ENCM 369 Winter 2016 Lab 11 for the Week of April 4
|
|
|
- Aileen Harvey
- 5 years ago
- Views:
Transcription
1 page 1 of 13 ENCM 369 Winter 2016 Lab 11 for the Week of April 4 Steve Norman Department of Electrical & Computer Engineering University of Calgary April 2016 Lab instructions and other documents for ENCM 369 can be found at 1 This Lab is important, but will not be marked If the usual pattern for ENCM 369 labs were followed, this lab would be due Friday, April 8, That would leave very little time for your TAs to get the lab marked before the last lab periods on April 12 So this lab will not be marked, and solutions will be posted sometime during the week of April 4 Please make a serious effort to solve the Exercises yourself before checking solutions! 2 Exercise A: Analysis of set-associative caches 21 Read This First As explained in lectures, set-associative caches provide a good (but not perfect) solution to the problem of set-bit conflicts in direct-mapped caches The difference between direct-mapped and set-associative structure is illustrated in Figure 1 Just as for a direct-mapped cache, in a set-associative cache an address must be split into parts: tag, set bits, block offset (if there are multi-word blocks), and byte offset The formulas for the widths of these address parts are exactly the same as given for direct-mapped caches in Section?? However, the equations for the capacity of a set-associative cache are slightly different from those for the capacity of a direct-mapped cache If C is capacity in bytes, S is the number of sets, N is the number of ways, and Bpl ( bytes per line ) is the size in bytes of a block, then C = S N Bpl To use a block size given in words instead of bytes: C = S N words per block bytes per word For units to make sense in these equations, it turns that appropriate units for N are blocks per set Here are some example calculations:
2 ENCM 369 Winter 2016 Lab 11 page 2 of 13 Figure 1: Graphical comparison of set-associative caches, direct-mapped caches, and fully-associative caches After reading this caption you should probably use the Rotate Right tool in your PDF reader to view the diagram The term search tag refers to the tag extracted from the address of the instruction or data item the processor core is seeking The diagrams are intended to show conceptual structure, and leave out wires and some important logic elements (eg, multiplexers) Layout in the diagram may or may not reflect actual physical layout within integrated circuits Key to colouring of storage cells status bit(s): 1 valid bit, plus, in the case of a write-back D-cache, 1 dirty bit tag bits block of data or instruction words bits that help with LRU or approximate-lru replacement Note: Relative sizes are not to scale A block might be as large as 64 bytes (512 bits), which is difficult to describe graphically in proportion to a single status bit N-way set-associative cache: Each way is organized like a direct-mapped cache For lookup, the index selects a set, and all N blocks in that set must be checked for a hit N valid-bits are checked all at once; at the same time N tags are compared with the search tag set 0 set 1 set 2 set 3 set S 3 set S 2 set S 1 way 0 way 1 way N 1 = = = set 0 set 1 set 2 set 3 set S 3 set S 2 set S 1 = set bits decoder N comparators for tags work in parallel Direct-mapped cache: Like a 1-way set-associative cache The set bits decide which set is inspected to test for a hit set bits decoder 1 tag comparator for the whole cache Fully-associative cache: Like a set-associative cache with only one set No set bits are required for lookup Instead all tags in the entire cache are checked at the same time Each tag has built-in comparison logic to test for a match with the search tag entry 0 entry 1 entry 2 entry N 2 entry N 1
3 ENCM 369 Winter 2016 Lab 11 page 3 of 13 What is the capacity of the cache of textbook Figure 89? Obtaining all the dimensions we need from Figure 89, C = S N words per block bytes per word = 4 sets 2 blocks set = 32 bytes 1 word block 4 bytes word Suppose we modify the design of the cache of Exercise A of Lab 10, so that it is two-way set-associative instead of direct-mapped, and has four-word blocks instead of one-word blocks The capacity will remain 1024 words, that is 4096 = 2 12 bytes How will addresses be split into parts to access this new design? We need to know S to determine the number of set bits C S = N words per block bytes per word 4 KB = = 2 blocks set 4 words block 4 bytes word bytes bytes/set = 128 sets The number of set bits is log 2 S = log = 7 The word size is 4 bytes, so there is a 2-bit byte offset The block size is 4 words, so the block offset is also 2 bits wide Here is the address split: bit tag set bits bit block offset 2-bit byte offset 22 What to Do Refer to Problem 4 in Exercise B of Lab 10 Do parts (a), (b), and (c) again, with the following assumptions: no change in word size; no change in block size; no changes to the capacities of the caches; L1 D-cache changed to 8-way set-associative; L2 cache changed to 16-way set-associative 3 Exercise B: Virtual and physical addresses of array elements 31 Read This First To understand how virtual memory works, it s useful to think about the common operation of sequentially accessing all of the elements in an array For example, consider this simple C function:
4 ENCM 369 Winter 2016 Lab 11 page 4 of 13 Figure 2: An array of byte ints Addresses must be sequential in virtual address space, but in physical address space, chunks of the array can be within pages that are far away from each other virtual address space address 0x elements 0 to 823 physical address space address 0x elements 824 to 1299 elements 0 to 823 0x x x x x elements 824 to x int sum_array(const int *arr, int n) { int sum = 0, i; for (i = 0; i < n; i++) sum += arr[i]; return sum; } arr should point to element 0 of an array, and n should indicate the number of elements belonging to the array In a system with virtual memory, the pointer argument arr will hold a virtual address Let s suppose sum_array is called with arr pointing to element 0 of an array of 1300 elements, each of which is a 4-byte int, and our virtual memory system uses 32-bit virtual addresses, 32-bit physical addresses, and 4 KB pages Further, let s suppose the virtual address of element 0 of the array is 0x1001_0320 if that s true, the layout of the array in virtual memory must look like the left side of Figure 2 However, there are many, many possible arrangements of the array in physical address space the right side of Figure 2 shows just one possible arrangement If the arguments arr and n and local variables sum and i are all in registers, the only data memory accesses the function will make will be reads of array elements, using virtual addresses 0x1001_0320, 0x1001_0324, and so on, in sequence Because parts of the array are in two different pages, two different VPN-to-PPN translations will be used by the load instructions that read the array element values The first translation is from VPN 0x10010 to PPN 0x33714 and the second translation is from VPN 0x10011 to PPN 0x25588 It s possible that both translations are in the D-TLB when the loop starts, in which case there will be no D-TLB misses at all while the loop runs At most there will be two D-TLB misses one on the access to arr[0], and another on the access to arr[824] (Remember, one of the effects of a TLB miss is copy a translation from a page table to the TLB)
5 ENCM 369 Winter 2016 Lab 11 page 5 of What to do, Part I Consider the scenario outlined in Read This First, but with the address of arr[0] changed to 0x1001_0fb0 Make a diagram similar to Figure 2, showing which array elements sit in which pages Be as detailed as you can There is essentially only one correct answer for the layout in virtual memory But there s a huge number of possible correct answers for the organization in physical memory come up with just one, making sure that it is consistent with the given information What the largest possible number of D-TLB misses as the loop runs? Which array element accesses could possibly cause D-TLB misses? 33 What to do, Part II Consider the same loop, but with a much larger array Suppose that the address of arr[0] is 0x1001_2f00, and that the value of n is 50,000 Determine the total number of pages partly or completely occupied by elements of the array Suppose the D-TLB has a capacity of 32 VPN-to-PPN translations Find the smallest and largest possible numbers of D-TLB misses as the loop runs from beginning to end 4 Exercise C: Integration of VM and caches 41 Read This First This problem asks you to trace some instruction fetches in a computer system that has both virtual memory and caches The computer runs the MIPS instruction set, so all instructions are 32 bits in size Both virtual and physical addresses are 32 bits wide The page size is 4KB There are two TLBs: one for instruction address translations, and one for data address translations The instruction TLB has room for 4 translations There are separate instruction and data caches The instruction cache is directmapped with 4-word blocks, and has a capacity of 256 bytes (The instruction TLB and instruction cache are both unrealistically small in order to make this a viable pencil-and-paper exercise) 42 What to Do Suppose a process attempts to fetch three instructions using the following virtual addresses, in the order given below: 040_0ff8 040_0ffc 040_1010 Suppose that none of the instructions are loads or stores The page table for the process contains the following information: virtual page number valid bit physical page number x900c x900ce x91076
6 ENCM 369 Winter 2016 Lab 11 page 6 of 13 0x x x7ffff 1 0x90fab When the sequence of instruction fetches starts, the following information is in the instruction TLB: virtual page number valid bit physical page number x x900c x x x80000 When the sequence of instruction fetches starts, the following information is in the instruction cache (along with 256 bytes of instructions): set bits valid bit tag 1 0x900c4f 0x1 1 0x900ce0 0x2 1 0x900ce0 0x3 1 0x900c4f 0x4 1 0x900c4f 0x5 1 0x900c4f 0x x x x xa 1 0x xb 1 0x xc 1 0x900c4f 0xd 1 0x900c4f 0xe 1 0x900c4f 0xf 1 0x For each of the three instruction fetches, answer the following questions: Is it a TLB hit or a TLB miss? Or is it not possible to tell with the given information? If it is a TLB miss, does the miss cause a page fault? Is it a cache hit or a cache miss? Or is it not possible to tell with the given information? Also, answer this: Why is it helpful to know that none of the instructions being fetched are loads or stores? 5 Exercise D: Why TLB miss handling must be fast 51 Read This First In programs with good spatial locality of reference, TLB misses will be relatively rare, and handling these misses will not add significantly to running time of the program However, certain important algorithms necessarily have bad spatial locality An example is binary search, which can very quickly find a number in a very large
7 ENCM 369 Winter 2016 Lab 11 page 7 of 13 sorted array of numbers (You do not have to know what binary search is or how it works to do this exercise) This exercise is designed to help you understand the importance of speed in a TLB miss handler in a case where there are frequent TLB misses 52 What to do Here is MIPS assembly language for a key loop within a procedure that performs a version of binary search: L1: srl $t1, $t0, 1 and $t9, $t1, $t8 lw $t3, ($t9) slt $t4, $a0, $t3 movn $a2, $t9, $t4 movz $a1, $t9, $t4 addiu $t5, $a1, 4 sltu $t6, $t5, $a2 bne $t6, $zero, L1 addu $t0, $a1, $a2 Note that it is coded for a true MIPS system with branch delays, so when the branch is taken, the sequence of instructions is bne, then addu, and then srl Question 1 Assume that the code is run on a MIPS processor that uses a simple pipeline that will normally start one instruction per clock cycle In the given loop, if there are no cache misses, one-cycle stalls will be needed only so that the slt instruction can use the lw result, and the the bne instruction can use the sltu result If there are no cache misses or TLB misses, how many clock cycles will it take to run through the loop 20 times? Question 2 To search a particular array of 1 million ints, the loop does in fact run 20 times, and the sequence of virtual data addresses used by the lw instruction is: 0x , 0x102fc6c0, 0x102825a0, 0x , 0x10226cc8, 0x102360ec, 0x1023dafc, 0x10239df4, 0x10237f70, 0x c, 0x c, 0x10236c5c, 0x10236e44, 0x10236f38, 0x10236fb0, 0x10236fec, 0x10236fcc, 0x10236fbc, 0x10236fc4, 0x10236fc8 The VPN for this system is bits of a virtual address Assume that when the loop runs, none of the needed VPN-to-PPN translations for data are in the data TLB, but all of the needed data pages are in physical memory Assume also (very unrealistically) that there are no D-cache misses as a result of any of the loads Finally, assume there are no misses in the instruction TLB or instruction cache If it takes 10 clock cycles to handle a miss in the data TLB, how many clock cycles in total does TLB miss handling add to the answer to Question 1? (This will require some analysis of the sequence of addresses used by the load instruction) Revise your answer, assuming now that it takes 100 cycles to handle a miss in the data TLB Would you say it doesn t matter much whether the TLB miss handler takes 10 or 100 cycles, or would you say that that it has a significant impact on the running time of the loop?
8 ENCM 369 Winter 2016 Lab 11 page 8 of Extra note This problem asks you to think about TLB misses in code that makes data memory accesses with poor spatial locality However, it is important to know that in most real-world cases of bad spatial locality cache misses will tend to cause more performance degradation than TLB misses 6 Exercise E: Page table organization 61 Read This First This exercise is designed to help you understand what a page table is, and what some of the design considerations are in choosing how to organize a page table The details about page table entries (PTEs) and page table organization are a blend of details taken from Section 84 of your textbook, address space and page table management in 32-bit x86 Linux, and 32-bit MIPS TLB miss handling So, put together, the details don t match any real computer system, past or current, but are realistic enough to give some insight about how virtual memory works on real computers We are considering a system with 32-bit virtual addresses, 32-bit physical addresses, and 4KB pages so, as seen in textbook and lecture examples, VPNs (virtual page numbers) and PPNs (physical page numbers) will both be 20 bits wide Our system will use one 32-bit memory word for each PTE: Alloc Valid Dirty Ref 20-bit PPN field The Valid, Ref, and Dirty bits play the same roles as exactly the V-bit described in textbook section 842, and the U-bit and D-bit described in textbook section 845 The purpose of the Alloc bit is to indicate whether or not a virtual page exists at all for a given VPN If a VPN is used to look up a PTE, and that PTE has Alloc=1 and Valid=1, that means the corresponding virtual page is in physical memory with the PPN given within the PTE If that PTE has Alloc=1 and Valid=0, the corresponding virtual page is on disk But if the PTE has Alloc=0, that means there is no virtual page for the given VPN Bits in our PTE format could be used for more status bits, such as writeaccess (does the process have permission to write to the page, or only to read?) or execute-permission (which would indicate whether a process is allowed to fetch instructions from the page) The simplest way to organize a page table is to simply make it a flat table, in other words, just a big array of PTEs, with one PTE for each possible VPN The VPN would be used simply as an array index to find a PTE Let s assume that the range of possible VPNs for a user process runs from 0000 to 0xbffff, which happens to be the range of allowable VPNs for user processes in current 32-bit x86 Linux systems Figure 3 shows an example of such a flat page table for a process with three pages of instructions starting at virtual address 040_0000, two pages of static data starting at virtual address 0x1001_0000, and three pages of stack starting at virtual address 0xbfff_d000 Notice that there are lots of PTEs filled with 0 bits in each of these PTEs bit 23, the Alloc bit, is zero So most of the page table is filled with information that indicates the nonexistence of many, many virtual pages! Let s suppose our computer uses the MIPS instruction set Then in assembly language the TLB miss handler would look something like the code shown in Figure 4
9 ENCM 369 Winter 2016 Lab 11 page 9 of 13 Figure 3: Flat page table PTEs are 32-bit words; in the diagram each nonzero PTE is shown split into a 12-bit status-bit field and a 20-bit PPN field Index 0xbffff 0xbfffe 0xbfffd 0xbfffc 0x x x x1000f ff e 0f 0f 08 0f 0d 0d 0d 0x81f23 0x x x x x86aba 0x9a9a0 0x92777
10 ENCM 369 Winter 2016 Lab 11 page 10 of 13 Figure 4: Sketch of TLB miss handler code for the page table organization of Figure 3 A few special memory management instructions to copy the VPN into $k0 and the base address of the page table into $k1 sll $k0, $k0, 2 # $k0 = VPN * 4 addu $k1, $k1, $k0 # $k1 = address of PTE lw $k1, ($k1) # $k1 = PTE srl $k0, $k0, 2 # restore VPN in $k0 A few more special memory management instructions to inspect the page status bits within the PTE in $k1 and make a quick decision The quick decision made in the second group of special memory management instructions is: If Alloc=1 and Valid=1, quickly update a TLB with information from $k0 and $k1, and restart a user process on whatever instruction caused the TLB miss If Alloc=1 but Valid=0, jump to kernel code to handle a page fault (in other words, get the kernel started on the disk operation needed to get the desired virtual page into physical memory) If Alloc=0, jump to kernel code to deal with an attempted illegal memory access by a user process Note that the MIPS register use conventions prohibit user processes from using GPRs $k0 and $k1 This rule is in place to help optimize TLB miss handlers for speed a miss handler can use those two registers without first saving them to memory to preserve data belonging to a user process Here is an example of how one of the all-zero PTEs in Figure 3 could be used Suppose our computer runs a Linux-like operating system A novice programmer writes a program for it in MIPS assembly language When the program runs as a user process, suppose it happens to be given virtual memory exactly corresponding to the page table shown in Figure 3 Suppose the program contains the instruction lw $t1, ($t0) Unfortunately the program is defective, and when the load instruction is reached, the address in $t0 is 0x1001_2468, which isn t in the set of virtual addresses the program is allowed to use What happens, in detail, is as follows: The VPN of 0x10012 is generated from 0x1001_2468 There is a miss in the data TLB (Make sure you understand why there cannot possibly be a hit!) The TLB miss handler software uses the VPN as an index in the page table, which produces an all-zero PTE in $k1 Because the Alloc bit in the PTE is zero, the TLB miss handler decides that the process has tried to make an illegal memory access, and shuts down the process Our novice programmer is left to figure out why the program died with a segmentation fault error message
11 ENCM 369 Winter 2016 Lab 11 page 11 of What to Do, Part 1 Review the Read This First information, then answer the following questions: For the process whose page table is shown in Figure 3, is the data word at virtual address 0x1001_1400 on disk or in physical memory? If it is in physical memory, what is the physical address for the word? Repeat the previous question, but use 0xbfff_dffc as the virtual address What is the combined size, in KB, of all the instruction, static data, and stack pages in use by the process of Figure 3? What is the size, in KB, of the page table shown in Figure 3? 63 Read This Second I hope you concluded from the last two answers you found in What to Do, Part 1, that the page table was unreasonably huge compared to how much memory was needed for the actual instructions and data of the process This example illustrates the fact that a flat page table is not a practical solution in the case of 32-bit addresses and 4 KB pages In Linux on x86 systems, addresses really are 32 bits wide and pages really are 4 KB in size Page table organization is close to what is shown in Figure 5 on page 12 (I am omitting some complicated details, so I can t say the organization is exactly as shown in the figure) Instead of one huge page table for each process, there are a number of medium-size page tables Part of the VPN is used to find a pointer within an array of pointers; this array of pointers is called a page directory If a valid (non-null) pointer is found in the page directory, that pointer is assumed to point at the base of the page table where the needed PTE is located Details about which bits of the VPN are used for what purposes are given in the caption to Figure 5 64 What to Do, Part 2 Answer the following questions: For the process with the page table information shown in Figure 5, describe how a TLB miss handler would determine that 0x10012 is not a legal VPN For the process whose page table is shown in Figure 5, is the instruction word at virtual address 040_2820 on disk or in physical memory? If it is in physical memory, what is the physical address for the word? Repeat the previous question, but consider the data word at virtual address 0x1001_1454 What is the combined size, in KB, of all the instruction, static data, and stack pages in use by the process of Figure 5? What is the combined size, in KB, of the page directory and the page tables shown in Figure 5? Does this seem reasonable compared to the size of the page table in Figure 3? Consider the TLB miss assembly language code of Figure 4 Replace the sll, addu, lw, and srl instructions with a sequence suitable for searching the page table organization of Figure 5 Pretend that in addition to $k0 and $k1, one more GPR called $k2 is available to hold intermediate results (Hint: Your sequence should be about 8 10 instructions in length, and should include two lw instructions)
12 ENCM 369 Winter 2016 Lab 11 page 12 of 13 Figure 5: Two-level page table structure PTEs have exactly the same format as in Figure 3 Bits of a virtual address (so, bits of the VPN for that virtual address) are used as an index into the page directory array If a non-null pointer is found in the page directory, that pointer is used as the base address of a 1024-word page table, and bits of the virtual address (so, bits 9 0 of the VPN for that virtual address) are used as an index into that page table (Note: Translations for the process of this figure are not the same as translations for the process with the page table of Figure 3) Page table 0e 0x e 0x84dfe 0f 0x91f01 Index 0x3ff 0x3fe 0x3fd 00 Index 0x2ff 0x2fe f Page directory Page table 0d 0f 0x88a62 0x9000e Index 0x3ff f Page table 0d 0x81fff 08 0x d 0x8a8a5 Index 0x3ff
13 ENCM 369 Winter 2016 Lab 11 page 13 of More notes about page table organization Real 32-bit MIPS systems use an efficient but somewhat hard-to-explain system for page tables that is not a two-level organization 32-bit x86 systems have a two-level page table organization much like what is presented in this exercise, but routine TLB miss handling is not done by kernel software instead special hardware is dedicated to fast searches for PTEs within page tables (However, if there is a miss in the page table after a miss in a TLB, then kernel software will have to manage the problem)
Slide Set 9. for ENCM 369 Winter 2018 Section 01. Steve Norman, PhD, PEng
 Slide Set 9 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
Slide Set 9 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
Winter 2009 FINAL EXAMINATION Location: Engineering A Block, Room 201 Saturday, April 25 noon to 3:00pm
 University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Lecture Instructors: S. A. Norman (L01), N. R. Bartley (L02) Winter 2009 FINAL EXAMINATION Location:
University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Lecture Instructors: S. A. Norman (L01), N. R. Bartley (L02) Winter 2009 FINAL EXAMINATION Location:
ENCM 369 Winter 2019 Lab 6 for the Week of February 25
 page of ENCM 369 Winter 29 Lab 6 for the Week of February 25 Steve Norman Department of Electrical & Computer Engineering University of Calgary February 29 Lab instructions and other documents for ENCM
page of ENCM 369 Winter 29 Lab 6 for the Week of February 25 Steve Norman Department of Electrical & Computer Engineering University of Calgary February 29 Lab instructions and other documents for ENCM
ENCM 369 Winter 2018 Lab 9 for the Week of March 19
 page 1 of 9 ENCM 369 Winter 2018 Lab 9 for the Week of March 19 Steve Norman Department of Electrical & Computer Engineering University of Calgary March 2018 Lab instructions and other documents for ENCM
page 1 of 9 ENCM 369 Winter 2018 Lab 9 for the Week of March 19 Steve Norman Department of Electrical & Computer Engineering University of Calgary March 2018 Lab instructions and other documents for ENCM
Slide Set 5. for ENCM 501 in Winter Term, Steve Norman, PhD, PEng
 Slide Set 5 for ENCM 501 in Winter Term, 2017 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2017 ENCM 501 W17 Lectures: Slide
Slide Set 5 for ENCM 501 in Winter Term, 2017 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2017 ENCM 501 W17 Lectures: Slide
Changelog. Virtual Memory (2) exercise: 64-bit system. exercise: 64-bit system
 Changelog Virtual Memory (2) Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Changelog Virtual Memory (2) Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Virtual Memory (2) 1
 Virtual Memory (2) 1 Changelog 1 Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Virtual Memory (2) 1 Changelog 1 Changes made in this version not seen in first lecture: 21 November 2017: 1-level example: added final answer of memory value, not just location 21 November 2017: two-level
Contents. Slide Set 1. About these slides. Outline of Slide Set 1. Typographical conventions: Italics. Typographical conventions. About these slides
 Slide Set 1 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
Slide Set 1 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructor: Steve Norman
 page of 9 University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructor: Steve Norman Winter 26 FINAL EXAMINATION (with corrections) Location: ICT 2
page of 9 University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructor: Steve Norman Winter 26 FINAL EXAMINATION (with corrections) Location: ICT 2
ENCM 501 Winter 2017 Assignment 6 for the Week of February 27
 page of 8 ENCM 5 Winter 27 Assignment 6 for the Week of February 27 Steve Norman Department of Electrical & Computer Engineering University of Calgary February 27 Assignment instructions and other documents
page of 8 ENCM 5 Winter 27 Assignment 6 for the Week of February 27 Steve Norman Department of Electrical & Computer Engineering University of Calgary February 27 Assignment instructions and other documents
Virtual Memory 1. Virtual Memory
 Virtual Memory 1 Virtual Memory key concepts virtual memory, physical memory, address translation, MMU, TLB, relocation, paging, segmentation, executable file, swapping, page fault, locality, page replacement
Virtual Memory 1 Virtual Memory key concepts virtual memory, physical memory, address translation, MMU, TLB, relocation, paging, segmentation, executable file, swapping, page fault, locality, page replacement
Virtual Memory 1. Virtual Memory
 Virtual Memory 1 Virtual Memory key concepts virtual memory, physical memory, address translation, MMU, TLB, relocation, paging, segmentation, executable file, swapping, page fault, locality, page replacement
Virtual Memory 1 Virtual Memory key concepts virtual memory, physical memory, address translation, MMU, TLB, relocation, paging, segmentation, executable file, swapping, page fault, locality, page replacement
ECE331 Homework 4. Due Monday, August 13, 2018 (via Moodle)
 ECE331 Homework 4 Due Monday, August 13, 2018 (via Moodle) 1. Below is a list of 32-bit memory address references, given as hexadecimal byte addresses. The memory accesses are all reads and they occur
ECE331 Homework 4 Due Monday, August 13, 2018 (via Moodle) 1. Below is a list of 32-bit memory address references, given as hexadecimal byte addresses. The memory accesses are all reads and they occur
CSE 378 Final Exam 3/14/11 Sample Solution
 Name There are 8 questions worth a total of 100 points. Please budget your time so you get to all of the questions don t miss the short questions at the end. Keep your answers brief and to the point. Copies
Name There are 8 questions worth a total of 100 points. Please budget your time so you get to all of the questions don t miss the short questions at the end. Keep your answers brief and to the point. Copies
Slide Set 5. for ENCM 369 Winter 2014 Lecture Section 01. Steve Norman, PhD, PEng
 Slide Set 5 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
Slide Set 5 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
Exercises 6 - Virtual vs. Physical Memory, Cache
 Questions 1. Consider a (very old!) computer with a hard disk of only 1 GB, main memory of 16 MB, and a cache with 512 blocks of 8 words each. Suppose the hard disk and main memory are partitioned into
Questions 1. Consider a (very old!) computer with a hard disk of only 1 GB, main memory of 16 MB, and a cache with 512 blocks of 8 words each. Suppose the hard disk and main memory are partitioned into
Virtual Memory. CS 3410 Computer System Organization & Programming. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon]
![Virtual Memory. CS 3410 Computer System Organization & Programming. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Virtual Memory. CS 3410 Computer System Organization & Programming. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon]](/thumbs/92/108243603.jpg) Virtual Memory CS 3410 Computer System Organization & Programming [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Click any letter let me know you re here today. Instead of a DJ Clicker Question today,
Virtual Memory CS 3410 Computer System Organization & Programming [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Click any letter let me know you re here today. Instead of a DJ Clicker Question today,
Memory Hierarchy. Mehran Rezaei
 Memory Hierarchy Mehran Rezaei What types of memory do we have? Registers Cache (Static RAM) Main Memory (Dynamic RAM) Disk (Magnetic Disk) Option : Build It Out of Fast SRAM About 5- ns access Decoders
Memory Hierarchy Mehran Rezaei What types of memory do we have? Registers Cache (Static RAM) Main Memory (Dynamic RAM) Disk (Magnetic Disk) Option : Build It Out of Fast SRAM About 5- ns access Decoders
Faculty of Science FINAL EXAMINATION
 Faculty of Science FINAL EXAMINATION COMPUTER SCIENCE COMP 273 INTRODUCTION TO COMPUTER SYSTEMS Examiner: Prof. Michael Langer April 18, 2012 Associate Examiner: Mr. Joseph Vybihal 2 P.M. 5 P.M. STUDENT
Faculty of Science FINAL EXAMINATION COMPUTER SCIENCE COMP 273 INTRODUCTION TO COMPUTER SYSTEMS Examiner: Prof. Michael Langer April 18, 2012 Associate Examiner: Mr. Joseph Vybihal 2 P.M. 5 P.M. STUDENT
CS 61 Section Notes 5
 CS 61 Section Notes 5 (Week of 10/22-10/26) Topics: Dangerous Instructions and Process Isolation Virtual Memory Memory Mapping Address Translation Some numbers Some Terms Processes and Fork What is a process?
CS 61 Section Notes 5 (Week of 10/22-10/26) Topics: Dangerous Instructions and Process Isolation Virtual Memory Memory Mapping Address Translation Some numbers Some Terms Processes and Fork What is a process?
Slides for Lecture 15
 Slides for Lecture 15 ENCM 501: Principles of Computer Architecture Winter 2014 Term Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 6 March,
Slides for Lecture 15 ENCM 501: Principles of Computer Architecture Winter 2014 Term Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 6 March,
Slide Set 3. for ENCM 369 Winter 2018 Section 01. Steve Norman, PhD, PEng
 Slide Set 3 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary January 2018 ENCM 369 Winter 2018 Section
Slide Set 3 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary January 2018 ENCM 369 Winter 2018 Section
ENCM 369 Winter 2017 Lab 3 for the Week of January 30
 page 1 of 11 ENCM 369 Winter 2017 Lab 3 for the Week of January 30 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2017 Lab instructions and other documents for
page 1 of 11 ENCM 369 Winter 2017 Lab 3 for the Week of January 30 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2017 Lab instructions and other documents for
Virtual Memory Overview
 Virtual Memory Overview Virtual address (VA): What your program uses Virtual Page Number Page Offset Physical address (PA): What actually determines where in memory to go Physical Page Number Page Offset
Virtual Memory Overview Virtual address (VA): What your program uses Virtual Page Number Page Offset Physical address (PA): What actually determines where in memory to go Physical Page Number Page Offset
Winter 2002 FINAL EXAMINATION
 University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructors: Dr. S. A. Norman (L01) and Dr. S. Yanushkevich (L02) Note for Winter 2005 students Winter
University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Instructors: Dr. S. A. Norman (L01) and Dr. S. Yanushkevich (L02) Note for Winter 2005 students Winter
Slide Set 1 (corrected)
 Slide Set 1 (corrected) for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary January 2018 ENCM 369 Winter 2018
Slide Set 1 (corrected) for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary January 2018 ENCM 369 Winter 2018
Contents Slide Set 9. Final Notes on Textbook Chapter 7. Outline of Slide Set 9. More about skipped sections in Chapter 7. Outline of Slide Set 9
 slide 2/41 Contents Slide Set 9 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014
slide 2/41 Contents Slide Set 9 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014
Contents. Slide Set 2. Outline of Slide Set 2. More about Pseudoinstructions. Avoid using pseudoinstructions in ENCM 369 labs
 Slide Set 2 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
Slide Set 2 for ENCM 369 Winter 2014 Lecture Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2014 ENCM 369 W14 Section
Virtual Memory. CS 3410 Computer System Organization & Programming
 Virtual Memory CS 3410 Computer System Organization & Programming These slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. Where are we now and
Virtual Memory CS 3410 Computer System Organization & Programming These slides are the product of many rounds of teaching CS 3410 by Professors Weatherspoon, Bala, Bracy, and Sirer. Where are we now and
Slide Set 8. for ENCM 369 Winter 2018 Section 01. Steve Norman, PhD, PEng
 Slide Set 8 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
Slide Set 8 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 369 Winter 2018 Section 01
Winter 2006 FINAL EXAMINATION Auxiliary Gymnasium Tuesday, April 18 7:00pm to 10:00pm
 University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Lecture Instructor for L01 and L02: Dr. S. A. Norman Winter 2006 FINAL EXAMINATION Auxiliary Gymnasium
University of Calgary Department of Electrical and Computer Engineering ENCM 369: Computer Organization Lecture Instructor for L01 and L02: Dr. S. A. Norman Winter 2006 FINAL EXAMINATION Auxiliary Gymnasium
(Refer Slide Time: 01:25)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
ENCM 501 Winter 2016 Assignment 1 for the Week of January 25
 page 1 of 5 ENCM 501 Winter 2016 Assignment 1 for the Week of January 25 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2016 Assignment instructions and other
page 1 of 5 ENCM 501 Winter 2016 Assignment 1 for the Week of January 25 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2016 Assignment instructions and other
Virtual Memory. Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. November 15, MIT Fall 2018 L20-1
 Virtual Memory Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. L20-1 Reminder: Operating Systems Goals of OS: Protection and privacy: Processes cannot access each other s data Abstraction:
Virtual Memory Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. L20-1 Reminder: Operating Systems Goals of OS: Protection and privacy: Processes cannot access each other s data Abstraction:
ENCM 501 Winter 2017 Assignment 3 for the Week of January 30
 page 1 of 7 ENCM 501 Winter 2017 Assignment 3 for the Week of January 30 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2017 Assignment instructions and other
page 1 of 7 ENCM 501 Winter 2017 Assignment 3 for the Week of January 30 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2017 Assignment instructions and other
Virtual Memory. Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. April 12, 2018 L16-1
 Virtual Memory Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. L16-1 Reminder: Operating Systems Goals of OS: Protection and privacy: Processes cannot access each other s data Abstraction:
Virtual Memory Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. L16-1 Reminder: Operating Systems Goals of OS: Protection and privacy: Processes cannot access each other s data Abstraction:
6.004 Tutorial Problems L20 Virtual Memory
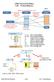 6.004 Tutorial Problems L20 Virtual Memory Page Table (v + p) bits in virtual address (m + p) bits in physical address 2 v number of virtual pages 2 m number of physical pages 2 p bytes per physical page
6.004 Tutorial Problems L20 Virtual Memory Page Table (v + p) bits in virtual address (m + p) bits in physical address 2 v number of virtual pages 2 m number of physical pages 2 p bytes per physical page
Slides for Lecture 6
 Slides for Lecture 6 ENCM 501: Principles of Computer Architecture Winter 2014 Term Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 28 January,
Slides for Lecture 6 ENCM 501: Principles of Computer Architecture Winter 2014 Term Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 28 January,
198:231 Intro to Computer Organization. 198:231 Introduction to Computer Organization Lecture 14
 98:23 Intro to Computer Organization Lecture 4 Virtual Memory 98:23 Introduction to Computer Organization Lecture 4 Instructor: Nicole Hynes nicole.hynes@rutgers.edu Credits: Several slides courtesy of
98:23 Intro to Computer Organization Lecture 4 Virtual Memory 98:23 Introduction to Computer Organization Lecture 4 Instructor: Nicole Hynes nicole.hynes@rutgers.edu Credits: Several slides courtesy of
COSC3330 Computer Architecture Lecture 20. Virtual Memory
 COSC3330 Computer Architecture Lecture 20. Virtual Memory Instructor: Weidong Shi (Larry), PhD Computer Science Department University of Houston Virtual Memory Topics Reducing Cache Miss Penalty (#2) Use
COSC3330 Computer Architecture Lecture 20. Virtual Memory Instructor: Weidong Shi (Larry), PhD Computer Science Department University of Houston Virtual Memory Topics Reducing Cache Miss Penalty (#2) Use
ENCM 369 Winter 2015 Lab 6 for the Week of March 2
 page of 2 ENCM 369 Winter 25 Lab 6 for the Week of March 2 Steve Norman Department of Electrical & Computer Engineering University of Calgary February 25 Lab instructions and other documents for ENCM 369
page of 2 ENCM 369 Winter 25 Lab 6 for the Week of March 2 Steve Norman Department of Electrical & Computer Engineering University of Calgary February 25 Lab instructions and other documents for ENCM 369
Address spaces and memory management
 Address spaces and memory management Review of processes Process = one or more threads in an address space Thread = stream of executing instructions Address space = memory space used by threads Address
Address spaces and memory management Review of processes Process = one or more threads in an address space Thread = stream of executing instructions Address space = memory space used by threads Address
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1
 CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
Pipelining Exercises, Continued
 Pipelining Exercises, Continued. Spot all data dependencies (including ones that do not lead to stalls). Draw arrows from the stages where data is made available, directed to where it is needed. Circle
Pipelining Exercises, Continued. Spot all data dependencies (including ones that do not lead to stalls). Draw arrows from the stages where data is made available, directed to where it is needed. Circle
Virtual Memory Worksheet
 Virtual Memory Worksheet (v + p) bits in virtual address (m + p) bits in physical address 2 v number of virtual pages 2 m number of physical pages 2 p bytes per physical page 2 v+p bytes in virtual memory
Virtual Memory Worksheet (v + p) bits in virtual address (m + p) bits in physical address 2 v number of virtual pages 2 m number of physical pages 2 p bytes per physical page 2 v+p bytes in virtual memory
ENCM 501 Winter 2018 Assignment 2 for the Week of January 22 (with corrections)
 page 1 of 5 ENCM 501 Winter 2018 Assignment 2 for the Week of January 22 (with corrections) Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2018 Assignment instructions
page 1 of 5 ENCM 501 Winter 2018 Assignment 2 for the Week of January 22 (with corrections) Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2018 Assignment instructions
Virtual Memory: From Address Translation to Demand Paging
 Constructive Computer Architecture Virtual Memory: From Address Translation to Demand Paging Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 12, 2014
Constructive Computer Architecture Virtual Memory: From Address Translation to Demand Paging Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 12, 2014
ENCM 501 Winter 2015 Assignment 3 for the Week of February 2
 page 1 of 6 ENCM 501 Winter 2015 Assignment 3 for the Week of February 2 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2015 Assignment instructions and other
page 1 of 6 ENCM 501 Winter 2015 Assignment 3 for the Week of February 2 Steve Norman Department of Electrical & Computer Engineering University of Calgary January 2015 Assignment instructions and other
Chapter 8 :: Topics. Chapter 8 :: Memory Systems. Introduction Memory System Performance Analysis Caches Virtual Memory Memory-Mapped I/O Summary
 Chapter 8 :: Systems Chapter 8 :: Topics Digital Design and Computer Architecture David Money Harris and Sarah L. Harris Introduction System Performance Analysis Caches Virtual -Mapped I/O Summary Copyright
Chapter 8 :: Systems Chapter 8 :: Topics Digital Design and Computer Architecture David Money Harris and Sarah L. Harris Introduction System Performance Analysis Caches Virtual -Mapped I/O Summary Copyright
Recall: Address Space Map. 13: Memory Management. Let s be reasonable. Processes Address Space. Send it to disk. Freeing up System Memory
 Recall: Address Space Map 13: Memory Management Biggest Virtual Address Stack (Space for local variables etc. For each nested procedure call) Sometimes Reserved for OS Stack Pointer Last Modified: 6/21/2004
Recall: Address Space Map 13: Memory Management Biggest Virtual Address Stack (Space for local variables etc. For each nested procedure call) Sometimes Reserved for OS Stack Pointer Last Modified: 6/21/2004
EN1640: Design of Computing Systems Topic 06: Memory System
 EN164: Design of Computing Systems Topic 6: Memory System Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University Spring
EN164: Design of Computing Systems Topic 6: Memory System Professor Sherief Reda http://scale.engin.brown.edu Electrical Sciences and Computer Engineering School of Engineering Brown University Spring
CS161 Design and Architecture of Computer Systems. Cache $$$$$
 CS161 Design and Architecture of Computer Systems Cache $$$$$ Memory Systems! How can we supply the CPU with enough data to keep it busy?! We will focus on memory issues,! which are frequently bottlenecks
CS161 Design and Architecture of Computer Systems Cache $$$$$ Memory Systems! How can we supply the CPU with enough data to keep it busy?! We will focus on memory issues,! which are frequently bottlenecks
ENCM 501 Winter 2015 Tutorial for Week 5
 ENCM 501 Winter 2015 Tutorial for Week 5 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 11 February, 2015 ENCM 501 Tutorial 11 Feb 2015 slide
ENCM 501 Winter 2015 Tutorial for Week 5 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary 11 February, 2015 ENCM 501 Tutorial 11 Feb 2015 slide
Simple idea 1: load-time linking. Our main questions. Some terminology. Simple idea 2: base + bound register. Protection mechanics.
 Our main questions! How is protection enforced?! How are processes relocated?! How is ory partitioned? Simple idea 1: load-time linking! Link as usual, but keep the list of references! At load time, determine
Our main questions! How is protection enforced?! How are processes relocated?! How is ory partitioned? Simple idea 1: load-time linking! Link as usual, but keep the list of references! At load time, determine
CS 537: Introduction to Operating Systems Fall 2016: Midterm Exam #1. All cell phones must be turned off and put away.
 CS 537: Introduction to Operating Systems Fall 2016: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off and put away. No calculators may be used. You have two hours
CS 537: Introduction to Operating Systems Fall 2016: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off and put away. No calculators may be used. You have two hours
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1
 CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
Slide Set 7. for ENCM 501 in Winter Term, Steve Norman, PhD, PEng
 Slide Set 7 for ENCM 501 in Winter Term, 2017 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2017 ENCM 501 W17 Lectures: Slide
Slide Set 7 for ENCM 501 in Winter Term, 2017 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary Winter Term, 2017 ENCM 501 W17 Lectures: Slide
Chapter 3 - Memory Management
 Chapter 3 - Memory Management Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 3 - Memory Management 1 / 222 1 A Memory Abstraction: Address Spaces The Notion of an Address Space Swapping
Chapter 3 - Memory Management Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 3 - Memory Management 1 / 222 1 A Memory Abstraction: Address Spaces The Notion of an Address Space Swapping
CS 61C: Great Ideas in Computer Architecture. Virtual Memory
 CS 61C: Great Ideas in Computer Architecture Virtual Memory Instructor: Justin Hsia 7/30/2012 Summer 2012 Lecture #24 1 Review of Last Lecture (1/2) Multiple instruction issue increases max speedup, but
CS 61C: Great Ideas in Computer Architecture Virtual Memory Instructor: Justin Hsia 7/30/2012 Summer 2012 Lecture #24 1 Review of Last Lecture (1/2) Multiple instruction issue increases max speedup, but
Memory Hierarchies &
 Memory Hierarchies & Cache Memory CSE 410, Spring 2009 Computer Systems http://www.cs.washington.edu/410 4/26/2009 cse410-13-cache 2006-09 Perkins, DW Johnson and University of Washington 1 Reading and
Memory Hierarchies & Cache Memory CSE 410, Spring 2009 Computer Systems http://www.cs.washington.edu/410 4/26/2009 cse410-13-cache 2006-09 Perkins, DW Johnson and University of Washington 1 Reading and
CS162 Operating Systems and Systems Programming Lecture 14. Caching (Finished), Demand Paging
 CS162 Operating Systems and Systems Programming Lecture 14 Caching (Finished), Demand Paging October 11 th, 2017 Neeraja J. Yadwadkar http://cs162.eecs.berkeley.edu Recall: Caching Concept Cache: a repository
CS162 Operating Systems and Systems Programming Lecture 14 Caching (Finished), Demand Paging October 11 th, 2017 Neeraja J. Yadwadkar http://cs162.eecs.berkeley.edu Recall: Caching Concept Cache: a repository
Module 2: Virtual Memory and Caches Lecture 3: Virtual Memory and Caches. The Lecture Contains:
 The Lecture Contains: Program Optimization for Multi-core: Hardware Side of It Contents RECAP: VIRTUAL MEMORY AND CACHE Why Virtual Memory? Virtual Memory Addressing VM VA to PA Translation Page Fault
The Lecture Contains: Program Optimization for Multi-core: Hardware Side of It Contents RECAP: VIRTUAL MEMORY AND CACHE Why Virtual Memory? Virtual Memory Addressing VM VA to PA Translation Page Fault
John Wawrzynek & Nick Weaver
 CS 61C: Great Ideas in Computer Architecture Lecture 23: Virtual Memory John Wawrzynek & Nick Weaver http://inst.eecs.berkeley.edu/~cs61c From Previous Lecture: Operating Systems Input / output (I/O) Memory
CS 61C: Great Ideas in Computer Architecture Lecture 23: Virtual Memory John Wawrzynek & Nick Weaver http://inst.eecs.berkeley.edu/~cs61c From Previous Lecture: Operating Systems Input / output (I/O) Memory
CS252 S05. Main memory management. Memory hardware. The scale of things. Memory hardware (cont.) Bottleneck
 Main memory management CMSC 411 Computer Systems Architecture Lecture 16 Memory Hierarchy 3 (Main Memory & Memory) Questions: How big should main memory be? How to handle reads and writes? How to find
Main memory management CMSC 411 Computer Systems Architecture Lecture 16 Memory Hierarchy 3 (Main Memory & Memory) Questions: How big should main memory be? How to handle reads and writes? How to find
CSE 153 Design of Operating Systems
 CSE 53 Design of Operating Systems Winter 28 Lecture 6: Paging/Virtual Memory () Some slides modified from originals by Dave O hallaron Today Address spaces VM as a tool for caching VM as a tool for memory
CSE 53 Design of Operating Systems Winter 28 Lecture 6: Paging/Virtual Memory () Some slides modified from originals by Dave O hallaron Today Address spaces VM as a tool for caching VM as a tool for memory
Section 7: Wait/Exit, Address Translation
 William Liu October 15, 2014 Contents 1 Wait and Exit 2 1.1 Thinking about what you need to do.............................. 2 1.2 Code................................................ 2 2 Vocabulary 4
William Liu October 15, 2014 Contents 1 Wait and Exit 2 1.1 Thinking about what you need to do.............................. 2 1.2 Code................................................ 2 2 Vocabulary 4
Embedded Systems Dr. Santanu Chaudhury Department of Electrical Engineering Indian Institute of Technology, Delhi
 Embedded Systems Dr. Santanu Chaudhury Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 13 Virtual memory and memory management unit In the last class, we had discussed
Embedded Systems Dr. Santanu Chaudhury Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 13 Virtual memory and memory management unit In the last class, we had discussed
Welcome to Part 3: Memory Systems and I/O
 Welcome to Part 3: Memory Systems and I/O We ve already seen how to make a fast processor. How can we supply the CPU with enough data to keep it busy? We will now focus on memory issues, which are frequently
Welcome to Part 3: Memory Systems and I/O We ve already seen how to make a fast processor. How can we supply the CPU with enough data to keep it busy? We will now focus on memory issues, which are frequently
HY225 Lecture 12: DRAM and Virtual Memory
 HY225 Lecture 12: DRAM and irtual Memory Dimitrios S. Nikolopoulos University of Crete and FORTH-ICS May 16, 2011 Dimitrios S. Nikolopoulos Lecture 12: DRAM and irtual Memory 1 / 36 DRAM Fundamentals Random-access
HY225 Lecture 12: DRAM and irtual Memory Dimitrios S. Nikolopoulos University of Crete and FORTH-ICS May 16, 2011 Dimitrios S. Nikolopoulos Lecture 12: DRAM and irtual Memory 1 / 36 DRAM Fundamentals Random-access
Digital Logic & Computer Design CS Professor Dan Moldovan Spring Copyright 2007 Elsevier 8-<1>
 Digital Logic & Computer Design CS 4341 Professor Dan Moldovan Spring 21 Copyright 27 Elsevier 8- Chapter 8 :: Memory Systems Digital Design and Computer Architecture David Money Harris and Sarah L.
Digital Logic & Computer Design CS 4341 Professor Dan Moldovan Spring 21 Copyright 27 Elsevier 8- Chapter 8 :: Memory Systems Digital Design and Computer Architecture David Money Harris and Sarah L.
ECE 571 Advanced Microprocessor-Based Design Lecture 13
 ECE 571 Advanced Microprocessor-Based Design Lecture 13 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 21 March 2017 Announcements More on HW#6 When ask for reasons why cache
ECE 571 Advanced Microprocessor-Based Design Lecture 13 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 21 March 2017 Announcements More on HW#6 When ask for reasons why cache
Computer System Architecture Midterm Examination Spring 2002
 Computer System Architecture 6.823 Midterm Examination Spring 2002 Name: This is an open book, open notes exam. 110 Minutes 1 Pages Notes: Not all questions are of equal difficulty, so look over the entire
Computer System Architecture 6.823 Midterm Examination Spring 2002 Name: This is an open book, open notes exam. 110 Minutes 1 Pages Notes: Not all questions are of equal difficulty, so look over the entire
Agenda. CS 61C: Great Ideas in Computer Architecture. Virtual Memory II. Goals of Virtual Memory. Memory Hierarchy Requirements
 CS 61C: Great Ideas in Computer Architecture Virtual II Guest Lecturer: Justin Hsia Agenda Review of Last Lecture Goals of Virtual Page Tables Translation Lookaside Buffer (TLB) Administrivia VM Performance
CS 61C: Great Ideas in Computer Architecture Virtual II Guest Lecturer: Justin Hsia Agenda Review of Last Lecture Goals of Virtual Page Tables Translation Lookaside Buffer (TLB) Administrivia VM Performance
CSE 141 Spring 2016 Homework 5 PID: Name: 1. Consider the following matrix transpose code int i, j,k; double *A, *B, *C; A = (double
 CSE 141 Spring 2016 Homework 5 PID: Name: 1. Consider the following matrix transpose code int i, j,k; double *A, *B, *C; A = (double *)malloc(sizeof(double)*n*n); B = (double *)malloc(sizeof(double)*n*n);
CSE 141 Spring 2016 Homework 5 PID: Name: 1. Consider the following matrix transpose code int i, j,k; double *A, *B, *C; A = (double *)malloc(sizeof(double)*n*n); B = (double *)malloc(sizeof(double)*n*n);
Computer Architecture CS372 Exam 3
 Name: Computer Architecture CS372 Exam 3 This exam has 7 pages. Please make sure you have all of them. Write your name on this page and initials on every other page now. You may only use the green card
Name: Computer Architecture CS372 Exam 3 This exam has 7 pages. Please make sure you have all of them. Write your name on this page and initials on every other page now. You may only use the green card
Virtual memory Paging
 Virtual memory Paging M1 MOSIG Operating System Design Renaud Lachaize Acknowledgments Many ideas and slides in these lectures were inspired by or even borrowed from the work of others: Arnaud Legrand,
Virtual memory Paging M1 MOSIG Operating System Design Renaud Lachaize Acknowledgments Many ideas and slides in these lectures were inspired by or even borrowed from the work of others: Arnaud Legrand,
Virtual Memory. Patterson & Hennessey Chapter 5 ELEC 5200/6200 1
 Virtual Memory Patterson & Hennessey Chapter 5 ELEC 5200/6200 1 Virtual Memory Use main memory as a cache for secondary (disk) storage Managed jointly by CPU hardware and the operating system (OS) Programs
Virtual Memory Patterson & Hennessey Chapter 5 ELEC 5200/6200 1 Virtual Memory Use main memory as a cache for secondary (disk) storage Managed jointly by CPU hardware and the operating system (OS) Programs
Structure of Computer Systems
 222 Structure of Computer Systems Figure 4.64 shows how a page directory can be used to map linear addresses to 4-MB pages. The entries in the page directory point to page tables, and the entries in a
222 Structure of Computer Systems Figure 4.64 shows how a page directory can be used to map linear addresses to 4-MB pages. The entries in the page directory point to page tables, and the entries in a
CS162 Operating Systems and Systems Programming Lecture 14. Caching and Demand Paging
 CS162 Operating Systems and Systems Programming Lecture 14 Caching and Demand Paging October 17, 2007 Prof. John Kubiatowicz http://inst.eecs.berkeley.edu/~cs162 Review: Hierarchy of a Modern Computer
CS162 Operating Systems and Systems Programming Lecture 14 Caching and Demand Paging October 17, 2007 Prof. John Kubiatowicz http://inst.eecs.berkeley.edu/~cs162 Review: Hierarchy of a Modern Computer
Slide Set 5. for ENCM 369 Winter 2018 Section 01. Steve Norman, PhD, PEng
 Slide Set 5 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary February 2018 ENCM 369 Winter 2018 Section
Slide Set 5 for ENCM 369 Winter 2018 Section 01 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary February 2018 ENCM 369 Winter 2018 Section
ECE 571 Advanced Microprocessor-Based Design Lecture 12
 ECE 571 Advanced Microprocessor-Based Design Lecture 12 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 1 March 2018 HW#6 will be posted Project will be coming up Announcements
ECE 571 Advanced Microprocessor-Based Design Lecture 12 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 1 March 2018 HW#6 will be posted Project will be coming up Announcements
Virtual Memory. Reading. Sections 5.4, 5.5, 5.6, 5.8, 5.10 (2) Lecture notes from MKP and S. Yalamanchili
 Virtual Memory Lecture notes from MKP and S. Yalamanchili Sections 5.4, 5.5, 5.6, 5.8, 5.10 Reading (2) 1 The Memory Hierarchy ALU registers Cache Memory Memory Memory Managed by the compiler Memory Managed
Virtual Memory Lecture notes from MKP and S. Yalamanchili Sections 5.4, 5.5, 5.6, 5.8, 5.10 Reading (2) 1 The Memory Hierarchy ALU registers Cache Memory Memory Memory Managed by the compiler Memory Managed
CS 61C: Great Ideas in Computer Architecture. Lecture 23: Virtual Memory. Bernhard Boser & Randy Katz
 CS 61C: Great Ideas in Computer Architecture Lecture 23: Virtual Memory Bernhard Boser & Randy Katz http://inst.eecs.berkeley.edu/~cs61c Agenda Virtual Memory Paged Physical Memory Swap Space Page Faults
CS 61C: Great Ideas in Computer Architecture Lecture 23: Virtual Memory Bernhard Boser & Randy Katz http://inst.eecs.berkeley.edu/~cs61c Agenda Virtual Memory Paged Physical Memory Swap Space Page Faults
CS 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring Lecture 13: Address Translation
 CS 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring 2004 Lecture 13: Address Translation 13.0 Main Points 13.1 Hardware Translation Overview CPU Virtual Address Translation
CS 162 Operating Systems and Systems Programming Professor: Anthony D. Joseph Spring 2004 Lecture 13: Address Translation 13.0 Main Points 13.1 Hardware Translation Overview CPU Virtual Address Translation
ENGN 2910A Homework 03 (140 points) Due Date: Oct 3rd 2013
 ENGN 2910A Homework 03 (140 points) Due Date: Oct 3rd 2013 Professor: Sherief Reda School of Engineering, Brown University 1. [from Debois et al. 30 points] Consider the non-pipelined implementation of
ENGN 2910A Homework 03 (140 points) Due Date: Oct 3rd 2013 Professor: Sherief Reda School of Engineering, Brown University 1. [from Debois et al. 30 points] Consider the non-pipelined implementation of
Question 13 1: (Solution, p 4) Describe the inputs and outputs of a (1-way) demultiplexer, and how they relate.
 Questions 1 Question 13 1: (Solution, p ) Describe the inputs and outputs of a (1-way) demultiplexer, and how they relate. Question 13 : (Solution, p ) In implementing HYMN s control unit, the fetch cycle
Questions 1 Question 13 1: (Solution, p ) Describe the inputs and outputs of a (1-way) demultiplexer, and how they relate. Question 13 : (Solution, p ) In implementing HYMN s control unit, the fetch cycle
CS 61C: Great Ideas in Computer Architecture. Lecture 23: Virtual Memory
 CS 61C: Great Ideas in Computer Architecture Lecture 23: Virtual Memory Krste Asanović & Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 1 Agenda Virtual Memory Paged Physical Memory Swap Space
CS 61C: Great Ideas in Computer Architecture Lecture 23: Virtual Memory Krste Asanović & Randy H. Katz http://inst.eecs.berkeley.edu/~cs61c/fa17 1 Agenda Virtual Memory Paged Physical Memory Swap Space
Virtual Memory 3. Hakim Weatherspoon CS 3410, Spring 2012 Computer Science Cornell University. P & H Chapter 5.4
 Virtual Memory 3 Hakim Weatherspoon CS 3410, Spring 2012 Computer Science Cornell University P & H Chapter 5.4 Project3 available now Administrivia Design Doc due next week, Monday, April 16 th Schedule
Virtual Memory 3 Hakim Weatherspoon CS 3410, Spring 2012 Computer Science Cornell University P & H Chapter 5.4 Project3 available now Administrivia Design Doc due next week, Monday, April 16 th Schedule
Slide Set 8. for ENCM 501 in Winter Steve Norman, PhD, PEng
 Slide Set 8 for ENCM 501 in Winter 2018 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 501 Winter 2018 Slide Set 8 slide
Slide Set 8 for ENCM 501 in Winter 2018 Steve Norman, PhD, PEng Electrical & Computer Engineering Schulich School of Engineering University of Calgary March 2018 ENCM 501 Winter 2018 Slide Set 8 slide
CS24: INTRODUCTION TO COMPUTING SYSTEMS. Spring 2015 Lecture 23
 CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 205 Lecture 23 LAST TIME: VIRTUAL MEMORY! Began to focus on how to virtualize memory! Instead of directly addressing physical memory, introduce a level of
CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 205 Lecture 23 LAST TIME: VIRTUAL MEMORY! Began to focus on how to virtualize memory! Instead of directly addressing physical memory, introduce a level of
registers data 1 registers MEMORY ADDRESS on-chip cache off-chip cache main memory: real address space part of virtual addr. sp.
 Cache associativity Cache and performance 12 1 CMPE110 Spring 2005 A. Di Blas 110 Spring 2005 CMPE Cache Direct-mapped cache Reads and writes Textbook Edition: 7.1 to 7.3 Second Third Edition: 7.1 to 7.3
Cache associativity Cache and performance 12 1 CMPE110 Spring 2005 A. Di Blas 110 Spring 2005 CMPE Cache Direct-mapped cache Reads and writes Textbook Edition: 7.1 to 7.3 Second Third Edition: 7.1 to 7.3
Carnegie Mellon. Bryant and O Hallaron, Computer Systems: A Programmer s Perspective, Third Edition
 Carnegie Mellon Virtual Memory: Concepts 5-23: Introduction to Computer Systems 7 th Lecture, October 24, 27 Instructor: Randy Bryant 2 Hmmm, How Does This Work?! Process Process 2 Process n Solution:
Carnegie Mellon Virtual Memory: Concepts 5-23: Introduction to Computer Systems 7 th Lecture, October 24, 27 Instructor: Randy Bryant 2 Hmmm, How Does This Work?! Process Process 2 Process n Solution:
CS 351 Exam 2 Mon. 11/2/2015
 CS 351 Exam 2 Mon. 11/2/2015 Name: Rules and Hints The MIPS cheat sheet and datapath diagram are attached at the end of this exam for your reference. You may use one handwritten 8.5 11 cheat sheet (front
CS 351 Exam 2 Mon. 11/2/2015 Name: Rules and Hints The MIPS cheat sheet and datapath diagram are attached at the end of this exam for your reference. You may use one handwritten 8.5 11 cheat sheet (front
Processes and Virtual Memory Concepts
 Processes and Virtual Memory Concepts Brad Karp UCL Computer Science CS 37 8 th February 28 (lecture notes derived from material from Phil Gibbons, Dave O Hallaron, and Randy Bryant) Today Processes Virtual
Processes and Virtual Memory Concepts Brad Karp UCL Computer Science CS 37 8 th February 28 (lecture notes derived from material from Phil Gibbons, Dave O Hallaron, and Randy Bryant) Today Processes Virtual
PROCESS VIRTUAL MEMORY. CS124 Operating Systems Winter , Lecture 18
 PROCESS VIRTUAL MEMORY CS124 Operating Systems Winter 2015-2016, Lecture 18 2 Programs and Memory Programs perform many interactions with memory Accessing variables stored at specific memory locations
PROCESS VIRTUAL MEMORY CS124 Operating Systems Winter 2015-2016, Lecture 18 2 Programs and Memory Programs perform many interactions with memory Accessing variables stored at specific memory locations
V. Primary & Secondary Memory!
 V. Primary & Secondary Memory! Computer Architecture and Operating Systems & Operating Systems: 725G84 Ahmed Rezine 1 Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM)
V. Primary & Secondary Memory! Computer Architecture and Operating Systems & Operating Systems: 725G84 Ahmed Rezine 1 Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic RAM (DRAM)
CSE 451: Operating Systems Winter Page Table Management, TLBs and Other Pragmatics. Gary Kimura
 CSE 451: Operating Systems Winter 2013 Page Table Management, TLBs and Other Pragmatics Gary Kimura Moving now from Hardware to how the OS manages memory Two main areas to discuss Page table management,
CSE 451: Operating Systems Winter 2013 Page Table Management, TLBs and Other Pragmatics Gary Kimura Moving now from Hardware to how the OS manages memory Two main areas to discuss Page table management,
Readings and References. Virtual Memory. Virtual Memory. Virtual Memory VPN. Reading. CSE Computer Systems December 5, 2001.
 Readings and References Virtual Memory Reading Chapter through.., Operating System Concepts, Silberschatz, Galvin, and Gagne CSE - Computer Systems December, Other References Chapter, Inside Microsoft
Readings and References Virtual Memory Reading Chapter through.., Operating System Concepts, Silberschatz, Galvin, and Gagne CSE - Computer Systems December, Other References Chapter, Inside Microsoft
CSE 351. Virtual Memory
 CSE 351 Virtual Memory Virtual Memory Very powerful layer of indirection on top of physical memory addressing We never actually use physical addresses when writing programs Every address, pointer, etc
CSE 351 Virtual Memory Virtual Memory Very powerful layer of indirection on top of physical memory addressing We never actually use physical addresses when writing programs Every address, pointer, etc
How to create a process? What does process look like?
 How to create a process? On Unix systems, executable read by loader Compile time runtime Ken Birman ld loader Cache Compiler: generates one object file per source file Linker: combines all object files
How to create a process? On Unix systems, executable read by loader Compile time runtime Ken Birman ld loader Cache Compiler: generates one object file per source file Linker: combines all object files
