1 /18 2 /16 3 /18 4 /26 5 /22
|
|
|
- Monica Shields
- 5 years ago
- Views:
Transcription
1 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22 Name Solutions Athena login name Score Recitation section WF 10, (Olivia) WF 12, (Maleen) WF 2, (Kathy) WF 10, (Chanwoo) WF 12, (Anurag) WF 2, (Song) WF 11, (Olivia) WF 1, (Maleen) WF 3, (Kathy) WF 11, (Chanwoo) WF 1, (Anurag) WF 3, (Song) Please enter your name, Athena login name, and recitation section above. Enter your answers in the spaces provided below. Show your work for partial credit. You can use the extra white space and the backs of the pages for scratch work. This quiz has a separate appendix with the RISC-V ISA reference tables. Problem 1. Assembly (18 points) (A) (6 points) For the RISC-V instruction sequence below, provide the hex values of the specified registers after the sequence has been executed. Assume the program is located beginning at address 0x0 in memory and that all registers are initialized to 0.. = 0x0 lui x4, 0x2 jal x5, L1 ori x4, x4, 0x3 L1: addi x0, x4, 0x16 addi x6, x0, 0x200 Value of x4 (in hex) 0x2000 Value of x5 (in hex) 0x8 Value of x6 (in hex) 0x Fall of 12 - Quiz #2
2 (B) (4 points) You are given the following C code along with a partial translation into RISC-V assembly that is missing a single instruction (the first one). Please complete the assembly implementation by specifying the single missing instruction. Assume that x and y are signed 32-bit integers (defined as int x; int y;). if (x > y) { x = 5; } else { y = 10; } // Partial assembly implementation // Registers x: x1, y: x2 bge x2, x1, else li x1, 5 j endif else: li x2, 10 endif: (fill in the missing instruction) (C) (8 points) Consider the following code sequence. This code is located beginning at address 0x0 in memory. Note that this code may modify itself.. = 0x0 bge x1, x0, L1 lw x2, 0xC(x0) sw x2, 0x10(x0) L1: addi x1, x1, 2 addi x1, x1, -1 (i) What is the address of label L1? 0xC (ii) What are the final values of the register x1, when this code is run with the following initial values for x1? If initial value of x1 = 5 Final value of x1 = 6 bge taken, final x1 = 5 (initial value) + 2 (addi) 1 (2 nd addi) If initial value of x1 = -5 Final value of x1 = -1 bge not taken, lw and sw overwrite 2 nd addi at 0x10 with addi at 0xC final x1 = -5 (initial value) + 2 (addi) + 2 (addi written by sw) Fall of 12 - Quiz #2
3 Problem 2. RISC-V Assembly and Calling Convention (16 points) (A) (6 points) The factorial C procedure given below implements the factorial function (e.g., factorial(5) = 5! = 5 x 4 x 3 x 2 x 1 = 120). This implementation uses a loop to compute the factorial. Since our RISC-V processor does not have a multiply instruction, the code uses a multiply procedure, mult, which multiplies two signed integers. Ben Bitdiddle decides to implement this procedure in RISC-V assembly. But his assembly code, shown below, is not behaving as expected. Please fix the bugs so that his code works correctly and obeys the RISC-V calling convention. The implementation of the mult procedure is not provided to you, but it does obey the calling convention. int factorial(int n) { int prod = 1; for (int i = 1; i <= n; i++) { prod = mult(prod, i); } return prod; } factorial: mv s0, a0 li s1, 1 // set up prod li s2, 1 // set up i loop: beq s0, s2, done mv a0, s1 mv a1, s2 jal ra, mult mv s1, a0 addi s2, s2, 1 j loop done: mv a0, s1 mult: Provide the correct assembly code here. Your implementation should obey the RISC-V calling convention. Note that there may be multiple errors in the code. Assume n 1. factorial : addi sp, sp, -16 sw s0, 0(sp) sw s1, 4(sp) sw s2, 8(sp) sw ra, 12(sp) mv s0, a0 li s1, 1 // set up prod li s2, 1 // set up i loop : blt s0, s2, done mv a0, s1 mv a1, s2 jal ra, mult mv s1, a0 addi s2, s2, 1 j loop done : mv a0, s1 lw s0, 0(sp) lw s1, 4(sp) lw s2, 8(sp) lw ra, 12(sp) addi sp, sp, Fall of 12 - Quiz #2
4 (B) (10 points) The sumsquares C procedure given below computes the sum-of-squares function. Specifically, the sumsquares procedure takes a single argument n and computes n i=1 i 2 (e.g., sumsquares(5) = = 55). This implementation is recursive. Again, since our RISC-V processor does not have a multiply instruction, the code uses a multiply procedure, mult, which multiplies two signed integers. Ben Bitdiddle decides to implement this procedure in RISC-V assembly. But his assembly code, shown below, is not behaving as expected. Please answer the question below and fix the bugs so that his code works correctly and obeys the RISC-V calling convention. The implementation of the mult procedure is not provided to you, but it does obey the calling convention. int sumsquares(int n) { if (n == 0) return 0; return sumsquares(n-1) + mult(n,n); } sumsquares: bltz a0, done addi sp, sp, -4 sw a0, 0(sp) addi a0, a0, -1 jal ra, sumsquares mv s0, a0 mv a1, a0 j mult add a0, a0, s0 lw a0, 0(sp) addi sp, sp, 4 done: mult: Ben s buggy assembly code is given below. Provide the full instruction that the PC points to after executing jr ra (i.e., ret) for the first time in the given buggy code. Assume n 1. mv s0, a0 Provide the correct assembly code here. Your implementation should obey the RISC-V calling convention. Note that there may be multiple errors in the code. sumsquares: beqz a0, done addi sp, sp, -12 sw a0, 0(sp) sw s0, 4(sp) sw ra, 8(sp) addi a0, a0, -1 jal ra, sumsquares mv s0, a0 lw a0, 0(sp) mv a1, a0 jal ra, mult add a0, a0, s0 lw s0, 4(sp) lw ra, 8(sp) addi sp, sp, 12 done: Fall of 12 - Quiz #2
5 Problem 3. Procedures and Stacks (18 points) Consider the C procedure below and its translation to RISC-V assembly code, shown on the right. int f(int a) { if (a == 1) return 0; if (a & 1 == 0) { // a is even return 1 + f(a / 2); } else { // a is odd return 1 + f(a * 3 + 1); } } (A) (3 points) Give the HEX encoding of the slli a1, a0, 1 instruction shamt rs1 001 rd x Hex encoding of slli a1, a0, 1: 0x f: li a1, 1 beq a0, a1, ONE andi a1, a0, 1 beqz a1, EVEN slli a1, a0, 1 add a0, a0, a1 addi a0, a0, 1 addi sp, sp, -4 sw ra, 0(sp) jal ra, f addi a0, a0, 1 lw ra, 0(sp) addi sp, sp, 4 EVEN: addi sp, sp, -4 sw ra, 0(sp) srli a0, a0, 1 jal ra, f addi a0, a0, 1 lw ra, 0(sp) addi sp, sp, 4 ONE: mv a0, zero (B) (2 points) How much total stack memory does the program use to calculate f(3)? f(3) f(10) f(5) f(16) f(8) f(4) f(2) f(1) 1 word each 0 words Number of words pushed onto the stack for f(3)? Fall of 12 - Quiz #2
6 The program s initial call to function f occurs outside of the function Memory Contents definition via the instruction jal ra, f. The program is interrupted Address at an execution (not necessarily the first) of function f, just prior to the execution of li a1, 1 at label f. The diagram on the right shows the 0xFB0 0x80 contents of a region of memory. All addresses and data values are shown 0XFB4 0x80 in hex. The current value in the SP register is 0xFBC and points to the location shown in the diagram. 0XFB8 0x60 SP 0XFBC 0x80 saved ra (C) (4 points) Is the argument to the initial call to f even or odd? Circle your choice: First recursive call has ra = 0x60, following ones have ra = 0x80, both jal instructions are 16 = 0x20 bytes away first jal (for odd argument) is at address 0x5C, second jal (for even argument) is at 0x7C, and first recursive call takes the jal for odd (ra = 0x60). Even Odd Can t tell 0xFC0 0x80 saved ra 0xFC4 0x60 saved ra 0xFC8 0x100 saved ra of initial call 0xFCC 0x500 0xFD0 0xFD4 0xFD8 0xFDC 0x400 0x0 0x0 0x0 (D) (3 points) What value was in SP just prior to the initial call to f? Initial contents of SP: 0x FCC (E) (3 points) What is the address of the jal ra, f instruction that made the initial call to f? Saved ra of initial call is 0x100 jal ra, f is at 0x100 4 = 0xFC Address of instruction that made initial call to f: 0x FC (F) (3 points) What is the hex address of the instruction at label EVEN? Address of instruction at label EVEN: 0x Fall of 12 - Quiz #2
7 Problem 4. Processor Implementation (26 points) The multicycle RISC-V processor built in Lab 5, which we call Processor A, uses 1) A shared instruction/data memory with split request (req) and response (resp) methods. 2) A register file with two read ports (rd1, rd2 methods) and a write port (wr method). Processor A uses three states (Fetch, Execute, LoadWait) to process instructions. It starts at Fetch and follows the state-transition diagram given below: Figure 1: State-Transition Diagram of Processor A Instead of using a register file with two read ports, we want to build another multicycle RISC-V processor, Processor B, that uses a register file with only one read port (rd method). Since it is not possible to read two registers in the same cycle as in Execute of Processor A, we split Execute into two states, namely Execute1 and Execute2, where only one register is read in each of the new rules. The state-transition diagram of Processor B is implemented as follows: Figure 2: State-Transition Diagram of Processor B (A) (6 points) Assume that the memory responds two cycles after a request is made (e.g., if a load request is made on cycle 1, the memory replies in cycle 3). How many cycles does each instruction below take in Processor A and Processor B? Processor A Processor B addi a4, a3, 0x134 3 cycles 4 cycles lw a3, 4(a2) 5 cycles 6_(or 5*)_ cycles bne a2, a3, 0x120 3 cycles 4 cycles (*) In processor B, a load can be issued at Execute1 instead of Execute2. This will take 5 cycles. After examining Processor B, we noticed that we can optimize it by having certain types of instructions (itype) spend fewer cycles. Processor C implements this optimization by completing the execution of these types of instructions in Execute1, and adding an extra state transition from Execute1 to Fetch. The state transition diagram is given in the next page and the suggested new transition is marked in red where iset is a subset of itype values: { OP, OPIMM, BRANCH, LUI, JAL, JALR, LOAD, STORE } Fall of 12 - Quiz #2
8 Figure 3: State-Transition Diagram of Processor C (B) (4 points) For each itype, place a check mark if the itype can be in iset to correctly implement Processor C (i.e., if this instruction can be executed completely in two states, Fetch and Execute1). itype OP OPIMM BRANCH LUI JAL JALR LOAD STORE In iset? All instructions with 0 or 1 source registers, except LOAD (which needs to go to LoadWait) (C) (6 points) You can further optimize Processor C for LOAD instructions so that they take fewer cycles in the processor. Finish the state-transition diagram below only for LOAD instructions to implement such optimization by drawing state-transition arrows. Let s implement Processor B using Bluespec. The almost complete code is given below. This code is similar to the code in Lab 5. The main differences are highlighted in red. Your job is to fill in the doexecute1 rule. Consider the following: 1) The new register file is implemented as a module named mkrfile1r1w whose x0 register is always zero and its interface RFile1R1W is given along with the code. 2) Types related to decode and execute functions are given along with the code. 3) You are only allowed to fill in the body of doexecute1. Other lines should remain the same. For example, you cannot add extra registers. (D) (10 points) Complete the doexecute1 rule for Processor B. typedef Bit#(32) Word; typedef Bit#(5) RIndx; interface RFile1R1W; method Word rd(rindx rindx); // Only 1 read port method Action wr(rindx rindx, Word data); endinterface typedef enum {Fetch, Execute1, Execute2, LoadWait} State deriving (Bits, Eq); //code continues on the next page Fall of 12 - Quiz #2
9 // types related to decode and execute functions typedef struct { IType itype; AluFunc alufunc; BrFunc brfunc; Word imm; Maybe#(RIndx) dst; RIndx src1; RIndx src2; } DecodedInst; typedef struct { IType itype; Maybe#(RIndx) dst; Word data; Word addr; Word nextpc; } ExecInst; function DecodedInst decode(word inst); function ExecInst execute(decodedinst dinst, Word rval1, Word rval2, Word pc); // Processor B implementation module mkprocmulticycleb(empty); Reg#(Word) pc <- mkreg(0); RFile1R1W rf <- mkrfile1r1w; // Register File with 1 read port Memory mem <- mkmemory; Reg#(State) state <- mkreg(fetch); Reg#(Word) rval1_e1 <- mkregu; Reg#(DecodedInst) dinst_e1 <- mkregu; Reg#(RIndx) dstload <- mkreg(0); rule dofetch if (state == Fetch); mem.req(memreq{op: Ld, addr: pc, data:?}); state <= Execute1; endrule rule doexecute1 if (state == Execute1); // Write your code in this box let inst <- mem.resp(); let dinst = decode(inst); rval1_e1 <= rf.rd(dinst.src1); dinst_e1 <= dinst; state <= Execute2; endrule //code continues on the next page Fall of 12 - Quiz #2
10 rule doexecute2 if (state == Execute2); let rval2 = rf.rd(dinst_e1.src2); let einst = execute(dinst_e1, rval1_e1, rval2, pc); if(einst.itype == Unsupported) begin $display("[halt] Reached unsupported instruction (0x%x)", inst); $finish; end else if (einst.itype == LOAD) begin mem.req(memreq{op: Ld, addr: einst.addr, data:?}); dstload <= frommaybe(?, einst.dst); state <= LoadWait; end else if (einst.itype == STORE) begin mem.req(memreq{op: St, addr: einst.addr, data: einst.data}); pc <= pc + 4; state <= Fetch; end else begin if(isvalid(einst.dst)) begin rf.wr(frommaybe(?, einst.dst), einst.data); end pc <= einst.nextpc; state <= Fetch; end endrule rule doloadwait if (state == LoadWait); Word data <- mem.resp(); rf.wr(dstload, data); pc <= pc + 4; state <= Fetch; endrule endmodule Fall of 12 - Quiz #2
11 Problem 5. Caches (22 points) Consider the two-way set associative cache shown below. It has 8 sets and a block size of 4 (4 words per line). The column labeled x corresponds to the x th word of the block. The V bit specifies whether the line is valid, and the D bit specifies whether the line is dirty. Assume that the data and addresses are 32 bits. V D Tag set x12 0x0A 0x1A 0x2A 0x3A set x12 0x4B 0x5B 0x6B 0x7B set x12 0x3C 0x2C 0x1C 0x0C set x12 0x7D 0x6D 0x5D 0x4D set x67 0x33 0x23 0x13 0x03 set x67 0x44 0x34 0x24 0x14 set x34 0x55 0x65 0x75 0x85 set x58 0x66 0x76 0x86 0x96 V D Tag x27 0x80 0x81 0x82 0x x27 0xB4 0xB5 0xB6 0xB x90 0xC3 0xC2 0xC1 0xC x90 0xD3 0xD4 0xD5 0xD x11 0x89 0x88 0x87 0x xA0 0x92 0x93 0x94 0x x37 0xF5 0xF6 0xF7 0xF x21 0xA7 0xA8 0xA9 0xAA (A) (2 points) Which address bits correspond to the block offset? Which bits provide the cache index? Which bits make up the tag field? address bits used for block offset: A[ 3 : 0 ] address bits used for cache index: A[ 6 : 4 ] address bits used for tag field: A[ 31 : 7 ] (B) (3 points) Would a load request to address 0x08C8 result in a hit or a miss? If it results in a hit, specify what value is returned; if it is a miss, write NA. Tag = 0x11, index = 4, block offset = 8 bytes = 2 words Hit / Miss: HIT Returned value if hit or NA if miss: 0x87 (C) (3 points) Would a load request to address 0x0910 result in a hit or a miss? If it results in a hit, specify what value is returned; if it is a miss, write NA. Tag = 0x12, index = 1, block offset = 0 Hit / Miss: HIT Returned value if hit or NA if miss: 0x4B Fall of 12 - Quiz #2
12 (D) (2 points) Would the following instruction result in a hit or a miss? sw x0, 0x104(x0) 0x104 tag = 0x02, index = 0, block offset = 4 bytes = 1 word Hit / Miss: MISS (E) (4 points) Which entries of the cache would be modified by executing the above instruction, sw x0, 0x104(x0)? Assume that Way 0 (the left one) is the least recently used way. Fill in the empty cache line below to indicate the changes that would be made to the cache from executing this instruction. Specify which set of way 0 is modified as well as the contents of valid, dirty, tag, and data words. For any unknown values, enter '?. Way 0 V D Tag set x02? 0x0?? (F) (8 points) Find the steady state cache hit ratio for the following loop on this two-way set associative cache with an LRU (least recently used) replacement policy. The loop is executed for many iterations, so report the average behavior of a loop iteration and ignore cold-start effects. Assume the cache is empty before execution begins (all valid bits are 0). Remember that the cache is used for both instruction and data accesses.. = 0x400 // Code starts at address 0x400 // Assume x1 is initialized to 0, x2 is initialized to 1000 (number of array elements), and x3 is initialized to the base address of array A. loop: addi x2, x2, -1 slli x4, x2, 2 add x4, x3, x4 lw x5, 0(x4) add x1, x1, x5 bnez x2, loop // x4 holds byte offset of array element x2 // x4 holds address of element x2 // x5 holds element x2 of array // x1 holds sum of array elements Instruction miss rate = 0 miss rate = ¼ (one miss every 4 iterations) Every 4 iterations: 24/24 instruction hits + ¾ data hits Hit rate is 27/28 Steady-state hit ratio: 27/28 END OF QUIZ 2! Fall of 12 - Quiz #2
1 /18 2 /16 3 /18 4 /26 5 /22
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
1 /15 2 /20 3 /20 4 /25 5 /20
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /15 2 /20 3 /20 4 /25 5 /20 Quiz
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /15 2 /20 3 /20 4 /25 5 /20 Quiz
1 /20 2 /18 3 /20 4 /18 5 /24
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /20 2 /18 3 /20 4 /18 5 /24 Practice
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /20 2 /18 3 /20 4 /18 5 /24 Practice
1 /20 2 /18 3 /20 4 /18 5 /24
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /20 2 /18 3 /20 4 /18 5 /24 Practice
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /20 2 /18 3 /20 4 /18 5 /24 Practice
Non-pipelined Multicycle processors
 Non-pipelined Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the code tab
Non-pipelined Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the code tab
Implementing RISC-V Interpreter in Hardware
 Implementing RISC-V Interpreter in Hardware Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 16, 2018 MIT 6.004 Fall 2018 L11-1 Instruction interpreter
Implementing RISC-V Interpreter in Hardware Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 16, 2018 MIT 6.004 Fall 2018 L11-1 Instruction interpreter
6.004 Recitation Problems L11 RISC-V Interpreter
 6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
Multicycle processors. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L14-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L14-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
6.004 Recitation Problems L11 RISC-V Interpreter
 6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
Multicycle processors. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L12-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L12-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Control Unit. Main Memory. control. status. address instructions. address data. Internal storage Datapath
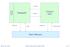 control Internal storage Datapath status Control Unit address data address instructions Main Memory March 20, 2018 http://csg.csail.mit.edu/6.s084 L11-1 Our interpreter is a Single-Cycle RISC-V Processor
control Internal storage Datapath status Control Unit address data address instructions Main Memory March 20, 2018 http://csg.csail.mit.edu/6.s084 L11-1 Our interpreter is a Single-Cycle RISC-V Processor
6.004 Recitation Problems L13 RISC-V Interpreter
 6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter
 6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Tutorial Problems L3 Procedures and Stacks
 6.004 Tutorial Problems L3 Procedures and Stacks RISC-V Calling Conventions: Caller places arguments in registers a0-a7 Caller transfers control to callee using jal (jump-and-link) to capture the urn address
6.004 Tutorial Problems L3 Procedures and Stacks RISC-V Calling Conventions: Caller places arguments in registers a0-a7 Caller transfers control to callee using jal (jump-and-link) to capture the urn address
Non-Pipelined Processors
 Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L10-1 Single-Cycle RISC Processor As an illustrative
Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L10-1 Single-Cycle RISC Processor As an illustrative
1 /10 2 /16 3 /18 4 /15 5 /20 6 /9 7 /12
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Practice Quiz #3B Name Athena login
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Practice Quiz #3B Name Athena login
Non-Pipelined Processors
 Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology September 29, 2014 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology September 29, 2014 http://csg.csail.mit.edu/6.175
Virtual Memory and Interrupts
 Constructive Computer Architecture Virtual Memory and Interrupts Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 13, 2015 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture Virtual Memory and Interrupts Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 13, 2015 http://csg.csail.mit.edu/6.175
Compiling Code, Procedures and Stacks
 Compiling Code, Procedures and Stacks L03-1 RISC-V Recap Computational Instructions executed by ALU Register-Register: op dest, src1, src2 Register-Immediate: op dest, src1, const Control flow instructions
Compiling Code, Procedures and Stacks L03-1 RISC-V Recap Computational Instructions executed by ALU Register-Register: op dest, src1, src2 Register-Immediate: op dest, src1, const Control flow instructions
Procedures and Stacks
 Procedures and Stacks Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. March 15, 2018 L10-1 Announcements Schedule has shifted due to snow day Quiz 2 is now on Thu 4/12 (one week later)
Procedures and Stacks Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. March 15, 2018 L10-1 Announcements Schedule has shifted due to snow day Quiz 2 is now on Thu 4/12 (one week later)
6.004 Tutorial Problems L14 Cache Implementation
 6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
Non-Pipelined Processors - 2
 Constructive Computer Architecture: Non-Pipelined Processors - 2 Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 4, 2017 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture: Non-Pipelined Processors - 2 Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 4, 2017 http://csg.csail.mit.edu/6.175
2) Using the same instruction set for the TinyProc2, convert the following hex values to assembly language: x0f
 CS2 Fall 28 Exam 2 Name: ) The Logisim TinyProc2 has four instructions, each using 8 bits. The instruction format is DR SR SR2 OpCode with OpCodes of for add, for subtract, and for multiply. Load Immediate
CS2 Fall 28 Exam 2 Name: ) The Logisim TinyProc2 has four instructions, each using 8 bits. The instruction format is DR SR SR2 OpCode with OpCodes of for add, for subtract, and for multiply. Load Immediate
MIPS%Assembly% E155%
 MIPS%Assembly% E155% Outline MIPS Architecture ISA Instruction types Machine codes Procedure call Stack 2 The MIPS Register Set Name Register Number Usage $0 0 the constant value 0 $at 1 assembler temporary
MIPS%Assembly% E155% Outline MIPS Architecture ISA Instruction types Machine codes Procedure call Stack 2 The MIPS Register Set Name Register Number Usage $0 0 the constant value 0 $at 1 assembler temporary
RISC-V Assembly and Binary Notation
 RISC-V Assembly and Binary Notation L02-1 Course Mechanics Reminders Course website: http://6004.mit.edu All lectures, videos, tutorials, and exam material can be found under Information/Resources tab.
RISC-V Assembly and Binary Notation L02-1 Course Mechanics Reminders Course website: http://6004.mit.edu All lectures, videos, tutorials, and exam material can be found under Information/Resources tab.
Computer Organization MIPS ISA
 CPE 335 Computer Organization MIPS ISA Dr. Iyad Jafar Adapted from Dr. Gheith Abandah Slides http://www.abandah.com/gheith/courses/cpe335_s08/index.html CPE 232 MIPS ISA 1 (vonneumann) Processor Organization
CPE 335 Computer Organization MIPS ISA Dr. Iyad Jafar Adapted from Dr. Gheith Abandah Slides http://www.abandah.com/gheith/courses/cpe335_s08/index.html CPE 232 MIPS ISA 1 (vonneumann) Processor Organization
CISC 662 Graduate Computer Architecture. Lecture 4 - ISA
 CISC 662 Graduate Computer Architecture Lecture 4 - ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
CISC 662 Graduate Computer Architecture Lecture 4 - ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
6.004 Tutorial Problems L14 Cache Implementation
 6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
6.004 Tutorial Problems L14 Cache Implementation Cache Miss Types Compulsory Miss: Starting with an empty cache, a cache line is first referenced (invalid) Capacity Miss: The cache is not big enough to
CISC 662 Graduate Computer Architecture. Lecture 4 - ISA MIPS ISA. In a CPU. (vonneumann) Processor Organization
 CISC 662 Graduate Computer Architecture Lecture 4 - ISA MIPS ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
CISC 662 Graduate Computer Architecture Lecture 4 - ISA MIPS ISA Michela Taufer http://www.cis.udel.edu/~taufer/courses Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer Architecture,
Programmable Machines
 Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
Programmable Machines
 Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
Programmable Machines Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. Quiz 1: next week Covers L1-L8 Oct 11, 7:30-9:30PM Walker memorial 50-340 L09-1 6.004 So Far Using Combinational
6.004 Recitation Problems L13 Caches
 6.004 Recitation Problems L13 Caches Keep the most often-used data in a small, fast SRAM (often local to CPU chip). The reason this strategy works: LOCALITY. Temporal locality: If a location has been accessed
6.004 Recitation Problems L13 Caches Keep the most often-used data in a small, fast SRAM (often local to CPU chip). The reason this strategy works: LOCALITY. Temporal locality: If a location has been accessed
ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design
 ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu School of Engineering Brown University Spring 2014 Sources: Computer
ENGN1640: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu School of Engineering Brown University Spring 2014 Sources: Computer
Chapter 2A Instructions: Language of the Computer
 Chapter 2A Instructions: Language of the Computer Copyright 2009 Elsevier, Inc. All rights reserved. Instruction Set The repertoire of instructions of a computer Different computers have different instruction
Chapter 2A Instructions: Language of the Computer Copyright 2009 Elsevier, Inc. All rights reserved. Instruction Set The repertoire of instructions of a computer Different computers have different instruction
Wawrzynek & Weaver CS 61C. Sp 2018 Great Ideas in Computer Architecture MT 1. Print your name:,
 Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
comp 180 Lecture 10 Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions
 Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions Procedure Calls A procedure of a subroutine is like an agent which needs certain information to perform a
Outline of Lecture Procedure calls Saving and restoring registers Summary of MIPS instructions Procedure Calls A procedure of a subroutine is like an agent which needs certain information to perform a
Examples of branch instructions
 Examples of branch instructions Beq rs,rt,target #go to target if rs = rt Beqz rs, target #go to target if rs = 0 Bne rs,rt,target #go to target if rs!= rt Bltz rs, target #go to target if rs < 0 etc.
Examples of branch instructions Beq rs,rt,target #go to target if rs = rt Beqz rs, target #go to target if rs = 0 Bne rs,rt,target #go to target if rs!= rt Bltz rs, target #go to target if rs < 0 etc.
Flow of Control -- Conditional branch instructions
 Flow of Control -- Conditional branch instructions You can compare directly Equality or inequality of two registers One register with 0 (>,
Flow of Control -- Conditional branch instructions You can compare directly Equality or inequality of two registers One register with 0 (>,
Wawrzynek & Weaver CS 61C. Sp 2018 Great Ideas in Computer Architecture MT 1. Print your name:,
 Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
Wawrzynek & Weaver CS 61C Sp 2018 Great Ideas in Computer Architecture MT 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that any academic
Computer Science and Engineering 331. Midterm Examination #1. Fall Name: Solutions S.S.#:
 Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
Instructions: Language of the Computer
 CS359: Computer Architecture Instructions: Language of the Computer Yanyan Shen Department of Computer Science and Engineering 1 The Language a Computer Understands Word a computer understands: instruction
CS359: Computer Architecture Instructions: Language of the Computer Yanyan Shen Department of Computer Science and Engineering 1 The Language a Computer Understands Word a computer understands: instruction
ELEC / Computer Architecture and Design Fall 2013 Instruction Set Architecture (Chapter 2)
 ELEC 5200-001/6200-001 Computer Architecture and Design Fall 2013 Instruction Set Architecture (Chapter 2) Victor P. Nelson, Professor & Asst. Chair Vishwani D. Agrawal, James J. Danaher Professor Department
ELEC 5200-001/6200-001 Computer Architecture and Design Fall 2013 Instruction Set Architecture (Chapter 2) Victor P. Nelson, Professor & Asst. Chair Vishwani D. Agrawal, James J. Danaher Professor Department
Course Administration
 Fall 2017 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture 2/4 Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701 E-mail: kodi@ohio.edu
Fall 2017 EE 3613: Computer Organization Chapter 2: Instruction Set Architecture 2/4 Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 45701 E-mail: kodi@ohio.edu
Anne Bracy CS 3410 Computer Science Cornell University. See P&H Chapter: , , Appendix B
 Anne Bracy CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. See P&H Chapter: 2.16-2.20, 4.1-4.4,
Anne Bracy CS 3410 Computer Science Cornell University The slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. See P&H Chapter: 2.16-2.20, 4.1-4.4,
CENG3420 Lecture 03 Review
 CENG3420 Lecture 03 Review Bei Yu byu@cse.cuhk.edu.hk 2017 Spring 1 / 38 CISC vs. RISC Complex Instruction Set Computer (CISC) Lots of instructions of variable size, very memory optimal, typically less
CENG3420 Lecture 03 Review Bei Yu byu@cse.cuhk.edu.hk 2017 Spring 1 / 38 CISC vs. RISC Complex Instruction Set Computer (CISC) Lots of instructions of variable size, very memory optimal, typically less
EN164: Design of Computing Systems Topic 03: Instruction Set Architecture Design
 EN164: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown
EN164: Design of Computing Systems Topic 03: Instruction Set Architecture Design Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown
6.004 Tutorial Problems L22 Branch Prediction
 6.004 Tutorial Problems L22 Branch Prediction Branch target buffer (BTB): Direct-mapped cache (can also be set-associative) that stores the target address of jumps and taken branches. The BTB is searched
6.004 Tutorial Problems L22 Branch Prediction Branch target buffer (BTB): Direct-mapped cache (can also be set-associative) that stores the target address of jumps and taken branches. The BTB is searched
1 5. Addressing Modes COMP2611 Fall 2015 Instruction: Language of the Computer
 1 5. Addressing Modes MIPS Addressing Modes 2 Addressing takes care of where to find data instruction We have seen, so far three addressing modes of MIPS (to find data): 1. Immediate addressing: provides
1 5. Addressing Modes MIPS Addressing Modes 2 Addressing takes care of where to find data instruction We have seen, so far three addressing modes of MIPS (to find data): 1. Immediate addressing: provides
CSc 256 Midterm (green) Fall 2018
 CSc 256 Midterm (green) Fall 2018 NAME: Problem 1 (5 points): Suppose we are tracing a C/C++ program using a debugger such as gdb. The code showing all function calls looks like this: main() { bat(5);
CSc 256 Midterm (green) Fall 2018 NAME: Problem 1 (5 points): Suppose we are tracing a C/C++ program using a debugger such as gdb. The code showing all function calls looks like this: main() { bat(5);
ece4750-tinyrv-isa.txt
 ========================================================================== Tiny RISC-V Instruction Set Architecture ========================================================================== # Author :
========================================================================== Tiny RISC-V Instruction Set Architecture ========================================================================== # Author :
Computer Organization MIPS Architecture. Department of Computer Science Missouri University of Science & Technology
 Computer Organization MIPS Architecture Department of Computer Science Missouri University of Science & Technology hurson@mst.edu Computer Organization Note, this unit will be covered in three lectures.
Computer Organization MIPS Architecture Department of Computer Science Missouri University of Science & Technology hurson@mst.edu Computer Organization Note, this unit will be covered in three lectures.
A Processor. Kevin Walsh CS 3410, Spring 2010 Computer Science Cornell University. See: P&H Chapter , 4.1-3
 A Processor Kevin Walsh CS 3410, Spring 2010 Computer Science Cornell University See: P&H Chapter 2.16-20, 4.1-3 Let s build a MIPS CPU but using Harvard architecture Basic Computer System Registers ALU
A Processor Kevin Walsh CS 3410, Spring 2010 Computer Science Cornell University See: P&H Chapter 2.16-20, 4.1-3 Let s build a MIPS CPU but using Harvard architecture Basic Computer System Registers ALU
Computer Architecture. The Language of the Machine
 Computer Architecture The Language of the Machine Instruction Sets Basic ISA Classes, Addressing, Format Administrative Matters Operations, Branching, Calling conventions Break Organization All computers
Computer Architecture The Language of the Machine Instruction Sets Basic ISA Classes, Addressing, Format Administrative Matters Operations, Branching, Calling conventions Break Organization All computers
CS 351 Exam 2 Mon. 11/2/2015
 CS 351 Exam 2 Mon. 11/2/2015 Name: Rules and Hints The MIPS cheat sheet and datapath diagram are attached at the end of this exam for your reference. You may use one handwritten 8.5 11 cheat sheet (front
CS 351 Exam 2 Mon. 11/2/2015 Name: Rules and Hints The MIPS cheat sheet and datapath diagram are attached at the end of this exam for your reference. You may use one handwritten 8.5 11 cheat sheet (front
Branch Addressing. Jump Addressing. Target Addressing Example. The University of Adelaide, School of Computer Science 28 September 2015
 Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Branch Addressing Branch instructions specify Opcode, two registers, target address Most branch targets are near branch Forward or backward op rs rt constant or address 6 bits 5 bits 5 bits 16 bits PC-relative
Do-While Example. In C++ In assembly language. do { z--; while (a == b); z = b; loop: addi $s2, $s2, -1 beq $s0, $s1, loop or $s2, $s1, $zero
 Do-While Example In C++ do { z--; while (a == b); z = b; In assembly language loop: addi $s2, $s2, -1 beq $s0, $s1, loop or $s2, $s1, $zero 25 Comparisons Set on less than (slt) compares its source registers
Do-While Example In C++ do { z--; while (a == b); z = b; In assembly language loop: addi $s2, $s2, -1 beq $s0, $s1, loop or $s2, $s1, $zero 25 Comparisons Set on less than (slt) compares its source registers
CS 61c: Great Ideas in Computer Architecture
 MIPS Functions July 1, 2014 Review I RISC Design Principles Smaller is faster: 32 registers, fewer instructions Keep it simple: rigid syntax, fixed instruction length MIPS Registers: $s0-$s7,$t0-$t9, $0
MIPS Functions July 1, 2014 Review I RISC Design Principles Smaller is faster: 32 registers, fewer instructions Keep it simple: rigid syntax, fixed instruction length MIPS Registers: $s0-$s7,$t0-$t9, $0
MIPS Functions and the Runtime Stack
 MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
MIPS Functions and the Runtime Stack COE 301 Computer Organization Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline
CS222: MIPS Instruction Set
 CS222: MIPS Instruction Set Dr. A. Sahu Dept of Comp. Sc. & Engg. Indian Institute of Technology Guwahati 1 Outline Previous Introduction to MIPS Instruction Set MIPS Arithmetic's Register Vs Memory, Registers
CS222: MIPS Instruction Set Dr. A. Sahu Dept of Comp. Sc. & Engg. Indian Institute of Technology Guwahati 1 Outline Previous Introduction to MIPS Instruction Set MIPS Arithmetic's Register Vs Memory, Registers
Instruction Set Architectures Part I: From C to MIPS. Readings:
 Instruction Set Architectures Part I: From C to MIPS Readings: 2.1-2.14 1 Goals for this Class Understand how CPUs run programs How do we express the computation the CPU? How does the CPU execute it? How
Instruction Set Architectures Part I: From C to MIPS Readings: 2.1-2.14 1 Goals for this Class Understand how CPUs run programs How do we express the computation the CPU? How does the CPU execute it? How
Processor. Han Wang CS3410, Spring 2012 Computer Science Cornell University. See P&H Chapter , 4.1 4
 Processor Han Wang CS3410, Spring 2012 Computer Science Cornell University See P&H Chapter 2.16 20, 4.1 4 Announcements Project 1 Available Design Document due in one week. Final Design due in three weeks.
Processor Han Wang CS3410, Spring 2012 Computer Science Cornell University See P&H Chapter 2.16 20, 4.1 4 Announcements Project 1 Available Design Document due in one week. Final Design due in three weeks.
CS31001 COMPUTER ORGANIZATION AND ARCHITECTURE. Debdeep Mukhopadhyay, CSE, IIT Kharagpur. Instructions and Addressing
 CS31001 COMPUTER ORGANIZATION AND ARCHITECTURE Debdeep Mukhopadhyay, CSE, IIT Kharagpur Instructions and Addressing 1 ISA vs. Microarchitecture An ISA or Instruction Set Architecture describes the aspects
CS31001 COMPUTER ORGANIZATION AND ARCHITECTURE Debdeep Mukhopadhyay, CSE, IIT Kharagpur Instructions and Addressing 1 ISA vs. Microarchitecture An ISA or Instruction Set Architecture describes the aspects
CSc 256 Midterm 1 Fall 2011
 CSc 256 Midterm 1 Fall 2011 NAME: Problem 1a: Given the C++ function prototype and variable declarations: int func(int arg0, int *arg1, int *arg2); int *ptr, n, arr[10]; which of the following statements
CSc 256 Midterm 1 Fall 2011 NAME: Problem 1a: Given the C++ function prototype and variable declarations: int func(int arg0, int *arg1, int *arg2); int *ptr, n, arr[10]; which of the following statements
MIPS Functions and Instruction Formats
 MIPS Functions and Instruction Formats 1 The Contract: The MIPS Calling Convention You write functions, your compiler writes functions, other compilers write functions And all your functions call other
MIPS Functions and Instruction Formats 1 The Contract: The MIPS Calling Convention You write functions, your compiler writes functions, other compilers write functions And all your functions call other
MIPS ISA and MIPS Assembly. CS301 Prof. Szajda
 MIPS ISA and MIPS Assembly CS301 Prof. Szajda Administrative HW #2 due Wednesday (9/11) at 5pm Lab #2 due Friday (9/13) 1:30pm Read Appendix B5, B6, B.9 and Chapter 2.5-2.9 (if you have not already done
MIPS ISA and MIPS Assembly CS301 Prof. Szajda Administrative HW #2 due Wednesday (9/11) at 5pm Lab #2 due Friday (9/13) 1:30pm Read Appendix B5, B6, B.9 and Chapter 2.5-2.9 (if you have not already done
101 Assembly. ENGR 3410 Computer Architecture Mark L. Chang Fall 2009
 101 Assembly ENGR 3410 Computer Architecture Mark L. Chang Fall 2009 What is assembly? 79 Why are we learning assembly now? 80 Assembly Language Readings: Chapter 2 (2.1-2.6, 2.8, 2.9, 2.13, 2.15), Appendix
101 Assembly ENGR 3410 Computer Architecture Mark L. Chang Fall 2009 What is assembly? 79 Why are we learning assembly now? 80 Assembly Language Readings: Chapter 2 (2.1-2.6, 2.8, 2.9, 2.13, 2.15), Appendix
Machine Language Instructions Introduction. Instructions Words of a language understood by machine. Instruction set Vocabulary of the machine
 Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Examples of IO, Interrupts, and Exceptions
 Examples of IO, Interrupts, and Exceptions Andy Wright, Thomas Bourgeat, Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L15-1 Keyboard Input
Examples of IO, Interrupts, and Exceptions Andy Wright, Thomas Bourgeat, Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L15-1 Keyboard Input
The MIPS Instruction Set Architecture
 The MIPS Set Architecture CPS 14 Lecture 5 Today s Lecture Admin HW #1 is due HW #2 assigned Outline Review A specific ISA, we ll use it throughout semester, very similar to the NiosII ISA (we will use
The MIPS Set Architecture CPS 14 Lecture 5 Today s Lecture Admin HW #1 is due HW #2 assigned Outline Review A specific ISA, we ll use it throughout semester, very similar to the NiosII ISA (we will use
Introduction to MIPS Processor
 Introduction to MIPS Processor The processor we will be considering in this tutorial is the MIPS processor. The MIPS processor, designed in 1984 by researchers at Stanford University, is a RISC (Reduced
Introduction to MIPS Processor The processor we will be considering in this tutorial is the MIPS processor. The MIPS processor, designed in 1984 by researchers at Stanford University, is a RISC (Reduced
are Softw Instruction Set Architecture Microarchitecture are rdw
 Program, Application Software Programming Language Compiler/Interpreter Operating System Instruction Set Architecture Hardware Microarchitecture Digital Logic Devices (transistors, etc.) Solid-State Physics
Program, Application Software Programming Language Compiler/Interpreter Operating System Instruction Set Architecture Hardware Microarchitecture Digital Logic Devices (transistors, etc.) Solid-State Physics
Topic Notes: MIPS Instruction Set Architecture
 Computer Science 220 Assembly Language & Comp. Architecture Siena College Fall 2011 Topic Notes: MIPS Instruction Set Architecture vonneumann Architecture Modern computers use the vonneumann architecture.
Computer Science 220 Assembly Language & Comp. Architecture Siena College Fall 2011 Topic Notes: MIPS Instruction Set Architecture vonneumann Architecture Modern computers use the vonneumann architecture.
CS 61c: Great Ideas in Computer Architecture
 MIPS Instruction Formats July 2, 2014 Review New registers: $a0-$a3, $v0-$v1, $ra, $sp New instructions: slt, la, li, jal, jr Saved registers: $s0-$s7, $sp, $ra Volatile registers: $t0-$t9, $v0-$v1, $a0-$a3
MIPS Instruction Formats July 2, 2014 Review New registers: $a0-$a3, $v0-$v1, $ra, $sp New instructions: slt, la, li, jal, jr Saved registers: $s0-$s7, $sp, $ra Volatile registers: $t0-$t9, $v0-$v1, $a0-$a3
Overview. Introduction to the MIPS ISA. MIPS ISA Overview. Overview (2)
 Introduction to the MIPS ISA Overview Remember that the machine only understands very basic instructions (machine instructions) It is the compiler s job to translate your high-level (e.g. C program) into
Introduction to the MIPS ISA Overview Remember that the machine only understands very basic instructions (machine instructions) It is the compiler s job to translate your high-level (e.g. C program) into
Chapter 2. Computer Abstractions and Technology. Lesson 4: MIPS (cont )
 Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
Chapter 2 Computer Abstractions and Technology Lesson 4: MIPS (cont ) Logical Operations Instructions for bitwise manipulation Operation C Java MIPS Shift left >>> srl Bitwise
Lectures 3-4: MIPS instructions
 Lectures 3-4: MIPS instructions Motivation Learn how a processor s native language looks like Discover the most important software-hardware interface MIPS Microprocessor without Interlocked Pipeline Stages
Lectures 3-4: MIPS instructions Motivation Learn how a processor s native language looks like Discover the most important software-hardware interface MIPS Microprocessor without Interlocked Pipeline Stages
Anne Bracy CS 3410 Computer Science Cornell University. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon]
![Anne Bracy CS 3410 Computer Science Cornell University. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Anne Bracy CS 3410 Computer Science Cornell University. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon]](/thumbs/92/108186036.jpg) Anne Bracy CS 3410 Computer Science Cornell University [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Understanding the basics of a processor We now have the technology to build a CPU! Putting it all
Anne Bracy CS 3410 Computer Science Cornell University [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Understanding the basics of a processor We now have the technology to build a CPU! Putting it all
Stored Program Concept. Instructions: Characteristics of Instruction Set. Architecture Specification. Example of multiple operands
 Stored Program Concept Instructions: Instructions are bits Programs are stored in memory to be read or written just like data Processor Memory memory for data, programs, compilers, editors, etc. Fetch
Stored Program Concept Instructions: Instructions are bits Programs are stored in memory to be read or written just like data Processor Memory memory for data, programs, compilers, editors, etc. Fetch
Bypassing and EHRs. Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. L23-1
 Bypassing and EHRs Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. L23-1 Bypassing F D RF bypass E/WB Bypassing is a technique to reduce the number of stalls (that is, the number
Bypassing and EHRs Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. L23-1 Bypassing F D RF bypass E/WB Bypassing is a technique to reduce the number of stalls (that is, the number
8*4 + 4 = 36 each int is 4 bytes
 CS 61CL (Clancy) Solutions and grading standards for exam 1 Spring 2009 169 students took the exam. The average score was 43.6; the median was 46. Scores ranged from 1 to 59. There were 89 scores between
CS 61CL (Clancy) Solutions and grading standards for exam 1 Spring 2009 169 students took the exam. The average score was 43.6; the median was 46. Scores ranged from 1 to 59. There were 89 scores between
SPIM Instruction Set
 SPIM Instruction Set This document gives an overview of the more common instructions used in the SPIM simulator. Overview The SPIM simulator implements the full MIPS instruction set, as well as a large
SPIM Instruction Set This document gives an overview of the more common instructions used in the SPIM simulator. Overview The SPIM simulator implements the full MIPS instruction set, as well as a large
Lecture 2. Instructions: Language of the Computer (Chapter 2 of the textbook)
 Lecture 2 Instructions: Language of the Computer (Chapter 2 of the textbook) Instructions: tell computers what to do Chapter 2 Instructions: Language of the Computer 2 Introduction Chapter 2.1 Chapter
Lecture 2 Instructions: Language of the Computer (Chapter 2 of the textbook) Instructions: tell computers what to do Chapter 2 Instructions: Language of the Computer 2 Introduction Chapter 2.1 Chapter
Instructions: MIPS ISA. Chapter 2 Instructions: Language of the Computer 1
 Instructions: MIPS ISA Chapter 2 Instructions: Language of the Computer 1 PH Chapter 2 Pt A Instructions: MIPS ISA Based on Text: Patterson Henessey Publisher: Morgan Kaufmann Edited by Y.K. Malaiya for
Instructions: MIPS ISA Chapter 2 Instructions: Language of the Computer 1 PH Chapter 2 Pt A Instructions: MIPS ISA Based on Text: Patterson Henessey Publisher: Morgan Kaufmann Edited by Y.K. Malaiya for
MIPS Datapath. MIPS Registers (and the conventions associated with them) MIPS Instruction Types
 1 Lecture 08 Introduction to the MIPS ISA + Procedure Calls in MIPS Longer instructions = more bits to address registers MIPS Datapath 6 bit opcodes... 2 MIPS Instructions are 32 bits More ways to address
1 Lecture 08 Introduction to the MIPS ISA + Procedure Calls in MIPS Longer instructions = more bits to address registers MIPS Datapath 6 bit opcodes... 2 MIPS Instructions are 32 bits More ways to address
Computer Organization and Components
 2 Course Structure Computer Organization and Components Module 4: Memory Hierarchy Module 1: Logic Design IS1500, fall 2014 Lecture 4: and F1 DC Ö1 F2 DC Ö2 F7b Lab: dicom F8 Module 2: C and Associate
2 Course Structure Computer Organization and Components Module 4: Memory Hierarchy Module 1: Logic Design IS1500, fall 2014 Lecture 4: and F1 DC Ö1 F2 DC Ö2 F7b Lab: dicom F8 Module 2: C and Associate
Instructions: Language of the Computer
 Instructions: Language of the Computer Tuesday 22 September 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class
Instructions: Language of the Computer Tuesday 22 September 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class
Computer Science 324 Computer Architecture Mount Holyoke College Fall Topic Notes: MIPS Instruction Set Architecture
 Computer Science 324 Computer Architecture Mount Holyoke College Fall 2009 Topic Notes: MIPS Instruction Set Architecture vonneumann Architecture Modern computers use the vonneumann architecture. Idea:
Computer Science 324 Computer Architecture Mount Holyoke College Fall 2009 Topic Notes: MIPS Instruction Set Architecture vonneumann Architecture Modern computers use the vonneumann architecture. Idea:
Thomas Polzer Institut für Technische Informatik
 Thomas Polzer tpolzer@ecs.tuwien.ac.at Institut für Technische Informatik Branch to a labeled instruction if a condition is true Otherwise, continue sequentially beq rs, rt, L1 if (rs == rt) branch to
Thomas Polzer tpolzer@ecs.tuwien.ac.at Institut für Technische Informatik Branch to a labeled instruction if a condition is true Otherwise, continue sequentially beq rs, rt, L1 if (rs == rt) branch to
Instruction Set Architecture
 Computer Architecture Instruction Set Architecture Lynn Choi Korea University Machine Language Programming language High-level programming languages Procedural languages: C, PASCAL, FORTRAN Object-oriented
Computer Architecture Instruction Set Architecture Lynn Choi Korea University Machine Language Programming language High-level programming languages Procedural languages: C, PASCAL, FORTRAN Object-oriented
The University of Alabama in Huntsville Electrical & Computer Engineering Department CPE Test II November 14, 2000
 The University of Alabama in Huntsville Electrical & Computer Engineering Department CPE 513 01 Test II November 14, 2000 Name: 1. (5 points) For an eight-stage pipeline, how many cycles does it take to
The University of Alabama in Huntsville Electrical & Computer Engineering Department CPE 513 01 Test II November 14, 2000 Name: 1. (5 points) For an eight-stage pipeline, how many cycles does it take to
Computer Architecture
 CS3350B Computer Architecture Winter 2015 Lecture 4.2: MIPS ISA -- Instruction Representation Marc Moreno Maza www.csd.uwo.ca/courses/cs3350b [Adapted from lectures on Computer Organization and Design,
CS3350B Computer Architecture Winter 2015 Lecture 4.2: MIPS ISA -- Instruction Representation Marc Moreno Maza www.csd.uwo.ca/courses/cs3350b [Adapted from lectures on Computer Organization and Design,
EN164: Design of Computing Systems Lecture 11: Processor / ISA 4
 EN164: Design of Computing Systems Lecture 11: Processor / ISA 4 Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University
EN164: Design of Computing Systems Lecture 11: Processor / ISA 4 Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University
The Single Cycle Processor
 EECS 322 Computer Architecture The Single Cycle Processor Instructor: Francis G. Wolff wolff@eecs.cwru.edu Case Western Reserve University This presentation uses powerpoint animation: please viewshow CWRU
EECS 322 Computer Architecture The Single Cycle Processor Instructor: Francis G. Wolff wolff@eecs.cwru.edu Case Western Reserve University This presentation uses powerpoint animation: please viewshow CWRU
Mips Code Examples Peter Rounce
 Mips Code Examples Peter Rounce P.Rounce@cs.ucl.ac.uk Some C Examples Assignment : int j = 10 ; // space must be allocated to variable j Possibility 1: j is stored in a register, i.e. register $2 then
Mips Code Examples Peter Rounce P.Rounce@cs.ucl.ac.uk Some C Examples Assignment : int j = 10 ; // space must be allocated to variable j Possibility 1: j is stored in a register, i.e. register $2 then
MIPS Instruction Set
 MIPS Instruction Set Prof. James L. Frankel Harvard University Version of 7:12 PM 3-Apr-2018 Copyright 2018, 2017, 2016, 201 James L. Frankel. All rights reserved. CPU Overview CPU is an acronym for Central
MIPS Instruction Set Prof. James L. Frankel Harvard University Version of 7:12 PM 3-Apr-2018 Copyright 2018, 2017, 2016, 201 James L. Frankel. All rights reserved. CPU Overview CPU is an acronym for Central
We will study the MIPS assembly language as an exemplar of the concept.
 MIPS Assembly Language 1 We will study the MIPS assembly language as an exemplar of the concept. MIPS assembly instructions each consist of a single token specifying the command to be carried out, and
MIPS Assembly Language 1 We will study the MIPS assembly language as an exemplar of the concept. MIPS assembly instructions each consist of a single token specifying the command to be carried out, and
Chapter 2. Instructions: Language of the Computer. HW#1: 1.3 all, 1.4 all, 1.6.1, , , , , and Due date: one week.
 Chapter 2 Instructions: Language of the Computer HW#1: 1.3 all, 1.4 all, 1.6.1, 1.14.4, 1.14.5, 1.14.6, 1.15.1, and 1.15.4 Due date: one week. Practice: 1.5 all, 1.6 all, 1.10 all, 1.11 all, 1.14 all,
Chapter 2 Instructions: Language of the Computer HW#1: 1.3 all, 1.4 all, 1.6.1, 1.14.4, 1.14.5, 1.14.6, 1.15.1, and 1.15.4 Due date: one week. Practice: 1.5 all, 1.6 all, 1.10 all, 1.11 all, 1.14 all,
Chapter 2. Instructions:
 Chapter 2 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive e.g., MIPS Arithmetic Instructions We ll be working with
Chapter 2 1 Instructions: Language of the Machine More primitive than higher level languages e.g., no sophisticated control flow Very restrictive e.g., MIPS Arithmetic Instructions We ll be working with
Reduced Instruction Set Computer (RISC)
 Reduced Instruction Set Computer (RISC) Focuses on reducing the number and complexity of instructions of the ISA. RISC Goals RISC: Simplify ISA Simplify CPU Design Better CPU Performance Motivated by simplifying
Reduced Instruction Set Computer (RISC) Focuses on reducing the number and complexity of instructions of the ISA. RISC Goals RISC: Simplify ISA Simplify CPU Design Better CPU Performance Motivated by simplifying
Computer System Architecture Midterm Examination Spring 2002
 Computer System Architecture 6.823 Midterm Examination Spring 2002 Name: This is an open book, open notes exam. 110 Minutes 1 Pages Notes: Not all questions are of equal difficulty, so look over the entire
Computer System Architecture 6.823 Midterm Examination Spring 2002 Name: This is an open book, open notes exam. 110 Minutes 1 Pages Notes: Not all questions are of equal difficulty, so look over the entire
