Configuring a Cisco Secure IDS Sensor in CSPM
|
|
|
- Ashley Elliott
- 5 years ago
- Views:
Transcription
1 Configuring a Cisco Secure IDS Sensor in CSPM Document ID: 6117 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Define the Network on Which the CSPM Host Resides Add the CSPM Host Add the Sensor Device Configure the Sensor Related Information Introduction This document explains the procedure used to configure a Cisco Secure Intrusion Detection System (IDS) Sensor on Cisco Secure Policy Manager (CSPM). This document assumes that you have installed CSPM version 2.3.I on your computer. Version "I" allows management of IDS devices (appliance Sensors, Cisco IOS routers, or IDS Blades) in a Cisco Catalyst 6000 switch. This document also assumes that the IDS postoffice parameters are correctly defined. These include HOSTID, ORGID, HOSTNAME, and ORGNAME. Please note that for the CSPM host to communicate with a Sensor, the ORGID and ORGNAME must match what is defined on the Sensor. Prerequisites Requirements There are no specific requirements for this document. Components Used The information in this document is based on CSPM 2.3.I and later. The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Conventions For more information on document conventions, refer to the Cisco Technical Tips Conventions. Configuration These sections explain the process used to configure an IDS sensor in CSPM. Launch CSPM and log in. A blank template appears (initial launch) that allows you to define your network.
2 These three definitions are required in the CSPM topology for IDS. 1. Define the network in which the control interface of the Sensor resides and the network in which the CSPM host resides. If they are on the same subnet, then only one network needs to be defined. Define this network first. 2. Define the CSPM host in its network. Without the CSPM host definition, the Sensor cannot be managed. 3. Define the Sensor in its network. Define the Network on Which the CSPM Host Resides Complete these steps: 1. Right click on the Internet icon in the topology and select New > Network to create a new network.
3 2. On the right hand side of the Network Panel, add the name of the new network, the network address, and the netmask that will be used. 3. Click the IP Address button, and enter the IP address for your network that it uses to reach the Internet. Normally it is the Default Gateway for the network. Note: When you manage Sensors, the gateway address does not necessarily have to be correct since the Sensor is not sent this default gateway information. It should already be defined in the Sensor. 4. Click OK. The network is added to the topology map without any errors.
4 Add the CSPM Host Use this procedure to add the CSPM host. 1. In the Network Topology, right click on the network you just added and select New > Host. CSPM brings up a screen similar to this. If not, then the network you just defined is not the network in which your CSPM host is located. Check the IP address on your CSPM host again. 2. Click Yes to install the CSPM host into the topology. 3. Verify that the information on the General screen for the CSPM host is ok. 4. Click OK on the General screen of the CSPM host.
5 Add the Sensor Device Use this procedure to add the Sensor device. 1. Right click on the network in which your Sensor resides and select Wizards > Add Sensor. Note: If the CSPM host and the control interface of your Sensor are not in the same network, define the network in which your Sensor resides. 2. Enter the correct postoffice parameters for the Sensor.
6 3. Click the Check here to verify the Sensor's address box. Note: If this is the first time you are setting up this Sensor, you do not want to capture the Sensor's configuration. If you have previously configured this Sensor elsewhere either via a UNIX director or another CSPM host and have made configuration changes to the Sensors signatures, then you want to capture the Sensor's configuration. 4. Click Next to define the signature versions on the Sensor. You can also issue the nrvers command to check this on the Sensor.
7 Note: If CSPM does not have the correct Sensor version that you are running on your Sensor, update the signatures on your CSPM host. Please see Software Download (registered customers only) for updates. 5. Click the Next button to continue. 6. Click Finish to complete the installation of the Sensor into the topology. 7. From the main CSPM menu, select File > Save and Update to compile the information entered in the topology into CSPM. Please note that this step is necessary to start the postoffice protocol on the CSPM host. 8. Verify that everything works by logging into your Sensor as the netrangr user. 9. Execute the nrconns command. >nrconns Connection Status for gacy.rtp > cspm.rtp Connection 1: [Established] sto:0004 with Version 1 Note: If the Sensor and CSPM host are not communicating, output similar to this appears instead: netrangr@gacy:/usr/nr >nrconns Connection Status for gacy.rtp insane.rtp Connection 1: sto:5000 syn NOT rcvd! [SynSent]
8 If this is the case, get a sniffer trace to see if both sides are sending UDP packets. UDP is what IDS devices use to communicate with each other. To test this on the Sensor, su to root and (depending on what Sensor you have) execute snoop d iprb1 port (for an IDS 4210 Sensor) and snoop d iprb0 port (for any other model of Sensor). Use <control c> to break out of a snoop session. This output appears if there is no communications between the Sensor and CSPM: netrangr@gacy:/usr/nr >su Password: Sun Microsystems Inc. SunOS 5.8 Generic February 2000 # snoop d spwr0 port Using device /dev/spwr (promiscuous mode) ^C# > UDP D=45000 S=45000 LEN= > UDP D=45000 S=45000 LEN= > UDP D=45000 S=45000 LEN= > UDP D=45000 S=45000 LEN=52 In the above output, the Sensor sends UDP packets, but does not receive any. A correct configuration produces output similar to this: # snoop d spwr0 port Using device /dev/iprb (promiscuous mode) > gacy UDP D=45000 S=45000 LEN=56 gacy > UDP D=45000 S=45000 LEN= > gacy UDP D=45000 S=45000 LEN=56 gacy > UDP D=45000 S=45000 LEN=56 In the above output, UDP traffic goes in both directions. If UDP packets flow in both directions and the output of nrconns on the Sensor still says that there is no connection established, the postoffice parameters on the Sensor and the CSPM host do not match. To check the postoffice parameters on the CSPM host manually: a. Use Windows Explorer to navigate to where you have CSPM installed on the NT machine.
9 b. Edit the host, route, and organization files with Write or Wordpad (do not use Notepad because the formatting will be corrupted). c. Ensure that these files look correct for your installation. If any of the values are not correct, edit them and reboot your NT computer using these steps: a. Click on the CSPM icon in the network topology. b. Click on the Policy Distribution tab to enter your postoffice parameters. c. Save and Update your changes. d. Reboot the NT computer.
10 Configure the Sensor After the configuration is saved in CSPM, configure the Sensor. In order to do this, first set the Sensor to write the alarms that it sees to its own log. Then set the Sensor to "sniff" on the correct interface. Write Alarms to the Log Use this procedure to write alarms to the log. 1. Click the Generate audit event log files box to tell the Sensor to send the alarms to its local logs. It also sends alarms to the CSPM box by default after you push a configuration down to it. 2. Click OK to continue. Set the Sensor to "Sniff" Use this procedure to set the Sensor to "Sniff". 1. Select the Sensor in your CSPM topology and click the Sensing tab. 2. Define the Packet Capture Device: iprb0 for an IDS 4210 Sensor spwr0 for any other Sensor model
11 3. Click OK to continue. 4. Click the Update icon on the CSPM menu bar to update CSPM with the information. Note: If everything goes well, a screen similar to this appears. Notice there are no red errors. Yellow warnings are typically ok. 5. Select the Sensor in the network topology and click the Command tab to send the updated configuration to the Sensor.
12 6. Click the Approve Now button to send the configuration to the Sensor. The Status pane displays the "Upload <#> completed" message. This indicates a valid and complete transfer process. The Sensor is now updated and should now run normally. If the Sensor is not running normally, go back to the Sensor and check the output of the nrconns command to make sure that the connection between the CSPM host and the Sensor is established.
13 After this is complete, you can look for alarms that the Sensor sends to the CSPM host in the event viewer. To view the event viewer, from the CSPM main menu select Tools > View Sensor Events > Database. Click OK to display the events database window. Your screen will vary depending on the alarms that you may be getting.
14 Related Information Technical Support & Documentation Cisco Systems Contacts & Feedback Help Site Map Cisco Systems, Inc. All rights reserved. Terms & Conditions Privacy Statement Cookie Policy Trademarks of Cisco Systems, Inc. Updated: Jan 19, 2006 Document ID: 6117
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454
 Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
Use NAT to Hide the Real IP Address of CTC to Establish a Session with ONS 15454 Document ID: 65122 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Topology
UCS Uplink Ethernet Connection Configuration Example
 UCS Uplink Ethernet Connection Configuration Example Document ID: 110267 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram 1. Configure Uplink Ethernet
UCS Uplink Ethernet Connection Configuration Example Document ID: 110267 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram 1. Configure Uplink Ethernet
CTC Fails to Start on Windows XP with Cisco Security Agent
 CTC Fails to Start on Windows XP with Cisco Security Agent Document ID: 64669 Contents Introduction Prerequisites Requirements Components Used Conventions Problem Solution Related Information Introduction
CTC Fails to Start on Windows XP with Cisco Security Agent Document ID: 64669 Contents Introduction Prerequisites Requirements Components Used Conventions Problem Solution Related Information Introduction
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
Configuring IDS TCP Reset Using VMS IDS MC
 Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
CRS Historical Reports Schedule and Session Establishment
 CRS Historical Reports Schedule and Session Establishment Document ID: 63424 Contents Introduction Prerequisites Requirements Components Used Conventions Background Schedule Historical Reports Session
CRS Historical Reports Schedule and Session Establishment Document ID: 63424 Contents Introduction Prerequisites Requirements Components Used Conventions Background Schedule Historical Reports Session
Intrusion Detection System Policy Manager
 9E0-572 9E0-572 Intrusion Detection System Policy Manager Version 1.0-1 - Important Note Please Read Carefully Study Tips This product will provide you questions and answers along with detailed explanations
9E0-572 9E0-572 Intrusion Detection System Policy Manager Version 1.0-1 - Important Note Please Read Carefully Study Tips This product will provide you questions and answers along with detailed explanations
Cisco Aironet Client Adapter Installation Tips for Windows NT v4.0
 Cisco Aironet Client Adapter Installation Tips for Windows NT v4.0 Document ID: 19057 To get Cisco Aironet drivers, firmware and utility software, use this link to the Cisco Wireless Software Center. Contents
Cisco Aironet Client Adapter Installation Tips for Windows NT v4.0 Document ID: 19057 To get Cisco Aironet drivers, firmware and utility software, use this link to the Cisco Wireless Software Center. Contents
Configure BIOS Policy for Cisco UCS
 Configure BIOS Policy for Cisco UCS Document ID: 112034 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure Network Diagram BIOS Policy Configuration
Configure BIOS Policy for Cisco UCS Document ID: 112034 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure Network Diagram BIOS Policy Configuration
Tune the CTC HEAP Variables on the PC to Improve CTC Performance
 Tune the CTC HEAP Variables on the PC to Improve CTC Performance Document ID: 68861 Contents Introduction Prerequisites Requirements Components Used Conventions Tune the CTC HEAP Variables Step by step
Tune the CTC HEAP Variables on the PC to Improve CTC Performance Document ID: 68861 Contents Introduction Prerequisites Requirements Components Used Conventions Tune the CTC HEAP Variables Step by step
Best Practices When Configuring Circuits on the ONS 15454
 Best Practices When Configuring Circuits on the ONS 15454 Document ID: 13557 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Automatically Provisioned
Best Practices When Configuring Circuits on the ONS 15454 Document ID: 13557 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Automatically Provisioned
Upgrade BIOS on Cisco UCS Server Blade
 Upgrade BIOS on Cisco UCS Server Blade Document ID: 110260 Contents Introduction Prerequisites Requirements Components Used Network Diagram Conventions Background Information Main Task Task 1. Upgrade
Upgrade BIOS on Cisco UCS Server Blade Document ID: 110260 Contents Introduction Prerequisites Requirements Components Used Network Diagram Conventions Background Information Main Task Task 1. Upgrade
The information in this document is based on the Cisco VPN 3000 Series Concentrator.
 What Is VRRP? Document ID: 7210 Contents Introduction Prerequisites Requirements Components Used Conventions How Does the VPN 3000 Concentrator Implement VRRP? Configure VRRP Synchronize the Configurations
What Is VRRP? Document ID: 7210 Contents Introduction Prerequisites Requirements Components Used Conventions How Does the VPN 3000 Concentrator Implement VRRP? Configure VRRP Synchronize the Configurations
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Configuring the VPN Client 3.x to Get a Digital Certificate
 Configuring the VPN Client 3.x to Get a Digital Certificate Document ID: 4302 Contents Introduction Prerequisites Requirements Components Used Conventions Configure the VPN Client Verify Troubleshoot Related
Configuring the VPN Client 3.x to Get a Digital Certificate Document ID: 4302 Contents Introduction Prerequisites Requirements Components Used Conventions Configure the VPN Client Verify Troubleshoot Related
Implementing Authentication Proxy
 Implementing Authentication Proxy Document ID: 17778 Contents Introduction Prerequisites Requirements Components Used Conventions How to Implement Authentication Proxy Server Profiles Cisco Secure UNIX
Implementing Authentication Proxy Document ID: 17778 Contents Introduction Prerequisites Requirements Components Used Conventions How to Implement Authentication Proxy Server Profiles Cisco Secure UNIX
Expanding an ICM SQL Database
 Expanding an ICM SQL Database Document ID: 20493 Contents Introduction Prerequisites Requirements Components Used Conventions The Basics Expand Space with Use of ICMDBA When To Use Enterprise Manager Expand
Expanding an ICM SQL Database Document ID: 20493 Contents Introduction Prerequisites Requirements Components Used Conventions The Basics Expand Space with Use of ICMDBA When To Use Enterprise Manager Expand
Configuring a Comm/Terminal Server for Sun Console Access
 Configuring a Comm/Terminal Server for Sun Console Access Document ID: 9588 Contents Introduction Prerequisites Requirements Components Used Conventions Set Up for Console Access to the Sun Server Adapters
Configuring a Comm/Terminal Server for Sun Console Access Document ID: 9588 Contents Introduction Prerequisites Requirements Components Used Conventions Set Up for Console Access to the Sun Server Adapters
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
How to Change the IP Address of One or More Cisco ICM NT Servers
 How to Change the IP Address of One or More Cisco ICM NT Servers Document ID: 20463 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information How Do I Change the
How to Change the IP Address of One or More Cisco ICM NT Servers Document ID: 20463 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information How Do I Change the
Using the Startup Wizard
 CHAPTER 3 This chapter describes the Startup wizard and how to use it to configure your sensor. It contains the following sections: Startup Wizard Introduction Window, page 3-1 Setting up the Sensor, page
CHAPTER 3 This chapter describes the Startup wizard and how to use it to configure your sensor. It contains the following sections: Startup Wizard Introduction Window, page 3-1 Setting up the Sensor, page
MeetingPlace for Outlook Onsite Installation or Upgrade
 MeetingPlace for Outlook Onsite Installation or Upgrade Document ID: 60124 Contents Introduction Prerequisites Requirements Components Used Conventions Items to Verify Before the Start of Onsite Work Remote
MeetingPlace for Outlook Onsite Installation or Upgrade Document ID: 60124 Contents Introduction Prerequisites Requirements Components Used Conventions Items to Verify Before the Start of Onsite Work Remote
IP Phone 7940/7960 Fails to BootProtocol Application Invalid
 IP Phone 7940/7960 Fails to BootProtocol Application Invalid Document ID: 67942 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Problem Solution Related
IP Phone 7940/7960 Fails to BootProtocol Application Invalid Document ID: 67942 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Problem Solution Related
Fixing Issues with Corporate Directory Lookup from the Cisco IP Phone
 Fixing Issues with Corporate Directory Lookup from the Cisco IP Phone Document ID: 13936 Contents Introduction Prerequisites Requirements Components Used Conventions Fix Corporate Directory Issues in Cisco
Fixing Issues with Corporate Directory Lookup from the Cisco IP Phone Document ID: 13936 Contents Introduction Prerequisites Requirements Components Used Conventions Fix Corporate Directory Issues in Cisco
Configure the Cisco VPN 3000 Series Concentrators to Support the NT Password Expiration Feature with the RADIUS Server
 Configure the Cisco VPN 3000 Series Concentrators to Support the NT Password Expiration Feature with the RADIUS Server Document ID: 12086 Contents Introduction Prerequisites Requirements Components Used
Configure the Cisco VPN 3000 Series Concentrators to Support the NT Password Expiration Feature with the RADIUS Server Document ID: 12086 Contents Introduction Prerequisites Requirements Components Used
Using NAT in Overlapping Networks
 Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
Using NAT in Overlapping Networks Document ID: 13774 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Related Information
Reestablishing a Broken CallManager Cluster SQL Subscription with Cisco CallManager
 Reestablishing a Broken CallManager Cluster SQL Subscription with Cisco CallManager Document ID: 46100 Contents Introduction Prerequisites Requirements Components Used Conventions Reestablish the Relationship
Reestablishing a Broken CallManager Cluster SQL Subscription with Cisco CallManager Document ID: 46100 Contents Introduction Prerequisites Requirements Components Used Conventions Reestablish the Relationship
Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM
 Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM Document ID: 70791 Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Configure
Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM Document ID: 70791 Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Configure
CDR Database Copy or Migration to Another Server
 CDR Database Copy or Migration to Another Server Document ID: 66974 Contents Introduction Prerequisites Requirements Components Used Conventions Background Supported Data Sources Topology Copy the CDR
CDR Database Copy or Migration to Another Server Document ID: 66974 Contents Introduction Prerequisites Requirements Components Used Conventions Background Supported Data Sources Topology Copy the CDR
PEAP under Unified Wireless Networks with ACS 5.1 and Windows 2003 Server
 PEAP under Unified Wireless Networks with ACS 5.1 and Windows 2003 Server Document ID: 112175 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Windows
PEAP under Unified Wireless Networks with ACS 5.1 and Windows 2003 Server Document ID: 112175 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Windows
Stealthwatch Flow Sensor Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0)
 Stealthwatch Flow Sensor Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: Flow Sensor VE v6.9.0 2017 Cisco Systems, Inc. All rights
Stealthwatch Flow Sensor Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: Flow Sensor VE v6.9.0 2017 Cisco Systems, Inc. All rights
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Reestablishing a Broken Cisco CallManager Cluster SQL Subscription with CallManager 3.0, 3.1 and 3.2
 Reestablishing a Broken Cisco CallManager Cluster SQL Subscription with CallManager 3.0, 3.1 and 3.2 Document ID: 13977 Contents Introduction Prerequisites Requirements Components Used Conventions Reestablish
Reestablishing a Broken Cisco CallManager Cluster SQL Subscription with CallManager 3.0, 3.1 and 3.2 Document ID: 13977 Contents Introduction Prerequisites Requirements Components Used Conventions Reestablish
WebView and IIS Connection Timeouts
 WebView and IIS Connection Timeouts Document ID: 62145 Contents Introduction Prerequisites Requirements Components Used Conventions Background Timeout Adjustment IIS Connection Timeout WebView Timeout
WebView and IIS Connection Timeouts Document ID: 62145 Contents Introduction Prerequisites Requirements Components Used Conventions Background Timeout Adjustment IIS Connection Timeout WebView Timeout
UCSM Faults Report and SNMP Traps
 UCSM Faults Report and SNMP Traps Document ID: 112003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram UCS Faults Reported through SNMP Traps SNMP
UCSM Faults Report and SNMP Traps Document ID: 112003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram UCS Faults Reported through SNMP Traps SNMP
Configuring Split and Dynamic DNS on the Cisco VPN 3000 Concentrator
 Configuring Split and Dynamic DNS on the Cisco VPN 3000 Concentrator Document ID: 26405 Contents Introduction Prerequisites Requirements Components Used Network Diagram Conventions Configuring Split DNS
Configuring Split and Dynamic DNS on the Cisco VPN 3000 Concentrator Document ID: 26405 Contents Introduction Prerequisites Requirements Components Used Network Diagram Conventions Configuring Split DNS
Troubleshooting Web Authentication on a Wireless LAN Controller (WLC)
 Troubleshooting Web Authentication on a Wireless LAN Controller (WLC) Document ID: 108501 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Web Authentication
Troubleshooting Web Authentication on a Wireless LAN Controller (WLC) Document ID: 108501 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Web Authentication
UDP Director Virtual Edition
 UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
Configuring SNMP. Understanding SNMP CHAPTER
 9 CHAPTER To have the sensor send SNMP traps, you must also choose Request SNMP Trap as the event action when you configure signatures. For more information, see Assigning Actions to Signatures, page 5-23.
9 CHAPTER To have the sensor send SNMP traps, you must also choose Request SNMP Trap as the event action when you configure signatures. For more information, see Assigning Actions to Signatures, page 5-23.
Configuration of trace and Log Central in RTMT
 About Trace Collection, page 1 Preparation for trace collection, page 2 Types of trace support, page 4 Configuration of trace collection, page 5 Collect audit logs, page 19 View Collected Trace Files with
About Trace Collection, page 1 Preparation for trace collection, page 2 Types of trace support, page 4 Configuration of trace collection, page 5 Collect audit logs, page 19 View Collected Trace Files with
AS Series Media Processor: Apple Segmenter HTTP Handler Setup
 AS Series Media Processor: Apple Segmenter HTTP Handler Setup Document ID: 112953 Contents Introduction Prerequisites Requirements Components Used Conventions Spinnaker Apple Segmenter HTTP Handler Setup
AS Series Media Processor: Apple Segmenter HTTP Handler Setup Document ID: 112953 Contents Introduction Prerequisites Requirements Components Used Conventions Spinnaker Apple Segmenter HTTP Handler Setup
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
CallManager Configuration Requirements for IPCC
 CallManager Configuration Requirements for IPCC Document ID: 27707 Contents Introduction Prerequisites Requirements Components Used Conventions ACD Lines CTI Route Point Private Lines Recovery Method on
CallManager Configuration Requirements for IPCC Document ID: 27707 Contents Introduction Prerequisites Requirements Components Used Conventions ACD Lines CTI Route Point Private Lines Recovery Method on
Lab - Connect to a Router for the First Time
 Introduction In this lab, you will configure basic settings on a wireless router. Recommended Equipment A computer with Windows installed An Ethernet NIC installed Wireless router Ethernet patch cable
Introduction In this lab, you will configure basic settings on a wireless router. Recommended Equipment A computer with Windows installed An Ethernet NIC installed Wireless router Ethernet patch cable
Cisco DSL Router Configuration and Troubleshooting Guide Cisco DSL Router Acting as a PPPoE Client with a Dynamic IP Address
 Cisco DSL Router Configuration and Troubleshooting Guide Cisco DSL Router Acting as a PPPoE Client with a Dynamic IP Address Document ID: 71118 Contents Introduction Prerequisites Requirements Components
Cisco DSL Router Configuration and Troubleshooting Guide Cisco DSL Router Acting as a PPPoE Client with a Dynamic IP Address Document ID: 71118 Contents Introduction Prerequisites Requirements Components
The following virtual machines are required for completion of this lab: Exercise I: Mapping a Network Topology Using
 Module 08: Sniffers Objective The objective of this lab is to make students learn to sniff a network and analyze packets for any attacks on the network. The primary objectives of this lab are to: Sniff
Module 08: Sniffers Objective The objective of this lab is to make students learn to sniff a network and analyze packets for any attacks on the network. The primary objectives of this lab are to: Sniff
Lab - System Restore in Windows 8
 Lab - System Restore in Windows 8 Introduction In this lab, you will create a restore point and use it to restore your computer. Recommended Equipment A computer running Windows 8 Step 1: Create a restore
Lab - System Restore in Windows 8 Introduction In this lab, you will create a restore point and use it to restore your computer. Recommended Equipment A computer running Windows 8 Step 1: Create a restore
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Products & Services Intrusion Detection System Compatibility Matrix
 Products & Services Intrusion Detection System Compatibility Matrix Document ID: 46386 Contents Introduction Prerequisites Requirements Components Used Conventions IPS Hardware/Software Compatibility Management
Products & Services Intrusion Detection System Compatibility Matrix Document ID: 46386 Contents Introduction Prerequisites Requirements Components Used Conventions IPS Hardware/Software Compatibility Management
Understanding Issues Related to Inter VLAN Bridging
 Understanding Issues Related to Inter VLAN Bridging Document ID: 11072 Contents Introduction Prerequisites Requirements Components Used Conventions Spanning Tree Topology Concerns Recommended Use of Hierarchical
Understanding Issues Related to Inter VLAN Bridging Document ID: 11072 Contents Introduction Prerequisites Requirements Components Used Conventions Spanning Tree Topology Concerns Recommended Use of Hierarchical
Silver Peak EC-V and Microsoft Azure Deployment Guide
 Silver Peak EC-V and Microsoft Azure Deployment Guide How to deploy an EC-V in Microsoft Azure 201422-001 Rev. A September 2018 2 Table of Contents Table of Contents 3 Copyright and Trademarks 5 Support
Silver Peak EC-V and Microsoft Azure Deployment Guide How to deploy an EC-V in Microsoft Azure 201422-001 Rev. A September 2018 2 Table of Contents Table of Contents 3 Copyright and Trademarks 5 Support
Configuring a Management IP Address on Catalyst 4500/4000, 5500/5000, 6500/6000, and Catalyst Fixed Configuration Switches
 Configuring a Management IP Address on Catalyst 4500/4000, 5500/5000, 6500/6000, and Catalyst Fixed Configuration Switches Document ID: 10594 Interactive: This document offers customized analysis of your
Configuring a Management IP Address on Catalyst 4500/4000, 5500/5000, 6500/6000, and Catalyst Fixed Configuration Switches Document ID: 10594 Interactive: This document offers customized analysis of your
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0)
 UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
Configuring the Cisco VPN 3000 Concentrator with MS RADIUS
 Configuring the Cisco VPN 3000 Concentrator with MS RADIUS Document ID: 20585 Contents Introduction Prerequisites Requirements Components Used Conventions Install and Configure the RADIUS Server on Windows
Configuring the Cisco VPN 3000 Concentrator with MS RADIUS Document ID: 20585 Contents Introduction Prerequisites Requirements Components Used Conventions Install and Configure the RADIUS Server on Windows
Integrating Cisco CallManager IVR and Active Directory
 Integrating Cisco CallManager IVR and Active Directory Document ID: 29969 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Cisco CallManager Configuration
Integrating Cisco CallManager IVR and Active Directory Document ID: 29969 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Cisco CallManager Configuration
Create a pfsense router for your private lab network template
 Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
Context Based Access Control (CBAC): Introduction and Configuration
 Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Context Based Access Control (CBAC): Introduction and Configuration Document ID: 13814 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information What Traffic Do
Lab 3.3 Configuring Wireshark and SPAN
 Lab 3.3 Configuring Wireshark and SPAN Learning Objectives Install Wireshark on a host PC Configure a switch to use the SPAN monitoring tool. Topology Diagram Scenario In this lab, you will configure a
Lab 3.3 Configuring Wireshark and SPAN Learning Objectives Install Wireshark on a host PC Configure a switch to use the SPAN monitoring tool. Topology Diagram Scenario In this lab, you will configure a
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example
 Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example Document ID: 113153 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Adjust Administrative Distance for Route Selection in Cisco IOS Routers Configuration Example Document ID: 113153 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
Configure the Catalyst Express 500 Switch with Cisco Network Assistant
 Cisco SMB Support Assistant Cisco Profile Contacts & Feedback Help Configure the Catalyst Express 500 Switch with Cisco Network Assistant Home > Work With My Switches > Cisco Catalyst Switches > Configure
Cisco SMB Support Assistant Cisco Profile Contacts & Feedback Help Configure the Catalyst Express 500 Switch with Cisco Network Assistant Home > Work With My Switches > Cisco Catalyst Switches > Configure
Cisco Unified IP Phone 7942/7945/7962/7965/7975 Firmware Upgrade from pre 8.3(3) to 9.3(1)
 Cisco Unified IP Phone 7942/7945/7962/7965/7975 Firmware Upgrade from pre 8.3(3) to 9.3(1) Document ID: 116054 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Conditions
Cisco Unified IP Phone 7942/7945/7962/7965/7975 Firmware Upgrade from pre 8.3(3) to 9.3(1) Document ID: 116054 Contents Introduction Prerequisites Requirements Components Used Conventions Overview Conditions
Tracking Packet Flow Using Path Analysis
 CHAPTER 4 Tracking Packet Flow Using Path Analysis Path Analysis is an operations and diagnostic application that traces the connectivity between two specified points on your network and the physical and
CHAPTER 4 Tracking Packet Flow Using Path Analysis Path Analysis is an operations and diagnostic application that traces the connectivity between two specified points on your network and the physical and
ECDS MDE 100XVB Installation Guide on ISR G2 UCS-E and VMWare vsphere Hypervisor (ESXi)
 ECDS MDE 100XVB Installation Guide on ISR G2 UCS-E and VMWare vsphere Hypervisor (ESXi) Revised: November, 2013 Contents Overview, page 1 Guidelines and Limitations, page 1 Prerequisites, page 2 Installation
ECDS MDE 100XVB Installation Guide on ISR G2 UCS-E and VMWare vsphere Hypervisor (ESXi) Revised: November, 2013 Contents Overview, page 1 Guidelines and Limitations, page 1 Prerequisites, page 2 Installation
Hotdial on IP Phones with CallManager Configuration Example
 Hotdial on IP Phones with CallManager Configuration Example Document ID: 47601 Contents Introduction Prerequisites Requirements Components Used Conventions Configuring Cisco CallManager Steps for Configuring
Hotdial on IP Phones with CallManager Configuration Example Document ID: 47601 Contents Introduction Prerequisites Requirements Components Used Conventions Configuring Cisco CallManager Steps for Configuring
Understanding Door Configuration
 CHAPTER 5 This chapter describes the concepts used to configure doors and templates. A door configuration is a collection of devices, such as locks and readers, connected to a Cisco Physical Access Gateway
CHAPTER 5 This chapter describes the concepts used to configure doors and templates. A door configuration is a collection of devices, such as locks and readers, connected to a Cisco Physical Access Gateway
Configuring Security on the Voice Network
 This chapter describes the procedure for configuring security on your Cisco BCS Verified Designs network using Cisco Security Device Manager (SDM). Cisco SDM is a web-based device management tool supported
This chapter describes the procedure for configuring security on your Cisco BCS Verified Designs network using Cisco Security Device Manager (SDM). Cisco SDM is a web-based device management tool supported
RHI on the Content Switching Module Configuration Example
 RHI on the Content Switching Module Configuration Example Document ID: 60043 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
RHI on the Content Switching Module Configuration Example Document ID: 60043 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
vrealize Operations Management Pack for NSX for vsphere 2.0
 vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Install Windows 2000 Drivers and Utilities for the Cisco Aironet 340/350 Series Client Adapters
 Install Windows 2000 Drivers and Utilities for the Cisco Aironet 340/350 Series Client Adapters Document ID: 9214 You need a valid Cisco.com account in order to download Cisco Aironet drivers, firmware,
Install Windows 2000 Drivers and Utilities for the Cisco Aironet 340/350 Series Client Adapters Document ID: 9214 You need a valid Cisco.com account in order to download Cisco Aironet drivers, firmware,
CHAPTER. Introduction
 CHAPTER 1 Cisco Unified Communications Manager (formerly Cisco Unified CallManager) serves as the software-based call-processing component of the Cisco Unified Communications family of products. A wide
CHAPTER 1 Cisco Unified Communications Manager (formerly Cisco Unified CallManager) serves as the software-based call-processing component of the Cisco Unified Communications family of products. A wide
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
Asymmetric Routing with Bridge Groups on Catalyst 2948G L3 and 4908G L3 Switches
 Asymmetric Routing with Bridge Groups on Catalyst 2948G L3 and 4908G L3 Switches Document ID: 14975 Contents Introduction Prerequisites Requirements Components Used Conventions Overview of Distributed
Asymmetric Routing with Bridge Groups on Catalyst 2948G L3 and 4908G L3 Switches Document ID: 14975 Contents Introduction Prerequisites Requirements Components Used Conventions Overview of Distributed
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
Install and Configure the TS Agent
 Install the TS Agent, page 1 Start the TS Agent Configuration Interface, page 2 Configure the TS Agent, page 2 Creating the REST VDI Role, page 7 Install the TS Agent Before You Begin Confirm that the
Install the TS Agent, page 1 Start the TS Agent Configuration Interface, page 2 Configure the TS Agent, page 2 Creating the REST VDI Role, page 7 Install the TS Agent Before You Begin Confirm that the
Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 CHAPTER 2 Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter contains information on the following topics: HTTPS Overview, page 2-1 HTTPS for Cisco Unified IP Phone Services,
CHAPTER 2 Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter contains information on the following topics: HTTPS Overview, page 2-1 HTTPS for Cisco Unified IP Phone Services,
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Understanding Cisco Express Forwarding
 Understanding Cisco Express Forwarding Document ID: 47321 Contents Introduction Prerequisites Requirements Components Used Conventions Overview CEF Operations Updating the GRP's Routing Tables Packet Forwarding
Understanding Cisco Express Forwarding Document ID: 47321 Contents Introduction Prerequisites Requirements Components Used Conventions Overview CEF Operations Updating the GRP's Routing Tables Packet Forwarding
Upgrading Software and Firmware
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
Cisco ACI vcenter Plugin
 This chapter contains the following sections: About Cisco ACI with VMware vsphere Web Client, page 1 Getting Started with, page 2 Features and Limitations, page 7 GUI, page 12 Performing ACI Object Configurations,
This chapter contains the following sections: About Cisco ACI with VMware vsphere Web Client, page 1 Getting Started with, page 2 Features and Limitations, page 7 GUI, page 12 Performing ACI Object Configurations,
Wave 5.0. Wave OpenVPN Server Guide for Wave 5.0
 Wave 5.0 Wave OpenVPN Server Guide for Wave 5.0 2015 by Vertical Communications, Inc. All rights reserved. Vertical Communications and the Vertical Communications logo and combinations thereof and Vertical
Wave 5.0 Wave OpenVPN Server Guide for Wave 5.0 2015 by Vertical Communications, Inc. All rights reserved. Vertical Communications and the Vertical Communications logo and combinations thereof and Vertical
OSPF Demand Circuit Feature
 OSPF Demand Circuit Feature Document ID: 5132 Contents Introduction Prerequisites Requirements Components Used Conventions How Is OSPF over Demand Circuit Different from a Normal Circuit? Suppressed Periodic
OSPF Demand Circuit Feature Document ID: 5132 Contents Introduction Prerequisites Requirements Components Used Conventions How Is OSPF over Demand Circuit Different from a Normal Circuit? Suppressed Periodic
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Troubleshooting Cisco Express Forwarding Routing Loops
 Troubleshooting Cisco Express Forwarding Routing Loops Document ID: 26083 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Problem Troubleshoot Solution Related
Troubleshooting Cisco Express Forwarding Routing Loops Document ID: 26083 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Problem Troubleshoot Solution Related
VMware vcenter AppSpeed Installation and Upgrade Guide AppSpeed 1.2
 VMware vcenter AppSpeed Installation and Upgrade Guide AppSpeed 1.2 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware vcenter AppSpeed Installation and Upgrade Guide AppSpeed 1.2 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
How to Configure SSH on Catalyst Switches Running CatOS
 How to Configure SSH on Catalyst Switches Running CatOS Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Switch Configuration Disabling SSH debug in the Catalyst
How to Configure SSH on Catalyst Switches Running CatOS Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Switch Configuration Disabling SSH debug in the Catalyst
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Configuring a Cisco 827 Router Using PPPoA With CHAP and PAP
 Configuring a Cisco 827 Router Using PPPoA With CHAP and PAP Document ID: 12886 Contents Introduction Before You Begin Conventions Prerequisites Components Used Configure Network Diagram PPPoA Using CHAP
Configuring a Cisco 827 Router Using PPPoA With CHAP and PAP Document ID: 12886 Contents Introduction Before You Begin Conventions Prerequisites Components Used Configure Network Diagram PPPoA Using CHAP
Command-Line Interface (CLI) Basics
 4 CHAPTER This chapter is intended as a quick reference, not as a step-by-step explanation of the Cisco IOS. The chapter describes basic Cisco IOS software command-line interfaces that you may need to
4 CHAPTER This chapter is intended as a quick reference, not as a step-by-step explanation of the Cisco IOS. The chapter describes basic Cisco IOS software command-line interfaces that you may need to
ASA Clientless SSL VPN (WebVPN) Troubleshooting Tech Note
 ASA Clientless SSL VPN (WebVPN) Troubleshooting Tech Note Document ID: 104298 Contents Introduction Prerequisites Requirements Components Used Conventions Troubleshooting ASA Version 7.1/7.2 Clientless
ASA Clientless SSL VPN (WebVPN) Troubleshooting Tech Note Document ID: 104298 Contents Introduction Prerequisites Requirements Components Used Conventions Troubleshooting ASA Version 7.1/7.2 Clientless
HPE IMC WSM Converged Topology Configuration Examples
 HPE IMC WSM Converged Topology Configuration Examples Part number: 5200-1397 Software version: IMC WSM 7.2 (E0502P04) The information in this document is subject to change without notice. Copyright 2016
HPE IMC WSM Converged Topology Configuration Examples Part number: 5200-1397 Software version: IMC WSM 7.2 (E0502P04) The information in this document is subject to change without notice. Copyright 2016
Configuring IOS Server Load Balancing with HTTP Probes in the Dispatched Mode
 Configuring IOS Server Load Balancing with HTTP Probes in the Dispatched Mode Document ID: 15055 Contents Introduction Prerequisites Requirements Components Used Conventions Configure HTTP Probes Network
Configuring IOS Server Load Balancing with HTTP Probes in the Dispatched Mode Document ID: 15055 Contents Introduction Prerequisites Requirements Components Used Conventions Configure HTTP Probes Network
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
BASIC USER TRAINING PROGRAM Module 4: Topology
 BASIC USER TRAINING PROGRAM Module 4: Topology Objective Students will learn to work in the Topology editor to create devices, specify links between devices, create and set properties. In addition, students
BASIC USER TRAINING PROGRAM Module 4: Topology Objective Students will learn to work in the Topology editor to create devices, specify links between devices, create and set properties. In addition, students
Basic Cisco Router Configuration: Multiple Routers
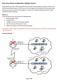 Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
SonicWALL / Toshiba General Installation Guide
 SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
MeetingPlace Web Patch Installation Package Deployment Procedure
 MeetingPlace Web Patch Installation Package Deployment Procedure Document ID: 51040 Contents Introduction Prerequisites Requirements Components Used Conventions Installer Features Utilization Scenarios
MeetingPlace Web Patch Installation Package Deployment Procedure Document ID: 51040 Contents Introduction Prerequisites Requirements Components Used Conventions Installer Features Utilization Scenarios
Sharing a Cisco Unity Voice Mail Box between Two or More IP Phones
 Sharing a Cisco Unity Voice Mail Box between Two or More IP Phones Document ID: 41600 Contents Introduction Before You Begin Conventions Prerequisites Components Used Network Diagram Cisco Unity Configuration
Sharing a Cisco Unity Voice Mail Box between Two or More IP Phones Document ID: 41600 Contents Introduction Before You Begin Conventions Prerequisites Components Used Network Diagram Cisco Unity Configuration
For Trace and Log Central to work, you must resolve DNS lookup for all nodes in the cluster on the client machine.
 Trace and Log Central, page 1 Log Viewers, page 42 Plugins, page 45 Trace and Log Central For Trace and Log Central to work, you must resolve DNS lookup for all nodes in the cluster on the client machine.
Trace and Log Central, page 1 Log Viewers, page 42 Plugins, page 45 Trace and Log Central For Trace and Log Central to work, you must resolve DNS lookup for all nodes in the cluster on the client machine.
