2018 Hands-on Guide. F5 Azure SACA. F5 Networks, Inc.
|
|
|
- Kimberly Lang
- 5 years ago
- Views:
Transcription
1 2018 Hands-on Guide F5 Azure SACA F5 Networks, Inc.
2 2
3 Contents: 1 F5 Azure SACA - Index Welcome
4 4
5 1 F5 Azure SACA - Index 1.1 Welcome Welcome to the F5 Azure SACA guide. The content contained here provides a Notional SCCA Deployment based on: stigs/pdf/scca_frd_v2-9.pdf Source code can be found in the GitHub repository at This is F5 Contributed Software About F5 Azure SACA The following is a guide of some of the terms that will be used in this document as well as a reference to resources for additional information. SACA Secure Azure Computing Architecture for DoD (SACA) is a notional deployment of SCCA. SCCA SCCA is an abrievation for Secure Cloud Computing Architecture that is outlined in the following document: This architecture provides guidance on requirements for securing Cloud Computing Environments based on US DoD experience. It outlines recommended components including a Cloud Access Point (CAP), Virtual Datacenter Security Stack (VDSS), Virtual Datacenter Managed Service (VDMS), and Trusted Cloud Credential Manager (TCCM). Azure Microsoft Azure is a leading provider of Cloud Computing resources and provides both a US Government and US DoD Cloud Computing Environments. 5
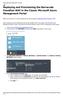
6 F5 F5 Networks provides products and solutions for high availability, security, and performance optimization of Cloud Computing environments. F5 Azure SCCA This document will focus on the deployment of virtual resources in support of an SCCA environment. SCCA can be a combination of physical and virtual resources. The deployed example architecture can be utilized to aid fulfilling requirements around segmentation of traffic, visibility of encrypted traffic, and security of application protocols that are outlined in the SCCA document Deploying F5 Azure SACA ARM Template To complete this guide requires that you have an Azure US Government account. The guide will go through the steps of launching an Azure ARM template to create a VNet that represents a VDSS and VDMS network. It will also create jumpbox resources (Windows/Linux) that will be used for Management access and F5 devices that will be used to secure ingress and egress traffic. Connect to Azure Portal First login to the Azure Portal at: (US Government) OR (Commercial) Note: This requires a Azure Government Subscription OR Azure Subscription Enable Programmatic Access to F5 Resources Before you launch the template; you will need to enable programmatic deployment for your F5 devices. Go to Marketplace From the top search field in the Azure Portal search for marketplace Find F5 BIG-IP In the Market place search enter f5 byol best and hit the enter key. 6
7 Click on F5 BIG-IP ADC BEST - BYOL Warning: DO NOT SELECT F5 BIG-IP ADC+SEC BEST BYOL Verify that you have the correct version by looking at the description and you should see..version: At the very bottom of the page click on Want to deploy programmatically? Enable Programmatic Deployment Click on Enable next to the Subscription 7
8 Create a Service Principal A Service Principal will be used to deploy F5 BIG-IP devices and be used by the BIG-IP s to dynamically update Azure User Defined Routes (UDR). The following steps are how to create a Service Principal via the Azure Portal. You will need to retrieve the following three pieces of information that will be used later. 1. Application ID (a.k.a. Client ID) 2. Application Key (a.k.a. Client Secret) 3. Tenant ID It is recommended to create a text file (i.e. using Notepad) that contains: tenant id: XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX client id: XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX secret: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX The following will guide you on how to retrieve this information via the Azure Portal OR Azure CLI (choose one method) Create Service Principal via Azure CLI Use this method if you prefer using a command line interface or have access to Cloud Shell (available in Azure Cloud, not available in Microsoft Azure Government). To access Azure Cloud Shell see: First verify the subscription. student01@azure:~$ az account show { "environmentname": "AzureCloud", "id": "XXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXXXX", "isdefault": true, "name": "my_subscription", "state": "Enabled", "tenantid": "YYYYY-YYYY-YYYY-YYYY-YYYYYYYYYY", "user": { "name": "studnt01@example.com", "type": "user" }} If you do not see the correct subscription run to view subscriptions student01@azure:~$ az account list Then set the default to the correct subscription. student01@azure:~$ az account set -s XXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXXXX To create your service principal run (replace student01 with a unique value or bigip ) student01@azure:~$ az ad sp create-for-rbac -n "student01-sp" Retrying role assignment creation: 1/36 { "appid": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX", "displayname": "student01-sp", 8
9 } "name": " "password": "SSSSSSSS-SSSS-SSSS-SSSS-SSSSSSSSSSSS", "tenant": "TTTTTTTT-TTTT-TTTT-TTTT-TTTTTTTTTTTT" Tip: When using Azure Cloud Shell you will need to highlight the text in your browser and right-click and select copy to copy and paste the text from the browser. Save the values of tenant, password, and appid to your text file that you created earlier. Create Service Principal via Azure Portal If you used the Azure CLI to create your Service Principal you can skip the following. Note: The following is adapted from: resource-group-create-service-principal-portal#create-an-azure-active-directory-application Click on Azure Active Directory In the menu on the left click on Azure Active Directory. Create App Registration Next click on App Registrations And click on New application registration. Enter a name (i.e. bigipsp ) and a Sign-on URL (i.e. ). Note: If you are using a shared subscription; please use a unique identifier i.e. student01-bigipsp Retrieve App ID Next you will need to retrieve the Application ID and authentication key. Under App Registrations find the App that you created in the previous step. Copy the Application ID. You will need this value later. This is the first piece of information that you will need. Tip: A Click to Copy button will appear when you hover on the right side of the ID 9
10 10
11 11
12 Generate Key To the right of the Application ID click on the Keys link. Provide a description (i.e. bigip key ) and duration. After saving the key be sure to save the value. This is the secret key and will not be retrievable again. This is the second piece of information that you will need. Grant Role The Service Principal will need to have Contributor access to create BIG-IP devices and manage UDR routes. The following steps will guide you in granting this role to your Azure Subscription. You can later opt to limit access to specific Resource Groups. Under Cost Management + Billing find your Azure Subscription. Click on Access control (IAM) Under Role select Contributor. Under Select type the name of the principal that you previously created (i.e. bigipsp ). Select that principal. Click Save Get Directory ID The third piece of information that you will need is the Tenant ID. Under Azure Active Directory retrieve the Directory ID. 12
13 13
14 Note: Please see: resource-group-create-service-principal-portal#get-tenant-id Launch Deployment Custom Deployment Click on the following link: Azure Government com%2ff5devcentral%2ff5-azure-saca%2fmaster%2froles%2ff5-azure-scca%2ffiles% 2Fazuredeploy.json Azure Cloud com%2ff5devcentral%2ff5-azure-saca%2fmaster%2froles%2ff5-azure-scca%2ffiles% 2Fazuredeploy.json You should see. Username and Password Fill in the required username/password for the VDSS Jump Boxes. These devices will be used for administrative access to the environment. F5 Information Next fill in the three pieces of information that was previously collected for the Service Principal and F5 license keys. 14
15 Terms and Conditions Accept the Terms and Conditions and click Purchase. Verify Template Complete It will take ~40 - ~60 minutes for the template to complete. Under Resource Groups find the Deployments item and verify that you see Succeeded F5 Azure SCCA - Architecture Overview The following is a diagram of the traffic flow of the template that was deployed. 15
16 Traffic originates from the Client through a Cloud Access Point. This would be an Express Route connection, but in the previous template the Public Internet can be used for demonstration purposes. As traffic enters the environment it is first inspected by an External pair of F5 devices. These External devices are responsible for providing edge filtering protection of traffic at L3/L4, address translation of egress traffic, and terminating SSL connections for later inspection by the IPS device and F5 Internal devices (WAF). For demonstration purposes a generic Linux server has been deployed to emulate an IPS device. High Availability The resources are deployed in an Active/Standby pair to provide High Availability. 16
17 Depending on the protocol and security requirements this can be also done in an Active/Active manner. In this example template, an Azure Load Balancer is utilized to reduce failover time, but this can be deployed without an Azure Load Balancer. This example also has a single point of failure with a single IPS device. In a production environment it would be expected to deploy an IPS solution in an HA configuration similar to the F5 Internal devices. Traffic Visibility The F5 External/Internal devices are both configured to collect Network Firewall event logs. For demonstration purposes these are being stored locally, but they can also send logs to external ArcSight, Splunk, IPFIX, Remote Syslog, or Azure OMS logging destinations. The F5 Internal device is also configured with a Web Application Firewall (WAF) and is capable of logging HTTP traffic. In this example template the Internal devices are configured to capture HTTP request logs locally. Similar to the Network Firewall, the WAF can be configured for external logging destinations. This architecture also provides the original Client IP to the destination Application through the use of Azure User Defined Routes (UDR). Using UDR, all egress Application traffic is also sent through the F5 devices. The F5 External devices can also be utilized to terminate SSL connections to provide SSL Visibility to the IPS and F5 Internal devices. The F5 Internal devices can re-encrypt SSL connections before the traffic is sent to Management or Mission Owner networks. Security The F5 External/Internal devices are tiered to provide mutiple levels of protections. 17
18 The F5 External devices and IPS device are capable of deflecting L3/L4 based attacks; while the F5 Internal device can address L7 based attacks. Integration Behind the scenes this sample environment is employing Azure services. Availability Sets ensure that the F5 Device pairs are scheduled for maintenance at appropriate times. The Azure SDK is utilized to failover Azure Route Table entries that provides the visiblity of Client IP address and ensures that all egress traffic traverses the F5 devices. The template itself is using Azure Resource Management templates to automate the process of deploying Azure resources. Azure Load Balancer is used to improve failover times and Azure OMS can be used for external logging where available SCCA Details Topology After the template completes deploying there will be the following devices deployed. 18
19 External F5 Devices (x2) IPS Device (Linux host) Internal F5 Devices (x2) Linux Jumpbox Windows Jumpbox SCCA VDSS As part of VDSS Security Requirements the Jumpbox is separated into its own subnet (SCCA Req. ID ) access is also limited to SSH/RDP (w/ TLS) (Req. ID ). The F5 BIG-IP acts as a reverse proxy (Req. ID ). Use of the F5 BIG-IP AFM (network firewall) and ASM (web application firewall) modules can be used in relation to limit/inspect/enforce application traffic (SCCA Req. ID , , , , , ). Event data capture on F5 BIG-IP can be sent to external log sources ( ). By performing SSL termination of application traffic BIG-IP can support requirements around break and inspect of SSL/TLS traffic (Req. ID ) and also support sending traffic inline or out-of-band to additional IPS/IDS devices in support of SCCA VDSS requirements. Verifying a complete deployment The template will create VDSS VNet VDSS Route Tables VDSS Management Hosts (Windows/Linux) IPS Host (Linux) Azure Load Balancers F5 External Resource Group F5 Internal Resource Group Verify that you see the expected resource groups (should appear within ~10 minutes of launch). You should see [original resource group] [original resource group]_f5_external [original resource group]_f5_internal 19
20 Resources Clicking on the [original resource group] name you should see a set of resources including. Virtual Network Azure Load Balancers Public IP Addresses Virtual Machines Public IP Addresses You should see 3 Public IP Addresses. The linux-vdssjumpbox-ip can be used to access the Linux jumpbox via SSH while the automation deployment is launching. Once the deployment completes you will no longer be able to access the environment via this IP Address. Record the Public IP Addresses for f5-ext-pip0 and f5-ext-pip1. Click on the resource and copy down the IP address. Note: Your IP Address will differ than the example screenshot. Troubleshooting the Deployment If you do not see the _F5_ resource groups you can log onto the linux jumpbox to check on the status of the deployment or look for errors. SSH to the linux-vdssjumpbox-ip host. 20
21 % tail -f /var/log/cloud-init-output.log PLAY [localhost] ******************************************************************************************** ***************************************************************************************************** TASK [Gathering Facts] ************************************************************************************** ***************************************************************************************************** ok: [localhost] TASK [f5-azure-scca : Check if resource group exists] ******************************************************* ***************************************************************************************************** ok: [localhost] TASK [f5-azure-scca : Deploy SCCA Environnment] ************************************************************* ***************************************************************************************************** skipping: [localhost]... Demo Sites Using a web browser try to access the IP Address of f5-ext-pip1 via HTTPS. i.e. Tip: You may need to click past certificate errors Also verify you can connect to address]. Access Windows Jumpbox The Windows Jumpbox can be used to access resources in the environment. The following will guide you through connecting to the jumpbox and configuring it to access internal resources. Using a Windows RDP client create an RDP connection to the Public IP Address f5-ext-pip0. 21
22 When prompted select the option to Use a different account. Specify the username/password entered for the VDMSS jumpbox username/password in the ARM template. Once you connect you should see the Server Manager Dashboard. Click on Local Server in the menu. Click on IE Enhanced Security Configuration -> On. Change the settings to Off (This is not recommended for production, but used for demonstration purposes). Open up Internet Explorer and accept default settings. Login to F5 BIG-IP Devices The F5 BIG-IP Devices are configured to only allow connections from the jumpbox devices. From the Windows jumpbox: Browse to Click past certificate warnings (recommended to install CA signed certificates for production use). 22
23 You should see the login for the F5 BIG-IP. Login using the same credentials to access the RDP host. Repeat for: Extend Idle Timeout (Optional) By default the session will timeout after 20 minutes. To change the timeout to 1 day. Go to System -> Preferences. Change the value to Active Device The F5 BIG-IP devices are deployed in an Active/Standby configuration. They can also be deployed in an Active/Active mode, but Active/Standby is used for this environment to ease the process of identifying the device that is processing traffic. To determine the Active device take note of the top left of the page. Firewall Logs The F5 BIG-IP AFM modules provides network firewall capabilities and DDoS protection. Find the Active device of the External F5 Devices. It will be either:
24 From the menu on the left of the screen access Security -> Event Logs -> Network -> Firewall An example of filtering the log output is to click on Custom Search then click and drag Port from the column to the top of the page. Enter the port 3389 and click search Note that you should see your connecting IP address as well as the destination address of the RDP connection. Normally you be unable to log the original destination IP address, but we are using the Azure Load Balancer to make this information visible. We ll take a look at the Azure Load Balancer in the next section. On the same BIG-IP device browse to Local Traffic -> Virtual Servers. You ll see that the external IP Address is configured on the BIG-IP. Azure Load Balancer - External Go back to the Azure Portal and click on the Resource Group and find the Azure Load Balancers (this is the same Resource Group where you found the Public IP Address). Click on f5-ext-alb and click on Load balancing rules 24
25 Then click on rdp_vs Note that Floating IP (direct server return) is set to Enabled WAF logs In addition to providing network firewall capabilities, F5 BIG-IP ASM module provides a web application firewall that can deter L7 attacks. Unlike a traditional firewall; a WAF is capable of providing a mixture of positive/negative security policies as well as intercept and modify response data as needed (DLP / BOT mitigation). Find the Active device of the Internal F5 Devices. It will be either:
26 From the menu on the left of the screen access Security -> Event Logs -> Application -> Requests Initially you will see no data. Click on the X next to Illegal Requests to show all results. You can browse through the requests to see more data. Simulated L7 Attack (optional) The following will simulate an attack that will trigger a WAF policy. First make a request to Change the method to propfind and submit. This will trigger a block for an illegal method. This type of attack can be used when an attacker is trying to find insecure webdav file shares. 26
27
MarkLogic Server. MarkLogic Server on Microsoft Azure Guide. MarkLogic 9 January, 2018
 MarkLogic Server on Microsoft Azure Guide 1 MarkLogic 9 January, 2018 Last Revised: 9.0-4, January, 2018 2018 MarkLogic Corporation. MarkLogic and the MarkLogic logo are trademarks or registered trademarks
MarkLogic Server on Microsoft Azure Guide 1 MarkLogic 9 January, 2018 Last Revised: 9.0-4, January, 2018 2018 MarkLogic Corporation. MarkLogic and the MarkLogic logo are trademarks or registered trademarks
How-to Guide: Tenable.io for Microsoft Azure. Last Updated: November 16, 2018
 How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
OnCommand Cloud Manager 3.2 Deploying and Managing ONTAP Cloud Systems
 OnCommand Cloud Manager 3.2 Deploying and Managing ONTAP Cloud Systems April 2017 215-12035_C0 doccomments@netapp.com Table of Contents 3 Contents Before you create ONTAP Cloud systems... 5 Logging in
OnCommand Cloud Manager 3.2 Deploying and Managing ONTAP Cloud Systems April 2017 215-12035_C0 doccomments@netapp.com Table of Contents 3 Contents Before you create ONTAP Cloud systems... 5 Logging in
How-to Guide: Tenable Nessus for Microsoft Azure. Last Updated: April 03, 2018
 How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
Cloud Operations Using Microsoft Azure. Nikhil Shampur
 Cloud Operations Using Microsoft Azure Nikhil Shampur Agenda - Overview - ArcGIS Enterprise on Azure strategy - Deployment Options - What s new - 10.6-10.6.1 - Automation, Upgrades - Tips and Tricks -
Cloud Operations Using Microsoft Azure Nikhil Shampur Agenda - Overview - ArcGIS Enterprise on Azure strategy - Deployment Options - What s new - 10.6-10.6.1 - Automation, Upgrades - Tips and Tricks -
EXPRESSCLUSTER X 4.0. HA Cluster Configuration Guide for Microsoft Azure (Windows) April 17, st Edition
 EXPRESSCLUSTER X 4.0 HA Cluster Configuration Guide for Microsoft Azure (Windows) April 17, 2018 1st Edition Revision History Edition Revised Date 1st Apr 17, 2018 New guide Description ii Copyright NEC
EXPRESSCLUSTER X 4.0 HA Cluster Configuration Guide for Microsoft Azure (Windows) April 17, 2018 1st Edition Revision History Edition Revised Date 1st Apr 17, 2018 New guide Description ii Copyright NEC
Configuring F5 for SSL Intercept
 Configuring F5 for Welcome to the F5 deployment guide for configuring the BIG-IP system for SSL intercept (formerly called with Air Gap Egress Inspection). This document contains guidance on configuring
Configuring F5 for Welcome to the F5 deployment guide for configuring the BIG-IP system for SSL intercept (formerly called with Air Gap Egress Inspection). This document contains guidance on configuring
Using RDP with Azure Linux Virtual Machines
 Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Tableau Server on Microsoft Azure:
 Tableau Server on Microsoft Azure: Deployment Guidelines and Best Practices April 2017 Table of Contents Abstract...3 Introduction to Tableau With Microsoft Azure...3 Option 1 Self Deployment via Azure
Tableau Server on Microsoft Azure: Deployment Guidelines and Best Practices April 2017 Table of Contents Abstract...3 Introduction to Tableau With Microsoft Azure...3 Option 1 Self Deployment via Azure
Best Practices for Migrating Servers to Microsoft Azure with PlateSpin Migrate
 White Paper PlateSpin Transformation Manager PlateSpin Migrate Best Practices for Migrating Servers to Microsoft Azure with PlateSpin Migrate Updated for PlateSpin Transformation Manager 1.1 and PlateSpin
White Paper PlateSpin Transformation Manager PlateSpin Migrate Best Practices for Migrating Servers to Microsoft Azure with PlateSpin Migrate Updated for PlateSpin Transformation Manager 1.1 and PlateSpin
F5 Analytics and Visibility Solutions
 Agility 2017 Hands-on Lab Guide F5 Analytics and Visibility Solutions F5 Networks, Inc. 2 Contents: 1 Class 1: Introduction to F5 Analytics 5 1.1 Lab Environment Setup.......................................
Agility 2017 Hands-on Lab Guide F5 Analytics and Visibility Solutions F5 Networks, Inc. 2 Contents: 1 Class 1: Introduction to F5 Analytics 5 1.1 Lab Environment Setup.......................................
Secure Cloud Computing Architecture (SCCA)
 Secure Cloud Computing Architecture (SCCA) Susan Casson PM, SCCA December 12, 2017 UNITED IN IN SERVICE TO OUR NATION 1 Unclassified DoD Commercial Cloud Deployment Approach Cyber Command C2 Operations
Secure Cloud Computing Architecture (SCCA) Susan Casson PM, SCCA December 12, 2017 UNITED IN IN SERVICE TO OUR NATION 1 Unclassified DoD Commercial Cloud Deployment Approach Cyber Command C2 Operations
CloudHealth. AWS and Azure On-Boarding
 CloudHealth AWS and Azure On-Boarding Contents 1. Enabling AWS Accounts... 3 1.1 Setup Usage & Billing Reports... 3 1.2 Setting Up a Read-Only IAM Role... 3 1.3 CloudTrail Setup... 5 1.4 Cost and Usage
CloudHealth AWS and Azure On-Boarding Contents 1. Enabling AWS Accounts... 3 1.1 Setup Usage & Billing Reports... 3 1.2 Setting Up a Read-Only IAM Role... 3 1.3 CloudTrail Setup... 5 1.4 Cost and Usage
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
F5 DDoS Hybrid Defender : Setup. Version
 F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
Note: Currently (December 3, 2017), the new managed Kubernetes service on Azure (AKS) does not yet support Windows agents.
 Create a Hybrid Kubernetes Linux/Windows Cluster in 7 Easy Steps Azure Container Service (ACS) makes it really easy to provision a Kubernetes cluster in Azure. Today, we'll walk through the steps to set
Create a Hybrid Kubernetes Linux/Windows Cluster in 7 Easy Steps Azure Container Service (ACS) makes it really easy to provision a Kubernetes cluster in Azure. Today, we'll walk through the steps to set
271 Waverley Oaks Rd. Telephone: Suite 206 Waltham, MA USA
 Contacting Leostream Leostream Corporation http://www.leostream.com 271 Waverley Oaks Rd. Telephone: +1 781 890 2019 Suite 206 Waltham, MA 02452 USA To submit an enhancement request, email features@leostream.com.
Contacting Leostream Leostream Corporation http://www.leostream.com 271 Waverley Oaks Rd. Telephone: +1 781 890 2019 Suite 206 Waltham, MA 02452 USA To submit an enhancement request, email features@leostream.com.
O365 Solutions. Three Phase Approach. Page 1 34
 O365 Solutions Three Phase Approach msfttechteam@f5.com Page 1 34 Contents Use Cases... 2 Use Case One Advanced Traffic Management for WAP and ADFS farms... 2 Use Case Two BIG-IP with ADFS-PIP... 3 Phase
O365 Solutions Three Phase Approach msfttechteam@f5.com Page 1 34 Contents Use Cases... 2 Use Case One Advanced Traffic Management for WAP and ADFS farms... 2 Use Case Two BIG-IP with ADFS-PIP... 3 Phase
Exam : Implementing Microsoft Azure Infrastructure Solutions
 Exam 70-533: Implementing Microsoft Azure Infrastructure Solutions Objective Domain Note: This document shows tracked changes that are effective as of January 18, 2018. Design and Implement Azure App Service
Exam 70-533: Implementing Microsoft Azure Infrastructure Solutions Objective Domain Note: This document shows tracked changes that are effective as of January 18, 2018. Design and Implement Azure App Service
Azure Archival Installation Guide
 Azure Archival Installation Guide Page 1 of 23 Table of Contents 1. Add Dynamics CRM Active Directory into Azure... 3 2. Add Application in Azure Directory... 5 2.1 Create application for application user...
Azure Archival Installation Guide Page 1 of 23 Table of Contents 1. Add Dynamics CRM Active Directory into Azure... 3 2. Add Application in Azure Directory... 5 2.1 Create application for application user...
Azure 209x Practical Exercises Overview
 Azure 209x Practical Exercises Overview This course includes optional exercises where you can try out the techniques demonstrated in the course for yourself. This guide lists the steps for the individual
Azure 209x Practical Exercises Overview This course includes optional exercises where you can try out the techniques demonstrated in the course for yourself. This guide lists the steps for the individual
Microsoft Architecting Microsoft Azure Solutions.
 Microsoft 70-535 Architecting Microsoft Azure Solutions https://killexams.com/pass4sure/exam-detail/70-535 QUESTION: 106 Your organization has developed and deployed several Azure App Service Web and API
Microsoft 70-535 Architecting Microsoft Azure Solutions https://killexams.com/pass4sure/exam-detail/70-535 QUESTION: 106 Your organization has developed and deployed several Azure App Service Web and API
Adobe Marketing Cloud Bloodhound for Mac 3.0
 Adobe Marketing Cloud Bloodhound for Mac 3.0 Contents Adobe Bloodhound for Mac 3.x for OSX...3 Getting Started...4 Processing Rules Mapping...6 Enable SSL...7 View Hits...8 Save Hits into a Test...9 Compare
Adobe Marketing Cloud Bloodhound for Mac 3.0 Contents Adobe Bloodhound for Mac 3.x for OSX...3 Getting Started...4 Processing Rules Mapping...6 Enable SSL...7 View Hits...8 Save Hits into a Test...9 Compare
Integrate your CSP Direct Agreement
 Overview: - The information needed to integrate your CSP Direct tenant is contained in this PDF Guide. You will be asked to create and access various authentication keys and which you need to do in the
Overview: - The information needed to integrate your CSP Direct tenant is contained in this PDF Guide. You will be asked to create and access various authentication keys and which you need to do in the
TECHNICAL NOTE MSM & CLEARPASS HOW TO CONFIGURE HPE MSM CONTROLLERS WITH ARUBA CLEARPASS VERSION 3, JUNE 2016
 HOW TO CONFIGURE HPE MSM CONTROLLERS WITH ARUBA CLEARPASS VERSION 3, JUNE 2016 CONTENTS Introduction... 5 MSM and AP Deployment Options... 5 MSM User Interfaces... 6 Assumptions... 7 Network Diagram...
HOW TO CONFIGURE HPE MSM CONTROLLERS WITH ARUBA CLEARPASS VERSION 3, JUNE 2016 CONTENTS Introduction... 5 MSM and AP Deployment Options... 5 MSM User Interfaces... 6 Assumptions... 7 Network Diagram...
Lab Guide. Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501
 Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Integrate your CSP Direct Agreement
 Overview: - The information needed to integrate your CSP Direct tenant is contained in this PDF Guide. You will be asked to create and access various authentication keys and which you need to do in the
Overview: - The information needed to integrate your CSP Direct tenant is contained in this PDF Guide. You will be asked to create and access various authentication keys and which you need to do in the
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
F5 Azure Cloud Try User Guide. F5 Networks, Inc. Rev. September 2016
 F5 Azure Cloud Try User Guide F5 Networks, Inc. Rev. September 2016 Azureinfo@f5.com Table of Contents Introduction... 3 F5 Web Application Firewall Solution, (WAF) Review... 3 Configuring SSO/Pre-authentication
F5 Azure Cloud Try User Guide F5 Networks, Inc. Rev. September 2016 Azureinfo@f5.com Table of Contents Introduction... 3 F5 Web Application Firewall Solution, (WAF) Review... 3 Configuring SSO/Pre-authentication
OnCommand Cloud Manager 3.2 Getting Up and Running
 OnCommand Cloud Manager 3.2 Getting Up and Running April 2017 215-12034_B0 doccomments@netapp.com Table of Contents 3 Contents Installation and setup workflow... 4 Preparing for installation and setup...
OnCommand Cloud Manager 3.2 Getting Up and Running April 2017 215-12034_B0 doccomments@netapp.com Table of Contents 3 Contents Installation and setup workflow... 4 Preparing for installation and setup...
Azure Application Deployment and Management: Service Fabric Create and Manage a Local and Azure hosted Service Fabric Cluster and Application
 Azure Application Deployment and Management: Service Fabric Create and Manage a Local and Azure hosted Service Fabric Cluster and Application Overview This course includes optional practical exercises
Azure Application Deployment and Management: Service Fabric Create and Manage a Local and Azure hosted Service Fabric Cluster and Application Overview This course includes optional practical exercises
Automation Anywhere Enterprise 10 LTS
 Automation Anywhere Enterprise 10 LTS Document Version: 1.3 Installation Guide Date of Publication: 15 th November, 2016 Update(s) to this document edition: Table of Contents 1. Client Prerequisites Processor
Automation Anywhere Enterprise 10 LTS Document Version: 1.3 Installation Guide Date of Publication: 15 th November, 2016 Update(s) to this document edition: Table of Contents 1. Client Prerequisites Processor
SaaS. Public Cloud. Co-located SaaS Containers. Cloud
 SaaS On-prem Private Cloud Public Cloud Co-located SaaS Containers APP SERVICES ACCESS TLS/SSL DNS NETWORK WAF LOAD BALANCING DNS ACCESS CONTROL SECURITY POLICIES F5 Beside the Cloud Why Get Closer to
SaaS On-prem Private Cloud Public Cloud Co-located SaaS Containers APP SERVICES ACCESS TLS/SSL DNS NETWORK WAF LOAD BALANCING DNS ACCESS CONTROL SECURITY POLICIES F5 Beside the Cloud Why Get Closer to
Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management Portal
 Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management This guide will walk you through the steps to load balance traffic across multiple instances of the Barracuda
Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management This guide will walk you through the steps to load balance traffic across multiple instances of the Barracuda
Course AZ-100T01-A: Manage Subscriptions and Resources
 Course AZ-100T01-A: Manage Subscriptions and Resources Module 1: Managing Azure Subscriptions In this module, you ll learn about the components that make up an Azure subscription and how management groups
Course AZ-100T01-A: Manage Subscriptions and Resources Module 1: Managing Azure Subscriptions In this module, you ll learn about the components that make up an Azure subscription and how management groups
Installation Guide Revision B. McAfee Cloud Workload Security 5.0.0
 Installation Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator,
Installation Guide Revision B McAfee Cloud Workload Security 5.0.0 COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator,
How to Configure VNET peering with the F-Series Firewall
 How to Configure VNET peering with the F-Series Firewall If you have multiple virtual networks in the same Azure region, you can connect them with a high bandwidth, low-latency connection via virtual network
How to Configure VNET peering with the F-Series Firewall If you have multiple virtual networks in the same Azure region, you can connect them with a high bandwidth, low-latency connection via virtual network
Amazon AppStream 2.0: SOLIDWORKS Deployment Guide
 2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
Deploying F5 with Microsoft Active Directory Federation Services
 F5 Deployment Guide Deploying F5 with Microsoft Active Directory Federation Services This F5 deployment guide provides detailed information on how to deploy Microsoft Active Directory Federation Services
F5 Deployment Guide Deploying F5 with Microsoft Active Directory Federation Services This F5 deployment guide provides detailed information on how to deploy Microsoft Active Directory Federation Services
How to Configure Azure Route Tables (UDR) using Azure Portal and ARM
 How to Configure Azure Route Tables (UDR) using Azure Portal and ARM Azure Route Tables, or User Defined Routing, allow you to create network routes so that your F-Series Firewall VM can handle the traffic
How to Configure Azure Route Tables (UDR) using Azure Portal and ARM Azure Route Tables, or User Defined Routing, allow you to create network routes so that your F-Series Firewall VM can handle the traffic
Deploying the Cisco Tetration Analytics Virtual Appliance in Microsoft Azure
 Deploying the Cisco Tetration Analytics Virtual Appliance in Microsoft Azure About, on page 1 Prerequisites for, on page 1, on page 3 AboutDeployingtheCiscoTetrationAnalyticsVirtualAppliance in Microsoft
Deploying the Cisco Tetration Analytics Virtual Appliance in Microsoft Azure About, on page 1 Prerequisites for, on page 1, on page 3 AboutDeployingtheCiscoTetrationAnalyticsVirtualAppliance in Microsoft
VMWARE HORIZON CLOUD WITH VMWARE IDENTITY MANAGER QUICK START GUIDE WHITE PAPER MARCH 2018
 VMWARE HORIZON CLOUD WITH VMWARE IDENTITY MANAGER QUICK START GUIDE WHITE PAPER MARCH 2018 Table of Contents Introduction to Horizon Cloud with Manager.... 3 Benefits of Integration.... 3 Single Sign-On....3
VMWARE HORIZON CLOUD WITH VMWARE IDENTITY MANAGER QUICK START GUIDE WHITE PAPER MARCH 2018 Table of Contents Introduction to Horizon Cloud with Manager.... 3 Benefits of Integration.... 3 Single Sign-On....3
Secure Cloud Computing Architecture (SCCA)
 Secure Cloud Computing Architecture (SCCA) Program Overview Susan Casson PM, SCCA May 15, 2018 UNITED IN IN SERVICE TO OUR NATION 1 Service Overview: Why SCCA? SCCA connects the DoD to Infrastructure and
Secure Cloud Computing Architecture (SCCA) Program Overview Susan Casson PM, SCCA May 15, 2018 UNITED IN IN SERVICE TO OUR NATION 1 Service Overview: Why SCCA? SCCA connects the DoD to Infrastructure and
Enhancing Exchange Mobile Device Security with the F5 BIG-IP Platform
 Enhancing Exchange Mobile Device Security with the F5 BIG-IP Platform By the F5 business development team for the Microsoft Global Alliance Version 1.0 Introduction As the use of mobile devices in the
Enhancing Exchange Mobile Device Security with the F5 BIG-IP Platform By the F5 business development team for the Microsoft Global Alliance Version 1.0 Introduction As the use of mobile devices in the
Course Outline. Module 1: Microsoft Azure for AWS Experts Course Overview
 Course Outline Module 1: Microsoft Azure for AWS Experts Course Overview In this module, you will get an overview of Azure services and features including deployment models, subscriptions, account types
Course Outline Module 1: Microsoft Azure for AWS Experts Course Overview In this module, you will get an overview of Azure services and features including deployment models, subscriptions, account types
VPN Solutions for Zerto Virtual Replication to Azure. SoftEther Installation Guide
 VPN Solutions for Zerto Virtual Replication to Azure SoftEther Installation Guide VERSION 1.0 JULY 2017 Table of Contents 1. Overview... 2 1.1 Use Cases... 2 2. Proofs of Concept and Lab Usage... 2 2.1
VPN Solutions for Zerto Virtual Replication to Azure SoftEther Installation Guide VERSION 1.0 JULY 2017 Table of Contents 1. Overview... 2 1.1 Use Cases... 2 2. Proofs of Concept and Lab Usage... 2 2.1
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3
 Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Microsoft Azure Course Content
 Cloud Computing Trainings @ STUCORNER & SHARPENCLOUD Microsoft Azure Course Content Lesson 1: Introduction to Azure 1. Overview of On-premise infrastructure 2. Transition from On-premise to datacenter
Cloud Computing Trainings @ STUCORNER & SHARPENCLOUD Microsoft Azure Course Content Lesson 1: Introduction to Azure 1. Overview of On-premise infrastructure 2. Transition from On-premise to datacenter
DEPLOYMENT GUIDE HOW TO DEPLOY MICROSOFT SHAREPOINT 2016 WITH A10 THUNDER ADC
 DEPLOYMENT GUIDE HOW TO DEPLOY MICROSOFT SHAREPOINT 2016 WITH A10 THUNDER ADC OVERVIEW Microsoft SharePoint Server 2016 is a collaboration platform that organizations of all sizes can use to improve the
DEPLOYMENT GUIDE HOW TO DEPLOY MICROSOFT SHAREPOINT 2016 WITH A10 THUNDER ADC OVERVIEW Microsoft SharePoint Server 2016 is a collaboration platform that organizations of all sizes can use to improve the
MOVEit Transfer on Azure Marketplace Quickstart Guide. How to deploy and use MOVEit Transfer from Microsoft Azure Marketplace
 MOVEit Transfer on Azure Marketplace Quickstart Guide How to deploy and use MOVEit Transfer from Microsoft Azure Marketplace Copyright Notice 1991-2017 Ipswitch, Inc. All rights reserved. This document,
MOVEit Transfer on Azure Marketplace Quickstart Guide How to deploy and use MOVEit Transfer from Microsoft Azure Marketplace Copyright Notice 1991-2017 Ipswitch, Inc. All rights reserved. This document,
Deploying F5 with Microsoft Active Directory Federation Services
 F5 Deployment Guide Deploying F5 with Microsoft Active Directory Federation Services This F5 deployment guide provides detailed information on how to deploy Microsoft Active Directory Federation Services
F5 Deployment Guide Deploying F5 with Microsoft Active Directory Federation Services This F5 deployment guide provides detailed information on how to deploy Microsoft Active Directory Federation Services
Azure MFA Integration with NetScaler
 Azure MFA Integration with NetScaler This guide focuses on describing the configuration required for integrating Azure MFA (Multi-Factor Authentication) with NetScaler. Citrix.com 1 NetScaler is a world-class
Azure MFA Integration with NetScaler This guide focuses on describing the configuration required for integrating Azure MFA (Multi-Factor Authentication) with NetScaler. Citrix.com 1 NetScaler is a world-class
agility17dns Release latest Jun 15, 2017
 agility17dns d ocsdocumentation Release latest Jun 15, 2017 Contents 1 Lab Access 1 2 Network Topology 3 3 GSLB 5 3.1 Initial Setup............................................... 5 3.2 Logging..................................................
agility17dns d ocsdocumentation Release latest Jun 15, 2017 Contents 1 Lab Access 1 2 Network Topology 3 3 GSLB 5 3.1 Initial Setup............................................... 5 3.2 Logging..................................................
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
VI. Corente Services Client
 VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
F5 BIG-IP Access Policy Manager: SAML IDP
 Agility 2018 Hands-on Lab Guide F5 BIG-IP Access Policy Manager: SAML IDP F5 Networks, Inc. 2 Contents: 1 Welcome 5 2 Class 1: SAML Identity Provider (IdP) Lab 7 2.1 Lab Topology & Environments...................................
Agility 2018 Hands-on Lab Guide F5 BIG-IP Access Policy Manager: SAML IDP F5 Networks, Inc. 2 Contents: 1 Welcome 5 2 Class 1: SAML Identity Provider (IdP) Lab 7 2.1 Lab Topology & Environments...................................
Introduction. The Safe-T Solution
 Secure Application Access Product Brief Contents Introduction 2 The Safe-T Solution 3 How It Works 3 Capabilities 4 Benefits 5 Feature List 6 6 Introduction As the world becomes much more digital and global,
Secure Application Access Product Brief Contents Introduction 2 The Safe-T Solution 3 How It Works 3 Capabilities 4 Benefits 5 Feature List 6 6 Introduction As the world becomes much more digital and global,
Check Point vsec for Microsoft Azure
 Check Point vsec for Microsoft Azure Test Drive User Guide 2017 Check Point Software Technologies Ltd. All rights reserved Page 1 Learn More: checkpoint.com Content 1 INTRODUCTION... 3 2 TEST DRIVE OVERVIEW...
Check Point vsec for Microsoft Azure Test Drive User Guide 2017 Check Point Software Technologies Ltd. All rights reserved Page 1 Learn More: checkpoint.com Content 1 INTRODUCTION... 3 2 TEST DRIVE OVERVIEW...
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster
 AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
LoadMaster for Azure Resource Manager. Feature Description
 LoadMaster for Azure Resource Manager Feature Description UPDATED: 16 October 2017 Copyright Notices Copyright 2002-2017 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies
LoadMaster for Azure Resource Manager Feature Description UPDATED: 16 October 2017 Copyright Notices Copyright 2002-2017 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies
VMware Horizon Cloud Service on Microsoft Azure Administration Guide
 VMware Horizon Cloud Service on Microsoft Azure Administration Guide Modified on 03 APR 2018 VMware Horizon Cloud Service VMware Horizon Cloud Service on Microsoft Azure 1.5 You can find the most up-to-date
VMware Horizon Cloud Service on Microsoft Azure Administration Guide Modified on 03 APR 2018 VMware Horizon Cloud Service VMware Horizon Cloud Service on Microsoft Azure 1.5 You can find the most up-to-date
DEPLOYING A 3SCALE API GATEWAY ON RED HAT OPENSHIFT
 TUTORIAL: DEPLOYING A 3SCALE API GATEWAY ON RED HAT OPENSHIFT This tutorial describes how to deploy a dockerized version of the 3scale API Gateway 1.0 (APIcast) that is packaged for easy installation and
TUTORIAL: DEPLOYING A 3SCALE API GATEWAY ON RED HAT OPENSHIFT This tutorial describes how to deploy a dockerized version of the 3scale API Gateway 1.0 (APIcast) that is packaged for easy installation and
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Load Balancing VMware Workspace Portal/Identity Manager
 Load Balancing VMware Workspace Portal/Identity Manager Overview VMware Workspace Portal/Identity Manager combines applications and desktops in a single, aggregated workspace. Employees can then access
Load Balancing VMware Workspace Portal/Identity Manager Overview VMware Workspace Portal/Identity Manager combines applications and desktops in a single, aggregated workspace. Employees can then access
Balabit s Privileged Session Management and Remote Desktop Protocol Scenarios
 Balabit s Privileged Session Management and Remote Desktop Protocol Scenarios May 02, 2018 Abstract Common RDP scenarios for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a
Balabit s Privileged Session Management and Remote Desktop Protocol Scenarios May 02, 2018 Abstract Common RDP scenarios for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a
Alliance Key Manager AKM for AWS Quick Start Guide. Software version: Documentation version:
 Alliance Key Manager AKM for AWS Quick Start Guide Software version: 4.0.0 Documentation version: 4.0.0.002 Townsend Security www.townsendsecurity.com 800.357.1019 +1 360.359.4400 Alliance Key Manager
Alliance Key Manager AKM for AWS Quick Start Guide Software version: 4.0.0 Documentation version: 4.0.0.002 Townsend Security www.townsendsecurity.com 800.357.1019 +1 360.359.4400 Alliance Key Manager
VMware AirWatch: Directory and Certificate Authority
 Table of Contents Lab Overview - HOL-1857-06-UEM - VMware AirWatch: Directory and Certificate Authority Integration... 2 Lab Guidance... 3 Module 1 - Advanced AirWatch Configuration, AD Integration/Certificates
Table of Contents Lab Overview - HOL-1857-06-UEM - VMware AirWatch: Directory and Certificate Authority Integration... 2 Lab Guidance... 3 Module 1 - Advanced AirWatch Configuration, AD Integration/Certificates
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
All rights reserved. All trademarks are the property of their respective owners.
 2017 5nine Software Inc. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
2017 5nine Software Inc. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Manager
 VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Table of Contents Lab Overview - HOL-1857-03-UEM - Workspace ONE UEM with App & Access Management... 2 Lab Guidance... 3 Module 1 - Workspace
VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Table of Contents Lab Overview - HOL-1857-03-UEM - Workspace ONE UEM with App & Access Management... 2 Lab Guidance... 3 Module 1 - Workspace
Application Visibility and Analytics SE Remote Demo Platform Information
 Application Visibility and Analytics SE Remote Demo Platform Information Table of Contents Introduction... 2 How to obtain access to the Demo?... 3 Demo Overview... 6 Network Diagram... 6 Demo Flow...
Application Visibility and Analytics SE Remote Demo Platform Information Table of Contents Introduction... 2 How to obtain access to the Demo?... 3 Demo Overview... 6 Network Diagram... 6 Demo Flow...
SIEM Tool Plugin Installation and Administration
 SIEM Tool Plugin Installation and Administration 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
SIEM Tool Plugin Installation and Administration 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Workspace ONE UEM VMware AirWatch Cloud Connector
 VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
Deploying VMware Identity Manager in the DMZ. JULY 2018 VMware Identity Manager 3.2
 Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal
 Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
The Balabit s Privileged Session Management 5 F5 Azure Reference Guide
 The Balabit s Privileged Session Management 5 F5 Azure Reference Guide March 12, 2018 Abstract Administrator Guide for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a One Identity
The Balabit s Privileged Session Management 5 F5 Azure Reference Guide March 12, 2018 Abstract Administrator Guide for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a One Identity
Read the following information carefully, before you begin an upgrade.
 Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
Release Notes. Dell SonicWALL SRA Release Notes
 Secure Remote Access Contents Platform Compatibility... 1 Licensing on the Dell SonicWALL SRA Appliances and Virtual Appliance... 1 Important Differences between the SRA Appliances... 2 Known Issues...
Secure Remote Access Contents Platform Compatibility... 1 Licensing on the Dell SonicWALL SRA Appliances and Virtual Appliance... 1 Important Differences between the SRA Appliances... 2 Known Issues...
Remote Asset Manager. Version 2.2. Administrator's Guide
 Remote Asset Manager Version 2.2 Administrator's Guide April 2018 www.lexmark.com Contents 2 Contents Change history... 3 Overview... 4 Deployment readiness checklist...5 Getting started... 6 Installing
Remote Asset Manager Version 2.2 Administrator's Guide April 2018 www.lexmark.com Contents 2 Contents Change history... 3 Overview... 4 Deployment readiness checklist...5 Getting started... 6 Installing
Azure for On-Premises Administrators Practice Exercises
 Azure for On-Premises Administrators Practice Exercises Overview This course includes optional practical exercises where you can try out the techniques demonstrated in the course for yourself. This guide
Azure for On-Premises Administrators Practice Exercises Overview This course includes optional practical exercises where you can try out the techniques demonstrated in the course for yourself. This guide
Privileged Identity App Launcher and Session Recording
 Privileged Identity App Launcher and Session Recording 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Privileged Identity App Launcher and Session Recording 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
EdgeConnect for Amazon Web Services (AWS)
 Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Table of Contents HOL-1757-MBL-6
 Table of Contents Lab Overview - - VMware AirWatch: Technology Partner Integration... 2 Lab Guidance... 3 Module 1 - F5 Integration with AirWatch (30 min)... 8 Getting Started... 9 F5 BigIP Configuration...
Table of Contents Lab Overview - - VMware AirWatch: Technology Partner Integration... 2 Lab Guidance... 3 Module 1 - F5 Integration with AirWatch (30 min)... 8 Getting Started... 9 F5 BigIP Configuration...
Load Balancing Web Servers with OWASP Top 10 WAF in Azure
 Load Balancing Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.3 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Web Servers and configure a
Load Balancing Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.3 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Web Servers and configure a
Getting Started with VMware Horizon Cloud Service on Microsoft Azure
 Getting Started with VMware Horizon Cloud Service on Microsoft Azure Modified on 28 MAR 2018 VMware Horizon Cloud Service VMware Horizon Cloud Service on Microsoft Azure 1.5 You can find the most up-to-date
Getting Started with VMware Horizon Cloud Service on Microsoft Azure Modified on 28 MAR 2018 VMware Horizon Cloud Service VMware Horizon Cloud Service on Microsoft Azure 1.5 You can find the most up-to-date
Implementing Microsoft Azure Infrastructure Solutions
 Implementing Microsoft Azure Infrastructure Solutions OD20533C; On-Demand, Video-based Course Description This course is intended for IT professionals who are familiar with managing on-premises IT deployments
Implementing Microsoft Azure Infrastructure Solutions OD20533C; On-Demand, Video-based Course Description This course is intended for IT professionals who are familiar with managing on-premises IT deployments
FUJITSU Cloud Service S5. Introduction Guide. Ver. 1.3 FUJITSU AMERICA, INC.
 FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 FUJITSU AMERICA, INC. 1 FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 Date of publish: September, 2011 All Rights Reserved, Copyright FUJITSU
FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 FUJITSU AMERICA, INC. 1 FUJITSU Cloud Service S5 Introduction Guide Ver. 1.3 Date of publish: September, 2011 All Rights Reserved, Copyright FUJITSU
ScaleArc Azure Deployment Guide
 ScaleArc Azure Deployment Guide ScaleArc 2901 Tasman Drive, Suite 210 Santa Clara, CA 95054 Page 1 of 17 Copyrights and Trademarks Copyright 2009-2012 ScaleArc, all rights reserved. The information contained
ScaleArc Azure Deployment Guide ScaleArc 2901 Tasman Drive, Suite 210 Santa Clara, CA 95054 Page 1 of 17 Copyrights and Trademarks Copyright 2009-2012 ScaleArc, all rights reserved. The information contained
Implementing Infoblox Data Connector 2.0
 DEPLOYMENT GUIDE Implementing Infoblox Data Connector 2.0 2017 Infoblox Inc. All rights reserved. Implementing Infoblox Data Connector, July 2017 Page 1 of 31 Contents Overview... 3 Prerequisites... 3
DEPLOYMENT GUIDE Implementing Infoblox Data Connector 2.0 2017 Infoblox Inc. All rights reserved. Implementing Infoblox Data Connector, July 2017 Page 1 of 31 Contents Overview... 3 Prerequisites... 3
CPM. Quick Start Guide V2.4.0
 CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop
 Deployment Guide Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop Important: The fully supported version of this iapp has been released, so this guide has been archived. See http://www.f5.com/pdf/deployment-guides/citrix-vdi-iapp-dg.pdf
Deployment Guide Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop Important: The fully supported version of this iapp has been released, so this guide has been archived. See http://www.f5.com/pdf/deployment-guides/citrix-vdi-iapp-dg.pdf
Deploying and Using ArcGIS Enterprise in the Cloud. Bill Major
 Deploying and Using ArcGIS Enterprise in the Cloud Bill Major Quick Survey Your role in your organization - Developer? - Cloud Admin? Already a cloud user Running Esri deployment on AWS Running Esri deployment
Deploying and Using ArcGIS Enterprise in the Cloud Bill Major Quick Survey Your role in your organization - Developer? - Cloud Admin? Already a cloud user Running Esri deployment on AWS Running Esri deployment
February 2017 Version: 1.0. Xerox App Gallery 4.0 Information Assurance Disclosure
 February 2017 Version: 1.0 Xerox App Gallery 4.0 Information Assurance Disclosure 2017 Xerox Corporation. All rights reserved. Xerox and Xerox and Design and ConnectKey and WorkCentre are trademarks of
February 2017 Version: 1.0 Xerox App Gallery 4.0 Information Assurance Disclosure 2017 Xerox Corporation. All rights reserved. Xerox and Xerox and Design and ConnectKey and WorkCentre are trademarks of
VMware Identity Manager Cloud Deployment. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager
 VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Ansible Tower Quick Setup Guide
 Ansible Tower Quick Setup Guide Release Ansible Tower 2.4.5 Red Hat, Inc. Jun 06, 2017 CONTENTS 1 Quick Start 2 2 Login as a Superuser 3 3 Import a License 4 4 Examine the Tower Dashboard 6 5 The Setup
Ansible Tower Quick Setup Guide Release Ansible Tower 2.4.5 Red Hat, Inc. Jun 06, 2017 CONTENTS 1 Quick Start 2 2 Login as a Superuser 3 3 Import a License 4 4 Examine the Tower Dashboard 6 5 The Setup
VMware Identity Manager Cloud Deployment. Modified on 01 OCT 2017 VMware Identity Manager
 VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
Microsoft Azure for AWS Experts
 Microsoft Azure for AWS Experts OD40390B; On-Demand, Video-based Course Description This course provides an in-depth discussion and practical hands-on training of Microsoft Azure Infrastructure Services
Microsoft Azure for AWS Experts OD40390B; On-Demand, Video-based Course Description This course provides an in-depth discussion and practical hands-on training of Microsoft Azure Infrastructure Services
Application Visibility and Analytics SE Remote Demo Platform Information
 Application Visibility and Analytics SE Remote Demo Platform Information Table of Contents Introduction... 2 How to obtain access to the Demo?... 3 Demo Overview... 6 Network Diagram... 6 Demo Flow...
Application Visibility and Analytics SE Remote Demo Platform Information Table of Contents Introduction... 2 How to obtain access to the Demo?... 3 Demo Overview... 6 Network Diagram... 6 Demo Flow...
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure
 Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and
