UNIT 10 Ubuntu Security
|
|
|
- Kristian Fleming
- 5 years ago
- Views:
Transcription
1 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 10 Ubuntu Security
2 Learning Objectives Participants will understand how to configure major components of Linux/Ubuntu Account management Updates Firewall Participants will understand how to implement user-level configurations within Ubuntu Account settings Group configuration Authentication and the PAM file Participants will understand commands that will be useful for securing a Linux machine Participants will understand system and audit logging Overview Configuration 2
3 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM SECTION 1 Basic GUI Security
4 Basic Linux Security This unit will show you how to make many of the same security settings you made on Windows in Units 7 and 8 Linux has many of the same vulnerabilities, so the fixes are similar Linux does not have Settings or Control Panel like in Windows The System Settings menu offers limited security tools Click the System Settings button in the menu bar 4
5 User Accounts Overview A. B. C. Click User Accounts in the System Settings window As in Windows, it is important to restrict root (Admin) privileges and password protect all accounts A. To make account management changes, you must enact root permissions by clicking Unlock and authenticate yourself by entering your password B. Switch users from Administrator to Standard User by clicking next to Account Type C. Change passwords by clicking the asterisks next to the Password option 5
6 User Accounts Account Type Select the user archimedes To make changes, click Unlock and authenticate Keep Automatic Login set to off The user account type can be changed by clicking the field next to Account Type 6
7 User Account -- Passwords Click the field next to Password Set a password now allows you to change a user s password Do not select Log in without a password The third option allows you to disable or enable an account Press Cancel to return to the User Accounts windows 7
8 Configuring Updates Click Software & Updates in the System Settings window 8
9 Installing Updates Overview The open-source community regularly develops improvements and patches for Ubuntu You should install these updates regularly 1. Click the Ubuntu button in the menu bar and search for Update Manager 2. Click Settings on the Update Manager Screen 3. To set automatic updates, go to the Updates Tab and make sure Automatically check for updates is set to Daily 4. After applying the changes, install any available updates from the main Update Manager window
10 Configuring Updates Click Software & Updates in the System Settings window 10
11 Update Policy Three Important Tabs Ubuntu Software Other Software Updates 11
12 Installing Updates Click the Ubuntu button in the left-hand menu and search for Update Manager 12
13 Enabling the Firewall Enable the Ubuntu Built-in Firewall (UFW) to prevent unauthorized access to the computer The UFW is deactivated by default By default, UFW is only accessible by command line You can download Gufw, a graphical firewall interface, from the Software Center and use it to make changes to the UFW in the GUI You might need to install Ubuntu updates before installing Gufw Source: 13
14 Using Gufw After downloading Gufw from the Software Center, click the Ubuntu button in your menu bar Search Firewall Configuration Click the Unlock button on the Gufw window Enact root permissions by authenticating Turn Firewall Status On The default (and recommended) rules governing traffic are to Deny all incoming traffic and Allow all outgoing traffic The Reject option is the same as Deny, but also sends a notification to the sender that connection has been blocked The Preconfigured rule panel allows incoming and/or outgoing traffic to be controlled for certain applications or services Similar to the Windows Firewall Exceptions list Open entire ports by clicking the Simple or Advanced tabs Source: 14
15 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM SECTION 2 Basic Command Line Security
16 The Password file /etc/passwd Usually does not contain passwords (anymore) Contains user information Type cat /etc/passwd Type man 5 passwd to view the manual for the password file When you are done, press q to quit 16
17 The Password File User Name User ID Password Group ID User Name The name associated with this user account This is primarily used by humans to identify a user account Password x denotes password is stored in shadow file User ID Numerical user ID, or UID The OS internally identifies users using their UID not Username Group ID Numerical primary group ID, or GID 17
18 The Password File User Name User ID Password Group ID Comment Home Directory Shell Comment Typically used to store the users real name Home Directory Shell The current working directory when this user log in The shell (or command) that gets executed when you log in How this user interacts with the computer when logging in on the command line 18
19 Listing Users Try running the following commands in the terminal: whoami Prints your current username users Prints the user names of users currently logged in to the current host who Prints information about users who are currently logged in w Displays information about the users currently on the machine, and their processes 19
20 The gedit Command Gedit is one of many text editor commands in Ubuntu Syntax: gedit [filepath] Unlike with other text editors, using gedit will cause a second window to pop-up where you can easily change the text of a file This command will allow you to edit security policy files You need to enact root permissions before using gedit to edit files that cannot be accessed by standard users (e.g. system and security files) When using gedit for the first time, go to Edit Preferences Uncheck Create a backup copy of files to avoid saving issues Try using gedit by opening Terminal and entering gedit hello2.txt You will not be prompted to authenticate because this is a public file 20
21 Using gedit to Turn off the Guest Account Like in Windows, the Ubuntu guest account is turned on by default You should disable it so people can t access the computer anonymously The guest account is controlled by LightDM, the display manager controlling the Ubuntu login screen To turn off the guest account, edit the LightDM file: After root authenticating, type gedit /etc/lightdm/lightdm.conf Add the line allow-guest=false to the end of the Light DM file that pops up and click Save Restart your system and click your username button in the top-right corner of your desktop. The guest account should be disabled. Sources:
22 Using gedit to Edit Password History Type gedit /etc/login.defs This is a much longer file. To easily find the section to edit, type Ctrl+F and then PASS_MAX_AGE Modify the following variables to the same recommended settings used in Windows: Maximum Password Duration: PASS_MAX_DAYS 90 Minimum Password Duration: PASS_MIN_DAYS 10 Days Before Expiration to Warn Users to Change Their Password: PASS_WARN_AGE 7 Save the file and close it Sources: 22
23 Using gedit to Set Account Policy Type gedit /etc/pam.d/common-auth This file allows you to set an account lockout policy Add this line to the end of the file: auth required pam_tally2.so deny=5 onerr=fail unlock_time=1800 Save the file and close it Sets the number of allowed failed login attempts (in this case 5) Sets the account lockout duration in seconds (in this case, 30 minutes) Source: 23
24 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM SECTION 3 Advanced Ubuntu Security
25 Turn off the Guest Account Turned on by default LightDM: display manager controlling the login screen Type sudo gedit /etc/lightdm/lightdm.conf Add the line allow-guest=false under [Seat:*] 25
26 Password Age Policy In a terminal, type sudo gedit /etc/login.defs Maximum Password Duration: Minimum Password Duration: Password Warning Before Expiration: PASS_MAX_DAYS 90 PASS_MIN_DAYS 5 PASS_WARN_AGE 7 26
27 The chmod Command Chmod allows you to change file permissions Change permissions for the user, group, or others Syntax: chmod [u,g or o][+ or -][r,w, or x] [filepath] Do not put spaces between the three fields after chmod Example: 1. Type chmod o-r hello2.txt 2. Type ls l hello2.txt Add or subtract permissions 3. If your permissions originally matched those on the last slide, you should see hello2.txt s new file permissions as shown below hello2.txt Specify whether read, write, or execute privileges are being changed Sources:
28 Groups Work very similarly to Windows Root permissions are required 1. To list all groups: cat /etc/group 2. To add a group: addgroup [groupname] 3. To add a user to a group: adduser [username] [groupname] 28
29 Services Can be viewed and managed in the GUI To install, type apt-get install bum in Terminal After installing, type bum to run To start a service, right-click it and select Start To enable a service, check the box next to it When a service is started, the light bulb will light up. When stopped, the light bulb will be dark. 29
Check List: Linux Machines
 Check List: Linux Machines High Level Install and maintain malware protection software o Install MalWare (Defender) o Install AntiVirus (Microsoft Security Essentials) Account Management o Remove guest
Check List: Linux Machines High Level Install and maintain malware protection software o Install MalWare (Defender) o Install AntiVirus (Microsoft Security Essentials) Account Management o Remove guest
UNIT 9 Introduction to Linux and Ubuntu
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT 9 Introduction to Linux and Ubuntu Learning Objectives Participants will understand the basics of Linux, including the nature,
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
Lab Authentication, Authorization, and Accounting
 Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Objectives Given a scenario, select the appropriate authentication, authorization, or access control Install and configure security controls when performing account management, based on best practices
Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers
 Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers Review of the Linux File System and Linux Commands 1. Introduction Becoming adept at using the Linux OS requires gaining familiarity
Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers Review of the Linux File System and Linux Commands 1. Introduction Becoming adept at using the Linux OS requires gaining familiarity
NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1
 NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1 Objective At the conclusion of this lab, the student will be able to add and delete users, create and assign users to groups, and assign users
NETW 110 Lab 5 Creating and Assigning Users and Groups Page 1 Objective At the conclusion of this lab, the student will be able to add and delete users, create and assign users to groups, and assign users
CS/CIS 249 SP18 - Intro to Information Security
 Lab assignment CS/CIS 249 SP18 - Intro to Information Security Lab #2 - UNIX/Linux Access Controls, version 1.2 A typed document is required for this assignment. You must type the questions and your responses
Lab assignment CS/CIS 249 SP18 - Intro to Information Security Lab #2 - UNIX/Linux Access Controls, version 1.2 A typed document is required for this assignment. You must type the questions and your responses
Setting up a Chaincoin Masternode
 Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Setting up a Chaincoin Masternode Introduction So you want to set up your own Chaincoin Masternode? You ve come to the right place! These instructions are correct as of April, 2017, and relate to version
Everything about Linux User- and Filemanagement
 Everything about Linux User- and Filemanagement Lukas Prokop 20. April 2009 Inhaltsverzeichnis 1 Who I am 2 1.1 whoami..................................... 3 1.2 passwd......................................
Everything about Linux User- and Filemanagement Lukas Prokop 20. April 2009 Inhaltsverzeichnis 1 Who I am 2 1.1 whoami..................................... 3 1.2 passwd......................................
User & Group Administration
 User & Group Administration David Morgan Users useradd/userdel /home/ /etc/passwd is the user database /etc/shadow has passwords (relocated from passwd) /etc/group whoami su / sudo / SUID process
User & Group Administration David Morgan Users useradd/userdel /home/ /etc/passwd is the user database /etc/shadow has passwords (relocated from passwd) /etc/group whoami su / sudo / SUID process
Commands are in black
 Starting From the Shell Prompt (Terminal) Commands are in black / +--------+---------+-------+---------+---------+------ +------ +------ +------ +------ +------ +-- Bin boot dev etc home media sbin bin
Starting From the Shell Prompt (Terminal) Commands are in black / +--------+---------+-------+---------+---------+------ +------ +------ +------ +------ +------ +-- Bin boot dev etc home media sbin bin
SCRIV NETWORK COLD WALLET MASTERNODE SETUP GUIDE DETAILED
 SCRIV NETWORK MASTERNODE SETUP GUIDE COLD WALLET DETAILED March, 2018 Table of Contents Requirements for running SCRIV cold wallet masternode on Linux VPS: 3 Setup Linux-based VPS... 3 1. Install SCRIV
SCRIV NETWORK MASTERNODE SETUP GUIDE COLD WALLET DETAILED March, 2018 Table of Contents Requirements for running SCRIV cold wallet masternode on Linux VPS: 3 Setup Linux-based VPS... 3 1. Install SCRIV
The Wonderful World of Services VINCE
 The Wonderful World of Services VINCE Agenda definitions services for Windows and Linux breaks? auditing Linux logs for Linux useful tools Goals develop a better understanding of Linux and Windows services
The Wonderful World of Services VINCE Agenda definitions services for Windows and Linux breaks? auditing Linux logs for Linux useful tools Goals develop a better understanding of Linux and Windows services
User accounts and authorization
 User accounts and authorization Authentication vs authorization Authentication: proving the identity of someone Authorization: allowing a user to access certain resources 1 Government authorization documents
User accounts and authorization Authentication vs authorization Authentication: proving the identity of someone Authorization: allowing a user to access certain resources 1 Government authorization documents
10 userdel: deleting a user account 9. 1 Context Tune the user environment and system environment variables [3]
![10 userdel: deleting a user account 9. 1 Context Tune the user environment and system environment variables [3] 10 userdel: deleting a user account 9. 1 Context Tune the user environment and system environment variables [3]](/thumbs/77/75340043.jpg) 1. Context 1.111.1 2 8 Deleting a group 8 1.111.1 Manage users and group accounts and related system files Weight 4 Outline Contents Linux Professional Institute Certification 102 Nick Urbanik
1. Context 1.111.1 2 8 Deleting a group 8 1.111.1 Manage users and group accounts and related system files Weight 4 Outline Contents Linux Professional Institute Certification 102 Nick Urbanik
Linux Kung-Fu. James Droste UBNetDef Fall 2016
 Linux Kung-Fu James Droste UBNetDef Fall 2016 $ init 1 GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org
Linux Kung-Fu James Droste UBNetDef Fall 2016 $ init 1 GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org GO TO https://apps.ubnetdef.org
SKYPE FOR BUSINESS INTEGRATION FOR COMCAST BUSINESS VOICEEDGE
 SKYPE FOR BUSINESS INTEGRATION FOR COMCAST BUSINESS VOICEEDGE USING THE SKYPE FOR BUSINESS INTEGRATION FOR BUSINESS VOICEEDGE The Skype Integration connects your Comcast Business VoiceEdge service to your
SKYPE FOR BUSINESS INTEGRATION FOR COMCAST BUSINESS VOICEEDGE USING THE SKYPE FOR BUSINESS INTEGRATION FOR BUSINESS VOICEEDGE The Skype Integration connects your Comcast Business VoiceEdge service to your
Perl and R Scripting for Biologists
 Perl and R Scripting for Biologists Lukas Mueller PLBR 4092 Course overview Linux basics (today) Linux advanced (Aure, next week) Why Linux? Free open source operating system based on UNIX specifications
Perl and R Scripting for Biologists Lukas Mueller PLBR 4092 Course overview Linux basics (today) Linux advanced (Aure, next week) Why Linux? Free open source operating system based on UNIX specifications
CSE 390a Lecture 3. Multi-user systems; remote login; editors; users/groups; permissions
 CSE 390a Lecture 3 Multi-user systems; remote login; editors; users/groups; permissions slides created by Marty Stepp, modified by Jessica Miller and Ruth Anderson http://www.cs.washington.edu/390a/ 1
CSE 390a Lecture 3 Multi-user systems; remote login; editors; users/groups; permissions slides created by Marty Stepp, modified by Jessica Miller and Ruth Anderson http://www.cs.washington.edu/390a/ 1
Race Condition Vulnerability Lab
 Concordia Institute for Information Systems Engineering - INSE 6130 1 Race Condition Vulnerability Lab Copyright c 2006-2012 Wenliang Du, Syracuse University. The development of this document is funded
Concordia Institute for Information Systems Engineering - INSE 6130 1 Race Condition Vulnerability Lab Copyright c 2006-2012 Wenliang Du, Syracuse University. The development of this document is funded
CENG 334 Computer Networks. Laboratory I Linux Tutorial
 CENG 334 Computer Networks Laboratory I Linux Tutorial Contents 1. Logging In and Starting Session 2. Using Commands 1. Basic Commands 2. Working With Files and Directories 3. Permission Bits 3. Introduction
CENG 334 Computer Networks Laboratory I Linux Tutorial Contents 1. Logging In and Starting Session 2. Using Commands 1. Basic Commands 2. Working With Files and Directories 3. Permission Bits 3. Introduction
Project #3: Implementing NIS
 Project #3: Implementing NIS NIS Daemons Limitations of NIS How We Will Use NIS NIS Domain Name NIS Software Setting Up NIS on it20 /etc/nsswitch.conf Creating New Accounts on Ubuntu /etc/passwd /etc/shadow
Project #3: Implementing NIS NIS Daemons Limitations of NIS How We Will Use NIS NIS Domain Name NIS Software Setting Up NIS on it20 /etc/nsswitch.conf Creating New Accounts on Ubuntu /etc/passwd /etc/shadow
Chapter 8: Security under Linux
 Chapter 8: Security under Linux 8.1 File and Password security Linux security may be divided into two major parts: a) Password security b) File security 8.1.1 Password security To connect to a Linux system
Chapter 8: Security under Linux 8.1 File and Password security Linux security may be divided into two major parts: a) Password security b) File security 8.1.1 Password security To connect to a Linux system
Configuring User Profiles and User Groups for Cisco Unified MeetingPlace
 Configuring User Profiles and User Groups for Cisco Unified MeetingPlace Release 7.1 Revised: April 6, 2011 12:15 pm How to Configure User Groups, page 1 How to Configure User Profiles, page 5 How to Configure
Configuring User Profiles and User Groups for Cisco Unified MeetingPlace Release 7.1 Revised: April 6, 2011 12:15 pm How to Configure User Groups, page 1 How to Configure User Profiles, page 5 How to Configure
MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL. 31 January 2017
 MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL 31 January 2017 Contents 1 Introduction... 2 1.1 Prerequisite for configuring the multi-factor authentication:... 2 1.1.1 On the Guest side... 2 1.1.2
MULTI FACTOR AUTHENTICATION USING THE NETOP PORTAL 31 January 2017 Contents 1 Introduction... 2 1.1 Prerequisite for configuring the multi-factor authentication:... 2 1.1.1 On the Guest side... 2 1.1.2
Linux Kung Fu. Stephen James UBNetDef, Spring 2017
 Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
Linux Kung Fu Stephen James UBNetDef, Spring 2017 Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and
The kernel is the low-level software that manages hardware, multitasks programs, etc.
 November 2011 1 Why Use Linux? Save Money Initial purchase and maintenance Resume Linux is used by MANY organizations More choices Tons of Linux operating systems November 2011 2 What is Linux? 1. Contains
November 2011 1 Why Use Linux? Save Money Initial purchase and maintenance Resume Linux is used by MANY organizations More choices Tons of Linux operating systems November 2011 2 What is Linux? 1. Contains
SERVER HARDENING CHECKLIST
 SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
Linux Kung Fu. Ross Ventresca UBNetDef, Fall 2017
 Linux Kung Fu Ross Ventresca UBNetDef, Fall 2017 GOTO: https://apps.ubnetdef.org/ What is Linux? Linux generally refers to a group of Unix-like free and open source operating system distributions built
Linux Kung Fu Ross Ventresca UBNetDef, Fall 2017 GOTO: https://apps.ubnetdef.org/ What is Linux? Linux generally refers to a group of Unix-like free and open source operating system distributions built
Information System Audit Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000)
 Information System Audit Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) armahmood786@yahoo.com alphasecure@gmail.com alphapeeler.sf.net/pubkeys/pkey.htm http://alphapeeler.sourceforge.net pk.linkedin.com/in/armahmood
Information System Audit Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) armahmood786@yahoo.com alphasecure@gmail.com alphapeeler.sf.net/pubkeys/pkey.htm http://alphapeeler.sourceforge.net pk.linkedin.com/in/armahmood
Dirty COW Attack Lab
 SEED Labs Dirty COW Attack Lab 1 Dirty COW Attack Lab Copyright 2017 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation under Award
SEED Labs Dirty COW Attack Lab 1 Dirty COW Attack Lab Copyright 2017 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation under Award
Optional Labs. 0Handouts: 2002 ProsoftTraining All Rights Reserved. Version 3.07
 0Handouts: Optional Lab 1-1: Understanding the /etc/securetty file In this lab, you will examine a PAM component, the /etc/securetty file. 1. Boot into Linux as root. Open a Telnet client and attempt to
0Handouts: Optional Lab 1-1: Understanding the /etc/securetty file In this lab, you will examine a PAM component, the /etc/securetty file. 1. Boot into Linux as root. Open a Telnet client and attempt to
INF322 Operating Systems
 Galatasaray University Computer Engineering Department INF322 Operating Systems TP01: Introduction to Linux Ozan Çağlayan ocaglayan@gsu.edu.tr ozancaglayan.com Fundamental Concepts Definition of Operating
Galatasaray University Computer Engineering Department INF322 Operating Systems TP01: Introduction to Linux Ozan Çağlayan ocaglayan@gsu.edu.tr ozancaglayan.com Fundamental Concepts Definition of Operating
Introduction. What is Linux? What is the difference between a client and a server?
 Linux Kung Fu Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and open-source operating system distributions
Linux Kung Fu Introduction What is Linux? What is the difference between a client and a server? What is Linux? Linux generally refers to a group of Unix-like free and open-source operating system distributions
Redhat Basic. Need. Your. What. Operation G U I D E. Technical Hand Note template version
 Redhat Basic Operation G U I D E What Need Your www.next-asia.com Readhat Basic Operation Guide, Prepared by Nazmul Khan Page 1 of 43 Redhat Basic Operation Guide RedHat Installation Guide... 2 Installation...
Redhat Basic Operation G U I D E What Need Your www.next-asia.com Readhat Basic Operation Guide, Prepared by Nazmul Khan Page 1 of 43 Redhat Basic Operation Guide RedHat Installation Guide... 2 Installation...
Basic Linux Security. Roman Bohuk University of Virginia
 Basic Linux Security Roman Bohuk University of Virginia What is Linux? An open source operating system Project started by Linus Torvalds kernel Kernel: core program that controls everything else (controls
Basic Linux Security Roman Bohuk University of Virginia What is Linux? An open source operating system Project started by Linus Torvalds kernel Kernel: core program that controls everything else (controls
TEL2821/IS2150: INTRODUCTION TO SECURITY Lab: Operating Systems and Access Control
 TEL2821/IS2150: INTRODUCTION TO SECURITY Lab: Operating Systems and Access Control Version 1.0, Last Edited 09/20/2005 Name of Students: Date of Experiment: Part I: Objective The objective of the exercises
TEL2821/IS2150: INTRODUCTION TO SECURITY Lab: Operating Systems and Access Control Version 1.0, Last Edited 09/20/2005 Name of Students: Date of Experiment: Part I: Objective The objective of the exercises
Veritas NetBackup Appliance Security Guide
 Veritas NetBackup Appliance Security Guide Release 2.7.3 NetBackup 52xx and 5330 Veritas NetBackup Appliance Security Guide Document version: 2.7.3 Legal Notice Copyright 2016 Veritas Technologies LLC.
Veritas NetBackup Appliance Security Guide Release 2.7.3 NetBackup 52xx and 5330 Veritas NetBackup Appliance Security Guide Document version: 2.7.3 Legal Notice Copyright 2016 Veritas Technologies LLC.
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
UNIX/Linux Auditing. Baccam Consulting, LLC Training Events
 UNIX/Linux Auditing Baccam Consulting, LLC tanya@securityaudits.org Training Events www.securityaudits.org/events.html ***CISSP Course being offered April 25-April 29, 2016 Copyright 2005-2016, Baccam
UNIX/Linux Auditing Baccam Consulting, LLC tanya@securityaudits.org Training Events www.securityaudits.org/events.html ***CISSP Course being offered April 25-April 29, 2016 Copyright 2005-2016, Baccam
INTRODUCTION TO LINUX
 INTRODUCTION TO LINUX REALLY SHORT HISTORY Before GNU/Linux there were DOS, MAC and UNIX. All systems were proprietary. The GNU project started in the early 80s by Richard Stallman Goal to make a free
INTRODUCTION TO LINUX REALLY SHORT HISTORY Before GNU/Linux there were DOS, MAC and UNIX. All systems were proprietary. The GNU project started in the early 80s by Richard Stallman Goal to make a free
Course Wiki. Today s Topics. Web Resources. Amazon EC2. Linux. Apache PHP. Workflow and Tools. Extensible Networking Platform 1
 Today s Topics Web Resources Amazon EC2 Linux Apache PHP Workflow and Tools Extensible Networking Platform 1 1 - CSE 330 Creative Programming and Rapid Prototyping Course Wiki Extensible Networking Platform
Today s Topics Web Resources Amazon EC2 Linux Apache PHP Workflow and Tools Extensible Networking Platform 1 1 - CSE 330 Creative Programming and Rapid Prototyping Course Wiki Extensible Networking Platform
Security Design in. Avaya Aura Presence Services. Release 5.2. Issue 1
 Security Design in Avaya Aura Presence Services Release 5.2 Issue 1 November 2009 2009 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document
Security Design in Avaya Aura Presence Services Release 5.2 Issue 1 November 2009 2009 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document
Lab 3a Using the vi editor
 Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Outline. UNIX security ideas Users and groups File protection Setting temporary privileges. Examples. Permission bits Program language components
 UNIX security Ulf Larson (modified by Erland Jonsson/Magnus Almgren) Computer security group Dept. of Computer Science and Engineering Chalmers University of Technology, Sweden Outline UNIX security ideas
UNIX security Ulf Larson (modified by Erland Jonsson/Magnus Almgren) Computer security group Dept. of Computer Science and Engineering Chalmers University of Technology, Sweden Outline UNIX security ideas
Exercise Sheet 2. (Classifications of Operating Systems)
 Exercise Sheet 2 Exercise 1 (Classifications of Operating Systems) 1. At any given moment, only a single program can be executed. What is the technical term for this operation mode? 2. What are half multi-user
Exercise Sheet 2 Exercise 1 (Classifications of Operating Systems) 1. At any given moment, only a single program can be executed. What is the technical term for this operation mode? 2. What are half multi-user
Setting Up and Using WebDrive
 Setting Up and Using WebDrive Rutgers University has a site license for WebDrive, an SFTP program used to transfer files to and from servers such as crab and clam. Both employees and students may download
Setting Up and Using WebDrive Rutgers University has a site license for WebDrive, an SFTP program used to transfer files to and from servers such as crab and clam. Both employees and students may download
CST8207: GNU/Linux Operating Systems I Lab Seven Linux User and Group Management. Linux User and Group Management
 Student Name: Lab Section: Linux User and Group Management 1 Due Date - Upload to Blackboard by 8:30am Monday April 2, 2012 Submit the completed lab to Blackboard following the Rules for submitting Online
Student Name: Lab Section: Linux User and Group Management 1 Due Date - Upload to Blackboard by 8:30am Monday April 2, 2012 Submit the completed lab to Blackboard following the Rules for submitting Online
User Accounts. The Passwd, Group, and Shadow Files
 User Accounts The Passwd, Group, and Shadow Files We'll start with the passwd (pronounced "password") file, located at /etc/passwd. This file holds information about all of the user accounts on the system.
User Accounts The Passwd, Group, and Shadow Files We'll start with the passwd (pronounced "password") file, located at /etc/passwd. This file holds information about all of the user accounts on the system.
Linux Local Security about Passwords and Data NZPAPER.BLOGSPOT.COM. Nz Paper Linux and Web Application Security. Zeeshan Khan 4/15/2013
 1 Linux Local Security about Passwords and Data NZPAPER.BLOGSPOT.COM Nz Paper Linux and Web Application Security Zeeshan Khan 4/15/2013 2 Abstract: As Passwords and other Linux Data play an important role
1 Linux Local Security about Passwords and Data NZPAPER.BLOGSPOT.COM Nz Paper Linux and Web Application Security Zeeshan Khan 4/15/2013 2 Abstract: As Passwords and other Linux Data play an important role
AT&T Business Messaging Account Management
 Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Managing WCS User Accounts
 7 CHAPTER This chapter describes how to configure global email parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Viewing or Editing User Information,
7 CHAPTER This chapter describes how to configure global email parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Viewing or Editing User Information,
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability.
 CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
CIS 76 Ethical Hacking Building an open source Pentest Sandbox, carrying out a Remote Code Execution exploit, and Remediating the RCE vulnerability. Ryan Borden December 3, 2017 Contact: ryanborden81@gmail.com
Upgrade Tool Guide. July
 Upgrade Tool Guide July 2015 http://www.liveaction.com 4.X to 5.0 The Upgrade Guide from 4.X to 5.0 consists of three parts: Upgrading the LiveAction Server Upgrading the LiveAction Node Upgrading the
Upgrade Tool Guide July 2015 http://www.liveaction.com 4.X to 5.0 The Upgrade Guide from 4.X to 5.0 consists of three parts: Upgrading the LiveAction Server Upgrading the LiveAction Node Upgrading the
Introduction to Systems Security
 Introduction to Systems Security CIM3571 Dr. S.F. Wu (wusf@vtc.edu.hk, R323, x706) Continuous Assessment 50% Examination 50% Security and Threat There are three aspects of computer security: Confidentiality
Introduction to Systems Security CIM3571 Dr. S.F. Wu (wusf@vtc.edu.hk, R323, x706) Continuous Assessment 50% Examination 50% Security and Threat There are three aspects of computer security: Confidentiality
Step by step to getting R installed on your computer
 Step by step to getting R installed on your computer 1. Go to the R-Project webpage (www.r-project.org) 2. Select the CRAN option under Download on the left hand side of the page: 3. On the CRAN Mirrors
Step by step to getting R installed on your computer 1. Go to the R-Project webpage (www.r-project.org) 2. Select the CRAN option under Download on the left hand side of the page: 3. On the CRAN Mirrors
Server virtualiza,on and security. CSCI 470: Web Science Keith Vertanen
 Server virtualiza,on and security CSCI 470: Web Science Keith Vertanen Mo*va*on Virtualiza*on Overview Setup process (DigitalOcean) Securing a new Ubuntu VM So
Server virtualiza,on and security CSCI 470: Web Science Keith Vertanen Mo*va*on Virtualiza*on Overview Setup process (DigitalOcean) Securing a new Ubuntu VM So
Managing WCS User Accounts
 CHAPTER 7 This chapter describes how to manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Changing Passwords, page 7-3 Deleting WCS User Accounts, page 7-3 Creating
CHAPTER 7 This chapter describes how to manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-2 Changing Passwords, page 7-3 Deleting WCS User Accounts, page 7-3 Creating
CSE 390a Lecture 4. Persistent shell settings; users/groups; permissions
 CSE 390a Lecture 4 Persistent shell settings; users/groups; permissions slides created by Marty Stepp, modified by Jessica Miller and Ruth Anderson http://www.cs.washington.edu/390a/ 1 2 Lecture summary
CSE 390a Lecture 4 Persistent shell settings; users/groups; permissions slides created by Marty Stepp, modified by Jessica Miller and Ruth Anderson http://www.cs.washington.edu/390a/ 1 2 Lecture summary
Managing WCS User Accounts
 CHAPTER 7 This chapter describes how to configure global e-mail parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-1 Viewing or Editing User Information,
CHAPTER 7 This chapter describes how to configure global e-mail parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-1 Viewing or Editing User Information,
BPPM Patrol Agent Installation Steps on Linux and Automation Integration
 BPPM Patrol Agent Installation Steps on Linux and Automation Integration Author: Karlis Peterson, Software Consultant, BMC Software Version: 1.0 Date: May 12, 2013 DISCLAIMER NOTICE This is Field Developed
BPPM Patrol Agent Installation Steps on Linux and Automation Integration Author: Karlis Peterson, Software Consultant, BMC Software Version: 1.0 Date: May 12, 2013 DISCLAIMER NOTICE This is Field Developed
Using TU Eindhoven s VPN with Ubuntu
 Using TU Eindhoven's VPN with Ubuntu 14.04 or 16.04 TU Eindhoven s Virtual Private Networking (VPN) service can be used on Linux computers. This document describes how to do it using Ubuntu 14.04 or 16.04
Using TU Eindhoven's VPN with Ubuntu 14.04 or 16.04 TU Eindhoven s Virtual Private Networking (VPN) service can be used on Linux computers. This document describes how to do it using Ubuntu 14.04 or 16.04
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades Q2
 Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Linux Operating System Environment Computadors Grau en Ciència i Enginyeria de Dades 2017-2018 Q2 Facultat d Informàtica de Barcelona This first lab session is focused on getting experience in working
Installation guide for Choic Multi User Edition
 Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Operating Systems Linux 1-2 Measurements Background material
 Operating Systems Linux 1-2 Measurements Background material Introduction The Linux measurements were designed to allow you to have an impression about the administration of Linux severs along with providing
Operating Systems Linux 1-2 Measurements Background material Introduction The Linux measurements were designed to allow you to have an impression about the administration of Linux severs along with providing
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
Network Monitoring & Management. A few Linux basics
 Network Monitoring & Management A few Linux basics Our chosen platform Ubuntu Linux 14.04.3 LTS 64-bit LTS = Long Term Support no GUI, we administer using ssh Ubuntu is Debian underneath There are other
Network Monitoring & Management A few Linux basics Our chosen platform Ubuntu Linux 14.04.3 LTS 64-bit LTS = Long Term Support no GUI, we administer using ssh Ubuntu is Debian underneath There are other
SECURITY DOCUMENT. 550archi
 SECURITY DOCUMENT 550archi Documentation for XTM Version 10.3 Published by XTM International Ltd. Copyright XTM International Ltd. All rights reserved. No part of this publication may be reproduced or
SECURITY DOCUMENT 550archi Documentation for XTM Version 10.3 Published by XTM International Ltd. Copyright XTM International Ltd. All rights reserved. No part of this publication may be reproduced or
Transport Gateway Installation / Registration / Configuration
 CHAPTER 4 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
CHAPTER 4 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
Linux Security & Firewall
 Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
Linux Security & Firewall Linux is not secure No computer system can ever be "completely secure". make it increasingly difficult for someone to compromise your system. The more secure your system, the
IRONKEY D300S SECURE USB 3.0 FLASH DRIVE
 IRONKEY D300S SECURE USB 3.0 FLASH DRIVE User Guide Document No. 48000130-001.A01 D300S Page 1 of 27 Table of Contents About This Manual... 3 System Requirements...3 Recommendations...3 Setup (Windows
IRONKEY D300S SECURE USB 3.0 FLASH DRIVE User Guide Document No. 48000130-001.A01 D300S Page 1 of 27 Table of Contents About This Manual... 3 System Requirements...3 Recommendations...3 Setup (Windows
CST8207: GNU/Linux Operating Systems I Lab Seven Linux User and Group Management. Linux User and Group Management
 Student Name: YOUR NAME Lab Section: 011 012 013 or 014 Linux User and Group Management 1 Due Date - Upload to Blackboard by 8:30am Monday April 2, 2012 Submit the completed lab to Blackboard following
Student Name: YOUR NAME Lab Section: 011 012 013 or 014 Linux User and Group Management 1 Due Date - Upload to Blackboard by 8:30am Monday April 2, 2012 Submit the completed lab to Blackboard following
NetSupport ServiceDesk Product Manual Version 3.10
 NetSupport ServiceDesk Product Manual Version 3.10 Manual COPYRIGHT (C) 2013 NetSupport Ltd. All rights reserved. The Information in this document is subject to change without notice. NetSupport Ltd. reserves
NetSupport ServiceDesk Product Manual Version 3.10 Manual COPYRIGHT (C) 2013 NetSupport Ltd. All rights reserved. The Information in this document is subject to change without notice. NetSupport Ltd. reserves
Operating Systems Lab 1 (Users, Groups, and Security)
 Operating Systems Lab 1 (Users, Groups, and Security) Overview This chapter covers the most common commands related to users, groups, and security. It will also discuss topics like account creation/deletion,
Operating Systems Lab 1 (Users, Groups, and Security) Overview This chapter covers the most common commands related to users, groups, and security. It will also discuss topics like account creation/deletion,
Parallel Programming Pre-Assignment. Setting up the Software Environment
 Parallel Programming Pre-Assignment Setting up the Software Environment Authors: B. Wilkinson and C. Ferner. Modification date: Aug 21, 2014 (Minor correction Aug 27, 2014.) Software The purpose of this
Parallel Programming Pre-Assignment Setting up the Software Environment Authors: B. Wilkinson and C. Ferner. Modification date: Aug 21, 2014 (Minor correction Aug 27, 2014.) Software The purpose of this
WA2592 Applied Data Science and Big Data Analytics. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc.
 WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
How to Secure SSH with Google Two-Factor Authentication
 How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
Cisco Unity Express Windows and Menus
 Last updated: June 21, 2007 This chapter describes the windows, menus, and icons available in the Cisco Unity Express voice-mail system and contains the following sections: Navigating Through the Cisco
Last updated: June 21, 2007 This chapter describes the windows, menus, and icons available in the Cisco Unity Express voice-mail system and contains the following sections: Navigating Through the Cisco
REACH Remote Deposit Capture
 REACH Remote Deposit Capture Company Administration CONTENTS Introduction to REACH... 1 Overview of Roles... 1 Session Timeouts and Maintenance... 1 User Login... 2 Login via Online Cash Management...
REACH Remote Deposit Capture Company Administration CONTENTS Introduction to REACH... 1 Overview of Roles... 1 Session Timeouts and Maintenance... 1 User Login... 2 Login via Online Cash Management...
Installation of the DigitalSystemsVM virtual machine
 Installation of the DigitalSystemsVM virtual machine Notice This document explains how to install the DigitalSystemsVM virtual machine on a computer with Linux Ubuntu 16.04 LTS. If questions or problems
Installation of the DigitalSystemsVM virtual machine Notice This document explains how to install the DigitalSystemsVM virtual machine on a computer with Linux Ubuntu 16.04 LTS. If questions or problems
Cisco Unified Serviceability
 Cisco Unified Serviceability Introduction, page 1 Installation, page 5 Introduction This document uses the following abbreviations to identify administration differences for these Cisco products: Unified
Cisco Unified Serviceability Introduction, page 1 Installation, page 5 Introduction This document uses the following abbreviations to identify administration differences for these Cisco products: Unified
Operating Systems. Copyleft 2005, Binnur Kurt
 3 Operating Systems Copyleft 2005, Binnur Kurt Content The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail.
3 Operating Systems Copyleft 2005, Binnur Kurt Content The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail.
Operating Systems 3. Operating Systems. Content. What is an Operating System? What is an Operating System? Resource Abstraction and Sharing
 Content 3 Operating Systems The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail. How to log into (and out
Content 3 Operating Systems The concept of an operating system. The internal architecture of an operating system. The architecture of the Linux operating system in more detail. How to log into (and out
IOL INTACT Installation Guide
 IOL INTACT Installation Guide February 25, 2014 Contents 1 System Requirements 1 2 Installing IOL INTACT 3 3 Post-Installation 4 3.1 Wireshark............................. 4 3.2 Opening pcap Files........................
IOL INTACT Installation Guide February 25, 2014 Contents 1 System Requirements 1 2 Installing IOL INTACT 3 3 Post-Installation 4 3.1 Wireshark............................. 4 3.2 Opening pcap Files........................
Operating System Security. 0Handouts: Quizzes ProsoftTraining All Rights Reserved. Version 3.07
 0Handouts: Lesson 1 Quiz 1. What is the working definition of authentication? a. The ability for a person or system to prove identity. b. Protection of data on a system or host from unauthorized access.
0Handouts: Lesson 1 Quiz 1. What is the working definition of authentication? a. The ability for a person or system to prove identity. b. Protection of data on a system or host from unauthorized access.
Once the VM is started, the VirtualBox OS Manager window can be closed. But our Ubuntu VM is still running.
 How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
Contents. Note: pay attention to where you are. Note: Plaintext version. Note: pay attention to where you are... 1 Note: Plaintext version...
 Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
Contents Note: pay attention to where you are........................................... 1 Note: Plaintext version................................................... 1 Hello World of the Bash shell 2 Accessing
How do I configure my LPL client to use SSL for incoming mail?
 How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
Interview Room Management System Administrator Manual
 Technical Support Interview Room Management System Administrator Manual www.casecracker.com support@casecracker.com (720) 442-7072 Table of Contents 1. System Overview 1 2. Users and Groups 1 3. Setup
Technical Support Interview Room Management System Administrator Manual www.casecracker.com support@casecracker.com (720) 442-7072 Table of Contents 1. System Overview 1 2. Users and Groups 1 3. Setup
Using RDP with Azure Linux Virtual Machines
 Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
Using RDP with Azure Linux Virtual Machines 1. Create a Linux Virtual Machine with Azure portal Create SSH key pair 1. Install Ubuntu Bash shell by downloading and running bash.exe file as administrator.
MAC HOST GUIDE. Remote Support & Management PC Mac Tablet Smartphone Embedded device. WiseMo Host module on your Mac computer
 MAC HOST GUIDE Remote Support & Management PC Mac Tablet Smartphone Embedded device WiseMo Guest module for example on your Windows PC WiseMo Host module on your Mac computer WiseMo develops software for
MAC HOST GUIDE Remote Support & Management PC Mac Tablet Smartphone Embedded device WiseMo Guest module for example on your Windows PC WiseMo Host module on your Mac computer WiseMo develops software for
File Properties and Permissions
 File Properties and Permissions Managing File Access in Linux Peter Perry July 2009 What is it about? Open a shell (terminal) and type ls -l You get quite a bit of information about each file. Tonight,
File Properties and Permissions Managing File Access in Linux Peter Perry July 2009 What is it about? Open a shell (terminal) and type ls -l You get quite a bit of information about each file. Tonight,
CSE 265: System and Network Administration
 CSE 265: System and Network Administration User accounts The /etc/passwd file The /etc/shadow file Root powers Ownership of files and processes The superuser The /etc/group file Adding users Removing users
CSE 265: System and Network Administration User accounts The /etc/passwd file The /etc/shadow file Root powers Ownership of files and processes The superuser The /etc/group file Adding users Removing users
commands exercises Linux System Administration and IP Services AfNOG 2015 Linux Commands # Notes
 Linux System Administration and IP Services AfNOG 2015 Linux Commands # Notes * Commands preceded with "$" imply that you should execute the command as a general user not as root. * Commands preceded with
Linux System Administration and IP Services AfNOG 2015 Linux Commands # Notes * Commands preceded with "$" imply that you should execute the command as a general user not as root. * Commands preceded with
OpenProject AdminGuide
 OpenProject AdminGuide I. Contents I. Contents... 1 II. List of figures... 2 1 Administration... 2 1.1 Manage projects...2 1.2 Manage users...5 1.3 Manage groups...11 1.4 Manage roles and permissions...13
OpenProject AdminGuide I. Contents I. Contents... 1 II. List of figures... 2 1 Administration... 2 1.1 Manage projects...2 1.2 Manage users...5 1.3 Manage groups...11 1.4 Manage roles and permissions...13
Pre-Assessment Answers-1
 Pre-Assessment Answers-1 0Pre-Assessment Answers Lesson 1 Pre-Assessment Questions 1. What is the name of a statistically unique number assigned to all users on a Windows 2000 system? a. A User Access
Pre-Assessment Answers-1 0Pre-Assessment Answers Lesson 1 Pre-Assessment Questions 1. What is the name of a statistically unique number assigned to all users on a Windows 2000 system? a. A User Access
About Backup and Restore, on page 1 Supported Backup and Restore Procedures, on page 3
 About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
About, on page 1 Supported Procedures, on page 3 Back Up Automation Data Using the GUI, on page 4 Restore Automation Data Using the GUI, on page 6 Schedule a Backup of Automation Data Using the GUI, on
User and System Administration
 CHAPTER 2 This chapter provides information about performing user and system administration tasks and generating diagnostic information for obtaining technical assistance. The top-level Admin window displays
CHAPTER 2 This chapter provides information about performing user and system administration tasks and generating diagnostic information for obtaining technical assistance. The top-level Admin window displays
Networks Lab Pod Diagram
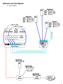 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
