Linear Network Coding
|
|
|
- Dominic Edwards
- 6 years ago
- Views:
Transcription
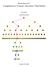
1 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 2, FEBRUARY Linear Network Codin Shuo-Yen Robert Li, Senior Member, IEEE, Raymond W. Yeun, Fellow, IEEE, Nin Cai Abstract Consider a communication network in which certain source nodes multicast inormation to other nodes on the network in the multihop ashion where every node can pass on any o its received data to others. We are interested in how ast each node can receive the complete inormation, or equivalently, what the inormation rate arrivin at each node is. Allowin a node to encode its received data beore passin it on, the question involves optimization o the multicast mechanisms at the nodes. Amon the simplest codin schemes is linear codin, which reards a block o data as a vector over a certain base ield allows a node to apply a linear transormation to a vector beore passin it on. We ormulate this multicast problem prove that linear codin suices to achieve the optimum, which is the max-low rom the source to each receivin node. Index Terms Codin, network routin, switchin. I. INTRODUCTION DEFINE a communication network as a pair,, where is a inite directed multiraph is the unique node in without any incomin edes. A directed ede in is called a channel in the communication network,. The special node is called the source, while every other node may serve as a sink as we shall explain. A channel in raph represents a noiseless communication link on which one unit o inormation (e.., a bit) can be transmitted per unit time. The multiplicity o the channels rom a node to another node represents the capacity o direct transmission rom to. In other words, every sinle channel has unit capacity. At the source, a inite amount o inormation is enerated multicast to other nodes on the network in the multihop ashion where every node can pass on any o its received data to other nodes. At each nonsource node which serves as a sink, the complete inormation enerated at is recovered. We are naturally interested in how ast each sink node can receive the complete inormation. As an example, consider the multicast o two data bits,, rom the source in the communication network depicted by Manuscript received November 4, 1999; revised September 12, The work o S.-Y. R. Li was supported in part by an MTK Computers Grant. The work o R. W. Yeun N. Cai was supported in part by the RGC Earmarked Grant CUHK4343/98E. The material in this paper was presented in part at the 1999 IEEE Inormation Theory Workshop, Metsovo, Greece, June/July S.-Y. R. Li R. W. Yeun are with the Department o Inormation Enineerin, The Chinese University o Hon Kon, N.T., Hon Kon ( bobli@ie.cuhk.edu.hk; whyeun@ie.cuhk.edu.hk). N. Cai was with Department o Inormation Enineerin, The Chinese University o Hon Kon, N.T., Hon Kon. He is now with the Fakultät ür Mathematik, Universität Bieleeld, Bieleeld, Germany ( cai@mathematik.uni-bieleeld.de). Communicated by V. Anantharam, Associate Editor or Communication Networks. Diital Object Identiier /TIT Fi. 1. Two communication networks. Fi. 1(a) to both nodes. One solution is to let the channels,,, carry the bit channels,,, carry the bit. Note that in this scheme, an intermediate node sends out a data bit only i it receives the same bit rom another node. For example, the node receives the bit sends a copy on each o the two channels. Similarly, the node receives the bit sends a copy into each o the two channels. In our model, we assume that there is no processin delay at the intermediate nodes. Unlike a conserved physical commodity, inormation can be replicated or coded. Introduced in [1] (see also [5, Ch. 11]), the notion o network codin reers to codin at the intermediate nodes when inormation is multicast in a network. Let us now illustrate network codin by considerin the communication network depicted by Fi. 1(b). In this network, we want to multicast two bits rom the source to both the nodes. A solution is to let the channels,, carry the bit, channels,, carry the bit, channels,, carry the exclusive-or. Then, the node receives, rom which the bit can be decoded. Similarly, the node can decode the bit rom. The codin/decodin scheme is assumed to have been areed upon beoreh. It is not diicult to see that the above scheme is the only solution to the problem. In other words, without network codin, it is impossible to multicast two bits per unit time rom the source to both the nodes. This shows the advantae o network codin. In act, replication o data can be rearded as a special case o network codin. As we have pointed out, the natures o physical commodities inormation are very dierent. Nevertheless, both o them are overned by certain laws o low. For the network low o a physical commodity, we have the ollowin. The law o commodity low: The total volume o the outlow rom a nonsource node cannot exceed the total volume o the inlow /03$ IEEE
2 372 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 2, FEBRUARY 2003 The counterpart or a communication network is as ollows. The law o inormation low: The content o any inormation lowin out o a set o nonsource nodes can be derived rom the accumulated inormation that has lown into the set o nodes. Ater all, inormation replication codin do not increase the inormation content. The inormation rate rom the source to a sink can potentially become hiher hiher when the permitted class o codin schemes is wider wider. However, the law o inormation low limits this inormation rate to the max-low (i.e., the maximum commodity low) rom the source to that particular sink or a very wide class o codin schemes. The details are iven in [1]. It has been proved in [1] that the inormation rate rom the source to a set o nodes can reach the minimum o the individual max-low bounds throuh codin. In the present paper, we shall prove constructively that by linear codin alone, the rate at which a messae reaches each node can achieve the individual max-low bound. (This result is somewhat stroner than the one in [1]. Please reer to the example in Section III.) More explicitly, we treat a block o data as a vector over a certain base ield allow a node to apply a linear transormation to a vector beore passin it on. A preliminary version o this paper has appeared in the conerence proceedins [3]. The remainder o the paper is oranized as ollows. In Section II, we introduce the basic notions, in particular, the notion o a linear-code multicast (LCM). In Section III, we show that with a eneric LCM, every node can simultaneously receive inormation rom the source at rate equal to its max-low bound. In Section IV, we describe the physical implementation o an LCM irst when the network is acyclic then when the network is cyclic. In Section V, we present a reedy alorithm or constructin a eneric LCM or an acyclic network. The same alorithm can be applied to a cyclic network by expin the network into an acyclic network. This results in a timevaryin LCM, which, however, requires hih complexity in implementation. In Section VI, we introduce the time-invariant LCM (TILCM) present a heuristic or constructin a eneric TILCM. Section VII presents concludin remarks. II. BASIC NOTIONS In this section, we irst introduce some raph-theoretic terminoloy notations which will be used throuhout the paper. Then we will introduce the notion o an LCM, an abstract alebraic description o a linear code on a communication network. Convention: The eneric notation or a nonsource node will be,,,,, or. The notation will st or any channel rom to. Deinition: Over a communication network a low rom the source to a nonsource node is a collection o channels, to be called the busy channels in the low, such that 1) the subnetwork deined by the busy channels is acyclic, i.e., the busy channels do not orm directed cycles; 2) or any node other than, the number o incomin busy channels equals the number o outoin busy channels; 3) the number o outoin busy channels rom equals the number o incomin busy channels to. In other words, a low is an acyclic collection o channels that abides by the law o commodity low. The number o outoin busy channels rom will be called the volume o the low. The node is called the sink o the low. All the channels on the communication network that are not busy channels o the low are called the idle channels with respect to the low. Proposition 2.1: The busy channels in a low with volume can be partitioned into simple paths rom the source to the sink. The proo o this proposition is omitted. Notation: For every nonsource node on a network,, the maximum volume o a low rom the source to is denoted as, or simply when there is no ambiuity. Deinition: A cut on a communication network, between the source a nonsource node means a collection o nodes which includes but not. A channel is said to be in the cut i. The number o channels in a cut is called the value o the cut. The well-known Max-Flow Min-Cut Theorem (see, or example, [2, Ch. 4, Theorem 2.3]) still applies despite the acyclic restriction in the deinition o a low. Max-Flow Min-Cut Theorem: For every nonsource node, the minimum value o a cut between the source a node is equal to. We are now ready to deine a linear code multicast. Notation: Let be the maximum o over all. Throuhout Sections II V, the symbol will denote a ixed -dimensional vector space over a suiciently lare base ield. Convention: The inormation unit is taken as a symbol in the base ield. In other words, symbol in the base ield can be transmitted on a channel every unit time. Deinition: A linear-code multicast (LCM) on a communication network, is an assinment o a vector space to every node a vector to every channel such that 1) ; 2) or every channel ; 3) or any collection o nonsource nodes in the network The notation is or linear span. Condition 3) says that the vector spaces on all nodes inside toether have the same linear span as the vectors on all channels to nodes in rom outside o. Conditions 2) 3) show that an LCM abides by the law o inormation low stated in Section I. The vector assined to every channel may be identiied with a -dimensional column vector over the base ield o by choosin a basis or. Applyin Condition 3) to the collection o a sinle nonsource node, the space is linearly spanned by vectors
3 LI et al.: LINEAR NETWORK CODING 373 on all incomin channels to. This shows that an LCM on a communication network is completely determined by the vectors it assins to the channels. Toether with Condition 2), we have 4) The vector assined to an outoin channel rom must be a linear combination o the vectors assined to the incomin channels o. Condition 4) may be rearded as the law o inormation low at a node. However, unlike in network low theory, the law o inormation low bein observed or every sinle node does not necessarily imply it bein observed or every set o nodes when the network contains a directed cycle. A counterexample will appear in Section IV. An LCM speciies a mechanism or data transmission over the network as ollows. We encode the inormation to be transmitted rom as a -dimensional row vector, which we shall call the inormation vector. Under the transmission mechanism prescribed by the LCM, the data lowin on a channel is the matrix product o the inormation (row) vector with the (column) vector. In this way, the vector acts as the kernel in the linear encoder or the channel. As a direct consequence o the deinition o an LCM, the vector assined to an outoin channel rom a node is a linear combination o the vectors assined to the incomin channels to. Consequently, the data sent on an outoin channel rom a node is a linear combination o the data sent on the incomin channels to. Under this mechanism, the amount o inormation reachin a node is iven by the dimension o the vector space when the LCM is used. The physical realization o this mechanism will be discussed in Section IV. Example 2.2: Consider the multicast o two bits,, rom to in the communication network in Fi. 1(b). This is achieved with the LCM speciied by Hence,, which is at most equal to the value o the cut. In particular, is upper-bounded by the minimum value o a cut between, which by the Max-Flow Min-Cut Theorem is equal to. This corollary says that is an upper bound on the amount o inormation received by when an LCM is used. III. ACHIEVING THE MAX-FLOW BOUND THROUGH A GENERIC LCM In this section, we derive a suicient condition or an LCM to achieve the max-low bound on in Proposition 2.3. Deinition: An LCM on a communication network is said to be eneric i the ollowin condition holds or any collection o channels or : or i only i the vectors,,, are linearly independent. I are linearly independent, then since. A eneric LCM requires that the converse is also true. In this sense, a eneric LCM assins vectors which are as linearly independent as possible to the channels. Example 3.1: With respect to the communication network in Fi. 1(b), the LCM in Example 2.2 is a eneric LCM. However, the LCM deined by is not eneric. This is seen by considerin the set o channels where The data sent on a channel is the matrix product o the row vector with the column vector assined to that channel by. For instance, the data sent on the channel is. Note that, in the special case when the base ield o is GF, the vector reduces to the exclusive-or in an earlier example. Proposition 2.3: For every LCM on a network, or all nodes Then,but are not linearly independent. Thereore, is not eneric. Lemma 3.2: Let be a eneric LCM. Any collection o channels rom a node with must be assined linearly independent vectors by. Theorem 3.3: I is a eneric LCM on a communication network, then or all nodes Proo: Fix a nonsource node any cut between the source Proo: Consider a node not equal to. Let be the common value o the minimum value o a cut between. The inequality
4 374 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 2, FEBRUARY 2003 ollows rom Proposition 2.3. Thus, we only have to show that. Let or any cut between. We will show that by contradiction. Assume let be the collection o cuts between such that. Since implies, where is the set o all the nodes in, is nonempty. By the assumption that is a eneric LCM, the number o edes out o is at least,. Thereore,. Then there must exist a minimal member in the sense that or any,. Clearly, because. Let be the set o channels in cut be the set o boundary nodes o, i.e., i only i there is a channel, such that. Then or all, which can be seen as ollows. The set o channels in cut but not in is iven by. Since is an LCM I, then, is con- the subspace spanned by the channels in cut tained by. This implies Proo: By removin an ede, the value o a cut between the source node (respectively, node ) is reduced by i ede is in, otherwise, the value o is unchaned. By the Max-Flow Min-Cut Theorem, we see that are reduced by at most when ede is removed rom the raph. Now consider the value o a cut between the source node.i contains node, then ede is not in,, thereore, the value o remains unchaned upon the removal o ede.i does not contain node, then is a cut between the source node. By the Max-Flow Min-Cut Theorem, the value o is at least. Then upon the removal o ede, the value o is lower-bounded by. Hence, by the Max-Flow Min-Cut Theorem, remains to be upon the removal o ede. The lemma is proved. Example 3.5: Consider a communication network or which,,or or nodes in the network. The source is to broadcast 12 symbols,, taken rom a suiciently lare base ield. (Note that is the least common multiple o,,.) Deine the set or For simplicity, we use the second as the time unit. We now describe how,, can be broadcast to the nodes in,, in 3, 4, 12 s, respectively, assumin the existence o an LCM on the network or. a) Let be an LCM on the network with. Let a contradiction. Thereore, or all,. For all, since implies Then, by the deinition o a eneric LCM, is a collection o vectors such that. Finally, by the Max-Flow Min-Cut Theorem,, since,. This is a contradiction to the assumption that. The theorem is proved. An LCM or which or all provides a way or broadcastin a messae enerated at the source or which every nonsource node receives the messae at rate equal to. This is illustrated by the next example, which is based upon the assumption that the base ield o is an ininite ield or a suiciently lare inite ield. In this example, we employ a technique which is justiied by the ollowin lemma. Lemma 3.4: Let, be nodes such that,,, where. By removin any ede in the raph, are reduced by at most, remains unchaned. In the irst second, transmit as the inormation vector usin, in the second second, transmit, in the third second, transmit. Ater 3 s, all the nodes in can recover,,. Throuhout this example, we assume that all transmissions computations are instantaneous. b) Let be a vector in such that intersects trivially with or all in, i.e., or all in. Such a vector can be ound when is suiciently lare because there are a inite number o nodes in. Deine or. Now remove incomin edes o nodes in, i necessary, so that becomes i is in, otherwise, remains unchaned. This is possible by virtue o Lemma 3.4. Let be an LCM on the resultin network with. Let transmit as the inormation vector usin in the ourth second. Then all the nodes in can recover hence,,. c) Let be two vectors in such that intersects with trivially or all in, i.e.,,, or all in. Deine or. Now remove incomin edes o nodes in, i necessary, so that becomes
5 LI et al.: LINEAR NETWORK CODING 375 i is in or, otherwise, remains unchaned. Aain, this is possible by virtue o Lemma 3.4. Now let be an LCM on the resultin network with. In the ith the sixth seconds, transmit as the inormation vectors usin. Then all the nodes in can recover. d) Let be two vectors in such that, intersects with trivially or all in, i.e.,,,, or all in. Deine. In the seventh eihth seconds, transmit as the inormation vectors usin. Since all the nodes in already knows, upon receivin, can then be recovered. e) Deine. In the nineth tenth seconds, transmit as the inormation vectors usin. Then can be recovered by all the nodes in. ) Deine. In the eleventh twelveth seconds, transmit as the inormation vectors usin. Then can be recovered by all the nodes in. Let us now ive a summary o the precedin scheme. In the th second or via the eneric LCM, each node in receives all our dimensions o, each node in receives three dimensions o, each node in receives one dimension o. In the ourth second, via the eneric LCM, each node in receives the vector, which provides the three missin dimensions o,, (one dimension or each) durin the irst 3 s o multicast by. At the same time, each node in receives one dimension o. Now, in order to recover, each node in needs to receive the two missin dimensions o durin the ourth second. This is achieved by the eneric LCM in the ith sixth seconds. So ar, each node in has received one dimension o or via durin the irst 3 s, one dimension o or rom via durin the ourth to sixth seconds. Thus, it remains to provide the six missin dimensions o,, (two dimensions or each) to each node in, this is achieved in the seventh to the twelveth seconds via the eneric LCM. Remark: The scheme in Example 3.5 can readily be eneralized to arbitrary sets o max-low values. The details are omitted here. In the scheme in Example 3.5, at the end o the 12-s session, each node receives a messae o 12 symbols taken rom the base ield. Thus, the averae inormation rate arrivin at each node over the whole session is 1 symbol/s. The result in [1] asserts that this rate, which is the minimum o the individual max-low bounds o all the nodes in the network, can be achieved. However, it is seen in our scheme that the nodes in,, can actually receive the whole messae in the irst 3, 4, 12 s, respectively. In this sense, each node in our scheme can receive the messae at rate equal to its individual max-low bound. Thus, our result is somewhat stroner than that in [1]. However, our result does not mean that inormation can be multicast continually rom the source to each node at rate equal to its individual max-low bound. I it is not necessary or the nodes in to receive the messae, i.e., the messae is multicast to the nodes in only, the session can be terminated ater 4 s. Then the averae inormation rate arrivin at each node in over the truncated session is 3 symbols/s, with the nodes in receivin the whole messae in the irst 3 4 s, respectively. IV. THE TRANSMISSION SCHEME ASSOCIATED WITH AN LCM Let be an LCM on a communication network,, where the vectors assined to outoin channels linearly span a -dimensional space. As beore, the vector assined to a channel is identiied with a -dimensional column vector over the base ield o by means o the choice o a basis. On the other h, the total inormation to be transmitted rom the source to the rest o the network is represented by a -dimensional row vector, called the inormation vector. Under the transmission scheme prescribed by the LCM, the data lowin over a channel is the matrix product o the inormation vector with the column vector.wenow consider the physical realization o this transmission scheme associated with an LCM. Deinition: A communication network, is said to be acyclic i the directed multiraph does not contain a directed cycle. Lemma 4.1: An LCM on an acyclic network, is an assinment o a vector space to every node a vector to every channel such that 1) ; 2) or every channel ; 3) or every nonsource node, the space is the linear span o vectors on all incomin channels to. In other words, or an acyclic network, the law o inormation low bein observed or every sinle node implies it bein observed or every set o nodes. Proo: Let be a set o nonsource nodes on an acyclic network. Let an ede be called an internal ede o when. Similarly, let an ede be called an incomin ede o when. We need to show that, or every internal ede o, is enerated by is an incomin ede o Because the network is acyclic, there exists a node in without any ede, where. Thus, 1) every incomin ede o is an incomin ede o. By induction on, we may assume that or every internal ede o 2) is enerated by : is an incomin ede o. Given an internal ede o, we need to show that is enerated by : is an incomin ede o. Since is enerated by is an ede
6 376 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 2, FEBRUARY 2003 it suices to show that is enerated by : is an incomin ede o. I the ede is incomin o, then it is incomin to by ). Otherwise, is enerated by is an incomin ede o accordin to 2), thereore, is also enerated by is an incomin ede o because o 1). Lemma 4.2: The nodes on an acyclic communication network can be sequentially indexed such that every channel is rom a smaller indexed node to a larer indexed node. Lemma 4.3: Assume that nodes in a communication network are sequentially indexed as such that every channel is rom a smaller indexed node to a larer indexed node. Then, every LCM on the network can be constructed by the ollowin procedure: or (j =0; j n; j++) arrane all outoin channels X jy rom X j in an arbitrary order; take one outoin channel rom X j at a time let the channel taken be X jy ; assin v(x jy ) to be a vector in the space v(x j ); v(x j+1) = linear span by vectors v(xx j+1) on all incomin channels XX j+1 to X j+1; On an acyclic network, a straihtorward realization o the above transmission scheme is as ollows. Take one node at a time accordin to the sequential indexin. For each node, wait until data is received rom every incomin channel beore perormin the linear encodin. Then send the appropriate data on each outoin channel. This physical realization o an LCM over an acyclic network, however, does not apply to a network that contains a directed cycle. This is illustrated by the ollowin example. Example 4.4: Let be vectors in, where are linearly independent. Deine This speciies an LCM on the network illustrated in Fi. 2 i the vector is a linear combination o. Otherwise, the unction ives an example in which the law o inormation low is observed or every sinle node but not observed or Fi. 2. An LCM on a cyclic network. every set o nodes. Speciically, the law o inormation low is observed or each o the nodes,,, but not or the set o nodes,,. Now, assume that Then, is an LCM. Write the inormation vector as, where belon to the base ield o. Accordin to the transmission scheme associated with the LCM, all three channels on the directed cycle transmit the same data. This leads to the loical problem o how any o these cyclic channels acquires the data in the irst place. In order to realize the transmission scheme associated with an LCM over a network containin a directed cycle, we shall introduce the parameter o time into the scheme. Instead o transmittin a sinle data symbol (i.e., an element o the base ield o ) throuh each channel, we shall transmit a time-parameterized stream o symbols. In other words, the channel will be time-slotted. Concomitantly, the operation o codin at a node will be time-slotted, as well. Deinition: Given a communication network, a positive inteer, the associated memoryless communication network denoted as, is deined as ollows. The set o nodes in includes the node all the pairs o the type,, where is a nonsource node in ranes throuh inteers to. The channels in the network, belon to one o the three types listed below. For any nonsource nodes in, 1) or, the multiplicity o the channel rom to, is the same as that o the channel in the network, ; 2) or, the multiplicity o the channel rom, to, is the same as that o the channel in the network, ; 3) or, the multiplicity o the channel rom, to, is equal to. Lemma 4.5: The memoryless communication network, is acyclic. Lemma 4.6: There exists a ixed number, independent o, such that or all nonsource nodes in,, the maximum volume o a low rom to the node, in, is at least times.
7 LI et al.: LINEAR NETWORK CODING 377 Proo: Given a nonsource node in, consider a maximum low rom to in the network,. This maximum low may be partitioned into directed simple paths rom to. Let be the maximum lenth amon these directed simple paths. Then, there exists a low rom to the node, in, that is isomorphic to the maximum low in,. Moreover, time-shited isomorphs o this low in, are lows rom to, or. Moreover, the isomorphs are ede-disjoint lows in the network, due to the acyclic nature in the deinition o a low. The union o these lows, toether with edes rom, to, or in,, constitute a low rom to, with volume times. The proo is completed by choosin to be the larest minus amon all. Transmission o data symbols over the network, may be interpreted as memoryless transmission o data streams over the network, as ollows. 1) A symbol sent rom to, in, corresponds to the symbol sent on the channel in, durin the time slot. 2) A symbol sent rom, to, in, corresponds to the symbol sent on the channel in, durin the time slot. This symbol is a linear combination o symbols received by durin the time slot is unrelated to symbols received earlier by. 3) The channels rom, to, or siniy the accumulation o received inormation by the node in, over time. Now suppose an LCM has been constructed on the network,. Since this is an acyclic network, the LCM can be physically realized in the way mentioned above. The physical realization can then be interpreted as a memoryless transmission o data streams over the oriinal network,. Transmission, with memory, o data streams over the oriinal network, is associated with the acyclic network deined below, which is just a sliht modiication rom,. Deinition: Given a communication network, a positive inteer, the associated communication network with memory, denoted as,, is deined as ollows. The set o nodes in includes the node all pairs o the type,, where is a nonsource node in ranes throuh inteers to. Channels in the network, belon to one o the three types listed below. For any nonsource nodes in, 1) or, the multiplicity o the channel rom to, is the same as that o the channel in the network ; 2) or, the multiplicity o the channel rom, to, is the same as that o the channel in the network ; 3) or, the multiplicity o channels rom, to is equal to times. Lemma 4.7: The communication network, is acyclic. Lemma 4.8: Every low rom the source to the node in the network, corresponds to a low with the same volume rom the source to the node, in the network,. Lemma 4.9: Every LCM on the network, corresponds to an LCM on the network, such that or all nodes in Communication networks with or without memory both have been deined in order to compensate or the lack o a direct physical realization o an LCM on a network that may contain a directed cycle. In Section VI, we shall present another way to make the compensation, which will oer a physical realization by time-invariant linear codin. V. CONSTRUCTION OF A GENERIC LCM ON AN ACYCLIC COMMUNICATION NETWORK We have proved that or a eneric LCM, the dimension o the vector space at each node is equal to the maximum low between. However, we have not shown how one can construct a eneric LCM or a iven communication network. In the next theorem, we present a procedure which constructs a eneric LCM or any acyclic communication network. Theorem 5.1: A eneric LCM exists on every acyclic communication network, provided that the base ield o is an ininite ield or a lare enouh inite ield. Proo: Let the nodes in the acyclic network be sequentially indexed as, such that every channel is rom a smaller indexed node to a larer indexed node. The ollowin procedure constructs an LCM by assinin a vector to each channel, one channel at a time. or all channels XY v(xy )= the zero vector; // initialization or (j =0; j n; j++) arrane all outoin channels X jy rom X j in an arbitrary order; take one outoin channel rom X j at a time let the channel taken be X j Y ; choose a vector w in the space v(x j ) such that w =2 hv(uz): UZ 2 i or any collection o at most d 0 1 channels with v(x j) 6 hv(uz): UZ 2 i; v(x j Y )=w; v(x j+1) = the linear span by vectors v(xx j+1) on all incomin channels XX j+1 to X j+1 ;
8 378 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 2, FEBRUARY 2003 The essence o the above procedure is to construct the eneric LCM iteratively make sure that in each step the partially constructed LCM is eneric. One point in the above construction procedure o needs to be clariied. Given a node, there can be only initely many collections o cardinality at most such that :. When the base ield o is lare enouh where the union is over all such. Hence, the choice o the vector in the above procedure has been possible. Let be any collection o channels such that or. In order to assert that the LCM is eneric, we need to prove the linear independence amon the vectors,,,. The proo is by induction on. Without loss o enerality, we may assume that is the last amon the channels to be assined a vector in the above construction procedure o. Since the construction procedure ives On the other h, the induction hypothesis asserts the linear independence amon. Thus, the vectors are linearly independent. The theorem is proved. Given a communication network, a positive inteer, there exists a eneric LCM on the associated memoryless communication network, by Lemma 4.5 Theorem 5.1. From Theorem 3.3, or every node in,, the dimension o or the node, in, is equal to the maximum volume o a low rom the source to,. This maximum volume, accordin to Lemma 4.6, is at least times, where is a ixed inteer. In view o Lemmas , we have the ollowin similar conclusion about the adapted communication network. For every node in,, the dimension o the space or the correspondin node, in, is equal to the maximum volume o a low rom the source to, in,, this maximum volume is at least times or some ixed number. We now translate this conclusion about linear-code multicast over the memoryless network back to the oriinal network,. Let be the minimum o over all nonsource nodes in. Then or a suiciently lare inteer, usin the technique in Example 3.5, it is possible to desin a broadcast session o lenth equal to time units which broadcasts a messae o approximately symbols rom the source. Moreover, the whole messae can be recovered at each nonsource node ater approximately time units. VI. TIME-INVARIANT LCM AND HEURISTIC CONSTRUCTION Let be a inite ield. Let denote the rin o ormal power series over with the variable. is a principal ideal domain, every ideal in it is enerated by or some. Alebraic properties o vector spaces over a ield can oten be eneralized to modules over a principle ideal domain. In act, our previous results on LCM eneric LCM on vector spaces can readily be eneralized to modules over. The concept o the dimension o a vector space is eneralized to the rank o a module. To acilitate our discussion, we shall reer to the rank o a module over as its dimension. The elements o the module will be called vectors. Throuhout this section, we assume that is a module over with a inite but very lare dimension (say, larer than the number o channels times the lenth o transmission stream in the problem instance). Physically, an element o is the -transorm o a stream o symbols,,,,, that are sent on a channel, one symbol at a time. The ormal variable is interpreted as a unit-time shit. Deinition: A time-invariant linear-code multicast (TILCM) on a communication network, is an assinment o a module over to every node a vector to every channel such that 1) ; 2) or every channel ; 3) or any collection o nonsource nodes in the network In particular, the vector assined to an outoin channel rom a node is times a linear combination o the vectors assined to incomin channels to the same node. Hence a TILCM is completely determined by the vectors that it assins to channels. The adoption o times a linear combination, instead o simply any linear combination, allows a unit-time delay or transmission/codin. This allows a physical realization or the transmission scheme speciied by a TILCM. I a certain physical system requires nonuniorm duration o delay on dierent channels, then artiicial nodes need to be inserted. For instance, i the delay on a channel is three unit times, then two serial nodes should be added on the channel so that the channel becomes a tem o three channels. Example 6.1: On the communication network illustrated in Fi. 2, deine the TILCM by One can readily check that is in act a TILCM. For example Thus, is equal to times the linear combination o with coeicients, respectively. This speciies an encodin process or the channel that does not chane with time. It can be seen that the same is true or the encodin process o every other channel in the network. This explains the terminoloy time-invariant or an LCM.
9 LI et al.: LINEAR NETWORK CODING 379 Write the inormation vector as, where belon to. The product o the inormation (row) vector with the (column) vector assined to that channel represents the data stream transmitted over a channel Fi. 3. Redundant channels in a network. That is, the data symbol is sent on the channel at the time slot. This TILCM, besides bein time invariant in nature, is a memoryless one because the ollowin linear equations allows an encodin mechanism that requires no memory: Adopt the convention that or all. Then the data symbol lowin over the channel, or example, at the time slot is or all. Example 6.2: Another TILCM on the same communication network can be deined by The data stream transmitted over the channel is represented by, or instance, There are potentially various ways to deine a eneric TILCM, as an analo to Theorem 3.3, to establish desirable dimensions o the module assined to every node. Another desirable characteristic o a TILCM is to be memoryless. Empirically, it has been relatively easy to construct a TILCM that carries all conceivable desirable properties. The remainder o this section presents a heuristic construction procedure or a ood TILCM. The heuristic construction will ollow the raph-theoretical block decomposition o the network. For the sake o computational eiciency, the procedure will irst remove redundant channels rom the network beore identiyin the blocks so that the blocks are smaller. Deinition: A channel in a communication network is said to be irredundant i it is on a simple path startin at the source. Else, it is said to be redundant. Moreover, a communication network is said to be irredundant i it contains no redundant channels. Example 6.3: In the network illustrated in Fi. 3, the channels,, are redundant. Lemma 6.4: The deletion o a redundant channel rom a network results in a subnetwork with the same set o irredundant channels. Consequently, the irredundant channels in a network deine an irredundant subnetwork. Theorem 6.5: Let be an LCM (respectively, a TILCM) on a network. Then also deines an LCM (respectively, a TILCM) on the subnetwork that results rom the deletion o any redundant channel.
10 380 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 2, FEBRUARY 2003 Proo: We shall prove the case o LCM, the case o TILCM bein similar. Denote the deleted redundant channel as. Given a set o nonsource nodes with, we need to show Due to the redundancy o, any simple path rom to must o throuh the node. Let denote the set consistin o the node plus all those nodes such that any path rom to must o throuh. (I there is no simple path rom to a particular node, then that node ully qualiies as a node in.) Then, every channel rom outside o into must be toward the node. Thereore, This implies the desired equality. Corollary 6.6: Let be an LCM (respectively, a TILCM) on a network. Then deines an LCM (respectively, a TILCM) on the subnetwork ormed by irredundant channels. In a directed multiraph, an equivalence relationship (which by deinition is relexive, symmetric transitive) amon nodes can be deined as ollows. Two nodes are equivalent i there exists a directed path leadin rom one node to the other vice versa. An equivalence class under this relationship is called a block in the raph. The source node by itsel always orms a block. When every block contracts into a sinle node, the resultin raph is acyclic. In other words, the blocks can be sequentially indexed so that every interblock channel is rom a smaller indexed block to a larer indexed block. For the construction o a ood TILCM, smaller sizes o blocks tend to acilitate the computation. The extreme avorable case o the block decomposition o a network is when the network is acyclic, which implies that every block consists o a sinle node. The opposite extreme is when all nonsource nodes orm a sinle block exempliied by the network illustrated in Fi. 3. The removal o redundant channels sometimes serves or the purpose o breakin up a block into pieces. For the network illustrated in Fi. 3, the removal o the three redundant channels breaks the block,,,, into the three blocks,,,,. In the construction o a ood LCM on an acyclic network, the procedure inside the proo o Theorem 5.1 takes one node at a time accordin to the acyclic orderin o nodes assins vectors to outoin channels rom the taken node. For a eneral network, we can start with the trivial TILCM on the network consistin o just the source then exp it to a ood TILCM that covers one more block at a time. The sequential choices o blocks are accordin to the acyclic order in the block decomposition o the network. Thus, the expansion o the ood TILCM at each step involves only incomin channels to nodes in the new block. A heuristic alorithm or assinin vectors to such channels is or to be times an arbitrary convenient linear combination o vectors assined to incomin channels to. In this way, a system o linear equations o the orm o is set up, where is a square matrix with the dimension equal to the total number o channels in the network is the unknown column vector whose entries are or all channels. The elements o are polynomials in. In particular, the elements o are either or a polynomial in containin the actor. Thereore, the determinant o is a ormal power series with the constant term (the zeroth power o ) bein,, hence is invertible in. Accordin to Cramer s rule, a unique solution exists. (This is consistent with the physical intuition because the whole network is completely determined once the encodin process or each channel is speciied.) I this unique solution does not happen to satisy the requirement or bein a ood TILCM, then the heuristic alorithm calls or adjustments on the coeicients o the linear equations on the trial--error basis. Ater a ood TILCM is constructed on the subnetwork ormed by irredundant channels in a iven network, we may simply assin the zero vectors to all redundant channels. Example 6.7: Ater the removal o redundant channels, the network depicted by Fi. 3 consists o our blocks in the order o,,,,,. The subnetwork consistin o the irst two blocks is the same as the network in Fi. 2. When we exp the trivial TILCM on the network consistin o just the source to cover the block,,, a heuristic trial would be toether with the ollowin linear equations: The result is the memoryless TILCM in the precedin example. This TILCM can be urther exped to cover the block then the block. VII. CONCLUDING REMARKS In this paper, we have presented an explicit construction o a code or multicast in a network that achieves the max-low bound on the inormation transmission rate. An important aspect o our code is its linearity, which makes encodin decodin easy to implement in practice. Our reedy alorithm or code construction works or all networks, but the code
11 LI et al.: LINEAR NETWORK CODING 381 so constructed is not necessarily the simplest possible. In act, there oten exist optimal LCMs much simpler than the ones constructed accordin to the presented reedy alorithm. Thereore, there is much room or urther research in this direction. The code we have constructed or a cyclic network is time varyin, which makes it less appealin in practice. To our knowlede, there has not been a proo or the existence o an optimal time-invariant code or a cyclic network. However, examples o such a code have been iven in the present paper also in [1]. Thereore, provin the existence o such codes, in particular, constructin such codes in simple linear orm, is a challenin problem or uture research. Further research problems in network codin include code construction when two or more sources are simultaneously multicast in the network. This is the so-called multisource network codin problem in [1] which is yet unexplored (see also [5, Ch. 15]). When networkin codin is implemented in computer or satellite networks, synchronization is a problem that needs to be addressed. Since an encoder at an intermediate node may take more than one incomin data stream as input, it is necessary to acquire synchronization amon these data streams. This is not a problem or nonreal-time applications (e.., ile transer), but it can be a serious problem or real-time applications (e.., voice video transmission). On the other h, certain types o networks, or example switchin networks, are inherently ully synchronized. These networks are excellent cidates or network codin,, in act, the possible use o linear network codes in switchin networks has been investiated [6]. ACKNOWLEDGMENT The authors would like to thank Venkat Anantharam or pointin out an error in the oriinal proo o Theorem 3.3 or his very careul readin o the manuscript. They also thank the anonymous reviewers or their useul comments. REFERENCES [1] R. Alshwede, N. Cai, S.-Y. R. Li, R. W. Yeun, Network inormation low: Sinle source, IEEE Trans. Inorm. Theory, submitted or publication. [2] E. L. Lawler, Combinatorial Optimization: Network Matroid. Fort Worth, TX: Saunder Collee Pub., [3] S.-Y. R. Li R. W. Yeun, Network multicast low via linear codin, in Proc. Int. Symp. Operational Research Its Applications (ISORA 98), Kunmin, China, Au. 1998, pp [4] D. J. A. Welsh, Matroid Theory. New York: Academic, [5] R. W. Yeun, A First Course in Inormation Theory. Norwell, MA/New York: Kluwer/Plenum, [6] F. R. Kschischan, private communication.
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006
 2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
2386 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 6, JUNE 2006 The Encoding Complexity of Network Coding Michael Langberg, Member, IEEE, Alexander Sprintson, Member, IEEE, and Jehoshua Bruck,
Reducing Network Cost of Many-to-Many Communication in Unidirectional WDM Rings with Network Coding
 1 Reducin Network Cost of Many-to-Many Communication in Unidirectional WDM Rins with Network Codin Lon Lon and Ahmed E. Kamal, Senior Member, IEEE Abstract In this paper we address the problem of traffic
1 Reducin Network Cost of Many-to-Many Communication in Unidirectional WDM Rins with Network Codin Lon Lon and Ahmed E. Kamal, Senior Member, IEEE Abstract In this paper we address the problem of traffic
A Nearest Neighbor Method for Efficient ICP
 A Nearest Neihbor Method or Eicient ICP Michael Greenspan Guy Godin Visual Inormation Technoloy Group Institute or Inormation Technoloy, National Research Council Canada Bld. M50, 1500 Montreal Rd., Ottawa,
A Nearest Neihbor Method or Eicient ICP Michael Greenspan Guy Godin Visual Inormation Technoloy Group Institute or Inormation Technoloy, National Research Council Canada Bld. M50, 1500 Montreal Rd., Ottawa,
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
Coarse Grained Parallel Maximum Matching In Convex Bipartite Graphs
 Coarse Grained Parallel Maximum Matchin In Convex Bipartite Graphs P. Bose, A. Chan, F. Dehne, and M. Latzel School o Computer Science Carleton University Ottawa, Canada K1S 5B6 jit,achan,dehne,mlatzel@scs.carleton.ca
Coarse Grained Parallel Maximum Matchin In Convex Bipartite Graphs P. Bose, A. Chan, F. Dehne, and M. Latzel School o Computer Science Carleton University Ottawa, Canada K1S 5B6 jit,achan,dehne,mlatzel@scs.carleton.ca
Communication Networks ( ) / Spring 2011 The Blavatnik School of Computer Science, Tel-Aviv University
 ommunication Networks (0368-3030) / Sprin 0 The lavatnik School o omputer Science, Tel-viv University llon Waner urose & Ross, hapters 5.5-5.6 (5 th ed.) Tanenbaum & Wetherall, hapters 4.3.4 4.3.8 (5 th
ommunication Networks (0368-3030) / Sprin 0 The lavatnik School o omputer Science, Tel-viv University llon Waner urose & Ross, hapters 5.5-5.6 (5 th ed.) Tanenbaum & Wetherall, hapters 4.3.4 4.3.8 (5 th
Reducing network cost of many-to-many communication in unidirectional WDM rings with network coding
 Reducin network cost of many-to-many communication in unidirectional WDM rins with network codin Lon Lon and Ahmed E. Kamal Department of Electrical and Computer Enineerin, Iowa State University Email:
Reducin network cost of many-to-many communication in unidirectional WDM rins with network codin Lon Lon and Ahmed E. Kamal Department of Electrical and Computer Enineerin, Iowa State University Email:
Rough Connected Topologized. Approximation Spaces
 International Journal o Mathematical Analysis Vol. 8 04 no. 53 69-68 HIARI Ltd www.m-hikari.com http://dx.doi.org/0.988/ijma.04.4038 Rough Connected Topologized Approximation Spaces M. J. Iqelan Department
International Journal o Mathematical Analysis Vol. 8 04 no. 53 69-68 HIARI Ltd www.m-hikari.com http://dx.doi.org/0.988/ijma.04.4038 Rough Connected Topologized Approximation Spaces M. J. Iqelan Department
A Proposed Approach for Solving Rough Bi-Level. Programming Problems by Genetic Algorithm
 Int J Contemp Math Sciences, Vol 6, 0, no 0, 45 465 A Proposed Approach or Solving Rough Bi-Level Programming Problems by Genetic Algorithm M S Osman Department o Basic Science, Higher Technological Institute
Int J Contemp Math Sciences, Vol 6, 0, no 0, 45 465 A Proposed Approach or Solving Rough Bi-Level Programming Problems by Genetic Algorithm M S Osman Department o Basic Science, Higher Technological Institute
Survey on Error Control Coding Techniques
 Survey on Error Control Codin Techniques Suriya.N 1 SNS Collee of Enineerin, Department of ECE, surikala@mail.com S.Kamalakannan 2 SNS Collee of Enineerin, Department of ECE, kamalakannan.ap@mail.com Abstract
Survey on Error Control Codin Techniques Suriya.N 1 SNS Collee of Enineerin, Department of ECE, surikala@mail.com S.Kamalakannan 2 SNS Collee of Enineerin, Department of ECE, kamalakannan.ap@mail.com Abstract
Status. We ll do code generation first... Outline
 Status Run-time Environments Lecture 11 We have covered the ront-end phases Lexical analysis Parsin Semantic analysis Next are the back-end phases Optimization Code eneration We ll do code eneration irst...
Status Run-time Environments Lecture 11 We have covered the ront-end phases Lexical analysis Parsin Semantic analysis Next are the back-end phases Optimization Code eneration We ll do code eneration irst...
Grooming Multicast Traffic in Unidirectional SONET/WDM Rings
 1 Groomin Multicast Traffic in Unidirectional SONET/WDM Rins Anuj Rawat, Richard La, Steven Marcus and Mark Shayman Abstract In this paper we study the problem of efficient roomin of iven non-uniform multicast
1 Groomin Multicast Traffic in Unidirectional SONET/WDM Rins Anuj Rawat, Richard La, Steven Marcus and Mark Shayman Abstract In this paper we study the problem of efficient roomin of iven non-uniform multicast
WHEN DO THREE LONGEST PATHS HAVE A COMMON VERTEX?
 WHEN DO THREE LONGEST PATHS HAVE A COMMON VERTEX? MARIA AXENOVICH Abstract. It is well known that any two longest paths in a connected graph share a vertex. It is also known that there are connected graphs
WHEN DO THREE LONGEST PATHS HAVE A COMMON VERTEX? MARIA AXENOVICH Abstract. It is well known that any two longest paths in a connected graph share a vertex. It is also known that there are connected graphs
Generell Topologi. Richard Williamson. May 6, 2013
 Generell Topologi Richard Williamson May 6, Thursday 7th January. Basis o a topological space generating a topology with a speciied basis standard topology on R examples Deinition.. Let (, O) be a topological
Generell Topologi Richard Williamson May 6, Thursday 7th January. Basis o a topological space generating a topology with a speciied basis standard topology on R examples Deinition.. Let (, O) be a topological
MATRIX ALGORITHM OF SOLVING GRAPH CUTTING PROBLEM
 UDC 681.3.06 MATRIX ALGORITHM OF SOLVING GRAPH CUTTING PROBLEM V.K. Pogrebnoy TPU Institute «Cybernetic centre» E-mail: vk@ad.cctpu.edu.ru Matrix algorithm o solving graph cutting problem has been suggested.
UDC 681.3.06 MATRIX ALGORITHM OF SOLVING GRAPH CUTTING PROBLEM V.K. Pogrebnoy TPU Institute «Cybernetic centre» E-mail: vk@ad.cctpu.edu.ru Matrix algorithm o solving graph cutting problem has been suggested.
FSM ENCODING FOR BDD REPRESENTATIONS
 Int. J. Appl. Math. Comput. Sci., 27, Vol. 7, No., 3 28 DOI:.2478/v6-7--6 FSM ENCODING FOR BDD REPRESENTATIONS WILSIN GOSTI, TIZIANO VILLA,, ALEX SALDANHA, ALBERTO L. SANGIOVANNI-VINCENTELLI, Cadence Desin
Int. J. Appl. Math. Comput. Sci., 27, Vol. 7, No., 3 28 DOI:.2478/v6-7--6 FSM ENCODING FOR BDD REPRESENTATIONS WILSIN GOSTI, TIZIANO VILLA,, ALEX SALDANHA, ALBERTO L. SANGIOVANNI-VINCENTELLI, Cadence Desin
The Role of Switching in Reducing the Number of Electronic Ports in WDM Networks
 1 The Role of Switchin in Reducin the Number of Electronic Ports in WDM Networks Randall A. Berry and Eytan Modiano Abstract We consider the role of switchin in minimizin the number of electronic ports
1 The Role of Switchin in Reducin the Number of Electronic Ports in WDM Networks Randall A. Berry and Eytan Modiano Abstract We consider the role of switchin in minimizin the number of electronic ports
WAVELENGTH Division Multiplexing (WDM) significantly
 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 25, NO. 6, AUGUST 27 1 Groomin Multicast Traffic in Unidirectional SONET/WDM Rins Anuj Rawat, Richard La, Steven Marcus, and Mark Shayman Abstract
IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 25, NO. 6, AUGUST 27 1 Groomin Multicast Traffic in Unidirectional SONET/WDM Rins Anuj Rawat, Richard La, Steven Marcus, and Mark Shayman Abstract
A SUIF Interface Module for Eli. W. M. Waite. University of Colorado
 A SUIF Interace Module or Eli W. M. Waite Department o Electrical and Computer Enineerin University o Colorado William.Waite@Colorado.edu 1 What is Eli? Eli [2] is a domain-specic prorammin environment
A SUIF Interace Module or Eli W. M. Waite Department o Electrical and Computer Enineerin University o Colorado William.Waite@Colorado.edu 1 What is Eli? Eli [2] is a domain-specic prorammin environment
MetaTeD A Meta Language for Modeling. Telecommunication Networks. Kalyan S. Perumalla and Richard M. Fujimoto
 MetaTeD A Meta Lanuae or Modelin Telecommunication Networks Kalyan S. Perumalla and Richard M. Fujimoto (kalyan@cc.atech.edu and ujimoto@cc.atech.edu) Collee o Computin Georia Institute o Technoloy Atlanta,
MetaTeD A Meta Lanuae or Modelin Telecommunication Networks Kalyan S. Perumalla and Richard M. Fujimoto (kalyan@cc.atech.edu and ujimoto@cc.atech.edu) Collee o Computin Georia Institute o Technoloy Atlanta,
ARITHMETIC operations based on residue number systems
 IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 53, NO. 2, FEBRUARY 2006 133 Improved Memoryless RNS Forward Converter Based on the Periodicity of Residues A. B. Premkumar, Senior Member,
IEEE TRANSACTIONS ON CIRCUITS AND SYSTEMS II: EXPRESS BRIEFS, VOL. 53, NO. 2, FEBRUARY 2006 133 Improved Memoryless RNS Forward Converter Based on the Periodicity of Residues A. B. Premkumar, Senior Member,
OCC and Its Variants. Jan Lindström. Helsinki 7. November Seminar on real-time systems UNIVERSITY OF HELSINKI. Department of Computer Science
 OCC and Its Variants Jan Lindström Helsinki 7. November 1997 Seminar on real-time systems UNIVERSITY OF HELSINKI Department o Computer Science Contents 1 Introduction 1 2 Optimistic Concurrency Control
OCC and Its Variants Jan Lindström Helsinki 7. November 1997 Seminar on real-time systems UNIVERSITY OF HELSINKI Department o Computer Science Contents 1 Introduction 1 2 Optimistic Concurrency Control
Chapter 3 Image Enhancement in the Spatial Domain
 Chapter 3 Image Enhancement in the Spatial Domain Yinghua He School o Computer Science and Technology Tianjin University Image enhancement approaches Spatial domain image plane itsel Spatial domain methods
Chapter 3 Image Enhancement in the Spatial Domain Yinghua He School o Computer Science and Technology Tianjin University Image enhancement approaches Spatial domain image plane itsel Spatial domain methods
MOST attention in the literature of network codes has
 3862 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 56, NO. 8, AUGUST 2010 Efficient Network Code Design for Cyclic Networks Elona Erez, Member, IEEE, and Meir Feder, Fellow, IEEE Abstract This paper introduces
3862 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 56, NO. 8, AUGUST 2010 Efficient Network Code Design for Cyclic Networks Elona Erez, Member, IEEE, and Meir Feder, Fellow, IEEE Abstract This paper introduces
A Cell Burst Scheduling for ATM Networking Part II: Implementation
 A Cell Burst Schedulin or ATM Networkin Part II: Implementation C. Tan, A. T. Chronopoulos, Senior Member, IEEE Computer Science Department Wayne State University email:ctan, chronos@cs.wayne.edu E. Yaprak,
A Cell Burst Schedulin or ATM Networkin Part II: Implementation C. Tan, A. T. Chronopoulos, Senior Member, IEEE Computer Science Department Wayne State University email:ctan, chronos@cs.wayne.edu E. Yaprak,
Image Fusion for Enhanced Vision System using Laplacian Pyramid
 Imae Fusion or Enhanced Vision System usin aplacian Pyramid Abhilash G, T.V. Rama Murthy Department o ECE REVA Institute o Technoloy and Manaement Banalore-64, India V. P. S Naidu MSDF ab, FMCD, CSIR-National
Imae Fusion or Enhanced Vision System usin aplacian Pyramid Abhilash G, T.V. Rama Murthy Department o ECE REVA Institute o Technoloy and Manaement Banalore-64, India V. P. S Naidu MSDF ab, FMCD, CSIR-National
Regenerating Codes for Errors and Erasures in Distributed Storage
 Regenerating Codes or Errors and Erasures in Distributed Storage K V Rashmi, Nihar B Shah, Kannan Ramchandran, Fellow, IEEE, and P Vijay Kumar, Fellow, IEEE arxiv:0050v csit] 3 May 0 Abstract Regenerating
Regenerating Codes or Errors and Erasures in Distributed Storage K V Rashmi, Nihar B Shah, Kannan Ramchandran, Fellow, IEEE, and P Vijay Kumar, Fellow, IEEE arxiv:0050v csit] 3 May 0 Abstract Regenerating
FPGA Technology Mapping: A Study of Optimality
 FPGA Technoloy Mappin: A Study o Optimality Andrew Lin Department o Electrical and Computer Enineerin University o Toronto Toronto, Canada alin@eec.toronto.edu Deshanand P. Sinh Altera Corporation Toronto
FPGA Technoloy Mappin: A Study o Optimality Andrew Lin Department o Electrical and Computer Enineerin University o Toronto Toronto, Canada alin@eec.toronto.edu Deshanand P. Sinh Altera Corporation Toronto
9.8 Graphing Rational Functions
 9. Graphing Rational Functions Lets begin with a deinition. Deinition: Rational Function A rational unction is a unction o the orm P where P and Q are polynomials. Q An eample o a simple rational unction
9. Graphing Rational Functions Lets begin with a deinition. Deinition: Rational Function A rational unction is a unction o the orm P where P and Q are polynomials. Q An eample o a simple rational unction
Treewidth and graph minors
 Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
Treewidth and graph minors Lectures 9 and 10, December 29, 2011, January 5, 2012 We shall touch upon the theory of Graph Minors by Robertson and Seymour. This theory gives a very general condition under
3 No-Wait Job Shops with Variable Processing Times
 3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
6. Lecture notes on matroid intersection
 Massachusetts Institute of Technology 18.453: Combinatorial Optimization Michel X. Goemans May 2, 2017 6. Lecture notes on matroid intersection One nice feature about matroids is that a simple greedy algorithm
Massachusetts Institute of Technology 18.453: Combinatorial Optimization Michel X. Goemans May 2, 2017 6. Lecture notes on matroid intersection One nice feature about matroids is that a simple greedy algorithm
A Connection between Network Coding and. Convolutional Codes
 A Connection between Network Coding and 1 Convolutional Codes Christina Fragouli, Emina Soljanin christina.fragouli@epfl.ch, emina@lucent.com Abstract The min-cut, max-flow theorem states that a source
A Connection between Network Coding and 1 Convolutional Codes Christina Fragouli, Emina Soljanin christina.fragouli@epfl.ch, emina@lucent.com Abstract The min-cut, max-flow theorem states that a source
Bijective Proofs of Two Broken Circuit Theorems
 Bijective Proofs of Two Broken Circuit Theorems Andreas Blass PENNSYLVANIA STATE UNIVERSITY UNIVERSITY PARK, PENNSYLVANIA 16802 Bruce Eli Sagan THE UNIVERSITY OF PENNSYLVANIA PHILADELPHIA, PENNSYLVANIA
Bijective Proofs of Two Broken Circuit Theorems Andreas Blass PENNSYLVANIA STATE UNIVERSITY UNIVERSITY PARK, PENNSYLVANIA 16802 Bruce Eli Sagan THE UNIVERSITY OF PENNSYLVANIA PHILADELPHIA, PENNSYLVANIA
Global Constraints. Combinatorial Problem Solving (CPS) Enric Rodríguez-Carbonell (based on materials by Javier Larrosa) February 22, 2019
 Global Constraints Combinatorial Problem Solving (CPS) Enric Rodríguez-Carbonell (based on materials by Javier Larrosa) February 22, 2019 Global Constraints Global constraints are classes o constraints
Global Constraints Combinatorial Problem Solving (CPS) Enric Rodríguez-Carbonell (based on materials by Javier Larrosa) February 22, 2019 Global Constraints Global constraints are classes o constraints
Math 5593 Linear Programming Lecture Notes
 Math 5593 Linear Programming Lecture Notes Unit II: Theory & Foundations (Convex Analysis) University of Colorado Denver, Fall 2013 Topics 1 Convex Sets 1 1.1 Basic Properties (Luenberger-Ye Appendix B.1).........................
Math 5593 Linear Programming Lecture Notes Unit II: Theory & Foundations (Convex Analysis) University of Colorado Denver, Fall 2013 Topics 1 Convex Sets 1 1.1 Basic Properties (Luenberger-Ye Appendix B.1).........................
Byzantine Consensus in Directed Graphs
 Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Byzantine Consensus in Directed Graphs Lewis Tseng 1,3, and Nitin Vaidya 2,3 1 Department of Computer Science, 2 Department of Electrical and Computer Engineering, and 3 Coordinated Science Laboratory
Piecewise polynomial interpolation
 Chapter 2 Piecewise polynomial interpolation In ection.6., and in Lab, we learned that it is not a good idea to interpolate unctions by a highorder polynomials at equally spaced points. However, it transpires
Chapter 2 Piecewise polynomial interpolation In ection.6., and in Lab, we learned that it is not a good idea to interpolate unctions by a highorder polynomials at equally spaced points. However, it transpires
EMILY RIEHL. X. This data is subject to the following axiom: to any pair X f Y g Z there must be some specified composite map = Z
 THE ALGEBRA AND GEOMETRY OF -CATEGORIES EMILY RIEHL Abstract. -cateories are a sopisticated tool or te study o matematical structures wit ier omotopical inormation. Tis note, directed at te Friends o Harvard
THE ALGEBRA AND GEOMETRY OF -CATEGORIES EMILY RIEHL Abstract. -cateories are a sopisticated tool or te study o matematical structures wit ier omotopical inormation. Tis note, directed at te Friends o Harvard
Scheduling in Multihop Wireless Networks without Back-pressure
 Forty-Eighth Annual Allerton Conerence Allerton House, UIUC, Illinois, USA September 29 - October 1, 2010 Scheduling in Multihop Wireless Networks without Back-pressure Shihuan Liu, Eylem Ekici, and Lei
Forty-Eighth Annual Allerton Conerence Allerton House, UIUC, Illinois, USA September 29 - October 1, 2010 Scheduling in Multihop Wireless Networks without Back-pressure Shihuan Liu, Eylem Ekici, and Lei
Composite functions. [Type the document subtitle] Composite functions, working them out.
![Composite functions. [Type the document subtitle] Composite functions, working them out. Composite functions. [Type the document subtitle] Composite functions, working them out.](/thumbs/76/73514886.jpg) Composite unctions [Type the document subtitle] Composite unctions, workin them out. luxvis 11/19/01 Composite Functions What are they? In the real world, it is not uncommon or the output o one thin to
Composite unctions [Type the document subtitle] Composite unctions, workin them out. luxvis 11/19/01 Composite Functions What are they? In the real world, it is not uncommon or the output o one thin to
From Java to C A Supplement to Computer Algorithms, Third Edition. Sara Baase Allen Van Gelder
 From Java to C A Supplement to Computer Alorithms, Third Edition Sara Baase Allen Van Gelder October 30, 2004 ii clcopyriht 2000, 2001 Sara Baase and Allen Van Gelder. All rihts reserved. This document
From Java to C A Supplement to Computer Alorithms, Third Edition Sara Baase Allen Van Gelder October 30, 2004 ii clcopyriht 2000, 2001 Sara Baase and Allen Van Gelder. All rihts reserved. This document
Some Inequalities Involving Fuzzy Complex Numbers
 Theory Applications o Mathematics & Computer Science 4 1 014 106 113 Some Inequalities Involving Fuzzy Complex Numbers Sanjib Kumar Datta a,, Tanmay Biswas b, Samten Tamang a a Department o Mathematics,
Theory Applications o Mathematics & Computer Science 4 1 014 106 113 Some Inequalities Involving Fuzzy Complex Numbers Sanjib Kumar Datta a,, Tanmay Biswas b, Samten Tamang a a Department o Mathematics,
a<b x = x = c!=d = y x = = x false true
 1 Introduction 1.1 Predicated execution Predicated execution [HD86, RYYT89, DT93, KSR93] is an architectural model in which each operation is uarded by a boolean operand whose value determines whether
1 Introduction 1.1 Predicated execution Predicated execution [HD86, RYYT89, DT93, KSR93] is an architectural model in which each operation is uarded by a boolean operand whose value determines whether
Crossing Families. Abstract
 Crossing Families Boris Aronov 1, Paul Erdős 2, Wayne Goddard 3, Daniel J. Kleitman 3, Michael Klugerman 3, János Pach 2,4, Leonard J. Schulman 3 Abstract Given a set of points in the plane, a crossing
Crossing Families Boris Aronov 1, Paul Erdős 2, Wayne Goddard 3, Daniel J. Kleitman 3, Michael Klugerman 3, János Pach 2,4, Leonard J. Schulman 3 Abstract Given a set of points in the plane, a crossing
A Combined Delay and Throughput Proportional Scheduling Scheme for Differentiated Services
 A Combined Delay and Throuhput Proportional Schedulin Scheme for Differentiated Services Samyukta Sankaran and Ahmed E.Kamal Department of Electrical and Computer Enineerin Iowa State University Ames,
A Combined Delay and Throuhput Proportional Schedulin Scheme for Differentiated Services Samyukta Sankaran and Ahmed E.Kamal Department of Electrical and Computer Enineerin Iowa State University Ames,
POLAR codes were proposed in [1] as a low-complexity
![POLAR codes were proposed in [1] as a low-complexity POLAR codes were proposed in [1] as a low-complexity](/thumbs/85/92295665.jpg) A Hih-Throuhput Enery-Eicient Implementation o Successive Cancellation Decoder or Polar Codes Usin Combinational Loic Onur Dizdar, Student Member, IEEE, and Erdal Arıkan, Fellow, IEEE arxiv:42.3829v5 [cs.ar]
A Hih-Throuhput Enery-Eicient Implementation o Successive Cancellation Decoder or Polar Codes Usin Combinational Loic Onur Dizdar, Student Member, IEEE, and Erdal Arıkan, Fellow, IEEE arxiv:42.3829v5 [cs.ar]
Rigidity, connectivity and graph decompositions
 First Prev Next Last Rigidity, connectivity and graph decompositions Brigitte Servatius Herman Servatius Worcester Polytechnic Institute Page 1 of 100 First Prev Next Last Page 2 of 100 We say that a framework
First Prev Next Last Rigidity, connectivity and graph decompositions Brigitte Servatius Herman Servatius Worcester Polytechnic Institute Page 1 of 100 First Prev Next Last Page 2 of 100 We say that a framework
Subdivided graphs have linear Ramsey numbers
 Subdivided graphs have linear Ramsey numbers Noga Alon Bellcore, Morristown, NJ 07960, USA and Department of Mathematics Raymond and Beverly Sackler Faculty of Exact Sciences Tel Aviv University, Tel Aviv,
Subdivided graphs have linear Ramsey numbers Noga Alon Bellcore, Morristown, NJ 07960, USA and Department of Mathematics Raymond and Beverly Sackler Faculty of Exact Sciences Tel Aviv University, Tel Aviv,
Bus-Based Communication Synthesis on System-Level
 Bus-Based Communication Synthesis on System-Level Michael Gasteier Manfred Glesner Darmstadt University of Technoloy Institute of Microelectronic Systems Karlstrasse 15, 64283 Darmstadt, Germany Abstract
Bus-Based Communication Synthesis on System-Level Michael Gasteier Manfred Glesner Darmstadt University of Technoloy Institute of Microelectronic Systems Karlstrasse 15, 64283 Darmstadt, Germany Abstract
4. Simplicial Complexes and Simplicial Homology
 MATH41071/MATH61071 Algebraic topology Autumn Semester 2017 2018 4. Simplicial Complexes and Simplicial Homology Geometric simplicial complexes 4.1 Definition. A finite subset { v 0, v 1,..., v r } R n
MATH41071/MATH61071 Algebraic topology Autumn Semester 2017 2018 4. Simplicial Complexes and Simplicial Homology Geometric simplicial complexes 4.1 Definition. A finite subset { v 0, v 1,..., v r } R n
Binary recursion. Unate functions. If a cover C(f) is unate in xj, x, then f is unate in xj. x
 Binary recursion Unate unctions! Theorem I a cover C() is unate in,, then is unate in.! Theorem I is unate in,, then every prime implicant o is unate in. Why are unate unctions so special?! Special Boolean
Binary recursion Unate unctions! Theorem I a cover C() is unate in,, then is unate in.! Theorem I is unate in,, then every prime implicant o is unate in. Why are unate unctions so special?! Special Boolean
INTRODUCTION TO THE HOMOLOGY GROUPS OF COMPLEXES
 INTRODUCTION TO THE HOMOLOGY GROUPS OF COMPLEXES RACHEL CARANDANG Abstract. This paper provides an overview of the homology groups of a 2- dimensional complex. It then demonstrates a proof of the Invariance
INTRODUCTION TO THE HOMOLOGY GROUPS OF COMPLEXES RACHEL CARANDANG Abstract. This paper provides an overview of the homology groups of a 2- dimensional complex. It then demonstrates a proof of the Invariance
Optics Quiz #2 April 30, 2014
 .71 - Optics Quiz # April 3, 14 Problem 1. Billet s Split Lens Setup I the ield L(x) is placed against a lens with ocal length and pupil unction P(x), the ield (X) on the X-axis placed a distance behind
.71 - Optics Quiz # April 3, 14 Problem 1. Billet s Split Lens Setup I the ield L(x) is placed against a lens with ocal length and pupil unction P(x), the ield (X) on the X-axis placed a distance behind
General Design of Grid-based Data Replication. Schemes Using Graphs and a Few Rules. availability of read and write operations they oer and
 General esin of Grid-based ata Replication Schemes Usin Graphs and a Few Rules Oliver Theel University of California epartment of Computer Science Riverside, C 92521-0304, US bstract Grid-based data replication
General esin of Grid-based ata Replication Schemes Usin Graphs and a Few Rules Oliver Theel University of California epartment of Computer Science Riverside, C 92521-0304, US bstract Grid-based data replication
GEODESIC RECONSTRUCTION, SADDLE ZONES & HIERARCHICAL SEGMENTATION
 Imae Anal Stereol 2001;20:xx-xx Oriinal Research Paper GEODESIC RECONSTRUCTION, SADDLE ZONES & HIERARCHICAL SEGMENTATION SERGE BEUCHER Centre de Morpholoie Mathématique, Ecole des Mines de Paris, 35, Rue
Imae Anal Stereol 2001;20:xx-xx Oriinal Research Paper GEODESIC RECONSTRUCTION, SADDLE ZONES & HIERARCHICAL SEGMENTATION SERGE BEUCHER Centre de Morpholoie Mathématique, Ecole des Mines de Paris, 35, Rue
A Rigorous Correctness Proof of a Tomasulo Scheduler Supporting Precise Interrupts
 A Riorous Correctness Proo o a Tomasulo Scheduler Supportin Precise Interrupts Daniel Kroenin Λ, Silvia M. Mueller y, and Wolan J. Paul Dept. 14: Computer Science, University o Saarland, Post Box 151150,
A Riorous Correctness Proo o a Tomasulo Scheduler Supportin Precise Interrupts Daniel Kroenin Λ, Silvia M. Mueller y, and Wolan J. Paul Dept. 14: Computer Science, University o Saarland, Post Box 151150,
The strong chromatic number of a graph
 The strong chromatic number of a graph Noga Alon Abstract It is shown that there is an absolute constant c with the following property: For any two graphs G 1 = (V, E 1 ) and G 2 = (V, E 2 ) on the same
The strong chromatic number of a graph Noga Alon Abstract It is shown that there is an absolute constant c with the following property: For any two graphs G 1 = (V, E 1 ) and G 2 = (V, E 2 ) on the same
Lecture 6: Faces, Facets
 IE 511: Integer Programming, Spring 2019 31 Jan, 2019 Lecturer: Karthik Chandrasekaran Lecture 6: Faces, Facets Scribe: Setareh Taki Disclaimer: These notes have not been subjected to the usual scrutiny
IE 511: Integer Programming, Spring 2019 31 Jan, 2019 Lecturer: Karthik Chandrasekaran Lecture 6: Faces, Facets Scribe: Setareh Taki Disclaimer: These notes have not been subjected to the usual scrutiny
x y x mod p g y mod p K= g xy mod p Alice Eve Bob g g x mod p x mod p g y y mod p y mod p K1= g mod p K2= g mod p
 6.857 Computer and Network Security Fall Term, 1997 Lecture 15 : October 23rd, 1997 Lecturer: Ron Rivest Scribe: Ben Adida 1 Topics Covered An Active Attack on RSA smart cards Secure Channels over Insecure
6.857 Computer and Network Security Fall Term, 1997 Lecture 15 : October 23rd, 1997 Lecturer: Ron Rivest Scribe: Ben Adida 1 Topics Covered An Active Attack on RSA smart cards Secure Channels over Insecure
ARELAY network consists of a pair of source and destination
 158 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 55, NO 1, JANUARY 2009 Parity Forwarding for Multiple-Relay Networks Peyman Razaghi, Student Member, IEEE, Wei Yu, Senior Member, IEEE Abstract This paper
158 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 55, NO 1, JANUARY 2009 Parity Forwarding for Multiple-Relay Networks Peyman Razaghi, Student Member, IEEE, Wei Yu, Senior Member, IEEE Abstract This paper
Group Secret Key Generation Algorithms
 Group Secret Key Generation Algorithms Chunxuan Ye and Alex Reznik InterDigital Communications Corporation King of Prussia, PA 9406 Email: {Chunxuan.Ye, Alex.Reznik}@interdigital.com arxiv:cs/07024v [cs.it]
Group Secret Key Generation Algorithms Chunxuan Ye and Alex Reznik InterDigital Communications Corporation King of Prussia, PA 9406 Email: {Chunxuan.Ye, Alex.Reznik}@interdigital.com arxiv:cs/07024v [cs.it]
Neighbourhood Operations
 Neighbourhood Operations Neighbourhood operations simply operate on a larger neighbourhood o piels than point operations Origin Neighbourhoods are mostly a rectangle around a central piel Any size rectangle
Neighbourhood Operations Neighbourhood operations simply operate on a larger neighbourhood o piels than point operations Origin Neighbourhoods are mostly a rectangle around a central piel Any size rectangle
RE2C { A More Versatile Scanner Generator. Peter Bumbulis Donald D. Cowan. University of Waterloo. April 15, Abstract
 RE2C { A More Versatile Scanner Generator Peter Bumbulis Donald D. Cowan Computer Science Department and Computer Systems Group University o Waterloo April 15, 1994 Abstract It is usually claimed that
RE2C { A More Versatile Scanner Generator Peter Bumbulis Donald D. Cowan Computer Science Department and Computer Systems Group University o Waterloo April 15, 1994 Abstract It is usually claimed that
PROJECTIVE REPRESENTATIONS OF QUIVERS
 IJMMS 31:2 22 97 11 II. S1611712218192 ttp://ijmms.indawi.com Hindawi ublisin Corp. ROJECTIVE RERESENTATIONS OF QUIVERS SANGWON ARK Received 3 Auust 21 We prove tat 2 is a projective representation o a
IJMMS 31:2 22 97 11 II. S1611712218192 ttp://ijmms.indawi.com Hindawi ublisin Corp. ROJECTIVE RERESENTATIONS OF QUIVERS SANGWON ARK Received 3 Auust 21 We prove tat 2 is a projective representation o a
EXTREME POINTS AND AFFINE EQUIVALENCE
 EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
EXTREME POINTS AND AFFINE EQUIVALENCE The purpose of this note is to use the notions of extreme points and affine transformations which are studied in the file affine-convex.pdf to prove that certain standard
Matching Algorithms. Proof. If a bipartite graph has a perfect matching, then it is easy to see that the right hand side is a necessary condition.
 18.433 Combinatorial Optimization Matching Algorithms September 9,14,16 Lecturer: Santosh Vempala Given a graph G = (V, E), a matching M is a set of edges with the property that no two of the edges have
18.433 Combinatorial Optimization Matching Algorithms September 9,14,16 Lecturer: Santosh Vempala Given a graph G = (V, E), a matching M is a set of edges with the property that no two of the edges have
Winning Positions in Simplicial Nim
 Winning Positions in Simplicial Nim David Horrocks Department of Mathematics and Statistics University of Prince Edward Island Charlottetown, Prince Edward Island, Canada, C1A 4P3 dhorrocks@upei.ca Submitted:
Winning Positions in Simplicial Nim David Horrocks Department of Mathematics and Statistics University of Prince Edward Island Charlottetown, Prince Edward Island, Canada, C1A 4P3 dhorrocks@upei.ca Submitted:
Optimal Exact-Regenerating Codes for Distributed Storage at the MSR and MBR Points via a Product-Matrix Construction
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 57, NO 8, AUGUST 2011 5227 Optimal Exact-Regenerating Codes for Distributed Storage at the MSR and MBR Points via a Product-Matrix Construction K V Rashmi,
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 57, NO 8, AUGUST 2011 5227 Optimal Exact-Regenerating Codes for Distributed Storage at the MSR and MBR Points via a Product-Matrix Construction K V Rashmi,
Math 170- Graph Theory Notes
 1 Math 170- Graph Theory Notes Michael Levet December 3, 2018 Notation: Let n be a positive integer. Denote [n] to be the set {1, 2,..., n}. So for example, [3] = {1, 2, 3}. To quote Bud Brown, Graph theory
1 Math 170- Graph Theory Notes Michael Levet December 3, 2018 Notation: Let n be a positive integer. Denote [n] to be the set {1, 2,..., n}. So for example, [3] = {1, 2, 3}. To quote Bud Brown, Graph theory
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email mikel,spalex,bruck @caltech.edu Abstract In the multicast network
FUTURE communication networks are expected to support
 1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
Unlabeled equivalence for matroids representable over finite fields
 Unlabeled equivalence for matroids representable over finite fields November 16, 2012 S. R. Kingan Department of Mathematics Brooklyn College, City University of New York 2900 Bedford Avenue Brooklyn,
Unlabeled equivalence for matroids representable over finite fields November 16, 2012 S. R. Kingan Department of Mathematics Brooklyn College, City University of New York 2900 Bedford Avenue Brooklyn,
MAPI Computer Vision. Multiple View Geometry
 MAPI Computer Vision Multiple View Geometry Geometry o Multiple Views 2- and 3- view geometry p p Kpˆ [ K R t]p Geometry o Multiple Views 2- and 3- view geometry Epipolar Geometry The epipolar geometry
MAPI Computer Vision Multiple View Geometry Geometry o Multiple Views 2- and 3- view geometry p p Kpˆ [ K R t]p Geometry o Multiple Views 2- and 3- view geometry Epipolar Geometry The epipolar geometry
Lecture 2 September 3
 EE 381V: Large Scale Optimization Fall 2012 Lecture 2 September 3 Lecturer: Caramanis & Sanghavi Scribe: Hongbo Si, Qiaoyang Ye 2.1 Overview of the last Lecture The focus of the last lecture was to give
EE 381V: Large Scale Optimization Fall 2012 Lecture 2 September 3 Lecturer: Caramanis & Sanghavi Scribe: Hongbo Si, Qiaoyang Ye 2.1 Overview of the last Lecture The focus of the last lecture was to give
An Efficient Configuration Methodology for Time-Division Multiplexed Single Resources
 An Eicient Coniguration Methodology or Time-Division Multiplexed Single Resources Benny Akesson 1, Anna Minaeva 1, Přemysl Šůcha 1, Andrew Nelson 2 and Zdeněk Hanzálek 1 1 Czech Technical University in
An Eicient Coniguration Methodology or Time-Division Multiplexed Single Resources Benny Akesson 1, Anna Minaeva 1, Přemysl Šůcha 1, Andrew Nelson 2 and Zdeněk Hanzálek 1 1 Czech Technical University in
11.1. Definitions. 11. Domination in Graphs
 11. Domination in Graphs Some definitions Minimal dominating sets Bounds for the domination number. The independent domination number Other domination parameters. 11.1. Definitions A vertex v in a graph
11. Domination in Graphs Some definitions Minimal dominating sets Bounds for the domination number. The independent domination number Other domination parameters. 11.1. Definitions A vertex v in a graph
Formalizing Cardinality-based Feature Models and their Staged Configuration
 Formalizing Cardinality-based Feature Models and their Staged Coniguration Krzyszto Czarnecki, Simon Helsen, and Ulrich Eisenecker 2 University o Waterloo, Canada 2 University o Applied Sciences Kaiserslautern,
Formalizing Cardinality-based Feature Models and their Staged Coniguration Krzyszto Czarnecki, Simon Helsen, and Ulrich Eisenecker 2 University o Waterloo, Canada 2 University o Applied Sciences Kaiserslautern,
arxiv: v4 [math.co] 25 Apr 2010
![arxiv: v4 [math.co] 25 Apr 2010 arxiv: v4 [math.co] 25 Apr 2010](/thumbs/89/98407334.jpg) QUIVERS OF FINITE MUTATION TYPE AND SKEW-SYMMETRIC MATRICES arxiv:0905.3613v4 [math.co] 25 Apr 2010 AHMET I. SEVEN Abstract. Quivers of finite mutation type are certain directed graphs that first arised
QUIVERS OF FINITE MUTATION TYPE AND SKEW-SYMMETRIC MATRICES arxiv:0905.3613v4 [math.co] 25 Apr 2010 AHMET I. SEVEN Abstract. Quivers of finite mutation type are certain directed graphs that first arised
Pentagon contact representations
 Pentagon contact representations Stean Felsner Institut ür Mathematik Technische Universität Berlin Hendrik Schrezenmaier Institut ür Mathematik Technische Universität Berlin August, 017 Raphael Steiner
Pentagon contact representations Stean Felsner Institut ür Mathematik Technische Universität Berlin Hendrik Schrezenmaier Institut ür Mathematik Technische Universität Berlin August, 017 Raphael Steiner
STANLEY S SIMPLICIAL POSET CONJECTURE, AFTER M. MASUDA
 Communications in Algebra, 34: 1049 1053, 2006 Copyright Taylor & Francis Group, LLC ISSN: 0092-7872 print/1532-4125 online DOI: 10.1080/00927870500442005 STANLEY S SIMPLICIAL POSET CONJECTURE, AFTER M.
Communications in Algebra, 34: 1049 1053, 2006 Copyright Taylor & Francis Group, LLC ISSN: 0092-7872 print/1532-4125 online DOI: 10.1080/00927870500442005 STANLEY S SIMPLICIAL POSET CONJECTURE, AFTER M.
9.5 Equivalence Relations
 9.5 Equivalence Relations You know from your early study of fractions that each fraction has many equivalent forms. For example, 2, 2 4, 3 6, 2, 3 6, 5 30,... are all different ways to represent the same
9.5 Equivalence Relations You know from your early study of fractions that each fraction has many equivalent forms. For example, 2, 2 4, 3 6, 2, 3 6, 5 30,... are all different ways to represent the same
Integer Programming Theory
 Integer Programming Theory Laura Galli October 24, 2016 In the following we assume all functions are linear, hence we often drop the term linear. In discrete optimization, we seek to find a solution x
Integer Programming Theory Laura Galli October 24, 2016 In the following we assume all functions are linear, hence we often drop the term linear. In discrete optimization, we seek to find a solution x
Improving Computer Security using Extended Static Checking
 Improvin Computer Security usin Extended Static Checkin Brian V. Chess Department o Computer Enineerin University o Caliornia, Santa Cruz Abstract We describe a method or indin security laws in source
Improvin Computer Security usin Extended Static Checkin Brian V. Chess Department o Computer Enineerin University o Caliornia, Santa Cruz Abstract We describe a method or indin security laws in source
Iterative Single-Image Digital Super-Resolution Using Partial High-Resolution Data
 Iterative Sinle-Imae Diital Super-Resolution Usin Partial Hih-Resolution Data Eran Gur, Member, IAENG and Zeev Zalevsky Abstract The subject of extractin hih-resolution data from low-resolution imaes is
Iterative Sinle-Imae Diital Super-Resolution Usin Partial Hih-Resolution Data Eran Gur, Member, IAENG and Zeev Zalevsky Abstract The subject of extractin hih-resolution data from low-resolution imaes is
STABILITY AND PARADOX IN ALGORITHMIC LOGIC
 STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
Superconcentrators of depth 2 and 3; odd levels help (rarely)
 Superconcentrators of depth 2 and 3; odd levels help (rarely) Noga Alon Bellcore, Morristown, NJ, 07960, USA and Department of Mathematics Raymond and Beverly Sackler Faculty of Exact Sciences Tel Aviv
Superconcentrators of depth 2 and 3; odd levels help (rarely) Noga Alon Bellcore, Morristown, NJ, 07960, USA and Department of Mathematics Raymond and Beverly Sackler Faculty of Exact Sciences Tel Aviv
CPSC 536N: Randomized Algorithms Term 2. Lecture 10
 CPSC 536N: Randomized Algorithms 011-1 Term Prof. Nick Harvey Lecture 10 University of British Columbia In the first lecture we discussed the Max Cut problem, which is NP-complete, and we presented a very
CPSC 536N: Randomized Algorithms 011-1 Term Prof. Nick Harvey Lecture 10 University of British Columbia In the first lecture we discussed the Max Cut problem, which is NP-complete, and we presented a very
Using Real-Time Serializability and Optimistic Concurrency Control in Firm Real-Time Databases
 Usin Real-Time Serializability and Optimistic Concurrency Control in Firm Real-Time Databases Jan Lindström and Kimmo Raatikainen University o Helsinki, Department o Computer Science P.O. Box 26 (Teollisuuskatu
Usin Real-Time Serializability and Optimistic Concurrency Control in Firm Real-Time Databases Jan Lindström and Kimmo Raatikainen University o Helsinki, Department o Computer Science P.O. Box 26 (Teollisuuskatu
Chapter 4. Coding systems. 4.1 Binary codes Gray (reflected binary) code
 Chapter 4 Codin systems Codin systems define how information is mapped to numbers. Different codin systems try to store/transmit information more efficiently [Sec. 4.], or protect it from damae while it
Chapter 4 Codin systems Codin systems define how information is mapped to numbers. Different codin systems try to store/transmit information more efficiently [Sec. 4.], or protect it from damae while it
9 Connectivity. Contents. 9.1 Vertex Connectivity
 9 Connectivity Contents 9.1 Vertex Connectivity.............................. 205 Connectivity and Local Connectivity............... 206 Vertex Cuts and Menger s Theorem................. 207 9.2 The Fan
9 Connectivity Contents 9.1 Vertex Connectivity.............................. 205 Connectivity and Local Connectivity............... 206 Vertex Cuts and Menger s Theorem................. 207 9.2 The Fan
Cyclic base orders of matroids
 Cyclic base orders of matroids Doug Wiedemann May 9, 2006 Abstract This is a typewritten version, with many corrections, of a handwritten note, August 1984, for a course taught by Jack Edmonds. The purpose
Cyclic base orders of matroids Doug Wiedemann May 9, 2006 Abstract This is a typewritten version, with many corrections, of a handwritten note, August 1984, for a course taught by Jack Edmonds. The purpose
A Reduction of Conway s Thrackle Conjecture
 A Reduction of Conway s Thrackle Conjecture Wei Li, Karen Daniels, and Konstantin Rybnikov Department of Computer Science and Department of Mathematical Sciences University of Massachusetts, Lowell 01854
A Reduction of Conway s Thrackle Conjecture Wei Li, Karen Daniels, and Konstantin Rybnikov Department of Computer Science and Department of Mathematical Sciences University of Massachusetts, Lowell 01854
Structured System Theory
 Appendix C Structured System Theory Linear systems are often studied from an algebraic perspective, based on the rank of certain matrices. While such tests are easy to derive from the mathematical model,
Appendix C Structured System Theory Linear systems are often studied from an algebraic perspective, based on the rank of certain matrices. While such tests are easy to derive from the mathematical model,
Performance and Overhead Measurements. on the Makbilan. Department of Computer Science. The Hebrew University of Jerusalem
 Perormance and Overhead Measurements on the Makbilan Yosi Ben-Asher Dror G. Feitelson Dtment o Computer Science The Hebrew University o Jerusalem 91904 Jerusalem, Israel E-mail: yosi,dror@cs.huji.ac.il
Perormance and Overhead Measurements on the Makbilan Yosi Ben-Asher Dror G. Feitelson Dtment o Computer Science The Hebrew University o Jerusalem 91904 Jerusalem, Israel E-mail: yosi,dror@cs.huji.ac.il
pp , John Wiley and Sons, 1991 No. 3, 1994, pp , Victoria, 1994 Vol. 37, No. 5, pp Baltimore, 1993 pp.
 termediate representation used is much simpler than a ull UI specication lanuae. We have also proposed to populate automatically the taret GUI builder space thus allowin desiners/developers to ully exploit
termediate representation used is much simpler than a ull UI specication lanuae. We have also proposed to populate automatically the taret GUI builder space thus allowin desiners/developers to ully exploit
6.854 Advanced Algorithms. Scribes: Jay Kumar Sundararajan. Duality
 6.854 Advanced Algorithms Scribes: Jay Kumar Sundararajan Lecturer: David Karger Duality This lecture covers weak and strong duality, and also explains the rules for finding the dual of a linear program,
6.854 Advanced Algorithms Scribes: Jay Kumar Sundararajan Lecturer: David Karger Duality This lecture covers weak and strong duality, and also explains the rules for finding the dual of a linear program,
Acyclic orientations do not lead to optimal deadlock-free packet routing algorithms
 Acyclic orientations do not lead to optimal deadloc-ree pacet routing algorithms Daniel Šteanovič 1 Department o Computer Science, Comenius University, Bratislava, Slovaia Abstract In this paper e consider
Acyclic orientations do not lead to optimal deadloc-ree pacet routing algorithms Daniel Šteanovič 1 Department o Computer Science, Comenius University, Bratislava, Slovaia Abstract In this paper e consider
FOUR EDGE-INDEPENDENT SPANNING TREES 1
 FOUR EDGE-INDEPENDENT SPANNING TREES 1 Alexander Hoyer and Robin Thomas School of Mathematics Georgia Institute of Technology Atlanta, Georgia 30332-0160, USA ABSTRACT We prove an ear-decomposition theorem
FOUR EDGE-INDEPENDENT SPANNING TREES 1 Alexander Hoyer and Robin Thomas School of Mathematics Georgia Institute of Technology Atlanta, Georgia 30332-0160, USA ABSTRACT We prove an ear-decomposition theorem
Assignment 4 Solutions of graph problems
 Assignment 4 Solutions of graph problems 1. Let us assume that G is not a cycle. Consider the maximal path in the graph. Let the end points of the path be denoted as v 1, v k respectively. If either of
Assignment 4 Solutions of graph problems 1. Let us assume that G is not a cycle. Consider the maximal path in the graph. Let the end points of the path be denoted as v 1, v k respectively. If either of
