Everest Group PEAK Matrix for IT Security Services
|
|
|
- Duane McDonald
- 6 years ago
- Views:
Transcription
1 Everest Group PEAK Matrix for IT Security Services Focus on Mphasis September 2017 Copyright 2017 Everest Global, Inc. This document has been licensed for exclusive use and distribution by Mphasis
2 Introduction and scope Everest Group recently released its report titled IT Security Services Market Trends and PEAK Matrix Assessment: Security The Biggest Digital Insecurity. As a part of this report, Everest Group analyzed 17 leading service providers on the Everest Group PEAK Matrix specific to IT security services and categorized them into Leaders, Major Contenders, and Aspirants. The PEAK Matrix is a composite framework that provides an objective, data-driven, and comparative assessment of IT security service providers based on their absolute market success and delivery capability. Based on the analysis, Mphasis emerged as a Major Contender and Star Performer. This document focuses on Mphasis IT security services experience and capabilities. It includes: Mphasis position on the IT security services PEAK Matrix Detailed profile of Mphasis IT security services capabilities Buyers can use the PEAK Matrix to identify and evaluate different service providers. It helps them understand the service providers relative strengths and gaps. However, it is also important to note that while the PEAK Matrix is a useful starting point, the results from the assessment may not be directly prescriptive for each buyer. Buyers will have to consider their unique situation and requirements, and match them against service provider capability for an ideal fit. 2
3 Background of the research Background of the research Security threats are increasing in complexity, size, and variety. The rapid digitalization has made the enterprise IT security landscape highly complex and challenging to handle, as CISOs look to guard their enterprise environments against burgeoning internal and external threats. The proliferation in digital touch-points, driven by increasing adoption of next-generation technologies / delivery models such as cloud, IOT, mobility, and social media have rendered existing traditional enterprise security and risk mitigation strategies obsolete. Enterprises are now required to take a more intelligence-driven, holistic security approach to deal with this rapidly changing threat landscape Technology complexities associated with security service deployment and lack of internal skills is pushing enterprises to increasingly seek third-party support for security services. Service providers are beefing up their global security service delivery capabilities and coverage, expanding their partnership networks to align with next-generation security requirements of clients, and investing in nurturing their security services talent in order to stay relevant In this research, we present fact-based trends impacting the security services market, along with the assessment and detailed profiles of 17 IT service providers featured on the IT security services PEAK Matrix. Each service provider profile gives a comprehensive picture of their security services vision, services suite, scale of operations, key solutions, and partnerships The assessment is based on Everest Group s annual RFI process conducted over Q1 and Q2 2017, interactions with leading IT security service providers, and analysis of the IT security services marketplace Scope of this report: Services: IT security services Geography: Global Service providers: 17 leading IT service providers This report includes the profiles of the following 17 service providers on the IT security services PEAK Matrix: Leaders: Accenture, DXC Technology, IBM, and Wipro Major Contenders: Cognizant, Fujitsu, HCL Technologies, Mphasis, NTT DATA, SecureWorks, TCS, Tech Mahindra, and Unisys Aspirants: Hexaware, Luxoft, Microland, and Syntel 3
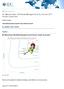
4 Market success (Revenue, growth, and enterprise adoption) 25 th percentile 75 th percentile Everest Group PEAK Matrix IT Security Services Market Trends and PEAK Matrix Assessment Mphasis positioned as Major Contender and Star Performer Everest Group PEAK Matrix for IT security services 1 High 75 th percentile Major Contenders Leaders DXC Technology 2 Accenture Fujitsu HCL Technologies Wipro TCS SecureWorks IBM Leaders Major Contenders Aspirants Star Performers Cognizant NTT DATA Unisys Mphasis Tech Mahindra Luxoft Syntel Microland Low Aspirants Low Hexaware 25 th percentile Delivery capability (Scale, scope, domain expertise and innovation, delivery footprint, and buyer satisfaction) High 1 Assessment for Cognizant, Fujitsu, IBM, DXC Technology, and Unisys excludes service provider inputs for this particular study and is based on Everest Group s estimates that leverage Everest Group s proprietary Transaction Intelligence (TI) database, ongoing coverage of these service providers, service provider public disclosures, and interaction with buyers 2 HPE Services and CSC have now combined to form DXC Technology Source: Everest Group (2017) 4
5 Mphasis IT security services profile (page 1 of 2) IT security services overview Strengths Credible investments in developing its security solution portfolio addressing next-generation concepts such as big data analytics, automation Has established itself as a cost-effective partner for security implementation, management, and monitoring services in the North American region Areas of improvement Limited proof points in driving large-scale security transformation leveraging existing solutions Focus on extending its delivery capabilities beyond North America to Europe and APAC; further invest in next-generation security themes to stay relevant Scope of coverage: Mphasis is estimated to have over 400 FTEs dedicated to IT security services. The company manages ~7 million IP addresses and 65,000 firewalls/intrusion prevention devices. Mphasis manages ~4.5million end-user devices including physical desktops/laptops, mobile devices, etc. IT security services revenue Adoption by service segments High (>20%) Medium (10-20%) Low (<10%) <US$200 million Adoption by service type Consulting US$200- US$500 million Design & implementation US$500 million- US$1 billion >US$1 billion High (>20%) Medium (10-20%) Low (<10%) Managed services As-a-service Identity & access management Application security Data security End-point security Network security Risk management and compliance Cloud security Adoption by industry High (>20%) Medium (10-20%) Low (<10%) Adoption by geography High (>25%) Moderate (10-25%) Low (<10%) BFSI Energy and utilities Technology Healthcare and life sciences Manufacturing Retail, distribution, and CPG Public Telecom, media, and entertainment Adoption by buyer groups High (>20%) Medium (10-20%) Low (<10%) Small (annual revenue < US$1 billion) Medium (annual revenue = US$1-5 billion) Large (annual revenue > US$5 billion) Source: Everest Group (2017) 5
6 Mphasis IT security services profile (page 2 of 2) IT security services offerings NOT EXHAUSTIVE Mphasis vision for IT security is to provide its clients with solutions that address security challenges across their hybrid IT. Mphasis aims to achieve this vision by consistently delivering integrated security operations as a service through its MTrust platform that has inbuilt automation, intelligent threat analytics, and threat response. Proprietary solutions (representative list) Solution MTrust ARBAC InfraGenie Digital Security Utility (DSU) Details It is a threat analytics platform, driven by Big Data, that identifies critical actionable intelligence from terabytes of log and event metadata. The solution automates the manual process of role-based access control implementation by creating platform-specific (Windows, Unix, SQL, Oracle) set of scripts starting from data pull, data validation, data permission, and clean-up. It is an intelligent automation platform that predicts incidents, reduces manual intervention, automates most activities, and saves money for the client in the process. It is an authentication-as-a-service platform, designed for end users, optimized for adoption, and enabled for increased protection. IT security services partnerships (representative list) Partner name Type of partnership Details Paladion Technology partnership Provides cyber security services by leveraging Paladion's security orchestration and automation platform Checkpoint Technology partnership Provides network security, endpoint security, and data security services Resilient Technology partnership Provides integrated security offerings Additionally, Mphasis has partnerships with Cisco, McAfee, HPE Arcsight, and Collibra. Recent activities (representative list). Development Acquisition of Digital Risk LLC Source: Everest Group (2017) Details In February 2013, Mphasis completed the acquisition of U.S.-based Digital Risk LLC, one of the leading providers of solutions related to risk, compliance, and transaction management to the U.S. mortgage market. 6
7 Appendix 7
8 Market success (Revenue, revenue growth, and enterprise adoption) 25 th percentile 75 th percentile Everest Group PEAK Matrix is a proprietary framework for assessment of a service provider s capability Everest Group PEAK Matrix for IT security services High Major Contenders 2 nd or 3 rd quartile performance across market success and capability 75 th percentile Leaders Top quartile performance across market success and capability Aspirants Low 4 th quartile performance across market success and capability Low 25 th percentile IT security services delivery capability (Scale, scope, domain expertise and innovation, delivery footprint, and buyer satisfaction) High Everest Group s PEAK Matrix is a composite index of a range of distinct metrics related to a service provider s scale, scope, technology/domain investments, delivery footprint, and resultant market success in the context of a given services function. 8
9 Market success Dimensions of service providers capability and market success underlying the PEAK Matrix Leaders Major Contenders Measures revenue, revenue growth, and adoption across enterprise segments Aspirants Delivery capability Measures ability to deliver services successfully. This is captured through five subdimensions Scale Scope Domain expertise and innovation Delivery footprint Buyer satisfaction Overall company revenue Percentage contribution of IT security services revenue to overall company revenue Focus across service segments (IAM, network security, GRC, endpoint security, etc.) Coverage across verticals Geographical coverage IP / proprietary solutions / assets / innovation Certifications Mergers & Acquisitions (M&A) and alliances Delivery centers / SOC Buyer satisfaction rating 9
10 Market success Additionally, Everest Group confers the Star Performers title on the providers that demonstrate the strongest forward movement over time on the PEAK Matrix Methodology Everest Group selects Star Performers based on the relative YOY movement of each service provider on the PEAK Matrix Year 1 Service provider Year 0 In order to assess advancements on market success, we evaluate the performance of each service provider on the PEAK Matrix across a number of parameters including: Annual revenue from the specific service line Relative adoption across enterprise segments Delivery capability In order to assess advancements on capability, we evaluate the performance of each service provider on the PEAK Matrix across a number of parameters including: Annual growth in scale Increase in scope of services Expansion of delivery footprint Domain-specific investments & innovation Improvement in buyer satisfaction This slide to be used ONLY for Star Performers The top quartile performers on each of the specified parameters are identified and the Star Performer rating is awarded to the service providers with: The maximum number of top quartile performances across all of the above / left-listed parameters and At least one area of top quartile performance in both market success and capability advancement 2017 IT security services Star Performers The Star Performers title relates to YOY performance for a given service provider and does not reflect the overall market leadership position. Those identified as Star Performers may include Leaders, Major Contenders, or Aspirants. 10
11 FAQs (page 1 of 2) Does the PEAK Matrix assessment incorporate any subjective criteria? Everest Group s PEAK Matrix assessment adopts an objective and fact-based approach (leveraging service provider RFIs and Everest Group s proprietary databases containing providers deals and operational capability information). In addition, these results are validated / fine-tuned based on our market experience, buyer interaction, and provider briefings Is being a Major Contender or Aspirant on the PEAK Matrix, an unfavorable outcome? No. PEAK Matrix highlights and positions only the best-in-class service providers in a particular functional/vertical services area. There are a number of providers from the broader universe that are assessed and do not make it to the PEAK Matrix at all. Therefore, being represented on the PEAK Matrix is itself a favorable recognition What other aspects of PEAK Matrix assessment are relevant to buyers and providers besides the PEAK Matrix position? PEAK Matrix position is only one aspect of Everest Group s overall assessment. In addition to assigning a Leader, Major Contender or Aspirant title, Everest Group highlights the distinctive capabilities and unique attributes of all the PEAK Matrix providers assessed in its report. The detailed metric level assessment and associated commentary is helpful for buyers in selecting particular providers for their specific requirements. It also helps providers showcase their strengths in specific areas What are the incentives for buyers and providers to participate/provide input to PEAK Matrix research? Participation incentives for buyers include a summary of key findings from the PEAK Matrix assessment Participation incentives for providers include adequate representation and recognition of their capabilities/success in the market place, and a copy of their own profile that is published by Everest Group as part of the compendium of PEAK Matrix providers profiles 11
12 FAQs (page 2 of 2) What is the process for a service provider to leverage their PEAK Matrix positioning status? Providers can use their PEAK positioning rating in multiple ways including: Issue a press release declaring their positioning/rating Customized PEAK profile for circulation (with clients, prospects, etc.) Quotes from Everest Group analysts could be disseminated to the media Leverage PEAK branding across communications ( signatures, marketing brochures, credential packs, client presentations, etc.) The provider must obtain the requisite licensing and distribution rights for the above activities through an agreement with the designated POC at Everest Group 12
13 About Everest Group Everest Group is a consulting and research firm focused on strategic IT, business services, and sourcing. We are trusted advisors to senior executives of leading enterprises, providers, and investors. Our firm helps clients improve operational and financial performance through a hands-on process that supports them in making well-informed decisions that deliver high-impact results and achieve sustained value. Our insight and guidance empower clients to improve organizational efficiency, effectiveness, agility, and responsiveness. What sets Everest Group apart is the integration of deep sourcing knowledge, problemsolving skills and original research. Details and in-depth content are available at Dallas (Headquarters) info@everestgrp.com Bangalore india@everestgrp.com Delhi india@everestgrp.com London unitedkingdom@everestgrp.com Stay connected Website Group New York info@everestgrp.com Blog Sherpas In Blue Shirts Toronto canada@everestgrp.com
Everest Group PEAK Matrix for Workplace Services
 Everest Group PEAK Matrix for Workplace Services Focus on HPE (DXC Technology) September 2017 Copyright 2017 Everest Global, Inc. This document has been licensed for exclusive use and distribution by HPE
Everest Group PEAK Matrix for Workplace Services Focus on HPE (DXC Technology) September 2017 Copyright 2017 Everest Global, Inc. This document has been licensed for exclusive use and distribution by HPE
Everest Group PEAK Matrix TM for private cloud enablement Services
 Everest Group PEAK Matrix TM for private cloud enablement Services Focus on Wipro September 2016 Copyright 2016 Everest Global, Inc. This document has been licensed for exclusive use and distribution by
Everest Group PEAK Matrix TM for private cloud enablement Services Focus on Wipro September 2016 Copyright 2016 Everest Global, Inc. This document has been licensed for exclusive use and distribution by
Everest Group PEAK Matrix for solutions : IT Infrastructure Services Automation (Focus on IT service providers)
 Everest Group PEAK Matrix for solutions : IT Infrastructure Services Automation (Focus on IT service providers) Focus on Wipro April 2017 Copyright 2017 Everest Global, Inc. This document has been licensed
Everest Group PEAK Matrix for solutions : IT Infrastructure Services Automation (Focus on IT service providers) Focus on Wipro April 2017 Copyright 2017 Everest Global, Inc. This document has been licensed
Cloud and Infrastructure Services Annual Report 2017: The Future of Stack is No Stack!
 Cloud and Infrastructure Services Annual Report 2017: The Future of Stack is No Stack! Cloud & Infrastructure Services (CIS) Annual Report November 2017: Complimentary Abstract / Table of Contents Our
Cloud and Infrastructure Services Annual Report 2017: The Future of Stack is No Stack! Cloud & Infrastructure Services (CIS) Annual Report November 2017: Complimentary Abstract / Table of Contents Our
IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2018 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES DELL EMC IDC MARKETSCAPE FIGURE FIGURE 1 IDC
DATACENTER SERVICES DATACENTER
 SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
Run the business. Not the risks.
 Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Run the business. Not the risks. RISK-RESILIENCE FOR THE DIGITAL BUSINESS Cyber-attacks are a known risk to business. Today, with enterprises becoming pervasively digital, these risks have grown multifold.
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Making hybrid IT simple with Capgemini and Microsoft Azure Stack
 Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
Making hybrid IT simple with Capgemini and Microsoft Azure Stack The significant evolution of cloud computing in the last few years has encouraged IT leaders to rethink their enterprise cloud strategy.
IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
IDC MarketScape IDC MarketScape: Worldwide Datacenter Transformation Consulting and Implementation Services 2016 Vendor Assessment Chad Huston Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES: WIPRO IDC
Optimisation drives digital transformation
 January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
January 2017 Executive summary Forward-thinking business leaders are challenging their organisations to achieve transformation by harnessing digital technologies with organisational, operational, and business
Better skilled workforce
 Better skilled workforce for the New Style of Business HPE Education Services November 20, 2015 Education is the most powerful weapon which you can use to change the world Nelson Mandela The New Style
Better skilled workforce for the New Style of Business HPE Education Services November 20, 2015 Education is the most powerful weapon which you can use to change the world Nelson Mandela The New Style
Hybrid IT for SMBs. HPE addressing SMB and channel partner Hybrid IT demands ANALYST ANURAG AGRAWAL REPORT : HPE. October 2018
 V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2014 Vendor Analysis Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
Predictive Insight, Automation and Expertise Drive Added Value for Managed Services
 Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Global IT Services Market Size, Status and Forecast 2025
 Report Information More information from: https://www.wiseguyreports.com/reports/3208352-global-it-services-market-size-status-and-forecast- 2025 Global IT Services Market Size, Status and Forecast 2025
Report Information More information from: https://www.wiseguyreports.com/reports/3208352-global-it-services-market-size-status-and-forecast- 2025 Global IT Services Market Size, Status and Forecast 2025
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Three Key Challenges Facing ISPs and Their Enterprise Clients
 Three Key Challenges Facing ISPs and Their Enterprise Clients GRC, enterprise services, and ever-evolving hybrid infrastructures are all dynamic and significant challenges to the ISP s enterprise clients.
Three Key Challenges Facing ISPs and Their Enterprise Clients GRC, enterprise services, and ever-evolving hybrid infrastructures are all dynamic and significant challenges to the ISP s enterprise clients.
Incentives for IoT Security. White Paper. May Author: Dr. Cédric LEVY-BENCHETON, CEO
 White Paper Incentives for IoT Security May 2018 Author: Dr. Cédric LEVY-BENCHETON, CEO Table of Content Defining the IoT 5 Insecurity by design... 5 But why are IoT systems so vulnerable?... 5 Integrating
White Paper Incentives for IoT Security May 2018 Author: Dr. Cédric LEVY-BENCHETON, CEO Table of Content Defining the IoT 5 Insecurity by design... 5 But why are IoT systems so vulnerable?... 5 Integrating
IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Network Consulting Services 2017 Vendor Assessment Leslie Rosenberg THIS IDC MARKETSCAPE EXCERPT FEATURES: CISCO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IT Consulting and Implementation Services
 PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
Cognizant Cloud Security Solution
 CLOUD SECURITY OVERVIEW Cognizant Cloud Security Solution Transform your security operation to protect your business across public and hybrid cloud environments. December 2017 The advantages of moving
CLOUD SECURITY OVERVIEW Cognizant Cloud Security Solution Transform your security operation to protect your business across public and hybrid cloud environments. December 2017 The advantages of moving
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS
 Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Cyber Defense Maturity Scorecard DEFINING CYBERSECURITY MATURITY ACROSS KEY DOMAINS Continual disclosed and reported
Sales Presentation Case 2018 Dell EMC
 Sales Presentation Case 2018 Dell EMC Introduction: As a member of the Dell Technologies unique family of businesses, Dell EMC serves a key role in providing the essential infrastructure for organizations
Sales Presentation Case 2018 Dell EMC Introduction: As a member of the Dell Technologies unique family of businesses, Dell EMC serves a key role in providing the essential infrastructure for organizations
Mid-Market Data Center Purchasing Drivers, Priorities and Barriers
 Mid-Market Data Center Purchasing Drivers, Priorities and Barriers Featuring Sophia Vargas, Forrester Research Inc. 30 May 2014 Introducing today s presenters: Matt Miszewski Senior Vice President of Sales
Mid-Market Data Center Purchasing Drivers, Priorities and Barriers Featuring Sophia Vargas, Forrester Research Inc. 30 May 2014 Introducing today s presenters: Matt Miszewski Senior Vice President of Sales
Singtel Investor Day Bill Chang, CEO, Group Enterprise and Country Chief Officer Singapore 13 June 2018
 Singtel Investor Day 2018 Bill Chang, CEO, Group Enterprise and Country Chief Officer Singapore 13 June 2018 Singtel Group Enterprise at a glance #1 International IPVPN in APeJ #1 EVPN and Eline in APeJ
Singtel Investor Day 2018 Bill Chang, CEO, Group Enterprise and Country Chief Officer Singapore 13 June 2018 Singtel Group Enterprise at a glance #1 International IPVPN in APeJ #1 EVPN and Eline in APeJ
Security In A Box. Modular Security Services Offering - BFSI. A new concept to Security Services Delivery.
 Modular Security Services Offering - BFSI Security In A Box A new concept to Security Services Delivery. 2017 Skillmine Technology Consulting Pvt. Ltd. The information in this document is the property
Modular Security Services Offering - BFSI Security In A Box A new concept to Security Services Delivery. 2017 Skillmine Technology Consulting Pvt. Ltd. The information in this document is the property
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
White Paper. View cyber and mission-critical data in one dashboard
 View cyber and mission-critical data in one dashboard Table of contents Rising cyber events 2 Mitigating threats 2 Heighten awareness 3 Evolving the solution 5 One of the direct benefits of the Homeland
View cyber and mission-critical data in one dashboard Table of contents Rising cyber events 2 Mitigating threats 2 Heighten awareness 3 Evolving the solution 5 One of the direct benefits of the Homeland
Growth Leadership, Unified Threat Management (UTM) Global, 2010
 Growth Leadership, Unified Threat Management (UTM) Global, 2010 Frost & Sullivan s Global Research Platform Frost & Sullivan is entering its 49 th year in business with a global research organization of
Growth Leadership, Unified Threat Management (UTM) Global, 2010 Frost & Sullivan s Global Research Platform Frost & Sullivan is entering its 49 th year in business with a global research organization of
Transformation in Technology Barbara Duck Chief Information Officer. Investor Day 2018
 Transformation in Technology Barbara Duck Chief Information Officer Investor Day 2018 Key Takeaways 1Transformation in Technology driving out cost, supporting a more technologyenabled business Our new
Transformation in Technology Barbara Duck Chief Information Officer Investor Day 2018 Key Takeaways 1Transformation in Technology driving out cost, supporting a more technologyenabled business Our new
2018 Trends in Hosting & Cloud Managed Services
 PREVIEW 2018 Trends in Hosting & Cloud Managed Services DEC 2017 Rory Duncan, Research Director, Managed Services & Hosting Penny Jones, Principal Analyst - MTDC & Managed Services Aaron Sherrill, Senior
PREVIEW 2018 Trends in Hosting & Cloud Managed Services DEC 2017 Rory Duncan, Research Director, Managed Services & Hosting Penny Jones, Principal Analyst - MTDC & Managed Services Aaron Sherrill, Senior
New Zealand Government IBM Infrastructure as a Service
 New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
EY Consulting. Is your strategy planning for the future or creating it? #TransformativeAge
 2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO #IIACHI
 Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO CHAPTER: @IIACHI #IIACHI WWW.FACEBOOK.COM/IIACHICAGO HTTPS://WWW.LINKEDIN.COM/GROUPS/1123977 1 CAE Communications and Common Audit Committee
Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO CHAPTER: @IIACHI #IIACHI WWW.FACEBOOK.COM/IIACHICAGO HTTPS://WWW.LINKEDIN.COM/GROUPS/1123977 1 CAE Communications and Common Audit Committee
PREPARE FOR TAKE OFF. Accelerate your organisation s journey to the Cloud.
 PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES
 IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES Introductions Agenda Overall data risk and benefit landscape / shifting risk and opportunity landscape and market expectations Looking at data
IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES Introductions Agenda Overall data risk and benefit landscape / shifting risk and opportunity landscape and market expectations Looking at data
Smart Data Center Solutions
 Smart Data Center Solutions New Data Center Challenges Require New Solutions Data Center Architecture. Inside and Out. Data centers are mission-critical facilities. A silo-based approach to designing,
Smart Data Center Solutions New Data Center Challenges Require New Solutions Data Center Architecture. Inside and Out. Data centers are mission-critical facilities. A silo-based approach to designing,
OVERVIEW BROCHURE GRC. When you have to be right
 OVERVIEW BROCHURE GRC When you have to be right WoltersKluwerFS.com In response to today s demanding economic and regulatory climate, many financial services firms are transforming operations to enhance
OVERVIEW BROCHURE GRC When you have to be right WoltersKluwerFS.com In response to today s demanding economic and regulatory climate, many financial services firms are transforming operations to enhance
Cybersecurity. Securely enabling transformation and change
 Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
SOLUTION BRIEF RSA ARCHER IT & SECURITY RISK MANAGEMENT
 RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
Jane s Defence Industry & Markets Intelligence Centre. Develop Advantage. Mitigate Risk. Capture Opportunity.
 Jane s Defence Industry & Markets Intelligence Centre Develop Advantage. Mitigate Risk. Capture Opportunity. OVERVIEW A challenging marketplace The global A&D industry is facing an increasingly volatile,
Jane s Defence Industry & Markets Intelligence Centre Develop Advantage. Mitigate Risk. Capture Opportunity. OVERVIEW A challenging marketplace The global A&D industry is facing an increasingly volatile,
FOR FINANCIAL SERVICES ORGANIZATIONS
 RSA BUSINESS-DRIVEN SECURITYTM FOR FINANCIAL SERVICES ORGANIZATIONS MANAGING THE NEXUS OF RISK & SECURITY A CHANGING LANDSCAPE AND A NEW APPROACH Today s financial services technology landscape is increasingly
RSA BUSINESS-DRIVEN SECURITYTM FOR FINANCIAL SERVICES ORGANIZATIONS MANAGING THE NEXUS OF RISK & SECURITY A CHANGING LANDSCAPE AND A NEW APPROACH Today s financial services technology landscape is increasingly
Cloud Computing. January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION
 Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
Finding Pure-Play Midtier ESPs: A Two-Step Process
 Research Brief Finding Pure-Play Midtier ESPs: A Two-Step Process Abstract: The pure-play midtier consulting and integration sector can be a competitive option to global integrators. Tier 2 and 3 vendors
Research Brief Finding Pure-Play Midtier ESPs: A Two-Step Process Abstract: The pure-play midtier consulting and integration sector can be a competitive option to global integrators. Tier 2 and 3 vendors
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
IBM Security Systems. IBM X-Force 2012 & CISO Survey. Cyber Security Threat Landscape IBM Corporation IBM Corporation
 IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
IDC MarketScape IDC MarketScape: Worldwide Managed Security Services 2017 Vendor Assessment Martha Vazquez THIS MARKETSCAPE EXCERPT WAS CREATED FOR BT IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide
LTI Security Services. Intelligent & integrated Approach to Cyber & Digital Security
 LTI Security Intelligent & integrated Approach to Cyber & Digital Security Overview As businesses are expanding globally into new territories, propelled and steered by digital disruption and technological
LTI Security Intelligent & integrated Approach to Cyber & Digital Security Overview As businesses are expanding globally into new territories, propelled and steered by digital disruption and technological
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services
 MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
Social Engineering: We are the target Sponsor Guide
 Lead Sponsor Social Engineering: We are the target Sponsor Guide ISfL Annual Cyber Security Conference Wednesday 8th November 2017 ųƚÿƌåú ƵĜƋĘ ŅĵŅųųŅƵ This ISfL Conference has been made possible by the
Lead Sponsor Social Engineering: We are the target Sponsor Guide ISfL Annual Cyber Security Conference Wednesday 8th November 2017 ųƚÿƌåú ƵĜƋĘ ŅĵŅųųŅƵ This ISfL Conference has been made possible by the
Best Practices in the Asia Pacific ICT Industry
 Best Practices in the Asia Pacific ICT Industry 2009 Asia Pacific Frost & Sullivan ICT Award for Collaboration & Conferencing Services Provider of the Year COLLABORATION & CONFERENCING SERVICES MARKETS
Best Practices in the Asia Pacific ICT Industry 2009 Asia Pacific Frost & Sullivan ICT Award for Collaboration & Conferencing Services Provider of the Year COLLABORATION & CONFERENCING SERVICES MARKETS
TSC Business Continuity & Disaster Recovery Session
 TSC Business Continuity & Disaster Recovery Session Mohamed Ashmawy Infrastructure Consulting Pursuit Hewlett-Packard Enterprise Saudi Arabia Mohamed.ashmawy@hpe.com Session Objectives and Outcomes Objectives
TSC Business Continuity & Disaster Recovery Session Mohamed Ashmawy Infrastructure Consulting Pursuit Hewlett-Packard Enterprise Saudi Arabia Mohamed.ashmawy@hpe.com Session Objectives and Outcomes Objectives
OVERVIEW MANAGED INFRASTRUCTURE SERVICES WHY INFRASTRUCTURE MANAGEMENT? KEY CHALLENGES HOW MANAGED INFRA SERVICES ADDRESS THE ABOVE CHALLENGES?
 MANAGED ENABLING AGILE & SECURE FOR DIGITAL TRANSFORMATION EXPLORE According to forecasts from MarketsandMarkets, the global managed services market is poised to grow from USD 138.27 Billion in 2016 to
MANAGED ENABLING AGILE & SECURE FOR DIGITAL TRANSFORMATION EXPLORE According to forecasts from MarketsandMarkets, the global managed services market is poised to grow from USD 138.27 Billion in 2016 to
Cyber Security in Smart Commercial Buildings 2017 to 2021
 Smart Buildings Cyber Security in Smart Commercial Buildings 2017 to 2021 Published: Q2 2017 Cyber Security in Smart Buildings Synopsis 2017 This report will help all stakeholders and investors in the
Smart Buildings Cyber Security in Smart Commercial Buildings 2017 to 2021 Published: Q2 2017 Cyber Security in Smart Buildings Synopsis 2017 This report will help all stakeholders and investors in the
Government IT Modernization and the Adoption of Hybrid Cloud
 Government IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Federal and National Governments Are at an Inflection Point Federal and national governments
Government IT Modernization and the Adoption of Hybrid Cloud An IDC InfoBrief, Sponsored by VMware June 2018 Federal and National Governments Are at an Inflection Point Federal and national governments
HCL GRC IT AUDIT & ASSURANCE SERVICES
 HCL GRC IT AUDIT & ASSURANCE SERVICES Overview The immense progress made in information and communications technology offers enterprises outstanding benefits. However this also results in making the risk
HCL GRC IT AUDIT & ASSURANCE SERVICES Overview The immense progress made in information and communications technology offers enterprises outstanding benefits. However this also results in making the risk
Cloud Going Mainstream All Are Trying, Some Are Benefiting; Few Are Maximizing Value. An IDC InfoBrief, sponsored by Cisco September 2016
 All Are Trying, Some Are Benefiting; Few Are Maximizing Value September 2016 Executive Summary Cloud adoption has increased 61% from last year, with 73% pursuing a hybrid cloud strategy and on-premises
All Are Trying, Some Are Benefiting; Few Are Maximizing Value September 2016 Executive Summary Cloud adoption has increased 61% from last year, with 73% pursuing a hybrid cloud strategy and on-premises
Micro Focus Partner Program. For Resellers
 Micro Focus Partner Program For Resellers Contents Micro Focus Today About Micro Focus Our solutions for digital transformation Products and Solutions Program Membership Tiers Become a Portfolio Expert
Micro Focus Partner Program For Resellers Contents Micro Focus Today About Micro Focus Our solutions for digital transformation Products and Solutions Program Membership Tiers Become a Portfolio Expert
Data Center Outsourcing
 Data Center Outsourcing Archetype Report A research report aligning enterprise requirements and provider capabilities March 2018 Customized reprint courtesy of: Section Name About this Report Information
Data Center Outsourcing Archetype Report A research report aligning enterprise requirements and provider capabilities March 2018 Customized reprint courtesy of: Section Name About this Report Information
DIGITAL TRANSFORMATION IN FINANCIAL SERVICES
 DIGITAL TRANSFORMATION IN FINANCIAL SERVICES Global Priorities, Progress, and Obstacles Insights from business and IT executives at financial services institutions worldwide reveal that while digital transformation
DIGITAL TRANSFORMATION IN FINANCIAL SERVICES Global Priorities, Progress, and Obstacles Insights from business and IT executives at financial services institutions worldwide reveal that while digital transformation
Securing Digital Transformation
 September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
Introduction: E.ON Strategic Co-Investments EcoSummit
 Introduction: E.ON Strategic Co-Investments EcoSummit An Overview of E.ON At facilities across Europe, Russia, and North America, our more than 72,000 employees generated approx. 122 billion in sales in
Introduction: E.ON Strategic Co-Investments EcoSummit An Overview of E.ON At facilities across Europe, Russia, and North America, our more than 72,000 employees generated approx. 122 billion in sales in
M&A Cyber Security Due Diligence
 M&A Cyber Security Due Diligence Prepared by: Robert Horton, Ollie Whitehouse & Sherief Hammad Contents Page 1 Introduction 3 2 Technical due diligence goals 3 3 Enabling the business through cyber security
M&A Cyber Security Due Diligence Prepared by: Robert Horton, Ollie Whitehouse & Sherief Hammad Contents Page 1 Introduction 3 2 Technical due diligence goals 3 3 Enabling the business through cyber security
I D C T E C H N O L O G Y S P O T L I G H T
 I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
I D C T E C H N O L O G Y S P O T L I G H T P ow e ring Digital Transfor m a t i o n T h r ough the C l o u d - R e a d y E n t e r p rise September 2016 Adapted from Developing a Cloud Strategy for Digital
21ST century enterprise. HCL Technologies Presents. Roadmap for Data Center Transformation
 21ST century enterprise HCL Technologies Presents Roadmap for Data Center Transformation june 2016 21st Century Impact on Data Centers The rising wave of digitalization has changed the way IT impacts business.
21ST century enterprise HCL Technologies Presents Roadmap for Data Center Transformation june 2016 21st Century Impact on Data Centers The rising wave of digitalization has changed the way IT impacts business.
Powering Resilience. Keep your business on 24/7. Proposition series September 2017
 Powering Resilience Keep your business on 24/7 Proposition series September 2017 Centrica Business Solutions Powering Resilience Reliable power is mission-critical As more businesses become digital, the
Powering Resilience Keep your business on 24/7 Proposition series September 2017 Centrica Business Solutions Powering Resilience Reliable power is mission-critical As more businesses become digital, the
Accelerate Your Cloud Journey
 Dubai, UAE 20th March 2013 Accelerate Your Cloud Journey James Spearman Dimension Data - Solutions Architect Cloud 2012 2011 Cisco and/or its affiliates. All rights reserved. Cisco Connect 1 Dimension
Dubai, UAE 20th March 2013 Accelerate Your Cloud Journey James Spearman Dimension Data - Solutions Architect Cloud 2012 2011 Cisco and/or its affiliates. All rights reserved. Cisco Connect 1 Dimension
Smart Data Center From Hitachi Vantara: Transform to an Agile, Learning Data Center
 Smart Data Center From Hitachi Vantara: Transform to an Agile, Learning Data Center Leverage Analytics To Protect and Optimize Your Business Infrastructure SOLUTION PROFILE Managing a data center and the
Smart Data Center From Hitachi Vantara: Transform to an Agile, Learning Data Center Leverage Analytics To Protect and Optimize Your Business Infrastructure SOLUTION PROFILE Managing a data center and the
in Action Delivering the digital enterprise Human Centric Innovation Ralf Salzmann Manager OEM
 Delivering the digital enterprise The five stages of infrastructure evolution Ralf Salzmann Human Centric Innovation in Action Manager OEM Sales @Brocade Agenda BRCD Company details What does digital mean
Delivering the digital enterprise The five stages of infrastructure evolution Ralf Salzmann Human Centric Innovation in Action Manager OEM Sales @Brocade Agenda BRCD Company details What does digital mean
Services solutions for Managed Service Providers (MSPs)
 McAfee Advanced Threat Defense Services solutions for Managed Service Providers (MSPs) Differentiate your services and protect customers against zero-day attacks with the industry s most comprehensive
McAfee Advanced Threat Defense Services solutions for Managed Service Providers (MSPs) Differentiate your services and protect customers against zero-day attacks with the industry s most comprehensive
Largest Latin American IT Services provider and an undisputed leader in systems integration, support and IT Outsourcing
 January, 2012 Company Overview Largest Latin American IT Services provider and an undisputed leader in systems integration, support and IT Outsourcing Independent service provider with world-class credentials
January, 2012 Company Overview Largest Latin American IT Services provider and an undisputed leader in systems integration, support and IT Outsourcing Independent service provider with world-class credentials
INVESTOR PRESENTATION
 INVESTOR PRESENTATION Jefferies Technology Conference May 2018 Safe Harbor 2 Safe Harbor Disclaimer This presentation may contain forward-looking information with respect to plans, projections, or future
INVESTOR PRESENTATION Jefferies Technology Conference May 2018 Safe Harbor 2 Safe Harbor Disclaimer This presentation may contain forward-looking information with respect to plans, projections, or future
Data Loss Prevention - Global Market Outlook ( )
 Report Information More information from: https://www.wiseguyreports.com/reports/826969-data-loss-prevention-global-market-outlook-2016-2022 Data Loss Prevention - Global Market Outlook (2016-2022) Report
Report Information More information from: https://www.wiseguyreports.com/reports/826969-data-loss-prevention-global-market-outlook-2016-2022 Data Loss Prevention - Global Market Outlook (2016-2022) Report
New Zealand Government IbM Infrastructure as a service
 New Zealand Government IbM Infrastructure as a service Global leverage / local experts World-class Scalable Agile Flexible Fast Secure What are we offering? IBM New Zealand Government Infrastructure as
New Zealand Government IbM Infrastructure as a service Global leverage / local experts World-class Scalable Agile Flexible Fast Secure What are we offering? IBM New Zealand Government Infrastructure as
ISO/ IEC (ITSM) Certification Roadmap
 ISO/ IEC 20000 (ITSM) Certification Roadmap Rasheed Adegoke June 2013 Outline About First Bank Motivations Definitions ITIL, ISO/IEC 20000 & DIFFERENCES ISO/ IEC 20000 Certification Roadmap First Bank
ISO/ IEC 20000 (ITSM) Certification Roadmap Rasheed Adegoke June 2013 Outline About First Bank Motivations Definitions ITIL, ISO/IEC 20000 & DIFFERENCES ISO/ IEC 20000 Certification Roadmap First Bank
Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges
 Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges An IDC InfoBrief, Sponsored by Cisco March 2018 EXECUTIVE SUMMARY Cloud is a key enabler of
Multicloud is the New Normal Cloud enables Digital Transformation (DX), but more clouds bring more challenges An IDC InfoBrief, Sponsored by Cisco March 2018 EXECUTIVE SUMMARY Cloud is a key enabler of
Global Headquarters: 5 Speen Street Framingham, MA USA P F
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e D a t a c e
Navigating the Clouds Fortifying ITIL for Cloud Governance
 Navigating the Clouds Fortifying ITIL for Cloud Governance DECEMBER 2011 Cloud adoption promises to be an interesting journey for an enterprise with its luring benefits of on-demand models enabling faster
Navigating the Clouds Fortifying ITIL for Cloud Governance DECEMBER 2011 Cloud adoption promises to be an interesting journey for an enterprise with its luring benefits of on-demand models enabling faster
Leading our discussion today
 Defending the Digital Retailer for NRFTech 2014 July 22, 2014 Leading our discussion today Security Leadership and Points of Contact Security and Infrastructure Services Leadership Kevin Richards NA Security
Defending the Digital Retailer for NRFTech 2014 July 22, 2014 Leading our discussion today Security Leadership and Points of Contact Security and Infrastructure Services Leadership Kevin Richards NA Security
Cyber attacks are coming. Amplify your security and risk management protect your data, customers, and future
 Cyber attacks are coming Amplify your security and risk management protect your data, customers, and future Table of contents Clear vulnerabilities Time for MSS Innovations at the SOC level Benefits of
Cyber attacks are coming Amplify your security and risk management protect your data, customers, and future Table of contents Clear vulnerabilities Time for MSS Innovations at the SOC level Benefits of
Organizational Readiness for Digital Transformation
 IVI Community Event Organizational Readiness for Digital Transformation Dr. Marian Carcary June 22nd 2017 Introduction Digital business transformation goes beyond traditional process optimization, to leveraging
IVI Community Event Organizational Readiness for Digital Transformation Dr. Marian Carcary June 22nd 2017 Introduction Digital business transformation goes beyond traditional process optimization, to leveraging
HPE IT Operations Management (ITOM) Thought Leadership Series
 haroldk@theedison.com 89 Fifth Avenue, 7th Floor New York, NY 10003 www.theedison.com HPE IT Operations Management (ITOM) Thought Leadership Series Supporting Transformation from Traditional IT to a Digital
haroldk@theedison.com 89 Fifth Avenue, 7th Floor New York, NY 10003 www.theedison.com HPE IT Operations Management (ITOM) Thought Leadership Series Supporting Transformation from Traditional IT to a Digital
The Little Fuchsia Book of HPE Data Center Solutions
 The Little Fuchsia Book of HPE Data Center Solutions Introduction The data center has become a core focus of the digital economy. It s always been an important, though quiet, IT function, operating behind
The Little Fuchsia Book of HPE Data Center Solutions Introduction The data center has become a core focus of the digital economy. It s always been an important, though quiet, IT function, operating behind
IoT & SCADA Cyber Security Services
 RIOT SOLUTIONS PTY LTD P.O. Box 10087 Adelaide St Brisbane QLD 4000 BRISBANE HEAD OFFICE Level 22, 144 Edward St Brisbane, QLD 4000 T: 1300 744 028 Email: sales@riotsolutions.com.au www.riotsolutions.com.au
RIOT SOLUTIONS PTY LTD P.O. Box 10087 Adelaide St Brisbane QLD 4000 BRISBANE HEAD OFFICE Level 22, 144 Edward St Brisbane, QLD 4000 T: 1300 744 028 Email: sales@riotsolutions.com.au www.riotsolutions.com.au
Paper. Delivering Strong Security in a Hyperconverged Data Center Environment
 Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
WEB-APIs DRIVING DIGITAL INNOVATION
 WEB-APIs DRIVING DIGITAL INNOVATION Importance of Web-APIs Simply put, Web-APIs are the medium to make a company s digital assets consumable to any channel, which has a current or latent need. It helps
WEB-APIs DRIVING DIGITAL INNOVATION Importance of Web-APIs Simply put, Web-APIs are the medium to make a company s digital assets consumable to any channel, which has a current or latent need. It helps
ACQUISITION OF MWR INFOSECURITY ACCELERATED REVENUE GROWTH F-Secure Q3 / 2018
 ACQUISITION OF MWR INFOSECURITY ACCELERATED REVENUE GROWTH F-Secure Q3 / 2018 1 AGENDA Key takeaways from Q3 Key figures Business updates Outlook Financials Supplementary material 2 KEY TAKEAWAYS FROM
ACQUISITION OF MWR INFOSECURITY ACCELERATED REVENUE GROWTH F-Secure Q3 / 2018 1 AGENDA Key takeaways from Q3 Key figures Business updates Outlook Financials Supplementary material 2 KEY TAKEAWAYS FROM
Q1 Revenues. Paris April 26 th, 2017
 2017 Q1 Revenues Paris April 26 th, 2017 Disclaimer This presentation does not contain or constitute an offer of securities for sale or an invitation or inducement to invest in securities in France, the
2017 Q1 Revenues Paris April 26 th, 2017 Disclaimer This presentation does not contain or constitute an offer of securities for sale or an invitation or inducement to invest in securities in France, the
Address C-level Cybersecurity issues to enable and secure Digital transformation
 Address C-level Cybersecurity issues to enable and secure Digital transformation We support cybersecurity transformations with assessments, diagnosis and audits of your organization, the protection mechanisms
Address C-level Cybersecurity issues to enable and secure Digital transformation We support cybersecurity transformations with assessments, diagnosis and audits of your organization, the protection mechanisms
Digital Forensics - Global Market Outlook ( )
 Report Information More information from: https://www.wiseguyreports.com/reports/456593-digital-forensics-global-market-outlook-2015-2022 Digital Forensics - Global Market Outlook (2015-2022) Report /
Report Information More information from: https://www.wiseguyreports.com/reports/456593-digital-forensics-global-market-outlook-2015-2022 Digital Forensics - Global Market Outlook (2015-2022) Report /
2016 Summary Annual Report and Annual Meeting Documents
 2016 Summary Annual Report and 2017 Annual Meeting Documents To Our Shareholders We enter 2017 with confidence in a bright future ahead for CenturyLink. We are clear in our approach to the market: we
2016 Summary Annual Report and 2017 Annual Meeting Documents To Our Shareholders We enter 2017 with confidence in a bright future ahead for CenturyLink. We are clear in our approach to the market: we
M2M device connections and revenue: worldwide forecast
 Research Forecast Report M2M device connections and revenue: worldwide forecast 2013 2023 August 2013 Morgan Mullooly and Steve Hilton 2 Contents Slide no. 5. About this report 6. Executive summary 7.
Research Forecast Report M2M device connections and revenue: worldwide forecast 2013 2023 August 2013 Morgan Mullooly and Steve Hilton 2 Contents Slide no. 5. About this report 6. Executive summary 7.
Cloud Going Mainstream All Are Trying, Some Are Benefiting; Few Are Maximizing Value
 All Are Trying, Some Are Benefiting; Few Are Maximizing Value Latin America Findings September 2016 Executive Summary Cloud adoption has increased 49% from last year, with 78% of companies in Latin America
All Are Trying, Some Are Benefiting; Few Are Maximizing Value Latin America Findings September 2016 Executive Summary Cloud adoption has increased 49% from last year, with 78% of companies in Latin America
Trend Micro Professional Services Partner Program
 Trend Micro Professional Services Partner Program PROGRAM OVERVIEW The Trend Micro Partner Program provides professional services companies with the certification, training, technical support and access
Trend Micro Professional Services Partner Program PROGRAM OVERVIEW The Trend Micro Partner Program provides professional services companies with the certification, training, technical support and access
MITIGATE CYBER ATTACK RISK
 SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
Samu Konttinen, CEO Q4 / 2017 CORPORATE SECURITY REVENUE GROWTH ACCELERATED TO 16%
 Samu Konttinen, CEO Q4 / 2017 CORPORATE SECURITY REVENUE GROWTH ACCELERATED TO 16% 1 AGENDA Key takeaways from Q4 Key figures Business review for 2017 Outlook 2018 Outlook for 2018-2021 Financials FAQ
Samu Konttinen, CEO Q4 / 2017 CORPORATE SECURITY REVENUE GROWTH ACCELERATED TO 16% 1 AGENDA Key takeaways from Q4 Key figures Business review for 2017 Outlook 2018 Outlook for 2018-2021 Financials FAQ
Enterprise)Cloud) Computing)Unlocks)Deep) Strategic)Value)Through) Increased)Business)Agility:) LEADING ADOPTERS REAP MORE BENEFITS
 Enterprise)Cloud) Computing)Unlocks)Deep) Strategic)Value)Through) Increased)Business)Agility:) LEADING ADOPTERS REAP MORE BENEFITS Business Benefits of Public Cloud More Cloud, More Business Value 79%
Enterprise)Cloud) Computing)Unlocks)Deep) Strategic)Value)Through) Increased)Business)Agility:) LEADING ADOPTERS REAP MORE BENEFITS Business Benefits of Public Cloud More Cloud, More Business Value 79%
Software Defined Storage Market Research Report - Global Forecast 2022
 Report Information More information from: https://www.marketresearchfuture.com/reports/1958 Software Defined Storage Market Research Report - Global Forecast 2022 Report / Search Code: MRFR/SEM/1426-HCRR
Report Information More information from: https://www.marketresearchfuture.com/reports/1958 Software Defined Storage Market Research Report - Global Forecast 2022 Report / Search Code: MRFR/SEM/1426-HCRR
Six Sigma in the datacenter drives a zero-defects culture
 Six Sigma in the datacenter drives a zero-defects culture Situation Like many IT organizations, Microsoft IT wants to keep its global infrastructure available at all times. Scope, scale, and an environment
Six Sigma in the datacenter drives a zero-defects culture Situation Like many IT organizations, Microsoft IT wants to keep its global infrastructure available at all times. Scope, scale, and an environment
