Step [2]: Hit on Create icon and Choose the "Create macos Profile" from the drop-down menu
|
|
|
- Winifred Webster
- 5 years ago
- Views:
Transcription
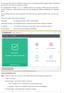
1 This guide allows a user to configure Antivirus Settings through a profile. The settings include all low-level details to be parameterized from ITSM hence the Realtime Scan (at the time of threats encountered), Scans (when the user invoke scan explicitly) and Exclusions (excludes specific paths, applications, and built-in groups) are executed as per the user conditions and expectations. Step [1]: Go to ITSM -> CONFIGURATION TEMPLATES > Profiles Step [2]: Hit on Create icon and Choose the "Create macos Profile" from the drop-down menu Step [3]: Fill the form with Name, Description of the profile and Click Create button Step [4]: Hit on "Add Profile Section" icon and Choose Antivirus from the drop-down menu Step [5]: In the antivirus tab, hit on the Antivirus option. Some parameters are available to complete the 1
2 setup such as Scanner Settings, Scan Profiles, and Scheduled scans. Step [6]: Let us have a look at following parameters available under the scanner setting such as Real-time scanning, Manual Scanning, Scheduled Scanning, and Exclusions. Realtime Scanning: Realtime scanning helps you to check files in real time when they are created, opened or copied. Options with the explanation: Realtime Scanning- It allows you to enable or disable realtime scanning. It has two option On access: It will perform the high-level on-access scanning and protection. Disabled: If it is disabled means it does not perform any scanning and the threats cannot be detected if any harm occurs in the endpoint. Do not scan files large than (MB)- Number of files size within the limit is set to be scanned on access. (For example, If the file size is 20 means it only scanned the within 20MB files) Keep an alert on the screen for (seconds)- Number of seconds the alert displayed on the screen. Automatically quarantine threats found during scanning- If it is enabled, all detected threats will be moved to quarantine at the device for your later scrutiny. Automatically update virus database- If it is enabled, Comodo Antivirus will check and download the latest virus database updates. Manual Scanning: It allows you to set the parameters that will be implemented when you run an 'On Demand' scan. 2
3 Options with the explanation: Do not scan files large than (MB)- Number of files size within the limit is set to be scanned on-demand scanning. Scan archives files (e.g. *.zip, *.rar)- It will scan all archive files in your endpoints such as RAR, WinRAR, ZIP, WinZIP ARJ, WinARJ and CAB archives. Automatically quarantine threats found during scanning-if it is enabled, quarantine threat is automatically found during an on-demand scan. Automatically update virus database before scanning-it will automatically update virus database before ondemand scan occurs. Scheduled Scanning: It allows you to set the parameters that will scan as per schedules set under the 'Scheduled Scans' tab. Options with the explanation: The following option is same as manual scanning such as Do not scan files large than (MB), Scan archives files (e.g. *.zip, *.rar), Automatically quarantine threats found during scanning and Automatically update virus database before scanning. Show Progress option- If It is enabled, the progress bar is displayed whenever a scheduled scan is run at the device. Step [8]: Select the Exclusions tab and Click Add button. Enter the Path and hit on OK button - To add more paths, repeat the steps Step [9]: Hit on "Scan profiles" from Antivirus tab. The list of pre-defined scan profiles will be displayed. Note: You can select the scan profiles while creating scan scheduled scans and while running on-demand 3
4 scans on the device applied with the profile. If you want to add the scan profile, Hit on "Add Scan Profile" from Scan Profiles option. Fill the form with Name (i.e My custom profile) Click 'Add Path' to add the locations to be scanned as per the My custom profile. Enter the path of the location to be scanned as per the custom profile and click 'Ok'. The path will be added to the profile. To add more paths, repeat the steps The profile will be added to the list of 'Scan Profiles'. 4
5 Step [10]: Hit on "Scheduled Scans" from Antivirus tab. The list of pre-defined Scheduled Scans will be displayed. If you want to add the Scheduled Scans, Hit on "Add Scheduled scan" from "Scheduled Scans option. The 'Add Scheduled Scan' dialog will appear. Enter the required details and Click 'OK' Name - Fill the form with Name(i.e Daily scan on application folder) 5
6 Profile- Choose the pre-defined or custom scan profile to be applied for the scheduled scan. The scan profiles included under the 'Scan Profiles' tab will be available in the drop-down. Days of week- Select the day(s) of the week on which the scan has to run. Time- Set the time at which the scans are to run on the selected days. Step [11]: The scheduled scan will be added to the list. To edit the settings of a scheduled scan, click the pencil icon beside it To remove a scheduled scan, select it and click 'Remove Scheduled Scan' Click 'Save' Step [12]: Once the information is saved then click Profiles menu and Check whether the name of the profile is available on the table. 6
Comodo Antivirus Software Version 2.1
 Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.2
 Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.0
 Comodo Antivirus Software Version 2.0 User Guide Guide Version 2.0.010215 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.0 User Guide Guide Version 2.0.010215 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Client - Security for Linux Software Version 2.2
 Comodo Client - Security for Linux Software Version 2.2 User Guide Guide Version 2.2.091818 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Client
Comodo Client - Security for Linux Software Version 2.2 User Guide Guide Version 2.2.091818 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Client
STEP 3 : Please select profile associated with device or group which requires exclusion.
 Experience the benefits of Endpoint Manager which encounters Exclusion based on File group by adding multiple file path as a Group. User can add as many rules as possible for excluding the application
Experience the benefits of Endpoint Manager which encounters Exclusion based on File group by adding multiple file path as a Group. User can add as many rules as possible for excluding the application
Trend Micro OfficeScan Client User Guide
 Trend Micro OfficeScan Client User Guide Overview The purpose of this document is to provide users with information on the Trend Micro OfficeScan antivirus client. OfficeScan is the new anti-virus/anti-malware
Trend Micro OfficeScan Client User Guide Overview The purpose of this document is to provide users with information on the Trend Micro OfficeScan antivirus client. OfficeScan is the new anti-virus/anti-malware
Even a non-technical user can even operate it with ease.the user can do any task in CCS with just a few clicks.
 The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
Quick Heal Microsoft Exchange Protection
 Quick Heal Microsoft Exchange Protection Intuitive. Effective. Comprehensive. Feature List Web-based console makes administrative management easy and simple. Comprehensive and rapid scanning of emails
Quick Heal Microsoft Exchange Protection Intuitive. Effective. Comprehensive. Feature List Web-based console makes administrative management easy and simple. Comprehensive and rapid scanning of emails
How to Create a *.vpn File
 You can import VPN profiles and Barracuda Personal Licenses to the Barracuda Network Access Client and the Barracuda VPN Client using configuration files with the suffix *.vpn that can be configured and
You can import VPN profiles and Barracuda Personal Licenses to the Barracuda Network Access Client and the Barracuda VPN Client using configuration files with the suffix *.vpn that can be configured and
ABF Software Issues Caused by Anti-Virus Programs
 ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
Comodo Antivirus for Linux Software Version 1.0
 Comodo Antivirus for Linux Software Version 1.0 User Guide Guide Version 1.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus for
Comodo Antivirus for Linux Software Version 1.0 User Guide Guide Version 1.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus for
Comodo. Cloud Antivirus. User Guide. Software Version Guide Version
 Comodo Cloud Antivirus Software Version 1.11 User Guide Guide Version 1.11.050317 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Comodo Cloud Antivirus Software Version 1.11 User Guide Guide Version 1.11.050317 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Administration Guide. . All right reserved. For more information about Specops Deploy and other Specops products, visit
 . All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
. All right reserved. For more information about Specops Deploy and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Deploy is a trademark owned by Specops Software. All
Steps. Step [1]: Click Download Bulk Enrolment Package Icon. (OR) Go to ITSM > Bulk Installation Package
![Steps. Step [1]: Click Download Bulk Enrolment Package Icon. (OR) Go to ITSM > Bulk Installation Package Steps. Step [1]: Click Download Bulk Enrolment Package Icon. (OR) Go to ITSM > Bulk Installation Package](/thumbs/75/72346319.jpg) Steps Step [1]: Click Download Bulk Enrolment Package Icon (OR) Go to ITSM > Bulk Installation Package Step [2]: Fill the form and Download the required package 1 1. User - Select the user of your company
Steps Step [1]: Click Download Bulk Enrolment Package Icon (OR) Go to ITSM > Bulk Installation Package Step [2]: Fill the form and Download the required package 1 1. User - Select the user of your company
AVG File Server. User Manual. Document revision ( )
 AVG File Server User Manual Document revision 2015.07 (5.2.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents
AVG File Server User Manual Document revision 2015.07 (5.2.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents
Comodo Comodo Dome Antispam MSP Software Version 2.12
 Comodo Comodo Dome Antispam MSP Software Version 2.12 User Guide Guide Version 2.12.111517 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Dome
Comodo Comodo Dome Antispam MSP Software Version 2.12 User Guide Guide Version 2.12.111517 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Dome
Comodo Antispam Gateway Software Version 2.12
 Comodo Antispam Gateway Software Version 2.12 User Guide Guide Version 2.12.112017 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Comodo Antispam Gateway Software Version 2.12 User Guide Guide Version 2.12.112017 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Installation Manual. and User Guide
 Installation Manual and User Guide ESET Mobile Antivirus For Windows Mobile Copyright 2009 by ESET, spol. s r. o. ESET Mobile Antivirus For Windows Mobile was developed by ESET, spol. s r.o. For more information
Installation Manual and User Guide ESET Mobile Antivirus For Windows Mobile Copyright 2009 by ESET, spol. s r. o. ESET Mobile Antivirus For Windows Mobile was developed by ESET, spol. s r.o. For more information
Comodo Antispam Gateway Software Version 2.1
 Comodo Antispam Gateway Software Version 2.1 User Guide Guide Version 2.1.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...
Comodo Antispam Gateway Software Version 2.1 User Guide Guide Version 2.1.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...
Comodo Rescue Disk Software Version 1.1
 Comodo Rescue Disk Software Version 1.1 User Guide Guide Version 1.1.070912 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Introduction to Comodo Rescue Disk...
Comodo Rescue Disk Software Version 1.1 User Guide Guide Version 1.1.070912 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Introduction to Comodo Rescue Disk...
MOVE AntiVirus page-level reference
 McAfee MOVE AntiVirus 4.7.0 Interface Reference Guide (McAfee epolicy Orchestrator) MOVE AntiVirus page-level reference General page (Configuration tab) Allows you to configure your McAfee epo details,
McAfee MOVE AntiVirus 4.7.0 Interface Reference Guide (McAfee epolicy Orchestrator) MOVE AntiVirus page-level reference General page (Configuration tab) Allows you to configure your McAfee epo details,
SecureAPlus User Guide. Version 3.4
 SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
How to Configure Anti-Virus to Permit SoftMiner Binaries
 How to Configure Anti-Virus to Permit Binaries If you trust a file, file type, folder, or a process that anti-virus has detected as malicious, you can stop anti-virus from alerting you or blocking the
How to Configure Anti-Virus to Permit Binaries If you trust a file, file type, folder, or a process that anti-virus has detected as malicious, you can stop anti-virus from alerting you or blocking the
Guardian Internet Security User Guide
 Guardian Internet Security User Guide Guardian Internet Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of
Guardian Internet Security User Guide Guardian Internet Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of
Seqrite Antivirus Server Edition
 Seqrite Antivirus Server Edition User Guide www.seqrite.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication may be reproduced,
Seqrite Antivirus Server Edition User Guide www.seqrite.com Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication may be reproduced,
Table of Contents. Page 1
 Table of Contents Google My Business Plugin... 2 Installation Is Not Required... 2 Generate GMB Unclaimed Data... 2 Reviewing The Unclaimed Listings... 2 Antivirus Applications... 3 AVG Antivirus... 3
Table of Contents Google My Business Plugin... 2 Installation Is Not Required... 2 Generate GMB Unclaimed Data... 2 Reviewing The Unclaimed Listings... 2 Antivirus Applications... 3 AVG Antivirus... 3
Kaspersky PURE 2.0. Exclusions
 Exclusions Content Exclusions... 2 Trusted zone... 2 Creating the list of trusted applications... 3 Creating exclusion rules... 5 1 10 Exclusions Trusted zone Trusted zone is a list of objects created
Exclusions Content Exclusions... 2 Trusted zone... 2 Creating the list of trusted applications... 3 Creating exclusion rules... 5 1 10 Exclusions Trusted zone Trusted zone is a list of objects created
Comodo. Cloud Antivirus. User Guide. Software Version Guide Version
 Comodo Cloud Antivirus Software Version 1.14 User Guide Guide Version 1.14.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Comodo Cloud Antivirus Software Version 1.14 User Guide Guide Version 1.14.111717 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA. Technical Setup and User Guide
 ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA Technical Setup and User Guide ESET REMOTE ADMINISTRATOR PLUG-INFOR KASEYA Copyright 2014 by ESET, spol. s r.o. ESET REMOTE ADMINISTRATOR Plug-in FOR KASEYA
ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA Technical Setup and User Guide ESET REMOTE ADMINISTRATOR PLUG-INFOR KASEYA Copyright 2014 by ESET, spol. s r.o. ESET REMOTE ADMINISTRATOR Plug-in FOR KASEYA
ESET Mobile Security for Windows Mobile. Installation Manual and User Guide - Public Beta
 ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
Endpoint Security Manager
 Comodo Endpoint Security Manager Software Version 1.6 CIS Configuration Editor Version 1.6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction
Comodo Endpoint Security Manager Software Version 1.6 CIS Configuration Editor Version 1.6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
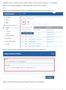 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
User Guide. Version R93. English
 Anti-Malware User Guide Version R93 English March 17, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS
Anti-Malware User Guide Version R93 English March 17, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS
Home page. Set Do Not Disturb. Set call forwarding
 Home page The Home page appears immediately after users log in to Cisco Unified CM User Options. It can also be accessed by clicking Home in the Toolbar. The Home page contains general settings. The Home
Home page The Home page appears immediately after users log in to Cisco Unified CM User Options. It can also be accessed by clicking Home in the Toolbar. The Home page contains general settings. The Home
ESET ENDPOINT SECURITY FOR ANDROID
 ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Endpoint Security 1.1 Installation...3
ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Endpoint Security 1.1 Installation...3
Kaseya 2. User Guide. Version 7.0. English
 Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Kaseya 2 AntiMalware User Guide Version 7.0 English January 6, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as
Sophos Anti-Virus standalone startup guide. For Windows and Mac OS X
 Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Comodo System Cleaner
 Comodo System Cleaner Version 3.0 Version 3.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo SystemCleaner Introduction... 3 1.1.System Requirements...5
Comodo System Cleaner Version 3.0 Version 3.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo SystemCleaner Introduction... 3 1.1.System Requirements...5
User Guide. Version R95. English
 Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
Anti-Malware (Classic) User Guide Version R95 English July 20, 2017 Copyright Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
CounterACT Check Point Threat Prevention Module
 CounterACT Check Point Threat Prevention Module Version 1.0.0 Table of Contents About the Check Point Threat Prevention Integration... 4 Use Cases... 4 Additional Check Point Threat Prevention Documentation...
CounterACT Check Point Threat Prevention Module Version 1.0.0 Table of Contents About the Check Point Threat Prevention Integration... 4 Use Cases... 4 Additional Check Point Threat Prevention Documentation...
Integrate Viper business antivirus EventTracker Enterprise
 Integrate Viper business antivirus EventTracker Enterprise Publication Date: June 2, 2016 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
Integrate Viper business antivirus EventTracker Enterprise Publication Date: June 2, 2016 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
How to install Internet Security for Android app
 How to install Internet Security for Android app 1. Go to Google Play Store app. 2. In the dialog window enter Kaspersky Mobile Antivirus: Web Security & AppLock. Tap INSTALL to allow the app to install
How to install Internet Security for Android app 1. Go to Google Play Store app. 2. In the dialog window enter Kaspersky Mobile Antivirus: Web Security & AppLock. Tap INSTALL to allow the app to install
Install Kaspersky Endpoint Security for Mac Version b (This user guide is applicable to Mac OS X 10.9 macos )
 Install Kaspersky Endpoint Security for Mac Version 10.2.1.319b (This user guide is applicable to Mac OS X 10.9 macos 10.14.) Contents A. Download Kaspersky Endpoint Security 10 for Mac... 1 B. Install
Install Kaspersky Endpoint Security for Mac Version 10.2.1.319b (This user guide is applicable to Mac OS X 10.9 macos 10.14.) Contents A. Download Kaspersky Endpoint Security 10 for Mac... 1 B. Install
Guardian NetSecure User Guide
 Guardian NetSecure User Guide Guardian NetSecure http://www.guardianav.co.in Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
Guardian NetSecure User Guide Guardian NetSecure http://www.guardianav.co.in Copyright & License Information Copyright 2017 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
ForeScout Extended Module for Symantec Endpoint Protection
 ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
ForeScout Extended Module for Symantec Endpoint Protection Version 1.0.0 Table of Contents About the Symantec Endpoint Protection Integration... 4 Use Cases... 4 Additional Symantec Endpoint Protection
Copyright 2018 Lepide Software Private Limited. All rights reserved.
 Copyright 2018 Lepide Software Private Limited. All rights reserved. Lepide Software Private Limited, Kernel, accompanied user manual and documentation are copyright of Lepide Software Private Limited,
Copyright 2018 Lepide Software Private Limited. All rights reserved. Lepide Software Private Limited, Kernel, accompanied user manual and documentation are copyright of Lepide Software Private Limited,
Comodo Antispam Gateway Software Version 2.11
 Comodo Antispam Gateway Software Version 2.11 User Guide Guide Version 2.11.041917 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Comodo Antispam Gateway Software Version 2.11 User Guide Guide Version 2.11.041917 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 Table of Contents 1 Introduction to Comodo Antispam Gateway...3
Using Antivirus Software in an Interplay Environment
 Using Antivirus Software in an Interplay Environment Support for Symantec Endpoint v12.1 Overview Avid Interplay v2.x supports the following components of Symantec Endpoint v12.1: Antivirus Antispyware
Using Antivirus Software in an Interplay Environment Support for Symantec Endpoint v12.1 Overview Avid Interplay v2.x supports the following components of Symantec Endpoint v12.1: Antivirus Antispyware
Anti-virus SCEP and Windows Defender. Common symptoms of an infection. How to Open SCEP or Windows Defender
 Anti-virus SCEP and Windows Defender The University of Aberdeen uses System Center Endpoint Protection software (SCEP) and Windows Defender to protect servers and networked Windows PCs against viruses,
Anti-virus SCEP and Windows Defender The University of Aberdeen uses System Center Endpoint Protection software (SCEP) and Windows Defender to protect servers and networked Windows PCs against viruses,
User Manual. www. K7Computing.com
 User Manual About the Admin Console The Admin Console is a centralized web-based management console. The web console is accessible through any modern web browser from any computer on the network and you
User Manual About the Admin Console The Admin Console is a centralized web-based management console. The web console is accessible through any modern web browser from any computer on the network and you
AntiVirus 8.5 Update 2. User Guide
 AntiVirus 8.5 Update 2 User Guide Notices Version Information Ivanti Endpoint Security: AntiVirus User Guide - Ivanti Endpoint Security: AntiVirus Version 8.5 Update 2 - Published: Apr 2018 Document Number:
AntiVirus 8.5 Update 2 User Guide Notices Version Information Ivanti Endpoint Security: AntiVirus User Guide - Ivanti Endpoint Security: AntiVirus Version 8.5 Update 2 - Published: Apr 2018 Document Number:
Avira Free Mac Security Version HowTo
 Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Sophos Anti-Virus for NetApp Storage Systems
 Sophos Anti-Virus for NetApp Storage Systems user guide Product Version: 3.0 Contents About this guide... 1 About Sophos Anti-Virus for NetApp Storage Systems...2 System requirements... 4 Before you install
Sophos Anti-Virus for NetApp Storage Systems user guide Product Version: 3.0 Contents About this guide... 1 About Sophos Anti-Virus for NetApp Storage Systems...2 System requirements... 4 Before you install
Comodo IT and Security Manager Software Version 5.4
 Comodo IT and Security Manager Software Version 5.4 End User Guide Guide Version 5.4.090716 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 5.4 End User Guide Guide Version 5.4.090716 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Quick Start Guide. PC, Mac, Android & ios
 Quick Start Guide PC, Mac, Android & ios Installation for PC Please refer to the ReadMe file on the installation disc or to the Trend Micro website for detailed system requirements. If you encounter difficulties
Quick Start Guide PC, Mac, Android & ios Installation for PC Please refer to the ReadMe file on the installation disc or to the Trend Micro website for detailed system requirements. If you encounter difficulties
Comodo Client Security Software Version 11.1
 Comodo Client Security Software Version 11.1 Quick Start Guide Guide Version 11.1.022219 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 United States Comodo Client Security - Quick Start
Comodo Client Security Software Version 11.1 Quick Start Guide Guide Version 11.1.022219 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 United States Comodo Client Security - Quick Start
Zemana Endpoint Security Administration Guide. Version
 Zemana Endpoint Security Administration Guide Version 1.9.290 Introduction 4 What is Zemana Endpoint Security? 4 What is Zemana Control Center? 4 How do Endpoint Agents and Control Center communicate with
Zemana Endpoint Security Administration Guide Version 1.9.290 Introduction 4 What is Zemana Endpoint Security? 4 What is Zemana Control Center? 4 How do Endpoint Agents and Control Center communicate with
Comodo IT and Security Manager Software Version 6.4
 Comodo IT and Security Manager Software Version 6.4 End User Guide Guide Version 6.4.040417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.4 End User Guide Guide Version 6.4.040417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Guardian Total Security User Guide
 Guardian Total Security User Guide Guardian Total Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
Guardian Total Security User Guide Guardian Total Security http://www.guardianav.co.in Copyright & License Information Copyright 2018 Quick Heal Technologies Ltd. All Rights Reserved. No part of this publication
IceWarp Unified Communications. AntiVirus Reference. Version 10.4
 IceWarp Unified Communications AntiVirus Reference Version 10.4 Printed on 30 November, 2012 Contents AntiVirus 1 Anti-Virus... 2 Latest Avast! Engine... 2 Kaspersky Anti-Virus Support... 2 Support for
IceWarp Unified Communications AntiVirus Reference Version 10.4 Printed on 30 November, 2012 Contents AntiVirus 1 Anti-Virus... 2 Latest Avast! Engine... 2 Kaspersky Anti-Virus Support... 2 Support for
F-Secure Client Security. Administrator's Guide
 F-Secure Client Security Administrator's Guide F-Secure Client Security TOC 2 Contents Chapter 1: Introduction...7 1.1 System requirements...8 1.1.1 Policy Manager Server...8 1.1.2 Policy Manager Console...8
F-Secure Client Security Administrator's Guide F-Secure Client Security TOC 2 Contents Chapter 1: Introduction...7 1.1 System requirements...8 1.1.1 Policy Manager Server...8 1.1.2 Policy Manager Console...8
CAST Aurora. How to Create a Project Back Up for the Support Desk
 CAST Aurora How to Create a Project Back Up for the Support Desk Guide Overview The aim of this document is to provide a step by step guide on how to create the smallest project database (in terms of file
CAST Aurora How to Create a Project Back Up for the Support Desk Guide Overview The aim of this document is to provide a step by step guide on how to create the smallest project database (in terms of file
Small Office Security 2. File Anti-Virus
 Small Office Security 2 File Anti-Virus Table of content Table of content... 1 File Anti-Virus... 2 What is File Anti-Virus... 2 Enabling/Disabling File Anti-Virus... 2 Operating algorithm of File Anti-Virus...
Small Office Security 2 File Anti-Virus Table of content Table of content... 1 File Anti-Virus... 2 What is File Anti-Virus... 2 Enabling/Disabling File Anti-Virus... 2 Operating algorithm of File Anti-Virus...
Comodo. Endpoint Security Manager Software Version 1.6. CIS Configuration Editor Guide Guide Version
 Comodo Endpoint Security Manager Software Version 6 CIS Configuration Editor Guide Guide Version 6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents Introduction
Comodo Endpoint Security Manager Software Version 6 CIS Configuration Editor Guide Guide Version 6.010511 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents Introduction
This document provides instructions for the following products.
 1.1 Introduction 1.1.1 Purpose 1.1.2 Scope To install anti-virus software on the Brevera Breast Biopsy system with CorLumina imaging technology system. This document applies to all CorLumina systems with
1.1 Introduction 1.1.1 Purpose 1.1.2 Scope To install anti-virus software on the Brevera Breast Biopsy system with CorLumina imaging technology system. This document applies to all CorLumina systems with
SIMATIC. Process Control System PCS 7 V7.0 SP1 Security Information Note: Setting up antivirus software. Preface. Using virus scanners 2
 SIMATIC Process Control System PCS 7 V7.0 SP1 SIMATIC Process Control System PCS 7 V7.0 SP1 Security Information Note: Setting up antivirus software Security Information Note Preface 1 Using virus scanners
SIMATIC Process Control System PCS 7 V7.0 SP1 SIMATIC Process Control System PCS 7 V7.0 SP1 Security Information Note: Setting up antivirus software Security Information Note Preface 1 Using virus scanners
Exchange Security. User Manual
 Exchange Security User Manual Avira Exchange Security Table of contents Table of contents 1 Quickstart... 5 1.1 Installing on an Exchange server... 5 1.2 Starting the Avira Exchange Security Management
Exchange Security User Manual Avira Exchange Security Table of contents Table of contents 1 Quickstart... 5 1.1 Installing on an Exchange server... 5 1.2 Starting the Avira Exchange Security Management
Using the Document Assembly Wizard
 Using the Document Assembly Wizard July 2012 Copyright 2012 CRM Software All Rights Reserved 1 Table of Contents Overview...3 Step 1: Create a new template...4 Step 2: Determine which clients will receive
Using the Document Assembly Wizard July 2012 Copyright 2012 CRM Software All Rights Reserved 1 Table of Contents Overview...3 Step 1: Create a new template...4 Step 2: Determine which clients will receive
Comodo IT and Security Manager Software Version 6.9
 Comodo IT and Security Manager Software Version 6.9 End User Guide Guide Version 6.9.072817 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.9 End User Guide Guide Version 6.9.072817 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.6
 Comodo IT and Security Manager Software Version 6.6 End User Guide Guide Version 6.6.053117 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Comodo IT and Security Manager Software Version 6.6 End User Guide Guide Version 6.6.053117 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo IT
Chapter 5: Configuring ServerProtect
 Chapter 5: Configuring ServerProtect Chapter Objectives After completing this chapter, you should be able to achieve the following objectives: Describe the types of ServerProtect tasks Describe which actions
Chapter 5: Configuring ServerProtect Chapter Objectives After completing this chapter, you should be able to achieve the following objectives: Describe the types of ServerProtect tasks Describe which actions
Security for Everyone - Reviewing Microsoft Security Essentials 2.0 & the Windows 7 Firewall By Chuck
 Security for Everyone - Reviewing Microsoft Security Essentials 2.0 & the Windows 7 Firewall By Chuck Security Essentials was released in September 2009 to differing opinions. In a short amount of time
Security for Everyone - Reviewing Microsoft Security Essentials 2.0 & the Windows 7 Firewall By Chuck Security Essentials was released in September 2009 to differing opinions. In a short amount of time
Comodo Offline Updater Utility Software Version
 Comodo Offline Updater Utility Software Version 1.2.30701.2 i User Guide Guide Version 1.2.011811 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Introduction to
Comodo Offline Updater Utility Software Version 1.2.30701.2 i User Guide Guide Version 1.2.011811 Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Introduction to
Integrate Sophos Enterprise Console. EventTracker v8.x and above
 Integrate Sophos Enterprise Console EventTracker v8.x and above Publication Date: September 22, 2017 Abstract This guide provides instructions to configure Sophos Enterprise Console to send the events
Integrate Sophos Enterprise Console EventTracker v8.x and above Publication Date: September 22, 2017 Abstract This guide provides instructions to configure Sophos Enterprise Console to send the events
RISC Analysis and Windows 10 Fall Creators Update
 RISC Analysis and Windows 10 Fall Creators Update The Windows 10 update released by Microsoft in October 2017 is known as The Fall Creators Update (FCU). (Win 10 Version #1709). Overview The FCU introduces
RISC Analysis and Windows 10 Fall Creators Update The Windows 10 update released by Microsoft in October 2017 is known as The Fall Creators Update (FCU). (Win 10 Version #1709). Overview The FCU introduces
Attachments to Purchase Requisitions 2013 Training Session
 Attachments to Purchase Requisitions 2013 Training Session PO Attachments June 2013 Page 1 of 7 PO Attachments WinCap has the ability to attach documents to a requisition or to a PO. This is done from
Attachments to Purchase Requisitions 2013 Training Session PO Attachments June 2013 Page 1 of 7 PO Attachments WinCap has the ability to attach documents to a requisition or to a PO. This is done from
Kaspersky Endpoint Security. AppConfig Technical Capabilities
 Kaspersky Endpoint Security AppConfig Technical Capabilities Introduction The following document describes the technical capabilities and deployment the native mobile Kaspersky Endpoint Security app to
Kaspersky Endpoint Security AppConfig Technical Capabilities Introduction The following document describes the technical capabilities and deployment the native mobile Kaspersky Endpoint Security app to
Configuring Symantec AntiVirus for BlueArc Storage System
 Configuring Symantec AntiVirus for BlueArc Storage System Configuring Symantec AntiVirus for BlueArc Storage System The software described in this book is furnished under a license agreement and may be
Configuring Symantec AntiVirus for BlueArc Storage System Configuring Symantec AntiVirus for BlueArc Storage System The software described in this book is furnished under a license agreement and may be
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
How to Configure ATP in the Firewall
 Configure when and which types of files are uploaded to the Barracuda ATP Cloud. Files with a size is limited by the Large File Watermark of the virus scanner and the 8 MB upload limit for the ATP cloud,
Configure when and which types of files are uploaded to the Barracuda ATP Cloud. Files with a size is limited by the Large File Watermark of the virus scanner and the 8 MB upload limit for the ATP cloud,
Comodo Mobile Security for Android Software Version 2.5
 Comodo Mobile Security for Android Software Version 2.5 User Guide Guide Version 2.5.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Mobile
Comodo Mobile Security for Android Software Version 2.5 User Guide Guide Version 2.5.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Mobile
Quick Start Guide. Microsoft Windows Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Mission Control for the Microsoft Cloud. 5nine Cloud Security. Web Portal Version 12.o. Getting Started Guide
 Mission Control for the Microsoft Cloud 5nine Cloud Security Web Portal Version 12.o Getting Started Guide 2018 5nine Software Inc. All rights reserved. All trademarks are the property of their respective
Mission Control for the Microsoft Cloud 5nine Cloud Security Web Portal Version 12.o Getting Started Guide 2018 5nine Software Inc. All rights reserved. All trademarks are the property of their respective
Antivirus Solution Guide. NetApp Clustered Data ONTAP 8.2.1
 Antivirus Solution Guide NetApp Clustered Data ONTAP 8.2.1 Contents Abstract... 4 Audience... 4 Purpose and Scope... 4 Introduction... 4 Antivirus Solution Architecture... 5 Components of the Vscan/AV
Antivirus Solution Guide NetApp Clustered Data ONTAP 8.2.1 Contents Abstract... 4 Audience... 4 Purpose and Scope... 4 Introduction... 4 Antivirus Solution Architecture... 5 Components of the Vscan/AV
Antivirus Solution Guide for Clustered Data ONTAP: Sophos
 Technical Report Antivirus Solution Guide for Clustered Data ONTAP: Sophos Saurabh Singh and Brahmanna Chowdary Kodavali, NetApp July 2016 TR-4309 Abstract An antivirus solution is key for enterprises
Technical Report Antivirus Solution Guide for Clustered Data ONTAP: Sophos Saurabh Singh and Brahmanna Chowdary Kodavali, NetApp July 2016 TR-4309 Abstract An antivirus solution is key for enterprises
Global Whitelist Exclude Specific Folder/File/Program/Application from All Avast Scans
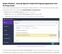 Global Whitelist Exclude Specific Folder/File/Program/Application from All Avast Scans If you want to add the exception for the specific website, domain, or URL from being scanned by Avast, follow these
Global Whitelist Exclude Specific Folder/File/Program/Application from All Avast Scans If you want to add the exception for the specific website, domain, or URL from being scanned by Avast, follow these
Comodo Unknown File Hunter Software Version 2.1
 rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
Avira Ultimate Protection Suite. Short guide
 Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Macros in Excel: Recording, Running, and Editing
 Macros in Excel: Recording, Running, and Editing This document provides instructions for creating, using, and revising macros in Microsoft Excel. Simple, powerful, and easy to customize, Excel macros can
Macros in Excel: Recording, Running, and Editing This document provides instructions for creating, using, and revising macros in Microsoft Excel. Simple, powerful, and easy to customize, Excel macros can
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
A backup is a copy of valued data, created as a replacement for situations when the original data is lost or corrupted.
 Backup guide 1 WHAT IS A BACKUP? A backup is a copy of valued data, created as a replacement for situations when the original data is lost or corrupted. 2 THE NEED FOR BACKUP Any kind of valued data should
Backup guide 1 WHAT IS A BACKUP? A backup is a copy of valued data, created as a replacement for situations when the original data is lost or corrupted. 2 THE NEED FOR BACKUP Any kind of valued data should
User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
Sophos Endpoint Security and Control standalone startup guide
 Sophos Endpoint Security and Control standalone startup guide Sophos Endpoint Security and Control, version 9.5 Sophos Anti-Virus for Mac OS X, version 7 Document date: June 2010 Contents 1 Before you
Sophos Endpoint Security and Control standalone startup guide Sophos Endpoint Security and Control, version 9.5 Sophos Anti-Virus for Mac OS X, version 7 Document date: June 2010 Contents 1 Before you
SIMATIC. Process Control System PCS 7 Symantec Endpoint Protection 11.0 Configuration. Using virus scanners 1. Configuration 2. Commissioning Manual
 SIMATIC Process Control System PCS 7 Using virus scanners 1 Configuration 2 SIMATIC Process Control System PCS 7 Symantec Endpoint Protection 11.0 Configuration Commissioning Manual 08/2009 A5E02634984-01
SIMATIC Process Control System PCS 7 Using virus scanners 1 Configuration 2 SIMATIC Process Control System PCS 7 Symantec Endpoint Protection 11.0 Configuration Commissioning Manual 08/2009 A5E02634984-01
Barracuda Threat Scanner for Exchange
 The is a free Windows application that allows you to scan onpremises Microsoft Exchange Servers for threats in existing user mailboxes. This tool provides insight into what threats have already entered
The is a free Windows application that allows you to scan onpremises Microsoft Exchange Servers for threats in existing user mailboxes. This tool provides insight into what threats have already entered
ESET ENDPOINT ANTIVIRUS
 ESET ENDPOINT ANTIVIRUS User Guide Microsoft Windows 8 / 7 / Vista / XP / 2000 / Home Server / NT4 (SP6) Click here to download the most recent version of this document ESET ENDPOINT ANTIVIRUS Copyright
ESET ENDPOINT ANTIVIRUS User Guide Microsoft Windows 8 / 7 / Vista / XP / 2000 / Home Server / NT4 (SP6) Click here to download the most recent version of this document ESET ENDPOINT ANTIVIRUS Copyright
BackupVault Desktop & Laptop Edition. USER MANUAL For Microsoft Windows
 BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
User Guide. Quick Heal Technologies Ltd.
 User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
User Guide Quick Heal Total Security Quick Heal Total Shield Quick Heal Internet Security Quick Heal Internet Security Essentials Quick Heal AntiVirus Pro Advanced Quick Heal AntiVirus Pro Quick Heal AntiVirus
