Call A.P.P.L.E. TOME OF COPY PROTECTION
|
|
|
- Daniella Stokes
- 5 years ago
- Views:
Transcription
1 Call A.P.P.L.E. World s Largest Apple User Group Since TOME OF COPY PROTECTION Technical Errata for First Printing Compiled August 2018 Changes are Bold Page 20 Half Tracks * BE5A: 0A C B BE 4E N 3D0G <RETURN> Page 22 Quick Sector Editor This table upon using "CALL 36864" will go to slot 6, drive 1. Use buffer $9000, read-in track 0, sector 1, store 3 bytes starting at $3C of the form "$3C: ", and then write the sector back out to disk. Page 26 Write Program 821B: 48 delay1 Page 27 Write Program Listing alignment & Comment : 18 wnib9 clc : 48 wnib7 pha : 9D 8D C0 wnibl sta $C08D,x 5 36 Thus, after the "sta" instruction, the logic state machine will perform a "lsl" on the data latch every 4 cycles. The bit that would normally become the carry bit becomes the bit that is written to disk. It can be seen now that if the latch is not loaded with another "sta" instruction the latch will continue to be "lsl" with zeroes being written to the disk.
2 Page 29 Write Program 29. A delay of 32 cycles is not afforded the last $FF because its purpose was to provide a smooth transition between the last bit of the $AA and the first bit of $FF. Page 41 Diagram 4-3 Gap 0 (Track Gap): Sync $FFs ~80 2. The program then writes 80 sync $FF's (10-bits). Page 42 DOS 3.3 Disk Initialization Steps 5. After these sync bytes a prologue of "D5 AA AD", sometimes called the data header, is written before actual data is encoded onto the disk. When a block of data (342 bytes + checksum, or 343 total bytes) has been written, it is followed by the epilogue "$DE $AA $EB". Page 43 DOS 3.3 Disk Initialization Steps 8. But the epilogue of the last data field will tend to overwrite some of these bytes. Page 46 Sector Gap Write Routine BC79: A9 D5 lda #$D5 (2);begin to write $D5 $AA $96 BCE3: 29 0F and #$0F (2);perform modulo 15 on acc. BCFA: D5 F7 AD AB hex D5F7ADAB Page 52 Forms of Nibble Count Classifications Type A.1: There is also no incidence of overwrite areas, that is, data areas where the bits of one byte overwrite the bits of another byte. This is often referred to as a "perfect track" protection scheme. Page 54 Forms of Nibble Count Classifications Type B.2.a: Moved paragraph to end of "Type B.2" above, and deleted "Type B.2.a" Type B.1.b: Renamed second instance of "Type B.1.b" to "Type B.2.a" Taking B.2 one step farther, the protection can involve checking the track gap not only for the number of bytes but by type, i.e., if the gap is composed of one-hundred, sync $FD's then any aberration will cause a read error. Thus with Types B.2, the formatting of the protection is extremely simple and unless the user is aware of what is being done, they are virtually impossible to copy. In order to be copied, the user must instruct the bit-copier to use a different gap as the write buffer. Page 55 Functional Code (second to last paragraph) GEN.CALLER is not used by NEW.INSTALL when formatting tracks for the various versions. It is only used when a protected disk is booted. GEN.CALLER's entry point is located at $BEB0 which is part of the initialization routine of DOS 3.3.
3 Page 56 Fourteen Works of Art This section describes the program NEW.INSTALL which allows you to protect disks using various nibble count methods. Because the disks protected actually have small programs attached to do the writing and checking of the protection, each version herein is referred to as a program. The source code for the write and read programs is on pages 153 to 250. Page 57 VERSION 4 (renamed to "BUFFER WRITER", moved before "VERSION 1-14" on page 56) These versions require a program that will write out data contained in a data buffer. The BUFFER WRITER, such a program, has three levels. The source code is on page 253. Page 56 VERSION 1-14 When selecting any program version, the user is presented with a standard pattern of messages. First, the program asks for insertion of master disk. If a mistake is made in selecting that version, the next message gives user a chance to abort. Page 56 VERSION 1 (end of last paragraph, etc) Just to make sure the track is read correctly, five bad reads are allowed. Remember, perfect tracks are hard to write, and require a very stable drive speed along with lots of retries. Perfect Tracks (Moved this last paragraph from Version 3 here, and added a new paragraph) One item that might not be clear is how perfect tracks (tracks with no overwrite areas) are created. When the write mode is terminated with the read mode, the drive head will continue to generate unpredictable pulses for at least 4 cycles. Thus, if the user terminates writing at a 36-cycle interval after the last byte is written then the last byte will have the best chance of being written correctly. Besides this, the user must rewrite continually until the last byte written falls on the byte interval of the data already present on the disk. If one type of byte is involved, not that many rewrites must be done. If more bytes are involved, the chances of creating no overwrite are very slim. For example, writing a track of $FF's is easier than writing a track of composed of only "$FF $FD $AD". The hardware required to create a commercial floppy disk with a perfect track is very expensive, while using normal hardware to write a disk with a perfect track takes a lot more time than with normal disks. Both result in a lot of failures, where the written floppy will not pass its copy protection check. When trying to manufacture thousands of floppy disks for retail distribution, this results in a significant increase in the cost of the final product. For this reason, no known commercial software uses a perfect track protection scheme. Pages Renamed VERSION 5-12 to VERSION 4-11 (5 became 4...) Page 58 VERSION 5 (renamed to "VERSION 4", first paragraph) This program uses Type A.3, whose structure was covered earlier in this chapter. In review, the target track is formatted with the following byte pattern where each byte represents one page (256) of bytes.
4 Page 58 VERSION 6 (renamed to "VERSION 5", first paragraph & third paragraph) This program uses Type B.1.a. Because 4-4 encoded data has not been fully covered this program will use 24 pages of $FD's to simulate data. To be more specific, first 32 pages of $FF's are written to erase all previous data on the disk. The read program located at $AE8E looks for the header to make sure the track contains valid data. Page 59 VERSION 7 (renamed to "VERSION 6", last paragraph) The read program located at $AE8E will first look for the address header to ensure the track contains valid data. The actual count is obtained by looking for sector zero and counting the number of bytes that occur before it is found again. Page 60 VERSION 8 (renamed to "VERSION 7", last paragraph) The read program will check the integrity of the track gap, that is, making sure it has 110 $FF's. It does this by checking all 16 sector gaps. One of these sector gaps is also the track gap. The program checks each gap to see if it is composed of 110 $FF's. If after 20 gaps (sectors), the correct one is not found, the program generates a read error. The read/write program from VERSION 6 is used to format the target track. Page 60 VERSION 9 (renamed to "VERSION 8", first paragraph & last paragraph) The track formatted in VERSION 6 can be copied if the user configures a bit-copier to use another gap as the write buffer. This delay loop is the only difference between the read program of VERSION 6 and VERSION 7. Page 61 VERSION 11 (renamed to "VERSION 10") This program relies on the fact that bit-copiers tend to set the track start at the beginning of the largest sync gap, and the $96 in step 6 will be included in that gap. It formats the gap with: sync $FF's (beginning of gap) Page 61 VERSION 12 (renamed to "VERSION 11") These are the transient bit-insertion routines from Chapter 6. An error is reported by rebooting instead of sounding the bell. The read program has no check for disk validity. Page 61 VERSION 12 (added this new version) This is a modified version of the invalid bytes code from Chapter 7. An error is reported by rebooting instead of sounding the bell. The read program has no check for disk validity. Page 62 Version 13 to: $B93E: 85 FC sta $FC
5 Page 63 Examining Nibble Counters in General (fifth paragraph) The counters in this chapter have some failsafe measures to avoid this by making sure the counts check numerous times while writing and then reading the disk more than once when checking for originality. Page 64 Examining Nibble Counters in General (listing alignment) test sei ;set interrupt tax cli ;clear interrupt Page 70 Diagram 6.2 NOTE: Numbers represent the number of bits in a byte. Arrows represent where bits are skipped to fit the stream. Page 71 Modifying DOS The following modifications allow you to test all four cases using DOS 3.3. Slight adjustment of the functional code has been made to be compatible with DOS 3.3, but all timings remain the same. Page 72 All Cases & Case One B6BD: 4C B9 B8 :1 jmp $B8B9 ;write byte B8A9: 20 B9 B6 jsr $B6B9 ;add two zeroes to $AB Page 79 SECTOR NUMBER Example 2. Take: a b c d e f g h Page 84 Read Code (added EXIT line) EXIT equ $E000 ;change to your program's exit point from this code *- ADJUST CODE FOR SUBSEQUENT READ -* Page 85 Read Code (top of listing alignment & jmp change) rd3 and #$7F ;strip high bit rd0 sta $4000,x ;store byte rdfix bit $A1 ;time delay for 9/10 sync *- SHIFT BUFFER -* bpl shift1 ;$80 jmp EXIT ;exit to caller
6 Page 86 Read Code (added "EXIT" line & "adj" alignment) EXIT equ $E000 ;change to your program's exit point from this code *- ADJUST CODE FOR SUBSEQUENT READ -* adj sta rd2+1 ;fix code for 23 or 27 cycle read Page 87 Read Code *- SHIFT BUFFER -* jmp EXIT ;exit to caller Page 89 Mechanics (last paragraph) Referring to Chapter 6 on Bit-Insertion, a delay of 35 cycles can be calculated (8*4+4*1-1). Page 91 Diagram 9-1 Both "35 Cycle Delay" arrows end immediately after the "Read 2" block. Page 95 Diagram 9-2 The "23 Cycle Delay" arrow ends immediately after the first "8 bits?" block. Page 107 Switching Code beq NORMAL lda #<CHECK sta PATCH+1 lda #>CHECK PATCH ldy #$E5 :1 sta $B860 ;if yes, normalize ;else, set up write patch Page 108 LOCKIT Addendum INTERNAL POINTS: $B83E = Sync Byte Used Page 116 Moving the Drive Head lda Ph0off,x ;select appropriate magnet on/off latch Page 122 Enter Calculator Mode by Pressing "C" Exit With Null String LIMITS: $FFFF = 65535
7 Page 124 ALG.xxx (first paragraph) This assumes of course that the file loads at $4000, has the instruction JMP $806 here, and that the rest of the page is 2 byte offsets into the file (one offset for each alg.) with $00's as fillers. Example: $4000: 4C Page 126 The Algorithm Toolkit (third to last paragraph) "In the example, alg# 50 has passed 5 bytes worth of local parameters (the values 01 through 05). If alg# 50 is successful the analysis is complete, otherwise control will pass to the 2nd alg# in the program." Page 152 *=TEST TRACK CLI ;CLEAR INTERRUPT FLAG Page 229 Read Program Version Four (between the last two ]LOOP) CMP #$DD ;FIND FIRST $DD Page 245 Invalid Nibbles Read Version Twelve (renamed title) Invalid Bytes Read Version Twelve
A Technical Overview of Commodore Copy Protection. Glenn Holmer ( ShadowM ) World of Commodore Expo, 12/01/2007
 A Technical Overview of Commodore Copy Protection Glenn Holmer ( ShadowM ) www.lyonlabs.org/commodore/c64.html World of Commodore Expo, 12/01/2007 Why Talk About This? These skills were a black art to
A Technical Overview of Commodore Copy Protection Glenn Holmer ( ShadowM ) www.lyonlabs.org/commodore/c64.html World of Commodore Expo, 12/01/2007 Why Talk About This? These skills were a black art to
COSC 243. Instruction Sets And Addressing Modes. Lecture 7&8 Instruction Sets and Addressing Modes. COSC 243 (Computer Architecture)
 COSC 243 Instruction Sets And Addressing Modes 1 Overview This Lecture Source Chapters 12 & 13 (10 th editition) Textbook uses x86 and ARM (we use 6502) Next 2 Lectures Assembly language programming 2
COSC 243 Instruction Sets And Addressing Modes 1 Overview This Lecture Source Chapters 12 & 13 (10 th editition) Textbook uses x86 and ARM (we use 6502) Next 2 Lectures Assembly language programming 2
; Once Initialized, monitor character in calls to CN05 ; set carry for input, to be tested CN35 C SEC
 // // Serialcode.s // 256 Byte Prom P8 and 512 Byte PROM P9A (second version) for Apple II Serial Card // P9A differs from P9 by adding RTS/ACK software flow control to output and // by removing batch
// // Serialcode.s // 256 Byte Prom P8 and 512 Byte PROM P9A (second version) for Apple II Serial Card // P9A differs from P9 by adding RTS/ACK software flow control to output and // by removing batch
Example Programs for 6502 Microprocessor Kit
 Example Programs for 6502 Microprocessor Kit 0001 0000 0002 0000 GPIO1.EQU $8000 0003 0000 0004 0000 0005 0200.ORG $200 0006 0200 0007 0200 A5 00 LDA $0 0008 0202 8D 00 80 STA $GPIO1 0009 0205 00 BRK 0010
Example Programs for 6502 Microprocessor Kit 0001 0000 0002 0000 GPIO1.EQU $8000 0003 0000 0004 0000 0005 0200.ORG $200 0006 0200 0007 0200 A5 00 LDA $0 0008 0202 8D 00 80 STA $GPIO1 0009 0205 00 BRK 0010
Code Secrets of Wolfenstein 3D IIGS. Eric Shepherd
 Code Secrets of Wolfenstein 3D IIGS Eric Shepherd Fast Screen Refresh with PEI Slamming Or, Dirty Tricks with the Direct Page IIGS Features We Can Abuse Super high-resolution graphics shadowing Bank $01
Code Secrets of Wolfenstein 3D IIGS Eric Shepherd Fast Screen Refresh with PEI Slamming Or, Dirty Tricks with the Direct Page IIGS Features We Can Abuse Super high-resolution graphics shadowing Bank $01
COSC 243. Assembly Language Techniques. Lecture 9. COSC 243 (Computer Architecture)
 COSC 243 Assembly Language Techniques 1 Overview This Lecture Source Handouts Next Lectures Memory and Storage Systems 2 Parameter Passing In a high level language we don t worry about the number of parameters
COSC 243 Assembly Language Techniques 1 Overview This Lecture Source Handouts Next Lectures Memory and Storage Systems 2 Parameter Passing In a high level language we don t worry about the number of parameters
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
The 6502 Instruction Set
 The 6502 Instruction Set Load and Store Group LDA Load Accumulator N,Z LDX Load X Register N,Z LDY Load Y Register N,Z STA Store Accumulator STX Store X Register STY Store Y Register Arithmetic Group ADC
The 6502 Instruction Set Load and Store Group LDA Load Accumulator N,Z LDX Load X Register N,Z LDY Load Y Register N,Z STA Store Accumulator STX Store X Register STY Store Y Register Arithmetic Group ADC
CIS-331 Exam 2 Spring 2016 Total of 110 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
CIS-331 Final Exam Spring 2015 Total of 115 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
CIS-331 Final Exam Spring 2018 Total of 120 Points. Version 1
 Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Intel Architecture Segment:Offset Memory Addressing
 Name: Date: Lab Section: Lab partner s name: Lab PC Number: Objectives: Understanding video memory and character mapping of CGA characters in ROM BIOS, using the DOS debug command. Writing simple assembly-language
Name: Date: Lab Section: Lab partner s name: Lab PC Number: Objectives: Understanding video memory and character mapping of CGA characters in ROM BIOS, using the DOS debug command. Writing simple assembly-language
Initial Bootloader. On power-up, when a computer is turned on, the following operations are performed:
 Initial Bootloader Introduction On power-up, when a computer is turned on, the following operations are performed: 1. The computer performs a power on self test (POST) to ensure that it meets the necessary
Initial Bootloader Introduction On power-up, when a computer is turned on, the following operations are performed: 1. The computer performs a power on self test (POST) to ensure that it meets the necessary
CIS-331 Fall 2014 Exam 1 Name: Total of 109 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
CIS-331 Exam 2 Fall 2014 Total of 105 Points. Version 1
 Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Unit 2 : Computer and Operating System Structure
 Unit 2 : Computer and Operating System Structure Lesson 1 : Interrupts and I/O Structure 1.1. Learning Objectives On completion of this lesson you will know : what interrupt is the causes of occurring
Unit 2 : Computer and Operating System Structure Lesson 1 : Interrupts and I/O Structure 1.1. Learning Objectives On completion of this lesson you will know : what interrupt is the causes of occurring
instruction 1 Fri Oct 13 13:05:
 instruction Fri Oct :0:0. Introduction SECTION INSTRUCTION SET This section describes the aressing modes and instruction types.. Aressing Modes The CPU uses eight aressing modes for flexibility in accessing
instruction Fri Oct :0:0. Introduction SECTION INSTRUCTION SET This section describes the aressing modes and instruction types.. Aressing Modes The CPU uses eight aressing modes for flexibility in accessing
Lab 10 CST8214 Ian! D. Allen Fall 2007
 Name: Date: Lab Section: Lab partner s name: Lab PC Number: Objectives: Understanding video memory and character mapping of CGA characters in ROM BIOS, using the DOS debug command. Writing simple assembly
Name: Date: Lab Section: Lab partner s name: Lab PC Number: Objectives: Understanding video memory and character mapping of CGA characters in ROM BIOS, using the DOS debug command. Writing simple assembly
MC68705U3 Bootstrap ROM
 MC68705U3 Bootstrap ROM ;This is a listing of the Bootstrap ROM which resides in Motorola's MC68705U3 single chip ;micros. Its sole purpose is to program its own EPROM by copying the data from an external
MC68705U3 Bootstrap ROM ;This is a listing of the Bootstrap ROM which resides in Motorola's MC68705U3 single chip ;micros. Its sole purpose is to program its own EPROM by copying the data from an external
538 Lecture Notes Week 5
 538 Lecture Notes Week 5 (Sept. 30, 2013) 1/15 538 Lecture Notes Week 5 Answers to last week's questions 1. With the diagram shown for a port (single bit), what happens if the Direction Register is read?
538 Lecture Notes Week 5 (Sept. 30, 2013) 1/15 538 Lecture Notes Week 5 Answers to last week's questions 1. With the diagram shown for a port (single bit), what happens if the Direction Register is read?
BINARY LOAD AND PUNCH
 BINARY LOAD AND PUNCH To easily decrease the amount of time it takes to load a long tape (Cassette or paper) a BINARY formatting technique can be used instead of the conventional ASCII format used by the
BINARY LOAD AND PUNCH To easily decrease the amount of time it takes to load a long tape (Cassette or paper) a BINARY formatting technique can be used instead of the conventional ASCII format used by the
B: Modbus Map and Retrieving Logs
 B: Modbus Map and Retrieving Logs B.: Introduction Communicator EXT User Manual B.: Modbus Register Map Sections B.3: Data Formats # B.4: Floating Point Values The formula to interpret a Floating Point
B: Modbus Map and Retrieving Logs B.: Introduction Communicator EXT User Manual B.: Modbus Register Map Sections B.3: Data Formats # B.4: Floating Point Values The formula to interpret a Floating Point
KORG DSS-1 UPGRADE 2009 NEW FEATURES LIST
 KORG DSS-1 UPGRADE 2009 NEW FEATURES LIST Introduction 4 Additional feature list 4 DSS-MSRK additions (1987) 4 New features (2009) 4 Part 1 5 DSS-1 Upgrade Summary 5 Part 2 6 Working with the enhanced
KORG DSS-1 UPGRADE 2009 NEW FEATURES LIST Introduction 4 Additional feature list 4 DSS-MSRK additions (1987) 4 New features (2009) 4 Part 1 5 DSS-1 Upgrade Summary 5 Part 2 6 Working with the enhanced
COMPUTE! ISSUE 36 / MAY 1983 / PAGE 244
 Versatile Data Acquisition with VIC Doug Homer and Stan Klein COMPUTE! ISSUE 36 / MAY 1983 / PAGE 244 This simple method of adjusting the VIC's internal jiffy dock can slow it down to match your timing
Versatile Data Acquisition with VIC Doug Homer and Stan Klein COMPUTE! ISSUE 36 / MAY 1983 / PAGE 244 This simple method of adjusting the VIC's internal jiffy dock can slow it down to match your timing
Computer Science and Engineering 331. Midterm Examination #1. Fall Name: Solutions S.S.#:
 Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
Computer Science and Engineering 331 Midterm Examination #1 Fall 2000 Name: Solutions S.S.#: 1 41 2 13 3 18 4 28 Total 100 Instructions: This exam contains 4 questions. It is closed book and notes. Calculators
538 Lecture Notes Week 5
 538 Lecture Notes Week 5 (October 4, 2017) 1/18 538 Lecture Notes Week 5 Announements Midterm: Tuesday, October 25 Answers to last week's questions 1. With the diagram shown for a port (single bit), what
538 Lecture Notes Week 5 (October 4, 2017) 1/18 538 Lecture Notes Week 5 Announements Midterm: Tuesday, October 25 Answers to last week's questions 1. With the diagram shown for a port (single bit), what
You can enter commands at the console any time after the prompt character is displayed.
 NJ7P MON80 Monitor The Monitor is a control program that provides supervisory functions for the Intel microcomputer Single Board Computers. It processes the commands you enter at the console device. The
NJ7P MON80 Monitor The Monitor is a control program that provides supervisory functions for the Intel microcomputer Single Board Computers. It processes the commands you enter at the console device. The
Apple /// Business BASIC Peek/Poke Invokable Module Information
 APPLE /// COMPUTER INFORMATION Apple /// Business BASIC Peek/Poke Invokable Module Information Source Dr. John Jeppson SOFTALK magazine -- August 1982 -- pages 38-48 Compiled By David T Craig -- December
APPLE /// COMPUTER INFORMATION Apple /// Business BASIC Peek/Poke Invokable Module Information Source Dr. John Jeppson SOFTALK magazine -- August 1982 -- pages 38-48 Compiled By David T Craig -- December
ECE3120: Computer Systems Hardware & Software Development Tools
 ECE3120: Computer Systems Hardware & Software Development Tools Manjeera Jeedigunta http://blogs.cae.tntech.edu/msjeedigun21 Email: msjeedigun21@tntech.edu Tel: 931-372-6181, Prescott Hall 120 Using the
ECE3120: Computer Systems Hardware & Software Development Tools Manjeera Jeedigunta http://blogs.cae.tntech.edu/msjeedigun21 Email: msjeedigun21@tntech.edu Tel: 931-372-6181, Prescott Hall 120 Using the
AN1742. Programming the 68HC705J1A In-Circuit By Chris Falk CSG Product Engineering Austin, Texas. Introduction. Overview
 Order this document by /D Programming the 68HC705J1A In-Circuit By Chris Falk CSG Product Engineering Austin, Texas Introduction Overview This application note describes how a user can program the 68HC705J1A
Order this document by /D Programming the 68HC705J1A In-Circuit By Chris Falk CSG Product Engineering Austin, Texas Introduction Overview This application note describes how a user can program the 68HC705J1A
CSE Computer Architecture I Fall 2011 Homework 07 Memory Hierarchies Assigned: November 8, 2011, Due: November 22, 2011, Total Points: 100
 CSE 30321 Computer Architecture I Fall 2011 Homework 07 Memory Hierarchies Assigned: November 8, 2011, Due: November 22, 2011, Total Points: 100 Problem 1: (30 points) Background: One possible organization
CSE 30321 Computer Architecture I Fall 2011 Homework 07 Memory Hierarchies Assigned: November 8, 2011, Due: November 22, 2011, Total Points: 100 Problem 1: (30 points) Background: One possible organization
4. Specifications and Additional Information
 4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
C1098 JPEG Module User Manual
 C1098 JPEG Module User Manual General Description C1098 is VGA camera module performs as a JPEG compressed still camera that can be attached to a wireless or PDA host. Users can send out a snapshot command
C1098 JPEG Module User Manual General Description C1098 is VGA camera module performs as a JPEG compressed still camera that can be attached to a wireless or PDA host. Users can send out a snapshot command
UC Santa Barbara. Operating Systems. Christopher Kruegel Department of Computer Science UC Santa Barbara
 Operating Systems Christopher Kruegel Department of Computer Science http://www.cs.ucsb.edu/~chris/ Input and Output Input/Output Devices The OS is responsible for managing I/O devices Issue requests Manage
Operating Systems Christopher Kruegel Department of Computer Science http://www.cs.ucsb.edu/~chris/ Input and Output Input/Output Devices The OS is responsible for managing I/O devices Issue requests Manage
Chapter 19. Floppy Disk Controller Discussion. Floppy Disk Controller 127
 Floppy Disk Controller 127 Chapter 19 Floppy Disk Controller 19-1. Discussion Without some "mass storage" device such as a floppy disk, even the largest computer would still be just a toy. The SK68K can
Floppy Disk Controller 127 Chapter 19 Floppy Disk Controller 19-1. Discussion Without some "mass storage" device such as a floppy disk, even the largest computer would still be just a toy. The SK68K can
Programming Book for 6809 Microprocessor Kit
 Programming Book for 6809 Microprocessor Kit Wichit Sirichote, wichit.sirichote@gmail.com Image By Konstantin Lanzet - CPU collection Konstantin Lanzet, CC BY-SA 3.0, Rev1.2 March 2018 1 Contents Lab 1
Programming Book for 6809 Microprocessor Kit Wichit Sirichote, wichit.sirichote@gmail.com Image By Konstantin Lanzet - CPU collection Konstantin Lanzet, CC BY-SA 3.0, Rev1.2 March 2018 1 Contents Lab 1
GE MDS, LLC. NETio Series. Protocol Communications Supplement. March 2013 Part No A01, Rev. C
 GE MDS, LLC. NETio Series Protocol Communications Supplement March 2013 Part No. 05-4672A01, Rev. C Modbus Protocol NETio Architectural Implementation As described in detail below, the Modbus RTU protocol
GE MDS, LLC. NETio Series Protocol Communications Supplement March 2013 Part No. 05-4672A01, Rev. C Modbus Protocol NETio Architectural Implementation As described in detail below, the Modbus RTU protocol
A. CPU INSTRUCTION SET SUMMARY
 A. CPU INSTRUCTION SET SUMMARY This appendix summarizes the CPU instruction set. Table A-1 is a matrix of CPU instructions and addressing modes arranged by operation code. Table A-2 lists the CPU instruction
A. CPU INSTRUCTION SET SUMMARY This appendix summarizes the CPU instruction set. Table A-1 is a matrix of CPU instructions and addressing modes arranged by operation code. Table A-2 lists the CPU instruction
MC68705P3 Bootstrap ROM
 MC68705P3 Bootstrap ROM ;This is a listing of the Bootstrap ROM which resides in Motorola's MC68705P3 single chip ;micros. Its sole purpose is to program its own EPROM by copying the data from an external
MC68705P3 Bootstrap ROM ;This is a listing of the Bootstrap ROM which resides in Motorola's MC68705P3 single chip ;micros. Its sole purpose is to program its own EPROM by copying the data from an external
460 Presentation Audio Mixer
 CONTROL PROTOCOL Revision 2.1 - For 460 version 1.08 Command Protocol 2000-2002 Symetrix, Inc. All rights reserved. Printed in the United States of America The information in this guide is subject to change
CONTROL PROTOCOL Revision 2.1 - For 460 version 1.08 Command Protocol 2000-2002 Symetrix, Inc. All rights reserved. Printed in the United States of America The information in this guide is subject to change
Lecture #3 Microcontroller Instruction Set Embedded System Engineering Philip Koopman Wednesday, 20-Jan-2015
 Lecture #3 Microcontroller Instruction Set 18-348 Embedded System Engineering Philip Koopman Wednesday, 20-Jan-2015 Electrical& Computer ENGINEERING Copyright 2006-2015, Philip Koopman, All Rights Reserved
Lecture #3 Microcontroller Instruction Set 18-348 Embedded System Engineering Philip Koopman Wednesday, 20-Jan-2015 Electrical& Computer ENGINEERING Copyright 2006-2015, Philip Koopman, All Rights Reserved
Understanding FAT12. Introduction to Computer Forensics. Kessler/Schirling
 Understanding FAT12 Introduction to Computer Forensics Kessler/Schirling Fall 2002 EXP 248 Project #3 You have a floppy disk image file Examine floppy to find an address and a password, and verify MD5
Understanding FAT12 Introduction to Computer Forensics Kessler/Schirling Fall 2002 EXP 248 Project #3 You have a floppy disk image file Examine floppy to find an address and a password, and verify MD5
USER S MANUAL. CD/DVD Duplication System. Automated Optical Disc Duplication & Printing System (01) 2005 All rights reserved AUTOPRINTER
 Cover.qxd 6/21/2005 10:31 AM Page 1 061605-510800-(01) TM AUTOPRINTER CD/DVD Duplication System Automated Optical Disc Duplication & Printing System USER S MANUAL 2005 All rights reserved TABLE OF CONTENT
Cover.qxd 6/21/2005 10:31 AM Page 1 061605-510800-(01) TM AUTOPRINTER CD/DVD Duplication System Automated Optical Disc Duplication & Printing System USER S MANUAL 2005 All rights reserved TABLE OF CONTENT
ATC-300+ Controller Modbus Communications Guide
 ATC-300+ Controller Modbus Communications Guide CI-AECG-00079-01-E (8/11) 66A7787 revision 1 3. Function Code Descriptions 3.1. Function Code 01 Read ATS Status bits Function code 01 reads the ON / OFF
ATC-300+ Controller Modbus Communications Guide CI-AECG-00079-01-E (8/11) 66A7787 revision 1 3. Function Code Descriptions 3.1. Function Code 01 Read ATS Status bits Function code 01 reads the ON / OFF
CPE/EE 421/521 Fall 2004 Chapter 4 The CPU Hardware Model. Dr. Rhonda Kay Gaede UAH. The CPU Hardware Model - Overview
 CPE/EE 421/521 Fall 2004 Chapter 4 The 68000 CPU Hardware Model Dr. Rhonda Kay Gaede UAH Fall 2004 1 The 68000 CPU Hardware Model - Overview 68000 interface Timing diagram Minimal configuration using the
CPE/EE 421/521 Fall 2004 Chapter 4 The 68000 CPU Hardware Model Dr. Rhonda Kay Gaede UAH Fall 2004 1 The 68000 CPU Hardware Model - Overview 68000 interface Timing diagram Minimal configuration using the
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1
 CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
Regarding the change of names mentioned in the document, such as Mitsubishi Electric and Mitsubishi XX, to Renesas Technology Corp.
 To all our customers Regarding the change of names mentioned in the document, such as Mitsubishi Electric and Mitsubishi XX, to Renesas Technology Corp. The semiconductor operations of Hitachi and Mitsubishi
To all our customers Regarding the change of names mentioned in the document, such as Mitsubishi Electric and Mitsubishi XX, to Renesas Technology Corp. The semiconductor operations of Hitachi and Mitsubishi
EXPERIMENT NO. 1 THE MKT 8085 MICROPROCESSOR TRAINER
 OBJECT: EXPERIMENT NO. 1 THE MKT 8085 MICROPROCESSOR TRAINER To understand the structure and operating instruction of the microprocessor trainer. INTRODUCTION: The MKT 8085 is a single-board microcomputer,
OBJECT: EXPERIMENT NO. 1 THE MKT 8085 MICROPROCESSOR TRAINER To understand the structure and operating instruction of the microprocessor trainer. INTRODUCTION: The MKT 8085 is a single-board microcomputer,
You can examine the contents of a single memory location by typing a single address followed by a Return.
 1 von 5 31.07.2012 14:49 The Woz Monitor When a computer is powered up it must know what it must do. It goes without saying that a piece of software must be executed. Since the computer has just been powered
1 von 5 31.07.2012 14:49 The Woz Monitor When a computer is powered up it must know what it must do. It goes without saying that a piece of software must be executed. Since the computer has just been powered
DNP3 Client Configuration
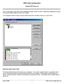 DNP3 Client Configuration in CallistoView version 5.0 This is a description of the unique DNP configuration dialogs and files in DAQ s CallistoView configuration program. It assumes the latest software,
DNP3 Client Configuration in CallistoView version 5.0 This is a description of the unique DNP configuration dialogs and files in DAQ s CallistoView configuration program. It assumes the latest software,
11. A Computing Machine
 COMPUTER SCIENCE S E D G E W I C K / W A Y N E Computer Science Including Programming in Java 11. A Computing Machine Section 5.1 http://introcs.cs.princeton.edu COMPUTER SCIENCE S E D G E W I C K / W
COMPUTER SCIENCE S E D G E W I C K / W A Y N E Computer Science Including Programming in Java 11. A Computing Machine Section 5.1 http://introcs.cs.princeton.edu COMPUTER SCIENCE S E D G E W I C K / W
III. Flags of the Processor Staus Register
 III. Flags of the Processor Staus Register INHALT 1. Meaning 2. Application 2.1 Shifts 2.2 Branches 2.3 Addition and Subtraction 2.4 Comparisons in magnitude 1. Meaning processor status register Overflow
III. Flags of the Processor Staus Register INHALT 1. Meaning 2. Application 2.1 Shifts 2.2 Branches 2.3 Addition and Subtraction 2.4 Comparisons in magnitude 1. Meaning processor status register Overflow
Communications guide. Line Distance Protection System * F1* GE Digital Energy. Title page
 Title page GE Digital Energy D90 Plus Line Distance Protection System Communications guide D90 Plus firmware revision:.9x GE publication code: 60-9070-F (GEK-3469) GE Digital Energy 650 Markland Street
Title page GE Digital Energy D90 Plus Line Distance Protection System Communications guide D90 Plus firmware revision:.9x GE publication code: 60-9070-F (GEK-3469) GE Digital Energy 650 Markland Street
Exam 2 E2-1 Fall Name: Exam 2
 Exam 2 E2-1 Fall 2004 1. Short Answer [20 pts] Exam 2 a. [4 points] Show the contents of registers A, B, SP, and X after the following code executes: lds #$a00 ldab #$23 A = ldaa #$87 ldx #$2543 B = pshd
Exam 2 E2-1 Fall 2004 1. Short Answer [20 pts] Exam 2 a. [4 points] Show the contents of registers A, B, SP, and X after the following code executes: lds #$a00 ldab #$23 A = ldaa #$87 ldx #$2543 B = pshd
GOLD SERIES DVD/CD Duplicator Manual
 GOLD SERIES DVD/CD Duplicator Manual User s Manual Version 3.0 0 TABLE OF CONTENTS Introduction 2 Setup 11 LCD Front Panel Overview 2 o Auto Start Time 11 Menu Overview 3-5 o Display Mode 12 Functions
GOLD SERIES DVD/CD Duplicator Manual User s Manual Version 3.0 0 TABLE OF CONTENTS Introduction 2 Setup 11 LCD Front Panel Overview 2 o Auto Start Time 11 Menu Overview 3-5 o Display Mode 12 Functions
Proposed Common Configuration Method
 Proposed Common Configuration Method July 9, 1991 The Common Configuration Method (CCM) simplifies configuration of disks and other storage devices. This definition includes a Standard AT Compatible Register
Proposed Common Configuration Method July 9, 1991 The Common Configuration Method (CCM) simplifies configuration of disks and other storage devices. This definition includes a Standard AT Compatible Register
Disassembly of MC9S12 op codes Decimal, Hexadecimal and Binary Numbers
 Disassembly of MC9S12 op codes Decimal, Hexadecimal and Binary Numbers o How to disassemble an MC9S12 instruction sequence o Binary numbers are a code and represent what the programmer intends for the
Disassembly of MC9S12 op codes Decimal, Hexadecimal and Binary Numbers o How to disassemble an MC9S12 instruction sequence o Binary numbers are a code and represent what the programmer intends for the
Disassembly of MC9S12 op codes Decimal, Hexadecimal and Binary Numbers
 Disassembly of MC9S12 op codes Decimal, Hexadecimal and Binary Numbers o How to disassemble an MC9S12 instruction sequence o Binary numbers are a code and represent what the programmer intends for the
Disassembly of MC9S12 op codes Decimal, Hexadecimal and Binary Numbers o How to disassemble an MC9S12 instruction sequence o Binary numbers are a code and represent what the programmer intends for the
Chapter 5 - Input / Output
 Chapter 5 - Input / Output Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 5 - Input / Output 1 / 90 1 Motivation 2 Principle of I/O Hardware I/O Devices Device Controllers Memory-Mapped
Chapter 5 - Input / Output Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 5 - Input / Output 1 / 90 1 Motivation 2 Principle of I/O Hardware I/O Devices Device Controllers Memory-Mapped
CISC 7310X. C11: Mass Storage. Hui Chen Department of Computer & Information Science CUNY Brooklyn College. 4/19/2018 CUNY Brooklyn College
 CISC 7310X C11: Mass Storage Hui Chen Department of Computer & Information Science CUNY Brooklyn College 4/19/2018 CUNY Brooklyn College 1 Outline Review of memory hierarchy Mass storage devices Reliability
CISC 7310X C11: Mass Storage Hui Chen Department of Computer & Information Science CUNY Brooklyn College 4/19/2018 CUNY Brooklyn College 1 Outline Review of memory hierarchy Mass storage devices Reliability
Read this before starting!
 Points missed: Student's Name: Total score: /100 points East Tennessee State University Department of Computer and Information Sciences CSCI 2150 (Tarnoff) Computer Organization TEST 3 for Fall Semester,
Points missed: Student's Name: Total score: /100 points East Tennessee State University Department of Computer and Information Sciences CSCI 2150 (Tarnoff) Computer Organization TEST 3 for Fall Semester,
NEXTGEN PROGRAMMING SOFTWARE QUICK START GUIDE Copyright Intermatic 2004
 NEXTGEN PROGRAMMING SOFTWARE QUICK START GUIDE Copyright Intermatic 2004 RECOMMENDED SYSTEM REQUIREMENTS Processor: 500-MHz Intel Pentium-class processor (Minimum: 90- MHz) Memory: 128MB RAM (Minimum:
NEXTGEN PROGRAMMING SOFTWARE QUICK START GUIDE Copyright Intermatic 2004 RECOMMENDED SYSTEM REQUIREMENTS Processor: 500-MHz Intel Pentium-class processor (Minimum: 90- MHz) Memory: 128MB RAM (Minimum:
Computer Systems Organization
 The IAS (von Neumann) Machine Computer Systems Organization Input Output Equipment Stored Program concept Main memory storing programs and data ALU operating on binary data Control unit interpreting instructions
The IAS (von Neumann) Machine Computer Systems Organization Input Output Equipment Stored Program concept Main memory storing programs and data ALU operating on binary data Control unit interpreting instructions
APPLESHARE PC UPDATE INTERNATIONAL SUPPORT IN APPLESHARE PC
 APPLESHARE PC UPDATE INTERNATIONAL SUPPORT IN APPLESHARE PC This update to the AppleShare PC User's Guide discusses AppleShare PC support for the use of international character sets, paper sizes, and date
APPLESHARE PC UPDATE INTERNATIONAL SUPPORT IN APPLESHARE PC This update to the AppleShare PC User's Guide discusses AppleShare PC support for the use of international character sets, paper sizes, and date
Decoding bitstreams for fun and profit
 2018-12-01 11:25 1/13 Decoding bitstreams for fun and profit Decoding bitstreams for fun and profit by lft This article describes a technique for extracting bitfields from a long sequence of bytes stored
2018-12-01 11:25 1/13 Decoding bitstreams for fun and profit Decoding bitstreams for fun and profit by lft This article describes a technique for extracting bitfields from a long sequence of bytes stored
Intecom. March
 Intecom Intecom Systems PDI-1000S MKO Application Manual March 1994 590-2269-002 COMPANY PROPRIETARY STATEMENT All information contained herein is considered company proprietary and is restricted solely
Intecom Intecom Systems PDI-1000S MKO Application Manual March 1994 590-2269-002 COMPANY PROPRIETARY STATEMENT All information contained herein is considered company proprietary and is restricted solely
UNH-IOL MIPI Alliance Test Program
 DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP
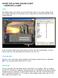 INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP GOAL The Ultima Online client utilizes too much CPU power when it s not doing anything useful. For example, when we are at the logon screen or when we
INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP GOAL The Ultima Online client utilizes too much CPU power when it s not doing anything useful. For example, when we are at the logon screen or when we
CPU08RM/AD REV 3 8M68HC08M. CPU08 Central Processor Unit. Reference Manual
 CPU08RM/AD REV 3 68HC08M6 HC08M68HC 8M68HC08M CPU08 Central Processor Unit Reference Manual blank CPU08 Central Processor Unit Reference Manual Motorola reserves the right to make changes without further
CPU08RM/AD REV 3 68HC08M6 HC08M68HC 8M68HC08M CPU08 Central Processor Unit Reference Manual blank CPU08 Central Processor Unit Reference Manual Motorola reserves the right to make changes without further
EI 338: Computer Systems Engineering (Operating Systems & Computer Architecture)
 EI 338: Computer Systems Engineering (Operating Systems & Computer Architecture) Dept. of Computer Science & Engineering Chentao Wu wuct@cs.sjtu.edu.cn Download lectures ftp://public.sjtu.edu.cn User:
EI 338: Computer Systems Engineering (Operating Systems & Computer Architecture) Dept. of Computer Science & Engineering Chentao Wu wuct@cs.sjtu.edu.cn Download lectures ftp://public.sjtu.edu.cn User:
Show Designer 1. Software Revision 3.11
 Show Designer 1 Software Revision 3.11 OVERVIEW The Show Designer 1 is a lighting controller based on the successful and simple to use Show Designer. The Show Designer 1 adds to the existing features of
Show Designer 1 Software Revision 3.11 OVERVIEW The Show Designer 1 is a lighting controller based on the successful and simple to use Show Designer. The Show Designer 1 adds to the existing features of
Communication and Networks. Problems
 Electrical and Information Technology Communication and Networks Problems Network Layer (IP) 2016 Problems 1. The table below describes the next hop for each destination in the network for all nodes in
Electrical and Information Technology Communication and Networks Problems Network Layer (IP) 2016 Problems 1. The table below describes the next hop for each destination in the network for all nodes in
Microprocessor Architecture. mywbut.com 1
 Microprocessor Architecture mywbut.com 1 Microprocessor Architecture The microprocessor can be programmed to perform functions on given data by writing specific instructions into its memory. The microprocessor
Microprocessor Architecture mywbut.com 1 Microprocessor Architecture The microprocessor can be programmed to perform functions on given data by writing specific instructions into its memory. The microprocessor
AN1239. HC05 MCU Keypad Decoding Techniques Using the MC68HC705J1A. Introduction
 Order this document by /D Rev. 1.0 HC05 MCU Keypad Decoding Techniques Using the MC68HC705J1A By David Yoder CSIC Applications Introduction This application note demonstrates the use of a matrix keypad
Order this document by /D Rev. 1.0 HC05 MCU Keypad Decoding Techniques Using the MC68HC705J1A By David Yoder CSIC Applications Introduction This application note demonstrates the use of a matrix keypad
Functional Units of a Modern Computer
 Functional Units of a Modern Computer We begin this lecture by repeating a figure from a previous lecture. Logically speaking a computer has four components. Connecting the Components Early schemes for
Functional Units of a Modern Computer We begin this lecture by repeating a figure from a previous lecture. Logically speaking a computer has four components. Connecting the Components Early schemes for
CSE Computer Architecture I Fall 2009 Homework 08 Pipelined Processors and Multi-core Programming Assigned: Due: Problem 1: (10 points)
 CSE 30321 Computer Architecture I Fall 2009 Homework 08 Pipelined Processors and Multi-core Programming Assigned: November 17, 2009 Due: December 1, 2009 This assignment can be done in groups of 1, 2,
CSE 30321 Computer Architecture I Fall 2009 Homework 08 Pipelined Processors and Multi-core Programming Assigned: November 17, 2009 Due: December 1, 2009 This assignment can be done in groups of 1, 2,
DAN64: an AVR based 8-bit Microcomputer
 DAN64: an AVR based 8-bit Microcomputer Juan J. Martínez jjm@usebox.net Manual for V.R - May 0, 06 Features Composite video black and white output, 56 x 9 resolution, x 4 characters (8 x 8 pixels font,
DAN64: an AVR based 8-bit Microcomputer Juan J. Martínez jjm@usebox.net Manual for V.R - May 0, 06 Features Composite video black and white output, 56 x 9 resolution, x 4 characters (8 x 8 pixels font,
Black Box Debugging of Embedded Systems
 Black Box Debugging of Embedded Systems Introduction: Alexandru Ariciu Background in hacking Worked as a hacker for my whole life Worked in corporate security before (Pentester) Currently an ICS Penetration
Black Box Debugging of Embedded Systems Introduction: Alexandru Ariciu Background in hacking Worked as a hacker for my whole life Worked in corporate security before (Pentester) Currently an ICS Penetration
Blu-ray/DVD/CD Duplicator Control Manual. User s Manual
 Blu-ray/DVD/CD Duplicator Control Manual User s Manual 0 TABLE OF CONTENTS Introduction 2 Setup 12 LCD Front Panel Overview 2 o Auto Start Time 12 HDD Manager o Select Image o Disc => Controller Connection
Blu-ray/DVD/CD Duplicator Control Manual User s Manual 0 TABLE OF CONTENTS Introduction 2 Setup 12 LCD Front Panel Overview 2 o Auto Start Time 12 HDD Manager o Select Image o Disc => Controller Connection
PowerLogic ION6200 Serial Communications Protocol and ION / Modbus Register Map
 70022-05-XX PROTOCOL DOCUMENT 04/2007 PowerLogic ION6200 Serial Communications Protocol and ION / Modbus Register Map This document explains the Modbus protocol on the ION6200 meter. The ION6200 meter
70022-05-XX PROTOCOL DOCUMENT 04/2007 PowerLogic ION6200 Serial Communications Protocol and ION / Modbus Register Map This document explains the Modbus protocol on the ION6200 meter. The ION6200 meter
A T T E N T I O N. Know Your Computer and Be Sure You Are Using the Correct Software
 A T T E N T I O N Know Your Computer and Be Sure You Are Using the Correct Software SWTPC has offered, or is now offering, three types of 6809 computers. In order to make SWTPC supplied software work correctly
A T T E N T I O N Know Your Computer and Be Sure You Are Using the Correct Software SWTPC has offered, or is now offering, three types of 6809 computers. In order to make SWTPC supplied software work correctly
UNIT 4 Device Management
 UNIT 4 Device Management (A) Device Function. (B) Device Characteristic. (C) Disk space Management. (D) Allocation and Disk scheduling Methods. [4.1] Device Management Functions The management of I/O devices
UNIT 4 Device Management (A) Device Function. (B) Device Characteristic. (C) Disk space Management. (D) Allocation and Disk scheduling Methods. [4.1] Device Management Functions The management of I/O devices
Software Revision 1.13
 Software Revision 1.13 OVERVIEW...1 REAR PANEL CONNECTIONS...1 TOP PANEL...1 MENU AND SETUP FUNCTIONS...3 CHOOSE FIXTURES...3 PATCH FIXTURES...4 PATCH CONVENTIONAL DIMMERS...4 COPY FIXTURE...5 LOAD FIXTURE
Software Revision 1.13 OVERVIEW...1 REAR PANEL CONNECTIONS...1 TOP PANEL...1 MENU AND SETUP FUNCTIONS...3 CHOOSE FIXTURES...3 PATCH FIXTURES...4 PATCH CONVENTIONAL DIMMERS...4 COPY FIXTURE...5 LOAD FIXTURE
NAM M6800 DISK-BUG DS VER 3.5 OPT PAG
 NAM M6800 DISK-BUG DS VER 3.5 OPT PAG Floppy Disk Controller Debug Monitor Written 27 Aug 1980 Michael Holley Record of modifications 18 OCT 1981 Disk routines DC-1 23 JAN 1982 Command Table 8 MAY 1982
NAM M6800 DISK-BUG DS VER 3.5 OPT PAG Floppy Disk Controller Debug Monitor Written 27 Aug 1980 Michael Holley Record of modifications 18 OCT 1981 Disk routines DC-1 23 JAN 1982 Command Table 8 MAY 1982
Run-Time Data Structures
 Run-Time Data Structures Static Structures For static structures, a fixed address is used throughout execution. This is the oldest and simplest memory organization. In current compilers, it is used for:
Run-Time Data Structures Static Structures For static structures, a fixed address is used throughout execution. This is the oldest and simplest memory organization. In current compilers, it is used for:
AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30]
![AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30]](/thumbs/80/81792243.jpg) AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] Note: Question Number 1 is compulsory. Marks : 10X1
AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] Note: Question Number 1 is compulsory. Marks : 10X1
Phoenix Technologies, Ltd.
 Phoenix Technologies, Ltd. AwardBIOS Version 4.51PG Post Codes & Error Messages Table of Contents POST Codes - 2 Error Messages - 7 ----------------------------------------------- Proprietary Notice and
Phoenix Technologies, Ltd. AwardBIOS Version 4.51PG Post Codes & Error Messages Table of Contents POST Codes - 2 Error Messages - 7 ----------------------------------------------- Proprietary Notice and
The Memory Component
 The Computer Memory Chapter 6 forms the first of a two chapter sequence on computer memory. Topics for this chapter include. 1. A functional description of primary computer memory, sometimes called by
The Computer Memory Chapter 6 forms the first of a two chapter sequence on computer memory. Topics for this chapter include. 1. A functional description of primary computer memory, sometimes called by
5 Computer Organization
 5 Computer Organization 5.1 Foundations of Computer Science ã Cengage Learning Objectives After studying this chapter, the student should be able to: q List the three subsystems of a computer. q Describe
5 Computer Organization 5.1 Foundations of Computer Science ã Cengage Learning Objectives After studying this chapter, the student should be able to: q List the three subsystems of a computer. q Describe
Introduction. Operating Systems. Outline. Hardware. I/O Device Types. Device Controllers. One OS function is to control devices
 Introduction Operating Systems Input/Output Devices (Ch12.1-12.3, 12.7; 13.1-13.3, 13.7) One OS function is to control devices significant fraction of code (80-90% of Linux) Want all devices to be simple
Introduction Operating Systems Input/Output Devices (Ch12.1-12.3, 12.7; 13.1-13.3, 13.7) One OS function is to control devices significant fraction of code (80-90% of Linux) Want all devices to be simple
Express5800 Urgent Notice
 Express5800 Urgent Notice Rev3 August. 17. 2005 110Ei BIOS PROBLEM (1) Relevant product: N8100-1004F/1005CF/1004CG/1004DG NEC Express5800/110Ei (Produced May ~ July 2005) (2) Problem The unit of BIOS REVISION
Express5800 Urgent Notice Rev3 August. 17. 2005 110Ei BIOS PROBLEM (1) Relevant product: N8100-1004F/1005CF/1004CG/1004DG NEC Express5800/110Ei (Produced May ~ July 2005) (2) Problem The unit of BIOS REVISION
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1
 CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
A program execution is memory safe so long as memory access errors never occur:
 A program execution is memory safe so long as memory access errors never occur: Buffer overflows, null pointer dereference, use after free, use of uninitialized memory, illegal free Memory safety categories
A program execution is memory safe so long as memory access errors never occur: Buffer overflows, null pointer dereference, use after free, use of uninitialized memory, illegal free Memory safety categories
ARM Assembly Language. Programming
 Outline: ARM Assembly Language the ARM instruction set writing simple programs examples Programming hands-on: writing simple ARM assembly programs 2005 PEVE IT Unit ARM System Design ARM assembly language
Outline: ARM Assembly Language the ARM instruction set writing simple programs examples Programming hands-on: writing simple ARM assembly programs 2005 PEVE IT Unit ARM System Design ARM assembly language
CSE Lecture In Class Example Handout
 CSE 30321 Lecture 07-08 In Class Example Handout Part A: J-Type Example: If you look in your book at the syntax for j (an unconditional jump instruction), you see something like: e.g. j addr would seemingly
CSE 30321 Lecture 07-08 In Class Example Handout Part A: J-Type Example: If you look in your book at the syntax for j (an unconditional jump instruction), you see something like: e.g. j addr would seemingly
MC9S12 Assembler Directives A Summary of MC9S12 Instructions Disassembly of MC9S12 op codes. Summary of HCS12 addressing modes ADDRESSING MODES
 MC9S12 Assembler Directives A Summary of MC9S12 Instructions Disassembly of MC9S12 op codes o Review of Addressing Modes o Which branch instruction to use (signed vs unsigned) o Using X and Y registers
MC9S12 Assembler Directives A Summary of MC9S12 Instructions Disassembly of MC9S12 op codes o Review of Addressing Modes o Which branch instruction to use (signed vs unsigned) o Using X and Y registers
Systems Architecture The ARM Processor
 Systems Architecture The ARM Processor The ARM Processor p. 1/14 The ARM Processor ARM: Advanced RISC Machine First developed in 1983 by Acorn Computers ARM Ltd was formed in 1988 to continue development
Systems Architecture The ARM Processor The ARM Processor p. 1/14 The ARM Processor ARM: Advanced RISC Machine First developed in 1983 by Acorn Computers ARM Ltd was formed in 1988 to continue development
The cache is 4-way set associative, with 4-byte blocks, and 16 total lines
 Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
