PUA Operation Spreads Thousands of Explicit Apps in the Wild and on Legitimate App Stores
|
|
|
- Brianne Beasley
- 6 years ago
- Views:
Transcription
1 Appendix PUA Operation Spreads Thousands of Explicit Apps in the Wild and on Legitimate App Stores Appendix TrendLabs Security Intelligence Blog Lilang Wu Mobile Threat Response Team May 2017
2 TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice. The information contained herein may not be applicable to all situations and may not reflect the most current situation. Nothing contained herein should be relied on or acted upon without the benefit of legal advice based on the particular facts and circumstances presented and nothing herein should be construed otherwise. Trend Micro reserves the right to modify the contents of this document at any time without prior notice. Translations of any material into other languages are intended solely as a convenience. Translation accuracy is not guaranteed nor implied. If any questions arise related to the accuracy of a translation, please refer to the original language official version of the document. Any discrepancies or differences created in the translation are not binding and have no legal effect for compliance or enforcement purposes. Although Trend Micro uses reasonable efforts to include accurate and up-to-date information herein, Trend Micro makes no warranties or representations of any kind as to its accuracy, currency, or completeness. You agree that access to and use of and reliance on this document and the content thereof is at your own risk. Trend Micro disclaims all warranties of any kind, express or implied. Neither Trend Micro nor any party involved in creating, producing, or delivering this document shall be liable for any consequence, loss, or damage, including direct, indirect, special, consequential, loss of business profits, or special damages, whatsoever arising out of access to, use of, or inability to use, or in connection with the use of this document, or any errors or omissions in the content thereof. Use of this information constitutes acceptance for use in an as is condition.
3 Indicators of Compromise (IoCs): Hashes (SHA256) for Android SHA256 Package Name App Label Detection 915d b65c5db3cdd006 ddad2a542e13d118b2ab6467e 9e71479b29a20e 5e21caf972f65c746e947a204b 1fa084e116436c4c7047a10bf1 369af6a9547d d5e93a816e7f73de0e73207c fd0bd7ed4924d62 cae ad fa0cd13d2780ee122211bcbef0 583c6b7e81c28b25acd8f58d47 e77db8a06e6f d2114b0e2059c53b e5 7552be4299e5c1f1bf8c1852d6 b cce7d114b917f112b0eeb7861 1d31d6cb55c0b89773e25f b4b76a47 bd6d528e713e64d5d03946eb2 1f4b542d87bb7dfd33696e34b 6acee88306eb38 c d4010a077ffeba8a e46d4e044d1a4517d94a e6bf18a69b 9e361c65275a499b ff6 a463e1b67e5d986b7f160b72d b5c779f3015ec a3eb017f a1d d7a7966ee04bff81e2e3b37325 f e7bf1 cn.g.hades.dea 成人影院 ANDROIDOS_SMSREG.AXMFA regre.trh.dwewf AV 快播 ANDROIDOS_HIDEICON.OPSA com.xiao.ht.kumg 幻想影院 ANDROIDOS_SMSREG.AXBDJ 3
4 Hashes (SHA256) for ios SHA256 Package Name App Label Detection afef6a1850ec6532f424 2e83a90b625ead8d912d89a9e e6408 cebb5a1dee4753af0ba483be8 e3234e004e20acc80da02e5a5 b96e1a3819eeb4 ab2f1c2674e01ffa28150a5585 a488d5414fd0d09380c979e1b 88a4b ada39d70d05ce08c124d1ac3 d5f0a10ed9f4efcb0c8b9d5285 4ddc921f5bca7 1aa7e843f08335bbe82c0b7dd 5d24e1f865b5a14eeedbe d2cd121 85e f944a3fb7693def c01a63c693a672573e26d1bb7 6deb571f85caa cd47f65f2595a2c1d528da cc9dd bda8139 f77e702fdebf4 2b6f55dce0ecca742bd23549e0 5b162dcd71e278e1f1e5c f4f f90d24a739c96a ef0 c1bcdbd224a619a8818ce9990 6f c2a 8314e5ddf7b08624ed38b51dd 9f7bd5b122b83075efc36ece34 f0424e2b510fc com.eddie.nguyen NightMovie_DXTX com.eddie.nguyen NightMovie_DXTX com.gjlixkl.hklcc 春爱影院 com.gjlixkl.hklcc 春爱影院 com.wt23.charmpl ay6 com.wt23.charmpl ay6 3D 快播 3D 快播 com.av.jx.6 快播鸡年版 com.av.jx.8 快播鸡年版 com.liuliu.yyer com.liuliu.yyer AV 快播 AV 快播 Hashes (SHA256) for ios (labels dependent on language on device) SHA256 Package Name Detection a97dd097d9e94b526df dfb14 ed5ab9a c5df12c94f 5f494e8a884223a a804ac97bcd55202da 4130e5aaa1b10a1c457ed01e com.yoshiya.wifi1 com.funplayer.st360 4
5 SHA256 Package Name Detection e8bc19f41a2c37e01df7f3ab84949ceec4d com.funplayer.sandtrap 16d6325ee1da167a67bff5a af028bd0fdbc870daa d0ecd8ae game.0002 f8c6d86f2c11f539760d5a3d 737bbee4d0e4cd710bd35d91547dd8bb8a0c218 gamekb.2 a c8b07f9fe3dbee67 c3f9a877de62ca35e8345f6b ba0aca com.app.kuaisusp b45285eb3ecec8bcd6f102a2 14e0bc60546c474ab1fad7b117aa61cf6ff com d7f8d059db e32cac8dbfbe2e7ec3f7c899387c20f9a784110b1 com.organge.kuaibo c7f0c380b4d9a410c26f6d9 5ba75c4ab6c7e65d8b796b2d d084c com.dehua.crzm 9a3888cbdefb7a81ba3c05387 d1d9d2d1b6ff7bde0648e3769b308b5a734a6d4 com efbaa c6cdc af9adfcfeeecfc618b f8 com acf3b8234e9e9590db728 a882b93bb50793a96f41d516bbd7a37d43cb711 com.shenpeng.ctttt 19750b25abc19fb5c62aa fbadaf1e88f04f5238ef500c55e f com.shenpeng.doto a4e0a729f cbc e559c2ed3bebcdcb06c7cd6c56db1a06b86ff0e6 com.fengqi.neoo 8833d609b7f8dcc870674a d0ecf764e4cfa2b89a56acd48811b com.dehua.stickman af3a367bbd18e90da0eeab79 e02a26bea3ff73ae95812cbe1cda8c0e2aafe0505 com.fengqi.dto fa1eb48b9b a3e aeb5a746c040aed5a8b542699b99d158e604ab3 com.fengqi.dt1024 9ac95d36f79dad726115e56a8 e3a063f4f31dcedc9faba0d179f3801f67ccd7fbd6 com b129844e175ce781e4ab9 002de9c5fcd5ec17d4e211bf9ebc28e0a44dd008 guas.bofa.gasa c430fd7d45e5bf5673fd2b90 ae3a60251f4ac4fca8f2813fa5d042271ca38dd54 nhb.bfqn.basq 30fec7b467e19d57fc0162f 35ea15eb2821a9af1e6bfcd83f5f b4087 com.nexmon.xfzyfree f14fde87ad54a007856ab01 368b ebdb7269f9514c0fdcfa731da21e4 com.nexmon.hkmj 1c645e90eca98ecb0ce8c806 a a b9b5927fb36d030cf6434a jie.yans.jybd 849f75b7ce2f da6 e4b05f064b6d58fdb5a8d00f034024f98edd3ff67 com.nexmon.vgsm 5
6 SHA256 Package Name Detection afdd1f75badfa9 fd6ac26c5ad86d6f242a505d7db0a900f37b7e e2b1fb764bab9631b06 7a763e43fe00c0c34735befe014dadd5e56419ad e86606e60fb8949ad1ce1f0f 75b fc64e14e9d6b b1b3c8f358 a4b00cea7f923a75f416bfa9 4ff285b0835a0e07bcaf18dd32c6484bd63e56fad becd1e4491ca504db47df7f e85ded2ab9c3b47da85b08579eee7e e5f8b3270d0fa31557a1179 2ba3f1802bb9c76974ef6f2d3be69569c999b24d ee3b6a70d5ab06f6dbd27e ff3185df646cda0425d31f 7b946eebb46e1137c14d92e d578ec8620d8cd44d75445d482ee43aa0e06f591 cbf49c622274d bd3d d17edf2a8782b52ae9f8a8ac6606ffa435944f f2464e60ef7b13e55a20 eb31442d0b088b253355e60add3038e3429b723 29b9446ac5bf432748f50968b 0fe4e431ba35ea be0cbfb133470b6d d3d42dcab377a6fec fcd29457f8a734b3747f188eacb5de29cef656 b0e3c5046b f 6ae76655cb89facfe474e e850301ba825 a2abb88bf634dac58155fb6d 720bd8dc4dd32deb0d9df8159e5e33e64af759ef 78adf837e3f2949f32606a28 c7ac bd038c0b490bea25c0f35f4256 b b7585e76f5ebd62 3c7ba6b5da972130b75b74d7da658fab428e7df3 864d0cf1d296f5bce4431d20 e1a2e69480e cd9c5437bba20bc1800f a26f32492c2a1028d0 com.nexmon.learnquote com.nexmon.papitube xle.xaza.xule zoxe.zaox.zaxi sof.sfan.dysf sen.papiyy.tori vga.xumb.vgxb com.papitb.xiaocao xio.ruiqin.ttmj xio.ruiqin.yunbo xio.ruiqin.nhba xio.ruiqin.tort xio.ruiqin.tita xio.ruiqin.jiji xio.ruiqin.yule xio.ruiqin.yese xio.ruiqin.xzs 6
7 Malicious Domains: URL/IP Address ygyl.bysun.cc jinm09a.eeeeioslyee4.pw woaikanpianyongjiumianfei.cc ffjj-2.com wdfw.ksmsmk.com www. afuxz.com mo.39lo.com html5.senruilicai.com e.919cp.com afuxz.com iosldy.hzt88.com waszyy.com Xmxli.cesicc.org.cn aaaaajbrg.cn in450.ejud7z.com 0318.weitaohu.com csdt.isoucha.com ghbyl. com hymxz. com syjlzs. com zgqlxw. com eduigou. com isoucha. com ksmsmk. com seuxm. cn 7
8 Trend Micro Incorporated, a global leader in security software, strives to make the world safe for exchanging digital information. Our innovative solutions for consumers, businesses and governments provide layered content security to protect information on mobile devices, endpoints, gateways, servers and the cloud. All of our solutions are powered by cloud-based global threat intelligence, the Trend Micro Smart Protection Network, and are supported by over 1,200 threat experts around the globe. For more information, visit by Trend Micro, Incorporated. All rights reserved. Trend Micro and the Trend Micro t-ball logo are trademarks or registered trademarks of Trend Micro, Incorporated. All other product or company names may be trademarks or registered trademarks of their owners N. De Anza Blvd. Cupertino, CA U.S. toll free: Phone: Fax:
Android Backdoor GhostCtrl can Silently Record Your Audio, Video, and More
 Appendix Android Backdoor GhostCtrl can Silently Record Your Audio, Video, and More Appendix TrendLabs Security Intelligence Blog Lenart Bermejo, Jordan Pan, and Cedric Pernet July 2017 TREND MICRO LEGAL
Appendix Android Backdoor GhostCtrl can Silently Record Your Audio, Video, and More Appendix TrendLabs Security Intelligence Blog Lenart Bermejo, Jordan Pan, and Cedric Pernet July 2017 TREND MICRO LEGAL
DRIDEX s New Tricks Lead to Global Spam Outbreak
 Appendix DRIDEX s New Tricks Lead to Global Spam Outbreak Appendix TrendLabs Security Intelligence Blog Michael Casayuran, Rhena Inocencio, and Jay Yaneza May 2016 TREND MICRO LEGAL DISCLAIMER The information
Appendix DRIDEX s New Tricks Lead to Global Spam Outbreak Appendix TrendLabs Security Intelligence Blog Michael Casayuran, Rhena Inocencio, and Jay Yaneza May 2016 TREND MICRO LEGAL DISCLAIMER The information
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
HDDCryptor: Subtle Updates, Still a Credible Threat
 Appendix HDDCryptor: Subtle Updates, Still a Credible Threat Appendix TrendLabs Security Intelligence Blog Stephen Hilt and Fernando Mercês November TREND MICRO LEGAL DISCLAIMER The information provided
Appendix HDDCryptor: Subtle Updates, Still a Credible Threat Appendix TrendLabs Security Intelligence Blog Stephen Hilt and Fernando Mercês November TREND MICRO LEGAL DISCLAIMER The information provided
FighterPOS Pos Malware Gets Worm Routine
 Appendix FighterPOS Pos Malware Gets Worm Routine Appendix TrendLabs Security Intelligence Blog Jay Yaneza and Erika Mendoza Trend Micro Cyber Safety Solutions Team February 2016 TREND MICRO LEGAL DISCLAIMER
Appendix FighterPOS Pos Malware Gets Worm Routine Appendix TrendLabs Security Intelligence Blog Jay Yaneza and Erika Mendoza Trend Micro Cyber Safety Solutions Team February 2016 TREND MICRO LEGAL DISCLAIMER
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
KillDisk and BlackEnergy Are Not Just Energy Sector Threats
 Appendix KillDisk and BlackEnergy Are Not Just Energy Sector Threats Appendix TrendLabs Security Intelligence Blog Kyle Wilhoit February 2016 TREND MICRO LEGAL DISCLAIMER The information provided herein
Appendix KillDisk and BlackEnergy Are Not Just Energy Sector Threats Appendix TrendLabs Security Intelligence Blog Kyle Wilhoit February 2016 TREND MICRO LEGAL DISCLAIMER The information provided herein
Apps Disguised as Security Tools Bombard Users With Ads and Track Users' Location
 Appendix Apps Disguised as Security Tools Bombard Users With Ads and Track Users' Location Appendix TrendLabs Security Intelligence Blog Lorin Wu January 2018 Trend Micro Apps Disguised as Security Tools
Appendix Apps Disguised as Security Tools Bombard Users With Ads and Track Users' Location Appendix TrendLabs Security Intelligence Blog Lorin Wu January 2018 Trend Micro Apps Disguised as Security Tools
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
Correlation and Phishing
 A Trend Micro Research Paper Email Correlation and Phishing How Big Data Analytics Identifies Malicious Messages RungChi Chen Contents Introduction... 3 Phishing in 2013... 3 The State of Email Authentication...
A Trend Micro Research Paper Email Correlation and Phishing How Big Data Analytics Identifies Malicious Messages RungChi Chen Contents Introduction... 3 Phishing in 2013... 3 The State of Email Authentication...
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TREND MICRO LEGAL DISCLAIMER
 TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
TrendLabs TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed to constitute legal advice.
Device Vulnerabilities in the Connected Home: Uncovering Remote Code Execution and More
 TrendLabs Device Vulnerabilities in the Connected Home: Uncovering Remote Code Execution and More Technical Brief TrendLabs Security Intelligence Blog Dove Chiu, Kenney Lu, and Tim Yeh Threats Analysts
TrendLabs Device Vulnerabilities in the Connected Home: Uncovering Remote Code Execution and More Technical Brief TrendLabs Security Intelligence Blog Dove Chiu, Kenney Lu, and Tim Yeh Threats Analysts
The Reigning King of IP Camera Botnets and its Challengers
 Appendix The Reigning King of IP Camera Botnets and its Challengers Appendix TrendLabs Security Intelligence Blog Dove Chu, Kenney Lu and Tim Yeh APT Team and CSS May 2017 Indicators of Compromise (IoCs):
Appendix The Reigning King of IP Camera Botnets and its Challengers Appendix TrendLabs Security Intelligence Blog Dove Chu, Kenney Lu and Tim Yeh APT Team and CSS May 2017 Indicators of Compromise (IoCs):
Trend Micro Portable Security 2. Malware Scanning and Cleanup Tool for Stand-alone PCs or Closed Systems
 Trend Micro Portable Security 2 Malware Scanning and Cleanup Tool for Stand-alone PCs or Closed Systems Contents TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information
Trend Micro Portable Security 2 Malware Scanning and Cleanup Tool for Stand-alone PCs or Closed Systems Contents TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information
CAS Quick Deployment Guide January 2018
 CAS January 2018 Page 2 of 18 Trend Micro CAS January 2018 This document is to guide TrendMicro SE and Solution Architect team run a successful Cloud App Security POC with prospective customers. It is
CAS January 2018 Page 2 of 18 Trend Micro CAS January 2018 This document is to guide TrendMicro SE and Solution Architect team run a successful Cloud App Security POC with prospective customers. It is
INCLUDING MEDICAL ADVICE DISCLAIMER
 Jordan s Guardian Angels Terms and Conditions of Use INCLUDING MEDICAL ADVICE DISCLAIMER Your use of this website and its content constitutes your agreement to be bound by these terms and conditions of
Jordan s Guardian Angels Terms and Conditions of Use INCLUDING MEDICAL ADVICE DISCLAIMER Your use of this website and its content constitutes your agreement to be bound by these terms and conditions of
ENTERPRISE ENDPOINT COMPARATIVE REPORT
 ENTERPRISE ENDPOINT COMPARATIVE REPORT SECURITY STACK: EXPLOITS Authors Randy Abrams, Thomas Skybakmoen Tested Products Bitdefender Endpoint Security v5.3 ESET Endpoint Antivirus v6.1 Fortinet FortiClient
ENTERPRISE ENDPOINT COMPARATIVE REPORT SECURITY STACK: EXPLOITS Authors Randy Abrams, Thomas Skybakmoen Tested Products Bitdefender Endpoint Security v5.3 ESET Endpoint Antivirus v6.1 Fortinet FortiClient
The Urpage Connection to Bahamut, Confucius and Patchwork
 TrendLabs The Urpage Connection to Bahamut, Confucius and Patchwork Appendix TrendLabs Security Intelligence Blog Daniel Lunghi and Ecular Xu August 2018 Android Indicators of Compromise (IoCs) SHA256
TrendLabs The Urpage Connection to Bahamut, Confucius and Patchwork Appendix TrendLabs Security Intelligence Blog Daniel Lunghi and Ecular Xu August 2018 Android Indicators of Compromise (IoCs) SHA256
OCTOSHAPE SDK AND CLIENT LICENSE AGREEMENT (SCLA)
 OCTOSHAPE SDK AND CLIENT LICENSE AGREEMENT (SCLA) This is a License Agreement (the "Agreement") for certain code (the Software ) owned by Akamai Technologies, Inc. ( Akamai ) that is useful in connection
OCTOSHAPE SDK AND CLIENT LICENSE AGREEMENT (SCLA) This is a License Agreement (the "Agreement") for certain code (the Software ) owned by Akamai Technologies, Inc. ( Akamai ) that is useful in connection
Terms of Use. Changes. General Use.
 Terms of Use THESE TERMS AND CONDITIONS (THE TERMS ) ARE A LEGAL CONTRACT BETWEEN YOU AND SPIN TRANSFER TECHNOLOGIES ( SPIN TRANSFER TECHNOLOGIES, STT, WE OR US ). THE TERMS EXPLAIN HOW YOU ARE PERMITTED
Terms of Use THESE TERMS AND CONDITIONS (THE TERMS ) ARE A LEGAL CONTRACT BETWEEN YOU AND SPIN TRANSFER TECHNOLOGIES ( SPIN TRANSFER TECHNOLOGIES, STT, WE OR US ). THE TERMS EXPLAIN HOW YOU ARE PERMITTED
HYCU SCOM Management Pack for F5 BIG-IP
 HYCU SCOM Management Pack for F5 BIG-IP Product version: 5.3 Product release date: March 2018 Document edition: Second Legal notices Copyright notice 2015-2018 HYCU. All rights reserved. This document
HYCU SCOM Management Pack for F5 BIG-IP Product version: 5.3 Product release date: March 2018 Document edition: Second Legal notices Copyright notice 2015-2018 HYCU. All rights reserved. This document
SUPPORT MATRIX. HYCU OMi Management Pack for Citrix
 HYCU OMi Management Pack for Citrix : 2.0 Product release date: October 2017 Document release data: April 2018 Legal notices Copyright notice 2014-2018 HYCU. All rights reserved. This document contains
HYCU OMi Management Pack for Citrix : 2.0 Product release date: October 2017 Document release data: April 2018 Legal notices Copyright notice 2014-2018 HYCU. All rights reserved. This document contains
NEXT GENERATION FIREWALL. Tested Products. Environment. SonicWall Security Value Map (SVM) JULY 11, 2017 Author Thomas Skybakmoen
 NEXT GENERATION FIREWALL SonicWall Security Value Map (SVM) JULY 11, 2017 Author Thomas Skybakmoen Tested Products NGFW Group Test: SonicWall NSA 6600 SonicOS Enhanced 6.2.5.10-70n Dynamic signature database
NEXT GENERATION FIREWALL SonicWall Security Value Map (SVM) JULY 11, 2017 Author Thomas Skybakmoen Tested Products NGFW Group Test: SonicWall NSA 6600 SonicOS Enhanced 6.2.5.10-70n Dynamic signature database
SUPPORT MATRIX. Comtrade OMi Management Pack for Citrix
 Comtrade OMi Management Pack for Citrix : 2.0 Product release date: December 2016 Document release date: July 2017 Legal notices Copyright notice 2017 Comtrade Software. All rights reserved. This document
Comtrade OMi Management Pack for Citrix : 2.0 Product release date: December 2016 Document release date: July 2017 Legal notices Copyright notice 2017 Comtrade Software. All rights reserved. This document
INTERNET ACCESS SERVICE AGREEMENT PLEASE READ CAREFULLY
 INTERNET ACCESS SERVICE AGREEMENT PLEASE READ CAREFULLY Plains Communication Services ( PCS ), LLC and Plainstel.com provides its subscribers with access to the Internet only on the terms and conditions
INTERNET ACCESS SERVICE AGREEMENT PLEASE READ CAREFULLY Plains Communication Services ( PCS ), LLC and Plainstel.com provides its subscribers with access to the Internet only on the terms and conditions
Network Security Protection Alternatives for the Cloud
 A Trend Micro White Paper May 2016 Network Security Protection Alternatives for the Cloud» A technical brief summarizing the deployment options that can be used to deploy IDS/IPS protection for cloud instances
A Trend Micro White Paper May 2016 Network Security Protection Alternatives for the Cloud» A technical brief summarizing the deployment options that can be used to deploy IDS/IPS protection for cloud instances
QUARTZ LEGAL TERMS AND CONDITIONS
 QUARTZ LEGAL TERMS AND CONDITIONS 1. USE OF THIS WEBSITE: The Quartz vodka website is owned and operated by Ungava Spirits Co. Ltd. (collectively hereafter "Site Owner"). Your use of this website is subject
QUARTZ LEGAL TERMS AND CONDITIONS 1. USE OF THIS WEBSITE: The Quartz vodka website is owned and operated by Ungava Spirits Co. Ltd. (collectively hereafter "Site Owner"). Your use of this website is subject
WEBSITE TERMS OF USE
 WEBSITE TERMS OF USE Effective Date: April 14, 2018 Welcome to the Center for Behavioral Sciences, Inc. ( CBS ) website! CBS, Inc. maintains this website ( Website ) for your personal information, education
WEBSITE TERMS OF USE Effective Date: April 14, 2018 Welcome to the Center for Behavioral Sciences, Inc. ( CBS ) website! CBS, Inc. maintains this website ( Website ) for your personal information, education
ADVANCED ENDPOINT PROTECTION COMPARATIVE REPORT
 ADVANCED ENDPOINT PROTECTION COMPARATIVE REPORT Total Cost of Ownership () MARCH 10, 2017 Authors Jason Brvenik, Thomas Skybakmoen, Morgan Dhanraj Tested Products Carbon Black Cb Protection v7.2.3.3106
ADVANCED ENDPOINT PROTECTION COMPARATIVE REPORT Total Cost of Ownership () MARCH 10, 2017 Authors Jason Brvenik, Thomas Skybakmoen, Morgan Dhanraj Tested Products Carbon Black Cb Protection v7.2.3.3106
1. License Grant; Related Provisions.
 IMPORTANT: READ THIS AGREEMENT CAREFULLY. THIS IS A LEGAL AGREEMENT BETWEEN AVG TECHNOLOGIES CY, Ltd. ( AVG TECHNOLOGIES ) AND YOU (ACTING AS AN INDIVIDUAL OR, IF APPLICABLE, ON BEHALF OF THE INDIVIDUAL
IMPORTANT: READ THIS AGREEMENT CAREFULLY. THIS IS A LEGAL AGREEMENT BETWEEN AVG TECHNOLOGIES CY, Ltd. ( AVG TECHNOLOGIES ) AND YOU (ACTING AS AN INDIVIDUAL OR, IF APPLICABLE, ON BEHALF OF THE INDIVIDUAL
MegaStat Installation Instructions
 MegaStat Installation Instructions 1. Download MegaStatInstallationFilesWindows.zip from the website. When you click the download link you will see options at the bottom of the screen that will depend
MegaStat Installation Instructions 1. Download MegaStatInstallationFilesWindows.zip from the website. When you click the download link you will see options at the bottom of the screen that will depend
Terms and Conditions of Website Use
 Terms and Conditions of Website Use This website (the "Site") is owned and operated by Hoshizaki Lancer Pty Ltd (ABN 84 007 706 461) ("Hoshizaki Lancer") and may contain material from Hoshizaki Lancer
Terms and Conditions of Website Use This website (the "Site") is owned and operated by Hoshizaki Lancer Pty Ltd (ABN 84 007 706 461) ("Hoshizaki Lancer") and may contain material from Hoshizaki Lancer
Entrust WAP Server Certificate Relying Party Agreement
 Entrust WAP Server Certificate Relying Party Agreement The WAP/WTLS specification v1.1 does not provide a means for certificate revocation checking. The following Relying Party Agreement" provides further
Entrust WAP Server Certificate Relying Party Agreement The WAP/WTLS specification v1.1 does not provide a means for certificate revocation checking. The following Relying Party Agreement" provides further
T E C H N I C A L S A L E S S E R V I C E S
 T E C H N I C A L S A L E S S E R V I C E S Trend Micro OfficeScan 7.0 and Cisco Security Agent 4.5 Configuration For Cisco Security Agent 4.5 August 2005 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino,
T E C H N I C A L S A L E S S E R V I C E S Trend Micro OfficeScan 7.0 and Cisco Security Agent 4.5 Configuration For Cisco Security Agent 4.5 August 2005 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino,
TERMS & CONDITIONS. Complied with GDPR rules and regulation CONDITIONS OF USE PROPRIETARY RIGHTS AND ACCEPTABLE USE OF CONTENT
 TERMS & CONDITIONS www.karnevalkings.com (the "Site") is a website and online service owned and operated by the ViisTek Media group of companies (collectively known as "Karnevalkings.com", "we," "group",
TERMS & CONDITIONS www.karnevalkings.com (the "Site") is a website and online service owned and operated by the ViisTek Media group of companies (collectively known as "Karnevalkings.com", "we," "group",
ADVANCED ENDPOINT PROTECTION TEST REPORT
 ADVANCED ENDPOINT PROTECTION TEST REPORT SentinelOne Endpoint Protection Platform v1.8.3#31 FEBRUARY 14, 2017 Authors Thomas Skybakmoen, Morgan Dhanraj Overview NSS Labs performed an independent test of
ADVANCED ENDPOINT PROTECTION TEST REPORT SentinelOne Endpoint Protection Platform v1.8.3#31 FEBRUARY 14, 2017 Authors Thomas Skybakmoen, Morgan Dhanraj Overview NSS Labs performed an independent test of
SafeNet Authentication Client
 SafeNet Authentication Client Compatibility Guide All information herein is either public information or is the property of and owned solely by Gemalto. and/or its subsidiaries who shall have and keep
SafeNet Authentication Client Compatibility Guide All information herein is either public information or is the property of and owned solely by Gemalto. and/or its subsidiaries who shall have and keep
MERIDIANSOUNDINGBOARD.COM TERMS AND CONDITIONS
 MERIDIANSOUNDINGBOARD.COM TERMS AND CONDITIONS Introduction This document sets forth the terms and conditions ("Terms and Conditions") governing your use of the MeridianHealth.com Web site ("Web Site")
MERIDIANSOUNDINGBOARD.COM TERMS AND CONDITIONS Introduction This document sets forth the terms and conditions ("Terms and Conditions") governing your use of the MeridianHealth.com Web site ("Web Site")
Oracle Binary Code License Agreement for Java Secure Sockets Extension for Connected Device Configuration 1.0.2
 Oracle Binary Code License Agreement for Java Secure Sockets Extension 1.0.3 for Connected Device Configuration 1.0.2 ORACLE AMERICA, INC. ("ORACLE"), FOR AND ON BEHALF OF ITSELF AND ITS SUBSIDIARIES AND
Oracle Binary Code License Agreement for Java Secure Sockets Extension 1.0.3 for Connected Device Configuration 1.0.2 ORACLE AMERICA, INC. ("ORACLE"), FOR AND ON BEHALF OF ITSELF AND ITS SUBSIDIARIES AND
HUAWEI H30-U10. Quick Start Guide
 HUAWEI H30-U10 Quick Start Guide Dual card dual standby single pass Your phone supports only dual card dual standby single pass, which means you cannot use both SIM cards for calls or data services simultaneously.
HUAWEI H30-U10 Quick Start Guide Dual card dual standby single pass Your phone supports only dual card dual standby single pass, which means you cannot use both SIM cards for calls or data services simultaneously.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Legal notice and Privacy policy
 Legal notice and Privacy policy We appreciate your interest in us. Below you will find information of legal relevance when visiting this website. In addition, you will find our Privacy Policy, which explains
Legal notice and Privacy policy We appreciate your interest in us. Below you will find information of legal relevance when visiting this website. In addition, you will find our Privacy Policy, which explains
Operation Iron Tiger: Exploring Chinese Cyber-Espionage Attacks on United States Defense Contractors
 A TrendLabs Report Operation Iron Tiger: Exploring Chinese Cyber-Espionage Attacks on United States Defense Contractors Appendix TrendLabs Security Intelligence Blog Operation Iron Tiger is a targeted
A TrendLabs Report Operation Iron Tiger: Exploring Chinese Cyber-Espionage Attacks on United States Defense Contractors Appendix TrendLabs Security Intelligence Blog Operation Iron Tiger is a targeted
CALSTRS ONLINE AGREEMENT TERMS AND CONDITIONS
 CALSTRS ONLINE AGREEMENT TERMS AND CONDITIONS INTRODUCTION: Before the California State Teachers Retirement System (hereinafter "CalSTRS," "We," or "Us") will provide services found at mycalstrs.com (the
CALSTRS ONLINE AGREEMENT TERMS AND CONDITIONS INTRODUCTION: Before the California State Teachers Retirement System (hereinafter "CalSTRS," "We," or "Us") will provide services found at mycalstrs.com (the
Policies & Medical Disclaimer
 Policies & Medical Disclaimer Money Back Guarantee Heather Woodruff Nutrition proudly stands behind its programs. To help you feel comfortable we offer a Money-Back Guarantee* If you are not absolutely
Policies & Medical Disclaimer Money Back Guarantee Heather Woodruff Nutrition proudly stands behind its programs. To help you feel comfortable we offer a Money-Back Guarantee* If you are not absolutely
Bar Code Discovery. Administrator's Guide
 Bar Code Discovery Administrator's Guide November 2012 www.lexmark.com Contents 2 Contents Overview...3 Configuring the application...4 Configuring the application...4 Configuring Bar Code Discovery...4
Bar Code Discovery Administrator's Guide November 2012 www.lexmark.com Contents 2 Contents Overview...3 Configuring the application...4 Configuring the application...4 Configuring Bar Code Discovery...4
NOOTRY TERMS OF SERVICE
 NOOTRY TERMS OF SERVICE Nootry LLC ( Nootry ), a Delaware limited liabilities company, provides access to and use of the services, including our website, APIs, email notifications, and application (the
NOOTRY TERMS OF SERVICE Nootry LLC ( Nootry ), a Delaware limited liabilities company, provides access to and use of the services, including our website, APIs, email notifications, and application (the
2.1 Website means operated and owned by UCS Technology Services, including any page, part of element thereof;
 WEBSITE USAGE TERMS AND CONDITIONS Acceptable Usage Terms 1. Introduction 1.1 By accessing the UCS Technology Services website, web pages or any part thereof for any reason whatsoever, the User agrees
WEBSITE USAGE TERMS AND CONDITIONS Acceptable Usage Terms 1. Introduction 1.1 By accessing the UCS Technology Services website, web pages or any part thereof for any reason whatsoever, the User agrees
Entrust SSL Web Server Certificate Subscription Agreement
 Entrust SSL Web Server Certificate Subscription Agreement ATTENTION - READ CAREFULLY: THIS SUBSCRIPTION AGREEMENT (THIS "AGREEMENT") IS A LEGAL CONTRACT BETWEEN THE PERSON, ENTITY, OR ORGANIZATION NAMED
Entrust SSL Web Server Certificate Subscription Agreement ATTENTION - READ CAREFULLY: THIS SUBSCRIPTION AGREEMENT (THIS "AGREEMENT") IS A LEGAL CONTRACT BETWEEN THE PERSON, ENTITY, OR ORGANIZATION NAMED
CONSUMER EPP COMPARATIVE ANALYSIS
 CONSUMER EPP COMPARATIVE ANALYSIS Socially Engineered Malware Randy Abrams, Jayendra Pathak, Mohamed Saher, Ahmed Garhy Tested Vendors AVG, F- Secure, Kaspersky, McAfee, Microsoft, Symantec, Trend Micro
CONSUMER EPP COMPARATIVE ANALYSIS Socially Engineered Malware Randy Abrams, Jayendra Pathak, Mohamed Saher, Ahmed Garhy Tested Vendors AVG, F- Secure, Kaspersky, McAfee, Microsoft, Symantec, Trend Micro
MDVR for the Blackberry
 MDVR for the Blackberry Instructions www.openeye.net OpenEye BlackBerry MDVR Software Manual (Ver1.09) Manual Edition 30156AC SEPTEMBER 2011 2000-2011, OPENEYE All Rights Reserved. No part of this documentation
MDVR for the Blackberry Instructions www.openeye.net OpenEye BlackBerry MDVR Software Manual (Ver1.09) Manual Edition 30156AC SEPTEMBER 2011 2000-2011, OPENEYE All Rights Reserved. No part of this documentation
Class Composer General Terms of Use
 Class Composer General Terms of Use Effective Date: July 24, 2017 Welcome to Class Composer! Please continue reading to learn about the terms by which you may use our Service. If you have any questions
Class Composer General Terms of Use Effective Date: July 24, 2017 Welcome to Class Composer! Please continue reading to learn about the terms by which you may use our Service. If you have any questions
SafeNet Authentication Client
 SafeNet Authentication Client Compatibility Guide All information herein is either public information or is the property of and owned solely by Gemalto. and/or its subsidiaries who shall have and keep
SafeNet Authentication Client Compatibility Guide All information herein is either public information or is the property of and owned solely by Gemalto. and/or its subsidiaries who shall have and keep
GENUINE USB Cable set
 GENUINE USB Cable set Owner's Manual (Apple CarPlay / Android Auto mode) Thank you for purchasing a genuine Mazda accessory. Before use, be sure to thoroughly read these instructions. Please read the contents
GENUINE USB Cable set Owner's Manual (Apple CarPlay / Android Auto mode) Thank you for purchasing a genuine Mazda accessory. Before use, be sure to thoroughly read these instructions. Please read the contents
Deep Security Integration with Sumo Logic
 A Trend Micro White Paper I May 2016 Install, Integrate and Analyze» This paper is aimed at information security and solution architects looking to integrate the Trend Micro Deep Security with Sumo Logic.
A Trend Micro White Paper I May 2016 Install, Integrate and Analyze» This paper is aimed at information security and solution architects looking to integrate the Trend Micro Deep Security with Sumo Logic.
Device Operation Process Diagrams. SAP Mobile Secure rapid-deployment solution September 2014
 Device Operation Process Diagrams SP Mobile Secure rapid-deployment solution September 2014 X94 Device Operation (1/6) Remote Device Management of ios Device Types SP faria faria dministrator Remote Lock
Device Operation Process Diagrams SP Mobile Secure rapid-deployment solution September 2014 X94 Device Operation (1/6) Remote Device Management of ios Device Types SP faria faria dministrator Remote Lock
Tisio CE Release Notes
 Tisio CE Release Notes Copyright Copyright 2005, 2006, 2007 and 2008 by ThinPATH Systems, Inc. The information contained in this document is subject to change without notice. ThinPATH Systems, Inc. shall
Tisio CE Release Notes Copyright Copyright 2005, 2006, 2007 and 2008 by ThinPATH Systems, Inc. The information contained in this document is subject to change without notice. ThinPATH Systems, Inc. shall
Player Loyalty Program Terms & Conditions
 Player Loyalty Program Terms & Conditions Important: This is a legal agreement between the New Mexico Lottery Authority ("NMLA") and the user ("you" or "user"). Please read the following terms carefully.
Player Loyalty Program Terms & Conditions Important: This is a legal agreement between the New Mexico Lottery Authority ("NMLA") and the user ("you" or "user"). Please read the following terms carefully.
BCDC 2E, 2012 (On-line Bidding Document for Stipulated Price Bidding)
 BCDC 2E, 2012 (On-line Bidding Document for Stipulated Price Bidding) CLAUSE 13 ON-LINE BIDDING 13.1 ON-LINE BIDDING.1 Definitions: Owner means the party and/or their agent designated to receive on-line
BCDC 2E, 2012 (On-line Bidding Document for Stipulated Price Bidding) CLAUSE 13 ON-LINE BIDDING 13.1 ON-LINE BIDDING.1 Definitions: Owner means the party and/or their agent designated to receive on-line
TERMS & CONDITIONS PLEASE READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THE SITE
 TERMS & CONDITIONS PLEASE READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THE SITE 1. General The term PPS refers to: Professional Provident Society Holdings Trust, (The Holding Trust); Professional
TERMS & CONDITIONS PLEASE READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THE SITE 1. General The term PPS refers to: Professional Provident Society Holdings Trust, (The Holding Trust); Professional
Refund Policy. About us. Use of Site. Disclaimer of Warranty 1/6
 Refund Policy draslcaribbean.com/index.php/refund-policy Terms and Conditions (including but not limited to the Description of Services offered, Refund/Return Policy, Merchant contact information, Export
Refund Policy draslcaribbean.com/index.php/refund-policy Terms and Conditions (including but not limited to the Description of Services offered, Refund/Return Policy, Merchant contact information, Export
InterScan Messaging Security Virtual Appliance (IMSVA) Sender Policy Framework. Best practice guide for versions 9.0 and 9.1
 InterScan Messaging Security Virtual Appliance (IMSVA) Sender Policy Framework Best practice guide for versions 9.0 and 9.1 1. Introduction Sender Policy Framework (SPF) is an open standard which provides
InterScan Messaging Security Virtual Appliance (IMSVA) Sender Policy Framework Best practice guide for versions 9.0 and 9.1 1. Introduction Sender Policy Framework (SPF) is an open standard which provides
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Advanced Threat Defense Certification Testing Report. Trend Micro Incorporated Trend Micro Deep Discovery Inspector
 Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Advanced Threat Defense Certification Testing Report Trend Micro Deep Discovery Inspector ICSA Labs Advanced Threat Defense July 12, 2016 Prepared by ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg,
Raspberry Pi shield board
 Raspberry Pi shield board Table of Contents Hardware Guide 1 1 Hardware Requirements 1 (1) PACKAGE CONTENTS 1 (2) Feature 1 2 Hardware Guide 2 (1) HARDWARE REQUIREMENTS 2 (2) HARDWARE CONNECTION 3 (3)
Raspberry Pi shield board Table of Contents Hardware Guide 1 1 Hardware Requirements 1 (1) PACKAGE CONTENTS 1 (2) Feature 1 2 Hardware Guide 2 (1) HARDWARE REQUIREMENTS 2 (2) HARDWARE CONNECTION 3 (3)
TERMS OF USE Effective Date: January 1, 2015 To review material modifications and their effective dates scroll to the bottom of the page. 1.Parties.
 TERMS OF USE Effective Date: January 1, 2015 To review material modifications and their effective dates scroll to the bottom of the page. 1.Parties. The parties to these Terms of Use are you, and the owner
TERMS OF USE Effective Date: January 1, 2015 To review material modifications and their effective dates scroll to the bottom of the page. 1.Parties. The parties to these Terms of Use are you, and the owner
Copyrights and Privacy Statement
 Copyrights and Privacy Statement Jesse James Hardscaping Authorization of Use Jesse James Hardscaping hereby authorizes any person to access this Website for informational purposes only. Jesse James Hardscaping
Copyrights and Privacy Statement Jesse James Hardscaping Authorization of Use Jesse James Hardscaping hereby authorizes any person to access this Website for informational purposes only. Jesse James Hardscaping
UX402 SAP SAPUI5 Development
 UX402 SAP SAPUI5 Development. COURSE OUTLINE Course Version: 03 Course Duration: SAP Copyrights and Trademarks 2018 SAP SE or an SAP affiliate company. All rights reserved. No part of this publication
UX402 SAP SAPUI5 Development. COURSE OUTLINE Course Version: 03 Course Duration: SAP Copyrights and Trademarks 2018 SAP SE or an SAP affiliate company. All rights reserved. No part of this publication
Automatic Classifying of Mac OS X Samples. Spencer Hsieh, Pin Wu and Haoping Liu Trend Micro Inc., Taiwan
 Automatic Classifying of Mac OS X Samples Spencer Hsieh, Pin Wu and Haoping Liu Trend Micro Inc., Taiwan TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational
Automatic Classifying of Mac OS X Samples Spencer Hsieh, Pin Wu and Haoping Liu Trend Micro Inc., Taiwan TREND MICRO LEGAL DISCLAIMER The information provided herein is for general information and educational
Yellow Intelligent User Guide A Guide To Downloading SDFI Secure Files
 Yellow Intelligent User Guide A Guide To Downloading SDFI Secure Files * This Guide Is Not For Independent Sale * May 3 rd, 2018 SDFI-TeleMedicine LLC 806 Buchanan Blvd STE 115-299 Boulder City, NV 89005
Yellow Intelligent User Guide A Guide To Downloading SDFI Secure Files * This Guide Is Not For Independent Sale * May 3 rd, 2018 SDFI-TeleMedicine LLC 806 Buchanan Blvd STE 115-299 Boulder City, NV 89005
Complementary Demo Guide
 Complementary Demo Guide SAP Business ByDesign SAP Business ByDesign Global October 23, 2017 1 Table of Content 1 About this Document... 3 1.1 Purpose... 3 1.2 Demo Business Context... 3 1.3 Prerequisites...
Complementary Demo Guide SAP Business ByDesign SAP Business ByDesign Global October 23, 2017 1 Table of Content 1 About this Document... 3 1.1 Purpose... 3 1.2 Demo Business Context... 3 1.3 Prerequisites...
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Specifications
 Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Specifications Export Controls Export laws and regulations of the United States and any other
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Specifications Export Controls Export laws and regulations of the United States and any other
SafeNet Authentication Client
 SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto and/or its subsidiaries who shall have and keep the
SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto and/or its subsidiaries who shall have and keep the
Terms and Conditions For Online-Payments
 Terms and Conditions For Online-Payments The Terms and Conditions contained herein shall apply to any person ( User ) using the services of Ghaziabad Nagar Nigam for making Tax payments through an online
Terms and Conditions For Online-Payments The Terms and Conditions contained herein shall apply to any person ( User ) using the services of Ghaziabad Nagar Nigam for making Tax payments through an online
SAP SMS 365 SAP Messaging Proxy 365 Product Description August 2016 Version 1.0
 SAP SMS 365 SAP Messaging Proxy 365 Product Description August 2016 Version 1.0 TABLE OF CONTENTS 1 INTRODUCTION...3 2 BENEFITS...4 3 FUNCTIONAL DESCRIPTION...5 4 MESSAGE CLASSIFICATION...6 5 ARCHITECTURE...7
SAP SMS 365 SAP Messaging Proxy 365 Product Description August 2016 Version 1.0 TABLE OF CONTENTS 1 INTRODUCTION...3 2 BENEFITS...4 3 FUNCTIONAL DESCRIPTION...5 4 MESSAGE CLASSIFICATION...6 5 ARCHITECTURE...7
Terms Of Use AGREEMENT BETWEEN USER AND DRAKE MODIFICATION OF THESE TERMS OF USE LINKS TO THIRD PARTY WEB SITES USE OF COOKIES
 Terms Of Use AGREEMENT BETWEEN USER AND DRAKE This website and other related websites and mobile applications (collectively referred to as "Sites") comprise various web pages and services operated by Drake
Terms Of Use AGREEMENT BETWEEN USER AND DRAKE This website and other related websites and mobile applications (collectively referred to as "Sites") comprise various web pages and services operated by Drake
The following Terms and Conditions apply to the use of this Website, as well as all transactions conducted through the site.
 The following Terms and Conditions apply to the use of this Website, as well as all transactions conducted through the site. Copyright All content appearing on this Web site is the property of: Osprey
The following Terms and Conditions apply to the use of this Website, as well as all transactions conducted through the site. Copyright All content appearing on this Web site is the property of: Osprey
SafeNet Authentication Client
 SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV and/or its subsidiaries who shall have and keep
SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV and/or its subsidiaries who shall have and keep
RTTL Certification Test - March Language: English. March Last Revision: 8 th April
 RTTL Certification Test March 2016 Language: English March 2016 Last Revision: 8 th April 2016-1 - Introduction 1 st AMTSO Real Time Threat List (RTTL) based certification test What is the RTTL? The Real-Time
RTTL Certification Test March 2016 Language: English March 2016 Last Revision: 8 th April 2016-1 - Introduction 1 st AMTSO Real Time Threat List (RTTL) based certification test What is the RTTL? The Real-Time
CA File Master Plus. Release Notes. Version
 CA File Master Plus Release Notes Version 9.0.00 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for
CA File Master Plus Release Notes Version 9.0.00 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is for
HP JetAdvantage Solutions
 Brief HP JetAdvantage Solutions Set office-wide productivity in motion Business Workflow and Printing Solutions HP JetAdvantage Management Solutions HP JetAdvantage Security Solutions HP JetAdvantage Mobile
Brief HP JetAdvantage Solutions Set office-wide productivity in motion Business Workflow and Printing Solutions HP JetAdvantage Management Solutions HP JetAdvantage Security Solutions HP JetAdvantage Mobile
Who s Really Attacking Your ICS Equipment?
 Trend Micro Incorporated Research Paper 2013 Who s Really Attacking Your ICS Equipment? By: Kyle Wilhoit LEGAL DISCLAIMER The information provided herein is for general information and educational purposes
Trend Micro Incorporated Research Paper 2013 Who s Really Attacking Your ICS Equipment? By: Kyle Wilhoit LEGAL DISCLAIMER The information provided herein is for general information and educational purposes
Protecting Your Digital World
 Protecting Your Digital World C O R P O R A T E O V E R V I E W With revenues of more than $105 Billion, cybercrime generates more revenue than the illegal drug trade. Source: U.S. Treasury, reported by
Protecting Your Digital World C O R P O R A T E O V E R V I E W With revenues of more than $105 Billion, cybercrime generates more revenue than the illegal drug trade. Source: U.S. Treasury, reported by
Native route discovery algorithm
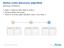 Native route discovery algorithm Starting conditions Node 1 needs to send data to node Routing tables are empty There is no direct path between node 1 and node Destination Next hop Destination Next hop
Native route discovery algorithm Starting conditions Node 1 needs to send data to node Routing tables are empty There is no direct path between node 1 and node Destination Next hop Destination Next hop
Certified Solution for Milestone
 Certified Solution for Milestone Z-series Workstations Table of Contents Executive Summary... 4 Certified Products... 4 HP Z2 Mini Quick Specs... 4 Enabling Intel Quick Synch... 5 Use Cases... 5 Workstation
Certified Solution for Milestone Z-series Workstations Table of Contents Executive Summary... 4 Certified Products... 4 HP Z2 Mini Quick Specs... 4 Enabling Intel Quick Synch... 5 Use Cases... 5 Workstation
ESS Utility Android App User Guide
 [01.2017] ESS Utility Android App User Guide 1VV0301574 Rev. 0 2018-12-21 Mod.0818 2017-01 Rev.0 SPECIFICATIONS ARE SUBJECT TO CHANGE WITHOUT NOTICE NOTICE While reasonable efforts have been made to assure
[01.2017] ESS Utility Android App User Guide 1VV0301574 Rev. 0 2018-12-21 Mod.0818 2017-01 Rev.0 SPECIFICATIONS ARE SUBJECT TO CHANGE WITHOUT NOTICE NOTICE While reasonable efforts have been made to assure
AhnLab Software License Agreement
 AhnLab Software License Agreement IMPORTANT - READ CAREFULLY BEFORE USING THE SOFTWARE. This AhnLab Software License Agreement (this "Agreement") is a legal agreement by and between you and AhnLab, Inc.
AhnLab Software License Agreement IMPORTANT - READ CAREFULLY BEFORE USING THE SOFTWARE. This AhnLab Software License Agreement (this "Agreement") is a legal agreement by and between you and AhnLab, Inc.
Online Localization Service
 DEVELOPER EXPRESS INC DEVEXPRESS Copyright (C) 2011-2017 Developer Express Inc. IMPORTANT- READ CAREFULLY: This DEVELOPER EXPRESS INC ("DEVEXPRESS") End-User License Agreement ("EULA") is a legal agreement
DEVELOPER EXPRESS INC DEVEXPRESS Copyright (C) 2011-2017 Developer Express Inc. IMPORTANT- READ CAREFULLY: This DEVELOPER EXPRESS INC ("DEVEXPRESS") End-User License Agreement ("EULA") is a legal agreement
End User License Agreement
 End User License Agreement Kyocera International, Inc. ( Kyocera ) End User License Agreement. CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS ( AGREEMENT ) BEFORE USING OR OTHERWISE ACCESSING THE SOFTWARE
End User License Agreement Kyocera International, Inc. ( Kyocera ) End User License Agreement. CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS ( AGREEMENT ) BEFORE USING OR OTHERWISE ACCESSING THE SOFTWARE
SafeNet Authentication Client
 SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have and keep
SafeNet Authentication Client Integration Guide All information herein is either public information or is the property of and owned solely by Gemalto NV. and/or its subsidiaries who shall have and keep
FAQs Data Sources SAP Hybris Cloud for Customer PUBLIC
 FAQs Data Sources SAP Hybris Cloud for Customer PUBLIC TABLE OF CONTENTS FAQS DATA SOURCES... 3 1. When I try to execute a custom report, throws an error: Report cannot be opened; report an incident, See
FAQs Data Sources SAP Hybris Cloud for Customer PUBLIC TABLE OF CONTENTS FAQS DATA SOURCES... 3 1. When I try to execute a custom report, throws an error: Report cannot be opened; report an incident, See
How to Secure Your Cloud with...a Cloud?
 A New Era of Thinking How to Secure Your Cloud with...a Cloud? Eitan Worcel Offering Manager - Application Security on Cloud IBM Security 1 2016 IBM Corporation 1 A New Era of Thinking Agenda IBM Cloud
A New Era of Thinking How to Secure Your Cloud with...a Cloud? Eitan Worcel Offering Manager - Application Security on Cloud IBM Security 1 2016 IBM Corporation 1 A New Era of Thinking Agenda IBM Cloud
HA100 SAP HANA Introduction
 HA100 SAP HANA Introduction. COURSE OUTLINE Course Version: 13 Course Duration: 2 Day(s) SAP Copyrights and Trademarks 2017 SAP SE or an SAP affiliate company. All rights reserved. No part of this publication
HA100 SAP HANA Introduction. COURSE OUTLINE Course Version: 13 Course Duration: 2 Day(s) SAP Copyrights and Trademarks 2017 SAP SE or an SAP affiliate company. All rights reserved. No part of this publication
Integration Guide. BlackBerry Workspaces. Version 1.0
 Integration Guide BlackBerry Workspaces Version 1.0 Published: 2017-12-27 SWD-20171227025930338 Contents Overview... 4 Okta... 5 Add BlackBerry Workspaces to your Okta account...5 Configure BlackBerry
Integration Guide BlackBerry Workspaces Version 1.0 Published: 2017-12-27 SWD-20171227025930338 Contents Overview... 4 Okta... 5 Add BlackBerry Workspaces to your Okta account...5 Configure BlackBerry
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Software Development Kits
 Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Software Development Kits Export Controls Export laws and regulations of the United States
Oracle Technology Network Developer License Terms for Java Card Classic Edition and Java Card Connected Edition Software Development Kits Export Controls Export laws and regulations of the United States
TippingPoint Intrusion Prevention System Release Notes
 TippingPoint Intrusion Prevention System Release Notes Version 3.6.7 December 2017 This document contains release-specific information for the TippingPoint Intrusion Prevention System (IPS) TippingPoint
TippingPoint Intrusion Prevention System Release Notes Version 3.6.7 December 2017 This document contains release-specific information for the TippingPoint Intrusion Prevention System (IPS) TippingPoint
Using Joinup as a catalogue for interoperability solutions. March 2014 PwC EU Services
 Using Joinup as a catalogue for interoperability solutions March 2014 PwC EU Services Learning objectives By the end of this module, you will have an understanding of: What is Joinup and the Interoperability
Using Joinup as a catalogue for interoperability solutions March 2014 PwC EU Services Learning objectives By the end of this module, you will have an understanding of: What is Joinup and the Interoperability
