Table of Contents. Contents iii
|
|
|
- Bethanie Pitts
- 6 years ago
- Views:
Transcription
1 Table of Contents Contents iii Foreword by Gerald Combs, Creator of Wireshark... xxvii Preface... xxix About This Book... xxxi Who is This Book For?... xxxi How is This Book Organized?... xxxi How Can I Find Something Fast in This Book?... xxxiii What Do Those Icons Mean?... xxxiii Trace Files Used in This Book (.pcapng Format)... xxxiii What s Online at xxxiv Which Version of Wireshark Did You Use to Write This Book?... xxxiv Which WCNA Exam Version Does This Book Cover?... xxxiv How Can I Submit Comments/Change Requests for This Book?... xxxv Wireshark Certified Network Analyst Program Overview... xxxv Why Should I Pursue the Wireshark CNA Certification?... xxxv How Do I Earn the Wireshark CNA Certified Status?... xxxv Wireshark CNA Exam Objectives... xxxvi Wireshark University and Wireshark University Training Partners... xxxvi Schedule Customized Onsite/Web-Based Training... xxxvi Chapter 1: The World of Network Analysis... 1 Define Network Analysis... 2 Follow an Analysis Example... 3 Walk-Through of a Troubleshooting Session... 6 Walk-Through of a Typical Security Scenario (aka Network Forensics)... 8 Troubleshooting Tasks for the Network Analyst... 9 Security Tasks for the Network Analyst Optimization Tasks for the Network Analyst Application Analysis Tasks for the Network Analyst Understand Security Issues Related to Network Analysis Define Policies Regarding Network Analysis Files Containing Network Traffic Should be Secured Protect Your Network against Unwanted Sniffers Be Aware of Legal Issues of Listening to Network Traffic Overcome the Needle in the Haystack Issue Review a Checklist of Analysis Tasks Understand Network Traffic Flows Switching Overview Routing Overview Proxy, Firewall and NAT/PAT Overview Other Technologies that Affect Packets Warnings about Smarter Infrastructure Devices Launch an Analysis Session... 19
2 iv Contents Case Study: Pruning the Puke Case Study: The Securely Invisible Network Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 2: Introduction to Wireshark Wireshark Creation and Maintenance Obtain the Latest Version of Wireshark Compare Wireshark Release and Development Versions Thanks to the Wireshark Developers! Calculating the Value of the Wireshark Code Report a Wireshark Bug or Submit an Enhancement Following Export Regulations Identifying Products that Leverage Wireshark s Capabilities Capture Packets on Wired or Wireless Networks Libpcap WinPcap AirPcap Open Various Trace File Types Understand How Wireshark Processes Packets Core Engine Dissectors and Plugins and Display Filters GIMP Toolkit (GTK+) Use the Start Page The Capture Area The Files Area The Online Area The Capture Help Area Identify the Nine GUI Elements Add the Wireshark Version to the Title Bar Displaying the Wireless Toolbar (Windows Only) Opening and Closing Panes Interpreting the Status Bar Navigate Wireshark s Main Menu File Menu Items Edit Menu Items View Menu Items Go Menu Items Capture Menu Items Analyze Menu Items Statistics Menu Items Telephony Menu Items Tools Menu Items Internals Menu Items Help Menu Items... 74
3 Use the Main Toolbar for Efficiency Toolbar Icon Definitions Focus Faster with the Filter Toolbar Make the Wireless Toolbar Visible Work Faster Using Right-Click Functionality Right Click Edit or Add Packet Comment Right Click Copy Right Click Apply As Column Right Click Wiki Protocol Page (Packet Details Pane) Right Click Filter Field Reference (Packet Details Pane) Right Click Resolve Name (Packet Details Pane) Right Click Protocol Preferences Sign Up for the Wireshark Mailing Lists Join ask.wireshark.org! Know Your Key Resources Get Some Trace Files Case Study: Detecting Database Death Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 3: Capture Traffic Know Where to Tap Into the Network Run Wireshark Locally Portable Wireshark Wireshark U Capture Traffic on Switched Networks Use a Simple Hub on Half-Duplex Networks Use a Test Access Port (TAP) on Full-Duplex Networks Using Analyzer Agents for Remote Capture Set up Port Spanning/Port Mirroring on a Switch Example of Span Commands Spanning VLANs Analyze Routed Networks Analyze Wireless Networks Monitor Mode Native Adapter Capture Issues Capture at Two Locations (Dual Captures) Select the Right Capture Interface Capture on Multiple Adapters Simultaneously Interface Details (Windows Only) Capture Traffic Remotely Configuration Parameters for Remote Capture with rpcapd.exe Remote Capture: Active and Passive Mode Configurations Save and Use Remote Capture Configurations Contents v
4 vi Contents Automatically Save Packets to One or More Files Create File Sets for Faster Access Use a Ring Buffer to Limit the Number of Files Saved Define an Automatic Stop Criteria Optimize Wireshark to Avoid Dropping Packets Consider a Dedicated Analyzer Laptop Capture Options for Optimization Display Options for Optimization Conserve Memory with Command-Line Capture Case Study: Dual Capture Points the Finger Case Study: Capturing Traffic at Home Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 4: Create and Apply Capture Filters The Purpose of Capture Filters Apply a Capture Filter to an Interface Build Your Own Set of Capture Filters Identifiers Qualifiers Filter by a Protocol Filter Incoming Connection Attempts Create MAC/IP Address or Host Name Capture Filters Use a My MAC Capture Filter for Application Analysis Filter Your Traffic Out of a Trace File (Exclusion Filter) Capture One Application s Traffic Only Use Operators to Combine Capture Filters Create Capture Filters to Look for Byte Values Manually Edit the Capture Filters File Sample cfilters File Share Capture Filters with Others Case Study: Kerberos UDP to TCP Issue Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 5: Define Global and Personal Preferences Find Your Configuration Folders Set Global and Personal Configurations Customize Your User Interface Settings File Open Dialog Behavior Maximum List Entries Pane Configurations Columns
5 Contents vii Define Your Capture Preferences Select a Default Interface for Faster Capture Launch Enable Promiscuous Mode to Analyze Other Hosts Traffic The Future Trace File Format is Here: pcap-ng See the Traffic in Real Time Automatically Scroll During Capture Automatically Resolve IP and MAC Names Resolve Hardware Addresses (MAC Name Resolution) Resolve IP Addresses (Network Name Resolution) Plot IP Addresses on a World Map with GeoIP Resolve Port Numbers (Transport Name Resolution) Resolve SNMP Information Configure Filter Expressions Configure Statistics Settings Define ARP, TCP, HTTP/HTTPS and Other Protocol Settings Detect Duplicate IP Addresses and ARP Storms Define How Wireshark Handles TCP Traffic Set Additional Ports for HTTP and HTTPS Dissection Enhance VoIP Analysis with RTP Settings Configure Wireshark to Decrypt SSL Traffic Configure Protocol Settings with Right-Click Case Study: Non-Standard Web Server Setup Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 6: Colorize Traffic Use Colors to Differentiate Traffic Types Disable One or More Coloring Rules Share and Manage Coloring Rules Identify Why a Packet is a Certain Color Create a Butt Ugly Coloring Rule for HTTP Errors Color Conversations to Distinguish Them Temporarily Mark Packets of Interest Alter Stream Reassembly Coloring Case Study: Colorizing SharePoint Connections During Login Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 7: Define Time Values and Interpret Summaries Use Time to Identify Network Problems Understand How Wireshark Measures Packet Time Choose the Ideal Time Display Format Deal with Timestamp Accuracy and Resolution Issues
6 viii Contents Send Trace Files Across Time Zones Identify Delays with Time Values Create Additional Time Columns Measure Packet Arrival Times with a Time Reference Identify Client, Server and Path Delays Calculate End-to-End Path Delays Locate Slow Server Responses Spot Overloaded Clients View a Summary of Traffic Rates, Packet Sizes and Overall Bytes Transferred Compare Up to Three Traffic Types in a Single Summary Window Compare Summary Information for Two or More Trace Files Case Study: Time Column Spots Delayed ACKs Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 8: Interpret Basic Trace File Statistics Launch Wireshark Statistics Identify Network Protocols and Applications Protocol Settings Can Affect Your Results Identify the Most Active Conversations List Endpoints and Map Them on the Earth Spot Suspicious Targets with GeoIP List Conversations or Endpoints for Specific Traffic Types Evaluate Packet Lengths List All IPv4/IPv6 Addresses in the Traffic List All Destinations in the Traffic List UDP and TCP Usage Analyze UDP Multicast Streams Graph the Flow of Traffic Gather Your HTTP Statistics Examine All WLAN Statistics Case Study: Application Analysis: Aptimize Website Accelerator Case Study: Finding VoIP Quality Issues Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 9: Create and Apply Display Filters Understand the Purpose of Display Filters Create Display Filters Using Auto-Complete Apply Saved Display Filters Use Expressions for Filter Assistance
7 Make Display Filters Quickly Using Right-Click Filtering Apply as Filter Prepare a Filter Copy As Filter Filter on Conversations and Endpoints Filter on the Protocol Hierarchy Window Understand Display Filter Syntax Combine Display Filters with Comparison Operators Alter Display Filter Meaning with Parentheses Filter on the Existence of a Field Filter on Specific Bytes in a Packet Find Key Words in Upper or Lower Case More Interesting Regex Filters Let Wireshark Catch Display Filter Mistakes Use Display Filter Macros for Complex Filtering Avoid Common Display Filter Mistakes Manually Edit the dfilters File Case Study: Using Filters and Graphs to Solve Database Issues Case Study: The Chatty Browser Case Study: Catching Viruses and Worms Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 10: Follow Streams and Reassemble Data The Basics of Traffic Reassembly Follow and Reassemble UDP Conversations Follow and Reassemble TCP Conversations Identify Common File Types Reassemble an FTP File Transfer Follow and Reassemble SSL Conversations Reassemble an SMB Transfer Case Study: Unknown Hosts Identified Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 11: Customize Wireshark Profiles Customize Wireshark with Profiles Create a New Profile Share Profiles Create a Troubleshooting Profile Create a Corporate Profile Create a WLAN Profile Create a VoIP Profile Create a Security Profile Contents ix
8 x Contents Case Study: Customizing Wireshark for the Customer Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 12: Annotate, Save, Export and Print Packets Annotate a Packet or an Entire Trace File Save Filtered, Marked and Ranges of Packets Export Packet Content for Use in Other Programs Export SSL Keys Save Conversations, Endpoints, IO Graphs and Flow Graph Information Export Packet Bytes Case Study: Saving Subsets of Traffic to Isolate Problems Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 13: Use Wireshark s Expert System Let Wireshark s Expert Information Guide You Launch Expert Info Quickly Colorize Expert Info Elements Filter on TCP Expert Information Elements Understand TCP Expert Information What Triggers TCP Retransmissions? What Triggers Previous Segment Lost? What Triggers ACKed Lost Packet? What Triggers Keep Alive? What Triggers Duplicate ACK? What Triggers Zero Window? What Triggers Zero Window Probe? What Triggers Zero Window Probe ACK? What Triggers Keep Alive ACK? What Triggers Out-of-Order? What Triggers Fast Retransmission? What Triggers Window Update? What Triggers Window is Full? What Triggers TCP Ports Reused? What Triggers 4 NOP in a Row? Case Study: Expert Info Catches Remote Access Headaches Summary Practice What You ve Learned Review Questions Answers to Review Questions
9 Chapter 14: TCP/IP Analysis Overview TCP/IP Functionality Overview When Everything Goes Right Follow the Multi-Step Resolution Process Step 1: Port Number Resolution Step 2: Network Name Resolution (Optional) Step 3: Route Resolution When the Target is Local Step 4: Local MAC Address Resolution Step 5: Route Resolution When the Target is Remote Step 6: Local MAC Address Resolution for a Gateway Build the Packet Case Study: Absolving the Network from Blame Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 15: Analyze Domain Name System (DNS) Traffic The Purpose of DNS Analyze Normal DNS Queries/Responses Analyze DNS Problems Dissect the DNS Packet Structure Transaction ID Flags Question Count Answer Resource Record (RR) Count Authority RRs Count Additional RRs Count Queries Answer RRs Authority RRs Additional RRs Resource Record Time to Live (TTL) Value Filter on DNS/MDNS Traffic Case Study: DNS Killed Web Browsing Performance Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 16: Analyze Address Resolution Protocol (ARP) Traffic Identify the Purpose of ARP Analyze Normal ARP Requests/Responses Analyze Gratuitous ARPs Analyze ARP Problems Contents xi
10 xii Contents Dissect the ARP Packet Structure Hardware Type Protocol Type Length of Hardware Address Length of Protocol Address Opcode Sender s Hardware Address Sender s Protocol Address Target Hardware Address Target Protocol Address Filter on ARP Traffic Case Study: Death by ARP Case Study: The Tale of the Missing ARP Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 17: Analyze Internet Protocol (IPv4/IPv6) Traffic Identify the Purpose of IP Analyze Normal IPv4 Traffic Analyze IPv4 Problems Dissect the IPv4 Packet Structure Version Field Header Length Field Differentiated Services Field and Explicit Congestion Notification Total Length Field Identification Field Flags Field Fragment Offset Field Time to Live Field Protocol Field Header Checksum Field IPv4 Source Address Field IPv4 Destination Address Field Options Field IPv4 Broadcast/Multicast Traffic An Introduction to IPv6 Traffic Dissect the IPv6 Packet Structure Version Field Traffic Class Fields (DiffServ, ECT and ECN-CE) Flow Label Field Payload Length Field Next Header Field Hop Limit Field Source IPv6 Address Field Destination IPv6 Address Field
11 Contents xiii Basic IPv6 Addressing Auto Configuration Mode (no DHCP Server) (M=0 and O=0) DHCPv6 Stateful Mode (M=1) DHCPv6 Stateless Mode (M=0 and O=1) to4 Tunneling (IPv6 Tunneled Inside IPv4) Teredo Intra-Site Automatic Tunnel Addressing Protocol (ISATAP) Sanitize Your IP Addresses in Trace Files Set Your IPv4 Protocol Preferences Reassemble Fragmented IP Datagrams Enable GeoIP Lookups Interpret the Reserved Flag as a Security Flag (RFC 3514) <g> Troubleshoot Encrypted Communications Filter on IPv4 Traffic Filter on IPv6 Traffic Case Study: Everyone Blamed the Router Case Study: It s Not the Network s Problem! Case Study: IPv6 Addressing Mayhem Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 18: Analyze Internet Control Message Protocol (ICMPv4/ICMPV6) Traffic The Purpose of ICMP Analyze Normal ICMP Traffic Analyze ICMP Problems Dissect the ICMP Packet Structure Type Code Checksum Basic ICMPv6 Functionality Filter on ICMP and ICMPv6 Traffic Case Study: The Dead-End Router Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 19: Analyze User Datagram Protocol (UDP) Traffic The Purpose of UDP Analyze Normal UDP Traffic Analyze UDP Problems
12 xiv Contents Dissect the UDP Packet Structure Source Port Field Destination Port Field Length Field Checksum Field Filter on UDP Traffic Case Study: Troubleshooting Time Synchronization Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 20: Analyze Transmission Control Protocol (TCP) Traffic The Purpose of TCP Analyze Normal TCP Communications The Establishment of TCP Connections When TCP-based Services are Refused The Termination of TCP Connections How TCP Tracks Packets Sequentially How TCP Recovers from Packet Loss Improve Packet Loss Recovery with Selective Acknowledgments Understand TCP Flow Control Understand Nagling and Delayed ACKs Analyze TCP Problems Dissect the TCP Packet Structure Source Port Field Destination Port Field Stream Index [Wireshark Field] Sequence Number Field Next Expected Sequence Number [Wireshark Field] Acknowledgment Number Field Data Offset Field Flags Field Window Field Checksum Field Urgent Pointer Field TCP Options Area (Optional) Filter on TCP Traffic Set TCP Protocol Preferences Validate the TCP Checksum if Possible Allow Subdissector to Reassemble TCP Streams Analyze TCP Sequence Numbers Relative Sequence Numbers Window Scaling is Calculated Automatically Track Number of Bytes in Flight Try Heuristic Sub-Dissectors First Ignore TCP Timestamps in Summary Calculate Conversation Timestamps
13 Contents xv Case Study: Connections Require Four Attempts Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 21: Graph IO Rates and TCP Trends Use Graphs to View Trends Generate Basic IO Graphs Filter IO Graphs Coloring Styles and Layers X and Y Axis Smoothing Print Your IO Graph Generate Advanced IO Graphs SUM(*) Calc MIN(*), AVG(*) and MAX(*) Calc Values COUNT(*) Calc LOAD(*) Calc Compare Traffic Trends in IO Graphs Graph Round Trip Time Graph Throughput Rates Graph TCP Sequence Numbers over Time Interpret TCP Window Size Issues Interpret Packet Loss, Duplicate ACKs and Retransmissions Case Study: Watching Performance Levels Drop Case Study: Graphing RTT to the Corporate Office Case Study: Testing QoS Policies Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 22: Analyze Dynamic Host Configuration Protocol (DHCPv4/DHCPv6) Traffic The Purpose of DHCP Analyze Normal DHCP Traffic Analyze DHCP Problems Dissect the DHCP Packet Structure Message Type Hardware Type Hardware Length Hops Transaction ID Seconds Elapsed BOOTP Flags Client IP Address Your (Client) IP Address
14 xvi Contents Next Server IP Address Relay Agent IP Address Client MAC Address Server Host Name Boot File Name Magic Cookie Option An Introduction to DHCPv Display BOOTP-DHCP Statistics Filter on DHCP/DHCPv6 Traffic Case Study: Declining Clients Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 23: Analyze Hypertext Transfer Protocol (HTTP) Traffic The Purpose of HTTP Analyze Normal HTTP Communications Analyze HTTP Problems Dissect HTTP Packet Structures HTTP Methods Host Request Modifiers Filter on HTTP or HTTPS Traffic Export HTTP Objects Display HTTP Statistics HTTP Load Distribution HTTP Packet Counter HTTP Requests Graph HTTP Traffic Flows Choose Packets Choose Flow Type Choose Node Address Type Set HTTP Preferences Analyze HTTPS Communications Analyze SSL/TLS Handshake Analyze TLS Encrypted Alerts Decrypt HTTPS Traffic Export SSL Keys Case Study: HTTP Proxy Problems Summary Practice What You ve Learned Review Questions Answers to Review Questions
15 Contents xvii Chapter 24: Analyze File Transfer Protocol (FTP) Traffic The Purpose of FTP Analyze Normal FTP Communications Analyze Passive Mode Connections Analyze Active Mode Connections Analyze FTP Problems Dissect the FTP Packet Structure Filter on FTP Traffic Reassemble FTP Traffic Case Study: Secret FTP Communications Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 25: Analyze Traffic The Purpose of POP Analyze Normal POP Communications Analyze POP Problems Dissect the POP Packet Structure Filter on POP Traffic The Purpose of SMTP Analyze Normal SMTP Communications Analyze SMTP Problems Dissect the SMTP Packet Structure Filter on SMTP Traffic Case Study: SMTP Problem Scan2 Job Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 26: Introduction to (WLAN) Analysis Analyze WLAN Traffic Analyze Signal Strength and Interference Capture WLAN Traffic Compare Monitor Mode vs. Promiscuous Mode Select the Wireless Interface Set Up WLAN Decryption Select to Prepend Radiotap or PPI Headers Compare Signal Strength and Signal-to-Noise Ratios Understand Traffic Basics Data Frames Management Frames Control Frames Analyze Normal Communications Dissect the Frame Structure
16 xviii Contents Filter on All WLAN Traffic Analyze Frame Control Types and Subtypes Customize Wireshark for WLAN Analysis Case Study: Cruddy Barcode Communications Case Study: Cooking the WLAN Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 27: Introduction to Voice over IP (VoIP) Analysis Understand VoIP Traffic Flows Session Bandwidth and RTP Port Definition Analyze VoIP Problems Packet Loss Jitter Examine SIP Traffic SIP Commands SIP Response Codes Examine RTP Traffic Play Back VoIP Conversations RTP Player Marker Definitions Create a VoIP Profile Filter on VoIP Traffic Case Study: Lost VoIP Tones Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 28: Baseline Normal Traffic Patterns Understand the Importance of Baselining Baseline Broadcast and Multicast Types and Rates Baseline Protocols and Applications Baseline Boot up Sequences Baseline Login/Logout Sequences Baseline Traffic during Idle Times Baseline Application Launch Sequences and Key Tasks Baseline Web Browsing Sessions Baseline Name Resolution Sessions Baseline Throughput Tests Baseline Wireless Connectivity Baseline VoIP Communications Case Study: Login Log Jam Case Study: Solving SAN Disconnects Summary Practice What You ve Learned Review Questions Answers to Review Questions
17 Contents xix Chapter 29: Find the Top Causes of Performance Problems Troubleshoot Performance Problems Identify High Latency Times Filter on Arrival Times Filter on the Delta Times Filter on the Time since Reference or First Packet Filter on TCP Conversation Times Point to Slow Processing Times Practice Working with Time Issues Find the Location of Packet Loss Watch Signs of Misconfigurations Analyze Traffic Redirections Watch for Small Payload Sizes Look for Congestion Identify Application Faults Note Any Name Resolution Faults An Important Note about Analyzing Performance Problems Case Study: One-Way Problems Case Study: The Perfect Storm of Network Problems Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 30: Network Forensics Overview Compare Host vs. Network Forensics Gather Evidence Avoid Detection Handle Evidence Properly Recognize Unusual Traffic Patterns Color Unusual Traffic Patterns Check Out Complementary Forensic Tools Case Study: SSL/TLS Vulnerability Studied Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 31: Detect Scanning and Discovery Processes The Purpose of Discovery and Reconnaissance Processes Detect ARP Scans (aka ARP Sweeps) Detect ICMP Ping Sweeps Detect Various Types of TCP Port Scans TCP Half-Open Scan (aka Stealth Scan ) TCP Full Connect Scan Null Scans Xmas Scan
18 xx Contents FIN Scan ACK Scan Detect UDP Port Scans Detect IP Protocol Scans Understand Idle Scans Know Your ICMP Types and Codes Try These Nmap Scan Commands Analyze Traceroute Path Discovery Detect Dynamic Router Discovery Understand Application Mapping Processes Use Wireshark for Passive OS Fingerprinting Detect Active OS Fingerprinting Identify Attack Tools Identify Spoofed Addresses in Scans Case Study: Learning the Conficker Lesson Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 32: Analyze Suspect Traffic What is Suspect Traffic? Identify Vulnerabilities in the TCP/IP Resolution Processes Port Resolution Vulnerabilities Name Resolution Process Vulnerabilities MAC Address Resolution Vulnerabilities Route Resolution Vulnerabilities Identify Unacceptable Traffic Find Maliciously Malformed Packets Identify Invalid or Dark Destination Addresses Differentiate Between Flooding and Denial of Service Traffic Find Clear Text Passwords and Data Identify Phone Home Traffic Catch Unusual Protocols and Applications Locate Route Redirection that Uses ICMP Catch ARP Poisoning Catch IP Fragmentation and Overwriting Spot TCP Splicing Watch Other Unusual TCP Traffic Identify Password Cracking Attempts Build Filters and Coloring Rules from IDS Rules Header Signatures Sequence Signatures Payload Signatures Sample Wireshark Filters from IDS/IPS Rules
19 Contents xxi Case Study: The Flooding Host Case Study: Catching Keylogging Traffic Case Study: Passively Finding Malware Summary Practice What You ve Learned Review Questions Answers to Review Questions Chapter 33: Effective Use of Command-Line Tools Understand the Power of Command-Line Tools Use Wireshark.exe (Command-Line Launch) Wireshark Syntax Customize Wireshark s Launch Capture Traffic with Tshark Tshark Syntax View Tshark Statistics Gather Host Name with Tshark Examine Service Response Times (SRT) with Tshark Tshark Examples Dealing with Bug List Trace File Details with Capinfos Capinfos Syntax Capinfos Examples Edit Trace Files with Editcap Editcap Syntax Editcap Examples Merge Trace Files with Mergecap Mergecap Syntax Mergecap Examples Convert Text with Text2pcap Text2pcap Syntax Text2pcap Examples Capture Traffic with Dumpcap Dumpcap Syntax Dumpcap Examples Understand Rawshark Rawshark Syntax Case Study: Getting GETS and a Suspect Summary Practice What You ve Learned Review Questions Answers to Review Questions
20 xxii Contents Appendix A: Resources on the Book Website Video Starters Chanalyzer Pro/Wi-Spy Recordings (.wsx Files) MaxMind GeoIP Database Files (.dat Files) PhoneFactor SSL/TLS Vulnerabilities Documents/Trace Files Wireshark Customized Profiles Practice Trace Files Index
Part 1: Training Project Information (Required for Formal Quotes) Online Live On-Demand (All Access Pass Subscriptions) Other
 Course Estimator and Quote Request Form Ready to train your team on Wireshark, TCP/IP analysis, troubleshooting and network forensics? Complete Part 1 of this Cost Estimator and Quote Request Form to determine
Course Estimator and Quote Request Form Ready to train your team on Wireshark, TCP/IP analysis, troubleshooting and network forensics? Complete Part 1 of this Cost Estimator and Quote Request Form to determine
Wireshark 101 Essential Skills for Network Analysis 2 nd Edition
 Wireshark 101 Essential Skills for Network Analysis 2 nd Edition Always ensure you have proper authorization before you listen to and capture network traffic. Protocol Analysis Institute, Inc 59 Damonte
Wireshark 101 Essential Skills for Network Analysis 2 nd Edition Always ensure you have proper authorization before you listen to and capture network traffic. Protocol Analysis Institute, Inc 59 Damonte
Wireshark 101 Essential Skills for Network Analysis 1 st Edition
 Wireshark 101 Essential Skills for Network Analysis 1 st Edition Always ensure you have proper authorization before you listen to and capture network traffic. Protocol Analysis Institute, Inc 5339 Prospect
Wireshark 101 Essential Skills for Network Analysis 1 st Edition Always ensure you have proper authorization before you listen to and capture network traffic. Protocol Analysis Institute, Inc 5339 Prospect
Introduction to Troubleshooting TCP/IP Networks with Wireshark
 Introduction to Troubleshooting TCP/IP Networks with Wireshark Course WIRE-1B 5 Days Instructor-led, Hands-on Introduction In this hands-on, instructor-led, five-day course, you will receive in-depth training
Introduction to Troubleshooting TCP/IP Networks with Wireshark Course WIRE-1B 5 Days Instructor-led, Hands-on Introduction In this hands-on, instructor-led, five-day course, you will receive in-depth training
Brief Contents. Acknowledgments... xv. Introduction...xvii. Chapter 1: Packet Analysis and Network Basics Chapter 2: Tapping into the Wire...
 Brief Contents Acknowledgments... xv Introduction...xvii Chapter 1: Packet Analysis and Network Basics... 1 Chapter 2: Tapping into the Wire... 17 Chapter 3: Introduction to Wireshark... 37 Chapter 4:
Brief Contents Acknowledgments... xv Introduction...xvii Chapter 1: Packet Analysis and Network Basics... 1 Chapter 2: Tapping into the Wire... 17 Chapter 3: Introduction to Wireshark... 37 Chapter 4:
Advanced Network Troubleshooting Using Wireshark (Hands-on)
 Advanced Network Troubleshooting Using Wireshark (Hands-on) Description This course is a continuation of the "Basic Network Troubleshooting Using Wireshark" course, and comes to provide the participants
Advanced Network Troubleshooting Using Wireshark (Hands-on) Description This course is a continuation of the "Basic Network Troubleshooting Using Wireshark" course, and comes to provide the participants
CONTENTS IN DETAIL ACKNOWLEDGMENTS INTRODUCTION 1 PACKET ANALYSIS AND NETWORK BASICS 1 2 TAPPING INTO THE WIRE 17 3 INTRODUCTION TO WIRESHARK 35
 CONTENTS IN DETAIL ACKNOWLEDGMENTS xv INTRODUCTION xvii Why This Book?...xvii Concepts and Approach...xviii How to Use This Book... xix About the Sample Capture Files... xx The Rural Technology Fund...
CONTENTS IN DETAIL ACKNOWLEDGMENTS xv INTRODUCTION xvii Why This Book?...xvii Concepts and Approach...xviii How to Use This Book... xix About the Sample Capture Files... xx The Rural Technology Fund...
NETWORK PACKET ANALYSIS PROGRAM
 NETWORK PACKET ANALYSIS PROGRAM Duration: 3 days (21 hours) Mode: 1. Instructor Led Class room Training and Labs 2. Online In this hands-on course, you will receive in-depth training on Protocol analysis
NETWORK PACKET ANALYSIS PROGRAM Duration: 3 days (21 hours) Mode: 1. Instructor Led Class room Training and Labs 2. Online In this hands-on course, you will receive in-depth training on Protocol analysis
Get Certified on the World s Foremost Network Protocol Analyzer
 Wireshark is downloaded over 500,000 per month on average Wireshark University Get Certified on the World s Foremost Network Protocol Analyzer Exam Version 102.1 (updated 07/02/2012) Welcome to Wireshark
Wireshark is downloaded over 500,000 per month on average Wireshark University Get Certified on the World s Foremost Network Protocol Analyzer Exam Version 102.1 (updated 07/02/2012) Welcome to Wireshark
Course List. December 2010
 Course List December 2010 List of Courses Syllabus for 'AAP-Core 1-Wireshark Functions & TCP/IP'... 1 Syllabus for 'AAP-Core 2-Troubleshoot/Secure Networks'... 2 Syllabus for 'AAP-CS41 Wireshark Jumpstart
Course List December 2010 List of Courses Syllabus for 'AAP-Core 1-Wireshark Functions & TCP/IP'... 1 Syllabus for 'AAP-Core 2-Troubleshoot/Secure Networks'... 2 Syllabus for 'AAP-CS41 Wireshark Jumpstart
Network Traffic Analysis - Course Outline
 Network Traffic Analysis - Course Outline This course is designed for system/network administrations with an overall understanding of computer networking. At the end of this course, students will have
Network Traffic Analysis - Course Outline This course is designed for system/network administrations with an overall understanding of computer networking. At the end of this course, students will have
TCP /IP Fundamentals Mr. Cantu
 TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
TCP /IP Fundamentals Mr. Cantu OSI Model and TCP/IP Model Comparison TCP / IP Protocols (Application Layer) The TCP/IP subprotocols listed in this layer are services that support a number of network functions:
Wireshark 101 Course Set
 Wireshark 101 Course Set Essential Skills for Network Analysis Nine separate online courses focusing on essential network analysis skills. These courses are based on the best-selling Wireshark 101: Essential
Wireshark 101 Course Set Essential Skills for Network Analysis Nine separate online courses focusing on essential network analysis skills. These courses are based on the best-selling Wireshark 101: Essential
Internet Layers. Physical Layer. Application. Application. Transport. Transport. Network. Network. Network. Network. Link. Link. Link.
 Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Internet Layers Application Application Transport Transport Network Network Network Network Link Link Link Link Ethernet Fiber Optics Physical Layer Wi-Fi ARP requests and responses IP: 192.168.1.1 MAC:
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Foreword xxiii Preface xxvii IPv6 Rationale and Features
 Contents Foreword Preface xxiii xxvii 1 IPv6 Rationale and Features 1 1.1 Internet Growth 1 1.1.1 IPv4 Addressing 1 1.1.2 IPv4 Address Space Utilization 3 1.1.3 Network Address Translation 5 1.1.4 HTTP
Contents Foreword Preface xxiii xxvii 1 IPv6 Rationale and Features 1 1.1 Internet Growth 1 1.1.1 IPv4 Addressing 1 1.1.2 IPv4 Address Space Utilization 3 1.1.3 Network Address Translation 5 1.1.4 HTTP
Hands-On Hacking Techniques 101
 Hands-On Hacking Techniques 101 University of Petra Faculty of Information Technology Department of Computer Networking 2014 Dr. Ali Al-Shemery bsc [at] ashemery [dot] com Dissecting Network Traffic using
Hands-On Hacking Techniques 101 University of Petra Faculty of Information Technology Department of Computer Networking 2014 Dr. Ali Al-Shemery bsc [at] ashemery [dot] com Dissecting Network Traffic using
Chapter 09 Network Protocols
 Chapter 09 Network Protocols Copyright 2011, Dr. Dharma P. Agrawal and Dr. Qing-An Zeng. All rights reserved. 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems
Chapter 09 Network Protocols Copyright 2011, Dr. Dharma P. Agrawal and Dr. Qing-An Zeng. All rights reserved. 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems
So What is WireShark?
 Drinking from the network hose So What is WireShark? Packet sniffer/protocol analyzer Open Source Network Tool Latest version of the ethereal tool 1 Source: www.fcc.gov A packet is a chunk of data enclosed
Drinking from the network hose So What is WireShark? Packet sniffer/protocol analyzer Open Source Network Tool Latest version of the ethereal tool 1 Source: www.fcc.gov A packet is a chunk of data enclosed
Networks Fall This exam consists of 10 problems on the following 13 pages.
 CSCI 466 Final Networks Fall 2011 Name: This exam consists of 10 problems on the following 13 pages. You may use your two- sided hand- written 8 ½ x 11 note sheet during the exam and a calculator. No other
CSCI 466 Final Networks Fall 2011 Name: This exam consists of 10 problems on the following 13 pages. You may use your two- sided hand- written 8 ½ x 11 note sheet during the exam and a calculator. No other
Layer 4: UDP, TCP, and others. based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers
 Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Layer 4: UDP, TCP, and others based on Chapter 9 of CompTIA Network+ Exam Guide, 4th ed., Mike Meyers Concepts application set transport set High-level, "Application Set" protocols deal only with how handled
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
Scanning. Course Learning Outcomes for Unit III. Reading Assignment. Unit Lesson UNIT III STUDY GUIDE
 UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
DKT 224/3 LAB 2 NETWORK PROTOCOL ANALYZER DATA COMMUNICATION & NETWORK SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK
 DKT 224/3 DATA COMMUNICATION & NETWORK LAB 2 NETWORK PROTOCOL ANALYZER SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK Lab #2 2 Lab #2 : Network Protocol Analyzer (Sniffing and Identify Protocol used
DKT 224/3 DATA COMMUNICATION & NETWORK LAB 2 NETWORK PROTOCOL ANALYZER SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK Lab #2 2 Lab #2 : Network Protocol Analyzer (Sniffing and Identify Protocol used
Guide To TCP/IP, Second Edition UDP Header Source Port Number (16 bits) IP HEADER Protocol Field = 17 Destination Port Number (16 bit) 15 16
 Guide To TCP/IP, Second Edition Chapter 5 Transport Layer TCP/IP Protocols Objectives Understand the key features and functions of the User Datagram Protocol (UDP) Explain the mechanisms that drive segmentation,
Guide To TCP/IP, Second Edition Chapter 5 Transport Layer TCP/IP Protocols Objectives Understand the key features and functions of the User Datagram Protocol (UDP) Explain the mechanisms that drive segmentation,
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin,
 Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Fundamental Questions to Answer About Computer Networking, Jan 2009 Prof. Ying-Dar Lin, ydlin@cs.nctu.edu.tw Chapter 1: Introduction 1. How does Internet scale to billions of hosts? (Describe what structure
Chapter 2 - Part 1. The TCP/IP Protocol: The Language of the Internet
 Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Chapter 2 - Part 1 The TCP/IP Protocol: The Language of the Internet Protocols A protocol is a language or set of rules that two or more computers use to communicate 2 Protocol Analogy: Phone Call Parties
Introduction to Computer Networks. CS 166: Introduction to Computer Systems Security
 Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Defining Networks with the OSI Model. Module 2
 Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Concept Questions Demonstrate your knowledge of these concepts by answering the following questions in the space that is provided.
 223 Chapter 19 Inter mediate TCP The Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols was developed as part of the research that the Defense Advanced Research Projects Agency
223 Chapter 19 Inter mediate TCP The Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols was developed as part of the research that the Defense Advanced Research Projects Agency
About this Troubleshooting Checklist
 Troubleshooting Checklist Based on the book Troubleshooting with Wireshark Author: Laura Chappell, Founder of Wireshark University Foreword: Gerald Combs, Creator of Wireshark Editor: Jim Aragon, Wireshark
Troubleshooting Checklist Based on the book Troubleshooting with Wireshark Author: Laura Chappell, Founder of Wireshark University Foreword: Gerald Combs, Creator of Wireshark Editor: Jim Aragon, Wireshark
Index. 913 Index. 4 NOPs in a Row, 8, 331, 481, 718, See also Expert Info See WLAN analysis
 913 Index Index 4 NOPs in a Row, 8, 331, 481, 718, See also Expert Info 802.11. See WLAN analysis A accelerator keys, 40, 47 ACKed Lost Segment, 896, See also Expert Info Active Directory Migration Tool
913 Index Index 4 NOPs in a Row, 8, 331, 481, 718, See also Expert Info 802.11. See WLAN analysis A accelerator keys, 40, 47 ACKed Lost Segment, 896, See also Expert Info Active Directory Migration Tool
ETSF05/ETSF10 Internet Protocols Network Layer Protocols
 ETSF05/ETSF10 Internet Protocols Network Layer Protocols 2016 Jens Andersson Agenda Internetworking IPv4/IPv6 Framentation/Reassembly ICMPv4/ICMPv6 IPv4 to IPv6 transition VPN/Ipsec NAT (Network Address
ETSF05/ETSF10 Internet Protocols Network Layer Protocols 2016 Jens Andersson Agenda Internetworking IPv4/IPv6 Framentation/Reassembly ICMPv4/ICMPv6 IPv4 to IPv6 transition VPN/Ipsec NAT (Network Address
Chapter 12 Network Protocols
 Chapter 12 Network Protocols 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems Interconnection (OSI) Transmission Control Protocol/Internetworking Protocol (TCP/IP)
Chapter 12 Network Protocols 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems Interconnection (OSI) Transmission Control Protocol/Internetworking Protocol (TCP/IP)
ECE4110 Internetwork Programming. Introduction and Overview
 ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition. Chapter 2 Investigating Network Traffic
 Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
Computer Networks. More on Standards & Protocols Quality of Service. Week 10. College of Information Science and Engineering Ritsumeikan University
 Computer Networks More on Standards & Protocols Quality of Service Week 10 College of Information Science and Engineering Ritsumeikan University Introduction to Protocols l A protocol is a set of rules
Computer Networks More on Standards & Protocols Quality of Service Week 10 College of Information Science and Engineering Ritsumeikan University Introduction to Protocols l A protocol is a set of rules
TCP/IP Networking. Training Details. About Training. About Training. What You'll Learn. Training Time : 9 Hours. Capacity : 12
 TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
TCP/IP Networking Training Details Training Time : 9 Hours Capacity : 12 Prerequisites : There are no prerequisites for this course. About Training About Training TCP/IP is the globally accepted group
CSC 574 Computer and Network Security. TCP/IP Security
 CSC 574 Computer and Network Security TCP/IP Security Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides by Will Enck and Micah Sherr) Network Stack, yet again Application Transport Network
CSC 574 Computer and Network Security TCP/IP Security Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides by Will Enck and Micah Sherr) Network Stack, yet again Application Transport Network
Tony Fortunato Sr Network Specialist The Technology Firm
 T2-11 Trace File Analysis - Analyzing HTTP Traffic Behavior April 2, 2008 Tony Fortunato Sr Network Specialist The Technology Firm SHARKFEST '08 Foothill College March 31 - April 2, 2008 SHARKFEST '08
T2-11 Trace File Analysis - Analyzing HTTP Traffic Behavior April 2, 2008 Tony Fortunato Sr Network Specialist The Technology Firm SHARKFEST '08 Foothill College March 31 - April 2, 2008 SHARKFEST '08
Chapter 2 Advanced TCP/IP
 Tactical Perimeter Defense 2-1 Chapter 2 Advanced TCP/IP At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional Projects Additional
Tactical Perimeter Defense 2-1 Chapter 2 Advanced TCP/IP At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional Projects Additional
Your Name: Your student ID number:
 CSC 573 / ECE 573 Internet Protocols October 11, 2005 MID-TERM EXAM Your Name: Your student ID number: Instructions Allowed o A single 8 ½ x11 (front and back) study sheet, containing any info you wish
CSC 573 / ECE 573 Internet Protocols October 11, 2005 MID-TERM EXAM Your Name: Your student ID number: Instructions Allowed o A single 8 ½ x11 (front and back) study sheet, containing any info you wish
Example questions for the Final Exam, part A
 ETSF10, ETSF05 Ht 2010 Example questions for the Final Exam, part A 1. In AdHoc routing there are two main strategies, reactive and proactive routing. Describe in a small number of words the concept of
ETSF10, ETSF05 Ht 2010 Example questions for the Final Exam, part A 1. In AdHoc routing there are two main strategies, reactive and proactive routing. Describe in a small number of words the concept of
This course prepares candidates for the CompTIA Network+ examination (2018 Objectives) N
 CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
Wireshark: Are You Under Attack? Kyle Feuz School of Computing
 Wireshark: Are You Under Attack? Kyle Feuz School of Computing Introduction Download Wireshark and capture files https://www.wireshark.org/download.html http://icarus.cs.weber.edu/~kfeuz/downloads/sai
Wireshark: Are You Under Attack? Kyle Feuz School of Computing Introduction Download Wireshark and capture files https://www.wireshark.org/download.html http://icarus.cs.weber.edu/~kfeuz/downloads/sai
Network Security. Kitisak Jirawannakool Electronics Government Agency (public organisation)
 1 Network Security Kitisak Jirawannakool Electronics Government Agency (public organisation) A Brief History of the World 2 OSI Model vs TCP/IP suite 3 TFTP & SMTP 4 ICMP 5 NAT/PAT 6 ARP/RARP 7 DHCP 8
1 Network Security Kitisak Jirawannakool Electronics Government Agency (public organisation) A Brief History of the World 2 OSI Model vs TCP/IP suite 3 TFTP & SMTP 4 ICMP 5 NAT/PAT 6 ARP/RARP 7 DHCP 8
Da t e: August 2 0 th a t 9: :00 SOLUTIONS
 Interne t working, Examina tion 2G1 3 0 5 Da t e: August 2 0 th 2 0 0 3 a t 9: 0 0 1 3:00 SOLUTIONS 1. General (5p) a) Place each of the following protocols in the correct TCP/IP layer (Application, Transport,
Interne t working, Examina tion 2G1 3 0 5 Da t e: August 2 0 th 2 0 0 3 a t 9: 0 0 1 3:00 SOLUTIONS 1. General (5p) a) Place each of the following protocols in the correct TCP/IP layer (Application, Transport,
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
COPYRIGHTED MATERIAL. Table of Contents. Assessment Test
 10089.book Page xi Monday, July 23, 2007 3:17 PM Introduction Assessment Test xxiii xxxiii Chapter 1 Internetworking 1 Internetworking Basics 4 Internetworking Models 11 The Layered Approach 12 Advantages
10089.book Page xi Monday, July 23, 2007 3:17 PM Introduction Assessment Test xxiii xxxiii Chapter 1 Internetworking 1 Internetworking Basics 4 Internetworking Models 11 The Layered Approach 12 Advantages
Internet Control Message Protocol (ICMP)
 Internet Control Message Protocol (ICMP) 1 Overview The IP (Internet Protocol) relies on several other protocols to perform necessary control and routing functions: Control functions (ICMP) Multicast signaling
Internet Control Message Protocol (ICMP) 1 Overview The IP (Internet Protocol) relies on several other protocols to perform necessary control and routing functions: Control functions (ICMP) Multicast signaling
Networking: Network layer
 control Networking: Network layer Comp Sci 3600 Security Outline control 1 2 control 3 4 5 Network layer control Outline control 1 2 control 3 4 5 Network layer purpose: control Role of the network layer
control Networking: Network layer Comp Sci 3600 Security Outline control 1 2 control 3 4 5 Network layer control Outline control 1 2 control 3 4 5 Network layer purpose: control Role of the network layer
20-CS Cyber Defense Overview Fall, Network Basics
 20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
IP - The Internet Protocol. Based on the slides of Dr. Jorg Liebeherr, University of Virginia
 IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
Lesson 5 TCP/IP suite, TCP and UDP Protocols. Chapter-4 L05: "Internet of Things ", Raj Kamal, Publs.: McGraw-Hill Education
 Lesson 5 TCP/IP suite, TCP and UDP Protocols 1 TCP/IP Suite: Application layer protocols TCP/IP Suite set of protocols with layers for the Internet TCP/IP communication 5 layers: L7, L4, L3, L2 and L1
Lesson 5 TCP/IP suite, TCP and UDP Protocols 1 TCP/IP Suite: Application layer protocols TCP/IP Suite set of protocols with layers for the Internet TCP/IP communication 5 layers: L7, L4, L3, L2 and L1
6.1 Internet Transport Layer Architecture 6.2 UDP (User Datagram Protocol) 6.3 TCP (Transmission Control Protocol) 6. Transport Layer 6-1
 6. Transport Layer 6.1 Internet Transport Layer Architecture 6.2 UDP (User Datagram Protocol) 6.3 TCP (Transmission Control Protocol) 6. Transport Layer 6-1 6.1 Internet Transport Layer Architecture The
6. Transport Layer 6.1 Internet Transport Layer Architecture 6.2 UDP (User Datagram Protocol) 6.3 TCP (Transmission Control Protocol) 6. Transport Layer 6-1 6.1 Internet Transport Layer Architecture The
Port Mirroring in CounterACT. CounterACT Technical Note
 Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Computer Networks (Introduction to TCP/IP Protocols)
 Network Security(CP33925) Computer Networks (Introduction to TCP/IP Protocols) 부산대학교공과대학정보컴퓨터공학부 Network Type Elements of Protocol OSI Reference Model OSI Layers What we ll learn today 2 Definition of
Network Security(CP33925) Computer Networks (Introduction to TCP/IP Protocols) 부산대학교공과대학정보컴퓨터공학부 Network Type Elements of Protocol OSI Reference Model OSI Layers What we ll learn today 2 Definition of
CCNA 1 Chapter 7 v5.0 Exam Answers 2013
 CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
Certified Penetration Testing Consultant
 Certified Penetration Testing Consultant Duration: 4 Days Language: English Course Delivery: Classroom COURSE BENEFITS The vendor neutral Certified Penetration Testing Consultant course is designed for
Certified Penetration Testing Consultant Duration: 4 Days Language: English Course Delivery: Classroom COURSE BENEFITS The vendor neutral Certified Penetration Testing Consultant course is designed for
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
OmniPeek Report: 21/01/ :17:00. Start: 21/01/ :16:06, Duration: 00:00:33. Total Bytes: , Total Packets: 5274
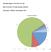 OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
Need For Protocol Architecture
 Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
48-Port Gigabit Ethernet Smart Managed Plus Switch User Manual
 48-Port Gigabit Ethernet Smart Managed Plus Switch User Manual Model GS750E July 2017 202-11784-01 350 E. Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. You
48-Port Gigabit Ethernet Smart Managed Plus Switch User Manual Model GS750E July 2017 202-11784-01 350 E. Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. You
Request for Proposal (RFP) for Supply and Implementation of Firewall for Internet Access (RFP Ref )
 Appendix 1 1st Tier Firewall The Solution shall be rack-mountable into standard 19-inch (482.6-mm) EIA rack. The firewall shall minimally support the following technologies and features: (a) Stateful inspection;
Appendix 1 1st Tier Firewall The Solution shall be rack-mountable into standard 19-inch (482.6-mm) EIA rack. The firewall shall minimally support the following technologies and features: (a) Stateful inspection;
Need For Protocol Architecture
 Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
Foreword by Katie Moussouris... Acknowledgments... xvii. Introduction...xix. Chapter 1: The Basics of Networking... 1
 Brief Contents Foreword by Katie Moussouris.... xv Acknowledgments... xvii Introduction...xix Chapter 1: The Basics of Networking... 1 Chapter 2: Capturing Application Traffic... 11 Chapter 3: Network
Brief Contents Foreword by Katie Moussouris.... xv Acknowledgments... xvii Introduction...xix Chapter 1: The Basics of Networking... 1 Chapter 2: Capturing Application Traffic... 11 Chapter 3: Network
EEC-682/782 Computer Networks I
 EEC-682/782 Computer Networks I Lecture 16 Wenbing Zhao w.zhao1@csuohio.edu http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser at
EEC-682/782 Computer Networks I Lecture 16 Wenbing Zhao w.zhao1@csuohio.edu http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser at
5105: BHARATHIDASAN ENGINEERING COLLEGE NATTARMPALLI UNIT I FUNDAMENTALS AND LINK LAYER PART A
 5105: BHARATHIDASAN ENGINEERING COLLEGE NATTARMPALLI 635 854. NAME OF THE STAFF : R.ANBARASAN DESIGNATION & DEPARTMENT : AP/CSE SUBJECT CODE : CS 6551 SUBJECT NAME : COMPUTER NETWORKS UNIT I FUNDAMENTALS
5105: BHARATHIDASAN ENGINEERING COLLEGE NATTARMPALLI 635 854. NAME OF THE STAFF : R.ANBARASAN DESIGNATION & DEPARTMENT : AP/CSE SUBJECT CODE : CS 6551 SUBJECT NAME : COMPUTER NETWORKS UNIT I FUNDAMENTALS
AccessEnforcer Version 4.0 Features List
 AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
AccessEnforcer Version 4.0 Features List AccessEnforcer UTM Firewall is the simple way to secure and manage your small business network. You can choose from six hardware models, each designed to protect
13. Internet Applications 최양희서울대학교컴퓨터공학부
 13. Internet Applications 최양희서울대학교컴퓨터공학부 Internet Applications Telnet File Transfer (FTP) E-mail (SMTP) Web (HTTP) Internet Telephony (SIP/SDP) Presence Multimedia (Audio/Video Broadcasting, AoD/VoD) Network
13. Internet Applications 최양희서울대학교컴퓨터공학부 Internet Applications Telnet File Transfer (FTP) E-mail (SMTP) Web (HTTP) Internet Telephony (SIP/SDP) Presence Multimedia (Audio/Video Broadcasting, AoD/VoD) Network
QUIZ: Longest Matching Prefix
 QUIZ: Longest Matching Prefix A router has the following routing table: 10.50.42.0 /24 Send out on interface Z 10.50.20.0 /24 Send out on interface A 10.50.24.0 /22 Send out on interface B 10.50.20.0 /22
QUIZ: Longest Matching Prefix A router has the following routing table: 10.50.42.0 /24 Send out on interface Z 10.50.20.0 /24 Send out on interface A 10.50.24.0 /22 Send out on interface B 10.50.20.0 /22
n Given a scenario, analyze and interpret output from n A SPAN has the ability to copy network traffic passing n Capacity planning for traffic
 Chapter Objectives n Understand how to use appropriate software tools to assess the security posture of an organization Chapter #7: Technologies and Tools n Given a scenario, analyze and interpret output
Chapter Objectives n Understand how to use appropriate software tools to assess the security posture of an organization Chapter #7: Technologies and Tools n Given a scenario, analyze and interpret output
Internetworking With TCP/IP
 Internetworking With TCP/IP Vol II: Design, Implementation, and Internals SECOND EDITION DOUGLAS E. COMER and DAVID L. STEVENS Department of Computer Sciences Purdue University West Lafayette, IN 47907
Internetworking With TCP/IP Vol II: Design, Implementation, and Internals SECOND EDITION DOUGLAS E. COMER and DAVID L. STEVENS Department of Computer Sciences Purdue University West Lafayette, IN 47907
OSI Transport Layer. objectives
 LECTURE 5 OSI Transport Layer objectives 1. Roles of the Transport Layer 1. segmentation of data 2. error detection 3. Multiplexing of upper layer application using port numbers 2. The TCP protocol Communicating
LECTURE 5 OSI Transport Layer objectives 1. Roles of the Transport Layer 1. segmentation of data 2. error detection 3. Multiplexing of upper layer application using port numbers 2. The TCP protocol Communicating
The following virtual machines are required for completion of this lab: Exercise I: Mapping a Network Topology Using
 Module 08: Sniffers Objective The objective of this lab is to make students learn to sniff a network and analyze packets for any attacks on the network. The primary objectives of this lab are to: Sniff
Module 08: Sniffers Objective The objective of this lab is to make students learn to sniff a network and analyze packets for any attacks on the network. The primary objectives of this lab are to: Sniff
INDEX. Symbols & Numbers
 INDEX Symbols & Numbers && (AND) operator, in BPF syntax, 58 tag (HTML), 200 tag (HTML), 198 199 tag (HTML), 200 == (equal-to) comparison operator, 64! (NOT) operator, in BPF syntax,
INDEX Symbols & Numbers && (AND) operator, in BPF syntax, 58 tag (HTML), 200 tag (HTML), 198 199 tag (HTML), 200 == (equal-to) comparison operator, 64! (NOT) operator, in BPF syntax,
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
K2289: Using advanced tcpdump filters
 K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
The Client Server Model and Software Design
 The Client Server Model and Software Design Prof. Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology Taipei, TAIWAN MCSE Lab, NTUT, TAIWAN 1 Introduction
The Client Server Model and Software Design Prof. Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology Taipei, TAIWAN MCSE Lab, NTUT, TAIWAN 1 Introduction
Sirindhorn International Institute of Technology Thammasat University
 Name.............................. ID............... Section...... Seat No...... Thammasat University Final Exam: Semester, 205 Course Title: Introduction to Data Communications Instructor: Steven Gordon
Name.............................. ID............... Section...... Seat No...... Thammasat University Final Exam: Semester, 205 Course Title: Introduction to Data Communications Instructor: Steven Gordon
Network Layer (1) Networked Systems 3 Lecture 8
 Network Layer (1) Networked Systems 3 Lecture 8 Role of the Network Layer Application Application The network layer is the first end-to-end layer in the OSI reference model Presentation Session Transport
Network Layer (1) Networked Systems 3 Lecture 8 Role of the Network Layer Application Application The network layer is the first end-to-end layer in the OSI reference model Presentation Session Transport
Chapter 7. The Transport Layer
 Chapter 7 The Transport Layer 1 2 3 4 5 6 7 8 9 10 11 Addressing TSAPs, NSAPs and transport connections. 12 For rarely used processes, the initial connection protocol is used. A special process server,
Chapter 7 The Transport Layer 1 2 3 4 5 6 7 8 9 10 11 Addressing TSAPs, NSAPs and transport connections. 12 For rarely used processes, the initial connection protocol is used. A special process server,
Statistics Available on the Phone, page 1 Statistics Available from the Phone Web Pages, page 8
 Statistics Available on the Phone, page 1 Statistics Available from the Phone Web Pages, page 8 Statistics Available on the Phone You can see statistics and information about the phone from the Settings
Statistics Available on the Phone, page 1 Statistics Available from the Phone Web Pages, page 8 Statistics Available on the Phone You can see statistics and information about the phone from the Settings
Paper solution Subject: Computer Networks (TE Computer pattern) Marks : 30 Date: 5/2/2015
 Paper solution Subject: Computer Networks (TE Computer- 2012 pattern) Marks : 30 Date: 5/2/2015 Q1 a) What is difference between persistent and non persistent HTTP? Also Explain HTTP message format. [6]
Paper solution Subject: Computer Networks (TE Computer- 2012 pattern) Marks : 30 Date: 5/2/2015 Q1 a) What is difference between persistent and non persistent HTTP? Also Explain HTTP message format. [6]
TSIN02 - Internetworking
 Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
Monitoring and Analysis
 CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
CHAPTER 3 Cisco Prime Network Analysis Module 5.1 has two types of dashboards: One type is the summary views found under the Monitor menu, and the other type is the over time views found under the Analyze
Using ICMP to Troubleshoot TCP/IP Networks
 Laura Chappell Using ICMP to Troubleshoot TCP/IP Networks Illustration: Norman Felchle Editor s Note: This article is based on Laura Chappell s upcoming book TCP/IP Analysis and Troubleshooting, which
Laura Chappell Using ICMP to Troubleshoot TCP/IP Networks Illustration: Norman Felchle Editor s Note: This article is based on Laura Chappell s upcoming book TCP/IP Analysis and Troubleshooting, which
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
Networking interview questions
 Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
When does it work? Packet Sniffers. INFO Lecture 8. Content 24/03/2009
 Packet Sniffers INFO 404 - Lecture 8 24/03/2009 nfoukia@infoscience.otago.ac.nz Definition Sniffer Capabilities How does it work? When does it work? Preventing Sniffing Detection of Sniffing References
Packet Sniffers INFO 404 - Lecture 8 24/03/2009 nfoukia@infoscience.otago.ac.nz Definition Sniffer Capabilities How does it work? When does it work? Preventing Sniffing Detection of Sniffing References
Introduction to Network. Topics
 Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Introduction to Network Security Chapter 7 Transport Layer Protocols 1 TCP Layer Topics Responsible for reliable end-to-end transfer of application data. TCP vulnerabilities UDP UDP vulnerabilities DNS
Networks Fall This exam consists of 10 problems on the following 13 pages.
 CSCI 466 Final Networks Fall 2011 Name: This exam consists of 10 problems on the following 13 pages. You may use your two- sided hand- written 8 ½ x 11 note sheet during the exam and a calculator. No other
CSCI 466 Final Networks Fall 2011 Name: This exam consists of 10 problems on the following 13 pages. You may use your two- sided hand- written 8 ½ x 11 note sheet during the exam and a calculator. No other
Introduction to Networks and the Internet
 Introduction to Networks and the Internet CMPE 80N Announcements Project 2. Reference page. Library presentation. Internet History video. Spring 2003 Week 7 1 2 Today Internetworking (cont d). Fragmentation.
Introduction to Networks and the Internet CMPE 80N Announcements Project 2. Reference page. Library presentation. Internet History video. Spring 2003 Week 7 1 2 Today Internetworking (cont d). Fragmentation.
CSCI Networking Name:
 CSCI 3335- Networking Name: Final Exam Problem 1: Error Checking and TCP (15 Points) (a) True or false: [2.5 points for circling correct answers, -1 points for each wrong answer] i. CRC can both correct
CSCI 3335- Networking Name: Final Exam Problem 1: Error Checking and TCP (15 Points) (a) True or false: [2.5 points for circling correct answers, -1 points for each wrong answer] i. CRC can both correct
ECE 650 Systems Programming & Engineering. Spring 2018
 ECE 650 Systems Programming & Engineering Spring 2018 Networking Transport Layer Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) TCP/IP Model 2 Transport Layer Problem solved:
ECE 650 Systems Programming & Engineering Spring 2018 Networking Transport Layer Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) TCP/IP Model 2 Transport Layer Problem solved:
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1
 What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
On Distributed Communications, Rand Report RM-3420-PR, Paul Baran, August 1964
 The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
IPv6 Protocols and Networks Hadassah College Spring 2018 Wireless Dr. Martin Land
 IPv6 1 IPv4 & IPv6 Header Comparison IPv4 Header IPv6 Header Ver IHL Type of Service Total Length Ver Traffic Class Flow Label Identification Flags Fragment Offset Payload Length Next Header Hop Limit
IPv6 1 IPv4 & IPv6 Header Comparison IPv4 Header IPv6 Header Ver IHL Type of Service Total Length Ver Traffic Class Flow Label Identification Flags Fragment Offset Payload Length Next Header Hop Limit
