guide Version 1.0 1 Palo Alto Networks, Inc. www.paloaltonetworks.com 2018 Palo Alto Networks, Inc. Palo Alto Networks is a registered trademark of Palo Alto Networks. You can find
Preparing Your Google Cloud VM for W4705
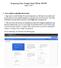 Preparing Your Google Cloud VM for W4705 August 27, 2017 1. Get a cloud.cs.columbia.edu account 1. Sign up for a cloud Columbia CS account using this link. Note that is is an entirely new account and is
Preparing Your Google Cloud VM for W4705 August 27, 2017 1. Get a cloud.cs.columbia.edu account 1. Sign up for a cloud Columbia CS account using this link. Note that is is an entirely new account and is
How to Secure SSH with Google Two-Factor Authentication
 How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
SmartCash SmartNode SCRIPT Setup Guide v2.2. Windows 10. Date: 20/02/2018. By (Jazz) yoyomonkey
 SmartCash SmartNode SCRIPT Setup Guide v2.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at
SmartCash SmartNode SCRIPT Setup Guide v2.2 Date: Introduction Welcome to this step by step guide that will take you through the process of creating your own SmartCash SmartNode. This guide is aimed at
Operating system hardening
 Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Mango AM335x (AM335X) Gbit. Lan 이용복사테스트. Crazy Embedded Laboratory
 Mango AM335x (AM335X) Gbit Lan 이용복사테스트 http://www.mangoboard.com/ http://cafe.naver.com/embeddedcrazyboys Crazy Embedded Laboratory Document History Revision Date Change note 목차 1. 테스트환경... 3 2. 이더넷속도측정...
Mango AM335x (AM335X) Gbit Lan 이용복사테스트 http://www.mangoboard.com/ http://cafe.naver.com/embeddedcrazyboys Crazy Embedded Laboratory Document History Revision Date Change note 목차 1. 테스트환경... 3 2. 이더넷속도측정...
2-1-1 ssh Secure SHell
 2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup Communicate Safely with Remote Systems What is Safely Authentication I am Assured of Which Host I am Talking
2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup Communicate Safely with Remote Systems What is Safely Authentication I am Assured of Which Host I am Talking
Appliance Guide. Version 1.0
 Appliance Guide Version 1.0 Contents Contents 1 Revision history 2 Getting Started 3 Getting to Know the R7-3000/5000/5000x 5 Getting to Know the R7-1000 6 Setting Up the Appliance 7 Logging in to the
Appliance Guide Version 1.0 Contents Contents 1 Revision history 2 Getting Started 3 Getting to Know the R7-3000/5000/5000x 5 Getting to Know the R7-1000 6 Setting Up the Appliance 7 Logging in to the
MarketC - Masternode Setup Guide
 MarketC - Masternode Setup Guide Preface In this guide we will be focusing on setting up a masternode for Marketc (CMK). This guide will focus on a typical "hot node" / "cold wallet" scenario. The "hot
MarketC - Masternode Setup Guide Preface In this guide we will be focusing on setting up a masternode for Marketc (CMK). This guide will focus on a typical "hot node" / "cold wallet" scenario. The "hot
Project 4: Penetration Test
 Project description Project 4: Penetration Test April 28, 2014 Bing Hao The learning objective of this project is to gain hands on experiences with the usage and functionality of Nmap, Neussus and Metsploit.
Project description Project 4: Penetration Test April 28, 2014 Bing Hao The learning objective of this project is to gain hands on experiences with the usage and functionality of Nmap, Neussus and Metsploit.
Everything about Linux User- and Filemanagement
 Everything about Linux User- and Filemanagement Lukas Prokop 20. April 2009 Inhaltsverzeichnis 1 Who I am 2 1.1 whoami..................................... 3 1.2 passwd......................................
Everything about Linux User- and Filemanagement Lukas Prokop 20. April 2009 Inhaltsverzeichnis 1 Who I am 2 1.1 whoami..................................... 3 1.2 passwd......................................
The Wonderful World of Services VINCE
 The Wonderful World of Services VINCE Agenda definitions services for Windows and Linux breaks? auditing Linux logs for Linux useful tools Goals develop a better understanding of Linux and Windows services
The Wonderful World of Services VINCE Agenda definitions services for Windows and Linux breaks? auditing Linux logs for Linux useful tools Goals develop a better understanding of Linux and Windows services
CENG 334 Computer Networks. Laboratory I Linux Tutorial
 CENG 334 Computer Networks Laboratory I Linux Tutorial Contents 1. Logging In and Starting Session 2. Using Commands 1. Basic Commands 2. Working With Files and Directories 3. Permission Bits 3. Introduction
CENG 334 Computer Networks Laboratory I Linux Tutorial Contents 1. Logging In and Starting Session 2. Using Commands 1. Basic Commands 2. Working With Files and Directories 3. Permission Bits 3. Introduction
Using RDP with Azure Linux Virtual Machines
 Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Operating Systems Linux 1-2 Measurements Background material
 Operating Systems Linux 1-2 Measurements Background material Introduction The Linux measurements were designed to allow you to have an impression about the administration of Linux severs along with providing
Operating Systems Linux 1-2 Measurements Background material Introduction The Linux measurements were designed to allow you to have an impression about the administration of Linux severs along with providing
Basic Linux Security. Roman Bohuk University of Virginia
 Basic Linux Security Roman Bohuk University of Virginia What is Linux? An open source operating system Project started by Linus Torvalds kernel Kernel: core program that controls everything else (controls
Basic Linux Security Roman Bohuk University of Virginia What is Linux? An open source operating system Project started by Linus Torvalds kernel Kernel: core program that controls everything else (controls
Quick Start Guide to Compute Canada Cloud Service
 Quick Start Guide to Compute Canada Cloud Service Launching your first instance (VM) Login to the East or West cloud Dashboard SSH key pair Importing an existing key pair Creating a new key pair Launching
Quick Start Guide to Compute Canada Cloud Service Launching your first instance (VM) Login to the East or West cloud Dashboard SSH key pair Importing an existing key pair Creating a new key pair Launching
John the Ripper on a Ubuntu MPI Cluster
 John the Ripper on a Ubuntu 10.04 MPI Cluster Pétur Ingi Egilsson petur [at] petur [.] eu 1 Table of Contents Foreword...3 History...3 Requirements...3 Configuring the Server...3 Requirements...3 Required
John the Ripper on a Ubuntu 10.04 MPI Cluster Pétur Ingi Egilsson petur [at] petur [.] eu 1 Table of Contents Foreword...3 History...3 Requirements...3 Configuring the Server...3 Requirements...3 Required
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability.
 CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
EASYLAMP UBUNTU V1.0 DOCUMENT OWNER: OUDHUIS, JONATHAN INGRAM MICRO CLOUD EUROPE
 EASYLAMP UBUNTU V1.0 DOCUMENT OWNER: OUDHUIS, JONATHAN INGRAM MICRO CLOUD EUROPE CONTENTS 1 Introduction... 2 2 Creating and configuring a virtual machine... 3 3 Installing Apache... 8 4 Installing MySQL...
EASYLAMP UBUNTU V1.0 DOCUMENT OWNER: OUDHUIS, JONATHAN INGRAM MICRO CLOUD EUROPE CONTENTS 1 Introduction... 2 2 Creating and configuring a virtual machine... 3 3 Installing Apache... 8 4 Installing MySQL...
What is Secure. Authenticated I know who I am talking to. Our communication is Encrypted
 Crypto App - SSH 1 What is Secure Authenticated I know who I am talking to Our communication is Encrypted Telnet clear text Servers Terminal clear text Routers SSH encrypted channel encrypted text Servers
Crypto App - SSH 1 What is Secure Authenticated I know who I am talking to Our communication is Encrypted Telnet clear text Servers Terminal clear text Routers SSH encrypted channel encrypted text Servers
Installing Oxwall completely in Amazon Cloud
 Contents Installing Oxwall completely in Amazon Cloud... 1 PART 1 Creating AWS Instance... 1 Section 1 Security Group... 1 Section 2 - A LAMP-friendly instance... 2 Section 3 - The Elastic IP... 5 PART
Contents Installing Oxwall completely in Amazon Cloud... 1 PART 1 Creating AWS Instance... 1 Section 1 Security Group... 1 Section 2 - A LAMP-friendly instance... 2 Section 3 - The Elastic IP... 5 PART
Masternode Setup Guide
 Masternode Setup Guide Preface The following guide to set up a CREDITS Masternode is geared towards beginners with no experience of servers nor of CREDITS. You can skip certain parts if you re already
Masternode Setup Guide Preface The following guide to set up a CREDITS Masternode is geared towards beginners with no experience of servers nor of CREDITS. You can skip certain parts if you re already
Cryptography Application : SSH. Cyber Security & Network Security March, 2017 Dhaka, Bangladesh
 Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Cryptography Application : SSH Cyber Security & Network Security 20-22 March, 2017 Dhaka, Bangladesh Issue Date: [31-12-2015] Revision: [v.1] What is Safely Authentication I am Assured of Which Host I
Network Monitoring & Management. A few Linux basics
 Network Monitoring & Management A few Linux basics Our chosen platform Ubuntu Linux 14.04.3 LTS 64-bit LTS = Long Term Support no GUI, we administer using ssh Ubuntu is Debian underneath There are other
Network Monitoring & Management A few Linux basics Our chosen platform Ubuntu Linux 14.04.3 LTS 64-bit LTS = Long Term Support no GUI, we administer using ssh Ubuntu is Debian underneath There are other
This is a guide about using Putty on Windows with OpenSSH on Linux. You would learn about how to:
 1 of 7 5/16/2011 5:37 PM Submitted by: Man-wai CHANG Update by: Man-wai CHANG Date Submitted: 31 May 2006 Document Version: 1.0 Last Updated: 08/01/2010 13:48:54 Last Updated: 02/02/2008 23:46:43 This
1 of 7 5/16/2011 5:37 PM Submitted by: Man-wai CHANG Update by: Man-wai CHANG Date Submitted: 31 May 2006 Document Version: 1.0 Last Updated: 08/01/2010 13:48:54 Last Updated: 02/02/2008 23:46:43 This
On-Line Password Breaks CSC 193 WAKE FOREST. U N I V E R S I T Y Department of Computer Science. Spring 2014
 On-Line Password Breaks CSC 193 WAKE FOREST U N I V E R S I T Y Department of Computer Science Spring 2014 Breaking Passwords We have focused on breaking system passwords Take the password file and run
On-Line Password Breaks CSC 193 WAKE FOREST U N I V E R S I T Y Department of Computer Science Spring 2014 Breaking Passwords We have focused on breaking system passwords Take the password file and run
90% 191 Security Best Practices. Blades. 52 Regulatory Requirements. Compliance Report PCI DSS 2.0. related to this regulation
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on April 16, 2018 15:41 PM O verview 1 90% Compliance About PCI DSS 2.0 PCI-DSS is a legal obligation mandated not by government
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on April 16, 2018 15:41 PM O verview 1 90% Compliance About PCI DSS 2.0 PCI-DSS is a legal obligation mandated not by government
Some Details. Network Startup Resource Center
 Some Details Network Startup Resource Center These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Some Details Network Startup Resource Center These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Linux Security & Firewall
 Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
Automatic Creation of a Virtual Network with VBoxManage [1]
![Automatic Creation of a Virtual Network with VBoxManage [1] Automatic Creation of a Virtual Network with VBoxManage [1]](/thumbs/78/77924363.jpg) Automatic Creation of a Virtual Network with V... 1 Automatic Creation of a Virtual Network with VBoxManage [1] Submitted by Steve [2] on Wed, 18/09/2013-5:46pm I am using VirtualBox to create multiple
Automatic Creation of a Virtual Network with V... 1 Automatic Creation of a Virtual Network with VBoxManage [1] Submitted by Steve [2] on Wed, 18/09/2013-5:46pm I am using VirtualBox to create multiple
Evaluating Website Security with Penetration Testing Methodology
 Evaluating Website Security with Penetration Testing Methodology D. Menoski, P. Mitrevski and T. Dimovski St. Clement of Ohrid University in Bitola/Faculty of Technical Sciences, Bitola, Republic of Macedonia
Evaluating Website Security with Penetration Testing Methodology D. Menoski, P. Mitrevski and T. Dimovski St. Clement of Ohrid University in Bitola/Faculty of Technical Sciences, Bitola, Republic of Macedonia
Due: October 8, 2013: 7.30 PM
 Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 1: Lab Project on using PGP GNU Privacy Guard (GPG)
Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 1: Lab Project on using PGP GNU Privacy Guard (GPG)
CDX REPORT TEAM #8 JACOB CHAPMAN SNEHESH THALAPANENI DEVISHA SRIVASTAVA
 CDX REPORT TEAM #8 JACOB CHAPMAN SNEHESH THALAPANENI DEVISHA SRIVASTAVA SANJAY ALEX KALLA HOSTING We installed Open VPN daemon, which can be used to securely link two or more private networks using an
CDX REPORT TEAM #8 JACOB CHAPMAN SNEHESH THALAPANENI DEVISHA SRIVASTAVA SANJAY ALEX KALLA HOSTING We installed Open VPN daemon, which can be used to securely link two or more private networks using an
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
Bitnami Phabricator for Huawei Enterprise Cloud
 Bitnami Phabricator for Huawei Enterprise Cloud IMPORTANT: Phabricator requires you to access the application using a specific domain. This domain is the public IP address for the cloud server. Description
Bitnami Phabricator for Huawei Enterprise Cloud IMPORTANT: Phabricator requires you to access the application using a specific domain. This domain is the public IP address for the cloud server. Description
Contents. Note: pay attention to where you are. Note: Plaintext version. Note: pay attention to where you are... 1 Note: Plaintext version...
 Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Build your own Lightweight Webserver - Hands-on I - Information Network I. Marius Georgescu. Internet Engineering Laboratory. 17 Apr
 Build your own Lightweight Webserver - Hands-on I - Information Network I Marius Georgescu Internet Engineering Laboratory 17 Apr. 2015 iplab Prerequisites Prerequisites Download and Install VirtualBox
Build your own Lightweight Webserver - Hands-on I - Information Network I Marius Georgescu Internet Engineering Laboratory 17 Apr. 2015 iplab Prerequisites Prerequisites Download and Install VirtualBox
2-1-1 ssh Secure SHell
 2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup 1 Communicate Safely with Remote Systems 2 What is Safely Authentication I am Assured of Which Host I am Talking
2-1-1 ssh Secure SHell Using Public Key Cryptography Keying, Key Exchange, and Session Setup 1 Communicate Safely with Remote Systems 2 What is Safely Authentication I am Assured of Which Host I am Talking
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 13: Operating System Security Department of Computer Science and Engineering University at Buffalo 1 Review Previous topics access control authentication session
CSE 565 Computer Security Fall 2018 Lecture 13: Operating System Security Department of Computer Science and Engineering University at Buffalo 1 Review Previous topics access control authentication session
Exercises. Cacti Installation and Configuration
 Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Exercises. Cacti Installation and Configuration
 Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Exercises Cacti Installation and Configuration Exercises Your Mission... Install Cacti Create device entry for your local router Create device entries for your local servers Create entries for class router
Cryptography - SSH. Network Security Workshop May 2017 Phnom Penh, Cambodia
 Cryptography - SSH Network Security Workshop 29-31 May 2017 Phnom Penh, Cambodia What is Safely Authentication I know who I am talking with Our communication is Encrypted Telnet Servers Terminal Routers
Cryptography - SSH Network Security Workshop 29-31 May 2017 Phnom Penh, Cambodia What is Safely Authentication I know who I am talking with Our communication is Encrypted Telnet Servers Terminal Routers
Strategic Infrastructure Security
 Strategic Infrastructure Security Course Number: SCPSIS Length: Certification Exam There are no exams currently associated with this course. Course Overview This course picks up right where Tactical Perimeter
Strategic Infrastructure Security Course Number: SCPSIS Length: Certification Exam There are no exams currently associated with this course. Course Overview This course picks up right where Tactical Perimeter
About Backup and Restore, on page 1 Supported Backup and Restore Procedures, on page 3
 About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
cpouta exercises
 CSC Bioweek. 8.2. 2018 cpouta exercises 1 Table of Contents cpouta exercises 8.2. 2018 1. Launching a virtual machine... 2 1.1 Login to cpouta interface in... 2 1.2 Create your own SSH key pair... 2 A.
CSC Bioweek. 8.2. 2018 cpouta exercises 1 Table of Contents cpouta exercises 8.2. 2018 1. Launching a virtual machine... 2 1.1 Login to cpouta interface in... 2 1.2 Create your own SSH key pair... 2 A.
The Basics of Linux Security
 The Basics of Linux Security What every Linux user should know about security Presented at the 2007 Nebraska CERT Conference Adam Haeder Vice President of Information Technology AIM Institute Basic Linux
The Basics of Linux Security What every Linux user should know about security Presented at the 2007 Nebraska CERT Conference Adam Haeder Vice President of Information Technology AIM Institute Basic Linux
FreeBSD Security Advisories
 Security FreeBSD Security Advisories http://www.freebsd.org/security/advisories.html 2 FreeBSD Security Advisories Advisory Security information Where to find it Web page (Security Advisories Channel)
Security FreeBSD Security Advisories http://www.freebsd.org/security/advisories.html 2 FreeBSD Security Advisories Advisory Security information Where to find it Web page (Security Advisories Channel)
HANDS UP IF YOU DON T HAVE A VM OR IF YOU DON T REMEMBER YOUR PASSWORDS. Or something broke
 HANDS UP IF YOU DON T HAVE A VM OR IF YOU DON T REMEMBER YOUR PASSWORDS Or something broke Securing your VM 101 Getting Comfy in Linux -> Comfort ++ You After This Talk Quick recap from last week. Setup
HANDS UP IF YOU DON T HAVE A VM OR IF YOU DON T REMEMBER YOUR PASSWORDS Or something broke Securing your VM 101 Getting Comfy in Linux -> Comfort ++ You After This Talk Quick recap from last week. Setup
Computer Security Coursework Exercise CW1 Web Server and Application Security
 Computer Security Coursework Exercise CW1 Web Server and Application Security In this coursework exercise we will guide you through an attack against a vulnerable machine. You will take the role of Mallet
Computer Security Coursework Exercise CW1 Web Server and Application Security In this coursework exercise we will guide you through an attack against a vulnerable machine. You will take the role of Mallet
Linux Systems Security. Logging and Network Monitoring NETS1028 Fall 2016
 Linux Systems Security Logging and Network Monitoring NETS1028 Fall 2016 Monitoring Monitoring can take many forms, from passive periodic inspection to realtime intrusion detection For this unit, we will
Linux Systems Security Logging and Network Monitoring NETS1028 Fall 2016 Monitoring Monitoring can take many forms, from passive periodic inspection to realtime intrusion detection For this unit, we will
Linux Kung Fu. Ross Ventresca UBNetDef, Fall 2017
 Linux Kung Fu Ross Ventresca UBNetDef, Fall 2017 GOTO: https://apps.ubnetdef.org/ What is Linux? Linux generally refers to a group of Unix-like free and open source operating system distributions built
Linux Kung Fu Ross Ventresca UBNetDef, Fall 2017 GOTO: https://apps.ubnetdef.org/ What is Linux? Linux generally refers to a group of Unix-like free and open source operating system distributions built
Starting Nmap 6.40 ( ) at :54 Pacific Daylight Time Nmap scan report for mass_dns: warning: Unable to
 Starting Nmap 6.40 ( http://nmap.org ) at 2016-06-12 12:54 Pacific Daylight Time Nmap scan report for 172.30.0.7 mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using
Starting Nmap 6.40 ( http://nmap.org ) at 2016-06-12 12:54 Pacific Daylight Time Nmap scan report for 172.30.0.7 mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using
Linux Kung-Fu. James Droste UBNetDef Fall 2016
 Linux Kung-Fu James Droste UBNetDef Fall 2016 $ init 1 GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org
Linux Kung-Fu James Droste UBNetDef Fall 2016 $ init 1 GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org
6.858 Lecture 4 OKWS. Today's lecture: How to build a secure web server on Unix. The design of our lab web server, zookws, is inspired by OKWS.
 6.858 Lecture 4 OKWS Administrivia: Lab 1 due this Friday. Today's lecture: How to build a secure web server on Unix. The design of our lab web server, zookws, is inspired by OKWS. Privilege separation
6.858 Lecture 4 OKWS Administrivia: Lab 1 due this Friday. Today's lecture: How to build a secure web server on Unix. The design of our lab web server, zookws, is inspired by OKWS. Privilege separation
Singularity: container formats
 Singularity Easy to install and configure Easy to run/use: no daemons no root works with scheduling systems User outside container == user inside container Access to host resources Mount (parts of) filesystems
Singularity Easy to install and configure Easy to run/use: no daemons no root works with scheduling systems User outside container == user inside container Access to host resources Mount (parts of) filesystems
SETTING UP 3 WORDPRESS SITES ON APACHE AND UBUNTU BY RAMI
 SETTING UP 3 WORDPRESS SITES ON APACHE AND UBUNTU 14.04 BY RAMI SETTING UP 3 WORDPRESS SITES ON APACHE SERVER AND UBUNTU 14.04 THE SET UP This may be a little rough in some places because not all the terms
SETTING UP 3 WORDPRESS SITES ON APACHE AND UBUNTU 14.04 BY RAMI SETTING UP 3 WORDPRESS SITES ON APACHE SERVER AND UBUNTU 14.04 THE SET UP This may be a little rough in some places because not all the terms
Spreedbox Getting Started Guide
 Spreedbox Getting Started Guide Last Updated: September 2017 CONTENTS 1. Introduction... 3 2. Prerequisites... 4 3. Opening the box... 5 4. USB Manual, Quick Start Guide & MAC Sticker... 6 5. International
Spreedbox Getting Started Guide Last Updated: September 2017 CONTENTS 1. Introduction... 3 2. Prerequisites... 4 3. Opening the box... 5 4. USB Manual, Quick Start Guide & MAC Sticker... 6 5. International
SSH. What is Safely 6/19/ June 2018 PacNOG 22, Honiara, Solomon Islands Supported by:
 SSH 25-29 June 2018 PacNOG 22, Honiara, Solomon Islands Supported by: Issue Date: Revision: 1 What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows
SSH 25-29 June 2018 PacNOG 22, Honiara, Solomon Islands Supported by: Issue Date: Revision: 1 What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows
Bitnami Piwik for Huawei Enterprise Cloud
 Bitnami Piwik for Huawei Enterprise Cloud Description Piwik is a real time web analytics software program. It provides detailed reports on website visitors: the search engines and keywords they used, the
Bitnami Piwik for Huawei Enterprise Cloud Description Piwik is a real time web analytics software program. It provides detailed reports on website visitors: the search engines and keywords they used, the
Linux Systems Administration Getting Started with Linux
 Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Linux Systems Administration Getting Started with Linux Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International
Course Wiki. Today s Topics. Web Resources. Amazon EC2. Linux. Apache PHP. Workflow and Tools. Extensible Networking Platform 1
 Today s Topics Web Resources Amazon EC2 Linux Apache PHP Workflow and Tools Extensible Networking Platform 1 1 - CSE 330 Creative Programming and Rapid Prototyping Course Wiki Extensible Networking Platform
Today s Topics Web Resources Amazon EC2 Linux Apache PHP Workflow and Tools Extensible Networking Platform 1 1 - CSE 330 Creative Programming and Rapid Prototyping Course Wiki Extensible Networking Platform
Bitnami Re:dash for Huawei Enterprise Cloud
 Bitnami Re:dash for Huawei Enterprise Cloud Description Re:dash is an open source data visualization and collaboration tool. It was designed to allow fast and easy access to billions of records in all
Bitnami Re:dash for Huawei Enterprise Cloud Description Re:dash is an open source data visualization and collaboration tool. It was designed to allow fast and easy access to billions of records in all
VIRTUALBOX UBUNTU EBOOK
 17 March, 2018 VIRTUALBOX UBUNTU EBOOK Document Filetype: PDF 277.47 KB 0 VIRTUALBOX UBUNTU EBOOK It installs on your existing Intel or AMD-based computers, whether they are running Windows, Mac, Linux
17 March, 2018 VIRTUALBOX UBUNTU EBOOK Document Filetype: PDF 277.47 KB 0 VIRTUALBOX UBUNTU EBOOK It installs on your existing Intel or AMD-based computers, whether they are running Windows, Mac, Linux
BitcoinMonster Masternode Linux VPS Tutorial - Vultr VPS Created By : Samshak Donet Mon: MKX8PFz1uvBkwNDTXtUuj6KinudhsKZh1K
 BitcoinMonster Masternode Linux VPS Tutorial - Vultr VPS Created By : Samshak Donet Mon: MKX8PFz1uvBkwNDTXtUuj6KinudhsKZh1K Step 1 Download, install and sync latest BitcoinMonster Windows s wallet on both
BitcoinMonster Masternode Linux VPS Tutorial - Vultr VPS Created By : Samshak Donet Mon: MKX8PFz1uvBkwNDTXtUuj6KinudhsKZh1K Step 1 Download, install and sync latest BitcoinMonster Windows s wallet on both
Installation Manual InfraManage.NET Installation Instructions for Ubuntu
 Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Lab Authentication, Authorization, and Accounting
 Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Bitnami MySQL for Huawei Enterprise Cloud
 Bitnami MySQL for Huawei Enterprise Cloud Description MySQL is a fast, reliable, scalable, and easy to use open-source relational database system. MySQL Server is intended for mission-critical, heavy-load
Bitnami MySQL for Huawei Enterprise Cloud Description MySQL is a fast, reliable, scalable, and easy to use open-source relational database system. MySQL Server is intended for mission-critical, heavy-load
Cryptography - SSH. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography - SSH Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 What is Secure Authentication I know who I am talking to Our communication is Encrypted Telnet Servers Terminal
Cryptography - SSH Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 What is Secure Authentication I know who I am talking to Our communication is Encrypted Telnet Servers Terminal
Cryptography Application : SSH. 7 Sept 2017, Taichung, Taiwan
 Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Cryptography Application : SSH 7 Sept 2017, Taichung, Taiwan What is Safely Authentication I am Assured of Which Host I am Talking With Authentication - The Host Knows Who I Am The Traffic is Encrypted
Bitnami MariaDB for Huawei Enterprise Cloud
 Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
Bitnami MariaDB for Huawei Enterprise Cloud First steps with the Bitnami MariaDB Stack Welcome to your new Bitnami application running on Huawei Enterprise Cloud! Here are a few questions (and answers!)
During security audits, over 15,000 vulnerability assessments are made, scanning the network IP by IP.
 Features LAN Guard Vulnerability scanning and Management Patch Management and Remediation Network and software Auditing Why Choose? 1. Powerful network, security and port scanner with network auditing
Features LAN Guard Vulnerability scanning and Management Patch Management and Remediation Network and software Auditing Why Choose? 1. Powerful network, security and port scanner with network auditing
Linux Kung Fu. Stephen James UBNetDef, Spring 2017
 Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
CS 356 Operating System Security. Fall 2013
 CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
CS 356 Operating System Security Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5 Database
Downloading and installing Db2 Developer Community Edition on Ubuntu Linux Roger E. Sanders Yujing Ke Published on October 24, 2018
 Downloading and installing Db2 Developer Community Edition on Ubuntu Linux Roger E. Sanders Yujing Ke Published on October 24, 2018 This guide will help you download and install IBM Db2 software, Data
Downloading and installing Db2 Developer Community Edition on Ubuntu Linux Roger E. Sanders Yujing Ke Published on October 24, 2018 This guide will help you download and install IBM Db2 software, Data
Masternode Setup Guide Local Wallet with VPS Server
 Masternode Setup Guide Local Wallet with VPS Server What you will need: 1) Local computer windows 7-10 2) Remote server VPS [vultr.com] 3) PuTTY to configure and setup VPS 4) 10,000 PHR If you would like
Masternode Setup Guide Local Wallet with VPS Server What you will need: 1) Local computer windows 7-10 2) Remote server VPS [vultr.com] 3) PuTTY to configure and setup VPS 4) 10,000 PHR If you would like
Jackson State University Department of Computer Science CSC / Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
Jackson State University Department of Computer Science CSC 437-01/539-01 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 2: Running Secure Shell (SSH) Server in a Virtual
We want to install putty, an ssh client on the laptops. In the web browser goto:
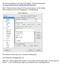 We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
We want to install putty, an ssh client on the laptops. In the web browser goto: www.chiark.greenend.org.uk/~sgtatham/putty/download.html Under Alternative binary files grab 32 bit putty.exe and put it
Ubuntu Practice and Configuration Post Installation Exercises interlab at AIT Bangkok, Thailand
 Ubuntu Practice and Configuration Post Installation Exercises interlab at AIT Bangkok, Thailand 1. Get used to using sudo 2. Create an inst account 3. Learn how to install software 4. Update /etc/apt/sources.list
Ubuntu Practice and Configuration Post Installation Exercises interlab at AIT Bangkok, Thailand 1. Get used to using sudo 2. Create an inst account 3. Learn how to install software 4. Update /etc/apt/sources.list
Getting Arduino / XLR8 Setup On Linux
 Getting Arduino / XLR8 Setup On Linux Unlike the Mac and Windows XLR8 packages, there are a couple of extra steps for getting XLR8 to run on Linux. There are three main focuses concentrated on in this
Getting Arduino / XLR8 Setup On Linux Unlike the Mac and Windows XLR8 packages, there are a couple of extra steps for getting XLR8 to run on Linux. There are three main focuses concentrated on in this
Nexpose. Hardening Guide. Product version: 6.0
 Nexpose Hardening Guide Product version: 6.0 Table of contents Table of contents 2 Revision history 3 File System 4 Installation 5 Configuration 6 Users 6 Services 6 Kernel Settings 6 CIS Benchmarks 8
Nexpose Hardening Guide Product version: 6.0 Table of contents Table of contents 2 Revision history 3 File System 4 Installation 5 Configuration 6 Users 6 Services 6 Kernel Settings 6 CIS Benchmarks 8
Bitnami Pimcore for Huawei Enterprise Cloud
 Bitnami Pimcore for Huawei Enterprise Cloud Description Pimcore is the open source platform for managing digital experiences. It is the consolidated platform for web content management, product information
Bitnami Pimcore for Huawei Enterprise Cloud Description Pimcore is the open source platform for managing digital experiences. It is the consolidated platform for web content management, product information
LOCAL WALLET (COLD WALLET):
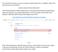 This tutorial will teach you how to create a masternode with a "cold/hot" setup. The whole process is as follows. LOCAL WALLET (COLD WALLET): Visit TRAID platform s official repository on GitHub and download
This tutorial will teach you how to create a masternode with a "cold/hot" setup. The whole process is as follows. LOCAL WALLET (COLD WALLET): Visit TRAID platform s official repository on GitHub and download
How To Start Mysql Using Linux Command Line Client In Ubuntu
 How To Start Mysql Using Linux Command Line Client In Ubuntu Step One: Install MySQL Client On Debian, Ubuntu or Linux Mint: Before you start typing commands at the MySQL prompt, remember that each In
How To Start Mysql Using Linux Command Line Client In Ubuntu Step One: Install MySQL Client On Debian, Ubuntu or Linux Mint: Before you start typing commands at the MySQL prompt, remember that each In
SSH. Partly a tool, partly an application Features:
 Internet security SSH 1 Secure Shell: SSH Partly a tool, partly an application Features: Encrypted login and shell connections Easy, drop-in replacements for rlogin, rsh, rcp Multiple means of authentication
Internet security SSH 1 Secure Shell: SSH Partly a tool, partly an application Features: Encrypted login and shell connections Easy, drop-in replacements for rlogin, rsh, rcp Multiple means of authentication
IMC inode Intelligent Client v7.0 (E0106) Copyright (c) Hewlett-Packard Development Company, L.P. and its licensors.
 IMC inode Intelligent Client v7.0 (E0106) Copyright (c) 2011-2014 Hewlett-Packard Development Company, L.P. and its licensors. Table of Contents 1. What's New in this Release 2. Problems Fixed in this
IMC inode Intelligent Client v7.0 (E0106) Copyright (c) 2011-2014 Hewlett-Packard Development Company, L.P. and its licensors. Table of Contents 1. What's New in this Release 2. Problems Fixed in this
FreeBSD Security Advisories
 Security FreeBSD Security Advisories http://www.freebsd.org/security/advisories.html 2 FreeBSD Security Advisories Advisory Security information Where to find it Web page (Security Advisories Channel)
Security FreeBSD Security Advisories http://www.freebsd.org/security/advisories.html 2 FreeBSD Security Advisories Advisory Security information Where to find it Web page (Security Advisories Channel)
Configure HOSTNAME by adding the hostname to the file /etc/sysconfig/network. Do the same to all the all nodes.
 Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
Network setup As the root user execute the command "ifconfig" on each host. Take a note of ipaddress's of all machines I have a home LAN so my addresses are class C which might be in the format 192.168.192.x.
