: <STX><LEN><CMD><data_1>...<data_n><CHECKSUM><ETX> : two-complement of the sum of all previous bytes in the packet
|
|
|
- Griselda Snow
- 5 years ago
- Views:
Transcription
1 VM201 TCP protocol Generic TCP Protocol description Packet STX LEN CMD data_x CHECKSUM ETX : <STX><LEN><CMD><data_1>...<data_n><CHECKSUM><ETX> : 0x02 : number of bytes in packet incl. STX & CHECKSUM : command byte : optional data bytes : two-complement of the sum of all previous bytes in the packet : 0x03 At opening a connection and no authentication is needed there will be send: - logged in successfully: <STX><5><CMD_LOGGED_IN><CHECKSUM><ETX> At opening a connection and authentication is needed there will be send: - authentication needed: <STX><5><CMD_AUTH><CHECKSUM><ETX> The client will answer with username and password (max 8 characters): - username: <STX><14><CMD_USERNAME><char1 of username>...<char9 of username><checksum><etx> - password: <STX><14><CMD_PASSWORD><char1 of password>...<char9 of password><checksum><etx> If the username and password are invalid the following packets will be send: - access denied: <STX><5><CMD_ACCESS_DENIED><CHECKSUM><ETX> - session closed: <STX><5><CMD_CLOSED><CHECKSUM><ETX> - the client will be disconnected If the username and password are valid the following packets will be send:
2 - logged in successfully: <STX><5><CMD_LOGGED_IN><CHECKSUM><ETX> After successfully logged in the names (max 16 characters) of the 8 output channels and input will be send: - channel names: <STX><22><CMD_NAME><Channelnr><char1 name>...<char16 of name><checksum><etx> The status will be send: - output, timer & input status: <STX><8><CMD_STATUS><output status><output timer status><input status><checksum><etx> Output status bits = channels ; bit=0 OFF; bit=1 ON Output timer status bits = timer channels ; bit=0 DISABLED; bit=1 ENABLED Input status bit 0 = input channel; bit=0 OFF; bit=1 ON Now we are listening to the following commands from the client: - status request: <STX><5><CMD_STATUS_REQ><CHECKSUM><ETX> - switch an output channel ON: <STX><6><CMD_ON><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 no change ; bit=1 switch channel ON - switch an output channel OFF: <STX><6><CMD_OFF><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 no change ; bit=1 switch channel OFF - toggle an output channel: <STX><6><CMD_TOGGLE><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 no change ; bit=1 toggle channel - pulse an output channel: <STX><8><CMD_PULSE><channels><pulsetime><units><CHECKSUM><ETX>
3 Channel bits = channels ; bit=0 no change ; bit=1 pulse channel pulse time: units: 's'= seconds; 'm' = minutes; 'h' = hours - update all output channels: <STX><6><CMD_UPDATE><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 switch channel OFF; bit=1 switch channel ON - enable an output channel timer: <STX><6><CMD_TMR_ENA><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 no change ; bit=1 switch channel ON - disable an output channel timer: <STX><6><CMD_TMR_DIS><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 no change ; bit=1 switch channel OFF - toggle an output channel timer: <STX><6><CMD_TMR_TOGGLE><channels><CHECKSUM><ETX> Channel bits = channels ; bit=0 no change ; bit=1 toggle channel - connection closed: <STX><5><CMD_CLOSED><CHECKSUM><ETX> Every time the status changes it will be send an update to the client #define MIN_GENERIC_TCP_PACKET_SIZE 5 #define MAX_GENERIC_TCP_PACKET_SIZE 22 #define STX 0x02 #define ETX 0x03 #define CMD_AUTH 'A' // connected with authentication needed
4 #define LEN_CMD_AUTH 5 #define CMD_USERNAME 'U' // connected with authentication needed #define LEN_CMD_USERNAME 14 #define CMD_PASSWORD 'W' // connected with authentication needed #define LEN_CMD_PASSWORD 14 #define CMD_LOGGED_IN 'L' // successfully logged in #define LEN_CMD_LOGGED_IN 5 #define CMD_ACCESS_DENIED 'X' // access denied #define LEN_CMD_ACCESS_DENIED 5 #define CMD_CLOSED 'C' // connection closed #define LEN_CMD_CLOSED 5 #define CMD_NAME 'N' // channel name #define LEN_CMD_NAME 22 #define CMD_STATUS_REQ 'R' // status request #define LEN_CMD_STATUS_REQ 5 #define CMD_STATUS 'S' // output, timer & input channel status #define LEN_CMD_STATUS 8
5 #define CMD_ON 'O' // switch channel on #define LEN_CMD_ON 6 #define CMD_OFF 'F' // switch channel off #define LEN_CMD_OFF 6 #define CMD_TOGGLE 'T' // toggle channel #define LEN_CMD_TOGGLE 6 #define CMD_PULSE 'P' // pulse channel #define LEN_CMD_PULSE 8 #define CMD_UPDATE 'V' // update all channels #define LEN_CMD_UPDATE 6 #define CMD_TMR_ENA 'E' // enable timer channel programs #define LEN_CMD_TMR_ENA 6 #define CMD_TMR_DIS 'D' // disable timer channel programs #define LEN_CMD_TMR_DIS 6 #define CMD_TMR_TOGGLE 'G' // toggle timer channel programs #define LEN_CMD_TMR_TOGGLE 6
6 VM201_CMD_AUTH_REQUIRED VM201_CMD_USERNAME VM201_CMD_PASSWORD VM201_CMD_AUTH_OK VM201_CMD_AUTH_FAILED VM201_CMD_CLOSING VM201_CMD_CHANNEL_NAME VM201_CMD_STATUS_REQUEST VM201_CMD_STATUS VM201_CMD_SWITCH_ON VM201_CMD_SWITCH_OFF VM201_CMD_TOGGLE VM201_CMD_PULSE VM201_CMD_ENABLE_TIMER VM201_CMD_DISABLE_TIMER VM201_CMD_TOGGLE_TIMER VM201_CMD_FORCE_STATUS = $41; // 'A' = $55; // 'U' = $57; // 'W' = $4C; // 'L' = $58; // 'X' = $43; // 'C' = $4E; // 'N' = $52; // 'R' = $53; // 'S' = $4F; // 'O' = $46; // 'F' = $54; // 'T' = $50; // 'P' = $45; // 'E' = $44; // 'D' = $47; // 'G' = $56; // 'V' Checksum calculation in Delphi (pascal): Code: function VM201Checksum(Data: array of Byte; Size: Integer): Byte; var i: Integer; n: Byte; begin n := 0; for i:=0 to Size-1 do n := n + Data[i]; Result := (1 + (not ($FF and n))); end; The length is the length of the entire packet, every byte <STX><6><CMD_TOGGLE><channels><CHECKSUM><ETX> 1 <STX> 2 <6> 3 <CMD_TOGGLE> 4 <channels> 5 <CHECKSUM> 6 <ETX>
7 The checksum is calculated by adding every byte up to the checksum byte checksum = <STX> + <6> + <CMD_TOGGLE> + <channels> Inverting the bits checksum = not checksum And adding one checksum = checksum + 1
Table of Contents. VM201 Protocol
 Table of Contents VM201...2 Packet...3 Structure...3 Calculating the checksum...3 Authentication process...4 No authentication required...4 With authentication enabled...4 s...5 Authentication required
Table of Contents VM201...2 Packet...3 Structure...3 Calculating the checksum...3 Authentication process...4 No authentication required...4 With authentication enabled...4 s...5 Authentication required
Dialog Box Displaying the VPN Connection Status.
 By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
By using SoftEther VPN Client to define the required connection settings of a connection setting and then connecting to that connection setting, you can start the connection to VPN Server. 4.5.1 Starting
EWBS Receiving Module Communication specifications
 2017/01/05 EWBS Receiving Module Communication specifications v1.00 Century Revision history Revision Date Changes 1.00 2017/01/05 Initial Release. 1 Serial communication specifications Asynchronous serial
2017/01/05 EWBS Receiving Module Communication specifications v1.00 Century Revision history Revision Date Changes 1.00 2017/01/05 Initial Release. 1 Serial communication specifications Asynchronous serial
D I G I M A X BINARY COMMUNICATIONS PROTOCOL SYSTEM COMMAND AND CONTROL LANGUAGE APPLICATION MANUAL. Revision B1 April 30, 1993
 D I G I M A X I V BINARY COMMUNICATIONS PROTOCOL SYSTEM COMMAND AND CONTROL LANGUAGE APPLICATION MANUAL Revision B1 April 30, 1993 POWERTEC Industrial Motors Mailing Address: P.O. Box 2650 * Rock Hill,
D I G I M A X I V BINARY COMMUNICATIONS PROTOCOL SYSTEM COMMAND AND CONTROL LANGUAGE APPLICATION MANUAL Revision B1 April 30, 1993 POWERTEC Industrial Motors Mailing Address: P.O. Box 2650 * Rock Hill,
Preview Test: HW3. Test Information Description Due:Nov. 3
 Preview Test: HW3 Test Information Description Due:Nov. 3 Instructions Multiple Attempts Not allowed. This test can only be taken once. Force Completion This test can be saved and resumed later. Question
Preview Test: HW3 Test Information Description Due:Nov. 3 Instructions Multiple Attempts Not allowed. This test can only be taken once. Force Completion This test can be saved and resumed later. Question
THANK YOU. Control System Communication Protocol Manual RackLink. Monitor Control Alert Report Analyze. Thank you for purchasing a RackLink product.
 Control System Communication Protocol Manual RackLink Monitor Control Alert Report Analyze THANK YOU Thank you for purchasing a RackLink product. I-00472 Rev D TABLE OF CONTENTS PROTOCOL TRANSPORTS...
Control System Communication Protocol Manual RackLink Monitor Control Alert Report Analyze THANK YOU Thank you for purchasing a RackLink product. I-00472 Rev D TABLE OF CONTENTS PROTOCOL TRANSPORTS...
PROTOCOL TRANSPORTS 4 RS232 SPECIFICATIONS 4 RS232 CABLING 4 TCP/IP 4 PROTOCOL DOCUMENT NOTES 4 COMMUNICATION 4
 Table of Contents PROTOCOL TRANSPORTS 4 RS232 SPECIFICATIONS 4 RS232 CABLING 4 TCP/IP 4 PROTOCOL DOCUMENT NOTES 4 COMMUNICATION 4 PROTOCOL MESSAGE STRUCTURE 5 GENERAL MESSAGE FORMAT 5 CHECKSUM 6 ELONGATED
Table of Contents PROTOCOL TRANSPORTS 4 RS232 SPECIFICATIONS 4 RS232 CABLING 4 TCP/IP 4 PROTOCOL DOCUMENT NOTES 4 COMMUNICATION 4 PROTOCOL MESSAGE STRUCTURE 5 GENERAL MESSAGE FORMAT 5 CHECKSUM 6 ELONGATED
LAN Control Protocol
 LAN Control Protocol Contents 1. Control commands via LAN... 2 2. When LAN control protocol is Protocol 1... 3 2.1. When Web Control Administrator-Authorized password has been set (Protected mode)... 3
LAN Control Protocol Contents 1. Control commands via LAN... 2 2. When LAN control protocol is Protocol 1... 3 2.1. When Web Control Administrator-Authorized password has been set (Protected mode)... 3
PPP configuration commands
 Contents PPP configuration commands 1 ip address ppp-negotiate 1 ip pool 1 link-protocol ppp 2 ppp authentication-mode 2 ppp chap password 4 ppp chap user 5 ppp ipcp remote-address forced 5 ppp pap local-user
Contents PPP configuration commands 1 ip address ppp-negotiate 1 ip pool 1 link-protocol ppp 2 ppp authentication-mode 2 ppp chap password 4 ppp chap user 5 ppp ipcp remote-address forced 5 ppp pap local-user
USING THE PASS-THROUGH COMMAND VERSION
 USING THE PASS-THROUGH COMMAND VERSION 011614 TABLE OF CONTENTS 1 Overview... 3 1.1 Required Reading... 3 1.2 Document Scope... 3 1.3 Limitations... 3 2 Pass-Through Command Examples... 4 2.1 SLI-S Get
USING THE PASS-THROUGH COMMAND VERSION 011614 TABLE OF CONTENTS 1 Overview... 3 1.1 Required Reading... 3 1.2 Document Scope... 3 1.3 Limitations... 3 2 Pass-Through Command Examples... 4 2.1 SLI-S Get
DirectNET Host. Communications Programs. In This Chapter...
 Communications Programs In This Chapter.... Why do you need a communications program? Modes of Operation Protocol Components Controlling the Communications Initiating the Request Acknowledging the Request
Communications Programs In This Chapter.... Why do you need a communications program? Modes of Operation Protocol Components Controlling the Communications Initiating the Request Acknowledging the Request
USR-TCP232-E45/M4 Cofig Protocol
 USR-TCP232-E45/M4 Cofig Protocol Protocol All data must be sent via UDP boardcast, local port 1901, sent to remote port 1901, broadcast address 255.255.255.255. First PC send a command, the device reply.
USR-TCP232-E45/M4 Cofig Protocol Protocol All data must be sent via UDP boardcast, local port 1901, sent to remote port 1901, broadcast address 255.255.255.255. First PC send a command, the device reply.
ArcaTrade Specification for Bonds
 Specification for Bonds For the New York Stock Exchange April 24, 2007 Version 1.07 Copyright 2006 Archipelago Holdings, Inc. All Rights Reserved. Copyright 2006 Archipelago Holdings, Inc. All rights reserved.
Specification for Bonds For the New York Stock Exchange April 24, 2007 Version 1.07 Copyright 2006 Archipelago Holdings, Inc. All Rights Reserved. Copyright 2006 Archipelago Holdings, Inc. All rights reserved.
USR-K2 Setting Protocol V1.0
 USR-K2 Setting Protocol V1.0 Content 1. Introduce... 3 2. command... 4 2.1. command List... 4 2.2. About Checksum... 4 2.3. search... 4 2.4. Reset... 4 2.5. Read parameter... 4 2.6. Base parameter... 5
USR-K2 Setting Protocol V1.0 Content 1. Introduce... 3 2. command... 4 2.1. command List... 4 2.2. About Checksum... 4 2.3. search... 4 2.4. Reset... 4 2.5. Read parameter... 4 2.6. Base parameter... 5
Transport Layer Overview
 Transport Layer Overview Kai Shen Transport-layer Overview Network layer: host-to-host to logical communication between hosts. Transport layer: logical communication between s. multiple comm. s can reside
Transport Layer Overview Kai Shen Transport-layer Overview Network layer: host-to-host to logical communication between hosts. Transport layer: logical communication between s. multiple comm. s can reside
BULLETIN 1203-GD2, -GK2 & 1336-GM2 DF1 MESSAGING (FULL DUPLEX / POINT-TO-POINT)
 BULLETIN 1203-GD2, -GK2 & 1336-GM2 DF1 MESSAGING (FULL DUPLEX / POINT-TO-POINT) APPLICATION NOTE OCTOBER 20, 1999 PURPOSE The purpose of this document is to provide information on using the DF1 Full Duplex/Point-to-Point
BULLETIN 1203-GD2, -GK2 & 1336-GM2 DF1 MESSAGING (FULL DUPLEX / POINT-TO-POINT) APPLICATION NOTE OCTOBER 20, 1999 PURPOSE The purpose of this document is to provide information on using the DF1 Full Duplex/Point-to-Point
ECS Service USER GUIDE
 ECS Service USER GUIDE TABLE OF CONTENTS 1. Preface... 3 2. Prerequisites... 4 2.1. Compatible platforms:... 4 2.2. Connection to Volvo... 4 2.2.1. Antivirus and Firewall... 4 2.2.2. Firewall Configuration...
ECS Service USER GUIDE TABLE OF CONTENTS 1. Preface... 3 2. Prerequisites... 4 2.1. Compatible platforms:... 4 2.2. Connection to Volvo... 4 2.2.1. Antivirus and Firewall... 4 2.2.2. Firewall Configuration...
CS 4453 Computer Networks Winter
 CS 4453 Computer Networks Chapter 2 OSI Network Model 2015 Winter OSI model defines 7 layers Figure 1: OSI model Computer Networks R. Wei 2 The seven layers are as follows: Application Presentation Session
CS 4453 Computer Networks Chapter 2 OSI Network Model 2015 Winter OSI model defines 7 layers Figure 1: OSI model Computer Networks R. Wei 2 The seven layers are as follows: Application Presentation Session
WF-700B User Manual. RS232 Interface for Coin Validators
 RS232 Interface for Coin Validators WF-700B User Manual Version 1.4-2010-01-15 1.0 Introduction The WF-700B is an RS232 interface module for most models of coin acceptor products. The WF-700B has a built-in
RS232 Interface for Coin Validators WF-700B User Manual Version 1.4-2010-01-15 1.0 Introduction The WF-700B is an RS232 interface module for most models of coin acceptor products. The WF-700B has a built-in
Contents. Configuring SSH 1
 Contents Configuring SSH 1 Overview 1 How SSH works 1 SSH authentication methods 2 SSH support for Suite B 3 FIPS compliance 3 Configuring the device as an SSH server 4 SSH server configuration task list
Contents Configuring SSH 1 Overview 1 How SSH works 1 SSH authentication methods 2 SSH support for Suite B 3 FIPS compliance 3 Configuring the device as an SSH server 4 SSH server configuration task list
PPP Configuration Options
 PPP Configuration Options 1 PPP Configuration Options PPP can be configured to support various functions including: Authentication using either PAP or CHAP Compression using either Stacker or Predictor
PPP Configuration Options 1 PPP Configuration Options PPP can be configured to support various functions including: Authentication using either PAP or CHAP Compression using either Stacker or Predictor
ELEC/TELE/PHTN Networked Communications Design Topic. Networked Communications Elective Topic, S Context and Objectives
 ELEC/TELE/PHTN 4123 Networked Communications Elective Topic, S1 2017 created by Prof. D. Taubman updated 21 May 2018 Networked Communications Design Topic Context and Objectives The objective of this design
ELEC/TELE/PHTN 4123 Networked Communications Elective Topic, S1 2017 created by Prof. D. Taubman updated 21 May 2018 Networked Communications Design Topic Context and Objectives The objective of this design
Fundamentals of Programming (C)
 Borrowed from lecturer notes by Omid Jafarinezhad Fundamentals of Programming (C) Group 8 Lecturer: Vahid Khodabakhshi Lecture Number Systems Department of Computer Engineering Outline Numeral Systems
Borrowed from lecturer notes by Omid Jafarinezhad Fundamentals of Programming (C) Group 8 Lecturer: Vahid Khodabakhshi Lecture Number Systems Department of Computer Engineering Outline Numeral Systems
CSE 123A Computer Networks
 CSE 123A Computer Networks Winter 2005 Lecture 4: Data-Link I: Framing and Errors Some portions courtesy Robin Kravets and Steve Lumetta Last time How protocols are organized & why Network layer Data-link
CSE 123A Computer Networks Winter 2005 Lecture 4: Data-Link I: Framing and Errors Some portions courtesy Robin Kravets and Steve Lumetta Last time How protocols are organized & why Network layer Data-link
The RS-485 user manual for B800 series communication
 The user manual of B800 Series Rs-485 The RS-485 user manual for B800 series RS-232 inbuilt inside the main board of B800 series frequency inverter, we can effect RS-485 through fitting board externally.
The user manual of B800 Series Rs-485 The RS-485 user manual for B800 series RS-232 inbuilt inside the main board of B800 series frequency inverter, we can effect RS-485 through fitting board externally.
Computer Networks. Transmission Control Protocol. Jianping Pan Spring /3/17 CSC361 1
 Computer Networks Transmission Control Protocol Jianping Pan Spring 2017 2/3/17 CSC361 1 https://connex.csc.uvic.ca/portal NSERC USRA awards available at UVic CSc for 2017/18 2/3/17 CSC361 2 TCP Transmission
Computer Networks Transmission Control Protocol Jianping Pan Spring 2017 2/3/17 CSC361 1 https://connex.csc.uvic.ca/portal NSERC USRA awards available at UVic CSc for 2017/18 2/3/17 CSC361 2 TCP Transmission
Xcalenets Console Setup Guide. Xcalenets Console Setup Guide (Standalone version)
 Xcalenets Console Setup Guide Xcalenets Console Setup Guide (Standalone version) 1 Content CONTENT... 2 Getting Started to Xcalenets Console Setup... 3 Account Level Introduction... 3 Login Console Setup...
Xcalenets Console Setup Guide Xcalenets Console Setup Guide (Standalone version) 1 Content CONTENT... 2 Getting Started to Xcalenets Console Setup... 3 Account Level Introduction... 3 Login Console Setup...
Embedded Modbus TCP Module GS11-MT. User Manual REV 1.1. SST Automation.
 Embedded Modbus TCP Module GS11-MT User Manual REV 1.1 SST Automation E-mail: SUPPORT@SSTCOMM.COM WWW.SSTCOMM.COM Catalog 1 About the Embedded Module... 4 1.1 General...4 1.2 Features... 4 1.3 Specifications...4
Embedded Modbus TCP Module GS11-MT User Manual REV 1.1 SST Automation E-mail: SUPPORT@SSTCOMM.COM WWW.SSTCOMM.COM Catalog 1 About the Embedded Module... 4 1.1 General...4 1.2 Features... 4 1.3 Specifications...4
plc numbers Encoded values; BCD and ASCII Error detection; parity, gray code and checksums
 plc numbers - 3. 3. NUMBERS AND DATA Topics: Number bases; binary, octal,, hexa Binary calculations; s compliments, addition, subtraction and Boolean operations Encoded values; BCD and ASCII Error detection;
plc numbers - 3. 3. NUMBERS AND DATA Topics: Number bases; binary, octal,, hexa Binary calculations; s compliments, addition, subtraction and Boolean operations Encoded values; BCD and ASCII Error detection;
Web server Access Control Server
 2 You can use access lists to control traffic based on the IP address and protocol. However, you must use authentication and authorization in order to control access and use for specific users or groups.
2 You can use access lists to control traffic based on the IP address and protocol. However, you must use authentication and authorization in order to control access and use for specific users or groups.
Security Assertions Markup Language
 . Send comments to: Phillip Hallam-Baker, Senior Author 401 Edgewater Place, Suite 280 Wakefield MA 01880 Tel 781 245 6996 x227 Email: pbaker@verisign.com Security Assertions Markup Language Straw-man
. Send comments to: Phillip Hallam-Baker, Senior Author 401 Edgewater Place, Suite 280 Wakefield MA 01880 Tel 781 245 6996 x227 Email: pbaker@verisign.com Security Assertions Markup Language Straw-man
RADIUS Configuration. Overview. Introduction to RADIUS. Client/Server Model
 Table of Contents RADIUS Configuration 1 Overview 1 Introduction to RADIUS 1 Client/Server Model 1 Security and Authentication Mechanisms 2 Basic Message Exchange Process of RADIUS 2 RADIUS Packet Format
Table of Contents RADIUS Configuration 1 Overview 1 Introduction to RADIUS 1 Client/Server Model 1 Security and Authentication Mechanisms 2 Basic Message Exchange Process of RADIUS 2 RADIUS Packet Format
DATA LINK LAYER UNIT 7.
 DATA LINK LAYER UNIT 7 1 Data Link Layer Design Issues: 1. Service provided to network layer. 2. Determining how the bits of the physical layer are grouped into frames (FRAMING). 3. Dealing with transmission
DATA LINK LAYER UNIT 7 1 Data Link Layer Design Issues: 1. Service provided to network layer. 2. Determining how the bits of the physical layer are grouped into frames (FRAMING). 3. Dealing with transmission
USR-TCP232-E45/M4 Cofig Protocol
 USR-TCP232-E45/M4 Cofig Protocol Protocol All data must be sent via UDP boardcast, local port 1901, sent to remote port 1901, broadcast address 255.255.255.255. First PC send a command, the device reply.
USR-TCP232-E45/M4 Cofig Protocol Protocol All data must be sent via UDP boardcast, local port 1901, sent to remote port 1901, broadcast address 255.255.255.255. First PC send a command, the device reply.
Managing CORBA Interfaces
 CHAPTER 12 This chapter contains the following information: 12.1 What is Cisco MGM GateWay/CORBA? 12.2 Using a Static CORBA Listener Port on the Cisco MGM Server 12.3 Configuring the CORBA Timeout Cisco
CHAPTER 12 This chapter contains the following information: 12.1 What is Cisco MGM GateWay/CORBA? 12.2 Using a Static CORBA Listener Port on the Cisco MGM Server 12.3 Configuring the CORBA Timeout Cisco
imag User Manual USER MANUAL imag Magnetic Stripe Reader for iphone 3G, 3GS and ipod Touch
 imag User Manual USER MANUAL imag Magnetic Stripe Reader for iphone 3G, 3GS and ipod Touch 80097503-001 06/10/2010 1 imag Firmware Command 1.1 Setting Command The setting data command is a collection of
imag User Manual USER MANUAL imag Magnetic Stripe Reader for iphone 3G, 3GS and ipod Touch 80097503-001 06/10/2010 1 imag Firmware Command 1.1 Setting Command The setting data command is a collection of
Groups of two-state devices are used to represent data in a computer. In general, we say the states are either: high/low, on/off, 1/0,...
 Chapter 9 Computer Arithmetic Reading: Section 9.1 on pp. 290-296 Computer Representation of Data Groups of two-state devices are used to represent data in a computer. In general, we say the states are
Chapter 9 Computer Arithmetic Reading: Section 9.1 on pp. 290-296 Computer Representation of Data Groups of two-state devices are used to represent data in a computer. In general, we say the states are
Zebra Mobile Printer, Zebra Setup Utility, Cisco ACS, Cisco Controller PEAP and WPA-PEAP
 Zebra Mobile Printer, Zebra Setup Utility, Cisco ACS, Cisco Controller PEAP and WPA-PEAP This section of the document illustrates the Cisco ACS radius server and how PEAP and WPA-PEAP was configured on
Zebra Mobile Printer, Zebra Setup Utility, Cisco ACS, Cisco Controller PEAP and WPA-PEAP This section of the document illustrates the Cisco ACS radius server and how PEAP and WPA-PEAP was configured on
TACACS+ Configuration Mode Commands
 Important TACACS Configuration Mode is available in releases 11.0 and later. This chapter describes all commands available in the TACACS+ Configuration Mode. TACACS+ (Terminal Access Controller Access-Control
Important TACACS Configuration Mode is available in releases 11.0 and later. This chapter describes all commands available in the TACACS+ Configuration Mode. TACACS+ (Terminal Access Controller Access-Control
LomaLink User s Guide
 LomaLink User s Guide The Serial Communications System for Loma Inspection Equipment Loma Part Number: 811153 Spectrum Inspection Systems Issue: K Southwood Date: July 2007 Farnborough Hampshire GU14 0NY
LomaLink User s Guide The Serial Communications System for Loma Inspection Equipment Loma Part Number: 811153 Spectrum Inspection Systems Issue: K Southwood Date: July 2007 Farnborough Hampshire GU14 0NY
NEO OPC Client Driver. The NEO OPC Client can be launched by configuring an OPC Link from the New Link or Add Link dialog as the followings:
 The configuration program provides a built-in OPC UA Client that enables connections to OPC Servers. The NEO OPC Client is built with the OPC Client SDK and can be used to interactively browse and retrieve
The configuration program provides a built-in OPC UA Client that enables connections to OPC Servers. The NEO OPC Client is built with the OPC Client SDK and can be used to interactively browse and retrieve
Using CSE Cisco Anyconnect with 2FA
 Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
Caller dialled digit during recording. Fax routing Config? Yes. Route to Fax Extensions
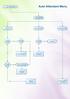 Auto Attendant Menu Caller dialled digit during recording Digits 0-7 Fax tone detected selection is made 2nd digit present Single Digit Config Fax routing Config? Ignore Fax Route to Extensions Route to
Auto Attendant Menu Caller dialled digit during recording Digits 0-7 Fax tone detected selection is made 2nd digit present Single Digit Config Fax routing Config? Ignore Fax Route to Extensions Route to
אי.די.פי.מוצריזיהויאלקטרוניים בע"מ תושיה 6 תל-אביב, , פקס
 אי.די.פי.מוצריזיהויאלקטרוניים בע"מ תושיה 6 תל-אביב, 03-5617395, פקס 03-5621823 Network connection and Http access Accessing the ETH008 from your browser Having plugged in your 12vdc power supply and Ethernet
אי.די.פי.מוצריזיהויאלקטרוניים בע"מ תושיה 6 תל-אביב, 03-5617395, פקס 03-5621823 Network connection and Http access Accessing the ETH008 from your browser Having plugged in your 12vdc power supply and Ethernet
Some portions courtesy Robin Kravets and Steve Lumetta
 CSE 123 Computer Networks Fall 2009 Lecture 4: Data-Link I: Framing and Errors Some portions courtesy Robin Kravets and Steve Lumetta Administrative updates I m Im out all next week no lectures, but You
CSE 123 Computer Networks Fall 2009 Lecture 4: Data-Link I: Framing and Errors Some portions courtesy Robin Kravets and Steve Lumetta Administrative updates I m Im out all next week no lectures, but You
c. If the sum contains a zero, the receiver knows there has been an error.
 ENSC-37 Fall 27 Assignment#3 Due Date 6 Oct. 27 Problem-:[4] UDP and TCP use s complement for their checksums. Suppose you have the following three 8-bit bytes:,, and. a. [6] What is the s complement of
ENSC-37 Fall 27 Assignment#3 Due Date 6 Oct. 27 Problem-:[4] UDP and TCP use s complement for their checksums. Suppose you have the following three 8-bit bytes:,, and. a. [6] What is the s complement of
Table of Contents 1 AAA Overview AAA Configuration 2-1
 Table of Contents 1 AAA Overview 1-1 Introduction to AAA 1-1 Authentication 1-1 Authorization 1-1 Accounting 1-2 Introduction to ISP Domain 1-2 Introduction to AAA Services 1-3 Introduction to RADIUS 1-3
Table of Contents 1 AAA Overview 1-1 Introduction to AAA 1-1 Authentication 1-1 Authorization 1-1 Accounting 1-2 Introduction to ISP Domain 1-2 Introduction to AAA Services 1-3 Introduction to RADIUS 1-3
PJLink Specifications
 PJLink Specifications Version 2.00 2017.1.31 1/51 Table of Contents PJLink Specifications Version2.00 2017.1.31 1. Overview... 4 2. Command Format... 5 2.1. Command line... 5 2.2. Response line... 5 2.3.
PJLink Specifications Version 2.00 2017.1.31 1/51 Table of Contents PJLink Specifications Version2.00 2017.1.31 1. Overview... 4 2. Command Format... 5 2.1. Command line... 5 2.2. Response line... 5 2.3.
The flow of transferring the machining programs of the server PC and starting an automatic operation is as below.
 CONTENTS 1 OUTLINE... 1 2 OVERALL FLOW... 1 3 NETWORK CONNECTION... 1 4 SETTING EXAMPLE... 1 5 SET SERVER PC... 2 5.1 Windows 7... 2 5.1.1 Install IIS... 2 5.1.2 Set IIS... 4 5.1.3 Set firewall... 9 5.1.4
CONTENTS 1 OUTLINE... 1 2 OVERALL FLOW... 1 3 NETWORK CONNECTION... 1 4 SETTING EXAMPLE... 1 5 SET SERVER PC... 2 5.1 Windows 7... 2 5.1.1 Install IIS... 2 5.1.2 Set IIS... 4 5.1.3 Set firewall... 9 5.1.4
Rev X 341. Table 111. Access Levels and Descriptions
 9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
TACACS+ Servers for AAA
 This chapter describes how to configure TACACS+ servers used in AAA. About, on page 1 Guidelines for, on page 3 Configure TACACS+ Servers, on page 3 Monitoring, on page 6 History for, on page 6 About TACACS+
This chapter describes how to configure TACACS+ servers used in AAA. About, on page 1 Guidelines for, on page 3 Configure TACACS+ Servers, on page 3 Monitoring, on page 6 History for, on page 6 About TACACS+
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
REMOTE AUTHENTICATION DIAL IN USER SERVICE
 AAA / REMOTE AUTHENTICATION DIAL IN USER SERVICE INTRODUCTION TO, A PROTOCOL FOR AUTHENTICATION, AUTHORIZATION AND ACCOUNTING SERVICES Peter R. Egli INDIGOO.COM 1/12 Contents 1. AAA - Access Control 2.
AAA / REMOTE AUTHENTICATION DIAL IN USER SERVICE INTRODUCTION TO, A PROTOCOL FOR AUTHENTICATION, AUTHORIZATION AND ACCOUNTING SERVICES Peter R. Egli INDIGOO.COM 1/12 Contents 1. AAA - Access Control 2.
Settings Settings
 ... 2 Overview... 2 WLAN & WAN Information... 3 Advanced... 4 Changing Security... 20 Internet Connectivity... 21 Overview Activating SoftBank 007Z Utility Use SoftBank 007Z Utility to change network settings,
... 2 Overview... 2 WLAN & WAN Information... 3 Advanced... 4 Changing Security... 20 Internet Connectivity... 21 Overview Activating SoftBank 007Z Utility Use SoftBank 007Z Utility to change network settings,
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Table of Contents 1 AAA Overview AAA Configuration 2-1
 Table of Contents 1 AAA Overview 1-1 Introduction to AAA 1-1 Authentication 1-1 Authorization 1-1 Accounting 1-2 Introduction to ISP Domain 1-2 Introduction to AAA Services 1-2 Introduction to RADIUS 1-2
Table of Contents 1 AAA Overview 1-1 Introduction to AAA 1-1 Authentication 1-1 Authorization 1-1 Accounting 1-2 Introduction to ISP Domain 1-2 Introduction to AAA Services 1-2 Introduction to RADIUS 1-2
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
Lesson 3. IPv4 and IPv6 Protocols. Chapter-4 L03: "Internet of Things ", Raj Kamal, Publs.: McGraw-Hill Education
 Lesson 3 IPv4 and IPv6 Protocols Publs.: McGraw-Hill Education 1 Internet layer Receives and forwards data to next stage Uses IP version 4 (IPv4), Uses IP version 6 (IPv6) protocol or [IPv6 Routing Protocol
Lesson 3 IPv4 and IPv6 Protocols Publs.: McGraw-Hill Education 1 Internet layer Receives and forwards data to next stage Uses IP version 4 (IPv4), Uses IP version 6 (IPv6) protocol or [IPv6 Routing Protocol
RADIUS Server Load Balancing
 The feature distributes authentication, authorization, and accounting (AAA) authentication and accounting transactions across RADIUS servers in a server group These servers can share the AAA transaction
The feature distributes authentication, authorization, and accounting (AAA) authentication and accounting transactions across RADIUS servers in a server group These servers can share the AAA transaction
Configuring Management Access
 37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
HWTACACS Technology White Paper
 S Series Switches HWTACACS Technology White Paper Issue 1.0 Date 2015-08-08 HUAWEI TECHNOLOGIES CO., LTD. 2015. All rights reserved. No part of this document may be reproduced or transmitted in any form
S Series Switches HWTACACS Technology White Paper Issue 1.0 Date 2015-08-08 HUAWEI TECHNOLOGIES CO., LTD. 2015. All rights reserved. No part of this document may be reproduced or transmitted in any form
TCP = Transmission Control Protocol Connection-oriented protocol Provides a reliable unicast end-to-end byte stream over an unreliable internetwork.
 Overview Formats, Data Transfer, etc. Connection Management (modified by Malathi Veeraraghavan) 1 Overview TCP = Transmission Control Protocol Connection-oriented protocol Provides a reliable unicast end-to-end
Overview Formats, Data Transfer, etc. Connection Management (modified by Malathi Veeraraghavan) 1 Overview TCP = Transmission Control Protocol Connection-oriented protocol Provides a reliable unicast end-to-end
Admin Guide ( Unix System Administration )
 Admin Guide ( Unix System Administration ) ProFTPD Server Configuration ProFTPD is a secure and configurable FTP server, written for use on Unix and Unix-like operating systems. ProFTPD is modeled around
Admin Guide ( Unix System Administration ) ProFTPD Server Configuration ProFTPD is a secure and configurable FTP server, written for use on Unix and Unix-like operating systems. ProFTPD is modeled around
Introduction to Computer Networks. 03 Data Link Layer Introduction
 Introduction to Computer Networks 03 Data Link Layer Introduction Link Layer 1 Introduction and services 2 Link Layer Services 2.1 Framing 2.2 Error detection and correction 2.3 Flow Control 2.4 Multiple
Introduction to Computer Networks 03 Data Link Layer Introduction Link Layer 1 Introduction and services 2 Link Layer Services 2.1 Framing 2.2 Error detection and correction 2.3 Flow Control 2.4 Multiple
8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista
 8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista Introduction If Vista is not available in your classroom, you may complete this lab by viewing the figures in this document. Print and
8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista Introduction If Vista is not available in your classroom, you may complete this lab by viewing the figures in this document. Print and
AFRecorder 4800R Serial Port Programming Interface Description For Software Version 9.5 (Last Revision )
 AFRecorder 4800R Serial Port Programming Interface Description For Software Version 9.5 (Last Revision 8-27-08) Changes from Version 9.2 1. The communication baud rate is raised to 9600. 2. Testing with
AFRecorder 4800R Serial Port Programming Interface Description For Software Version 9.5 (Last Revision 8-27-08) Changes from Version 9.2 1. The communication baud rate is raised to 9600. 2. Testing with
<dalf1_api.doc> API Interface. Revision 0.13 June 28, 2007
 DALF 1; Rev F Motor Control Board API Interface Revision 0.13 June 28, 2007 Embedded Electronics Page 1 8/7/2007 Table of Contents INTRODUCTION...4 PHYSICAL LAYER...4 PACKET LAYER...5 TRANSACTION
DALF 1; Rev F Motor Control Board API Interface Revision 0.13 June 28, 2007 Embedded Electronics Page 1 8/7/2007 Table of Contents INTRODUCTION...4 PHYSICAL LAYER...4 PACKET LAYER...5 TRANSACTION
Network Technology 1 5th - Transport Protocol. Mario Lombardo -
 Network Technology 1 5th - Transport Protocol Mario Lombardo - lombardo@informatik.dhbw-stuttgart.de 1 overview Transport Protocol Layer realizes process to process communication data unit is called a
Network Technology 1 5th - Transport Protocol Mario Lombardo - lombardo@informatik.dhbw-stuttgart.de 1 overview Transport Protocol Layer realizes process to process communication data unit is called a
µtasker Document µtasker Multicasting and Internet Group Management Protocol (IGMP)
 Embedding it better... µtasker Document µtasker Multicasting and Internet Group Management Protocol (IGMP) utasker_igmp.doc/0.01 Copyright 2014 M.J.Butcher Consulting Table of Contents 1. Introduction...3
Embedding it better... µtasker Document µtasker Multicasting and Internet Group Management Protocol (IGMP) utasker_igmp.doc/0.01 Copyright 2014 M.J.Butcher Consulting Table of Contents 1. Introduction...3
Computer Networks. Homework #4: No Grading
 Computer Networks Homework #4: No Grading Problem #1. Assume you need to write and test a client-server application program on two hosts you have at home. a. What is the range of port numbers you would
Computer Networks Homework #4: No Grading Problem #1. Assume you need to write and test a client-server application program on two hosts you have at home. a. What is the range of port numbers you would
Serial-to-Ethernet Tunnel Application Note
 Serial-to-Ethernet Tunnel Application Note Introduction This application note applies to the platforms listed below. SBL2e based Serial To Ethernet devices can also do serial tunneling but the default
Serial-to-Ethernet Tunnel Application Note Introduction This application note applies to the platforms listed below. SBL2e based Serial To Ethernet devices can also do serial tunneling but the default
ETH002-2 Relays at 16A Technical Documentation
 ETH002-2 Relays at 16A Technical Documentation Overview The ETH002 provides two volt free contact relay outputs with a current rating of up to 16Am. The module is powered from a 12vdc supply which can
ETH002-2 Relays at 16A Technical Documentation Overview The ETH002 provides two volt free contact relay outputs with a current rating of up to 16Am. The module is powered from a 12vdc supply which can
V850ES/SG3, V850ES/SJ3
 APPLICATION NOTE V850ES/SG3, V850ES/SJ3 V850ES/SG3, V850ES/SJ3 Microcontrollers R01AN0930EJ0200 Rev.2.00 Introduction This application note is intended for users who understand the functions of the V850ES/SG3
APPLICATION NOTE V850ES/SG3, V850ES/SJ3 V850ES/SG3, V850ES/SJ3 Microcontrollers R01AN0930EJ0200 Rev.2.00 Introduction This application note is intended for users who understand the functions of the V850ES/SG3
Syntax instance instance [interface interface-name [vrid virtual-router-id] instance interface interface-name vrid virtual-router-id ipv6
![Syntax instance instance [interface interface-name [vrid virtual-router-id] instance interface interface-name vrid virtual-router-id ipv6 Syntax instance instance [interface interface-name [vrid virtual-router-id] instance interface interface-name vrid virtual-router-id ipv6](/thumbs/92/108512470.jpg) VRRP Show Commands instance Syntax instance instance [interface interface-name [vrid virtual-router-id] instance interface interface-name vrid virtual-router-id ipv6 Context show>vrrp Description This
VRRP Show Commands instance Syntax instance instance [interface interface-name [vrid virtual-router-id] instance interface interface-name vrid virtual-router-id ipv6 Context show>vrrp Description This
Data Link Layer. Srinidhi Varadarajan
 Data Link Layer Srinidhi Varadarajan Data Link Layer: Functionality The data link layer must: Detect errors (using redundancy bits) Request retransmission if data is lost (using automatic repeat request
Data Link Layer Srinidhi Varadarajan Data Link Layer: Functionality The data link layer must: Detect errors (using redundancy bits) Request retransmission if data is lost (using automatic repeat request
Operation Manual 802.1x. Table of Contents
 Table of Contents Table of Contents... 1-1 1.1 802.1x Overview... 1-1 1.1.1 Architecture of 802.1x... 1-1 1.1.2 Operation of 802.1x... 1-3 1.1.3 EAP Encapsulation over LANs... 1-4 1.1.4 EAP Encapsulation
Table of Contents Table of Contents... 1-1 1.1 802.1x Overview... 1-1 1.1.1 Architecture of 802.1x... 1-1 1.1.2 Operation of 802.1x... 1-3 1.1.3 EAP Encapsulation over LANs... 1-4 1.1.4 EAP Encapsulation
CMPE 80N: Introduction to Networking and the Internet
 CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 11 CMPE 80N Fall'10 1 Announcements Forum #2 due on 11.05. CMPE 80N Fall'10 2 Last
CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 11 CMPE 80N Fall'10 1 Announcements Forum #2 due on 11.05. CMPE 80N Fall'10 2 Last
Transport Layer TCP / UDP
 Transport Layer TCP / UDP Chapter 6 section 6.5 is TCP 12 Mar 2012 Layers Application Transport Why do we need the Transport Layer? Network Host-to-Network/Physical/DataLink High Level Overview TCP (RFC
Transport Layer TCP / UDP Chapter 6 section 6.5 is TCP 12 Mar 2012 Layers Application Transport Why do we need the Transport Layer? Network Host-to-Network/Physical/DataLink High Level Overview TCP (RFC
CS 4390 Computer Networks. Transport Services and Protocols
 CS 4390 Computer Networks UT D data Session 07 Transport Layer Overview and UDP Adapted from Computer Networking a Top-Down Approach 1996-2012 by J.F Kurose and K.W. Ross, All Rights Reserved Transport
CS 4390 Computer Networks UT D data Session 07 Transport Layer Overview and UDP Adapted from Computer Networking a Top-Down Approach 1996-2012 by J.F Kurose and K.W. Ross, All Rights Reserved Transport
Zebra Setup Utility, Zebra Mobile Printer, Microsoft NPS, Cisco Controller, PEAP and WPA-PEAP
 Zebra Setup Utility, Zebra Mobile Printer, Microsoft NPS, Cisco Controller, PEAP and WPA-PEAP This section of the document illustrates the Microsoft Network Policy Server and how PEAP and WPA- PEAP was
Zebra Setup Utility, Zebra Mobile Printer, Microsoft NPS, Cisco Controller, PEAP and WPA-PEAP This section of the document illustrates the Microsoft Network Policy Server and how PEAP and WPA- PEAP was
Chapter 2 Number System
 Chapter 2 Number System Embedded Systems with ARM Cortext-M Updated: Tuesday, January 16, 2018 What you should know.. Before coming to this class Decimal Binary Octal Hex 0 0000 00 0x0 1 0001 01 0x1 2
Chapter 2 Number System Embedded Systems with ARM Cortext-M Updated: Tuesday, January 16, 2018 What you should know.. Before coming to this class Decimal Binary Octal Hex 0 0000 00 0x0 1 0001 01 0x1 2
Administrative Guide
 Administrative Guide Admin Home: Wiley Digital Archives (WDA) Admin pages. Please login using the admin name and password assigned to the institution 1. The first screen shows information about the institution,
Administrative Guide Admin Home: Wiley Digital Archives (WDA) Admin pages. Please login using the admin name and password assigned to the institution 1. The first screen shows information about the institution,
POINT TO POINT DATALINK PROTOCOLS. ETI 2506 Telecommunication Systems Monday, 7 November 2016
 POINT TO POINT DATALINK PROTOCOLS ETI 2506 Telecommunication Systems Monday, 7 November 2016 TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember PPP Frame
POINT TO POINT DATALINK PROTOCOLS ETI 2506 Telecommunication Systems Monday, 7 November 2016 TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember PPP Frame
TCP/IP Transport Layer Protocols, TCP and UDP
 TCP/IP Transport Layer Protocols, TCP and UDP Learning Objectives Identify TCP header fields and operation using a Wireshark FTP session capture. Identify UDP header fields and operation using a Wireshark
TCP/IP Transport Layer Protocols, TCP and UDP Learning Objectives Identify TCP header fields and operation using a Wireshark FTP session capture. Identify UDP header fields and operation using a Wireshark
DDR Routing Commands
 DDR Routing Commands This section describes the function and displays the syntax of each dial-on-demand routing (DDR) command. For more information about defaults and usage guidelines, see the corresponding
DDR Routing Commands This section describes the function and displays the syntax of each dial-on-demand routing (DDR) command. For more information about defaults and usage guidelines, see the corresponding
VERTIV. Avocent ACS8xxx Advanced Console System Release Notes VERSION 2.4.2, AUGUST 24, Release Notes Section Outline. 1 Update Instructions
 VERTIV Avocent ACS8xxx Advanced Console System Release Notes VERSION 2.4.2, AUGUST 24, 2018 Release Notes Section Outline 1 Update Instructions 2 Appliance Firmware Version Information 3 Local Client Requirements
VERTIV Avocent ACS8xxx Advanced Console System Release Notes VERSION 2.4.2, AUGUST 24, 2018 Release Notes Section Outline 1 Update Instructions 2 Appliance Firmware Version Information 3 Local Client Requirements
Remote Process Explorer
 Remote Process Explorer Frequently Asked Questions LizardSystems Table of Contents Introduction 3 What is Remote Process Explorer? 3 Before Installing 3 How can I download Remote Process Explorer? 3 Will
Remote Process Explorer Frequently Asked Questions LizardSystems Table of Contents Introduction 3 What is Remote Process Explorer? 3 Before Installing 3 How can I download Remote Process Explorer? 3 Will
PRE32 RS232 protocol v1.21 Tomas Andersson
 PRE32 RS232 protocol 2014-11-07 v1.21 Tomas Andersson Description This document describes the RS232 protocol used to control the PRE32 device. Command structure Commands are sent to the device using the
PRE32 RS232 protocol 2014-11-07 v1.21 Tomas Andersson Description This document describes the RS232 protocol used to control the PRE32 device. Command structure Commands are sent to the device using the
SoupBinTCP for Nasdaq Nordic. Version August 21, 2015
 SoupBinTCP for Nasdaq Nordic Version 3.00.2 August 21, 2015 Overview Confidentiality/Disclaimer Confidentiality/Disclaimer This specification is being forwarded to you strictly for informational purposes
SoupBinTCP for Nasdaq Nordic Version 3.00.2 August 21, 2015 Overview Confidentiality/Disclaimer Confidentiality/Disclaimer This specification is being forwarded to you strictly for informational purposes
User Guide IP Connect CSD
 The contents of this document are subject to revision without notice due to continued progress in methodology, design and manufacturing. Wireless Maingate AB shall have no liability for any error or damages
The contents of this document are subject to revision without notice due to continued progress in methodology, design and manufacturing. Wireless Maingate AB shall have no liability for any error or damages
Managing GSS User Accounts Through a TACACS+ Server
 CHAPTER 4 Managing GSS User Accounts Through a TACACS+ Server This chapter describes how to configure the GSS, primary GSSM, or standby GSSM as a client of a Terminal Access Controller Access Control System
CHAPTER 4 Managing GSS User Accounts Through a TACACS+ Server This chapter describes how to configure the GSS, primary GSSM, or standby GSSM as a client of a Terminal Access Controller Access Control System
CSMC 417. Computer Networks Prof. Ashok K Agrawala Ashok Agrawala Set 4. September 09 CMSC417 Set 4 1
 CSMC 417 Computer Networks Prof. Ashok K Agrawala 2009 Ashok Agrawala Set 4 1 The Data Link Layer 2 Data Link Layer Design Issues Services Provided to the Network Layer Framing Error Control Flow Control
CSMC 417 Computer Networks Prof. Ashok K Agrawala 2009 Ashok Agrawala Set 4 1 The Data Link Layer 2 Data Link Layer Design Issues Services Provided to the Network Layer Framing Error Control Flow Control
HP 5120 SI Switch Series
 HP 5120 SI Switch Series Network Management and Monitoring Configuration Guide Part number: 5998-1813 Software version: Release 1505 Document version: 6W102-20121111 Legal and notice information Copyright
HP 5120 SI Switch Series Network Management and Monitoring Configuration Guide Part number: 5998-1813 Software version: Release 1505 Document version: 6W102-20121111 Legal and notice information Copyright
CSC 401 Data and Computer Communications Networks
 CSC 401 Data and Computer Communications Networks Transport Layer Intro, Mutliplexing/Demultiplexing, UDP Sec 3.1 3.4 Prof. Lina Battestilli Fall 2017 Chapter 3: Transport Layer our goals: understand principles
CSC 401 Data and Computer Communications Networks Transport Layer Intro, Mutliplexing/Demultiplexing, UDP Sec 3.1 3.4 Prof. Lina Battestilli Fall 2017 Chapter 3: Transport Layer our goals: understand principles
migra CAN Large Format Graphics Compatible LED Display with CANopen Interface
 User s Manual Table of Contents 1 GENERAL 5 2 OVERVIEW 6 3 TECHNICAL DATA 7 3.1 General Specifications 7 3.2 Device Configuration 8 3.3 Tips and Tricks 9 3.4 Display Elements 10 3.5 System and Device Initialisation
User s Manual Table of Contents 1 GENERAL 5 2 OVERVIEW 6 3 TECHNICAL DATA 7 3.1 General Specifications 7 3.2 Device Configuration 8 3.3 Tips and Tricks 9 3.4 Display Elements 10 3.5 System and Device Initialisation
ECE4110 Internetwork Programming. Introduction and Overview
 ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
Lock and Key: Dynamic Access Lists
 Lock and Key: Dynamic Access Lists Document ID: 7604 Contents Introduction Prerequisites Requirements Components Used Conventions Spoofing Considerations Performance When to Use Lock and Key Access Lock
Lock and Key: Dynamic Access Lists Document ID: 7604 Contents Introduction Prerequisites Requirements Components Used Conventions Spoofing Considerations Performance When to Use Lock and Key Access Lock
PROBLEMSAND EXERCISES
 Departamento de Tecnología Electrónica Computer Networking Unit 3: Transport layer PROBLEMSAND EXERCISES Transport Layer 95 Pr1: port numbers Suppose that the client A initiates a TCP connection to a Web
Departamento de Tecnología Electrónica Computer Networking Unit 3: Transport layer PROBLEMSAND EXERCISES Transport Layer 95 Pr1: port numbers Suppose that the client A initiates a TCP connection to a Web
match protocol http cookie (cookie map submode)
 Chapter 2 22 match protocol http cookie (cookie map submode) match protocol http cookie (cookie map submode) To add cookies to a cookie map, use the match protocol http cookie command in SLB cookie map
Chapter 2 22 match protocol http cookie (cookie map submode) match protocol http cookie (cookie map submode) To add cookies to a cookie map, use the match protocol http cookie command in SLB cookie map
JUMO ctron 04/08/16. Compact controller with timer and ramp function. B Interface Description Modbus /
 JUMO ctron 04/08/16 Compact controller with timer and ramp function 702071 702072 702074 B 70.2070.2.0 Interface Description Modbus 2008-08-11/00492538 Contents 1 Introduction 5 1.1 Preface... 5 1.2 Typographical
JUMO ctron 04/08/16 Compact controller with timer and ramp function 702071 702072 702074 B 70.2070.2.0 Interface Description Modbus 2008-08-11/00492538 Contents 1 Introduction 5 1.1 Preface... 5 1.2 Typographical
