Lab 8: Firewalls ASA Firewall Device
|
|
|
- Amanda Heath
- 6 years ago
- Views:
Transcription
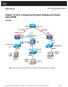
1 Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality, and the creation of a DMZ network and associated firewall rulesets. 8.2 Activities Create Virtual Topology Connect to our vsphere virtual environment at vc2003.napier.ac.uk using a vsphere Client. Navigate to the Module folder such as VMs & Templates>Production>CSN11111/8. You will be assigned a group folder to work with which contains the 4 VMs needed for the lab (check Moodle for the Groups and IP Addressing for each Group). Lab VMs: Windows7 VM running GNS3, a Windows2003 VM and 2 Linux Ubuntu VMs running network services. Power on your Windows7-GNS3 VM, open a console window, login to the Windows7-GNS3 VM, and run the GNS3 network simulator AS ADMINISTRATOR You can create a new project for Lab8, or a preconfigured starting project should be in the Projects folder. If you wish to start with that just click Recent Projects button and select lab8_start, then save as a project called lab8 or suchlike (save as, before you power on devices). The topology, shown below, mimics an organisation with an ASA firewall at its perimeter. It is connected via the untrusted Internet via the 10.1.Y.0/24 network. The ASA will be configured to provide security for the organisation from the network policy. Starting Topology You will be assigned networks to address the hosts and ASA gateway interfaces to from Moodle: X.0/24, 10.1.Y.0/24 and Z.0/24 THE CORRECT NETWORKS MUST BE USED BY EACH STUDENT AS WE ARE SHARING VIRTUAL NETWORKS. ANNOTATE YOUR DIAGRAM/TAKE NOTE OF THE ADDRESS RANGES FOR YOUR GRP. PLEASE ONLY USE GROUP VMs AND NETWORK IP ADDRESSES ASSIGNED TO YOUR GROUP. Network Security ASA Firewall Rich Macfarlane 1
2 PLEASE DO NOT USE YOUR OWN IP ADDRESSES OR THE LAB DEMO ADDRESSES IN THIS DOCUMENT! (For Windows versions up to and including Windows 7, BES can be used to limit the percentage CPU usage for applications. It can be download from Configure the Hosts Power on your Linux Ubuntu_205 VM and Windows2003_206 VM. Configure the X.10 and 10.1.Y.10 network IP Addresses on the Ubuntu_205 and Windows2003_206 systems respectively, and set the Default Gateways to the ASA interface addresses at X.254 and Y.254 the appropriate hosts. To configure the Linux system for IP Address and Default Gateway: Or for the new style ip address / ip route Linux commands: The following document has a section on setting the Windows IP and default gateway: (Section: Windows-Setting Static IP Address and Default Gateway) Basic ASA Configuration Boot the ASA security device, and open a Console Window. Using a similar CLI to a router, the ASA uses the same command modes structure, starting in User Exec Mode with the ciscoasa> prompt. Use? to see the available commands for the current command mode. Even less commands are available than on a router in this mode: Change from User Exec Mode to Privileged Exec command mode, the password should not be set so just press <RETURN>. Use the show version command to check the device setup. Q: Which Cisco ASA security appliance is being simulated? Network Security ASA Firewall Rich Macfarlane 2
3 Q: Which version is the OS? Q: How much RAM does it have? The Cisco PIX and ASA firewall devices are hardware devices built specifically for firewalling, unlike the firewall software running on routers which we have encountered in previous labs. The device (or being simulated) in this lab is a PIX 525, a medium to large enterprise device, with up to eight 10/100 Fast Ethernet interfaces, or three Gigabit interfaces. Display the list of commands available in Privilege mode using? View the PIX configuration file with the command show running-config Q: Which version of the ASA firewall Operating System is running? Q: Compared to a router, which extra attributes can be defined for each interface of the ASA? Configure Interfaces and Security Levels ASA security devices use an algorithm called the Adaptive Security Algorithm (ASA), which allows traffic to flow between the interfaces depending on the security level set on the interfaces (related to the trust levels for each attached network). The security trust level value can be set from 0 (the lowest) to 100) the highest). By default the inside interface (trusted network) is set to 100, and the outside interface (untrusted Internet) is set to 0. Other networks, such as DMZs are set to values of By default, the ASA allows traffic to flow from a higher security level to a lower one, and between levels with the same value, but blocks traffic flowing from a lower level to a higher one, as shown in the figure below. Network Security ASA Firewall Rich Macfarlane 3
4 Untrusted Internet PIX Trusted Internal Network Trust Level 0 DMZ ASA Trust Level 100 Public Facing Servers Trust Level 50 Configure the Interfaces Certain attributes must be set on the interfaces, and then the default security behaviour can be observed. Set up the outside interface, which is connected to the internet, using the following commands. ciscoasa(config)# interface gigabitethernet 0 ciscoasa(config-if)# nameif outside INFO: Security level for "outside" set to 0 by default. ciscoasa(config-if)# ip address 10.1.Y Additionally configure the MAC Address on the interfaces with the following command, using the format <ca0 module code grpno 0 intno> such as the following for module csn11118 group 99: ciscoasa(config-if)# mac-address ciscoasa(config-if)# no shutdown Set up the inside interface, which is connected to the trusted internal network: ciscoasa(config)# interface gigabitethernet 1 ciscoasa(config-if)# nameif inside INFO: Security level for "inside" set to 100 by default. ciscoasa(config-if)# ip address X ciscoasa(config-if)# mac-address 000p.pppp.qq0r ciscoasa(config-if)# no shutdown Set up the DMZ interface, which is connected to the DMZ network: ciscoasa(config)# interface Ethernet2 ciscoasa(config-if)# nameif dmz ciscoasa(config-if)# security-level 50 ciscoasa(config-if)# ip address Z ciscoasa(config-if)# mac-address 000p.pppp.qq0r ciscoasa(config-if)# no shutdown Annotate your diagram/notes with the security trust levels for each interaface/connected network. Network Security ASA Firewall Rich Macfarlane 4
5 Q: Why did we only set the security level on the dmz interface, and not the inside or outside interfaces? Review Interface configuration Check the interfaces security levels have been configured correctly using the show nameif command: Check the addressing has been set up correctly on the right interfaces, by viewing the running configuration, and by using the show ip address command, as shown. For detail on the interfaces status, use the show interface ip brief command: For detail on the interfaces, use the show interface detail command, as shown below. Save the firewall configuration using copy run start Test Connectivity From the firewall, ping each local interface, and each of the attached VM s interfaces in turn to test the interfaces are up and connectivity to the VMs: Network Security ASA Firewall Rich Macfarlane 5
6 Q: Where the pings to the firewall interfaces successful? Q: Where the pings to the directly connected VM s successful? If not, troubleshoot the configuration, until connectivity is achieved. Switch on the ICMP debugging trace logging, using the following command: ciscoasa(config)# debug icmp trace From the two VM s connectivity can be checked using ping from console windows. Limit the ping packets to a max of 3 with n3 c3 or CTRL+C to stop the ping. DO NOT LEAVE PINGS RUNNING AS WE ARE WORKING ON SHARED VIRTUAL NETWORKS! Linux: ping c3 dest_adddress Windows: ping n3 dest_adddress Q: Can the WINDOWS VM ping the Linux VM? Q: Can the Linux VM ping the WINDOWS VM? Q: What might be causing this? The ICMP ping traffic and traceroute traffic on the ASA are handled differently to a router by default. ICMP to an interface is replied to, but inbound ICMP through the ASA is blocked by default, as traffic is not allowed to go from an interface with a lower security level to an interface with a higher level (outside 0 to inside 100 is not allowed). Outbound ICMP is permitted (inside 100 to ouside 0 is allowed), but the reply is blocked by default. Network Security ASA Firewall Rich Macfarlane 6
7 There are two options which will allow inside users to ping hosts on the outside. The first option is to setup a specific firewall rule for the echo-reply traffic, and the other is to create application inspection for ICMP. Create an ACL Rule. Note the command is access-list, not ip access-list, as on a router, the syntax is slightly different, having to enter the ruleset name for every rule. ciscoasa(config)# access-list ICMP_REPLY extended permit icmp any any echoreply Review ugin the show access-list command to check it is configured correctly. Apply the ACL to the outside interface. Note that the syntax is again slightly different from a router. ciscoasa(config)# access-group ICMP_REPLY in interface outside Use the show run command to check it is configured correctly. The show run command can be used with filters to only config lines of interest: show run include ICMP_REPLY Q: What filter might be used to show all access list config lines? Check the VM s connectivity again. Q: Can the WINDOWS VM ping the Linux VM now? Network Security ASA Firewall Rich Macfarlane 7
8 Use the show access-list command to check the ACL passed the ICMP traffic. The ICMP debugging trace logging can be switched off, using:: ciscoasa(config)# undebug all Network Services Test the Linux VM Server Test the Inside Linux VM Web Server from the Outside Network From the Linux system, check the network services running, using the netstat command. Try netstat h to check the options for the command. You can also filter output using grep, (or use the l flag) There should be an Apache server running on the Linux VM. This is on the inside network (behind the perimeter firewall). From the Linux VM, check the local web server is running correctly, using the web browser: From the Outside Windows VM, use a web browser to test if the PIX firewall allows the web traffic through to the Inside network. (Use CTRL+F5 to refresh the web page from the server, and make use the page is not from the local cache). Q: Was the Web site successfully loaded? Q: Why is this? Network Security ASA Firewall Rich Macfarlane 8
9 9.2.7 Network Services Test the Linux VM Server Test the Outside Windows Web Server from the Inside Network There should be an IIS web server running on the WINDOWS VM. This is out on the untrusted outside network (typically the Internet). From the Window system, check the network services running, using the Windows version of the netstat tool. Try netstat h to check the options for the command. : Q. What command could be used to only list TCP connections? You can also filter output using findstr: From the Windows VM, check the local web server is running correctly, using the web browser: Network Security ASA Firewall Rich Macfarlane 9
10 From the Linux VM, use a web browser to test if the PIX firewall allows the traffic from Inside to the Windows server Outside and back. (Use CTRL+F5 to refresh the page from the server, and not just the local cache). Q: Was the Web site successfully loaded? Test the FTP Server From the Linux VM, connect to the FTP Server from, via a web browser using ftp://w.x.y.z. Log in with the Windows server credential. Q: Was the FTP Server successfully accessed? Test the Telnet server From the Linux VM, Telnet to the Windows VM, using Putty - user: napier password: napier123. Then use ifconfig to check you are logged into the Linux VM. Q: Could the Linux server be accessed with Telnet? Q: Why is this traffic not being blocked? The tests should look like the following: Windows Web Server Network Security ASA Firewall Rich Macfarlane 10
11 Windows FTP Server Windows Remote Admin via Telnet Server Scan the ASA Perimeter Perimeter Router for Vulnerabilities Using the nmap network scanner, check for public services running on the PIX, by running a port scan against the firewall device s outside interface. From the Windows VM open a console window and run nmap against the router, as shown below. nmap n 10.1.Y.254 Monitor Traffic On Windows, run Wireshark and resize to the width to width of the window. Start a capture on the ethernet interface, and then use a display filter to monitor only packets on the Outside network. Try the nmap scan again, and you should see some traffic: Network Security ASA Firewall Rich Macfarlane 11
12 Q: What services are shown to be running on the firewall? Q: Does the ASA seem up. i.e. responding to the host scan packets? Q: Why do we get this result? The ASA firewall device implements a closed firewall on the outside interface, by default. (based on the security level settings) Try from WINDOWS VM, scanning the firewalls inside interface. Q: What services are shown to be running on the firewall? ASA Stateful Firewall The ASA performs stateful firewalling as default for TCP and UDP traffic. It stores connection details for inbound or outbound TCP sessions established through the firewall (either passed through due to the security levels, or explicit ACL firewall rules). Network Connections State Table The connection details are stored in a session/connection state cache. If a connection is passed through the firewall (via security levels, or an ACL rule), its details are stored in the Conn table. Then returning traffic is checked against the Conn table and passed without checking security levels or ACLs. Network Security ASA Firewall Rich Macfarlane 12
13 ACL Firewall Rules PIX ASA Conn State Table The sessions/connections currently stored in the conn table can be viewed using: ciscoasa(config)# show conn Details on the states of connections can be viewed using show conn detail as shown below. On the Linux VM, refresh the web page from the Outside Windows VM server. Q: How many connections are in the PIX firewalls connections state table? Q: What are the services, and their source and destination IP Addresses and Port Numbers? Q: Compare to how this type of stateful firewalling would be implemented on a Cisco Router Would similar functionality take more of less complex configuration on a router? Wait for a period, and check the connections being stored again. Q: How many connections are in the PIX firewalls connections state table? Network Security ASA Firewall Rich Macfarlane 13
14 Q: Which service has been removed? Q: Why was the connection removed? Log out of the Telnet session from the Linux VM to the Windows Server, and check the connections being stored again. Q: How many connections are in the PIX firewalls connections state table? Q: Why was the connection removed? When the connection is terminated, for example with a teardown handshake, the connection information is removed from the firewalls state connection table. Also timeouts are used to remove idle connections. Stateful Session Timeouts The connection timeout settings can be reviewed using the show run timeout command, or the show timeout command. ciscoasa(config)# show run timeout timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute ciscoasa(config)# Q: What is the default time out (in minutes), for standard TCP connections? Network Security ASA Firewall Rich Macfarlane 14
15 Create a DMZ Network Add a DMZ Server to the Topology Attach a 2 nd Linux_202 VM server to the DMZ via LAN CONNECTION 2, as shown below. In the new Linux DMZ Server, navigate to the /var/www directory. Use the ls command to list the contents of the directory. Edit the index.html file using vi or a GUI-based editor such as gedit. Change the text to indicate this is the DMZ Web Server: Saves the changes and exit the editor (:wq command in vi). Test the webserver locally from the Linux DMZ Server using the loopback IP address, as shown below. Test the DMZ Web Server from the Inside network Linux VM From the Linux VM on theinside network, use a web browser to connect to the Apache web server running on the Linux VM DMZ Server (CTRL+F5 to refresh the cache) Q: Is the Linux VM Web traffic allowed to the Linux DMZ Server? Network Security ASA Firewall Rich Macfarlane 15
16 Q: Why? The security levels should allow traffic moving from a higher security level to a lower one, and the stateful firewall functionality allows the return traffic The web page should be accessible from the inside network: Test the DMZ Web Server from Outside the Firewall From the Windows outside VM, use a web browser to connect to the web server running on the Linux VM DMZ Server (CTRL+F5 to refresh the cache) Q: Can the Internet VM get Web traffic, fromthe Linux Server? Q: Why? The Internet system should not be able to connect, as the outside interface has a lower security trust level than the DMZ Allow Outside Access to the DMZ Server To allow access from the lower trust level outside network to the higher security trust level DMZ, a firewall rule must be created! Create Out>DMZ Ingress ACL We can create the ACL to only allow access to the Web Server on the DMZ server. Create an Ingress ACL Rule. Earlier we added a ICMP_REPLY ACL to the outside interface, so first remove that, and we can incorporate into the new ACL. Network Security ASA Firewall Rich Macfarlane 16
17 Remove from outside interface. pix(config# no access-group ICMP_REPLY in interface outside Remove the ACL ruleset. ciscoasa(config)# no access-list ICMP_REPLY extended permit icmp any any echoreply Create the new INGRESS ACL. Allow only Web traffic to the single DMZ Web server. ciscoasa(config)# access-list INGRESS extended permit tcp any host Z.10 eq 80 Add rest of previous ICMP_REPLY ruleset. ciscoasa(config)# access-list INGRESS extended permit icmp any any echo-reply Apply the new ruleset to the outside interface for Ingress traffic. pix(config# access-group INGRESS in interface outside pix(config# access-group INGRESS in interface outside Trusted, Internal Network E1 E0 Untrusted Internet DMZ Http traffic to the web server Use the show run access-list command to check the ruleset is configured correctly. Use show run access-group and show run access-list to check the ruleset has been applied correctly to the ouside interface for ingress traffic. (another way of filtering out parts of the running config) Use the show access-list command to check if the rules have been matched on yet (hitcnt=??). Network Security ASA Firewall Rich Macfarlane 17
18 Test the DMZ Web Server from the Windows VM Outside the Firewall From the Internet VM, use a web browser to connect to the web server running on the Linux VM DMZ Server Q: Can the Internet VM connect to the Linux Web Server on the DMZ now? Q: Can you see the HTTP connection in the ASA state table (be quick before it times out) The web server should be available now: Use the show access-list command to check the the ACL passed the web traffic. Test the Internet Web Server from the Linux DMZ VM From the Linux DMZ VM, use a web browser to connect to the web server running on the Linux VM Internet Server (CTRL+F5 to refresh the cache) Q: Can the DMZ VM connect to the Linux Internet Server? The server should be available to the DMZ VM currently as the higher trust level can initiate connections and receive return traffic. Q: Why might this default policy not be a good idea? Network Security ASA Firewall Rich Macfarlane 18
19 Misuse the DMZ >OutsideTrust Relationship From the Inside Linux VM, send 3 ICMP packets to the DMZ Linux VM using the ping tool. Q: Do we have connectivity? Now try the same using the hping tool. Use hping h more to check the help for the format of the command. Send 3 ICMP packets, using c 3 and -1 (ICMP): Now try using the a Outside_Win2003_VM_IP to spoof our source IP: Q: Can you see the packets arriving at the Outside server? (wireshark) Q: What type of attack is this? NOTE: Be VERY VERY careful when using tools such as hping, to only send a limited number of packets, and do not use random source or destination addresses as this can cause unexpected results Restrict Traffic Originating from the DMZ It is typically good practice to allow no traffic out to the Internet which originates on a DMZ, if none is required by the security policy. This can stop a host of malware based attacks, and well as backdoors and suchlike. Create a new Egress traffic ACL ruleset blocking all traffic originating on the DMZ network. Network Security ASA Firewall Rich Macfarlane 19
20 ciscoasa(config)# access-list EGRESS extended deny ip any any Before applying the rule, check you can ping the Outside VM from the DMZ VM. Apply the new ruleset to the dmz interface for Egress traffic. pix(config# access-group EGRESS in interface dmz Use the show access-list command to check that the rules have not been matched yet (hitcnt). Test the Internet Web Server from the Linux DMZ VM From the Linux DMZ VM, use a web browser to connect to the web server running on the Linux VM Internet Server (CTRL+F5 to refresh the cache). Try using ping from the DMZ VM to the outside VM. Q: Can the DMZ VM connect to the Linux Internet Server? The traffic originating on the DMZ should now be blocked. Use the show access-list command to check that the rules have been matched (hitcnt>0). Q: Reflect on the type of threats which may be mitigated by blocking traffic originating on the DMZ out to the Internet? Test the DMZ Web Server from the Linux VM Outside the Firewall From the Linux Internet VM, check the VM DMZ Server is still accessible (CTRL+F5 to refresh the cache). Back to the question from before: Q: Why is DMZ return traffic still being passed back to the Internet Linux VM, even though we have blocked all traffic from the DMZ? Network Security ASA Firewall Rich Macfarlane 20
21 Allow Only Web Access to the Internet from Inside Network The users including the Linux VM user on the inside network, are now to be restricted to only have Web access to the Internet, and no other services should be accessed from the inside network. An ACL firewall ruleset should be created to allow the allowed traffic, and block and log all other traffic. Q: What ACL firewall rules should be used? Q: Draw on the figure below should the ACL firewall rules be applied, and in which direction? Test the Web, FTP, and Telnet Server Before the ACL is added, test the services from the inside host. From the Inside Linux VM, browse to the outside website, access the FTP server via a browser, and Telnet to the Windows VM. Q: Could the Linux Web server, FTP server, and Telnet server be accessed? Now create the ACL(s) and apply to interface(s). Test the services again. Q: Are the Linux FTP server, and Telnet server being blocked? Q: Can the Web server still be accessed? If the answers are not YES, rethink the ACLs Network Security ASA Firewall Rich Macfarlane 21
22 Allow Administrative Access to the DMZ Server To allow administration of the DMZ server only from the Administrators machine on the inside network (use the Linux VM for testing), an ACL firewall ruleset should be created. Access to the lower security level DMZ from the higher level inside network is allowed by default, but a rule is needed to prevent any other hosts to access the server via Telnet. Q: What ACL firewall rules should be used? Q: Draw on the figure below should the ACL firewall rules be applied, and in which direction? Now create the ACL(s) and apply to interface(s). Test the Telnet server From the Linux VM, Telnet to the Linux DMZ VM. Then use ifconfig to check you are logged into the Linux DMZ VM. Maybe change the web page contents. Q: Could the Linux server be accessed with Telnet? If the answer is not YES, rethink your ACL To test the ACL is only allowing access from the administrators system, change the IP Address of the WINDOWS VM to and test the telnet server again. Q: Is the Telnet access being blocked? If the answer is not YES, rethink the ACLs Network Security ASA Firewall Rich Macfarlane 22
23 8.3 Appendix A Adding ASA to GNS3 Download the ASA OS Kernal and RAM files (should be on the lab machines already). Start GNS3, as Administrator. Select Edit>Preferences, and QEMU VMs. Then new, and select ASA. Add the files in the Advanced tab, and leave everything else to default. Network Security ASA Firewall Rich Macfarlane 23
24 8.4 Appendix B ASA Firewall with DMZ Configuration PIX PIX Version 8.0(4)! hostname ciscoasa enable password 8Ry2YjIyt7RRXU24 encrypted passwd 2KFQnbNIdI.2KYOU encrypted names! interface gigabitethernet0 nameif outside security-level 0 ip address 10.1.Y ! interface gigabitethernet 1 nameif inside security-level 100 ip address X ! interface gigabitethernet 2 nameif dmz security-level 50 ip address Z ! interface Ethernet3 shutdown no nameif no security-level no ip address! interface Ethernet4 shutdown no nameif no security-level no ip address! ftp mode passive access-list INGRESS extended permit tcp any host Z.10 eq www access-list INGRESS extended permit icmp any any echo-reply access-list EGRESS extended deny ip any any... SNIPPED... Network Security ASA Firewall Rich Macfarlane 24
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Lab 9: VPNs IPSec Remote Access VPN
 Lab 9: VPNs IPSec Remote Access VPN Rich Macfarlane 2015 Aim: Details The aim of this lab is to introduce Virtual Private Network (VPN) concepts, using an IPSec remote access VPN between a remote users
Lab 9: VPNs IPSec Remote Access VPN Rich Macfarlane 2015 Aim: Details The aim of this lab is to introduce Virtual Private Network (VPN) concepts, using an IPSec remote access VPN between a remote users
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Lab 10: IDPS Snort & Cisco IDPS Sensors
 Lab 10: IDPS Snort & Cisco IDPS Sensors 9.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate IDPS Sensors, using the open source Snort IDS Sensor software and the Cisco IPS software
Lab 10: IDPS Snort & Cisco IDPS Sensors 9.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate IDPS Sensors, using the open source Snort IDS Sensor software and the Cisco IPS software
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example
 VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example Document ID: 66171 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure
VPN Between Sonicwall Products and Cisco Security Appliance Configuration Example Document ID: 66171 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure
co Configuring PIX to Router Dynamic to Static IPSec with
 co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
Configuration Examples
 CHAPTER 4 Before using this chapter, be sure that you have planned your site s security policy, as described in Chapter 1, Introduction, and configured the PIX Firewall, as described in Chapter 2, Configuring
CHAPTER 4 Before using this chapter, be sure that you have planned your site s security policy, as described in Chapter 1, Introduction, and configured the PIX Firewall, as described in Chapter 2, Configuring
NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example
 NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example Document ID: 71573 Contents Introduction Prerequisites Requirements Components Used Network Diagram
NAC Appliance (Cisco Clean Access) In Band Virtual Gateway for Remote Access VPN Configuration Example Document ID: 71573 Contents Introduction Prerequisites Requirements Components Used Network Diagram
Table of Contents. Cisco IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example
 Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users
 PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users Document ID: 69308 Contents Introduction Prerequisites Requirements Components Used Related Products Network Diagram Conventions
PIX/ASA 7.x ASDM: Restrict the Network Access of Remote Access VPN Users Document ID: 69308 Contents Introduction Prerequisites Requirements Components Used Related Products Network Diagram Conventions
Troubleshooting. Testing Your Configuration CHAPTER
 82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example
 ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
ASA/PIX: Remote VPN Server with Inbound NAT for VPN Client Traffic with CLI and ASDM Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development
 Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Weekly Tasks Week 5 Rich Macfarlane 2013 Week Date Teaching Attended 5 Feb 2013 Lab 7: Snort IDS Rule Development Aim: The aim of these labs are to further investigate the Snort, network IDS, and methods
Table of Contents. Cisco Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0
 Table of Contents Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0...1 Document ID: 64693...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1
Table of Contents Enhanced Spoke to Client VPN Configuration Example for PIX Security Appliance Version 7.0...1 Document ID: 64693...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1
Table of Contents. Cisco PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example
 Table of Contents PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example...1 Document ID: 64692...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 Configure...2
Table of Contents PIX/ASA 7.x Enhanced Spoke to Spoke VPN Configuration Example...1 Document ID: 64692...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...2 Configure...2
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Permitting PPTP Connections Through the PIX/ASA
 Permitting PPTP Connections Through the PIX/ASA Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions PPTP with the Client Inside and the Server Outside Network
Permitting PPTP Connections Through the PIX/ASA Contents Introduction Prerequisites Requirements Components Used Background Theory Conventions PPTP with the Client Inside and the Server Outside Network
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands
 PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
: Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21: UTC Thu Dec !
 : Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21:59.078 UTC Thu Dec 17 2015 ASA Version 9.2(2)4 hostname ciscoasa enable password
: Saved : : Serial Number: JMX1813Z0GJ : Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz : Written by enable_15 at 09:21:59.078 UTC Thu Dec 17 2015 ASA Version 9.2(2)4 hostname ciscoasa enable password
Troubleshooting the Security Appliance
 CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX
 This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX Firewall 8. Time setting and NTP support 13. DHCP server
This chapter covers the following exam topics for the Secure PIX Firewall Advanced Exam (CSPFA 9E0-511): 5. User interface 6. Configuring the PIX Firewall 8. Time setting and NTP support 13. DHCP server
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Network Security Laboratory 23 rd May STATEFUL FIREWALL LAB
 Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Document ID: Contents. Introduction. Prerequisites. Requirements. Introduction. Prerequisites Requirements
 Products & Services ASA/PIX 7.x: Redundant or Backup ISP Links Configuration Example Document ID: 70559 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Products & Services ASA/PIX 7.x: Redundant or Backup ISP Links Configuration Example Document ID: 70559 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Background
Web server Access Control Server
 2 You can use access lists to control traffic based on the IP address and protocol. However, you must use authentication and authorization in order to control access and use for specific users or groups.
2 You can use access lists to control traffic based on the IP address and protocol. However, you must use authentication and authorization in order to control access and use for specific users or groups.
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
DOWNLOAD PDF CISCO ASA 5505 CONFIGURATION GUIDE
 Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector
Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector
Firewall Stateful Inspection of ICMP
 The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
Teacher s Reference Manual
 UNIVERSITY OF MUMBAI Teacher s Reference Manual Subject: Security in Computing Practical with effect from the academic year 2018 2019 Practical 1: Packet Tracer - Configure Cisco Routers for Syslog, NTP,
UNIVERSITY OF MUMBAI Teacher s Reference Manual Subject: Security in Computing Practical with effect from the academic year 2018 2019 Practical 1: Packet Tracer - Configure Cisco Routers for Syslog, NTP,
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
PIX/ASA: PPPoE Client Configuration Example
 PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
Lab Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance
 Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Lab 9.4.10 Configure and Test Advanced Protocol Handling on the Cisco PIX Security Appliance Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Display the
Lab 1: Creating Secure Architectures (Revision)
 Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
Lab 1: Creating Secure Architectures (Revision) A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For
CCNA Discovery 3 Chapter 8 Reading Organizer
 Name Date Chapter 8 Reading Organizer After completion of this chapter, you should be able to: Describe traffic filtering and explain how Access Control Lists (ACLs) can filter traffic at router interfaces.
Name Date Chapter 8 Reading Organizer After completion of this chapter, you should be able to: Describe traffic filtering and explain how Access Control Lists (ACLs) can filter traffic at router interfaces.
Lab Configure Cisco IOS Firewall CBAC
 Lab 3.8.3 Configure Cisco IOS Firewall CBAC Objective Scenario Topology Estimated Time: 50 minutes Number of Team Members: Two teams with four students per team. In this lab, students will complete the
Lab 3.8.3 Configure Cisco IOS Firewall CBAC Objective Scenario Topology Estimated Time: 50 minutes Number of Team Members: Two teams with four students per team. In this lab, students will complete the
Physical Topology. Logical Topology
 Physical Topology Logical Topology Please, note that the configurations given below can certainly be clean-up and tuned. Some commands are still embedded for testing purposes. Note also that the text highlighted
Physical Topology Logical Topology Please, note that the configurations given below can certainly be clean-up and tuned. Some commands are still embedded for testing purposes. Note also that the text highlighted
Lab 2: Creating Secure Architectures
 Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Firewall Authentication Proxy for FTP and Telnet Sessions
 Firewall Authentication Proxy for FTP and Telnet Sessions Last Updated: January 18, 2012 Before the introduction of the Firewall Authentication Proxy for FTP and Telnet Sessions feature, users could enable
Firewall Authentication Proxy for FTP and Telnet Sessions Last Updated: January 18, 2012 Before the introduction of the Firewall Authentication Proxy for FTP and Telnet Sessions feature, users could enable
Lab Configure Cisco IOS Firewall CBAC on a Cisco Router
 Lab 3.8.3 Configure Cisco IOS Firewall CBAC on a Cisco Router Objective Scenario Topology Estimated Time: 35 minutes Number of Team Members: Two teams with four students per team In this lab, students
Lab 3.8.3 Configure Cisco IOS Firewall CBAC on a Cisco Router Objective Scenario Topology Estimated Time: 35 minutes Number of Team Members: Two teams with four students per team In this lab, students
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
Implementing Firewall Technologies
 Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501.
 1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
FWSM: Multiple Context Configuration Example
 FWSM: Multiple Context Configuration Example Document ID: 107524 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported
FWSM: Multiple Context Configuration Example Document ID: 107524 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Context Configuration Files Unsupported
Lab b Simple DMZ Extended Access Lists Instructor Version 2500
 Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Downloaded from: justpaste.it/i2os
 : Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
: Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
LAB THREE STATIC ROUTING
 LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
IPSec tunnel for ER75i routers application guide
 IPSec tunnel for ER75i routers application guide 1 Contents 1. Generally...3 2. IPSec limitation...3 3. Example of use IPSec tunnel Client side at ER75i...4 3.1. IPSec tunnel client side at ER75i...4 3.1.1.
IPSec tunnel for ER75i routers application guide 1 Contents 1. Generally...3 2. IPSec limitation...3 3. Example of use IPSec tunnel Client side at ER75i...4 3.1. IPSec tunnel client side at ER75i...4 3.1.1.
Table of Contents. Cisco Configuring IP Access Lists
 Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
Firewalling Avid ISIS in a Cisco environment
 Firewalling Avid ISIS in a Cisco environment Interoperability testing between Cisco ASA and ISIS results Francesca Martucci Consulting System Engineer for Security - Cisco David Shephard - Senior Network
Firewalling Avid ISIS in a Cisco environment Interoperability testing between Cisco ASA and ISIS results Francesca Martucci Consulting System Engineer for Security - Cisco David Shephard - Senior Network
Multihoming with BGP and NAT
 Eliminating ISP as a single point of failure www.noction.com Table of Contents Introduction 1. R-NAT Configuration 1.1 NAT Configuration 5. ISPs Routers Configuration 3 15 7 7 5.1 ISP-A Configuration 5.2
Eliminating ISP as a single point of failure www.noction.com Table of Contents Introduction 1. R-NAT Configuration 1.1 NAT Configuration 5. ISPs Routers Configuration 3 15 7 7 5.1 ISP-A Configuration 5.2
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Computer Network Vulnerabilities
 Computer Network Vulnerabilities Objectives Explain how routers are used to protect networks Describe firewall technology Describe intrusion detection systems Describe honeypots Routers Routers are like
Computer Network Vulnerabilities Objectives Explain how routers are used to protect networks Describe firewall technology Describe intrusion detection systems Describe honeypots Routers Routers are like
Lab c Simple DMZ Extended Access Lists
 Lab 11.2.3c Simple DMZ Extended Access Lists Objective In this lab, the use extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics v 3.0
Lab 11.2.3c Simple DMZ Extended Access Lists Objective In this lab, the use extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics v 3.0
CCNA Security 1.0 Student Packet Tracer Manual
 1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec
 Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec Document ID: 14095 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Configuring the PIX Firewall and VPN Clients Using PPTP, MPPE and IPSec Document ID: 14095 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Lab Configure ACLs in the PIX Security Appliance using CLI
 Lab 9.1.9 Configure ACLs in the PIX Security Appliance using CLI Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Disable pinging to an interface. Configure
Lab 9.1.9 Configure ACLs in the PIX Security Appliance using CLI Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Disable pinging to an interface. Configure
Chapter 4. Threat Defence Architecture
 Chapter 4. Threat Defence Architecture Technology Brief The very primary function of using a dedicated device named as firewall at the edge of corporate network is isolation. Firewall prevents the direct
Chapter 4. Threat Defence Architecture Technology Brief The very primary function of using a dedicated device named as firewall at the edge of corporate network is isolation. Firewall prevents the direct
Connection Settings. What Are Connection Settings? management connections that go to the ASA.
 This chapter describes how to configure connection settings for connections that go through the ASA, or for management connections that go to the ASA. What Are?, page 1 Configure, page 2 Monitoring Connections,
This chapter describes how to configure connection settings for connections that go through the ASA, or for management connections that go to the ASA. What Are?, page 1 Configure, page 2 Monitoring Connections,
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
SonicWALL / Toshiba General Installation Guide
 SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
ASA/PIX Security Appliance
 I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts.
 Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Configuring Security Contexts Created by Bob Eckhoff This study aid describes the purpose of security contexts and explains how to enable, configure, and manage multiple contexts. Security Context Overview
Context Based Access Control (CBAC): Introduction and Configuration
 Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Lab Configure Service Object Groups using ASDM
 Lab 9.2.3 Configure Service Object Groups using ASDM Objective Scenario In this lab, the students will complete the following tasks: Configure an inbound access control list (ACL) with object groups. Configure
Lab 9.2.3 Configure Service Object Groups using ASDM Objective Scenario In this lab, the students will complete the following tasks: Configure an inbound access control list (ACL) with object groups. Configure
PT Activity 5.6.1: Packet Tracer Skills Integration Challenge Topology Diagram
 Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
Chapter 2: Configure a Network Operating System. Every computer requires an operating system to function, including computerbased
 2.0.1.1 Chapter 2: Configure a Network Operating System Every computer requires an operating system to function, including computerbased network devices such as switches, routers, access points, and firewalls.
2.0.1.1 Chapter 2: Configure a Network Operating System Every computer requires an operating system to function, including computerbased network devices such as switches, routers, access points, and firewalls.
Lab Catalyst 2950 and 3550 Series Intra-VLAN Security
 Lab 7.2.5.1 Catalyst 2950 and 3550 Series Intra-VLAN Security Objective Scenario Configure intra-vlan security with Access Control Lists (ACLs) using the command-line interface (CLI) mode. This lab will
Lab 7.2.5.1 Catalyst 2950 and 3550 Series Intra-VLAN Security Objective Scenario Configure intra-vlan security with Access Control Lists (ACLs) using the command-line interface (CLI) mode. This lab will
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
Broadcast Infrastructure Cybersecurity - Part 2
 SBE Webinar Series - 2018 Broadcast Infrastructure Cybersecurity - Part 2 Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services KAMU FM-TV Broadcast Infrastructure Cybersecurity
SBE Webinar Series - 2018 Broadcast Infrastructure Cybersecurity - Part 2 Wayne M. Pecena, CPBE, CBNE Texas A&M University Educational Broadcast Services KAMU FM-TV Broadcast Infrastructure Cybersecurity
Object Groups for ACLs
 The feature lets you classify users, devices, or protocols into groups and apply these groups to access control lists (ACLs) to create access control policies for these groups. This feature lets you use
The feature lets you classify users, devices, or protocols into groups and apply these groups to access control lists (ACLs) to create access control policies for these groups. This feature lets you use
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Contents. Introduction
 Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces
Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces
Wireless LANs (CO72047) Bill Buchanan, Reader, School of Computing.
 Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Practical Network Defense Labs
 Practical Network Defense Labs ABOUT This document showcases my practical hands-on engagements in the elearnsecurity HERA labs environment for the Network Defense Professional certification course. I utilized
Practical Network Defense Labs ABOUT This document showcases my practical hands-on engagements in the elearnsecurity HERA labs environment for the Network Defense Professional certification course. I utilized
Lab b Simple DMZ Extended Access Lists
 Lab 11.2.3b Simple DMZ Extended Access Lists Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics
Lab 11.2.3b Simple DMZ Extended Access Lists Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics
Exam Name: Implementing Cisco Edge Network Security Solutions
 Vendor: Cisco Exam Code: 300-206 Exam Name: Implementing Cisco Edge Network Security Solutions Version: Demo QUESTION 1 The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three
Vendor: Cisco Exam Code: 300-206 Exam Name: Implementing Cisco Edge Network Security Solutions Version: Demo QUESTION 1 The Cisco ASA must support dynamic routing and terminating VPN traffic. Which three
Summer Webinar Series
 Summer Webinar Series Troubleshooting Traffic Flows Through Cisco ASA Firewalls Christopher Rose Sr. Client Network Engineer crose@mcnc.org Webinar Links: www.mcnc.org/cne-webinars Agenda 1. Firewall best
Summer Webinar Series Troubleshooting Traffic Flows Through Cisco ASA Firewalls Christopher Rose Sr. Client Network Engineer crose@mcnc.org Webinar Links: www.mcnc.org/cne-webinars Agenda 1. Firewall best
Extended ACL Configuration Mode Commands
 Extended ACL Configuration Mode Commands To create and modify extended access lists on a WAAS device for controlling access to interfaces or applications, use the ip access-list extended global configuration
Extended ACL Configuration Mode Commands To create and modify extended access lists on a WAAS device for controlling access to interfaces or applications, use the ip access-list extended global configuration
SSL VPN Configuration of a Cisco ASA 8.0
 Published on Jisc community (https://community.jisc.ac.uk) Home > Advisory services > Multi-site Connectivity Advisory Service > Technical guides > Secure Virtual Private Networks > SSL VPN Configuration
Published on Jisc community (https://community.jisc.ac.uk) Home > Advisory services > Multi-site Connectivity Advisory Service > Technical guides > Secure Virtual Private Networks > SSL VPN Configuration
CCNA Access List Questions
 CCNA Access List Questions Here you will find answers to CCNA Access list questions Note: If you are not sure about how to use Access list, please read my Access list tutorial Question 1 Your boss is learning
CCNA Access List Questions Here you will find answers to CCNA Access list questions Note: If you are not sure about how to use Access list, please read my Access list tutorial Question 1 Your boss is learning
Chapter 4 Lab A: Configuring CBAC and Zone-Based Firewalls
 Chapter 4 Lab A: Configuring CBAC and Zone-Based Firewalls Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet Interfaces. IP Addressing Table Device Interface IP Address
Chapter 4 Lab A: Configuring CBAC and Zone-Based Firewalls Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet Interfaces. IP Addressing Table Device Interface IP Address
ASA Version 7.2(4)30! hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name
 ASA Version 7.2(4)30 hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name 172.30.232.128 XL description XL / idot name 172.28.28.0
ASA Version 7.2(4)30 hostname vpn domain-name hollywood.com enable password BO5OGdtIUElAVJc7 encrypted passwd BO5OGdtIUElAVJc7 encrypted names name 172.30.232.128 XL description XL / idot name 172.28.28.0
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Contents. Introduction
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram ISE - Configuration Steps 1. SGT for Finance and Marketing 2. Security group ACL for traffic Marketing ->Finance
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram ISE - Configuration Steps 1. SGT for Finance and Marketing 2. Security group ACL for traffic Marketing ->Finance
upgrade-mp through xlate-bypass Commands
 CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring Management Access
 37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
37 CHAPTER This chapter describes how to access the ASA for system management through Telnet, SSH, and HTTPS (using ASDM), how to authenticate and authorize users, how to create login banners, and how
Lab 6: Access Lists. Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/ R1
 Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
