Potential business impact of cybercrime on small and medium enterprises (SMEs) in 2016 Survey report USA. October, 2016
|
|
|
- Moses Clark
- 5 years ago
- Views:
Transcription
1 Potential business impact of cybercrime on small and medium enterprises (SMEs) in 2016 Survey report October, 2016
2 Table of Contents Project design P. 3 Results Summary P. 4 Year-on-year comparison P. 5 Comparison to countries of the same region P. 6 Sample composition P. 7 2
3 Project Design Method Target Group Small and Medium Enterprises (up to 250 full-time employees) Telephone Interviews (CATI) Average length: 6 minutes CEO/Owner, GM, CFO/Treasurer, COO/Head of Operations Sample structure Indication of a trend in score is significantly higher vs interviews, representative in terms of enterprise size (# of full-time employees) and industry 2016 score is significantly lower vs
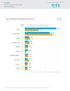
4 A larger share of SMEs perceive their magnitude as significant enough to become victims of cybercrime Results: Summary Steal customer data (22.5%) remains the most critical risk of cybercrime in the United States Compared to one year ago, fewer SMEs think their company is too insignificant for cyber criminals (9.5%) Steal customer data, Theft of money / savings and Disrupt business ranked as top 3 risks of cybercrime in the US 4
5 Decreasing share of US SMEs think that their company is too insignificant for cyber criminals Results: Year-on-year comparison Statistics in % Damage reputation Steal intellectual property Steal customer data Steal employee data Theft of money / savings Use your identity maliciously Disrupt business (e.g. introduce a virus, take down website, etc.) Cause third party lawsuits I think our company is too insignificant for cyber criminals None of our business data are digitally stored We have fully functioning updated protection in place I haven't thought about this and have no opinion today Don t know (n=200) 2015 (n=200) Q3: Now we would like you to think about cybercrime. How could cyber criminals affect your business if at all? Please select up to 2 answers that are most critical to your business. Base: n= score is significantly higher vs score is significantly lower vs
6 Steal customer data, Theft of money / savings, and Disrupt business as top 3 risks of cybercrime in the US Results: Comparison to countries of the same region Note: A fair country comparison needs to consider both the chart on the left (bubbles) and the chart on the right (ranks). Statistics in % Ranks Damage reputation Steal intellectual property Steal customer data Steal employee data Theft of money / savings Use your identity maliciously Disrupt business (e.g. introduce a virus, take down website, etc.) Cause third party lawsuits I think our company is too insignificant for cyber criminals None of our business data are digitally stored We have fully functioning and updated protection in place I haven't thought about this and have no opinion today Don t know % 16 30% 31%+ Q3: Now we would like you to think about cybercrime. How could cyber criminals affect your business if at all? Please select up to 2 answers that are most critical to your business. Base: n=200 6
7 Sample Composition 1/2 Function and full-time employees Statistics in % North America Function CEO/Owner 39.0 CFO/Treasurer 11.0 COO/Head of operations 12.0 General Manager 38.0 Full-time employees 0 employees to 9 employees to 19 employees to 49 employees to 99 employees to 250 employees
8 Sample Composition 2/2 Revenue and Industry Statistics in % North America Revenue* Up to 2 Million EUR 28.0 More than 2 to 5 Million EUR 19.0 More than 5 to 10 Million EUR 8.5 More than 10 to 50 Million EUR 6.5 More than 50 Million EUR 1.0 Industry Agriculture 3.0 Manufacturing and construction 18.0 Wholesale and retail trade 20.0 Information and communication 8.0 Financial activities (including insurance) 12.0 Administrative and support service 2.0 Public administration 2.0 Transport and storage 10.0 Accommodation and food service 11.0 Consumer services 5.0 Other service activities 9.0 *Figures don t sum up to 100% due to DK / No Answer 8
The Cyber War on Small Business
 The Cyber War on Small Business Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Meet Our Speaker Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Previously worked as Cyber
The Cyber War on Small Business Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Meet Our Speaker Dillon Behr Executive Lines Broker Risk Placement Services, Inc. Previously worked as Cyber
Cyber Attack: Is Your Business at Risk?
 15 July 2017 Cyber Attack: Is Your Business at Risk? Stanley Wong Regional Head of Financial Lines, Asia Pacific Agenda Some common misconceptions by SMEs around cyber protection Cyber Claims and Industry
15 July 2017 Cyber Attack: Is Your Business at Risk? Stanley Wong Regional Head of Financial Lines, Asia Pacific Agenda Some common misconceptions by SMEs around cyber protection Cyber Claims and Industry
CRITICAL INFRASTRUCTURE AND CYBER THREAT CRITICAL INFRASTRUCTURE AND CYBER THREAT
 CRITICAL INFRASTRUCTURE SAFER CITIES. THRIVING COMMUNITIES. Critical Infrastructure sectors have become prime targets for cyber criminals due to their vitality to a nation s security and stability. 16
CRITICAL INFRASTRUCTURE SAFER CITIES. THRIVING COMMUNITIES. Critical Infrastructure sectors have become prime targets for cyber criminals due to their vitality to a nation s security and stability. 16
Cyber Security in Smart Commercial Buildings 2017 to 2021
 Smart Buildings Cyber Security in Smart Commercial Buildings 2017 to 2021 Published: Q2 2017 Cyber Security in Smart Buildings Synopsis 2017 This report will help all stakeholders and investors in the
Smart Buildings Cyber Security in Smart Commercial Buildings 2017 to 2021 Published: Q2 2017 Cyber Security in Smart Buildings Synopsis 2017 This report will help all stakeholders and investors in the
Why you MUST protect your customer data
 Why you MUST protect your customer data If you think you re exempt from compliance with customer data security and privacy laws because you re a small business, think again. Businesses of all sizes are
Why you MUST protect your customer data If you think you re exempt from compliance with customer data security and privacy laws because you re a small business, think again. Businesses of all sizes are
Cyber Risk for. Small and Medium-Sized Enterprises (SMEs)
 R Cyber Risk for Small and Medium-Sized Enterprises (SMEs) Presenters: Jing Guo, Junyi Yang 09/09/2016 New York Times Headlines: No business too small to be hacked Rokenbok Education 7 employees Restructure
R Cyber Risk for Small and Medium-Sized Enterprises (SMEs) Presenters: Jing Guo, Junyi Yang 09/09/2016 New York Times Headlines: No business too small to be hacked Rokenbok Education 7 employees Restructure
Personal Cybersecurity
 Personal Cybersecurity The Basic Principles Jeremiah School, CEO How big is the issue? 9 8 7 6 5 4 3 2 1 Estimated global damages in 2018 0 2016 2018 2020 2022 2024 2026 2028 2030 Internet Users Billions
Personal Cybersecurity The Basic Principles Jeremiah School, CEO How big is the issue? 9 8 7 6 5 4 3 2 1 Estimated global damages in 2018 0 2016 2018 2020 2022 2024 2026 2028 2030 Internet Users Billions
Combating Cyber Risk in the Supply Chain
 SESSION ID: CIN-W10 Combating Cyber Risk in the Supply Chain Ashok Sankar Senior Director Cyber Strategy Raytheon Websense @ashoksankar Introduction The velocity of data breaches is accelerating at an
SESSION ID: CIN-W10 Combating Cyber Risk in the Supply Chain Ashok Sankar Senior Director Cyber Strategy Raytheon Websense @ashoksankar Introduction The velocity of data breaches is accelerating at an
2015 VORMETRIC INSIDER THREAT REPORT
 Research Conducted by Research Analyzed by 2015 VORMETRIC INSIDER THREAT REPORT Trends and Future Directions in Data Security GLOBAL EDITION #2015InsiderThreat EXECUTIVE PERSPECTIVE 1 INSIDER THREATS:
Research Conducted by Research Analyzed by 2015 VORMETRIC INSIDER THREAT REPORT Trends and Future Directions in Data Security GLOBAL EDITION #2015InsiderThreat EXECUTIVE PERSPECTIVE 1 INSIDER THREATS:
2014 NETWORK SECURITY & CYBER RISK MANAGEMENT: THE THIRD ANNUAL SURVEY OF ENTERPRISE-WIDE CYBER RISK MANAGEMENT PRACTICES IN EUROPE
 2014 NETWORK SECURITY & CYBER RISK MANAGEMENT: THE THIRD ANNUAL SURVEY OF ENTERPRISE-WIDE CYBER RISK MANAGEMENT PRACTICES IN EUROPE February 2014 Sponsored by: 2014 Network Security & Cyber Risk Management:
2014 NETWORK SECURITY & CYBER RISK MANAGEMENT: THE THIRD ANNUAL SURVEY OF ENTERPRISE-WIDE CYBER RISK MANAGEMENT PRACTICES IN EUROPE February 2014 Sponsored by: 2014 Network Security & Cyber Risk Management:
Reference Research: Disk-based Storage Capacity Trends Date: September 2012 Author: Bill Lundell, Senior Research Analyst
 Research Brief Reference Research: Disk-based Storage Capacity Trends Date: September 2012 Author: Bill Lundell, Senior Research Analyst Abstract: ESG Reference Research includes data-centric reports and
Research Brief Reference Research: Disk-based Storage Capacity Trends Date: September 2012 Author: Bill Lundell, Senior Research Analyst Abstract: ESG Reference Research includes data-centric reports and
2014 NETWORK SECURITY & CYBER RISK MANAGEMENT:
 2014 NETWORK SECURITY & CYBER RISK MANAGEMENT: A SURVEY OF ENTERPRISE-WIDE CYBER RISK MANAGEMENT PRACTICES IN THE ASIA-PACIFIC REGION April 2014 Sponsored by: 2014 NETWORK SECURITY & CYBER RISK MANAGEMENT:
2014 NETWORK SECURITY & CYBER RISK MANAGEMENT: A SURVEY OF ENTERPRISE-WIDE CYBER RISK MANAGEMENT PRACTICES IN THE ASIA-PACIFIC REGION April 2014 Sponsored by: 2014 NETWORK SECURITY & CYBER RISK MANAGEMENT:
THE IMPACT OF MOBILE DEVICES ON INFORMATION SECURITY:
 June 2013 Sponsored by Introduction Mobile devices cause ongoing concern for IT teams responsible for information security. Sensitive corporate information can be easily transported and lost, while the
June 2013 Sponsored by Introduction Mobile devices cause ongoing concern for IT teams responsible for information security. Sensitive corporate information can be easily transported and lost, while the
IC B01: Internet Security Threat Report: How to Stay Protected
 IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
IC B01: Internet Security Threat Report: How to Stay Protected Piero DePaoli Director, Product Marketing IC B01: Internet Security Threat Report: How to Stay Protected 1 Topics 1 Targeted Attacks 2 Spam
Cyber Crime Update. Mark Brett Programme Director February 2016
 Cyber Crime Update Mark Brett Programme Director February 2016 What is Cyber Crime? What are the current threats? What is the capability of local and regional Cyber Crime Investigations? What support is
Cyber Crime Update Mark Brett Programme Director February 2016 What is Cyber Crime? What are the current threats? What is the capability of local and regional Cyber Crime Investigations? What support is
Panda Security 2010 Page 1
 Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Panda Security 2010 Page 1 Executive Summary The malware economy is flourishing and affecting both consumers and businesses of all sizes. The reality is that cybercrime is growing exponentially in frequency
Trends in Next Generation Data Center Infrastructure. Summary Results January 2018
 Trends in Next Generation Data Center Infrastructure Survey Summary Between October 2017 and January 2018 Gatepoint Research invited selected executives to participate in a survey themed Trends in Next
Trends in Next Generation Data Center Infrastructure Survey Summary Between October 2017 and January 2018 Gatepoint Research invited selected executives to participate in a survey themed Trends in Next
THE LIFE AND TIMES OF CYBERSECURITY PROFESSIONALS
 SESSION ID: AST3-R02 THE LIFE AND TIMES OF CYBERSECURITY PROFESSIONALS Jon Oltsik Senior Principal Analyst Enterprise Strategy Group @joltsik Candy Alexander, CISSP CISM International Board Director ISSA
SESSION ID: AST3-R02 THE LIFE AND TIMES OF CYBERSECURITY PROFESSIONALS Jon Oltsik Senior Principal Analyst Enterprise Strategy Group @joltsik Candy Alexander, CISSP CISM International Board Director ISSA
Building a Threat Intelligence Program
 WHITE PAPER Building a Threat Intelligence Program Research findings on best practices and impact www. Building a Threat Intelligence Program 2 Methodology FIELD DATES: March 30th - April 4th 2018 351
WHITE PAPER Building a Threat Intelligence Program Research findings on best practices and impact www. Building a Threat Intelligence Program 2 Methodology FIELD DATES: March 30th - April 4th 2018 351
Tripwire State of Container Security Report
 RESEARCH Tripwire State of Container Security Report January 2019 FOUNDATIONAL CONTROLS FOR SECURITY, COMPLIANCE & IT OPERATIONS As DevOps continues to drive increased use of containers, security teams
RESEARCH Tripwire State of Container Security Report January 2019 FOUNDATIONAL CONTROLS FOR SECURITY, COMPLIANCE & IT OPERATIONS As DevOps continues to drive increased use of containers, security teams
Governance Ideas Exchange
 www.pwc.com.au Anatomy of a Hack Governance Ideas Exchange Robert Di Pietro October 2018 Cyber Security Anatomy of a Hack Cyber Security Introduction Who are the bad guys? Profiling the victim Insights
www.pwc.com.au Anatomy of a Hack Governance Ideas Exchange Robert Di Pietro October 2018 Cyber Security Anatomy of a Hack Cyber Security Introduction Who are the bad guys? Profiling the victim Insights
2007 AT&T Business Continuity Study CLEVELAND Results
 2007 AT&T Business Continuity Study CLEVELAND Results Methodology The following results are based on a telephone survey of 100 Information Technology (IT) executives in the Cleveland metropolitan area.
2007 AT&T Business Continuity Study CLEVELAND Results Methodology The following results are based on a telephone survey of 100 Information Technology (IT) executives in the Cleveland metropolitan area.
2017 RIMS CYBER SURVEY
 2017 RIMS CYBER SURVEY This report marks the third year that RIMS has surveyed its membership about cyber risks and transfer practices. This is, of course, a topic that only continues to captivate the
2017 RIMS CYBER SURVEY This report marks the third year that RIMS has surveyed its membership about cyber risks and transfer practices. This is, of course, a topic that only continues to captivate the
Top 10 Global Threat Rank by Source
 Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Symantec Internet Security Threat Report, Volume 21 1 Top 10 Threat by Source WORLD RANK PERCENTAGE OF GLOBAL DETECTIONS China 1 2 10.6% 23.7% United States 2 1 18.9% 20.7% India Netherlands Taiwan Turkey
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
THE IMPACT OF MOBILE DEVICES ON INFORMATION SECURITY:
 October Sponsored by Introduction Mobile devices cause ongoing concern for IT teams responsible for information security. Sensitive corporate information is easily transported outside of managed environments,
October Sponsored by Introduction Mobile devices cause ongoing concern for IT teams responsible for information security. Sensitive corporate information is easily transported outside of managed environments,
Overview Of The German Energy Efficiency Market
 Overview Of The German Energy Efficiency Market Dr. Tina Flegel, Deputy Head of Division, Federal Energy Efficiency Center Energieeffizienzmarkt und -dienstleistungen in Deutschland und Frankreich, Berlin,
Overview Of The German Energy Efficiency Market Dr. Tina Flegel, Deputy Head of Division, Federal Energy Efficiency Center Energieeffizienzmarkt und -dienstleistungen in Deutschland und Frankreich, Berlin,
Template for data breach notifications I
 Template for data breach notifications I I. Identification of the data controller This information is exclusively for the relevant Data Protection Authority, not to be shared with third-parties. 1. Details
Template for data breach notifications I I. Identification of the data controller This information is exclusively for the relevant Data Protection Authority, not to be shared with third-parties. 1. Details
2017 Ethics & Compliance Hotline & Incident Management Benchmark Report Webinar
 2017 Ethics & Compliance Hotline & Incident Management Benchmark Report Webinar Presented by Carrie Penman Chief Compliance Officer & Senior Vice President, Advisory Services Edwin O Mara Operations Manager,
2017 Ethics & Compliance Hotline & Incident Management Benchmark Report Webinar Presented by Carrie Penman Chief Compliance Officer & Senior Vice President, Advisory Services Edwin O Mara Operations Manager,
Socioeconomic Overview of Ohio
 2 Socioeconomic Overview of Ohio Introduction The magnitude of the economic impact of Ohio s airports is linked to the demand that is generated within the state for aviation goods and services. As population,
2 Socioeconomic Overview of Ohio Introduction The magnitude of the economic impact of Ohio s airports is linked to the demand that is generated within the state for aviation goods and services. As population,
Are you safe? Your business growth strategies are at the heart of the cyber risks your organization faces
 Are you safe? Your business growth strategies are at the heart of the cyber risks your organization faces 36 Deloitte A Middle East Point of View Summer 2015 Cyber Security Most reports on cyber security
Are you safe? Your business growth strategies are at the heart of the cyber risks your organization faces 36 Deloitte A Middle East Point of View Summer 2015 Cyber Security Most reports on cyber security
RISING CYBER SECURITY CAPABILITY WITH A UNIQUE NETWORK OF TRUSTED PARTNERS. Jan De Blauwe Chairman Cyber Security Coalition Belgium
 RISING CYBER SECURITY CAPABILITY WITH A UNIQUE NETWORK OF TRUSTED PARTNERS Jan De Blauwe Chairman Cyber Security Coalition Belgium Brussels, 3 October 2017 FACTS AND FIGURES ABOUT BELGIAN COMPANIES 79%
RISING CYBER SECURITY CAPABILITY WITH A UNIQUE NETWORK OF TRUSTED PARTNERS Jan De Blauwe Chairman Cyber Security Coalition Belgium Brussels, 3 October 2017 FACTS AND FIGURES ABOUT BELGIAN COMPANIES 79%
DeMystifying Data Breaches and Information Security Compliance
 May 22-25, 2016 Los Angeles Convention Center Los Angeles, California DeMystifying Data Breaches and Information Security Compliance Presented by James Harrison OM32 5/25/2016 3:00 PM - 4:15 PM The handouts
May 22-25, 2016 Los Angeles Convention Center Los Angeles, California DeMystifying Data Breaches and Information Security Compliance Presented by James Harrison OM32 5/25/2016 3:00 PM - 4:15 PM The handouts
2012 Cost of Cyber Crime Study: United States
 2012 Cost of Cyber Crime Study: United States Sponsored by HP Enterprise Security Independently conducted by Ponemon Institute LLC Publication Date: October 2012 Ponemon Institute Research Report Part
2012 Cost of Cyber Crime Study: United States Sponsored by HP Enterprise Security Independently conducted by Ponemon Institute LLC Publication Date: October 2012 Ponemon Institute Research Report Part
2007 AT&T Business Continuity Study BOSTON Results
 2007 AT&T Business Continuity Study BOSTON Results Methodology The following results are based on a telephone survey of 100 Information Technology (IT) executives in the Boston metropolitan area. The sample
2007 AT&T Business Continuity Study BOSTON Results Methodology The following results are based on a telephone survey of 100 Information Technology (IT) executives in the Boston metropolitan area. The sample
2005 E-Crime Watch Survey Survey Results Conducted by CSO magazine in cooperation with the U.S. Secret Service and CERT Coordination Center
 OVERALL RESULTS E-Crime Watch Survey: 2005 Field Dates: 3/3/05 3/14/05 Total completed surveys: 819 Margin of Error: +/- 3.4% NOTE TO EDITOR For the purpose of this survey, electronic crime, intrusion,
OVERALL RESULTS E-Crime Watch Survey: 2005 Field Dates: 3/3/05 3/14/05 Total completed surveys: 819 Margin of Error: +/- 3.4% NOTE TO EDITOR For the purpose of this survey, electronic crime, intrusion,
Insider Threat Program: Protecting the Crown Jewels. Monday, March 2, 2:15 pm - 3:15 pm
 Insider Threat Program: Protecting the Crown Jewels Monday, March 2, 2:15 pm - 3:15 pm Take Away Identify your critical information Recognize potential insider threats What happens after your critical
Insider Threat Program: Protecting the Crown Jewels Monday, March 2, 2:15 pm - 3:15 pm Take Away Identify your critical information Recognize potential insider threats What happens after your critical
ISACA January 2016 Cybersecurity Snapshot US Results. Number of respondents (n) = 862
 ISACA January 2016 Cybersecurity Snapshot US Results www.isaca.org/2016-cybersecurity-snapshot Number of respondents (n) = 862 Media Inquiries: Kristen Kessinger, ISACA, +1.847.660.5512, news@isaca.org
ISACA January 2016 Cybersecurity Snapshot US Results www.isaca.org/2016-cybersecurity-snapshot Number of respondents (n) = 862 Media Inquiries: Kristen Kessinger, ISACA, +1.847.660.5512, news@isaca.org
Midsize Business Voice Service Spending Steady for 2003
 End-User Analysis Midsize Business Voice Service Spending Steady for 23 Abstract: Telecom service providers need to know the voice telecom spending plans of the margin-rich midsize business segment in
End-User Analysis Midsize Business Voice Service Spending Steady for 23 Abstract: Telecom service providers need to know the voice telecom spending plans of the margin-rich midsize business segment in
Cyber Security Updates and Trends Affecting the Real Estate Industry
 Cyber Security Updates and Trends Affecting the Real Estate Industry What, Why, and How? Agenda Cyber Security Today Changes to Security Standards and Trends Protecting Yourself and Your Organization Takeways
Cyber Security Updates and Trends Affecting the Real Estate Industry What, Why, and How? Agenda Cyber Security Today Changes to Security Standards and Trends Protecting Yourself and Your Organization Takeways
SMALL BUSINESS CYBERSECURITY SURVIVAL GUIDE
 SMALL BUSINESS CYBERSECURITY SURVIVAL GUIDE Small business cybersecurity survival guide By Stephen Cobb, ESET Senior Security Researcher Computers and the internet bring many benefits to small businesses,
SMALL BUSINESS CYBERSECURITY SURVIVAL GUIDE Small business cybersecurity survival guide By Stephen Cobb, ESET Senior Security Researcher Computers and the internet bring many benefits to small businesses,
2013 Cost of Cyber Crime Study: Global Report
 2013 Cost of Cyber Crime Study: Global Report Sponsored by HP Enterprise Security Independently conducted by Ponemon Institute LLC Publication Date: October 2013 Ponemon Institute Research Report Part
2013 Cost of Cyber Crime Study: Global Report Sponsored by HP Enterprise Security Independently conducted by Ponemon Institute LLC Publication Date: October 2013 Ponemon Institute Research Report Part
Global security intelligence. YoUR DAtA UnDeR siege: DeFenD it with encryption. #enterprisesec kaspersky.com/enterprise
 Global security intelligence YoUR DAtA UnDeR siege: DeFenD it with encryption #enterprisesec kaspersky.com/enterprise Contents Your Data Under Siege: Defend it with Encryption 3 Steps Taken to Minimise
Global security intelligence YoUR DAtA UnDeR siege: DeFenD it with encryption #enterprisesec kaspersky.com/enterprise Contents Your Data Under Siege: Defend it with Encryption 3 Steps Taken to Minimise
Data - a crucial consideration in your cloud migration
 OPINION PIECE Johannesburg, South Africa, 3 November, 2016 Data - a crucial consideration in your cloud migration By AJ Hartenberg, Portfolio Manager: Data Centre Services for T-Systems, South Africa The
OPINION PIECE Johannesburg, South Africa, 3 November, 2016 Data - a crucial consideration in your cloud migration By AJ Hartenberg, Portfolio Manager: Data Centre Services for T-Systems, South Africa The
"Stay Smart, Keep Cyber Scam Away" Seminar Build a Secure Cyberspace 2018
 "Stay Smart, Keep Cyber Scam Away" Seminar Build a Secure Cyberspace 2018 2018-05-25 16:00 16:30 Lecture Theatre, Hong Kong Central Library Frankie Leung Program Director, PISA (2015-2018) Email: frankie.leung@pisa.org.hk
"Stay Smart, Keep Cyber Scam Away" Seminar Build a Secure Cyberspace 2018 2018-05-25 16:00 16:30 Lecture Theatre, Hong Kong Central Library Frankie Leung Program Director, PISA (2015-2018) Email: frankie.leung@pisa.org.hk
Vertical Market Trends: Western Europe, (Executive Summary) Executive Summary
 Vertical Market Trends: Western Europe, (Executive Summary) Executive Summary Publication Date: 21 March 2003 Authors Cathy Tornbohm Peter Redshaw This document has been published to the following Marketplace
Vertical Market Trends: Western Europe, (Executive Summary) Executive Summary Publication Date: 21 March 2003 Authors Cathy Tornbohm Peter Redshaw This document has been published to the following Marketplace
74% 2014 SIEM Efficiency Report. Hunting out IT changes with SIEM
 2014 SIEM Efficiency Report Hunting out IT changes with SIEM 74% OF USERS ADMITTED THAT DEPLOYING A SIEM SOLUTION DIDN T PREVENT SECURITY BREACHES FROM HAPPENING Contents Introduction 4 Survey Highlights
2014 SIEM Efficiency Report Hunting out IT changes with SIEM 74% OF USERS ADMITTED THAT DEPLOYING A SIEM SOLUTION DIDN T PREVENT SECURITY BREACHES FROM HAPPENING Contents Introduction 4 Survey Highlights
Risk Outlook Anti money Laundering and Cybercrime. Steve Wilmott and George Hawkins
 Risk Outlook Anti money Laundering and Cybercrime Steve Wilmott and George Hawkins Introductions Steve Wilmott, Director of Intelligence and Investigations George Hawkins, Senior Technical Advisor, Risk
Risk Outlook Anti money Laundering and Cybercrime Steve Wilmott and George Hawkins Introductions Steve Wilmott, Director of Intelligence and Investigations George Hawkins, Senior Technical Advisor, Risk
ACHIEVING FIFTH GENERATION CYBER SECURITY
 ACHIEVING FIFTH GENERATION CYBER SECURITY A Survey Research Report of IT and Security Professionals MARCH 2018 INTRODUCTION The pursuit of the highest level of cyber security is a top priority for IT and
ACHIEVING FIFTH GENERATION CYBER SECURITY A Survey Research Report of IT and Security Professionals MARCH 2018 INTRODUCTION The pursuit of the highest level of cyber security is a top priority for IT and
Just Like New: Understanding the Secondary Smartphone Market
 Just Like New: Understanding the Secondary Smartphone Market William Stofega, Program Director, Mobile Device Technology and Trends Anthony Scarsella, Research Manager, Mobile Phones IDC Web Conference
Just Like New: Understanding the Secondary Smartphone Market William Stofega, Program Director, Mobile Device Technology and Trends Anthony Scarsella, Research Manager, Mobile Phones IDC Web Conference
ESET CYBERSECURITY BAROMETER
 ESET Survey Report Canada // November 2018 ESET CYBERSECURITY BAROMETER CANADA 2018 More than 80 percent of Canadians surveyed believe that the risk of becoming a victim of cybercrime is increasing. Nine
ESET Survey Report Canada // November 2018 ESET CYBERSECURITY BAROMETER CANADA 2018 More than 80 percent of Canadians surveyed believe that the risk of becoming a victim of cybercrime is increasing. Nine
CYBER SECURITY AND THE PENSIONS INDUSTRY Karen Tasker 1 February 2018
 CYBER SECURITY AND THE PENSIONS INDUSTRY Karen Tasker 1 February 2018 What s the relevance for pension schemes? What do cyber risks look like? What should Trustees be doing? Cyber risk means any risk of
CYBER SECURITY AND THE PENSIONS INDUSTRY Karen Tasker 1 February 2018 What s the relevance for pension schemes? What do cyber risks look like? What should Trustees be doing? Cyber risk means any risk of
Information Security Is a Business
 Information Security Is a Business Continuity Issue: Are You Ready? Dr. Nader Mehravari Cyber Risk and Resilience Management Team CERT Division Software Engineering Institute Carnegie Mellon University
Information Security Is a Business Continuity Issue: Are You Ready? Dr. Nader Mehravari Cyber Risk and Resilience Management Team CERT Division Software Engineering Institute Carnegie Mellon University
IP Risk Assessment & Loss Prevention By Priya Kanduri Happiest Minds, Security Services Practice
 IP Risk Assessment & Loss Prevention By Priya Kanduri Happiest Minds, Security Services Practice IP Risk Assessment & Loss Prevention Often when organizations are expanding rapidly, they do not give sufficient
IP Risk Assessment & Loss Prevention By Priya Kanduri Happiest Minds, Security Services Practice IP Risk Assessment & Loss Prevention Often when organizations are expanding rapidly, they do not give sufficient
How Your Organization Can Drive Success in the Age of Digital Disruption
 How Your Organization Can Drive Success in the Age of Digital Disruption Produced by How Your Organization Can Drive Success in the Age of Digital Disruption Digital success isn t just about technology,
How Your Organization Can Drive Success in the Age of Digital Disruption Produced by How Your Organization Can Drive Success in the Age of Digital Disruption Digital success isn t just about technology,
2007 AT&T Business Continuity Study SAN FRANCISCO Results
 2007 AT&T Business Continuity Study SAN FRANCISCO Results Methodology The following results are based on a telephone survey of 100 Information Technology (IT) executives in the San Francisco metropolitan
2007 AT&T Business Continuity Study SAN FRANCISCO Results Methodology The following results are based on a telephone survey of 100 Information Technology (IT) executives in the San Francisco metropolitan
ENDPOINT SECURITY WHITE PAPER. Endpoint Security and the Case For Automated Sandboxing
 WHITE PAPER Endpoint Security and the Case For Automated Sandboxing A World of Constant Threat We live in a world of constant threat. Every hour of every day in every country around the globe hackers are
WHITE PAPER Endpoint Security and the Case For Automated Sandboxing A World of Constant Threat We live in a world of constant threat. Every hour of every day in every country around the globe hackers are
KEY FINDINGS INTERACTIVE GUIDE. Uncovering Hidden Threats within Encrypted Traffic
 KEY FINDINGS INTERACTIVE GUIDE Uncovering Hidden Threats within Encrypted Traffic Introduction In a study commissioned by A10 Networks, Ponemon surveyed 1,023 IT and IT security practitioners in North
KEY FINDINGS INTERACTIVE GUIDE Uncovering Hidden Threats within Encrypted Traffic Introduction In a study commissioned by A10 Networks, Ponemon surveyed 1,023 IT and IT security practitioners in North
You ve Been Hacked Now What? Incident Response Tabletop Exercise
 You ve Been Hacked Now What? Incident Response Tabletop Exercise Date or subtitle Jeff Olejnik, Director Cybersecurity Services 1 Agenda Incident Response Planning Mock Tabletop Exercise Exercise Tips
You ve Been Hacked Now What? Incident Response Tabletop Exercise Date or subtitle Jeff Olejnik, Director Cybersecurity Services 1 Agenda Incident Response Planning Mock Tabletop Exercise Exercise Tips
Securing the Empowered Branch with Cisco Network Admission Control. September 2007
 Securing the Empowered Branch with Cisco Network Admission Control September 2007 Presentation_ID 2006 Cisco Systems, Inc. All rights reserved. 1 Contents 1 The Cisco Empowered Branch 2 Security Considerations
Securing the Empowered Branch with Cisco Network Admission Control September 2007 Presentation_ID 2006 Cisco Systems, Inc. All rights reserved. 1 Contents 1 The Cisco Empowered Branch 2 Security Considerations
Verizon Wireless Ranks Highest in Wireless Network Quality Performance in Five Regions; U.S. Cellular Ranks Highest in One Region
 J.D. Power and Associates Reports: Wireless Customers Using 4G LTE Technology-Enabled Devices Experience Fewer Problems Than Those Using 3G and Other 4G-Enabled Devices Verizon Wireless Ranks Highest in
J.D. Power and Associates Reports: Wireless Customers Using 4G LTE Technology-Enabled Devices Experience Fewer Problems Than Those Using 3G and Other 4G-Enabled Devices Verizon Wireless Ranks Highest in
RSA Cybersecurity Poverty Index
 RSA Cybersecurity Poverty Index 2016 RSA Cybersecurity Poverty Index Overview Welcome to RSA s second annual Cybersecurity Poverty Index. The RSA Cybersecurity Poverty Index is the result of an annual
RSA Cybersecurity Poverty Index 2016 RSA Cybersecurity Poverty Index Overview Welcome to RSA s second annual Cybersecurity Poverty Index. The RSA Cybersecurity Poverty Index is the result of an annual
The RSA Cyber Risk policy is simple and offers wide-ranging cover, designed to work
 Suits: Small / Medium enterprise The RSA Cyber Risk policy is simple and offers wide-ranging cover, designed to work alongside traditional insurances to cover a business for all the types of cyber risks
Suits: Small / Medium enterprise The RSA Cyber Risk policy is simple and offers wide-ranging cover, designed to work alongside traditional insurances to cover a business for all the types of cyber risks
IT Monitoring Tool Gaps are Impacting the Business A survey of IT Professionals and Executives
 IT Monitoring Tool Gaps are Impacting the Business A survey of IT Professionals and Executives June 2018 1 Executive Summary This research finds that large enterprise customers and employees endure a substantial
IT Monitoring Tool Gaps are Impacting the Business A survey of IT Professionals and Executives June 2018 1 Executive Summary This research finds that large enterprise customers and employees endure a substantial
RSA Cybersecurity Poverty Index : APJ
 RSA Cybersecurity Poverty Index : APJ 2016 Overview Welcome to RSA s second annual Cybersecurity Poverty Index. The RSA Cybersecurity Poverty Index is the result of an annual maturity self-assessment completed
RSA Cybersecurity Poverty Index : APJ 2016 Overview Welcome to RSA s second annual Cybersecurity Poverty Index. The RSA Cybersecurity Poverty Index is the result of an annual maturity self-assessment completed
S e c u rity S o lu tio n s
 1 S e c u rity S o lu tio n s Introduction to security 2 Why Security Is Necessary? Following question may be familiar to some people Doing all that security is expensive and generates no money. Do we
1 S e c u rity S o lu tio n s Introduction to security 2 Why Security Is Necessary? Following question may be familiar to some people Doing all that security is expensive and generates no money. Do we
Frauds & Scams. Why is the Internet so attractive to scam artists? 2006 Internet Fraud Trends. Fake Checks. Nigerian Scam
 Frauds & Scams Why is the Internet so attractive to scam artists? Anonymity Low cost Rapid growth Easy to adapt Be Cyber Savvy with C-SAFE 118 2006 Internet Fraud Trends Average Loss Online Auctions 34%
Frauds & Scams Why is the Internet so attractive to scam artists? Anonymity Low cost Rapid growth Easy to adapt Be Cyber Savvy with C-SAFE 118 2006 Internet Fraud Trends Average Loss Online Auctions 34%
The Cost of Phishing. Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015
 The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
The Cost of Phishing Understanding the True Cost Dynamics Behind Phishing Attacks A CYVEILLANCE WHITE PAPER MAY 2015 Executive Summary.... 3 The Costs... 4 How To Estimate the Cost of an Attack.... 5 Table
Cyber Security. June 2015
 Cyber Security June 2015 Table of contents Section Pages Introduction and methodology 3 Key findings 4 Respondent profile 5-9 Cyber security practices 10-25 Resources for monitoring cyber security events
Cyber Security June 2015 Table of contents Section Pages Introduction and methodology 3 Key findings 4 Respondent profile 5-9 Cyber security practices 10-25 Resources for monitoring cyber security events
J.D. Power and Associates Reports: Social Networking and Gaming Applications Driving Smartphone Usage and Revenue
 J.D. Power and Associates Reports: Social Networking and Gaming Applications Driving Smartphone Usage and Revenue Apple Ranks Highest in Customer Satisfaction among Smartphone Manufacturers, While LG Ranks
J.D. Power and Associates Reports: Social Networking and Gaming Applications Driving Smartphone Usage and Revenue Apple Ranks Highest in Customer Satisfaction among Smartphone Manufacturers, While LG Ranks
Altitude Software. Data Protection Heading 2018
 Altitude Software Data Protection Heading 2018 How to prevent our Contact Centers from Data Leaks? Why is this a priority for Altitude? How does it affect the Contact Center environment? How does this
Altitude Software Data Protection Heading 2018 How to prevent our Contact Centers from Data Leaks? Why is this a priority for Altitude? How does it affect the Contact Center environment? How does this
The Evolving Threat. Today s cyber security challenges and solutions
 The Evolving Threat Today s cyber security challenges and solutions Are Water Lines At Risk? Security lacking in networks controlling critical infrastructure Hackers, terrorists could find way into controls
The Evolving Threat Today s cyber security challenges and solutions Are Water Lines At Risk? Security lacking in networks controlling critical infrastructure Hackers, terrorists could find way into controls
Experian Fraud Prevention Solutions
 Experian Fraud Prevention Solutions FMVÖ Business Breakfast Cyber Crime prevention for the financial services industry 1 Experian Internal use only Introducing Experian 2 Experian Identity Theft is a Global
Experian Fraud Prevention Solutions FMVÖ Business Breakfast Cyber Crime prevention for the financial services industry 1 Experian Internal use only Introducing Experian 2 Experian Identity Theft is a Global
Project 2020: Preparing Your Organization for Future Threats Today
 Project 2020: Preparing Your Organization for Future Threats Today SESSION ID: STU-W01B Rik Ferguson Vice President Security Research Trend Micro @rik_ferguson PROJECT 2020 An initiative of the International
Project 2020: Preparing Your Organization for Future Threats Today SESSION ID: STU-W01B Rik Ferguson Vice President Security Research Trend Micro @rik_ferguson PROJECT 2020 An initiative of the International
Cloud Foundry User Survey
 Cloud Foundry User Survey Semi-annual snapshot of Cloud Foundry users deployments and productivity April 2018 Introduction Cloud Foundry is the prevailing open source cloud application platform used by
Cloud Foundry User Survey Semi-annual snapshot of Cloud Foundry users deployments and productivity April 2018 Introduction Cloud Foundry is the prevailing open source cloud application platform used by
Emerging Technologies The risks they pose to your organisations
 Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
2016 State of Cybersecurity in Small & Medium-Sized Businesses (SMB)
 2016 State of Cybersecurity in Small & Medium-Sized Businesses (SMB) Sponsored by Keeper Security Independently conducted by Ponemon Institute LLC Publication Date: June 2016 Ponemon Institute Research
2016 State of Cybersecurity in Small & Medium-Sized Businesses (SMB) Sponsored by Keeper Security Independently conducted by Ponemon Institute LLC Publication Date: June 2016 Ponemon Institute Research
Cyber Insurance: What is your bank doing to manage risk? presented by
 Cyber Insurance: What is your bank doing to manage risk? David Kitchen presented by Lisa Micciche Today s Agenda Claims Statistics Common Types of Cyber Attacks Typical Costs Incurred to Respond to an
Cyber Insurance: What is your bank doing to manage risk? David Kitchen presented by Lisa Micciche Today s Agenda Claims Statistics Common Types of Cyber Attacks Typical Costs Incurred to Respond to an
Rethink Enterprise Endpoint Security In The Cloud Computing Era
 A Forrester Consulting Thought Leadership Spotlight Commissioned By Google September 2017 Rethink Enterprise Endpoint Security In The Cloud Computing Era Project Director: Karin Fenty, Senior Market Impact
A Forrester Consulting Thought Leadership Spotlight Commissioned By Google September 2017 Rethink Enterprise Endpoint Security In The Cloud Computing Era Project Director: Karin Fenty, Senior Market Impact
Conducted by Vanson Bourne Research
 Conducted by Vanson Bourne Research N o v e m b e r 2 0 1 3 1 3200 INTERVIEWS ALTOGETHER, 1600 IT & 1600 BUSINESS DECISION- MAKERS 100 & 100 IT BUSINESS DECISION- DECISION- MAKERS MAKERS COUNTRIES USA
Conducted by Vanson Bourne Research N o v e m b e r 2 0 1 3 1 3200 INTERVIEWS ALTOGETHER, 1600 IT & 1600 BUSINESS DECISION- MAKERS 100 & 100 IT BUSINESS DECISION- DECISION- MAKERS MAKERS COUNTRIES USA
Orange: Cisco & Orange: a human touch for a digital experience
 BRKPAR-4667 Orange: Cisco & Orange: a human touch for a digital experience Pierre louis Biaggi, SVP Head of Connectivity Business Unit, Orange Business Services Eric Masseboeuf, Collaboration Head of Business
BRKPAR-4667 Orange: Cisco & Orange: a human touch for a digital experience Pierre louis Biaggi, SVP Head of Connectivity Business Unit, Orange Business Services Eric Masseboeuf, Collaboration Head of Business
Larry Clinton President & CEO Internet Security Alliance
 Larry Clinton President & CEO Internet Security Alliance lclinton@isalliance.org 703-907-7028 202-236-0001 Sr. Management & Cyber Security Good News!!! Pricewaterhouse Coopers survey of 9,000 executives
Larry Clinton President & CEO Internet Security Alliance lclinton@isalliance.org 703-907-7028 202-236-0001 Sr. Management & Cyber Security Good News!!! Pricewaterhouse Coopers survey of 9,000 executives
AIRMIC ENTERPRISE RISK MANAGEMENT FORUM
 AIRMIC ENTERPRISE RISK MANAGEMENT FORUM Date 10 November 2016 Name Nick Gibbons Position, PARTNER BLM T: 0207 457 3567 E: Nick.Gibbons@blmlaw.com SUMMARY Cyber crime is now a daily reality Every business
AIRMIC ENTERPRISE RISK MANAGEMENT FORUM Date 10 November 2016 Name Nick Gibbons Position, PARTNER BLM T: 0207 457 3567 E: Nick.Gibbons@blmlaw.com SUMMARY Cyber crime is now a daily reality Every business
ISO in the world today
 ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
ISO 27001 in the world today 1 Agenda ISO 27001 worldwide Why ISO 27001 Framework to implement ISO 27001 2 ISO 27001 worldwide Source: ISO Annual Survey 3 ISO 27001 worldwide Number of Certificates Year
Managing complexity and rapid change in 2019
 2019 Predictions Managing complexity and rapid change in 2019 No-one has a crystal ball, but here at NTT Security we ve worked with our security experts around the world to identify trends that affect
2019 Predictions Managing complexity and rapid change in 2019 No-one has a crystal ball, but here at NTT Security we ve worked with our security experts around the world to identify trends that affect
Cybersecurity and Hospitals: A Board Perspective
 Cybersecurity and Hospitals: A Board Perspective Cybersecurity is an important issue for both the public and private sector. At a time when so many of our activities depend on information systems and technology,
Cybersecurity and Hospitals: A Board Perspective Cybersecurity is an important issue for both the public and private sector. At a time when so many of our activities depend on information systems and technology,
Federation of Tax Administrators Conference Minneapolis, Minnesota September 26, 2001
 Federation of Tax Administrators Conference Minneapolis, Minnesota September 26, 2001 Measurement Framework Measurement Activities Overview н Present, Future & Unfunded Lessons Learned Opportunities to
Federation of Tax Administrators Conference Minneapolis, Minnesota September 26, 2001 Measurement Framework Measurement Activities Overview н Present, Future & Unfunded Lessons Learned Opportunities to
«SINGLE MARKET MONITOR SURVEY»
 FLASH EUROBAROMETER 106 (SPECIAL TARGETS) «SINGLE MARKET MONITOR SURVEY» SEPTEMBER 2001 Survey managed and organised by: the European Commission - DG Press & Communication (Unit B/1) Conducted for : Conducted
FLASH EUROBAROMETER 106 (SPECIAL TARGETS) «SINGLE MARKET MONITOR SURVEY» SEPTEMBER 2001 Survey managed and organised by: the European Commission - DG Press & Communication (Unit B/1) Conducted for : Conducted
Understanding the Changing Cybersecurity Problem
 Understanding the Changing Cybersecurity Problem Keith Price BBus, MSc, CGEIT, CISM, CISSP Founder & Principal Consultant 1 About About me - Specialise in information security strategy, architecture, and
Understanding the Changing Cybersecurity Problem Keith Price BBus, MSc, CGEIT, CISM, CISSP Founder & Principal Consultant 1 About About me - Specialise in information security strategy, architecture, and
BUSINESS AND THE CYBER THREAT: THE RISE OF DIGITAL CRIMINALITY.
 BUSINESS AND THE CYBER THREAT: THE RISE OF DIGITAL CRIMINALITY. The 2014 Cyber Security Monitor: a North American perspective. February 2014 2 BAE Systems Applied Intelligence CONTENTS. Introduction EXECUTIVE
BUSINESS AND THE CYBER THREAT: THE RISE OF DIGITAL CRIMINALITY. The 2014 Cyber Security Monitor: a North American perspective. February 2014 2 BAE Systems Applied Intelligence CONTENTS. Introduction EXECUTIVE
Living on the Edge. Myla V. Pilao - Director TrendLabs Marketing Trend #CLOUDSEC
 Living on the Edge Myla V. Pilao - Director TrendLabs Marketing Trend Micro @trendlabs www.cloudsec.com #CLOUDSEC Outline Picture calm and carefree world Auto command (pattern/trend), voice command, change
Living on the Edge Myla V. Pilao - Director TrendLabs Marketing Trend Micro @trendlabs www.cloudsec.com #CLOUDSEC Outline Picture calm and carefree world Auto command (pattern/trend), voice command, change
Cybowall Solution Overview
 Cybowall Solution Overview 1 EVOLVING SECURITY CHALLENGES 2 EXAMPLES OF CYBER BREACHES INCLUDING CARD DATA 2013: Adobe Systems Hackers raided an Adobe back-up server on which they found and published a
Cybowall Solution Overview 1 EVOLVING SECURITY CHALLENGES 2 EXAMPLES OF CYBER BREACHES INCLUDING CARD DATA 2013: Adobe Systems Hackers raided an Adobe back-up server on which they found and published a
Where s the Money? The Strategic Value of Quantifying Cybersecurity Impact in Dollars
 Where s the Money? The Strategic Value of Quantifying Cybersecurity Impact in Dollars VivoSecurity Inc San Jose Tech Security Conference February 19, 2015 Quantifying Risk Your organizations has many categories
Where s the Money? The Strategic Value of Quantifying Cybersecurity Impact in Dollars VivoSecurity Inc San Jose Tech Security Conference February 19, 2015 Quantifying Risk Your organizations has many categories
Cyber Security. Activities of an national insurance association based on the example of VVO
 Cyber Security Activities of an national insurance association based on the example of VVO Michael Brandstetter EU and International Affairs Austrian Insurance Association (VVO) IIF Insurance in the Digital
Cyber Security Activities of an national insurance association based on the example of VVO Michael Brandstetter EU and International Affairs Austrian Insurance Association (VVO) IIF Insurance in the Digital
LinkedIn Economic Graph Project
 LinkedIn Economic Graph Project Understanding Trade Through International Connections In Partnership with the Ontario Ministry of International Trade FEBRUARY 8 The Economic Graph as a Tool to Advance
LinkedIn Economic Graph Project Understanding Trade Through International Connections In Partnership with the Ontario Ministry of International Trade FEBRUARY 8 The Economic Graph as a Tool to Advance
CHIME and AEHIS Cybersecurity Survey. October 2016
 CHIME and AEHIS Cybersecurity Survey October 2016 Fielding and Reponses Responses: 190 Survey fielded: Approximately a month (8/29-9/30) Demographics In what state or U.S. territory do you currently work?
CHIME and AEHIS Cybersecurity Survey October 2016 Fielding and Reponses Responses: 190 Survey fielded: Approximately a month (8/29-9/30) Demographics In what state or U.S. territory do you currently work?
Operational Network Security
 Tim Boerner April 25, 2013 CS598 Network Security Operational Network Security or how I learned that the purpose of network security has little to do with actually securing the network Introduction Thinking
Tim Boerner April 25, 2013 CS598 Network Security Operational Network Security or how I learned that the purpose of network security has little to do with actually securing the network Introduction Thinking
Mobile Security Trends in the Workplace
 Mobile Security Trends in the Workplace June 2014 Table of Contents 2 Abstract... 3 Key Findings... 4 Mobile Security is a Top Priority for 2014... 4 Organizations still navigating BYOD... 5 Mobile security
Mobile Security Trends in the Workplace June 2014 Table of Contents 2 Abstract... 3 Key Findings... 4 Mobile Security is a Top Priority for 2014... 4 Organizations still navigating BYOD... 5 Mobile security
IBM Cloud Internet Services: Optimizing security to protect your web applications
 WHITE PAPER IBM Cloud Internet Services: Optimizing security to protect your web applications Secure Internet applications and APIs against denialof-service attacks, customer data compromise, and abusive
WHITE PAPER IBM Cloud Internet Services: Optimizing security to protect your web applications Secure Internet applications and APIs against denialof-service attacks, customer data compromise, and abusive
Ponemon Institute s 2018 Cost of a Data Breach Study
 Ponemon Institute s 2018 Cost of a Data Breach Study September 18, 2018 1 IBM Security Speakers Deborah Snyder CISO State of New York Dr. Larry Ponemon Chairman and Founder Ponemon Institute Megan Powell
Ponemon Institute s 2018 Cost of a Data Breach Study September 18, 2018 1 IBM Security Speakers Deborah Snyder CISO State of New York Dr. Larry Ponemon Chairman and Founder Ponemon Institute Megan Powell
