Network Architectural Design for Cybersecurity in a Virtual World
|
|
|
- Magnus Fleming
- 6 years ago
- Views:
Transcription
1 Network Architectural Design for Cybersecurity in a Virtual World Standards Certification Education & Training Publishing Conferences & Exhibits Kenneth Frische aesolutions 2016 ISA Water / Wastewater and Automatic Controls Symposium August 2-4, 2016 Orlando, Florida, USA
2 Kenneth Frische Industrial Cyber Security Principal at aesolutions 28 years of IT & OT experience Contributed to NIST and ISA cyber security standards Titles / credentials? School & degree? Aug 2-4, 2015 Orlando, Florida, USA 2
3 Presentation Outline NIST and ISA Series Cybersecurity Standards (quick view) OT Cyber Assessment (to ISA/IEC Standards) What If? Deliverable: Network Architectural Design Deliverable: Zones and Conduits Model We virtualize some of the devices in the Network Architectural Design Review issues Review Options Documentation Fixing the Zones and Conduits Model Questions and Discussion Aug 2-4, 2015 Orlando, Florida, USA 3
4 NIST Cybersecurity Framework Common Terminology Mapping your CSMS Aug 2-4, 2015 Orlando, Florida, USA 4
5 ISA Series Cybersecurity Standards Aug 2-4, 2015 Orlando, Florida, USA 5
6 Presentation Scope NIST Cybersecurity Framework: Protect and Recover ISA Standards ( ): Security Risk Assessment and System Design Aug 2-4, 2015 Orlando, Florida, USA 6
7 Sample Physical Network Architecture Level 4+ Level 3.5 DMZ Historian Antivirus Patch Mgmt Web Reporting Workstations Domain Controllers Supervisory Control Network (Levels 2 & 3) Development HMI Operator Stations Database Server Application Server Terminal Server Level 1.5 DMZ I/O Server(s) Control Network (Levels 0 & 1) Non TCP/IP based (serial) PLC Network PLCs Aug 2-4, 2015 Orlando, Florida, USA 7
8 Zones Level 4+ Level 3.5 DMZ Historian Antivirus Patch Mgmt Web Reporting Workstations Domain Controllers Supervisory Control Network (Levels 2 & 3) Development HMI Operator Stations Database Server Application Server Terminal Server Level 1.5 DMZ I/O Server(s) Control Network (Levels 0 & 1) Non TCP/IP based (serial) PLC Network PLCs Aug 2-4, 2015 Orlando, Florida, USA 8
9 Challenge Scenario: Decision made to virtualize all of the OT servers - IT currently manages the Domain Controllers in the OT DMZ - Database Server only needs data flow to the Application Server How can we apply the NIST Framework and the ISA Series Zones and Conduits model to the architectural design of our process control systems so as to enable safe, secure, and high performance operations? Aug 2-4, 2015 Orlando, Florida, USA 9
10 Standards and Best Practices (a few of them anyway) Network Architecture: DMZ between Purdue Model levels Zones and Conduits Model VM Management and Architecture: Locate Redundant VMs on separate Hardware Separation of Duties (IT vs OT); separate hosts Separation by Purdue Model and Zone Document the VM Architectures Aug 2-4, 2015 Orlando, Florida, USA 10
11 VM Architecture - what is possible? VM Host Domain Controller 1 VM ISA Level 3.5 Level 4+ Historian VM Antivirus VM Patch Mgmt VM Web Reporting VM Database Server VM Application Server VM ISA Level 2 Terminal Server VM I/O Server & Store and Forward VM ISA Level 1.5 Aug 2-4, 2015 Orlando, Florida, USA 11
12 VM Architecture A better way Level 4+ VM Host Domain Controller 1 VM ISA Level 3.5 Historian VM VM Host Antivirus VM Patch Mgmt VM Web Reporting VM VM Host Database Server VM Application Server VM Terminal Server VM ISA Level 2 VM Host I/O Server & Store and Forward VM ISA Level 1.5 Aug 2-4, 2015 Orlando, Florida, USA 12
13 VM Architecture - Redundancy Aug 2-4, 2015 Orlando, Florida, USA 13
14 VM Architecture Serial Networks Aug 2-4, 2015 Orlando, Florida, USA 14
15 Our Combined Architectural Design Level 4+ Level 3.5 DMZ Workstations Supervisory Control Network (Level 2 & 3) Level 1.5 DMZ I/O Server(s) Development HMI Operator Stations Control Network Non TCP/IP based (serial) PLC Network Aug 2-4, 2015 Orlando, Florida, USA 15 PLCs
16 Remember.every environment is different Aug 2-4, 2015 Orlando, Florida, USA
17 Questions and Discussion Kenneth Frische ( frish ) has over 28 years of experience in providing IT & OT Solutions for Military, Oil & Gas, Pharma, Food & Beverage, Packaging, Chemical, Water/Wastewater, Discrete Manufacturing, Supply Chain Logistics, and Correctional Facilities. From hands-on coding to management and consulting, Kenneth Frische has worn many hats to include: IT Director, Solutions Architect, Enterprise Architect, Project Manager, Req/Tech Spec Writer, and Programmer Lead. Kenneth.Frische@aesolns.com His domain expertise includes Process Control and HMI Systems Design and Development, MES integration, Database Management and Design, Business Intelligence / Data Analytics, Business Process Improvement, and Data Warehousing. Kenneth Frische has contributed to both NIST and ISA Cyber Security standards and currently provides Cyber Risk Assessment, Solutions Design services, cyber consulting, and ISA Series training as a member of the Cyber Security Services department at aesolutions. Aug 2-4, 2015 Orlando, Florida, USA 17
18 Discussion Example #1 Aug 2-4, 2015 Orlando, Florida, USA 18
Use Case: Data Diode Cybersecurity Implementation Protects Water Utility OT Network
 Use Case: Data Diode Cybersecurity Implementation Protects Water Utility OT Network Four Step Process to Network Cybersecurity & Providing Remote User/Data Access Standards Certification Education & Training
Use Case: Data Diode Cybersecurity Implementation Protects Water Utility OT Network Four Step Process to Network Cybersecurity & Providing Remote User/Data Access Standards Certification Education & Training
Centralized Control System Architecture
 Centralized Control System Architecture Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Hassan Ajami, PE CAP Anil Gosine 2016 ISA Water / Wastewater and Automatic
Centralized Control System Architecture Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Hassan Ajami, PE CAP Anil Gosine 2016 ISA Water / Wastewater and Automatic
Municipality Moves SCADA System from Desktop Computers to Terminal Services
 Municipality Moves SCADA System from Desktop Computers to Terminal Services Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Bosko Bob Loncar 2014 ISA Water / Wastewater
Municipality Moves SCADA System from Desktop Computers to Terminal Services Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Bosko Bob Loncar 2014 ISA Water / Wastewater
Cybersecurity. Can Standards Bring Clarity from the Confusion? Speaker: David Doggett
 Cybersecurity Can Standards Bring Clarity from the Confusion? Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: David Doggett 2014 ISA Water / Wastewater and Automatic
Cybersecurity Can Standards Bring Clarity from the Confusion? Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: David Doggett 2014 ISA Water / Wastewater and Automatic
ISA99 - Industrial Automation and Controls Systems Security
 ISA99 - Industrial Automation and Controls Systems Security Committee Summary and Activity Update Standards Certification Education & Training Publishing Conferences & Exhibits September 2016 Copyright
ISA99 - Industrial Automation and Controls Systems Security Committee Summary and Activity Update Standards Certification Education & Training Publishing Conferences & Exhibits September 2016 Copyright
An Overview of ISA-99 & Cyber Security for the Water or Wastewater Specialist
 An Overview of ISA-99 & Cyber Security for the Water or Wastewater Specialist Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Bryan L. Singer, CISM, CISSP, CAP
An Overview of ISA-99 & Cyber Security for the Water or Wastewater Specialist Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Bryan L. Singer, CISM, CISSP, CAP
How ISA Technical Divisions Benefited my Career
 How ISA Technical Divisions Benefited my Career also known as. Introduction to ISA Technical Divisions Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Graham Nasby
How ISA Technical Divisions Benefited my Career also known as. Introduction to ISA Technical Divisions Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Graham Nasby
SCADA Upgrades to Otay Water Treatment Plant
 SCADA Upgrades to Otay Water Treatment Plant Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Dr. Noune Garounts 2012 ISA Water & Wastewater and Automatic Controls
SCADA Upgrades to Otay Water Treatment Plant Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Dr. Noune Garounts 2012 ISA Water & Wastewater and Automatic Controls
ISA99 - Industrial Automation and Controls Systems Security
 ISA99 - Industrial Automation and Controls Systems Security Committee Summary and Activity Update Standards Certification Education & Training Publishing Conferences & Exhibits February 2018 Copyright
ISA99 - Industrial Automation and Controls Systems Security Committee Summary and Activity Update Standards Certification Education & Training Publishing Conferences & Exhibits February 2018 Copyright
SCADA Security at. City of Guelph Water Services
 SCADA Security at City of Guelph Water Services Graham Nasby, P.Eng., PMP, CAP Water SCADA & Security Specialist City of Guelph Water Services 1 1 Rationale Our Reliance on SCADA for Operations & Compliance
SCADA Security at City of Guelph Water Services Graham Nasby, P.Eng., PMP, CAP Water SCADA & Security Specialist City of Guelph Water Services 1 1 Rationale Our Reliance on SCADA for Operations & Compliance
Introduction to ICS Security
 Introduction to ICS Security Design. Build. Protect. Presented by Jack D. Oden, June 1, 2018 ISSA Mid-Atlantic Information Security Conference, Rockville, MD Copyright 2018 Parsons Federal 2018 Critical
Introduction to ICS Security Design. Build. Protect. Presented by Jack D. Oden, June 1, 2018 ISSA Mid-Atlantic Information Security Conference, Rockville, MD Copyright 2018 Parsons Federal 2018 Critical
DNP3 for Water Systems
 DNP3 for Water Systems United Water New Jersey Use Case Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Keith Kolkebeck 2015 ISA Water / Wastewater and Automatic
DNP3 for Water Systems United Water New Jersey Use Case Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Keith Kolkebeck 2015 ISA Water / Wastewater and Automatic
Data Diode Cybersecurity Implementation Protects SCADA Network and Facilitates Transfer of Operations Information to Business Users
 Data Diode Cybersecurity Implementation Protects SCADA Network and Facilitates Transfer of Operations Information to Business Users Standards Certification Education & Training Publishing Conferences &
Data Diode Cybersecurity Implementation Protects SCADA Network and Facilitates Transfer of Operations Information to Business Users Standards Certification Education & Training Publishing Conferences &
Getting the Most from Your SCADA Data
 Getting the Most from Your SCADA Data Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Emile Richard 2015 ISA Water / Wastewater and Automatic Controls Symposium
Getting the Most from Your SCADA Data Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Emile Richard 2015 ISA Water / Wastewater and Automatic Controls Symposium
How can I use ISA/IEC (Formally ISA 99) to minimize risk? Standards Certification Education & Training Publishing Conferences & Exhibits
 How can I use ISA/IEC- 62443 (Formally ISA 99) to minimize risk? Standards Certification Education & Training Publishing Conferences & Exhibits What is ISA 62443? A series of ISA standards that addresses
How can I use ISA/IEC- 62443 (Formally ISA 99) to minimize risk? Standards Certification Education & Training Publishing Conferences & Exhibits What is ISA 62443? A series of ISA standards that addresses
Securing Industrial Control Systems
 L OCKHEED MARTIN Whitepaper Securing Industrial Control Systems The Basics Abstract Critical infrastructure industries such as electrical power, oil and gas, chemical, and transportation face a daunting
L OCKHEED MARTIN Whitepaper Securing Industrial Control Systems The Basics Abstract Critical infrastructure industries such as electrical power, oil and gas, chemical, and transportation face a daunting
Cybersecurity Training
 Standards Certification Education & Training Publishing Conferences & Exhibits Cybersecurity Training Safeguarding industrial automation and control systems www.isa.org/cybetrn Expert-led training with
Standards Certification Education & Training Publishing Conferences & Exhibits Cybersecurity Training Safeguarding industrial automation and control systems www.isa.org/cybetrn Expert-led training with
The Water Sector Approach to Cybersecurity
 The Water Sector Approach to Cybersecurity Standards Certification Education & Training Publishing Conferences & Exhibits Kevin M. Morley, PhD American Water Works Association 2016 ISA Water / Wastewater
The Water Sector Approach to Cybersecurity Standards Certification Education & Training Publishing Conferences & Exhibits Kevin M. Morley, PhD American Water Works Association 2016 ISA Water / Wastewater
Demystifying Cyber Attacks on ICS:
 Demystifying Cyber Attacks on ICS: Standards Certification Education & Training Publishing Conferences & Exhibits How They Work and How to Use Engineered and Cyber Layer of Protections Put title Here Speaker:
Demystifying Cyber Attacks on ICS: Standards Certification Education & Training Publishing Conferences & Exhibits How They Work and How to Use Engineered and Cyber Layer of Protections Put title Here Speaker:
Virtualizing SCADA. Improving Control System Reliability with proven IT Technology. Speakers: Jason Hamlin Carter Farley
 Virtualizing SCADA Improving Control System Reliability with proven IT Technology Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Jason Hamlin Carter Farley 2014
Virtualizing SCADA Improving Control System Reliability with proven IT Technology Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Jason Hamlin Carter Farley 2014
Comprehensive Networking Solutions
 Comprehensive Networking Solutions End to End Networking Solutions in the Water and Wastewater Sectors Standards Certification Education & Training Publishing Conferences & Exhibits Aug 5-7, 2014 Orlando,
Comprehensive Networking Solutions End to End Networking Solutions in the Water and Wastewater Sectors Standards Certification Education & Training Publishing Conferences & Exhibits Aug 5-7, 2014 Orlando,
Mike Spear, Ops Leader Greg Maciel, Cyber Director INDUSTRIAL CYBER SECURITY PROGRAMS
 Mike Spear, Ops Leader Greg Maciel, Cyber Director INDUSTRIAL CYBER SECURITY PROGRAMS Can You Answer These Questions? 1 What s my company s exposure to the latest industrial cyber threat? Are my plants
Mike Spear, Ops Leader Greg Maciel, Cyber Director INDUSTRIAL CYBER SECURITY PROGRAMS Can You Answer These Questions? 1 What s my company s exposure to the latest industrial cyber threat? Are my plants
SCADA Security - how to safely audit and protect Industrial Control Systems?
 SCADA Security - how to safely audit and protect Industrial Control Systems? Mariusz Stawowski, Ph.D. CISSP, CEH Technical Director, CLICO CLICO Competence Center +35 security and networking experts Biggest
SCADA Security - how to safely audit and protect Industrial Control Systems? Mariusz Stawowski, Ph.D. CISSP, CEH Technical Director, CLICO CLICO Competence Center +35 security and networking experts Biggest
Cyber security - why and how
 Cyber security - why and how Frankfurt, 14 June 2018 ACHEMA Cyber Attack Continuum Prevent, Detect and Respond Pierre Paterni Rockwell Automation, Connected Services EMEA Business Development Manager PUBLIC
Cyber security - why and how Frankfurt, 14 June 2018 ACHEMA Cyber Attack Continuum Prevent, Detect and Respond Pierre Paterni Rockwell Automation, Connected Services EMEA Business Development Manager PUBLIC
Cybersecurity Framework Manufacturing Profile
 Cybersecurity Framework Manufacturing Profile Keith Stouffer Project Leader, Cybersecurity for Smart Manufacturing Systems Engineering Lab, NIST National Institute of Standards and Technology (NIST) NIST
Cybersecurity Framework Manufacturing Profile Keith Stouffer Project Leader, Cybersecurity for Smart Manufacturing Systems Engineering Lab, NIST National Institute of Standards and Technology (NIST) NIST
The Industrial Internet of Things
 The Industrial Internet of Things Presentation and Agenda How ICS has Evolved. Changing Landscapes of ICS 2013 End User Cyber Security Survey. Gaps and Recommendations About Your Presenter Previous: Irving
The Industrial Internet of Things Presentation and Agenda How ICS has Evolved. Changing Landscapes of ICS 2013 End User Cyber Security Survey. Gaps and Recommendations About Your Presenter Previous: Irving
Security Issues and Best Practices for Water Facilities
 Security Issues and Best Practices for Water Facilities Standards Certification Jeff Hayes Business Development Manager Beijer Electronics Education & Training Publishing Conferences & Exhibits 2013 ISA
Security Issues and Best Practices for Water Facilities Standards Certification Jeff Hayes Business Development Manager Beijer Electronics Education & Training Publishing Conferences & Exhibits 2013 ISA
TARGET, PROTECT. your cyber vulnerabilities
 Standards Certification Education & Training Publishing Conferences & Exhibits TARGET, PROTECT New from ISA! your cyber vulnerabilities your critical control systems System Wide Awareness Training Industrial
Standards Certification Education & Training Publishing Conferences & Exhibits TARGET, PROTECT New from ISA! your cyber vulnerabilities your critical control systems System Wide Awareness Training Industrial
Just How Vulnerable is Your Safety System?
 Theme 3: Cyber Security Just How Vulnerable is Your Safety System? Colin Easton MSc, CEng, FInstMC, MIET, ISA Senior Member TUV Rhienland FS Senior Expert PHRA & SIS 6 th July 2017 1 Safety System Security
Theme 3: Cyber Security Just How Vulnerable is Your Safety System? Colin Easton MSc, CEng, FInstMC, MIET, ISA Senior Member TUV Rhienland FS Senior Expert PHRA & SIS 6 th July 2017 1 Safety System Security
Safdar Akhtar, Cyber Director Sema Tutucu, Ops Leader 27 September CYBER SECURITY PROGRAM: Policies to Controls
 Safdar Akhtar, Cyber Director Sema Tutucu, Ops Leader 27 September 2017 CYBER SECURITY PROGRAM: Policies to Controls Can You Answer These Questions? 1 What s my company s exposure to the latest industrial
Safdar Akhtar, Cyber Director Sema Tutucu, Ops Leader 27 September 2017 CYBER SECURITY PROGRAM: Policies to Controls Can You Answer These Questions? 1 What s my company s exposure to the latest industrial
Sneak Peek at the ISA112 SCADA Systems Standard
 Sneak Peek at the ISA112 SCADA Systems Standard April 2017 Standards Certification Education & Training Publishing Conferences & Exhibits Graham Nasby ISA112 committee co-chair What is ISA112? ISA112 is
Sneak Peek at the ISA112 SCADA Systems Standard April 2017 Standards Certification Education & Training Publishing Conferences & Exhibits Graham Nasby ISA112 committee co-chair What is ISA112? ISA112 is
IE156: ICS410: ICS/SCADA Security Essentials
 IE156: ICS410: ICS/SCADA Security Essentials IE156 Rev.001 CMCT COURSE OUTLINE Page 1 of 6 Training Description: In this five-day intensive training, participants will develop and reinforce a common language
IE156: ICS410: ICS/SCADA Security Essentials IE156 Rev.001 CMCT COURSE OUTLINE Page 1 of 6 Training Description: In this five-day intensive training, participants will develop and reinforce a common language
Who Goes There? Access Control in Water/Wastewater Siemens AG All Rights Reserved. siemens.com/ruggedcom
 WEAT Webinar Who Goes There? Access Control in Water/Wastewater Siemens AG 2018. siemens.com/ruggedcom ACCESS CONTROL WEBINAR TABLE OF CONTENTS TOPIC Why Access Control? Risks If Not Used Factors of Authentication
WEAT Webinar Who Goes There? Access Control in Water/Wastewater Siemens AG 2018. siemens.com/ruggedcom ACCESS CONTROL WEBINAR TABLE OF CONTENTS TOPIC Why Access Control? Risks If Not Used Factors of Authentication
SCADA Control and Monitoring Of Groundwater Remediation Facilities: Past, Present and Planning For the Future
 SCADA Control and Monitoring Of Groundwater Remediation Facilities: Past, Present and Planning For the Future Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Obadiah
SCADA Control and Monitoring Of Groundwater Remediation Facilities: Past, Present and Planning For the Future Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Obadiah
FLUID COMPUTING. ARC FORUM, India Ricky Watts Director of Industrial Solutions, Wind River IN A SOFTWARE-DEFINED WORLD
 FLUID COMPUTING IN A SOFTWARE-DEFINED WORLD ARC FORUM, India Ricky Watts Director of Industrial Solutions, Wind River Chemical Sector Commercial Building Sector Communications Sector Critical Manufacturing
FLUID COMPUTING IN A SOFTWARE-DEFINED WORLD ARC FORUM, India Ricky Watts Director of Industrial Solutions, Wind River Chemical Sector Commercial Building Sector Communications Sector Critical Manufacturing
System Wide Awareness Training. your cyber vulnerabilities. your critical control systems
 Standards Certification Education & Training Publishing Conferences & Exhibits your cyber vulnerabilities your critical control systems Early- Bird Discount Save $250 when you register by 15 December!
Standards Certification Education & Training Publishing Conferences & Exhibits your cyber vulnerabilities your critical control systems Early- Bird Discount Save $250 when you register by 15 December!
Reinventing the Role of the SCADA Historian
 Reinventing the Role of the SCADA Historian Distributed Redundancy, Centralized Access Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Blair Sooley, M. B. A., P.
Reinventing the Role of the SCADA Historian Distributed Redundancy, Centralized Access Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Blair Sooley, M. B. A., P.
OSIsoft PI System Usage For Academia
 OSIsoft PI System Usage For Academia Jim O Rourke, Academic Acct. Mgr. OSIsoft jorourke@osisoft.com 281-433-3399 Mike Mihuc, Academic Principal OSIsoft mmihuc@osisoft.com 412-779-6804 March 17, 2016 We
OSIsoft PI System Usage For Academia Jim O Rourke, Academic Acct. Mgr. OSIsoft jorourke@osisoft.com 281-433-3399 Mike Mihuc, Academic Principal OSIsoft mmihuc@osisoft.com 412-779-6804 March 17, 2016 We
No compromises for secure SCADA Communications even over 3rd Party Networks
 No compromises for secure SCADA Communications even over 3rd Party Networks The Gamble of Using ISP Private Networks How to Stack the Odds in Your Favor Standards Certification Education & Training Publishing
No compromises for secure SCADA Communications even over 3rd Party Networks The Gamble of Using ISP Private Networks How to Stack the Odds in Your Favor Standards Certification Education & Training Publishing
control system vulnerabilities > analysis of 5 years of field data
 control system vulnerabilities > analysis of 5 years of field data Jonathan Pollet, CISSP, CAP, PCIP Red Tiger Security [on behalf of the DHS CSSP program - contract #240704] 1 Jonathan Pollet CISSP, PCIP,
control system vulnerabilities > analysis of 5 years of field data Jonathan Pollet, CISSP, CAP, PCIP Red Tiger Security [on behalf of the DHS CSSP program - contract #240704] 1 Jonathan Pollet CISSP, PCIP,
2014 Software Global Client Conference
 WW HMI SCADA-10 Best practices for distributed SCADA Stan DeVries Senior Director Solutions Architecture What is Distributed SCADA? It s much more than a distributed architecture (SCADA always has this)
WW HMI SCADA-10 Best practices for distributed SCADA Stan DeVries Senior Director Solutions Architecture What is Distributed SCADA? It s much more than a distributed architecture (SCADA always has this)
ICS/SCADA Cybersecurity and IT Cybersecurity: Comparing Apples and Oranges
 8 December 2017 HITCON PACIFIC 2017 ICS/SCADA Cybersecurity and IT Cybersecurity: Comparing Apples and Oranges Presented by David Ong CEO of Attila Cybertech Quote by Donald Rumsfeld But there are also
8 December 2017 HITCON PACIFIC 2017 ICS/SCADA Cybersecurity and IT Cybersecurity: Comparing Apples and Oranges Presented by David Ong CEO of Attila Cybertech Quote by Donald Rumsfeld But there are also
Benefits of a SCADA Master Plan for Utilities
 Benefits of a SCADA Master for Utilities Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Manoj Yegnaraman, Carollo Engineers, Inc. Norman Anderson, Polk County
Benefits of a SCADA Master for Utilities Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Manoj Yegnaraman, Carollo Engineers, Inc. Norman Anderson, Polk County
Secure Water Treatment (SWaT) Testbed
 Secure Water Treatment (SWaT) Testbed Version: 4.2 Last updated: 5 October 2018 Contact information: itrust@sutd.edu.sg Website: https://itrust.sutd.edu.sg/ INTRODUCTION Aim This documentation provides
Secure Water Treatment (SWaT) Testbed Version: 4.2 Last updated: 5 October 2018 Contact information: itrust@sutd.edu.sg Website: https://itrust.sutd.edu.sg/ INTRODUCTION Aim This documentation provides
Cyber Security Requirements for Electronic Safety and Security
 This document is to provide suggested language to address cyber security elements as they may apply to physical and electronic security projects. Security consultants and specifiers should consider this
This document is to provide suggested language to address cyber security elements as they may apply to physical and electronic security projects. Security consultants and specifiers should consider this
Future Challenges and Changes in Industrial Cybersecurity. Sid Snitkin VP Cybersecurity Services ARC Advisory Group
 Future Challenges and Changes in Industrial Cybersecurity Sid Snitkin VP Cybersecurity Services ARC Advisory Group Srsnitkin@ARCweb.com Agenda Industrial Cybersecurity Today Scope, Assumptions and Strategies
Future Challenges and Changes in Industrial Cybersecurity Sid Snitkin VP Cybersecurity Services ARC Advisory Group Srsnitkin@ARCweb.com Agenda Industrial Cybersecurity Today Scope, Assumptions and Strategies
Top 10 ICS Cybersecurity Problems Observed in Critical Infrastructure
 SESSION ID: SBX1-R07 Top 10 ICS Cybersecurity Problems Observed in Critical Infrastructure Bryan Hatton Cyber Security Researcher Idaho National Laboratory In support of DHS ICS-CERT @phaktor 16 Critical
SESSION ID: SBX1-R07 Top 10 ICS Cybersecurity Problems Observed in Critical Infrastructure Bryan Hatton Cyber Security Researcher Idaho National Laboratory In support of DHS ICS-CERT @phaktor 16 Critical
Using ANSI/ISA-99 Standards to Improve Control System Security
 Tofino Security White Paper Version 1.1 Published May 2012 Using ANSI/ISA-99 Standards to Improve Control System Security Contents 1. Executive Summary... 1 2. Why the Push for Productivity has degraded
Tofino Security White Paper Version 1.1 Published May 2012 Using ANSI/ISA-99 Standards to Improve Control System Security Contents 1. Executive Summary... 1 2. Why the Push for Productivity has degraded
SCADA System Specification. Vantage Pipeline Project # May 2013
 SCADA System Specification Vantage Pipeline Project #201011 May 2013 Revision 0 Issued for Approval May 24, 2013 TABLE OF CONTENTS REVISION HISTORY:...2 1 PROJECT OVERVIEW...3 2 SCOPE AND PURPOSE...4 3
SCADA System Specification Vantage Pipeline Project #201011 May 2013 Revision 0 Issued for Approval May 24, 2013 TABLE OF CONTENTS REVISION HISTORY:...2 1 PROJECT OVERVIEW...3 2 SCOPE AND PURPOSE...4 3
Lowering Lifecycle Costs
 Lowering Lifecycle Costs with Intelligent Motor Control Centers Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Presented and Authored by Jeff M. Miller, PE, ENV
Lowering Lifecycle Costs with Intelligent Motor Control Centers Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Presented and Authored by Jeff M. Miller, PE, ENV
SIMIT Simulation. Optimize your plant, increase your competitiveness
 SIMIT Simulation Optimize your plant, increase your competitiveness Sustainable creation of customer value and satisfaction Purposes Virtual commissioning (VCO) Test the original automation software by
SIMIT Simulation Optimize your plant, increase your competitiveness Sustainable creation of customer value and satisfaction Purposes Virtual commissioning (VCO) Test the original automation software by
ABB Ability Cyber Security Services Protection against cyber threats takes ability
 ABB Ability Cyber Security Services Protection against cyber threats takes ability In today s business environment, cyber security is critical for ensuring reliability of automation and control systems.
ABB Ability Cyber Security Services Protection against cyber threats takes ability In today s business environment, cyber security is critical for ensuring reliability of automation and control systems.
Guide to Industrial Control Systems (ICS) Security
 Special Publication 800-82 SECOND PUBLIC DRAFT Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and other
Special Publication 800-82 SECOND PUBLIC DRAFT Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and other
Practical SCADA Cyber Security Lifecycle Steps
 Practical SCADA Cyber Security Lifecycle Steps Standards Certification Jim McGlone CMO, Kenexis Education & Training Publishing Conferences & Exhibits Bio Jim McGlone, CMO, Kenexis GICSP ISA Safety & Security
Practical SCADA Cyber Security Lifecycle Steps Standards Certification Jim McGlone CMO, Kenexis Education & Training Publishing Conferences & Exhibits Bio Jim McGlone, CMO, Kenexis GICSP ISA Safety & Security
*** THIS DOCUMENT IS CLASSIFIED FOR PUBLIC ACCESS ***
 Introduction and Bio CyberSecurity Defined CyberSecurity Risks NIST CyberSecurity Framework References *** THIS DOCUMENT IS CLASSIFIED FOR PUBLIC ACCESS *** Chapter 3. Framework Implementation Relationship
Introduction and Bio CyberSecurity Defined CyberSecurity Risks NIST CyberSecurity Framework References *** THIS DOCUMENT IS CLASSIFIED FOR PUBLIC ACCESS *** Chapter 3. Framework Implementation Relationship
Maarten Oosterink for PPA 2010 Delft, Vendor Requirements. Process Control Domain - Security Requirements for Vendors
 Maarten Oosterink for PPA 2010 Delft, 11-03-2010 Vendor Requirements Process Control Domain - Security Requirements for Vendors Contents Purpose, Scope and Audience Development process Contents of WIB
Maarten Oosterink for PPA 2010 Delft, 11-03-2010 Vendor Requirements Process Control Domain - Security Requirements for Vendors Contents Purpose, Scope and Audience Development process Contents of WIB
NCCoE TRUSTED CLOUD: A SECURE SOLUTION
 SESSION ID: SPO1-W14 NCCoE TRUSTED CLOUD: A SECURE SOLUTION Donna Dodson Associate Director Chief Cyber Security Advisor of the Information Technology Laboratory, Chief Cybersecurity Advisor for the National
SESSION ID: SPO1-W14 NCCoE TRUSTED CLOUD: A SECURE SOLUTION Donna Dodson Associate Director Chief Cyber Security Advisor of the Information Technology Laboratory, Chief Cybersecurity Advisor for the National
Wireless Mesh Infrastructure Networks for Supporting Water Districts Data, SCADA and Video Requirements
 Wireless Mesh Infrastructure Networks for Supporting Water Districts Data, SCADA and Video Requirements Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Matthew Selby
Wireless Mesh Infrastructure Networks for Supporting Water Districts Data, SCADA and Video Requirements Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: Matthew Selby
Securing Plant Operation The Important Steps
 Stevens Point, WI Securing Plant Operation The Important Steps September 24, 2012 Slide 1 Purpose of this Presentation During this presentation, we will introduce the subject of securing your control system
Stevens Point, WI Securing Plant Operation The Important Steps September 24, 2012 Slide 1 Purpose of this Presentation During this presentation, we will introduce the subject of securing your control system
HMI Development. Techniques for Reduction of Development Time. Speakers: Lucas Jordan, PE
 HMI Development Techniques for Reduction of Development Time Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Lucas Jordan, PE 2014 ISA Water / Wastewater and Automatic
HMI Development Techniques for Reduction of Development Time Standards Certification Education & Training Publishing Conferences & Exhibits Speakers: Lucas Jordan, PE 2014 ISA Water / Wastewater and Automatic
Cybersecurity: Considerations for Internal Audit. Gina Gondron Senior Manager Frazier & Deeter Geek Week August 10, 2016
 Cybersecurity: Considerations for Internal Audit Gina Gondron Senior Manager Frazier & Deeter Geek Week August 10, 2016 Agenda Key Risks Incorporating Internal Audit Resources Questions 2 San Francisco
Cybersecurity: Considerations for Internal Audit Gina Gondron Senior Manager Frazier & Deeter Geek Week August 10, 2016 Agenda Key Risks Incorporating Internal Audit Resources Questions 2 San Francisco
Project Life Cycle Support (SCADA)
 Project Life Cycle Support (SCADA) Texas Association of Clean Water Agencies Garland, TX March 26, 2010 Yehuda Morag CH2M HILL, Austin TX WBG030410171936AUS Agenda Introduction to SCADA Utility Managers
Project Life Cycle Support (SCADA) Texas Association of Clean Water Agencies Garland, TX March 26, 2010 Yehuda Morag CH2M HILL, Austin TX WBG030410171936AUS Agenda Introduction to SCADA Utility Managers
ICS Security. Trends, Issues, and New Standards. Speaker: David Mattes CTO, Asguard Networks
 ICS Security Trends, Issues, and New Standards Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: David Mattes CTO, Asguard Networks 2013 ISA Water / Wastewater and
ICS Security Trends, Issues, and New Standards Standards Certification Education & Training Publishing Conferences & Exhibits Speaker: David Mattes CTO, Asguard Networks 2013 ISA Water / Wastewater and
Best Practices to Modernize and Simplify SCADA Systems
 Best Practices to Modernize and Simplify SCADA Systems John Fryer, Senior Director, Industry Solutions Brought to you by 1 Todays Speakers David Greenfield Moderator Director of Content/Editor-in-Chief
Best Practices to Modernize and Simplify SCADA Systems John Fryer, Senior Director, Industry Solutions Brought to you by 1 Todays Speakers David Greenfield Moderator Director of Content/Editor-in-Chief
T14 - Network, Storage and Virtualization Technologies for Industrial Automation. Copyright 2012 Rockwell Automation, Inc. All rights reserved.
 T14 - Network, Storage and Virtualization Technologies for Industrial Automation Rev 5058-CO900C Copyright 2012 Rockwell Automation, Inc. All rights reserved. 2 Agenda Overview & Drivers Virtualization
T14 - Network, Storage and Virtualization Technologies for Industrial Automation Rev 5058-CO900C Copyright 2012 Rockwell Automation, Inc. All rights reserved. 2 Agenda Overview & Drivers Virtualization
IoT & SCADA Cyber Security Services
 RIOT SOLUTIONS PTY LTD P.O. Box 10087 Adelaide St Brisbane QLD 4000 BRISBANE HEAD OFFICE Level 22, 144 Edward St Brisbane, QLD 4000 T: 1300 744 028 Email: sales@riotsolutions.com.au www.riotsolutions.com.au
RIOT SOLUTIONS PTY LTD P.O. Box 10087 Adelaide St Brisbane QLD 4000 BRISBANE HEAD OFFICE Level 22, 144 Edward St Brisbane, QLD 4000 T: 1300 744 028 Email: sales@riotsolutions.com.au www.riotsolutions.com.au
2016 Webinar Sponsors
 Copyright 2016 American Water Works Association 2016 Webinar Sponsors 2 Please consider the environment before printing. 1 Webinar Moderator No Image Available Kevin Morley, Ph.D. Security & Preparedness
Copyright 2016 American Water Works Association 2016 Webinar Sponsors 2 Please consider the environment before printing. 1 Webinar Moderator No Image Available Kevin Morley, Ph.D. Security & Preparedness
Cyber Security of Industrial Control Systems and Potential Impacts on Nuclear Power Plants
 Cyber Security of Industrial Control Systems and Potential Impacts on Nuclear Power Plants IEEE NPEC April 18, 2006 Joe Weiss, PE, CISM KEMA, Inc. Joe.weiss@kema.com (408) 253-7934 2 Why are we here? Ostensibly:
Cyber Security of Industrial Control Systems and Potential Impacts on Nuclear Power Plants IEEE NPEC April 18, 2006 Joe Weiss, PE, CISM KEMA, Inc. Joe.weiss@kema.com (408) 253-7934 2 Why are we here? Ostensibly:
IEC A cybersecurity standard approaching the Rail IoT
 IEC 62443 A cybersecurity standard approaching the Rail IoT siemens.com/communications-for-transportation Today s Siemens company structure focusing on several businesses Siemens AG Power and Gas (PG)
IEC 62443 A cybersecurity standard approaching the Rail IoT siemens.com/communications-for-transportation Today s Siemens company structure focusing on several businesses Siemens AG Power and Gas (PG)
Welcome to the Second Annual Intelligence & National Security Forum
 Welcome to the Second Annual Intelligence & National Security Forum Today s Agenda 0800 0900 Registration and Light Breakfast 0900 0910 Opening Remarks Mr. Paul J. Geraci, Senior Director Intelligence
Welcome to the Second Annual Intelligence & National Security Forum Today s Agenda 0800 0900 Registration and Light Breakfast 0900 0910 Opening Remarks Mr. Paul J. Geraci, Senior Director Intelligence
Chapter 18 SaskPower Managing the Risk of Cyber Incidents 1.0 MAIN POINTS
 Chapter 18 SaskPower Managing the Risk of Cyber Incidents 1.0 MAIN POINTS The Saskatchewan Power Corporation (SaskPower) is the principal supplier of power in Saskatchewan with its mission to deliver power
Chapter 18 SaskPower Managing the Risk of Cyber Incidents 1.0 MAIN POINTS The Saskatchewan Power Corporation (SaskPower) is the principal supplier of power in Saskatchewan with its mission to deliver power
Industrial Cyber Security. ICS SHIELD Top-down security for multi-vendor OT assets
 Industrial Cyber Security ICS SHIELD Top-down security for multi-vendor OT assets OT SECURITY NEED Industrial organizations are increasingly integrating their OT and IT infrastructures. The huge benefits
Industrial Cyber Security ICS SHIELD Top-down security for multi-vendor OT assets OT SECURITY NEED Industrial organizations are increasingly integrating their OT and IT infrastructures. The huge benefits
Cyber Security. June 2015
 Cyber Security June 2015 Table of contents Section Pages Introduction and methodology 3 Key findings 4 Respondent profile 5-9 Cyber security practices 10-25 Resources for monitoring cyber security events
Cyber Security June 2015 Table of contents Section Pages Introduction and methodology 3 Key findings 4 Respondent profile 5-9 Cyber security practices 10-25 Resources for monitoring cyber security events
Introducing the 9202-ETS MTL Tofino industrial Ethernet security appliance
 Introducing the 9202-ETS MTL Tofino industrial Ethernet security appliance HAKIM- Sales Engineer 1 Cybersecurity of valuable assets and processes in a wide range of industry verticals, such as: Oil & Gas
Introducing the 9202-ETS MTL Tofino industrial Ethernet security appliance HAKIM- Sales Engineer 1 Cybersecurity of valuable assets and processes in a wide range of industry verticals, such as: Oil & Gas
KENYA SCHOOL OF GOVERNMENT EMPLOYMENT OPORTUNITY (EXTERNAL ADVERTISEMENT)
 KENYA SCHOOL OF GOVERNMENT EMPLOYMENT OPORTUNITY (EXTERNAL ADVERTISEMENT) 1. DIRECTOR, LEARNING & DEVELOPMENT - LOWER KABETE Reporting to the Director General, Campus Directors will be responsible for
KENYA SCHOOL OF GOVERNMENT EMPLOYMENT OPORTUNITY (EXTERNAL ADVERTISEMENT) 1. DIRECTOR, LEARNING & DEVELOPMENT - LOWER KABETE Reporting to the Director General, Campus Directors will be responsible for
Using Defense in Depth to Safely Present SCADA Data for Read-Only and Corporate Reporting. Rick Bryson
 Using Defense in Depth to Safely Present SCADA Data for Read-Only and Corporate Reporting Rick Bryson 2017 by Schweitzer Engineering Laboratories, Inc. All rights reserved. All brand or product names appearing
Using Defense in Depth to Safely Present SCADA Data for Read-Only and Corporate Reporting Rick Bryson 2017 by Schweitzer Engineering Laboratories, Inc. All rights reserved. All brand or product names appearing
ITIL Service Lifecycle: Service Operation Duration: 4 days
 Let s Reach For TAN DUC INFORMATION TECHNOLOGY SCHOOL JSC Address: 103 Pasteur, Dist.1, HCMC Tel: 08 38245819; 38239761 Email: traincert@tdt-tanduc.com Website: www.tdt-tanduc.com; www.tanducits.com ITIL
Let s Reach For TAN DUC INFORMATION TECHNOLOGY SCHOOL JSC Address: 103 Pasteur, Dist.1, HCMC Tel: 08 38245819; 38239761 Email: traincert@tdt-tanduc.com Website: www.tdt-tanduc.com; www.tanducits.com ITIL
Server/ Engineering Station. Filed Instrument. Filed Instrument. Filed Instrument. Switches. Fig1: Scheme for micro PLC to Master PLC Interface
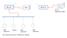 PC Micro PLC HMI HMI Master PLC Server/ Engineering Station Filed Instrument Switches Filed Instrument Filed Instrument Fig1: Scheme for micro PLC to Master PLC Interface PC Historian Server Communication
PC Micro PLC HMI HMI Master PLC Server/ Engineering Station Filed Instrument Switches Filed Instrument Filed Instrument Fig1: Scheme for micro PLC to Master PLC Interface PC Historian Server Communication
TRAINING DAYS 2017 Using the ISA/IEC Standards to Secure Your Control Systems (IC32) Milan, July 3th 4th
 TRAINING DAYS 2017 Using the ISA/IEC 62443 Standards to Secure Your Control Systems (IC32) Milan, July 3th 4th DESCRIPTION The move to using open standards such as Ethernet, TCP/IP, and web technologies
TRAINING DAYS 2017 Using the ISA/IEC 62443 Standards to Secure Your Control Systems (IC32) Milan, July 3th 4th DESCRIPTION The move to using open standards such as Ethernet, TCP/IP, and web technologies
Industrial Network Trends & Technologies
 Industrial Network Trends & Technologies EtherNet/IP on the Plant Floor PUBLIC INFORMATION 5058-CO900F IHS Technology Industrial Internet of Things 2014, April 2014 PUBLIC INFORMATION Forecasts tremendous
Industrial Network Trends & Technologies EtherNet/IP on the Plant Floor PUBLIC INFORMATION 5058-CO900F IHS Technology Industrial Internet of Things 2014, April 2014 PUBLIC INFORMATION Forecasts tremendous
Guide to Industrial Control Systems (ICS) Security
 NIST Special Publication 800-82 Revision 2 Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS), and Other Control
NIST Special Publication 800-82 Revision 2 Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS), and Other Control
Manufacturing security: Bridging the gap between IT and OT
 Manufacturing security: Bridging the gap between IT and OT For manufacturers, every new connection point is an opportunity. And a risk. The state of IT/OT security in manufacturing On the plant floor,
Manufacturing security: Bridging the gap between IT and OT For manufacturers, every new connection point is an opportunity. And a risk. The state of IT/OT security in manufacturing On the plant floor,
Why you should adopt the NIST Cybersecurity Framework
 Why you should adopt the NIST Cybersecurity Framework It s important to note that the Framework casts the discussion of cybersecurity in the vocabulary of risk management Stating it in terms Executive
Why you should adopt the NIST Cybersecurity Framework It s important to note that the Framework casts the discussion of cybersecurity in the vocabulary of risk management Stating it in terms Executive
Vulnerabilities in Process Control Networks: What Are We Protecting Against?
 Vulnerabilities in Process Control Networks: What Are We Protecting Against? Mark Benedict Ultra Electronics, 3eTI Standards Certification Education & Training Publishing Conferences & Exhibits 2014 ISA
Vulnerabilities in Process Control Networks: What Are We Protecting Against? Mark Benedict Ultra Electronics, 3eTI Standards Certification Education & Training Publishing Conferences & Exhibits 2014 ISA
Functional. Safety and. Cyber Security. Pete Brown Safety & Security Officer PI-UK
 Functional Safety and Cyber Security Pete Brown Safety & Security Officer PI-UK Setting the Scene 2 Functional Safety requires Security Consider just Cyber Security for FS Therefore Industrial Control
Functional Safety and Cyber Security Pete Brown Safety & Security Officer PI-UK Setting the Scene 2 Functional Safety requires Security Consider just Cyber Security for FS Therefore Industrial Control
INDUSTRIAL CYBER SECURITY
 Rudrajit Roy 20 October 2016 INDUSTRIAL CYBER SECURITY A Comprehensive Approach Agenda 1 Global Industrial Cyber Security Journey Industry Best Practices Honeywell Industrial Cyber Security Who we are,
Rudrajit Roy 20 October 2016 INDUSTRIAL CYBER SECURITY A Comprehensive Approach Agenda 1 Global Industrial Cyber Security Journey Industry Best Practices Honeywell Industrial Cyber Security Who we are,
The IT Implications of ISA 95 and ISA 99 Dennis Brandl
 The IT Implications of ISA 95 and ISA 99 Dennis Brandl dnbrandl@brlconsulting.com Abstract As manufacturing operations, defined in the ISA 95 standard, moves more into the standard information technology
The IT Implications of ISA 95 and ISA 99 Dennis Brandl dnbrandl@brlconsulting.com Abstract As manufacturing operations, defined in the ISA 95 standard, moves more into the standard information technology
NW NATURAL CYBER SECURITY 2016.JUNE.16
 NW NATURAL CYBER SECURITY 2016.JUNE.16 ADOPTED CYBER SECURITY FRAMEWORKS CYBER SECURITY TESTING SCADA TRANSPORT SECURITY AID AGREEMENTS CONCLUSION QUESTIONS ADOPTED CYBER SECURITY FRAMEWORKS THE FOLLOWING
NW NATURAL CYBER SECURITY 2016.JUNE.16 ADOPTED CYBER SECURITY FRAMEWORKS CYBER SECURITY TESTING SCADA TRANSPORT SECURITY AID AGREEMENTS CONCLUSION QUESTIONS ADOPTED CYBER SECURITY FRAMEWORKS THE FOLLOWING
Function Block Applications in Control Systems Based on IEC 61804
 Applications in Control Systems Based on IEC 61804 Christian Diedrich Department Control System Ifak Magdeburg, Germany Francesco Russo Standards Coordinator ENEL Milan, Italy Ludwig Winkel Terry Blevins
Applications in Control Systems Based on IEC 61804 Christian Diedrich Department Control System Ifak Magdeburg, Germany Francesco Russo Standards Coordinator ENEL Milan, Italy Ludwig Winkel Terry Blevins
Industry Best Practices for Securing Critical Infrastructure
 Industry Best Practices for Securing Critical Infrastructure Cyber Security and Critical Infrastructure AGENDA - Difference between IT and OT - Real World Examples of Cyber Attacks Across the IT/OT Boundary
Industry Best Practices for Securing Critical Infrastructure Cyber Security and Critical Infrastructure AGENDA - Difference between IT and OT - Real World Examples of Cyber Attacks Across the IT/OT Boundary
Firewalls (IDS and IPS) MIS 5214 Week 6
 Firewalls (IDS and IPS) MIS 5214 Week 6 Agenda Defense in Depth Evolution of IT risk in automated control systems Security Domains Where to put firewalls in an N-Tier Architecture? In-class exercise Part
Firewalls (IDS and IPS) MIS 5214 Week 6 Agenda Defense in Depth Evolution of IT risk in automated control systems Security Domains Where to put firewalls in an N-Tier Architecture? In-class exercise Part
Cybersecurity Presidential Policy Directive Frequently Asked Questions. kpmg.com
 Cybersecurity Presidential Policy Directive Frequently Asked Questions kpmg.com Introduction On February 12, 2013, the White House released the official version of the Presidential Policy Directive regarding
Cybersecurity Presidential Policy Directive Frequently Asked Questions kpmg.com Introduction On February 12, 2013, the White House released the official version of the Presidential Policy Directive regarding
ARTO LIND ABB Ability Datacenter Automation. The way to monitor & control your DC infrastructure (DCIM) Datacenter Infrastructure Management
 ARTO LIND ABB Ability Datacenter Automation The way to monitor & control your DC infrastructure (DCIM) Datacenter Infrastructure Management Data Center common functionality DCIM needs to be open to handle
ARTO LIND ABB Ability Datacenter Automation The way to monitor & control your DC infrastructure (DCIM) Datacenter Infrastructure Management Data Center common functionality DCIM needs to be open to handle
NERC Staff Organization Chart Budget 2018
 NERC Staff Organization Chart Budget 2018 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Senior Vice President, General Counsel and Corporate
NERC Staff Organization Chart Budget 2018 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Senior Vice President, General Counsel and Corporate
CFAM Manufacturing Environment Team (MET) Update and Manufacturing Boundaries
 CFAM Manufacturing Environment Team (MET) Update and Manufacturing Boundaries Dr. Marilyn Gaska 11 April, 2016 "Delivering Value through Defense Manufacturing Technology" Agenda MET Membership Deliverables
CFAM Manufacturing Environment Team (MET) Update and Manufacturing Boundaries Dr. Marilyn Gaska 11 April, 2016 "Delivering Value through Defense Manufacturing Technology" Agenda MET Membership Deliverables
CCNA Cybersecurity Operations 1.1 Scope and Sequence
 CCNA Cybersecurity Operations 1.1 Scope and Sequence Last updated June 18, 2018 Introduction Today's organizations are challenged with rapidly detecting cybersecurity breaches and effectively responding
CCNA Cybersecurity Operations 1.1 Scope and Sequence Last updated June 18, 2018 Introduction Today's organizations are challenged with rapidly detecting cybersecurity breaches and effectively responding
77% 56% 74% 52% PACKAGING WORLD SURVEY: Ethernet And Wireless In Production Facilities
 Ethernet Usage + Strategy Survey 2012 A joint survey by Packaging World and XYZ Company was conducted in late 2012 to obtain insight into current engineering and management applications and opinions surrounding
Ethernet Usage + Strategy Survey 2012 A joint survey by Packaging World and XYZ Company was conducted in late 2012 to obtain insight into current engineering and management applications and opinions surrounding
Indegy. Industrial Cyber Security. Matt Petrauskas Regional Director.
 Indegy Industrial Cyber Security Matt Petrauskas Regional Director mpetrauskas@indegy.com Discussion Focus Unveiling Security Gaps in Industrial Control Networks About the Presenter Matt Petrauskas 33
Indegy Industrial Cyber Security Matt Petrauskas Regional Director mpetrauskas@indegy.com Discussion Focus Unveiling Security Gaps in Industrial Control Networks About the Presenter Matt Petrauskas 33
Maritime Cyber Security Project Work Plan. Maritime Cyber Security. Work Plan Draft
 Maritime Cyber Security Project Maritime Cyber Security Draft August 8, 2016 1 INTRODUCTION On July 27, 016, the American Bureau of Shipping (ABS) received notification of award of the Maritime Cyber Security
Maritime Cyber Security Project Maritime Cyber Security Draft August 8, 2016 1 INTRODUCTION On July 27, 016, the American Bureau of Shipping (ABS) received notification of award of the Maritime Cyber Security
Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure
 Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure Executive Order 13800 Update July 2017 In Brief On May 11, 2017, President Trump issued Executive Order 13800, Strengthening
Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure Executive Order 13800 Update July 2017 In Brief On May 11, 2017, President Trump issued Executive Order 13800, Strengthening
