General Firewall Configuration
|
|
|
- Isaac Williamson
- 5 years ago
- Views:
Transcription
1 To adjust resources used by your firewall service you can change the sizing parameters in the General Firewall Configuration (CONFIGURATION > Configuration Tree > Box > Infrastructure Services) of the Barracuda NG Firewall. After changing general firewall configuration settings, perform a Firmware Restart (CONTROL > Box) for the changes to take effect. Default values vary depending on the NG Firewall model. Check the default value table below for more information. In this article: Firewall Sizing Maximum Number of Connections Max Session Slots Set the maximum number of session slots allowed. (min: 512, default: 65536, max: ) The amount of memory consumed by the firewall is updated when this value is changed and displayed in the Firewall Memory [MB] field. (with the default value the firewall service will consumer about 150MB RAM). If you set this parameter to the maximum allowed value, you will need to add vmalloc=896m to the the kernel boot parameters and execute a reboot. For more information, see How to Configure the Bootloader. Firewall Memory [MB] Displays the estimated memory requirement according to the current firewall configuration settings. If the value exceeds 200 MB an additional bootloader parameter may be required. On i686 based Barracuda NG Firewall systems with more than 768MB RAM requiring additional vmalloc space to satisfy the increased memory demand of non-default firewall settings we recommend to increase the vmalloc area in steps of 128MB, starting at the 384MB. For more information, see How to Configure the Bootloader. Reboot the box after setting the parameter and wait if the firewall service successfully starts after the system boot. Do not use vmalloc areas bigger than 640MB. The vmalloc area is shared among several kernel subsystems. Therefore the exact size of the allocated vmalloc area that is required to load the firewall cannot be predetermined. Setting the vmalloc parameter to enable increased acpf memory operation is discouraged on systems with 768MB of RAM or on "i386" architecture systems. Setting this parameter on those boxes could negatively affect the system performance and/or stability. The architecture of a installed Barracuda NG Firewall box can be determined with the following command: rpm -q kernel --qf %{ARCH}\\n. Max UDP (%) Defines how many percent of the the Max Session Slots are allowed to be UDP sessions. (min: 1; max. 100; default: 30). With eventing activated (parameter UDP Limit Exceeded set to yes), the event FW UDP Connection Limit Exceeded [4009] is generated when the limit is exceeded. Max Echo (%) Defines how many percent of the Max Session Slots are allowed to be ICMP sessions. 1 / 11
2 (min: 1, max: 100, default: 30). With eventing activated (parameter Echo Limit Exceeded set to yes), the event FW ICMP-ECHO Connection Limit Exceeded [4027] is generated when the limit is exceeded. Max Other (%) Defines how many percent of the Max Session Slots are allowed to be of an IP protocol type except TCP, UDP or ICMP. (min:1, max: 100, default: 10). With eventing activated (parameter Other Limit Exceeded set to yes), the event FW OTHER-IP Session Limit Exceeded [4029] is generated when the limit is exceeded. Global Limits 1 Max SIP Calls Set the maximum number of concurrent SIP calls that can be handled by the legacy SIP firewall plugin (min: 64, max: 16384, default: 512). Barracuda Networks recommends using the SIP proxy service instead of the SIP firewall plugin. Max SIP Transactions Set the maximum amount of SIP transactions that can be handled by the legacy SIP firewall plugin (min: 64, max: 16384, default: 512). Max SIP Media Define the maximum amount of SIP Media (RTP) connections allowed for the legacy SIP firewall plugin. The inactivity timeout for the media connections can be configured by setting the Balanced Timeout for the service object. Max DNS Entries Defines the maximum number of DNS queries that may be triggered by use of network objects containing hostnames. (default: 512) 75% of the queries are reserved for the forwarding firewall and 25% for the host firewall. Network objects used in both forwarding and host firewall rule sets will trigger two DNS queries and be counted twice. The firewall can only match on IP addresses. When the maximum amount of allowed DNS queries are exceeded, hostnames can not longer be resolved causing firewall rules using these networks objects to never match. Max Acceptors Maximum number of pending accepts for inbound rules (min: 2000; max: ; default: 8192). An acceptor is a dynamic implicit rule that is generated by plugins handling dynamic connection requests. The FTP protocol for example uses a data connection beside the control connection on TCP port 21 to perform the actual file transfer. By analyzing the FTP protocol, the firewall knows when such data connections occur and creates an acceptor to allow the corresponding data transfer session. Max Pending Inbounds Maximum number of pending TCP inbound requests (min: 2000; max: ; default: 16384). This parameter only comes into effect when the TCP accept policy is set to inbound for the firewall rule. Max BARPs Defines the maximum number of bridging ARPs allowed (default: 2048). A bridging ARP entry (BARP) stores the information that specifies which bridge interface corresponds to a certain MAC address. Additionally, associated IP addresses are stored along with the BARP entry. Modifying this value may be useful for large bridging setups. Max Plugins Maximum number of rules using plugins (min: 0, max: 65536, default: 8192). Dyn Service Names (RPC) Maximum number of dynamic service name entries (min:0, max: 65536, 2 / 11
3 default: 8192). Global Limits 2 Inbound Mode Threshold (%) Threshold of pending accepts, at which the firewall switches to the inbound TCP accept policy to guard against SYN flooding attacks (min:1. max: 100, default: 20). SYN Cookie High Watermark (%) Percentage (of maximum pending inbounds) of pending inbound accepts to switch to SYN cookie usage for enhanced SYN flooding protection (min: 0, max: 100, default: 20). SYN Cookie Low Watermark (%) Percentage (of maximum pending inbounds) of pending inbound accepts to go back to ordinary SYN handling (min: 0; max: 100; default: 15). Max Dynamic Rules Maximum number of dynamically activated rules (min: 1; max: 1024; default: 128). Max Multiple Redirect IPs Maximum number of IP addresses in rules with multiple redirect target IPs (min:1, max: 1024, default: 128). Max TCP Proxy Workers Total number of available sessions for the Generic TCP proxy mode depends on the number of workers. Each worker can handle up to 400 sessions. Workers are created on demand. Max SOCKS Workers Maximum number of available SOCKS worker when Generic TCP proxy mode is enabled. Source Based Session Limits Max Local-On Session/Src Maximum number of sessions per source IP address. Can not be set to more than Max Session Slots (min: 1; max. Max Session Slots; default: 8192). With eventing activated (parameter Session/Src Limit Exceeded set to yes), the event FW Global Connection per Source Limit Exceeded [4024] is generated when the limit is exceeded. Max Local-In UDP/Src Maximum number of UDP sessions per source IP address. (min: 1, default: 512). With eventing activated (parameter UDP/Src Limit Exceeded set to yes), the event FW UDP Connection per Source Limit Exceeded [4008] is generated when the limit is exceeded. Max Local-In Echo/Src Maximum number of ICMP Echo sessions per source IP (min:1, default: 512). With eventing activated (parameter Echo/Src Limit Exceeded set to yes), the event FW ICMP-ECHO Connection per Source Limit Exceeded [4026] is generated when the limit is exceeded. Max Local-In Other/Src Maximum number of sessions for all other IP protocols (not TCP, UDP, ICMP) per source IP address (min: 1, default 128). With eventing activated (parameter Other/Src Limit Exceeded set to yes), the event FW OTHER-IP Connection per Source Limit Exceeded [4028] is generated when the limit is exceeded. Max Pending Local Accepts/Src Maximum number of pending accepts per source IP address (min: 5, max: 1024, default: 64) History Cache The firewall history stores connection information for troubleshooting purposes. You can configure how many 3 / 11
4 and how long connections are stored in the settings. Use the Advanced View to configure these settings. Access Entries Determines the size of the visualization caches: min: 128; max: 8192; default: Block Entries min: 128; max: 8192; default: Drop Entries min: 128; max: 8192; default: Fail Entries min: 128; max: 8192; default: ARP Entries min: 128; max: 8192; default: DNS Resolve IPs Setting this parameter to yes (default: no) will resolve IPs to hostnames on the firewall history. This may cause excessive load on the DNS servers. Operational Ruleset Related Settings Rule Matching Policy Selects the way in which a rule lookup is performed. Kernel space linear lookup adequate for small rulesets. Kernel space tree lookup preferred option for large rulesets with hundreds of rules. As a rule of thumb for about 1000 session/s the Kernel space should be enabled for better firewall performance. Additionally if many firewall objects (> 200) are used, the Kernel space - tree option is recommended. Rule Change Behavior Specifies whether an existing connection is terminated ( Terminate-onchange ; default) or not ( Keep-on-change ) if the rule set changes and the session is no longer allowed by the new rule set. No Rule Update Time Range This option allows defining a time range during which firewall rules may not be updated. Use international time format, for example to disallow rule update from 14:00 through 22:00, insert Default TCP Policy Syn Flood Protection Defines the default behavior of the firewall with regard to the TCP three-wayhandshake. Outbound Passes on the SYN to the target address. Inbound The firewall completes the handshake and only then performs a handshake with the actual target. This helps to protect the target from SYN flood attacks. Disabling will cause an overhead in packet transmission but may speed up interactive protocols like SSH. Nagle Algorithm This parameter enables/disables the Nagle algorithm. This option is only available when using stream forwarding. Perform TCP Sequence Check This parameter enables/disables TCP sequence checks.you can select one of the following options: RST-Packets-Only All Packets None Raw TCP Mode Policy RAW TCP Idle Timeout Defines the idle timeout value in seconds for RAW TCP mode. RAW TCP Timeout Policy Defines the timeout policy that will be used for RAW TCP mode. Use-global-timeouts (default) Sets the timeout value that has been configured in the previous sections. Use-tcp-timeouts Uses the timeout values from standard TCP set in the matching rule. 4 / 11
5 Default Anti Spoofing Policy ARP Reverse Route Check Setting this parameter to Yes causes answers to ARP requests to be checked if Source IP and interface match. Reverse Interface Policy The options of this parameter specify whether requests and replies must use the same (outgoing) interface (same-interface; default or not (interface-may-change). This parameter specifies the global policy. You may change the policy per rule, though it is NOT recommended to do so. Port Scan Policy Port Scan Threshold When the number of blocked request exceed the threshold, a port scan is detected and a port scan event is triggered. (min value: 2 max: , default: 10) Port Scan Detection Interval Detection interval in seconds to check for not allowed activity (min: 0; max: ; default: 60). In combination with the parameter Port Scan Threshold it defines the condition when to report a port scan. Performance Related Policies Session Creation CPU Limit (%) (advanced) Reserves a specific amount of CPU resources for the Barracuda OS to prevent the Barracuda NG Firewall becoming unmanageable in case of a high amount of concurrent sessions being initiated. Barracuda Networks recommends to keep the Default value. Validate TCP Checksum (advanced) Enables an additional TCP packet consistency check. This will reduce performance. 5 / 11
6 Validate UDP Checksum (advanced) Enables an additional UDP packet consistency check. This will reduce performance. High Availability Related Policies Allow Active-Active Mode (advanced) Active-Active firewall operation mode is deactivated by default (no). It has to be enabled in preparation for operation of multiple active firewalls on one box with a load balancer connected upstream. Enable Session Sync (advanced) All currently established sessions will be synced to the HA partner to improve failover performance. Log Synced Sessions (advanced) This setting determines logging of access cache sessions, which have been synchronized between HA partners (default: Yes). Set to No to disable logging. Generically Forwarded Networks (advanced) Traffic between networks inserted into this field will be excluded from firewall monitoring and will be forwarded without source and destination differentiation, even if no forwarding firewall is installed. Local sessions are not reevaluated on rule change. This parameter only effects forwarding sessions. Workflow for enforcing changed local rules: manually terminate local sessions in the Firewall Live tab. Only make use of this feature, if you are operating your Barracuda NG Firewall system for routing and NOT for firewall purposes, as generic network forwarding might cause severe security issues. Operational IPS Per default TCP stream reassembly and HTML parsing is set to auto. The operating system enables or disables these features to best match your current configuration and performance. TCP Stream Reassembly for IPS Reassembles the TCP stream before scanning for vulnerabilities. HTML Parsing for IPS Toggles HTML obfuscation detection. If this setting is changed, you must reboot your Barracuda NG Firewall for the changes to take effect. IPS Scan Mode Select the scanning mode for IPS. You must reboot for the changes to take effect. Auto (default) The Barracuda NG Firewall automatically chooses the mode best suited for your Barracuda NG Firewall. Fast Scan Scan select packets to improve performance and throughput. Full Scan Scan all packets. Operational TAP TCP Proxy Settings TCP Proxy Version Select the TCP proxy version. Default: V2. You must restart the boxfw service for a change of the TCP proxy version to take effect. TCP Proxy V1 Settings 6 / 11
7 Max Worker Processes Set the maximum number of workers created when using the TCP proxy mode (stream forwarding). Each worker can handle up to 400 sessions. You must restart the boxfw service for changes to the number of workers to take effect. TCP Proxy V2 Settings Number of Threads Set the number of thready manually or enter 0 for the NG Firewall to handle creating and removing threads automatically. Default: 0 You must restart the boxfw service for changes to the number of threads to take effect. Log Level Choose how verbose the logs should be. Default: info Log Rate Limit Enter the maximum number of log entries per second for a single log message. Set to 0 to disable the log rate limit. Default: 5 Operational VPN VPN Rate Limit (Mbps) Limits how fast VPN traffic is encrypted and decrypted. If you experience excessive CPU load in an environment with many VPN tunnels, then change this value. The default value 0 does not impose any restriction. Restart the VPN service after changing this value. (CONTROL > Server). All active VPN connections will be terminated when restarting the VPN service. Enable Assembler Ciphers By default these assembler ciphers are enabled. Using the assembler implementation for AES/SHA/MD5 increases VPN performance significantly. Enable Intel AVX Extensions Enables or disables the usage of Intel s AVX extension (also valid on AMD processors). Enable VIA PadLock Enables or disables the usage of VIAs PadLock Security Engine. Enable Cavium Enable or disable Cavium crypto acceleration cards. Reboot for this setting to take effect. Globally clear DF bit (default: no) Clears the DF bit for each ipv4 packet routed through a VPN tunnel. For more information on MTU, see Routing. Application Detection Resource Failure Policy Out of Memory Policy An out of memory condition may disable protocol and application detection. As a consequence all deeper analysis will be disabled as well. Fail-Open Select to continue forwarding. Fail-Close Select to terminate the affected sessions. Url Categorization 7 / 11
8 Working Mode Enable/disable URL categorization. Cache Entries The maximum number of entries in the kernel cache. 0 is auto selection depending on RAM size. Categorization Timeout (sec) Set the maximum timeout to wait for categorization response. Cache Entry Expiration (sec) After the configured time the cached entries category will be updated. Application and Port Protocol Protection Enable Port Protocol Detection Enable this option to use Application Detection and/or Port Protocol Protection. Application Detection Default Policy (Legacy) Application Policy The default action upon application detection. This policy can be referenced as the default policy within the application control view of a firewall rule. Alternatively an explicit setting can be adopted on a per firewall rule basis for all policy actions except for traffic bandwidth limitation and QoS band assignment which needs to be set here. Application Bandwidth [kbit/s] Select an explicit maximum bandwidth that will be assigned to a traffic flow upon detection of an application as defined by the default policy or a firewall rule specific policy. Note that a bandwidth of 10kitb/s can be used to render many evasive peer-to-peer applications useless. Application QoS Band Select a QoS band that will be assigned to a traffic flow upon detection of an application as defined by the default policy or a firewall rule specific policy. Note that you can choose a band from the predefined basic QoS profile template but you will still need to activate the overall use profile on the various network interfaces within the traffic shaping config. Application Detection Default Selection (Legacy) Use Preselected Applications Select yes to include the list of preselected applications into the scope of application detection. You can add and exclude specific applications using the list selections below. Explicitly Add Applications Explicitly specify applications that will be added to the list of preselected. Explicitly Skip Applications Explicitly specify applications that will be skipped. Audit and Reporting Statistics Policy Generate Dashboard Information Enable/disable the firewall dashboard. Statistics for Host Firewall This option enables statistics for connections passing through the host firewall. Generate Protocol Statistics If enabled, protocol and P2P specific statistics are created and listed within the statistics viewer under.../server/box/proto-stat/... Use username if available If set to yes, usernames are used for statistic if available, otherwise the source IP address. Eventing Policy Generate Events Enable/Disable event generation. Event Data Use this section to selectively enable or disable event generation. Log Policy Appid logging Global application control log policy. This setting can be overridden on a per access rule basis. Default: Log-Blocked-Applications Log Level Decides whether log messages are accumulated to avoid too large log files. Cumulative Interval [s] Interval (in sec) for which cumulative logging is activated for either matching 8 / 11
9 or similar log entries. Minimum 1, maximum 60 sec. Cumulative Maximum Maximum of similar log entries to start cumulative logging. Minimum 1, maximum Generate Audit Log Enable the generation of structured firewall audit data that can be stored locally and/or forwarded. If enabled the 'Audit Log' tab of the firewall UI will get populated with data. Audit Log Data Use this section to selectively enable or disable audit log generation. IPFIX Streaming Enable IPFIX/Netflow Internet Protocol Flow Information Export (IPFIX, RFC 3917) is based on NetFlow Version 9. You can use this setting to stream the FW audit log via IPFIX. Note that using this also requires an adjustment of Audit Delivery within section Audit Log Data to Send-IPFIX. Settings Opens the IPFIX Exporter Setup window where you can configure IPFIX settings. Out of Session (OOS) Packet Policy Interfaces to Send TCP RST The firewall sends TCP RST packets to these network interfaces if it detects packets not belonging to an active session. This is useful to avoid timeouts on certain servers. IPV4 Networks to Send TCP RST The firewall sends TCP RST packets to these IPv4 networks if it detects packets not belonging to an active session. IPV6 Networks to Send TCP RST The firewall sends TCP RST packets to these IPv6 networks if it detects packets not belonging to an active session. Default Values for all Hardware Barracuda NG Firewall Models Barracuda NG Firewall models use different default values depending on the hardware capabilities of the system. Session Slots UDP (%) Echo [%] Other [%] SIP Calls F10 F18 F80 F100 F180 F200 F280 F300 F380 F400 F600 F800 F900 F1000 C400 C SIP Transactions SIP Media Pending Inbounds Plugins Dyn. Service Names (RPC) Inbound Mode Threshold [%] / 11
10 Dynamic Rules Multiple Redirect IPs Local- In Sessions/Src Local- In UDP/Src Local- In Echo/Src Local- In Other/Src Pending Local Accepts/Src Access Entries Block Entries Drop Entries Fail Entries Acceptors ARP Entries VPN Rate Limit (Mbps) Enable Protocol Detection Forwarding Session/Src Forwarding UDP/Src Forwarding Echo/Src Forwarding Other/Src Pending Forward Accept/Src Forwarding Settings / 11
11 Figures 11 / 11
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies
 Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies In order to establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies In order to establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies
To get a feel for how to use the FIREWALL > Live page in NextGen Admin, watch the following video:
 Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live
Under the Live tab, you can view and filter real-time information for the traffic that passes through the Barracuda NextGen Firewall F-Series. You can also manage the traffic sessions. To access the Live
IPv6 Firewall Support for Prevention of Distributed Denial of Service Attacks and Resource Management
 IPv6 Firewall Support for Prevention of Distributed Denial of Service Attacks and Resource Management IPv6 zone-based firewalls support the Protection of Distributed Denial of Service Attacks and the Firewall
IPv6 Firewall Support for Prevention of Distributed Denial of Service Attacks and Resource Management IPv6 zone-based firewalls support the Protection of Distributed Denial of Service Attacks and the Firewall
Hostname (DNS Resolvable) Network Objects
 Introduction The following article explains the configuration of hostname (DNS Resolvable) network objects. Note that the maximum amount of a single DNS resolvable hostname is limited to 24 IP addresses.
Introduction The following article explains the configuration of hostname (DNS Resolvable) network objects. Note that the maximum amount of a single DNS resolvable hostname is limited to 24 IP addresses.
How to Set Up VPN Certificates
 For the VPN service, you can use either self-signed certificates or certificates that are generated by an external CA. In this article: Before You Begin Before you set up VPN certificates, verify that
For the VPN service, you can use either self-signed certificates or certificates that are generated by an external CA. In this article: Before You Begin Before you set up VPN certificates, verify that
High Availability Synchronization PAN-OS 5.0.3
 High Availability Synchronization PAN-OS 5.0.3 Revision B 2013, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Device Configuration... 4 Network Configuration... 9 Objects Configuration...
High Availability Synchronization PAN-OS 5.0.3 Revision B 2013, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Device Configuration... 4 Network Configuration... 9 Objects Configuration...
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
AccessEnforcer Version 4.0 Features List
 AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
DPX8000 Series Deep Service Switching Gateway User Configuration Guide Firewall Service Board Module v1.0
 DPX8000 Series Deep Service Switching Gateway User Configuration Guide Firewall Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any
DPX8000 Series Deep Service Switching Gateway User Configuration Guide Firewall Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any
Avi Networks Technical Reference (16.3)
 Page 1 of 7 view online A TCP/UDP profile determines the type and settings of the network protocol that a subscribing virtual service will use. It sets a number of parameters, such as whether the virtual
Page 1 of 7 view online A TCP/UDP profile determines the type and settings of the network protocol that a subscribing virtual service will use. It sets a number of parameters, such as whether the virtual
Protection Against Distributed Denial of Service Attacks
 Protection Against Distributed Denial of Service Attacks The Protection Against Distributed Denial of Service Attacks feature provides protection from Denial of Service (DoS) attacks at the global level
Protection Against Distributed Denial of Service Attacks The Protection Against Distributed Denial of Service Attacks feature provides protection from Denial of Service (DoS) attacks at the global level
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Implementation Guide - VPN Network with Static Routing
 Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
Configuring Flood Protection
 Configuring Flood Protection NOTE: Control Plane flood protection is located on the Firewall Settings > Advanced Settings page. TIP: You must click Accept to activate any settings you select. The Firewall
Configuring Flood Protection NOTE: Control Plane flood protection is located on the Firewall Settings > Advanced Settings page. TIP: You must click Accept to activate any settings you select. The Firewall
BIG-IQ Centralized Management: ADC. Version 5.0
 BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
ICS 451: Today's plan
 ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
Request for Proposal (RFP) for Supply and Implementation of Firewall for Internet Access (RFP Ref )
 Appendix 1 1st Tier Firewall The Solution shall be rack-mountable into standard 19-inch (482.6-mm) EIA rack. The firewall shall minimally support the following technologies and features: (a) Stateful inspection;
Appendix 1 1st Tier Firewall The Solution shall be rack-mountable into standard 19-inch (482.6-mm) EIA rack. The firewall shall minimally support the following technologies and features: (a) Stateful inspection;
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls
 How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
NAT Command Reference
 Command Reference Command Hierarchies ISA Configuration Commands on page 639 NAT Service Configuration Commands on page 640 VPRN Commands on page 643 NAT Subscriber Management Commands on page 645 NAT
Command Reference Command Hierarchies ISA Configuration Commands on page 639 NAT Service Configuration Commands on page 640 VPRN Commands on page 643 NAT Subscriber Management Commands on page 645 NAT
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings 4. Select the check box for SPoE as default.
 Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Peplink Balance Multi-WAN Routers
 Peplink Balance Multi-WAN Routers Model 20/30/210/310/380/390/580/710/1350 User Manual Firmware 5.1 September 10 Copyright & Trademarks Specifications are subject to change without prior notice. Copyright
Peplink Balance Multi-WAN Routers Model 20/30/210/310/380/390/580/710/1350 User Manual Firmware 5.1 September 10 Copyright & Trademarks Specifications are subject to change without prior notice. Copyright
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
Configuring Advanced Firewall Settings
 Configuring Advanced Firewall Settings This section provides advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule
Configuring Advanced Firewall Settings This section provides advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision A McAfee Next Generation Firewall 5.7.8 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision A McAfee Next Generation Firewall 5.7.8 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Configuring Caching Services
 CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
Configuring NetFlow and NetFlow Data Export
 This module contains information about and instructions for configuring NetFlow to capture and export network traffic data. NetFlow capture and export are performed independently on each internetworking
This module contains information about and instructions for configuring NetFlow to capture and export network traffic data. NetFlow capture and export are performed independently on each internetworking
IPv6 Commands: ipv6 h to ipv6 mi
 IPv6 Commands: ipv6 h to ipv6 mi ipv6 hello-interval eigrp, page 3 ipv6 hold-time eigrp, page 5 ipv6 hop-limit, page 7 ipv6 host, page 8 ipv6 icmp error-interval, page 10 ipv6 inspect, page 12 ipv6 inspect
IPv6 Commands: ipv6 h to ipv6 mi ipv6 hello-interval eigrp, page 3 ipv6 hold-time eigrp, page 5 ipv6 hop-limit, page 7 ipv6 host, page 8 ipv6 icmp error-interval, page 10 ipv6 inspect, page 12 ipv6 inspect
Zone-Based Firewall Logging Export Using NetFlow
 Zone-Based Firewall Logging Export Using NetFlow Zone-based firewalls support the logging of messages to an external collector using NetFlow Version 9 export format. NetFlow Version 9 export format uses
Zone-Based Firewall Logging Export Using NetFlow Zone-based firewalls support the logging of messages to an external collector using NetFlow Version 9 export format. NetFlow Version 9 export format uses
Access Rules. Controlling Network Access
 This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: September 4, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: September 4, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Access Rules
 Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
Configuring Access Rules Rules > Access Rules About Access Rules Displaying Access Rules Specifying Maximum Zone-to-Zone Access Rules Changing Priority of a Rule Adding Access Rules Editing an Access Rule
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
BIG-IP Service Provider: Message Routing Administration. Version 13.0
 BIG-IP Service Provider: Message Routing Administration Version 13.0 Table of Contents Table of Contents Using the Diameter Configuration Wizard...5 Overview: Diameter Configuration Wizard... 5 About
BIG-IP Service Provider: Message Routing Administration Version 13.0 Table of Contents Table of Contents Using the Diameter Configuration Wizard...5 Overview: Diameter Configuration Wizard... 5 About
ipv6 hello-interval eigrp
 ipv6 hello-interval eigrp ipv6 hello-interval eigrp To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) for IPv6 routing process designated by an autonomous system
ipv6 hello-interval eigrp ipv6 hello-interval eigrp To configure the hello interval for the Enhanced Interior Gateway Routing Protocol (EIGRP) for IPv6 routing process designated by an autonomous system
NGF0401 Instructor Slides
 Advanced Site to Site VPN Barracuda NextGen Firewall F VPN Tunnel Routing Separate routing table Default behavior Uses source based routing Creates separate premain routing tables for every VPN tunnel
Advanced Site to Site VPN Barracuda NextGen Firewall F VPN Tunnel Routing Separate routing table Default behavior Uses source based routing Creates separate premain routing tables for every VPN tunnel
INF5290 Ethical Hacking. Lecture 3: Network reconnaissance, port scanning. Universitetet i Oslo Laszlo Erdödi
 INF5290 Ethical Hacking Lecture 3: Network reconnaissance, port scanning Universitetet i Oslo Laszlo Erdödi Lecture Overview Identifying hosts in a network Identifying services on a host What are the typical
INF5290 Ethical Hacking Lecture 3: Network reconnaissance, port scanning Universitetet i Oslo Laszlo Erdödi Lecture Overview Identifying hosts in a network Identifying services on a host What are the typical
Barracuda Firewall Release Notes 6.5.x
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Firepower Threat Defense Cluster for the Firepower 4100/9300
 Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
Intercepting Web Requests
 This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
SANGFOR AD Product Series
 SANGFOR Application Delivery (AD) Product Series provides customers with the global server load balance(gslb), inbound/outbound load balance, server load balance, SSL off-load and anti-ddos solutions for
SANGFOR Application Delivery (AD) Product Series provides customers with the global server load balance(gslb), inbound/outbound load balance, server load balance, SSL off-load and anti-ddos solutions for
Configuring IPv4. Finding Feature Information. This chapter contains the following sections:
 This chapter contains the following sections: Finding Feature Information, page 1 Information About IPv4, page 2 Virtualization Support for IPv4, page 6 Licensing Requirements for IPv4, page 6 Prerequisites
This chapter contains the following sections: Finding Feature Information, page 1 Information About IPv4, page 2 Virtualization Support for IPv4, page 6 Licensing Requirements for IPv4, page 6 Prerequisites
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
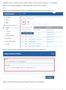 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Modular Policy Framework. Class Maps SECTION 4. Advanced Configuration
 [ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
[ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
HPE Security ArcSight Connectors
 HPE Security ArcSight Connectors SmartConnector for IP Flow (NetFlow/J-Flow) Configuration Guide October 17, 2017 SmartConnector for IP Flow (NetFlow/J-Flow) October 17, 2017 Copyright 2004 2017 Hewlett
HPE Security ArcSight Connectors SmartConnector for IP Flow (NetFlow/J-Flow) Configuration Guide October 17, 2017 SmartConnector for IP Flow (NetFlow/J-Flow) October 17, 2017 Copyright 2004 2017 Hewlett
Configuring Management Access
 37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
Internet Layers. Physical Layer. Application. Application. Transport. Transport. Network. Network. Network. Network. Link. Link. Link.
 Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Network Address Translation (NAT)
 The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
Configuring Health Monitoring
 CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
Configuring DDoS Prevention
 CHAPTER 10 This chapter describes how to configure a GSS to prevent Distributed Denial of Service (DDoS) attacks. It contains the following major sections: Logging in to the CLI and Enabling Privileged
CHAPTER 10 This chapter describes how to configure a GSS to prevent Distributed Denial of Service (DDoS) attacks. It contains the following major sections: Logging in to the CLI and Enabling Privileged
Load Balancing Technology White Paper
 Load Balancing Technology White Paper Keywords: Server, gateway, link, load balancing, SLB, LLB Abstract: This document describes the background, implementation, and operating mechanism of the load balancing
Load Balancing Technology White Paper Keywords: Server, gateway, link, load balancing, SLB, LLB Abstract: This document describes the background, implementation, and operating mechanism of the load balancing
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2630 Software version: F1000-E/Firewall module: R3166 F5000-A5: R3206 Document version: 6PW101-20120706 Legal and notice information
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2630 Software version: F1000-E/Firewall module: R3166 F5000-A5: R3206 Document version: 6PW101-20120706 Legal and notice information
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-618 Title : Deploying Cisco ASA Firewall Solutions (FIREWALL v2.0) Vendors : Cisco
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-618 Title : Deploying Cisco ASA Firewall Solutions (FIREWALL v2.0) Vendors : Cisco
Managing Latency in IPS Networks
 Revision C McAfee Network Security Platform (Managing Latency in IPS Networks) Managing Latency in IPS Networks McAfee Network Security Platform provides you with a set of pre-defined recommended settings
Revision C McAfee Network Security Platform (Managing Latency in IPS Networks) Managing Latency in IPS Networks McAfee Network Security Platform provides you with a set of pre-defined recommended settings
Connection Settings. What Are Connection Settings? management connections that go to the ASA.
 This chapter describes how to configure connection settings for connections that go through the ASA, or for management connections that go to the ASA. What Are?, page 1 Configure, page 2 Monitoring Connections,
This chapter describes how to configure connection settings for connections that go through the ASA, or for management connections that go to the ASA. What Are?, page 1 Configure, page 2 Monitoring Connections,
F5 DDoS Hybrid Defender : Setup. Version
 F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1
 What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
What s New in Fireware v12.3 WatchGuard Training
 What s New in Fireware v12.3 2 What s New in Fireware v12.3 Updates to Networking functionality: SD-WAN actions SD-WAN reporting enhancements NetFlow support Link monitor enhancements Centralized FireCluster
What s New in Fireware v12.3 2 What s New in Fireware v12.3 Updates to Networking functionality: SD-WAN actions SD-WAN reporting enhancements NetFlow support Link monitor enhancements Centralized FireCluster
H3C SecPath Series High-End Firewalls
 H3C SecPath Series High-End Firewalls Attack Protection Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: SECPATHF1000SAI&F1000AEI&F1000ESI-CMW520-R3721 SECPATH5000FA-CMW520-F3210
H3C SecPath Series High-End Firewalls Attack Protection Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: SECPATHF1000SAI&F1000AEI&F1000ESI-CMW520-R3721 SECPATH5000FA-CMW520-F3210
INBOUND AND OUTBOUND NAT
 INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
Firepower Threat Defense Site-to-site VPNs
 About, on page 1 Managing, on page 3 Configuring, on page 3 Monitoring Firepower Threat Defense VPNs, on page 11 About Firepower Threat Defense site-to-site VPN supports the following features: Both IPsec
About, on page 1 Managing, on page 3 Configuring, on page 3 Monitoring Firepower Threat Defense VPNs, on page 11 About Firepower Threat Defense site-to-site VPN supports the following features: Both IPsec
Fireware-Essentials. Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.
 Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Fireware-Essentials Number: Fireware Essentials Passing Score: 800 Time Limit: 120 min File Version: 7.0 http://www.gratisexam.com/ Fireware Essentials Fireware Essentials Exam Exam A QUESTION 1 Which
Junos Security. Chapter 4: Security Policies Juniper Networks, Inc. All rights reserved. Worldwide Education Services
 Junos Security Chapter 4: Security Policies 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter,
Junos Security Chapter 4: Security Policies 2012 Juniper Networks, Inc. All rights reserved. www.juniper.net Worldwide Education Services Chapter Objectives After successfully completing this chapter,
Configuration Guide TL-ER5120/TL-ER6020/TL-ER REV3.0.0
 Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
Test Accredited Configuration Engineer (ACE) Exam PAN OS 6.0 Version
 Test Accredited Configuration Engineer (ACE) Exam PAN OS 6.0 Version ACE Exam Question 1 of 50. Which of the following statements is NOT True regarding a Decryption Mirror interface? Supports SSL outbound
Test Accredited Configuration Engineer (ACE) Exam PAN OS 6.0 Version ACE Exam Question 1 of 50. Which of the following statements is NOT True regarding a Decryption Mirror interface? Supports SSL outbound
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision A McAfee Next Generation Firewall 5.7.6 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision A McAfee Next Generation Firewall 5.7.6 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
F5 BIG-IQ Centralized Management: Local Traffic & Network. Version 5.2
 F5 BIG-IQ Centralized Management: Local Traffic & Network Version 5.2 Table of Contents Table of Contents BIG-IQ Local Traffic & Network: Overview... 5 What is Local Traffic & Network?... 5 Understanding
F5 BIG-IQ Centralized Management: Local Traffic & Network Version 5.2 Table of Contents Table of Contents BIG-IQ Local Traffic & Network: Overview... 5 What is Local Traffic & Network?... 5 Understanding
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster
 AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
Best Practice - VPN Performance Testing
 Follow these instructions to create a standardized VPN performance testing environment. Using standardized settings is required for support to be able to compare performance tests with our in-house testing
Follow these instructions to create a standardized VPN performance testing environment. Using standardized settings is required for support to be able to compare performance tests with our in-house testing
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision A McAfee Next Generation Firewall 5.7.1 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision A McAfee Next Generation Firewall 5.7.1 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Context Based Access Control (CBAC): Introduction and Configuration
 Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Information About NAT
 CHAPTER 27 This chapter provides an overview of how Network Address Translation (NAT) works on the adaptive security appliance. This chapter includes the following sections: Why Use NAT?, page 27-1 NAT
CHAPTER 27 This chapter provides an overview of how Network Address Translation (NAT) works on the adaptive security appliance. This chapter includes the following sections: Why Use NAT?, page 27-1 NAT
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
ASA Access Control. Section 3
 [ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
[ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
HTG XROADS NETWORKS. Network Appliance How To Guide: EdgeBPR (Shaping) How To Guide
 HTG X XROADS NETWORKS Network Appliance How To Guide: EdgeBPR (Shaping) How To Guide V 3. 8 E D G E N E T W O R K A P P L I A N C E How To Guide EdgeBPR XRoads Networks 17165 Von Karman Suite 112 888-9-XROADS
HTG X XROADS NETWORKS Network Appliance How To Guide: EdgeBPR (Shaping) How To Guide V 3. 8 E D G E N E T W O R K A P P L I A N C E How To Guide EdgeBPR XRoads Networks 17165 Von Karman Suite 112 888-9-XROADS
BIG-IP CGNAT: Implementations. Version 13.0
 BIG-IP CGNAT: Implementations Version 13.0 Table of Contents Table of Contents Deploying a Carrier Grade NAT... 9 Overview: The carrier-grade NAT (CGNAT) module... 9 About ALG Profiles...10 About CGNAT
BIG-IP CGNAT: Implementations Version 13.0 Table of Contents Table of Contents Deploying a Carrier Grade NAT... 9 Overview: The carrier-grade NAT (CGNAT) module... 9 About ALG Profiles...10 About CGNAT
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision B McAfee Next Generation Firewall 5.7.4 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision B McAfee Next Generation Firewall 5.7.4 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 18: Network Attacks Department of Computer Science and Engineering University at Buffalo 1 Lecture Overview Network attacks denial-of-service (DoS) attacks SYN
CSE 565 Computer Security Fall 2018 Lecture 18: Network Attacks Department of Computer Science and Engineering University at Buffalo 1 Lecture Overview Network attacks denial-of-service (DoS) attacks SYN
Applied IT Security. System Security. Dr. Stephan Spitz 6 Firewalls & IDS. Applied IT Security, Dr.
 Applied IT Security System Security Dr. Stephan Spitz Stephan.Spitz@de.gi-de.com Overview & Basics System Security Network Protocols and the Internet Operating Systems and Applications Operating System
Applied IT Security System Security Dr. Stephan Spitz Stephan.Spitz@de.gi-de.com Overview & Basics System Security Network Protocols and the Internet Operating Systems and Applications Operating System
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision B McAfee Next Generation Firewall 5.7.3 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision B McAfee Next Generation Firewall 5.7.3 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Snapt Accelerator Manual
 Snapt Accelerator Manual Version 2.0 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 3 Accelerator Dashboard... 4 Standard Configuration Default Settings... 5 Standard Configuration
Snapt Accelerator Manual Version 2.0 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 3 Accelerator Dashboard... 4 Standard Configuration Default Settings... 5 Standard Configuration
How to Configure an ISP with DHCP
 This article provides information on how to configure an ISP with DHCP and specify the settings for the DHCP client. You can configure up to six DHCP links on a Barracuda NG Firewall. In this article:
This article provides information on how to configure an ISP with DHCP and specify the settings for the DHCP client. You can configure up to six DHCP links on a Barracuda NG Firewall. In this article:
Configuring Firewall Access Rules
 Firewall Configuring Firewall Access Rules Configuring Application Control Rules Configuring Advanced App Control Settings Configuring Match Objects Configuring Action Objects Configuring Address Objects
Firewall Configuring Firewall Access Rules Configuring Application Control Rules Configuring Advanced App Control Settings Configuring Match Objects Configuring Action Objects Configuring Address Objects
Security Manager Policy Table Lookup from a MARS Event
 CHAPTER 17 Security Manager Policy Table Lookup from a MARS Event This chapter describes how to configure and use Security Manager and MARS so as to enable bi-directional lookup between events recieved
CHAPTER 17 Security Manager Policy Table Lookup from a MARS Event This chapter describes how to configure and use Security Manager and MARS so as to enable bi-directional lookup between events recieved
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Introduction to Network. Topics
 Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN.
 This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN. Requirements: When configuring NSRP-Lite for the NS-50, confirm the following necessary requirements: The NS-25 or
This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN. Requirements: When configuring NSRP-Lite for the NS-50, confirm the following necessary requirements: The NS-25 or
Transport Over IP. CSCI 690 Michael Hutt New York Institute of Technology
 Transport Over IP CSCI 690 Michael Hutt New York Institute of Technology Transport Over IP What is a transport protocol? Choosing to use a transport protocol Ports and Addresses Datagrams UDP What is a
Transport Over IP CSCI 690 Michael Hutt New York Institute of Technology Transport Over IP What is a transport protocol? Choosing to use a transport protocol Ports and Addresses Datagrams UDP What is a
SANGFOR AD Product Series
 SANGFOR Application Delivery (AD) Product Series provides customers with the global server load balance(gslb), inbound/outbound load balance, server load balance, SSL off-load and anti-ddos solutions for
SANGFOR Application Delivery (AD) Product Series provides customers with the global server load balance(gslb), inbound/outbound load balance, server load balance, SSL off-load and anti-ddos solutions for
match protocol http cookie (cookie map submode)
 Chapter 2 22 match protocol http cookie (cookie map submode) match protocol http cookie (cookie map submode) To add cookies to a cookie map, use the match protocol http cookie command in SLB cookie map
Chapter 2 22 match protocol http cookie (cookie map submode) match protocol http cookie (cookie map submode) To add cookies to a cookie map, use the match protocol http cookie command in SLB cookie map
DPX8000 Series Deep Service Switching Gateway User Configuration Guide Probe Service Board Module v1.0
 DPX8000 Series Deep Service Switching Gateway User Configuration Guide Probe Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any help,
DPX8000 Series Deep Service Switching Gateway User Configuration Guide Probe Service Board Module v1.0 i Hangzhou DPtech Technologies Co., Ltd. provides full- range technical support. If you need any help,
