Michael Rash DEFCON 12 07/31/2004
|
|
|
- Warren Chase
- 5 years ago
- Views:
Transcription
1 Advanced Netfilter: Content Replacement (ala Snort_inline) and Combining Port Knocking with p0f Michael Rash DEFCON 12 07/31/
2 Introduction Port knocking Passive OS fingerprinting with p0f fwknop Iptables string match extension String replacement patch Netperf benchmarks
3 Port Knocking Information hiding within sequences of connections to closed (or open) ports Access control modification Can be encrypted or shared Multiple protocols Relative timings Third party IP access Server side is totally passive Martin Krzywinski
4 Shared Sequence (1) Knock client ( ): tcp/1001 tcp/1002 tcp/1003 tcp/1004 tcp/22 Knock server ( ): opens tcp/22
5 Shared Sequence (2) Knock client ( ): tcp/64531 udp/63533 tcp/5001 tcp/5002 icmp echo request icmp echo request (wait at least 10 seconds) udp/5003 Knock server ( ): opens tcp/22 and udp/5000 for five minutes
6 Encrypted Sequence (1) Knock client ( ): IP: four 8 bit values ( ) Port: concatenation of two 8 bit values (5500) Protocol: one 8 bit value (1, 6, 17) Rijndael block size = 16 bytes plain text: cipher text: Knock server ( ): Special range of ports, 8 bits wide (e.g )
7 Encrypted Sequence (2) Knock client ( ): tcp/60186 tcp/60242 tcp/60110 tcp/60108 tcp/60160 tcp/60231 tcp/ Knock server ( ): Give access through firewall to tcp/5500 for IP
8 p0f OS fingerprinting via tcp SYN packets SYN+ACK fingerprinting RST fingerprinting libpcap Michal Zalewski
9 Header Fields tcp SYN flag tcp window size maximum segment size selective acknowledgement OK? NOP tcp window scale timestamp ttl fragment bits packet size
10 p0f Signatures FreeBSD:4.4::FreeBSD 4.4: 1024:64:1:60:M*,N,W0,N,N,T Linux:2.4::Linux 2.4/2.6: S4:64:1:60:M*,S,T,N,W0 Window size Initial TTL Don't fragment bit Packet size TCP options
11 Iptables Logs iptables -A INPUT -p tcp -i eth0 -j LOG --log-prefix DROP --log-tcp-options (iptables -A INPUT -p tcp -i eth0 -j DROP)
12 Iptables Logs; Decoded IP header fields Source and destination IP addresses IP datagram length Type of service TTL IP ID Fragment bits Protocol Jul 8 03:06:12 orthanc kernel: DROP IN=eth0 OUT= MAC=00:a0:cc:28:42:5a:00:00:00:22:2d:42:00:00 SRC: DST: LEN=60 TOS=0x10 PREC=0x00 TTL=64 ID=6854 DF PROTO=TCP
13 Iptables Logs; Decoded TCP header fields Source and destination ports TCP window size TCP flags Jul 8 03:06:12 orthanc kernel: DROP IN=eth0 OUT= MAC=00:a0:cc:28:42:5a:00:00:00:22:2d:42:00:00 SRC: DST: LEN=60 TOS=0x10 PREC=0x00 TTL=64 ID=6854 DF PROTO=TCP SPT=32788 DPT=5500 WINDOW=5840 RES=0x00 SYN URGP=0
14 Iptables Logs; Encoded TCP header fields TCP options!!! p0f depends on this. Jul 8 03:06:12 orthanc kernel: DROP IN=eth0 OUT= MAC=00:a0:cc:28:42:5a:00:00:00:22:2d:42:00:00 SRC: DST: LEN=60 TOS=0x10 PREC=0x00 TTL=64 ID=6854 DF PROTO=TCP SPT=32788 DPT=5500 WINDOW=5840 RES=0x00 SYN URGP=0 OPT (020405B A006F1D8E )
15 TCP options encoding Two formats: type (8 bits) type (8 bits) / length (8 bits) / value (n-16 bits) e.g b4 = MSS / 4 bytes / = NOP 00 = End of options
16 Decoded TCP options OPT (020405B A00749E ) MSS = 1460 Selective Acknowledgement permitted Timestamp NOP Window Scale = 0
17 Packet Summary Length = 60 Don't fragment bit TTL = 64 Window size = 5840 MSS = 1460 Selective Acknowledgement permitted Timestamp NOP Window Scale = 0
18 What does p0f have to say? S4:64:1:60:M*,S,T,N,W0 Linux:2.4::Linux 2.4/2.6
19 Other fingerprinting strategies IP ID Type of Service Passive OS Fingerprinting: Details and Techniques, Toby Miller Xprobe Ofir Arkin
20 fwknop Iptables log messages Shared or encrypted knock sequences Multi-protocol (tcp, udp, icmp) IP/network restriction Relative and absolute port timings Local username identification Selectable iptables ruleset entry Access timeouts Exact or regex OS match
21 Implementation client/server Knock sequences encrypted via Rijndael syslog monitor knopmd named pipe sysklogd and syslog-ng Process monitoring knopwatchd OpenBSD /etc/pf.os
22 Live Demo...
23 PART II
24 Iptables string match extension Application layer inspection Boyer-Moore algorithm BM_MAX_HLEN = 1024 linux/include/linux/netfilter_ipv4/ipt_ string.h
25 String match interface Snort SID 940: WEB-FRONTPAGE shtml.dll iptables -I FORWARD 1 -p tcp --dport 80 --tcp-flags ACK ACK -m string --string /_vti_bin/shtml.dll -j LOG --logprefix SID940
26 String match interface (2) Snort SID 261: DNS EXPLOIT named overflow attempt iptables -I FORWARD 1 -p tcp --dport 53 --tcp-flags ACK ACK -m string --hexstring CD80 E8D7 FFFF FF /bin/sh -j LOG --log-prefix SID261
27 Iptables targets -j ACCEPT -j DROP -j RETURN -j REJECT --reject-with icmp-net-unreachable icmp-host-unreachable icmp-port-unreachable... tcp-reset
28 fwsnort Translates Snort rules into equivalent iptables rules String match extension 70% translation rate
29 Evasion Packet fragmentation Polymorphic shellcode URL encoding Session splicing (Whisker)
30 Inline IDS/IPS Linux bridge Netfilter libipq libnet Snort_inline
31 Snort_inline packet decisions Alert Drop Reject Replace Pass content: /bin/sh ; replace: /ben/sh ;
32 Snort_inline packet journey (kernel space) packet in ingress interface (kernel space) iptables FORWARD chain (kernel space) QUEUE target -> libipq (user space) context switch to Snort_inline (user space) Snort detection engine (user space) libipq and packet verdict (kernel space) packet on egress interface
33 Iptables string match patch linux/net/ipv4/netfilter/ipt_string.c char * search(char *needle, char *haystack, int nlen, int hlen) We get a pointer to the data!!! What about checksums?
34 Replace string interface Snort SID 940: WEB-FRONTPAGE shtml.dll iptables -I FORWARD 1 -p tcp --dport 80 --tcp-flags ACK ACK -m string --string /_vti_bin/shtml.dll --replace-string /vti_bin/shtml.dab -j LOG --logprefix nullify SID940
35 Replace string interface (2) Snort SID 261: DNS EXPLOIT named overflow attempt iptables -I FORWARD 1 -p tcp --dport 53 --tcp-flags ACK ACK -m string --hexstring CD80 E8D7 FFFF FF /bin/sh -- replace-hex-string /ben/sh -j LOG --log-prefix nullify SID261
36 Iptables packet journey (kernel space) packet on ingress interface (kernel space) packet match in FORWARD chain (kernel space) string match function (kernel space) data replacement (kernel space) packet on egress interface
37 Netperf bencharks Netperf Data port patch netperf client snort/iptables netperf server
38 Throughput; 100MB Network Iptables forwarding: 1.95MB/s Snort_inline forwarding: 1.72MB/s 12% faster Iptables replace: 1.92MB/s Snort_inline replace: 1.72MB/s 10% faster Iptables replace and log: 1.53MB/s Snort_inline replace and log: 1.02MB/s 43% faster
39 Applications? Well-defined exploits Preserve application layer responses
40 References fwknop: fwsnort: snort2iptables: Snort_inline: The Base Rate Fallacy and its Implications for the Difficulty of Intrusion Detection :
41
IDS signature matching with iptables, psad, and fwsnort
 M I K E R A S H IDS signature matching with iptables, psad, and fwsnort Michael Rash holds a Master s degree in Applied Mathematics and works as a Security Architect for Enterasys Networks, Inc. He is
M I K E R A S H IDS signature matching with iptables, psad, and fwsnort Michael Rash holds a Master s degree in Applied Mathematics and works as a Security Architect for Enterasys Networks, Inc. He is
Meet the Anti-Nmap: PSAD (EnGarde Secure Linux)
 By Ryan Published: 2008-02-18 17:16 Meet the Anti-Nmap: PSAD (EnGarde Secure Linux) (by Eckie S. from Linuxsecurity.com) The Port Scan Attack Detector (psad) is an excellent tool for detecting various
By Ryan Published: 2008-02-18 17:16 Meet the Anti-Nmap: PSAD (EnGarde Secure Linux) (by Eckie S. from Linuxsecurity.com) The Port Scan Attack Detector (psad) is an excellent tool for detecting various
How to use IP Tables
 How to use IP Tables ******************************************************************* *** IPTABLES TUTORIAL I. Definitions and similarities to ipchains II. Chain types and options III. Command line
How to use IP Tables ******************************************************************* *** IPTABLES TUTORIAL I. Definitions and similarities to ipchains II. Chain types and options III. Command line
Zero Day Attack Prevention via Single Packet Authorization
 Zero Day Attack Prevention via Single Packet Authorization Michael Rash Security Architect Enterasys Networks, Inc. http://www.cipherdyne.org/ 2007.06.05 Techno Security Copyright (C) 2007, Michael Rash
Zero Day Attack Prevention via Single Packet Authorization Michael Rash Security Architect Enterasys Networks, Inc. http://www.cipherdyne.org/ 2007.06.05 Techno Security Copyright (C) 2007, Michael Rash
Advances In Single Packet Authorization
 Advances In Single Packet Authorization Michael Rash Enterasys Networks, Inc. http://www.cipherdyne.org/ ShmooCon 01/14/2006 Agenda Vulnerabilities vs. IDS/IPS Why another authentication / authorization
Advances In Single Packet Authorization Michael Rash Enterasys Networks, Inc. http://www.cipherdyne.org/ ShmooCon 01/14/2006 Agenda Vulnerabilities vs. IDS/IPS Why another authentication / authorization
CSCI 680: Computer & Network Security
 CSCI 680: Computer & Network Security Lecture 21 Prof. Adwait Nadkarni Fall 2017 Derived from slides by William Enck, Micah Sherr and Patrick McDaniel 1 Filtering: Firewalls Filtering traffic based on
CSCI 680: Computer & Network Security Lecture 21 Prof. Adwait Nadkarni Fall 2017 Derived from slides by William Enck, Micah Sherr and Patrick McDaniel 1 Filtering: Firewalls Filtering traffic based on
Service Cloaking and Anonymous Access; Combining Tor with Single Packet Authorization (SPA)
 Service Cloaking and Anonymous Access; Combining Tor with Single Packet Authorization (SPA) Michael Rash CTO, Solirix Inc. michael.rash@solirix.com http://www.cipherdyne.org/ DEF CON 08/05/2006 Agenda
Service Cloaking and Anonymous Access; Combining Tor with Single Packet Authorization (SPA) Michael Rash CTO, Solirix Inc. michael.rash@solirix.com http://www.cipherdyne.org/ DEF CON 08/05/2006 Agenda
Firewalls. Firewall. means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense
 FIREWALLS 3 Firewalls Firewall means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense administered network public Internet firewall
FIREWALLS 3 Firewalls Firewall means of protecting a local system or network of systems from network-based security threats creates a perimeter of defense administered network public Internet firewall
 This is Google's cache of http://www.rigacci.org/wiki/lib/exe/fetch.php/doc/appunti/linux/sa/iptables/conntrack.html. It is a snapshot of the page as it appeared on 24 Oct 2012 08:53:12 GMT. The current
This is Google's cache of http://www.rigacci.org/wiki/lib/exe/fetch.php/doc/appunti/linux/sa/iptables/conntrack.html. It is a snapshot of the page as it appeared on 24 Oct 2012 08:53:12 GMT. The current
Linux Firewalls. Frank Kuse, AfNOG / 30
 Linux Firewalls Frank Kuse, AfNOG 2017 1 / 30 About this presentation Based on a previous talk by Kevin Chege and Chris Wilson, with thanks! You can access this presentation at: Online: http://afnog.github.io/sse/firewalls/
Linux Firewalls Frank Kuse, AfNOG 2017 1 / 30 About this presentation Based on a previous talk by Kevin Chege and Chris Wilson, with thanks! You can access this presentation at: Online: http://afnog.github.io/sse/firewalls/
inside: THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN
 THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 inside: SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN & The Advanced Computing Systems Association & The System Administrators
THE MAGAZINE OF USENIX & SAGE April 2002 Volume 27 Number 2 inside: SECURITY A Remote Active OS Fingerprinting Tool Using ICMP BY OFIR ARKIN & The Advanced Computing Systems Association & The System Administrators
8/19/2010. Computer Forensics Network forensics. Data sources. Monitoring
 Computer Forensics Network forensics Thomas Mundt thm@informatik.uni-rostock.de Data sources Assessment Monitoring Monitoring Software Logs and Log Analysis Incident Analysis External Assessment Hackers
Computer Forensics Network forensics Thomas Mundt thm@informatik.uni-rostock.de Data sources Assessment Monitoring Monitoring Software Logs and Log Analysis Incident Analysis External Assessment Hackers
Internet Protocol and Transmission Control Protocol
 Internet Protocol and Transmission Control Protocol CMSC 414 November 13, 2017 Internet Protcol Recall: 4-bit version 4-bit hdr len 8-bit type of service 16-bit total length (bytes) 8-bit TTL 16-bit identification
Internet Protocol and Transmission Control Protocol CMSC 414 November 13, 2017 Internet Protcol Recall: 4-bit version 4-bit hdr len 8-bit type of service 16-bit total length (bytes) 8-bit TTL 16-bit identification
Building an IPS solution for inline usage during Red Teaming
 Building an IPS solution for inline usage during Red Teaming Repurposing defensive technologies for offensive Red Team operations K. Mladenov A. Zismer {kmladenov,azismer}@os3.nl Master Students in System
Building an IPS solution for inline usage during Red Teaming Repurposing defensive technologies for offensive Red Team operations K. Mladenov A. Zismer {kmladenov,azismer}@os3.nl Master Students in System
Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y / P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A
 Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y 2 01 6 / 2 017 P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A Slides are based on slides by Dr Lawrie Brown (UNSW@ADFA) for Computer
Firewalls N E T W O R K ( A N D D ATA ) S E C U R I T Y 2 01 6 / 2 017 P E D R O B R A N D Ã O M A N U E L E D U A R D O C O R R E I A Slides are based on slides by Dr Lawrie Brown (UNSW@ADFA) for Computer
IK2206 Internet Security and Privacy Firewall & IP Tables
 IK2206 Internet Security and Privacy Firewall & IP Tables Group Assignment Following persons were members of group C and authors of this report: Name: Christoph Moser Mail: chmo@kth.se P-Nr: 850923-T513
IK2206 Internet Security and Privacy Firewall & IP Tables Group Assignment Following persons were members of group C and authors of this report: Name: Christoph Moser Mail: chmo@kth.se P-Nr: 850923-T513
Packet Header Formats
 A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
NIDS: Snort. Group 8. Niccolò Bisagno, Francesco Fiorenza, Giulio Carlo Gialanella, Riccardo Isoli
 NIDS: Snort Group 8 Niccolò Bisagno, Francesco Fiorenza, Giulio Carlo Gialanella, Riccardo Isoli 1 Summary NIDS Snort Syn Flood Attack Exploit Kit Detection: Bleeding Life Packet Level Evasion Snort as
NIDS: Snort Group 8 Niccolò Bisagno, Francesco Fiorenza, Giulio Carlo Gialanella, Riccardo Isoli 1 Summary NIDS Snort Syn Flood Attack Exploit Kit Detection: Bleeding Life Packet Level Evasion Snort as
! ' ,-. +) +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+, ) 05,-. /,*+), 01/-*+) + 01/.*+)
 ! "#! # $ %& #! '!!!( &!)'*+' '(,-. +) /,*+), 01/-*+) + 01/.*+) ) 05,-. +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+,3 4 +. 6*! ) ) ) ) 5 ) ) ) ) + 5 + + ) ) ) 5 9 + ) ) + 5 4 ) ) + ) 5, ) )
! "#! # $ %& #! '!!!( &!)'*+' '(,-. +) /,*+), 01/-*+) + 01/.*+) ) 05,-. +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+,3 4 +. 6*! ) ) ) ) 5 ) ) ) ) + 5 + + ) ) ) 5 9 + ) ) + 5 4 ) ) + ) 5, ) )
Inside Products TCP Problem Finder Thinking Inside the Box
 Inside Products TCP Problem Finder Thinking Inside the Box www.insidethestack.com (831) 659-8360 sales@insidethestack.com Inside Products Products Inside the Stack Early Warning System TCP Problem Finder
Inside Products TCP Problem Finder Thinking Inside the Box www.insidethestack.com (831) 659-8360 sales@insidethestack.com Inside Products Products Inside the Stack Early Warning System TCP Problem Finder
K2289: Using advanced tcpdump filters
 K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
Chapter 7. Network Intrusion Detection and Analysis. SeoulTech UCS Lab (Daming Wu)
 SeoulTech UCS Lab Chapter 7 Network Intrusion Detection and Analysis 2015. 11. 3 (Daming Wu) Email: wdm1517@gmail.com Copyright c 2015 by USC Lab All Rights Reserved. Table of Contents 7.1 Why Investigate
SeoulTech UCS Lab Chapter 7 Network Intrusion Detection and Analysis 2015. 11. 3 (Daming Wu) Email: wdm1517@gmail.com Copyright c 2015 by USC Lab All Rights Reserved. Table of Contents 7.1 Why Investigate
Veryx ATTEST TM. Sample Test cases Overview. Conformance Test Suite. Internet Protocol version 4 (IPv4) Part Number: T / TCLS IPv /1.
 Veryx ATTEST TM Conformance Test Suite Internet Protocol version 4 (IPv4) Sample Test cases Overview Part Number: T / TCLS IPv4 1.0-1110/1.0 This page is intentionally left blank. Introduction The Veryx
Veryx ATTEST TM Conformance Test Suite Internet Protocol version 4 (IPv4) Sample Test cases Overview Part Number: T / TCLS IPv4 1.0-1110/1.0 This page is intentionally left blank. Introduction The Veryx
IpMorph : Unification of OS fingerprinting defeating or, how to defeat common OSFP tools.
 IpMorph : Unification of OS fingerprinting defeating or, how to defeat common OSFP tools. Guillaume PRIGENT Florian VICHOT DIATEAM - Brest 1 Context Reason for creating IpMorph : Hynesim Project: We needed
IpMorph : Unification of OS fingerprinting defeating or, how to defeat common OSFP tools. Guillaume PRIGENT Florian VICHOT DIATEAM - Brest 1 Context Reason for creating IpMorph : Hynesim Project: We needed
Table of Contents. 1 Intrusion Detection Statistics 1-1 Overview 1-1 Displaying Intrusion Detection Statistics 1-1
 Table of Contents 1 Intrusion Detection Statistics 1-1 Overview 1-1 Displaying Intrusion Detection Statistics 1-1 i 1 Intrusion Detection Statistics Overview Intrusion detection is an important network
Table of Contents 1 Intrusion Detection Statistics 1-1 Overview 1-1 Displaying Intrusion Detection Statistics 1-1 i 1 Intrusion Detection Statistics Overview Intrusion detection is an important network
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Certification. Securing Networks
 Certification Securing Networks UNIT 9 Securing Networks 1 Objectives Explain packet filtering architecture Explain primary filtering command syntax Explain Network Address Translation Provide examples
Certification Securing Networks UNIT 9 Securing Networks 1 Objectives Explain packet filtering architecture Explain primary filtering command syntax Explain Network Address Translation Provide examples
Sharing is Caring: Improving Detection with Sigma
 SANS Tactical Detection and Data Analytics Summit 2018 Sharing is Caring: Improving Detection with Sigma John Hubbard (@SecHubb) The Blue Team's Journey Sharing is Caring - John Hubbard @SecHubb 2 Blue
SANS Tactical Detection and Data Analytics Summit 2018 Sharing is Caring: Improving Detection with Sigma John Hubbard (@SecHubb) The Blue Team's Journey Sharing is Caring - John Hubbard @SecHubb 2 Blue
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Computer Security Spring Firewalls. Aggelos Kiayias University of Connecticut
 Computer Security Spring 2008 Firewalls Aggelos Kiayias University of Connecticut Idea: Monitor inbound/ outbound traffic at a communication point Firewall firewall Internet LAN A firewall can run on any
Computer Security Spring 2008 Firewalls Aggelos Kiayias University of Connecticut Idea: Monitor inbound/ outbound traffic at a communication point Firewall firewall Internet LAN A firewall can run on any
Distributed Systems. 27. Firewalls and Virtual Private Networks Paul Krzyzanowski. Rutgers University. Fall 2013
 Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Information Network 1 TCP 1/2
 Functions provided by the transport layer Information Network 1 TCP 1/2 Youki Kadobayashi NAIST! Communication between processes " designation of process " identification of inter-process channel! Interface
Functions provided by the transport layer Information Network 1 TCP 1/2 Youki Kadobayashi NAIST! Communication between processes " designation of process " identification of inter-process channel! Interface
Transport: How Applications Communicate
 Transport: How Applications Communicate Week 2 Philip Levis 1 7 Layers (or 4) 7. 6. 5. 4. 3. 2. 1. Application Presentation Session Transport Network Link Physical segments packets frames bits/bytes Application
Transport: How Applications Communicate Week 2 Philip Levis 1 7 Layers (or 4) 7. 6. 5. 4. 3. 2. 1. Application Presentation Session Transport Network Link Physical segments packets frames bits/bytes Application
Configuring Firepower Threat Defense interfaces in Routed mode
 Configuring Firepower Threat Defense interfaces in Routed mode Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Configure a Routed Interface
Configuring Firepower Threat Defense interfaces in Routed mode Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Configure a Routed Interface
Network Interconnection
 Network Interconnection Covers different approaches for ensuring border or perimeter security Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Lecture
Network Interconnection Covers different approaches for ensuring border or perimeter security Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Lecture
I TCP 1/2. Internet TA: Connection-oriented (virtual circuit) Connectionless (datagram) (flow control) (congestion control) TCP Connection-oriented
 I TCP 1/2 TA: Connection-oriented (virtual circuit) Connectionless (datagram) (flow control) (congestion control) Internet TCP Connection-oriented UDP Connectionless IP + TCP (connection-oriented) (byte
I TCP 1/2 TA: Connection-oriented (virtual circuit) Connectionless (datagram) (flow control) (congestion control) Internet TCP Connection-oriented UDP Connectionless IP + TCP (connection-oriented) (byte
App. App. Master Informatique 1 st year 1 st term. ARes/ComNet Applications (7 points) Anonymous ID: stick number HERE
 Master Informatique 1 st year 1 st term Anonymous ID: stick number HERE Master Informatique 1 st year 1 st term App ARes/ComNet 2015-2016 Midterm exam : Version A in English Duration: 2h00 Allowed: One
Master Informatique 1 st year 1 st term Anonymous ID: stick number HERE Master Informatique 1 st year 1 st term App ARes/ComNet 2015-2016 Midterm exam : Version A in English Duration: 2h00 Allowed: One
A quick theorical introduction to network scanning. 23rd November 2005
 A quick theorical introduction to network ASBL CSRRT-LU (Computer Security Research and Response Team Luxembourg) http://www.csrrt.org/ 23rd November 2005 IP protocol ACK Network is not exact science When
A quick theorical introduction to network ASBL CSRRT-LU (Computer Security Research and Response Team Luxembourg) http://www.csrrt.org/ 23rd November 2005 IP protocol ACK Network is not exact science When
Networking Technologies and Applications
 Networking Technologies and Applications Rolland Vida BME TMIT Transport Protocols UDP User Datagram Protocol TCP Transport Control Protocol and many others UDP One of the core transport protocols Used
Networking Technologies and Applications Rolland Vida BME TMIT Transport Protocols UDP User Datagram Protocol TCP Transport Control Protocol and many others UDP One of the core transport protocols Used
Security Impacts of Abusing IPv6 Extension Headers
 Security Impacts of Abusing IPv6 Extension Headers Antonios Atlasis antonios.atlasis@cscss.org Centre for Strategic Cyberspace + Security Science Bio Independent IT Security analyst/researcher. MPhil Univ.
Security Impacts of Abusing IPv6 Extension Headers Antonios Atlasis antonios.atlasis@cscss.org Centre for Strategic Cyberspace + Security Science Bio Independent IT Security analyst/researcher. MPhil Univ.
Zone-Based Firewall Logging Export Using NetFlow
 Zone-Based Firewall Logging Export Using NetFlow Zone-based firewalls support the logging of messages to an external collector using NetFlow Version 9 export format. NetFlow Version 9 export format uses
Zone-Based Firewall Logging Export Using NetFlow Zone-based firewalls support the logging of messages to an external collector using NetFlow Version 9 export format. NetFlow Version 9 export format uses
CNIT 50: Network Security Monitoring. 6 Command Line Packet Analysis Tools
 CNIT 50: Network Security Monitoring 6 Command Line Packet Analysis Tools Topics SO Tool Categories Running Tcpdump Using Dumpcap and Tshark Running Argus and the Ra Client SO Tool Categories Three Types
CNIT 50: Network Security Monitoring 6 Command Line Packet Analysis Tools Topics SO Tool Categories Running Tcpdump Using Dumpcap and Tshark Running Argus and the Ra Client SO Tool Categories Three Types
CIT 480: Securing Computer Systems
 CIT 480: Securing Computer Systems Intrusion Detection CIT 480: Securing Computer Systems Slide #1 Topics 1. Definitions and Goals 2. Models of Intrusion Detection 3. False Positives 4. Architecture of
CIT 480: Securing Computer Systems Intrusion Detection CIT 480: Securing Computer Systems Slide #1 Topics 1. Definitions and Goals 2. Models of Intrusion Detection 3. False Positives 4. Architecture of
Distributed Systems. 29. Firewalls. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Distributed Systems 29. Firewalls Paul Krzyzanowski Rutgers University Fall 2015 2013-2015 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive data & systems not accessible Integrity:
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
network security s642 computer security adam everspaugh
 network security s642 adam everspaugh ace@cs.wisc.edu computer security today Announcement: HW3 to be released WiFi IP, TCP DoS, DDoS, prevention 802.11 (wifi) STA = station AP = access point BSS = basic
network security s642 adam everspaugh ace@cs.wisc.edu computer security today Announcement: HW3 to be released WiFi IP, TCP DoS, DDoS, prevention 802.11 (wifi) STA = station AP = access point BSS = basic
CIT 480: Securing Computer Systems
 CIT 480: Securing Computer Systems Scanning CIT 480: Securing Computer Systems Slide #1 Topics 1. Port Scanning 2. Stealth Scanning 3. Version Identification 4. OS Fingerprinting CIT 480: Securing Computer
CIT 480: Securing Computer Systems Scanning CIT 480: Securing Computer Systems Slide #1 Topics 1. Port Scanning 2. Stealth Scanning 3. Version Identification 4. OS Fingerprinting CIT 480: Securing Computer
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6
 FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
CS 465 Networks. Disassembling Datagram Headers
 CS 465 Networks Disassembling Datagram Headers School of Computer Science Howard Hughes College of Engineering University of Nevada, Las Vegas (c) Matt Pedersen, 2006 Recall the first 5x4 octets of the
CS 465 Networks Disassembling Datagram Headers School of Computer Science Howard Hughes College of Engineering University of Nevada, Las Vegas (c) Matt Pedersen, 2006 Recall the first 5x4 octets of the
A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers
 A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers Objectives The main objective of this assignment is to gain a deeper understanding of network activities and network packet formats using
A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers Objectives The main objective of this assignment is to gain a deeper understanding of network activities and network packet formats using
CS 356: Computer Network Architectures. Lecture 10: IP Fragmentation, ARP, and ICMP. Xiaowei Yang
 CS 356: Computer Network Architectures Lecture 10: IP Fragmentation, ARP, and ICMP Xiaowei Yang xwy@cs.duke.edu Overview Homework 2-dimension parity IP fragmentation ARP ICMP Fragmentation and Reassembly
CS 356: Computer Network Architectures Lecture 10: IP Fragmentation, ARP, and ICMP Xiaowei Yang xwy@cs.duke.edu Overview Homework 2-dimension parity IP fragmentation ARP ICMP Fragmentation and Reassembly
Introduction to Networking. Operating Systems In Depth XXVII 1 Copyright 2017 Thomas W. Doeppner. All rights reserved.
 Introduction to Networking Operating Systems In Depth XXVII 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Distributed File Systems Operating Systems In Depth XXVII 2 Copyright 2017 Thomas W.
Introduction to Networking Operating Systems In Depth XXVII 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Distributed File Systems Operating Systems In Depth XXVII 2 Copyright 2017 Thomas W.
Handbook. Step by step practical hacking training
 HACKING SCHOOL Handbook Step by step practical hacking training Title: Hacking School - Handbook First English Edition, 2010. ISBN: 978-83-923745-3-4 Copyright 2010 by CSH Press. All rights reserved. The
HACKING SCHOOL Handbook Step by step practical hacking training Title: Hacking School - Handbook First English Edition, 2010. ISBN: 978-83-923745-3-4 Copyright 2010 by CSH Press. All rights reserved. The
Covert channels in TCP/IP: attack and defence
 Covert channels in TCP/IP: attack and defence The creation and detection of TCP/IP steganography for covert channels and device fingerprinting Steven J. Murdoch and Stephen Lewis http://www.cl.cam.ac.uk/users/{sjm217,
Covert channels in TCP/IP: attack and defence The creation and detection of TCP/IP steganography for covert channels and device fingerprinting Steven J. Murdoch and Stephen Lewis http://www.cl.cam.ac.uk/users/{sjm217,
Linux. Sirindhorn International Institute of Technology Thammasat University. Linux. Firewalls with iptables. Concepts. Examples
 Linux Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 14 October 2013 Common/Reports/-introduction.tex, r715 1/14 Contents 2/14 Linux, netfilter and netfilter:
Linux Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 14 October 2013 Common/Reports/-introduction.tex, r715 1/14 Contents 2/14 Linux, netfilter and netfilter:
Firewalls and NAT. Firewalls. firewall isolates organization s internal net from larger Internet, allowing some packets to pass, blocking others.
 Firews and NAT 1 Firews By conventional definition, a firew is a partition made of fireproof material designed to prevent the spread of fire from one part of a building to another. firew isolates organization
Firews and NAT 1 Firews By conventional definition, a firew is a partition made of fireproof material designed to prevent the spread of fire from one part of a building to another. firew isolates organization
Basics of executing a penetration test
 Basics of executing a penetration test 25.04.2013, WrUT BAITSE guest lecture Bernhards Blumbergs, CERT.LV Outline Reconnaissance and footprinting Scanning and enumeration System exploitation Outline Reconnaisance
Basics of executing a penetration test 25.04.2013, WrUT BAITSE guest lecture Bernhards Blumbergs, CERT.LV Outline Reconnaissance and footprinting Scanning and enumeration System exploitation Outline Reconnaisance
Sirindhorn International Institute of Technology Thammasat University
 1 Name...ID....Section. Seat No.. Sirindhorn International Institute of Technology Thammasat University Midterm Examination: Semester 2/2007 Course Title : ITS 332 Information Technology II Lab (Networking)
1 Name...ID....Section. Seat No.. Sirindhorn International Institute of Technology Thammasat University Midterm Examination: Semester 2/2007 Course Title : ITS 332 Information Technology II Lab (Networking)
Using Neural Networks for remote OS Identification
 Using Neural Networks for remote OS Identification Javier Burroni - Carlos Sarraute Core Security Technologies PacSec/core05 conference OUTLINE 1. Introduction 2. DCE-RPC Endpoint mapper 3. OS Detection
Using Neural Networks for remote OS Identification Javier Burroni - Carlos Sarraute Core Security Technologies PacSec/core05 conference OUTLINE 1. Introduction 2. DCE-RPC Endpoint mapper 3. OS Detection
Setting the Table When users think about their workstations at home, they often forget about
 Configuring Netfilter/iptables with Shorewall Setting the Table When users think about their workstations at home, they often forget about security. But danger is out there, waiting to pounce on the unsuspecting.
Configuring Netfilter/iptables with Shorewall Setting the Table When users think about their workstations at home, they often forget about security. But danger is out there, waiting to pounce on the unsuspecting.
Suricata IDPS and Nftables: The Mixed Mode
 Suricata IDPS and Nftables: The Mixed Mode Giuseppe Longo Stamus Networks Jul 5, 2016 Giuseppe Longo (Stamus Networks) Suricata IDPS and Nftables: The Mixed Mode Jul 5, 2016 1 / 60 1 Netfilter Nftables
Suricata IDPS and Nftables: The Mixed Mode Giuseppe Longo Stamus Networks Jul 5, 2016 Giuseppe Longo (Stamus Networks) Suricata IDPS and Nftables: The Mixed Mode Jul 5, 2016 1 / 60 1 Netfilter Nftables
Network and Security: Introduction
 Network and Security: Introduction Seungwon Shin KAIST Some slides are from Dr. Srinivasan Seshan Some slides are from Dr. Nick Mckeown Network Overview Computer Network Definition A computer network or
Network and Security: Introduction Seungwon Shin KAIST Some slides are from Dr. Srinivasan Seshan Some slides are from Dr. Nick Mckeown Network Overview Computer Network Definition A computer network or
tcp-map through type echo Commands
 CHAPTER 31 31-1 tcp-map Chapter 31 tcp-map To define a set of TCP normalization actions, use the tcp-map command in global configuration mode. The TCP normalization feature lets you specify criteria that
CHAPTER 31 31-1 tcp-map Chapter 31 tcp-map To define a set of TCP normalization actions, use the tcp-map command in global configuration mode. The TCP normalization feature lets you specify criteria that
FLARE! Stapling together syslog-ng, elk, alerting, and incident tracking with metadata! Jeff Albert University of Victoria
 FLARE! Stapling together syslog-ng, elk, alerting, and incident tracking with metadata! Jeff Albert University of Victoria Hi, I m Jeff UNIX Systems Administrator at UVic Hi, I m Jeff UNIX Systems Administrator
FLARE! Stapling together syslog-ng, elk, alerting, and incident tracking with metadata! Jeff Albert University of Victoria Hi, I m Jeff UNIX Systems Administrator at UVic Hi, I m Jeff UNIX Systems Administrator
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
CSCI-GA Operating Systems. Networking. Hubertus Franke
 CSCI-GA.2250-001 Operating Systems Networking Hubertus Franke frankeh@cs.nyu.edu Source: Ganesh Sittampalam NYU TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute
CSCI-GA.2250-001 Operating Systems Networking Hubertus Franke frankeh@cs.nyu.edu Source: Ganesh Sittampalam NYU TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute
Internetworking models
 TEL3214 Computer Communication s Lecture 2 Internetworking models SSH (Secure Shell) SNMP (Simple Management Protocol) SMTP (Simple Mail Transfer Protocol) FTP (File Transfer Protocol) TFTP (Trivial File
TEL3214 Computer Communication s Lecture 2 Internetworking models SSH (Secure Shell) SNMP (Simple Management Protocol) SMTP (Simple Mail Transfer Protocol) FTP (File Transfer Protocol) TFTP (Trivial File
Introduction to Network. Topics
 Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
OpenWRT + cheap routers
 OpenWRT + cheap routers = Cheap, customized security sensors & training devices Ryan Wilson @SpotlightCybsec spotlightcybersecurity.com My Plan for Today Why Should You Care About OpenWRT? Quick History
OpenWRT + cheap routers = Cheap, customized security sensors & training devices Ryan Wilson @SpotlightCybsec spotlightcybersecurity.com My Plan for Today Why Should You Care About OpenWRT? Quick History
Internet Layers. Physical Layer. Application. Application. Transport. Transport. Network. Network. Network. Network. Link. Link. Link.
 Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
To get a feel for how to use the FIREWALL > Live page in NextGen Admin, watch the following video:
 Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live
Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live
CSE/EE 461 Lecture 13 Connections and Fragmentation. TCP Connection Management
 CSE/EE 461 Lecture 13 Connections and Fragmentation Tom Anderson tom@cs.washington.edu Peterson, Chapter 5.2 TCP Connection Management Setup assymetric 3-way handshake Transfer sliding window; data and
CSE/EE 461 Lecture 13 Connections and Fragmentation Tom Anderson tom@cs.washington.edu Peterson, Chapter 5.2 TCP Connection Management Setup assymetric 3-way handshake Transfer sliding window; data and
Transport Over IP. CSCI 690 Michael Hutt New York Institute of Technology
 Transport Over IP CSCI 690 Michael Hutt New York Institute of Technology Transport Over IP What is a transport protocol? Choosing to use a transport protocol Ports and Addresses Datagrams UDP What is a
Transport Over IP CSCI 690 Michael Hutt New York Institute of Technology Transport Over IP What is a transport protocol? Choosing to use a transport protocol Ports and Addresses Datagrams UDP What is a
Layered Networking and Port Scanning
 Layered Networking and Port Scanning David Malone 22nd June 2004 1 IP Header IP a way to phrase information so it gets from one computer to another. IPv4 Header: Version Head Len ToS Total Length 4 bit
Layered Networking and Port Scanning David Malone 22nd June 2004 1 IP Header IP a way to phrase information so it gets from one computer to another. IPv4 Header: Version Head Len ToS Total Length 4 bit
Network Intrusion Detection Systems. Beyond packet filtering
 Network Intrusion Detection Systems Beyond packet filtering Goal of NIDS Detect attacks as they happen: Real-time monitoring of networks Provide information about attacks that have succeeded: Forensic
Network Intrusion Detection Systems Beyond packet filtering Goal of NIDS Detect attacks as they happen: Real-time monitoring of networks Provide information about attacks that have succeeded: Forensic
What this talk is about?
 On the Current State of Remote Active OS Fingerprinting Tools Ofir Arkin CTO ofir.arkin@insightix.com Defcon 13 1 What this talk is about? This talk examines different aspects of remote active operating
On the Current State of Remote Active OS Fingerprinting Tools Ofir Arkin CTO ofir.arkin@insightix.com Defcon 13 1 What this talk is about? This talk examines different aspects of remote active operating
INF5290 Ethical Hacking. Lecture 3: Network reconnaissance, port scanning. Universitetet i Oslo Laszlo Erdödi
 INF5290 Ethical Hacking Lecture 3: Network reconnaissance, port scanning Universitetet i Oslo Laszlo Erdödi Lecture Overview Identifying hosts in a network Identifying services on a host What are the typical
INF5290 Ethical Hacking Lecture 3: Network reconnaissance, port scanning Universitetet i Oslo Laszlo Erdödi Lecture Overview Identifying hosts in a network Identifying services on a host What are the typical
Layer 4: UDP, TCP, and others. based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers
 Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Pre processors. Detection Engine
 Packet Decoder Pre processors Detection Engine Logging and Alerting System Output Modules Filesystem Syslog Database XML Firewall config You should know how the rules are constructed in order to fully
Packet Decoder Pre processors Detection Engine Logging and Alerting System Output Modules Filesystem Syslog Database XML Firewall config You should know how the rules are constructed in order to fully
Junos Security. Chapter 4: Security Policies Juniper Networks, Inc. All rights reserved. Worldwide Education Services
 Junos Security Chapter 4: Security Policies 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter,
Junos Security Chapter 4: Security Policies 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter,
CSCI-1680 Network Layer: IP & Forwarding Rodrigo Fonseca
 CSCI-1680 Network Layer: IP & Forwarding Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Today Network layer: Internet Protocol (v4) Forwarding Next 2 classes:
CSCI-1680 Network Layer: IP & Forwarding Rodrigo Fonseca Based partly on lecture notes by David Mazières, Phil Levis, John Jannotti Today Network layer: Internet Protocol (v4) Forwarding Next 2 classes:
Introduction to TCP/IP networking
 Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
Design and Performance of the OpenBSD Stateful Packet Filter (pf)
 Usenix 2002 p.1/22 Design and Performance of the OpenBSD Stateful Packet Filter (pf) Daniel Hartmeier dhartmei@openbsd.org Systor AG Usenix 2002 p.2/22 Introduction part of a firewall, working on IP packet
Usenix 2002 p.1/22 Design and Performance of the OpenBSD Stateful Packet Filter (pf) Daniel Hartmeier dhartmei@openbsd.org Systor AG Usenix 2002 p.2/22 Introduction part of a firewall, working on IP packet
NAT Router Performance Evaluation
 University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
IPv4. Christian Grothoff.
 IPv4 christian@grothoff.org http://grothoff.org/christian/ Sites need to be able to interact in one single, universal space. Tim Berners-Lee 1 The Network Layer Transports datagrams from sending to receiving
IPv4 christian@grothoff.org http://grothoff.org/christian/ Sites need to be able to interact in one single, universal space. Tim Berners-Lee 1 The Network Layer Transports datagrams from sending to receiving
Communication Networks ( ) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University. Allon Wagner
 Communication Networks (0368-3030) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University Allon Wagner Kurose & Ross, Chapter 4 (5 th ed.) Many slides adapted from: J. Kurose & K. Ross
Communication Networks (0368-3030) / Fall 2013 The Blavatnik School of Computer Science, Tel-Aviv University Allon Wagner Kurose & Ross, Chapter 4 (5 th ed.) Many slides adapted from: J. Kurose & K. Ross
The Internet Protocol. IP Addresses Address Resolution Protocol: IP datagram format and forwarding: IP fragmentation and reassembly
 The Internet Protocol IP Addresses Address Resolution Protocol: IP datagram format and forwarding: IP fragmentation and reassembly IP Addresses IP Addresses are 32 bit. Written in dotted decimal format:
The Internet Protocol IP Addresses Address Resolution Protocol: IP datagram format and forwarding: IP fragmentation and reassembly IP Addresses IP Addresses are 32 bit. Written in dotted decimal format:
Troubleshooting Communication in WebSphere MQ
 IBM Software Group Troubleshooting Communication in WebSphere MQ Rick Armstrong (rickied@us.ibm.com) Advisory Software Engineer 27 October 2010 WebSphere Support Technical Exchange Agenda TCP/IP networking
IBM Software Group Troubleshooting Communication in WebSphere MQ Rick Armstrong (rickied@us.ibm.com) Advisory Software Engineer 27 October 2010 WebSphere Support Technical Exchange Agenda TCP/IP networking
IPv6 NAT. Open Source Days 9th-10th March 2013 Copenhagen, Denmark. Patrick McHardy
 IPv6 NAT Open Source Days 9th-10th March 2013 Copenhagen, Denmark Patrick McHardy Netfilter and IPv6 NAT historically http://lists.netfilter.org/pipermail/netfilter/2005-march/059463.html
IPv6 NAT Open Source Days 9th-10th March 2013 Copenhagen, Denmark Patrick McHardy Netfilter and IPv6 NAT historically http://lists.netfilter.org/pipermail/netfilter/2005-march/059463.html
FIREWALLS. Firewall: isolates organization s internal net from larger Internet, allowing some packets to pass, blocking others
 FIREWALLS 1 FIREWALLS Firewall: isolates organization s internal net from larger Internet, allowing some packets to pass, blocking others FIREWALLS: WHY Prevent denial of service attacks: SYN ooding: attacker
FIREWALLS 1 FIREWALLS Firewall: isolates organization s internal net from larger Internet, allowing some packets to pass, blocking others FIREWALLS: WHY Prevent denial of service attacks: SYN ooding: attacker
FireHOL + FireQOS Reference
 FireHOL + FireQOS Reference FireHOL Team Release 2.0.0-pre7 Built 13 Apr 2014 FireHOL + FireQOS Reference Release 2.0.0-pre7 i Copyright 2012-2014 Phil Whineray Copyright 2004, 2013-2014
FireHOL + FireQOS Reference FireHOL Team Release 2.0.0-pre7 Built 13 Apr 2014 FireHOL + FireQOS Reference Release 2.0.0-pre7 i Copyright 2012-2014 Phil Whineray Copyright 2004, 2013-2014
> : S. timestamp > : (0) win <mss 1460,nop,wscale 0,nop,nop, 4 different options used
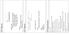 TCP Options Source Port Destination Port Sequence Number Acknowledgment Number HdrLen Reserved UA P RS F Window Size Checksum Urgent Pointer Options (optional...) Header Length Allows size of options to
TCP Options Source Port Destination Port Sequence Number Acknowledgment Number HdrLen Reserved UA P RS F Window Size Checksum Urgent Pointer Options (optional...) Header Length Allows size of options to
Internetworking/Internetteknik, Examination 2G1305 Date: August 18 th 2004 at 9:00 13:00 SOLUTIONS
 Internetworking/Internetteknik, Examination 2G1305 Date: August 18 th 2004 at 9:00 13:00 SOLUTIONS 1. General (5p) a) The so-called hourglass model (sometimes referred to as a wine-glass ) has been used
Internetworking/Internetteknik, Examination 2G1305 Date: August 18 th 2004 at 9:00 13:00 SOLUTIONS 1. General (5p) a) The so-called hourglass model (sometimes referred to as a wine-glass ) has been used
Firewalls. October 13, 2017
 Firewalls October 13, 2017 Administrative submittal instructions answer the lab assignment s questions in written report form, as a text, pdf, or Word document file (no obscure formats please) email to
Firewalls October 13, 2017 Administrative submittal instructions answer the lab assignment s questions in written report form, as a text, pdf, or Word document file (no obscure formats please) email to
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 20: Intrusion Prevention Department of Computer Science and Engineering University at Buffalo 1 Lecture Overview Firewalls purpose types locations Network perimeter
CSE 565 Computer Security Fall 2018 Lecture 20: Intrusion Prevention Department of Computer Science and Engineering University at Buffalo 1 Lecture Overview Firewalls purpose types locations Network perimeter
Toward an ebpf-based clone of iptables
 Toward an ebpf-based clone of iptables Matteo Bertrone, Sebastiano Miano, Jianwen Pi, Fulvio Risso, Massimo Tumolo Netdev 0x12, Montréal (Canada), July 12th, 2018 Objective Started in Nov 2017, with a
Toward an ebpf-based clone of iptables Matteo Bertrone, Sebastiano Miano, Jianwen Pi, Fulvio Risso, Massimo Tumolo Netdev 0x12, Montréal (Canada), July 12th, 2018 Objective Started in Nov 2017, with a
CIS-331 Exam 2 Fall 2014 Total of 105 Points. Version 1
 Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Lecture 18 Overview. Last Lecture. This Lecture. Next Lecture. Internet Protocol (1) Internet Protocol (2)
 Last Lecture Internet Protocol (1) This Lecture Internet Protocol (2) Lecture 18 Overview Source: chapters 19.1, 19.2, 22,1 22.2, 26.6 Next Lecture Transport Control Protocol (1) Source: chapters 24.1,
Last Lecture Internet Protocol (1) This Lecture Internet Protocol (2) Lecture 18 Overview Source: chapters 19.1, 19.2, 22,1 22.2, 26.6 Next Lecture Transport Control Protocol (1) Source: chapters 24.1,
Interconnecting Networks with TCP/IP
 Chapter 8 Interconnecting s with TCP/IP 1999, Cisco Systems, Inc. 8-1 Introduction to TCP/IP Internet TCP/IP Early protocol suite Universal 1999, Cisco Systems, Inc. www.cisco.com ICND 8-2 TCP/IP Protocol
Chapter 8 Interconnecting s with TCP/IP 1999, Cisco Systems, Inc. 8-1 Introduction to TCP/IP Internet TCP/IP Early protocol suite Universal 1999, Cisco Systems, Inc. www.cisco.com ICND 8-2 TCP/IP Protocol
