Web server reconnaissance
|
|
|
- Chrystal Hardy
- 5 years ago
- Views:
Transcription
1 Web server reconnaissance
2 Reconnaissance and fingerprinting Finding information about a target web server/web site May be illegal to perform reconnaissance on a web server and web site without prior approval/permission. Simulate via war games to demonstrate issues with trusting clients with URLs and filenames Fingerprinting information Name and version of server Database backend Use of reverse proxy (nginx) Programming language and web application server
3 1. Viewing HTTP headers $ nc C vulnerable 80 GET / HTTP/1.1 Host: vulnerable HTTP/ OK Date: Sun, 03 Mar :56:20 GMT Server: Apache/ (Debian) X-Powered-By: PHP/ squeeze14 Content-Length: 6988 Content-Type: text/html $ nc C oregonctf.org 80 HEAD / HTTP/1.1 Host: foobar $ nc C cs410.oregonctf.org 80 HEAD / HTTP/1.1 Host: cs410.oregonctf.org
4 2. Viewing source content Look for comments, links, or directory structure Wikipedia (en.wikipedia.org) Mercedes-Benz (
5 2. Viewing source content Hyatt.com GitHub Hint: Asset cache busting pipeline Blackboard
6 2. Viewing source content External services
7 3. Search engine signals Google, Yahoo, Bing, will crawl everything on your site unless you tell them otherwise. Prevent via use of robots.txt file Instructs search engine spiders how to interact with your content. Can also reveal sensitive information
8 3. Search engine signals For hacker, robots.txt can contain interesting folders, files, and data to investigate. Sometimes even passwords, usernames,... Example Specifies that no robots should visit any URL starting with "/cyberworld/map/" or "/tmp/", or /foo.html.
9 # If the Joomla site is installed within a folder such as at # e.g. the robots.txt file MUST be # moved to the site root at e.g. # AND the joomla folder name MUST be prefixed to the disallowed # path, e.g. the Disallow rule for the /administrator/ folder # MUST be changed to read Disallow: /joomla/administrator/ # # For more information about the robots.txt standard, see: # # # For syntax checking, see: # User-agent: * Disallow: /administrator/ Disallow: /cache/ Disallow: /cli/ Disallow: /components/ Disallow: /images/ Disallow: /includes/ Disallow: /installation/ Disallow: /language/ Disallow: /libraries/ Disallow: /logs/ Disallow: /media/ Disallow: /modules/ Disallow: /plugins/ Disallow: /templates/ Disallow: /tmp/
10 4. Artifacts favicon.ico Default icons indicate software package being used Which package? Search-engine worms (Santy worm 2004) phpbb
11 4. Artifacts Application-specific 404 error pages Tomcat, Ruby on Rails Rub on Rails
12 4. Artifacts Stack trace of web application Inject %00, %22, %27 to check for injection vulnerabilities
13 5. TLS transparency reports Rogue certificate authority can create valid certificates for sites it is not supposed to Force all authorities to log every certificate (for HTTPS) issued to a central location Browsers eventually will reject those that are not logged But, exposes all of the names of machines an organization has generated certificates for Potential targets for adversaries (TLS section) Demo: Lookup all oregonctf.org certificates and who issued them
14 6. Fuzzing Brute-force common directory names (e.g. admin, config, conf, src) Brute-force admin pages with default admin credentials wfuzz tool Detect directories and pages on the web server using wordlists of common resource names. $ wfuzz -c -z file,wordlist/general/common.txt --hc nmap tool General tool supporting any number of scans Can specifically be used to enumerate directories in web servers similar to wfuzz nmap --script http-enum w.x.y.z
15 Lab: A0 Reconaissance See handout
Lecture Overview. IN5290 Ethical Hacking. Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing
 Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
CIS 700/002 : Special Topics : OWASP ZED (ZAP)
 CIS 700/002 : Special Topics : OWASP ZED (ZAP) Hitali Sheth CIS 700/002: Security of EMBS/CPS/IoT Department of Computer and Information Science School of Engineering and Applied Science University of
CIS 700/002 : Special Topics : OWASP ZED (ZAP) Hitali Sheth CIS 700/002: Security of EMBS/CPS/IoT Department of Computer and Information Science School of Engineering and Applied Science University of
Lab 5: Web Attacks using Burp Suite
 Lab 5: Web Attacks using Burp Suite Aim The aim of this lab is to provide a foundation in performing security testing of web applications using Burp Suite and its various tools. Burp Suite and its tools
Lab 5: Web Attacks using Burp Suite Aim The aim of this lab is to provide a foundation in performing security testing of web applications using Burp Suite and its various tools. Burp Suite and its tools
DreamFactory Security Guide
 DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
Lab 2. All datagrams related to favicon.ico had been ignored. Diagram 1. Diagram 2
 Lab 2 All datagrams related to favicon.ico had been ignored. Diagram 1 Diagram 2 1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running? According to the diagram
Lab 2 All datagrams related to favicon.ico had been ignored. Diagram 1 Diagram 2 1. Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running? According to the diagram
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
Web Push Notification
 Web Push Notification webkul.com/blog/web-push-notification-for-magento2/ On - January 13, 2017 This impressive module allows you to send push notification messages directly to the web browser. The biggest
Web Push Notification webkul.com/blog/web-push-notification-for-magento2/ On - January 13, 2017 This impressive module allows you to send push notification messages directly to the web browser. The biggest
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address :
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
CORS Attacks. Author: Milad Khoshdel Blog: P a g e. CORS Attacks
 Author: Milad Khoshdel Blog: https://blog.regux.com Email: miladkhoshdel@gmail.com 1 P a g e Contents What is CORS?...3 How to Test?...4 CORS Checker Script...6 References...9 2 P a g e What is CORS? CORS
Author: Milad Khoshdel Blog: https://blog.regux.com Email: miladkhoshdel@gmail.com 1 P a g e Contents What is CORS?...3 How to Test?...4 CORS Checker Script...6 References...9 2 P a g e What is CORS? CORS
Only applies where the starting URL specifies a starting location other than the root folder. For example:
 Allows you to set crawling rules for a Website Index. Character Encoding Allow Navigation Above Starting Directory Only applies where the starting URL specifies a starting location other than the root
Allows you to set crawling rules for a Website Index. Character Encoding Allow Navigation Above Starting Directory Only applies where the starting URL specifies a starting location other than the root
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Okta Integration Guide for Web Access Management with F5 BIG-IP
 Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
s642 web security computer security adam everspaugh
 s642 computer security web security adam everspaugh ace@cs.wisc.edu review memory protections / data execution prevention / address space layout randomization / stack protector Sandboxing / Limit damage
s642 computer security web security adam everspaugh ace@cs.wisc.edu review memory protections / data execution prevention / address space layout randomization / stack protector Sandboxing / Limit damage
Here's how we are going to Supercharge WordPress.
 Here's how we are going to Supercharge WordPress. Fix the default WordPress settings. Optimize WordPress s operation. Correct the on-page SEO. Optimize our internal link juice. Upgrade the promotion engines.
Here's how we are going to Supercharge WordPress. Fix the default WordPress settings. Optimize WordPress s operation. Correct the on-page SEO. Optimize our internal link juice. Upgrade the promotion engines.
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):ekk.worldtravelink.com
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
CNIT 129S: Securing Web Applications. Ch 4: Mapping the Application
 CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary
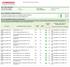 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
5/15/2009. Introduction
 Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Monitoring Apache Tomcat Servers With Nagios XI
 Purpose This document describes how to add custom Apache Tomcat plugins and checks, namely check_tomcatsessions, to your server. Implementing Apache Tomcat plugins within will allow you the to monitor
Purpose This document describes how to add custom Apache Tomcat plugins and checks, namely check_tomcatsessions, to your server. Implementing Apache Tomcat plugins within will allow you the to monitor
I started off with a quick nmap scan, which showed both port 80 and 443 open.
 Mr-Robot: 1 Walkthrough Author: mrb3n Download location: https://download.vulnhub.com/mrrobot/mrrobot.ova Goal: Find 3 keys hidden in different locations -----------------------------------------------------------------------------------------------------------------
Mr-Robot: 1 Walkthrough Author: mrb3n Download location: https://download.vulnhub.com/mrrobot/mrrobot.ova Goal: Find 3 keys hidden in different locations -----------------------------------------------------------------------------------------------------------------
SBCC Web File System - Xythos
 Table of Contents Table of Contents...1 Purpose...1 Login Procedure...1 Creating and Sharing a Web Folder for MAT153...2 Dreamweaver Remote Info...4 I Forgot My Pipeline Credentials...6 Purpose This purpose
Table of Contents Table of Contents...1 Purpose...1 Login Procedure...1 Creating and Sharing a Web Folder for MAT153...2 Dreamweaver Remote Info...4 I Forgot My Pipeline Credentials...6 Purpose This purpose
Collecting information
 Mag. iur. Dr. techn. Michael Sonntag Collecting information E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor Technology
Mag. iur. Dr. techn. Michael Sonntag Collecting information E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor Technology
Web Application Penetration Testing
 Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Penetration Testing. James Walden Northern Kentucky University
 Penetration Testing James Walden Northern Kentucky University Topics 1. What is Penetration Testing? 2. Rules of Engagement 3. Penetration Testing Process 4. Map the Application 5. Analyze the Application
Penetration Testing James Walden Northern Kentucky University Topics 1. What is Penetration Testing? 2. Rules of Engagement 3. Penetration Testing Process 4. Map the Application 5. Analyze the Application
Novell Access Manager
 Setup Guide AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP3 February 02, 2011 www.novell.com Novell Access Manager 3.1 SP3 Setup Guide Legal Notices Novell, Inc., makes no representations or warranties
Setup Guide AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP3 February 02, 2011 www.novell.com Novell Access Manager 3.1 SP3 Setup Guide Legal Notices Novell, Inc., makes no representations or warranties
Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion
 IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
Introduction to Ethical Hacking
 Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Import Data Connection to an SAP ERP System
 Import Data Connection to an SAP ERP System SAP Analytics Cloud allows you to import data from supported versions SAP ERP Central Component. NOTE: It is recommended that the SAP Cloud Platform Cloud Connector
Import Data Connection to an SAP ERP System SAP Analytics Cloud allows you to import data from supported versions SAP ERP Central Component. NOTE: It is recommended that the SAP Cloud Platform Cloud Connector
TexSaw Penetration Te st in g
 TexSaw Penetration Te st in g What is penetration testing? The process of breaking something or using something for an unintended used case for the purpose of bettering the system or application. This
TexSaw Penetration Te st in g What is penetration testing? The process of breaking something or using something for an unintended used case for the purpose of bettering the system or application. This
Lab 2: Creating Secure Architectures
 Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Crawling. CS6200: Information Retrieval. Slides by: Jesse Anderton
 Crawling CS6200: Information Retrieval Slides by: Jesse Anderton Motivating Problem Internet crawling is discovering web content and downloading it to add to your index. This is a technically complex,
Crawling CS6200: Information Retrieval Slides by: Jesse Anderton Motivating Problem Internet crawling is discovering web content and downloading it to add to your index. This is a technically complex,
A1 (Part 1): Injection Command and Code injection
 A1 (Part 1): Injection Command and Code injection A1 Injection Tricking an application into executing commands or code embedded in data Data and code mixing! Often injected into interpreters SQL, PHP,
A1 (Part 1): Injection Command and Code injection A1 Injection Tricking an application into executing commands or code embedded in data Data and code mixing! Often injected into interpreters SQL, PHP,
OWASP Broken Web Application Project. When Bad Web Apps are Good
 OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
HTTP Protocol and Server-Side Basics
 HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
Scan Report Executive Summary
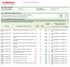 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Create Import Data Connection to SAP BPC MS
 Create Import Data Connection to SAP BPC MS You can create a connection that allows you to import data and models from an SAP Business Planning and Consolidation (BPC) system. Prerequisites SAP BPC for
Create Import Data Connection to SAP BPC MS You can create a connection that allows you to import data and models from an SAP Business Planning and Consolidation (BPC) system. Prerequisites SAP BPC for
Nessus Scan Report. Hosts Summary (Executive) Hosts Summary (Executive) Mon, 15 May :27:44 EDT
 Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Lab 1: Creating Secure Architectures (Revision)
 Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
HHC 2017 writeup, by RedTeam611
 HHC 2017 writeup, by RedTeam611 After you complete the terminal challenges in the snowball games you will then move onto the web server challenges. Our first task to is to investigate the Letters to Santa
HHC 2017 writeup, by RedTeam611 After you complete the terminal challenges in the snowball games you will then move onto the web server challenges. Our first task to is to investigate the Letters to Santa
BraindumpsIT. BraindumpsIT - IT Certification Company provides Braindumps pdf!
 BraindumpsIT http://www.braindumpsit.com BraindumpsIT - IT Certification Company provides Braindumps pdf! Exam : GPEN Title : GIAC Certified Penetration Tester Vendor : GIAC Version : DEMO Get Latest &
BraindumpsIT http://www.braindumpsit.com BraindumpsIT - IT Certification Company provides Braindumps pdf! Exam : GPEN Title : GIAC Certified Penetration Tester Vendor : GIAC Version : DEMO Get Latest &
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
IronWASP (Iron Web application Advanced Security testing Platform)
 IronWASP (Iron Web application Advanced Security testing Platform) 1. Introduction: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability
IronWASP (Iron Web application Advanced Security testing Platform) 1. Introduction: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability
GOOGLE HACKING!! Date : 10/31/2007. Krishna Prasad Yerrapragada
 GOOGLE HACKING!! Date : 10/31/2007 Krishna Prasad Yerrapragada Introduction AGENDA What is Google Hacking/GHDB? GHDB Johnny Long How it works? Possible Reasons Approaches to AVOID/RESOLVE Google s Response
GOOGLE HACKING!! Date : 10/31/2007 Krishna Prasad Yerrapragada Introduction AGENDA What is Google Hacking/GHDB? GHDB Johnny Long How it works? Possible Reasons Approaches to AVOID/RESOLVE Google s Response
Import Data Connection from an SAP Universe
 Import Data Connection from an SAP Universe SAP Analytics Cloud allows you to connect to SAP Universe and import your data. NOTE: It is recommended that the SAP Cloud Platform Cloud Connector (SAP CP CC)
Import Data Connection from an SAP Universe SAP Analytics Cloud allows you to connect to SAP Universe and import your data. NOTE: It is recommended that the SAP Cloud Platform Cloud Connector (SAP CP CC)
epldt Web Builder Security March 2017
 epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
Import Data Connection to an SAP BW System
 Import Data Connection to an SAP BW System SAP Analytics Cloud allows you to import data from an SAP BW System. You must connect to an SAP BW system, version 7.3x or higher release. NOTE: It is recommended
Import Data Connection to an SAP BW System SAP Analytics Cloud allows you to import data from an SAP BW System. You must connect to an SAP BW system, version 7.3x or higher release. NOTE: It is recommended
Advanced Vmware Security The Lastest Threats and Tools
 Advanced Vmware Security The Lastest Threats and Tools Introduction Who is VMTraining VMWARE Security around VMware What are you in for? Hold On! Does ESX really have some major issues? Recent Cases involving
Advanced Vmware Security The Lastest Threats and Tools Introduction Who is VMTraining VMWARE Security around VMware What are you in for? Hold On! Does ESX really have some major issues? Recent Cases involving
ECCouncil Exam v8 Certified Ethical Hacker v8 Exam Version: 7.0 [ Total Questions: 357 ]
![ECCouncil Exam v8 Certified Ethical Hacker v8 Exam Version: 7.0 [ Total Questions: 357 ] ECCouncil Exam v8 Certified Ethical Hacker v8 Exam Version: 7.0 [ Total Questions: 357 ]](/thumbs/89/101183176.jpg) s@lm@n ECCouncil Exam 312-50v8 Certified Ethical Hacker v8 Exam Version: 7.0 [ Total Questions: 357 ] Topic break down Topic No. of Questions Topic 1: Background 38 Topic 3: Security 57 Topic 4: Tools
s@lm@n ECCouncil Exam 312-50v8 Certified Ethical Hacker v8 Exam Version: 7.0 [ Total Questions: 357 ] Topic break down Topic No. of Questions Topic 1: Background 38 Topic 3: Security 57 Topic 4: Tools
Proxying. Why and How. Alon Altman. Haifa Linux Club. Proxying p.1/24
 Proxying p.1/24 Proxying Why and How Alon Altman alon@haifux.org Haifa Linux Club Proxying p.2/24 Definition proxy \Prox"y\, n.; pl. Proxies. The agency for another who acts through the agent; authority
Proxying p.1/24 Proxying Why and How Alon Altman alon@haifux.org Haifa Linux Club Proxying p.2/24 Definition proxy \Prox"y\, n.; pl. Proxies. The agency for another who acts through the agent; authority
Session 8. Reading and Reference. en.wikipedia.org/wiki/list_of_http_headers. en.wikipedia.org/wiki/http_status_codes
 Session 8 Deployment Descriptor 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/_status_codes
Session 8 Deployment Descriptor 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/_status_codes
How A Website Works. - Shobha
 How A Website Works - Shobha Synopsis 1. 2. 3. 4. 5. 6. 7. 8. 9. What is World Wide Web? What makes web work? HTTP and Internet Protocols. URL s Client-Server model. Domain Name System. Web Browser, Web
How A Website Works - Shobha Synopsis 1. 2. 3. 4. 5. 6. 7. 8. 9. What is World Wide Web? What makes web work? HTTP and Internet Protocols. URL s Client-Server model. Domain Name System. Web Browser, Web
The WebGUI Runtime Environment. Roy Johnson Plain Black Corporation
 The WebGUI Runtime Environment Roy Johnson Plain Black Corporation What is the WRE? All the supporting software required to host WebGUI Apache 2 / Mod_Perl 2 MySQL 5 Supporting Perl Modules AWStats Utilities
The WebGUI Runtime Environment Roy Johnson Plain Black Corporation What is the WRE? All the supporting software required to host WebGUI Apache 2 / Mod_Perl 2 MySQL 5 Supporting Perl Modules AWStats Utilities
CSC 5930/9010 Offensive Security: OSINT
 CSC 5930/9010 Offensive Security: OSINT Professor Henry Carter Spring 2019 Recap Designing shellcode requires intimate knowledge of assembly, system calls, and creative combinations of operations But allows
CSC 5930/9010 Offensive Security: OSINT Professor Henry Carter Spring 2019 Recap Designing shellcode requires intimate knowledge of assembly, system calls, and creative combinations of operations But allows
EZDRM Service Integration Into Kaltura CE with Nginx
 EZDRM Service Integration Into Kaltura CE with Nginx Table of Contents Introduction... 3 Requirements... 3 Architecture... 3 Widevine/PlayReady Universal DRM... 4 Setup Instructions... 4 Apple FairPlay
EZDRM Service Integration Into Kaltura CE with Nginx Table of Contents Introduction... 3 Requirements... 3 Architecture... 3 Widevine/PlayReady Universal DRM... 4 Setup Instructions... 4 Apple FairPlay
Google Hacking. Information Security Summit Cleveland, Ohio. Pete Garvin.
 Google Hacking Information Security Summit Cleveland, Ohio Pete Garvin pgarvin@protectus.com October 2005 Google Hacking Overview A few words about Google What is Google Hacking? Why it s relevant How-to
Google Hacking Information Security Summit Cleveland, Ohio Pete Garvin pgarvin@protectus.com October 2005 Google Hacking Overview A few words about Google What is Google Hacking? Why it s relevant How-to
CNIT 129S: Securing Web Applications. Ch 10: Attacking Back-End Components
 CNIT 129S: Securing Web Applications Ch 10: Attacking Back-End Components Injecting OS Commands Web server platforms often have APIs To access the filesystem, interface with other processes, and for network
CNIT 129S: Securing Web Applications Ch 10: Attacking Back-End Components Injecting OS Commands Web server platforms often have APIs To access the filesystem, interface with other processes, and for network
NotifySCM Workspace Administration Guide
 NotifySCM Workspace Administration Guide TABLE OF CONTENTS 1 Overview... 3 2 Login... 4 2.1 Main View... 5 3 Manage... 6 3.1 PIM... 6 3.2 Document...12 3.3 Server...13 4 Workspace Configuration... 14 4.1
NotifySCM Workspace Administration Guide TABLE OF CONTENTS 1 Overview... 3 2 Login... 4 2.1 Main View... 5 3 Manage... 6 3.1 PIM... 6 3.2 Document...12 3.3 Server...13 4 Workspace Configuration... 14 4.1
Yioop Full Historical Indexing In Cache Navigation. Akshat Kukreti
 Yioop Full Historical Indexing In Cache Navigation Akshat Kukreti Agenda Introduction History Feature Cache Page Validation Feature Conclusion Demo Introduction Project goals History feature for enabling
Yioop Full Historical Indexing In Cache Navigation Akshat Kukreti Agenda Introduction History Feature Cache Page Validation Feature Conclusion Demo Introduction Project goals History feature for enabling
Vidder PrecisionAccess
 Vidder PrecisionAccess Transparent Multi-Factor Authentication June 2015 910 E HAMILTON AVENUE. SUITE 430. CAMPBELL, CA 95008 P: 408.418.0440 F: 408.706.5590 WWW.VIDDER.COM Table of Contents I. Overview...
Vidder PrecisionAccess Transparent Multi-Factor Authentication June 2015 910 E HAMILTON AVENUE. SUITE 430. CAMPBELL, CA 95008 P: 408.418.0440 F: 408.706.5590 WWW.VIDDER.COM Table of Contents I. Overview...
Hacking Our Way to Better Security: Lessons from a Web Application Penetration Test. Tyler Rasmussen Mercer Engineer Research Center
 Hacking Our Way to Better Security: Lessons from a Web Application Penetration Test Tyler Rasmussen Mercer Engineer Research Center About Me Cybersecurity Engineering Intern @ MERC Senior IT/Cybersecurity
Hacking Our Way to Better Security: Lessons from a Web Application Penetration Test Tyler Rasmussen Mercer Engineer Research Center About Me Cybersecurity Engineering Intern @ MERC Senior IT/Cybersecurity
SSH Product Overview
 SSH Product Overview SSH Product Overview Understanding SSH SSH Discovery and Remediation Agentless SSH Agent Based SSH 2018 Venafi. All Rights Reserved. 2 Where is SSH used? File Transfer & Remote Script
SSH Product Overview SSH Product Overview Understanding SSH SSH Discovery and Remediation Agentless SSH Agent Based SSH 2018 Venafi. All Rights Reserved. 2 Where is SSH used? File Transfer & Remote Script
Sawmill TECH TIPS help for Web, Security, & Data Professionals
 Sawmill TECH TIPS help for Web, Security, & Data Professionals TECH TIPS # 2 Welcome to Sawmill TECH TIPS #2 Sawmill Tech Tips is a regular newsletter designed to help you make the most of Sawmill Reporting
Sawmill TECH TIPS help for Web, Security, & Data Professionals TECH TIPS # 2 Welcome to Sawmill TECH TIPS #2 Sawmill Tech Tips is a regular newsletter designed to help you make the most of Sawmill Reporting
EveBox Documentation. Jason Ish
 Jason Ish May 29, 2018 Contents: 1 Installation 1 2 Server 3 2.1 Running................................................. 3 2.2 Oneshot Mode.............................................. 4 2.3 Authentication..............................................
Jason Ish May 29, 2018 Contents: 1 Installation 1 2 Server 3 2.1 Running................................................. 3 2.2 Oneshot Mode.............................................. 4 2.3 Authentication..............................................
Novell Access Manager
 Quick Start AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP2 June 11, 2010 www.novell.com Novell Access Manager 3.1 SP2 Quick Start Legal Notices Novell, Inc., makes no representations or warranties
Quick Start AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP2 June 11, 2010 www.novell.com Novell Access Manager 3.1 SP2 Quick Start Legal Notices Novell, Inc., makes no representations or warranties
Sophos UTM Web Application Firewall For: Microsoft Exchange Services
 How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
How to configure: Sophos UTM Web Application Firewall For: Microsoft Exchange Services This guide explains how to configure your Sophos UTM 9.3+ to allow access to the relevant Microsoft Exchange services
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0. Last Revised: January 16, 2019
 Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
KANA Enterprise Knowledge Management Administration Guide
 KANA Enterprise Knowledge Management Administration Guide Product Release 13R2 SP1 Document Version 1.0 Publication date: 05 March 2014 Copyright 2013 KANA. All rights reserved. The copyright, trademarks
KANA Enterprise Knowledge Management Administration Guide Product Release 13R2 SP1 Document Version 1.0 Publication date: 05 March 2014 Copyright 2013 KANA. All rights reserved. The copyright, trademarks
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Troubleshooting Web Inbox
 , page 1 Introduction The Web Inbox application provides access to voice messages and receipts stored on the Cisco Unity Connection server. The Web Inbox enables users to play, compose, reply to or forward,
, page 1 Introduction The Web Inbox application provides access to voice messages and receipts stored on the Cisco Unity Connection server. The Web Inbox enables users to play, compose, reply to or forward,
Tumbling Down the Rabbit Hole:
 Tumbling Down the Rabbit Hole: Exploring the Idiosyncrasies of Botmaster Systems in a Multi-Tier Botnet Infrastructure Chris Nunnery Greg Sinclair Brent ByungHoon Kang [ University of North Carolina at
Tumbling Down the Rabbit Hole: Exploring the Idiosyncrasies of Botmaster Systems in a Multi-Tier Botnet Infrastructure Chris Nunnery Greg Sinclair Brent ByungHoon Kang [ University of North Carolina at
BEAAquaLogic Enterprise Repository. IBM Rational ClearCase and IBM Rational ClearQuest Integration Guide
 BEAAquaLogic Enterprise Repository IBM Rational ClearCase and IBM Rational ClearQuest Integration Guide Version 3.0 Document Revised: August 2007 Connector for IBM Rational ClearCase and IBM Rational
BEAAquaLogic Enterprise Repository IBM Rational ClearCase and IBM Rational ClearQuest Integration Guide Version 3.0 Document Revised: August 2007 Connector for IBM Rational ClearCase and IBM Rational
Real Life Web Development. Joseph Paul Cohen
 Real Life Web Development Joseph Paul Cohen joecohen@cs.umb.edu Index 201 - The code 404 - How to run it? 500 - Your code is broken? 200 - Someone broke into your server? 400 - How are people using your
Real Life Web Development Joseph Paul Cohen joecohen@cs.umb.edu Index 201 - The code 404 - How to run it? 500 - Your code is broken? 200 - Someone broke into your server? 400 - How are people using your
WFUZZ! for Penetration Testers! Christian Martorella & Xavier Mendez! SOURCE Conference 2011! Barcelona!
 ! WFUZZ! for Penetration Testers! Christian Martorella & Xavier Mendez! SOURCE Conference 2011! Barcelona!! Who we are? Security Consultants at Verizon Business Threat and Vulnerability Team EMEA Members
! WFUZZ! for Penetration Testers! Christian Martorella & Xavier Mendez! SOURCE Conference 2011! Barcelona!! Who we are? Security Consultants at Verizon Business Threat and Vulnerability Team EMEA Members
Table of Contents. Configure and Manage Logging in to the Management Portal Verify and Trust Certificates
 Table of Contents Configure and Manage Logging in to the Management Portal Verify and Trust Certificates Configure System Settings Add Cloud Administrators Add Viewers, Developers, or DevOps Administrators
Table of Contents Configure and Manage Logging in to the Management Portal Verify and Trust Certificates Configure System Settings Add Cloud Administrators Add Viewers, Developers, or DevOps Administrators
EveBox Documentation. Release. Jason Ish
 EveBox Documentation Release Jason Ish Jan 25, 2018 Contents: 1 Installation 1 2 Server 3 2.1 Running................................................. 3 2.2 Oneshot Mode..............................................
EveBox Documentation Release Jason Ish Jan 25, 2018 Contents: 1 Installation 1 2 Server 3 2.1 Running................................................. 3 2.2 Oneshot Mode..............................................
Penetration Testing with Kali Linux
 Penetration Testing with Kali Linux PWK Copyright Offensive Security Ltd. All rights reserved. Page 1 of 11 All rights reserved to Offensive Security No part of this publication, in whole or in part, may
Penetration Testing with Kali Linux PWK Copyright Offensive Security Ltd. All rights reserved. Page 1 of 11 All rights reserved to Offensive Security No part of this publication, in whole or in part, may
INSTALLATION GUIDE FOR ACPL FM220 RD WINDOWS APPLICATION INDEX
 INSTALLATION GUIDE FOR ACPL FM220 RD WINDOWS APPLICATION INDEX CONTENT PAGE No. Setup FM220 RD Service 2 Setup FM220 RD Service Support Tool 5 Instructions to enable HTTPS in RD Service 8 RD Service troubleshooting
INSTALLATION GUIDE FOR ACPL FM220 RD WINDOWS APPLICATION INDEX CONTENT PAGE No. Setup FM220 RD Service 2 Setup FM220 RD Service Support Tool 5 Instructions to enable HTTPS in RD Service 8 RD Service troubleshooting
McAfee Certified Assessment Specialist Network
 McAfee MA0-150 McAfee Certified Assessment Specialist Network Version: 4.0 Topic 1, Volume A QUESTION NO: 1 An attacker has compromised a Linux/Unix host and discovers a suspicious file called "password"
McAfee MA0-150 McAfee Certified Assessment Specialist Network Version: 4.0 Topic 1, Volume A QUESTION NO: 1 An attacker has compromised a Linux/Unix host and discovers a suspicious file called "password"
Novell Access Manager
 Setup Guide AUTHORIZED DOCUMENTATION Novell Access Manager 3.0 SP4 IR2 January 30, 2009 www.novell.com Novell Access Manager 3.0 SP4 Setup Guide Legal Notices Novell, Inc., makes no representations or
Setup Guide AUTHORIZED DOCUMENTATION Novell Access Manager 3.0 SP4 IR2 January 30, 2009 www.novell.com Novell Access Manager 3.0 SP4 Setup Guide Legal Notices Novell, Inc., makes no representations or
Lecture 9a: Sessions and Cookies
 CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
CS 655 / 441 Fall 2007 Lecture 9a: Sessions and Cookies 1 Review: Structure of a Web Application On every interchange between client and server, server must: Parse request. Look up session state and global
USER MANUAL. DynamicsPort - Customer Portal for Dynamics CRM TABLE OF CONTENTS. Version: 1.1
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 Dynamics CRM Plug-in Installation... 2 Plug-in Configuration... 5 Dynamics CRM Configuration
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 Dynamics CRM Plug-in Installation... 2 Plug-in Configuration... 5 Dynamics CRM Configuration
SECURE CODING ESSENTIALS
 SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
1. Configuring Azure and EBP for a simple demo
 1. Configuring Azure and EBP for a simple demo These steps assume you already have an Azure subscription and at least familiarity with the Azure portal. Create a new App Service Search for Apache Tomcat
1. Configuring Azure and EBP for a simple demo These steps assume you already have an Azure subscription and at least familiarity with the Azure portal. Create a new App Service Search for Apache Tomcat
Smart Links for SEO. Miva Module for Miva Merchant 5. Contents
 Smart Links for SEO user manual Miva Module for Miva Merchant 5 Contents Introduction Requirements Installation Rewrite Rules Template Customization Best Practices Support copyright 2009 by NetBlazon LLC
Smart Links for SEO user manual Miva Module for Miva Merchant 5 Contents Introduction Requirements Installation Rewrite Rules Template Customization Best Practices Support copyright 2009 by NetBlazon LLC
NEST Kali Linux Tutorial: Burp Suite
 NEST Kali Linux Tutorial: Burp Suite Burp gives you full control, letting you combine advanced manual techniques with state-of-the-art automation, to make your work faster, more effective, and more fun.
NEST Kali Linux Tutorial: Burp Suite Burp gives you full control, letting you combine advanced manual techniques with state-of-the-art automation, to make your work faster, more effective, and more fun.
CNIT 129S: Securing Web Applications. Ch 3: Web Application Technologies
 CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
Comodo Certificate Manager Software Version 5.0
 Comodo Certificate Manager Software Version 5.0 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United
Comodo Certificate Manager Software Version 5.0 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United
OWASP Thailand. Proxy Caches and Web Application Security. OWASP AppSec Asia October 21, Using the Recent Google Docs 0-Day as an Example
 Proxy Caches and Web Application Security Using the Recent Google Docs 0-Day as an Example Tim Bass, CISSP Chapter Leader, Thailand +66832975101, tim@unix.com AppSec Asia October 21, 2008 Thailand Worldwide
Proxy Caches and Web Application Security Using the Recent Google Docs 0-Day as an Example Tim Bass, CISSP Chapter Leader, Thailand +66832975101, tim@unix.com AppSec Asia October 21, 2008 Thailand Worldwide
wagtail-robots Documentation
 wagtail-robots Documentation Release dev Adrian Turjak Feb 28, 2018 Contents 1 Wagtail Robots In Action 3 2 Installation 9 3 Initialization 11 4 Rules 13 5 URLs 15 6 Caching 17 7 Sitemaps 19 8 Host directive
wagtail-robots Documentation Release dev Adrian Turjak Feb 28, 2018 Contents 1 Wagtail Robots In Action 3 2 Installation 9 3 Initialization 11 4 Rules 13 5 URLs 15 6 Caching 17 7 Sitemaps 19 8 Host directive
Session 9. Deployment Descriptor Http. Reading and Reference. en.wikipedia.org/wiki/http. en.wikipedia.org/wiki/list_of_http_headers
 Session 9 Deployment Descriptor Http 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/http_status_codes
Session 9 Deployment Descriptor Http 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/http_status_codes
USER MANUAL. DynamicsPort - Customer Portal for Dynamics CRM TABLE OF CONTENTS. Version: 1.2
 USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 Dynamics CRM Plug-in Installation... 2 Plug-in Configuration... 5 Dynamics CRM Configuration
USER MANUAL TABLE OF CONTENTS Introduction... 1 Benefits of Customer Portal... 1 Prerequisites... 1 Installation... 2 Dynamics CRM Plug-in Installation... 2 Plug-in Configuration... 5 Dynamics CRM Configuration
VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Manager
 VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Table of Contents Lab Overview - HOL-1857-03-UEM - Workspace ONE UEM with App & Access Management... 2 Lab Guidance... 3 Module 1 - Workspace
VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Table of Contents Lab Overview - HOL-1857-03-UEM - Workspace ONE UEM with App & Access Management... 2 Lab Guidance... 3 Module 1 - Workspace
Table of Contents Chapter 1: Upgrading to Observer v Index...8
 Upgrading to 17.5.2.0 User Guide 29 Mar 2019 Table of Contents Chapter 1: Upgrading to v17... 3 Before upgrading to v17...3 What is new in v17...3 What is needed for upgrading...4 Installing and licensing...5
Upgrading to 17.5.2.0 User Guide 29 Mar 2019 Table of Contents Chapter 1: Upgrading to v17... 3 Before upgrading to v17...3 What is new in v17...3 What is needed for upgrading...4 Installing and licensing...5
Manually Password Protect Directories Apache Ubuntu
 Manually Password Protect Directories Apache Ubuntu Apache can be configured to force users to login before being Password protection can be useful for securing a directory that planning to edit them manually,
Manually Password Protect Directories Apache Ubuntu Apache can be configured to force users to login before being Password protection can be useful for securing a directory that planning to edit them manually,
Using Hive for Data Warehousing
 An IBM Proof of Technology Using Hive for Data Warehousing Unit 1: Exploring Hive An IBM Proof of Technology Catalog Number Copyright IBM Corporation, 2013 US Government Users Restricted Rights - Use,
An IBM Proof of Technology Using Hive for Data Warehousing Unit 1: Exploring Hive An IBM Proof of Technology Catalog Number Copyright IBM Corporation, 2013 US Government Users Restricted Rights - Use,
How to configure the UTM Web Application Firewall for Microsoft Remote Desktop Gateway connectivity
 How to configure the UTM Web Application Firewall for Microsoft Remote Desktop Gateway connectivity This article explains how to configure your Sophos UTM to allow access Microsoft s Remote Desktop Gateway
How to configure the UTM Web Application Firewall for Microsoft Remote Desktop Gateway connectivity This article explains how to configure your Sophos UTM to allow access Microsoft s Remote Desktop Gateway
HTTP Security. CSC 482/582: Computer Security Slide #1
 HTTP Security CSC 482/582: Computer Security Slide #1 Topics 1. How HTTP works 2. HTTP methods, headers, and responses 3. URIs, URLs, and URNs 4. Statelessness 5. Cookies 6. More HTTP methods and headers
HTTP Security CSC 482/582: Computer Security Slide #1 Topics 1. How HTTP works 2. HTTP methods, headers, and responses 3. URIs, URLs, and URNs 4. Statelessness 5. Cookies 6. More HTTP methods and headers
