IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
|
|
|
- Winifred Hamilton
- 5 years ago
- Views:
Transcription
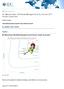
1 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Managed Security Services Vendor Assessment Source: IDC, 2017 Please see the Appendix for detailed methodology, market definition, and scoring criteria. August 2017, IDC #US
2 IDC OPINION The managed security services (MSS) market continues to evolve rapidly. Within just the past few years, even the past 18 months, managed security services providers (MSSPs) have added more capabilities and advanced security services to assist organizations in defending against and responding to today's attacks. Using the IDC MarketScape model, IDC has compared 12 organizations that offer MSS worldwide. Through in-depth MSSP interviews and more than 20 interviews with providers' customers, IDC learned that all the providers included in this study have the necessary capabilities to deliver traditional worldwide MSS. However, most are now able to go beyond the traditional services areas, incorporating advanced services such as distributed denial of service (DDoS), web application security, identity access management (IAM), managed security and information event management (SIEM), and managed security operation center (SOC) (see Appendix for further details) into their propositions. By its very nature, inclusion in this rating study indicates that participants are top-rated global providers and should be considered for managed security services. Furthermore, as a result of this IDC MarketScape evaluation, IDC identified the following eight companies as Leaders: IBM, BT, Verizon, AT&T, Accenture, Deloitte, DXC Technology, and SecureWorks. The group of Major Players consists of Symantec, Wipro, HCL, and NTT Security. Given the rapid pace of development within the MSS market, it is important that all providers continue to develop upon MSS capabilities and go beyond the traditional offerings. This is essential to keep pace with the development of the market, let alone remaining ahead of the chasing pack. Through more granular evaluation, IDC found that each provider possesses some unique strengths and weaknesses when compared with its peer group. At a high level, the major differences centered on their strategies for the next 12 months. Many of the providers now offer a breadth of complementary security transformation services to assist customers with digital transformation. Other factors that were looked at include pricing, marketing, security operation centers staffing, and customer portal capabilities. IDC believes that the following areas will drive the MSS market forward while providing vendors with the opportunity to hone a differentiated proposition: Complementary services that provide customizable opportunities for assistance in security transformation and maturity; these can include enabling security within a customer's journey to the cloud Cloud monitoring, visibility, and management capabilities that seamlessly enable hybrid implementations Flexible consumption models that match customers' preferences for integrating MSSP expertise, processes, and technology Pricing models that support the end customer's buying preference Mobility and IoT solutions Advanced detection methods and analytics techniques, including advanced detection and response capabilities, threat intelligence, and big data Robust customer support, including incident response (IR) and forensics, to assist with recovery from breaches Customer portal and reporting capabilities Security orchestration and automation technologies to provide more efficient incident response workflow Security operations centers Advanced methods of acquiring and retaining security talent 2017 IDC #US
3 IDC MARKETSCAPE VENDOR INCLUSION CRITERIA IDC collected and analyzed data on 12 MSSPs within the 2016 IDC MarketScape worldwide managed security services market assessment. While the market arena for MSS is broad and there are many suppliers that offer these services, IDC narrowed the field of participants for this study based on the following criteria: Service capability across the MSS life cycle. Each service provider was required to possess full-service MSS delivery capabilities (see the Appendix section for an explanation of MSS). Revenue. Each service provider was required to have 2015 total MSS global revenue in excess of $180 million and a SOC presence in each of three regions the Americas, EMEA, and APAC in addition to having a minimum of five SOCs. Geographic presence. Each vendor was required to have MSS delivery capability in each of three regions: the Americas, EMEA, and APAC. ADVICE FOR TECHNOLOGY BUYERS Buyers face complex choices in selecting an MSSP because of the number of providers and a multitude of variables: breadth and depth of offerings; staffing, capabilities, and locations; complementary services, onboarding methods, service-level agreements (SLAs), payment options, customer portal capabilities, customer service delivery methods, partnerships, and more. Given the pace of technology change, buyers should evaluate current and future MSSP offerings along with the MSSPs' product/service/investment road maps. This is important to be sure that future offerings align with anticipated business and cost projections. It can be expensive and disruptive to change providers, so it is worthwhile for buyers to take the time to find the right fit, no matter how many security services are being outsourced. An MSSP's customer satisfaction surveys, pricing benchmarks, use cases, proofs of concept, and/or best practices can aid the decision process. To enhance the decision-making process in vendor selection, IDC recommends that buyers bear in mind the following considerations: Evaluate the MSS research and development (R&D) road map. Many organizations are embarking on a digital transformation journey and are changing the way they operate, deliver services, and interact with their customers. It is imperative that an MSSP supports these organizations by providing trusted relationships and the security services needed to achieve their goals. Forward-looking MSSPs are paying attention to these changes and are enhancing their proposition around themes such as cloud evolution, incident response, forensics, advanced detection techniques, threat intelligence, artificial intelligence, machine learning, and big data analytics. Organizations need to evaluate an MSSP's future road map strategies and determine whether the MSSP will be able to provide the security support necessitated by digital transformation. For example, cloud monitoring services are becoming more important as organizations adopt cloud. A knock-on effect of this change is that identity access management will be a critical factor as more applications move to the cloud and users move to hybrid clouds. A further example is provided by the trend of MSSPs seeking to implement software-defined networking (SDN) and network function virtualization (NFV) technologies as a means to create internal cost efficiencies and provide more nimble and flexible services. Review cloud adoption strategy and future security strategy. Workloads are shifting to multiple cloud platforms. This makes it important to select an MSSP that can deliver the offerings that best fit your business needs and can be flexible to meet future changes occurring within your 2017 IDC #US
4 FIGURE 2 infrastructure. Many MSSPs are working with customers to help them move to the cloud securely and successfully, perhaps as part of broader IT services engagements. In fact, for some enterprises and public entities, this has become a top priority. MSSPs are working with customers to expand the delivery of cloud offerings, and they are helping organizations with management and monitoring using on-premises equipment for log collection. Organizations are looking for ways to monitor their infrastructures as well as applications when delivered through public cloud platforms such as AWS and Azure. While on-premises has been a stable delivery model for MSSPs, ongoing cloud migrations are driving the demand for MSSPS to offer hosted and even cloud-based delivery models (see Figure 2). Hybrid Outsourcing Prevails Q. For the managed security services you purchased in the past 12 months, how does that break down for the following? Source: IDC's Global Security Services Survey, 2016 Referring back to Figure 2, it illustrates the total number of respondents reporting to use MSS as an on-premises delivery, multitenant environment hosted by the service provider, or for security as a services (SaaS). From a global perspective, 37.3% of total respondents are using MSS for onpremises delivery service, 30.8% are using a multitenant environment hosted by the service provider, and 31.9% reported using MSS for SaaS delivery. Use of all three outsourcing delivery mechanisms is an ongoing trend across all regions. Further: Leverage threat intelligence and big data analytics. Cyberattacks are only going to increase in frequency and severity. Organizations can no longer afford a "do the minimum" security 2017 IDC #US
5 FIGURE 3 strategy, which is simply not sufficient to thwart advanced persistent threats, distributed denial of service, identity theft, and other sophisticated attack strategies. A commonsense best practice in retaliation to mitigate against these advanced attacks is to acquire and use reliable, "predictive" intelligence that results from a robust combination of technology and expertise. Buyers may want to evaluate MSSP capabilities such as large databases (for long-term analysis), data aggregation and correlation, user behavior- and heuristic-based detection (versus signature-based detection), anomaly detection, machine learning, emulation/sandboxing, virtual containerization, forensics, detection, and response tools (see Figure 3). Buyers should look at how threat intelligence is being analyzed and distributed and whether MSSPs are using big data platforms such as Hadoop or Elastic Stack. Many MSSPs are investing in decreasing the human impact by automating data-related processes and analysis, which in turn will lead to faster decisions and response times. Buyers should look at how these MSSPS are investing in big data analytics, in growing their specialized skilled pool of researchers, adding dark web analytics, and cognitive and artificial intelligence. Most Effective Methods in Threat Detection Q. Which methods do you believe are the most effective in detecting a threat in your environment? Please rank order by their effectiveness. n = 1,003 *46.8% of MNCs ranked advanced detection techniques as most effective. Note: Methods are believed to be most effective at threat detection (first ranked). Source: IDC's Global Security Services Survey, IDC #US
6 Referring back to Figure 3, it illustrates the methods believed to be most effective at threat detection. Nearly 40% of firms ranked advanced detection techniques like capturing network data to analyze behavior, correlating to white and black threat lists, sandboxing, and so forth as the most effective. Less than a quarter, 21.6%, believed methods such as use of signature-based lists of known vulnerabilities or threats that are put into firewall rules, AV patches were effective. Further: Review customer portals. Portals are the primary conduits of information between MSSPs and their customers, and they determine the scope and ease of visibility and control. Portals can be a competitive differentiator, and as such, they should be able to satisfy broad user requirements. Many providers are revamping their MSSP portals to make them user friendly and easy to navigate with visualization tools and customizable reporting capabilities. In addition, portals typically include real-time data analysis and advanced analytic capabilities to improve investigation workflow for purposes of enhancing detection and response times. Increasingly, portals include role-based access, querying of security and information event management data with broad correlation capabilities, and real-time chat or instant messaging. MSSPs are expanding search and communication, self-service capabilities, and in-depth reporting and enhancing visibility for customers. MSSPs should be able to demonstrate how their MSS are integrated into the portal and how the portal can be customized for different types of users (e.g., executives and security personnel). Consider security expertise and customer engagement. Buyers should consider how the engagement will occur between them and an MSSP once the services are established. It is important that the MSSP acts as a trusted advisor and as an extension to the customer's IT team. Buyers may want to review whether staff augmentation is needed to support their initiatives and bring on staff to work with them on-premises or evaluate the expertise of the analysts being provided to them. MSSPs should be investing in cybersecurity proficiency and acquiring and retaining security talent. Investments in training and retention methods are important differentiation in a competitive marketplace. Evaluate complementary services. MSSPs included in this study offer some or all of the following services that are complementary to MSS: assessment of architecture and design, breach management, incident response, forensics, and compliance services. Some MSSPs offer additional services such as security transformation, IoT, adversary simulation, security awareness training, and cloud security. Buyers should consider an MSSP that can help develop, strengthen, and continue to evaluate their security programs. Enterprises must have a strategy to respond to incidents and collect forensic evidence for legal and/or compliance reasons. A preemptive strategy is even better one that does not treat all security threats as equal and apportions resources based on a current-state/future-state risk analysis. Review package security solutions. Security is becoming important not only in large enterprises but also in small to midsize organizations that are looking for lower cost, bundled security solutions. Services such as DDoS protection can be bundled with internet services and so forth. Small to midsize organizations should evaluate providers that will be able to provide these bundled services and products at a reasonable cost. Investigate flexible pricing methods. MSSPs typically offer their customers a number of pricing models. Ordinarily, a customer will choose to pay per device, by consumption of data (utility price option), or per IP pricing options. As MSS starts to downstream into midsize and smaller businesses, pricing models are becoming more flexible to accommodate the differences in scale and prioritization of smaller enterprises in comparison with larger ones. For example, some MSSPs are looking at newer and more innovative approaches. These include pricing per change request, logs/events collected, device-volume basis for which different tiers are offered, or pay-as-you-go pricing. Further, some MSSPs are investigating prepaid concepts, 2017 IDC #US
7 which hold some similarities in comparison with incident response "retainer" contracts. For example, customers can pay for a certain number of credits in advance using a standard rate. They allocate those credits against the activities they want at different times throughout the contract. With the introduction of new technologies, buyers need to be aware of the new pricing models and evaluate what will work best for their organizations. Review security orchestration and automation technologies. Providers are investing in automation and orchestration of technologies. The new techniques have a variety of benefits that can help customers order new services on demand and provide a more efficient workflow for analyzing threats. Buyers should be aware of what the MSSP road map looks like in implementing these new efficient technologies. Determine which SOC implementation matches business requirements. The types of SOC implementations are: In-region: A standalone SOC in a country or region Follow the sun (FTS): A type of global workflow in which tasks are passed around daily at the end of work shifts among work sites that may be in different time zones Global: Workflow that occurs in one global location in a 24 x 7 and multishift arrangement Some combination of in-region, FTS, and global SOC More advanced MSSPs are able to offer a combination of SOC service delivery models in order to create a smooth handoff of change orders, tickets, and implementation as well as to create monitoring redundancy. In-region SOCs allow customer data to be retained in that region or country, which satisfies data privacy concerns and, in some cases, data sovereignty laws. To stay at the forefront of threat intelligence, however, MSSPs need to provide for anonymized meta-level data to leave the region or country for correlation purposes. FTS creates an advantage for MSSPs with international or multinational clients (MNCs) that require around-the-clock monitoring and management. The single-shift nature often associated with FTS allows employees to live their lives without working a nighttime shift and can create a cost benefit for the customer. The disadvantage of FTS can be a lack of consistency in support around handoff processes, installations, and incidents as well as in a possible lack of monitoring redundancy. Finally, FTS allows for localization of talent, which satisfies clients that prefer in-region language support and cultural perspective. However, there can be disconnects between each SOC in the rotation, and these cultural/language barriers can become an obstacle. IDC believes the highest tier of MSSPs, which are on the cutting edge of a truly global MSS delivery (versus international see the Terminology section), can satisfy regional data privacy concerns and the facilitation of an MNC security strategy with a combination of in-region, FTS, and global SOC structure. VENDOR SUMMARY PROFILES This section briefly explains IDC's key observations resulting in a vendor's position in the IDC MarketScape. While every vendor is evaluated against each of the criteria outlined in the Appendix, the description here provides a summary of each vendor's strengths and challenges. IDC reviewed 12 MSSPs against current capabilities and future strategy criteria as part of its IDC MarketScape on the worldwide MSS market. IDC also conducted customer interviews of more than 20 vendor customers to obtain feedback on how the vendors performed in delivering MSS. Vendors 2017 IDC #US
8 participating in the analysis are Accenture, AT&T, BT, DXC Technology, Deloitte, HCL Technologies, IBM, NTT Security, SecureWorks, Symantec, Wipro, and Verizon. Accenture Accenture is positioned as a Leader in the IDC MarketScape for worldwide managed security services. Accenture is a global professional services company, providing a broad range of services and solutions in strategy, consulting, digital, technology, and operations for clients across multiple industries. Accenture operates delivery centers globally, with Cyber Fusion Centers located in Washington, D.C.; Prague, Czech Republic; Tel Aviv, Israel; and Bangalore, India. Accenture's Cyber Fusion Centers fuse three components: cyberlabs to develop innovative solutions, proof of concepts (POCs) through Accenture's Liquid Studios where solutions are built specific to customers' needs, and the delivery arm for the managed security services business. Accenture employs more than 1,500 SOC analysts across the multiple Cyber Fusion Centers, which follow a 24 x 7 model. Accenture's MSS provides flexible operating models, detailed transition plans, mature runbooks, and other capabilities that enable continuity of security operations and seamless handoff of incident management. Accenture Security offers end-to-end services that include strategy and risk, cyberdefense, digital identity, application security, and managed security services. Within managed security, Accenture Security provides managed cyberdefense services such as security monitoring and response, application security, vulnerability management, threat hunting, and penetration testing. In addition, Accenture Security provides managed identity and managed compliance services. In the past year, Accenture has made significant investments in the growth of its people and its MSS business. These investments were made organically in the Accenture Labs and Innovation Centers. Nearly all of Accenture's innovation in MSS prior to FY17 was driven by organic investment to industrialize, train, and improve delivery. Further, Accenture has made strategic acquisitions to acquire skills and capabilities: Arismore, Cimation, Defense Point, FusionX, idefense, Maglan, RedCore, and the U.S. federal government services business of Endgame Inc. These acquisitions position Accenture with up-to-date security solutions and engagement capabilities. Strengths Because of Accenture's global reach and consulting-led engagements, the company markets its MSS offerings into broader security engagements, which allows Accenture a competitive advantage against other MSSPs. Accenture's experience also emphasizes value through end-to-end, industry-specific offerings. For example, customer feedback shows that Accenture provides improved insight based on the breadth and depth of use cases applicable to the customer's environment or industry. In addition, one customer commented that Accenture provided a customized solution specific to the customer's needs instead of a cookie-cutter solution. Accenture consistently demonstrates that security is at the forefront of its business by investing in technologies such as machine learning, automation, artificial intelligence, and cognitive analytics. Accenture's commitment to security is also evidenced through its investment in people development through career growth and skills enhancement. Large organizations, with global operations, in verticals that need industry-focused security solutions should consider partnering with Accenture IDC #US
9 Challenges Accenture's investments in its security services are recent, so market awareness of MSS offerings is nascent. Accenture focuses on large enterprises (5,000+ employees) and government entities, which makes its go-to-market model less conducive to small and medium-sized organizations. In addition, the customer-facing portal lacks features such as enhanced analytics and visualization tools. AT&T AT&T is positioned as a Leader in the IDC MarketScape for worldwide managed security services. AT&T offers a breadth of managed and monitoring security services for all types of midsize and enterprise organizations. AT&T is based in Dallas, Texas, and has eight SOCs located across each geographic region United States, EMEA, and Asia/Pacific. All SOCs are staffed with full-time AT&T employees, and they support global customers. Customers also have the option to select a preferred SOC for their company to support regulatory, compliance, and/or privacy requirements. Five AT&T SOCs (three in the United States, one in EMEA, and one in Asia/Pacific) operate 24 x 7 x 365, and three AT&T SOCs (one in EMEA, one in Asia/Pacific, and one Latin America) operate during local business hours in a follow-the-sun model. AT&T offers basic and advanced services such as AT&T Cloud Web Security Services, AT&T Secure Gateway, Enhanced Cyber Security Service, encryption, premise- and network-based firewalls/unified threat management, virtual firewall/unified threat management, DDoS mitigation, and AT&T Threat Manager. AT&T's managed security services rest upon AT&T Threat Intellect, which uses advanced analytics to detect and respond to threats on customers' endpoints, data, and connectivity. With AT&T Threat Manager, AT&T detects threats and updates and customers' security policies, and in some cases automatically. To assist smaller businesses that are affected by DDoS attacks, AT&T launched a new DDoS solution in 2017 that allows them to receive active monitoring of their circuits and IPs without buying full DDoS protection. It is considered an on-demand service because customers can call and initiate the traffic to be sent to a scrubbing center if needed. Strengths AT&T has made security a top focus. It is making investments related to advanced threat detection and analysis, threat intelligence, virtualized security functions, and complementary services. In addition, along with its investments in security, the company has made progress in offering flexible delivery options and pricing options and in making security an easy and cost-effective solution for all types of buyers. AT&T is making investments in network function virtualization (NFV), which will give customers more flexibility on how they deploy security solutions. AT&T has improved its portal capabilities by creating a more comprehensive user experience that allows customers to choose how involved they want to be in threat detection, investigation, and remediation. For the customers who prefer to be hands-on, the portal allows them to look at alerts and dig deeper into them, and it enables customers to work collaboratively with AT&T on remediation, including AT&T-suggested steps. According to customer feedback, AT&T has top-notch local support people who are very knowledgeable in their area of expertise IDC #US
10 Challenges The AT&T platform is newly integrated and the migration of customers was only completed at the end of 1Q17; therefore, time will tell how well received customers have adopted to the new platform. AT&T has been investing heavily in revamping its portal and is constantly making improvements in this area. Customer feedback was that the portal was hard to initially access and much work still needs to be done. BT BT is positioned as a Leader in the IDC MarketScape for worldwide managed security services. BT Group is a United Kingdom headquartered multinational communications services company with global operations. Managed security services are contained in the BT security portfolio. BT has more than 2,500 security practitioners in 180 countries, offering a global reach to a large customer base. Of the company's 15 global SOCs, seven are dedicated SOCs and eight are colocated with other network services, offering around-the-clock coverage with a follow-the-sun model. In addition, BT builds and manages customer-specific SOCs. Support work is handed off between shifts around the globe, and all teams work from a single incident queue, offering continuous monitoring and remediation. A virtual CISO is available to clients as a complementary offering. BT's differentiation comes from the ability to seamlessly integrate a broad security portfolio of managed services with a customer's BT-provided WAN, LAN and compute solutions. This allows BT to be a one-stop shop for its customers. An extensive network gives BT the insight into attacks so that BT can watch, learn, predict, and respond to the latest threats. BT's investments are focused on assisting customers in their digital journeys as they operate in new environments created by cloud, virtualized services, and IoT. BT offers advanced services that help customers transition with confidence and exploit these new technologies. To respond to the digital ecosystem that customers are facing, BT invested in what it calls "Cloud of Clouds." This initiative combines choice and control of services from key cloud service providers privately pre-connected to BT's network, enabling BT to have a global ecosystem by bringing together multinational corporations. Strengths BT's strengths include its focus on big data analytics, threat intelligence, and complementary services. In addition, BT has made strides in addressing enterprise challenges of migrating to the cloud and as a result provides enterprises guidance to migrate to the cloud securely using BT's cloud partnerships and other vendor technologies. BT combines its own innovation with partner technology that may include market leaders or innovating technology from emerging start-ups. BT makes a practice of developing flexible pricing and payment options and for methods of acquiring and retaining talent. BT uses a variety of tools to identify talent and invests time and resources in developing cybersecurity talent an example is the BT Security Academy. Challenges Although BT is well known in the EMEA region, it has less awareness within other geographic markets. MSS offerings are sold predominantly through a global or regional direct salesforce with limited resale by channel partners IDC #US
11 The current portal does not allow role-based access. In the future, BT plans to include this and provide increased visibility for customers to view events and drill down into data. DXC Technology According to IDC analysis and buyer perception, DXC Technology is considered an IDC MarketScape Leader worldwide. In early 2017, CSC and Hewlett Packard Enterprise (HPE) combined to create a service provider named DXC Technology. CSC is a multinational corporation based in the state of Virginia that provides IT services and professional services. Hewlett Packard Enterprise is located in Palo Alto, California. For this research, IDC has analyzed DXC Technology as HPE's capabilities and then combined CSC's capabilities into its future strategy. As of today, both offerings are still separate but will be consolidating their offerings starting in 2Q17. These two companies together bring significant mass and expertise to the MSSP landscape. Both companies bring capabilities to the other to strengthen and fill gaps in the overall offering. For example, HPE has nine SOCs globally, with two in EMEA, four in the Americas, and three in the APJ region. All of the SOCs function on a 24 x 7 x 365 model, with in-region pairing for support of regional clients in a model that ensures client familiarity and failover in case of disaster. The support model is used by some providers where the support for customers includes level one SOC analysts along with higher senior level SOC analysts. They are all grouped around a small number of clients within the same industry and can also be assigned to just one large enterprise client. CSC brings six global SOCs all managed under a 24 x 7 x 365 workflow model. The SOC locations include three in APJ, two in the United Kingdom, and one in the United States many supporting both public sector and commercial clients. HPE describes one of its key differentiators as the combination of its security advisory, threat intelligence, and managed security services capabilities. This is particularly beneficial to organizations that are looking for an end-to-end, advisory-led approach, especially in meeting country-specific data privacy requirements. HPE is focused on helping organizations through security transformation, security maturity improvement, and managed services for those clients that require hybrid or ongoing comanaged services. These capabilities are supported by a full portfolio of MSS services that provide clients device and operational management of their security infrastructure, monitoring, and incident response. HPE believes that the combination in the MSS business of one player that can offer an integrated proposition between advisory, security management, security monitoring, and incident response is offering significant value to its customers from both a detection and a response perspective. CSC differentiates itself in the market by being a vendor independent end-to-end IT services company. CSC has developed cloud partnerships to offer cloud security services. CSC is creating cloud security solutions that can be deployed in virtual, public, and private cloud environments. In addition, CSC has also invested in a similar security monitoring offering to HPE called Integrated Security Operations (ISecOps) that will further integrate with client's workflow and the remediation processes. This new capability provides a set of cybersecurity operational processes and advanced workflows built on top of the ServiceNow platform. As DXC Technology consolidates its offerings and platforms for MSS, IDC expects a blend of detection and response capabilities from HPE and workflow, orchestration, and response capabilities from CSC IDC #US
12 Strengths Both companies have a stable reputation and brand name. The combination of CSC and HPE will result in a span of new capabilities and complement some service gaps lacking in each. HPE's advisory and consulting services and CSC's strong partnerships will also enable DXC Technology to make a leap in creating new cloud security services as well as improve automation and orchestration techniques. Challenges DXC Technology could further enhance its advanced detection and analytic technologies such as behavioral and heuristic-based detection techniques and big data analytics, which we understand has been in progress on the HPE side. IDC anticipates that the new company may run into challenges related to retaining employees and transitioning customers to new processes. Deloitte Deloitte is positioned as a Leader in the IDC MarketScape for worldwide managed security services. Deloitte is a privately held, global services organization, providing audit, consulting, technology, financial advisory, risk advisory, tax and legal, and related services with more than 1,000+ managed security employees worldwide. Deloitte's value proposition is the ability to bring a risk-based approach to solving security issues. Deloitte believes its offerings go beyond basic MSS services because it includes an end-to-end (Advise, Implement & Operate) cyber-risk solution. Deloitte's market strategy is centered on large enterprises (5,000+ employees) in vertical markets such as financial services, the consumer and industrial market, and media and telecommunications. Although considered a global competitor, its strongest geographic market is North America and Europe, especially Spain and the United Kingdom. Deloitte has a comprehensive suite of cyber-risk offerings that integrates strategy and governance. Customer organizations are secured using a three-step approach: secure (e.g., identity and access management), vigilant (e.g., threat intelligence and analytics), and resilient (e.g., cyberincident response). Deloitte has more than 25 cyberintelligence centers globally, and each is considered local to the company's clients with local languages as well as specialists for each industry. The processes and tools used in these centers are all based around the same global platform in which they provide their services from. Deloitte has developed its MSS capabilities both organically and via internal research and development as well as through vendor partnerships. Also, Deloitte has acquired a number of companies. These include Integrity-Paahi Solutions Inc. (IPS), Qubit Consulting, Licetus, AXOA, Urgentis, HCS, LRA Worldwide, and Vigilant. Deloitte recently launched a hosted managed digital identity service (MDIS) that enables clients to manage identity using an "as a service" model. Deloitte is in the process of rolling out a managed SOC in the cloud service with orchestration capabilities. Strengths Deloitte offers a range of managed cyberservices, from basic MSS to some advanced detection capabilities, and tailors its offering from a risk perspective. The company continues to strengthen its offerings with investments in research and development and growth strategies IDC #US
13 Deloitte has created its own Cyber Academy to create more specialized cybersecurity training and is categorized for its excellence, expertise, and innovative ideas. The Academy provides training centers in the country with presence in different organizations and diverse types of personnel. Challenges Deloitte is known for its strong presence in the large enterprise sector but less so for engagements in the midmarket. While the company has enterprise solutions that can work well with midmarket organizations, Deloitte still may be challenged from a combination of two factors in addressing this area: less of a reputation for working with midmarket firms and its perception as a higher-cost provider. However, Deloitte's relationships with regional channel partners can help build up its midmarket presence. HCL Technologies HCL Technologies is positioned as a Major Player in the IDC MarketScape for worldwide managed security services. HCL Technologies is a global service provider headquartered in Noida, India. The company has five SOCs: two in India, one in Europe (regional), one in Asia (regional), and one in the United States. All operate 24 x 7 except the SOC located in the United States. HCL has basic and advanced MSS offerings and will typically provide these services with large IT outsourcing contracts. HCL Technologies, which is part of the HCL Enterprise, encompasses 110,000 employees and is considered one of the fastest-growing outsourcing companies in India. HCL business is split into three service areas: Mode 1 (traditional services such as application services, infrastructure, and engineering services), Mode 2 (experience-centric and outcome-oriented services), and Mode 3 (Evo-System driven services). Mode 2 includes the HCL Cybersecurity & GRC business, which is considered a high-growth business segment for HCL. HCL offers advanced detection and analytics capabilities through its SecIntAI framework, which uses big data and security analytics. Also, by leveraging artificial intelligence-based pattern matching, social media, and dark net analytics, the framework predicts threats that help HCL customers prevent breaches. HCL has developed the DRYiCE automation and orchestration platform, which brings in artificial intelligence. DRYiCE SecInt provides global threat intelligence that delivers early warning and actionable security intelligence tailored specifically to an enterprise, enabling it to protect against threats and vulnerabilities before they impact the organization. Other DRYiCE frameworks include DRYiCE SecAl, which focuses on big data for security analytics, and DRYiCE SecMon, which provides threat detection and security incident response through real-time collection and gathers historical analysis of security events. Strengths HCL provides MSS by leveraging advanced and niche technologies. Along with its technical capabilities and large-scale investments, HCL can provide customized solutions to its customers. Based on customer feedback, from a technology perspective, HCL does try to accommodate any customization needed by a customer even if it was not in the scope of the contract. Another customer noted that HCL does a very good job at maintaining its IT environments, especially its security 2017 IDC #US
14 environment. HCL makes sure that everything is working properly and is good at reporting any incidents or issues within the environment. Challenges HCL offers standalone MSS services only to its existing customers and select F500 clients but has not marketed to a broader market; however, HCL is revisiting this strategy. Most of its MSS deals till date were part of much larger infrastructure engagement. With increasing traction for standalone MSS deals, HCL should aggressively position and market these services actively. HCL does not work with channels, which could hinder its sales opportunity. IDC also believes the company could engage with its customers regarding their road map strategies more frequently. Portal capabilities could be improved by adding visualization tools. IBM IBM is positioned as a Leader in the IDC MarketScape for worldwide managed security services. IBM, a New York based multinational technology and consulting business, began offering MSS in IBM is one of a few study participants whose MSS delivery can be considered truly global, in part because of its ability to integrate MSS and security services worldwide. IBM offers MSS offerings that can be delivered as separate security offerings or part of larger IT engagements. IBM delivers its MSS from eight of its X-Force Command centers: two in the United States (Georgia and Colorado), two in Europe (Poland and Belgium); one in Bangalore, India; one in Heredia, Costa Rica; one on Hortolanda, Brazil; and one in Tokyo, Japan. SOCs provide 24 x 7 live communication support such as chat and phone in English, Spanish, Portuguese, and Japanese. At times, there are capabilities to communicate in French, German, Dutch, and Chinese. IBM's goal is to support its clients in their native languages whenever possible, so the company can provide live, simultaneous translation services for some languages at no additional cost. As of March 2017, IBM also will provide a local in-person delivery to clients in three regions: EU-only delivery out of Wroclaw, Poland; India-domestic delivery out of Bangalore, India; and Japan-domestic delivery out of Tokyo, Japan. IBM can provide custom delivery on a case-by-case basis in other locations around the world. IBM X-Force threat analysis services delivers threat intelligence, which is customizable with daily news and a vulnerability watch-list service. The X-Force Protection Platform (XPS) performs the data collection and aggregation for customers' devices. On-premises appliances stream data to IBM to facilitate threat correlation and analysis. During the past year, IBM has been creating new services, including an incident response and intelligence services team named IRIS. IBM is also making investments in cognitive technology. Watson is expected to enhance IBM's MSS capabilities by enabling faster and quicker decisions to be made in security issues. Large enterprises that are looking for capabilities that go beyond MSS traditional offerings and need assistance with security transformation should consider partnering with a company such as IBM. Strengths IBM offers advanced MSS capabilities such as threat intelligence, cloud security, portal offerings, and complementary services. Along with its strong brand name and reputation in the market, IBM offers a 2017 IDC #US
15 more complete list of services than many MSSPs. In addition, IBM operates on a true global scale and provides a technology road map that can help guide customers through their security journeys. IBM Security Transformation Services has grouped 2017 investments into three categories, all of which apply to MSS: cognitive capabilities powered by Watson to enhance security threat monitoring and improve customer service, cloud services, and offerings centered around specialized skills in testing, incident response, and intelligence. IBM also possesses benefits by proving a global market presence. Because of this, IBM offers a deep insight and visibility into the threat landscape as demonstrated by its X-Force threat intelligence group. Challenges IBM has converted a portion of its MSS platform to use QRadar technology, a process that may pose issues with customers when migrating. An area of opportunity for IBM is to continue increasing its flexibility related to payment and pricing options. NTT Security NTT Security is positioned as a Major Player in the IDC MarketScape for worldwide managed security services. NTT Security, the specialized security company of NTT Group, covers 87 countries and consists of 244 datacenters and 241,000 employees. The company brings together Solutionary and NTT Com Security and further consists of MSSP components that have been acquired by the NTT Group (via NTT Communications, NTTi3, and Dimension Data). Each company delivers specific MSS capabilities in different regions. For example, Solutionary is the distributer of security services in North America while Dimension Data distributes services within the APAC region. NTT Communications and NTT Com Security delivers services in EMEA and Japan. The company's stated mission is to bring cyber-resilience to the global digital economy using a full security life-cycle approach. NTT's MSS capabilities are delivered from three platforms, and the services are currently sold on each platform. The platform used depends on the location of the customer and provider (e.g., NTT Communications or Dimension Data). The goal for NTT Security is to bring these platforms ActiveGuard, WideAngle, and NTT's Global Threat Platform together to provide the operational efficiencies and scalability needed to deliver its MSS solutions. NTT offers modular services that enable customers to choose the specific services that match their requirements rather than imposing a "one size fits all" approach. NTT believes that this approach enables customers to choose different service levels based on different areas of the network to ensure they make the best use of their budget and meet their security and compliance needs. NTT Security operates 10 SOCs and seven research and development centers located in North America, EMEA, and APAC. Many of the SOCs operate with 24 x 7 workflow, but others such as those in the EMEA offer in-region workflow models. Strengths NTT Security's portfolio spans basic MSS to a full life cycle of security services that brings in complementary services. NTT Security is addressing cloud offerings by working with its group companies such as Dimension Data, NTT Communications, and NTT Data to provide embedded cloud offerings into the MSS offerings. The company is collecting data feeds from third-party cloud vendors 2017 IDC #US
16 such as AWS to provide monitoring of services through API. NTT Security continues to enhance its threat intelligence capabilities and vendor partner relationships. According to customer feedback, the portal provides technical information, such as information about the devices being monitored, that is interesting to the security team. In addition, a customer stated that NTT Security offers very good support and service at a reasonable cost, and the quality of service continues to improve. Challenges NTT Security could look at offering advanced services like managed encryption and an endpoint offering. NTT Security is working through platform and portal integration; therefore, IDC expects some challenges to occur when customers are moved to the new platform. SecureWorks SecureWorks is positioned as a Leader in the IDC MarketScape for worldwide managed security services. SecureWorks, which was acquired by Dell in 2011, is one of the few pure-play MSSPs. In 2016, Dell spun off SecureWorks, allowing the company to file an IPO and refocus its security strategy. SecureWorks, based in Atlanta, Georgia, has five SOCs: three in the United States, one in the United Kingdom, and one in APAC. All SOCs work in a virtual SOC model with 24 x 7 coverage. Japan is regionally based, supporting Japanese clients 24 x 7. The SecureWorks Counter Threat Platform leverages both proprietary and third-party technology. The platform utilizes predictive technology that consists of artificial intelligence and machine learning to address threats in an automated rapid response. The Counter Threat Unit (CTU) research team and the Senior Intrusion Analyst (SIA) team use proprietary tools, including a very large database, to monitor the global threat landscape and analyze emerging threats and vulnerabilities. SecureWorks continues to research and provide advanced threat prevention and detection tools such as sandboxing and endpoint threat prevention as well as detection and response tools. SecureWorks' strategy is to use machine learning and behavioral analytics that can decrease the impact on human analysts by analyzing telemetry collected in a fast and automated process, which in turn can provide quicker response time. In 2014, SecureWorks launched Advanced Endpoint Threat Detection (AETD), which is a managed endpoint detection and response (EDR) service. SecureWorks offers AETD Carbon Black, based on Carbon Black's Cb Response, and AETD Red Cloak, based on SecureWorks proprietary technology. AETD Red Cloak advanced analytics technology is also being leveraged for other services to provide more value to clients. Together, the AETD solutions provide enhanced protection and visibility to identify file-less attacks that use little or no malware and often get past antivirus and antimalware products. This year, SecureWorks is launching Advanced Endpoint Threat Prevention (AETP), a managed next-generation antivirus service based on Carbon Black's Cb Defense. AETP complements the visibility provided with AETD and stops even advanced threats via connection and process disruption. SecureWorks also released in 2015 its Advanced Malware Protection and Detection (AMPD) offering, which is a fully managed security service designed to rapidly detect and stop advanced threat actor activity on the network. The service combines SecureWorks' threat intelligence services with next-generation network sandbox technology from Lastline IDC #US
17 Strengths SecureWorks offers threat intelligence and advanced threat detection services that are highly sophisticated. The company provides big data analytics, artificial intelligence, and sandboxing techniques as well as a portfolio of complementary services such as incident response and breach management. The portal offers self-service capabilities and allows customization for specific users. Customer feedback included praise for SecureWorks' portal improvements, for the breadth of reports, and for the flexibility of services. In addition, SecureWorks promotes its capabilities through various marketing promotion tactics to help the buyer understand its solution and offers multiple routes to purchase its services. Challenges SecureWorks is well known in North America, but the company is building out its global delivery of services in other areas such as Europe and APAC. Areas of opportunity for SecureWorks include strengthening its talent acquisition and development program and providing channel support for its partners. Symantec Symantec is positioned as a Major Player in the IDC MarketScape for worldwide managed security services. Symantec is a global security software and services company with more than 13,000 employees that operates in more than 50 countries. Symantec offers security monitoring with services that range from ad hoc to formalized security programs in regulated industries. With the sale of Veritas, Symantec refocused its security business and revamped its cybersecurity services portfolio in late The cybersecurity services portfolio includes in-depth offerings that covers the full life cycle of an attack by providing services before, during, and after a breach. In 2015, Symantec expanded its emergency response and retainer services globally, which engaged more than 120 customers within a year of its launch. Symantec also expanded the depth of the service by deploying new incident response retainer and simulation services. In addition, the company introduced the CyberOne offering, which combines its intelligence, monitoring, and incident response services into a single offering. Symantec has six global SOCs: one in North America, one in the EMEA, and four in APAC. The SOCs operate 24 x 7 and are staffed by more than 800 dedicated cybersecurity professionals. Each SOC includes a cross-functional and delivery service by customer industry and security maturity. The SOCs provide services in 11 different languages, which include English, Japanese, French, Spanish, Mandarin, Indian, Korean, Indonesian, Hindi, Punjabi, and Malay. Each segment has a dedicated analyst team, which includes a principal analyst, a technical analyst, and an account manager. In 2016, Symantec acquired Blue Coat and associated technologies such as Blue Coat Security Intelligence Network (GIN), Blue Coat Security Analytics, and Blue Coat CloudSOC. Integrations with Blue Coat began from day one and, as of today, is now providing deeper visibility into web-based attacks. Symantec has also completed integration with CASB, Security Analytics, and Cloud Proxy (WSS). By adding Blue Coat technologies, customers will benefit by gaining faster detection, response times and deeper visibility into the threat landscape IDC #US
18 Strengths To enhance delivery options, Symantec developed strategic partnerships with companies such as Splunk and LogRhythm to enhance its threat intelligence capabilities. Further, Symantec has improved its advanced threat analytics capabilities as a result of its acquisition with Blue Coat. Blue Coat Security Intelligence Network will provide access to new threat intelligence that is being leveraged by the SOC analysts and its analytics platform. Symantec's advanced portal capabilities allow customers to gain detailed information about an incident, and the portal includes role-based options and customization. Customer feedback stated that the portal was easy to use for gathering log analysis information. Symantec offers enterprise pricing that has given companies the flexibility to be priced on the total number of monitored devices in a customer environment versus meter-based pricing. Challenges Symantec has a very good road map for the future but still has limited device management capabilities. Areas of opportunity for Symantec include offering a stronger talent development program for its employees as well as a flexible onboarding method for its customers. Verizon Verizon is positioned as a Leader in the IDC MarketScape for worldwide managed security services. Verizon is a New York-based telecommunications company that offers a breadth of security services to enterprises across the globe. Verizon has nine SOCs: three in the United States, four in APAC, and two in EMEA. Verizon's SOC workflow is a global 24 x 7, follow-the-sun model. Tier 1 and tier 2 support is delivered from Chennai, India, and tier 3 support is provided by the regional SOC teams in Australia, Germany, and the United States. In each region, Verizon also offers a local SOC to meet inregion data sovereignty requirements. Canberra SOC #1 serves Australian government agencies with SOC, Luxembourg SOC and security datacenter serve public sector and industry verticals that require European Union data sovereignty, and a U.S. federal SOC is 24 x 7 in-region and meets specific federal requirements for the United States. In 2016, Verizon launched an integrated MSS and analytics platform that consists of Splunk, Verizon analytics (SEAM), and a proprietary big data analytics platform. Verizon's threat analytics platform ingests billions of events each month, including both cyberthreat and device health logs, then analyzes those events and creates actionable incidents. This level of threat analytics automation enables both Verizon's MSS customers and the MSS SOCs to maximize personnel efficiencies for incident investigation and response. In 2016, Verizon launched a cyber-risk assessment and expanded its global incident response retainer program into its MSS portfolio. Verizon has invested in developing its own threat intelligence from a number of sources that include the global IP backbone, partnerships in development of the Data Breach Intelligence Report, internal threat intelligence development teams such as the Threat Library and Verizon Threat Research Advisory Center (VTRACK) team, and the ICSA Labs. Strengths In 2016, Verizon launched data-volume-based pricing for the MSS analytics service and plans to extend that pricing model where it makes sense in the portfolio. Verizon continues to consider alternative pricing models that can offer more flexibility to customers IDC #US
19 Verizon continues to develop and enhance its advanced detection and analytics platform. Today the analytics platform is designed to handle multiple engines, allowing Verizon to continue to build new technologies. In addition, Verizon has put effort into its incident response service and capabilities that can assist customers with investigations or responses to breaches. Verizon's portal has been updated with capabilities that allow customers to view security incident status updates and netflow data, with enhanced user interface functions and with self-service features. According to customer feedback, Verizon is always improving its back-end systems and the portal. Challenges Although the portal is being enhanced, customer feedback stated that it is difficult to navigate and is not intuitive in identifying things like specific tickets. Customers are still being integrated into the new portal, so this could be causing some challenges. Verizon could also look at developing more methods to attract, acquire, and train talent. Wipro Wipro is positioned as a Major Player in the IDC MarketScape for worldwide managed security services. Wipro provides a span of MSS and consulting offerings to large enterprises across the globe. Offerings include advanced services such as managed SIEM, managed encryption, penetration testing, and threat intelligence as well as advanced detection and analytic techniques. Wipro is headquartered in Bangalore, India, and MSS is delivered from 12 global SOCs: six in India, three in the United States, one in Canada, and two in Europe. Wipro has 10 security platforms that support a vendor-agnostic approach to services. Wipro has strategic partnerships with prominent public cloud providers including AWS, Microsoft Azure, and Google. Wipro has been an AWS alliance partner for the past seven years, and Wipro has been an AWS Premier Consulting Partner in the AWS Partner Network (APN). Wipro has been part of the Google Cloud Platform Partner Program since Wipro launched its partnership with Microsoft Azure in Wipro has developed many of its solutions organically as well as through acquisition. Wipro uses inhouse tools and scripts to help automate and mechanize support tasks, service reporting aspects, scheduled compliance audits, patches and updates, and more. Wipro has made strategic investments to improve its intelligence, automation, and analytics, and these include partnerships with age, Vectra, INTsights, and Demisto. Strengths Wipro offers customized solutions to its customers that can be used on top of its standard MSS offerings. Wipro has solid partnerships with public cloud providers, and this can help strengthen its portfolio. Wipro supports multiple pricing and payment options, enabling customers to pick and choose what works best for them. In addition, Wipro invests in its people by offering a number of cybersecurity trainings per year in addition to regular quarterly trainings IDC #US
20 Challenges The onboarding process does not allow for self-service capabilities. Portal capabilities could be improved with enhanced analysis reporting and real-time updates. Wipro does not offer any channel support to its partners. Vendors to Watch The following vendors are notable players in the worldwide MSS market, but some have more presence in specific regions of the world such as North America, APAC, or EMEA. In addition, they may have not reached the revenue requirements for this particular IDC MarketScape. Because of the vendor inclusion criteria, they were not included in the IDC MarketScape: Airbus Atos BAE Cisco CenturyLink EY Fujitsu Herjavec Infosys Kudelski Security Nuspire Optiv Orange Proficio PwC Telefonica T-Systems Trustwave Unisys APPENDIX The security landscape is complex and challenging an understatement, given the number of moving parts that are involved in defending an enterprise from cyberattacks. IDC recommends that companies undertake a holistic, enterprisewide security posture that is proactive and predictive. It's a daunting effort, however, to sustain the necessary level of threat intelligence and advanced analytics capabilities along with the skills to interpret and act on findings. In-house 24 x 7 security solutions are expensive, and security talent is scarce. As a result, organizations debate "build versus buy," and many are turning to MSSPs. A security services provider can allow organizations to meet several objectives: Transfer the cost of ownership, thereby reducing capex and transferring the budget to opex 2017 IDC #US
21 Create a predictable expense with a regular cadence in the budget cycle Enable a dedicated application of technology, processes, and people to the rapidly changing threat landscape Implement best practices that are evolving with a rapidly changing threat landscape Benefit from "strength in numbers" from an intelligence perspective The rise in frequency and complexity of attacks and the need for increasingly sophisticated security solutions have led to a new echelon of MSS that IDC is calling MSS 2.0. An MSSP 2.0 is further "up the stack" than MSSPs that are offering MSS 1.0 services, which include the following: Log monitoring Basic managed and monitored services (firewalls and intrusion detection services/intrusion prevention services) Unified threat management Identity and access management Vulnerability scanning MSSPs 1.0 may also offer advanced services such as DDoS, managed SIEM, and managed SOC. MSSPs 2.0 deliver basic and advanced MSS plus professional/complementary services (for more details, see the Market Definition section). They are also investing in mobile/iot, cloud, threat intelligence/big data analytics, incident response/forensics, and advanced detection techniques. Cloud, mobile/iot, and big data are three of four pillars that IDC has identified as top trends. The fourth pillar, social media, doesn't factor into this IDC MarketScape; however, advanced MSSP capabilities can help detect, analyze, and protect against security threats in the social media arena. Security, in general, is complicated by the shortage of security talent. Innovative MSSPs focus on short- and long-term employee acquisition, training, and retention using both traditional and progressive practices. Some of their tactics are apprentice programs, scholarships, in-house universities, university partnerships, and flexible career paths. Further, regulatory requirements continue to evolve, and MSSPs can provide the expertise and evidence needed for oversight and compliance based on industry-standard certifications. Businesses increasingly are turning to MSSPs to monitor and manage some or all of their security needs. Based on IDC market sizing, the MSS market is expected to continue to see growth in double digits in coming years. Reading an IDC MarketScape Graph For the purposes of this analysis, IDC divided potential key measures for success into two primary categories: capabilities and strategies. Positioning on the y-axis reflects the vendor's current capabilities and menu of services and how well aligned the vendor is to customer needs. The capabilities category focuses on the capabilities of the company and product today, here and now. Under this category, IDC analysts will look at how well a vendor is building/delivering capabilities that enable it to execute its chosen strategy in the market. Positioning on the x-axis, or strategies axis, indicates how well the vendor's future strategy aligns with what customers will require in three to five years. The strategies category focuses on high-level 2017 IDC #US
22 decisions and underlying assumptions about offerings, customer segments, and business and go-tomarket plans for the next three to five years. The size of the individual vendor markers in the IDC MarketScape represents the market share of each individual vendor within the specific market segment being assessed. IDC MarketScape Methodology IDC MarketScape criteria selection, weightings, and vendor scores represent well-researched IDC judgment about the market and specific vendors. IDC analysts tailor the range of standard characteristics by which vendors are measured through structured discussions, surveys, and interviews with market leaders, participants, and end users. Market weightings are based on user interviews, buyer surveys, and the input of a review board of IDC experts in each market. IDC analysts base individual vendor scores, and ultimately vendor positions on the IDC MarketScape, on detailed surveys and interviews with the vendors, publicly available information, and end-user experiences in an effort to provide an accurate and consistent assessment of each vendor's characteristics, behavior, and capability. Market Definition Managed Security Services For the purposes of this research, IDC defines managed security services as "the around-the-clock remote management or monitoring of IT security functions delivered via remote security operations centers (SOCs), not through personnel onsite." Exceptions and Inclusions Managed security services can include complementary consulting and advisory activities that are typically defined under professional security services. The study did seek to understand whether the MSSPs offer complementary services as IDC believes these services are critical to the evolution and maturity of MSS. The MSSPs in this study do provide complementary services; although, there is no standard approach for how they are offered. Commonly, an initial assessment is bundled with the onboarding fees, and some may bundle other services. Most, however, offer complementary services as optional add-ons and may charge separately for them. Complementary services surveyed in the study include breach management, incident response, forensics, compliance services, and assessment of architecture and design. Not all MSSPs provide all of these services. Some MSSPs provide all of the listed complementary services and others such as managed security testing, application security testing, advisory services, integration services, and data privacy assessment. Terminology Managed security and information event management (managed SIEM). This managed onpremises event collector transmits the raw log data to an MSSP's SOC for analysis, reporting, and archiving. This is an advanced, niche capability that is offered currently by half of the participants in this study. Managed SOC. A security operations center includes the people, processes, and technologies involved in detecting, containing, and remediating security threats. Some MSSPs take over the operation of SOCs that their customers have built and no longer want to manage. This is an advanced, niche offering that is offered currently by a majority of the participants in this study IDC #US
23 Security operations center types: In-region. A standalone SOC in a country or region Follow the sun. A type of global workflow in which tasks are passed around daily at the end of work shifts among sites that may be in different time zones Global. Workflow that occurs in one global location in a 24 x 7 multishift arrangement Strategies and Capabilities Criteria This section includes an introduction of market-specific weighting definitions and weighting values (see Tables 1 and 2). TABLE 1 Key Strategy Measures for Success: Worldwide Managed Security Services Strategy Criteria Definition Weight (%) Functionality or offering strategy Excellence is marked by plans to offer a full spectrum of MSS services with advanced MSS functionality including, for example, threat intelligence. Excellence is marked by plans to offer advanced MSS functionality including, for example, big data and analytics and behavioral and heuristic-based detection methods. The provider has plans to offer customers and partners insight to its road map. 3.0 Delivery model Excellence is marked by plans to meet customers' shifting preference for adoption and consumption. Excellence is marked by future plans for offering delivery models that provide scalability. Excellence is marked by plans to meet customers' shifting preference for adoption and consumption. Cost management strategy The provider plans to employ tools to ensure a competitive cost that supports the requirements of customers in the near future. Service calls for plans to which the provider employs tools such as case studies to ensure pricing will help clients justify expenditures for MSS. Portfolio strategy Excellence is marked by plans to enhance the portfolio with complementary services such as breach management, which will add value for the customer in the future. The provider plans to provide services that are enhanced by utilizing a mix of intellectual property by the vendor and its partners' technology The provider plans to provide a mix of the vendor and partner and integration and support to deliver maximum customer benefit. 3.0 Excellence is marked by future plans to provide flexibility of services through deployment options that meet the customers' preferences IDC #US
24 TABLE 1 Key Strategy Measures for Success: Worldwide Managed Security Services Strategy Criteria Definition Weight (%) Pricing model The provider plans to offer flexible pricing models to support what customers want in the future. Excellence is marked by plans to offer flexible payment options to the customer. Sales and distribution strategy Excellence is demonstrated by plans to offer multiple routes of purchase globally. Excellence is demonstrated by plans to offer methods such as dedicated channel representatives to expand channel support. 3.5 Marketing strategy The provider plans to have marketing promotion tactics such as webinars to help market its capabilities in the future. A well-articulated plan demonstrates how capabilities will be marketed in the future, especially in customer acquisition, upselling, and retaining Customer service strategy Provider demonstrates continuous focus on ways to improve portal capabilities to improve customer satisfaction. Customer service excellence is marked by having plans to provide consistent customer engagement. 3.5 Provider plans to offer exceptional customer service delivery options by offering methods such as live 24 x 7 support. 3.0 MSSP provides methods such as customer satisfaction surveys to help improve customer satisfaction ratings. 3.5 Growth strategy Innovation strategy Employee management strategy Firms poised for growth in the near term address macrotechnology trends such as IoT, mobility, cloud evolution, and threat intelligence. Firms have plans to expand R&D activities and innovation initiatives such as tech challenges for purposes of refreshing offerings and adding value for customers. Provider has clearly articulated plans for attracting talent such as driving the development of curriculum and programs to increase the security talent. Provider has clearly articulated plans such as mentoring for retaining and cultivating talent. 3.5 The provider has clearly articulated plans for offering various career paths such as a predefined. Total Source: IDC, IDC #US
25 TABLE 2 Key Capability Measures for Success: Worldwide Managed Security Services Criteria Definition Weight (%) Functionality or offering capabilities Excellence is marked by the ability to offer a full spectrum of MSS services with advanced MSS functionality including, for example, threat intelligence. 3.5 Excellence is marked by the ability to offer advanced MSS functionality including, for example, big data and analytics and behavioral and heuristicbased detection methods. The provider offers customers and partners insight to the road map. 3.0 Delivery capabilities The provider's current delivery model meets end-user preference for adoption and consumption. 3.0 Excellence is marked by offering delivery models today to meet the demand for scalability. 3.5 Excellence is marked by meeting customers' shifting preference for adoption and consumption. Cost management capabilities Pricing must be competitive with market pricing and modular and scalable to meet customer requirements. Various methods such as case studies used to create competitive pricing is meeting customer pricing requirements for today. 3.0 Portfolio capabilities MSS portfolio is enhanced with complementary services such as breach management, which helps add value. The provider offers services that are enhanced by utilizing intellectual property by the provider and the partners' technology. 3.0 The provider has partner integration and support to deliver maximum customer benefit. 3.0 The firm provides flexibility of services through deployment options that meet the customers' preferences. 3.0 Price model capabilities The provider offers flexible pricing models that customers want today. 3.5 The provider offers currently flexible payment options to the customer. 3.5 Sales and distribution capabilities The provider demonstrates the ability to offer multiple routes of purchase globally. 3.5 Provider provides channel support methods such as dedicated channel representatives to expand marketing presence IDC #US
26 TABLE 2 Key Capability Measures for Success: Worldwide Managed Security Services Criteria Definition Weight (%) Marketing capabilities The provider has marketing promotion tactics such as webinars to help market its capabilities. 3.0 Customer service offering Customer service excellence is marked by demonstrating robust portal capabilities. Customer service excellence is marked by providing consistent customer engagement. 3.5 Provider offers exceptional customer service delivery options by offering methods such as live 24 x 7 support. 3.0 MSSP plans to provide methods such as customer satisfaction surveys to help improve customer satisfaction ratings. 3.5 Growth capabilities Firms poised for growth are addressing macrotechnology trends such as IoT, mobility, cloud evolution, and threat intelligence. 3.5 Provider demonstrates the ability to retain customers. Provider demonstrates the ability to provide customer and revenue growth. Innovation Firms are engaged in R&D activities and innovation initiatives such as tech challenges purposes of refreshing offerings and adding value for customers. 3.5 Employee management capabilities The MSSP demonstrates a method of attracting talent such as driving the development of curriculum and programs to increase the security talent. 3.0 The provider demonstrates methods such as mentoring for retaining and cultivating talent. 3.0 The provider demonstrates methods for a career path. 3.0 Provider demonstrates the ability to retain employees. Total Source: IDC, IDC #US
27 LEARN MORE Related Research IDC MarketScape: Western Europe Managed Security Services 2017 Vendor Assessment (forthcoming) Worldwide DDoS Prevention Products and Services Forecast, (IDC #US , May 2017) IDC MarketScape: U.S. Emerging Managed Security Services 2016 Vendor Assessment (IDC #US , August 2016) Synopsis This IDC study presents a vendor assessment of providers offering managed security services (MSS) through the IDC MarketScape model. The assessment reviews both quantitative and qualitative characteristics that define current market demands and expected buyer needs for MSS. The evaluation is based on a comprehensive and rigorous framework that assesses how each vendor stacks up to one another, and the framework highlights the key factors that are expected to be the most significant for achieving success in the MSS market over the short term and the long term. "The security landscape is changing rapidly, and organizations continue to struggle to maintain their own in-house security solutions and staff. As a result, organizations are turning to managed security service providers (MSSPs) to deliver a wide span of security capabilities and consulting services, which include predicative threat intelligence and advanced detection and analysis expertise that are necessary to overcome the security challenges happening today as well as prepare organizations against future attacks. The MSSP market is highly competitive, and many MSSPs have a breadth of security services in their MSS portfolio. The differentiation among these MSSPs will be tied around their flexibility in delivering security services and advanced MSS capabilities and how these MSSPs can continue to assist organizations with their security needs today and in the future." Martha Vazquez, senior research analyst, Infrastructure Services 2017 IDC #US
28 About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. Global Headquarters 5 Speen Street Framingham, MA USA idc-community.com Copyright and Trademark Notice This IDC research document was published as part of an IDC continuous intelligence service, providing written research, analyst interactions, telebriefings, and conferences. Visit to learn more about IDC subscription and consulting services. To view a list of IDC offices worldwide, visit Please contact the IDC Hotline at , ext (or ) or sales@idc.com for information on applying the price of this document toward the purchase of an IDC service or for information on additional copies or web rights. IDC and IDC MarketScape are trademarks of International Data Group, Inc. Copyright 2017 IDC. Reproduction is forbidden unless authorized. All rights reserved.
IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS IDC MARKETSCAPE EXCERPT FEATURES: DXC IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS IDC MARKETSCAPE EXCERPT FEATURES: DXC IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
Making hybrid IT simple with Capgemini and Microsoft Azure Stack
 Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SOLUTION BRIEF RSA ARCHER IT & SECURITY RISK MANAGEMENT
 RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
White Paper. How to Write an MSSP RFP
 White Paper How to Write an MSSP RFP https://www.solutionary.com (866) 333-2133 Contents 3 Introduction 3 Why a Managed Security Services Provider? 5 Major Items to Consider Before Writing an RFP 5 Current
White Paper How to Write an MSSP RFP https://www.solutionary.com (866) 333-2133 Contents 3 Introduction 3 Why a Managed Security Services Provider? 5 Major Items to Consider Before Writing an RFP 5 Current
IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment Christina Richmond THIS IDC MARKETSCAPE EXCERPT FEATURES: AT&T IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2014 Vendor Assessment Christina Richmond THIS IDC MARKETSCAPE EXCERPT FEATURES: AT&T IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
How to Write an MSSP RFP. White Paper
 How to Write an MSSP RFP White Paper Tables of Contents Introduction 3 Benefits Major Items of On-Premise to Consider SIEM Before Solutions Security Writing an RFP and Privacy 45 Benefits Building an of
How to Write an MSSP RFP White Paper Tables of Contents Introduction 3 Benefits Major Items of On-Premise to Consider SIEM Before Solutions Security Writing an RFP and Privacy 45 Benefits Building an of
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATACENTER SERVICES DATACENTER
 SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
Traditional Security Solutions Have Reached Their Limit
 Traditional Security Solutions Have Reached Their Limit CHALLENGE #1 They are reactive They force you to deal only with symptoms, rather than root causes. CHALLENGE #2 256 DAYS TO IDENTIFY A BREACH TRADITIONAL
Traditional Security Solutions Have Reached Their Limit CHALLENGE #1 They are reactive They force you to deal only with symptoms, rather than root causes. CHALLENGE #2 256 DAYS TO IDENTIFY A BREACH TRADITIONAL
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM
 SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
SOLUTION BRIEF RSA NETWITNESS SUITE 3X THE IMPACT WITH YOUR EXISTING SECURITY TEAM OVERVIEW The Verizon 2016 Data Breach Investigations Report highlights that attackers are regularly outpacing the defenders.
Run the business. Not the risks.
 Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Security in India: Enabling a New Connected Era
 White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
White Paper Security in India: Enabling a New Connected Era India s economy is growing rapidly, and the country is expanding its network infrastructure to support digitization. India s leapfrogging mobile
Cybersecurity. Securely enabling transformation and change
 Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
RSA Solution Brief. Managing Risk Within Advanced Security Operations. RSA Solution Brief
 RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Managed Endpoint Defense
 DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
CYBER RESILIENCE & INCIDENT RESPONSE
 CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
CYBER RESILIENCE & INCIDENT RESPONSE www.nccgroup.trust Introduction The threat landscape has changed dramatically over the last decade. Once the biggest threats came from opportunist attacks and preventable
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Conquer New Digital Frontiers with leading Public Cloud Platforms.
 Singtel Business Product Factsheet Brochure Managed Defense Public Cloud Services Conquer New Digital Frontiers with leading Public Cloud Platforms. Singtel Managed Public Cloud supports enterprises in
Singtel Business Product Factsheet Brochure Managed Defense Public Cloud Services Conquer New Digital Frontiers with leading Public Cloud Platforms. Singtel Managed Public Cloud supports enterprises in
Predictive Insight, Automation and Expertise Drive Added Value for Managed Services
 Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Symantec Data Center Transformation
 Symantec Data Center Transformation A holistic framework for IT evolution As enterprises become increasingly dependent on information technology, the complexity, cost, and performance of IT environments
Symantec Data Center Transformation A holistic framework for IT evolution As enterprises become increasingly dependent on information technology, the complexity, cost, and performance of IT environments
Are we breached? Deloitte's Cyber Threat Hunting
 Are we breached? Deloitte's Cyber Threat Hunting Brochure / report title goes here Section title goes here Have we been breached? Are we exposed? How do we proactively detect an attack and minimize the
Are we breached? Deloitte's Cyber Threat Hunting Brochure / report title goes here Section title goes here Have we been breached? Are we exposed? How do we proactively detect an attack and minimize the
Cyber Incident Response. Prepare for the inevitable. Respond to evolving threats. Recover rapidly. Cyber Incident Response
 Cyber Incident Response Prepare for the inevitable. Respond to evolving threats. Recover rapidly. Cyber Incident Response 1 2 Today, no Canadian business is immune from a potential attack. It s no longer
Cyber Incident Response Prepare for the inevitable. Respond to evolving threats. Recover rapidly. Cyber Incident Response 1 2 Today, no Canadian business is immune from a potential attack. It s no longer
LTI Security Services. Intelligent & integrated Approach to Cyber & Digital Security
 LTI Security Intelligent & integrated Approach to Cyber & Digital Security Overview As businesses are expanding globally into new territories, propelled and steered by digital disruption and technological
LTI Security Intelligent & integrated Approach to Cyber & Digital Security Overview As businesses are expanding globally into new territories, propelled and steered by digital disruption and technological
Incident Response Services to Help You Prepare for and Quickly Respond to Security Incidents
 Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Evolution For Enterprises In A Cloud World
 Evolution For Enterprises In A Cloud World Foreword Cloud is no longer an unseen, futuristic technology that proves unattainable for enterprises. Rather, it s become the norm; a necessity for realizing
Evolution For Enterprises In A Cloud World Foreword Cloud is no longer an unseen, futuristic technology that proves unattainable for enterprises. Rather, it s become the norm; a necessity for realizing
RSA NetWitness Suite Respond in Minutes, Not Months
 RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment Ali Zaidi Gard Little THIS IDC MARKETSCAPE EXCERPT FEATURES: HCL IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2014 Vendor Assessment Ali Zaidi Gard Little THIS IDC MARKETSCAPE EXCERPT FEATURES: HCL IDC MARKETSCAPE
OVERVIEW BROCHURE GRC. When you have to be right
 OVERVIEW BROCHURE GRC When you have to be right WoltersKluwerFS.com In response to today s demanding economic and regulatory climate, many financial services firms are transforming operations to enhance
OVERVIEW BROCHURE GRC When you have to be right WoltersKluwerFS.com In response to today s demanding economic and regulatory climate, many financial services firms are transforming operations to enhance
NEXT GENERATION SECURITY OPERATIONS CENTER
 DTS SOLUTION NEXT GENERATION SECURITY OPERATIONS CENTER SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 - SUCCESS FACTORS SOC 2.0 - FUNCTIONAL COMPONENTS DTS SOLUTION SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 Protecting
DTS SOLUTION NEXT GENERATION SECURITY OPERATIONS CENTER SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 - SUCCESS FACTORS SOC 2.0 - FUNCTIONAL COMPONENTS DTS SOLUTION SOC 2.0 - ENHANCED SECURITY O&M SOC 2.0 Protecting
IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment Courtney Munroe THIS IDC MARKETSCAPE EXCERPT FEATURES NTT COMMUNICATIONS IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Service Providers 2018 Vendor Assessment Courtney Munroe THIS IDC MARKETSCAPE EXCERPT FEATURES NTT COMMUNICATIONS IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
Drive digital transformation with an enterprise-grade Managed Private Cloud
 Singtel Business Product Factsheet Brochure Managed Private Defense Cloud Services Drive digital transformation with an enterprise-grade Managed Private Cloud Singtel Managed Private Cloud enables enterprises
Singtel Business Product Factsheet Brochure Managed Private Defense Cloud Services Drive digital transformation with an enterprise-grade Managed Private Cloud Singtel Managed Private Cloud enables enterprises
I D C T E C H N O L O G Y S P O T L I G H T
 I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
CenturyLink for Microsoft
 Strategic Partner Alliances CenturyLink for Microsoft EMPOWER REACH AGILITY 2017 CenturyLink. All Rights Reserved. The CenturyLink mark, pathways logo and certain CenturyLink product names are the property
Strategic Partner Alliances CenturyLink for Microsoft EMPOWER REACH AGILITY 2017 CenturyLink. All Rights Reserved. The CenturyLink mark, pathways logo and certain CenturyLink product names are the property
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
Government IT Modernization and the Adoption of Hybrid Cloud
 Government IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Federal and National Governments Are at an Inflection Point Federal and national governments
Government IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Federal and National Governments Are at an Inflection Point Federal and national governments
PREPARE FOR TAKE OFF. Accelerate your organisation s journey to the Cloud.
 PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP)
 SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP) Adaptive Cybersecurity at the Speed of Your Business Attackers Evolve. Risk is in Constant Fluctuation. Security is a Never-ending Cycle.
SOLUTION BRIEF esentire Risk Advisory and Managed Prevention (RAMP) Adaptive Cybersecurity at the Speed of Your Business Attackers Evolve. Risk is in Constant Fluctuation. Security is a Never-ending Cycle.
IT Consulting and Implementation Services
 PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS
 Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
THALES DATA THREAT REPORT
 2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security INDIA EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Rising risks for sensitive data in India In India, as in the rest of the
2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security INDIA EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Rising risks for sensitive data in India In India, as in the rest of the
The Emerging Role of a CDN in Facilitating Secure Cloud Deployments
 White Paper The Emerging Role of a CDN in Facilitating Secure Cloud Deployments Sponsored by: Fastly Robert Ayoub August 2017 IDC OPINION The ongoing adoption of cloud services and the desire for anytime,
White Paper The Emerging Role of a CDN in Facilitating Secure Cloud Deployments Sponsored by: Fastly Robert Ayoub August 2017 IDC OPINION The ongoing adoption of cloud services and the desire for anytime,
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS. Security Without Compromise
 DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
DEFINING SECURITY FOR TODAY S CLOUD ENVIRONMENTS Security Without Compromise CONTENTS INTRODUCTION 1 SECTION 1: STRETCHING BEYOND STATIC SECURITY 2 SECTION 2: NEW DEFENSES FOR CLOUD ENVIRONMENTS 5 SECTION
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services
 MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
SIEM: Five Requirements that Solve the Bigger Business Issues
 SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
Incident Response Services
 Services Enhanced with Supervised Machine Learning and Human Intelligence Empowering clients to stay one step ahead of the adversary. Secureworks helps clients enable intelligent actions to outsmart and
Services Enhanced with Supervised Machine Learning and Human Intelligence Empowering clients to stay one step ahead of the adversary. Secureworks helps clients enable intelligent actions to outsmart and
Analytics Driven, Simple, Accurate and Actionable Cyber Security Solution CYBER ANALYTICS
 Analytics Driven, Simple, Accurate and Actionable Cyber Security Solution CYBER ANALYTICS Overview Cyberattacks are increasingly getting more frequent, more sophisticated and more widespread than ever
Analytics Driven, Simple, Accurate and Actionable Cyber Security Solution CYBER ANALYTICS Overview Cyberattacks are increasingly getting more frequent, more sophisticated and more widespread than ever
THE ACCENTURE CYBER DEFENSE SOLUTION
 THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
THE ACCENTURE CYBER DEFENSE SOLUTION A MANAGED SERVICE FOR CYBER DEFENSE FROM ACCENTURE AND SPLUNK. YOUR CURRENT APPROACHES TO CYBER DEFENSE COULD BE PUTTING YOU AT RISK Cyber-attacks are increasingly
Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges
 Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges An IDC InfoBrief, Sponsored by Cisco March 2018 EXECUTIVE SUMMARY Cloud is a key enabler of
Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges An IDC InfoBrief, Sponsored by Cisco March 2018 EXECUTIVE SUMMARY Cloud is a key enabler of
Services solutions for Managed Service Providers (MSPs)
 McAfee Advanced Threat Defense Services solutions for Managed Service Providers (MSPs) Differentiate your services and protect customers against zero-day attacks with the industry s most comprehensive
McAfee Advanced Threat Defense Services solutions for Managed Service Providers (MSPs) Differentiate your services and protect customers against zero-day attacks with the industry s most comprehensive
DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI
 DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI EXECUTIVE SUMMARY The shortage of cybersecurity skills Organizations continue to face a shortage of IT skill
DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI EXECUTIVE SUMMARY The shortage of cybersecurity skills Organizations continue to face a shortage of IT skill
Protecting organisations from the ever evolving Cyber Threat
 Protecting organisations from the ever evolving Cyber Threat Who we are .At a glance 16+ Up to 190B 2B+ Dell SecureWorks is one of the most promising MSSPs in the GCC region MSS Market Report on GCC, Frost
Protecting organisations from the ever evolving Cyber Threat Who we are .At a glance 16+ Up to 190B 2B+ Dell SecureWorks is one of the most promising MSSPs in the GCC region MSS Market Report on GCC, Frost
THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM
 THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM Modern threats demand analytics-driven security and continuous monitoring Legacy SIEMs are Stuck in the Past Finding a mechanism to collect, store
THE SIX ESSENTIAL CAPABILITIES OF AN ANALYTICS-DRIVEN SIEM Modern threats demand analytics-driven security and continuous monitoring Legacy SIEMs are Stuck in the Past Finding a mechanism to collect, store
Background FAST FACTS
 Background Terra Verde was founded in 2008 by cybersecurity, risk and compliance executives. The founders believed that the market needed a company that was focused on using security, risk and compliance
Background Terra Verde was founded in 2008 by cybersecurity, risk and compliance executives. The founders believed that the market needed a company that was focused on using security, risk and compliance
PONEMON INSTITUTE RESEARCH REPORT 2018 STUDY ON GLOBAL MEGATRENDS IN CYBERSECURITY
 PONEMON INSTITUTE RESEARCH REPORT 2018 STUDY ON GLOBAL MEGATRENDS IN CYBERSECURITY Benchmark research sponsored by Raytheon. Independently conducted by Ponemon Institute LLC. February 2018 2018 Study on
PONEMON INSTITUTE RESEARCH REPORT 2018 STUDY ON GLOBAL MEGATRENDS IN CYBERSECURITY Benchmark research sponsored by Raytheon. Independently conducted by Ponemon Institute LLC. February 2018 2018 Study on
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Symantec Security Monitoring Services
 24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
New Zealand Government IBM Infrastructure as a Service
 New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats.
 IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
INTELLIGENCE DRIVEN GRC FOR SECURITY
 INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
Staffing Services UnderDefense your source of experienced professionals to solve security staffing challenges today
 Security Staffing Services UnderDefense your source of experienced professionals to solve security staffing challenges today Staff Augmentation, Executive Staffing, Flex Staffing Achieving our main goal
Security Staffing Services UnderDefense your source of experienced professionals to solve security staffing challenges today Staff Augmentation, Executive Staffing, Flex Staffing Achieving our main goal
RSA ADVANCED SOC SERVICES
 RSA ADVANCED SOC SERVICES Consulting services to improve threat detection and response EXECUTIVE SUMMARY A holistic approach to enhanced cybersecurity operations This service is for organizations needing
RSA ADVANCED SOC SERVICES Consulting services to improve threat detection and response EXECUTIVE SUMMARY A holistic approach to enhanced cybersecurity operations This service is for organizations needing
Choosing the Right Cloud. ebook
 Choosing the Right Cloud ebook Contents Choosing the Right Cloud...3 The Cloud Explained: Public Cloud...4 The Cloud Explained: Private Cloud...5 Assessing Workload Characteristics...6 Right Application.
Choosing the Right Cloud ebook Contents Choosing the Right Cloud...3 The Cloud Explained: Public Cloud...4 The Cloud Explained: Private Cloud...5 Assessing Workload Characteristics...6 Right Application.
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
to Enhance Your Cyber Security Needs
 Our Service to Enhance Your Cyber Security Needs Since the business critical systems by its nature are ON all of the time and the increasingly connected world makes you open your organization to everything
Our Service to Enhance Your Cyber Security Needs Since the business critical systems by its nature are ON all of the time and the increasingly connected world makes you open your organization to everything
Sales Presentation Case 2018 Dell EMC
 Sales Presentation Case 2018 Dell EMC Introduction: As a member of the Dell Technologies unique family of businesses, Dell EMC serves a key role in providing the essential infrastructure for organizations
Sales Presentation Case 2018 Dell EMC Introduction: As a member of the Dell Technologies unique family of businesses, Dell EMC serves a key role in providing the essential infrastructure for organizations
BUILDING AND MAINTAINING SOC
 BUILDING AND MAINTAINING SOC Digit Oktavianto KOMINFO 7 December 2016 digit dot oktavianto at gmail dot com 1 Digit Oktavianto Profile in 1 Page Currently working as a Security Architect Professional Certifications:
BUILDING AND MAINTAINING SOC Digit Oktavianto KOMINFO 7 December 2016 digit dot oktavianto at gmail dot com 1 Digit Oktavianto Profile in 1 Page Currently working as a Security Architect Professional Certifications:
Professional Services for Cloud Management Solutions
 Professional Services for Cloud Management Solutions Accelerating Your Cloud Management Capabilities CEOs need people both internal staff and thirdparty providers who can help them think through their
Professional Services for Cloud Management Solutions Accelerating Your Cloud Management Capabilities CEOs need people both internal staff and thirdparty providers who can help them think through their
Mapping Your Requirements to the NIST Cybersecurity Framework. Industry Perspective
 Mapping Your Requirements to the NIST Cybersecurity Framework Industry Perspective 1 Quest has the solutions and services to help your organization identify, protect, detect, respond and recover, better
Mapping Your Requirements to the NIST Cybersecurity Framework Industry Perspective 1 Quest has the solutions and services to help your organization identify, protect, detect, respond and recover, better
Hybrid IT for SMBs. HPE addressing SMB and channel partner Hybrid IT demands ANALYST ANURAG AGRAWAL REPORT : HPE. October 2018
 V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
Supporting the Cloud Transformation of Agencies across the Public Sector
 SOLUTION SERVICES Supporting the Cloud Transformation of Agencies across the Public Sector BRIEF Digital transformation, aging IT infrastructure, the Modernizing Government Technology (MGT) Act, the Datacenter
SOLUTION SERVICES Supporting the Cloud Transformation of Agencies across the Public Sector BRIEF Digital transformation, aging IT infrastructure, the Modernizing Government Technology (MGT) Act, the Datacenter
IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment Robert Palmer Allison Correia THIS IDC MARKETSCAPE EXCERPT FEATURES: HP IDC MARKETSCAPE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Security Solutions and Services Hardcopy 2017 Vendor Assessment Robert Palmer Allison Correia THIS IDC MARKETSCAPE EXCERPT FEATURES: HP IDC MARKETSCAPE FIGURE
Six Weeks to Security Operations The AMP Story. Mike Byrne Cyber Security AMP
 Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
Canada Highlights. Cybersecurity: Do you know which protective measures will make your company cyber resilient?
 Canada Highlights Cybersecurity: Do you know which protective measures will make your company cyber resilient? 21 st Global Information Security Survey 2018 2019 1 Canada highlights According to the EY
Canada Highlights Cybersecurity: Do you know which protective measures will make your company cyber resilient? 21 st Global Information Security Survey 2018 2019 1 Canada highlights According to the EY
Service Provider Consulting
 From Microsoft Services 1 Industry Overview More and more businesses are looking to outsource IT, decrease management requirements and ultimately save money. With worldwide public cloud spending expected
From Microsoft Services 1 Industry Overview More and more businesses are looking to outsource IT, decrease management requirements and ultimately save money. With worldwide public cloud spending expected
Transformation Through Innovation
 Transformation Through Innovation A service provider strategy to prosper from digitization People will have 11.6 billion mobile-ready devices and connections by 2020. For service providers to thrive today
Transformation Through Innovation A service provider strategy to prosper from digitization People will have 11.6 billion mobile-ready devices and connections by 2020. For service providers to thrive today
2018 MANAGED SECURITY SERVICE PROVIDER (MSSP): BENCHMARK SURVEY Insights That Inform Decision-Making for Retail Industry Outsourcing
 2018 MANAGED SECURITY SERVICE PROVIDER (MSSP): BENCHMARK SURVEY Insights That Inform Decision-Making for Retail Industry Outsourcing Powered by the Retail ISAC, A Division of the R-CISC Overview Last October,
2018 MANAGED SECURITY SERVICE PROVIDER (MSSP): BENCHMARK SURVEY Insights That Inform Decision-Making for Retail Industry Outsourcing Powered by the Retail ISAC, A Division of the R-CISC Overview Last October,
Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services
 Solution Overview Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services OPTIMIZE YOUR CLOUD SERVICES TO DRIVE BETTER BUSINESS OUTCOMES Reduce Cloud Business Risks and Costs
Solution Overview Gain Control Over Your Cloud Use with Cisco Cloud Consumption Professional Services OPTIMIZE YOUR CLOUD SERVICES TO DRIVE BETTER BUSINESS OUTCOMES Reduce Cloud Business Risks and Costs
SOLUTION BRIEF RSA NETWITNESS EVOLVED SIEM
 RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
RSA NETWITNESS EVOLVED SIEM OVERVIEW A SIEM is technology originally intended for compliance and log management. Later, as SIEMs became the aggregation points for security alerts, they began to be more
Optimisation drives digital transformation
 January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
Securing Digital Transformation
 September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
If you were under cyber attack would you ever know?
 If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
locuz.com SOC Services
 locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
IDC MarketScape: Worldwide Mobile Threat Management Software Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Mobile Threat Management Software 2018 2019 Vendor Assessment Phil Hochmuth THIS IDC MARKETSCAPE EXCERPT FEATURES LOOKOUT IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Mobile Threat Management Software 2018 2019 Vendor Assessment Phil Hochmuth THIS IDC MARKETSCAPE EXCERPT FEATURES LOOKOUT IDC MARKETSCAPE FIGURE FIGURE 1 IDC
RFP/RFI Questions for Managed Security Services. Sample MSSP RFP Template
 RFP/RFI Questions for Managed Security Services Sample MSSP RFP Template Table of Contents Request for Proposal Template Overview 1 Introduction... 1 How to Use this Document... 1 Suggested RFP Outline
RFP/RFI Questions for Managed Security Services Sample MSSP RFP Template Table of Contents Request for Proposal Template Overview 1 Introduction... 1 How to Use this Document... 1 Suggested RFP Outline
HPE Partner Ready Digital Marketing Program
 HPE Partner Ready Digital Marketing Program Accelerating your digital marketing proficiency and execution to drive business growth Collaborate Get started Table of Contents Changing B2B Buyer Behavior
HPE Partner Ready Digital Marketing Program Accelerating your digital marketing proficiency and execution to drive business growth Collaborate Get started Table of Contents Changing B2B Buyer Behavior
RSA INCIDENT RESPONSE SERVICES
 RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
RSA INCIDENT RESPONSE SERVICES Enabling early detection and rapid response EXECUTIVE SUMMARY Technical forensic analysis services RSA Incident Response services are for organizations that need rapid access
Security Monitoring. Managed Vulnerability Services. Managed Endpoint Protection. Platform. Platform Managed Endpoint Detection and Response
 Security Operations Flexible and Scalable Solutions to Improve Your Security Capabilities Security threats continue to rise each year and are increasing in sophistication and malicious intent. Unfortunately,
Security Operations Flexible and Scalable Solutions to Improve Your Security Capabilities Security threats continue to rise each year and are increasing in sophistication and malicious intent. Unfortunately,
CASE STUDY: USING THE HYBRID CLOUD TO INCREASE CORPORATE VALUE AND ADAPT TO COMPETITIVE WORLD TRENDS
 CASE STUDY: USING THE HYBRID CLOUD TO INCREASE CORPORATE VALUE AND ADAPT TO COMPETITIVE WORLD TRENDS Geoff Duncan, Senior Solutions Architect, Digital Fortress Brandon Tanner, Senior Manager, Rentsys Recovery
CASE STUDY: USING THE HYBRID CLOUD TO INCREASE CORPORATE VALUE AND ADAPT TO COMPETITIVE WORLD TRENDS Geoff Duncan, Senior Solutions Architect, Digital Fortress Brandon Tanner, Senior Manager, Rentsys Recovery
VMware vcloud Air Network Service Providers Ensure Smooth Cloud Deployment
 VMware vcloud Air Network Service Providers Ensure Smooth Cloud Deployment RELIABLE, FAMILIAR INFRASTRUCTURE BACKED BY VMWARE AND DELIVERED THROUGH PARTNERS HELPS OPTIMIZE CLOUD INVESTMENTS AS ENTERPRISES
VMware vcloud Air Network Service Providers Ensure Smooth Cloud Deployment RELIABLE, FAMILIAR INFRASTRUCTURE BACKED BY VMWARE AND DELIVERED THROUGH PARTNERS HELPS OPTIMIZE CLOUD INVESTMENTS AS ENTERPRISES
Angela McKay Director, Government Security Policy and Strategy Microsoft
 Angela McKay Director, Government Security Policy and Strategy Microsoft Demographic Trends: Internet Users in 2005.ru.ca.is.uk.nl.be.no.de.pl.ua.us.fr.es.ch.it.eg.il.sa.jo.tr.qa.ae.kz.cn.tw.kr.jp.mx.co.br.pk.th.ph.ng.in.sg.my.ar.id.au
Angela McKay Director, Government Security Policy and Strategy Microsoft Demographic Trends: Internet Users in 2005.ru.ca.is.uk.nl.be.no.de.pl.ua.us.fr.es.ch.it.eg.il.sa.jo.tr.qa.ae.kz.cn.tw.kr.jp.mx.co.br.pk.th.ph.ng.in.sg.my.ar.id.au
Cloud for Government: A Transformative Digital Tool to Better Serve Communities
 Cloud for Government: A Transformative Digital Tool to Better Serve Communities 1 005181004 From state to local agencies, government organizations crave access to the same cloud-based tools enabling digital
Cloud for Government: A Transformative Digital Tool to Better Serve Communities 1 005181004 From state to local agencies, government organizations crave access to the same cloud-based tools enabling digital
