Subject: Wireless Networking Policy Effective Date: May 2005 Responsible Office: Department of Information Technology _ Responsible Officer:
|
|
|
- Spencer Walton
- 6 years ago
- Views:
Transcription
1 Section Number Section Header: Subject: Wireless Networking Policy Effective Date: May 2005 Responsible Office: Department of Information Technology _ Responsible Officer: TABLE OF CONTENTS Introduction...1 Purpose...1 Scope...2 Definitions...2 Policy...2 Key Performance Indicators...3 Procedures...3 Related Documents...4 Forms...5 Responsible Personnel...5 INTRODUCTION The Department of Information Technology (DoIT) began implementation of wireless LAN technology as an extension of the University s data network summer The Wireless LAN is not a replacement to the existing university hard-wired network but a supplement to it. Wireless service is available in most areas where people tend to congregate, including to the main campus center court, GSUB cafeteria, and other locations. PURPOSE Although wireless technology is a common means of connecting to a network and the devices readily available at commodity pricing, simply plugging such hardware into the University network without proper configuration presents a potential service problem and serious security risk for the entire campus community. Unauthorized wireless access points will conflict with the university wireless service. The standard Wireless Encryption Protocol (WEP) used by these devices provides only limited protection and the proliferation of wireless sniffers gives unauthorized intruders an easy means of testing and breaking these simple security features. Revision Date: October 1, 2007 Page 1 of 5
2 To avoid potential conflicts, site surveys are critical to the success of the wireless infrastructure. In addition, measures must be taken to ensure that wireless LAN access is limited to authenticated NJCU faculty, staff and students, and to secure data through high-level encryption while being transmitted. Further, a single vendor solution for access points is the only way to provide seamless roaming over the wireless infrastructure. It is therefore imperative that all requests for wireless service go through THE DOIT. Further, it is critical to develop policy, procedures and guidelines that assure the safety and integrity of the University s wireless network in the future. SCOPE This document applies to all members of the university community, including third party vendors, contractors and consultants. DEFINITIONS Wireless Network A wireless-based data network. The University s wireless network uses the current standard wireless protocols, b and g. Wireless Protocol The transport specification that provides the interface for wireless communications. There are several protocols in use today. The most common are b and g. A new protocol, n, is currently being ratified and will most likely replace both b and g protocols over time. Wireless Adapter A device that provides connectivity to a wireless network. This device is commonly built into laptop computers but can be added as a PC-Card peripheral. Access Point A device that provided the wireless service. Several are needed to provide service to any given area, depending on the coverage area desired. Access points are physically connected to the wired network, which provides the interconnectivity to other network resources. POLICY Access Access is provided through network authentication using a login and password. All members of the University community may use the wireless network, provided they have a valid GothicNet account. Revision Date: October 1, 2007 Page 2 of 5
3 Connectivity University visitors can be provided limited access to the wireless network by applying for guest access. Guest access requires sponsorship and authentication. The guest access form is available from the DoIT website, support page, GothicAir section. All wireless adapters must conform to the University s Wireless Network Standards. These standards are available from the internal Technology Standards & Services website. Use of the University Wireless Network shall be subject to the University Computer Usage Policy and Guidelines. Unauthorized persons attempting to compromise the University s wireless network or interfere with the University s wireless airspace will be prosecuted to the full extent of the law. Installation, engineering, maintenance, and operation of the wireless network and access points on any property owned or tenanted by the University are the sole responsibility of the DoIT. The DoIT will extend the university network to provide wireless service to any area based on the application need, demand and funding. The installation of any device that interferes with authorized wireless transmissions is strictly prohibited. (see the Potential Interfering Devices section, below) Installation of Access Points by individuals or departments is prohibited. Due to interference, wireless 2.4 GHz telephones and other 2.4 GHz devices will are not permitted in areas of wireless technologies. Unauthorized wireless connections to the university network will be terminated. All wireless Access Points must conform to the University s Wireless Network Standards. KEY PERFORMANCE INDICATORS The following success of the policy will be assessed annually using the following quantifiable measures: 1. There is no interference from rogue APs 2. All supplemental APs are known and accounted for PROCEDURES Accessing the wireless network Revision Date: October 1, 2007 Page 3 of 5
4 Please refer to the GothicAir User Guide, which can be found on the DoIT website, support page, GothicAir section. Requesting access point installations Fill out the Wireless Service Request Form. This form can be filled out online and submitted electronically or a hardcopy can be downloaded from the DoIT website, Support page, GothicAir section and submitted to the Help Desk, Rossey Hall, Room 58. A DoIT network administrator will contact you for additional information and set up or supervise installation. Installation may require the services of an outside contractor. Charges may be assumed by the requestor depending on budget constraints and the complexity of installation. As requirements and usage patterns change, it may be necessary to resurvey the wireless coverage areas. This is a necessity in order to provide the appropriate level of service and maintain seamless roaming between wireless cells. Potential Interfering Devices There are many devices that utilize the 2.4 GHz radio frequency and new devices are released regularly. The following is a sample list of devices that are known to cause interference with wireless networks. In some cases, simply moving the device may clear the interference. If moving the device does not clear the interference, it must be removed from operation. Microwave ovens operating within approximately 10 feet an Access Point 2.4 GHz Wireless Telephones 2.4 GHz Wireless Speakers Rogue Access Points and computers acting as Access Points The DoIT may be contacted to help determine if a device utilizes the 2.4 GHz frequency and if it will cause interference. It is hoped that all faculty, staff, and students will abide by the airspace policies & procedures set forth in this document which will help in providing the best wireless network service possible. RELATED DOCUMENTS GothicAir User Guide Outdoor Wireless Coverage Indoor Wireless Locations Wireless Security Recommendations Revision Date: October 1, 2007 Page 4 of 5
5 Hints for Wireless Road Warriors FORMS GothicAir Guest Access Form Wireless Service Request Form All documents and forms are available from the DoIT website, Documents page and the University Policy website page. RESPONSIBLE PERSONNEL Responsibility Title Department Telephone Fax AP Installation Helpdesk DoIT Ext. HELP Revision Date: October 1, 2007 Page 5 of 5
Wireless Network Standard
 Last Modified: 10/20/15 Wireless Network Standard Purpose The standard and guidelines described in this document will ensure the uniformity of wireless network access points at the University of Georgia.
Last Modified: 10/20/15 Wireless Network Standard Purpose The standard and guidelines described in this document will ensure the uniformity of wireless network access points at the University of Georgia.
UC Santa Cruz Wireless Access Policy
 UC Santa Cruz Wireless Access Policy VERSION: 1.4 STATUS: DRAFT DATE: 26 APRIL 2004 STEWARD: Director, Network & Telecommunications Services Tad Reynales AUTHORITY: Vice-Provost, Information Technology
UC Santa Cruz Wireless Access Policy VERSION: 1.4 STATUS: DRAFT DATE: 26 APRIL 2004 STEWARD: Director, Network & Telecommunications Services Tad Reynales AUTHORITY: Vice-Provost, Information Technology
This regulation outlines the policy and procedures for the implementation of wireless networking for the University Campus.
 UAR NUMBER: 400.01 TITLE: Wireless Network Policy and Procedure INITIAL ADOPTION: 11/6/2003 REVISION DATES: PURPOSE: Set forth the policy for using wireless data technologies and assigns responsibilities
UAR NUMBER: 400.01 TITLE: Wireless Network Policy and Procedure INITIAL ADOPTION: 11/6/2003 REVISION DATES: PURPOSE: Set forth the policy for using wireless data technologies and assigns responsibilities
Wireless Network Policy and Procedures Version 1.5 Dated November 27, 2002
 Wireless Network Policy and Procedures Version 1.5 Dated November 27, 2002 Pace University reserves the right to amend or otherwise revise this document as may be necessary to reflect future changes made
Wireless Network Policy and Procedures Version 1.5 Dated November 27, 2002 Pace University reserves the right to amend or otherwise revise this document as may be necessary to reflect future changes made
POLICY 8200 NETWORK SECURITY
 POLICY 8200 NETWORK SECURITY Policy Category: Information Technology Area of Administrative Responsibility: Information Technology Services Board of Trustees Approval Date: April 17, 2018 Effective Date:
POLICY 8200 NETWORK SECURITY Policy Category: Information Technology Area of Administrative Responsibility: Information Technology Services Board of Trustees Approval Date: April 17, 2018 Effective Date:
ISSP Network Security Plan
 ISSP-000 - Network Security Plan 1 CONTENTS 2 INTRODUCTION (Purpose and Intent)... 1 3 SCOPE... 2 4 STANDARD PROVISIONS... 2 5 STATEMENT OF PROCEDURES... 3 5.1 Network Control... 3 5.2 DHCP Services...
ISSP-000 - Network Security Plan 1 CONTENTS 2 INTRODUCTION (Purpose and Intent)... 1 3 SCOPE... 2 4 STANDARD PROVISIONS... 2 5 STATEMENT OF PROCEDURES... 3 5.1 Network Control... 3 5.2 DHCP Services...
Marshall University Information Technology Council. Procedure ITP-16 IT INFRASTRUCTURE AUTHORIZATION PROCEDURE
 Marshall University Information Technology Council Procedure ITP-16 IT INFRASTRUCTURE AUTHORIZATION PROCEDURE General Information: 1.1 Scope: This procedure applies to all University employees, including
Marshall University Information Technology Council Procedure ITP-16 IT INFRASTRUCTURE AUTHORIZATION PROCEDURE General Information: 1.1 Scope: This procedure applies to all University employees, including
S T A N D A R D : M O B I L E D E V I C E S
 S T A N D A R D : M O B I L E D E V I C E S Contents 1 Purpose... 2 2 Scope... 2 3 Standard... 2 3.1 Lost or Stolen devices... 2 3.2 Administration of Mobile Devices... 2 3.3 Remote Device Wipe... 2 3.4
S T A N D A R D : M O B I L E D E V I C E S Contents 1 Purpose... 2 2 Scope... 2 3 Standard... 2 3.1 Lost or Stolen devices... 2 3.2 Administration of Mobile Devices... 2 3.3 Remote Device Wipe... 2 3.4
PHYSICAL AND ENVIRONMENTAL SECURITY
 PHYSICAL AND ENVIRONMENTAL SECURITY 1.0 STANDARD FOR PHYSICAL AND ENVIRONMENTAL SECURITY - EQUIPMENT 1.1 PURPOSE The purpose of this standard is to establish baseline controls to prevent loss, damage,
PHYSICAL AND ENVIRONMENTAL SECURITY 1.0 STANDARD FOR PHYSICAL AND ENVIRONMENTAL SECURITY - EQUIPMENT 1.1 PURPOSE The purpose of this standard is to establish baseline controls to prevent loss, damage,
POLICY FOR DATA AND INFORMATION SECURITY AT BMC IN LUND. October Table of Contents
 POLICY FOR DATA AND INFORMATION SECURITY AT BMC IN LUND October 2005 Table of Contents Introduction... 1 Purpose Of This Policy... 1 Responsibility... 1 General Policy... 2 Data Classification Policy...
POLICY FOR DATA AND INFORMATION SECURITY AT BMC IN LUND October 2005 Table of Contents Introduction... 1 Purpose Of This Policy... 1 Responsibility... 1 General Policy... 2 Data Classification Policy...
 Wireless Networking WiFi Standards 802.11a 5GHz 54MB 802.11b 2.4 GHz 11MB 802.11g 2.4GHz 52MB 802.11n 2.4/5GHz 108MB 802.11b The 802.11b standard has a maximum raw data rate of 11 Mbit/s, and uses
Wireless Networking WiFi Standards 802.11a 5GHz 54MB 802.11b 2.4 GHz 11MB 802.11g 2.4GHz 52MB 802.11n 2.4/5GHz 108MB 802.11b The 802.11b standard has a maximum raw data rate of 11 Mbit/s, and uses
Department of Public Health O F S A N F R A N C I S C O
 PAGE 1 of 7 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
PAGE 1 of 7 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
Wireless Attacks and Countermeasures
 Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Security Awareness, Training, And Education Plan
 Security Awareness, Training, And Education Plan Version 2.0 December 2016 TABLE OF CONTENTS 1.1 SCOPE 2 1.2 PRINCIPLES 2 1.3 REVISIONS 3 2.1 OBJECTIVE 4 3.1 PLAN DETAILS 4 3.2 WORKFORCE DESIGNATION 4
Security Awareness, Training, And Education Plan Version 2.0 December 2016 TABLE OF CONTENTS 1.1 SCOPE 2 1.2 PRINCIPLES 2 1.3 REVISIONS 3 2.1 OBJECTIVE 4 3.1 PLAN DETAILS 4 3.2 WORKFORCE DESIGNATION 4
A POLYCOM WHITEPAPER Deploying Enterprise-Grade Wi-Fi Telephony : Coverage, Capacity, Quality of Service, and Security Considerations for Delivering
 Deploying Enterprise-Grade Wi-Fi Telephony : Coverage, Capacity, Quality of Service, and Security Considerations for Delivering Excellent Voice Quality on Enterprise Wi-Fi Networks November 2010 Coverage,
Deploying Enterprise-Grade Wi-Fi Telephony : Coverage, Capacity, Quality of Service, and Security Considerations for Delivering Excellent Voice Quality on Enterprise Wi-Fi Networks November 2010 Coverage,
Security Surveillance Camera and Video Policy
 UW-Madison Security Surveillance Camera and Policy Effective Date: Oct. 1, 2014 Last Updated: August 1, 2018 Last Reviewed: August 1, 2018 Functional Owner Executive Sponsor Policy Contact Dir. of Security
UW-Madison Security Surveillance Camera and Policy Effective Date: Oct. 1, 2014 Last Updated: August 1, 2018 Last Reviewed: August 1, 2018 Functional Owner Executive Sponsor Policy Contact Dir. of Security
Guest Wireless Policy
 Effective: April 1, 2016 Last Revised: November 27, 2017 Responsible University Office: Information Technology Services Responsible University Administrator: Chief Information Officer Policy Contact: Deb
Effective: April 1, 2016 Last Revised: November 27, 2017 Responsible University Office: Information Technology Services Responsible University Administrator: Chief Information Officer Policy Contact: Deb
Digital Entertainment. Networking Made Easy
 Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Wireless technology Principles of Security
 Wireless technology Principles of Security 1 Wireless technologies 2 Overview This module provides an introduction to the rapidly evolving technology of wireless LANs (WLANs). WLANs redefine the way the
Wireless technology Principles of Security 1 Wireless technologies 2 Overview This module provides an introduction to the rapidly evolving technology of wireless LANs (WLANs). WLANs redefine the way the
CERTIFIED WIRELESS NETWORK PROFESSSIONAL CWNP Certified Wireless Network Administrator (CWNA)
 Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Employee Security Awareness Training Program
 Employee Security Awareness Training Program Date: September 15, 2015 Version: 2015 1. Scope This Employee Security Awareness Training Program is designed to educate any InComm employee, independent contractor,
Employee Security Awareness Training Program Date: September 15, 2015 Version: 2015 1. Scope This Employee Security Awareness Training Program is designed to educate any InComm employee, independent contractor,
Secure Mobility Challenges. Fat APs, Decentralized Risk. Physical Access. Business Requirements
 Unified Wireless Switching Enabling a Truly Converged Network White Paper Abstract As businesses scale, traditional wireless network deployments become more complex, more costly and less secure. Users
Unified Wireless Switching Enabling a Truly Converged Network White Paper Abstract As businesses scale, traditional wireless network deployments become more complex, more costly and less secure. Users
Annals of Mathematics Electronic License Agreement
 Annals of Mathematics Electronic License Agreement Annals of Mathematics, Fine Hall-Washington Road, Princeton University, Princeton, NJ 08544-1000, USA. Fax: 1-609-258-1367 Phone: 1-609-258-4191. By this
Annals of Mathematics Electronic License Agreement Annals of Mathematics, Fine Hall-Washington Road, Princeton University, Princeton, NJ 08544-1000, USA. Fax: 1-609-258-1367 Phone: 1-609-258-4191. By this
Lab WLAN Design
 Lab 9.3.9 WLAN Design Estimated Time: The time needed for this lab may vary Number of Team Members: Students will work individually or in small groups. Objective In this lab, students will identify various
Lab 9.3.9 WLAN Design Estimated Time: The time needed for this lab may vary Number of Team Members: Students will work individually or in small groups. Objective In this lab, students will identify various
University Facilities Management (UFM) Access Control Procedure (non-residence areas)
 University Facilities Management (UFM) Access Control Procedure (non-residence areas) Date of Issue: October 1, 2015 A. PURPOSE University Facilities Management s (UFM) Lock Shop Access Control Procedure
University Facilities Management (UFM) Access Control Procedure (non-residence areas) Date of Issue: October 1, 2015 A. PURPOSE University Facilities Management s (UFM) Lock Shop Access Control Procedure
Acceptable Use Policy
 Acceptable Use Policy This Acceptable Use Policy is in addition to South Central Communication s Terms of Service and together the documents constitute the Agreement between South Central Communications
Acceptable Use Policy This Acceptable Use Policy is in addition to South Central Communication s Terms of Service and together the documents constitute the Agreement between South Central Communications
RMU-IT-SEC-01 Acceptable Use Policy
 1.0 Purpose 2.0 Scope 2.1 Your Rights and Responsibilities 3.0 Policy 3.1 Acceptable Use 3.2 Fair Share of Resources 3.3 Adherence with Federal, State, and Local Laws 3.4 Other Inappropriate Activities
1.0 Purpose 2.0 Scope 2.1 Your Rights and Responsibilities 3.0 Policy 3.1 Acceptable Use 3.2 Fair Share of Resources 3.3 Adherence with Federal, State, and Local Laws 3.4 Other Inappropriate Activities
Wireless Security Access Policy and Agreement
 Wireless Security Access Policy and Agreement Purpose The purpose of this policy is to define standards, procedures, and restrictions for connecting to Fort Valley State University s internal network(s)
Wireless Security Access Policy and Agreement Purpose The purpose of this policy is to define standards, procedures, and restrictions for connecting to Fort Valley State University s internal network(s)
CCBC is equipped with 3 computer rooms, one at each main campus location:
 Policy: Computer Room Procedures Policy: Draft 12/14/2009 1.0 Purpose The purpose of this document is to establish procedures for the Community College of Baltimore County (CCBC) Information Technology
Policy: Computer Room Procedures Policy: Draft 12/14/2009 1.0 Purpose The purpose of this document is to establish procedures for the Community College of Baltimore County (CCBC) Information Technology
II.C.4. Policy: Southeastern Technical College Computer Use
 II.C.4. Policy: Southeastern Technical College Computer Use 1.0 Overview Due to the technological revolution in the workplace, businesses such as Southeastern Technical College (STC) have turned to computer
II.C.4. Policy: Southeastern Technical College Computer Use 1.0 Overview Due to the technological revolution in the workplace, businesses such as Southeastern Technical College (STC) have turned to computer
CITY OF DUBUQUE ADMINISTRATIVE POLICY REVISED OCTOBER 24, 2011 RETROACTIVE TO JANUARY 1, 2011
 CITY OF DUBUQUE ADMINISTRATIVE POLICY POLICY NUMBER: 2. 13 SUBJECT: ACQUISITION AND USE OF CELLULAR TELEPHONE EQUIPMENT APPROVED BY: CITY MANAGER EFFECTIVE DATE: AUGUST 6, 1996 REVISED FEBRUARY 1, 2004
CITY OF DUBUQUE ADMINISTRATIVE POLICY POLICY NUMBER: 2. 13 SUBJECT: ACQUISITION AND USE OF CELLULAR TELEPHONE EQUIPMENT APPROVED BY: CITY MANAGER EFFECTIVE DATE: AUGUST 6, 1996 REVISED FEBRUARY 1, 2004
Information Services IT Security Policies L. Network Management
 Information Services IT Security Policies L. Network Management Version 1.1 Last updated: 11th August 2010 Approved by Directorate: 2nd July 2009 Review date: 1st August 2011 Primary owner of security
Information Services IT Security Policies L. Network Management Version 1.1 Last updated: 11th August 2010 Approved by Directorate: 2nd July 2009 Review date: 1st August 2011 Primary owner of security
Standard For IIUM Wireless Networking
 INTERNATIONAL ISLAMIC UNIVERSITY MALAYSIA (IIUM) Document No : IIUM/ITD/ICTPOL/4.3 Effective Date : 13/11/2008 1.0 OBJECTIVE Standard For IIUM Wireless Networking Chapter : Network Status : APPROVED Version
INTERNATIONAL ISLAMIC UNIVERSITY MALAYSIA (IIUM) Document No : IIUM/ITD/ICTPOL/4.3 Effective Date : 13/11/2008 1.0 OBJECTIVE Standard For IIUM Wireless Networking Chapter : Network Status : APPROVED Version
WELLSBORO AREA SCHOOL DISTRICT
 No. 815.2 SECTION: OPERATIONS WELLSBORO AREA SCHOOL DISTRICT TITLE: DISTRICT-ISSUED LAPTOPS: STUDENT USE, RIGHTS, AND RESPONSIBILITIES ADOPTED: April 14, 2015 REVISED: October 7, 2015 815.2. DISTRICT-ISSUED
No. 815.2 SECTION: OPERATIONS WELLSBORO AREA SCHOOL DISTRICT TITLE: DISTRICT-ISSUED LAPTOPS: STUDENT USE, RIGHTS, AND RESPONSIBILITIES ADOPTED: April 14, 2015 REVISED: October 7, 2015 815.2. DISTRICT-ISSUED
Red Flags/Identity Theft Prevention Policy: Purpose
 Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Information Technology Standards
 Information Technology Standards IT Standard Issued: 9/16/2009 Supersedes: New Standard Mobile Device Security Responsible Executive: HSC CIO Responsible Office: HSC IT Contact: For questions about this
Information Technology Standards IT Standard Issued: 9/16/2009 Supersedes: New Standard Mobile Device Security Responsible Executive: HSC CIO Responsible Office: HSC IT Contact: For questions about this
Virginia Commonwealth University School of Medicine Information Security Standard
 Virginia Commonwealth University School of Medicine Information Security Standard Title: Scope: Personnel Security Standard This standard is applicable to all VCU School of Medicine personnel. Approval
Virginia Commonwealth University School of Medicine Information Security Standard Title: Scope: Personnel Security Standard This standard is applicable to all VCU School of Medicine personnel. Approval
HISPOL The United States House of Representatives Internet/ Intranet Security Policy. CATEGORY: Telecommunications Security
 HISPOL 003.0 The United States House of Representatives Internet/ Intranet Security Policy CATEGORY: Telecommunications Security ISSUE DATE: February 4, 1998 REVISION DATE: August 23, 2000 The United States
HISPOL 003.0 The United States House of Representatives Internet/ Intranet Security Policy CATEGORY: Telecommunications Security ISSUE DATE: February 4, 1998 REVISION DATE: August 23, 2000 The United States
ENJOY THE FREEDOM OF WIRELESS NETWORKING
 ENJOY THE FREEDOM OF WIRELESS NETWORKING Chances are there s a need for wireless in your enterprise network. Our user community includes town administration, Consider this... Today, wireless networking
ENJOY THE FREEDOM OF WIRELESS NETWORKING Chances are there s a need for wireless in your enterprise network. Our user community includes town administration, Consider this... Today, wireless networking
Information technology security and system integrity policy.
 3359-11-10.3 Information technology security and system integrity policy. (A) Need for security and integrity. The university abides by and honors its long history of supporting the diverse academic values
3359-11-10.3 Information technology security and system integrity policy. (A) Need for security and integrity. The university abides by and honors its long history of supporting the diverse academic values
IT Service Level Agreement
 The Glasgow School of Art IT Service Level Agreement September 2016 Policy Control Title IT Service Level Agreement Date Approved Sep 2016 Approving Bodies Executive Group Implementation Date September
The Glasgow School of Art IT Service Level Agreement September 2016 Policy Control Title IT Service Level Agreement Date Approved Sep 2016 Approving Bodies Executive Group Implementation Date September
MERU WIRELESS NETWORK DESIGN SERVICE
 MERU WIRELESS NETWORK DESIGN SERVICE INTRODUCTION. It is worth investing a little in the design phase to ensure that the Meru network infrastructure technical design meets or exceeds the specification
MERU WIRELESS NETWORK DESIGN SERVICE INTRODUCTION. It is worth investing a little in the design phase to ensure that the Meru network infrastructure technical design meets or exceeds the specification
Table of Contents. PCI Information Security Policy
 PCI Information Security Policy Policy Number: ECOMM-P-002 Effective Date: December, 14, 2016 Version Number: 1.0 Date Last Reviewed: December, 14, 2016 Classification: Business, Finance, and Technology
PCI Information Security Policy Policy Number: ECOMM-P-002 Effective Date: December, 14, 2016 Version Number: 1.0 Date Last Reviewed: December, 14, 2016 Classification: Business, Finance, and Technology
Securing Wireless Networks by By Joe Klemencic Mon. Apr
 http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
Wireless File Transmitter WFT-E6 Guide for EOS C300 Mark II Users
 DIE-0478-000 Wireless File Transmitter WFT-E6 Guide for EOS C300 Mark II Users E Introduction About this Guide You can attach a WFT-E6 Wireless File Transmitter to the Canon Digital Cinema Camera EOS C300
DIE-0478-000 Wireless File Transmitter WFT-E6 Guide for EOS C300 Mark II Users E Introduction About this Guide You can attach a WFT-E6 Wireless File Transmitter to the Canon Digital Cinema Camera EOS C300
Wireless LAN Security (RM12/2002)
 Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
2 University International Medical University
 POLICY OWNER : Information Technology Services TITLE : Document Code : IMU/POL/ITS/09 Edition : 1 Approval Body : Management Approval : 03/05/17 Committee Date Effective Date : 03/05/17 Pages : 6 1.0 OBJECTIVE
POLICY OWNER : Information Technology Services TITLE : Document Code : IMU/POL/ITS/09 Edition : 1 Approval Body : Management Approval : 03/05/17 Committee Date Effective Date : 03/05/17 Pages : 6 1.0 OBJECTIVE
Touchstone WECB460 Wi-Fi MoCA Bridge
 Touchstone WECB460 Wi-Fi MoCA Bridge Installation Guide ARRIS Enterprises, Inc. 2014 All rights reserved. No part of this publication may be reproduced in any form or by any means or used to make any derivative
Touchstone WECB460 Wi-Fi MoCA Bridge Installation Guide ARRIS Enterprises, Inc. 2014 All rights reserved. No part of this publication may be reproduced in any form or by any means or used to make any derivative
Donor Credit Card Security Policy
 Donor Credit Card Security Policy INTRODUCTION This document explains the Community Foundation of Northeast Alabama s credit card security requirements for donors as required by the Payment Card Industry
Donor Credit Card Security Policy INTRODUCTION This document explains the Community Foundation of Northeast Alabama s credit card security requirements for donors as required by the Payment Card Industry
Managed Campus WiFi Networks A Brief Overview. For academic, not-for-profit use only.
 Managed Campus WiFi Networks A Brief Overview For academic, not-for-profit use only. 1 Your Typical WiFi Users I can t use my FaceBook!! What s wrong with YOUR system? Image borrowed from the Internet
Managed Campus WiFi Networks A Brief Overview For academic, not-for-profit use only. 1 Your Typical WiFi Users I can t use my FaceBook!! What s wrong with YOUR system? Image borrowed from the Internet
VPN. The Remote Access Solution. A Comprehensive Guide to Evaluating: Security Administration Implementation. the virtual leader
 VPN The Remote Access Solution A Comprehensive Guide to Evaluating: Security Administration Implementation the virtual leader www.compatible.com VPN: The Remote Access Solution Contents The Promise of
VPN The Remote Access Solution A Comprehensive Guide to Evaluating: Security Administration Implementation the virtual leader www.compatible.com VPN: The Remote Access Solution Contents The Promise of
Access to University Data Policy
 UNIVERSITY OF OKLAHOMA Health Sciences Center Information Technology Security Policy Access to University Data Policy 1. Purpose This policy defines roles and responsibilities for protecting OUHSC s non-public
UNIVERSITY OF OKLAHOMA Health Sciences Center Information Technology Security Policy Access to University Data Policy 1. Purpose This policy defines roles and responsibilities for protecting OUHSC s non-public
TechNotes. Revision 3/3/2011. Third-Party Access Point Setup Basics
 Overview: TechNotes Revision 3/3/2011 Third-Party Access Point Setup Basics There are many instances where you may wish to add additional Access Points (AP) to a system. Typically, an additional AP is
Overview: TechNotes Revision 3/3/2011 Third-Party Access Point Setup Basics There are many instances where you may wish to add additional Access Points (AP) to a system. Typically, an additional AP is
Simple, full featured and budgetary deployment of single AP or distributed APs Hot-Spot for small scale projects.
 Colubris Wireless Hot-Spot solution for small and medium scale deployments 1. Definitions, goals, and objectives Simple, full featured and budgetary deployment of single AP or distributed APs Hot-Spot
Colubris Wireless Hot-Spot solution for small and medium scale deployments 1. Definitions, goals, and objectives Simple, full featured and budgetary deployment of single AP or distributed APs Hot-Spot
Identity Theft Prevention Policy
 Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Red Flags Program. Purpose
 Red Flags Program Purpose The purpose of this Red Flags Rules Program is to document the protocol adopted by the University of Memphis in compliance with the Red Flags Rules. Many offices at the University
Red Flags Program Purpose The purpose of this Red Flags Rules Program is to document the protocol adopted by the University of Memphis in compliance with the Red Flags Rules. Many offices at the University
It is requested that the Board approve the Northern Arizona University s Network Upgrade and Wireless Expansion Project.
 Page 1 of 7 EXECUTIVE SUMMARY ACTION ITEM: Network Upgrade and Wireless Expansion Project. ISSUE: Information Technology Services (ITS) proposes a campus-wide data network upgrade and the expansion of
Page 1 of 7 EXECUTIVE SUMMARY ACTION ITEM: Network Upgrade and Wireless Expansion Project. ISSUE: Information Technology Services (ITS) proposes a campus-wide data network upgrade and the expansion of
Password Standard Version 2.0 October 2006
 Password Standard Version 2.0 October 2006 TABLE OF CONTENTS 1.1 SCOPE 2 1.2 PRINCIPLES 2 1.3 REVISIONS 3 2.1 OBJECTIVE 4 3.1 POLICY 4 3.2 PROTECTION 4 3.3 LENGTH 4 3.4 SELECTIONS 4 3.5 EXPIRATION 5 3.6
Password Standard Version 2.0 October 2006 TABLE OF CONTENTS 1.1 SCOPE 2 1.2 PRINCIPLES 2 1.3 REVISIONS 3 2.1 OBJECTIVE 4 3.1 POLICY 4 3.2 PROTECTION 4 3.3 LENGTH 4 3.4 SELECTIONS 4 3.5 EXPIRATION 5 3.6
Information Technology Services UNMANAGED CO-LOCATION S E R V I C E L E V E L A G R E E M E N T
 Information Technology Services UNMANAGED CO-LOCATION S E R V I C E L E V E L A G R E E M E N T Department/School/Division: Effective USC Account Number (Required): 1. General Conditions 1.1. This agreement
Information Technology Services UNMANAGED CO-LOCATION S E R V I C E L E V E L A G R E E M E N T Department/School/Division: Effective USC Account Number (Required): 1. General Conditions 1.1. This agreement
Next Generation WLAN Technology for School Networks
 Next Generation WLAN Technology for School Networks AB&R 3431 East Elwood Street Phoenix, Arizona 85040 800-281-3056 info@abr.com www.abr.com/education The Fundamental Problems of Wireless Networking for
Next Generation WLAN Technology for School Networks AB&R 3431 East Elwood Street Phoenix, Arizona 85040 800-281-3056 info@abr.com www.abr.com/education The Fundamental Problems of Wireless Networking for
Wireless Andrew 2.0. February 13, Dan McCarriar Director, NICS
 Wireless Andrew 2.0 February 13, 2012 Dan McCarriar Director, NICS dlm@cmu.edu Agenda The history of Wireless Andrew Wireless standards 802.11n at Carnegie Mellon Planning the upgrade Deploying the network
Wireless Andrew 2.0 February 13, 2012 Dan McCarriar Director, NICS dlm@cmu.edu Agenda The history of Wireless Andrew Wireless standards 802.11n at Carnegie Mellon Planning the upgrade Deploying the network
HPE Aruba Airwave Installation and Startup Service
 Data sheet HPE Aruba Airwave Installation and Startup Service Support Services HPE Installation and Startup Service for select Aruba Airwave products coordinates installation, configuration, and verification
Data sheet HPE Aruba Airwave Installation and Startup Service Support Services HPE Installation and Startup Service for select Aruba Airwave products coordinates installation, configuration, and verification
Wireless LANs in Higher Education. Benefits of Wireless in Higher Education. Students & Faculty. Institution
 Wireless LANs in Higher Education Universities and colleges are among the most aggressive adopters of Wi-Fi technology. The trend toward more collaborative and open learning environments, fueled by the
Wireless LANs in Higher Education Universities and colleges are among the most aggressive adopters of Wi-Fi technology. The trend toward more collaborative and open learning environments, fueled by the
Detecting & Eliminating Rogue Access Point in IEEE WLAN
 Detecting & Eliminating Rogue Access Point in IEEE 802.11 WLAN S.B.Vanjale, Amol K. Kadam, Pramod A. Jadhav Department of Computer Engg Bharati Vidyapeeth Deemed University College of Engineering Pune.
Detecting & Eliminating Rogue Access Point in IEEE 802.11 WLAN S.B.Vanjale, Amol K. Kadam, Pramod A. Jadhav Department of Computer Engg Bharati Vidyapeeth Deemed University College of Engineering Pune.
Cisco Unified Wireless Network Solution Overview
 1 CHAPTER Unified Wireless Network Solution Overview This chapter summarizes the benefits and characteristics of the Unified Wireless Network for the enterprise.the Unified Wireless Network solution offers
1 CHAPTER Unified Wireless Network Solution Overview This chapter summarizes the benefits and characteristics of the Unified Wireless Network for the enterprise.the Unified Wireless Network solution offers
A. Facilities and critical systems employees subject to afterhours call out.
 ADMINISTRATIVE PROCEDURE 6450: Mobile Communication Devices and Cellular Phones Purpose To establish procedures for the assignment of an allowance for cellular telephones and other wireless, handheld mobile
ADMINISTRATIVE PROCEDURE 6450: Mobile Communication Devices and Cellular Phones Purpose To establish procedures for the assignment of an allowance for cellular telephones and other wireless, handheld mobile
Clear Desk, Clear Screen Policy
 Clear Desk, Clear Screen Policy 1 P a g e Table of Contents 1 Introduction... 3 2 Purpose... 3 3 Non Operations Policy... 3 4 Operations Policy.4 5 Review and Approvals... 5 2 P a g e 1 Introduction Synchronoss
Clear Desk, Clear Screen Policy 1 P a g e Table of Contents 1 Introduction... 3 2 Purpose... 3 3 Non Operations Policy... 3 4 Operations Policy.4 5 Review and Approvals... 5 2 P a g e 1 Introduction Synchronoss
IEEE n Wireless PCI Adapter. User s Manual
 IEEE 802.11n Wireless PCI Adapter User s Manual October, 2008 FCC Warning This equipment has been tested and found to comply with the limits for a Class C digital device, pursuant to part 15 of the FCC
IEEE 802.11n Wireless PCI Adapter User s Manual October, 2008 FCC Warning This equipment has been tested and found to comply with the limits for a Class C digital device, pursuant to part 15 of the FCC
IBM Case Manager on Cloud
 Service Description IBM Case Manager on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients of the
Service Description IBM Case Manager on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients of the
ICT-Guideline. Contents. Computer Science Steering group
 CATHOLIC UNIVERSITY OF LEUVEN FACULTY OF THEOLOGY AND RELIGIOUS STUDIES SINT- MICHIELSSTRAAT 4 BOX 3100 3000 LEUVEN, BELGIUM LEUVEN Computer Science Steering group 2014-12-09 ICT-Guideline In addition
CATHOLIC UNIVERSITY OF LEUVEN FACULTY OF THEOLOGY AND RELIGIOUS STUDIES SINT- MICHIELSSTRAAT 4 BOX 3100 3000 LEUVEN, BELGIUM LEUVEN Computer Science Steering group 2014-12-09 ICT-Guideline In addition
Wednesday, May 16, 2018
 Wednesday, May 16, 2018 8:00 AM - 5:00 PM Wi Fi/WLAN Fundamentals Training by Tessco; Day Two of a Two Day Training. (Attendees must bring laptop computers for this training. Attendees should bring available
Wednesday, May 16, 2018 8:00 AM - 5:00 PM Wi Fi/WLAN Fundamentals Training by Tessco; Day Two of a Two Day Training. (Attendees must bring laptop computers for this training. Attendees should bring available
Celestix Networks, Inc. 702 Brown Road. Fremont, California Ph Fx Introduction to Wireless Local Area Network
 Introduction to Wireless Local Area Network white paper Introduction A wireless local area network (WLAN) is a flexible data communications system that can use either infrared or radio frequency (RF) technology
Introduction to Wireless Local Area Network white paper Introduction A wireless local area network (WLAN) is a flexible data communications system that can use either infrared or radio frequency (RF) technology
Mobile Device policy Frequently Asked Questions April 2016
 Mobile Device policy Frequently Asked Questions April 2016 In an attempt to help the St. Lawrence University community understand this policy, the following FAQ document was developed by IT in collaboration
Mobile Device policy Frequently Asked Questions April 2016 In an attempt to help the St. Lawrence University community understand this policy, the following FAQ document was developed by IT in collaboration
IT EQUIPMENT POLICY REPLACEMENT CYCLE
 IT EQUIPMENT POLICY REPLACEMENT CYCLE It is an objective of the Hibbing Community College (HCC) Information Technology department to regularly replace aging computer equipment with more modern items as
IT EQUIPMENT POLICY REPLACEMENT CYCLE It is an objective of the Hibbing Community College (HCC) Information Technology department to regularly replace aging computer equipment with more modern items as
Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy
 CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
Cyber Security Guidelines for Public Wi-Fi Networks
 Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
MESH TECHNOLOGY PRIMER
 MESH TECHNOLOGY PRIMER The Evolution of Wi-Fi: From Hot Spots to Hot Zones to Municipal Networks Wi-Fi technology has experienced unprecedented growth for both consumer and enterprise use in a very short
MESH TECHNOLOGY PRIMER The Evolution of Wi-Fi: From Hot Spots to Hot Zones to Municipal Networks Wi-Fi technology has experienced unprecedented growth for both consumer and enterprise use in a very short
Computer Classroom Security Standard
 Computer Classroom Security Standard Cal State Fullerton operates a heterogeneous network environment composed of centrally supported workstations, servers, and the network infrastructure. Along with administrative
Computer Classroom Security Standard Cal State Fullerton operates a heterogeneous network environment composed of centrally supported workstations, servers, and the network infrastructure. Along with administrative
Designing and Building a Campus Wireless Network
 Designing and Building a Campus Wireless Network For the K- 12 Community of North Carolina Version 3 2/20/2017 Designing and Building a Campus Wireless Network For the K- 12 Community of North Carolina
Designing and Building a Campus Wireless Network For the K- 12 Community of North Carolina Version 3 2/20/2017 Designing and Building a Campus Wireless Network For the K- 12 Community of North Carolina
QuickSpecs. HPE OfficeConnect M n Access Point Series. Overview. HPE OfficeConnect M n Access Point Series
 Overview Models HPE OfficeConnect M220 802.11n (AM) Access Point HPE OfficeConnect M220 802.11n (WW) Access Point J9798A J9799A Key features IEEE 802.11a/b/g/n access point Single-radio, dual-band (2.4
Overview Models HPE OfficeConnect M220 802.11n (AM) Access Point HPE OfficeConnect M220 802.11n (WW) Access Point J9798A J9799A Key features IEEE 802.11a/b/g/n access point Single-radio, dual-band (2.4
Office of Human Resources 3/28/13 Page 1 of 7
 JOB FAMILY CONCEPT This job family consists of eight levels of Information Systems Technical work distinguished by the complexity of the responsibilities assigned and characterized by the type of equipment,
JOB FAMILY CONCEPT This job family consists of eight levels of Information Systems Technical work distinguished by the complexity of the responsibilities assigned and characterized by the type of equipment,
Connecting to KSUGuest WiFi on Windows 8.1
 University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Connecting to KSUGuest WiFi on Windows 8.1 The following guide walks you through connecting to the KSUGuest
University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Connecting to KSUGuest WiFi on Windows 8.1 The following guide walks you through connecting to the KSUGuest
Connecting to KSUGuest WiFi on Windows 10
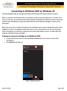 University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Connecting to KSUGuest WiFi on Windows 10 The following guide walks you through connecting to the KSUGuest
University Information Technology Services Learning Technologies, Training & Audiovisual Outreach Connecting to KSUGuest WiFi on Windows 10 The following guide walks you through connecting to the KSUGuest
What is a Wireless LAN? The wireless telegraph is not difficult to understand. The ordinary telegraph is like a very long cat. You pull the tail in Ne
 Introduction to Wireless Networking and Security Chino Information Technology Center Steve Siedschlag, Associate Professor What is a Wireless LAN? The wireless telegraph is not difficult to understand.
Introduction to Wireless Networking and Security Chino Information Technology Center Steve Siedschlag, Associate Professor What is a Wireless LAN? The wireless telegraph is not difficult to understand.
BROWARD COUNTY AVIATION DEPARTMENT INSIDE PLANT INFRASTRUCTURE SPECIFICATIONS
 BROWARD COUNTY AVIATION DEPARTMENT INSIDE PLANT INFRASTRUCTURE SPECIFICATIONS All noted standards apply to the current revisions applicable at the time of construction or intended construction. NO SUBSTITUTIONS
BROWARD COUNTY AVIATION DEPARTMENT INSIDE PLANT INFRASTRUCTURE SPECIFICATIONS All noted standards apply to the current revisions applicable at the time of construction or intended construction. NO SUBSTITUTIONS
Data Center Access Policies and Procedures
 Data Center Access Policies and Procedures Version 2.0 Tuesday, April 6, 2010 1 Table of Contents UITS Data Center Access Policies and Procedures!3 Introduction!3. Overview!3 Data Center Access!3 Data
Data Center Access Policies and Procedures Version 2.0 Tuesday, April 6, 2010 1 Table of Contents UITS Data Center Access Policies and Procedures!3 Introduction!3. Overview!3 Data Center Access!3 Data
Access Control Procedure
 HIPAA Security Procedure # Last Revised: 3/15/2006 Approved: Scope of Procedure The scope of this Policy covers the unique user identification and password, emergency access, automatic logoff, encryption
HIPAA Security Procedure # Last Revised: 3/15/2006 Approved: Scope of Procedure The scope of this Policy covers the unique user identification and password, emergency access, automatic logoff, encryption
Cyber Security Guidelines for Securing Home and Small Office Routers
 Cyber Security Guidelines for Securing Home and Small Office Routers Author: CS Risk Management Section Document Published Date: March 2018 Document History: Version Description Date 1.0 Published V1.0
Cyber Security Guidelines for Securing Home and Small Office Routers Author: CS Risk Management Section Document Published Date: March 2018 Document History: Version Description Date 1.0 Published V1.0
Security Standards for Electric Market Participants
 Security Standards for Electric Market Participants PURPOSE Wholesale electric grid operations are highly interdependent, and a failure of one part of the generation, transmission or grid management system
Security Standards for Electric Market Participants PURPOSE Wholesale electric grid operations are highly interdependent, and a failure of one part of the generation, transmission or grid management system
Wireless Networks
 802.11 Wireless Networks Presentation for North Central Regional Meeting October 19, 2010 Tom Jones, PE, RCDD / NTS Field Sales Engineer, D-Link Agenda Brief History of Wireless Networks 802.11b, 802.11g
802.11 Wireless Networks Presentation for North Central Regional Meeting October 19, 2010 Tom Jones, PE, RCDD / NTS Field Sales Engineer, D-Link Agenda Brief History of Wireless Networks 802.11b, 802.11g
XAVi Technologies Corporation Tel: Fax: F, No. 129, Hsing Te Road, Sanchung City, Taipei County 241, Taiwan
 XAVi Technologies Corporation Tel: +886-2-2995-7953 Fax: +886-2-29957954 9F, No. 129, Hsing Te Road, Sanchung City, Taipei County 241, Taiwan Copyright 2005, XAVi Technologies Corporation Information in
XAVi Technologies Corporation Tel: +886-2-2995-7953 Fax: +886-2-29957954 9F, No. 129, Hsing Te Road, Sanchung City, Taipei County 241, Taiwan Copyright 2005, XAVi Technologies Corporation Information in
CCNA Discovery 4.0 Designing and Supporting Computer Networks
 CCNA Discovery 4.0 Designing and Supporting Computer Networks Characterizing Existing Network Chapter 3 1 Objectives 2 Creating a Network Diagram Typically, the first step in installing a new network is
CCNA Discovery 4.0 Designing and Supporting Computer Networks Characterizing Existing Network Chapter 3 1 Objectives 2 Creating a Network Diagram Typically, the first step in installing a new network is
GRE AMERICA, INC. Wireless LAN USB Client Instllation
 GRE AMERICA, INC Wireless LAN USB Client Instllation Table of Contents FCC Warning Information Chapter 1 Introduction Package Contents 1 System Requirement 1 Features 1 Chapter 2 Installing Application
GRE AMERICA, INC Wireless LAN USB Client Instllation Table of Contents FCC Warning Information Chapter 1 Introduction Package Contents 1 System Requirement 1 Features 1 Chapter 2 Installing Application
Complying with RBI Guidelines for Wi-Fi Vulnerabilities
 A Whitepaper by AirTight Networks, Inc. 339 N. Bernardo Avenue, Mountain View, CA 94043 www.airtightnetworks.com 2013 AirTight Networks, Inc. All rights reserved. Reserve Bank of India (RBI) guidelines
A Whitepaper by AirTight Networks, Inc. 339 N. Bernardo Avenue, Mountain View, CA 94043 www.airtightnetworks.com 2013 AirTight Networks, Inc. All rights reserved. Reserve Bank of India (RBI) guidelines
Wireless Communication Device Policy Policy No September 2, Standard. Practice
 Standard This establishes the business need and use of cellular phones (hereinafter referred to as wireless communication devices ) as an effective means of conducting City of Richland business, and to
Standard This establishes the business need and use of cellular phones (hereinafter referred to as wireless communication devices ) as an effective means of conducting City of Richland business, and to
IDAHO STATE UNIVERSITY POLICIES AND PROCEDURES (ISUPP) ITS Responsible Use of Telephone, Telecommunications, and Networking Resources ISUPP 2280
 IDAHO STATE UNIVERSITY POLICIES AND PROCEDURES (ISUPP) ITS Responsible Use of Telephone, Telecommunications, and Networking Resources ISUPP 2280 POLICY INFORMATION Policy Section: Information Technology
IDAHO STATE UNIVERSITY POLICIES AND PROCEDURES (ISUPP) ITS Responsible Use of Telephone, Telecommunications, and Networking Resources ISUPP 2280 POLICY INFORMATION Policy Section: Information Technology
PCI PA-DSS Implementation Guide
 PCI PA-DSS Implementation Guide For Atos Worldline Banksys XENTA, XENTEO, XENTEO ECO, XENOA ECO YOMANI and YOMANI XR terminals using the Point BKX Payment Core Software Versions A05.01 and A05.02 Version
PCI PA-DSS Implementation Guide For Atos Worldline Banksys XENTA, XENTEO, XENTEO ECO, XENOA ECO YOMANI and YOMANI XR terminals using the Point BKX Payment Core Software Versions A05.01 and A05.02 Version
Technology being employed in educational institutions has fundamentally changed over the past few years and is continuing to evolve.
 Technology being employed in educational institutions has fundamentally changed over the past few years and is continuing to evolve. Mobile devices such as ipads, laptops and smart phones are quickly replacing
Technology being employed in educational institutions has fundamentally changed over the past few years and is continuing to evolve. Mobile devices such as ipads, laptops and smart phones are quickly replacing
How Insecure is Wireless LAN?
 Page 1 of 7 How Insecure is Wireless LAN? Abstract Wireless LAN has gained popularity in the last few years due to its enormous benefits such as scalability, mobile access of the network, and reduced cost
Page 1 of 7 How Insecure is Wireless LAN? Abstract Wireless LAN has gained popularity in the last few years due to its enormous benefits such as scalability, mobile access of the network, and reduced cost
TARGET2-SECURITIES INFORMATION SECURITY REQUIREMENTS
 Target2-Securities Project Team TARGET2-SECURITIES INFORMATION SECURITY REQUIREMENTS Reference: T2S-07-0270 Date: 09 October 2007 Version: 0.1 Status: Draft Target2-Securities - User s TABLE OF CONTENTS
Target2-Securities Project Team TARGET2-SECURITIES INFORMATION SECURITY REQUIREMENTS Reference: T2S-07-0270 Date: 09 October 2007 Version: 0.1 Status: Draft Target2-Securities - User s TABLE OF CONTENTS
