Incremental Mining of Partial Periodic Patterns in Time-series Databases
|
|
|
- Julie Page
- 5 years ago
- Views:
Transcription
1 CERIAS Teh Report Inremental Mining of Partial Periodi Patterns in Time-series Dataases Mohamed G. Elfeky Center for Eduation and Researh in Information Assurane and Seurity Purdue University, West Lafayette, IN 47907
2 Inremental Mining of Partial Periodi Patterns in Time-Series Dataases Mohamed G. Elfeky Feruary 3, Introdution A Time-Series Dataase is a dataase that ontains data for eah point in time; e.g., weather data that ontains several measures (e.g., the temperature) at different times per day. Some other examples are the stok pries and the power onsumption. Mining timeseries dataases involves two general kinds of periodi patterns: full periodi patterns and partial periodi patterns. In full periodi patterns, every point in time ontriutes to the yli ehavior of the time series for eah period [1]. For example, desriing the weekly stok pries pattern onsidering all the days of the week. The other kind is partial periodi patterns, whih speify the ehavior of the time series at some ut not all the points in time [1]. For example, disovering that a speifi stok pries are high every Saturday and low every Tuesday ut do not have suh regularity on other days. An effiient algorithm for mining partial periodi patterns is introdued in [1]. One of the important prolems of the data mining prolem is how to maintain the disovered rules or patterns over the time in the sense that the data is updated regularly. Espeially in time-series dataases, new data is added ontinuously over the time. Inremental mining onerns this prolem. It is how to mine a previously mined dataase after the addition of some data without running the mining algorithm again on the new dataase. A new algorithm is proposed for inrementally mine partial periodi patterns in time-series dataases ased on the algorithm disussed in [1]. Another prolem that is arisen here is that what if there are two time-series dataases and now it is wanted to omine them into one, how to disover the partial periodi patterns of the omined dataase, given that the two dataases were previously mined, without running the mining algorithm again on the omined dataase. The proposed algorithm is extended to solve this prolem. The rest of this report is organized as follows. In Setion 2, the algorithm of mining partial periodi patterns disussed in [1] is riefly introdued. Setion 3 disusses in detail the proposed algorithm for inremental mining of partial periodi patterns. In setion 4, some statistial analysis of the proposed algorithm is shown. Finally, Setion 5 presents a proposed solution to the latter prolem disussed aove. 2 Mining Partial Periodi Patterns 2.1 Prolem Definition Assume that a sequene of n time-stamped datasets have een olleted in a dataase. For eah time instant i, let D i e a feature derived from the dataset. Thus, the time series 1
3 of features is represented as, S = D 1, D 2,..., D n. A pattern is: s = s 1... s p over the set of features L and the letter *, suh that p is the period of the pattern. L-length of a pattern s is the numer of s i that is not *. A pattern with L-length j is also alled a j-pattern. A supattern of a pattern s is a pattern s =s 1... s p suh that for eah position i: s i = s i or s i = *. For example, if the period is 5, the pattern: a * de is alled 4-pattern. Two of his supatterns are: a * * e and ** d *. Eah segment of the form D ip+1... D ip+p is alled a period segment. A period segment mathes a pattern s if it is a supattern of s. The frequeny ount of a pattern in a time series is the numer of period segments of this time series that mathes that pattern. The onfidene of a pattern is defined as the division of its frequeny ount y the maximum numer of period segments in the time series. A pattern is alled frequent if its onfidene not less than a minimum threshold. For example, in the series aaeaed, the pattern: a *, whose period is 3, has frequeny ount 2, and onfidene 2/3 where 3 is the maximum numer of period segments of length Max-Supattern Hit Set Method A max-pattern C max is the maximal pattern that an e generated from F 1 (the set of frequent 1-patterns). For example, if F 1 = {a ****, * ***, ** **, **** d}, then C max = a * d. A supattern of C max is hit in a period segment S i if it is the maximal supattern of C max in S i. For example, if C max = a * d and S i = add, then its hit supattern is: a ** d. Algorithm: 1. San the dataase to find F 1, the frequent patterns of length 1, and form the andidate max-pattern C max. 2. San the dataase one again, and for eah period segment, onsider its max supattern and update the max-supattern tree (either add the pattern setting its ount to 1 if it is not exist, or otherwise inrease its ount y 1). 3. Traverse the tree to determine the atual ount of eah pattern, and determine the frequent ones. ad * 10 a d * d * 2 a * d * 50 a * d * 40 a ** 32 d a d a ** d * 18 * * d * 8 a ** d * 5 a * ** 19 a *** 2 Figure 1. An example to a max-supattern tree 2
4 Figure 1 shows an example of a max-supattern tree used to store the set of maxsupatterns hit in the time series. It shows that the root node is the C max. A hild node is a supattern of the parent node with one non * -letter missing. The link is laeled y this letter. The 1-patterns are not stored in the tree sine they already exist in F 1 tale. Eah node has a ount field that registers its numer of hits. A dotted link is a non-existing (virtual) link that represents a andidate parent of the hild node. The frequeny ount of eah pattern represented y a node is the sum of its ount and those of all its reahale parents (physial or virtual link). For example, the frequeny ount of ** d * is 80, and the frequeny ount of a ** d * is Inremental Mining of Partial Periodi Patterns 3.1 Prolem Definition The prolem of inremental mining takes as an input a previously mined dataase after some additions of new data, and suffiient information aout the previously mined patterns olleted efore from running the mining algorithm over the old dataase. Here, it is suffiient to store the max-supattern tree and all the 1-patterns along with their respetive ounts. 3.2 Algorithm 1. San the new data for the 1-patterns and add them to the whole list of 1-patterns, and determine the new max-pattern C max. 2. If C max is not hanged, there will e no hange on the tree. 3. If C max is hanged, there are two ases: deleted letters and inserted letters (either or oth). a. For the deleted letters, delete from the new C max the inserted letters, and onsider the resulted pattern, that is surely a supattern of the old C max, as the root of the new tree. Insert into the new tree the hit of eah pattern in the old tree with the same ount. Now, the old C max is the new C max.. For the inserted letters, the old C max is surely a supattern of the new one. Hene, onsider the new C max as the root of the tree making the old root a hild. San the old dataase, and for eah period segment ontaining at least one of the inserted letters, insert its hit in the tree, and derement the node that ontains the hit without the inserted letters. 4. San the new data and update the max-supattern tree as step 2 of the original mining algorithm. 5. Traverse the tree to determine the atual ount of eah pattern, and determine the frequent ones. The following example, followed from Figure 1, illustrates the idea ehind this algorithm. Assume that the new C max is a * e, whih means one deleted letter d and one inserted letter e. Following step 3a of the algorithm, the root of the new tree is: a **, resulting in Figure 2. Notie that: (i) the frequeny ount of eah pattern is the same as in the old tree, and this why the hits of the patterns of the old tree are inserted in the new one, (ii) the virtual links eome physial, (iii) a new node appears * ** resulted from inserting the hit of the node * d *. 3
5 a ** 42 a * ** 2 a * ** a *** Figure 2. The max-supattern tree of Figure 1. after deleting the letter d. Now, following step 3 of the algorithm, the root is a * e, resulting in Figure 3. Notie that: (i) there are new nodes other than the root, like a ** e, and this is why the old dataase must e resanned to disover the hits given the new max pattern, (ii) the frequeny ount of eah pattern is the same as in the old tree, and this why some nodes must e deremented. e a * e 4 a ** 38 a ** e 22 a e * ** 2 a * ** a *** a *** e 12 Figure 3. The max-supattern tree of Figure 2. after inserting the letter e. 4 Analysis Clearly, inremental mining will speed up the proess of mining a previously mined dataase after the addition of some new data, ut it relies on how muh often the algorithm is applied; i.e., with eah new segment of data or after a signifiant numer of additions. The following statistis may e inomplete ut give an idea aout the speed up of the proposed algorithm over applying the original mining algorithm on the new dataase again. Also, the proposed algorithm implies some overhead of the original mining algorithm in the sense that the reated tree must e stored on the physial storage, whih requires additional time and spae. 4
6 It an e inferred easily from the algorithm that it has a worst ase of one san over the old dataase if there are inserted letters in C max (Step 3). This san an e eliminated if a list of the segments that ontain any 1-pattern is stored along with this 1-pattern. This list is alled inverted list. Now, step 3 is modified suh that the period segments that must e reinserted in the tree are now loated in the inverted list without a need to resan the old dataase searhing for those period segments. 5 Merging Mined Dataases 5.1 Prolem Definition The prolem of merging two previously mined dataases and disover the partial periodi patterns from the new one an e onsidered a generalization to the prolem of inremental mining. Now the input is two trees and two 1-pattern lists, one for eah dataase. The worst ase in the proposed algorithm is to san eah dataase one, if the last modifiation is not onsidered, instead of sanning the new dataase twie if the original mining algorithm is onsidered. 5.2 Algorithm 1. Determine the C max that will e the root of the new tree. This an e done y either way of the following: a. Merge the two 1-pattern lists and determine the new C max as Step 1 of the original algorithm.. Interset the two C max s of the two trees, and for eah position that will have a *, selet either the letter of the first C max or the seond one ased on how frequent is this letter in the merged list. 2. Apply Steps 2 and 3 of the proposed algorithm for eah tree onsidering the new C max determined in the previous step. 3. Now, the two trees have the same root and then an e omined into one y seleting the one that has smaller numer of nodes and insert it into the other. 4. Traverse the tree to determine the atual ount of eah pattern, and determine the frequent ones. Referenes [1] Jiawei Han, Guozhu Dong, and Yiwen Yin. Effiient Mining of Partial Periodi Patterns in Time Series Dataases. In Proeedings of 1999 Int. Conf. on Data Engineering (ICDE 99), Sydney, Australia, Marh [2] Shiy Thomas, Sreenath Bodagala, Khaled Alsati, and Sanjay Ranka. An Effiient Algorithm for the Inremental Updation of Assoiation Rules in Large Dataases. In Proeedings of the 3 rd Int. Conf. on Knowledge Disovery and Data Mining, New Port Beah, California, August
7 Implementation Both the original mining algorithm and the proposed inremental one are implemented using Java programming language. To use the original mining algorithm: use java Mine arg1 arg2 arg3, suh that arg1 is the numer of the data file, arg2 is the period, and arg3 is the onfidene threshold. For examples, java Mine means to mine the first data file with period 7 (7 days per week), and the onfidene threshold is 0.6. For eah data file there are two versions, one with the original data, and the other after the addition of new data. Now, to use the inremental algorithm: use java InMine arg1, suh that arg1 is the numer of the data file. For example, java InMine 1 means to apply the inremental mining algorithm over the new data file. To ensure that the results of the inremental mining algorithm are orret, it is needed to apply the original mining algorithm over the new data file and this an e done using: java Mine 1i 7 60, suh that 1i is the numer of the new data file. 6
Path Sharing and Predicate Evaluation for High-Performance XML Filtering*
 Path Sharing and Prediate Evaluation for High-Performane XML Filtering Yanlei Diao, Mihael J. Franklin, Hao Zhang, Peter Fisher EECS, University of California, Berkeley {diaoyl, franklin, nhz, fisherp}@s.erkeley.edu
Path Sharing and Prediate Evaluation for High-Performane XML Filtering Yanlei Diao, Mihael J. Franklin, Hao Zhang, Peter Fisher EECS, University of California, Berkeley {diaoyl, franklin, nhz, fisherp}@s.erkeley.edu
Mining Edge-Weighted Call Graphs to Localise Software Bugs
 Mining Edge-Weighted Call Graphs to Loalise Software Bugs Frank Eihinger, Klemens Böhm, and Matthias Huer Institute for Program Strutures and Data Organisation (IPD), Universität Karlsruhe (TH), Germany
Mining Edge-Weighted Call Graphs to Loalise Software Bugs Frank Eihinger, Klemens Böhm, and Matthias Huer Institute for Program Strutures and Data Organisation (IPD), Universität Karlsruhe (TH), Germany
On - Line Path Delay Fault Testing of Omega MINs M. Bellos 1, E. Kalligeros 1, D. Nikolos 1,2 & H. T. Vergos 1,2
 On - Line Path Delay Fault Testing of Omega MINs M. Bellos, E. Kalligeros, D. Nikolos,2 & H. T. Vergos,2 Dept. of Computer Engineering and Informatis 2 Computer Tehnology Institute University of Patras,
On - Line Path Delay Fault Testing of Omega MINs M. Bellos, E. Kalligeros, D. Nikolos,2 & H. T. Vergos,2 Dept. of Computer Engineering and Informatis 2 Computer Tehnology Institute University of Patras,
Efficient and scalable trie-based algorithms for computing set containment relations
 Effiient and salale trie-ased algorithms for omputing set ontainment relations Yongming Luo #1, George H. L. Flether #2, Jan Hidders 3, Paul De Bra #4 # Eindhoven University of Tehnology, The Netherlands
Effiient and salale trie-ased algorithms for omputing set ontainment relations Yongming Luo #1, George H. L. Flether #2, Jan Hidders 3, Paul De Bra #4 # Eindhoven University of Tehnology, The Netherlands
Automatic Physical Design Tuning: Workload as a Sequence Sanjay Agrawal Microsoft Research One Microsoft Way Redmond, WA, USA +1-(425)
 Automati Physial Design Tuning: Workload as a Sequene Sanjay Agrawal Mirosoft Researh One Mirosoft Way Redmond, WA, USA +1-(425) 75-357 sagrawal@mirosoft.om Eri Chu * Computer Sienes Department University
Automati Physial Design Tuning: Workload as a Sequene Sanjay Agrawal Mirosoft Researh One Mirosoft Way Redmond, WA, USA +1-(425) 75-357 sagrawal@mirosoft.om Eri Chu * Computer Sienes Department University
A Load-Balanced Clustering Protocol for Hierarchical Wireless Sensor Networks
 International Journal of Advanes in Computer Networks and Its Seurity IJCNS A Load-Balaned Clustering Protool for Hierarhial Wireless Sensor Networks Mehdi Tarhani, Yousef S. Kavian, Saman Siavoshi, Ali
International Journal of Advanes in Computer Networks and Its Seurity IJCNS A Load-Balaned Clustering Protool for Hierarhial Wireless Sensor Networks Mehdi Tarhani, Yousef S. Kavian, Saman Siavoshi, Ali
1. The collection of the vowels in the word probability. 2. The collection of real numbers that satisfy the equation x 9 = 0.
 C HPTER 1 SETS I. DEFINITION OF SET We begin our study of probability with the disussion of the basi onept of set. We assume that there is a ommon understanding of what is meant by the notion of a olletion
C HPTER 1 SETS I. DEFINITION OF SET We begin our study of probability with the disussion of the basi onept of set. We assume that there is a ommon understanding of what is meant by the notion of a olletion
Algorithms for External Memory Lecture 6 Graph Algorithms - Weighted List Ranking
 Algorithms for External Memory Leture 6 Graph Algorithms - Weighted List Ranking Leturer: Nodari Sithinava Sribe: Andi Hellmund, Simon Ohsenreither 1 Introdution & Motivation After talking about I/O-effiient
Algorithms for External Memory Leture 6 Graph Algorithms - Weighted List Ranking Leturer: Nodari Sithinava Sribe: Andi Hellmund, Simon Ohsenreither 1 Introdution & Motivation After talking about I/O-effiient
A Support-Based Algorithm for the Bi-Objective Pareto Constraint
 A Support-Based Algorithm for the Bi-Ojetive Pareto Constraint Renaud Hartert and Pierre Shaus UCLouvain, ICTEAM, Plae Sainte Bare 2, 1348 Louvain-la-Neuve, Belgium {renaud.hartert, pierre.shaus,}@ulouvain.e
A Support-Based Algorithm for the Bi-Ojetive Pareto Constraint Renaud Hartert and Pierre Shaus UCLouvain, ICTEAM, Plae Sainte Bare 2, 1348 Louvain-la-Neuve, Belgium {renaud.hartert, pierre.shaus,}@ulouvain.e
A Support-Based Algorithm for the Bi-Objective Pareto Constraint
 Proeedings of the Twenty-Eighth AAAI Conferene on Artifiial Intelligene A Support-Based Algorithm for the Bi-Ojetive Pareto Constraint Renaud Hartert and Pierre Shaus UCLouvain, ICTEAM, Plae Sainte Bare
Proeedings of the Twenty-Eighth AAAI Conferene on Artifiial Intelligene A Support-Based Algorithm for the Bi-Ojetive Pareto Constraint Renaud Hartert and Pierre Shaus UCLouvain, ICTEAM, Plae Sainte Bare
Learning Convention Propagation in BeerAdvocate Reviews from a etwork Perspective. Abstract
 CS 9 Projet Final Report: Learning Convention Propagation in BeerAdvoate Reviews from a etwork Perspetive Abstrat We look at the way onventions propagate between reviews on the BeerAdvoate dataset, and
CS 9 Projet Final Report: Learning Convention Propagation in BeerAdvoate Reviews from a etwork Perspetive Abstrat We look at the way onventions propagate between reviews on the BeerAdvoate dataset, and
Query Evaluation Overview. Query Optimization: Chap. 15. Evaluation Example. Cost Estimation. Query Blocks. Query Blocks
 Query Evaluation Overview Query Optimization: Chap. 15 CS634 Leture 12 SQL query first translated to relational algebra (RA) Atually, some additional operators needed for SQL Tree of RA operators, with
Query Evaluation Overview Query Optimization: Chap. 15 CS634 Leture 12 SQL query first translated to relational algebra (RA) Atually, some additional operators needed for SQL Tree of RA operators, with
Outline. CS38 Introduction to Algorithms. Administrative Stuff. Administrative Stuff. Motivation/Overview. Administrative Stuff
 Outline CS38 Introdution to Algorithms Leture 1 April 1, 2014 administrative stuff motivation and overview of the ourse stale mathings example graphs, representing graphs graph traversals (BFS, DFS) onnetivity,
Outline CS38 Introdution to Algorithms Leture 1 April 1, 2014 administrative stuff motivation and overview of the ourse stale mathings example graphs, representing graphs graph traversals (BFS, DFS) onnetivity,
A Novel Validity Index for Determination of the Optimal Number of Clusters
 IEICE TRANS. INF. & SYST., VOL.E84 D, NO.2 FEBRUARY 2001 281 LETTER A Novel Validity Index for Determination of the Optimal Number of Clusters Do-Jong KIM, Yong-Woon PARK, and Dong-Jo PARK, Nonmembers
IEICE TRANS. INF. & SYST., VOL.E84 D, NO.2 FEBRUARY 2001 281 LETTER A Novel Validity Index for Determination of the Optimal Number of Clusters Do-Jong KIM, Yong-Woon PARK, and Dong-Jo PARK, Nonmembers
HEXA: Compact Data Structures for Faster Packet Processing
 Washington University in St. Louis Washington University Open Sholarship All Computer Siene and Engineering Researh Computer Siene and Engineering Report Number: 27-26 27 HEXA: Compat Data Strutures for
Washington University in St. Louis Washington University Open Sholarship All Computer Siene and Engineering Researh Computer Siene and Engineering Report Number: 27-26 27 HEXA: Compat Data Strutures for
A Compressed Breadth-First Search for Satisfiability
 A Compressed Breadth-First Searh for Satisfiaility DoRon B. Motter and Igor L. Markov Department of EECS, University of Mihigan, 1301 Beal Ave, Ann Aror, MI 48109-2122 dmotter, imarkov @ees.umih.edu Astrat.
A Compressed Breadth-First Searh for Satisfiaility DoRon B. Motter and Igor L. Markov Department of EECS, University of Mihigan, 1301 Beal Ave, Ann Aror, MI 48109-2122 dmotter, imarkov @ees.umih.edu Astrat.
Drawing lines. Naïve line drawing algorithm. drawpixel(x, round(y)); double dy = y1 - y0; double dx = x1 - x0; double m = dy / dx; double y = y0;
 Naïve line drawing algorithm // Connet to grid points(x0,y0) and // (x1,y1) by a line. void drawline(int x0, int y0, int x1, int y1) { int x; double dy = y1 - y0; double dx = x1 - x0; double m = dy / dx;
Naïve line drawing algorithm // Connet to grid points(x0,y0) and // (x1,y1) by a line. void drawline(int x0, int y0, int x1, int y1) { int x; double dy = y1 - y0; double dx = x1 - x0; double m = dy / dx;
Exploiting Enriched Contextual Information for Mobile App Classification
 Exploiting Enrihed Contextual Information for Mobile App Classifiation Hengshu Zhu 1 Huanhuan Cao 2 Enhong Chen 1 Hui Xiong 3 Jilei Tian 2 1 University of Siene and Tehnology of China 2 Nokia Researh Center
Exploiting Enrihed Contextual Information for Mobile App Classifiation Hengshu Zhu 1 Huanhuan Cao 2 Enhong Chen 1 Hui Xiong 3 Jilei Tian 2 1 University of Siene and Tehnology of China 2 Nokia Researh Center
Calculation of typical running time of a branch-and-bound algorithm for the vertex-cover problem
 Calulation of typial running time of a branh-and-bound algorithm for the vertex-over problem Joni Pajarinen, Joni.Pajarinen@iki.fi Otober 21, 2007 1 Introdution The vertex-over problem is one of a olletion
Calulation of typial running time of a branh-and-bound algorithm for the vertex-over problem Joni Pajarinen, Joni.Pajarinen@iki.fi Otober 21, 2007 1 Introdution The vertex-over problem is one of a olletion
Automated Test Generation from Vulnerability Signatures
 Automated Test Generation from Vulneraility Signatures Adulaki Aydin, Muath Alkhalaf, and Tevfik Bultan Computer Siene Department University of California, Santa Barara Email: {aki,muath,ultan}@s.us.edu
Automated Test Generation from Vulneraility Signatures Adulaki Aydin, Muath Alkhalaf, and Tevfik Bultan Computer Siene Department University of California, Santa Barara Email: {aki,muath,ultan}@s.us.edu
Circular Pruning for Lazy Diagnosis of Active Systems
 Cirular Pruning for Lazy Diagnosis of Ative Systems Andrea Duoli, Gianfrano Lamperti, Emanuele Piantoni, Marina Zanella Dipartimento di Elettronia per l Automazione, Università di Bresia, Italy Astrat:
Cirular Pruning for Lazy Diagnosis of Ative Systems Andrea Duoli, Gianfrano Lamperti, Emanuele Piantoni, Marina Zanella Dipartimento di Elettronia per l Automazione, Università di Bresia, Italy Astrat:
A DYNAMIC ACCESS CONTROL WITH BINARY KEY-PAIR
 Malaysian Journal of Computer Siene, Vol 10 No 1, June 1997, pp 36-41 A DYNAMIC ACCESS CONTROL WITH BINARY KEY-PAIR Md Rafiqul Islam, Harihodin Selamat and Mohd Noor Md Sap Faulty of Computer Siene and
Malaysian Journal of Computer Siene, Vol 10 No 1, June 1997, pp 36-41 A DYNAMIC ACCESS CONTROL WITH BINARY KEY-PAIR Md Rafiqul Islam, Harihodin Selamat and Mohd Noor Md Sap Faulty of Computer Siene and
Gray Codes for Reflectable Languages
 Gray Codes for Refletable Languages Yue Li Joe Sawada Marh 8, 2008 Abstrat We lassify a type of language alled a refletable language. We then develop a generi algorithm that an be used to list all strings
Gray Codes for Refletable Languages Yue Li Joe Sawada Marh 8, 2008 Abstrat We lassify a type of language alled a refletable language. We then develop a generi algorithm that an be used to list all strings
INTEGRATING PHOTOGRAMMETRY AND INERTIAL SENSORS FOR ROBOTICS NAVIGATION AND MAPPING
 INTEGRATING PHOTOGRAMMETRY AND INERTIAL SENSORS FOR ROBOTICS NAVIGATION AND MAPPING Fadi Bayoud, Jan Skaloud, Bertrand Merminod Eole Polytehnique Fédérale de Lausanne (EPFL) Geodeti Engineering Laoratory
INTEGRATING PHOTOGRAMMETRY AND INERTIAL SENSORS FOR ROBOTICS NAVIGATION AND MAPPING Fadi Bayoud, Jan Skaloud, Bertrand Merminod Eole Polytehnique Fédérale de Lausanne (EPFL) Geodeti Engineering Laoratory
The Minimum Redundancy Maximum Relevance Approach to Building Sparse Support Vector Machines
 The Minimum Redundany Maximum Relevane Approah to Building Sparse Support Vetor Mahines Xiaoxing Yang, Ke Tang, and Xin Yao, Nature Inspired Computation and Appliations Laboratory (NICAL), Shool of Computer
The Minimum Redundany Maximum Relevane Approah to Building Sparse Support Vetor Mahines Xiaoxing Yang, Ke Tang, and Xin Yao, Nature Inspired Computation and Appliations Laboratory (NICAL), Shool of Computer
Parallelizing Frequent Web Access Pattern Mining with Partial Enumeration for High Speedup
 Parallelizing Frequent Web Aess Pattern Mining with Partial Enumeration for High Peiyi Tang Markus P. Turkia Department of Computer Siene Department of Computer Siene University of Arkansas at Little Rok
Parallelizing Frequent Web Aess Pattern Mining with Partial Enumeration for High Peiyi Tang Markus P. Turkia Department of Computer Siene Department of Computer Siene University of Arkansas at Little Rok
1 The Knuth-Morris-Pratt Algorithm
 5-45/65: Design & Analysis of Algorithms September 26, 26 Leture #9: String Mathing last hanged: September 26, 27 There s an entire field dediated to solving problems on strings. The book Algorithms on
5-45/65: Design & Analysis of Algorithms September 26, 26 Leture #9: String Mathing last hanged: September 26, 27 There s an entire field dediated to solving problems on strings. The book Algorithms on
Extracting Partition Statistics from Semistructured Data
 Extrating Partition Statistis from Semistrutured Data John N. Wilson Rihard Gourlay Robert Japp Mathias Neumüller Department of Computer and Information Sienes University of Strathlyde, Glasgow, UK {jnw,rsg,rpj,mathias}@is.strath.a.uk
Extrating Partition Statistis from Semistrutured Data John N. Wilson Rihard Gourlay Robert Japp Mathias Neumüller Department of Computer and Information Sienes University of Strathlyde, Glasgow, UK {jnw,rsg,rpj,mathias}@is.strath.a.uk
Contents Contents...I List of Tables...VIII List of Figures...IX 1. Introduction Information Retrieval... 8
 Contents Contents...I List of Tables...VIII List of Figures...IX 1. Introdution... 1 1.1. Internet Information...2 1.2. Internet Information Retrieval...3 1.2.1. Doument Indexing...4 1.2.2. Doument Retrieval...4
Contents Contents...I List of Tables...VIII List of Figures...IX 1. Introdution... 1 1.1. Internet Information...2 1.2. Internet Information Retrieval...3 1.2.1. Doument Indexing...4 1.2.2. Doument Retrieval...4
Chapter 2: Introduction to Maple V
 Chapter 2: Introdution to Maple V 2-1 Working with Maple Worksheets Try It! (p. 15) Start a Maple session with an empty worksheet. The name of the worksheet should be Untitled (1). Use one of the standard
Chapter 2: Introdution to Maple V 2-1 Working with Maple Worksheets Try It! (p. 15) Start a Maple session with an empty worksheet. The name of the worksheet should be Untitled (1). Use one of the standard
Runtime Support for OOLs Part II Comp 412
 COMP 412 FALL 2017 Runtime Support for OOLs Part II Comp 412 soure IR Front End Optimizer Bak End IR target Copright 2017, Keith D. Cooper & Linda Torzon, all rights reserved. Students enrolled in Comp
COMP 412 FALL 2017 Runtime Support for OOLs Part II Comp 412 soure IR Front End Optimizer Bak End IR target Copright 2017, Keith D. Cooper & Linda Torzon, all rights reserved. Students enrolled in Comp
Cluster-Based Cumulative Ensembles
 Cluster-Based Cumulative Ensembles Hanan G. Ayad and Mohamed S. Kamel Pattern Analysis and Mahine Intelligene Lab, Eletrial and Computer Engineering, University of Waterloo, Waterloo, Ontario N2L 3G1,
Cluster-Based Cumulative Ensembles Hanan G. Ayad and Mohamed S. Kamel Pattern Analysis and Mahine Intelligene Lab, Eletrial and Computer Engineering, University of Waterloo, Waterloo, Ontario N2L 3G1,
The Happy Ending Problem
 The Happy Ending Problem Neeldhara Misra STATUTORY WARNING This doument is a draft version 1 Introdution The Happy Ending problem first manifested itself on a typial wintery evening in 1933 These evenings
The Happy Ending Problem Neeldhara Misra STATUTORY WARNING This doument is a draft version 1 Introdution The Happy Ending problem first manifested itself on a typial wintery evening in 1933 These evenings
Abstract. Key Words: Image Filters, Fuzzy Filters, Order Statistics Filters, Rank Ordered Mean Filters, Channel Noise. 1.
 Fuzzy Weighted Rank Ordered Mean (FWROM) Filters for Mixed Noise Suppression from Images S. Meher, G. Panda, B. Majhi 3, M.R. Meher 4,,4 Department of Eletronis and I.E., National Institute of Tehnology,
Fuzzy Weighted Rank Ordered Mean (FWROM) Filters for Mixed Noise Suppression from Images S. Meher, G. Panda, B. Majhi 3, M.R. Meher 4,,4 Department of Eletronis and I.E., National Institute of Tehnology,
A Novel Bit Level Time Series Representation with Implication of Similarity Search and Clustering
 A Novel Bit Level Time Series Representation with Impliation of Similarity Searh and lustering hotirat Ratanamahatana, Eamonn Keogh, Anthony J. Bagnall 2, and Stefano Lonardi Dept. of omputer Siene & Engineering,
A Novel Bit Level Time Series Representation with Impliation of Similarity Searh and lustering hotirat Ratanamahatana, Eamonn Keogh, Anthony J. Bagnall 2, and Stefano Lonardi Dept. of omputer Siene & Engineering,
International Journal of Advancements in Research & Technology, Volume 3, Issue 3, March-2014 ISSN
 International Journal of Advanements in Researh & Tehnology, Volume 3, Issue 3, Marh-204 ISSN 2278-773 47 Phrase Based Doument Retrieving y Comining Suffix Tree index data struture and Boyer- Moore faster
International Journal of Advanements in Researh & Tehnology, Volume 3, Issue 3, Marh-204 ISSN 2278-773 47 Phrase Based Doument Retrieving y Comining Suffix Tree index data struture and Boyer- Moore faster
Partial Character Decoding for Improved Regular Expression Matching in FPGAs
 Partial Charater Deoding for Improved Regular Expression Mathing in FPGAs Peter Sutton Shool of Information Tehnology and Eletrial Engineering The University of Queensland Brisbane, Queensland, 4072, Australia
Partial Charater Deoding for Improved Regular Expression Mathing in FPGAs Peter Sutton Shool of Information Tehnology and Eletrial Engineering The University of Queensland Brisbane, Queensland, 4072, Australia
Capturing Large Intra-class Variations of Biometric Data by Template Co-updating
 Capturing Large Intra-lass Variations of Biometri Data by Template Co-updating Ajita Rattani University of Cagliari Piazza d'armi, Cagliari, Italy ajita.rattani@diee.unia.it Gian Lua Marialis University
Capturing Large Intra-lass Variations of Biometri Data by Template Co-updating Ajita Rattani University of Cagliari Piazza d'armi, Cagliari, Italy ajita.rattani@diee.unia.it Gian Lua Marialis University
Test Case Generation from UML State Machines
 Test Case Generation from UML State Mahines Dirk Seifert Loria Université Nany 2 Campus Sientifique, BP 239 F-54506 Vandoeuvre lès Nany edex Dirk.Seifert@Loria.fr inria-00268864, version 2-23 Apr 2008
Test Case Generation from UML State Mahines Dirk Seifert Loria Université Nany 2 Campus Sientifique, BP 239 F-54506 Vandoeuvre lès Nany edex Dirk.Seifert@Loria.fr inria-00268864, version 2-23 Apr 2008
1 Disjoint-set data structure.
 CS 124 Setion #4 Union-Fin, Greey Algorithms 2/20/17 1 Disjoint-set ata struture. 1.1 Operations Disjoint-set ata struture enale us to effiiently perform operations suh as plaing elements into sets, querying
CS 124 Setion #4 Union-Fin, Greey Algorithms 2/20/17 1 Disjoint-set ata struture. 1.1 Operations Disjoint-set ata struture enale us to effiiently perform operations suh as plaing elements into sets, querying
CA Test Data Manager 4.x Implementation Proven Professional Exam (CAT-681) Study Guide Version 1.0
 Implementation Proven Professional Study Guide Version 1.0 PROPRIETARY AND CONFIDENTIAL INFORMATION 2017 CA. All rights reserved. CA onfidential & proprietary information. For CA, CA Partner and CA Customer
Implementation Proven Professional Study Guide Version 1.0 PROPRIETARY AND CONFIDENTIAL INFORMATION 2017 CA. All rights reserved. CA onfidential & proprietary information. For CA, CA Partner and CA Customer
An Interactive-Voting Based Map Matching Algorithm
 Eleventh International Conferene on Mobile Data Management An Interative-Voting Based Map Mathing Algorithm Jing Yuan* University of Siene and Tehnology of China Hefei, China yuanjing@mail.ust.edu.n Yu
Eleventh International Conferene on Mobile Data Management An Interative-Voting Based Map Mathing Algorithm Jing Yuan* University of Siene and Tehnology of China Hefei, China yuanjing@mail.ust.edu.n Yu
Machine Vision. Laboratory Exercise Name: Student ID: S
 Mahine Vision 521466S Laoratory Eerise 2011 Name: Student D: General nformation To pass these laoratory works, you should answer all questions (Q.y) with an understandale handwriting either in English
Mahine Vision 521466S Laoratory Eerise 2011 Name: Student D: General nformation To pass these laoratory works, you should answer all questions (Q.y) with an understandale handwriting either in English
NONLINEAR BACK PROJECTION FOR TOMOGRAPHIC IMAGE RECONSTRUCTION. Ken Sauer and Charles A. Bouman
 NONLINEAR BACK PROJECTION FOR TOMOGRAPHIC IMAGE RECONSTRUCTION Ken Sauer and Charles A. Bouman Department of Eletrial Engineering, University of Notre Dame Notre Dame, IN 46556, (219) 631-6999 Shool of
NONLINEAR BACK PROJECTION FOR TOMOGRAPHIC IMAGE RECONSTRUCTION Ken Sauer and Charles A. Bouman Department of Eletrial Engineering, University of Notre Dame Notre Dame, IN 46556, (219) 631-6999 Shool of
Gradient based progressive probabilistic Hough transform
 Gradient based progressive probabilisti Hough transform C.Galambos, J.Kittler and J.Matas Abstrat: The authors look at the benefits of exploiting gradient information to enhane the progressive probabilisti
Gradient based progressive probabilisti Hough transform C.Galambos, J.Kittler and J.Matas Abstrat: The authors look at the benefits of exploiting gradient information to enhane the progressive probabilisti
Smooth Trajectory Planning Along Bezier Curve for Mobile Robots with Velocity Constraints
 Smooth Trajetory Planning Along Bezier Curve for Mobile Robots with Veloity Constraints Gil Jin Yang and Byoung Wook Choi Department of Eletrial and Information Engineering Seoul National University of
Smooth Trajetory Planning Along Bezier Curve for Mobile Robots with Veloity Constraints Gil Jin Yang and Byoung Wook Choi Department of Eletrial and Information Engineering Seoul National University of
Multi-Level Modeling of Concurrent and Distributed Systems
 Multi-Level Modeling of Conurrent and Distriuted Systems Peter Taeling Hasso-Plattner-Institute for Software Systems Engineering P.O. Box 90 04 60, 14440 Potsdam, Germany taeling@hpi.uni-potsdam.de strat
Multi-Level Modeling of Conurrent and Distriuted Systems Peter Taeling Hasso-Plattner-Institute for Software Systems Engineering P.O. Box 90 04 60, 14440 Potsdam, Germany taeling@hpi.uni-potsdam.de strat
An Efficient and Scalable Approach to CNN Queries in a Road Network
 An Effiient and Salable Approah to CNN Queries in a Road Network Hyung-Ju Cho Chin-Wan Chung Dept. of Eletrial Engineering & Computer Siene Korea Advaned Institute of Siene and Tehnology 373- Kusong-dong,
An Effiient and Salable Approah to CNN Queries in a Road Network Hyung-Ju Cho Chin-Wan Chung Dept. of Eletrial Engineering & Computer Siene Korea Advaned Institute of Siene and Tehnology 373- Kusong-dong,
Implementing Load-Balanced Switches With Fat-Tree Networks
 Implementing Load-Balaned Swithes With Fat-Tree Networks Hung-Shih Chueh, Ching-Min Lien, Cheng-Shang Chang, Jay Cheng, and Duan-Shin Lee Department of Eletrial Engineering & Institute of Communiations
Implementing Load-Balaned Swithes With Fat-Tree Networks Hung-Shih Chueh, Ching-Min Lien, Cheng-Shang Chang, Jay Cheng, and Duan-Shin Lee Department of Eletrial Engineering & Institute of Communiations
And, the (low-pass) Butterworth filter of order m is given in the frequency domain by
 Problem Set no.3.a) The ideal low-pass filter is given in the frequeny domain by B ideal ( f ), f f; =, f > f. () And, the (low-pass) Butterworth filter of order m is given in the frequeny domain by B
Problem Set no.3.a) The ideal low-pass filter is given in the frequeny domain by B ideal ( f ), f f; =, f > f. () And, the (low-pass) Butterworth filter of order m is given in the frequeny domain by B
A Partial Sorting Algorithm in Multi-Hop Wireless Sensor Networks
 A Partial Sorting Algorithm in Multi-Hop Wireless Sensor Networks Abouberine Ould Cheikhna Department of Computer Siene University of Piardie Jules Verne 80039 Amiens Frane Ould.heikhna.abouberine @u-piardie.fr
A Partial Sorting Algorithm in Multi-Hop Wireless Sensor Networks Abouberine Ould Cheikhna Department of Computer Siene University of Piardie Jules Verne 80039 Amiens Frane Ould.heikhna.abouberine @u-piardie.fr
Pipelined Multipliers for Reconfigurable Hardware
 Pipelined Multipliers for Reonfigurable Hardware Mithell J. Myjak and José G. Delgado-Frias Shool of Eletrial Engineering and Computer Siene, Washington State University Pullman, WA 99164-2752 USA {mmyjak,
Pipelined Multipliers for Reonfigurable Hardware Mithell J. Myjak and José G. Delgado-Frias Shool of Eletrial Engineering and Computer Siene, Washington State University Pullman, WA 99164-2752 USA {mmyjak,
Detection and Recognition of Non-Occluded Objects using Signature Map
 6th WSEAS International Conferene on CIRCUITS, SYSTEMS, ELECTRONICS,CONTROL & SIGNAL PROCESSING, Cairo, Egypt, De 9-31, 007 65 Detetion and Reognition of Non-Oluded Objets using Signature Map Sangbum Park,
6th WSEAS International Conferene on CIRCUITS, SYSTEMS, ELECTRONICS,CONTROL & SIGNAL PROCESSING, Cairo, Egypt, De 9-31, 007 65 Detetion and Reognition of Non-Oluded Objets using Signature Map Sangbum Park,
Flow Demands Oriented Node Placement in Multi-Hop Wireless Networks
 Flow Demands Oriented Node Plaement in Multi-Hop Wireless Networks Zimu Yuan Institute of Computing Tehnology, CAS, China {zimu.yuan}@gmail.om arxiv:153.8396v1 [s.ni] 29 Mar 215 Abstrat In multi-hop wireless
Flow Demands Oriented Node Plaement in Multi-Hop Wireless Networks Zimu Yuan Institute of Computing Tehnology, CAS, China {zimu.yuan}@gmail.om arxiv:153.8396v1 [s.ni] 29 Mar 215 Abstrat In multi-hop wireless
On Optimal Total Cost and Optimal Order Quantity for Fuzzy Inventory Model without Shortage
 International Journal of Fuzzy Mathemat and Systems. ISSN 48-9940 Volume 4, Numer (014, pp. 193-01 Researh India Puliations http://www.ripuliation.om On Optimal Total Cost and Optimal Order Quantity for
International Journal of Fuzzy Mathemat and Systems. ISSN 48-9940 Volume 4, Numer (014, pp. 193-01 Researh India Puliations http://www.ripuliation.om On Optimal Total Cost and Optimal Order Quantity for
Lazy Updates: An Efficient Technique to Continuously Monitoring Reverse knn
 Lazy Updates: An Effiient Tehniue to Continuously onitoring Reverse k uhammad Aamir Cheema, Xuemin Lin, Ying Zhang, Wei Wang, Wenjie Zhang The University of ew South Wales, Australia ICTA, Australia {maheema,
Lazy Updates: An Effiient Tehniue to Continuously onitoring Reverse k uhammad Aamir Cheema, Xuemin Lin, Ying Zhang, Wei Wang, Wenjie Zhang The University of ew South Wales, Australia ICTA, Australia {maheema,
Self-Adaptive Parent to Mean-Centric Recombination for Real-Parameter Optimization
 Self-Adaptive Parent to Mean-Centri Reombination for Real-Parameter Optimization Kalyanmoy Deb and Himanshu Jain Department of Mehanial Engineering Indian Institute of Tehnology Kanpur Kanpur, PIN 86 {deb,hjain}@iitk.a.in
Self-Adaptive Parent to Mean-Centri Reombination for Real-Parameter Optimization Kalyanmoy Deb and Himanshu Jain Department of Mehanial Engineering Indian Institute of Tehnology Kanpur Kanpur, PIN 86 {deb,hjain}@iitk.a.in
A Practical Tool for Visualizing and Data Mining Medical Time Series
 A Pratial Tool for Visualizing and Data Mining Medial Time Series Astrat The inreasing interest in time series data mining in the last deade has had surprisingly little impat on real world medial appliations.
A Pratial Tool for Visualizing and Data Mining Medial Time Series Astrat The inreasing interest in time series data mining in the last deade has had surprisingly little impat on real world medial appliations.
Performance of Histogram-Based Skin Colour Segmentation for Arms Detection in Human Motion Analysis Application
 World Aademy of Siene, Engineering and Tehnology 8 009 Performane of Histogram-Based Skin Colour Segmentation for Arms Detetion in Human Motion Analysis Appliation Rosalyn R. Porle, Ali Chekima, Farrah
World Aademy of Siene, Engineering and Tehnology 8 009 Performane of Histogram-Based Skin Colour Segmentation for Arms Detetion in Human Motion Analysis Appliation Rosalyn R. Porle, Ali Chekima, Farrah
1. Inversions. A geometric construction relating points O, A and B looks as follows.
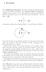 1. Inversions. 1.1. Definitions of inversion. Inversion is a kind of symmetry about a irle. It is defined as follows. he inversion of degree R 2 entered at a point maps a point to the point on the ray
1. Inversions. 1.1. Definitions of inversion. Inversion is a kind of symmetry about a irle. It is defined as follows. he inversion of degree R 2 entered at a point maps a point to the point on the ray
Taming Decentralized POMDPs: Towards Efficient Policy Computation for Multiagent Settings
 Taming Deentralized PMDPs: Towards ffiient Poliy omputation for Multiagent Settings. Nair and M. Tambe omputer Siene Dept. University of Southern alifornia Los Angeles A 90089 nair,tambe @us.edu M. Yokoo
Taming Deentralized PMDPs: Towards ffiient Poliy omputation for Multiagent Settings. Nair and M. Tambe omputer Siene Dept. University of Southern alifornia Los Angeles A 90089 nair,tambe @us.edu M. Yokoo
A Dictionary based Efficient Text Compression Technique using Replacement Strategy
 A based Effiient Text Compression Tehnique using Replaement Strategy Debashis Chakraborty Assistant Professor, Department of CSE, St. Thomas College of Engineering and Tehnology, Kolkata, 700023, India
A based Effiient Text Compression Tehnique using Replaement Strategy Debashis Chakraborty Assistant Professor, Department of CSE, St. Thomas College of Engineering and Tehnology, Kolkata, 700023, India
Computational Biology 6.095/6.895 Database Search Lecture 5 Prof. Piotr Indyk
 Computational Biology 6.095/6.895 Database Searh Leture 5 Prof. Piotr Indyk Previous letures Leture -3: Global alignment in O(mn) Dynami programming Leture -2: Loal alignment, variants, in O(mn) Leture
Computational Biology 6.095/6.895 Database Searh Leture 5 Prof. Piotr Indyk Previous letures Leture -3: Global alignment in O(mn) Dynami programming Leture -2: Loal alignment, variants, in O(mn) Leture
A New RBFNDDA-KNN Network and Its Application to Medical Pattern Classification
 A New RBFNDDA-KNN Network and Its Appliation to Medial Pattern Classifiation Shing Chiang Tan 1*, Chee Peng Lim 2, Robert F. Harrison 3, R. Lee Kennedy 4 1 Faulty of Information Siene and Tehnology, Multimedia
A New RBFNDDA-KNN Network and Its Appliation to Medial Pattern Classifiation Shing Chiang Tan 1*, Chee Peng Lim 2, Robert F. Harrison 3, R. Lee Kennedy 4 1 Faulty of Information Siene and Tehnology, Multimedia
13.1 Numerical Evaluation of Integrals Over One Dimension
 13.1 Numerial Evaluation of Integrals Over One Dimension A. Purpose This olletion of subprograms estimates the value of the integral b a f(x) dx where the integrand f(x) and the limits a and b are supplied
13.1 Numerial Evaluation of Integrals Over One Dimension A. Purpose This olletion of subprograms estimates the value of the integral b a f(x) dx where the integrand f(x) and the limits a and b are supplied
Data Structures in Java
 Data Strutures in Java Leture 8: Trees and Tree Traversals. 10/5/2015 Daniel Bauer 1 Trees in Computer Siene A lot of data omes in a hierarhial/nested struture. Mathematial expressions. Program struture.
Data Strutures in Java Leture 8: Trees and Tree Traversals. 10/5/2015 Daniel Bauer 1 Trees in Computer Siene A lot of data omes in a hierarhial/nested struture. Mathematial expressions. Program struture.
Constructing Transaction Serialization Order for Incremental. Data Warehouse Refresh. Ming-Ling Lo and Hui-I Hsiao. IBM T. J. Watson Research Center
 Construting Transation Serialization Order for Inremental Data Warehouse Refresh Ming-Ling Lo and Hui-I Hsiao IBM T. J. Watson Researh Center July 11, 1997 Abstrat In typial pratie of data warehouse, the
Construting Transation Serialization Order for Inremental Data Warehouse Refresh Ming-Ling Lo and Hui-I Hsiao IBM T. J. Watson Researh Center July 11, 1997 Abstrat In typial pratie of data warehouse, the
Improved flooding of broadcast messages using extended multipoint relaying
 Improved flooding of broadast messages using extended multipoint relaying Pere Montolio Aranda a, Joaquin Garia-Alfaro a,b, David Megías a a Universitat Oberta de Catalunya, Estudis d Informàtia, Mulimèdia
Improved flooding of broadast messages using extended multipoint relaying Pere Montolio Aranda a, Joaquin Garia-Alfaro a,b, David Megías a a Universitat Oberta de Catalunya, Estudis d Informàtia, Mulimèdia
University of California - Riverside Department of Computer Science & Engineering Riverside, CA 92521, USA
 Trak Title: Paper Title: Authors: Speial Trak on Data Mining A Pratial Tool for Visualizing and Data Mining Medial Time Series Li Wei (wli@s.ur.edu) Nitin Kumar (nkumar@s.ur.edu) Venkata Nishanth Lolla
Trak Title: Paper Title: Authors: Speial Trak on Data Mining A Pratial Tool for Visualizing and Data Mining Medial Time Series Li Wei (wli@s.ur.edu) Nitin Kumar (nkumar@s.ur.edu) Venkata Nishanth Lolla
Visualization of patent analysis for emerging technology
 Available online at www.sienediret.om Expert Systems with Appliations Expert Systems with Appliations 34 (28) 84 82 www.elsevier.om/loate/eswa Visualization of patent analysis for emerging tehnology Young
Available online at www.sienediret.om Expert Systems with Appliations Expert Systems with Appliations 34 (28) 84 82 www.elsevier.om/loate/eswa Visualization of patent analysis for emerging tehnology Young
Routing Protocols for Wireless Ad Hoc Networks Hybrid routing protocols Theofanis Kilinkaridis
 Routing Protools for Wireless Ad Ho Networks Hyrid routing protools Theofanis Kilinkaridis tkilinka@.hut.fi Astrat This paper presents a partiular group of routing protools that aim to omine the advantages
Routing Protools for Wireless Ad Ho Networks Hyrid routing protools Theofanis Kilinkaridis tkilinka@.hut.fi Astrat This paper presents a partiular group of routing protools that aim to omine the advantages
The SPS Algorithm: Patching Figural Continuity and Transparency by Split-Patch Search
 The SPS Algorithm: Pathing Figural Continuity and Transpareny y Split-Path Searh Astrat A. Criminisi and A. Blake Mirosoft Researh Ltd., 7 J J Thomson Ave, Camridge, CB3 0FB, UK antrim@mirosoft.om This
The SPS Algorithm: Pathing Figural Continuity and Transpareny y Split-Path Searh Astrat A. Criminisi and A. Blake Mirosoft Researh Ltd., 7 J J Thomson Ave, Camridge, CB3 0FB, UK antrim@mirosoft.om This
Performance Benchmarks for an Interactive Video-on-Demand System
 Performane Benhmarks for an Interative Video-on-Demand System. Guo,P.G.Taylor,E.W.M.Wong,S.Chan,M.Zukerman andk.s.tang ARC Speial Researh Centre for Ultra-Broadband Information Networks (CUBIN) Department
Performane Benhmarks for an Interative Video-on-Demand System. Guo,P.G.Taylor,E.W.M.Wong,S.Chan,M.Zukerman andk.s.tang ARC Speial Researh Centre for Ultra-Broadband Information Networks (CUBIN) Department
Detecting Outliers in High-Dimensional Datasets with Mixed Attributes
 Deteting Outliers in High-Dimensional Datasets with Mixed Attributes A. Koufakou, M. Georgiopoulos, and G.C. Anagnostopoulos 2 Shool of EECS, University of Central Florida, Orlando, FL, USA 2 Dept. of
Deteting Outliers in High-Dimensional Datasets with Mixed Attributes A. Koufakou, M. Georgiopoulos, and G.C. Anagnostopoulos 2 Shool of EECS, University of Central Florida, Orlando, FL, USA 2 Dept. of
SAND Unlimited Release Printed November 1995 Updated November 29, :26 PM EXODUS II: A Finite Element Data Model
 SAND92-2137 Unlimited Release Printed November 1995 Updated November 29, 2006 12:26 PM EXODUS II: A Finite Element Data Model Gregory D. Sjaardema (updated version) Larry A. Shoof, Vitor R. Yarberry Computational
SAND92-2137 Unlimited Release Printed November 1995 Updated November 29, 2006 12:26 PM EXODUS II: A Finite Element Data Model Gregory D. Sjaardema (updated version) Larry A. Shoof, Vitor R. Yarberry Computational
Direct-Mapped Caches
 A Case for Diret-Mapped Cahes Mark D. Hill University of Wisonsin ahe is a small, fast buffer in whih a system keeps those parts, of the ontents of a larger, slower memory that are likely to be used soon.
A Case for Diret-Mapped Cahes Mark D. Hill University of Wisonsin ahe is a small, fast buffer in whih a system keeps those parts, of the ontents of a larger, slower memory that are likely to be used soon.
Improved Circuit-to-CNF Transformation for SAT-based ATPG
 Improved Ciruit-to-CNF Transformation for SAT-based ATPG Daniel Tille 1 René Krenz-Bååth 2 Juergen Shloeffel 2 Rolf Drehsler 1 1 Institute of Computer Siene, University of Bremen, 28359 Bremen, Germany
Improved Ciruit-to-CNF Transformation for SAT-based ATPG Daniel Tille 1 René Krenz-Bååth 2 Juergen Shloeffel 2 Rolf Drehsler 1 1 Institute of Computer Siene, University of Bremen, 28359 Bremen, Germany
Intra- and Inter-Stream Synchronisation for Stored Multimedia Streams
 IEEE International Conferene on Multimedia Computing & Systems, June 17-23, 1996, in Hiroshima, Japan, p 372-381 Intra- and Inter-Stream Synhronisation for Stored Multimedia Streams Ernst Biersak, Werner
IEEE International Conferene on Multimedia Computing & Systems, June 17-23, 1996, in Hiroshima, Japan, p 372-381 Intra- and Inter-Stream Synhronisation for Stored Multimedia Streams Ernst Biersak, Werner
A Multi-Head Clustering Algorithm in Vehicular Ad Hoc Networks
 International Journal of Computer Theory and Engineering, Vol. 5, No. 2, April 213 A Multi-Head Clustering Algorithm in Vehiular Ad Ho Networks Shou-Chih Lo, Yi-Jen Lin, and Jhih-Siao Gao Abstrat Clustering
International Journal of Computer Theory and Engineering, Vol. 5, No. 2, April 213 A Multi-Head Clustering Algorithm in Vehiular Ad Ho Networks Shou-Chih Lo, Yi-Jen Lin, and Jhih-Siao Gao Abstrat Clustering
Tracking Table Tennis Balls in Real Match Scenes for Umpiring Applications
 British Journal of Mathematis & Computer Siene 1(4): 228-241, 2011 SCIENCEDOMAIN international www.sienedomain.org Traking Tale Tennis Balls in Real Math Senes for Umpiring Appliations K. C. P. Wong 1*
British Journal of Mathematis & Computer Siene 1(4): 228-241, 2011 SCIENCEDOMAIN international www.sienedomain.org Traking Tale Tennis Balls in Real Math Senes for Umpiring Appliations K. C. P. Wong 1*
Uplink Channel Allocation Scheme and QoS Management Mechanism for Cognitive Cellular- Femtocell Networks
 62 Uplink Channel Alloation Sheme and QoS Management Mehanism for Cognitive Cellular- Femtoell Networks Kien Du Nguyen 1, Hoang Nam Nguyen 1, Hiroaki Morino 2 and Iwao Sasase 3 1 University of Engineering
62 Uplink Channel Alloation Sheme and QoS Management Mehanism for Cognitive Cellular- Femtoell Networks Kien Du Nguyen 1, Hoang Nam Nguyen 1, Hiroaki Morino 2 and Iwao Sasase 3 1 University of Engineering
Sparse Certificates for 2-Connectivity in Directed Graphs
 Sparse Certifiates for 2-Connetivity in Direted Graphs Loukas Georgiadis Giuseppe F. Italiano Aikaterini Karanasiou Charis Papadopoulos Nikos Parotsidis Abstrat Motivated by the emergene of large-sale
Sparse Certifiates for 2-Connetivity in Direted Graphs Loukas Georgiadis Giuseppe F. Italiano Aikaterini Karanasiou Charis Papadopoulos Nikos Parotsidis Abstrat Motivated by the emergene of large-sale
Adapting K-Medians to Generate Normalized Cluster Centers
 Adapting -Medians to Generate Normalized Cluster Centers Benamin J. Anderson, Deborah S. Gross, David R. Musiant Anna M. Ritz, Thomas G. Smith, Leah E. Steinberg Carleton College andersbe@gmail.om, {dgross,
Adapting -Medians to Generate Normalized Cluster Centers Benamin J. Anderson, Deborah S. Gross, David R. Musiant Anna M. Ritz, Thomas G. Smith, Leah E. Steinberg Carleton College andersbe@gmail.om, {dgross,
Tackling IPv6 Address Scalability from the Root
 Takling IPv6 Address Salability from the Root Mei Wang Ashish Goel Balaji Prabhakar Stanford University {wmei, ashishg, balaji}@stanford.edu ABSTRACT Internet address alloation shemes have a huge impat
Takling IPv6 Address Salability from the Root Mei Wang Ashish Goel Balaji Prabhakar Stanford University {wmei, ashishg, balaji}@stanford.edu ABSTRACT Internet address alloation shemes have a huge impat
Analysis of input and output configurations for use in four-valued CCD programmable logic arrays
 nalysis of input and output onfigurations for use in four-valued D programmable logi arrays J.T. utler H.G. Kerkhoff ndexing terms: Logi, iruit theory and design, harge-oupled devies bstrat: s in binary,
nalysis of input and output onfigurations for use in four-valued D programmable logi arrays J.T. utler H.G. Kerkhoff ndexing terms: Logi, iruit theory and design, harge-oupled devies bstrat: s in binary,
Staircase Join: Teach a Relational DBMS to Watch its (Axis) Steps
 Stairase Join: Teah a Relational DBMS to Wath its (Axis) Steps Torsten Grust Maurie van Keulen Jens Teubner University of Konstanz Department of Computer and Information Siene P.O. Box D 88, 78457 Konstanz,
Stairase Join: Teah a Relational DBMS to Wath its (Axis) Steps Torsten Grust Maurie van Keulen Jens Teubner University of Konstanz Department of Computer and Information Siene P.O. Box D 88, 78457 Konstanz,
arxiv: v1 [cs.db] 13 Sep 2017
![arxiv: v1 [cs.db] 13 Sep 2017 arxiv: v1 [cs.db] 13 Sep 2017](/thumbs/96/126543346.jpg) An effiient lustering algorithm from the measure of loal Gaussian distribution Yuan-Yen Tai (Dated: May 27, 2018) In this paper, I will introdue a fast and novel lustering algorithm based on Gaussian distribution
An effiient lustering algorithm from the measure of loal Gaussian distribution Yuan-Yen Tai (Dated: May 27, 2018) In this paper, I will introdue a fast and novel lustering algorithm based on Gaussian distribution
Multi-Piece Mold Design Based on Linear Mixed-Integer Program Toward Guaranteed Optimality
 INTERNATIONAL CONFERENCE ON MANUFACTURING AUTOMATION (ICMA200) Multi-Piee Mold Design Based on Linear Mixed-Integer Program Toward Guaranteed Optimality Stephen Stoyan, Yong Chen* Epstein Department of
INTERNATIONAL CONFERENCE ON MANUFACTURING AUTOMATION (ICMA200) Multi-Piee Mold Design Based on Linear Mixed-Integer Program Toward Guaranteed Optimality Stephen Stoyan, Yong Chen* Epstein Department of
Figure 1. LBP in the field of texture analysis operators.
 L MEHODOLOGY he loal inary pattern (L) texture analysis operator is defined as a gray-sale invariant texture measure, derived from a general definition of texture in a loal neighorhood. he urrent form
L MEHODOLOGY he loal inary pattern (L) texture analysis operator is defined as a gray-sale invariant texture measure, derived from a general definition of texture in a loal neighorhood. he urrent form
Acoustic Links. Maximizing Channel Utilization for Underwater
 Maximizing Channel Utilization for Underwater Aousti Links Albert F Hairris III Davide G. B. Meneghetti Adihele Zorzi Department of Information Engineering University of Padova, Italy Email: {harris,davide.meneghetti,zorzi}@dei.unipd.it
Maximizing Channel Utilization for Underwater Aousti Links Albert F Hairris III Davide G. B. Meneghetti Adihele Zorzi Department of Information Engineering University of Padova, Italy Email: {harris,davide.meneghetti,zorzi}@dei.unipd.it
EXODUS II: A Finite Element Data Model
 SAND92-2137 Unlimited Release Printed November 1995 Distribution Category UC-705 EXODUS II: A Finite Element Data Model Larry A. Shoof, Vitor R. Yarberry Computational Mehanis and Visualization Department
SAND92-2137 Unlimited Release Printed November 1995 Distribution Category UC-705 EXODUS II: A Finite Element Data Model Larry A. Shoof, Vitor R. Yarberry Computational Mehanis and Visualization Department
Series/1 GA File No i=:: IBM Series/ Battery Backup Unit Description :::5 ~ ~ >-- ffi B~88 ~0 (] II IIIIII
![Series/1 GA File No i=:: IBM Series/ Battery Backup Unit Description :::5 ~ ~ >-- ffi B~88 ~0 (] II IIIIII Series/1 GA File No i=:: IBM Series/ Battery Backup Unit Description :::5 ~ ~ >-- ffi B~88 ~0 (] II IIIIII](/thumbs/88/117260360.jpg) Series/1 I. (.. GA34-0032-0 File No. 51-10 a i=:: 5 Q 1 IBM Series/1 4999 Battery Bakup Unit Desription B88 0 (] o. :::5 >-- ffi "- I II1111111111IIIIII1111111 ---- - - - - ----- --_.- Series/1 «h: ",
Series/1 I. (.. GA34-0032-0 File No. 51-10 a i=:: 5 Q 1 IBM Series/1 4999 Battery Bakup Unit Desription B88 0 (] o. :::5 >-- ffi "- I II1111111111IIIIII1111111 ---- - - - - ----- --_.- Series/1 «h: ",
Detection of RF interference to GPS using day-to-day C/No differences
 1 International Symposium on GPS/GSS Otober 6-8, 1. Detetion of RF interferene to GPS using day-to-day /o differenes Ryan J. R. Thompson 1#, Jinghui Wu #, Asghar Tabatabaei Balaei 3^, and Andrew G. Dempster
1 International Symposium on GPS/GSS Otober 6-8, 1. Detetion of RF interferene to GPS using day-to-day /o differenes Ryan J. R. Thompson 1#, Jinghui Wu #, Asghar Tabatabaei Balaei 3^, and Andrew G. Dempster
We don t need no generation - a practical approach to sliding window RLNC
 We don t need no generation - a pratial approah to sliding window RLNC Simon Wunderlih, Frank Gabriel, Sreekrishna Pandi, Frank H.P. Fitzek Deutshe Telekom Chair of Communiation Networks, TU Dresden, Dresden,
We don t need no generation - a pratial approah to sliding window RLNC Simon Wunderlih, Frank Gabriel, Sreekrishna Pandi, Frank H.P. Fitzek Deutshe Telekom Chair of Communiation Networks, TU Dresden, Dresden,
Video Data and Sonar Data: Real World Data Fusion Example
 14th International Conferene on Information Fusion Chiago, Illinois, USA, July 5-8, 2011 Video Data and Sonar Data: Real World Data Fusion Example David W. Krout Applied Physis Lab dkrout@apl.washington.edu
14th International Conferene on Information Fusion Chiago, Illinois, USA, July 5-8, 2011 Video Data and Sonar Data: Real World Data Fusion Example David W. Krout Applied Physis Lab dkrout@apl.washington.edu
Tree Awareness for Relational DBMS Kernels: Staircase Join
 Tree Awareness for Relational DBMS Kernels: Stairase Join Torsten Grust 1 and Maurie van Keulen 2 1 Department of Computer and Information Siene, University of Konstanz, P.O. Box D188, 78457 Konstanz,
Tree Awareness for Relational DBMS Kernels: Stairase Join Torsten Grust 1 and Maurie van Keulen 2 1 Department of Computer and Information Siene, University of Konstanz, P.O. Box D188, 78457 Konstanz,
One Against One or One Against All : Which One is Better for Handwriting Recognition with SVMs?
 One Against One or One Against All : Whih One is Better for Handwriting Reognition with SVMs? Jonathan Milgram, Mohamed Cheriet, Robert Sabourin To ite this version: Jonathan Milgram, Mohamed Cheriet,
One Against One or One Against All : Whih One is Better for Handwriting Reognition with SVMs? Jonathan Milgram, Mohamed Cheriet, Robert Sabourin To ite this version: Jonathan Milgram, Mohamed Cheriet,
Weak Dependence on Initialization in Mixture of Linear Regressions
 Proeedings of the International MultiConferene of Engineers and Computer Sientists 8 Vol I IMECS 8, Marh -6, 8, Hong Kong Weak Dependene on Initialization in Mixture of Linear Regressions Ryohei Nakano
Proeedings of the International MultiConferene of Engineers and Computer Sientists 8 Vol I IMECS 8, Marh -6, 8, Hong Kong Weak Dependene on Initialization in Mixture of Linear Regressions Ryohei Nakano
Layout Compliance for Triple Patterning Lithography: An Iterative Approach
 Layout Compliane for Triple Patterning Lithography: An Iterative Approah Bei Yu, Gilda Garreton, David Z. Pan ECE Dept. University of Texas at Austin, Austin, TX, USA Orale Las, Orale Corporation, Redwood
Layout Compliane for Triple Patterning Lithography: An Iterative Approah Bei Yu, Gilda Garreton, David Z. Pan ECE Dept. University of Texas at Austin, Austin, TX, USA Orale Las, Orale Corporation, Redwood
 A Method for Measuring Co-authorship Relationships in MediaWiki Libby Veng-Sam Tang Department of Computer and Information Siene Faulty of Siene and Tehnology University of Maau Maau S.A.R., China Tel:
A Method for Measuring Co-authorship Relationships in MediaWiki Libby Veng-Sam Tang Department of Computer and Information Siene Faulty of Siene and Tehnology University of Maau Maau S.A.R., China Tel:
