/tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page 1
|
|
|
- Alfred Bartholomew Wilcox
- 6 years ago
- Views:
Transcription
1 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP > www [S YN] Seq=0 Ack=0 Win=5840 Len=0 MSS=1460 TSV= TSER=0 WS=7 Frame 9 (74 bytes on wire, 74 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 9 Packet Length: 74 bytes Capture Length: 74 bytes Ethernet II, Src: 00:18:f3:a8:0a:8a, Dst: fe:fd:c0:a8:01:01 Destination: fe:fd:c0:a8:01:01 ( ) Source: 00:18:f3:a8:0a:8a ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 60 Identification: 0xbe3b (48699) Flags: 0x04 (Don t Fragment).1.. = Don t fragment: Set Time to live: 64 Header checksum: 0xb957 (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: (54940), Dst Port: www (80), Seq: 0, Ack : 0, Len: 0 Source port: (54940) Destination port: www (80) Sequence number: 0 (relative sequence number) Header length: 40 bytes Flags: 0x0002 (SYN) = Acknowledgment: Not set = Syn: Set Window size: 5840 Checksum: 0x1d0b (correct) Options: (20 bytes) Maximum segment size: 1460 bytes SACK permitted Time stamp: tsval , tsecr 0 Window scale: 7 (multiply by 128) 0000 fe fd c0 a f3 a8 0a 8a E c be 3b b9 57 c0 a8 01 1c cd 9c.<.;@.@..W c8 d6 9c c8 e7 ab a P d0 1d 0b b a 00 0b Y...
2 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP www > [S YN, ACK] Seq=0 Ack=1 Win=65500 Len=0 MSS=512 WS=0 TSV= TSER= Frame 12 (74 bytes on wire, 74 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 12 Packet Length: 74 bytes Capture Length: 74 bytes Ethernet II, Src: fe:fd:c0:a8:01:01, Dst: 00:18:f3:a8:0a:8a Destination: 00:18:f3:a8:0a:8a ( ) Source: fe:fd:c0:a8:01:01 ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 60 Identification: 0x79c4 (31172) Flags: 0x = Don t fragment: Not set Time to live: 43 Header checksum: 0x52cf (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: www (80), Dst Port: (54940), Seq: 0, Ack : 1, Len: 0 Source port: www (80) Destination port: (54940) Sequence number: 0 (relative sequence number) Acknowledgement number: 1 (relative ack number) Header length: 40 bytes Flags: 0x0012 (SYN, ACK) = Syn: Set Window size: Checksum: 0x94af (correct) Options: (20 bytes) Maximum segment size: 512 bytes Window scale: 0 (multiply by 1) Time stamp: tsval , tsecr This is an ACK to the segment in frame: 9 The RTT to ACK the segment was: seconds f3 a8 0a 8a fe fd c0 a E c 79 c b cf cd 9c 33 c8 c0 a8.<y...+.r c d6 9c fd 6c d c8 e7 ac a P...l ff dc 94 af a 45 bf 8f ba 00 0b E...Y.
3 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP > www [A CK] Seq=1 Ack=1 Win=5888 Len=0 TSV= TSER= Frame 13 (66 bytes on wire, 66 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 13 Packet Length: 66 bytes Capture Length: 66 bytes Ethernet II, Src: 00:18:f3:a8:0a:8a, Dst: fe:fd:c0:a8:01:01 Destination: fe:fd:c0:a8:01:01 ( ) Source: 00:18:f3:a8:0a:8a ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 52 Identification: 0xbe3c (48700) Flags: 0x04 (Don t Fragment).1.. = Don t fragment: Set Time to live: 64 Header checksum: 0xb95e (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: (54940), Dst Port: www (80), Seq: 1, Ack : 1, Len: 0 Source port: (54940) Destination port: www (80) Sequence number: 1 (relative sequence number) Acknowledgement number: 1 (relative ack number) Flags: 0x0010 (ACK) Window size: 5888 (scaled) Checksum: 0xbc54 (correct) Time stamp: tsval , tsecr This is an ACK to the segment in frame: 12 The RTT to ACK the segment was: seconds 0000 fe fd c0 a f3 a8 0a 8a E be 3c b9 5e c0 a8 01 1c cd 9c.4.<@.@..^ c8 d6 9c c8 e7 ac fd 6c d P8...l e bc a 00 0b 59 aa 45 bf...t...y.e f ba..
4 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page HTTP GET /pub/data/ observations/metar/stations/edny.txt HTTP/1.1 Frame 14 (448 bytes on wire, 448 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 14 Packet Length: 448 bytes Capture Length: 448 bytes :http Ethernet II, Src: 00:18:f3:a8:0a:8a, Dst: fe:fd:c0:a8:01:01 Destination: fe:fd:c0:a8:01:01 ( ) Source: 00:18:f3:a8:0a:8a ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 434 Identification: 0xbe3d (48701) Flags: 0x04 (Don t Fragment).1.. = Don t fragment: Set Time to live: 64 Header checksum: 0xb7df (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: (54940), Dst Port: www (80), Seq: 1, Ack : 1, Len: 382 Source port: (54940) Destination port: www (80) Sequence number: 1 (relative sequence number) Next sequence number: 383 (relative sequence number) Acknowledgement number: 1 (relative ack number) Flags: 0x0018 (PSH, ACK) = Push: Set Window size: 5888 (scaled) Checksum: 0x468b (correct) Time stamp: tsval , tsecr Hypertext Transfer Protocol GET /pub/data/observations/metar/stations/edny.txt HTTP/1.1\r\n Request Method: GET Request URI: /pub/data/observations/metar/stations/edny.txt Request Version: HTTP/1.1 User-Agent: Mozilla/5.0 (compatible; Konqueror/3.5; Linux) KHTML/3.5.5 (like Gecko) (De bian)\r\n Pragma: no-cache\r\n Cache-control: no-cache\r\n Accept: text/html, image/jpeg, image/png, text/*, image/*, */*\r\n Accept-Charset: utf-8, utf-8;q=0.5, *;q=0.5\r\n Accept-Language: de, en\r\n Host: weather.noaa.gov\r\n Connection: Keep-Alive\r\n \r\n
5 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page fe fd c0 a f3 a8 0a 8a E b2 be 3d b7 df c0 a8 01 1c cd 9c...=@.@ c8 d6 9c c8 e7 ac fd 6c d P8...l e 46 8b a 00 0b 59 aa 45 bf..f...y.e f ba f f f..GET /pub/data/ f f 6e 73 2f 6d observations/met f f 6e 73 2f e 59 ar/stations/edny e f 31 2e 31 0d 0a 55.TXT HTTP/1.1..U d e 74 3a 20 4d 6f 7a 69 6c ser-agent: Mozil c 61 2f 35 2e f 6d la/5.0 (compatib 00a0 6c 65 3b 20 4b 6f 6e f 72 2f 33 2e le; Konqueror/3. 00b0 35 3b 20 4c 69 6e b d 4c 2f 5; Linux) KHTML/ 00c0 33 2e 35 2e c 69 6b b (like Geck 00d0 6f e 29 0d 0a o) (Debian)..Pra 00e0 67 6d 61 3a 20 6e 6f 2d d 0a 43 gma: no-cache..c 00f d 63 6f 6e f 6c 3a 20 6e 6f ache-control: no d d 0a a 20 -cache..accept: f d 6c 2c d text/html, image f 6a c d f 70 6e 67 /jpeg, image/png c f 2a 2c d f, text/*, image/ a 2c 20 2a 2f 2a 0d 0a d 43 *, */*..Accept-C a d 38 2c harset: utf-8, u d 38 3b 71 3d 30 2e 35 2c 20 2a 3b 71 3d tf-8;q=0.5, *;q= e 35 0d 0a d 4c 61 6e Accept-Lang a c e 0d 0a 48 6f uage: de, en..ho a e 6e 6f st: weather.noaa 01a0 2e 67 6f 76 0d 0a 43 6f 6e 6e f 6e.gov..Connection 01b0 3a 20 4b d 41 6c d 0a 0d 0a : Keep-Alive...
6 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page HTTP HTTP/ O K (text/plain) Frame 15 (416 bytes on wire, 416 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 15 Packet Length: 416 bytes Capture Length: 416 bytes : Ethernet II, Src: fe:fd:c0:a8:01:01, Dst: 00:18:f3:a8:0a:8a Destination: 00:18:f3:a8:0a:8a ( ) Source: fe:fd:c0:a8:01:01 ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 402 Identification: 0x7b08 (31496) Flags: 0x = Don t fragment: Not set Time to live: 43 Header checksum: 0x5035 (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: www (80), Dst Port: (54940), Seq: 1, Ack : 383, Len: 350 Source port: www (80) Destination port: (54940) Sequence number: 1 (relative sequence number) Next sequence number: 351 (relative sequence number) Acknowledgement number: 383 (relative ack number) Flags: 0x0018 (PSH, ACK) = Push: Set Window size: Checksum: 0x01a0 (correct) Time stamp: tsval , tsecr This is an ACK to the segment in frame: 14 The RTT to ACK the segment was: seconds Hypertext Transfer Protocol HTTP/ OK\r\n Request Version: HTTP/1.1 Response Code: 200 Date: Sun, 21 Jan :24:00 GMT\r\n Server: Apache/ (Unix) mod_perl/1.27\r\n Last-Modified: Sun, 21 Jan :12:46 GMT\r\n ETag: "1ae b34aae"\r\n Accept-Ranges: bytes\r\n Content-Length: 88\r\n Connection: close\r\n Content-Type: text/plain\r\n \r\n
7 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page 7 Line-based text data: text/plain 2007/01/21 10:50 EDNY Z 25021KT 230V FEW025 BKN070 07/01 Q1019 RMK ATIS H f3 a8 0a 8a fe fd c0 a E b b cd 9c 33 c8 c0 a8..{...+.p c d6 9c fd 6c d c8 e9 2a P...l..8..* ff dc 01 a a 45 bf 8f ba 00 0b...E aa f 31 2e f Y.HTTP/ O b 0d 0a a e 2c K..Date: Sun, a 61 6e a a Jan :24: d 54 0d 0a a GMT..Server: f 31 2e 33 2e Apache/ (U e d 6f 64 5f c 2f 31 2e nix) mod_perl/1. 00a d 0a 4c d 4d 6f Last-Modifie 00b0 64 3a e 2c a 61 6e d: Sun, 21 Jan 2 00c a a d :12:46 GMT 00d0 0d 0a a ETag: "1ae e0 2d d d 0a b34aae"..A 00f d e a ccept-ranges: by d 0a 43 6f 6e e 74 2d 4c 65 6e tes..content-len a d 0a 43 6f 6e 6e gth: 88..Connect f 6e 3a c 6f d 0a 43 6f 6e 74 ion: close..cont e 74 2d a f 70 ent-type: text/p c e 0d 0a 0d 0a f f lain /01/ a a e :50.EDNY a b Z 25021KT V FEW b 4e f BKN070 07/01 Q d 4b a 1019 RMK ATIS H.
8 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP > www [A CK] Seq=383 Ack=351 Win=6912 Len=0 TSV= TSER= Frame 16 (66 bytes on wire, 66 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 16 Packet Length: 66 bytes Capture Length: 66 bytes Ethernet II, Src: 00:18:f3:a8:0a:8a, Dst: fe:fd:c0:a8:01:01 Destination: fe:fd:c0:a8:01:01 ( ) Source: 00:18:f3:a8:0a:8a ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 52 Identification: 0xbe3e (48702) Flags: 0x04 (Don t Fragment).1.. = Don t fragment: Set Time to live: 64 Header checksum: 0xb95c (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: (54940), Dst Port: www (80), Seq: 383, A ck: 351, Len: 0 Source port: (54940) Destination port: www (80) Sequence number: 383 (relative sequence number) Acknowledgement number: 351 (relative ack number) Flags: 0x0010 (ACK) Window size: 6912 (scaled) Checksum: 0xb953 (correct) Time stamp: tsval , tsecr This is an ACK to the segment in frame: 15 The RTT to ACK the segment was: seconds 0000 fe fd c0 a f3 a8 0a 8a E be 3e b9 5c c0 a8 01 1c cd 9c.4.>@.@..\ c8 d6 9c c8 e9 2a fd 6c d P8..*.l.q b a 00 0b 59 c7 45 bf.6.s...y.e f ba..
9 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP www > [F IN, ACK] Seq=351 Ack=383 Win=65500 Len=0 TSV= TSER= Frame 17 (66 bytes on wire, 66 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 17 Packet Length: 66 bytes Capture Length: 66 bytes Ethernet II, Src: fe:fd:c0:a8:01:01, Dst: 00:18:f3:a8:0a:8a Destination: 00:18:f3:a8:0a:8a ( ) Source: fe:fd:c0:a8:01:01 ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 52 Identification: 0x7b0b (31499) Flags: 0x = Don t fragment: Not set Time to live: 43 Header checksum: 0x5190 (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: www (80), Dst Port: (54940), Seq: 351, A ck: 383, Len: 0 Source port: www (80) Destination port: (54940) Sequence number: 351 (relative sequence number) Acknowledgement number: 383 (relative ack number) Flags: 0x0011 (FIN, ACK) = Fin: Set Window size: Checksum: 0xb9c8 (correct) Time stamp: tsval , tsecr f3 a8 0a 8a fe fd c0 a E b 0b b cd 9c 33 c8 c0 a8.4{...+.q c d6 9c fd 6c d c8 e9 2a P...l.q8..* ff dc b9 c a 45 bf 8f ba 00 0b...E aa Y.
10 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP > www [F IN, ACK] Seq=383 Ack=352 Win=6912 Len=0 TSV= TSER= Frame 18 (66 bytes on wire, 66 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 18 Packet Length: 66 bytes Capture Length: 66 bytes Ethernet II, Src: 00:18:f3:a8:0a:8a, Dst: fe:fd:c0:a8:01:01 Destination: fe:fd:c0:a8:01:01 ( ) Source: 00:18:f3:a8:0a:8a ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 52 Identification: 0xbe3f (48703) Flags: 0x04 (Don t Fragment).1.. = Don t fragment: Set Time to live: 64 Header checksum: 0xb95b (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: (54940), Dst Port: www (80), Seq: 383, A ck: 352, Len: 0 Source port: (54940) Destination port: www (80) Sequence number: 383 (relative sequence number) Acknowledgement number: 352 (relative ack number) Flags: 0x0011 (FIN, ACK) = Fin: Set Window size: 6912 (scaled) Checksum: 0xb950 (correct) Time stamp: tsval , tsecr This is an ACK to the segment in frame: 17 The RTT to ACK the segment was: seconds 0000 fe fd c0 a f3 a8 0a 8a E be 3f b9 5b c0 a8 01 1c cd 9c.4.?@.@..[ c8 d6 9c c8 e9 2a fd 6c d P8..*.l.r b a 00 0b 59 c8 45 bf.6.p...y.e f ba..
11 /tmp/dump/dump02_arp_dns-weather_syn_fin complete-session - Ethereal Page TCP www > [A CK] Seq=352 Ack=384 Win=65500 Len=0 TSV= TSER= Frame 19 (66 bytes on wire, 66 bytes captured) Arrival Time: Jan 21, :24: Time delta from previous packet: seconds Time since reference or first frame: seconds Frame Number: 19 Packet Length: 66 bytes Capture Length: 66 bytes Ethernet II, Src: fe:fd:c0:a8:01:01, Dst: 00:18:f3:a8:0a:8a Destination: 00:18:f3:a8:0a:8a ( ) Source: fe:fd:c0:a8:01:01 ( ) Internet Protocol, Src Addr: ( ), Dst Addr: ( ) Total Length: 52 Identification: 0x7bb7 (31671) Flags: 0x = Don t fragment: Not set Time to live: 43 Header checksum: 0x50e4 (correct) Source: ( ) Destination: ( ) Transmission Control Protocol, Src Port: www (80), Dst Port: (54940), Seq: 352, A ck: 384, Len: 0 Source port: www (80) Destination port: (54940) Sequence number: 352 (relative sequence number) Acknowledgement number: 384 (relative ack number) Flags: 0x0010 (ACK) Window size: Checksum: 0xb9a8 (correct) Time stamp: tsval , tsecr This is an ACK to the segment in frame: 18 The RTT to ACK the segment was: seconds f3 a8 0a 8a fe fd c0 a E b b b e4 cd 9c 33 c8 c0 a8.4{...+.p c d6 9c fd 6c d c8 e9 2b P...l.r ff dc b9 a a 45 bf 8f bb 00 0b...E c8 Y.
Sirindhorn International Institute of Technology Thammasat University
 1 Name...ID....Section. Seat No.. Sirindhorn International Institute of Technology Thammasat University Midterm Examination: Semester 2/2007 Course Title : ITS 332 Information Technology II Lab (Networking)
1 Name...ID....Section. Seat No.. Sirindhorn International Institute of Technology Thammasat University Midterm Examination: Semester 2/2007 Course Title : ITS 332 Information Technology II Lab (Networking)
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
CIS-331 Exam 2 Spring 2016 Total of 110 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 121.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 8,100 subnets? b. (5 Points) What is
Muhammad Farooq-i-Azam CHASE-2006 Lahore
 Muhammad Farooq-i-Azam CHASE-2006 Lahore Overview Theory Existing Sniffers in action Switched Environment ARP Protocol and Exploitation Develop it yourself 2 Network Traffic Computers and network devices
Muhammad Farooq-i-Azam CHASE-2006 Lahore Overview Theory Existing Sniffers in action Switched Environment ARP Protocol and Exploitation Develop it yourself 2 Network Traffic Computers and network devices
CIS-331 Fall 2014 Exam 1 Name: Total of 109 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
CIS-331 Exam 2 Fall 2014 Total of 105 Points. Version 1
 Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
Version 1 1. (20 Points) Given the class A network address 119.0.0.0 will be divided into a maximum of 15,900 subnets. a. (5 Points) How many bits will be necessary to address the 15,900 subnets? b. (5
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Wire Shark Lab1. Intro
 Jae Sook Lee FA16 CSIT 340 01 Dr. Constantine Coutras Wire Shark Lab1 Intro 1. List 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above. : 1)
Jae Sook Lee FA16 CSIT 340 01 Dr. Constantine Coutras Wire Shark Lab1 Intro 1. List 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above. : 1)
CIS-331 Final Exam Spring 2018 Total of 120 Points. Version 1
 Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
! ' ,-. +) +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+, ) 05,-. /,*+), 01/-*+) + 01/.*+)
 ! "#! # $ %& #! '!!!( &!)'*+' '(,-. +) /,*+), 01/-*+) + 01/.*+) ) 05,-. +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+,3 4 +. 6*! ) ) ) ) 5 ) ) ) ) + 5 + + ) ) ) 5 9 + ) ) + 5 4 ) ) + ) 5, ) )
! "#! # $ %& #! '!!!( &!)'*+' '(,-. +) /,*+), 01/-*+) + 01/.*+) ) 05,-. +))+, /+*, 2 01/)*,, 01/)*, + 01/+*, ) 054 +) +++++))+,3 4 +. 6*! ) ) ) ) 5 ) ) ) ) + 5 + + ) ) ) 5 9 + ) ) + 5 4 ) ) + ) 5, ) )
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
The key networking element that are typically used in an analysis of network traffic are:
 9 Network Forensics 8 On-line lecture: http://asecuritysite.com/subjects/chapter09 9.1 Objectives The key objectives of this unit are to: Understand some of the methodologies used in network forensics.
9 Network Forensics 8 On-line lecture: http://asecuritysite.com/subjects/chapter09 9.1 Objectives The key objectives of this unit are to: Understand some of the methodologies used in network forensics.
CS 43: Computer Networks. HTTP September 10, 2018
 CS 43: Computer Networks HTTP September 10, 2018 Reading Quiz Lecture 4 - Slide 2 Five-layer protocol stack HTTP Request message Headers protocol delineators Last class Lecture 4 - Slide 3 HTTP GET vs.
CS 43: Computer Networks HTTP September 10, 2018 Reading Quiz Lecture 4 - Slide 2 Five-layer protocol stack HTTP Request message Headers protocol delineators Last class Lecture 4 - Slide 3 HTTP GET vs.
CS 43: Computer Networks. Layering & HTTP September 7, 2018
 CS 43: Computer Networks Layering & HTTP September 7, 2018 Last Class: Five-layer Internet Model Application: the application (e.g., the Web, Email) Transport: end-to-end connections, reliability Network:
CS 43: Computer Networks Layering & HTTP September 7, 2018 Last Class: Five-layer Internet Model Application: the application (e.g., the Web, Email) Transport: end-to-end connections, reliability Network:
CIS-331 Final Exam Spring 2015 Total of 115 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
CIS-331 Final Exam Fall 2015 Total of 120 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Internetworking models
 TEL3214 Computer Communication s Lecture 2 Internetworking models SSH (Secure Shell) SNMP (Simple Management Protocol) SMTP (Simple Mail Transfer Protocol) FTP (File Transfer Protocol) TFTP (Trivial File
TEL3214 Computer Communication s Lecture 2 Internetworking models SSH (Secure Shell) SNMP (Simple Management Protocol) SMTP (Simple Mail Transfer Protocol) FTP (File Transfer Protocol) TFTP (Trivial File
TCP/IP Networking Basics
 TCP/IP Networking Basics 1 A simple TCP/IP Example A user on host argon.tcpip-lab.edu ( Argon ) makes a web access to URL http://neon.tcpip-lab.edu/index.html. What actually happens in the network? 2 HTTP
TCP/IP Networking Basics 1 A simple TCP/IP Example A user on host argon.tcpip-lab.edu ( Argon ) makes a web access to URL http://neon.tcpip-lab.edu/index.html. What actually happens in the network? 2 HTTP
CIS-331 Final Exam Spring 2016 Total of 120 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
University of Toronto Faculty of Applied Science and Engineering. Final Exam, December ECE 461: Internetworking Examiner: J.
 University of Toronto Faculty of Applied Science and Engineering Final Exam, December 2010 ECE 461: Internetworking Examiner: J. Liebeherr Exam Type: B Calculator: Type 2 There are a total of 10 problems.
University of Toronto Faculty of Applied Science and Engineering Final Exam, December 2010 ECE 461: Internetworking Examiner: J. Liebeherr Exam Type: B Calculator: Type 2 There are a total of 10 problems.
DATA COMMUNICATOIN NETWORKING
 DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach By: Kurose, Ross Introduction Course Overview Basics of Computer Networks Internet
DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach By: Kurose, Ross Introduction Course Overview Basics of Computer Networks Internet
ID: Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version:
 ID: 59176 Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
ID: 59176 Cookbook: browseurl.jbs Time: 19:37:50 Date: 11/05/2018 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Analysis
How the Internet Works
 How the Internet Works Contents World Wide Web, which is made of HTML and HTTP and communicates over TCP/IP, which uses Ethernet and other network media. Supported by routing and DNS 2 WWW Page 3 HTML
How the Internet Works Contents World Wide Web, which is made of HTML and HTTP and communicates over TCP/IP, which uses Ethernet and other network media. Supported by routing and DNS 2 WWW Page 3 HTML
The cache is 4-way set associative, with 4-byte blocks, and 16 total lines
 Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
App. App. Master Informatique 1 st year 1 st term. ARes/ComNet Applications (7 points) Anonymous ID: stick number HERE
 Master Informatique 1 st year 1 st term Anonymous ID: stick number HERE Master Informatique 1 st year 1 st term App ARes/ComNet 2015-2016 Midterm exam : Version A in English Duration: 2h00 Allowed: One
Master Informatique 1 st year 1 st term Anonymous ID: stick number HERE Master Informatique 1 st year 1 st term App ARes/ComNet 2015-2016 Midterm exam : Version A in English Duration: 2h00 Allowed: One
Technical Specification. Third Party Control Protocol. AV Revolution
 Technical Specification Third Party Control Protocol AV Revolution Document AM-TS-120308 Version 1.0 Page 1 of 31 DOCUMENT DETAILS Document Title: Technical Specification, Third Party Control Protocol,
Technical Specification Third Party Control Protocol AV Revolution Document AM-TS-120308 Version 1.0 Page 1 of 31 DOCUMENT DETAILS Document Title: Technical Specification, Third Party Control Protocol,
Introduction to TCP/IP networking
 Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
EE 610 Part 2: Encapsulation and network utilities
 EE 610 Part 2: Encapsulation and network utilities Objective: After this experiment, the students should be able to: i. Understand the format of standard frames and packet headers. Overview: The Open Systems
EE 610 Part 2: Encapsulation and network utilities Objective: After this experiment, the students should be able to: i. Understand the format of standard frames and packet headers. Overview: The Open Systems
Information Network 1 TCP 1/2. Youki Kadobayashi NAIST
 Information Network 1 TCP 1/2 Youki Kadobayashi NAIST 1 Transport layer: a birds-eye view Hosts maintain state for each transport-layer endpoint Routers don t maintain per-host state H R R R R H Transport
Information Network 1 TCP 1/2 Youki Kadobayashi NAIST 1 Transport layer: a birds-eye view Hosts maintain state for each transport-layer endpoint Routers don t maintain per-host state H R R R R H Transport
C1098 JPEG Module User Manual
 C1098 JPEG Module User Manual General Description C1098 is VGA camera module performs as a JPEG compressed still camera that can be attached to a wireless or PDA host. Users can send out a snapshot command
C1098 JPEG Module User Manual General Description C1098 is VGA camera module performs as a JPEG compressed still camera that can be attached to a wireless or PDA host. Users can send out a snapshot command
CSCI-GA Operating Systems. Networking. Hubertus Franke
 CSCI-GA.2250-001 Operating Systems Networking Hubertus Franke frankeh@cs.nyu.edu Source: Ganesh Sittampalam NYU TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute
CSCI-GA.2250-001 Operating Systems Networking Hubertus Franke frankeh@cs.nyu.edu Source: Ganesh Sittampalam NYU TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute
ID: Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/2018 Version:
 ID: 42417 Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
ID: 42417 Cookbook: urldownload.jbs Time: 23:23:00 Date: 11/01/201 Version: 20.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence Classification Signature
TLS 1.2 Protocol Execution Transcript
 Appendix C TLS 1.2 Protocol Execution Transcript In Section 2.3, we overviewed a relatively simple protocol execution transcript for SSL 3.0. In this appendix, we do something similar for TLS 1.2. Since
Appendix C TLS 1.2 Protocol Execution Transcript In Section 2.3, we overviewed a relatively simple protocol execution transcript for SSL 3.0. In this appendix, we do something similar for TLS 1.2. Since
Module : ServerIron ADX Packet Capture
 Module : ServerIron ADX Packet Capture Objectives Upon completion of this module, you will be able to: Describe Brocade ServerIron ADX (ADX) Packet Capture feature Configure and verify the Packet Capture
Module : ServerIron ADX Packet Capture Objectives Upon completion of this module, you will be able to: Describe Brocade ServerIron ADX (ADX) Packet Capture feature Configure and verify the Packet Capture
Introduction to Internet. Ass. Prof. J.Y. Tigli University of Nice Sophia Antipolis
 Introduction to Internet Ass. Prof. J.Y. Tigli University of Nice Sophia Antipolis What about inter-networks communications? Between LANs? Ethernet?? Ethernet Example Similarities and Differences between
Introduction to Internet Ass. Prof. J.Y. Tigli University of Nice Sophia Antipolis What about inter-networks communications? Between LANs? Ethernet?? Ethernet Example Similarities and Differences between
CCNA 1 Chapter 7 v5.0 Exam Answers 2013
 CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
Troubleshooting Communication in WebSphere MQ
 IBM Software Group Troubleshooting Communication in WebSphere MQ Rick Armstrong (rickied@us.ibm.com) Advisory Software Engineer 27 October 2010 WebSphere Support Technical Exchange Agenda TCP/IP networking
IBM Software Group Troubleshooting Communication in WebSphere MQ Rick Armstrong (rickied@us.ibm.com) Advisory Software Engineer 27 October 2010 WebSphere Support Technical Exchange Agenda TCP/IP networking
Sirindhorn International Institute of Technology Thammasat University
 Name...ID... Section...Seat No... Sirindhorn International Institute of Technology Thammasat University Midterm Examination s: Semester 2/2009 Course Title Instructor : ITS332 Information Technology II
Name...ID... Section...Seat No... Sirindhorn International Institute of Technology Thammasat University Midterm Examination s: Semester 2/2009 Course Title Instructor : ITS332 Information Technology II
Application Layer: The Web and HTTP Sec 2.2 Prof Lina Battestilli Fall 2017
 CSC 401 Data and Computer Communications Networks Application Layer: The Web and HTTP Sec 2.2 Prof Lina Battestilli Fall 2017 Outline Application Layer (ch 2) 2.1 principles of network applications 2.2
CSC 401 Data and Computer Communications Networks Application Layer: The Web and HTTP Sec 2.2 Prof Lina Battestilli Fall 2017 Outline Application Layer (ch 2) 2.1 principles of network applications 2.2
HTTP TRAFFIC CONSISTS OF REQUESTS AND RESPONSES. All HTTP traffic can be
 3 HTTP Transactions HTTP TRAFFIC CONSISTS OF REQUESTS AND RESPONSES. All HTTP traffic can be associated with the task of requesting content or responding to those requests. Every HTTP message sent from
3 HTTP Transactions HTTP TRAFFIC CONSISTS OF REQUESTS AND RESPONSES. All HTTP traffic can be associated with the task of requesting content or responding to those requests. Every HTTP message sent from
Packet Header Formats
 A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
A P P E N D I X C Packet Header Formats S nort rules use the protocol type field to distinguish among different protocols. Different header parts in packets are used to determine the type of protocol used
The HTTP protocol. Fulvio Corno, Dario Bonino. 08/10/09 http 1
 The HTTP protocol Fulvio Corno, Dario Bonino 08/10/09 http 1 What is HTTP? HTTP stands for Hypertext Transfer Protocol It is the network protocol used to delivery virtually all data over the WWW: Images
The HTTP protocol Fulvio Corno, Dario Bonino 08/10/09 http 1 What is HTTP? HTTP stands for Hypertext Transfer Protocol It is the network protocol used to delivery virtually all data over the WWW: Images
Fall 2003 Wincati Issue
 Fall 2003 Wincati Issues SUMMARY...2 OVERVIEW...2 HISTORY...2 TECHNICAL DETAILS...2 ANALYSIS...3 DATA-GATHERING...3 RESULTS...3 Wincati...3 Efi Fiery Server ZX...3 WHAT REMAINS...3 LESSONS LEARNED...3
Fall 2003 Wincati Issues SUMMARY...2 OVERVIEW...2 HISTORY...2 TECHNICAL DETAILS...2 ANALYSIS...3 DATA-GATHERING...3 RESULTS...3 Wincati...3 Efi Fiery Server ZX...3 WHAT REMAINS...3 LESSONS LEARNED...3
The Transport Layer. Internet solutions. Nixu Oy PL 21. (Mäkelänkatu 91) Helsinki, Finland. tel fax.
 The Transport Layer Nixu Oy PL 21 (Mäkelänkatu 91) 00601 Helsinki, Finland tel. +358 9 478 1011 fax. +358 9 478 1030 info@nixu.fi http://www.nixu.fi OVERVIEW User Datagram Protocol Transmission Control
The Transport Layer Nixu Oy PL 21 (Mäkelänkatu 91) 00601 Helsinki, Finland tel. +358 9 478 1011 fax. +358 9 478 1030 info@nixu.fi http://www.nixu.fi OVERVIEW User Datagram Protocol Transmission Control
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1
 CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
CS 537: Introduction to Operating Systems Fall 2015: Midterm Exam #1 This exam is closed book, closed notes. All cell phones must be turned off. No calculators may be used. You have two hours to complete
Computer Networks. Transmission Control Protocol. Jianping Pan Spring /3/17 CSC361 1
 Computer Networks Transmission Control Protocol Jianping Pan Spring 2017 2/3/17 CSC361 1 https://connex.csc.uvic.ca/portal NSERC USRA awards available at UVic CSc for 2017/18 2/3/17 CSC361 2 TCP Transmission
Computer Networks Transmission Control Protocol Jianping Pan Spring 2017 2/3/17 CSC361 1 https://connex.csc.uvic.ca/portal NSERC USRA awards available at UVic CSc for 2017/18 2/3/17 CSC361 2 TCP Transmission
Networking Technologies and Applications
 Networking Technologies and Applications Rolland Vida BME TMIT Transport Protocols UDP User Datagram Protocol TCP Transport Control Protocol and many others UDP One of the core transport protocols Used
Networking Technologies and Applications Rolland Vida BME TMIT Transport Protocols UDP User Datagram Protocol TCP Transport Control Protocol and many others UDP One of the core transport protocols Used
Transmission Control Protocol (TCP)
 Transmission Control Protocol (TCP) Antonio Carzaniga Faculty of Informatics University of Lugano May 3, 2005 Outline Intro to TCP Sequence numbers and acknowledgment numbers Timeouts and RTT estimation
Transmission Control Protocol (TCP) Antonio Carzaniga Faculty of Informatics University of Lugano May 3, 2005 Outline Intro to TCP Sequence numbers and acknowledgment numbers Timeouts and RTT estimation
Computer Networks Principles
 Computer Networks Principles Introduction Prof. Andrzej Duda duda@imag.fr http://duda.imag.fr 1 Contents Introduction protocols and layered architecture encapsulation interconnection structures performance
Computer Networks Principles Introduction Prof. Andrzej Duda duda@imag.fr http://duda.imag.fr 1 Contents Introduction protocols and layered architecture encapsulation interconnection structures performance
Network Interconnection
 Network Interconnection Covers different approaches for ensuring border or perimeter security Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Lecture
Network Interconnection Covers different approaches for ensuring border or perimeter security Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Lecture
4. Specifications and Additional Information
 4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
NYC Utility DAS SCADA Network General Protocol and Traffic Analysis September 2005 Applied Methodologies, Inc.
 NYC Utility DAS SCADA Network General Protocol and Traffic Analysis September 2005 Applied Methodologies, Inc. Table of Contents INTRODUCTION...3 BEHAVIOR OBSERVED...4 OTHER GENERAL OBSERVATIONS ABOUT
NYC Utility DAS SCADA Network General Protocol and Traffic Analysis September 2005 Applied Methodologies, Inc. Table of Contents INTRODUCTION...3 BEHAVIOR OBSERVED...4 OTHER GENERAL OBSERVATIONS ABOUT
Chapter 2: outline. 2.6 P2P applications 2.7 socket programming with UDP and TCP
 Chapter 2: outline 2.1 principles of network applications app architectures app requirements 2.2 Web and HTTP 2.3 FTP 2.4 electronic mail SMTP, POP3, IMAP 2.5 DNS 2.6 P2P applications 2.7 socket programming
Chapter 2: outline 2.1 principles of network applications app architectures app requirements 2.2 Web and HTTP 2.3 FTP 2.4 electronic mail SMTP, POP3, IMAP 2.5 DNS 2.6 P2P applications 2.7 socket programming
Transparent TCP Timestamps draft-scheffenegger-tcpm-timestampnegotiation-03
 Transparent TCP Timestamps draft-scheffenegger-tcpm-timestampnegotiation-03 Richard Scheffenegger [rs@netapp.com] Mirja Kühlewind [mirja.kuehlewind@ikr.uni-stuttgart.de] 16. November 2011 82nd IETF, Taipei,
Transparent TCP Timestamps draft-scheffenegger-tcpm-timestampnegotiation-03 Richard Scheffenegger [rs@netapp.com] Mirja Kühlewind [mirja.kuehlewind@ikr.uni-stuttgart.de] 16. November 2011 82nd IETF, Taipei,
I TCP 1/2. Internet TA: Connection-oriented (virtual circuit) Connectionless (datagram) (flow control) (congestion control) TCP Connection-oriented
 I TCP 1/2 TA: Connection-oriented (virtual circuit) Connectionless (datagram) (flow control) (congestion control) Internet TCP Connection-oriented UDP Connectionless IP + TCP (connection-oriented) (byte
I TCP 1/2 TA: Connection-oriented (virtual circuit) Connectionless (datagram) (flow control) (congestion control) Internet TCP Connection-oriented UDP Connectionless IP + TCP (connection-oriented) (byte
Homework 2 50 points. CSE422 Computer Networking Spring 2018
 Homework 2 50 points ATM Application-Level Protocol (10 points) Design and describe an application-level protocol to be used between an automatic teller machine and a bank s centralized computer. Your
Homework 2 50 points ATM Application-Level Protocol (10 points) Design and describe an application-level protocol to be used between an automatic teller machine and a bank s centralized computer. Your
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers
 A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers Objectives The main objective of this assignment is to gain a deeper understanding of network activities and network packet formats using
A Simple Network Analyzer Decoding TCP, UDP, DNS and DHCP headers Objectives The main objective of this assignment is to gain a deeper understanding of network activities and network packet formats using
The Transport Layer. Part 1
 The Transport Layer Part 1 2 OVERVIEW Part 1 User Datagram Protocol Transmission Control Protocol ARQ protocols Part 2 TCP congestion control Mowgli XTP SCTP WAP 3 Transport Layer Protocols Connect applications
The Transport Layer Part 1 2 OVERVIEW Part 1 User Datagram Protocol Transmission Control Protocol ARQ protocols Part 2 TCP congestion control Mowgli XTP SCTP WAP 3 Transport Layer Protocols Connect applications
ECE 358 Project 3 Encapsulation and Network Utilities
 ECE 358 Project 3 Encapsulation and Network Utilities Objective: After this project, students are expected to: i. Understand the format of standard frames and packet headers. ii. Use basic network utilities
ECE 358 Project 3 Encapsulation and Network Utilities Objective: After this project, students are expected to: i. Understand the format of standard frames and packet headers. ii. Use basic network utilities
3. Provide the routing table of host H located in LAN E, assuming that the host s network interface is called i1. ARes/ComNet
 Anonymous number: 3 Provide the routing table of host H located in LAN E, assuming that the host s network interface is called i1 AResComNet 20172018 Rou destination Final exam : Version A in English Rou
Anonymous number: 3 Provide the routing table of host H located in LAN E, assuming that the host s network interface is called i1 AResComNet 20172018 Rou destination Final exam : Version A in English Rou
CSC358 Week 2. Adapted from slides by J.F. Kurose and K. W. Ross. All material copyright J.F Kurose and K.W. Ross, All Rights Reserved
 CSC358 Week 2 Adapted from slides by J.F. Kurose and K. W. Ross. All material copyright 1996-2016 J.F Kurose and K.W. Ross, All Rights Reserved Logistics Tutorial this Friday Assignment 1 will be out shortly
CSC358 Week 2 Adapted from slides by J.F. Kurose and K. W. Ross. All material copyright 1996-2016 J.F Kurose and K.W. Ross, All Rights Reserved Logistics Tutorial this Friday Assignment 1 will be out shortly
Trp. Trp. Master Informatique 1 st year 1 st term. ARes/ComNet Transport layer (7 points) Anonymous ID: stick number HERE
 Master Informatique 1 st year 1 st term Anonymous ID: stick number HERE Master Informatique 1 st year 1 st term App ARes/ComNet 2015-2016 Midterm exam : Version A in English Duration: 2h00 Allowed: One
Master Informatique 1 st year 1 st term Anonymous ID: stick number HERE Master Informatique 1 st year 1 st term App ARes/ComNet 2015-2016 Midterm exam : Version A in English Duration: 2h00 Allowed: One
Chapter 2 Application Layer
 Chapter 2 Application Layer Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Application Layer 2-1 Some network apps e-mail web text messaging remote
Chapter 2 Application Layer Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Application Layer 2-1 Some network apps e-mail web text messaging remote
HyperText Transfer Protocol
 Outline Introduce Socket Programming Domain Name Service (DNS) Standard Application-level Protocols email (SMTP) HTTP HyperText Transfer Protocol Defintitions A web page consists of a base HTML-file which
Outline Introduce Socket Programming Domain Name Service (DNS) Standard Application-level Protocols email (SMTP) HTTP HyperText Transfer Protocol Defintitions A web page consists of a base HTML-file which
Transport Layer Review
 Transport Layer Review Mahalingam Mississippi State University, MS October 1, 2014 Transport Layer Functions Distinguish between different application instances through port numbers Make it easy for applications
Transport Layer Review Mahalingam Mississippi State University, MS October 1, 2014 Transport Layer Functions Distinguish between different application instances through port numbers Make it easy for applications
Lecture 04: Application Layer (Part 01) Principles and the World Wide Web (HTTP) Dr. Anis Koubaa
 NET 331 Computer Networks Lecture 04: Application Layer (Part 01) Principles and the World Wide Web (HTTP) Dr. Anis Koubaa Reformatted slides from textbook Computer Networking a top-down appraoch, Fifth
NET 331 Computer Networks Lecture 04: Application Layer (Part 01) Principles and the World Wide Web (HTTP) Dr. Anis Koubaa Reformatted slides from textbook Computer Networking a top-down appraoch, Fifth
UNH-IOL MIPI Alliance Test Program
 DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
Applications & Application-Layer Protocols: The Web & HTTP
 CPSC 360 Network Programming Applications & Application-Layer Protocols: The Web & HTTP Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu http://www.cs.clemson.edu/~mweigle/courses/cpsc360
CPSC 360 Network Programming Applications & Application-Layer Protocols: The Web & HTTP Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu http://www.cs.clemson.edu/~mweigle/courses/cpsc360
TCP/IP Networking An Example
 TCP/IP Networking An Example Complexity of networking: an example Review: Layered communication architecture The TCP/IP protocol suite Jörg Liebeherr, 1998,1999 1 A simple TCP/IP Example A user at Cerf
TCP/IP Networking An Example Complexity of networking: an example Review: Layered communication architecture The TCP/IP protocol suite Jörg Liebeherr, 1998,1999 1 A simple TCP/IP Example A user at Cerf
KNX TinySerial 810. Communication Protocol. WEINZIERL ENGINEERING GmbH
 WEINZIERL ENGINEERING GmbH KNX TinySerial 810 Communication Protocol WEINZIERL ENGINEERING GmbH Bahnhofstr. 6 DE-84558 Tyrlaching GERMAY Tel. +49 8623 / 987 98-03 Fax +49 8623 / 987 98-09 E-Mail: info@weinzierl.de
WEINZIERL ENGINEERING GmbH KNX TinySerial 810 Communication Protocol WEINZIERL ENGINEERING GmbH Bahnhofstr. 6 DE-84558 Tyrlaching GERMAY Tel. +49 8623 / 987 98-03 Fax +49 8623 / 987 98-09 E-Mail: info@weinzierl.de
Identifying Operating System Using Flow-based Traffic Fingerprinting
 Identifying Operating System Using Flow-based Traffic Fingerprinting Tomáš Jirsík, Pavel Čeleda {jirsik celeda}@ics.muni.cz Institute of Computer Science, Masaryk University EUNICE 2014 September, 1. 5.,
Identifying Operating System Using Flow-based Traffic Fingerprinting Tomáš Jirsík, Pavel Čeleda {jirsik celeda}@ics.muni.cz Institute of Computer Science, Masaryk University EUNICE 2014 September, 1. 5.,
Banner Engineering Corp. DXM Controller API. 4/30/ Rev H
 Banner Engineering Corp DXM Controller API 4/30/2018 186221 Rev H Contents Overview... 3 Device-Initiated Protocol... 3 Input Parameters... 4 GET Request... 4 POST Request... 6 Authentication... 7 Messages
Banner Engineering Corp DXM Controller API 4/30/2018 186221 Rev H Contents Overview... 3 Device-Initiated Protocol... 3 Input Parameters... 4 GET Request... 4 POST Request... 6 Authentication... 7 Messages
TCP = Transmission Control Protocol Connection-oriented protocol Provides a reliable unicast end-to-end byte stream over an unreliable internetwork.
 Overview Formats, Data Transfer, etc. Connection Management (modified by Malathi Veeraraghavan) 1 Overview TCP = Transmission Control Protocol Connection-oriented protocol Provides a reliable unicast end-to-end
Overview Formats, Data Transfer, etc. Connection Management (modified by Malathi Veeraraghavan) 1 Overview TCP = Transmission Control Protocol Connection-oriented protocol Provides a reliable unicast end-to-end
Gateway Ascii Command Protocol
 Gateway Ascii Command Protocol Table Of Contents Introduction....2 Ascii Commands.....3 Messages Received From The Gateway....3 Button Down Message.....3 Button Up Message....3 Button Maintain Message....4
Gateway Ascii Command Protocol Table Of Contents Introduction....2 Ascii Commands.....3 Messages Received From The Gateway....3 Button Down Message.....3 Button Up Message....3 Button Maintain Message....4
ECE697AA Lecture 2. Today s lecture
 ECE697AA Lecture 2 Application Layer: HTTP Tilman Wolf Department of Electrical and Computer Engineering 09/04/08 Protocol stack Application layer Client-server architecture Example protocol: HTTP Demo
ECE697AA Lecture 2 Application Layer: HTTP Tilman Wolf Department of Electrical and Computer Engineering 09/04/08 Protocol stack Application layer Client-server architecture Example protocol: HTTP Demo
6. The Transport Layer and protocols
 6. The Transport Layer and protocols 1 Dr.Z.Sun Outline Transport layer services Transmission Control Protocol Connection set-up and tear-down Ports and Well-know-ports Flow control and Congestion control
6. The Transport Layer and protocols 1 Dr.Z.Sun Outline Transport layer services Transmission Control Protocol Connection set-up and tear-down Ports and Well-know-ports Flow control and Congestion control
EECS 3214: Computer Network Protocols and Applications
 EECS 3214: Computer Network Protocols and Applications Suprakash Datta Course page: http://www.eecs.yorku.ca/course/3214 Office: LAS 3043 Email: datta [at] cse.yorku.ca These slides are adapted from Jim
EECS 3214: Computer Network Protocols and Applications Suprakash Datta Course page: http://www.eecs.yorku.ca/course/3214 Office: LAS 3043 Email: datta [at] cse.yorku.ca These slides are adapted from Jim
Produced by. Mobile Application Development. Higher Diploma in Science in Computer Science. Eamonn de Leastar
 Mobile Application Development Higher Diploma in Science in Computer Science Produced by Eamonn de Leastar (edeleastar@wit.ie) Department of Computing, Maths & Physics Waterford Institute of Technology
Mobile Application Development Higher Diploma in Science in Computer Science Produced by Eamonn de Leastar (edeleastar@wit.ie) Department of Computing, Maths & Physics Waterford Institute of Technology
Web, HTTP and Web Caching
 Web, HTTP and Web Caching 1 HTTP overview HTTP: hypertext transfer protocol Web s application layer protocol client/ model client: browser that requests, receives, displays Web objects : Web sends objects
Web, HTTP and Web Caching 1 HTTP overview HTTP: hypertext transfer protocol Web s application layer protocol client/ model client: browser that requests, receives, displays Web objects : Web sends objects
ID: Cookbook: browseurl.jbs Time: 09:46:57 Date: 19/10/2018 Version: Fire Opal
 ID: 85066 Cookbook: browseurl.jbs Time: 09:46:57 Date: 19/10/2018 Version: 24.0.0 Fire Opal Table of Contents Table of Contents Analysis Report http://lux-motors.com/nnngg/nngbbgh/fffee Overview General
ID: 85066 Cookbook: browseurl.jbs Time: 09:46:57 Date: 19/10/2018 Version: 24.0.0 Fire Opal Table of Contents Table of Contents Analysis Report http://lux-motors.com/nnngg/nngbbgh/fffee Overview General
I'IHITIIBIFI UI'IIVERSITY
 I I'IHITIIBIFI UI'IIVERSITY 0F SCIEITCE FII'ID TECHI IOLOGY FACULTY OF COMPUTING AND INFORMATICS DEPARTMENT OF COMPUTER SCIENCE QUALIFICATION: BACHELOR OF COMPUTER SCIENCE, BACHELOR OF INFORMATICS, BACHELOR
I I'IHITIIBIFI UI'IIVERSITY 0F SCIEITCE FII'ID TECHI IOLOGY FACULTY OF COMPUTING AND INFORMATICS DEPARTMENT OF COMPUTER SCIENCE QUALIFICATION: BACHELOR OF COMPUTER SCIENCE, BACHELOR OF INFORMATICS, BACHELOR
Chapter 2 Application Layer
 Chapter 2 Application Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Chapter 2 Application Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
TCPDUMP. Chia-Tien Dan Lo Department of Computer Science and Software Engineering Southern Polytechnic State University
 TCPDUMP Chia-Tien Dan Lo Department of Computer Science and Software Engineering Southern Polytechnic State University PURPOSE Dump the content of a packet Analyze network traffic You have to be root to
TCPDUMP Chia-Tien Dan Lo Department of Computer Science and Software Engineering Southern Polytechnic State University PURPOSE Dump the content of a packet Analyze network traffic You have to be root to
ECE4110 Internetwork Programming. Introduction and Overview
 ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
COSC4377. Chapter 2: Outline
 Lecture 5 Chapter 2: Outline 2.1 principles of network applications app architectures app requirements 2.2 Web and HTTP 2.3 FTP 2.4 electronic mail SMTP, POP3, IMAP 2.5 DNS 2.6 P2P applications 2.7 socket
Lecture 5 Chapter 2: Outline 2.1 principles of network applications app architectures app requirements 2.2 Web and HTTP 2.3 FTP 2.4 electronic mail SMTP, POP3, IMAP 2.5 DNS 2.6 P2P applications 2.7 socket
Network and Security: Introduction
 Network and Security: Introduction Seungwon Shin KAIST Some slides are from Dr. Srinivasan Seshan Some slides are from Dr. Nick Mckeown Network Overview Computer Network Definition A computer network or
Network and Security: Introduction Seungwon Shin KAIST Some slides are from Dr. Srinivasan Seshan Some slides are from Dr. Nick Mckeown Network Overview Computer Network Definition A computer network or
The aim of this unit is to review the main concepts related to TCP and UDP transport protocols, as well as application protocols. These concepts are
 The aim of this unit is to review the main concepts related to TCP and UDP transport protocols, as well as application protocols. These concepts are important requirements for developing programs that
The aim of this unit is to review the main concepts related to TCP and UDP transport protocols, as well as application protocols. These concepts are important requirements for developing programs that
> : S. timestamp > : (0) win <mss 1460,nop,wscale 0,nop,nop, 4 different options used
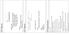 TCP Options Source Port Destination Port Sequence Number Acknowledgment Number HdrLen Reserved UA P RS F Window Size Checksum Urgent Pointer Options (optional...) Header Length Allows size of options to
TCP Options Source Port Destination Port Sequence Number Acknowledgment Number HdrLen Reserved UA P RS F Window Size Checksum Urgent Pointer Options (optional...) Header Length Allows size of options to
Filtering An Introduction
 Filtering An Olivier Paul RST department, TSP Overview. The Level. The Level. The Level. Firewall. Some history: 80s: Intense activity around system security. End of 80s: Security based on formal proofs.
Filtering An Olivier Paul RST department, TSP Overview. The Level. The Level. The Level. Firewall. Some history: 80s: Intense activity around system security. End of 80s: Security based on formal proofs.
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6
 FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
FOCUS on Intrusion Detection: Intrusion Detection Level Analysis of Nmap and Queso Page 1 of 6 Intrusion Detection Level Analysis of Nmap and Queso by Toby Miller last updated Wednesday, August 30, 2000
CPE 448 Exam #2 (50 pts) April Name Class: 448
 Name Class: 448 1) (5 pts) Draw the three way handshake used to establish a TCP connection. Show all SYN and ACK packets. Also show all sequence and acknowledgement numbers associated with the SYN and
Name Class: 448 1) (5 pts) Draw the three way handshake used to establish a TCP connection. Show all SYN and ACK packets. Also show all sequence and acknowledgement numbers associated with the SYN and
EE 122: Transport Protocols. Kevin Lai October 16, 2002
 EE 122: Transport Protocols Kevin Lai October 16, 2002 Motivation IP provides a weak, but efficient service model (best-effort) - packets can be delayed, dropped, reordered, duplicated - packets have limited
EE 122: Transport Protocols Kevin Lai October 16, 2002 Motivation IP provides a weak, but efficient service model (best-effort) - packets can be delayed, dropped, reordered, duplicated - packets have limited
Experiential Learning Workshop on Understanding Network Basics
 Experiential Learning Workshop on Understanding Network Basics June 27, 2018 Dr. Ram P Rustagi Professor, CSE Dept KSIT, Bangalore rprustagi@ksit.edu.in Resources & Acknowledgements Resources https://rprustagi.com/elnt/experiential-
Experiential Learning Workshop on Understanding Network Basics June 27, 2018 Dr. Ram P Rustagi Professor, CSE Dept KSIT, Bangalore rprustagi@ksit.edu.in Resources & Acknowledgements Resources https://rprustagi.com/elnt/experiential-
Chapter 2: outline. 2.6 P2P applications 2.7 socket programming with UDP and TCP
 Chapter 2: outline 2.1 principles of network applications 2.2 Web and HTTP 2.3 FTP 2.4 electronic mail SMTP, POP3, IMAP 2.5 DNS 2.6 P2P applications 2.7 socket programming with UDP and TCP Application
Chapter 2: outline 2.1 principles of network applications 2.2 Web and HTTP 2.3 FTP 2.4 electronic mail SMTP, POP3, IMAP 2.5 DNS 2.6 P2P applications 2.7 socket programming with UDP and TCP Application
Review of Important Networking Concepts. Recall the Example from last lecture
 Review of Important ing Concepts Review: ed communication architecture The TCP/IP protocol suite Jörg Liebeherr, 1998,1999 1 Recall the Example from last lecture Ellington.cs.virginia.edu establishes an
Review of Important ing Concepts Review: ed communication architecture The TCP/IP protocol suite Jörg Liebeherr, 1998,1999 1 Recall the Example from last lecture Ellington.cs.virginia.edu establishes an
Capturing & Analyzing Network Traffic: tcpdump/tshark and Wireshark
 Capturing & Analyzing Network Traffic: tcpdump/tshark and Wireshark EE 122: Intro to Communication Networks Vern Paxson / Jorge Ortiz / Dilip Anthony Joseph 1 Some slides added from Fei Xu's slides, Small
Capturing & Analyzing Network Traffic: tcpdump/tshark and Wireshark EE 122: Intro to Communication Networks Vern Paxson / Jorge Ortiz / Dilip Anthony Joseph 1 Some slides added from Fei Xu's slides, Small
Transport Layer. <protocol, local-addr,local-port,foreign-addr,foreign-port> ϒ Client uses ephemeral ports /10 Joseph Cordina 2005
 Transport Layer For a connection on a host (single IP address), there exist many entry points through which there may be many-to-many connections. These are called ports. A port is a 16-bit number used
Transport Layer For a connection on a host (single IP address), there exist many entry points through which there may be many-to-many connections. These are called ports. A port is a 16-bit number used
HTTP Protocol and Server-Side Basics
 HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
HTTP Protocol and Server-Side Basics Web Programming Uta Priss ZELL, Ostfalia University 2013 Web Programming HTTP Protocol and Server-Side Basics Slide 1/26 Outline The HTTP protocol Environment Variables
