An Automatic Abnormal Data Elimination Method Towards A Higher Quality Finger Vein Dataset
|
|
|
- Bruno Cunningham
- 5 years ago
- Views:
Transcription
1 An Automatic Abnormal Data Elimination Method Towards A Higher Quality Finger Vein Dataset Liao Ni Advisor: Wen-xin Li
2 Outline Motivation Proposed Method Experiments and Results Performance Evaluation Conclusion and Future work Page 2
3 Motivation Since 2009, we have collected a finger vein data set in the millions through PKU sports attendance checking system based on finger-vein recognition Problems during the collection: malfunction of users users registered more than one ID cards users put in the wrong finger users put finger in a wrong way bad environment lighting capture device fault Page 3
4 Motivation abnormal data Interclass low-quality image(interlqi):unexpected high-similarity To propose a method to automatically detect and delete the abnormal data with a reasonable cost to get a higher quality finger vein dataset for the use of further research. Intraclass low-quality image(intralqi):unexpected low-similarity Page 4
5 percentage Proposed Method Get the matching scores of each pair in the image set using a good algorithm % Score Distribution 20.00% genuine 15.00% imposter 10.00% 5.00% 0.00% score Page 5
6 percentage IntraLQI Process 8.00% 6.00% 4.00% 2.00% 0.00% Genuine Score AVE genuine m STD score Threshold Threshold Calculating Formula AVE - m STD efficient for various algorithm Chebyshev's Theorem: For any set of observations (sample or population), the proportion of the values that lie within m standard deviation of the mean is at least 1-1/ m2, where m is any constant greater than 1. Page 6
7 其他 percentage IntraLQI Process Challenge inaccuracy of the algorithm Indicator LR(Lifting Rate) = Method EER original EER set number original set number get matching score of each pair from the same class identify IntraLQI with score lower than threshold AVE 1.55 STD 40.00% 30.00% 20.00% 10.00% 0.00% IntraLQI Score scores remove the whole class which IntraLQI is related to bad but normal data real abnormal data Page 7
8 percentage 其他 InterLQI Process Challenge inaccuracy of the algorithm Method InterLQI Score % 50.00% 0.00% score bad but normal data real abnormal data get matching score of each pair from different classes identify InterLQI with score higher than threshold AVE 1 STD remove the whole class which InterLQI is related to Page 8
9 Experiment experimental purpose determine the coefficient of the threshold calculating formula evaluate the performance of the method experimental condition experimental platform: RATE* GOOD algorithm: the algorithm currently run on the attendance system data source: 1009 classes gathered during spring semester ( marked InterLQI) RATE*(Recognition Algorithm Test Engine): rate.pku.edu.cn Page 9
10 Performance Evaluation I purpose to verify the method is effective on different datasets process choose a certain algorithm to be the GOOD algorithm in the method. Apply the method on different sets. result Dataset Original Set Number Processed Set Number Original EER(%) Set Processed EER(%) Set analysis reasonable cost, higher quality Page 10
11 Performance Evaluation II purpose to verify the method is effective for different algorithms process choose different algorithms to be the GOOD algorithm in the method. Apply the method on a certain set. Run another verification algorithm on the original set and processed set. result GOOD Algorithm/ Verification Algorithm Algorithm1/Algor ithm2 Original Set Number Processed Set Number Original EER(%) Processed EER(%) Algorithm3/Algor ithm1 analysis reasonable cost, higher quality Page 11
12 Conclusion and Future Work Conclusion Propose a method to be applied on finger vein dataset to automatically detect and delete its abnormal data. And we validate its effectiveness through comprehensive experiments. Future Work For a continually increasing date set, how to make use of the proposed method to incrementally detect and delete its abnormal data remains to be solved. Page 12
13 Thanks Thank the teachers! Thank my advisor! Thank those who have helped me during the work! Page 13
Rotation Invariant Finger Vein Recognition *
 Rotation Invariant Finger Vein Recognition * Shaohua Pang, Yilong Yin **, Gongping Yang, and Yanan Li School of Computer Science and Technology, Shandong University, Jinan, China pangshaohua11271987@126.com,
Rotation Invariant Finger Vein Recognition * Shaohua Pang, Yilong Yin **, Gongping Yang, and Yanan Li School of Computer Science and Technology, Shandong University, Jinan, China pangshaohua11271987@126.com,
3.5 Applying the Normal Distribution: Z - Scores
 3.5 Applying the Normal Distribution: Z - Scores Objective: Today s lesson will answer the following questions: 1. How can you use the normal curve to accurately determine the percent of data that lies
3.5 Applying the Normal Distribution: Z - Scores Objective: Today s lesson will answer the following questions: 1. How can you use the normal curve to accurately determine the percent of data that lies
A Framework for Efficient Fingerprint Identification using a Minutiae Tree
 A Framework for Efficient Fingerprint Identification using a Minutiae Tree Praveer Mansukhani February 22, 2008 Problem Statement Developing a real-time scalable minutiae-based indexing system using a
A Framework for Efficient Fingerprint Identification using a Minutiae Tree Praveer Mansukhani February 22, 2008 Problem Statement Developing a real-time scalable minutiae-based indexing system using a
CHAPTER 6 RESULTS AND DISCUSSIONS
 151 CHAPTER 6 RESULTS AND DISCUSSIONS In this chapter the performance of the personal identification system on the PolyU database is presented. The database for both Palmprint and Finger Knuckle Print
151 CHAPTER 6 RESULTS AND DISCUSSIONS In this chapter the performance of the personal identification system on the PolyU database is presented. The database for both Palmprint and Finger Knuckle Print
Math 214 Introductory Statistics Summer Class Notes Sections 3.2, : 1-21 odd 3.3: 7-13, Measures of Central Tendency
 Math 14 Introductory Statistics Summer 008 6-9-08 Class Notes Sections 3, 33 3: 1-1 odd 33: 7-13, 35-39 Measures of Central Tendency odd Notation: Let N be the size of the population, n the size of the
Math 14 Introductory Statistics Summer 008 6-9-08 Class Notes Sections 3, 33 3: 1-1 odd 33: 7-13, 35-39 Measures of Central Tendency odd Notation: Let N be the size of the population, n the size of the
Lecture 3: Chapter 3
 Lecture 3: Chapter 3 C C Moxley UAB Mathematics 12 September 16 3.2 Measurements of Center Statistics involves describing data sets and inferring things about them. The first step in understanding a set
Lecture 3: Chapter 3 C C Moxley UAB Mathematics 12 September 16 3.2 Measurements of Center Statistics involves describing data sets and inferring things about them. The first step in understanding a set
Internal vs. External Parameters in Fitness Functions
 Internal vs. External Parameters in Fitness Functions Pedro A. Diaz-Gomez Computing & Technology Department Cameron University Lawton, Oklahoma 73505, USA pdiaz-go@cameron.edu Dean F. Hougen School of
Internal vs. External Parameters in Fitness Functions Pedro A. Diaz-Gomez Computing & Technology Department Cameron University Lawton, Oklahoma 73505, USA pdiaz-go@cameron.edu Dean F. Hougen School of
Biometrics Technology: Hand Geometry
 Biometrics Technology: Hand Geometry References: [H1] Gonzeilez, S., Travieso, C.M., Alonso, J.B., and M.A. Ferrer, Automatic biometric identification system by hand geometry, Proceedings of IEEE the 37th
Biometrics Technology: Hand Geometry References: [H1] Gonzeilez, S., Travieso, C.M., Alonso, J.B., and M.A. Ferrer, Automatic biometric identification system by hand geometry, Proceedings of IEEE the 37th
CHAPTER 3 ASSOCIATION RULE MINING WITH LEVELWISE AUTOMATIC SUPPORT THRESHOLDS
 23 CHAPTER 3 ASSOCIATION RULE MINING WITH LEVELWISE AUTOMATIC SUPPORT THRESHOLDS This chapter introduces the concepts of association rule mining. It also proposes two algorithms based on, to calculate
23 CHAPTER 3 ASSOCIATION RULE MINING WITH LEVELWISE AUTOMATIC SUPPORT THRESHOLDS This chapter introduces the concepts of association rule mining. It also proposes two algorithms based on, to calculate
The Normal Distribution
 The Normal Distribution Lecture 20 Section 6.3.1 Robb T. Koether Hampden-Sydney College Wed, Sep 28, 2011 Robb T. Koether (Hampden-Sydney College) The Normal Distribution Wed, Sep 28, 2011 1 / 41 Outline
The Normal Distribution Lecture 20 Section 6.3.1 Robb T. Koether Hampden-Sydney College Wed, Sep 28, 2011 Robb T. Koether (Hampden-Sydney College) The Normal Distribution Wed, Sep 28, 2011 1 / 41 Outline
When comparing in different sets of, the deviations should be compared only if the two sets of data use the
 CHEBYSHEV S THEOREM The (or fraction) of any data set lying within K standard deviations of the mean is always 2 the following statements: 1 1, K 1 K At least ¾ or 75% of all values lie within 2 standard
CHEBYSHEV S THEOREM The (or fraction) of any data set lying within K standard deviations of the mean is always 2 the following statements: 1 1, K 1 K At least ¾ or 75% of all values lie within 2 standard
Using Support Vector Machines to Eliminate False Minutiae Matches during Fingerprint Verification
 Using Support Vector Machines to Eliminate False Minutiae Matches during Fingerprint Verification Abstract Praveer Mansukhani, Sergey Tulyakov, Venu Govindaraju Center for Unified Biometrics and Sensors
Using Support Vector Machines to Eliminate False Minutiae Matches during Fingerprint Verification Abstract Praveer Mansukhani, Sergey Tulyakov, Venu Govindaraju Center for Unified Biometrics and Sensors
FACE DETECTION AND LOCALIZATION USING DATASET OF TINY IMAGES
 FACE DETECTION AND LOCALIZATION USING DATASET OF TINY IMAGES Swathi Polamraju and Sricharan Ramagiri Department of Electrical and Computer Engineering Clemson University ABSTRACT: Being motivated by the
FACE DETECTION AND LOCALIZATION USING DATASET OF TINY IMAGES Swathi Polamraju and Sricharan Ramagiri Department of Electrical and Computer Engineering Clemson University ABSTRACT: Being motivated by the
2) In the formula for the Confidence Interval for the Mean, if the Confidence Coefficient, z(α/2) = 1.65, what is the Confidence Level?
 Pg.431 1)The mean of the sampling distribution of means is equal to the mean of the population. T-F, and why or why not? True. If you were to take every possible sample from the population, and calculate
Pg.431 1)The mean of the sampling distribution of means is equal to the mean of the population. T-F, and why or why not? True. If you were to take every possible sample from the population, and calculate
Biometric Security Roles & Resources
 Biometric Security Roles & Resources Part 1 Biometric Systems Skip Linehan Biometrics Systems Architect, Raytheon Intelligence and Information Systems Outline Biometrics Overview Biometric Architectures
Biometric Security Roles & Resources Part 1 Biometric Systems Skip Linehan Biometrics Systems Architect, Raytheon Intelligence and Information Systems Outline Biometrics Overview Biometric Architectures
A hierarchical classification method for finger knuckle print recognition
 Kong et al. EURASIP Journal on Advances in Signal Processing 014, 014:44 RESEARCH A hierarchical classification method for finger knuckle print recognition Tao Kong, Gongping Yang * and Lu Yang Open Access
Kong et al. EURASIP Journal on Advances in Signal Processing 014, 014:44 RESEARCH A hierarchical classification method for finger knuckle print recognition Tao Kong, Gongping Yang * and Lu Yang Open Access
MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question.
 31-32 Review Name 1) Which of the following is the properly rounded mean for the given data? 7, 8, 13, 9, 10, 11 A) 9 B) 967 C) 97 D) 10 2) What is the median of the following set of values? 5, 19, 17,
31-32 Review Name 1) Which of the following is the properly rounded mean for the given data? 7, 8, 13, 9, 10, 11 A) 9 B) 967 C) 97 D) 10 2) What is the median of the following set of values? 5, 19, 17,
3.5 Applying the Normal Distribution: Z-Scores
 3.5 Applying the Normal Distribution: Z-Scores In the previous section, you learned about the normal curve and the normal distribution. You know that the area under any normal curve is 1, and that 68%
3.5 Applying the Normal Distribution: Z-Scores In the previous section, you learned about the normal curve and the normal distribution. You know that the area under any normal curve is 1, and that 68%
Z-TEST / Z-STATISTIC: used to test hypotheses about. µ when the population standard deviation is unknown
 Z-TEST / Z-STATISTIC: used to test hypotheses about µ when the population standard deviation is known and population distribution is normal or sample size is large T-TEST / T-STATISTIC: used to test hypotheses
Z-TEST / Z-STATISTIC: used to test hypotheses about µ when the population standard deviation is known and population distribution is normal or sample size is large T-TEST / T-STATISTIC: used to test hypotheses
8 2 Properties of a normal distribution.notebook Properties of the Normal Distribution Pages
 8 2 Properties of the Normal Distribution Pages 422 431 normal distribution a common continuous probability distribution in which the data are distributed symmetrically and unimodally about the mean. Can
8 2 Properties of the Normal Distribution Pages 422 431 normal distribution a common continuous probability distribution in which the data are distributed symmetrically and unimodally about the mean. Can
How individual data points are positioned within a data set.
 Section 3.4 Measures of Position Percentiles How individual data points are positioned within a data set. P k is the value such that k% of a data set is less than or equal to P k. For example if we said
Section 3.4 Measures of Position Percentiles How individual data points are positioned within a data set. P k is the value such that k% of a data set is less than or equal to P k. For example if we said
Chapter 6. The Normal Distribution. McGraw-Hill, Bluman, 7 th ed., Chapter 6 1
 Chapter 6 The Normal Distribution McGraw-Hill, Bluman, 7 th ed., Chapter 6 1 Bluman, Chapter 6 2 Chapter 6 Overview Introduction 6-1 Normal Distributions 6-2 Applications of the Normal Distribution 6-3
Chapter 6 The Normal Distribution McGraw-Hill, Bluman, 7 th ed., Chapter 6 1 Bluman, Chapter 6 2 Chapter 6 Overview Introduction 6-1 Normal Distributions 6-2 Applications of the Normal Distribution 6-3
Chapter 3. Descriptive Measures. Slide 3-2. Copyright 2012, 2008, 2005 Pearson Education, Inc.
 Chapter 3 Descriptive Measures Slide 3-2 Section 3.1 Measures of Center Slide 3-3 Definition 3.1 Mean of a Data Set The mean of a data set is the sum of the observations divided by the number of observations.
Chapter 3 Descriptive Measures Slide 3-2 Section 3.1 Measures of Center Slide 3-3 Definition 3.1 Mean of a Data Set The mean of a data set is the sum of the observations divided by the number of observations.
A FINGER PRINT RECOGNISER USING FUZZY EVOLUTIONARY PROGRAMMING
 A FINGER PRINT RECOGNISER USING FUZZY EVOLUTIONARY PROGRAMMING Author1: Author2: K.Raghu Ram K.Krishna Chaitanya 4 th E.C.E 4 th E.C.E raghuram.kolipaka@gmail.com chaitu_kolluri@yahoo.com Newton s Institute
A FINGER PRINT RECOGNISER USING FUZZY EVOLUTIONARY PROGRAMMING Author1: Author2: K.Raghu Ram K.Krishna Chaitanya 4 th E.C.E 4 th E.C.E raghuram.kolipaka@gmail.com chaitu_kolluri@yahoo.com Newton s Institute
Fingerprint Matching Using Minutiae-Singular Points Network
 , pp. 375-388 http://dx.doi.org/1.14257/ijsip.215.8.2.35 Fingerprint Matching Using Minutiae-Singular Points Network Iwasokun Gabriel Babatunde Department of Computer Science Federal University of Technology,
, pp. 375-388 http://dx.doi.org/1.14257/ijsip.215.8.2.35 Fingerprint Matching Using Minutiae-Singular Points Network Iwasokun Gabriel Babatunde Department of Computer Science Federal University of Technology,
Disclaimer. Lect 2: empirical analyses of graphs
 462 Page 1 Lect 2: empirical analyses of graphs Tuesday, September 11, 2007 8:30 AM Disclaimer These are my personal notes from this lecture. They may be wrong or inaccurate, and have not carefully been
462 Page 1 Lect 2: empirical analyses of graphs Tuesday, September 11, 2007 8:30 AM Disclaimer These are my personal notes from this lecture. They may be wrong or inaccurate, and have not carefully been
Homography estimation
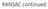 RANSAC continued Homography estimation x w? ~x img H~x w Homography estimation? x img ~x w = H 1 ~x img Homography estimation (0,0) (1,0) (6.4,2.8) (8.0,2.9) (5.6, 4.0) (7.8, 4.2) (0,1) (1,1) Ah =0s.tkhk
RANSAC continued Homography estimation x w? ~x img H~x w Homography estimation? x img ~x w = H 1 ~x img Homography estimation (0,0) (1,0) (6.4,2.8) (8.0,2.9) (5.6, 4.0) (7.8, 4.2) (0,1) (1,1) Ah =0s.tkhk
Active Query Sensing for Mobile Location Search
 (by Mac Funamizu) Active Query Sensing for Mobile Location Search Felix. X. Yu, Rongrong Ji, Shih-Fu Chang Digital Video and Multimedia Lab Columbia University November 29, 2011 Outline Motivation Problem
(by Mac Funamizu) Active Query Sensing for Mobile Location Search Felix. X. Yu, Rongrong Ji, Shih-Fu Chang Digital Video and Multimedia Lab Columbia University November 29, 2011 Outline Motivation Problem
Econ 3790: Business and Economics Statistics. Instructor: Yogesh Uppal
 Econ 3790: Business and Economics Statistics Instructor: Yogesh Uppal Email: yuppal@ysu.edu Chapter 8: Interval Estimation Population Mean: Known Population Mean: Unknown Margin of Error and the Interval
Econ 3790: Business and Economics Statistics Instructor: Yogesh Uppal Email: yuppal@ysu.edu Chapter 8: Interval Estimation Population Mean: Known Population Mean: Unknown Margin of Error and the Interval
CDAA No. 4 - Part Two - Multiple Regression - Initial Data Screening
 CDAA No. 4 - Part Two - Multiple Regression - Initial Data Screening Variables Entered/Removed b Variables Entered GPA in other high school, test, Math test, GPA, High school math GPA a Variables Removed
CDAA No. 4 - Part Two - Multiple Regression - Initial Data Screening Variables Entered/Removed b Variables Entered GPA in other high school, test, Math test, GPA, High school math GPA a Variables Removed
NRS STATE DATA QUALITY CHECKLIST
 A Project of the U.S. Department of Education NRS STATE DATA QUALITY CHECKLIST State: Date: Completed by (name and title): A. Data Foundation and Structure Acceptable Quality 1. State has written assessment
A Project of the U.S. Department of Education NRS STATE DATA QUALITY CHECKLIST State: Date: Completed by (name and title): A. Data Foundation and Structure Acceptable Quality 1. State has written assessment
height VUD x = x 1 + x x N N 2 + (x 2 x) 2 + (x N x) 2. N
 Math 3: CSM Tutorial: Probability, Statistics, and Navels Fall 2 In this worksheet, we look at navel ratios, means, standard deviations, relative frequency density histograms, and probability density functions.
Math 3: CSM Tutorial: Probability, Statistics, and Navels Fall 2 In this worksheet, we look at navel ratios, means, standard deviations, relative frequency density histograms, and probability density functions.
7.1 INTRODUCTION Wavelet Transform is a popular multiresolution analysis tool in image processing and
 Chapter 7 FACE RECOGNITION USING CURVELET 7.1 INTRODUCTION Wavelet Transform is a popular multiresolution analysis tool in image processing and computer vision, because of its ability to capture localized
Chapter 7 FACE RECOGNITION USING CURVELET 7.1 INTRODUCTION Wavelet Transform is a popular multiresolution analysis tool in image processing and computer vision, because of its ability to capture localized
Improving Hand-Based Verification Through Online Finger Template Update Based on Fused Confidences
 Improving Hand-Based Verification Through Online Finger Template Update Based on Fused Confidences Gholamreza Amayeh, George Bebis and Mircea Nicolescu {amayeh, bebis, mircea}@cse.unr.edu Computer Vision
Improving Hand-Based Verification Through Online Finger Template Update Based on Fused Confidences Gholamreza Amayeh, George Bebis and Mircea Nicolescu {amayeh, bebis, mircea}@cse.unr.edu Computer Vision
Discovery of Genuine Functional Dependencies from Relational Data with Missing Values
 Functional Dependencies from Relational Data with Missing VLDB 2018 Dependency Discovery and Data Models Session Rio de Janeiro-Brazil 29 th August 2018 Laure Berti-Equille (LIS, Aix Marseille Uni) (HPI,
Functional Dependencies from Relational Data with Missing VLDB 2018 Dependency Discovery and Data Models Session Rio de Janeiro-Brazil 29 th August 2018 Laure Berti-Equille (LIS, Aix Marseille Uni) (HPI,
Incorporating Touch Biometrics to Mobile One-Time Passwords: Exploration of Digits
 Incorporating Touch Biometrics to Mobile One-Time Passwords: Exploration of Digits Ruben Tolosana, Ruben Vera-Rodriguez, Julian Fierrez and Javier Ortega-Garcia BiDA Lab- Biometrics and Data Pattern Analytics
Incorporating Touch Biometrics to Mobile One-Time Passwords: Exploration of Digits Ruben Tolosana, Ruben Vera-Rodriguez, Julian Fierrez and Javier Ortega-Garcia BiDA Lab- Biometrics and Data Pattern Analytics
Data Presentation. Figure 1. Hand drawn data sheet
 Data Presentation The purpose of putting results of experiments into graphs, charts and tables is two-fold. First, it is a visual way to look at the data and see what happened and make interpretations.
Data Presentation The purpose of putting results of experiments into graphs, charts and tables is two-fold. First, it is a visual way to look at the data and see what happened and make interpretations.
Predictive Analysis: Evaluation and Experimentation. Heejun Kim
 Predictive Analysis: Evaluation and Experimentation Heejun Kim June 19, 2018 Evaluation and Experimentation Evaluation Metrics Cross-Validation Significance Tests Evaluation Predictive analysis: training
Predictive Analysis: Evaluation and Experimentation Heejun Kim June 19, 2018 Evaluation and Experimentation Evaluation Metrics Cross-Validation Significance Tests Evaluation Predictive analysis: training
AUTOMATED human identification is one of the most critical
 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 6, NO. 4, DECEMBER 2011 1259 Human Identification Using Palm-Vein Images Yingbo Zhou and Ajay Kumar, Senior Member, IEEE Abstract This paper
IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 6, NO. 4, DECEMBER 2011 1259 Human Identification Using Palm-Vein Images Yingbo Zhou and Ajay Kumar, Senior Member, IEEE Abstract This paper
Palm Vein Verification System Based on SIFT Matching
 Palm Vein Verification System Based on SIFT Matching Pierre-Olivier Ladoux 1, Christophe Rosenberger 2, and Bernadette Dorizzi 1 1 Institue TELECOM Télécom & Management SudParis 9 Rue Charles Fourier,
Palm Vein Verification System Based on SIFT Matching Pierre-Olivier Ladoux 1, Christophe Rosenberger 2, and Bernadette Dorizzi 1 1 Institue TELECOM Télécom & Management SudParis 9 Rue Charles Fourier,
Collaborative Filtering using a Spreading Activation Approach
 Collaborative Filtering using a Spreading Activation Approach Josephine Griffith *, Colm O Riordan *, Humphrey Sorensen ** * Department of Information Technology, NUI, Galway ** Computer Science Department,
Collaborative Filtering using a Spreading Activation Approach Josephine Griffith *, Colm O Riordan *, Humphrey Sorensen ** * Department of Information Technology, NUI, Galway ** Computer Science Department,
The first few questions on this worksheet will deal with measures of central tendency. These data types tell us where the center of the data set lies.
 Instructions: You are given the following data below these instructions. Your client (Courtney) wants you to statistically analyze the data to help her reach conclusions about how well she is teaching.
Instructions: You are given the following data below these instructions. Your client (Courtney) wants you to statistically analyze the data to help her reach conclusions about how well she is teaching.
So..to be able to make comparisons possible, we need to compare them with their respective distributions.
 Unit 3 ~ Modeling Distributions of Data 1 ***Section 2.1*** Measures of Relative Standing and Density Curves (ex) Suppose that a professional soccer team has the money to sign one additional player and
Unit 3 ~ Modeling Distributions of Data 1 ***Section 2.1*** Measures of Relative Standing and Density Curves (ex) Suppose that a professional soccer team has the money to sign one additional player and
3. CENTRAL TENDENCY MEASURES AND OTHER CLASSICAL ITEM ANALYSES OF THE 2011 MOD-MSA: MATHEMATICS
 3. CENTRAL TENDENCY MEASURES AND OTHER CLASSICAL ITEM ANALYSES OF THE 2011 MOD-MSA: MATHEMATICS This section provides central tendency statistics and results of classical statistical item analyses for
3. CENTRAL TENDENCY MEASURES AND OTHER CLASSICAL ITEM ANALYSES OF THE 2011 MOD-MSA: MATHEMATICS This section provides central tendency statistics and results of classical statistical item analyses for
CVEN Computer Applications in Engineering and Construction. Programming Assignment #2 Random Number Generation and Particle Diffusion
 CVE 0-50 Computer Applications in Engineering and Construction Programming Assignment # Random umber Generation and Particle Diffusion Date distributed: 0/06/09 Date due: 0//09 by :59 pm (submit an electronic
CVE 0-50 Computer Applications in Engineering and Construction Programming Assignment # Random umber Generation and Particle Diffusion Date distributed: 0/06/09 Date due: 0//09 by :59 pm (submit an electronic
Trademark Matching and Retrieval in Sport Video Databases
 Trademark Matching and Retrieval in Sport Video Databases Andrew D. Bagdanov, Lamberto Ballan, Marco Bertini and Alberto Del Bimbo {bagdanov, ballan, bertini, delbimbo}@dsi.unifi.it 9th ACM SIGMM International
Trademark Matching and Retrieval in Sport Video Databases Andrew D. Bagdanov, Lamberto Ballan, Marco Bertini and Alberto Del Bimbo {bagdanov, ballan, bertini, delbimbo}@dsi.unifi.it 9th ACM SIGMM International
Data Mining. 3.5 Lazy Learners (Instance-Based Learners) Fall Instructor: Dr. Masoud Yaghini. Lazy Learners
 Data Mining 3.5 (Instance-Based Learners) Fall 2008 Instructor: Dr. Masoud Yaghini Outline Introduction k-nearest-neighbor Classifiers References Introduction Introduction Lazy vs. eager learning Eager
Data Mining 3.5 (Instance-Based Learners) Fall 2008 Instructor: Dr. Masoud Yaghini Outline Introduction k-nearest-neighbor Classifiers References Introduction Introduction Lazy vs. eager learning Eager
Math 120 Introduction to Statistics Mr. Toner s Lecture Notes 3.1 Measures of Central Tendency
 Math 1 Introduction to Statistics Mr. Toner s Lecture Notes 3.1 Measures of Central Tendency lowest value + highest value midrange The word average: is very ambiguous and can actually refer to the mean,
Math 1 Introduction to Statistics Mr. Toner s Lecture Notes 3.1 Measures of Central Tendency lowest value + highest value midrange The word average: is very ambiguous and can actually refer to the mean,
Prepare a stem-and-leaf graph for the following data. In your final display, you should arrange the leaves for each stem in increasing order.
 Chapter 2 2.1 Descriptive Statistics A stem-and-leaf graph, also called a stemplot, allows for a nice overview of quantitative data without losing information on individual observations. It can be a good
Chapter 2 2.1 Descriptive Statistics A stem-and-leaf graph, also called a stemplot, allows for a nice overview of quantitative data without losing information on individual observations. It can be a good
Regression Test Selection for C++ Software
 Technical Report 99-60-01, Computer Science Department, Oregon State University, January 1999 Regression Test Selection for C++ Authors: Gregg Rothermel Mary Jean Harrold Jeinay Dedhia Software Sanjay
Technical Report 99-60-01, Computer Science Department, Oregon State University, January 1999 Regression Test Selection for C++ Authors: Gregg Rothermel Mary Jean Harrold Jeinay Dedhia Software Sanjay
Use of Extreme Value Statistics in Modeling Biometric Systems
 Use of Extreme Value Statistics in Modeling Biometric Systems Similarity Scores Two types of matching: Genuine sample Imposter sample Matching scores Enrolled sample 0.95 0.32 Probability Density Decision
Use of Extreme Value Statistics in Modeling Biometric Systems Similarity Scores Two types of matching: Genuine sample Imposter sample Matching scores Enrolled sample 0.95 0.32 Probability Density Decision
Confidence Interval of a Proportion
 Confidence Interval of a Proportion FPP 20-21 Using the sample to learn about the box Box models and CLT assume we know the contents of the box (the population). In real-world problems, we do not. In random
Confidence Interval of a Proportion FPP 20-21 Using the sample to learn about the box Box models and CLT assume we know the contents of the box (the population). In real-world problems, we do not. In random
PERSONAL identification and verification both play an
 1 Multimodal Palmprint Biometric System using SPIHT and Radial Basis Function Djamel Samai 1, Abdallah Meraoumia 1, Salim Chitroub 2 and Noureddine Doghmane 3 1 Université Kasdi Merbah Ouargla, Laboratoire
1 Multimodal Palmprint Biometric System using SPIHT and Radial Basis Function Djamel Samai 1, Abdallah Meraoumia 1, Salim Chitroub 2 and Noureddine Doghmane 3 1 Université Kasdi Merbah Ouargla, Laboratoire
STP 226 ELEMENTARY STATISTICS NOTES PART 2 - DESCRIPTIVE STATISTICS CHAPTER 3 DESCRIPTIVE MEASURES
 STP 6 ELEMENTARY STATISTICS NOTES PART - DESCRIPTIVE STATISTICS CHAPTER 3 DESCRIPTIVE MEASURES Chapter covered organizing data into tables, and summarizing data with graphical displays. We will now use
STP 6 ELEMENTARY STATISTICS NOTES PART - DESCRIPTIVE STATISTICS CHAPTER 3 DESCRIPTIVE MEASURES Chapter covered organizing data into tables, and summarizing data with graphical displays. We will now use
A Method of weld Edge Extraction in the X-ray Linear Diode Arrays. Real-time imaging
 17th World Conference on Nondestructive Testing, 25-28 Oct 2008, Shanghai, China A Method of weld Edge Extraction in the X-ray Linear Diode Arrays Real-time imaging Guang CHEN, Keqin DING, Lihong LIANG
17th World Conference on Nondestructive Testing, 25-28 Oct 2008, Shanghai, China A Method of weld Edge Extraction in the X-ray Linear Diode Arrays Real-time imaging Guang CHEN, Keqin DING, Lihong LIANG
Creating Study Package Structures
 Overview A study package structure is an outline of the course components that students are required to complete in order to attain their award. It contains information about majors, streams and units
Overview A study package structure is an outline of the course components that students are required to complete in order to attain their award. It contains information about majors, streams and units
Multimodal Fusion Vulnerability to Non-Zero Effort (Spoof) Imposters
 Multimodal Fusion Vulnerability to Non-Zero Effort (Spoof) mposters P. A. Johnson, B. Tan, S. Schuckers 3 ECE Department, Clarkson University Potsdam, NY 3699, USA johnsopa@clarkson.edu tanb@clarkson.edu
Multimodal Fusion Vulnerability to Non-Zero Effort (Spoof) mposters P. A. Johnson, B. Tan, S. Schuckers 3 ECE Department, Clarkson University Potsdam, NY 3699, USA johnsopa@clarkson.edu tanb@clarkson.edu
Technical White Paper. Behaviometrics. Measuring FAR/FRR/EER in Continuous Authentication
 Technical White Paper Behaviometrics Measuring FAR/FRR/EER in Continuous Authentication Draft version 12/22/2009 Table of Contents Background... 1 Calculating FAR/FRR/EER in the field of Biometrics...
Technical White Paper Behaviometrics Measuring FAR/FRR/EER in Continuous Authentication Draft version 12/22/2009 Table of Contents Background... 1 Calculating FAR/FRR/EER in the field of Biometrics...
News-Oriented Keyword Indexing with Maximum Entropy Principle.
 News-Oriented Keyword Indexing with Maximum Entropy Principle. Li Sujian' Wang Houfeng' Yu Shiwen' Xin Chengsheng2 'Institute of Computational Linguistics, Peking University, 100871, Beijing, China Ilisujian,
News-Oriented Keyword Indexing with Maximum Entropy Principle. Li Sujian' Wang Houfeng' Yu Shiwen' Xin Chengsheng2 'Institute of Computational Linguistics, Peking University, 100871, Beijing, China Ilisujian,
Measures of Central Tendency. A measure of central tendency is a value used to represent the typical or average value in a data set.
 Measures of Central Tendency A measure of central tendency is a value used to represent the typical or average value in a data set. The Mean the sum of all data values divided by the number of values in
Measures of Central Tendency A measure of central tendency is a value used to represent the typical or average value in a data set. The Mean the sum of all data values divided by the number of values in
Automatic Cluster Number Selection using a Split and Merge K-Means Approach
 Automatic Cluster Number Selection using a Split and Merge K-Means Approach Markus Muhr and Michael Granitzer 31st August 2009 The Know-Center is partner of Austria's Competence Center Program COMET. Agenda
Automatic Cluster Number Selection using a Split and Merge K-Means Approach Markus Muhr and Michael Granitzer 31st August 2009 The Know-Center is partner of Austria's Competence Center Program COMET. Agenda
Feature-level Fusion for Effective Palmprint Authentication
 Feature-level Fusion for Effective Palmprint Authentication Adams Wai-Kin Kong 1, 2 and David Zhang 1 1 Biometric Research Center, Department of Computing The Hong Kong Polytechnic University, Kowloon,
Feature-level Fusion for Effective Palmprint Authentication Adams Wai-Kin Kong 1, 2 and David Zhang 1 1 Biometric Research Center, Department of Computing The Hong Kong Polytechnic University, Kowloon,
A casual approach to numerical modeling
 A casual approach to numerical modeling Spring-Mass-Damper System - part 2. by George Lungu It contains a tutorial about the implementation of a static SMD model in Excel
A casual approach to numerical modeling Spring-Mass-Damper System - part 2. by George Lungu It contains a tutorial about the implementation of a static SMD model in Excel
COMPRESSING U-NET USING KNOWLEDGE DISTILLATION
 COMPRESSING U-NET USING KNOWLEDGE DISTILLATION Karttikeya Mangalam Master s Semester Project Computer Vision Lab EPFL, Switzerland Mentored By: Dr. Mathieu Salzmann 17 th January 2018 Introduction Objective
COMPRESSING U-NET USING KNOWLEDGE DISTILLATION Karttikeya Mangalam Master s Semester Project Computer Vision Lab EPFL, Switzerland Mentored By: Dr. Mathieu Salzmann 17 th January 2018 Introduction Objective
FINGER VEIN RECOGNITION USING LOCAL MEAN BASED K-NEAREST CENTROID NEIGHBOR AS CLASSIFIER
 FINGER VEIN RECOGNITION USING LOCAL MEAN BASED K-NEAREST CENTROID NEIGHBOR AS CLASSIFIER By Saba nazari Thesis submitted in fulfillment of the requirements for the degree of bachelor of Science 2012 ACKNOWLEDGEMENT
FINGER VEIN RECOGNITION USING LOCAL MEAN BASED K-NEAREST CENTROID NEIGHBOR AS CLASSIFIER By Saba nazari Thesis submitted in fulfillment of the requirements for the degree of bachelor of Science 2012 ACKNOWLEDGEMENT
Finger Vein Biometric Approach for Personal Identification Using IRT Feature and Gabor Filter Implementation
 Finger Vein Biometric Approach for Personal Identification Using IRT Feature and Gabor Filter Implementation Sowmya. A (Digital Electronics (MTech), BITM Ballari), Shiva kumar k.s (Associate Professor,
Finger Vein Biometric Approach for Personal Identification Using IRT Feature and Gabor Filter Implementation Sowmya. A (Digital Electronics (MTech), BITM Ballari), Shiva kumar k.s (Associate Professor,
Comparison of ROC-based and likelihood methods for fingerprint verification
 Comparison of ROC-based and likelihood methods for fingerprint verification Sargur Srihari, Harish Srinivasan, Matthew Beal, Prasad Phatak and Gang Fang Department of Computer Science and Engineering University
Comparison of ROC-based and likelihood methods for fingerprint verification Sargur Srihari, Harish Srinivasan, Matthew Beal, Prasad Phatak and Gang Fang Department of Computer Science and Engineering University
IT 403 Practice Problems (1-2) Answers
 IT 403 Practice Problems (1-2) Answers #1. Using Tukey's Hinges method ('Inclusionary'), what is Q3 for this dataset? 2 3 5 7 11 13 17 a. 7 b. 11 c. 12 d. 15 c (12) #2. How do quartiles and percentiles
IT 403 Practice Problems (1-2) Answers #1. Using Tukey's Hinges method ('Inclusionary'), what is Q3 for this dataset? 2 3 5 7 11 13 17 a. 7 b. 11 c. 12 d. 15 c (12) #2. How do quartiles and percentiles
Finger-Vein Image Enhancement Using a Fuzzy-Based Fusion Method with Gabor and Retinex Filtering
 Sensors 2014, 14, 3095-3129; doi:10.3390/s140203095 Article OPEN ACCESS sensors ISSN 1424-8220 www.mdpi.com/journal/sensors Finger-Vein Image Enhancement Using a Fuzzy-Based Fusion Method with Gabor and
Sensors 2014, 14, 3095-3129; doi:10.3390/s140203095 Article OPEN ACCESS sensors ISSN 1424-8220 www.mdpi.com/journal/sensors Finger-Vein Image Enhancement Using a Fuzzy-Based Fusion Method with Gabor and
Chapter 2 Describing, Exploring, and Comparing Data
 Slide 1 Chapter 2 Describing, Exploring, and Comparing Data Slide 2 2-1 Overview 2-2 Frequency Distributions 2-3 Visualizing Data 2-4 Measures of Center 2-5 Measures of Variation 2-6 Measures of Relative
Slide 1 Chapter 2 Describing, Exploring, and Comparing Data Slide 2 2-1 Overview 2-2 Frequency Distributions 2-3 Visualizing Data 2-4 Measures of Center 2-5 Measures of Variation 2-6 Measures of Relative
Biometric quality for error suppression
 Biometric quality for error suppression Elham Tabassi NIST 22 July 2010 1 outline - Why measure quality? - What is meant by quality? - What are they good for? - What are the challenges in quality computation?
Biometric quality for error suppression Elham Tabassi NIST 22 July 2010 1 outline - Why measure quality? - What is meant by quality? - What are they good for? - What are the challenges in quality computation?
Distorted Fingerprint Verification System
 Informatica Economică vol. 15, no. 4/2011 13 Distorted Fingerprint Verification System Divya KARTHIKAESHWARAN 1, Jeyalatha SIVARAMAKRISHNAN 2 1 Department of Computer Science, Amrita University, Bangalore,
Informatica Economică vol. 15, no. 4/2011 13 Distorted Fingerprint Verification System Divya KARTHIKAESHWARAN 1, Jeyalatha SIVARAMAKRISHNAN 2 1 Department of Computer Science, Amrita University, Bangalore,
Label Distribution Learning. Wei Han
 Label Distribution Learning Wei Han, Big Data Research Center, UESTC Email:wei.hb.han@gmail.com Outline 1. Why label distribution learning? 2. What is label distribution learning? 2.1. Problem Formulation
Label Distribution Learning Wei Han, Big Data Research Center, UESTC Email:wei.hb.han@gmail.com Outline 1. Why label distribution learning? 2. What is label distribution learning? 2.1. Problem Formulation
Tri-modal Human Body Segmentation
 Tri-modal Human Body Segmentation Master of Science Thesis Cristina Palmero Cantariño Advisor: Sergio Escalera Guerrero February 6, 2014 Outline 1 Introduction 2 Tri-modal dataset 3 Proposed baseline 4
Tri-modal Human Body Segmentation Master of Science Thesis Cristina Palmero Cantariño Advisor: Sergio Escalera Guerrero February 6, 2014 Outline 1 Introduction 2 Tri-modal dataset 3 Proposed baseline 4
Averages and Variation
 Averages and Variation 3 Copyright Cengage Learning. All rights reserved. 3.1-1 Section 3.1 Measures of Central Tendency: Mode, Median, and Mean Copyright Cengage Learning. All rights reserved. 3.1-2 Focus
Averages and Variation 3 Copyright Cengage Learning. All rights reserved. 3.1-1 Section 3.1 Measures of Central Tendency: Mode, Median, and Mean Copyright Cengage Learning. All rights reserved. 3.1-2 Focus
FVC-on Going Test Result for Union Community. on 9 Sep 2009
 FVC-on Going Test Result for Union Community on 9 Sep 2009 1. WHAT IS FVC-on Going? FVC stands for Fingerprint Verification Competition * FVC on Going is the evolution of FVC: The international Fingerprint
FVC-on Going Test Result for Union Community on 9 Sep 2009 1. WHAT IS FVC-on Going? FVC stands for Fingerprint Verification Competition * FVC on Going is the evolution of FVC: The international Fingerprint
Chapter 3: User Authentication
 Chapter 3: User Authentication Comp Sci 3600 Security Outline 1 2 3 4 Outline 1 2 3 4 User Authentication NIST SP 800-63-3 (Digital Authentication Guideline, October 2016) defines user as: The process
Chapter 3: User Authentication Comp Sci 3600 Security Outline 1 2 3 4 Outline 1 2 3 4 User Authentication NIST SP 800-63-3 (Digital Authentication Guideline, October 2016) defines user as: The process
Technical Report. Cross-Sensor Comparison: LG4000-to-LG2200
 Technical Report Cross-Sensor Comparison: LG4000-to-LG2200 Professors: PhD. Nicolaie Popescu-Bodorin, PhD. Lucian Grigore, PhD. Valentina Balas Students: MSc. Cristina M. Noaica, BSc. Ionut Axenie, BSc
Technical Report Cross-Sensor Comparison: LG4000-to-LG2200 Professors: PhD. Nicolaie Popescu-Bodorin, PhD. Lucian Grigore, PhD. Valentina Balas Students: MSc. Cristina M. Noaica, BSc. Ionut Axenie, BSc
VIRTUAL SHAPE RECOGNITION USING LEAP MOTION. David Lavy and Dung Pham
 VIRTUAL SHAPE RECOGNITION USING LEAP MOTION David Lavy and Dung Pham Boston University Department of Electrical and Computer Engineering 8 Saint Mary s Street Boston, MA 02215 www.bu.edu/ece May. 03, 2015
VIRTUAL SHAPE RECOGNITION USING LEAP MOTION David Lavy and Dung Pham Boston University Department of Electrical and Computer Engineering 8 Saint Mary s Street Boston, MA 02215 www.bu.edu/ece May. 03, 2015
COSC160: Detection and Classification. Jeremy Bolton, PhD Assistant Teaching Professor
 COSC160: Detection and Classification Jeremy Bolton, PhD Assistant Teaching Professor Outline I. Problem I. Strategies II. Features for training III. Using spatial information? IV. Reducing dimensionality
COSC160: Detection and Classification Jeremy Bolton, PhD Assistant Teaching Professor Outline I. Problem I. Strategies II. Features for training III. Using spatial information? IV. Reducing dimensionality
Graph Matching Iris Image Blocks with Local Binary Pattern
 Graph Matching Iris Image Blocs with Local Binary Pattern Zhenan Sun, Tieniu Tan, and Xianchao Qiu Center for Biometrics and Security Research, National Laboratory of Pattern Recognition, Institute of
Graph Matching Iris Image Blocs with Local Binary Pattern Zhenan Sun, Tieniu Tan, and Xianchao Qiu Center for Biometrics and Security Research, National Laboratory of Pattern Recognition, Institute of
A NOVEL PERSONAL AUTHENTICATION USING KNUCKLE MULTISPECTRAL PATTERN
 A NOVEL PERSONAL AUTHENTICATION USING KNUCKLE MULTISPECTRAL PATTERN Gayathri Rajagopal, Dhivya Sampath, Saranya Velu and Preethi Sampath Department of Electronics and Communication Engineering, Sri venkateswara
A NOVEL PERSONAL AUTHENTICATION USING KNUCKLE MULTISPECTRAL PATTERN Gayathri Rajagopal, Dhivya Sampath, Saranya Velu and Preethi Sampath Department of Electronics and Communication Engineering, Sri venkateswara
Voiceprint-based Access Control for Wireless Insulin Pump Systems
 Voiceprint-based Access Control for Wireless Insulin Pump Systems Presenter: Xiaojiang Du Bin Hao, Xiali Hei, Yazhou Tu, Xiaojiang Du, and Jie Wu School of Computing and Informatics, University of Louisiana
Voiceprint-based Access Control for Wireless Insulin Pump Systems Presenter: Xiaojiang Du Bin Hao, Xiali Hei, Yazhou Tu, Xiaojiang Du, and Jie Wu School of Computing and Informatics, University of Louisiana
FND Math Orientation MATH TEAM
 FND Math Orientation MATH TEAM Key Goals of Foundation Math Build strong Foundation in Mathematics Improve motivation to learn Inculcate good study habits Enhance independent & mobile learning skills Improve
FND Math Orientation MATH TEAM Key Goals of Foundation Math Build strong Foundation in Mathematics Improve motivation to learn Inculcate good study habits Enhance independent & mobile learning skills Improve
FILTERBANK-BASED FINGERPRINT MATCHING. Dinesh Kapoor(2005EET2920) Sachin Gajjar(2005EET3194) Himanshu Bhatnagar(2005EET3239)
 FILTERBANK-BASED FINGERPRINT MATCHING Dinesh Kapoor(2005EET2920) Sachin Gajjar(2005EET3194) Himanshu Bhatnagar(2005EET3239) Papers Selected FINGERPRINT MATCHING USING MINUTIAE AND TEXTURE FEATURES By Anil
FILTERBANK-BASED FINGERPRINT MATCHING Dinesh Kapoor(2005EET2920) Sachin Gajjar(2005EET3194) Himanshu Bhatnagar(2005EET3239) Papers Selected FINGERPRINT MATCHING USING MINUTIAE AND TEXTURE FEATURES By Anil
Advanced Systems Lab Report
 Advanced Systems Lab Report Autumn Semester 2018 Name: YOUR NAME Legi: YOUR LEGI Grading Section 1 2 3 4 5 6 7 Total Points Version: 25.09.2018 1 Notes on writing the report (remove this page for submission)
Advanced Systems Lab Report Autumn Semester 2018 Name: YOUR NAME Legi: YOUR LEGI Grading Section 1 2 3 4 5 6 7 Total Points Version: 25.09.2018 1 Notes on writing the report (remove this page for submission)
Musings on Analysis of Measurements of a Real-Time Workload
 Musings on Analysis of Measurements of a Real-Time Workload Analysis of real-time performance is often focused on the worst case "bad" value, such as maximum latency or maximum interrupt disabled time.
Musings on Analysis of Measurements of a Real-Time Workload Analysis of real-time performance is often focused on the worst case "bad" value, such as maximum latency or maximum interrupt disabled time.
Sec 6.3. Bluman, Chapter 6 1
 Sec 6.3 Bluman, Chapter 6 1 Bluman, Chapter 6 2 Review: Find the z values; the graph is symmetrical. z = ±1. 96 z 0 z the total area of the shaded regions=5% Bluman, Chapter 6 3 Review: Find the z values;
Sec 6.3 Bluman, Chapter 6 1 Bluman, Chapter 6 2 Review: Find the z values; the graph is symmetrical. z = ±1. 96 z 0 z the total area of the shaded regions=5% Bluman, Chapter 6 3 Review: Find the z values;
Introduction to Artificial Intelligence
 Introduction to Artificial Intelligence COMP307 Evolutionary Computing 3: Genetic Programming for Regression and Classification Yi Mei yi.mei@ecs.vuw.ac.nz 1 Outline Statistical parameter regression Symbolic
Introduction to Artificial Intelligence COMP307 Evolutionary Computing 3: Genetic Programming for Regression and Classification Yi Mei yi.mei@ecs.vuw.ac.nz 1 Outline Statistical parameter regression Symbolic
Outline. Incorporating Biometric Quality In Multi-Biometrics FUSION. Results. Motivation. Image Quality: The FVC Experience
 Incorporating Biometric Quality In Multi-Biometrics FUSION QUALITY Julian Fierrez-Aguilar, Javier Ortega-Garcia Biometrics Research Lab. - ATVS Universidad Autónoma de Madrid, SPAIN Loris Nanni, Raffaele
Incorporating Biometric Quality In Multi-Biometrics FUSION QUALITY Julian Fierrez-Aguilar, Javier Ortega-Garcia Biometrics Research Lab. - ATVS Universidad Autónoma de Madrid, SPAIN Loris Nanni, Raffaele
Measures of Central Tendency
 Page of 6 Measures of Central Tendency A measure of central tendency is a value used to represent the typical or average value in a data set. The Mean The sum of all data values divided by the number of
Page of 6 Measures of Central Tendency A measure of central tendency is a value used to represent the typical or average value in a data set. The Mean The sum of all data values divided by the number of
6th Grade Advanced Math Algebra
 6th Grade Advanced Math Algebra If your student is considering a jump from 6th Advanced Math to Algebra, please be advised of the following gaps in instruction. 19 of the 7th grade mathematics TEKS and
6th Grade Advanced Math Algebra If your student is considering a jump from 6th Advanced Math to Algebra, please be advised of the following gaps in instruction. 19 of the 7th grade mathematics TEKS and
AUTOMATED STUDENT S ATTENDANCE ENTERING SYSTEM BY ELIMINATING FORGE SIGNATURES
 AUTOMATED STUDENT S ATTENDANCE ENTERING SYSTEM BY ELIMINATING FORGE SIGNATURES K. P. M. L. P. Weerasinghe 149235H Faculty of Information Technology University of Moratuwa June 2017 AUTOMATED STUDENT S
AUTOMATED STUDENT S ATTENDANCE ENTERING SYSTEM BY ELIMINATING FORGE SIGNATURES K. P. M. L. P. Weerasinghe 149235H Faculty of Information Technology University of Moratuwa June 2017 AUTOMATED STUDENT S
Data Mining Clustering
 Data Mining Clustering Jingpeng Li 1 of 34 Supervised Learning F(x): true function (usually not known) D: training sample (x, F(x)) 57,M,195,0,125,95,39,25,0,1,0,0,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0 0
Data Mining Clustering Jingpeng Li 1 of 34 Supervised Learning F(x): true function (usually not known) D: training sample (x, F(x)) 57,M,195,0,125,95,39,25,0,1,0,0,0,1,0,0,0,0,0,0,1,1,0,0,0,0,0,0,0,0 0
Fusion of Hand Geometry and Palmprint Biometrics
 (Working Paper, Dec. 2003) Fusion of Hand Geometry and Palmprint Biometrics D.C.M. Wong, C. Poon and H.C. Shen * Department of Computer Science, Hong Kong University of Science and Technology, Clear Water
(Working Paper, Dec. 2003) Fusion of Hand Geometry and Palmprint Biometrics D.C.M. Wong, C. Poon and H.C. Shen * Department of Computer Science, Hong Kong University of Science and Technology, Clear Water
USING MAKE-UP FORMS IN WEB ATTENDANCE
 USING MAKE-UP FORMS IN WEB ATTENDANCE Pitt Community College Revised 4/10/13 2 Using Make-up forms in Web Attendance Batch Attendance Entry Class Cancelled Faculty or Designated Staff Members complete
USING MAKE-UP FORMS IN WEB ATTENDANCE Pitt Community College Revised 4/10/13 2 Using Make-up forms in Web Attendance Batch Attendance Entry Class Cancelled Faculty or Designated Staff Members complete
DEFORMABLE MATCHING OF HAND SHAPES FOR USER VERIFICATION. Ani1 K. Jain and Nicolae Duta
 DEFORMABLE MATCHING OF HAND SHAPES FOR USER VERIFICATION Ani1 K. Jain and Nicolae Duta Department of Computer Science and Engineering Michigan State University, East Lansing, MI 48824-1026, USA E-mail:
DEFORMABLE MATCHING OF HAND SHAPES FOR USER VERIFICATION Ani1 K. Jain and Nicolae Duta Department of Computer Science and Engineering Michigan State University, East Lansing, MI 48824-1026, USA E-mail:
Efficient Top-k Algorithms for Fuzzy Search in String Collections
 Efficient Top-k Algorithms for Fuzzy Search in String Collections Rares Vernica Chen Li Department of Computer Science University of California, Irvine First International Workshop on Keyword Search on
Efficient Top-k Algorithms for Fuzzy Search in String Collections Rares Vernica Chen Li Department of Computer Science University of California, Irvine First International Workshop on Keyword Search on
Quality Assessment for Fingerprints Collected by Smartphone Cameras
 2013 IEEE Conference on Computer Vision and Pattern Recognition Workshops Quality Assessment for Fingerprints Collected by Smartphone Cameras Guoqiang Li, Bian Yang, Martin Aastrup Olsen, and Christoph
2013 IEEE Conference on Computer Vision and Pattern Recognition Workshops Quality Assessment for Fingerprints Collected by Smartphone Cameras Guoqiang Li, Bian Yang, Martin Aastrup Olsen, and Christoph
Classroom Messaging Summary
 lassroom Messaging Reports of 3 10/21/2016 7:49 AM Important: This feature is only visible if your system includes the Classroom Messaging feature. For more information regarding the Classroom Messaging
lassroom Messaging Reports of 3 10/21/2016 7:49 AM Important: This feature is only visible if your system includes the Classroom Messaging feature. For more information regarding the Classroom Messaging
