Shyjan Mahamud Karvel K. Thornber Lance R. Williams. Carnegie Mellon University 4 Independence Way University of New Mexico
|
|
|
- Pauline McKinney
- 6 years ago
- Views:
Transcription
1 Segmentation of Salient Closed Contours from Real Images Shyjan Mahamud Karvel K. Thornber Lance R. Williams Dept. of Computer Science NEC Research Institute, Inc. Dept. of Computer Science Carnegie Mellon University 4 Independence Way University of New Mexico Pittsburgh, PA Princeton, NJ Albuquerque, NM Abstract Using a saliency measure based on the global property of contour closure, we have developed a method that reliably segments out salient contours bounding unknown objects from real edge images. The measure also incorporates the Gestalt principles of proximity and smooth continuity that previous methods have exploited. Unlike previous measures, we incorporate contour closure by nding the eigen-solution associated with a stochastic process that models the distribution of contours passing through edges in the scene. The segmentation algorithm utilizes the saliency measure to identify multiple closed contours by nding stronglyconnected components on an induced graph. The determination of strongly-connected components is a direct consequence of the property of closure. We report for the rst time, results on large real images for which segmentation takes an average of about 10 secs per object on a general-purpose workstation. The segmentation is made ecient for such large images by exploiting the inherent symmetry in the task. 1 Introduction Visual perception evolved in a world of objects many of which are bounded by smooth closed contours. We hypothesize that these contours obey a stochastic distribution which is utilized by perceptual processes in nding contours bounding objects. In prior work [10, 12, 13] this distribution has been modeled and used to derive a saliency measure that exploits the closure of contours bounding objects. It was found that this measure provides a signicant improvement over previous approaches in highlighting edges lying on contours bounding objects in small synthetic scenes created from contours of real objects and natural background texture [13]. However, no method was presented for actually segmenting out the salient object contours. Despite the eectiveness of the saliency measure, it will be shown later that a simple threshold on the saliency measure is not sucient for segmentation, escpecially in cases where two or more object contours have similar saliencies. In this paper, we present a method for segmenting out multiple contours bounding salient objects. Moreover, previously [13] the determination of the saliencies was computationally infeasible for large real images. We have developed an ecient technique that exploits the symmetry inherent in the task, using which, we report for the rst time, results on large real images. Given an edge image as in Fig. 1 (a), we would like to extract out separately the individual contours bounding the two pears. We wish to achieve such a segmentation with no a-priori knowledge of the specic objects that generate these contours. Such a task is one of the goals of perceptual grouping. In lieu of any specic knowledge about the objects generating the contours, we impose a subset of the Gestalt principles for perceptual organization. Most previous approaches to perceptual grouping of edges have incorporated the local principles of proximity of edges and smooth-continuation of contours in some form or other (e.g., [4, 8]). These methods assume that successive edges are in close proximity and that contours bounding objects are smooth. In addition to these two local properties, we exploit the global property that contours bounding objects must be closed. Unlike proximity and smooth-continuation, closure cannot be reduced to any local property of the contour. Previous approaches [2, 3]have used graph based search techniques to nd closed contours. A graph of anities between edges is constructed where the anities model proximity and smooth-continuation. The anity between two edges is a purely local measure that is proportional to the likelihood that a smooth contour (open or closed) passes through the given edges. Closure is imposed by searching the graph for closed contours while minimizing a global cost function that is related to how salient the closed contours are. Our approach diers from these previous approaches because we rst use the local anity measure (which as noted above does not dierentiate between open and closed contours) to compute a global
2 saliency measure, which is proportional to the relative number of closed contours which join a pair of edges. Such a measure for closed contours was rst proposed and compared extensively with previous approaches (including [7, 8, 12]) that do not incorporate closure in [13]. It is only after the computation of this global saliency that we employ a graph search to identify individual closed contours. We will show that in our case, the incorporation of closure in the saliency measure leads naturally to a specic type of graph search, namely, the determination of strongly connected components. This dependency of the specic graph search used on the saliency measure is a distinguishing feature of our work as compared with previous approaches where generic search techniques have been employed that are not dependent on the properties of the specic saliency measures that were used. To illustrate the crucial role played by the global property of closure, we show that a method based on a purely local anity measure produces poor segmentations. The determination of the saliency measure requires the solution of an eigen-problem of a matrix that exhibits a special kind of symmetry. Ordinary techniques for the solution of the eigen-problem are infeasible for large real images. We have developed ecient techniques that exploit the special symmetry of the matrix to signicantly reduce the time required to compute the eigen-solution. In this paper, we report the rst results on real images with a large number of edges. Our technique reduces the time taken to compute the segmentation for each object contour from an average of around 2 1=2 hrs. to around 10 seconds. 2 Problem Formulation Since the Gestalt principles of proximity and smooth-continuation arise from local properties of the positions and orientations of two edges, we can model them using only local information. Following [10, 12], both of these local properties can be modeled by the distribution of smooth curves that join two given edges. The distribution of curves is modeled by a particle with motion determined by a stochastic process favoring short, smooth, trajectories. Given two directed edges i and j, they determine the probability that a particle starts with the position and direction of edge i and ends with the position and direction of edge j. The particles leave or arrive at an edge at a constant speed independent of the edge. The \anity" from edge i to edge j is denoted by P ji and is the sum of the probabilities of all paths that a particle can take between the two edges (see [10] for details). Essentially, two parameters control the motion of the particle and embody the principles of proximity and smooth-continuation. Each particle has a half-life () which models the principle of proximity. The variance (T ) of the directional change of the particle model the principle of smooth-continuation. The speed determines the eective scale at which the scene is analyzed, since the anity between a pair of edges varies with the speed of the particle. At larger speeds, a pair of edges are eectively closer to each other, whereas at slower speeds the same pair are eectively farther apart. In our application we choose a xed speed that we judge to give a good eective scale for all images. Because particles need not reach any another edge due to the half-life, in general Pj P ji < 1. Hence P is not a stochastic (Markov) matrix, and methods based on Markov chains are not applicable. While closed contours do form a Markov chain, the corresponding Markov matrix for the edge saliencies is not known until the edge and link saliencies have been determined. Smooth-continuity of a curve between two edges implies that the tangent at any point along the curve is continuous. Such tangent-continuity for curves passing between a pair of edges is modeled by the smooth stochastic motion of the particle going from one edge to the other. If we wish to extend the curves to include additional edges then tangent continuity must be enforced at the edges themselves. A contour coming in along a given direction must continue along that direction to satisfy tangent-continuity. This requirement can be ensured by replacing each edge of a given orientation with two oppositely directed edges. A contour can come into and leave a directed edge only along a single direction. If we do not impose tangentcontinuity at the edges, we could get contours with cusps (i.e., reversals in direction) at the edges, which are not judged to be salient in practice. For more details see [13]. Since every directed edge i has a sibling edge at the same position but pointing in the opposite direction, it will be convenient to denote the sibling edge by {. Imposing tangent-continuity through directed edges has an important implication for the structure of the matrix of anities P. From symmetry, the probability that any particle travels along a curve starting from edge i and ending in edge j is the same as the probability of a particle traveling the same curve along the reverse direction from edge to edge {. Hence P ji = P {. We call this special symmetry of the anity matrix reversal-symmetry which is distinct from the usual symmetry P ji = P ij which need not hold in general. Reversal-symmetry has important implications for both the form of
3 the expressions which dene the saliencies and for eciently computing them. In the rest of the paper we will have occasion to associate a vector s with the set of directed edges (e.g. the vector of saliencies for each directed edge), one component for each directed edge. Analogous with the case for edges, a component of such avector s i associated with edge i will have a sibling component denoted by s i = s { associated with edge {. 3 Saliency measure In this section, we rst motivate the expression for the saliency measure [13]. We then show that the saliency measure can be determined by the solution to an eigen-problem associated with the anity matrix P. Given an edge image, we dene a closed contour as a nite closed sequence of edges. By a closed sequence we mean that if we start from any edge in the sequence and trace out the contour we will return to the same edge. Each closed contour has a likelihood (or probability) associated with it, which we denote by p() and is the product of the transition probabilities (given by the anity matrix P )between successive edges in the contour. 3.1 Edge Saliency We would like to dene our saliency measure for an edge to be related to the likelihoods of the various closed contours that thread through that edge. Rather than derive the contribution of each individual closed contour to the saliency for an edge, it is simpler to consider the contribution of the ensemble of all closed contours through that edge by considering the set of innite closed contours passing through that edge. Each innite closed contour can be decomposed into a sequence of nite closed contours, and hence the relative likelihood of dierent innite closed contours passing through an edge depends on the relative likelihood of the individual nite closed contours that they are composed of. In order to calculate the relative saliencies of innite contours, we start by considering the relative saliencies of closed contours of nite but large length and take the limit as the length goes to in- nity. Restricting ourselves to nite contours for now, the saliency of an edge should be proportional to the expected number of closed contours that pass through that edge. The expected number of closed contours of length n that thread through edge i is simply the sum of the probabilities X of all such closed contours : = p( j i 2 ; jj = n) (1) E n i Since we are interested in the relative saliencies of the various innite contours that thread through dierent edges, we take the limit n!1for the expected number of closed contours through a given edge i relative to the expected number through all edges and obtain the formal denition for the saliency of edge i : C i = lim P i n!1 E n j En j With this denition, it turns out that there is a simple relationship between edge saliencies and the eigenvector corresponding to the largest eigenvalue of the anity matrix P. Theorem 1 (First Saliency Theorem) The saliency for edge i is given by : C i = s i s i (2) where the s i 's are the components of the eigenvector (normalized such that Pi s is i =1)corresponding to the largest eigenvalue in magnitude of the anity matrix P, i.e. Ps = s. Proof. See [5] and also [13] for an earlier proof. Note that due to reversal-symmetry, wewould expect C i = C { as can be veried from the expression above. 3.2 Link Saliency For the purpose of segmentation, in addition to the edge saliencies, we will also need information that will help us trace out contours given a starting edge. Specically, given two edges j and i we would like to know the relative likelihood that closed contours pass through edges j and i successively. We dene the link saliency C ij to be the relative saliencies of the closed contours that pass through edges j and i successively. Analogous to the denition for the edge saliencies, we have : C ij = lim n!1 P En ij l En l where E n ij is the expected number of closed contours of length n that go through edges j and i successively, and E n is as dened before in (1). The link saliencies also turn out to have a simple relationship with l the eigenvector corresponding to the largest eigenvalue of P. Theorem 2 (Second Saliency Theorem) The link-saliencies between any two edges j and i are given by : C ij = s ip ij s j (3)
4 (a) (b) Figure 1: (a) An example edge image created from two copies of a real pear contour superimposed on a background texture (b) Saliency plot. where the s i 's are the components of the eigenvector (normalized such that Pi s is i =1)corresponding to the largest eigenvalue of the anity matrix P. Proof. See [5]. It should be noted that the notion of the edge saliencies C i 's was rst introduced in [13]. However, the notion of link saliencies and the above theorem is new and has not been presented before. Again, as in the case of the edge saliencies, due to reversal-symmetry we would expect C ij = C { as can be veried from the expression above (recall, P ij = P { and s i = s i ). Since we are concerned with closed contours, an important conservation property holds for all edges. Any closed contour that goes from some edge k into a second edge i must continue onto some third edge j. This is not necessarily true in the case of open contours. We conrm this conservation property and at the same time use it as a consistency check onthe expressions for the C ij 's and C i 's : X X s i (P ik s k ) C ik = = s i(s i ) =s i s i = C i k k Doing a similar calculation for Pj C ji, we nd X X C ik = C i = k j C ji We conclude this section by demonstrating how well our saliency measure performs for the two-pear example of Fig. 1. The saliency measure for each edge in the gure was determined through the expressions for C i in equation (2) after solving for the largest eigenvalue of P and its corresponding eigenvector. The saliency plot is shown in Fig. 1 (b). The length of an edge in the plot is proportional to its saliency. As can be seen, the edges bounding both pears have high (and comparable) saliencies. The saliencies of all other edges have been suppressed (numerically, their saliencies are 20 orders of magnitude smaller than those of the pears). In order to separately identify the two contours bounding the pears, we might think of simply thresholding the saliencies. However, as illustrated in this example (and in general), it is possible for such a simple thresholding scheme to group together edges bounding distinct objects. In the next section, we develop a more robust approach that uses the link saliencies C ij 's to group together the set of edges that belong to distinct objects. 4 Segmentation The goal of segmentation is to group together in distinct sets, edges bounding distinct objects in the scene. To motivate our segmentation algorithm, consider the hypothetical case where some oracle provided us with a set S of closed contours in the scene whose saliencies are above some threshold. We can construct a graph whose vertices correspond to the edges in our scene. We create a directed link in this graph from edge i to edge j if i and j are successive edges in some salient contour in S. It is proved in [5] that such a construction induces a partition of the graph into a set of isolated strongly-connected components. A strongly-connected component [1] is a set of edges in which any pair of edges i and j have a path from one to the other, i.e., i j as well as j i. In general each strongly-connected component will contain multiple salient contours that share common edges. It is shown in [5] that the partition into a set of stronglyconnected components is a direct consequence of the property of closure of the contours in S. As noted in the introduction, the strong dependence between the nature of the partition and the property of closure is a distinguishing feature of our approach, as compared with other approaches [2, 3] that employ generic graph search techniques that are not dependent onany specic property of the saliency measures used. More precisely, in our approach, the determination of strongly-connected components makes sense only in the context of using a saliency measure that incorporates closure. In practice, of course, we do not know the salient contours beforehand. Nevertheless, since the links in the salient contours become the links in the graph, all we need to know is which of the links are salient, i.e. the likelihood that some salient contour passes through a given link. The link-saliencies (C ij 's) provide precisely an encoding of such information. Ideally, the set of edges will be partitioned into
5 isolated components. However, in practice not all of the components provide reliable segmentations. The dominant contours tend to suppress the saliencies of all other contours to such an extent that the saliencies of these non-dominant contours are not sucient to induce components that can be isolated reliably. Hence in practice, we begin by extracting the most salient contours. Since such contours will normally pass through the most salient edge, we rst identify the contours corresponding to the strongly-connected component containing the most salient edge. Having identied the most salient contours, we suppress their link saliencies in order to reveal the next set of dominant contours. We suppress the current set of dominant contours by deating the anities of all links among the edges in the strongly-connected component. Specically, ifi and j are edges in the component, then the link i! j is deated by setting P ji = 0 (as well as setting the reversal-symmetric \sibling" P { = 0). We then iterate this process to reveal multiple salient contours. Again considering the ideal case, the stronglyconnected component containing the most salient edge will be isolated from the other components. In practice, due to noise, some of the C ij 's might wrongly indicate that the strongly-connected component containing the most salient edge is connected to one or more of the other strongly-connected components. Nevertheless, we can extract the component ofinter- est by utilizing an important property of stronglyconnected components{the set of edges in a stronglyconnected component containing a given edge is the intersection of the set of edges reachable from the given edge and the set of edges reachable from the same edge when all the links have their directions reversed [1]. In our case, due to reversal-symmetry, the above property reduces to a particularly simple form. In order to identify the strongly-connected component containing the most salient edge i, we nd the intersection of the set of undirected edges reachable from edge i and the set of undirected edges reachable from { (note that both i and { have the same saliency as discussed in section 3). 5 Results We show results of our segmentation algorithm on a few real images. All the images were taken using a Kodak DC50 480x480 pixel digital color camera. The Canny edge detector was run on the images after converting them to greyscale, with the parameters =3:0, low hysteresis threshold = 0:2 and high hysteresis threshold = 0:8. The set of edges returned by the Canny edge detector were found to be quite re- 3 4 (a) (b) Figure 2: Fruits on concrete. (a) Greyscale image with the segmented contours numbered in the order they are extracted (b) Canny edge output. dundant. The edges are sampled to improve running times with almost no sacrice in performance. In our experiments we sample the edges such that no two edges are closer than 5 pixels apart. The entries of the anity matrix P were calculated with parameter settings (see x 2 for their descriptions and also [10]) = 0:15, T = 0:004 and = 5:0. All edge images are remapped to a image size. Since the anity matrix P has a special symmetry (the reversal symmetry), we had previously developed an algorithm that nds the eigenvector corresponding to the largest eigenvalue of P (required for the computation of our saliency measures) by exploiting the reversal symmetry. See [11] for details. In our rst example we chose a simple scene where non-occluding objects (fruits) were placed on a textured background 2 1
6 1 2 Figure 3: Fruits on concrete. When the C ij 's have been replaced by P ij 's the segmentation during the second iteration breaks down (see text) (concrete). Fig. 2 shows four fruits on a concrete background in greyscale (a) and the corresponding edge image (b) (with 2800 directed edges after the sampling process described above). Notice that the contrast between the texture of the fruit on the top-left (a cantelope) and that of the background is quite low. As a result, few edges are detected along some parts of the boundary of the cantelope. Superimposed on Fig. 2 (a) are the contours which are identied during the successive iterations of the segmentation algorithm. It is interesting to note that the contour bounding the cantelope has been extracted despite the fact that there are large gaps in some parts of the contour. We next show the importance of the global information encoded by our link saliencies C ij 's for segmentation by replacing them with the P ij 's that encode only local information. The edge saliencies C i 's are left unchanged. With this replacement, the segmentation algorithm extracts out the same contour in the rst iteration as the original algorithm with the C ij 's. Note that this contour is easy to trace out since there are no large gaps present between successive edges of the contour. However, the hard part is to get a starting edge (i.e., the most salient edge in the current iteration) which (for this demonstration) is still being provided by the C i 's. Fig. 3 shows the segmentation after the second iteration. As can be seen, the segmentation completely breaks down. The P ij 's are sucient as long as we start o from the most salient edge in each iteration and there are no large gaps in the contours being traced. The breakdown in the second iteration shows the need for the more global information encoded in the C ij 's in cases where there are large gaps Figure 4: Fruits on grass. Greyscale image with segmentations superimposed. in the contours being traced. The eigen-solver for the matrix P described above (see [11] for details) is adaptive, the time roughly varying according to the complexity of the contours extracted and the number of edges in it. As expected the rst iteration took the least time of 3 sec since the contour extracted is relatively simple. The third iteration took the longest time of 20 sec possibly because of the large gaps in the contour being extracted (bounding the cantelope). The average time for the 4 iterations is 9:9 sec. Fig. 4 shows the same four fruits with grass as the background and with one of the fruits occluding another. Due to poor contrast between the two dark fruits and the background the Canny edge detector does not reliably detect the edges bounding the two fruits. The fruits are hardly salient in the edge image (not shown) even for human observers. Our algorithm can be expected to extract out contours only when provided with reliable edge information. In this case the algorithm picks out only the other two fruits in the image. Of the two fruits that it does pick out, one partly occludes the other. Due to the poor contrast between the two fruits, the edge information (especially the orientation) is quite poor in the region around the occlusion. However, despite this fact, and the fact that the contour bounding the occluded fruit contains a large gap at the occlusion, the algorithm segments out both fruits individually. Finally, Fig. 5 shows an example where there are signicant shadows (around the stones) which produce strong smooth contours. However, since they are open contours, they are not as salient as the closed contours bounding the stones and hence do not confuse the algorithm.
7 3 4 Figure 5: Stones on pavement. Greyscale image with segmentations superimposed. 6 Conclusion 2 1 We have demonstrated the usefulness of a saliency measure based on the global property of contour closure in segmenting out multiple closed contours from real images. We have shown the importance of the global information encoded by our link saliencies C ij 's for segmentation as opposed to using just the P ij 's that encode only local information. Our approach to grouping edges into salient contours involves the solution of an eigen-problem. Recently, other approaches [6, 9, 7] have also proposed grouping image features by solving a corresponding eigen-problem. The normalized minimum-cut approach proposed in [9] can group more general image features than our approach can. However, since we restrict ourselves to grouping edges into salient closed contours, we are able to impose the important constraint of edge-directionality that is not applicable for other features like pixel intensities. Also, imposing edge-directionality results in a non-symmetric anity matrix P for which the min-cut approach proposed in [9] does not apply. As noted in x 2, we can get a symmetric anity matrix if we do not impose edgedirectionality, in which case the min-cut approach would apply. However, the symmetric anity matrix permits contours with cusps at the edges to be salient (see the discussion in x 2). Hence, we would expect poor performance with a min-cut approach when edgedirectionality is not imposed. The dominant eigenvector approach that was proposed in [6, 7], while applicable to more general features than edges, also applies only to symmetric matrices and hence cannot exploit edge-directionality. Summarizing, since in this paper, we are interested in nding out how much can be accomplished using only edge information, methods that exploit constraints from the specic domain, such as ours, are expected to give better results compared with more general-purpose methods. The segmentation algorithm assumes a xed value for the speed of the particle modeling the distribution of curves between two given edges. Equivalently, this xes the eective scale or size for the input image (see x 2). A more principled approach would be able to extract out a contour regardless of the rate at which its edges are sampled. A straightforward approach would be to sweep the scale (by varying the speed ) in each iteration and nd the most salient contour across all scales (see [11]). Contours with dierent samplings would become dominant at dierent scales. We are currently investigating this approach and expect it to result in improved, scale-invariant segmentations. References [1] Cormen, T.H., Leiserson, C.E. and Rivest, R.L Introduction to Algorithms, Chapter 23, MIT Press. [2] Elder, J.H. and Zucker, S.W Computing contour closure. In ECCV '96, Cambridge, UK. Vol. I:14{18. [3] Jacobs, D Robust and Ecient Detection of Convex Groups. In CVPR, 770{771. [4] Lowe, D.G Perceptual Organization and Visual Recognition, Kluwer, Boston. [5] Mahamud, S., Thornber, K.K. and Williams, L.R Extracting Multiple Salient Closed Contours from Real Images. NEC Tech. Report [6] Perona, P. and Freeman, W A Factorization Approach to Grouping. In ECCV, Freiburg, Germany. [7] Sarkar, S. and Boyer, K Quantitative Measures for Change based on Feature Organization: Eigenvalues and Eigenvectors, In CVPR '96, San Fransisco, CA. [8] Shashua, A. and Ullman, S \Structural Saliency : The Detection of Globally Salient Structures Using a Locally Connected Network", In ICCV, FL. [9] Shi, J. and Malik, J Normalized Cuts and Image Segmentation. In CVPR '97, Puerto Rico, USA. [10] Thornber, K.K. and Williams, L.R Analytic Solution of Stochastic Completion Fields. Biol. Cybern. 75:141{151. [11] Thornber, K.K., Mahamud, S. and Williams, L.R The Eigenvalue Problem for Reversal Matrices. NEC Tech. Report [12] Williams, L.R. and Jacobs, D.W Local Parallel Computation of Stochastic Completion Fields. Neural Computation 9:859{881. [13] Williams, L.R. and Thornber, K.K A Comparison of Measures for Detecting Natural Shapes in Cluttered Backgrounds. In ECCV, Freiburg, Germany.
Edge Grouping Combining Boundary and Region Information
 University of South Carolina Scholar Commons Faculty Publications Computer Science and Engineering, Department of 10-1-2007 Edge Grouping Combining Boundary and Region Information Joachim S. Stahl Song
University of South Carolina Scholar Commons Faculty Publications Computer Science and Engineering, Department of 10-1-2007 Edge Grouping Combining Boundary and Region Information Joachim S. Stahl Song
Edge Grouping for Detecting Salient Boundaries with Sharp Corners
 Edge Grouping for Detecting Salient Boundaries with Sharp Corners Joachim S. Stahl Department of Computer Science Clarkson University, Potsdam, NY 13676 jstahl@clarkson.edu Abstract. The Gestalt law of
Edge Grouping for Detecting Salient Boundaries with Sharp Corners Joachim S. Stahl Department of Computer Science Clarkson University, Potsdam, NY 13676 jstahl@clarkson.edu Abstract. The Gestalt law of
Carnegie Mellon University. Pittsburgh, PA [6] require the determination of the SVD of. the measurement matrix constructed from the frame
![Carnegie Mellon University. Pittsburgh, PA [6] require the determination of the SVD of. the measurement matrix constructed from the frame Carnegie Mellon University. Pittsburgh, PA [6] require the determination of the SVD of. the measurement matrix constructed from the frame](/thumbs/91/105590593.jpg) Ecient Recovery of Low-dimensional Structure from High-dimensional Data Shyjan Mahamud Martial Hebert Dept. of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Abstract Many modeling tasks
Ecient Recovery of Low-dimensional Structure from High-dimensional Data Shyjan Mahamud Martial Hebert Dept. of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Abstract Many modeling tasks
From Fragments to Salient Closed Boundaries: An In-Depth Study
 From Fragments to Salient Closed Boundaries: An In-Depth Study Song Wang, Jun Wang, and Toshiro Kubota Department of Computer Science and Engineering University of South Carolina, Columbia, SC 29208 songwang@cse.sc.edu,
From Fragments to Salient Closed Boundaries: An In-Depth Study Song Wang, Jun Wang, and Toshiro Kubota Department of Computer Science and Engineering University of South Carolina, Columbia, SC 29208 songwang@cse.sc.edu,
Extracting the Canonical Set of Closed Contours Using the Best-First Search Algorithm
 Extracting the Canonical Set of Closed Contours Using the Best-First Search Algorithm Siniša Šegvić, Zoran Kalafatić and Slobodan Ribarić Faculty of Electrical Engineering and Computing Unska 3, 1 Zagreb,
Extracting the Canonical Set of Closed Contours Using the Best-First Search Algorithm Siniša Šegvić, Zoran Kalafatić and Slobodan Ribarić Faculty of Electrical Engineering and Computing Unska 3, 1 Zagreb,
Convex Grouping Combining Boundary and Region Information
 Convex Grouping Combining Boundary and Region Information Joachim S. Stahl and Song Wang Department of Computer Science and Engineering University of South Carolina, Columbia, SC 29208 stahlj@cse.sc.edu,
Convex Grouping Combining Boundary and Region Information Joachim S. Stahl and Song Wang Department of Computer Science and Engineering University of South Carolina, Columbia, SC 29208 stahlj@cse.sc.edu,
Salient Boundary Detection using Ratio Contour
 Salient Boundary Detection using Ratio Contour Song Wang, Toshiro Kubota Dept. Computer Science & Engineering University of South Carolina Columbia, SC 29208 {songwang kubota}@cse.sc.edu Jeffrey Mark Siskind
Salient Boundary Detection using Ratio Contour Song Wang, Toshiro Kubota Dept. Computer Science & Engineering University of South Carolina Columbia, SC 29208 {songwang kubota}@cse.sc.edu Jeffrey Mark Siskind
CS 534: Computer Vision Segmentation and Perceptual Grouping
 CS 534: Computer Vision Segmentation and Perceptual Grouping Ahmed Elgammal Dept of Computer Science CS 534 Segmentation - 1 Outlines Mid-level vision What is segmentation Perceptual Grouping Segmentation
CS 534: Computer Vision Segmentation and Perceptual Grouping Ahmed Elgammal Dept of Computer Science CS 534 Segmentation - 1 Outlines Mid-level vision What is segmentation Perceptual Grouping Segmentation
Optimal Grouping of Line Segments into Convex Sets 1
 Optimal Grouping of Line Segments into Convex Sets 1 B. Parvin and S. Viswanathan Imaging and Distributed Computing Group Information and Computing Sciences Division Lawrence Berkeley National Laboratory,
Optimal Grouping of Line Segments into Convex Sets 1 B. Parvin and S. Viswanathan Imaging and Distributed Computing Group Information and Computing Sciences Division Lawrence Berkeley National Laboratory,
Lecture 9 - Matrix Multiplication Equivalences and Spectral Graph Theory 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanfordedu) February 6, 2018 Lecture 9 - Matrix Multiplication Equivalences and Spectral Graph Theory 1 In the
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanfordedu) February 6, 2018 Lecture 9 - Matrix Multiplication Equivalences and Spectral Graph Theory 1 In the
What is Computer Vision?
 Perceptual Grouping in Computer Vision Gérard Medioni University of Southern California What is Computer Vision? Computer Vision Attempt to emulate Human Visual System Perceive visual stimuli with cameras
Perceptual Grouping in Computer Vision Gérard Medioni University of Southern California What is Computer Vision? Computer Vision Attempt to emulate Human Visual System Perceive visual stimuli with cameras
A Comparison of Measures for Detecting Natural Shapes in Cluttered Backgrounds
 International Journal of Computer Vision 34(2/3), 81 96 (2000) c 2000 Kluwer Academic Publishers. Manufactured in The Netherlands. A Comparison of Measures for Detecting Natural Shapes in Cluttered Backgrounds
International Journal of Computer Vision 34(2/3), 81 96 (2000) c 2000 Kluwer Academic Publishers. Manufactured in The Netherlands. A Comparison of Measures for Detecting Natural Shapes in Cluttered Backgrounds
Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) January 11, 2018 Lecture 2 - Graph Theory Fundamentals - Reachability and Exploration 1 In this lecture
CS443: Digital Imaging and Multimedia Perceptual Grouping Detecting Lines and Simple Curves
 CS443: Digital Imaging and Multimedia Perceptual Grouping Detecting Lines and Simple Curves Spring 2008 Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines Perceptual Grouping and Segmentation
CS443: Digital Imaging and Multimedia Perceptual Grouping Detecting Lines and Simple Curves Spring 2008 Ahmed Elgammal Dept. of Computer Science Rutgers University Outlines Perceptual Grouping and Segmentation
Fl(P) -> Left contribution. P Fr(P) -> Right contribution P-1 P-2 P+2 P+1. F(P) = [ Fl(P) + Fr(P) ]
![Fl(P) -> Left contribution. P Fr(P) -> Right contribution P-1 P-2 P+2 P+1. F(P) = [ Fl(P) + Fr(P) ] Fl(P) -> Left contribution. P Fr(P) -> Right contribution P-1 P-2 P+2 P+1. F(P) = [ Fl(P) + Fr(P) ]](/thumbs/74/70088017.jpg) Perceptual Organization of thin networks with active contour functions applied to medical and aerial images. Philippe Montesinos, Laurent Alquier LGIP - Parc scientique G. BESSE NIMES, F-30000 E-mail:
Perceptual Organization of thin networks with active contour functions applied to medical and aerial images. Philippe Montesinos, Laurent Alquier LGIP - Parc scientique G. BESSE NIMES, F-30000 E-mail:
Image Segmentation continued Graph Based Methods
 Image Segmentation continued Graph Based Methods Previously Images as graphs Fully-connected graph node (vertex) for every pixel link between every pair of pixels, p,q affinity weight w pq for each link
Image Segmentation continued Graph Based Methods Previously Images as graphs Fully-connected graph node (vertex) for every pixel link between every pair of pixels, p,q affinity weight w pq for each link
THE preceding chapters were all devoted to the analysis of images and signals which
 Chapter 5 Segmentation of Color, Texture, and Orientation Images THE preceding chapters were all devoted to the analysis of images and signals which take values in IR. It is often necessary, however, to
Chapter 5 Segmentation of Color, Texture, and Orientation Images THE preceding chapters were all devoted to the analysis of images and signals which take values in IR. It is often necessary, however, to
Egemen Tanin, Tahsin M. Kurc, Cevdet Aykanat, Bulent Ozguc. Abstract. Direct Volume Rendering (DVR) is a powerful technique for
 Comparison of Two Image-Space Subdivision Algorithms for Direct Volume Rendering on Distributed-Memory Multicomputers Egemen Tanin, Tahsin M. Kurc, Cevdet Aykanat, Bulent Ozguc Dept. of Computer Eng. and
Comparison of Two Image-Space Subdivision Algorithms for Direct Volume Rendering on Distributed-Memory Multicomputers Egemen Tanin, Tahsin M. Kurc, Cevdet Aykanat, Bulent Ozguc Dept. of Computer Eng. and
Hyperplane Ranking in. Simple Genetic Algorithms. D. Whitley, K. Mathias, and L. Pyeatt. Department of Computer Science. Colorado State University
 Hyperplane Ranking in Simple Genetic Algorithms D. Whitley, K. Mathias, and L. yeatt Department of Computer Science Colorado State University Fort Collins, Colorado 8523 USA whitley,mathiask,pyeatt@cs.colostate.edu
Hyperplane Ranking in Simple Genetic Algorithms D. Whitley, K. Mathias, and L. yeatt Department of Computer Science Colorado State University Fort Collins, Colorado 8523 USA whitley,mathiask,pyeatt@cs.colostate.edu
CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS
 CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS This chapter presents a computational model for perceptual organization. A figure-ground segregation network is proposed based on a novel boundary
CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS This chapter presents a computational model for perceptual organization. A figure-ground segregation network is proposed based on a novel boundary
Using Game Theory for Image Segmentation
 Using Game Theory for Image Segmentation Elizabeth Cassell Sumanth Kolar Alex Yakushev 1 Introduction 21st March 2007 The goal of image segmentation, is to distinguish objects from background. Robust segmentation
Using Game Theory for Image Segmentation Elizabeth Cassell Sumanth Kolar Alex Yakushev 1 Introduction 21st March 2007 The goal of image segmentation, is to distinguish objects from background. Robust segmentation
CS 664 Segmentation. Daniel Huttenlocher
 CS 664 Segmentation Daniel Huttenlocher Grouping Perceptual Organization Structural relationships between tokens Parallelism, symmetry, alignment Similarity of token properties Often strong psychophysical
CS 664 Segmentation Daniel Huttenlocher Grouping Perceptual Organization Structural relationships between tokens Parallelism, symmetry, alignment Similarity of token properties Often strong psychophysical
Chapter 11 Arc Extraction and Segmentation
 Chapter 11 Arc Extraction and Segmentation 11.1 Introduction edge detection: labels each pixel as edge or no edge additional properties of edge: direction, gradient magnitude, contrast edge grouping: edge
Chapter 11 Arc Extraction and Segmentation 11.1 Introduction edge detection: labels each pixel as edge or no edge additional properties of edge: direction, gradient magnitude, contrast edge grouping: edge
3 No-Wait Job Shops with Variable Processing Times
 3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
along the curves is usually an image of edge points that represent simple incomplete shapes. These edge points are represented as a binary image with
 Multiple Contour Finding and Perceptual Grouping using Minimal Paths Laurent D. COHEN CEREMADE, UMR 7534, Universite Paris-Dauphine 75775 Paris cedex 16, France; Email: cohen@ceremade.dauphine.fr Abstract
Multiple Contour Finding and Perceptual Grouping using Minimal Paths Laurent D. COHEN CEREMADE, UMR 7534, Universite Paris-Dauphine 75775 Paris cedex 16, France; Email: cohen@ceremade.dauphine.fr Abstract
An Ecient Approximation Algorithm for the. File Redistribution Scheduling Problem in. Fully Connected Networks. Abstract
 An Ecient Approximation Algorithm for the File Redistribution Scheduling Problem in Fully Connected Networks Ravi Varadarajan Pedro I. Rivera-Vega y Abstract We consider the problem of transferring a set
An Ecient Approximation Algorithm for the File Redistribution Scheduling Problem in Fully Connected Networks Ravi Varadarajan Pedro I. Rivera-Vega y Abstract We consider the problem of transferring a set
Computer Vision I. Announcements. Fourier Tansform. Efficient Implementation. Edge and Corner Detection. CSE252A Lecture 13.
 Announcements Edge and Corner Detection HW3 assigned CSE252A Lecture 13 Efficient Implementation Both, the Box filter and the Gaussian filter are separable: First convolve each row of input image I with
Announcements Edge and Corner Detection HW3 assigned CSE252A Lecture 13 Efficient Implementation Both, the Box filter and the Gaussian filter are separable: First convolve each row of input image I with
Local qualitative shape from stereo. without detailed correspondence. Extended Abstract. Shimon Edelman. Internet:
 Local qualitative shape from stereo without detailed correspondence Extended Abstract Shimon Edelman Center for Biological Information Processing MIT E25-201, Cambridge MA 02139 Internet: edelman@ai.mit.edu
Local qualitative shape from stereo without detailed correspondence Extended Abstract Shimon Edelman Center for Biological Information Processing MIT E25-201, Cambridge MA 02139 Internet: edelman@ai.mit.edu
A B. A: sigmoid B: EBA (x0=0.03) C: EBA (x0=0.05) U
 Extending the Power and Capacity of Constraint Satisfaction Networks nchuan Zeng and Tony R. Martinez Computer Science Department, Brigham Young University, Provo, Utah 8460 Email: zengx@axon.cs.byu.edu,
Extending the Power and Capacity of Constraint Satisfaction Networks nchuan Zeng and Tony R. Martinez Computer Science Department, Brigham Young University, Provo, Utah 8460 Email: zengx@axon.cs.byu.edu,
Edge and corner detection
 Edge and corner detection Prof. Stricker Doz. G. Bleser Computer Vision: Object and People Tracking Goals Where is the information in an image? How is an object characterized? How can I find measurements
Edge and corner detection Prof. Stricker Doz. G. Bleser Computer Vision: Object and People Tracking Goals Where is the information in an image? How is an object characterized? How can I find measurements
CS 534: Computer Vision Segmentation and Perceptual Grouping
 CS 534: Computer Vision Segmentation and Perceptual Grouping Spring 2005 Ahmed Elgammal Dept of Computer Science CS 534 Segmentation - 1 Where are we? Image Formation Human vision Cameras Geometric Camera
CS 534: Computer Vision Segmentation and Perceptual Grouping Spring 2005 Ahmed Elgammal Dept of Computer Science CS 534 Segmentation - 1 Where are we? Image Formation Human vision Cameras Geometric Camera
Edge Detection (with a sidelight introduction to linear, associative operators). Images
 Images (we will, eventually, come back to imaging geometry. But, now that we know how images come from the world, we will examine operations on images). Edge Detection (with a sidelight introduction to
Images (we will, eventually, come back to imaging geometry. But, now that we know how images come from the world, we will examine operations on images). Edge Detection (with a sidelight introduction to
Computer Vision I. Announcement. Corners. Edges. Numerical Derivatives f(x) Edge and Corner Detection. CSE252A Lecture 11
 Announcement Edge and Corner Detection Slides are posted HW due Friday CSE5A Lecture 11 Edges Corners Edge is Where Change Occurs: 1-D Change is measured by derivative in 1D Numerical Derivatives f(x)
Announcement Edge and Corner Detection Slides are posted HW due Friday CSE5A Lecture 11 Edges Corners Edge is Where Change Occurs: 1-D Change is measured by derivative in 1D Numerical Derivatives f(x)
However, m pq is just an approximation of M pq. As it was pointed out by Lin [2], more precise approximation can be obtained by exact integration of t
![However, m pq is just an approximation of M pq. As it was pointed out by Lin [2], more precise approximation can be obtained by exact integration of t However, m pq is just an approximation of M pq. As it was pointed out by Lin [2], more precise approximation can be obtained by exact integration of t](/thumbs/86/94610569.jpg) FAST CALCULATION OF GEOMETRIC MOMENTS OF BINARY IMAGES Jan Flusser Institute of Information Theory and Automation Academy of Sciences of the Czech Republic Pod vodarenskou vez 4, 82 08 Prague 8, Czech
FAST CALCULATION OF GEOMETRIC MOMENTS OF BINARY IMAGES Jan Flusser Institute of Information Theory and Automation Academy of Sciences of the Czech Republic Pod vodarenskou vez 4, 82 08 Prague 8, Czech
A Min-Cover Approach for Finding Salient Curves
 A Min-Cover Approach for Finding Salient Curves Pedro Felzenszwalb University of Chicago pff@cs.uchicago.edu David McAllester TTI at Chicago mcallester@tti-c.org Abstract We consider the problem of deriving
A Min-Cover Approach for Finding Salient Curves Pedro Felzenszwalb University of Chicago pff@cs.uchicago.edu David McAllester TTI at Chicago mcallester@tti-c.org Abstract We consider the problem of deriving
Enumeration of Full Graphs: Onset of the Asymptotic Region. Department of Mathematics. Massachusetts Institute of Technology. Cambridge, MA 02139
 Enumeration of Full Graphs: Onset of the Asymptotic Region L. J. Cowen D. J. Kleitman y F. Lasaga D. E. Sussman Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139 Abstract
Enumeration of Full Graphs: Onset of the Asymptotic Region L. J. Cowen D. J. Kleitman y F. Lasaga D. E. Sussman Department of Mathematics Massachusetts Institute of Technology Cambridge, MA 02139 Abstract
Intersection of sets *
 OpenStax-CNX module: m15196 1 Intersection of sets * Sunil Kumar Singh This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 We have pointed out that a set
OpenStax-CNX module: m15196 1 Intersection of sets * Sunil Kumar Singh This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 We have pointed out that a set
Issues with Curve Detection Grouping (e.g., the Canny hysteresis thresholding procedure) Model tting They can be performed sequentially or simultaneou
 an edge image, nd line or curve segments present Given the image. in Line and Curves Detection 1 Issues with Curve Detection Grouping (e.g., the Canny hysteresis thresholding procedure) Model tting They
an edge image, nd line or curve segments present Given the image. in Line and Curves Detection 1 Issues with Curve Detection Grouping (e.g., the Canny hysteresis thresholding procedure) Model tting They
Solution: filter the image, then subsample F 1 F 2. subsample blur subsample. blur
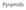 Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Perceptual Grouping from Motion Cues Using Tensor Voting
 Perceptual Grouping from Motion Cues Using Tensor Voting 1. Research Team Project Leader: Graduate Students: Prof. Gérard Medioni, Computer Science Mircea Nicolescu, Changki Min 2. Statement of Project
Perceptual Grouping from Motion Cues Using Tensor Voting 1. Research Team Project Leader: Graduate Students: Prof. Gérard Medioni, Computer Science Mircea Nicolescu, Changki Min 2. Statement of Project
- J. Edge outputs to higher visual areas. Inputs Ic to inhibitory cells An interconnected neuron pair for edge segment i. inhibitory.
 Primary Cortical Dynamics for Visual Grouping Zhaoping Li Hong Kong University of Science and Technology Clear Water Bay, Hong Kong Abstract. The classical receptive elds of V1 neurons contain only local
Primary Cortical Dynamics for Visual Grouping Zhaoping Li Hong Kong University of Science and Technology Clear Water Bay, Hong Kong Abstract. The classical receptive elds of V1 neurons contain only local
Adaptive Estimation of Distributions using Exponential Sub-Families Alan Gous Stanford University December 1996 Abstract: An algorithm is presented wh
 Adaptive Estimation of Distributions using Exponential Sub-Families Alan Gous Stanford University December 1996 Abstract: An algorithm is presented which, for a large-dimensional exponential family G,
Adaptive Estimation of Distributions using Exponential Sub-Families Alan Gous Stanford University December 1996 Abstract: An algorithm is presented which, for a large-dimensional exponential family G,
Investigating How and When Perceptual Organization Cues Improve Boundary Detection in Natural Images
 Investigating How and When Perceptual Organization Cues Improve Boundary Detection in Natural Images Leandro A. Loss, George Bebis, Mircea Nicolescu Computer Vision Laboratory University of Nevada, Reno
Investigating How and When Perceptual Organization Cues Improve Boundary Detection in Natural Images Leandro A. Loss, George Bebis, Mircea Nicolescu Computer Vision Laboratory University of Nevada, Reno
Normalized cuts and image segmentation
 Normalized cuts and image segmentation Department of EE University of Washington Yeping Su Xiaodan Song Normalized Cuts and Image Segmentation, IEEE Trans. PAMI, August 2000 5/20/2003 1 Outline 1. Image
Normalized cuts and image segmentation Department of EE University of Washington Yeping Su Xiaodan Song Normalized Cuts and Image Segmentation, IEEE Trans. PAMI, August 2000 5/20/2003 1 Outline 1. Image
Applying Synthetic Images to Learning Grasping Orientation from Single Monocular Images
 Applying Synthetic Images to Learning Grasping Orientation from Single Monocular Images 1 Introduction - Steve Chuang and Eric Shan - Determining object orientation in images is a well-established topic
Applying Synthetic Images to Learning Grasping Orientation from Single Monocular Images 1 Introduction - Steve Chuang and Eric Shan - Determining object orientation in images is a well-established topic
A Hierarchical Compositional System for Rapid Object Detection
 A Hierarchical Compositional System for Rapid Object Detection Long Zhu and Alan Yuille Department of Statistics University of California at Los Angeles Los Angeles, CA 90095 {lzhu,yuille}@stat.ucla.edu
A Hierarchical Compositional System for Rapid Object Detection Long Zhu and Alan Yuille Department of Statistics University of California at Los Angeles Los Angeles, CA 90095 {lzhu,yuille}@stat.ucla.edu
Chapter 3. Quadric hypersurfaces. 3.1 Quadric hypersurfaces Denition.
 Chapter 3 Quadric hypersurfaces 3.1 Quadric hypersurfaces. 3.1.1 Denition. Denition 1. In an n-dimensional ane space A; given an ane frame fo;! e i g: A quadric hypersurface in A is a set S consisting
Chapter 3 Quadric hypersurfaces 3.1 Quadric hypersurfaces. 3.1.1 Denition. Denition 1. In an n-dimensional ane space A; given an ane frame fo;! e i g: A quadric hypersurface in A is a set S consisting
3.1. Solution for white Gaussian noise
 Low complexity M-hypotheses detection: M vectors case Mohammed Nae and Ahmed H. Tewk Dept. of Electrical Engineering University of Minnesota, Minneapolis, MN 55455 mnae,tewk@ece.umn.edu Abstract Low complexity
Low complexity M-hypotheses detection: M vectors case Mohammed Nae and Ahmed H. Tewk Dept. of Electrical Engineering University of Minnesota, Minneapolis, MN 55455 mnae,tewk@ece.umn.edu Abstract Low complexity
1 INTRODUCTION The LMS adaptive algorithm is the most popular algorithm for adaptive ltering because of its simplicity and robustness. However, its ma
 MULTIPLE SUBSPACE ULV ALGORITHM AND LMS TRACKING S. HOSUR, A. H. TEWFIK, D. BOLEY University of Minnesota 200 Union St. S.E. Minneapolis, MN 55455 U.S.A fhosur@ee,tewk@ee,boley@csg.umn.edu ABSTRACT. The
MULTIPLE SUBSPACE ULV ALGORITHM AND LMS TRACKING S. HOSUR, A. H. TEWFIK, D. BOLEY University of Minnesota 200 Union St. S.E. Minneapolis, MN 55455 U.S.A fhosur@ee,tewk@ee,boley@csg.umn.edu ABSTRACT. The
Skill. Robot/ Controller
 Skill Acquisition from Human Demonstration Using a Hidden Markov Model G. E. Hovland, P. Sikka and B. J. McCarragher Department of Engineering Faculty of Engineering and Information Technology The Australian
Skill Acquisition from Human Demonstration Using a Hidden Markov Model G. E. Hovland, P. Sikka and B. J. McCarragher Department of Engineering Faculty of Engineering and Information Technology The Australian
SYDE Winter 2011 Introduction to Pattern Recognition. Clustering
 SYDE 372 - Winter 2011 Introduction to Pattern Recognition Clustering Alexander Wong Department of Systems Design Engineering University of Waterloo Outline 1 2 3 4 5 All the approaches we have learned
SYDE 372 - Winter 2011 Introduction to Pattern Recognition Clustering Alexander Wong Department of Systems Design Engineering University of Waterloo Outline 1 2 3 4 5 All the approaches we have learned
An Iterative Multi-Scale Tensor Voting Scheme for Perceptual Grouping of Natural Shapes in Cluttered Backgrounds
 An Iterative Multi-Scale Tensor Voting Scheme for Perceptual Grouping of Natural Shapes in Cluttered Backgrounds Leandro Loss 1, George Bebis 1, Mircea Nicolescu 1, and Alexei Skurikhin 2 1 Computer Vision
An Iterative Multi-Scale Tensor Voting Scheme for Perceptual Grouping of Natural Shapes in Cluttered Backgrounds Leandro Loss 1, George Bebis 1, Mircea Nicolescu 1, and Alexei Skurikhin 2 1 Computer Vision
BMVC 1996 doi: /c.10.41
 On the use of the 1D Boolean model for the description of binary textures M Petrou, M Arrigo and J A Vons Dept. of Electronic and Electrical Engineering, University of Surrey, Guildford GU2 5XH, United
On the use of the 1D Boolean model for the description of binary textures M Petrou, M Arrigo and J A Vons Dept. of Electronic and Electrical Engineering, University of Surrey, Guildford GU2 5XH, United
Chapter 8. Voronoi Diagrams. 8.1 Post Oce Problem
 Chapter 8 Voronoi Diagrams 8.1 Post Oce Problem Suppose there are n post oces p 1,... p n in a city. Someone who is located at a position q within the city would like to know which post oce is closest
Chapter 8 Voronoi Diagrams 8.1 Post Oce Problem Suppose there are n post oces p 1,... p n in a city. Someone who is located at a position q within the city would like to know which post oce is closest
Unconstrained Optimization
 Unconstrained Optimization Joshua Wilde, revised by Isabel Tecu, Takeshi Suzuki and María José Boccardi August 13, 2013 1 Denitions Economics is a science of optima We maximize utility functions, minimize
Unconstrained Optimization Joshua Wilde, revised by Isabel Tecu, Takeshi Suzuki and María José Boccardi August 13, 2013 1 Denitions Economics is a science of optima We maximize utility functions, minimize
Occluded Facial Expression Tracking
 Occluded Facial Expression Tracking Hugo Mercier 1, Julien Peyras 2, and Patrice Dalle 1 1 Institut de Recherche en Informatique de Toulouse 118, route de Narbonne, F-31062 Toulouse Cedex 9 2 Dipartimento
Occluded Facial Expression Tracking Hugo Mercier 1, Julien Peyras 2, and Patrice Dalle 1 1 Institut de Recherche en Informatique de Toulouse 118, route de Narbonne, F-31062 Toulouse Cedex 9 2 Dipartimento
Silhouette-based Multiple-View Camera Calibration
 Silhouette-based Multiple-View Camera Calibration Prashant Ramanathan, Eckehard Steinbach, and Bernd Girod Information Systems Laboratory, Electrical Engineering Department, Stanford University Stanford,
Silhouette-based Multiple-View Camera Calibration Prashant Ramanathan, Eckehard Steinbach, and Bernd Girod Information Systems Laboratory, Electrical Engineering Department, Stanford University Stanford,
A Survey of Light Source Detection Methods
 A Survey of Light Source Detection Methods Nathan Funk University of Alberta Mini-Project for CMPUT 603 November 30, 2003 Abstract This paper provides an overview of the most prominent techniques for light
A Survey of Light Source Detection Methods Nathan Funk University of Alberta Mini-Project for CMPUT 603 November 30, 2003 Abstract This paper provides an overview of the most prominent techniques for light
Prof. Fanny Ficuciello Robotics for Bioengineering Visual Servoing
 Visual servoing vision allows a robotic system to obtain geometrical and qualitative information on the surrounding environment high level control motion planning (look-and-move visual grasping) low level
Visual servoing vision allows a robotic system to obtain geometrical and qualitative information on the surrounding environment high level control motion planning (look-and-move visual grasping) low level
HOUGH TRANSFORM CS 6350 C V
 HOUGH TRANSFORM CS 6350 C V HOUGH TRANSFORM The problem: Given a set of points in 2-D, find if a sub-set of these points, fall on a LINE. Hough Transform One powerful global method for detecting edges
HOUGH TRANSFORM CS 6350 C V HOUGH TRANSFORM The problem: Given a set of points in 2-D, find if a sub-set of these points, fall on a LINE. Hough Transform One powerful global method for detecting edges
2 The original active contour algorithm presented in [] had some inherent computational problems in evaluating the energy function, which were subsequ
![2 The original active contour algorithm presented in [] had some inherent computational problems in evaluating the energy function, which were subsequ 2 The original active contour algorithm presented in [] had some inherent computational problems in evaluating the energy function, which were subsequ](/thumbs/91/107202403.jpg) Linguistic contour modelling through Fuzzy Snakes Frank Howing University of Glamorgan, School of Electronics also with Fachhochschule Braunschweig/Wolfenbuttel, FB E f.hoewing@fh-wolfenbuettel.de Laurence
Linguistic contour modelling through Fuzzy Snakes Frank Howing University of Glamorgan, School of Electronics also with Fachhochschule Braunschweig/Wolfenbuttel, FB E f.hoewing@fh-wolfenbuettel.de Laurence
Fast Fuzzy Clustering of Infrared Images. 2. brfcm
 Fast Fuzzy Clustering of Infrared Images Steven Eschrich, Jingwei Ke, Lawrence O. Hall and Dmitry B. Goldgof Department of Computer Science and Engineering, ENB 118 University of South Florida 4202 E.
Fast Fuzzy Clustering of Infrared Images Steven Eschrich, Jingwei Ke, Lawrence O. Hall and Dmitry B. Goldgof Department of Computer Science and Engineering, ENB 118 University of South Florida 4202 E.
Image Segmentation continued Graph Based Methods. Some slides: courtesy of O. Capms, Penn State, J.Ponce and D. Fortsyth, Computer Vision Book
 Image Segmentation continued Graph Based Methods Some slides: courtesy of O. Capms, Penn State, J.Ponce and D. Fortsyth, Computer Vision Book Previously Binary segmentation Segmentation by thresholding
Image Segmentation continued Graph Based Methods Some slides: courtesy of O. Capms, Penn State, J.Ponce and D. Fortsyth, Computer Vision Book Previously Binary segmentation Segmentation by thresholding
J. Weston, A. Gammerman, M. Stitson, V. Vapnik, V. Vovk, C. Watkins. Technical Report. February 5, 1998
 Density Estimation using Support Vector Machines J. Weston, A. Gammerman, M. Stitson, V. Vapnik, V. Vovk, C. Watkins. Technical Report CSD-TR-97-3 February 5, 998!()+, -./ 3456 Department of Computer Science
Density Estimation using Support Vector Machines J. Weston, A. Gammerman, M. Stitson, V. Vapnik, V. Vovk, C. Watkins. Technical Report CSD-TR-97-3 February 5, 998!()+, -./ 3456 Department of Computer Science
CS 664 Slides #11 Image Segmentation. Prof. Dan Huttenlocher Fall 2003
 CS 664 Slides #11 Image Segmentation Prof. Dan Huttenlocher Fall 2003 Image Segmentation Find regions of image that are coherent Dual of edge detection Regions vs. boundaries Related to clustering problems
CS 664 Slides #11 Image Segmentation Prof. Dan Huttenlocher Fall 2003 Image Segmentation Find regions of image that are coherent Dual of edge detection Regions vs. boundaries Related to clustering problems
The goals of segmentation
 Image segmentation The goals of segmentation Group together similar-looking pixels for efficiency of further processing Bottom-up process Unsupervised superpixels X. Ren and J. Malik. Learning a classification
Image segmentation The goals of segmentation Group together similar-looking pixels for efficiency of further processing Bottom-up process Unsupervised superpixels X. Ren and J. Malik. Learning a classification
II (Sorting and) Order Statistics
 II (Sorting and) Order Statistics Heapsort Quicksort Sorting in Linear Time Medians and Order Statistics 8 Sorting in Linear Time The sorting algorithms introduced thus far are comparison sorts Any comparison
II (Sorting and) Order Statistics Heapsort Quicksort Sorting in Linear Time Medians and Order Statistics 8 Sorting in Linear Time The sorting algorithms introduced thus far are comparison sorts Any comparison
Lecture 25: Bezier Subdivision. And he took unto him all these, and divided them in the midst, and laid each piece one against another: Genesis 15:10
 Lecture 25: Bezier Subdivision And he took unto him all these, and divided them in the midst, and laid each piece one against another: Genesis 15:10 1. Divide and Conquer If we are going to build useful
Lecture 25: Bezier Subdivision And he took unto him all these, and divided them in the midst, and laid each piece one against another: Genesis 15:10 1. Divide and Conquer If we are going to build useful
Image Segmentation. Selim Aksoy. Bilkent University
 Image Segmentation Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr Examples of grouping in vision [http://poseidon.csd.auth.gr/lab_research/latest/imgs/s peakdepvidindex_img2.jpg]
Image Segmentation Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr Examples of grouping in vision [http://poseidon.csd.auth.gr/lab_research/latest/imgs/s peakdepvidindex_img2.jpg]
Image Segmentation. Selim Aksoy. Bilkent University
 Image Segmentation Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr Examples of grouping in vision [http://poseidon.csd.auth.gr/lab_research/latest/imgs/s peakdepvidindex_img2.jpg]
Image Segmentation Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr Examples of grouping in vision [http://poseidon.csd.auth.gr/lab_research/latest/imgs/s peakdepvidindex_img2.jpg]
Exploring Curve Fitting for Fingers in Egocentric Images
 Exploring Curve Fitting for Fingers in Egocentric Images Akanksha Saran Robotics Institute, Carnegie Mellon University 16-811: Math Fundamentals for Robotics Final Project Report Email: asaran@andrew.cmu.edu
Exploring Curve Fitting for Fingers in Egocentric Images Akanksha Saran Robotics Institute, Carnegie Mellon University 16-811: Math Fundamentals for Robotics Final Project Report Email: asaran@andrew.cmu.edu
Region-based Segmentation
 Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
Copyright (C) 1997, 1998 by the Association for Computing Machinery, Inc. Permission to make digital or hard copies of part or all of this work for
 Copyright (C) 1997, 1998 by the Association for Computing Machinery, Inc. Permission to make digital or hard copies of part or all of this work for personal or classroom use is granted without fee provided
Copyright (C) 1997, 1998 by the Association for Computing Machinery, Inc. Permission to make digital or hard copies of part or all of this work for personal or classroom use is granted without fee provided
A General Framework for Contour
 Chapter 8 A General Framework for Contour Extraction In the previous chapter, we described an efficient search framework for convex contour extraction. The framework is based on a simple measure of affinity
Chapter 8 A General Framework for Contour Extraction In the previous chapter, we described an efficient search framework for convex contour extraction. The framework is based on a simple measure of affinity
A NOVEL FEATURE EXTRACTION METHOD BASED ON SEGMENTATION OVER EDGE FIELD FOR MULTIMEDIA INDEXING AND RETRIEVAL
 A NOVEL FEATURE EXTRACTION METHOD BASED ON SEGMENTATION OVER EDGE FIELD FOR MULTIMEDIA INDEXING AND RETRIEVAL Serkan Kiranyaz, Miguel Ferreira and Moncef Gabbouj Institute of Signal Processing, Tampere
A NOVEL FEATURE EXTRACTION METHOD BASED ON SEGMENTATION OVER EDGE FIELD FOR MULTIMEDIA INDEXING AND RETRIEVAL Serkan Kiranyaz, Miguel Ferreira and Moncef Gabbouj Institute of Signal Processing, Tampere
Simultaneous surface texture classification and illumination tilt angle prediction
 Simultaneous surface texture classification and illumination tilt angle prediction X. Lladó, A. Oliver, M. Petrou, J. Freixenet, and J. Martí Computer Vision and Robotics Group - IIiA. University of Girona
Simultaneous surface texture classification and illumination tilt angle prediction X. Lladó, A. Oliver, M. Petrou, J. Freixenet, and J. Martí Computer Vision and Robotics Group - IIiA. University of Girona
The Encoding Complexity of Network Coding
 The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
The Encoding Complexity of Network Coding Michael Langberg Alexander Sprintson Jehoshua Bruck California Institute of Technology Email: mikel,spalex,bruck @caltech.edu Abstract In the multicast network
Image Resizing Based on Gradient Vector Flow Analysis
 Image Resizing Based on Gradient Vector Flow Analysis Sebastiano Battiato battiato@dmi.unict.it Giovanni Puglisi puglisi@dmi.unict.it Giovanni Maria Farinella gfarinellao@dmi.unict.it Daniele Ravì rav@dmi.unict.it
Image Resizing Based on Gradient Vector Flow Analysis Sebastiano Battiato battiato@dmi.unict.it Giovanni Puglisi puglisi@dmi.unict.it Giovanni Maria Farinella gfarinellao@dmi.unict.it Daniele Ravì rav@dmi.unict.it
FMA901F: Machine Learning Lecture 6: Graphical Models. Cristian Sminchisescu
 FMA901F: Machine Learning Lecture 6: Graphical Models Cristian Sminchisescu Graphical Models Provide a simple way to visualize the structure of a probabilistic model and can be used to design and motivate
FMA901F: Machine Learning Lecture 6: Graphical Models Cristian Sminchisescu Graphical Models Provide a simple way to visualize the structure of a probabilistic model and can be used to design and motivate
LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can
![LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can](/thumbs/96/128999908.jpg) 208 IEEE TRANSACTIONS ON MAGNETICS, VOL 42, NO 2, FEBRUARY 2006 Structured LDPC Codes for High-Density Recording: Large Girth and Low Error Floor J Lu and J M F Moura Department of Electrical and Computer
208 IEEE TRANSACTIONS ON MAGNETICS, VOL 42, NO 2, FEBRUARY 2006 Structured LDPC Codes for High-Density Recording: Large Girth and Low Error Floor J Lu and J M F Moura Department of Electrical and Computer
Segmentation and Grouping
 Segmentation and Grouping How and what do we see? Fundamental Problems ' Focus of attention, or grouping ' What subsets of pixels do we consider as possible objects? ' All connected subsets? ' Representation
Segmentation and Grouping How and what do we see? Fundamental Problems ' Focus of attention, or grouping ' What subsets of pixels do we consider as possible objects? ' All connected subsets? ' Representation
Lecture 2 September 3
 EE 381V: Large Scale Optimization Fall 2012 Lecture 2 September 3 Lecturer: Caramanis & Sanghavi Scribe: Hongbo Si, Qiaoyang Ye 2.1 Overview of the last Lecture The focus of the last lecture was to give
EE 381V: Large Scale Optimization Fall 2012 Lecture 2 September 3 Lecturer: Caramanis & Sanghavi Scribe: Hongbo Si, Qiaoyang Ye 2.1 Overview of the last Lecture The focus of the last lecture was to give
Recognition of the Target Image Based on POM
 Recognition of the Target Image Based on POM R.Haritha Department of ECE SJCET Yemmiganur K.Sudhakar Associate Professor HOD, Department of ECE SJCET Yemmiganur T.Chakrapani Associate Professor Department
Recognition of the Target Image Based on POM R.Haritha Department of ECE SJCET Yemmiganur K.Sudhakar Associate Professor HOD, Department of ECE SJCET Yemmiganur T.Chakrapani Associate Professor Department
International Journal of Foundations of Computer Science c World Scientic Publishing Company DFT TECHNIQUES FOR SIZE ESTIMATION OF DATABASE JOIN OPERA
 International Journal of Foundations of Computer Science c World Scientic Publishing Company DFT TECHNIQUES FOR SIZE ESTIMATION OF DATABASE JOIN OPERATIONS KAM_IL SARAC, OMER E GEC_IO GLU, AMR EL ABBADI
International Journal of Foundations of Computer Science c World Scientic Publishing Company DFT TECHNIQUES FOR SIZE ESTIMATION OF DATABASE JOIN OPERATIONS KAM_IL SARAC, OMER E GEC_IO GLU, AMR EL ABBADI
Bias-Variance Tradeos Analysis Using Uniform CR Bound. Mohammad Usman, Alfred O. Hero, Jerey A. Fessler and W. L. Rogers. University of Michigan
 Bias-Variance Tradeos Analysis Using Uniform CR Bound Mohammad Usman, Alfred O. Hero, Jerey A. Fessler and W. L. Rogers University of Michigan ABSTRACT We quantify fundamental bias-variance tradeos for
Bias-Variance Tradeos Analysis Using Uniform CR Bound Mohammad Usman, Alfred O. Hero, Jerey A. Fessler and W. L. Rogers University of Michigan ABSTRACT We quantify fundamental bias-variance tradeos for
Shape Descriptor using Polar Plot for Shape Recognition.
 Shape Descriptor using Polar Plot for Shape Recognition. Brijesh Pillai ECE Graduate Student, Clemson University bpillai@clemson.edu Abstract : This paper presents my work on computing shape models that
Shape Descriptor using Polar Plot for Shape Recognition. Brijesh Pillai ECE Graduate Student, Clemson University bpillai@clemson.edu Abstract : This paper presents my work on computing shape models that
Supervised texture detection in images
 Supervised texture detection in images Branislav Mičušík and Allan Hanbury Pattern Recognition and Image Processing Group, Institute of Computer Aided Automation, Vienna University of Technology Favoritenstraße
Supervised texture detection in images Branislav Mičušík and Allan Hanbury Pattern Recognition and Image Processing Group, Institute of Computer Aided Automation, Vienna University of Technology Favoritenstraße
ARTIFICIAL INTELLIGENCE LABORATORY. A.I. Memo No August, Extracting Salient Curves from Images: An Analysis of the Saliency Network
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY ARTIFICIAL INTELLIGENCE LABORATORY A.I. Memo No. 55 August, 995 Extracting Salient Curves from Images: An Analysis of the Saliency Network T. D. Alter Ronen Basri
MASSACHUSETTS INSTITUTE OF TECHNOLOGY ARTIFICIAL INTELLIGENCE LABORATORY A.I. Memo No. 55 August, 995 Extracting Salient Curves from Images: An Analysis of the Saliency Network T. D. Alter Ronen Basri
Implementations of Dijkstra's Algorithm. Based on Multi-Level Buckets. November Abstract
 Implementations of Dijkstra's Algorithm Based on Multi-Level Buckets Andrew V. Goldberg NEC Research Institute 4 Independence Way Princeton, NJ 08540 avg@research.nj.nec.com Craig Silverstein Computer
Implementations of Dijkstra's Algorithm Based on Multi-Level Buckets Andrew V. Goldberg NEC Research Institute 4 Independence Way Princeton, NJ 08540 avg@research.nj.nec.com Craig Silverstein Computer
A technique for adding range restrictions to. August 30, Abstract. In a generalized searching problem, a set S of n colored geometric objects
 A technique for adding range restrictions to generalized searching problems Prosenjit Gupta Ravi Janardan y Michiel Smid z August 30, 1996 Abstract In a generalized searching problem, a set S of n colored
A technique for adding range restrictions to generalized searching problems Prosenjit Gupta Ravi Janardan y Michiel Smid z August 30, 1996 Abstract In a generalized searching problem, a set S of n colored
SEMI-BLIND IMAGE RESTORATION USING A LOCAL NEURAL APPROACH
 SEMI-BLIND IMAGE RESTORATION USING A LOCAL NEURAL APPROACH Ignazio Gallo, Elisabetta Binaghi and Mario Raspanti Universitá degli Studi dell Insubria Varese, Italy email: ignazio.gallo@uninsubria.it ABSTRACT
SEMI-BLIND IMAGE RESTORATION USING A LOCAL NEURAL APPROACH Ignazio Gallo, Elisabetta Binaghi and Mario Raspanti Universitá degli Studi dell Insubria Varese, Italy email: ignazio.gallo@uninsubria.it ABSTRACT
Refine boundary at resolution r. r+1 r. Update context information CI(r) based on CI(r-1) Classify at resolution r, based on CI(r), update CI(r)
 Context Based Multiscale Classication of Images Jia Li Robert M. Gray EE Department EE Department Stanford Univ., CA 94305 Stanford Univ., CA 94305 jiali@isl.stanford.edu rmgray@stanford.edu Abstract This
Context Based Multiscale Classication of Images Jia Li Robert M. Gray EE Department EE Department Stanford Univ., CA 94305 Stanford Univ., CA 94305 jiali@isl.stanford.edu rmgray@stanford.edu Abstract This
Segmentation and Grouping April 19 th, 2018
 Segmentation and Grouping April 19 th, 2018 Yong Jae Lee UC Davis Features and filters Transforming and describing images; textures, edges 2 Grouping and fitting [fig from Shi et al] Clustering, segmentation,
Segmentation and Grouping April 19 th, 2018 Yong Jae Lee UC Davis Features and filters Transforming and describing images; textures, edges 2 Grouping and fitting [fig from Shi et al] Clustering, segmentation,
THE FREUDENTHAL-HOPF THEOREM
 THE FREUDENTHAL-HOPF THEOREM SOFI GJING JOVANOVSKA Abstract. In this paper, we will examine a geometric property of groups: the number of ends of a group. Intuitively, the number of ends of a group is
THE FREUDENTHAL-HOPF THEOREM SOFI GJING JOVANOVSKA Abstract. In this paper, we will examine a geometric property of groups: the number of ends of a group. Intuitively, the number of ends of a group is
Outline. Segmentation & Grouping. Examples of grouping in vision. Grouping in vision. Grouping in vision 2/9/2011. CS 376 Lecture 7 Segmentation 1
 Outline What are grouping problems in vision? Segmentation & Grouping Wed, Feb 9 Prof. UT-Austin Inspiration from human perception Gestalt properties Bottom-up segmentation via clustering Algorithms: Mode
Outline What are grouping problems in vision? Segmentation & Grouping Wed, Feb 9 Prof. UT-Austin Inspiration from human perception Gestalt properties Bottom-up segmentation via clustering Algorithms: Mode
Visual Representations for Machine Learning
 Visual Representations for Machine Learning Spectral Clustering and Channel Representations Lecture 1 Spectral Clustering: introduction and confusion Michael Felsberg Klas Nordberg The Spectral Clustering
Visual Representations for Machine Learning Spectral Clustering and Channel Representations Lecture 1 Spectral Clustering: introduction and confusion Michael Felsberg Klas Nordberg The Spectral Clustering
Ray shooting from convex ranges
 Discrete Applied Mathematics 108 (2001) 259 267 Ray shooting from convex ranges Evangelos Kranakis a, Danny Krizanc b, Anil Maheshwari a;, Jorg-Rudiger Sack a, Jorge Urrutia c a School of Computer Science,
Discrete Applied Mathematics 108 (2001) 259 267 Ray shooting from convex ranges Evangelos Kranakis a, Danny Krizanc b, Anil Maheshwari a;, Jorg-Rudiger Sack a, Jorge Urrutia c a School of Computer Science,
CS 556: Computer Vision. Lecture 18
 CS 556: Computer Vision Lecture 18 Prof. Sinisa Todorovic sinisa@eecs.oregonstate.edu 1 Color 2 Perception of Color The sensation of color is caused by the brain Strongly affected by: Other nearby colors
CS 556: Computer Vision Lecture 18 Prof. Sinisa Todorovic sinisa@eecs.oregonstate.edu 1 Color 2 Perception of Color The sensation of color is caused by the brain Strongly affected by: Other nearby colors
(SHT) share the same one-to-many voting pattern and the representation of the accumulator array. In the original paper on the Probabilistic Hough Tran
 Progressive Probabilistic Hough Transform J. Matas y x, C. Galambos y and J. Kittler y y CVSSP, University of Surrey, Guildford, Surrey GU2 5XH, United Kingdom e-mail: g.matas@ee.surrey.ac.uk x Centre
Progressive Probabilistic Hough Transform J. Matas y x, C. Galambos y and J. Kittler y y CVSSP, University of Surrey, Guildford, Surrey GU2 5XH, United Kingdom e-mail: g.matas@ee.surrey.ac.uk x Centre
Medial Visual Fragments as an Intermediate Image Representation for Segmentation and Perceptual Grouping
 Medial Visual Fragments as an Intermediate Image Representation for Segmentation and Perceptual Grouping I. M. Anonymous M. Y. Coauthor My Department My Institute City, STATE zipcode Coauthor Department
Medial Visual Fragments as an Intermediate Image Representation for Segmentation and Perceptual Grouping I. M. Anonymous M. Y. Coauthor My Department My Institute City, STATE zipcode Coauthor Department
