Setup Service Account in AD
|
|
|
- Ashlyn Norman
- 5 years ago
- Views:
Transcription
1 Table of contents Setup Service Account in AD... 2 Security setup on Service Account in AD... 2 Create Organization Units (OU) in AD... 4 Security setup on OUs in AD... 5
2 Setup Service Account in AD 1. Create service account user in AD e.g, domain\crm.serviceuser Note: remember password, as password required to be mentioned in the scripts for installation and configuration. 2. Set the user created in step 1 as local administrator on both Application Server machine and Database Server. 3. Add the user created in step 1 as sysadmin in the SQL Server 2008 Database instance which will be used for installation of CRM Security setup on Service Account in AD The objective for this setup is that the service account should be able to dynamically create Service Principal Name (SPN) for the services it is set to run. Typically SQL Service requires that for named instances where port could be dynamically allocated to service each time service is restarted. So it becomes difficult to change the SPN every time the port is changed. Note: If network service is configured as the running user of SQL Server than you do not need to give SPN permissions to this user To add the permissions, follow these steps: 1. Click Start, click Run, type Adsiedit.msc, and then click OK. 2. In the ADSI Edit snap-in, expand Domain [DomainName], expand DC= RootDomainName, expand CN=Users, right-click CN= AccountName, and then click Properties. 3. In the CN= AccountName Properties dialog box, click the Security tab. 4. On the Security tab, click Advanced 5. In the Advanced Security Settings dialog box, make sure that SELF is listed under Permission entries. If SELF is not listed, click Add, and then add SELF. 6. Under Permission entries, click SELF, and then click Edit. 7. In the Permission Entry dialog box, click the Properties tab. 8. On the Properties tab, click This object only in the Apply onto list, and then make sure that the check boxes for the following permissions are selected under Permissions: Read serviceprincipalname Write serviceprincipalname 9. Click OK three times, and then exit the ADSI Edit snap-in. Following picture illustrates the permissions
3
4 Create Organization Units (OU) in AD 1. Create Organizational Units in AD, these OUs will be used by CRM installation for giving proper access to SQL, reporting and application services. Each installation of CRM will create 5 security groups under this OU. So create these OUs in such a way that they individually represent the environment they are supposed to be used for. For example there will be an installation of CRM for each of Test, PreProd & Prod. An example structure could be as following: rootdom.abc.xyz Users Computers CRM (OU) Test_env (OU) PreProd_env (OU) Prod_env (OU) 2. After creating the OU, take some time to get the Distinguished name of the OU. This OU will be required for usage in CRM installation script, for example following table illustrates OU Path in AD rootdom.abc.xyz/crm/test_env rootdom.abc.xyz/crm/preprod_env rootdom.abc.xyz/crm/prod_env Distinguished name OU=TEST_env,OU=CRM,DC=rootdom,DC=abc,DC=xyz OU=PreProd_env,OU= CRM,DC=rootdom,DC=abc,DC=xyz OU=Prod_env,OU=CRM, DC=rootdom,DC=abc,DC=xyz To get the distinguished name for above mentioned, use the following ldap query as a domain administrator on command prompt, results will be written out to c:\temp\output.txt: ldifde -d "OU=CRM,DC=rootdom,DC=abc,DC=xyz" -f c:\temp\output.txt -l "dn" -r "(&(objectclass=organizationalunit)(name=*_env))
5 Security setup on OUs in AD For the user account of the user who is installing CRM, add the following permissions to the organizational unit (OU) in the AD. Perform this step for the OU which you select for installation of CRM. For example, in test it is at following path in AD: rootdom.abc.xyz/crm/test_env Permissions o Full control Advanced permissions o Read Permissions o Modify Permissions o Read Members o Write Members To add the permissions, follow these steps: 1. Log on to the domain controller server as a user who has domain administrator permissions. 2. Click Start, click Administrative Tools, and then click Active Directory Users and Computers. 3. On the View menu, click Advanced Features. 4. In the navigation pane, find the OU that you want to use for the Microsoft Dynamics CRM installation. To do this, expand the tree to the node that contains the security group. 5. Right-click the security group, click Properties, and then click the Security tab. 6. In the Group or user names list, click the user account of the user who is installing Microsoft Dynamics CRM if the account is listed. If the account is not listed, click Add to add the user account. 7. In the Allow column, click to select the check box for the Full control permission. Note By default, the Allow check box is selected for the Read permission. 8. Click Advanced. 9. In the Permission entries list, click Add, select the user account of the user who is installing Microsoft Dynamics CRM, and then click OK. 10. In the Apply onto list, click Descendant Group objects. 11. In the Allow column, click to select the following check boxes: o Read Permissions o Modify Permissions 12. Click the Properties tab. 13. In the Apply onto list, click Descendant Group objects. 14. In the Allow column, click to select the following check boxes: o Read Members o Write Members 15. Click OK three times.
Active Directory Auditing Guide
 Active Directory Auditing Guide www.adauditplus.com Table of Contents Document summary 1. Configuring Active Directory domains and domain controllers in ADAudit Plus 1.1 Automatic configuration 1.2 Manual
Active Directory Auditing Guide www.adauditplus.com Table of Contents Document summary 1. Configuring Active Directory domains and domain controllers in ADAudit Plus 1.1 Automatic configuration 1.2 Manual
User Manual. Active Directory Change Tracker
 User Manual Active Directory Change Tracker Last Updated: March 2018 Copyright 2018 Vyapin Software Systems Private Ltd. All rights reserved. This document is being furnished by Vyapin Software Systems
User Manual Active Directory Change Tracker Last Updated: March 2018 Copyright 2018 Vyapin Software Systems Private Ltd. All rights reserved. This document is being furnished by Vyapin Software Systems
Exchange Server 2010 Permissions Document
 Exchange Server 2010 Permissions Document Summary This document is designed to help you quickly create the users, security group, organizational unit, set a group policy, use ADSI Edit, and assign the
Exchange Server 2010 Permissions Document Summary This document is designed to help you quickly create the users, security group, organizational unit, set a group policy, use ADSI Edit, and assign the
Active Directory 2000 Plugin Installation for Cisco CallManager
 Active Directory 2000 Plugin Installation for Cisco CallManager Document ID: 15323 Contents Introduction Prerequisites Requirements Components Used Conventions Before You Begin Task 1: Create the Cisco
Active Directory 2000 Plugin Installation for Cisco CallManager Document ID: 15323 Contents Introduction Prerequisites Requirements Components Used Conventions Before You Begin Task 1: Create the Cisco
Guide to Deploy the AXIGEN Outlook Connector via Active Directory
 Guide to Deploy the AXIGEN Outlook Connector via Active Directory Active Directory contains a very useful feature which allows system administrators to automatically deploy software onto machines or users
Guide to Deploy the AXIGEN Outlook Connector via Active Directory Active Directory contains a very useful feature which allows system administrators to automatically deploy software onto machines or users
Comodo Certificate Manager
 Comodo Certificate Manager Windows Auto Enrollment Setup Guide Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United Kingdom. Table of
Comodo Certificate Manager Windows Auto Enrollment Setup Guide Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United Kingdom. Table of
Installation Guide. . All right reserved. For more information about Specops Command and other Specops products, visit
 . All right reserved. For more information about Specops Command and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Command is a trademark owned by Specops Software.
. All right reserved. For more information about Specops Command and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Command is a trademark owned by Specops Software.
AD Sync Client Install Guide. Contents
 AD Sync Client Install Guide Contents AD Sync Client Install Guide... 1 Introduction... 2 Deployment Prerequisites... 2 Configure SQL Prerequisites... 3 Switch SQL to Mixed Mode authentication... 3 Create
AD Sync Client Install Guide Contents AD Sync Client Install Guide... 1 Introduction... 2 Deployment Prerequisites... 2 Configure SQL Prerequisites... 3 Switch SQL to Mixed Mode authentication... 3 Create
Password Reset Utility. Configuration
 Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Password Reset Utility Configuration 1 Table of Contents 1. Uninstalling Legacy Password Reset... 2 2. Password Reset Utility: How to deploy and configure via Group Policy... 2 3. Configuring Group Policy
Workspace ONE UEM Certificate Authentication for EAS with ADCS. VMware Workspace ONE UEM 1902
 Workspace ONE UEM Certificate Authentication for EAS with ADCS VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Workspace ONE UEM Certificate Authentication for EAS with ADCS VMware Workspace ONE UEM 1902 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Configuring Microsoft ADAM
 Proven Practice Configuring Microsoft ADAM Product(s): IBM Cognos Series 7 Area of Interest: Security Configuring Microsoft ADAM 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated). Cognos
Proven Practice Configuring Microsoft ADAM Product(s): IBM Cognos Series 7 Area of Interest: Security Configuring Microsoft ADAM 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated). Cognos
MS Addons Smart Open. User Guide Smart Open
 User Guide Smart Open 1 Overview Smart Open feature enables the user to search a project in the project server. Besides, it contains all the regular capabilities offered by the default open dialog box.
User Guide Smart Open 1 Overview Smart Open feature enables the user to search a project in the project server. Besides, it contains all the regular capabilities offered by the default open dialog box.
SPNEGO SINGLE SIGN-ON USING SECURE LOGIN SERVER X.509 CLIENT CERTIFICATES
 SPNEGO SINGLE SIGN-ON USING SECURE LOGIN SERVER X.509 CLIENT CERTIFICATES TABLE OF CONTENTS SCENARIO... 2 IMPLEMENTATION STEPS... 2 PREREQUISITES... 3 1. CONFIGURE ADMINISTRATOR FOR THE SECURE LOGIN ADMINISTRATION
SPNEGO SINGLE SIGN-ON USING SECURE LOGIN SERVER X.509 CLIENT CERTIFICATES TABLE OF CONTENTS SCENARIO... 2 IMPLEMENTATION STEPS... 2 PREREQUISITES... 3 1. CONFIGURE ADMINISTRATOR FOR THE SECURE LOGIN ADMINISTRATION
Installation of LAPS Password Management Demo Deployment
 Installation of LAPS Password Management Demo Deployment Version: 1.0 Last Modified: 2017.11.2 Installation The content of this document is property of Omni Technology Solutions, Inc. All Rights Reserved.
Installation of LAPS Password Management Demo Deployment Version: 1.0 Last Modified: 2017.11.2 Installation The content of this document is property of Omni Technology Solutions, Inc. All Rights Reserved.
CONFIGURING LDAP. What is LDAP? Getting Started with LDAP
 CONFIGURING LDAP In this tutorial you will learn how to manage your LDAP Directories within your EmailHosting.com account. We will walkthrough how to setup your directories and access them with your email
CONFIGURING LDAP In this tutorial you will learn how to manage your LDAP Directories within your EmailHosting.com account. We will walkthrough how to setup your directories and access them with your email
Security 3. NiFi Authentication. Date of Publish:
 3 Date of Publish: 2018-08-13 http://docs.hortonworks.com Contents... 3 Enabling SSL with a NiFi Certificate Authority... 5 Enabling SSL with Existing Certificates... 5 (Optional) Setting Up Identity Mapping...6
3 Date of Publish: 2018-08-13 http://docs.hortonworks.com Contents... 3 Enabling SSL with a NiFi Certificate Authority... 5 Enabling SSL with Existing Certificates... 5 (Optional) Setting Up Identity Mapping...6
LDAP Synchronization
 LDAP Synchronization Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval of the Celonis
LDAP Synchronization Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval of the Celonis
User Account Manager
 CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
Securing LDAP Directory Integration with Cisco Unified CallManager 4.x
 Securing LDAP Directory Integration with Cisco Unified CallManager 4.x Document ID: 109804 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information For Existent
Securing LDAP Directory Integration with Cisco Unified CallManager 4.x Document ID: 109804 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information For Existent
INSTALLING OUTLOOK CRM
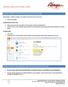 INSTALLING OUTLOOK CRM FIND OUT WHETHER YOU ARE USING 32-BIT OR 64-BIT OUTLOOK Open Outlook. To find out whether your Outlook is the 64-bit or the 32-bit version: 1. Click FILE in Outlook. In Outlook 2013
INSTALLING OUTLOOK CRM FIND OUT WHETHER YOU ARE USING 32-BIT OR 64-BIT OUTLOOK Open Outlook. To find out whether your Outlook is the 64-bit or the 32-bit version: 1. Click FILE in Outlook. In Outlook 2013
Web Authentication Using LDAP on Wireless LAN Controllers (WLCs) Configuration Example
 Web Authentication Using LDAP on Wireless LAN Controllers (WLCs) Configuration Example Document ID: 108008 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication
Web Authentication Using LDAP on Wireless LAN Controllers (WLCs) Configuration Example Document ID: 108008 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication
> dsadd user "<UserDN>" -upn <UserUPN> -fn "<UserFirstName>" -ln "<UserLastName>"[RETURN] -display "<UserDisplayName>" -pwd <UserPasswd>
![> dsadd user <UserDN> -upn <UserUPN> -fn <UserFirstName> -ln <UserLastName>[RETURN] -display <UserDisplayName> -pwd <UserPasswd> > dsadd user <UserDN> -upn <UserUPN> -fn <UserFirstName> -ln <UserLastName>[RETURN] -display <UserDisplayName> -pwd <UserPasswd>](/thumbs/92/107890112.jpg) Creating a User You want to create a user object. 6.1.2 6.1.2.1 1. Open the Active Directory Users and Computers (ADUC) snap-in. 2. If you need to change domains, right-click on "Active Directory Users
Creating a User You want to create a user object. 6.1.2 6.1.2.1 1. Open the Active Directory Users and Computers (ADUC) snap-in. 2. If you need to change domains, right-click on "Active Directory Users
Polycom CMA System Upgrade Guide
 Polycom CMA System Upgrade Guide 4.1.2 June 2009 3725-77606-001B2 Trademark Information Polycom, the Polycom Triangles logo, and the names and marks associated with Polycom s products are trademarks and/or
Polycom CMA System Upgrade Guide 4.1.2 June 2009 3725-77606-001B2 Trademark Information Polycom, the Polycom Triangles logo, and the names and marks associated with Polycom s products are trademarks and/or
Installing GFI MailArchiver
 Installing GFI MailArchiver GFI MailArchiver System requirements Windows 2000/2003 Server or Advanced Server. Microsoft Exchange Server 2000/2003. (The product is installed on the Exchange Server machine).net
Installing GFI MailArchiver GFI MailArchiver System requirements Windows 2000/2003 Server or Advanced Server. Microsoft Exchange Server 2000/2003. (The product is installed on the Exchange Server machine).net
Windows Server 2003 Network Administration Goals
 Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Objectives Differentiate between the different editions of Windows Server 2003 Explain Windows Server 2003 network models and server roles Identify concepts relating to Windows Server 2003 network management
Dealing with Event Viewer
 Dealing with Event Viewer Event Viewer is a troubleshooting tool in Microsoft Windows 2000.This how-to article will describe how to use Event Viewer. Event Viewer displays detailed information about system
Dealing with Event Viewer Event Viewer is a troubleshooting tool in Microsoft Windows 2000.This how-to article will describe how to use Event Viewer. Event Viewer displays detailed information about system
User Management in Resource Manager
 CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
SharePoint AD Administration Tutorial for SharePoint 2007
 SharePoint AD Administration Tutorial for SharePoint 2007 1. General Note Please note that AD Administration has to be activated before it can be used. For further reference, please see our Product Installation
SharePoint AD Administration Tutorial for SharePoint 2007 1. General Note Please note that AD Administration has to be activated before it can be used. For further reference, please see our Product Installation
Netwrix Auditor. Tips and Tricks: How To Create Custom Active Directory Alerts. Version: /22/2014
 Netwrix Auditor Tips and Tricks: How To Create Custom Active Directory s Version: 6.5 10/22/2014 Legal Notice The information in this publication is furnished for information use only, and does not constitute
Netwrix Auditor Tips and Tricks: How To Create Custom Active Directory s Version: 6.5 10/22/2014 Legal Notice The information in this publication is furnished for information use only, and does not constitute
INF220x Security Practical Exercises
 INF220x Security Practical Exercises This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password is Pa55w.rd,
INF220x Security Practical Exercises This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password is Pa55w.rd,
NetWrix Privileged Account Manager Version 4.1 User Guide
 NetWrix Privileged Account Manager Version 4.1 User Guide Table of Contents 1. Introduction... 1 1.1 About Security Roles... 1 2. Configuring Product... 2 2.1 Configuring Child Folders... 2 2.2 Configuring
NetWrix Privileged Account Manager Version 4.1 User Guide Table of Contents 1. Introduction... 1 1.1 About Security Roles... 1 2. Configuring Product... 2 2.1 Configuring Child Folders... 2 2.2 Configuring
SMS 2.0 SSO / LDAP Launch Kit
 SMS 2.0 SSO / LDAP Launch Kit Table of Contents What options are available in SMS 2.0 for Single Sign On?... 4 LDAP (Lightweight Directory Access Protocol)... 4 SkySSO (Skyward Single Sign On)... 4 SkySTS
SMS 2.0 SSO / LDAP Launch Kit Table of Contents What options are available in SMS 2.0 for Single Sign On?... 4 LDAP (Lightweight Directory Access Protocol)... 4 SkySSO (Skyward Single Sign On)... 4 SkySTS
9.4 Authentication Server
 9 Useful Utilities 9.4 Authentication Server The Authentication Server is a password and account management system for multiple GV-VMS. Through the Authentication Server, the administrator can create the
9 Useful Utilities 9.4 Authentication Server The Authentication Server is a password and account management system for multiple GV-VMS. Through the Authentication Server, the administrator can create the
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
Parallels Mac Management for Microsoft SCCM
 Parallels Mac Management for Microsoft SCCM Administrator's Guide v4.5 Copyright 1999-2016 Parallels IP Holdings GmbH and its affiliates. All rights reserved. Parallels IP Holdings GmbH Vordergasse 59
Parallels Mac Management for Microsoft SCCM Administrator's Guide v4.5 Copyright 1999-2016 Parallels IP Holdings GmbH and its affiliates. All rights reserved. Parallels IP Holdings GmbH Vordergasse 59
CONFIGURING ENTERGROUP. What is LDAP? Getting Started with LDAP
 CONFIGURING LDAP @ ENTERGROUP In this tutorial you will learn how to manage your LDAP Directories within your EnterGroup account. We will walkthrough how to setup your directories and access them with
CONFIGURING LDAP @ ENTERGROUP In this tutorial you will learn how to manage your LDAP Directories within your EnterGroup account. We will walkthrough how to setup your directories and access them with
System Software Update Instructions
 System Software Update Instructions This document provides instructions for installing updated system software on the VERUS Diagnostic Platform. Installing an update is a two-part process: First install
System Software Update Instructions This document provides instructions for installing updated system software on the VERUS Diagnostic Platform. Installing an update is a two-part process: First install
Active Directory Synchronisation
 Active Directory Synchronisation Table of Contents Overview... 3 Important Notes... 3 Installation & Configuration... 4 Configuration & Field Mappings... 4 Attribute Mappings... 7 Adding New Mappings...
Active Directory Synchronisation Table of Contents Overview... 3 Important Notes... 3 Installation & Configuration... 4 Configuration & Field Mappings... 4 Attribute Mappings... 7 Adding New Mappings...
How to Integrate an External Authentication Server
 How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
How to Integrate an External Authentication Server Required Product Model and Version This article applies to the Barracuda Load Balancer ADC 540 and above, version 5.1 and above, and to all Barracuda
Grandstream Networks, Inc. LDAP Configuration Guide
 Grandstream Networks, Inc. Table of Contents INTRODUCTION... 4 LDAP SERVER CONFIGURATION... 5 LDAP PHONEBOOK... 6 Access the Default Phonebook DN... 6 Add a New Phonebook DN... 7 Add contacts to Phonebook
Grandstream Networks, Inc. Table of Contents INTRODUCTION... 4 LDAP SERVER CONFIGURATION... 5 LDAP PHONEBOOK... 6 Access the Default Phonebook DN... 6 Add a New Phonebook DN... 7 Add contacts to Phonebook
OOOCTA Version 4.1. Installation and Users Guide.
 OOOCTA Version 4.1 Installation and Users Guide www.telnetport25.com Contents Introduction... 2 Pre-Requisites... 2 Changes from Version 3.5... 2 Changes from Version 4.0... 2 Installation and Setup...
OOOCTA Version 4.1 Installation and Users Guide www.telnetport25.com Contents Introduction... 2 Pre-Requisites... 2 Changes from Version 3.5... 2 Changes from Version 4.0... 2 Installation and Setup...
ForeScout Extended Module for IBM BigFix
 Version 1.1 Table of Contents About BigFix Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 About Support for Dual Stack Environments... 5 Concepts, Components,
Version 1.1 Table of Contents About BigFix Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 About Support for Dual Stack Environments... 5 Concepts, Components,
One Identity Active Roles 7.2. Quick Start Guide
 One Identity Active Roles 7.2 Quick Start Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this
One Identity Active Roles 7.2 Quick Start Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this
S/MIME on Good for Enterprise MS Online Certificate Status Protocol. Installation and Configuration Notes. Updated: November 10, 2011
 S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
S/MIME on Good for Enterprise MS Online Certificate Status Protocol Installation and Configuration Notes Updated: November 10, 2011 Installing the Online Responder service... 1 Preparing the environment...
Reliable High-Speed Connection to Publication Database for Synchronization
 PCS Axis v1.9 Client/Server New Installation with Replication May 2015 Introduction American Innovations (AI) is pleased to announce version 1.9 of our Pipeline Compliance System Axis software (PCS Axis
PCS Axis v1.9 Client/Server New Installation with Replication May 2015 Introduction American Innovations (AI) is pleased to announce version 1.9 of our Pipeline Compliance System Axis software (PCS Axis
Configuring SAML-based Single Sign-on for Informatica Web Applications
 Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Overview of AdminSDHolder, protected groups and SDPROP Controlling groups that are protected by AdminSDHolder Security Descriptor propagator
 AdminSDHolder, Protected Groups and SDPROP John Policelli At a Glance: Overview of AdminSDHolder, protected groups and SDPROP Controlling groups that are protected by AdminSDHolder Security Descriptor
AdminSDHolder, Protected Groups and SDPROP John Policelli At a Glance: Overview of AdminSDHolder, protected groups and SDPROP Controlling groups that are protected by AdminSDHolder Security Descriptor
Enabling the Bullhorn and Calendar Integration with Google Apps
 Enabling the Bullhorn Email and Calendar Integration with Google Apps If you are interested in enabling this integration, please send a request to switch@bullhorn.com. Note that these instructions are
Enabling the Bullhorn Email and Calendar Integration with Google Apps If you are interested in enabling this integration, please send a request to switch@bullhorn.com. Note that these instructions are
BusinessObjects Enterprise XI Release 2
 Configuring Kerberos End-to-End Single Sign-On using IIS Overview Contents This document provides information and instructions for setting up Kerberos end-to-end Single Sign-On (SSO) using IIS to the database
Configuring Kerberos End-to-End Single Sign-On using IIS Overview Contents This document provides information and instructions for setting up Kerberos end-to-end Single Sign-On (SSO) using IIS to the database
Installation Guide. . All right reserved. For more information about Specops Inventory and other Specops products, visit
 . All right reserved. For more information about Specops Inventory and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Inventory is a trademark owned by Specops Software.
. All right reserved. For more information about Specops Inventory and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Inventory is a trademark owned by Specops Software.
Installation Guide. Mobile Print for Business version 1.0. July 2014 Issue 1.0
 Installation Guide Mobile Print for Business version 1.0 July 2014 Issue 1.0 Fuji Xerox Australia 101 Waterloo Road North Ryde NSW 2113 For technical queries please contact the Fuji Xerox Australia Customer
Installation Guide Mobile Print for Business version 1.0 July 2014 Issue 1.0 Fuji Xerox Australia 101 Waterloo Road North Ryde NSW 2113 For technical queries please contact the Fuji Xerox Australia Customer
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server
 Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Integrating Cisco CallManager IVR and Active Directory
 Integrating Cisco CallManager IVR and Active Directory Document ID: 29969 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Cisco CallManager Configuration
Integrating Cisco CallManager IVR and Active Directory Document ID: 29969 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Cisco CallManager Configuration
Configuring Embedded LDAP Authentication
 HP Restricted Configuring Embedded LDAP Authentication configure Configuring Embedded LDAP Authentication For HP product models: LaserJet 4345mfp, LaserJet 9040mfp, LaserJet 9050mfp, LaserJet 9500mfp,
HP Restricted Configuring Embedded LDAP Authentication configure Configuring Embedded LDAP Authentication For HP product models: LaserJet 4345mfp, LaserJet 9040mfp, LaserJet 9050mfp, LaserJet 9500mfp,
ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/grpolwt.htm
 Page 1 of 17 Windows 2000 Server Step-by-Step Guide to Understanding the Group Policy Feature Set Operating System Abstract Group Policy is the central component of the Change and Configuration Management
Page 1 of 17 Windows 2000 Server Step-by-Step Guide to Understanding the Group Policy Feature Set Operating System Abstract Group Policy is the central component of the Change and Configuration Management
Network+ Guide to Networks, Fourth Edition. Chapter 8 Network Operating Systems and Windows Server 2003-Based Networking
 Network+ Guide to Networks, Fourth Edition Chapter 8 Network Operating Systems and Windows Server 2003-Based Networking Objectives Discuss the functions and features of a network operating system Define
Network+ Guide to Networks, Fourth Edition Chapter 8 Network Operating Systems and Windows Server 2003-Based Networking Objectives Discuss the functions and features of a network operating system Define
WMI log collection using a non-admin domain user
 WMI log collection using a non-admin domain user To collect WMI logs from a domain controller in EventLog Analyer, it is necessary to add a domain admin account of that domain in it. Alternatively, you
WMI log collection using a non-admin domain user To collect WMI logs from a domain controller in EventLog Analyer, it is necessary to add a domain admin account of that domain in it. Alternatively, you
Implementing Single-Sign-On(SSO) for APM UI
 Implementing Single-Sign-On(SSO) for APM UI 1.Introduction...2 2.Overview of SSO with LTPA...3 3.Installing and configuring TDS...5 3.1.Installing TDS 6.3...5 3.2.Changing the administrator password (Optional)...7
Implementing Single-Sign-On(SSO) for APM UI 1.Introduction...2 2.Overview of SSO with LTPA...3 3.Installing and configuring TDS...5 3.1.Installing TDS 6.3...5 3.2.Changing the administrator password (Optional)...7
Quick Tips & Tricks. Important You must use SEMICOLONS ( ie; ) to separate address when sending mail to multiple users
 Quick Tips & Tricks Important You must use SEMICOLONS ( ie; ) to separate email address when sending mail to multiple users Customize Mail View Click, View, and then highlight Current View Click, Customize
Quick Tips & Tricks Important You must use SEMICOLONS ( ie; ) to separate email address when sending mail to multiple users Customize Mail View Click, View, and then highlight Current View Click, Customize
Quest Migration Manager for Exchange Target Exchange 2007 Environment Preparation
 Quest Migration Manager for Exchange 8.14 Target Exchange 2007 Environment Preparation 2017 Quest Software Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright.
Quest Migration Manager for Exchange 8.14 Target Exchange 2007 Environment Preparation 2017 Quest Software Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright.
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
Identity Policies. Identity Policy Overview. Establishing User Identity through Active Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Copyright 2012 Pulse Systems, Inc. Page 1 of 26
 The Procedures Table stores information about the Current Procedural Terminology, or CPT, procedure codes which are used in your practice. There are some CPT codes that are consistently used as a group.
The Procedures Table stores information about the Current Procedural Terminology, or CPT, procedure codes which are used in your practice. There are some CPT codes that are consistently used as a group.
INF204x Module 1, Lab 3 - Configure Windows 10 VPN
 INF204x Module 1, Lab 3 - Configure Windows 10 VPN Estimated Time: 40 minutes Your organization plans to allow Windows 10 users to connect to the internal network by using the VPN client built into the
INF204x Module 1, Lab 3 - Configure Windows 10 VPN Estimated Time: 40 minutes Your organization plans to allow Windows 10 users to connect to the internal network by using the VPN client built into the
APPENDIX B: INSTALLATION AND SETUP
 APPENDIX B: INSTALLATION AND SETUP Page A. Overview... B:1 How do I install and setup ICMS?... B:1 Do I need special security rights to install ICMS?... B:1 Installation Basics... B:1 How do I get a quick
APPENDIX B: INSTALLATION AND SETUP Page A. Overview... B:1 How do I install and setup ICMS?... B:1 Do I need special security rights to install ICMS?... B:1 Installation Basics... B:1 How do I get a quick
Accessing Personnel Info & Payslips
 Accessing Personnel Info & Payslips Agresso web services Contents 1. Logging In... 1 2. Viewing Personnel Information... 3 3. Viewing Payslips... 4 4. Printing Payslips... 6 1. Logging In 1. In the Internet
Accessing Personnel Info & Payslips Agresso web services Contents 1. Logging In... 1 2. Viewing Personnel Information... 3 3. Viewing Payslips... 4 4. Printing Payslips... 6 1. Logging In 1. In the Internet
IPBrick - Member of an AD domain IPBRICK SA
 IPBrick - Member of an AD domain IPBRICK SA October 4, 2016 2 Copyright c IPBRICK All rights reserved. 2015. The information contained in this document is subject to alterations without prior notice. Statements,
IPBrick - Member of an AD domain IPBRICK SA October 4, 2016 2 Copyright c IPBRICK All rights reserved. 2015. The information contained in this document is subject to alterations without prior notice. Statements,
Baan OpenWorld Broker 2.1. Installation Guide for Baan OpenWorld Broker 2.1
 Baan OpenWorld Broker 2.1 Installation Guide for Baan OpenWorld Broker 2.1 A publication of: Baan Development B.V. P.O.Box 143 3770 AC Barneveld The Netherlands Printed in the Netherlands Baan Development
Baan OpenWorld Broker 2.1 Installation Guide for Baan OpenWorld Broker 2.1 A publication of: Baan Development B.V. P.O.Box 143 3770 AC Barneveld The Netherlands Printed in the Netherlands Baan Development
OneStop Reporting 4.5 OSR Administration User Guide
 OneStop Reporting 4.5 OSR Administration User Guide Doc. Version 1.2 Updated: 10-Dec-14 Copyright OneStop Reporting AS Contents Introduction... 1 Who should read this manual... 1 What s included in this
OneStop Reporting 4.5 OSR Administration User Guide Doc. Version 1.2 Updated: 10-Dec-14 Copyright OneStop Reporting AS Contents Introduction... 1 Who should read this manual... 1 What s included in this
Abila MIP. Human Resource Management Installation Guide
 Human Resource Management Installation Guide This is a publication of Abila, Inc. Version 2017.2 2017 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila
Human Resource Management Installation Guide This is a publication of Abila, Inc. Version 2017.2 2017 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila
How to Configure Impersonation for OneDrive for Business Data Sources
 How to Configure Impersonation for OneDrive for Business Data Sources Before Getting Started Download and install the SharePoint Online Management Shell from the Microsoft Windows Download Center to a
How to Configure Impersonation for OneDrive for Business Data Sources Before Getting Started Download and install the SharePoint Online Management Shell from the Microsoft Windows Download Center to a
ForeScout Extended Module for IBM BigFix
 ForeScout Extended Module for IBM BigFix Version 1.0.0 Table of Contents About this Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 Concepts, Components, Considerations...
ForeScout Extended Module for IBM BigFix Version 1.0.0 Table of Contents About this Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 Concepts, Components, Considerations...
Installation Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
NBC-IG Installation Guide. Version 7.2
 Installation Guide Version 7.2 2017 Nuance Business Connect 7.2 Installation Guide Document Revision History Revision Date August 8, 2017 Revision List Updated supported SQL Server versions June 14, 2017
Installation Guide Version 7.2 2017 Nuance Business Connect 7.2 Installation Guide Document Revision History Revision Date August 8, 2017 Revision List Updated supported SQL Server versions June 14, 2017
Enabling Smart Card Logon for Linux Using Centrify Suite
 DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Linux Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Linux Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
Mac OS X - Adding a Networked Printer
 Overview... 1 Before You Begin... 1 Part 1: Installation Process... 2 1. Open the System Preferences Application... 2 2. Click on "Print & Scan" and unlock the preference pane (if necessary).... 2 3. Click
Overview... 1 Before You Begin... 1 Part 1: Installation Process... 2 1. Open the System Preferences Application... 2 2. Click on "Print & Scan" and unlock the preference pane (if necessary).... 2 3. Click
LDAP Servers for AAA
 This chapter describes how to configure LDAP servers used in AAA. About LDAP and the ASA, page 1 Guidelines for, page 5 Configure, page 5 Test LDAP Server Authentication and Authorization, page 9 Monitoring,
This chapter describes how to configure LDAP servers used in AAA. About LDAP and the ASA, page 1 Guidelines for, page 5 Configure, page 5 Test LDAP Server Authentication and Authorization, page 9 Monitoring,
CounterACT User Directory Plugin
 Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Version 6.1.2 and Above Table of Contents About the User Directory Plugin... 3 Endpoint User Details... 3 Verify Endpoint Authentication... 3 User Directory Inventory... 4 HTTP Login Action... 5 HTTP Sign
Introduction to LAN Introduction to TDC 363 Lecture 05 Course Outline What is NOS?
 Introduction to LAN TDC 363 Lecture 05 Nt Network rkoprti Operating Systems tm Windows Based Networking NetWare Based Networking Book Reading: Chapters 8 1 Course Outline Network operating system (NOS)
Introduction to LAN TDC 363 Lecture 05 Nt Network rkoprti Operating Systems tm Windows Based Networking NetWare Based Networking Book Reading: Chapters 8 1 Course Outline Network operating system (NOS)
Microsoft SQL Installation and Setup
 This chapter provides information about installing and setting up Microsoft SQL. Encrypted Database Not Supported, page 1 Install and Setup Microsoft SQL Server, page 1 Database Migration Required for
This chapter provides information about installing and setting up Microsoft SQL. Encrypted Database Not Supported, page 1 Install and Setup Microsoft SQL Server, page 1 Database Migration Required for
Setting up Certificate Authentication for SonicWall SRA / SMA 100 Series
 Setting up Certificate Authentication for SonicWall SRA / SMA 100 Series SonicWall SRA and SMA devices now have the option to authenticate using Client User Certificates. This is a guide on how to implement
Setting up Certificate Authentication for SonicWall SRA / SMA 100 Series SonicWall SRA and SMA devices now have the option to authenticate using Client User Certificates. This is a guide on how to implement
LDAP Configuration Guide
 LDAP Configuration Guide Publication date: 11/8/2017 www.xcalar.com Copyright 2017 Xcalar, Inc. All rights reserved. Table of Contents About this guide 3 Configuring LDAP 4 Before you start 5 Configuring
LDAP Configuration Guide Publication date: 11/8/2017 www.xcalar.com Copyright 2017 Xcalar, Inc. All rights reserved. Table of Contents About this guide 3 Configuring LDAP 4 Before you start 5 Configuring
Data Privilege Adding or Removing Members
 Data Privilege allows you to add or remove Members, aka Users, (individuals permitted to access all or portions of a group s resources) from any security group for which you are an Owner or an Authorizer.
Data Privilege allows you to add or remove Members, aka Users, (individuals permitted to access all or portions of a group s resources) from any security group for which you are an Owner or an Authorizer.
Outlook 2003, Level 2 Page 1
 Outlook 2003, Level 2 Page 1 Course Topics Creating and Sharing Contacts Customizing Views Sorting / Organizing Folders Managing Address Books Auto Signatures Sharing Folders (Calendars, Email Inboxes,
Outlook 2003, Level 2 Page 1 Course Topics Creating and Sharing Contacts Customizing Views Sorting / Organizing Folders Managing Address Books Auto Signatures Sharing Folders (Calendars, Email Inboxes,
Managing External Identity Sources
 CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
CHAPTER 5 The Cisco Identity Services Engine (Cisco ISE) integrates with external identity sources to validate credentials in user authentication functions, and to retrieve group information and other
Published By Imanami Corporation 5099 Preston Ave. Livermore, CA 94551, United States. Copyright 2008 by Imanami Corporation.
 Installation Guide Published By Imanami Corporation 5099 Preston Ave. Livermore, CA 94551, United States Copyright 2008 by Imanami Corporation. All rights reserved. No part of the contents of this document
Installation Guide Published By Imanami Corporation 5099 Preston Ave. Livermore, CA 94551, United States Copyright 2008 by Imanami Corporation. All rights reserved. No part of the contents of this document
Data Store and Admin Tool User Guide
 Data Store and Admin Tool User Guide Contents Contents What is a Data Store?... 8 Getting Started... 8 System Requirements... 8 Supported Operating Systems... 8 Support SQL Servers... 8 Tools Required
Data Store and Admin Tool User Guide Contents Contents What is a Data Store?... 8 Getting Started... 8 System Requirements... 8 Supported Operating Systems... 8 Support SQL Servers... 8 Tools Required
BLUEPRINT TEAM REPOSITORY. For Requirements Center & Requirements Center Test Definition
 BLUEPRINT TEAM REPOSITORY Installation Guide for Windows For Requirements Center & Requirements Center Test Definition Table Of Contents Contents Table of Contents Getting Started... 3 About the Blueprint
BLUEPRINT TEAM REPOSITORY Installation Guide for Windows For Requirements Center & Requirements Center Test Definition Table Of Contents Contents Table of Contents Getting Started... 3 About the Blueprint
inforouter V7 implementation Guide.
 inforouter V7 implementation Guide. http://www.inforouter.com inforouter V7 implementation Guide This guide will take you through the step-by-step installation procedures required for a successful inforouter
inforouter V7 implementation Guide. http://www.inforouter.com inforouter V7 implementation Guide This guide will take you through the step-by-step installation procedures required for a successful inforouter
Contents Overview... 5 Downloading Primavera Gateway... 5 Primavera Gateway On-Premises Installation Prerequisites... 6
 Gateway Installation and Configuration Guide for On-Premises Version 17 September 2017 Contents Overview... 5 Downloading Primavera Gateway... 5 Primavera Gateway On-Premises Installation Prerequisites...
Gateway Installation and Configuration Guide for On-Premises Version 17 September 2017 Contents Overview... 5 Downloading Primavera Gateway... 5 Primavera Gateway On-Premises Installation Prerequisites...
Envelope Journaling for Microsoft Exchange 2003 Version 1.0
 Barracuda Message Archiver Organizations using Microsoft Exchange 2003 can take advantage of its envelope journaling feature to send all messages along with all recipient information directly to the Barracuda
Barracuda Message Archiver Organizations using Microsoft Exchange 2003 can take advantage of its envelope journaling feature to send all messages along with all recipient information directly to the Barracuda
EMC SourceOne Discovery Manager Version 6.5
 EMC SourceOne Discovery Manager Version 6.5 Installation and Administration Guide 300-008-569 REV A01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748-9103 1-508-435-1000 www.emc.com Copyright
EMC SourceOne Discovery Manager Version 6.5 Installation and Administration Guide 300-008-569 REV A01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748-9103 1-508-435-1000 www.emc.com Copyright
SYNTHESYS MANAGEMENT
 SYNTHESYS MANAGEMENT Teams User Management Synthesys.Net Management Basics 1 SYNTHESYS.NET MANAGEMENT Introduction... 3 Synthesys Management Features... 4 User Login... 5 Synthesys Management Main Screen...
SYNTHESYS MANAGEMENT Teams User Management Synthesys.Net Management Basics 1 SYNTHESYS.NET MANAGEMENT Introduction... 3 Synthesys Management Features... 4 User Login... 5 Synthesys Management Main Screen...
Configure SharePoint Server 2010 as a single server with the Unitrends appliance. farm with the Unitrends appliance
 Configure SharePoint Server 2010 as a single server with the Unitrends appliance I. Configure SharePoint single server 1. Logon to the server with an account that has local administrator credentials 2.
Configure SharePoint Server 2010 as a single server with the Unitrends appliance I. Configure SharePoint single server 1. Logon to the server with an account that has local administrator credentials 2.
How does it look like?
 EasyAdmin Windows Authentication KB4031b 1 The OpenLM EasyAdmin administrative web interface incorporates a role-based security access scheme, facilitating different levels of access to different role
EasyAdmin Windows Authentication KB4031b 1 The OpenLM EasyAdmin administrative web interface incorporates a role-based security access scheme, facilitating different levels of access to different role
Deploying a System Center 2012 R2 Configuration Manager Hierarchy
 Deploying a System Center 2012 R2 Configuration Manager Hierarchy This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION
Deploying a System Center 2012 R2 Configuration Manager Hierarchy This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION
CRM Integration LDAP 06/01/2016
 CRM Integration LDAP 06/01/2016 CRM Integration LDAP Page 0 CRM Integration Contents Intro... 2 Configuration... 2 Connection... 2 Fields... 2 Show Contact... 3 Testing... 4 CRM Integration LDAP Page 1
CRM Integration LDAP 06/01/2016 CRM Integration LDAP Page 0 CRM Integration Contents Intro... 2 Configuration... 2 Connection... 2 Fields... 2 Show Contact... 3 Testing... 4 CRM Integration LDAP Page 1
edp 8.2 Info Sheet - Integrating the ediscovery Platform 8.2 & Enterprise Vault
 edp 8.2 Info Sheet - Integrating the ediscovery Platform 8.2 & Enterprise Vault 12.0.1 Date: December 2017 Author: Technical Field Enablement (II-TEC@veritas.com) Applies to: ediscovery Platform 8.x and
edp 8.2 Info Sheet - Integrating the ediscovery Platform 8.2 & Enterprise Vault 12.0.1 Date: December 2017 Author: Technical Field Enablement (II-TEC@veritas.com) Applies to: ediscovery Platform 8.x and
Copyright
 Active Directory allows multiple password policies to be created in the same domain. This is referred to as fine grained password policy. This video looks at how to use multiple passwords policies applying
Active Directory allows multiple password policies to be created in the same domain. This is referred to as fine grained password policy. This video looks at how to use multiple passwords policies applying
Use mail merge to create and print letters and other documents
 Use mail merge to create and print letters and other documents Contents Use mail merge to create and print letters and other documents... 1 Set up the main document... 1 Connect the document to a data
Use mail merge to create and print letters and other documents Contents Use mail merge to create and print letters and other documents... 1 Set up the main document... 1 Connect the document to a data
