FlightPATH. User Manual:
|
|
|
- Elfreda Wade
- 6 years ago
- Views:
Transcription
1 User Manual: FlightPATH Author: Andrew Knowlson Review: Greg Howett Version: 1.0-DRAFT Date: 05 st April 2011 Created: 05 st April 2011 Modified
2 Contents: What is FlightPATH? So what can it do? How do I access FlightPath How do I Build a FlightPATH rule? o Conditions o Sense o Check o Variables o Actions How do I apply FlightPATH rules? Troubleshooting Page 2 of 11
3 What is flightpath: FlightPATH is a rule engine developed by jetnexus to intelligently manipulate and route HTTP and HTTPS traffic. It is highly configurable, very powerful and yet easy to use. A FlightPATH rule has three components: Conditions - Set multiple Criteria to trigger the rule Evaluation - Create custom variables that can be used in the Action Actions - The behaviour once the rule has triggered So what can it do? FlightPATH can be used to modify Incoming and Outgoing HTTP/S content and requests. As well as using simple string matches such as starts with, Ends With etc. For more for complete control powerful Perl compatible regular expressions can be implemented. In addition, custom variables can be created and used in the Action enabling many different possibilities Due to the configurable nature of FlightPATH the options are infinite but some common uses are as follows. Application firewalling and Security Force user to HTTPs for specific (or all) content Block or redirect spiders Prevent and alert cross site scripting Prevent and alert SQL injection Hide internal directory structure Secure directory for particular users Features Redirect users based on path Provide Single sign on across multiple system Segment users bases on User ID or Cookie Add headers for SSL offload Language detection Rewrite user request Fix broken URL s Prevent directory access/ browsing Send spiders different content Page 3 of 11
4 How do I access FlightPath? The FlightPATH Configuration options can be found in the following location (Configure FlightPATH) this will open the FlightPATH tab This will open the FlightPATH configuration screen: Page 4 of 11
5 How do I build a FlightPATH rule? A flight path rule consists of conditions and actions. Multiple conditions can be added and are always added together. To add a new rule click the Add New button on Details, this enables you to give the FlightPATH rule a name and also a Description. Multiple actions can also be created and are all executed if the conditions are met. Variables can also be created to set values to be dynamically included on the action response. Conditions new conditions can be added by clicking, Add new button. Multiple conditions can be use but all must be met for the rule to execute. To use an OR you would need to create an additional FlightPATH rule. Each condition contains three elements and a value or not depending on the condition. Some conditions can accept two values such as Cookie that can have the Match Value i.e. the cookie name and the Value i.e. the Value of the cookie The conditions are listed below: Condition Description Example Host Language This is the host extracted from the URL This is the Language extracted from the language HTTP header or This condition will produce a dropdown with a list of Languages Path This is the path of the website /mywebsite/index.asp Page 5 of 11
6 File Name This is the name of the file index.asp Cookie Query Query String The is the name of a cookie This is the name and Value of a Query as such it can either accept the query name or a value also. The is the whole query string after the? char Best=jetNEXUS Where the Match is Best and the Value is jetnexus Best=jetNEXUS&Name=Me Method This is a drop down of HTTP methods This is a dropdown that includes GET, POST etc Version This is the HTTP version HTTP/1.0 OR HTTP/1.1 Header This can be any HTTP Header Referrer, User-Agent, From, Date Sense The sense is allows you to create a positive match or a negative match Does Does not Value is true Value is not true Check This sets the condition for the rule being fired Check Description Example Exist Start End Check that the Match Item is present Check that the Match starts with the value in specified in the Value column Check that the Match Ends with the value in specified in the Value column Check Host starts with www Value = www = TRUE jetnexus.com = False Check Host Ends with com Value = com Page 6 of 11
7 Contain Checks any part of the Match for the Value = TRUE = False Check Host Contains jetnexus Value = jetnexus = TRUE = TRUE = FALSE Equal Check the Mach for an exact match Check Host Equals jetnexus Value = jetnexus = FALSE jetnexus = TRUE Have Length Check the length of the match Check the length of the Host Value=16 = TRUE = FALUE Match RegEX This enables you to enter a full Perl compatible regular expression. Test for IP Address ^(25[0-5] 2[0-4][0-9] [0-1]{1}[0-9]{2} [1-9]{1}[0-9]{1} [1-9])\.(25[0-5] 2[0-4][0-9] [0-1]{1}[0-9]{2} [1-9]{1}[0-9]{1} [1-9] 0)\.(25[0-5] 2[0-4][0-9] [0-1]{1}[0-9]{2} [1-9]{1}[0-9]{1} [1-9] 0)\.(25[0-5] 2[0-4][0-9] [0-1]{1}[0-9]{2} [1-9]{1}[0-9]{1} [0-9])$ Page 7 of 11
8 So for example we create a condition if the Path does contain the IP Address , the actions and Evaluations can be applied to it. Evaluation Adding a Variable is a very powerful feature that will allow you to extract data from the request and include this in the actions. For example you could log a user username or send an if there is a security problem. New Variables can be added by clicking, Add New button. A variable name has to be in the following format $name$ So for example we would like the create a variable of the file extension $fileextension$ = Path (From the drop down) = Page 8 of 11
9 Actions new actions can be added by clicking, Add New button. The action is the task or tasks that are enabled once the rule is fired. Actions Description Data Rewrite Path Redirect Log Event Drop This will allow you to redirect the request to new URL This will issue a permanent redirect This will log an event to the System log Will send an . You can use a variable as the address or the message This will drop the connection You can use this redirect to by setting a Variable to the path and URL So for example we create a redirect action so the URL is redirected to an external site. Page 9 of 11
10 How do I apply FlightPATH rules? FlightPATH rules are designed to manipulate HTTP traffic as such the option for flightpath is not visible for non HTTP protocols. To enable a FlightPATH rule go to (Setup IP Services) page. This will open the IP Service tab Flight path rules can be applied in the IP services screen under Action. The list of available rules is on the right and the current rules in use are on the left. To add a new rule drag and drop the rule into position. The order for execution is important and will start with the top rule being executed fist. To change the order simple drag and drop into the correct location. To remove a rule simply drag and drop it back to the rule inventory. Page 10 of 11
11 Troubleshooting Further help can be found on the jetnexus websites I hope you have found this User Manual informative, but if you need any clarification or further information, please do not hesitate to get in contact with jetnexus Support: support@jetnexus.com Phone+44 (0870) Check out our blog Follow us on twitter Page 11 of 11
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
jetnexus Virtual Load Balancer
 jetnexus Virtual Load Balancer Mitigate the Risk of Downtime and Optimise Application Delivery We were looking for a robust yet easy to use solution that would fit in with our virtualisation policy and
jetnexus Virtual Load Balancer Mitigate the Risk of Downtime and Optimise Application Delivery We were looking for a robust yet easy to use solution that would fit in with our virtualisation policy and
jetnexus Virtual Load Balancer
 jetnexus Virtual Load Balancer Mitigate the Risk of Downtime and Optimise Application Delivery We were looking for a robust yet easy to use solution that would fit in with our virtualisation policy and
jetnexus Virtual Load Balancer Mitigate the Risk of Downtime and Optimise Application Delivery We were looking for a robust yet easy to use solution that would fit in with our virtualisation policy and
jetnexus Load Balancer
 Mitigate the Risk of Downtime and Optimise Application Delivery jetnexus load balancers improve the performance, scalability and reliability of applications for a superb end user experience. Our business
Mitigate the Risk of Downtime and Optimise Application Delivery jetnexus load balancers improve the performance, scalability and reliability of applications for a superb end user experience. Our business
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
SCRIPT REFERENCE. UBot Studio Version 4. The Settings Commands
 SCRIPT REFERENCE UBot Studio Version 4 The Settings Commands This entire section of commands is related specifically to settings that are available for the main browser as well as the in new browser command.
SCRIPT REFERENCE UBot Studio Version 4 The Settings Commands This entire section of commands is related specifically to settings that are available for the main browser as well as the in new browser command.
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Cloud Help for Community Managers...3. Release Notes System Requirements Administering Jive for Office... 6
 for Office Contents 2 Contents Cloud Help for Community Managers...3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
for Office Contents 2 Contents Cloud Help for Community Managers...3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
IMPORT GUIDE. PowerPhone
 IMPORT GUIDE PowerPhone Contents Import... 3 Register... 6 Setup Tab & Configuration... 7 Grid Mapping... 8 Search... 9 Record to Pop... 9 Reading Pane... 10 Settings Tab... 11 Record Page... 11 Search
IMPORT GUIDE PowerPhone Contents Import... 3 Register... 6 Setup Tab & Configuration... 7 Grid Mapping... 8 Search... 9 Record to Pop... 9 Reading Pane... 10 Settings Tab... 11 Record Page... 11 Search
ForeScout Extended Module for ArcSight
 Version 2.8 Table of Contents About the ArcSight Integration... 4 Use Cases... 4 Send Endpoint Status, Compliance, or Property Changes from CounterACT to ArcSight... 5 SmartConnector Health and Compliance
Version 2.8 Table of Contents About the ArcSight Integration... 4 Use Cases... 4 Send Endpoint Status, Compliance, or Property Changes from CounterACT to ArcSight... 5 SmartConnector Health and Compliance
Filtering - Zimbra
 Filtering Email - Zimbra Email filtering allows you to definite rules to manage incoming email. For instance, you may apply a filter on incoming email to route particular emails into folders or delete
Filtering Email - Zimbra Email filtering allows you to definite rules to manage incoming email. For instance, you may apply a filter on incoming email to route particular emails into folders or delete
Prophet 21 CommerceCenter Automating Workflow with Business Alerts. This class is designed for anyone in your organization that is:
 Prophet 21 CommerceCenter Automating Workflow with Business Alerts This class is designed for anyone in your organization that is: familiar with the CommerceCenter processes and transactions looking to
Prophet 21 CommerceCenter Automating Workflow with Business Alerts This class is designed for anyone in your organization that is: familiar with the CommerceCenter processes and transactions looking to
release notes effective version 10.3 ( )
 Introduction We are pleased to announce that Issuetrak 10.3 is available today! 10.3 focuses on improved security, introducing a new methodology for storing passwords. This document provides a brief outline
Introduction We are pleased to announce that Issuetrak 10.3 is available today! 10.3 focuses on improved security, introducing a new methodology for storing passwords. This document provides a brief outline
How to Configure User Authentication and Access Control
 How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or
How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or
ForeScout Extended Module for HPE ArcSight
 ForeScout Extended Module for HPE ArcSight Version 2.7.1 Table of Contents About the HPE ArcSight Integration... 4 Use Cases... 4 Send Endpoint Status, Compliance, or Property Changes from CounterACT to
ForeScout Extended Module for HPE ArcSight Version 2.7.1 Table of Contents About the HPE ArcSight Integration... 4 Use Cases... 4 Send Endpoint Status, Compliance, or Property Changes from CounterACT to
IMPORT GUIDE. PowerPhone
 IMPORT GUIDE PowerPhone Contents Import... 3 Register... 6 Setup Tab & Configuration... 7 Grid Mapping... 8 Search... 9 Record to Pop... 9 Reading Pane... 10 Settings Tab... 11 Record Page... 11 Search
IMPORT GUIDE PowerPhone Contents Import... 3 Register... 6 Setup Tab & Configuration... 7 Grid Mapping... 8 Search... 9 Record to Pop... 9 Reading Pane... 10 Settings Tab... 11 Record Page... 11 Search
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1
 What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
How to configure the UTM Web Application Firewall for Microsoft Lync Web Services connectivity
 How to configure the UTM Web Application Firewall for Microsoft Lync Web Services connectivity This article explains how to configure your Sophos UTM to allow access Microsoft s Lync Web Services (the
How to configure the UTM Web Application Firewall for Microsoft Lync Web Services connectivity This article explains how to configure your Sophos UTM to allow access Microsoft s Lync Web Services (the
BIG-IP DataSafe Configuration. Version 13.1
 BIG-IP DataSafe Configuration Version 13.1 Table of Contents Table of Contents Adding BIG-IP DataSafe to the BIG-IP System...5 Overview: Adding BIG-IP DataSafe to the BIG-IP system... 5 Provisioning Fraud
BIG-IP DataSafe Configuration Version 13.1 Table of Contents Table of Contents Adding BIG-IP DataSafe to the BIG-IP System...5 Overview: Adding BIG-IP DataSafe to the BIG-IP system... 5 Provisioning Fraud
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP System v10 with Microsoft IIS 7.0 and 7.5
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v10 with Microsoft IIS 7.0 and 7.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft IIS Prerequisites and configuration
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v10 with Microsoft IIS 7.0 and 7.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft IIS Prerequisites and configuration
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Secure Parameter Filter (SPF) (AKA Protecting Vulnerable Applications with IIS7) Justin Clarke, Andrew Carey Nairn
 Secure Parameter Filter (SPF) (AKA Protecting Vulnerable Applications with IIS7) Justin Clarke, Andrew Carey Nairn Our Observations The same old code-level problems Input Validation, Parameter Manipulation,
Secure Parameter Filter (SPF) (AKA Protecting Vulnerable Applications with IIS7) Justin Clarke, Andrew Carey Nairn Our Observations The same old code-level problems Input Validation, Parameter Manipulation,
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP System v9.x with Microsoft IIS 7.0 and 7.5
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v9.x with Microsoft IIS 7.0 and 7.5 Deploying F5 with Microsoft IIS 7.0 and 7.5 F5's BIG-IP system can increase the existing benefits of deploying
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v9.x with Microsoft IIS 7.0 and 7.5 Deploying F5 with Microsoft IIS 7.0 and 7.5 F5's BIG-IP system can increase the existing benefits of deploying
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
BIG-IP Analytics: Implementations. Version 13.1
 BIG-IP Analytics: Implementations Version 13.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles... 5 Overview:
BIG-IP Analytics: Implementations Version 13.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles... 5 Overview:
DEPLOYMENT GUIDE DEPLOYING THE BIG-IP SYSTEM WITH BEA WEBLOGIC SERVER
 DEPLOYMENT GUIDE DEPLOYING THE BIG-IP SYSTEM WITH BEA WEBLOGIC SERVER Deploying the BIG-IP LTM system for BEA WebLogic Server F5 Networks and BEA systems have created a highly effective way to direct traffic
DEPLOYMENT GUIDE DEPLOYING THE BIG-IP SYSTEM WITH BEA WEBLOGIC SERVER Deploying the BIG-IP LTM system for BEA WebLogic Server F5 Networks and BEA systems have created a highly effective way to direct traffic
Web insecurity Security strategies General security Listing of server-side risks Language specific security. Web Security.
 Web Security Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming Web Security Slide 1/25 Outline Web insecurity Security strategies General security Listing of server-side risks Language
Web Security Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming Web Security Slide 1/25 Outline Web insecurity Security strategies General security Listing of server-side risks Language
LOD Data GW Installation (1.0)
 LOD Data GW Installation (1.0) 1. Installation of IIS Role in Windows Server (2008R2 or later Operating System)... 1 1. Installation of IIS Role in Windows Server, continued (2008R2 or later Operating
LOD Data GW Installation (1.0) 1. Installation of IIS Role in Windows Server (2008R2 or later Operating System)... 1 1. Installation of IIS Role in Windows Server, continued (2008R2 or later Operating
Deploying the BIG-IP System v10 with Oracle s BEA WebLogic
 DEPLOYMENT GUIDE Deploying the BIG-IP System v10 with Oracle s BEA WebLogic Version 1.0 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Oracle s BEA WebLogic Prerequisites and
DEPLOYMENT GUIDE Deploying the BIG-IP System v10 with Oracle s BEA WebLogic Version 1.0 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Oracle s BEA WebLogic Prerequisites and
Release Notes Version 7.8
 Please Read Before Updating Before installing any firmware version, be sure to make a backup of your configuration and read all release notes that apply to versions more recent than the one currently running
Please Read Before Updating Before installing any firmware version, be sure to make a backup of your configuration and read all release notes that apply to versions more recent than the one currently running
1. INTRODUCTION to Object Storage
 1. INTRODUCTION to Object Storage Welcome to AURO Enterprise Cloud! This document will be help you get started using our Object Storage service. Object Storage is a storage system where objects are stored
1. INTRODUCTION to Object Storage Welcome to AURO Enterprise Cloud! This document will be help you get started using our Object Storage service. Object Storage is a storage system where objects are stored
Web Browser Application Troubleshooting Guide. Table of Contents
 Web Browser Application Troubleshooting Guide The following trouble shooting guide outlines tips for common problems which may resolve incorrect or unexpected behavior of NMFTA s web based applications.
Web Browser Application Troubleshooting Guide The following trouble shooting guide outlines tips for common problems which may resolve incorrect or unexpected behavior of NMFTA s web based applications.
WhosOn server help
 server help Server help Important For WhosOn to work, you will need to ensure that certain ports are open in the firewall. With the default setup for WhosOn, you would need to open ports 80, 443, 8080
server help Server help Important For WhosOn to work, you will need to ensure that certain ports are open in the firewall. With the default setup for WhosOn, you would need to open ports 80, 443, 8080
Detects Potential Problems. Customizable Data Columns. Support for International Characters
 Home Buy Download Support Company Blog Features Home Features HttpWatch Home Overview Features Compare Editions New in Version 9.x Awards and Reviews Download Pricing Our Customers Who is using it? What
Home Buy Download Support Company Blog Features Home Features HttpWatch Home Overview Features Compare Editions New in Version 9.x Awards and Reviews Download Pricing Our Customers Who is using it? What
BIG-IP Application Security Manager : Attack and Bot Signatures. Version 13.0
 BIG-IP Application Security Manager : Attack and Bot Signatures Version 13.0 Table of Contents Table of Contents Assigning Attack Signatures to Security Policies...5 About attack signatures...5 About
BIG-IP Application Security Manager : Attack and Bot Signatures Version 13.0 Table of Contents Table of Contents Assigning Attack Signatures to Security Policies...5 About attack signatures...5 About
dotdefender v5.18 User Guide
 dotdefender v5.18 User Guide Applicure Web Application Firewall Table of Contents 1. Introduction... 5 1.1 Overview... 5 1.2 Components... 6 1.3 Benefits... 7 1.4 Organization of this Guide... 8 2. Getting
dotdefender v5.18 User Guide Applicure Web Application Firewall Table of Contents 1. Introduction... 5 1.1 Overview... 5 1.2 Components... 6 1.3 Benefits... 7 1.4 Organization of this Guide... 8 2. Getting
F5 Big-IP Application Security Manager v11
 F5 F5 Big-IP Application Security Manager v11 Code: ACBE F5-ASM Days: 4 Course Description: This four-day course gives networking professionals a functional understanding of the BIG- IP LTM v11 system
F5 F5 Big-IP Application Security Manager v11 Code: ACBE F5-ASM Days: 4 Course Description: This four-day course gives networking professionals a functional understanding of the BIG- IP LTM v11 system
Activant Prophet 21. Automating Workflow with Business Alerts
 Activant Prophet 21 Automating Workflow with Business Alerts This class is designed for Anyone in your organization that is familiar with the Prophet 21 processes and transactions looking to streamline
Activant Prophet 21 Automating Workflow with Business Alerts This class is designed for Anyone in your organization that is familiar with the Prophet 21 processes and transactions looking to streamline
Step by Step SQL Server Alerts and Operator Notifications
 Step by Step SQL Server Alerts and Email Operator Notifications Hussain Shakir LinkedIn: https://www.linkedin.com/in/mrhussain Twitter: https://twitter.com/hshakir_ms Blog: http://mstechguru.blogspot.ae/
Step by Step SQL Server Alerts and Email Operator Notifications Hussain Shakir LinkedIn: https://www.linkedin.com/in/mrhussain Twitter: https://twitter.com/hshakir_ms Blog: http://mstechguru.blogspot.ae/
CUSTOMER CONTROL PANEL... 2 DASHBOARD... 3 HOSTING &
 Table of Contents CUSTOMER CONTROL PANEL... 2 LOGGING IN... 2 RESET YOUR PASSWORD... 2 DASHBOARD... 3 HOSTING & EMAIL... 4 WEB FORWARDING... 4 WEBSITE... 5 Usage... 5 Subdomains... 5 SSH Access... 6 File
Table of Contents CUSTOMER CONTROL PANEL... 2 LOGGING IN... 2 RESET YOUR PASSWORD... 2 DASHBOARD... 3 HOSTING & EMAIL... 4 WEB FORWARDING... 4 WEBSITE... 5 Usage... 5 Subdomains... 5 SSH Access... 6 File
ATS Test Documentation
 ATS Test Documentation Release 0.1 Feifei Cai Jul 20, 2017 Contents 1 HTTP 3 1.1 Keep-alive................................................ 3 1.2 Connection Timeouts...........................................
ATS Test Documentation Release 0.1 Feifei Cai Jul 20, 2017 Contents 1 HTTP 3 1.1 Keep-alive................................................ 3 1.2 Connection Timeouts...........................................
Snapt Accelerator Manual
 Snapt Accelerator Manual Version 2.0 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 3 Accelerator Dashboard... 4 Standard Configuration Default Settings... 5 Standard Configuration
Snapt Accelerator Manual Version 2.0 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 3 Accelerator Dashboard... 4 Standard Configuration Default Settings... 5 Standard Configuration
Center for Academic Excellence engaging faculty inspiring learning. WordPress Quick-Reference Manual
 Center for Academic Excellence engaging faculty inspiring learning WordPress Quick-Reference Manual Contents Signing up for a WordPress account... 2 Adding a new blog... 2 Changing the theme of your blog...
Center for Academic Excellence engaging faculty inspiring learning WordPress Quick-Reference Manual Contents Signing up for a WordPress account... 2 Adding a new blog... 2 Changing the theme of your blog...
Hostopia WebMail Help
 Hostopia WebMail Help Table of Contents GETTING STARTED WITH WEBMAIL...5 Version History...6 Introduction to WebMail...6 Cookies and WebMail...6 Logging in to your account...6 Connection time limit...7
Hostopia WebMail Help Table of Contents GETTING STARTED WITH WEBMAIL...5 Version History...6 Introduction to WebMail...6 Cookies and WebMail...6 Logging in to your account...6 Connection time limit...7
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
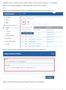 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
8.0 Help for Community Managers Release Notes System Requirements Administering Jive for Office... 6
 for Office Contents 2 Contents 8.0 Help for Community Managers... 3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
for Office Contents 2 Contents 8.0 Help for Community Managers... 3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
BIG-IP Access Policy Manager : Portal Access. Version 12.1
 BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
Citrix 1Y0-240 Exam. Volume: 69 Questions
 Volume: 69 Questions Question: 1 Scenario: A NetScaler is configured with the following modes: *MBF *USIP *USNIP *Layer 3 mode A Citrix Administrator configured a new router and now requires some of the
Volume: 69 Questions Question: 1 Scenario: A NetScaler is configured with the following modes: *MBF *USIP *USNIP *Layer 3 mode A Citrix Administrator configured a new router and now requires some of the
HTTP Protocol and Server-Side Basics
 HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
Andrew Muller, Canberra Managing Director, Ionize, Canberra The challenges of Security Testing. Security Testing. Taming the Wild West
 Andrew Muller, Canberra Managing Director, Ionize, Canberra The challenges of Security Testing Advancing Expertise in Security Testing Taming the Wild West Canberra, Australia 1 Who is this guy? Andrew
Andrew Muller, Canberra Managing Director, Ionize, Canberra The challenges of Security Testing Advancing Expertise in Security Testing Taming the Wild West Canberra, Australia 1 Who is this guy? Andrew
Crystal Enterprise. Overview. Contents. Web Server Overview - Internet Information System (IIS)
 Overview Contents This document provides an overview to web server technology particularly Microsoft s Internet Information Server (IIS) and its relationship with. Although this article has been written
Overview Contents This document provides an overview to web server technology particularly Microsoft s Internet Information Server (IIS) and its relationship with. Although this article has been written
Nuvia End-User Portal Quick Reference Guide
 Nuvia End-User Portal Quick Reference Guide This user guide illustrates Nuvia End-User Portal features and use, enabling end-users to listen to messages, manage their address book, set-up routing rules,
Nuvia End-User Portal Quick Reference Guide This user guide illustrates Nuvia End-User Portal features and use, enabling end-users to listen to messages, manage their address book, set-up routing rules,
Akamai Workbook QUICK 30 MIN TUTORIALS VERSION 2
 Akamai Workbook QUICK 30 MIN TUTORIALS VERSION 2 Akamai Workbook Part 2 More adventures, for users who have completed the Akamai Workbook Sign up for the Akamai Developer Program Get access to the latest
Akamai Workbook QUICK 30 MIN TUTORIALS VERSION 2 Akamai Workbook Part 2 More adventures, for users who have completed the Akamai Workbook Sign up for the Akamai Developer Program Get access to the latest
Sophos UTM Web Application Firewall For: Microsoft Exchange Services
 How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
Adding your IMAP Mail Account in Outlook 2013 on Windows
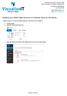 Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Notification Module Script
 Notification Module Script The notification module enables the user to specify a set of notification events that could occur during data transactions and as a result trigger the automatic generation of
Notification Module Script The notification module enables the user to specify a set of notification events that could occur during data transactions and as a result trigger the automatic generation of
Learn how to login to Sitefinity and what possible errors you can get if you do not have proper permissions.
 USER GUIDE This guide is intended for users of all levels of expertise. The guide describes in detail Sitefinity user interface - from logging to completing a project. Use it to learn how to create pages
USER GUIDE This guide is intended for users of all levels of expertise. The guide describes in detail Sitefinity user interface - from logging to completing a project. Use it to learn how to create pages
Checklist for Testing of Web Application
 Checklist for Testing of Web Application Web Testing in simple terms is checking your web application for potential bugs before its made live or before code is moved into the production environment. During
Checklist for Testing of Web Application Web Testing in simple terms is checking your web application for potential bugs before its made live or before code is moved into the production environment. During
End User Monitoring. AppDynamics Pro Documentation. Version Page 1
 End User Monitoring AppDynamics Pro Documentation Version 4.1.1 Page 1 End User Monitoring....................................................... 4 Browser Real User Monitoring.............................................
End User Monitoring AppDynamics Pro Documentation Version 4.1.1 Page 1 End User Monitoring....................................................... 4 Browser Real User Monitoring.............................................
Security Provider Integration Kerberos Authentication
 Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Data Import Assistant
 System Administrator's Handbook Data Import Assistant Introduction Overview The Data Import Assistant is a utility program designed to assist in importing new part definitions and pricing information into
System Administrator's Handbook Data Import Assistant Introduction Overview The Data Import Assistant is a utility program designed to assist in importing new part definitions and pricing information into
TaskCentre v4.5 SalesLogix Connector Tool White Paper
 TaskCentre v4.5 SalesLogix Connector Tool White Paper Document Number: WP010-04 Issue: 01 Orbis Software Limited 2008 Table of Contents ABOUT SALESLOGIX CONNECTOR TOOL... 1 INTRODUCTION... 3 SalesLogix
TaskCentre v4.5 SalesLogix Connector Tool White Paper Document Number: WP010-04 Issue: 01 Orbis Software Limited 2008 Table of Contents ABOUT SALESLOGIX CONNECTOR TOOL... 1 INTRODUCTION... 3 SalesLogix
Argos Version 3.1 Release Guide, Version 1.0 Last Updated 04/04/2008 TABLE OF CONTENTS. Introduction MAP Server Updates... 4
 Argos Version 3.1 Release Guide Document version 1.0 TABLE OF CONTENTS Introduction... 3 MAP Server Updates... 4 Thread Lock Fix... 4 Individual Processes for Each Scheduled Report... 4 Automatic Termination
Argos Version 3.1 Release Guide Document version 1.0 TABLE OF CONTENTS Introduction... 3 MAP Server Updates... 4 Thread Lock Fix... 4 Individual Processes for Each Scheduled Report... 4 Automatic Termination
Fireware-Essentials. Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.
 Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Administering isupport
 Administering isupport Tracking and Monitoring isupport Usage Agents perform tasks in the background that are an integral part of isupport functionality. See Enabling and Scheduling Agents on page 2 for
Administering isupport Tracking and Monitoring isupport Usage Agents perform tasks in the background that are an integral part of isupport functionality. See Enabling and Scheduling Agents on page 2 for
SOAP Integration - 1
 SOAP Integration - 1 SOAP (Simple Object Access Protocol) can be used to import data (actual values) from Web Services that have been published by companies or organizations that want to provide useful
SOAP Integration - 1 SOAP (Simple Object Access Protocol) can be used to import data (actual values) from Web Services that have been published by companies or organizations that want to provide useful
XIA Configuration Server
 XIA Configuration Server XIA Configuration Server v6 Cloud Services Quick Start Guide Tuesday, 20 May 2014 1 P a g e X I A C o n f i g u r a t i o n C l o u d S e r v i c e s Contents Overview... 3 Creating
XIA Configuration Server XIA Configuration Server v6 Cloud Services Quick Start Guide Tuesday, 20 May 2014 1 P a g e X I A C o n f i g u r a t i o n C l o u d S e r v i c e s Contents Overview... 3 Creating
Kerio Control. User Guide. Kerio Technologies
 Kerio Control User Guide Kerio Technologies 2017 Kerio Technologies s.r.o. Contents Viewing activity reports in Kerio Control Statistics......................... 5 Overview..................................................................
Kerio Control User Guide Kerio Technologies 2017 Kerio Technologies s.r.o. Contents Viewing activity reports in Kerio Control Statistics......................... 5 Overview..................................................................
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
Mastering phpmyadmiri 3.4 for
 Mastering phpmyadmiri 3.4 for Effective MySQL Management A complete guide to getting started with phpmyadmin 3.4 and mastering its features Marc Delisle [ t]open so 1 I community experience c PUBLISHING
Mastering phpmyadmiri 3.4 for Effective MySQL Management A complete guide to getting started with phpmyadmin 3.4 and mastering its features Marc Delisle [ t]open so 1 I community experience c PUBLISHING
Proxying. Why and How. Alon Altman. Haifa Linux Club. Proxying p.1/24
 Proxying p.1/24 Proxying Why and How Alon Altman alon@haifux.org Haifa Linux Club Proxying p.2/24 Definition proxy \Prox"y\, n.; pl. Proxies. The agency for another who acts through the agent; authority
Proxying p.1/24 Proxying Why and How Alon Altman alon@haifux.org Haifa Linux Club Proxying p.2/24 Definition proxy \Prox"y\, n.; pl. Proxies. The agency for another who acts through the agent; authority
Adding Items to the Course Menu
 Adding Items to the Course Menu The course menu, located in the upper left of the screen, contains links to materials and tools within the course. To add more items to the menu, click the plus sign at
Adding Items to the Course Menu The course menu, located in the upper left of the screen, contains links to materials and tools within the course. To add more items to the menu, click the plus sign at
How to Configure User Authentication and Access Control
 How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or
How to Configure User Authentication and Access Control For user authentication with the HTTP Proxy, the external authentication scheme that you can use depends on the proxy mode. With a transparent or
MYOB EXO Business Services
 MYOB EXO Business Services Release Notes 1.3 SP1 Contents Introduction 1 What s New in this Release?... 1 Installation 2 Pre-Install Requirements... 2 Installing the EXO Business Services... 2 Setting
MYOB EXO Business Services Release Notes 1.3 SP1 Contents Introduction 1 What s New in this Release?... 1 Installation 2 Pre-Install Requirements... 2 Installing the EXO Business Services... 2 Setting
Kaseya 2. Installation guide. Version R8. English
 Kaseya 2 Kaseya Server Setup Installation guide Version R8 English October 24, 2014 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Kaseya 2 Kaseya Server Setup Installation guide Version R8 English October 24, 2014 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Configuring User Defined Patterns
 The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
The allows you to create customized data patterns which can be detected and handled according to the configured security settings. The uses regular expressions (regex) to define data type patterns. Custom
BI Office. Web Authentication Model Guide Version 6
 Web Authentication Model Guide Version 6 Copyright Pyramid Analytics 2010-2016 Contents 1. Web Authentication Model Overview... 3 A. Basic Authentication Models... 3 B. Windows Authentication Models...
Web Authentication Model Guide Version 6 Copyright Pyramid Analytics 2010-2016 Contents 1. Web Authentication Model Overview... 3 A. Basic Authentication Models... 3 B. Windows Authentication Models...
Force.com Sites Implementation Guide
 Force.com Sites Implementation Guide Salesforce, Spring 18 @salesforcedocs Last updated: February 23, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Force.com Sites Implementation Guide Salesforce, Spring 18 @salesforcedocs Last updated: February 23, 2018 Copyright 2000 2018 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
CIS 700/002 : Special Topics : OWASP ZED (ZAP)
 CIS 700/002 : Special Topics : OWASP ZED (ZAP) Hitali Sheth CIS 700/002: Security of EMBS/CPS/IoT Department of Computer and Information Science School of Engineering and Applied Science University of
CIS 700/002 : Special Topics : OWASP ZED (ZAP) Hitali Sheth CIS 700/002: Security of EMBS/CPS/IoT Department of Computer and Information Science School of Engineering and Applied Science University of
SAS Workflow Manager 2.1: Quick Start Tutorial
 SAS Workflow Manager 2.1: Quick Start Tutorial Overview This Quick Start tutorial introduces the workflow design features of SAS Workflow Manager. It covers the most common tasks that you use to create
SAS Workflow Manager 2.1: Quick Start Tutorial Overview This Quick Start tutorial introduces the workflow design features of SAS Workflow Manager. It covers the most common tasks that you use to create
Automated SQL Ownage Techniques. OWASP October 30 th, The OWASP Foundation
 Automated SQL Ownage Techniques October 30 th, 2009 Sebastian Cufre Developer Core Security Technologies sebastian.cufre@coresecurity.com Copyright The Foundation Permission is granted to copy, distribute
Automated SQL Ownage Techniques October 30 th, 2009 Sebastian Cufre Developer Core Security Technologies sebastian.cufre@coresecurity.com Copyright The Foundation Permission is granted to copy, distribute
Kishin Fatnani. Founder & Director K-Secure. Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009
 Securing Web Applications: Defense Mechanisms Kishin Fatnani Founder & Director K-Secure Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009 1 Agenda Current scenario in Web Application
Securing Web Applications: Defense Mechanisms Kishin Fatnani Founder & Director K-Secure Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009 1 Agenda Current scenario in Web Application
(CNS-301) Citrix NetScaler 11 Advance Implementation
 (CNS-301) Citrix NetScaler 11 Advance Implementation Overview Designed for students with previous NetScaler experience, this course is best suited for individuals who will be deploying or managing advanced
(CNS-301) Citrix NetScaler 11 Advance Implementation Overview Designed for students with previous NetScaler experience, this course is best suited for individuals who will be deploying or managing advanced
BIG-IP Analytics: Implementations. Version 12.1
 BIG-IP Analytics: Implementations Version 12.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles...5 Overview: Collecting
BIG-IP Analytics: Implementations Version 12.1 Table of Contents Table of Contents Setting Up Application Statistics Collection...5 What is Analytics?...5 About HTTP Analytics profiles...5 Overview: Collecting
ForeScout Extended Module for VMware AirWatch MDM
 ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
Example - Reverse Proxy for Exchange Services
 The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure
 Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and
ForeScout Extended Module for MobileIron
 Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Integrate Microsoft IIS
 Integrate Microsoft IIS EventTracker Enterprise Publication Date: Jan. 5, 2017 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract IIS (Internet Information Services) is
Integrate Microsoft IIS EventTracker Enterprise Publication Date: Jan. 5, 2017 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract IIS (Internet Information Services) is
Using AD360 as a reverse proxy server
 Using AD360 as a reverse proxy server www.manageengine.com/active-directory-360/ Table of Contents Document summary 1 What is a reverse proxy? 1 Configuring AD360 as a reverse proxy 2 Enabling a context-based
Using AD360 as a reverse proxy server www.manageengine.com/active-directory-360/ Table of Contents Document summary 1 What is a reverse proxy? 1 Configuring AD360 as a reverse proxy 2 Enabling a context-based
Unified Management Console
 Unified Management Console Transition Guide The unified management console provides the same functionality that the older MailGuard and WebGuard management consoles provided if not more. This guide is
Unified Management Console Transition Guide The unified management console provides the same functionality that the older MailGuard and WebGuard management consoles provided if not more. This guide is
ForeScout Extended Module for MaaS360
 Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
dotdefender User Guide Applicure Web Application Firewall
 dotdefender User Guide Applicure Web Application Firewall Table of Contents Chapter 1 Introduction... 5 1.1 Overview... 5 1.2 Components... 6 1.2.1 Specific Windows components... 6 1.2.2 Specific Linux/Unix
dotdefender User Guide Applicure Web Application Firewall Table of Contents Chapter 1 Introduction... 5 1.1 Overview... 5 1.2 Components... 6 1.2.1 Specific Windows components... 6 1.2.2 Specific Linux/Unix
Access Control Rules: Realms and Users
 The following topics describe how to control user traffic on your network: Realm, User, User Group, and ISE Attribute (SGT, Endpoint Profile, and Endpoint Location) Access Control Rule Conditions, page
The following topics describe how to control user traffic on your network: Realm, User, User Group, and ISE Attribute (SGT, Endpoint Profile, and Endpoint Location) Access Control Rule Conditions, page
SharpSchool Chapter 7 USER MANUAL EXTERNAL LINK PAGE For more information, please visit:
 SHARPSCHOOL USER MANUAL CHAPTER 7 EXTERNAL LINK PAGE For more information, please visit: www.customernet.sharpschool.com www.sharpschool.com 0 TABLE OF CONTENTS 1. 2. 3. 4. INTRODUCTION... 1 KEY INFORMATION...
SHARPSCHOOL USER MANUAL CHAPTER 7 EXTERNAL LINK PAGE For more information, please visit: www.customernet.sharpschool.com www.sharpschool.com 0 TABLE OF CONTENTS 1. 2. 3. 4. INTRODUCTION... 1 KEY INFORMATION...
Content Rules. Feature Description
 Feature Description UPDATED: 11 January 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks
Feature Description UPDATED: 11 January 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks
User Manual. Admin Report Kit for IIS (ARKIIS)
 User Manual Admin Report Kit for IIS (ARKIIS) Table of Contents 1 Admin Report Kit for Internet Information Server-(ARKIIS)... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements...
User Manual Admin Report Kit for IIS (ARKIIS) Table of Contents 1 Admin Report Kit for Internet Information Server-(ARKIIS)... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements...
Snapt WAF Manual. Version 1.2. February pg. 1
 Snapt WAF Manual Version 1.2 February 2018 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 3 IP Blacklisting IP Groups... 4 IP Blacklisting IP Access Control... 5 IP Blacklisting
Snapt WAF Manual Version 1.2 February 2018 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 3 IP Blacklisting IP Groups... 4 IP Blacklisting IP Access Control... 5 IP Blacklisting
High Availability Configuration Guide
 High Availability Configuration Guide Table of Contents PURPOSE OF THE DOCUMENT 3 ABOUT EVENTLOG ANALYZER 3 WHY IT IS NECESSARY TO ENSURE HIGH AVAILABILITY OF EVENTLOG ANALYZER? 3 WORKING OF HIGH AVAILABILITY
High Availability Configuration Guide Table of Contents PURPOSE OF THE DOCUMENT 3 ABOUT EVENTLOG ANALYZER 3 WHY IT IS NECESSARY TO ENSURE HIGH AVAILABILITY OF EVENTLOG ANALYZER? 3 WORKING OF HIGH AVAILABILITY
