2017 Ethics & Compliance Hotline & Incident Management Benchmark Report Webinar
|
|
|
- Chloe Norton
- 5 years ago
- Views:
Transcription
1 2017 Ethics & Compliance Hotline & Incident Management Benchmark Report Webinar Presented by Carrie Penman Chief Compliance Officer & Senior Vice President, Advisory Services Edwin O Mara Operations Manager, Advisory Services Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0
2 Presented By Carrie Penman Chief Compliance Officer & Senior Vice President, Advisory Services Edwin O Mara Operations Manager, Advisory Services Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 1
3 Agenda Introductions Our Benchmarking Methodology Business Imperatives of Benchmarking Key Findings Key Takeaways & Best Practice Recommendations Q&A Additional Resources Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 2
4 Our Comprehensive Ecosystem Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 3
5 Benchmark Methodology Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 4
6 Hotline Benchmark Statistical Snapshot Our database starts with 12,500+ NAVEX Global clients Of those 5,132 received a report in 2016 through NAVEX Global s Hotline and EthicsPoint Incident Management solutions 2,382 clients received 10 or more reports in 2016 (representing 38.5 million employees) These 2,300+ clients received approximately 1,000,000 reports in 2016 Data reflects all reports documented in clients EthicsPoint Incident Management system regardless of reporting channel (web, hotline, open door, mobile, , mail, etc. ) Data covers 26 industries, and an additional 45 sub-industries We use medians (or midpoints) rather than averages to reduce the impact of outliers Normal ranges identify extreme data points as potential areas of concern Medians and ranges provide context for benchmarks Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 5
7 Key Findings Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 6
8 Key Finding #1 Report Volume per 100 Employees Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 7
9 Median Report Volume Increases to an All-Time High Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 8
10 What do you think is the biggest driver of report volume increases? Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 9
11 Impact of Using a Unified Incident Management System Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 10
12 What is your organization s approach to documenting E&C reports? Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 11
13 Health Care Leads in Reporting Volume Highest Rate 1) Health Care 2) Not for Profit 3) Real Estate 4) Pharmaceuticals 5) Retail 6) Agriculture, Forestry, Fishing & Hunting 7) Arts & Entertainment 8) Energy & Utilities 9) Commercial Transportation 10) Consumer Manufacturing Lowest Rate Overall Median Rate: 1.4 reports per 100 employees 11) Finance & Insurance 12) Security 13) Business Support Services 14) Food Services 15) Construction 16) Aerospace & Defense 17) Automotive Transportation 18) Government 19) Professional, Scientific & Technical Services 20) Education 21) Media 22) Mining 23) Computer Services, Hardware & Software 24) Industrial Manufacturing 25) Wholesale Trade 26) Electronics Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 12
14 Key Finding #2 Report Allegation Categories Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 13
15 Categories of Reports Used Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 14
16 Categories of Reports Remain Relatively Consistent Allegation Categories 2012 Median 2013 Median 2014 Median 2015 Median 2016 Median Accounting, Auditing and Financial Reporting 3% 3% 2% 2% 2% Business Integrity 17% 18% 17% 15% 14% HR, Diversity and Workplace Respect Environment, Health and Safety Misuse, Misappropriation of Corporate Assets 69% 73% 69% 71% 72% 7% 7% 6% 5% 7% 6% 6% 6% 7% 5% Source: NAVEX Global's 2016 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 15
17 Industries with the Highest Median Reporting Rate by Allegation Category Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 16
18 Key Finding #3 Anonymous vs. Named Reporters Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 17
19 Anonymous Reporting Continues to Decrease Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 18
20 No Change In Follow-Ups to Anonymous Reports Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 19
21 Education Leads Anonymous Reporting by Industry Highest Rate 1) Education 2) Automotive Transportation 3) Electronics 4) Mining 5) Consumer Manufacturing 6) Security 7) Industrial Manufacturing 8) Government 9) Construction 10) Not for Profit Lowest Rate Overall Median Rate: 58% 11) Commercial Transportation 12) Finance & Insurance 13) Wholesale Trade 14) Energy & Utilities 15) Arts & Entertainment 16) Health Care 17) Professional, Scientific & Technical Services 18) Computer Services, Hardware & Software 19) Retail 20) Media 21) Agriculture, Forestry, Fishing & Hunting 22) Business Support Services 23) Real Estate 24) Food Services 25) Aerospace & Defense 26) Pharmaceuticals Source: NAVEX Global's 2016 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 20
22 Key Finding #4 Substantiated Reports Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 21
23 Overall Substantiation Rate Remains High Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 22
24 Overall Substantiation Rate by Industry Highest Rate 1) Media 2) Arts & Entertainment 3) Agriculture, Forestry, Fishing & Hunting 4) Real Estate 5) Health Care 6) Pharmaceuticals 7) Retail 8) Computer Services, Hardware & Software 9) Business Support Services 10) Not for Profit Lowest Rate Overall Median Rate: 40% 11) Electronics 12) Food Services 13) Energy & Utilities 14) Finance & Insurance 15) Professional, Scientific & Technical Services 16) Government 17) Consumer Manufacturing 18) Security 19) Construction 20) Commercial Transportation 21) Industrial Manufacturing 22) Aerospace & Defense 23) Education 24) Wholesale Trade 25) Mining 26) Automotive Transportation Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 23
25 Substantiated Anonymous vs. Named Reports Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 24
26 Substantiation Rate by Allegation Category Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 25
27 Key Finding #5 Case Closure Time Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 26
28 Case Closure Shows Improvement in 2016 Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 27
29 What do you think was the biggest factor in the decreasing case closure times? Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 28
30 Industry Case Closure Times Highest Rate 1) Mining 2) Computer Services, Hardware & Software 3) Electronics 4) Government 5) Pharmaceuticals 6) Automotive Transportation 7) Not for Profit 8) Real Estate 9) Agriculture, Forestry, Fishing & Hunting 10) Food Services Lowest Rate Overall Median Rate: 42 Days 11) Education 12) Energy & Utilities 13) Professional, Scientific & Technical Services 14) Construction 15) Security 16) Industrial Manufacturing 17) Finance & Insurance 18) Business Support Services 19) Media 20) Aerospace & Defense 21) Commercial Transportation 22) Consumer Manufacturing 23) Wholesale Trade 24) Health Care 25) Arts & Entertainment 26) Retail Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 29
31 Key Finding #6 Report Intake Methods Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 30
32 Web Reporting Continues to Trend Up Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 31
33 Substantiation Rates by Report Intake Method Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 32
34 Key Finding #7 Reports of Retaliation Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 33
35 Where does retaliation prevention fall on your list of E&C program priorities for 2017? Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 34
36 Organizations Still Not Getting the Chance to Address Retaliation Allegations Internally Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 35
37 Retaliation Substantiation Rates Remain Elevated Source: NAVEX Global's 2016 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 36
38 Key Finding #8 Geographical Data Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 37
39 Geographic Reporting Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 38
40 Substantiated reports by Geography Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 39
41 Key Finding #9 Organizational Employee Count Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 40
42 Report Volume by Organizational Employee Count Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 41
43 Anonymity and Case Closure by Organizational Employee Count Source: NAVEX Global's 2017 Ethics and Compliance Hotline Benchmark Report Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 42
44 Overall Substantiation Rate by Organizational Employee Count Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 43
45 Anonymous vs Named Substantiation Rates Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 44
46 Key Takeaways & Best Practice Recommendations Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 45
47 6 Key Takeaways 1) Increase focus on anti-retaliation efforts 2) Continue work on getting case closure times back within best practice ranges 3) Get a more complete picture of your risks by documenting all reports in one centralized incident management system 4) Make the business case for matching your report volume with appropriate resources 5) Encourage employees to see your hotline as a resource for information, not just a channel for reporting 6) Take advantage of the new data this year relating to geography and organizational size Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 46
48 Moving Beyond the Basics Incident Management Systems Create Exponential Visibility & Program Effectiveness Nearly Double Risk Visibility: Documenting reports from all intake channels (not just web & hotline) in an incident management system creates nearly twice as much visibility into potential E&C risks Work Smarter: Customized workflows standardize and simplify report management tasks, helping you capture, assign and resolve cases more effectively, efficiently and consistently See Trends: Advanced analytics gives you the ability to see program gaps, measure program effectiveness, proactively spot trends and identify and address issues Make it Easier to Document Issues: Custom web forms allow you to more efficiently capture and route reports and make it easier for employees and managers to document issues Better Protect Your Organization: More documentation also provides a stronger legal defense in the event of a lawsuit or regulatory action Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 47
49 Moving Beyond the Basics Industry-Specific Benchmarking Provides More & Better Insight Into E&C Health As our industry ranking slides showed, using accurate industry-specific benchmarking is critical, as there can be striking differences in benchmarks across industries. Industry-specific benchmarking can help you, your board and your senior leadership understand critical issues such as: Are our metrics consistent with or out of line with peers? What E&C trends are prevalent or unique in our industry and which ones should we focus on? Are there opportunities to achieve a competitive advantage by adding focus or resources to an aspect of our E&C program that may be an issue for competitors? Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 48
50 Join Compliance Next! Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 49
51 Additional Resources NAVEX Global offers many valuable resources for helping you increase program effectiveness by leveraging your hotline and incident management data. Visit our website to find these resources and more: White Papers: Whistleblower Hotlines and Case Management Solutions Major Challenges and Best Practice Recommendations Key Elements for Effective Compliance Program Board Reporting Maximizing the Benefits of Hotline Data: Analysis and Benchmarking On-Demand Webinars: Whistleblowing & Retaliation: Legal Developments And Practical Advice How Do I Prove My E&C Program is Effective? The Art & Science of Effectiveness Measurement Learn More About Our Solutions: Hotline Solutions EthicsPoint Incident Management Integrity Diagnostics Custom Benchmarking Strategic Consulting: The Advisory Services Team Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 50
52 Thank You for Your Participation Carrie Penman, CCO & SVP of Advisory Services Edwin O Mara, Ops Manager, Advisory Services eomara@navexglobal.com Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 51
A Framework for Managing Crime and Fraud
 A Framework for Managing Crime and Fraud ASIS International Asia Pacific Security Forum & Exhibition Macau, December 4, 2013 Torsten Wolf, CPP Head of Group Security Operations Agenda Introduction Economic
A Framework for Managing Crime and Fraud ASIS International Asia Pacific Security Forum & Exhibition Macau, December 4, 2013 Torsten Wolf, CPP Head of Group Security Operations Agenda Introduction Economic
INTELLIGENCE DRIVEN GRC FOR SECURITY
 INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
Six Weeks to Security Operations The AMP Story. Mike Byrne Cyber Security AMP
 Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
Six Weeks to Security Operations The AMP Story Mike Byrne Cyber Security AMP 1 Agenda Introductions The AMP Security Operations Story Lessons Learned 2 Speaker Introduction NAME: Mike Byrne TITLE: Consultant
GRC SURVEY RESULT Please indicate your profession
 COPENHAGEN?=! CO?=! MPLIANCE T o p i c a l a n d T i m e l y Riskability GRC Controllers Governance, Risk & Compliance COPENHAGEN?=! CHARTER Bribery, Fraud & Corruption GRC SURVEY RESULT. Please indicate
COPENHAGEN?=! CO?=! MPLIANCE T o p i c a l a n d T i m e l y Riskability GRC Controllers Governance, Risk & Compliance COPENHAGEN?=! CHARTER Bribery, Fraud & Corruption GRC SURVEY RESULT. Please indicate
Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO #IIACHI
 Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO CHAPTER: @IIACHI #IIACHI WWW.FACEBOOK.COM/IIACHICAGO HTTPS://WWW.LINKEDIN.COM/GROUPS/1123977 1 CAE Communications and Common Audit Committee
Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO CHAPTER: @IIACHI #IIACHI WWW.FACEBOOK.COM/IIACHICAGO HTTPS://WWW.LINKEDIN.COM/GROUPS/1123977 1 CAE Communications and Common Audit Committee
VALUE OF A CYBERSECURITY SELF-ASSESSMENT
 VALUE OF A CYBERSECURITY SELF-ASSESSMENT RC3 Self-Assessment Research Program RC3 Self-Assessment Research Program Directors Cybersecurity Ecosystem CEO/GM E&O Member Services Marketing Information Technology
VALUE OF A CYBERSECURITY SELF-ASSESSMENT RC3 Self-Assessment Research Program RC3 Self-Assessment Research Program Directors Cybersecurity Ecosystem CEO/GM E&O Member Services Marketing Information Technology
RSA Cybersecurity Poverty Index
 RSA Cybersecurity Poverty Index 2016 RSA Cybersecurity Poverty Index Overview Welcome to RSA s second annual Cybersecurity Poverty Index. The RSA Cybersecurity Poverty Index is the result of an annual
RSA Cybersecurity Poverty Index 2016 RSA Cybersecurity Poverty Index Overview Welcome to RSA s second annual Cybersecurity Poverty Index. The RSA Cybersecurity Poverty Index is the result of an annual
Information Security Risk Strategies. By
 Information Security Risk Strategies By Larry.Boettger@Berbee.com Meeting Agenda Challenges Faced By IT Importance of ISO-17799 & NIST The Security Pyramid Benefits of Identifying Risks Dealing or Not
Information Security Risk Strategies By Larry.Boettger@Berbee.com Meeting Agenda Challenges Faced By IT Importance of ISO-17799 & NIST The Security Pyramid Benefits of Identifying Risks Dealing or Not
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
Embedding Privacy by Design
 Embedding Privacy by Design Metric Stream Customer Conference May 12, 2015 TRUSTe Data Privacy Management Solutions 1 Today s Agenda Privacy in the Context of GRC Data Privacy Management and Top Privacy
Embedding Privacy by Design Metric Stream Customer Conference May 12, 2015 TRUSTe Data Privacy Management Solutions 1 Today s Agenda Privacy in the Context of GRC Data Privacy Management and Top Privacy
Ponemon Institute s 2018 Cost of a Data Breach Study
 Ponemon Institute s 2018 Cost of a Data Breach Study September 18, 2018 1 IBM Security Speakers Deborah Snyder CISO State of New York Dr. Larry Ponemon Chairman and Founder Ponemon Institute Megan Powell
Ponemon Institute s 2018 Cost of a Data Breach Study September 18, 2018 1 IBM Security Speakers Deborah Snyder CISO State of New York Dr. Larry Ponemon Chairman and Founder Ponemon Institute Megan Powell
RICK RAMPOLLA WHO WE ARE. ITDM Security Operations, Publix Super Markets Inc.
 RICK RAMPOLLA ITDM Security Operations, Publix Super Markets Inc. Intelligence shared through the R-CISC has played a key role in our efforts to combat cyber threats. We can directly correlate the value
RICK RAMPOLLA ITDM Security Operations, Publix Super Markets Inc. Intelligence shared through the R-CISC has played a key role in our efforts to combat cyber threats. We can directly correlate the value
Transformation in Technology Barbara Duck Chief Information Officer. Investor Day 2018
 Transformation in Technology Barbara Duck Chief Information Officer Investor Day 2018 Key Takeaways 1Transformation in Technology driving out cost, supporting a more technologyenabled business Our new
Transformation in Technology Barbara Duck Chief Information Officer Investor Day 2018 Key Takeaways 1Transformation in Technology driving out cost, supporting a more technologyenabled business Our new
RIMS Perk Session Protecting the Crown Jewels A Risk Manager's guide to cyber security March 18, 2015
 www.pwc.com RIMS Perk Session 2015 - Protecting the Crown Jewels A Risk Manager's guide to cyber security March 18, 2015 Los Angeles RIMS Agenda Introductions What is Cybersecurity? Crown jewels The bad
www.pwc.com RIMS Perk Session 2015 - Protecting the Crown Jewels A Risk Manager's guide to cyber security March 18, 2015 Los Angeles RIMS Agenda Introductions What is Cybersecurity? Crown jewels The bad
Audit and Compliance Committee - Agenda
 Audit and Compliance Committee - Agenda Board of Trustees Audit and Compliance Committee April 17, 2018, 1:30 2:30 p.m. President s Board Room Conference Call-In Phone #1-800-442-5794, passcode 463796
Audit and Compliance Committee - Agenda Board of Trustees Audit and Compliance Committee April 17, 2018, 1:30 2:30 p.m. President s Board Room Conference Call-In Phone #1-800-442-5794, passcode 463796
Key Findings from the Global State of Information Security Survey 2017 Indonesian Insights
 www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
www.pwc.com/id Key Findings from the State of Information Security Survey 2017 n Insights Key Findings from the State of Information Security Survey 2017 n Insights By now, the numbers have become numbing.
LinkedIn Economic Graph Project
 LinkedIn Economic Graph Project Understanding Trade Through International Connections In Partnership with the Ontario Ministry of International Trade FEBRUARY 8 The Economic Graph as a Tool to Advance
LinkedIn Economic Graph Project Understanding Trade Through International Connections In Partnership with the Ontario Ministry of International Trade FEBRUARY 8 The Economic Graph as a Tool to Advance
Presented by Ingrid Fredeen and Pamela Passman. Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0
 Cyber Security and Inside Threats: Turning Policies into Practices Presented by Ingrid Fredeen and Pamela Passman Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0 Presented By Ingrid Fredeen, J.D.
Cyber Security and Inside Threats: Turning Policies into Practices Presented by Ingrid Fredeen and Pamela Passman Copyright 2017NAVEXGlobal,Inc. AllRightsReserved. Page 0 Presented By Ingrid Fredeen, J.D.
RCISC_11014 Prospect Brochure_V3.indd 1
 RCISC_11014 Prospect Brochure_V3.indd 1 4/26/18 2:38 PM RICK RAMPOLLA ITDM Security Operations, Publix Super Markets Inc. Intelligence shared through the R-CISC has played a key role in our efforts to
RCISC_11014 Prospect Brochure_V3.indd 1 4/26/18 2:38 PM RICK RAMPOLLA ITDM Security Operations, Publix Super Markets Inc. Intelligence shared through the R-CISC has played a key role in our efforts to
Intelligent Building and Cybersecurity 2016
 Intelligent Building and Cybersecurity 2016 Landmark Research Executive Summary 2016, Continental Automated Buildings Association Presentation Contents 1. About CABA, Compass Intelligence & This Research
Intelligent Building and Cybersecurity 2016 Landmark Research Executive Summary 2016, Continental Automated Buildings Association Presentation Contents 1. About CABA, Compass Intelligence & This Research
DAVID J BEHINFAR, JD., LLM., CHC, CHRC, CCEP, HCISPP, CIPP/US P23: AN EFFECTIVE PRIVACY PROGRAM BUILT THROUGH STRATEGIC VISION AND LEADERSHIP SUPPORT
 P23: AN EFFECTIVE PRIVACY PROGRAM BUILT THROUGH STRATEGIC VISION AND LEADERSHIP SUPPORT APRIL 7, 2019 David Behinfar, Chief Privacy Officer University of North Carolina Health Katherine Georger, Associate
P23: AN EFFECTIVE PRIVACY PROGRAM BUILT THROUGH STRATEGIC VISION AND LEADERSHIP SUPPORT APRIL 7, 2019 David Behinfar, Chief Privacy Officer University of North Carolina Health Katherine Georger, Associate
BPS Suite and the OCEG Capability Model. Mapping the OCEG Capability Model to the BPS Suite s product capability.
 BPS Suite and the OCEG Capability Model Mapping the OCEG Capability Model to the BPS Suite s product capability. BPS Contents Introduction... 2 GRC activities... 2 BPS and the Capability Model for GRC...
BPS Suite and the OCEG Capability Model Mapping the OCEG Capability Model to the BPS Suite s product capability. BPS Contents Introduction... 2 GRC activities... 2 BPS and the Capability Model for GRC...
The Impact of Cloud Computing on Business
 The Impact of Cloud Computing on Business Ms LIM May-Ann Executive Director Asia Cloud Computing Association mayann@asiacloudcomputing.org @eilonwy @accacloud +65-98471950 2017 TM Forum 1 About the ACCA
The Impact of Cloud Computing on Business Ms LIM May-Ann Executive Director Asia Cloud Computing Association mayann@asiacloudcomputing.org @eilonwy @accacloud +65-98471950 2017 TM Forum 1 About the ACCA
Security Metrics Establishing unambiguous and logically defensible security metrics. Steven Piliero CSO The Center for Internet Security
 Security Metrics Establishing unambiguous and logically defensible security metrics Steven Piliero CSO The Center for Internet Security The Center for Internet Security (CIS) Formed - October 2000 As a
Security Metrics Establishing unambiguous and logically defensible security metrics Steven Piliero CSO The Center for Internet Security The Center for Internet Security (CIS) Formed - October 2000 As a
Template for data breach notifications I
 Template for data breach notifications I I. Identification of the data controller This information is exclusively for the relevant Data Protection Authority, not to be shared with third-parties. 1. Details
Template for data breach notifications I I. Identification of the data controller This information is exclusively for the relevant Data Protection Authority, not to be shared with third-parties. 1. Details
May 14, :30PM to 2:30PM CST. In Plain English: Cybersecurity and IT Exam Expectations
 May 14, 2018 1:30PM to 2:30PM CST In Plain English: Cybersecurity and IT Exam Expectations Options to Join Webinar and audio Click on the link: https://www.webcaster4.com/webcast/page/584/24606 Choose
May 14, 2018 1:30PM to 2:30PM CST In Plain English: Cybersecurity and IT Exam Expectations Options to Join Webinar and audio Click on the link: https://www.webcaster4.com/webcast/page/584/24606 Choose
Operationalizing Cybersecurity in Healthcare IT Security & Risk Management Study Quantitative and Qualitative Research Program Results
 Operationalizing Cybersecurity in Healthcare - - 2017 IT Security & Risk Management Study Quantitative and Qualitative Research Program Results David S. Finn, CISA, CISM, CRISC Health IT Officer, Symantec
Operationalizing Cybersecurity in Healthcare - - 2017 IT Security & Risk Management Study Quantitative and Qualitative Research Program Results David S. Finn, CISA, CISM, CRISC Health IT Officer, Symantec
Mid-Market Data Center Purchasing Drivers, Priorities and Barriers
 Mid-Market Data Center Purchasing Drivers, Priorities and Barriers Featuring Sophia Vargas, Forrester Research Inc. 30 May 2014 Introducing today s presenters: Matt Miszewski Senior Vice President of Sales
Mid-Market Data Center Purchasing Drivers, Priorities and Barriers Featuring Sophia Vargas, Forrester Research Inc. 30 May 2014 Introducing today s presenters: Matt Miszewski Senior Vice President of Sales
The Office of Infrastructure Protection
 The Office of Infrastructure Protection National Protection and Programs Directorate Department of Homeland Security Organisation for the Prohibition of Chemical Weapons September 13, 2011 Overall Landscape
The Office of Infrastructure Protection National Protection and Programs Directorate Department of Homeland Security Organisation for the Prohibition of Chemical Weapons September 13, 2011 Overall Landscape
EY Consulting. Is your strategy planning for the future or creating it? #TransformativeAge
 2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
Enhancing Security With SQL Server How to balance the risks and rewards of using big data
 Enhancing Security With SQL Server 2016 How to balance the risks and rewards of using big data Data s security demands and business opportunities With big data comes both great reward and risk. Every company
Enhancing Security With SQL Server 2016 How to balance the risks and rewards of using big data Data s security demands and business opportunities With big data comes both great reward and risk. Every company
How to implement NIST Cybersecurity Framework using ISO WHITE PAPER. Copyright 2017 Advisera Expert Solutions Ltd. All rights reserved.
 How to implement NIST Cybersecurity Framework using ISO 27001 WHITE PAPER Copyright 2017 Advisera Expert Solutions Ltd. All rights reserved. Copyright 2017 Advisera Expert Solutions Ltd. All rights reserved.
How to implement NIST Cybersecurity Framework using ISO 27001 WHITE PAPER Copyright 2017 Advisera Expert Solutions Ltd. All rights reserved. Copyright 2017 Advisera Expert Solutions Ltd. All rights reserved.
NERC Staff Organization Chart Budget 2019
 NERC Staff Organization Chart Budget 2019 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Senior Vice President, General Counsel and Corporate
NERC Staff Organization Chart Budget 2019 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Senior Vice President, General Counsel and Corporate
APMP Certification. Webinar presentation by: Mark Wigginton Regional Director, Shipley Associates September 11, 2013
 APMP Certification Webinar presentation by: Mark Wigginton Regional Director, Shipley Associates September 11, 2013 Webinar Agenda Overview of APMP Certification Program 3 Levels of certification Qualifications
APMP Certification Webinar presentation by: Mark Wigginton Regional Director, Shipley Associates September 11, 2013 Webinar Agenda Overview of APMP Certification Program 3 Levels of certification Qualifications
STRATEGIC PLAN
 STRATEGIC PLAN 2013-2018 In an era of growing demand for IT services, it is imperative that strong guiding principles are followed that will allow for the fulfillment of the Division of Information Technology
STRATEGIC PLAN 2013-2018 In an era of growing demand for IT services, it is imperative that strong guiding principles are followed that will allow for the fulfillment of the Division of Information Technology
Socioeconomic Overview of Ohio
 2 Socioeconomic Overview of Ohio Introduction The magnitude of the economic impact of Ohio s airports is linked to the demand that is generated within the state for aviation goods and services. As population,
2 Socioeconomic Overview of Ohio Introduction The magnitude of the economic impact of Ohio s airports is linked to the demand that is generated within the state for aviation goods and services. As population,
7 Steps to Complete Privileged Account Management. September 5, 2017 Fabricio Simao Country Manager
 7 Steps to Complete Privileged Account Management September 5, 2017 Fabricio Simao Country Manager AGENDA Implications of less mature privileged account management What does a more mature approach look
7 Steps to Complete Privileged Account Management September 5, 2017 Fabricio Simao Country Manager AGENDA Implications of less mature privileged account management What does a more mature approach look
Bringing cyber to the Board of Directors & C-level and keeping it there. Dirk Lybaert, Proximus September 9 th 2016
 Bringing cyber to the Board of Directors & C-level and keeping it there Dirk Lybaert, Proximus September 9 th 2016 Dirk Lybaert Chief Group Corporate Affairs We constantly keep people connected to the
Bringing cyber to the Board of Directors & C-level and keeping it there Dirk Lybaert, Proximus September 9 th 2016 Dirk Lybaert Chief Group Corporate Affairs We constantly keep people connected to the
ACL Interpretive Visual Remediation
 January 2016 ACL Interpretive Visual Remediation Innovation in Internal Control Management SOLUTIONPERSPECTIVE Governance, Risk Management & Compliance Insight 2015 GRC 20/20 Research, LLC. All Rights
January 2016 ACL Interpretive Visual Remediation Innovation in Internal Control Management SOLUTIONPERSPECTIVE Governance, Risk Management & Compliance Insight 2015 GRC 20/20 Research, LLC. All Rights
Incident Response Services to Help You Prepare for and Quickly Respond to Security Incidents
 Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
ISO Certification. How we got there and why it s worth it! Worried that your compliance program isn t good enough?
 ISO 37001 Certification How we got there and why it s worth it! Diana Trevley Chief of Global Services Spark Compliance Consulting Mark Speck Managing Partner Specktrum Inc. Worried that your compliance
ISO 37001 Certification How we got there and why it s worth it! Diana Trevley Chief of Global Services Spark Compliance Consulting Mark Speck Managing Partner Specktrum Inc. Worried that your compliance
Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach
 White Paper Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach Sponsored by: Red Hat Tim Grieser January 2018 IN THIS WHITE PAPER This IDC White Paper discusses
White Paper Optimizing Infrastructure Management with Predictive Analytics: The Red Hat Insights Approach Sponsored by: Red Hat Tim Grieser January 2018 IN THIS WHITE PAPER This IDC White Paper discusses
NERC Staff Organization Chart Budget 2018
 NERC Staff Organization Chart Budget 2018 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Senior Vice President, General Counsel and Corporate
NERC Staff Organization Chart Budget 2018 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Senior Vice President, General Counsel and Corporate
Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK.
 Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK. In today s escalating cyber risk environment, you need to make sure you re focused on the right priorities by
Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK. In today s escalating cyber risk environment, you need to make sure you re focused on the right priorities by
Cybersecurity Session IIA Conference 2018
 www.pwc.com/me Cybersecurity Session IIA Conference 2018 Wael Fattouh Partner PwC Cybersecurity and Technology Risk PwC 2 There are only two types of companies: Those that have been hacked, and those that
www.pwc.com/me Cybersecurity Session IIA Conference 2018 Wael Fattouh Partner PwC Cybersecurity and Technology Risk PwC 2 There are only two types of companies: Those that have been hacked, and those that
IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES
 IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES Introductions Agenda Overall data risk and benefit landscape / shifting risk and opportunity landscape and market expectations Looking at data
IMPLEMENTING SECURITY, PRIVACY, AND FAIR DATA USE PRINCIPLES Introductions Agenda Overall data risk and benefit landscape / shifting risk and opportunity landscape and market expectations Looking at data
Thailand Digital Government Development Plan Digital Government Development Agency (Public Organization) (DGA)
 ขอแค ประมาณ ร ปน นะโม Thailand Digital Government Development Plan Digital Government Development Agency (Public Organization) (DGA) 1 Government agencies need to develop the Digital Government Master
ขอแค ประมาณ ร ปน นะโม Thailand Digital Government Development Plan Digital Government Development Agency (Public Organization) (DGA) 1 Government agencies need to develop the Digital Government Master
The Cost of Denial-of-Services Attacks
 The Cost of Denial-of-Services Attacks Sponsored by Akamai Technologies Independently conducted by Ponemon Institute LLC Publication Date: March 2015 Ponemon Institute Research Report The Cost of Denial-of-Service
The Cost of Denial-of-Services Attacks Sponsored by Akamai Technologies Independently conducted by Ponemon Institute LLC Publication Date: March 2015 Ponemon Institute Research Report The Cost of Denial-of-Service
NERC Staff Organization Chart Budget 2019
 NERC Staff Organization Chart Budget 2019 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Officer Senior Vice President, General Counsel and Corporate
NERC Staff Organization Chart Budget 2019 President and CEO Associate Director to the Office of the CEO Senior Vice President and Chief Reliability Officer Senior Vice President, General Counsel and Corporate
UAE National Space Policy Agenda Item 11; LSC April By: Space Policy and Regulations Directory
 UAE National Space Policy Agenda Item 11; LSC 2017 06 April 2017 By: Space Policy and Regulations Directory 1 Federal Decree Law No.1 of 2014 establishes the UAE Space Agency UAE Space Agency Objectives
UAE National Space Policy Agenda Item 11; LSC 2017 06 April 2017 By: Space Policy and Regulations Directory 1 Federal Decree Law No.1 of 2014 establishes the UAE Space Agency UAE Space Agency Objectives
GIIM. Global Institute for IT Management. A unique (outside-of-the-box) approach for educating executives
 Institute Objective The 21st Century is marked by the continued penetration of Information Technology (IT) into all facets of the organization. Businesses, regardless of their size, cannot function without
Institute Objective The 21st Century is marked by the continued penetration of Information Technology (IT) into all facets of the organization. Businesses, regardless of their size, cannot function without
FTA 2017 SEATTLE. Cybersecurity and the State Tax Threat Environment. Copyright FireEye, Inc. All rights reserved.
 FTA 2017 SEATTLE Cybersecurity and the State Tax Threat Environment 1 Agenda Cybersecurity Trends By the Numbers Attack Trends Defensive Trends State and Local Intelligence What Can You Do? 2 2016: Who
FTA 2017 SEATTLE Cybersecurity and the State Tax Threat Environment 1 Agenda Cybersecurity Trends By the Numbers Attack Trends Defensive Trends State and Local Intelligence What Can You Do? 2 2016: Who
Critical Infrastructure Protection Version 5
 Critical Infrastructure Protection Version 5 Tobias Whitney, Senior CIP Manager, Grid Assurance, NERC Compliance Committee Open Meeting August 9, 2017 Agenda Critical Infrastructure Protection (CIP) Standards
Critical Infrastructure Protection Version 5 Tobias Whitney, Senior CIP Manager, Grid Assurance, NERC Compliance Committee Open Meeting August 9, 2017 Agenda Critical Infrastructure Protection (CIP) Standards
Code of Ethics Certification 2018 CHECKLIST
 Code of Ethics Certification 2018 CHECKLIST Medical technology companies (both AdvaMed members and non-members) may participate in this certification program. The certification affirms that the company
Code of Ethics Certification 2018 CHECKLIST Medical technology companies (both AdvaMed members and non-members) may participate in this certification program. The certification affirms that the company
ISO 37001:2016 Anti-Bribery Management Systems - Benefits of Implementation and Certification
 ISO 37001:2016 Anti-Bribery Management Systems - Benefits of Implementation and Certification by Nor afiza Saim Senior General Manager Management System Certification Department SIRIM QAS International
ISO 37001:2016 Anti-Bribery Management Systems - Benefits of Implementation and Certification by Nor afiza Saim Senior General Manager Management System Certification Department SIRIM QAS International
Level 2 Diploma in Team Leading (combined qualification)
 Level 2 Diploma in Team Leading (combined qualification) Title Credit Value 40 Level 3 Reference Minimum GLH 206 Maximum GLH 260 Level 2 Diploma in Team Leading (QCF) S/016/374 To achieve a Level 2 Diploma
Level 2 Diploma in Team Leading (combined qualification) Title Credit Value 40 Level 3 Reference Minimum GLH 206 Maximum GLH 260 Level 2 Diploma in Team Leading (QCF) S/016/374 To achieve a Level 2 Diploma
2017 PORT SECURITY SEMINAR & EXPO. ISACA/CISM Information Security Management Training for Security Directors/Managers
 2017 PORT SECURITY SEMINAR & EXPO ISACA/CISM Information Security Management Training for Security Directors/Managers Agenda Introduction ISACA Information security vs. cybersecurity CISM certification
2017 PORT SECURITY SEMINAR & EXPO ISACA/CISM Information Security Management Training for Security Directors/Managers Agenda Introduction ISACA Information security vs. cybersecurity CISM certification
Uncovering the Risk of SAP Cyber Breaches
 Uncovering the Risk of SAP Cyber Breaches Research sponsored by Onapsis Independently Conducted by Ponemon Institute LLC February 2016 1 Part 1. Introduction Uncovering the Risks of SAP Cyber Breaches
Uncovering the Risk of SAP Cyber Breaches Research sponsored by Onapsis Independently Conducted by Ponemon Institute LLC February 2016 1 Part 1. Introduction Uncovering the Risks of SAP Cyber Breaches
Physical security advisory services Securing your organisation s future
 Physical security advisory services Securing your organisation s future August 2018 KPMG.com/in Physical security threats on the rise In a dynamic geo-political, economic and social environment, businesses
Physical security advisory services Securing your organisation s future August 2018 KPMG.com/in Physical security threats on the rise In a dynamic geo-political, economic and social environment, businesses
Risk: Security s New Compliance. Torsten George VP Worldwide Marketing and Products, Agiliance Professional Strategies - S23
 Risk: Security s New Compliance Torsten George VP Worldwide Marketing and Products, Agiliance Professional Strategies - S23 Agenda Market Dynamics Organizational Challenges Risk: Security s New Compliance
Risk: Security s New Compliance Torsten George VP Worldwide Marketing and Products, Agiliance Professional Strategies - S23 Agenda Market Dynamics Organizational Challenges Risk: Security s New Compliance
Measuring Cybersecurity Readiness: The Cybersecurity Maturity Model
 Measuring Cybersecurity Readiness: The Cybersecurity Maturity Model NCHICA Cybersecurity Thought Leader Forum Richard Roberts, CISO & Director of Technology Strategy 757.213.6875 www.divurgent.com What
Measuring Cybersecurity Readiness: The Cybersecurity Maturity Model NCHICA Cybersecurity Thought Leader Forum Richard Roberts, CISO & Director of Technology Strategy 757.213.6875 www.divurgent.com What
Cybersecurity. Securely enabling transformation and change
 Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
Cybersecurity Securely enabling transformation and change Contents... Cybersecurity overview Business drivers Cybersecurity strategy and roadmap Cybersecurity in practice CGI s cybersecurity offering Why
Cyber Risks in the Boardroom Conference
 Cyber Risks in the Boardroom Conference Managing Business, Legal and Reputational Risks Perspectives for Directors and Executive Officers Preparing Your Company to Identify, Mitigate and Respond to Risks
Cyber Risks in the Boardroom Conference Managing Business, Legal and Reputational Risks Perspectives for Directors and Executive Officers Preparing Your Company to Identify, Mitigate and Respond to Risks
CCISO Blueprint v1. EC-Council
 CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
Critical Infrastructure Resilience
 Critical Infrastructure Resilience Climate Resilience Webinar Series U.S. Department of Housing and Urban Development Disclaimer This presentation is intended to provide communities and states with the
Critical Infrastructure Resilience Climate Resilience Webinar Series U.S. Department of Housing and Urban Development Disclaimer This presentation is intended to provide communities and states with the
Investor Presentation
 Valued Quality. Delivered. Investor Presentation May 2011 For further information contact: aston.swift@intertek.com sarah.ogilvie@intertek.com +44 (0)20 7396 3400 Cautionary statement regarding forward-looking
Valued Quality. Delivered. Investor Presentation May 2011 For further information contact: aston.swift@intertek.com sarah.ogilvie@intertek.com +44 (0)20 7396 3400 Cautionary statement regarding forward-looking
Getting Your Privacy House in Order
 Getting Your Privacy House in Order Lisa J. Sotto Ewa Abrams Victoria King Partner Associate General Counsel Global Privacy Officer Hunton & Williams LLP Tiffany & Co. UPS (212) 309-1223 (212) 230-5351
Getting Your Privacy House in Order Lisa J. Sotto Ewa Abrams Victoria King Partner Associate General Counsel Global Privacy Officer Hunton & Williams LLP Tiffany & Co. UPS (212) 309-1223 (212) 230-5351
CFE Exam Review Course
 CFE Exam Review Course Leading Excellence in Banking BIBF plays a vital role in the training and development of human capital in the Kingdom of Bahrain. Our commitment to excellence has strengthened our
CFE Exam Review Course Leading Excellence in Banking BIBF plays a vital role in the training and development of human capital in the Kingdom of Bahrain. Our commitment to excellence has strengthened our
Emerging Technologies The risks they pose to your organisations
 Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
Building YOUR Privacy Program: One Size Does Not Fit All. IBM Security Services
 Building YOUR Privacy Program: One Size Does Not Fit All Justine Gottshall Partner, InfoLawGroup, LLP Chief Privacy Officer, Signal Jgottshall@infolawgroup.com Adam Nelson Executive Consultant Global Data
Building YOUR Privacy Program: One Size Does Not Fit All Justine Gottshall Partner, InfoLawGroup, LLP Chief Privacy Officer, Signal Jgottshall@infolawgroup.com Adam Nelson Executive Consultant Global Data
IT Monitoring Tool Gaps are Impacting the Business A survey of IT Professionals and Executives
 IT Monitoring Tool Gaps are Impacting the Business A survey of IT Professionals and Executives June 2018 1 Executive Summary This research finds that large enterprise customers and employees endure a substantial
IT Monitoring Tool Gaps are Impacting the Business A survey of IT Professionals and Executives June 2018 1 Executive Summary This research finds that large enterprise customers and employees endure a substantial
Isaca EXAM - CISM. Certified Information Security Manager. Buy Full Product.
 Isaca EXAM - CISM Certified Information Security Manager Buy Full Product http://www.examskey.com/cism.html Examskey Isaca CISM exam demo product is here for you to test the quality of the product. This
Isaca EXAM - CISM Certified Information Security Manager Buy Full Product http://www.examskey.com/cism.html Examskey Isaca CISM exam demo product is here for you to test the quality of the product. This
Quality Assurance and IT Risk Management
 Quality Assurance and IT Risk Deutsche Bank s QA and Testing Transformation Journey Michael Venditti Head of Enterprise Testing Services, Deutsche Bank IT RISK - REGULATORY GOVERNANCE Major shifts in the
Quality Assurance and IT Risk Deutsche Bank s QA and Testing Transformation Journey Michael Venditti Head of Enterprise Testing Services, Deutsche Bank IT RISK - REGULATORY GOVERNANCE Major shifts in the
August Objectives. Agenda. Promoting Your Professional Development with ACMPE. Describe the foundation and value of certification and fellowship
 Promoting Your Professional Development with ACMPE 2015 MGMA-Louisiana Annual Conference August 19-21, 2015 Objectives Describe the foundation and value of certification and fellowship Explain the steps
Promoting Your Professional Development with ACMPE 2015 MGMA-Louisiana Annual Conference August 19-21, 2015 Objectives Describe the foundation and value of certification and fellowship Explain the steps
TSC Business Continuity & Disaster Recovery Session
 TSC Business Continuity & Disaster Recovery Session Mohamed Ashmawy Infrastructure Consulting Pursuit Hewlett-Packard Enterprise Saudi Arabia Mohamed.ashmawy@hpe.com Session Objectives and Outcomes Objectives
TSC Business Continuity & Disaster Recovery Session Mohamed Ashmawy Infrastructure Consulting Pursuit Hewlett-Packard Enterprise Saudi Arabia Mohamed.ashmawy@hpe.com Session Objectives and Outcomes Objectives
SOLUTION BRIEF RSA ARCHER IT & SECURITY RISK MANAGEMENT
 RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Understanding Cybersecurity Talent Needs Findings From Surveys of Business Executives and College Presidents
 Understanding Cybersecurity Talent Needs Findings From Surveys of Business Executives and College Presidents BHEF_Report_mk_050817_ms Acknowledgements This report is supported primarily by a grant from
Understanding Cybersecurity Talent Needs Findings From Surveys of Business Executives and College Presidents BHEF_Report_mk_050817_ms Acknowledgements This report is supported primarily by a grant from
Level 2 Diploma in Team Leading (combined qualification)
 Level 2 Diploma in Team Leading (combined qualification) Title Credit Value 40 Level 3 Reference Minimum GLH 201 Maximum GLH 259 Level 2 Diploma in Team Leading (QCF) S/016/614 To achieve a Level 2 Diploma
Level 2 Diploma in Team Leading (combined qualification) Title Credit Value 40 Level 3 Reference Minimum GLH 201 Maximum GLH 259 Level 2 Diploma in Team Leading (QCF) S/016/614 To achieve a Level 2 Diploma
EGM, 9-10 December A World that Counts: Mobilising the Data Revolution for Sustainable Development. 9 December 2014 BACKGROUND
 A World that Counts: Mobilising the Data Revolution for Sustainable Development 9 December 2014 BACKGROUND 1 Creation of the group Establishment of an Independent Expert Advisory Group on the Data Revolution
A World that Counts: Mobilising the Data Revolution for Sustainable Development 9 December 2014 BACKGROUND 1 Creation of the group Establishment of an Independent Expert Advisory Group on the Data Revolution
Tripwire State of Container Security Report
 RESEARCH Tripwire State of Container Security Report January 2019 FOUNDATIONAL CONTROLS FOR SECURITY, COMPLIANCE & IT OPERATIONS As DevOps continues to drive increased use of containers, security teams
RESEARCH Tripwire State of Container Security Report January 2019 FOUNDATIONAL CONTROLS FOR SECURITY, COMPLIANCE & IT OPERATIONS As DevOps continues to drive increased use of containers, security teams
Enabling efficiency through Data Governance: a phased approach
 Enabling efficiency through Data Governance: a phased approach Transform your process efficiency, decision-making, and customer engagement by improving data accuracy An Experian white paper Enabling efficiency
Enabling efficiency through Data Governance: a phased approach Transform your process efficiency, decision-making, and customer engagement by improving data accuracy An Experian white paper Enabling efficiency
Exam4Tests. Latest exam questions & answers help you to pass IT exam test easily
 Exam4Tests http://www.exam4tests.com Latest exam questions & answers help you to pass IT exam test easily Exam : CISM Title : Certified Information Security Manager Vendor : ISACA Version : DEMO 1 / 10
Exam4Tests http://www.exam4tests.com Latest exam questions & answers help you to pass IT exam test easily Exam : CISM Title : Certified Information Security Manager Vendor : ISACA Version : DEMO 1 / 10
Reducing Cybersecurity Costs & Risk through Automation Technologies
 Reducing Cybersecurity Costs & Risk through Automation Technologies Sponsored by Juniper Networks Independently conducted by Ponemon Institute LLC Publication Date: November 2017 Ponemon Institute Research
Reducing Cybersecurity Costs & Risk through Automation Technologies Sponsored by Juniper Networks Independently conducted by Ponemon Institute LLC Publication Date: November 2017 Ponemon Institute Research
Nokia Conference Call 1Q 2012 Financial Results
 Nokia Internal Use Only Nokia Conference Call 1Q 2012 Financial Results April 19 th, 2012 15.00 Helsinki time 8.00 New York time Stephen Elop President & CEO Timo Ihamuotila CFO Matt Shimao Head of Investor
Nokia Internal Use Only Nokia Conference Call 1Q 2012 Financial Results April 19 th, 2012 15.00 Helsinki time 8.00 New York time Stephen Elop President & CEO Timo Ihamuotila CFO Matt Shimao Head of Investor
Department of Management Services REQUEST FOR INFORMATION
 RESPONSE TO Department of Management Services REQUEST FOR INFORMATION Cyber-Security Assessment, Remediation, and Identity Protection, Monitoring, and Restoration Services September 3, 2015 250 South President
RESPONSE TO Department of Management Services REQUEST FOR INFORMATION Cyber-Security Assessment, Remediation, and Identity Protection, Monitoring, and Restoration Services September 3, 2015 250 South President
What It Takes to be a CISO in 2017
 What It Takes to be a CISO in 2017 Doug Copley Deputy CISO Sr. Security & Privacy Strategist February 2017 IMAGINE You re the CISO In Bangladesh Of a bank On a Friday when you re closed You realize 6 huge
What It Takes to be a CISO in 2017 Doug Copley Deputy CISO Sr. Security & Privacy Strategist February 2017 IMAGINE You re the CISO In Bangladesh Of a bank On a Friday when you re closed You realize 6 huge
Cyber Security: Threat and Prevention
 Expand Your Horizons Webinar Series Cyber Security: Threat and Prevention February 24, 2015 1:00 1:45pm The Webinar will begin shortly. You can ask a question in the box on the right hand side. We will
Expand Your Horizons Webinar Series Cyber Security: Threat and Prevention February 24, 2015 1:00 1:45pm The Webinar will begin shortly. You can ask a question in the box on the right hand side. We will
building a security culture to counter emerging cybersecurity threats
 Academic Medical Center Security and Privacy Conference June 2017 building a security culture to counter emerging cybersecurity threats Chuck Kesler, MBA, CISSP, CISM Chief Information Security Officer
Academic Medical Center Security and Privacy Conference June 2017 building a security culture to counter emerging cybersecurity threats Chuck Kesler, MBA, CISSP, CISM Chief Information Security Officer
Nomination Form Architecture Excellence Awards 2018
 Nomination Form Architecture Excellence Awards 2018 Presented by: [Presenter's name] Company Overview 1. Name of the Company: 2. Name of the CEO (Chief Executive Officer): 3. Name of the CIO (Chief Information
Nomination Form Architecture Excellence Awards 2018 Presented by: [Presenter's name] Company Overview 1. Name of the Company: 2. Name of the CEO (Chief Executive Officer): 3. Name of the CIO (Chief Information
Healthcare Security Success Story
 Regional Forum on Cybersecurity in the Era of Emerging Technologies & the Second Meeting of the Successful Administrative Practices -2017 Cairo, Egypt 28-29 November 2017 Healthcare Security Success Story
Regional Forum on Cybersecurity in the Era of Emerging Technologies & the Second Meeting of the Successful Administrative Practices -2017 Cairo, Egypt 28-29 November 2017 Healthcare Security Success Story
EUROPEAN ICT PROFESSIONAL ROLE PROFILES VERSION 2 CWA 16458:2018 LOGFILE
 EUROPEAN ICT PROFESSIONAL ROLE PROFILES VERSION 2 CWA 16458:2018 LOGFILE Overview all ICT Profile changes in title, summary, mission and from version 1 to version 2 Versions Version 1 Version 2 Role Profile
EUROPEAN ICT PROFESSIONAL ROLE PROFILES VERSION 2 CWA 16458:2018 LOGFILE Overview all ICT Profile changes in title, summary, mission and from version 1 to version 2 Versions Version 1 Version 2 Role Profile
The Resilient Incident Response Platform
 The Resilient Incident Response Platform Accelerate Your Response with the Industry s Most Advanced, Battle-Tested Platform for Incident Response Orchestration The Resilient Incident Response Platform
The Resilient Incident Response Platform Accelerate Your Response with the Industry s Most Advanced, Battle-Tested Platform for Incident Response Orchestration The Resilient Incident Response Platform
SecOps : Security Operations. Saurav Sinha Head of Presales India
 SecOps : Security Operations Saurav Sinha Head of Presales India 1 The World s Best and Most Innovative Companies Trust BMC #1 Ranked ITOM Vendor by Gartner for 3 consecutive years 300+ Patents $8B Investment
SecOps : Security Operations Saurav Sinha Head of Presales India 1 The World s Best and Most Innovative Companies Trust BMC #1 Ranked ITOM Vendor by Gartner for 3 consecutive years 300+ Patents $8B Investment
Addressing Vulnerabilities By Integrating Your Incident Response Plans. Brian Coates Enaxis Consulting
 Addressing Vulnerabilities By Integrating Your Incident Response Plans Brian Coates Enaxis Consulting Contents Enaxis Introduction Presenter Bio: Brian Coates Incident Response / Incident Management in
Addressing Vulnerabilities By Integrating Your Incident Response Plans Brian Coates Enaxis Consulting Contents Enaxis Introduction Presenter Bio: Brian Coates Incident Response / Incident Management in
BUILDING CYBERSECURITY CAPABILITY, MATURITY, RESILIENCE
 BUILDING CYBERSECURITY CAPABILITY, MATURITY, RESILIENCE 1 WHAT IS YOUR SITUATION? Excel spreadsheets Manually intensive Too many competing priorities Lack of effective reporting Too many consultants Not
BUILDING CYBERSECURITY CAPABILITY, MATURITY, RESILIENCE 1 WHAT IS YOUR SITUATION? Excel spreadsheets Manually intensive Too many competing priorities Lack of effective reporting Too many consultants Not
Changing the Game: An HPR Approach to Cyber CRM007
 Speakers: Changing the Game: An HPR Approach to Cyber CRM007 Michal Gnatek, Senior Vice President, Marsh & McLennan Karen Miller, Sr. Treasury & Risk Manager, FireEye, Inc. Learning Objectives At the end
Speakers: Changing the Game: An HPR Approach to Cyber CRM007 Michal Gnatek, Senior Vice President, Marsh & McLennan Karen Miller, Sr. Treasury & Risk Manager, FireEye, Inc. Learning Objectives At the end
RICE COUNTY, MN GETTING TO KNOW RICE COUNTY & THE RICE COUNTY COMMUNITIES FAM Tour ~ August 12, 2014
 RICE COUNTY, MN GETTING TO KNOW RICE COUNTY & THE RICE COUNTY COMMUNITIES 2014 FAM Tour ~ August 12, 2014 AN INTRODUCTION TO RICE COUNTY Who is RICE COUNTY our people & our companies Where is RICE COUNTY
RICE COUNTY, MN GETTING TO KNOW RICE COUNTY & THE RICE COUNTY COMMUNITIES 2014 FAM Tour ~ August 12, 2014 AN INTRODUCTION TO RICE COUNTY Who is RICE COUNTY our people & our companies Where is RICE COUNTY
Top 10 Global Threat Rank by Source
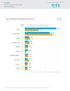 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Technical Requirements COMPLIANCE AND FRAUD HELPLINE AND CASE MANAGEMENT SERVICES
 Technical Requirements COMPLIANCE AND FRAUD HELPLINE AND CASE MANAGEMENT SERVICES No. Requirement Vendor #1 1. 1. Incident Reporting Reporting methods are available to all employees 24 hours per day, 365
Technical Requirements COMPLIANCE AND FRAUD HELPLINE AND CASE MANAGEMENT SERVICES No. Requirement Vendor #1 1. 1. Incident Reporting Reporting methods are available to all employees 24 hours per day, 365
