Learning to Align Sequences: A Maximum-Margin Approach
|
|
|
- Lenard Miles
- 5 years ago
- Views:
Transcription
1 Learning to Align Sequences: A Maximum-Margin Approach Thorsten Joachims Department of Computer Science Cornell University Ithaca, NY tj@cs.cornell.edu August 28, 2003 Abstract We propose a discriminative method for learning the parameters (e.g. cost of substitutions, deletions, insertions) of linear sequence alignment models from training examples. While the resulting training problem leads to an optimization problem with an exponential number of constraints, we present a simple algorithm that finds an arbitrarily close approximation after considering only a subset of the constraints that is linear in the number of training examples and polynomial in the length of the sequences. We also evaluate empirically that the method effectively learns good parameter values while being computationally feasible. 1 Introduction Methods for sequence alignment are common tools for analyzing sequence data ranging from biological applications [3] to natural language processing [1]. They can be thought of as measures of similarity between sequences where the similarity score is the result of a discrete optimization problem that is typically solved via dynamic programming. While the dynamic programming algorithm determines the general notion of similarity (e.g. local alignment vs. global alignment), any such similarity measure requires specific parameter values before it is fully specified. Examples of such parameter values are the costs for substituting one sequence elements for another, as well as costs for deletions and insertions. These parameter values greatly determine how well the measure works for a particular task. In this paper we tackle the problem of inferring the parameter values from training data. Our goal is to find parameter values so that the resulting similarity measure best reflects the desired notion of similarity. We consider training data where we have examples of similar and dissimilar sequences. Instead of assuming a generative model of sequence alignment (e.g. [9]), we take a discriminative approach to training. In particular, we aim to find the set of parameter values that corresponds to the best similarity 1
2 : ¾ : : m m s m m i m m Figure 1: Example of a local sequence alignment. measure a given alignment algorithm can represent. Taking a large-margin approach, we show that we can solve the resulting training problem efficiently for a large class of alignment algorithms that implement a linear scoring function. While the resulting optimization problems have exponentially many constraints, our algorithm finds an arbitrarily good approximation after considering only a subset of constraints that scales polynomially with the length of the sequences and linearly with the number of training examples. We empirically and theoretically analyze the scaling of the algorithm and show that the learned similarity score performs well on test data. 2 Sequence Alignment Sequence alignment computes a similarity score for two (or more) sequences and ¾ from an alphabet. An alignment is a sequence of operations that transforms one sequence into the other. In global alignment, the whole sequence is transformed. In local alignment, only an arbitrarily sized subsequence is aligned. Commonly used alignment operations are match (m), substitution (s), deletion (d) and insertion (i). An example of a local alignment is given in Figure 1. In the example, there are 6 matches, 1 substitution, and 1 insertion/deletion. With each operation there is an associated cost/reward. Assuming a reward of for match, a cost of for substitution, and a cost of ¾ for insertion/deletion, the total alignment score Û ¾ µ in the example is. The optimal alignment is the one that maximizes the score for a given cost model. More generally, we consider alignment algorithms that optimize a linear scoring function Û ¾ µ Û Ì ¾ µ where ¾ µ is some function that generates features based on an alignment (e.g. # of substitutions, # of deletions) and Û is a given cost vector. ¾ µ depends on the particular alignment algorithm and can be any feature vector. Finding the optimal alignment corresponds to the following optimization problem Û ¾ µ ÑÜ Û ¾ µ ÑÜ Û Ì ¾ µ (1) This type of problem is typically solved via dynamic programming. In the following we consider local alignment via the Smith/Waterman algorithm [10]. However, the results can be extended to any alignment algorithm that optimizes a linear scoring function and that solves (1) globally optimally 1. 1 This also holds for other structures besides sequences. 2
3 3 Inverse Sequence Alignment Inverse sequence alignment is the problem of using training data to learn the parameters Û of an alignment model and algorithm so that the resulting similarity measure Û ¾ µ best represents the desired notion of similarity on new data. While previous approaches to this problem exist [5, 11], they are limited to special cases and very small numbers of parameters. We will present an algorithm that applies to any linear alignment model with no restriction on the function or number of parameters. We assume the following model, for which the notation is inspired by protein alignment. In protein alignment the goal is a similarity measure so that homologous protein sequences are similar to a native sequence, but also so that non-homologous (i.e. decoy) sequences are not similar to the native sequence. We assume that examples are generated i.i.d. according to a distribution È Æ À Ë µ. Æ is the native sequence, À the homologous sequence, and Ë is a set of decoy sequences. The goal is a similarity measure so that native sequence Æ and homolog À are more similar than the native sequence Æ and any decoy, i.e. Û Æ À µ Û Æ µ (2) The goal of learning can be formulated in two reasonable ways based on two different loss functions. In the first setting, the goal is to find the cost parameters Û that minimize the probability ÖÖ È Ûµ that the similarity with any decoy sequence Û Æ µ is higher than the similarity with the homolog sequence Û Æ À µ. ÖÖ È Ûµ ÑÜ Û Æ µ Û Æ À µ ¾Ë È Æ À Ë µ (3) The function µ returns, if its argument is false, ¼ otherwise. In the second setting, the goal is less ambitious. We do not want a homolog that is necessarily more similar than all decoys. Instead, we merely want to have the homolog sequence ranked highly, but not necessarily on top of the ranking. In particular, we could optimize the average rank of the homolog. This is equivalent to the following kind of error rate. ÖÖÈ Ûµ Û Æ µ Û Æ À µ È Æ À Ë µ (4) ¾Ë In the following, we consider only the first type of error ÖÖ È Ûµ for conciseness. 4 A Maximum-Margin Approach to Learning the Cost Parameters The distribution È À Ë µ is unknown. However, we have a training sample Ë from È Æ À Ë µ. It consists of native sequences Æ Æ Ò, homolog sequences À À Ò, and a set of decoy sequences Ë Ë Ò for each native Æ Æ Ò. As a simplifying assumption, we assume that between native and homolog sequences the alignment ÆÀ ÆÀ Ò of maximum score is known 2. The goal is to find an optimal 2 For protein alignment, for example, this could be generated via structural alignment. 3
4 Û so that the error rate ÖÖ È Ûµ is low. First, we consider the case where there exists a Û such that the error on the training set ÖÖ Ë Ûµ Ò ÑÜ ¾Ë Û Æ µ Û Æ À µ is zero. Since we assume a scoring function that is linear in the parameters Û ¾ µ Û Ì ¾ µ (6) the condition of zero training error can be written as a set of linear inequality constraints. There is one constraint for each combination of native sequence Æ, decoy sequence, and possible alignment of Æ into. ¾ Ë Û Æ µ Û Æ À ÆÀ µ (7) Ò ¾ Ë Ò Û Æ Ò Ò µ Û Æ Ò À Ò ÆÀ µ This approach of writing the training problem as a linear system follows the method in [8] proposed for the special case of global alignment without free insertions/deletions. However, for the general case in Equation (7) the number of constraints is exponential, since the number of alignments between Æ and is exponential in the length of Æ and. Unlike the restricted case in [8], standard optimization algorithms cannot handle this size problem. To overcome this limitation, in Section 5 we will propose an algorithm that exploits the special structure of Equation (7) so that it needs to examine only a subset that is at most linear in the number of training examples Ò. If the set of inequalities in Equation (7) is feasible, there will typically be more than one solution Û. To specify a unique solution, we select the Û for which the similarity of the homolog Û Æ Ò À Ò ÔÆÀ µ is uniformly most different from the similarity ÑÜ ¾Ë Û Æ µ of the best alignment with any decoy. This corresponds to the maximum-margin principle employed in Support Vector Machines [12]. Denoting the margin by Æ and restricting the Ä ¾ norm of Û to make the problem well-posed, this leads to the following optimization problem. ÑÜ Û (5) ¾ ƾ (8) ¾ Ë Û Æ µ Û Æ À ÆÀ µ Æ (9) (10) Ò ¾ ËÒ Û Æ Ò Ò µ Û Æ Ò À Ò ÆÀ µ Æ (11) Û (12) Due to the linearity of the similarity function (6), the length of Û is a free variable and we can fix it to Æ. Substituting for Æ and rearranging leads to the equivalent optimization problem ÑÒ Û ¾ ÛÌ Û (13) 4
5 ¾ Ë Æ À ÆÀ µ Æ µ Û (14) (15) Ò ¾ ËÒ Æ Ò À Ò ÆÀ µ Æ Ò Ò µ Û (16) Since this quadratic program (QP) has a positive-definite objective function and (feasible) linear constraints, it is strictly convex. This means it has a unique global minimum and no local minima [4]. The constraints are similar to the ordinal regression approach in [6] and it has a structure similar to the Ranking SVM described in [7] for information retrieval. However, the number of constraints is much larger. To allow errors in the training set, we introduce slack variables [2]. Corresponding to the error measure ÖÖ È Ûµ we have one slack variable for each native sequence. This is different from a normal classification or regression SVM, where there is a different slack variable for each constraint. The slacks enter the objective function according to a trade-off parameter. For simplicity, we consider only the case where the slacks enter the objective function squared. Ò ÑÒ Û ¾ ÛÌ Û ¾ (17) ¾ Ë Æ À ÆÀ µ Æ µ Û (18) (19) Ò ¾ Ë Ò Æ Ò À Ò ÆÀ µ Æ Ò Ò µ Û Ò (20) È Ò Note that ¾ is an upper bound on the training error ÖÖ Ë Ûµ. Therefore, the algorithm minimizes the training error ÖÖ Ë Ûµ while maximizing margin. 5 Training Algorithm Due to the exponential number of constraints, standard optimization software cannot handle the number of constraints resulting from problems of interesting size. However, by exploiting the special structure of the problem, we propose the following algorithm that finds the solution of (17)-(20) after examining only a small number of constraints. The algorithm proceeds by greedily adding constraints from (18)-(20) to a working set Ã. The algorithm stops, when all constraints in (18)-(20) are fulfilled up to a precision of. 5
6 Input: native sequences Æ Æ Ò, homolog sequences À À Ò sets of decoy sequences Ë Ë Ò, tolerated approximation error ¼. Ã, Û ¼, ¼ repeat à ÓÖ Ã for from to Ò until(ã à ÓÖ ) Output: Û for from to Ë via dynamic program- find ÖÑÜ Û Ì Æ µ ming Û Ì Æ À ÆÀ µ Æ, alignments ÆÀ if Û Ì Æ À ÆÀ µ Æ µµ Ò Ó Ã Ã µµ È solve QP Û µ ÖÑÒ Û ¾ ÛÌ Ò Û Ã. ¾ subject to The following two theorems show that the algorithm returns the correct solution and that it stops after Ç Òµ iterations through the repeat-loop. Theorem 1 (CORRECTNESS) The algorithm returns an approximation to (17)-(20) that has an objective value not higher than the solution of (17)-(20), and that fulfills all constraints up to a precision of. For ¼, the algorithm returns the solution Û µ of (17)-(20). ÆÀ Ò, Proof Let Û and be the solution of (17)-(20). Since the algorithm solves the QP on a subset È of the constraints in È each iteration, it must return a solution Û with ¾ ÛÌ Û Ò ¾ ¾ Û Ì Û Ò ¾. This follows from the fact that decreasing the feasible region cannot lead to a lower minimum. It is left to show that the algorithm does not terminate before all constraints (18)- (20) are fulfilled up to precision. In the final iteration, the algorithm finds the highest scoring alignment for each decoy and checks whether the constraint Û Ì Æ À ÆÀ µ Æ µµ is fulfilled. Three cases can occur: First, the constraint can be violated and the algorithm will not terminate yet. Second, it is already in à and is fulfilled by construction. Third, the constraint is not in à but fulfilled anyway and it is not added. If the constraint is fulfilled, the constraints for all other alignments into this decoy are fulfilled as well, since we checked the constraint for which the margin was smallest for the given Û. It follows that the algorithm terminates only if all constraints are fulfilled up to precision. Similarly, it can be shown that for ¼ the algorithm finds a solution so that the KKT-conditions of the Wolfe Dual of (17)-(20) are fulfilled up to a precision of. We omit the proof for brevity. 6
7 Theorem 2 (TERMINATION) The algorithm stops after adding at most ¾Î Ê ¾ ¾ (21) constraints to the set Ã. Î is the minimum of (17)-(20) and Ê ¾ is a constant bounded by the maximum of Æ À ÆÀ µ Æ µµ ¾ ¾. Proof The first part of the proof is to show that the objective value increases by some constant with every constraint that È is added to Ã. Denote with Î the solution Î È Û µ ÑÒ Û ¾ ÛÌ Ò Û ¾ subject to à after adding constraints. This primal optimization problem can be transformed into an equivalent problem of the form Î È Û ¼ µ ÑÒ Û ¼ ¾ Û¼Ì Û ¼ subject to à ¼, where each constraint has the form Û Ì Ü with Ô Ü Æ À ÆÀ µ Æ µ ¼ ¼ ¾ ¼ ¼). Its corresponding Wolfe dual is «µ ÑÜ «¼ È «¾ È È ««Ü Ü. At the solution «µ È Û¼ µ È Û µ Î and for every feasible point «µ È Û µ. Primal and dual are È È connected via Û ¼ «Ü. Adding a constraint to the dual with Û ¼ Ì Ü «Ü Ü means extending the dual to «µ ÑÜ ««¼ ¾ «µ ÑÜ «¼ ««««Ü Ü «««µ ÑÜ «¼ ««µ «Ü Ü «Ü Ü ¾ «¾ ܾ ¾ «¾ ܾ Solving the remaining scalar optimization problem over «shows that «¼ and that Î Î Since the algorithm only adds constraints that are violated by the current solution by more than, after adding ÑÜ constraints the solution Î ÑÜ over the ¾ ¾Ê ¾. ¾Î ʾ ¾ ¾Î ʾ ¾ subset à ÑÜ is at least Î ÑÜ Î ¼ ¼ Î. Any additional constraint that is violated by more than would lead to a minimum that is larger than Î. Since the minimum over a subset of constraints can only be smaller than the minimum over all constraints, there cannot be any more constraints violated by more than and the algorithm stops. The theorem directly leads to the conclusion that the maximum number of constraints in à scales linearly with the number of training examples Ò, since Î can be upper bounded as Î Ò using the feasible point Û ¼ and in (17)-(20). Furthermore, it scales only polynomially with the length of the sequences, since Ê is polynomial in the length of the sequences. While the number of constraints can potentially explode for small values of, experience with Support Vector Machines for classification showed that relatively large ¾ ¾Ê ¾ ¾ «¾ ܾ 7
8 ThreeParam Train ThreeParam Test IndivSubstCost Train IndivSubstCost Test Average Train/Test Error (delta) Number of Training Examples Figure 2: Left: Train and test error rates for the 3 and the 403 parameter model depending on the number of training examples. Right: Typical learned substitution matrix after 40 training examples for the 403-parameter model. values of are sufficient without loss of generalization performance. We will verify the efficiency and the prediction performance of the algorithm empirically in the following. 6 Experiments To analyze the behavior of the algorithm under varying conditions, we constructed a synthetic dataset according to the following sequence and alignment model. The native sequence and the decoys are generated by drawing randomly from a 20 letter alphabet ¾¼ so that letter ¾ has probability ¾¼. Each sequence has length 50, and there are 10 decoys per native. To generate the homolog, we generate an alignment string of length 30 consisting of 4 characters match, substitute, insert, delete. For simplicity of illustration, substitutions are always mod ¾¼µ. While we experiment with several alignment models, we only report typical results here where matches occur with probability ¼¾, substitutions with ¼, insertion with ¼¾, deletion with ¼¾. The homolog is created by applying the alignment string to a randomly selected substring of the native. The shortening of the sequences through insertions and deletions is padded by additional random characters. Figure 2 shows training and test error rates for two models depending on the number of training examples averaged over 10 trials. The first model has only 3 parameters ( match, substitute, insert/delete ) and uses a uniform substitution matrix. The second model also learns the 400 parameters of the substitution matrix, resulting in a total of 403 parameters. We chose ¼¼ and ¼. The left-hand graph of Figure 2 shows that for the 403-parameter model, the generalization error is high for small numbers of training examples, but quickly drops as the number of examples increases. The 3-parameter model cannot fit the data as well. Its training error starts out much higher and training and test error essentially converge after only a few examples. The right-hand graph of Figure 2 shows the learned matrix of substitution costs for the 403-parameter model. As desired, the elements of the matrix are close to zero except for the off-diagonal. This captures the substitution model mod ¾¼µ. Figure 3 analyzes the efficiency of the algorithm via the number of constraints that 8
9 ThreeParam IndivSubstCost ThreeParam IndivSubstCost Average Number of Constraints Average Number of Constraints Number of Training Examples Epsilon Figure 3: Number of constraints added to à depending on the number of training examples (left) and the value of (right). If not stated otherwise, ¼, ¼¼, and Ò ¾¼. are added to à before convergence. The left-hand graph shows the scaling with the number of training examples. As predicted by Theorem 2, the number of constraints grows (sub-)linearly with the number of examples. Furthermore, the actual number of constraints is small enough so that it can easily be handled by standard quadratic optimization software. The right-hand graph shows how the number of constraints in the final à changes with ÐÓ µ. The observed scaling appears to be better than suggested by the upper bound in Theorem 2. A good value for is ¼. We observed that larger values lead to worse prediction accuracy, while smaller values decrease efficiency while not providing further benefit. 7 Conclusions The paper presented a discriminative learning approach to inferring the cost parameters of a linear sequence alignment model from training data. We proposed an algorithm for solving the resulting training problem and showed its efficiency both theoretically and empirically. Experiments show that the algorithm can effectively learn the alignment parameters on a synthetic task. We are currently applying the algorithm to learning alignment models for protein homology detection. An open question is whether it is possible to remove the assumption that the alignment between native and homolog is known while maintaining the tractability of the problem. Acknowledgments Many thanks to Ron Elber and Tamara Galor for their insightful discussions and their contribution to the research that lead to this paper. 9
10 References [1] R. Barzilay and L. Lee. Bootstrapping lexical choice via multiple-sequence alignment. In Conference on Empirical Methods in Natural Language Processing (EMNLP), [2] Corinna Cortes and Vladimir N. Vapnik. Support vector networks. Machine Learning Journal, 20: , [3] R. Durbin, S. Eddy, A. Krogh, and G. Mitchison. Biological Sequence Analysis. Cambridge University Press, [4] P. E. Gill, W. Murray, and M. H. Wright. Practical Optimization. Academic Press, [5] D. Gusfield and P. Stelling. Parametric and inverse-parametric sequence alignment with xparal. Methods in Enzymology, 266: , [6] R. Herbrich, T. Graepel, and K. Obermayer. Large margin rank boundaries for ordinal regression. In Advances in Large Margin Classifiers, pages MIT Press, Cambridge, MA, [7] T. Joachims. Optimizing search engines using clickthrough data. In Proceedings of the ACM Conference on Knowledge Discovery and Data Mining (KDD), [8] J. Meller and R. Elber. Linear programming optimization and a double statistical filter for protein threading protocols. Proteins Structure, Function, and Genetics, 45: , [9] S. E Ristad and P. N. Yianilos. Learning string edit distance. IEEE Transactions on Pattern Recognition and Machine Intelligence, Vol. 20(5): , [10] T. Smith and M. Waterman. Identification of common molecular subsequences. Journal of Molecular Biology, 147: , [11] Fangting Sun, D. Fernandez-Baca, and Wei Yu. Inverse parametric sequence alignment. In International Computing and Combinatorics Conference (CO- COON), [12] V. Vapnik. Statistical Learning Theory. Wiley, Chichester, GB,
Scan Scheduling Specification and Analysis
 Scan Scheduling Specification and Analysis Bruno Dutertre System Design Laboratory SRI International Menlo Park, CA 94025 May 24, 2000 This work was partially funded by DARPA/AFRL under BAE System subcontract
Scan Scheduling Specification and Analysis Bruno Dutertre System Design Laboratory SRI International Menlo Park, CA 94025 May 24, 2000 This work was partially funded by DARPA/AFRL under BAE System subcontract
A General Greedy Approximation Algorithm with Applications
 A General Greedy Approximation Algorithm with Applications Tong Zhang IBM T.J. Watson Research Center Yorktown Heights, NY 10598 tzhang@watson.ibm.com Abstract Greedy approximation algorithms have been
A General Greedy Approximation Algorithm with Applications Tong Zhang IBM T.J. Watson Research Center Yorktown Heights, NY 10598 tzhang@watson.ibm.com Abstract Greedy approximation algorithms have been
Support Vector Machine Learning for Interdependent and Structured Output Spaces
 Support Vector Machine Learning for Interdependent and Structured Output Spaces I. Tsochantaridis, T. Hofmann, T. Joachims, and Y. Altun, ICML, 2004. And also I. Tsochantaridis, T. Joachims, T. Hofmann,
Support Vector Machine Learning for Interdependent and Structured Output Spaces I. Tsochantaridis, T. Hofmann, T. Joachims, and Y. Altun, ICML, 2004. And also I. Tsochantaridis, T. Joachims, T. Hofmann,
Kernel Methods & Support Vector Machines
 & Support Vector Machines & Support Vector Machines Arvind Visvanathan CSCE 970 Pattern Recognition 1 & Support Vector Machines Question? Draw a single line to separate two classes? 2 & Support Vector
& Support Vector Machines & Support Vector Machines Arvind Visvanathan CSCE 970 Pattern Recognition 1 & Support Vector Machines Question? Draw a single line to separate two classes? 2 & Support Vector
Inverse Sequence Alignment from Partial Examples
 Inverse Sequence Alignment from Partial Examples Eagu Kim and John Kececioglu Department of Computer Science The University of Arizona, Tucson AZ 85721, USA {egkim,kece}@cs.arizona.edu Abstract. When aligning
Inverse Sequence Alignment from Partial Examples Eagu Kim and John Kececioglu Department of Computer Science The University of Arizona, Tucson AZ 85721, USA {egkim,kece}@cs.arizona.edu Abstract. When aligning
Exponentiated Gradient Algorithms for Large-margin Structured Classification
 Exponentiated Gradient Algorithms for Large-margin Structured Classification Peter L. Bartlett U.C.Berkeley bartlett@stat.berkeley.edu Ben Taskar Stanford University btaskar@cs.stanford.edu Michael Collins
Exponentiated Gradient Algorithms for Large-margin Structured Classification Peter L. Bartlett U.C.Berkeley bartlett@stat.berkeley.edu Ben Taskar Stanford University btaskar@cs.stanford.edu Michael Collins
From Static to Dynamic Routing: Efficient Transformations of Store-and-Forward Protocols
 From Static to Dynamic Routing: Efficient Transformations of Store-and-Forward Protocols Christian Scheideler Ý Berthold Vöcking Þ Abstract We investigate how static store-and-forward routing algorithms
From Static to Dynamic Routing: Efficient Transformations of Store-and-Forward Protocols Christian Scheideler Ý Berthold Vöcking Þ Abstract We investigate how static store-and-forward routing algorithms
Data Mining: Concepts and Techniques. Chapter 9 Classification: Support Vector Machines. Support Vector Machines (SVMs)
 Data Mining: Concepts and Techniques Chapter 9 Classification: Support Vector Machines 1 Support Vector Machines (SVMs) SVMs are a set of related supervised learning methods used for classification Based
Data Mining: Concepts and Techniques Chapter 9 Classification: Support Vector Machines 1 Support Vector Machines (SVMs) SVMs are a set of related supervised learning methods used for classification Based
Optimizing Search Engines using Click-through Data
 Optimizing Search Engines using Click-through Data By Sameep - 100050003 Rahee - 100050028 Anil - 100050082 1 Overview Web Search Engines : Creating a good information retrieval system Previous Approaches
Optimizing Search Engines using Click-through Data By Sameep - 100050003 Rahee - 100050028 Anil - 100050082 1 Overview Web Search Engines : Creating a good information retrieval system Previous Approaches
SFU CMPT Lecture: Week 8
 SFU CMPT-307 2008-2 1 Lecture: Week 8 SFU CMPT-307 2008-2 Lecture: Week 8 Ján Maňuch E-mail: jmanuch@sfu.ca Lecture on June 24, 2008, 5.30pm-8.20pm SFU CMPT-307 2008-2 2 Lecture: Week 8 Universal hashing
SFU CMPT-307 2008-2 1 Lecture: Week 8 SFU CMPT-307 2008-2 Lecture: Week 8 Ján Maňuch E-mail: jmanuch@sfu.ca Lecture on June 24, 2008, 5.30pm-8.20pm SFU CMPT-307 2008-2 2 Lecture: Week 8 Universal hashing
Optimal Time Bounds for Approximate Clustering
 Optimal Time Bounds for Approximate Clustering Ramgopal R. Mettu C. Greg Plaxton Department of Computer Science University of Texas at Austin Austin, TX 78712, U.S.A. ramgopal, plaxton@cs.utexas.edu Abstract
Optimal Time Bounds for Approximate Clustering Ramgopal R. Mettu C. Greg Plaxton Department of Computer Science University of Texas at Austin Austin, TX 78712, U.S.A. ramgopal, plaxton@cs.utexas.edu Abstract
RSA (Rivest Shamir Adleman) public key cryptosystem: Key generation: Pick two large prime Ô Õ ¾ numbers È.
 RSA (Rivest Shamir Adleman) public key cryptosystem: Key generation: Pick two large prime Ô Õ ¾ numbers È. Let Ò Ô Õ. Pick ¾ ½ ³ Òµ ½ so, that ³ Òµµ ½. Let ½ ÑÓ ³ Òµµ. Public key: Ò µ. Secret key Ò µ.
RSA (Rivest Shamir Adleman) public key cryptosystem: Key generation: Pick two large prime Ô Õ ¾ numbers È. Let Ò Ô Õ. Pick ¾ ½ ³ Òµ ½ so, that ³ Òµµ ½. Let ½ ÑÓ ³ Òµµ. Public key: Ò µ. Secret key Ò µ.
Support Vector Machines. James McInerney Adapted from slides by Nakul Verma
 Support Vector Machines James McInerney Adapted from slides by Nakul Verma Last time Decision boundaries for classification Linear decision boundary (linear classification) The Perceptron algorithm Mistake
Support Vector Machines James McInerney Adapted from slides by Nakul Verma Last time Decision boundaries for classification Linear decision boundary (linear classification) The Perceptron algorithm Mistake
COMS 4771 Support Vector Machines. Nakul Verma
 COMS 4771 Support Vector Machines Nakul Verma Last time Decision boundaries for classification Linear decision boundary (linear classification) The Perceptron algorithm Mistake bound for the perceptron
COMS 4771 Support Vector Machines Nakul Verma Last time Decision boundaries for classification Linear decision boundary (linear classification) The Perceptron algorithm Mistake bound for the perceptron
Leave-One-Out Support Vector Machines
 Leave-One-Out Support Vector Machines Jason Weston Department of Computer Science Royal Holloway, University of London, Egham Hill, Egham, Surrey, TW20 OEX, UK. Abstract We present a new learning algorithm
Leave-One-Out Support Vector Machines Jason Weston Department of Computer Science Royal Holloway, University of London, Egham Hill, Egham, Surrey, TW20 OEX, UK. Abstract We present a new learning algorithm
Support Vector Machines.
 Support Vector Machines srihari@buffalo.edu SVM Discussion Overview 1. Overview of SVMs 2. Margin Geometry 3. SVM Optimization 4. Overlapping Distributions 5. Relationship to Logistic Regression 6. Dealing
Support Vector Machines srihari@buffalo.edu SVM Discussion Overview 1. Overview of SVMs 2. Margin Geometry 3. SVM Optimization 4. Overlapping Distributions 5. Relationship to Logistic Regression 6. Dealing
Generating the Reduced Set by Systematic Sampling
 Generating the Reduced Set by Systematic Sampling Chien-Chung Chang and Yuh-Jye Lee Email: {D9115009, yuh-jye}@mail.ntust.edu.tw Department of Computer Science and Information Engineering National Taiwan
Generating the Reduced Set by Systematic Sampling Chien-Chung Chang and Yuh-Jye Lee Email: {D9115009, yuh-jye}@mail.ntust.edu.tw Department of Computer Science and Information Engineering National Taiwan
Theoretical Concepts of Machine Learning
 Theoretical Concepts of Machine Learning Part 2 Institute of Bioinformatics Johannes Kepler University, Linz, Austria Outline 1 Introduction 2 Generalization Error 3 Maximum Likelihood 4 Noise Models 5
Theoretical Concepts of Machine Learning Part 2 Institute of Bioinformatics Johannes Kepler University, Linz, Austria Outline 1 Introduction 2 Generalization Error 3 Maximum Likelihood 4 Noise Models 5
All lecture slides will be available at CSC2515_Winter15.html
 CSC2515 Fall 2015 Introduc3on to Machine Learning Lecture 9: Support Vector Machines All lecture slides will be available at http://www.cs.toronto.edu/~urtasun/courses/csc2515/ CSC2515_Winter15.html Many
CSC2515 Fall 2015 Introduc3on to Machine Learning Lecture 9: Support Vector Machines All lecture slides will be available at http://www.cs.toronto.edu/~urtasun/courses/csc2515/ CSC2515_Winter15.html Many
RSA (Rivest Shamir Adleman) public key cryptosystem: Key generation: Pick two large prime Ô Õ ¾ numbers È.
 RSA (Rivest Shamir Adleman) public key cryptosystem: Key generation: Pick two large prime Ô Õ ¾ numbers È. Let Ò Ô Õ. Pick ¾ ½ ³ Òµ ½ so, that ³ Òµµ ½. Let ½ ÑÓ ³ Òµµ. Public key: Ò µ. Secret key Ò µ.
RSA (Rivest Shamir Adleman) public key cryptosystem: Key generation: Pick two large prime Ô Õ ¾ numbers È. Let Ò Ô Õ. Pick ¾ ½ ³ Òµ ½ so, that ³ Òµµ ½. Let ½ ÑÓ ³ Òµµ. Public key: Ò µ. Secret key Ò µ.
Random projection for non-gaussian mixture models
 Random projection for non-gaussian mixture models Győző Gidófalvi Department of Computer Science and Engineering University of California, San Diego La Jolla, CA 92037 gyozo@cs.ucsd.edu Abstract Recently,
Random projection for non-gaussian mixture models Győző Gidófalvi Department of Computer Science and Engineering University of California, San Diego La Jolla, CA 92037 gyozo@cs.ucsd.edu Abstract Recently,
Introduction to Machine Learning
 Introduction to Machine Learning Maximum Margin Methods Varun Chandola Computer Science & Engineering State University of New York at Buffalo Buffalo, NY, USA chandola@buffalo.edu Chandola@UB CSE 474/574
Introduction to Machine Learning Maximum Margin Methods Varun Chandola Computer Science & Engineering State University of New York at Buffalo Buffalo, NY, USA chandola@buffalo.edu Chandola@UB CSE 474/574
Chapter 4: Non-Parametric Techniques
 Chapter 4: Non-Parametric Techniques Introduction Density Estimation Parzen Windows Kn-Nearest Neighbor Density Estimation K-Nearest Neighbor (KNN) Decision Rule Supervised Learning How to fit a density
Chapter 4: Non-Parametric Techniques Introduction Density Estimation Parzen Windows Kn-Nearest Neighbor Density Estimation K-Nearest Neighbor (KNN) Decision Rule Supervised Learning How to fit a density
Online Facility Location
 Online Facility Location Adam Meyerson Abstract We consider the online variant of facility location, in which demand points arrive one at a time and we must maintain a set of facilities to service these
Online Facility Location Adam Meyerson Abstract We consider the online variant of facility location, in which demand points arrive one at a time and we must maintain a set of facilities to service these
Kernels + K-Means Introduction to Machine Learning. Matt Gormley Lecture 29 April 25, 2018
 10-601 Introduction to Machine Learning Machine Learning Department School of Computer Science Carnegie Mellon University Kernels + K-Means Matt Gormley Lecture 29 April 25, 2018 1 Reminders Homework 8:
10-601 Introduction to Machine Learning Machine Learning Department School of Computer Science Carnegie Mellon University Kernels + K-Means Matt Gormley Lecture 29 April 25, 2018 1 Reminders Homework 8:
Lecture Linear Support Vector Machines
 Lecture 8 In this lecture we return to the task of classification. As seen earlier, examples include spam filters, letter recognition, or text classification. In this lecture we introduce a popular method
Lecture 8 In this lecture we return to the task of classification. As seen earlier, examples include spam filters, letter recognition, or text classification. In this lecture we introduce a popular method
Response Time Analysis of Asynchronous Real-Time Systems
 Response Time Analysis of Asynchronous Real-Time Systems Guillem Bernat Real-Time Systems Research Group Department of Computer Science University of York York, YO10 5DD, UK Technical Report: YCS-2002-340
Response Time Analysis of Asynchronous Real-Time Systems Guillem Bernat Real-Time Systems Research Group Department of Computer Science University of York York, YO10 5DD, UK Technical Report: YCS-2002-340
Second Order SMO Improves SVM Online and Active Learning
 Second Order SMO Improves SVM Online and Active Learning Tobias Glasmachers and Christian Igel Institut für Neuroinformatik, Ruhr-Universität Bochum 4478 Bochum, Germany Abstract Iterative learning algorithms
Second Order SMO Improves SVM Online and Active Learning Tobias Glasmachers and Christian Igel Institut für Neuroinformatik, Ruhr-Universität Bochum 4478 Bochum, Germany Abstract Iterative learning algorithms
Lecture 7: Support Vector Machine
 Lecture 7: Support Vector Machine Hien Van Nguyen University of Houston 9/28/2017 Separating hyperplane Red and green dots can be separated by a separating hyperplane Two classes are separable, i.e., each
Lecture 7: Support Vector Machine Hien Van Nguyen University of Houston 9/28/2017 Separating hyperplane Red and green dots can be separated by a separating hyperplane Two classes are separable, i.e., each
Linear methods for supervised learning
 Linear methods for supervised learning LDA Logistic regression Naïve Bayes PLA Maximum margin hyperplanes Soft-margin hyperplanes Least squares resgression Ridge regression Nonlinear feature maps Sometimes
Linear methods for supervised learning LDA Logistic regression Naïve Bayes PLA Maximum margin hyperplanes Soft-margin hyperplanes Least squares resgression Ridge regression Nonlinear feature maps Sometimes
J. Weston, A. Gammerman, M. Stitson, V. Vapnik, V. Vovk, C. Watkins. Technical Report. February 5, 1998
 Density Estimation using Support Vector Machines J. Weston, A. Gammerman, M. Stitson, V. Vapnik, V. Vovk, C. Watkins. Technical Report CSD-TR-97-3 February 5, 998!()+, -./ 3456 Department of Computer Science
Density Estimation using Support Vector Machines J. Weston, A. Gammerman, M. Stitson, V. Vapnik, V. Vovk, C. Watkins. Technical Report CSD-TR-97-3 February 5, 998!()+, -./ 3456 Department of Computer Science
Mathematical Programming and Research Methods (Part II)
 Mathematical Programming and Research Methods (Part II) 4. Convexity and Optimization Massimiliano Pontil (based on previous lecture by Andreas Argyriou) 1 Today s Plan Convex sets and functions Types
Mathematical Programming and Research Methods (Part II) 4. Convexity and Optimization Massimiliano Pontil (based on previous lecture by Andreas Argyriou) 1 Today s Plan Convex sets and functions Types
Efficiency versus Convergence of Boolean Kernels for On-Line Learning Algorithms
 Efficiency versus Convergence of Boolean Kernels for On-Line Learning Algorithms Roni Khardon Tufts University Medford, MA 02155 roni@eecs.tufts.edu Dan Roth University of Illinois Urbana, IL 61801 danr@cs.uiuc.edu
Efficiency versus Convergence of Boolean Kernels for On-Line Learning Algorithms Roni Khardon Tufts University Medford, MA 02155 roni@eecs.tufts.edu Dan Roth University of Illinois Urbana, IL 61801 danr@cs.uiuc.edu
SVMs for Structured Output. Andrea Vedaldi
 SVMs for Structured Output Andrea Vedaldi SVM struct Tsochantaridis Hofmann Joachims Altun 04 Extending SVMs 3 Extending SVMs SVM = parametric function arbitrary input binary output 3 Extending SVMs SVM
SVMs for Structured Output Andrea Vedaldi SVM struct Tsochantaridis Hofmann Joachims Altun 04 Extending SVMs 3 Extending SVMs SVM = parametric function arbitrary input binary output 3 Extending SVMs SVM
Development in Object Detection. Junyuan Lin May 4th
 Development in Object Detection Junyuan Lin May 4th Line of Research [1] N. Dalal and B. Triggs. Histograms of oriented gradients for human detection, CVPR 2005. HOG Feature template [2] P. Felzenszwalb,
Development in Object Detection Junyuan Lin May 4th Line of Research [1] N. Dalal and B. Triggs. Histograms of oriented gradients for human detection, CVPR 2005. HOG Feature template [2] P. Felzenszwalb,
CSE 417T: Introduction to Machine Learning. Lecture 22: The Kernel Trick. Henry Chai 11/15/18
 CSE 417T: Introduction to Machine Learning Lecture 22: The Kernel Trick Henry Chai 11/15/18 Linearly Inseparable Data What can we do if the data is not linearly separable? Accept some non-zero in-sample
CSE 417T: Introduction to Machine Learning Lecture 22: The Kernel Trick Henry Chai 11/15/18 Linearly Inseparable Data What can we do if the data is not linearly separable? Accept some non-zero in-sample
The Online Median Problem
 The Online Median Problem Ramgopal R. Mettu C. Greg Plaxton November 1999 Abstract We introduce a natural variant of the (metric uncapacitated) -median problem that we call the online median problem. Whereas
The Online Median Problem Ramgopal R. Mettu C. Greg Plaxton November 1999 Abstract We introduce a natural variant of the (metric uncapacitated) -median problem that we call the online median problem. Whereas
Introduction to Support Vector Machines
 Introduction to Support Vector Machines CS 536: Machine Learning Littman (Wu, TA) Administration Slides borrowed from Martin Law (from the web). 1 Outline History of support vector machines (SVM) Two classes,
Introduction to Support Vector Machines CS 536: Machine Learning Littman (Wu, TA) Administration Slides borrowed from Martin Law (from the web). 1 Outline History of support vector machines (SVM) Two classes,
Support Vector Machines
 Support Vector Machines . Importance of SVM SVM is a discriminative method that brings together:. computational learning theory. previously known methods in linear discriminant functions 3. optimization
Support Vector Machines . Importance of SVM SVM is a discriminative method that brings together:. computational learning theory. previously known methods in linear discriminant functions 3. optimization
Robust Signal-Structure Reconstruction
 Robust Signal-Structure Reconstruction V. Chetty 1, D. Hayden 2, J. Gonçalves 2, and S. Warnick 1 1 Information and Decision Algorithms Laboratories, Brigham Young University 2 Control Group, Department
Robust Signal-Structure Reconstruction V. Chetty 1, D. Hayden 2, J. Gonçalves 2, and S. Warnick 1 1 Information and Decision Algorithms Laboratories, Brigham Young University 2 Control Group, Department
Constructive floorplanning with a yield objective
 Constructive floorplanning with a yield objective Rajnish Prasad and Israel Koren Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA 13 E-mail: rprasad,koren@ecs.umass.edu
Constructive floorplanning with a yield objective Rajnish Prasad and Israel Koren Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA 13 E-mail: rprasad,koren@ecs.umass.edu
Agglomerative Information Bottleneck
 Agglomerative Information Bottleneck Noam Slonim Naftali Tishby Institute of Computer Science and Center for Neural Computation The Hebrew University Jerusalem, 91904 Israel email: noamm,tishby@cs.huji.ac.il
Agglomerative Information Bottleneck Noam Slonim Naftali Tishby Institute of Computer Science and Center for Neural Computation The Hebrew University Jerusalem, 91904 Israel email: noamm,tishby@cs.huji.ac.il
Programming, numerics and optimization
 Programming, numerics and optimization Lecture C-4: Constrained optimization Łukasz Jankowski ljank@ippt.pan.pl Institute of Fundamental Technological Research Room 4.32, Phone +22.8261281 ext. 428 June
Programming, numerics and optimization Lecture C-4: Constrained optimization Łukasz Jankowski ljank@ippt.pan.pl Institute of Fundamental Technological Research Room 4.32, Phone +22.8261281 ext. 428 June
Approximation by NURBS curves with free knots
 Approximation by NURBS curves with free knots M Randrianarivony G Brunnett Technical University of Chemnitz, Faculty of Computer Science Computer Graphics and Visualization Straße der Nationen 6, 97 Chemnitz,
Approximation by NURBS curves with free knots M Randrianarivony G Brunnett Technical University of Chemnitz, Faculty of Computer Science Computer Graphics and Visualization Straße der Nationen 6, 97 Chemnitz,
Data Analysis 3. Support Vector Machines. Jan Platoš October 30, 2017
 Data Analysis 3 Support Vector Machines Jan Platoš October 30, 2017 Department of Computer Science Faculty of Electrical Engineering and Computer Science VŠB - Technical University of Ostrava Table of
Data Analysis 3 Support Vector Machines Jan Platoš October 30, 2017 Department of Computer Science Faculty of Electrical Engineering and Computer Science VŠB - Technical University of Ostrava Table of
Tolls for heterogeneous selfish users in multicommodity networks and generalized congestion games
 Tolls for heterogeneous selfish users in multicommodity networks and generalized congestion games Lisa Fleischer Kamal Jain Mohammad Mahdian Abstract We prove the existence of tolls to induce multicommodity,
Tolls for heterogeneous selfish users in multicommodity networks and generalized congestion games Lisa Fleischer Kamal Jain Mohammad Mahdian Abstract We prove the existence of tolls to induce multicommodity,
Lecture 10. Sequence alignments
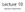 Lecture 10 Sequence alignments Alignment algorithms: Overview Given a scoring system, we need to have an algorithm for finding an optimal alignment for a pair of sequences. We want to maximize the score
Lecture 10 Sequence alignments Alignment algorithms: Overview Given a scoring system, we need to have an algorithm for finding an optimal alignment for a pair of sequences. We want to maximize the score
Worst-Case Utilization Bound for EDF Scheduling on Real-Time Multiprocessor Systems
 Worst-Case Utilization Bound for EDF Scheduling on Real-Time Multiprocessor Systems J.M. López, M. García, J.L. Díaz, D.F. García University of Oviedo Department of Computer Science Campus de Viesques,
Worst-Case Utilization Bound for EDF Scheduling on Real-Time Multiprocessor Systems J.M. López, M. García, J.L. Díaz, D.F. García University of Oviedo Department of Computer Science Campus de Viesques,
Lecture 10: SVM Lecture Overview Support Vector Machines The binary classification problem
 Computational Learning Theory Fall Semester, 2012/13 Lecture 10: SVM Lecturer: Yishay Mansour Scribe: Gitit Kehat, Yogev Vaknin and Ezra Levin 1 10.1 Lecture Overview In this lecture we present in detail
Computational Learning Theory Fall Semester, 2012/13 Lecture 10: SVM Lecturer: Yishay Mansour Scribe: Gitit Kehat, Yogev Vaknin and Ezra Levin 1 10.1 Lecture Overview In this lecture we present in detail
Lecture 9: Support Vector Machines
 Lecture 9: Support Vector Machines William Webber (william@williamwebber.com) COMP90042, 2014, Semester 1, Lecture 8 What we ll learn in this lecture Support Vector Machines (SVMs) a highly robust and
Lecture 9: Support Vector Machines William Webber (william@williamwebber.com) COMP90042, 2014, Semester 1, Lecture 8 What we ll learn in this lecture Support Vector Machines (SVMs) a highly robust and
Semi-Supervised Clustering with Partial Background Information
 Semi-Supervised Clustering with Partial Background Information Jing Gao Pang-Ning Tan Haibin Cheng Abstract Incorporating background knowledge into unsupervised clustering algorithms has been the subject
Semi-Supervised Clustering with Partial Background Information Jing Gao Pang-Ning Tan Haibin Cheng Abstract Incorporating background knowledge into unsupervised clustering algorithms has been the subject
Application of Support Vector Machine Algorithm in Spam Filtering
 Application of Support Vector Machine Algorithm in E-Mail Spam Filtering Julia Bluszcz, Daria Fitisova, Alexander Hamann, Alexey Trifonov, Advisor: Patrick Jähnichen Abstract The problem of spam classification
Application of Support Vector Machine Algorithm in E-Mail Spam Filtering Julia Bluszcz, Daria Fitisova, Alexander Hamann, Alexey Trifonov, Advisor: Patrick Jähnichen Abstract The problem of spam classification
Natural Language Processing
 Natural Language Processing Classification III Dan Klein UC Berkeley 1 Classification 2 Linear Models: Perceptron The perceptron algorithm Iteratively processes the training set, reacting to training errors
Natural Language Processing Classification III Dan Klein UC Berkeley 1 Classification 2 Linear Models: Perceptron The perceptron algorithm Iteratively processes the training set, reacting to training errors
A Simple Additive Re-weighting Strategy for Improving Margins
 A Simple Additive Re-weighting Strategy for Improving Margins Fabio Aiolli and Alessandro Sperduti Department of Computer Science, Corso Italia 4, Pisa, Italy e-mail: aiolli, perso@di.unipi.it Abstract
A Simple Additive Re-weighting Strategy for Improving Margins Fabio Aiolli and Alessandro Sperduti Department of Computer Science, Corso Italia 4, Pisa, Italy e-mail: aiolli, perso@di.unipi.it Abstract
Network Traffic Measurements and Analysis
 DEIB - Politecnico di Milano Fall, 2017 Sources Hastie, Tibshirani, Friedman: The Elements of Statistical Learning James, Witten, Hastie, Tibshirani: An Introduction to Statistical Learning Andrew Ng:
DEIB - Politecnico di Milano Fall, 2017 Sources Hastie, Tibshirani, Friedman: The Elements of Statistical Learning James, Witten, Hastie, Tibshirani: An Introduction to Statistical Learning Andrew Ng:
Part 4. Decomposition Algorithms Dantzig-Wolf Decomposition Algorithm
 In the name of God Part 4. 4.1. Dantzig-Wolf Decomposition Algorithm Spring 2010 Instructor: Dr. Masoud Yaghini Introduction Introduction Real world linear programs having thousands of rows and columns.
In the name of God Part 4. 4.1. Dantzig-Wolf Decomposition Algorithm Spring 2010 Instructor: Dr. Masoud Yaghini Introduction Introduction Real world linear programs having thousands of rows and columns.
CS 229 Midterm Review
 CS 229 Midterm Review Course Staff Fall 2018 11/2/2018 Outline Today: SVMs Kernels Tree Ensembles EM Algorithm / Mixture Models [ Focus on building intuition, less so on solving specific problems. Ask
CS 229 Midterm Review Course Staff Fall 2018 11/2/2018 Outline Today: SVMs Kernels Tree Ensembles EM Algorithm / Mixture Models [ Focus on building intuition, less so on solving specific problems. Ask
9. Support Vector Machines. The linearly separable case: hard-margin SVMs. The linearly separable case: hard-margin SVMs. Learning objectives
 Foundations of Machine Learning École Centrale Paris Fall 25 9. Support Vector Machines Chloé-Agathe Azencot Centre for Computational Biology, Mines ParisTech Learning objectives chloe agathe.azencott@mines
Foundations of Machine Learning École Centrale Paris Fall 25 9. Support Vector Machines Chloé-Agathe Azencot Centre for Computational Biology, Mines ParisTech Learning objectives chloe agathe.azencott@mines
Apprenticeship Learning for Reinforcement Learning. with application to RC helicopter flight Ritwik Anand, Nick Haliday, Audrey Huang
 Apprenticeship Learning for Reinforcement Learning with application to RC helicopter flight Ritwik Anand, Nick Haliday, Audrey Huang Table of Contents Introduction Theory Autonomous helicopter control
Apprenticeship Learning for Reinforcement Learning with application to RC helicopter flight Ritwik Anand, Nick Haliday, Audrey Huang Table of Contents Introduction Theory Autonomous helicopter control
IDENTIFICATION AND ELIMINATION OF INTERIOR POINTS FOR THE MINIMUM ENCLOSING BALL PROBLEM
 IDENTIFICATION AND ELIMINATION OF INTERIOR POINTS FOR THE MINIMUM ENCLOSING BALL PROBLEM S. DAMLA AHIPAŞAOĞLU AND E. ALPER Yıldırım Abstract. Given A := {a 1,..., a m } R n, we consider the problem of
IDENTIFICATION AND ELIMINATION OF INTERIOR POINTS FOR THE MINIMUM ENCLOSING BALL PROBLEM S. DAMLA AHIPAŞAOĞLU AND E. ALPER Yıldırım Abstract. Given A := {a 1,..., a m } R n, we consider the problem of
BINARY pattern recognition involves constructing a decision
 1 Incremental Training of Support Vector Machines A Shilton, M Palaniswami, Senior Member, IEEE, D Ralph, and AC Tsoi Senior Member, IEEE, Abstract We propose a new algorithm for the incremental training
1 Incremental Training of Support Vector Machines A Shilton, M Palaniswami, Senior Member, IEEE, D Ralph, and AC Tsoi Senior Member, IEEE, Abstract We propose a new algorithm for the incremental training
Designing Networks Incrementally
 Designing Networks Incrementally Adam Meyerson Kamesh Munagala Ý Serge Plotkin Þ Abstract We consider the problem of incrementally designing a network to route demand to a single sink on an underlying
Designing Networks Incrementally Adam Meyerson Kamesh Munagala Ý Serge Plotkin Þ Abstract We consider the problem of incrementally designing a network to route demand to a single sink on an underlying
Using Analytic QP and Sparseness to Speed Training of Support Vector Machines
 Using Analytic QP and Sparseness to Speed Training of Support Vector Machines John C. Platt Microsoft Research 1 Microsoft Way Redmond, WA 9805 jplatt@microsoft.com Abstract Training a Support Vector Machine
Using Analytic QP and Sparseness to Speed Training of Support Vector Machines John C. Platt Microsoft Research 1 Microsoft Way Redmond, WA 9805 jplatt@microsoft.com Abstract Training a Support Vector Machine
Support Vector Machines and their Applications
 Purushottam Kar Department of Computer Science and Engineering, Indian Institute of Technology Kanpur. Summer School on Expert Systems And Their Applications, Indian Institute of Information Technology
Purushottam Kar Department of Computer Science and Engineering, Indian Institute of Technology Kanpur. Summer School on Expert Systems And Their Applications, Indian Institute of Information Technology
Large Margin Classification Using the Perceptron Algorithm
 Large Margin Classification Using the Perceptron Algorithm Yoav Freund Robert E. Schapire Presented by Amit Bose March 23, 2006 Goals of the Paper Enhance Rosenblatt s Perceptron algorithm so that it can
Large Margin Classification Using the Perceptron Algorithm Yoav Freund Robert E. Schapire Presented by Amit Bose March 23, 2006 Goals of the Paper Enhance Rosenblatt s Perceptron algorithm so that it can
Generalized version of the support vector machine for binary classification problems: supporting hyperplane machine.
 E. G. Abramov 1*, A. B. Komissarov 2, D. A. Kornyakov Generalized version of the support vector machine for binary classification problems: supporting hyperplane machine. In this paper there is proposed
E. G. Abramov 1*, A. B. Komissarov 2, D. A. Kornyakov Generalized version of the support vector machine for binary classification problems: supporting hyperplane machine. In this paper there is proposed
Support Vector Machines: Brief Overview" November 2011 CPSC 352
 Support Vector Machines: Brief Overview" Outline Microarray Example Support Vector Machines (SVMs) Software: libsvm A Baseball Example with libsvm Classifying Cancer Tissue: The ALL/AML Dataset Golub et
Support Vector Machines: Brief Overview" Outline Microarray Example Support Vector Machines (SVMs) Software: libsvm A Baseball Example with libsvm Classifying Cancer Tissue: The ALL/AML Dataset Golub et
Programs. Introduction
 16 Interior Point I: Linear Programs Lab Objective: For decades after its invention, the Simplex algorithm was the only competitive method for linear programming. The past 30 years, however, have seen
16 Interior Point I: Linear Programs Lab Objective: For decades after its invention, the Simplex algorithm was the only competitive method for linear programming. The past 30 years, however, have seen
Information Management course
 Università degli Studi di Milano Master Degree in Computer Science Information Management course Teacher: Alberto Ceselli Lecture 20: 10/12/2015 Data Mining: Concepts and Techniques (3 rd ed.) Chapter
Università degli Studi di Milano Master Degree in Computer Science Information Management course Teacher: Alberto Ceselli Lecture 20: 10/12/2015 Data Mining: Concepts and Techniques (3 rd ed.) Chapter
Machine Learning. Support Vector Machines. Fabio Vandin November 20, 2017
 Machine Learning Support Vector Machines Fabio Vandin November 20, 2017 1 Classification and Margin Consider a classification problem with two classes: instance set X = R d label set Y = { 1, 1}. Training
Machine Learning Support Vector Machines Fabio Vandin November 20, 2017 1 Classification and Margin Consider a classification problem with two classes: instance set X = R d label set Y = { 1, 1}. Training
Optimal Separating Hyperplane and the Support Vector Machine. Volker Tresp Summer 2018
 Optimal Separating Hyperplane and the Support Vector Machine Volker Tresp Summer 2018 1 (Vapnik s) Optimal Separating Hyperplane Let s consider a linear classifier with y i { 1, 1} If classes are linearly
Optimal Separating Hyperplane and the Support Vector Machine Volker Tresp Summer 2018 1 (Vapnik s) Optimal Separating Hyperplane Let s consider a linear classifier with y i { 1, 1} If classes are linearly
Structured Learning. Jun Zhu
 Structured Learning Jun Zhu Supervised learning Given a set of I.I.D. training samples Learn a prediction function b r a c e Supervised learning (cont d) Many different choices Logistic Regression Maximum
Structured Learning Jun Zhu Supervised learning Given a set of I.I.D. training samples Learn a prediction function b r a c e Supervised learning (cont d) Many different choices Logistic Regression Maximum
I How does the formulation (5) serve the purpose of the composite parameterization
 Supplemental Material to Identifying Alzheimer s Disease-Related Brain Regions from Multi-Modality Neuroimaging Data using Sparse Composite Linear Discrimination Analysis I How does the formulation (5)
Supplemental Material to Identifying Alzheimer s Disease-Related Brain Regions from Multi-Modality Neuroimaging Data using Sparse Composite Linear Discrimination Analysis I How does the formulation (5)
On-line multiplication in real and complex base
 On-line multiplication in real complex base Christiane Frougny LIAFA, CNRS UMR 7089 2 place Jussieu, 75251 Paris Cedex 05, France Université Paris 8 Christiane.Frougny@liafa.jussieu.fr Athasit Surarerks
On-line multiplication in real complex base Christiane Frougny LIAFA, CNRS UMR 7089 2 place Jussieu, 75251 Paris Cedex 05, France Université Paris 8 Christiane.Frougny@liafa.jussieu.fr Athasit Surarerks
Perceptron Learning Algorithm
 Perceptron Learning Algorithm An iterative learning algorithm that can find linear threshold function to partition linearly separable set of points. Assume zero threshold value. 1) w(0) = arbitrary, j=1,
Perceptron Learning Algorithm An iterative learning algorithm that can find linear threshold function to partition linearly separable set of points. Assume zero threshold value. 1) w(0) = arbitrary, j=1,
Classification by Support Vector Machines
 Classification by Support Vector Machines Florian Markowetz Max-Planck-Institute for Molecular Genetics Computational Molecular Biology Berlin Practical DNA Microarray Analysis 2003 1 Overview I II III
Classification by Support Vector Machines Florian Markowetz Max-Planck-Institute for Molecular Genetics Computational Molecular Biology Berlin Practical DNA Microarray Analysis 2003 1 Overview I II III
Probabilistic analysis of algorithms: What s it good for?
 Probabilistic analysis of algorithms: What s it good for? Conrado Martínez Univ. Politècnica de Catalunya, Spain February 2008 The goal Given some algorithm taking inputs from some set Á, we would like
Probabilistic analysis of algorithms: What s it good for? Conrado Martínez Univ. Politècnica de Catalunya, Spain February 2008 The goal Given some algorithm taking inputs from some set Á, we would like
The Tractability of Global Constraints
 The Tractability of Global Constraints Christian Bessiere ½, Emmanuel Hebrard ¾, Brahim Hnich ¾, and Toby Walsh ¾ ¾ ½ LIRMM-CNRS, Montpelier, France. bessiere@lirmm.fr Cork Constraint Computation Center,
The Tractability of Global Constraints Christian Bessiere ½, Emmanuel Hebrard ¾, Brahim Hnich ¾, and Toby Walsh ¾ ¾ ½ LIRMM-CNRS, Montpelier, France. bessiere@lirmm.fr Cork Constraint Computation Center,
A 2-Approximation Algorithm for the Soft-Capacitated Facility Location Problem
 A 2-Approximation Algorithm for the Soft-Capacitated Facility Location Problem Mohammad Mahdian Yinyu Ye Ý Jiawei Zhang Þ Abstract This paper is divided into two parts. In the first part of this paper,
A 2-Approximation Algorithm for the Soft-Capacitated Facility Location Problem Mohammad Mahdian Yinyu Ye Ý Jiawei Zhang Þ Abstract This paper is divided into two parts. In the first part of this paper,
Part 5: Structured Support Vector Machines
 Part 5: Structured Support Vector Machines Sebastian Nowozin and Christoph H. Lampert Providence, 21st June 2012 1 / 34 Problem (Loss-Minimizing Parameter Learning) Let d(x, y) be the (unknown) true data
Part 5: Structured Support Vector Machines Sebastian Nowozin and Christoph H. Lampert Providence, 21st June 2012 1 / 34 Problem (Loss-Minimizing Parameter Learning) Let d(x, y) be the (unknown) true data
Support Vector Machines.
 Support Vector Machines srihari@buffalo.edu SVM Discussion Overview. Importance of SVMs. Overview of Mathematical Techniques Employed 3. Margin Geometry 4. SVM Training Methodology 5. Overlapping Distributions
Support Vector Machines srihari@buffalo.edu SVM Discussion Overview. Importance of SVMs. Overview of Mathematical Techniques Employed 3. Margin Geometry 4. SVM Training Methodology 5. Overlapping Distributions
Linear Programming Problems
 Linear Programming Problems Two common formulations of linear programming (LP) problems are: min Subject to: 1,,, 1,2,,;, max Subject to: 1,,, 1,2,,;, Linear Programming Problems The standard LP problem
Linear Programming Problems Two common formulations of linear programming (LP) problems are: min Subject to: 1,,, 1,2,,;, max Subject to: 1,,, 1,2,,;, Linear Programming Problems The standard LP problem
Table of Contents. Recognition of Facial Gestures... 1 Attila Fazekas
 Table of Contents Recognition of Facial Gestures...................................... 1 Attila Fazekas II Recognition of Facial Gestures Attila Fazekas University of Debrecen, Institute of Informatics
Table of Contents Recognition of Facial Gestures...................................... 1 Attila Fazekas II Recognition of Facial Gestures Attila Fazekas University of Debrecen, Institute of Informatics
A Fast Algorithm for Optimal Alignment between Similar Ordered Trees
 Fundamenta Informaticae 56 (2003) 105 120 105 IOS Press A Fast Algorithm for Optimal Alignment between Similar Ordered Trees Jesper Jansson Department of Computer Science Lund University, Box 118 SE-221
Fundamenta Informaticae 56 (2003) 105 120 105 IOS Press A Fast Algorithm for Optimal Alignment between Similar Ordered Trees Jesper Jansson Department of Computer Science Lund University, Box 118 SE-221
Key Grids: A Protocol Family for Assigning Symmetric Keys
 Key Grids: A Protocol Family for Assigning Symmetric Keys Amitanand S. Aiyer University of Texas at Austin anand@cs.utexas.edu Lorenzo Alvisi University of Texas at Austin lorenzo@cs.utexas.edu Mohamed
Key Grids: A Protocol Family for Assigning Symmetric Keys Amitanand S. Aiyer University of Texas at Austin anand@cs.utexas.edu Lorenzo Alvisi University of Texas at Austin lorenzo@cs.utexas.edu Mohamed
Learning Monotonic Transformations for Classification
 Learning Monotonic Transformations for Classification Andrew G. Howard Department of Computer Science Columbia University New York, NY 27 ahoward@cs.columbia.edu Tony Jebara Department of Computer Science
Learning Monotonic Transformations for Classification Andrew G. Howard Department of Computer Science Columbia University New York, NY 27 ahoward@cs.columbia.edu Tony Jebara Department of Computer Science
Feature Selection for SVMs
 Feature Selection for SVMs J. Weston, S. Mukherjee, O. Chapelle, M. Pontil T. Poggio, V. Vapnik Barnhill BioInformatics.com, Savannah, Georgia, USA. CBCL MIT, Cambridge, Massachusetts, USA. AT&T Research
Feature Selection for SVMs J. Weston, S. Mukherjee, O. Chapelle, M. Pontil T. Poggio, V. Vapnik Barnhill BioInformatics.com, Savannah, Georgia, USA. CBCL MIT, Cambridge, Massachusetts, USA. AT&T Research
Classification by Support Vector Machines
 Classification by Support Vector Machines Florian Markowetz Max-Planck-Institute for Molecular Genetics Computational Molecular Biology Berlin Practical DNA Microarray Analysis 2003 1 Overview I II III
Classification by Support Vector Machines Florian Markowetz Max-Planck-Institute for Molecular Genetics Computational Molecular Biology Berlin Practical DNA Microarray Analysis 2003 1 Overview I II III
Chapter 15 Introduction to Linear Programming
 Chapter 15 Introduction to Linear Programming An Introduction to Optimization Spring, 2015 Wei-Ta Chu 1 Brief History of Linear Programming The goal of linear programming is to determine the values of
Chapter 15 Introduction to Linear Programming An Introduction to Optimization Spring, 2015 Wei-Ta Chu 1 Brief History of Linear Programming The goal of linear programming is to determine the values of
SVM in Analysis of Cross-Sectional Epidemiological Data Dmitriy Fradkin. April 4, 2005 Dmitriy Fradkin, Rutgers University Page 1
 SVM in Analysis of Cross-Sectional Epidemiological Data Dmitriy Fradkin April 4, 2005 Dmitriy Fradkin, Rutgers University Page 1 Overview The goals of analyzing cross-sectional data Standard methods used
SVM in Analysis of Cross-Sectional Epidemiological Data Dmitriy Fradkin April 4, 2005 Dmitriy Fradkin, Rutgers University Page 1 Overview The goals of analyzing cross-sectional data Standard methods used
Content-based image and video analysis. Machine learning
 Content-based image and video analysis Machine learning for multimedia retrieval 04.05.2009 What is machine learning? Some problems are very hard to solve by writing a computer program by hand Almost all
Content-based image and video analysis Machine learning for multimedia retrieval 04.05.2009 What is machine learning? Some problems are very hard to solve by writing a computer program by hand Almost all
PRIMAL-DUAL INTERIOR POINT METHOD FOR LINEAR PROGRAMMING. 1. Introduction
 PRIMAL-DUAL INTERIOR POINT METHOD FOR LINEAR PROGRAMMING KELLER VANDEBOGERT AND CHARLES LANNING 1. Introduction Interior point methods are, put simply, a technique of optimization where, given a problem
PRIMAL-DUAL INTERIOR POINT METHOD FOR LINEAR PROGRAMMING KELLER VANDEBOGERT AND CHARLES LANNING 1. Introduction Interior point methods are, put simply, a technique of optimization where, given a problem
Training Data Selection for Support Vector Machines
 Training Data Selection for Support Vector Machines Jigang Wang, Predrag Neskovic, and Leon N Cooper Institute for Brain and Neural Systems, Physics Department, Brown University, Providence RI 02912, USA
Training Data Selection for Support Vector Machines Jigang Wang, Predrag Neskovic, and Leon N Cooper Institute for Brain and Neural Systems, Physics Department, Brown University, Providence RI 02912, USA
10. Support Vector Machines
 Foundations of Machine Learning CentraleSupélec Fall 2017 10. Support Vector Machines Chloé-Agathe Azencot Centre for Computational Biology, Mines ParisTech chloe-agathe.azencott@mines-paristech.fr Learning
Foundations of Machine Learning CentraleSupélec Fall 2017 10. Support Vector Machines Chloé-Agathe Azencot Centre for Computational Biology, Mines ParisTech chloe-agathe.azencott@mines-paristech.fr Learning
16.410/413 Principles of Autonomy and Decision Making
 16.410/413 Principles of Autonomy and Decision Making Lecture 17: The Simplex Method Emilio Frazzoli Aeronautics and Astronautics Massachusetts Institute of Technology November 10, 2010 Frazzoli (MIT)
16.410/413 Principles of Autonomy and Decision Making Lecture 17: The Simplex Method Emilio Frazzoli Aeronautics and Astronautics Massachusetts Institute of Technology November 10, 2010 Frazzoli (MIT)
Modeling System Calls for Intrusion Detection with Dynamic Window Sizes
 Modeling System Calls for Intrusion Detection with Dynamic Window Sizes Eleazar Eskin Computer Science Department Columbia University 5 West 2th Street, New York, NY 27 eeskin@cs.columbia.edu Salvatore
Modeling System Calls for Intrusion Detection with Dynamic Window Sizes Eleazar Eskin Computer Science Department Columbia University 5 West 2th Street, New York, NY 27 eeskin@cs.columbia.edu Salvatore
Computing Gaussian Mixture Models with EM using Equivalence Constraints
 Computing Gaussian Mixture Models with EM using Equivalence Constraints Noam Shental, Aharon Bar-Hillel, Tomer Hertz and Daphna Weinshall email: tomboy,fenoam,aharonbh,daphna@cs.huji.ac.il School of Computer
Computing Gaussian Mixture Models with EM using Equivalence Constraints Noam Shental, Aharon Bar-Hillel, Tomer Hertz and Daphna Weinshall email: tomboy,fenoam,aharonbh,daphna@cs.huji.ac.il School of Computer
BIOINF 585: Machine Learning for Systems Biology & Clinical Informatics
 BIOINF 585: Machine Learning for Systems Biology & Clinical Informatics Lecture 12: Ensemble Learning I Jie Wang Department of Computational Medicine & Bioinformatics University of Michigan 1 Outline Bias
BIOINF 585: Machine Learning for Systems Biology & Clinical Informatics Lecture 12: Ensemble Learning I Jie Wang Department of Computational Medicine & Bioinformatics University of Michigan 1 Outline Bias
Optimization Methods for Machine Learning (OMML)
 Optimization Methods for Machine Learning (OMML) 2nd lecture Prof. L. Palagi References: 1. Bishop Pattern Recognition and Machine Learning, Springer, 2006 (Chap 1) 2. V. Cherlassky, F. Mulier - Learning
Optimization Methods for Machine Learning (OMML) 2nd lecture Prof. L. Palagi References: 1. Bishop Pattern Recognition and Machine Learning, Springer, 2006 (Chap 1) 2. V. Cherlassky, F. Mulier - Learning
A Comparative Study of SVM Kernel Functions Based on Polynomial Coefficients and V-Transform Coefficients
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 6 Issue 3 March 2017, Page No. 20765-20769 Index Copernicus value (2015): 58.10 DOI: 18535/ijecs/v6i3.65 A Comparative
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 6 Issue 3 March 2017, Page No. 20765-20769 Index Copernicus value (2015): 58.10 DOI: 18535/ijecs/v6i3.65 A Comparative
