Lab b Simple DMZ Extended Access Lists Instructor Version 2500
|
|
|
- Damon Turner
- 6 years ago
- Views:
Transcription
1 Lab b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
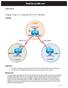
2 Scenario The BMTC is a small manufacturing company located in Gadsden. They have decided that they would like to create an awareness of their products over the Internet. Therefore their immediate requirement is to promote their products to potential customers by providing product overviews, reports, and testimonials. Future requirements could include , FTP, DNS, and online e- commerce services. They have contracted you to design and configure a secure infrastructure to support their internal and external network requirements while maintaining fiscal responsibility which means make it secure but keep costs down. After careful analysis, it is proposed to create a two-tier security architecture consisting of a corporate network zone and a DeMilitarized Zone (DMZ). The corporate network zone would house private servers and internal clients. The DMZ would house only one external server that would provide World Wide Web services. Although the one server creates a single point of failure, the service is only informational and not considered mission critical. They liked the proposal and have signed a contract. Step 1 Basic Router and Host Configurations a. Interconnect the routers and hosts as shown in the diagram. Configure all router basics such as hostname, router interfaces, and routing protocol. Use the preceding diagram and tables for reference. The configurations on each router should similar to the following: GAD#show running-config <Output Omitted> hostname GAD interface FastEthernet0 ip address interface Serial0 ip address clock rate interface FastEthernet/1 ip address router rip network network GAD# ISP#show running-config <Output Omitted> hostname ISP interface FastEthernet0 ip address interface Serial0 ip address CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
3 router rip network ISP# b. Configure the hosts with the correct settings using the information previously defined. c. To make the lab more realistic, web server software should be installed on the web server host. Examples include Microsoft IIS or Microsoft Personal Web Server (Windows 98). A third-party software such as TinyWeb Server ( can be used. If TinyWeb Server is used, it is recommended that TinyBox ( also be installed, which is a GUI front-end for TinyWeb Server. Be sure to create a default index.html page. The web page should include a message such as Hello World. Save the page as instructed by the Web Server software. d. Before applying any type of access list, it is important to verify reachability between systems. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping Host B? Yes Can Host A ping the Web Server? Yes Can Host B ping Host A? Yes Can Host B ping the Web Server? Yes Host A IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=16ms TTL= CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
4 Minimum = 0ms, Maximum = 16ms, Average = 4ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Minimum = 16ms, Maximum = 31ms, Average = 19ms All hosts should be able to ping each other, if not troubleshoot the unsuccessful interfaces. Always verify the physical layer connections, because they are a common source of connectivity problems. e. On Host A, open a Web browser such as Windows Explorer or Netscape Navigator and enter the address of the Web Server in the address location CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
5 [ ] Verify that each Host has Web access to the Web Server. Can Host A view the index.html page? Yes Can Host B view the index.html page? Yes Both hosts should be able to view the index.html page in the Web Browser. Troubleshoot as necessary. f. Now that the infrastructure is in place, it is time to begin securing the internetwork. Step 2 Protect the Corporate Network a. The corporate network zone houses private servers and internal clients. No other network should be able to access it. b. Configure an extended access list to protect the corporate network. Protecting a corporate network begins by specifying which traffic can exit out the network. Although this may initially sound strange, it becomes clearer when it is known that most hackers are internal employees. The first access list will specify which network can exit out of the network. Enter the following: GAD#conf terminal Enter configuration commands, one per line. End with CNTL/Z. GAD(config)#access-list 101 permit ip any GAD(config)#access-list 101 deny ip any any The first line defines of access list 101 will only let valid corporate users on network into the router. The second line is not really required because of the implicit deny all, but has been added for readability. c. Now we need to apply the access list to the corporate network interface. Enter the following: GAD(config)#interface fa1 GAD(config-if)#ip access-group 101 in d. Now it is necessary to test the access lists. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? Yes Can Host B ping Host A? Yes All hosts should be able to ping any location. Host A IP Address : Default Gateway : CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
6 C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
7 Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Minimum = 16ms, Maximum = 31ms, Average = 19ms e. Next, configure an outbound extended access list on the corporate network interface. Traffic entering the corporate network will be coming from either the Internet or the DMZ. For this reason which traffic can be allowed into the corporate network must be limited. f. The first issue to address is to make sure that only traffic that originated from the corporate network can be allowed back into that network. Enter the following: GAD(config)#access-list 102 permit tcp any any established The keyword established in this line only permits TCP traffic that originated from the network. g. To make network management and troubleshooting easier, it is also decided to permit ICMP into the network. This will allow the internal hosts to receive ICMP messages (e.g., ping messages). Enter the following: GAD(config)#access-list 102 permit icmp any any echo-reply GAD(config)#access-list 102 permit icmp any any unreachable The first line only allows successful pings back into the corporate network. The second line allows unsuccessful ping messages to be displayed. h. At this time no other traffic is desired into the corporate network. Therefore enter the following: GAD(config)#access-list 102 deny ip any any i. Finally, apply the access-list to the corporate network Fast Ethernet port. GAD(config)#interface ethernet1 GAD(config-if)#ip access-group 102 out j. Remember that an interface can support one incoming and one outgoing access list. To verify this, issue the show ip interface fa1 command. The output should confirm that the outgoing access list is 102 and that the inbound access list is 101. k. Use the show access-lists command to verify the syntax of the access lists. The output should be similar to the following: CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
8 GAD#show access-lists Extended IP access list 101 permit ip any deny ip any any Extended IP access list 102 permit tcp any any established permit icmp any any echo-reply permit icmp any any unreachable deny ip any any Access lists may have to deleted and re-entered if there is any discrepancy between the preceding output and the configuration. l. Now the access list needs to be tested. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? Yes Can Host B ping Host A? YesNo Host A IP Address : Default Gateway : C:\> Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL= CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
9 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Windows 2000 IP Configuration IP Address : Default Gateway : Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Minimum = 15ms, Maximum = 31ms, Average = 19ms C:\>ping Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms Host A should be able to ping all locations. However, no other host should be able to ping Host A CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
10 m. On Host A, open a Web browser such as Windows Explorer or Netscape Navigator and enter the address of the Web Server in the address location. [ ] Verify that Host A still has Web access to the Web Server. Can Host A view the index.html page? Yes n. Host A should still be able to view the index.html page in the Web Browser. Troubleshoot as necessary. o. The internal corporate network is now secure. Next we need to secure the DMZ network. Step 3 Protect the DMZ Network a. The DMZ network will house only one external server that will provide World Wide Web services. Other services such as , FTP, and DNS will be implemented at a later time. Although the one server creates a single point of failure, the service is only informational and not considered mission critical. b. Configure an extended access list to protect the DMZ network. Again, as with the corporate network, specify which traffic can exit the network and apply it to the interface. Enter the following: GAD#conf terminal Enter configuration commands, one per line. End with CNTL/Z. GAD(config)#access-list 111 permit ip any GAD(config)#access-list 111 deny ip any any GAD(config)#interface ethernetfa0 GAD(config-if)#ip access-group 111 in c. Now test the new access lists. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? Yes Can Host B ping Host A? YesNo Host A IP Address : Default Gateway : C:\> CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
11 Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Minimum = 15ms, Maximum = 31ms, Average = 19ms C:\>ping CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
12 Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms Host A should be able to ping all locations. However, external hosts should not be able to ping Host A. d. Next, an outbound extended access list is required to specify which traffic can enter the DMZ network. Traffic entering the DMZ network will be coming from either the Internet or the corporate network requesting World Wide Web services. e. Configure an outbound extended access-list specifying that World Wide Web requests be allowed into the network. Enter the following: GAD(config)#access-list 112 permit tcp any host eq www This line will allow World Wide Web services destined for the Web server into the DMZ network. What command would be entered to allow DNS requests into the DMZ? eq 53 What command would be entered to allow requests into the DMZ? eq 25 What command would be entered to allow FTP requests into the DMZ? eq 21 f. For management purposes, it would be useful to let corporate users ping the Web Server. However, Internet users should not be provided the same privilege. Add a line to the access list to allow only corporate users ICMP access into the DMZ network. Enter the following: GAD(config)#access-list 112 permit icmp host This line only allows hosts on the Corporate network to ping the Web Server. Although the configuration could be more restrictive with the ICMP options, it is not viewed as being necessary. g. Other services could be permitted into the DMZ network in the future. However, at this time, no other traffic is to be permitted into the DMZ network. Therefore enter the following: GAD(config)#access-list 112 deny ip any any h. Apply the outbound access-list to the DMZ network Fast Ethernet port. GAD(config)#interface fa ethernet 0 GAD(config-if)#ip access-group 112 out CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
13 i. To verify the syntax of the access lists, use the show-access-lists command. The output should be similar to the following: GAD#show access-lists Extended IP access list 101 permit ip any (70 matches) deny ip any any Extended IP access list 102 permit tcp any any established (8 matches) permit icmp any any echo-reply (12 matches) permit icmp any any unreachable deny ip any any (4 matches) Extended IP access list 111 permit ip any (59 matches) deny ip any any Extended IP access list 112 permit tcp any host eq www (29 matches) permit icmp host (4 matches) deny ip any any (14 matches) The access lists may have to be deleted and re-entered if there is any discrepancy between the preceding output and the configuration. j. The access lists now need to be tested. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? No Can Host B ping Host A? No Host A IP Address : Default Gateway : C:\> Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
14 C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Host B IP Address : Default Gateway : Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\>ping Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\> CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
15 k. Only Host A should be able to ping all locations. Use a Web browser such as Windows Explorer or Netscape Navigator on each host and enter the address of the Web Server in the address location. [ ] Verify that the hosts still have Web access to the Web Server. Can Host A view the index.html page? Yes Can Host B view the index.html page? Yes Both hosts should still be able to view the index.html page in the Web Browser. Troubleshoot as necessary. l. The DMZ network is now secure. Next, we need to configure our external interface to deter spoofing and hacking practices. Step 4 Deter Spoofing a. Networks are becoming increasingly prone to attacks from outside users. Hackers, crackers, and script kiddies are titles used to describe various individuals who maliciously try to break into networks or render networks incapable of responding to legitimate requests (Denial of Service (DoS) attacks). This has proven to be a troublesome for the Internet community. b. You are well aware of the practices used by some of these hackers. A common method that they employ is to attempt to forge a valid internal source IP addresses. This practice is commonly known as spoofing. c. To deter spoofing, it is decided to configure an access list so that Internet hosts cannot easily spoof an internal network addresses. Three common source IP addresses that hackers attempt to forge are valid internal addresses (e.g., ), loopback addresses (i.e., 127.x.x.x), and multicast addresses (i.e., 224.x.x.x 239.x.x.x). d. Configure an inbound access list that will make it difficult for outside users to spoof internal addresses and apply it to the Serial 0 interface. Enter the following: GAD(config)#access-list 121 deny ip any GAD(config)#access-list 121 deny ip any GAD(config)#access-list 121 deny ip any GAD(config)#access-list 121 permit ip any any GAD(config)#interface serial 0 GAD(config-if)#ip access-group 121 in The first line will stop outside users from forging a valid source IP address. The second line stops them from using the loopback address range. The third line stops the practice of hackers using the multicast range of addresses (i.e., ) to create unnecessary internal traffic. e. Verify the syntax of the access lists with the show-access-lists command. The output should be similar to the following: GAD#show access-lists GAD#show access-lists Extended IP access list 101 permit ip any (168 matches) deny ip any any Extended IP access list 102 permit tcp any any established (24 matches) permit icmp any any echo-reply (28 matches) permit icmp any any unreachable CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
16 deny ip any any (12 matches) Extended IP access list 111 permit ip any (122 matches) deny ip any any Extended IP access list 112 permit tcp any host eq www (69 matches) permit icmp host (12 matches) deny ip any any (22 matches) Extended IP access list 121 deny ip any deny ip any deny ip any permit ip any any (47 matches) The access lists may have to be deleted and re-entered if there is any discrepancy between the preceding output and the configuration. f. Finally, test if connectivity still exists. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? No Can Host B ping the Web Server? No Can Host B ping Host A? No Host A IP Address : Default Gateway : Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\>ping Pinging with 32 bytes of data: CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
17 Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\>ping Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms Only Host A should be able to ping all locations. g. Use a Web browser such as Windows Explorer or Netscape Navigator on each host and enter the address of the Web Server in the address location. [ ] Verify that the hosts still have Web access to the Web Server CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
18 Can Host A view the index.html page? Yes Can Host B view the index.html page? Yes Both hosts should still be able to view the index.html page in the Web Browser. Troubleshoot as necessary. h. The BMTC network is now secure. Note: The preceding lab is a basic solution to providing a secure network. It is by no means intended to be a complete solution. To properly protect enterprise networks, dedicated network devices such as Cisco PIX devices should be implemented. As well, advanced features such as Network Address Translation and advanced access lists options such as Reflexive access lists, Content Based Access Lists (CBAC), are strongly recommended and well beyond the scope of CCNA certification. Finally, it is recommended that network administrators maintain strong relationships with their service providers to help when network security is compromised. Step 7 Document the ACL a. As a part of all network management, documentation needs to be created. Using the text file created for the configuration, add additional comments. This files should also contain output from the show access-list and the show ip interface commands. b. The file should be saved with other network documentation. The file naming convention should reflect the function of the file and the date of implementation. c. Once finished, erase the start-up configuration on routers, remove and store the cables and Adapter. Also logoff and turn the router off CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
19 Erasing and reloading the router Enter into the privileged EXEC mode by typing enable. If prompted for a password, enter class. If class does not work, ask the instructor for assistance. Router>enable At the privileged EXEC mode, enter the command erase startup-config. Router#erase startup-config The responding line prompt will be: Erasing the nvram filesystem will remove all files Continue? [confirm] Press Enter to confirm. The response should be: Erase of nvram: complete Now at the privileged EXEC mode, enter the command reload. Router#reload The responding line prompt will be: System configuration has been modified. Save? [yes/no]: Type n and then press Enter. The responding line prompt will be: Proceed with reload? [confirm] Press Enter to confirm. In the first line of the response will be: Reload requested by console. After the router has reloaded the line prompt will be: Would you like to enter the initial configuration dialog? [yes/no]: Type n and then press Enter. The responding line prompt will be: Press RETURN to get started Press Enter. The router is ready for the assigned lab to be performed CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
20 ISP#show running-config Building configuration... Current configuration : 592 bytes version 12.2 service timestamps debug uptime service timestamps log uptime no service password-encryption hostname ISP enable secret 5 $1$rc2l$H7OPlBGUn8Lw3WKGHt4820 ip subnet-zero no ip domain-lookup interface Ethernet0 ip address interface Serial0 ip address no fair-queue interface Serial1 no ip address shutdown router rip network ip classless ip http server line con 0 password cisco login line aux 0 password cisco login line vty 0 4 password cisco login end CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
21 ISP#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is not set C C R /24 is subnetted, 2 subnets is directly connected, Serial0/ is directly connected, Ethernet /8 [120/1] via , 00:00:20, Serial0 GAD: GAD#show running-config Building configuration... Current configuration : 1586 bytes version 12.1 service timestamps debug uptime service timestamps log uptime no service password-encryption hostname GAD ip subnet-zero no ip domain-lookup interface Ethernet0 ip address ip access-group 111 in ip access-group 112 out interface Serial0 ip address ip access-group 121 in no fair-queue clockrate interface Ethernet1 ip address ip access-group 101 in ip access-group 102 out interface Serial0/1 no ip address shutdown router rip network network CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
22 ip classless no ip http server access-list 101 permit ip any access-list 101 deny ip any any access-list 102 permit tcp any any established access-list 102 permit icmp any any echo-reply access-list 102 permit icmp any any unreachable access-list 102 deny ip any any access-list 111 permit ip any access-list 111 deny ip any any access-list 112 permit tcp any host eq www access-list 112 permit icmp host access-list 112 deny ip any any access-list 121 deny ip any access-list 121 deny ip any access-list 121 deny ip any access-list 121 permit ip any any line con 0 password cisco login line aux 0 password cisco login line vty 0 4 password cisco login end GAD#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is not set C R C C /24 is subnetted, 2 subnets is directly connected, Serial0/ [120/1] via , 00:00:13, Serial0/ /24 is subnetted, 2 subnets is directly connected, Ethernet is directly connected, Ethernet CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
23 Lab b Simple DMZ Extended Access Lists Instructor Version 2600 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
24 Scenario The BMTC is a small manufacturing company located in Gadsden. They have decided that they would like to create an awareness of their products over the Internet. Therefore their immediate requirement is to promote their products to potential customers by providing product overviews, reports, and testimonials. Future requirements could include , FTP, DNS, and online e- commerce services. They have contracted you to design and configure a secure infrastructure to support their internal and external network requirements while maintaining fiscal responsibility which means make it secure but keep costs down. After careful analysis, it is proposed to create a two-tier security architecture consisting of a corporate network zone and a DeMilitarized Zone (DMZ). The corporate network zone would house private servers and internal clients. The DMZ would house only one external server that would provide World Wide Web services. Although the one server creates a single point of failure, the service is only informational and not considered mission critical. They liked the proposal and have signed a contract. Step 1 Basic Router and Host Configurations a. Interconnect the routers and hosts as shown in the diagram. Configure all router basics such as hostname, router interfaces, and routing protocol. Use the preceding diagram and tables for reference. The configurations on each router should similar to the following: GAD#show running-config <Output Omitted> hostname GAD interface FastEthernet0/0 ip address interface Serial0/0 ip address clock rate interface FastEthernet0/1 ip address router rip network network GAD# ISP#show running-config <Output Omitted> hostname ISP interface FastEthernet0/0 ip address interface Serial0/0 ip address CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
25 router rip network ISP# b. Configure the hosts with the correct settings using the information previously defined. c. To make the lab more realistic, web server software should be installed on the web server host. Examples include Microsoft IIS or Microsoft Personal Web Server (Windows 98). A third-party software such as TinyWeb Server ( can be used. If TinyWeb Server is used, it is recommended that TinyBox ( also be installed, which is a GUI front-end for TinyWeb Server. Be sure to create a default index.html page. The web page should include a message such as Hello World. Save the page as instructed by the Web Server software. d. Before applying any type of access list, it is important to verify reachability between systems. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping Host B? Yes Can Host A ping the Web Server? Yes Can Host B ping Host A? Yes Can Host B ping the Web Server? Yes Host A IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=16ms TTL= CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
26 Minimum = 0ms, Maximum = 16ms, Average = 4ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Minimum = 16ms, Maximum = 31ms, Average = 19ms All hosts should be able to ping each other, if not troubleshoot the unsuccessful interfaces. Always verify the physical layer connections, because they are a common source of connectivity problems. e. On Host A, open a Web browser such as Windows Explorer or Netscape Navigator and enter the address of the Web Server in the address location. [ ] Verify that each Host has Web access to the Web Server. Can Host A view the index.html page? Yes Can Host B view the index.html page? Yes Both hosts should be able to view the index.html page in the Web Browser. Troubleshoot as necessary. f. Now that the infrastructure is in place, it is time to begin securing the internetwork CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
27 Step 2 Protect the Corporate Network a. The corporate network zone houses private servers and internal clients. No other network should be able to access it. b. Configure an extended access list to protect the corporate network. Protecting a corporate network begins by specifying which traffic can exit out the network. Although this may initially sound strange, it becomes clearer when it is known that most hackers are internal employees. The first access list will specify which network can exit out of the network. Enter the following: GAD#conf terminal Enter configuration commands, one per line. End with CNTL/Z. GAD(config)#access-list 101 permit ip any GAD(config)#access-list 101 deny ip any any The first line defines of access list 101 will only let valid corporate users on network into the router. The second line is not really required because of the implicit deny all, but has been added for readability. c. Now we need to apply the access list to the corporate network interface. Enter the following: GAD(config)#interface fa0/1 GAD(config-if)#ip access-group 101 in d. Now it is necessary to test the access lists. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? Yes Can Host B ping Host A? Yes All hosts should be able to ping any location. Host A IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
28 Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Reply from : bytes=32 time=16ms TTL=254 Ping statistics for : Minimum = 16ms, Maximum = 16ms, Average = 16ms Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Minimum = 16ms, Maximum = 31ms, Average = 19ms e. Next, configure an outbound extended access list on the corporate network interface. Traffic entering the corporate network will be coming from either the Internet or the DMZ. For this reason which traffic can be allowed into the corporate network must be limited CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
29 f. The first issue to address is to make sure that only traffic that originated from the corporate network can be allowed back into that network. Enter the following: GAD(config)#access-list 102 permit tcp any any established The keyword established in this line only permits TCP traffic that originated from the network. g. To make network management and troubleshooting easier, it is also decided to permit ICMP into the network. This will allow the internal hosts to receive ICMP messages (e.g., ping messages). Enter the following: GAD(config)#access-list 102 permit icmp any any echo-reply GAD(config)#access-list 102 permit icmp any any unreachable The first line only allows successful pings back into the corporate network. The second line allows unsuccessful ping messages to be displayed. h. At this time no other traffic is desired into the corporate network. Therefore enter the following: GAD(config)#access-list 102 deny ip any any i. Finally, apply the access-list to the corporate network Fast Ethernet port. GAD(config)#interface fa0/1 GAD(config-if)#ip access-group 102 out j. Remember that an interface can support one incoming and one outgoing access list. To verify this, issue the show ip interface fa1 command. The output should confirm that the outgoing access list is 102 and that the inbound access list is 101. k. Use the show access-lists command to verify the syntax of the access lists. The output should be similar to the following: GAD#show access-lists Extended IP access list 101 permit ip any deny ip any any Extended IP access list 102 permit tcp any any established permit icmp any any echo-reply permit icmp any any unreachable deny ip any any Access lists may have to deleted and re-entered if there is any discrepancy between the preceding output and the configuration. l. Now the access list needs to be tested. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? Yes Can Host B ping Host A? No CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
30 Host A C:\> IP Address : Default Gateway : Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Windows 2000 IP Configuration IP Address : Default Gateway : Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL= CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
31 Minimum = 15ms, Maximum = 31ms, Average = 19ms C:\>ping Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms Host A should be able to ping all locations. However, no other host should be able to ping Host A. m. On Host A, open a Web browser such as Windows Explorer or Netscape Navigator and enter the address of the Web Server in the address location. [ ] Verify that Host A still has Web access to the Web Server. Can Host A view the index.html page? Yes n. Host A should still be able to view the index.html page in the Web Browser. Troubleshoot as necessary. o. The internal corporate network is now secure. Next we need to secure the DMZ network. Step 3 Protect the DMZ Network a. The DMZ network will house only one external server that will provide World Wide Web services. Other services such as , FTP, and DNS will be implemented at a later time. Although the one server creates a single point of failure, the service is only informational and not considered mission critical. b. Configure an extended access list to protect the DMZ network. Again, as with the corporate network, specify which traffic can exit the network and apply it to the interface. Enter the following: GAD#conf terminal Enter configuration commands, one per line. End with CNTL/Z. GAD(config)#access-list 111 permit ip any GAD(config)#access-list 111 deny ip any any GAD(config)#interface fa0/0 GAD(config-if)#ip access-group 111 in c. Now test the new access lists. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? Yes Can Host B ping Host A? No Host A CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
32 C:\> IP Address : Default Gateway : Reply from : bytes=32 time=16ms TTL=127 Minimum = 0ms, Maximum = 16ms, Average = 4ms C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Host B Windows 2000 IP Configuration IP Address : Default Gateway : Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL= CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
33 Minimum = 15ms, Maximum = 31ms, Average = 19ms C:\>ping Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms Host A should be able to ping all locations. However, external hosts should not be able to ping Host A. d. Next, an outbound extended access list is required to specify which traffic can enter the DMZ network. Traffic entering the DMZ network will be coming from either the Internet or the corporate network requesting World Wide Web services. e. Configure an outbound extended access-list specifying that World Wide Web requests be allowed into the network. Enter the following: GAD(config)#access-list 112 permit tcp any host eq www This line will allow World Wide Web services destined for the Web server into the DMZ network. What command would be entered to allow DNS requests into the DMZ? eq 53 What command would be entered to allow requests into the DMZ? eq 25 What command would be entered to allow FTP requests into the DMZ? eq 21 f. For management purposes, it would be useful to let corporate users ping the Web Server. However, Internet users should not be provided the same privilege. Add a line to the access list to allow only corporate users ICMP access into the DMZ network. Enter the following: GAD(config)#access-list 112 permit icmp host This line only allows hosts on the Corporate network to ping the Web Server. Although the configuration could be more restrictive with the ICMP options, it is not viewed as being necessary. g. Other services could be permitted into the DMZ network in the future. However, at this time, no other traffic is to be permitted into the DMZ network. Therefore enter the following: GAD(config)#access-list 112 deny ip any any h. Apply the outbound access-list to the DMZ network Fast Ethernet port CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
34 GAD(config)#interface fa 0/0 GAD(config-if)#ip access-group 112 out i. To verify the syntax of the access lists, use the show-access-lists command. The output should be similar to the following: GAD#show access-lists Extended IP access list 101 permit ip any (70 matches) deny ip any any Extended IP access list 102 permit tcp any any established (8 matches) permit icmp any any echo-reply (12 matches) permit icmp any any unreachable deny ip any any (4 matches) Extended IP access list 111 permit ip any (59 matches) deny ip any any Extended IP access list 112 permit tcp any host eq www (29 matches) permit icmp host (4 matches) deny ip any any (14 matches) The access lists may have to be deleted and re-entered if there is any discrepancy between the preceding output and the configuration. j. The access lists now need to be tested. [ ] Verify reachability by pinging all systems and routers from each system. Can Host A ping the Web Server? Yes Can Host A ping Host B? Yes Can Host B ping the Web Server? No Can Host B ping Host A? No Host A IP Address : Default Gateway : C:\> Reply from : bytes=32 time=16ms TTL= CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
35 Minimum = 0ms, Maximum = 16ms, Average = 4ms C:\>ping Pinging with 32 bytes of data: Reply from : bytes=32 time=31ms TTL=126 Reply from : bytes=32 time=15ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Reply from : bytes=32 time=16ms TTL=126 Ping statistics for : Minimum = 15ms, Maximum = 31ms, Average = 19ms Host B IP Address : Default Gateway : Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\>ping Pinging with 32 bytes of data: Ping statistics for : Minimum = 0ms, Maximum = 0ms, Average = 0ms C:\> k. Only Host A should be able to ping all locations. Use a Web browser such as Windows Explorer or Netscape Navigator on each host and enter the address of the Web Server in the address location CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
36 [ ] Verify that the hosts still have Web access to the Web Server. Can Host A view the index.html page? Yes Can Host B view the index.html page? Yes Both hosts should still be able to view the index.html page in the Web Browser. Troubleshoot as necessary. l. The DMZ network is now secure. Next, we need to configure our external interface to deter spoofing and hacking practices. Step 4 Deter Spoofing a. Networks are becoming increasingly prone to attacks from outside users. Hackers, crackers, and script kiddies are titles used to describe various individuals who maliciously try to break into networks or render networks incapable of responding to legitimate requests (Denial of Service (DoS) attacks). This has proven to be a troublesome for the Internet community. b. You are well aware of the practices used by some of these hackers. A common method that they employ is to attempt to forge a valid internal source IP addresses. This practice is commonly known as spoofing. c. To deter spoofing, it is decided to configure an access list so that Internet hosts cannot easily spoof an internal network addresses. Three common source IP addresses that hackers attempt to forge are valid internal addresses (e.g., ), loopback addresses (i.e., 127.x.x.x), and multicast addresses (i.e., 224.x.x.x 239.x.x.x). d. Configure an inbound access list that will make it difficult for outside users to spoof internal addresses and apply it to the Serial 0 interface. Enter the following: GAD(config)#access-list 121 deny ip any GAD(config)#access-list 121 deny ip any GAD(config)#access-list 121 deny ip any GAD(config)#access-list 121 permit ip any any GAD(config)#interface serial 0/0 GAD(config-if)#ip access-group 121 in The first line will stop outside users from forging a valid source IP address. The second line stops them from using the loopback address range. The third line stops the practice of hackers using the multicast range of addresses (i.e., ) to create unnecessary internal traffic. e. Verify the syntax of the access lists with the show-access-lists command. The output should be similar to the following: GAD#show access-lists GAD#show access-lists Extended IP access list 101 permit ip any (168 matches) deny ip any any Extended IP access list 102 permit tcp any any established (24 matches) permit icmp any any echo-reply (28 matches) permit icmp any any unreachable deny ip any any (12 matches) Extended IP access list 111 permit ip any (122 matches) deny ip any any CCNA 2: Routers and Routing Basics v Lab b Copyright 2003, Cisco Systems, Inc.
Lab b Simple DMZ Extended Access Lists
 Lab 11.2.3b Simple DMZ Extended Access Lists Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics
Lab 11.2.3b Simple DMZ Extended Access Lists Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics
Lab c Simple DMZ Extended Access Lists
 Lab 11.2.3c Simple DMZ Extended Access Lists Objective In this lab, the use extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics v 3.0
Lab 11.2.3c Simple DMZ Extended Access Lists Objective In this lab, the use extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 1-9 CCNA 2: Routers and Routing Basics v 3.0
Lab VTY Restriction Instructor Version 2500
 Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab b Standard ACLs Instructor Version 2500
 Lab 11.2.1b Standard ACLs Instructor Version 2500 Objective Scenario Plan, configure, and apply a standard ACL to permit or deny specific traffic and test the ACL to determine if the desired results were
Lab 11.2.1b Standard ACLs Instructor Version 2500 Objective Scenario Plan, configure, and apply a standard ACL to permit or deny specific traffic and test the ACL to determine if the desired results were
Lab Configuring IGRP Instructor Version 2500
 Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500
 Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab b Simple Extended Access Lists
 Lab 11.2.2b Simple Extended Access Lists 1-7 CCNA 2: Simple Extended Access Lists v 3.1 - Lab 11.2.2b Copyright 2003, Cisco Systems, Inc. Objective Scenario In this lab, configuring extended access lists
Lab 11.2.2b Simple Extended Access Lists 1-7 CCNA 2: Simple Extended Access Lists v 3.1 - Lab 11.2.2b Copyright 2003, Cisco Systems, Inc. Objective Scenario In this lab, configuring extended access lists
Lab Configuring Static Routes Instructor Version 2500
 Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Lab Troubleshooting IP Address Issues Instructor Version 2500
 Lab 4.2.6 Troubleshooting IP Address Issues Instructor Version 2500 Objective Configure two routers and two workstations in a small WAN. Troubleshoot problems introduced by incorrect configurations. Background/Preparation
Lab 4.2.6 Troubleshooting IP Address Issues Instructor Version 2500 Objective Configure two routers and two workstations in a small WAN. Troubleshoot problems introduced by incorrect configurations. Background/Preparation
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Lab Troubleshooting Routing Issues with debug Instructor Version 2500
 Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab Establishing and Verifying a Telnet Connection Instructor Version 2500
 Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Lab Backing up Configuration Files Instructor Version 2500
 Lab 3.2.9 Backing up Configuration Files Instructor Version 2500 Objective Demonstrate the capture of the running configuration of a router to an ASCII text file with HyperTerminal. Edit or modify the
Lab 3.2.9 Backing up Configuration Files Instructor Version 2500 Objective Demonstrate the capture of the running configuration of a router to an ASCII text file with HyperTerminal. Edit or modify the
Lab Configuring OSPF Timers 2500 Series
 Lab 2.3.5 Configuring OSPF Timers 2500 Series Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Lab 2.3.5 Configuring OSPF Timers 2500 Series Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Lab Troubleshooting RIP
 Lab 7.2.6 Troubleshooting RIP Objective Set up an IP addressing scheme using class B networks. Configure RIP on routers. Observe routing activity using the debug ip rip command. Examine routes using the
Lab 7.2.6 Troubleshooting RIP Objective Set up an IP addressing scheme using class B networks. Configure RIP on routers. Observe routing activity using the debug ip rip command. Examine routes using the
Lab Configuring OSPF Authentication 2500 Series
 Lab 2.3.4 Configuring OSPF Authentication 2500 Series Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication
Lab 2.3.4 Configuring OSPF Authentication 2500 Series Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication
Lab 4.2.5a Connectivity Tests Ping
 Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
Lab Verifying RIP v2 Configuration
 Lab 1.2.5 Verifying RIP v2 Configuration Objective Configure RIP v1 and v2 on routers. Use show commands to verify RIP v2 operation. Background/Preparation Cable a network similar to the one shown in the
Lab 1.2.5 Verifying RIP v2 Configuration Objective Configure RIP v1 and v2 on routers. Use show commands to verify RIP v2 operation. Background/Preparation Cable a network similar to the one shown in the
Lab Configuring Router Passwords. Objective. Background/Preparation. Step 1 Login to the router in user EXEC mode
 Lab 3.1.3 Configuring Router Passwords Objective Configure a password for console login to user EXEC mode. Configure a password for virtual terminal (Telnet) sessions. Configure a secret password for privileged
Lab 3.1.3 Configuring Router Passwords Objective Configure a password for console login to user EXEC mode. Configure a password for virtual terminal (Telnet) sessions. Configure a secret password for privileged
Lab Configuring a Serial Interface
 Lab 3.1.5 Configuring a Serial Interface Objective Configure a serial interface on each of two routers so they can communicate. Background/Preparation Any router that meets the interface requirements may
Lab 3.1.5 Configuring a Serial Interface Objective Configure a serial interface on each of two routers so they can communicate. Background/Preparation Any router that meets the interface requirements may
Lab Configuring OSPF Timers
 Lab 2.3.5 Configuring OSPF Timers Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Lab 2.3.5 Configuring OSPF Timers Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Lab Troubleshooting Using traceroute Instructor Version 2500
 Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
TELECOMMUNICATION MANAGEMENT AND NETWORKS
 QUAID-E-AWAM UNIVERSITY OF ENGINEERING SCIENCE AND TECHNOLOGY, NAWABSHAH TELECOMMUNICATION MANAGEMENT AND NETWORKS LAB # 3 CONFIGURING INTERFACES OF ROUTER AND SWITCH Topology Diagram Addressing Table
QUAID-E-AWAM UNIVERSITY OF ENGINEERING SCIENCE AND TECHNOLOGY, NAWABSHAH TELECOMMUNICATION MANAGEMENT AND NETWORKS LAB # 3 CONFIGURING INTERFACES OF ROUTER AND SWITCH Topology Diagram Addressing Table
Lab Well-Known Port Numbers and Multiple Sessions
 Lab 10.2.5 Well-Known Port Numbers and Multiple Sessions Objective Enable HTTP services on a router. Show multiple HTTP and Telnet sessions on a single host. Observe well-known TCP port numbers on the
Lab 10.2.5 Well-Known Port Numbers and Multiple Sessions Objective Enable HTTP services on a router. Show multiple HTTP and Telnet sessions on a single host. Observe well-known TCP port numbers on the
Lab Backing up Configuration Files
 Lab 3.2.9 Backing up Configuration Files Objective Demonstrate the capture of the running configuration of a router to an ASCII text file with HyperTerminal. Edit or modify the configuration with a text
Lab 3.2.9 Backing up Configuration Files Objective Demonstrate the capture of the running configuration of a router to an ASCII text file with HyperTerminal. Edit or modify the configuration with a text
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Lab Advanced Telnet Operations Instructor Version 2500
 Lab 4.2.4 Advanced Telnet Operations Instructor Version 2500 Objective Use the telnet command to remotely access other routers. Verify that the application layer between the source and the destination
Lab 4.2.4 Advanced Telnet Operations Instructor Version 2500 Objective Use the telnet command to remotely access other routers. Verify that the application layer between the source and the destination
Lab 2.8.1: Basic Static Route Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
KIM DONNERBORG / RTS. Cisco Lab Øvelse Af Kim Donnerborg / RTS. Side 0 af 8
 KIM DONNERBORG / RTS Side 0 af 8 INDHOLDSFORTEGNELSE Lab: Basic Router Configuration... 2 Topology Diagram... 2 Addressing Table... 2 Learning Objectives... 2 Scenario... 2 Task 1: Cable the Network....
KIM DONNERBORG / RTS Side 0 af 8 INDHOLDSFORTEGNELSE Lab: Basic Router Configuration... 2 Topology Diagram... 2 Addressing Table... 2 Learning Objectives... 2 Scenario... 2 Task 1: Cable the Network....
Lab Command Modes and Router Identification. Objective. Background/Preparation. Step 1 Login to the router in user EXEC mode
 Lab 3.1.2 Command Modes and Router Identification Objective Identify basic router modes of user EXEC and privileged EXEC. Use commands to enter specific modes. Become familiar with the router prompt for
Lab 3.1.2 Command Modes and Router Identification Objective Identify basic router modes of user EXEC and privileged EXEC. Use commands to enter specific modes. Become familiar with the router prompt for
Lab 1.1.4c Configuring Static NAT Addresses
 Lab 1.1.4c Configuring Static NAT Addresses Objective Configure a router to use network address translation (NAT) to convert internal IP addresses, typically private addresses, into outside public addresses.
Lab 1.1.4c Configuring Static NAT Addresses Objective Configure a router to use network address translation (NAT) to convert internal IP addresses, typically private addresses, into outside public addresses.
Lab Configuring OSPF Authentication
 Lab 2.3.4 Configuring OSPF Authentication Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication into the area.
Lab 2.3.4 Configuring OSPF Authentication Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication into the area.
RealCiscoLAB.com. Chapter 6 Lab 6-2, Using the AS_PATH Attribute. Topology. Objectives. Background. CCNPv6 ROUTE
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab Using the Boot System Command. Objective. Background/Preparation
 Lab 5.1.3 Using the Boot System Command Objective Display information about the Cisco IOS Image (software) that is currently running. Determine where the IOS is booting from. Check the amount of RAM, Flash
Lab 5.1.3 Using the Boot System Command Objective Display information about the Cisco IOS Image (software) that is currently running. Determine where the IOS is booting from. Check the amount of RAM, Flash
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab 1.1.4a Configuring NAT
 Lab 1.1.4a Configuring NAT Objective Configure a router to use network address translation (NAT) to convert internal IP addresses, typically private addresses, into outside public addresses. Background/Preparation
Lab 1.1.4a Configuring NAT Objective Configure a router to use network address translation (NAT) to convert internal IP addresses, typically private addresses, into outside public addresses. Background/Preparation
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Lab Configuring DHCP
 Lab 1.2.6 Configuring DHCP Objective Configure a router for Dynamic Host Configuration Protocol (DHCP) to dynamically assign addresses to attached hosts. Background/Preparation Routing between the ISP
Lab 1.2.6 Configuring DHCP Objective Configure a router for Dynamic Host Configuration Protocol (DHCP) to dynamically assign addresses to attached hosts. Background/Preparation Routing between the ISP
Module 9, Assignment 7
 Module 9, Assignment 7 7.2.3 Control Router via Console (in Packet Tracer) 1. Prepare a Cisco 1841 Router (see figure 6-9). 2. Prepare a PC for administration. 3. Prepare a console cable and plug the serial
Module 9, Assignment 7 7.2.3 Control Router via Console (in Packet Tracer) 1. Prepare a Cisco 1841 Router (see figure 6-9). 2. Prepare a PC for administration. 3. Prepare a console cable and plug the serial
Lab Verifying NAT and PAT Configuration
 Lab 1.1.5 Verifying NAT and PAT Configuration Objective Configure a router for Network Address Translation (NAT) and Port Address Translation (PAT) Test the configuration and verify NAT/PAT statistics
Lab 1.1.5 Verifying NAT and PAT Configuration Objective Configure a router for Network Address Translation (NAT) and Port Address Translation (PAT) Test the configuration and verify NAT/PAT statistics
Lab Configuring Static NAT
 Lab 10.5.1 Configuring Static NAT Objective Configure Network Address Translation (NAT) static translation to provide reliable outside access to three shared company servers. Scenario Step 1 The International
Lab 10.5.1 Configuring Static NAT Objective Configure Network Address Translation (NAT) static translation to provide reliable outside access to three shared company servers. Scenario Step 1 The International
CIS 83 LAB 3 - EIGRP Rich Simms September 23, Objective. Scenario. Topology
 CIS 83 LAB 3 - EIGRP Rich Simms September 23, 2006 Objective The objective of this lab is to become familiar setting up and configuring EIGRP on three routers. EIGRP is a Cisco proprietary distance-vector
CIS 83 LAB 3 - EIGRP Rich Simms September 23, 2006 Objective The objective of this lab is to become familiar setting up and configuring EIGRP on three routers. EIGRP is a Cisco proprietary distance-vector
Lab Verifying PPP Configuration
 Lab 3.3.4 Verifying PPP Configuration Objective Configure a serial interface on two routers with the PPP protocol. Verify and test the link for connectivity. Background/Preparation Cable a network similar
Lab 3.3.4 Verifying PPP Configuration Objective Configure a serial interface on two routers with the PPP protocol. Verify and test the link for connectivity. Background/Preparation Cable a network similar
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Lab Configuring the OSPF Routing Process
 Lab 2.3.1 Configuring the OSPF Routing Process Objective Setup an IP addressing scheme for OSPF area 0. Configure and verify Open Shortest Path First (OSPF) routing. Background/Preparation Cable a network
Lab 2.3.1 Configuring the OSPF Routing Process Objective Setup an IP addressing scheme for OSPF area 0. Configure and verify Open Shortest Path First (OSPF) routing. Background/Preparation Cable a network
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
STUDENT LAB GUIDE CCNA ( )
 STUDENT LAB GUIDE CCNA (640-802) Developed By, Router Infotech Career Academy LAB: 09 Static Route Configuration Objective: To configure & implement Static Route successfully on said devices and test its
STUDENT LAB GUIDE CCNA (640-802) Developed By, Router Infotech Career Academy LAB: 09 Static Route Configuration Objective: To configure & implement Static Route successfully on said devices and test its
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA 2: Routers
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA 2: Routers
Building the Routing Table. Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles
 Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Lab Managing the MAC Address Table 2900XL Series
 Lab 6.2.3 Managing the MAC Address Table 2900XL Series Objective Create a basic switch configuration. Manage the switch MAC table. Background/Preparation Cable a network similar to the one in the diagram.
Lab 6.2.3 Managing the MAC Address Table 2900XL Series Objective Create a basic switch configuration. Manage the switch MAC table. Background/Preparation Cable a network similar to the one in the diagram.
Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on a router.
 Lab 5.2.5 Managing IOS Images with TFTP Objective Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on a router. Background/Preparation
Lab 5.2.5 Managing IOS Images with TFTP Objective Backup a copy of a router IOS from flash to a TFTP server. Reload the backup IOS software image from a TFTP server into flash on a router. Background/Preparation
Lab : Challenge OSPF Configuration Lab. Topology Diagram. Addressing Table. Default Gateway. Device Interface IP Address Subnet Mask
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 HQ S0/0/0 S0/0/1 Lo1 10.10.10.1 255.255.255.252 Fa0/0 Branch1 S0/0/0 S0/0/1 Fa0/0 Branch2 S0/0/0 S0/0/1 PC1
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 HQ S0/0/0 S0/0/1 Lo1 10.10.10.1 255.255.255.252 Fa0/0 Branch1 S0/0/0 S0/0/1 Fa0/0 Branch2 S0/0/0 S0/0/1 PC1
CIS 83 LAB 2 - Single Area OSPF Rich Simms September 12, Objective. Scenario. Topology
 CIS 83 LAB 2 - Single Area OSPF Rich Simms September 12, 2006 Objective The objective of this lab is to become familiar setting up and configuring OSPF on three routers for a single area. OSPF is our first
CIS 83 LAB 2 - Single Area OSPF Rich Simms September 12, 2006 Objective The objective of this lab is to become familiar setting up and configuring OSPF on three routers for a single area. OSPF is our first
Lab Capturing and Analyzing Network Traffic
 Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Table of Contents. Cisco NAT Order of Operation
 Table of Contents NAT Order of Operation...1 Document ID: 6209...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...1 NAT Overview...1 NAT Configuration and Output...2
Table of Contents NAT Order of Operation...1 Document ID: 6209...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...1 Conventions...1 NAT Overview...1 NAT Configuration and Output...2
Lab 6: Access Lists. Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/ R1
 Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Lab Router Configuration Using Setup Instructor Version 2500
 Lab 2.2.1 Router Configuration Using Setup Instructor Version 2500 Objective Use the System Configuration dialog (setup). Establish some basic router configurations. Background/Preparation A new router
Lab 2.2.1 Router Configuration Using Setup Instructor Version 2500 Objective Use the System Configuration dialog (setup). Establish some basic router configurations. Background/Preparation A new router
Seattle Cisco Users Group
 Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Context Based Access Control (CBAC): Introduction and Configuration
 Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Device Interface IP Address Subnet Mask Default Gateway
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP Fa0/0 172.20.1.129 255.255.255.128 N/A S0/0/0 172.20.1.1 255.255.255.128 N/A Fa0/0 172.20.0.129 255.255.255.128
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP Fa0/0 172.20.1.129 255.255.255.128 N/A S0/0/0 172.20.1.1 255.255.255.128 N/A Fa0/0 172.20.0.129 255.255.255.128
Troubleshooting Network analysis Software communication tests and development Education. Protocols used for communication (10 seconds capture)
 Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab Configuring Legacy DDR
 Lab 4.3.2 Configuring Legacy DDR Objective Configure an ISDN router to make a legacy dial-on-demand routing (DDR) call to another ISDN capable router. When the DDR connection is successfully made, augment
Lab 4.3.2 Configuring Legacy DDR Objective Configure an ISDN router to make a legacy dial-on-demand routing (DDR) call to another ISDN capable router. When the DDR connection is successfully made, augment
Case Study 2: Frame Relay and OSPF Solution
 Case Study 2: Frame Relay and OSPF Solution Objective In this case study, you troubleshoot a complex scenario involving Frame Relay and Open Shortest Path First (OSPF). Figure 2-1 shows the topology for
Case Study 2: Frame Relay and OSPF Solution Objective In this case study, you troubleshoot a complex scenario involving Frame Relay and Open Shortest Path First (OSPF). Figure 2-1 shows the topology for
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Chapter 8 Lab 8-3, Configuring 6to4 Tunnels
 Chapter 8 Lab 8-3, Configuring 6to4 Tunnels Topology Objectives Configure EIGRP for IPv4. Create a 6to4 tunnel. Configure static IPv6 routes. Background In this lab, you configure EIGRP for full connectivity
Chapter 8 Lab 8-3, Configuring 6to4 Tunnels Topology Objectives Configure EIGRP for IPv4. Create a 6to4 tunnel. Configure static IPv6 routes. Background In this lab, you configure EIGRP for full connectivity
Lab Configuring ISDN BRI (U-Interface)
 Lab 4.2.1 Configuring ISDN BRI (U-Interface) Objective Configure an ISDN router to make a successful connection to a local ISDN switch. Background/Preparation This lab assumes that a router with an ISDN
Lab 4.2.1 Configuring ISDN BRI (U-Interface) Objective Configure an ISDN router to make a successful connection to a local ISDN switch. Background/Preparation This lab assumes that a router with an ISDN
Lab Configure Cisco IOS Firewall CBAC
 Lab 3.8.3 Configure Cisco IOS Firewall CBAC Objective Scenario Topology Estimated Time: 50 minutes Number of Team Members: Two teams with four students per team. In this lab, students will complete the
Lab 3.8.3 Configure Cisco IOS Firewall CBAC Objective Scenario Topology Estimated Time: 50 minutes Number of Team Members: Two teams with four students per team. In this lab, students will complete the
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
Seattle Cisco Users Group
 Seattle Cisco Users Group CCNA Lab Project Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP December 18, 2010 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Seattle Cisco Users Group CCNA Lab Project Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP December 18, 2010 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Chapter 7 Lab 7-2, Using the AS_PATH Attribute
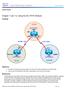 Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Lab Modifying OSPF Cost Metric
 Lab 2.3.3 Modifying OSPF Cost Metric Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Modify OSPF cost metric on an interface. Background/Preparation
Lab 2.3.3 Modifying OSPF Cost Metric Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Modify OSPF cost metric on an interface. Background/Preparation
Lab 9.6.2: Challenge EIGRP Configuration Lab
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway HQ BRANCH1 BRANCH2 PC1 PC2 PC3 Fa0/0 S0/0/0 S0/0/1 Lo1 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/0 S0/0/1 NIC NIC NIC All
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway HQ BRANCH1 BRANCH2 PC1 PC2 PC3 Fa0/0 S0/0/0 S0/0/1 Lo1 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/0 S0/0/1 NIC NIC NIC All
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Lab 9.1.5a Trunking with ISL 2924XL Series
 Lab 9.1.5a Trunking with ISL 2924XL Series Objective Create a basic switch configuration and verify it. Create multiple VLANs, name them and assign multiple member ports to them. Create an ISL trunk line
Lab 9.1.5a Trunking with ISL 2924XL Series Objective Create a basic switch configuration and verify it. Create multiple VLANs, name them and assign multiple member ports to them. Create an ISL trunk line
Firewall Stateful Inspection of ICMP
 The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
Configuration and Management of Networks
 Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Lab Catalyst 2950T and 3550 Series Basic Setup
 Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab: RIP v2 with VLSM
 Lab: RIP v2 with VLSM Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 PC4 PC5 Lo1 S0/0/0 Lo1 S0/0/0 S0/0/1 S/0/0/1 Learning Objectives
Lab: RIP v2 with VLSM Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 PC4 PC5 Lo1 S0/0/0 Lo1 S0/0/0 S0/0/1 S/0/0/1 Learning Objectives
Lab 5.6.2: Challenge RIP Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Lab Configuring IPv6 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
(Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
LAB MANUAL for Computer Network
 LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design,
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design,
Study Guide. Using ACLs to Secure Networks
 CHAPTER 5 ACLs The Study Guide portion of this chapter uses a combination of matching, multiple-choice, and open-ended question exercises to test your knowledge of the various types of access control lists
CHAPTER 5 ACLs The Study Guide portion of this chapter uses a combination of matching, multiple-choice, and open-ended question exercises to test your knowledge of the various types of access control lists
Cisco IOS Firewall Authentication Proxy
 Cisco IOS Firewall Authentication Proxy This feature module describes the Cisco IOS Firewall Authentication Proxy feature. It includes information on the benefits of the feature, supported platforms, configuration
Cisco IOS Firewall Authentication Proxy This feature module describes the Cisco IOS Firewall Authentication Proxy feature. It includes information on the benefits of the feature, supported platforms, configuration
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Lab Managing Router Configuration Files with Terminal Emulation Software
 Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
EIGRP Lab / lo1. .1 lo / /30
 EIGRP Lab 172,16,1.0/24.1 lo1 192.168.20.0/30.2.1 Merida fa0 fa0 Vargas lo2.1 lo2.5.1 lo1 192.168.30.0/24 172.16.2.0/24 192.168.20.4.0/30 Scenario: Loopback0 is used for RouterID Loopback1 is a virtual
EIGRP Lab 172,16,1.0/24.1 lo1 192.168.20.0/30.2.1 Merida fa0 fa0 Vargas lo2.1 lo2.5.1 lo1 192.168.30.0/24 172.16.2.0/24 192.168.20.4.0/30 Scenario: Loopback0 is used for RouterID Loopback1 is a virtual
