Global Whitelist Exclude Specific Folder/File/Program/Application from All Avast Scans
|
|
|
- Lester Sherman
- 5 years ago
- Views:
Transcription
1 Global Whitelist Exclude Specific Folder/File/Program/Application from All Avast Scans If you want to add the exception for the specific website, domain, or URL from being scanned by Avast, follow these steps. This is so-called Global Whitelist or Exclusion List. 1. Open the Avast user interface and go to Settings» General 2. Find the tab Exclusions and add specific programs to the File paths tab 3. Added applications and/or paths will now be excluded from any Avast scanning Adding File/Folder/Program Exception into Avast 2018 On the screenshot above you can see that application FileZilla FTP Client and DAEMON Tools Lite are excluded. Such exceptions also apply to all sub-folders on these folders as we have used /* in the path.
2 Global Whitelist Exclude Specific Website/URL from All Avast Scans If you want to add the exception for the specific Avast shield, follow these steps. 1. Open the Avast user interface and go to Settings» General 2. Find the tab Exclusions and add specific websites or URLs in the Urls tab. Please note will be added automatically, so if you want to exclude Yahoo, just type yahoo.com. Please note you need to differentiate between and 3. Added websites/urls will now be excluded from any Avast scanning Adding Website/Domain/URL Exception into Avast 2018 On the screenshot above you can see that URLs and http(s)://.gmail.com are excluded. Such exception also applies to all pages on these domains as we have used /* in the path.
3 Add Exception for Specific Avast Antivirus Shield (File System Shield, Mail Shield, or Web Shield) If you want to add the exception for the specific Avast shield, follow the steps further. 1. Open the Avast user interface and go to Settings» Active Protection 2. Select the shield (File System, Mail, or Web) for which you want to add the exception, and click on Customize link 3. Find the menu item Exclusions and add item you want to exclude from scanning by the specific Avast shield. You can also specify when the exclusion applies (for reading, writing, or executing) 4. Please note that global exclusions are always applied although they aren t listed in the specific shield. Also please note lot of items are listed there by default Adding Specific Shield (File System, Mail, or Web) Exception into Avast 2018 On the screenshot above, you can see many items are excluded from the File System Shield scan by default. We haven t added any of them.
4 [IMPORTANT] Restart All Avast Shields to Make Exclusion Work After you successfully add the file or webpage to exclusions you need to actually restart all Avast shields to make it work. Otherwise, Avast will keep detecting and blocking it as a threat. 1. Find Avast icon in the Windows system tray (click on the top arrow) 2. Go to Avast shields control» Disable for 10 minutes» confirm 3. Go again back to Avast shields control» Enable all shields Restarting All Avast Shields From the Windows System Tray Now Avast should stop detecting the added files/urls in the exclusions. You can also simply just restart your Windows.
5 Report a False Positive Detection to Avast We also strongly suggest to report the detection you believe is a false positive directly to Avast team. They will look into it and eventually confirm the reported file, software, or website is clean. Link to report is included on every in-product pop-up displayed when the harmful webpage or file is blocked. Just click on Report the file as a false positive. Avast Web Shield Has Blocked a Harmful Webpage or File Pop-up Then you need to fill-in following simple form. In the additional info you can add a link from VirusTotal scan. Don t forget to check the option I know what I m doing and click on Submit.
6 Form for Reporting False Positive Detection of Files or Websites Alternatively you can use the official web form for reporting false positive detection. Avast In-product Official Avast Web Form for Reporting False Positive Detection of Files or Websites Additional Notes Although we have used Avast Free Antivirus 2018 screenshots in this article, these steps are also applicable for all Avast Antivirus solutions (i.e. also for Avast Pro Antivirus, Avast Internet Security, or Avast Premier) running the latest version available. Steps are relevant for all Windows versions Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8.1 and Windows 10 (including Anniversary Update).
7 Managing exceptions or turning off Avast protection may leave your computer at risk.
ABF Software Issues Caused by Anti-Virus Programs
 ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
ABF Software Issues Caused by Anti-Virus Programs Downloading Problems: I) Check your browser settings: Copy and paste one of the following url addresses for support settings to prevent your browser from
How To Remove Virus From Computer Without Using Antivirus In Windows Xp
 How To Remove Virus From Computer Without Using Antivirus In Windows Xp How to remove a virus - how to clean PC and laptop of virus, spyware and other PC internet security software that includes up to
How To Remove Virus From Computer Without Using Antivirus In Windows Xp How to remove a virus - how to clean PC and laptop of virus, spyware and other PC internet security software that includes up to
SecureAPlus User Guide. Version 3.4
 SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
SecureAPlus User Guide Version 3.4 September 2015 Copyright Information Information in this document is subject to change without notice. Companies, names and data used in examples herein are fictitious
SP HDD Lock Utility User Manual rev.01. SP HDD Lock Utility. User Manual
 SP HDD Lock Utility User Manual 1 Table of Contents 1. Disclaimer... 3 2. Product Introduction... 3 3. System Requirements... 3 4. Getting Started... 4 4.1 Installing SP HDD Lock Utility... 4 4.2 Enable
SP HDD Lock Utility User Manual 1 Table of Contents 1. Disclaimer... 3 2. Product Introduction... 3 3. System Requirements... 3 4. Getting Started... 4 4.1 Installing SP HDD Lock Utility... 4 4.2 Enable
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
DAG Currently Supports the following Operating Systems and web browsers
 Overview This reference guide provides process steps and screenshots on the installation of the DAG Access Software comprised of: Citrix Receiver Installation Netscaler Gateway Endpoint Analysis Important
Overview This reference guide provides process steps and screenshots on the installation of the DAG Access Software comprised of: Citrix Receiver Installation Netscaler Gateway Endpoint Analysis Important
Your guide to using the Lead Retrieval App. A powerful and easy way to capture sales leads using your own Smartphone. Powered by
 Your guide to using the Lead Retrieval App A powerful and easy way to capture sales leads using your own Smartphone Powered by APP FEATURES Capture and view lead information in real-time on and off the
Your guide to using the Lead Retrieval App A powerful and easy way to capture sales leads using your own Smartphone Powered by APP FEATURES Capture and view lead information in real-time on and off the
How to remove Adware from Mozilla Firefox
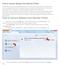 How to remove Adware from Mozilla Firefox Mozilla Firefox is one of the most popular browsers, and therefore also a popular target for installing adware and other untwanted extensions. In this article
How to remove Adware from Mozilla Firefox Mozilla Firefox is one of the most popular browsers, and therefore also a popular target for installing adware and other untwanted extensions. In this article
Comodo Antivirus Software Version 2.0
 Comodo Antivirus Software Version 2.0 User Guide Guide Version 2.0.010215 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.0 User Guide Guide Version 2.0.010215 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Manually Remove Of Xp Internet Security Pro Virus Windows 7
 Manually Remove Of Xp Internet Security Pro Virus Windows 7 How to remove Defender PRO 2015 virus (Removal Guide) kits that use vulnerabilities on your computer to install this rogue antivirus without
Manually Remove Of Xp Internet Security Pro Virus Windows 7 How to remove Defender PRO 2015 virus (Removal Guide) kits that use vulnerabilities on your computer to install this rogue antivirus without
SEP for Windows: FAQ. Updating Security. Definitions (AV and IPS) it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu)
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > SEP for Windows: FAQ SEP for Windows: FAQ Cyndi Galvan
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > SEP for Windows: FAQ SEP for Windows: FAQ Cyndi Galvan
Table of Contents. Page 1
 Table of Contents Google My Business Plugin... 2 Installation Is Not Required... 2 Generate GMB Unclaimed Data... 2 Reviewing The Unclaimed Listings... 2 Antivirus Applications... 3 AVG Antivirus... 3
Table of Contents Google My Business Plugin... 2 Installation Is Not Required... 2 Generate GMB Unclaimed Data... 2 Reviewing The Unclaimed Listings... 2 Antivirus Applications... 3 AVG Antivirus... 3
How to Configure Anti-Virus to Permit SoftMiner Binaries
 How to Configure Anti-Virus to Permit Binaries If you trust a file, file type, folder, or a process that anti-virus has detected as malicious, you can stop anti-virus from alerting you or blocking the
How to Configure Anti-Virus to Permit Binaries If you trust a file, file type, folder, or a process that anti-virus has detected as malicious, you can stop anti-virus from alerting you or blocking the
Step [2]: Hit on Create icon and Choose the "Create macos Profile" from the drop-down menu
![Step [2]: Hit on Create icon and Choose the Create macos Profile from the drop-down menu Step [2]: Hit on Create icon and Choose the Create macos Profile from the drop-down menu](/thumbs/82/84933536.jpg) This guide allows a user to configure Antivirus Settings through a profile. The settings include all low-level details to be parameterized from ITSM hence the Realtime Scan (at the time of threats encountered),
This guide allows a user to configure Antivirus Settings through a profile. The settings include all low-level details to be parameterized from ITSM hence the Realtime Scan (at the time of threats encountered),
IANSEO ScoreKeeper Quick Start Guide Revision 1.3
 IANSEO ScoreKeeper Quick Start Guide Revision 1.3 This guide will help you get started using the ScoreKeeper app. To be fully functional, the app requires access to the IANSEO Archery software to send
IANSEO ScoreKeeper Quick Start Guide Revision 1.3 This guide will help you get started using the ScoreKeeper app. To be fully functional, the app requires access to the IANSEO Archery software to send
Configuring the WebDAV Folder for Adding Multiple Files to the Content Collection and Editing Them
 Configuring the WebDAV Folder for Adding Multiple Files to the Content Collection and Editing Them The Content Collection should be the repository for all of the files used in Blackboard. The Content Collection
Configuring the WebDAV Folder for Adding Multiple Files to the Content Collection and Editing Them The Content Collection should be the repository for all of the files used in Blackboard. The Content Collection
Even a non-technical user can even operate it with ease.the user can do any task in CCS with just a few clicks.
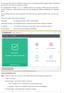 The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
The Comodo Client Security identifies all security risks and provides protection against it.now, the interface of the Comodo Client Security is made very simple. It is integrated with Firewall, Antivirus,
FRM FOR OUTLOOK PLUGIN INSTALLATION GUIDE FRM Solutions, Inc.
 FRM FOR OUTLOOK PLUGIN INSTALLATION GUIDE FRM Solutions, Inc. TABLE OF CONTENTS System Requirements... 2 I. Determining the.bit version of your Microsoft Office Suite... 2 III. Configuring the Outlook
FRM FOR OUTLOOK PLUGIN INSTALLATION GUIDE FRM Solutions, Inc. TABLE OF CONTENTS System Requirements... 2 I. Determining the.bit version of your Microsoft Office Suite... 2 III. Configuring the Outlook
WP FB Mirror Pro Installation Guide
 We have created a detailed guide on installing and setting up the WP FB Mirror Pro. Please go through it and let us know if you get stuck at any step. If you need any help, we are available at support@kvsocial.zendesk.com
We have created a detailed guide on installing and setting up the WP FB Mirror Pro. Please go through it and let us know if you get stuck at any step. If you need any help, we are available at support@kvsocial.zendesk.com
This document provides instructions for the following products.
 1.1 Introduction 1.1.1 Purpose 1.1.2 Scope To install anti-virus software on the Brevera Breast Biopsy system with CorLumina imaging technology system. This document applies to all CorLumina systems with
1.1 Introduction 1.1.1 Purpose 1.1.2 Scope To install anti-virus software on the Brevera Breast Biopsy system with CorLumina imaging technology system. This document applies to all CorLumina systems with
Comodo Antivirus Software Version 2.1
 Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.1 User Guide Guide Version 2.1.030515 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
MD5 FILE HASHER USER MANUAL
 User Manual Digital-Tronic Software Development MD5 FILE HASHER USER MANUAL Dated: October 2014 WELCOME MD5 File Hasher is a simple program which allows you to create and compare check sums. This allows
User Manual Digital-Tronic Software Development MD5 FILE HASHER USER MANUAL Dated: October 2014 WELCOME MD5 File Hasher is a simple program which allows you to create and compare check sums. This allows
Manually Remove Of Xp Internet Security Protect
 Manually Remove Of Xp Internet Security Protect McAfee Family Protection McAfee Internet Security NOTE: To determine which McAfee Security software version you have installed, You must uninstall your McAfee
Manually Remove Of Xp Internet Security Protect McAfee Family Protection McAfee Internet Security NOTE: To determine which McAfee Security software version you have installed, You must uninstall your McAfee
Auslogics BOOSTSPEED USER MANUAL. auslogics.
 Auslogics BOOSTSPEED 10 USER MANUAL www..com TABLE OF CONTENTS: Welcome Installation Guide Registering Auslogics BoostSpeed 10 Backing up with the Rescue Center Your First Scan Navigation Panel Navigation
Auslogics BOOSTSPEED 10 USER MANUAL www..com TABLE OF CONTENTS: Welcome Installation Guide Registering Auslogics BoostSpeed 10 Backing up with the Rescue Center Your First Scan Navigation Panel Navigation
Trend Micro OfficeScan Client User Guide
 Trend Micro OfficeScan Client User Guide Overview The purpose of this document is to provide users with information on the Trend Micro OfficeScan antivirus client. OfficeScan is the new anti-virus/anti-malware
Trend Micro OfficeScan Client User Guide Overview The purpose of this document is to provide users with information on the Trend Micro OfficeScan antivirus client. OfficeScan is the new anti-virus/anti-malware
How To Remove Virus From Windows OS
 9/30/2018 How To Remove Virus From Windows OS Detailed Instructions To Remove Virus From Your MAC OS Step 1. Ending Process Running Under The Ac tivity Monitor 1. Type Activity Monitor in the Launchpad
9/30/2018 How To Remove Virus From Windows OS Detailed Instructions To Remove Virus From Your MAC OS Step 1. Ending Process Running Under The Ac tivity Monitor 1. Type Activity Monitor in the Launchpad
Client Instructions - ID Tech Configuration Instructions
 Client Instructions - ID Tech Configuration Instructions Please follow the steps below to get started with the configuration process for your ID Tech reader. A student ID card will be necessary for the
Client Instructions - ID Tech Configuration Instructions Please follow the steps below to get started with the configuration process for your ID Tech reader. A student ID card will be necessary for the
Sophos Anti-Virus standalone startup guide. For Windows and Mac OS X
 Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Arrow Contract Management System. Electronic Tendering Guide
 Arrow Contract Management System Electronic Tendering Guide CONTENTS 1. RECEIVING & VIEWING A TENDER INVITATION... 3 2. LOGGING INTO PROCON... 4 3. OBTAINING TENDER DOCUMENTS... 5 4. HOW TO RESPOND ELECTRONICALLY
Arrow Contract Management System Electronic Tendering Guide CONTENTS 1. RECEIVING & VIEWING A TENDER INVITATION... 3 2. LOGGING INTO PROCON... 4 3. OBTAINING TENDER DOCUMENTS... 5 4. HOW TO RESPOND ELECTRONICALLY
NEO Installation Guide
 NEO Installation Guide Version Control Version Number Date Changed by 1 9 th September 2015 Nicola Latter 2 15 th October 2015 Nicola Latter 3 6 th January 2016 Nicola Latter 4 13 th January 2016 Nicola
NEO Installation Guide Version Control Version Number Date Changed by 1 9 th September 2015 Nicola Latter 2 15 th October 2015 Nicola Latter 3 6 th January 2016 Nicola Latter 4 13 th January 2016 Nicola
SECURITY SHIELD 2013 User's Guide
 SECURITY SHIELD 2013 User's Guide Published 2012.12.12 Copyright 2013 PCSecurityShield Legal Notice All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means,
SECURITY SHIELD 2013 User's Guide Published 2012.12.12 Copyright 2013 PCSecurityShield Legal Notice All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means,
New Dropbox Users (don t have a Dropbox account set up with your Exeter account)
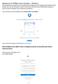 The setup process will determine if you already have a Dropbox account associated with an Exeter email address, and if so, you'll be given a choice to move those contents to your Phillips Exeter Dropbox
The setup process will determine if you already have a Dropbox account associated with an Exeter email address, and if so, you'll be given a choice to move those contents to your Phillips Exeter Dropbox
Jet-Tech video tutorials
 Installation Instructions Step by Step Guide All versions of Jet-Tech Software are installed in the same way, just follow these instructions carefully and your software will install correctly. Failure
Installation Instructions Step by Step Guide All versions of Jet-Tech Software are installed in the same way, just follow these instructions carefully and your software will install correctly. Failure
Quick Start Guide. Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
SQLite Server - About
 SQLite Server - About Description: The SQLite Server application allows a SQLite database to be hosted over a network connection, allowing multiple clients to concurrently write & read to the SQLite database.
SQLite Server - About Description: The SQLite Server application allows a SQLite database to be hosted over a network connection, allowing multiple clients to concurrently write & read to the SQLite database.
Comodo Antivirus Software Version 2.2
 Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
Comodo Antivirus Software Version 2.2 User Guide Guide Version 2.2.082318 Comodo Security Solutions Inc. 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Antivirus... 4 1.1.System
How To Remove Internet Security Pro Virus. Manually >>>CLICK HERE<<<
 How To Remove Internet Security Pro Virus Manually Instructions to remove Defender PRO 2015 virus and get rid of Defender PRO 2015 malware from Windows. Tech & Internet Security / News & Guides Click the
How To Remove Internet Security Pro Virus Manually Instructions to remove Defender PRO 2015 virus and get rid of Defender PRO 2015 malware from Windows. Tech & Internet Security / News & Guides Click the
Installation Guide. Contents. Overview. Dell SonicWALL Advanced Reporting Installation Guide. Secure Remote Access. SonicOS
 Secure Remote Access SonicOS Contents Overview...1 Server Requirements...2 Licensing and Activation...2 Installing and Upgrading...4 Collecting Dell SonicWALL Aventail Access Logs...8 Initial Setup of
Secure Remote Access SonicOS Contents Overview...1 Server Requirements...2 Licensing and Activation...2 Installing and Upgrading...4 Collecting Dell SonicWALL Aventail Access Logs...8 Initial Setup of
1320 Electronics LLC USB-ALDL Cable User s Guide Electronics LLC. User s Guide for: USB-ALDL Cable
 1320 Electronics LLC User s Guide for: USB-ALDL Cable 1 Contents Warnings 3 Specifications 4 Configuration 5 Automatic Driver Installation 6 Manual Driver Installation 7 Driver Installation Verification
1320 Electronics LLC User s Guide for: USB-ALDL Cable 1 Contents Warnings 3 Specifications 4 Configuration 5 Automatic Driver Installation 6 Manual Driver Installation 7 Driver Installation Verification
Setting up the PC ready for BESA 11
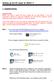 Setting up the PC ready for BESA 11 1 - Installing Driver. Important Note: Before you start to install the driver, please do not plug BESA 11 into the computer s USB port or else the installation will
Setting up the PC ready for BESA 11 1 - Installing Driver. Important Note: Before you start to install the driver, please do not plug BESA 11 into the computer s USB port or else the installation will
AFN Setup. If you have any trouble setting it up please contact the Help Desk by at Outlook 2007 and 2010
 AFN Email Setup Each version of Outlook is set up in the same general way. Some of the screens may have a few variations to them but they all should have the same options. Outlook 2007 and 2010 are very
AFN Email Setup Each version of Outlook is set up in the same general way. Some of the screens may have a few variations to them but they all should have the same options. Outlook 2007 and 2010 are very
Manual Update Avg Antivirus 2012 Full Version For Windows 7
 Manual Update Avg Antivirus 2012 Full Version For Windows 7 AVG Antivirus software updates. Stay secure by Implemented support for Windows 10. Program Fixed issue with setup freeze during the process of
Manual Update Avg Antivirus 2012 Full Version For Windows 7 AVG Antivirus software updates. Stay secure by Implemented support for Windows 10. Program Fixed issue with setup freeze during the process of
SAP Standard Reporting Quick Reference Guide
 Standard reports are run within the SAP application and are pre-delivered by SAP to fulfill basic legal, financial, and everyday business reporting requirements. This guide demonstrates features common
Standard reports are run within the SAP application and are pre-delivered by SAP to fulfill basic legal, financial, and everyday business reporting requirements. This guide demonstrates features common
Graduate e-portfolio Setup Directions
 Graduate e-portfolio Setup Directions This set of instructions is in several sections so that you may use the ones that you need. Section 1 Structure (It is a good idea to create folders in one place on
Graduate e-portfolio Setup Directions This set of instructions is in several sections so that you may use the ones that you need. Section 1 Structure (It is a good idea to create folders in one place on
AVG 9 Free. User Manual. Document revision 90.4 ( )
 AVG 9 Free User Manual Document revision 90.4 (14.9.2009) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This product uses
AVG 9 Free User Manual Document revision 90.4 (14.9.2009) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. This product uses
Kaspersky PURE 2.0. Exclusions
 Exclusions Content Exclusions... 2 Trusted zone... 2 Creating the list of trusted applications... 3 Creating exclusion rules... 5 1 10 Exclusions Trusted zone Trusted zone is a list of objects created
Exclusions Content Exclusions... 2 Trusted zone... 2 Creating the list of trusted applications... 3 Creating exclusion rules... 5 1 10 Exclusions Trusted zone Trusted zone is a list of objects created
How To Manually Open Ports In Internet Connection Firewall In Windows 8 >>>CLICK HERE<<<
 How To Manually Open Ports In Internet Connection Firewall In Windows 8 The Windows Firewall (formerly known as Internet Connection Firewall) Resetting the firewall settings will enable the firewall regardless
How To Manually Open Ports In Internet Connection Firewall In Windows 8 The Windows Firewall (formerly known as Internet Connection Firewall) Resetting the firewall settings will enable the firewall regardless
Welcome to Crowd Force PRO
 Welcome to Crowd Force PRO User Guide Version: 0_43_0 Table of Contents Introduction... 4 Using the User Guide... 4 Printing the User Guide... 4 Contact Crowd Force PRO Support Desk... 4 Crowd Force PRO...
Welcome to Crowd Force PRO User Guide Version: 0_43_0 Table of Contents Introduction... 4 Using the User Guide... 4 Printing the User Guide... 4 Contact Crowd Force PRO Support Desk... 4 Crowd Force PRO...
Sitecore guide building a blog
 Sitecore guide building a blog Creating the page Log in to Sitecore and open the content editor. In the content tree on the left hand side use the + icon to expand the area of the site the blog is intended
Sitecore guide building a blog Creating the page Log in to Sitecore and open the content editor. In the content tree on the left hand side use the + icon to expand the area of the site the blog is intended
FRM FOR OUTLOOK PLUGIN INSTALLATION GUIDE FRM Solutions, Inc.
 FRM FOR OUTLOOK PLUGIN INSTALLATION GUIDE FRM Solutions, Inc. TABLE OF CONTENTS System Requirements... 2 I. Determining the.bit version of your Microsoft Office Suite... 2 II. Determine your version of
FRM FOR OUTLOOK PLUGIN INSTALLATION GUIDE FRM Solutions, Inc. TABLE OF CONTENTS System Requirements... 2 I. Determining the.bit version of your Microsoft Office Suite... 2 II. Determine your version of
Real Fast PC. Real Fast PC Win 7.
 Real Fast PC Win 7 www.realfastpc.com 1 Real Fast PC Win 7 Disclaimer: Please note that while every effort is made to ensure that the information provided in this ebook is up to date, effective, and useful,
Real Fast PC Win 7 www.realfastpc.com 1 Real Fast PC Win 7 Disclaimer: Please note that while every effort is made to ensure that the information provided in this ebook is up to date, effective, and useful,
ESET NOD32 ANTIVIRUS 8
 ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 7
 ESET NOD32 ANTIVIRUS 7 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 7 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
Optimal Global Procurement System. (KG-Pro) Login Manual
 Optimal Global Procurement System (KG-Pro) Login Manual Ver.1.1 Contents 1 Foreword... 2 2 Preparation for using KG-Pro... 2 2.1 Hardware... 2 2.2 Software... 2 2.3 User ID... 3 2.4 Required items for
Optimal Global Procurement System (KG-Pro) Login Manual Ver.1.1 Contents 1 Foreword... 2 2 Preparation for using KG-Pro... 2 2.1 Hardware... 2 2.2 Software... 2 2.3 User ID... 3 2.4 Required items for
FAQ. Safe Anywhere PC 12. Disclaimer:
 FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
FAQ Safe Anywhere PC 12 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch pad, F-Secure
Latest version of google chrome for windows
 Latest version of google chrome for windows What makes a browser different from other similar ones are its features. Just have a glance at the brilliant features of this browser: Difficulty to install
Latest version of google chrome for windows What makes a browser different from other similar ones are its features. Just have a glance at the brilliant features of this browser: Difficulty to install
Product Guide. McAfee GetSusp
 Product Guide McAfee GetSusp 3.0.0.461 COPYRIGHT LICENSE INFORMATION Copyright 2013-2017 McAfee, LLC. YOUR RIGHTS TO COPY AND RUN THIS TOOL ARE DEFINED BY THE MCAFEE SOFTWARE ROYALTY-FREE LICENSE FOUND
Product Guide McAfee GetSusp 3.0.0.461 COPYRIGHT LICENSE INFORMATION Copyright 2013-2017 McAfee, LLC. YOUR RIGHTS TO COPY AND RUN THIS TOOL ARE DEFINED BY THE MCAFEE SOFTWARE ROYALTY-FREE LICENSE FOUND
User Experience Review
 User Experience Review Review Format For each of the tested products, we have looked at the following points (where applicable). Which versions of Windows does it work with? We list the versions of Windows
User Experience Review Review Format For each of the tested products, we have looked at the following points (where applicable). Which versions of Windows does it work with? We list the versions of Windows
Tap to enter a search item or web address. Open a new tab. Your open tabs. See pages open on other devices.
 Safari 7 Safari at a glance Use Safari on ipad to browse the web. Use Reading List to collect webpages to read later. Add page icons to the Home screen for quick access. Use icloud to see pages you have
Safari 7 Safari at a glance Use Safari on ipad to browse the web. Use Reading List to collect webpages to read later. Add page icons to the Home screen for quick access. Use icloud to see pages you have
Using SANDBOXIE to Safely Browse the Internet (verified with ver 5.22) Jim McKnight Sandboxie.lwp revised
 Using SANDBOXIE to Safely Browse the Internet (verified with ver 5.22) Jim McKnight www.jimopi.net Sandboxie.lwp revised 11-8-2017 WINDOWS 10 USERS: The Fall Creators Update build 1709 requires Sandboxie
Using SANDBOXIE to Safely Browse the Internet (verified with ver 5.22) Jim McKnight www.jimopi.net Sandboxie.lwp revised 11-8-2017 WINDOWS 10 USERS: The Fall Creators Update build 1709 requires Sandboxie
Training Booking System User Guide Contents:
 Training Booking System User Guide Contents: Register to Use the System... 2 Password Reminder... 4 Log In and Page Overview... 6 Book a Course for Yourself... 7 Book Yourself and Another Staff Member
Training Booking System User Guide Contents: Register to Use the System... 2 Password Reminder... 4 Log In and Page Overview... 6 Book a Course for Yourself... 7 Book Yourself and Another Staff Member
Data Manager Installation and Update Instructions
 Data Manager Installation and Update Instructions These instructions describe how to update or install Data Manager desktop software from YSI s website. Failure to follow these instructions may cause you
Data Manager Installation and Update Instructions These instructions describe how to update or install Data Manager desktop software from YSI s website. Failure to follow these instructions may cause you
User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
TRANSFLO NOW! Table of Contents
 TRANSFLO NOW! Welcome to Transflo Now! Transflo Now! allows you to scan your trip documents anywhere, even if you don t have a connection to the Internet. Once you have access to a High Speed Internet
TRANSFLO NOW! Welcome to Transflo Now! Transflo Now! allows you to scan your trip documents anywhere, even if you don t have a connection to the Internet. Once you have access to a High Speed Internet
Comodo. Cloud Antivirus. User Guide. Software Version Guide Version
 Comodo Cloud Antivirus Software Version 1.11 User Guide Guide Version 1.11.050317 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
Comodo Cloud Antivirus Software Version 1.11 User Guide Guide Version 1.11.050317 Comodo Security Solutions 1255 Broad Street Clifton, NJ, 07013 United States Table of Contents 1. Introduction to Comodo
WebAnalyzer Plus Getting Started Guide
 WebAnalyzer Plus Getting Started Guide www.manageengine.com/web-analytics Contents 1 Introduction 4 2 3 4 5 WebAnalyzer Plus Overview Getting Started System Requirements Installation Starting and Accessing
WebAnalyzer Plus Getting Started Guide www.manageengine.com/web-analytics Contents 1 Introduction 4 2 3 4 5 WebAnalyzer Plus Overview Getting Started System Requirements Installation Starting and Accessing
Sonatype CLM Enforcement Points - Nexus. Sonatype CLM Enforcement Points - Nexus
 Sonatype CLM Enforcement Points - Nexus i Sonatype CLM Enforcement Points - Nexus Sonatype CLM Enforcement Points - Nexus ii Contents 1 Introduction 1 2 Sonatype CLM for Repository Managers 2 3 Nexus Pro
Sonatype CLM Enforcement Points - Nexus i Sonatype CLM Enforcement Points - Nexus Sonatype CLM Enforcement Points - Nexus ii Contents 1 Introduction 1 2 Sonatype CLM for Repository Managers 2 3 Nexus Pro
Quick Start Guide. Microsoft Windows Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Manual Removal Norton Internet Security Won't Open Or
 Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
How to setup Google DNS in your Windows computer
 Submitted by Jess on Thu, 01/22/2015-17:08 This is a very common issue with internet connections: you are able to access certain websites and other sites are inaccessible; websites that you used to access
Submitted by Jess on Thu, 01/22/2015-17:08 This is a very common issue with internet connections: you are able to access certain websites and other sites are inaccessible; websites that you used to access
Accessing McKesson Radiology 12.3 PACS Remotely Over VPN
 Accessing McKesson Radiology 12.3 PACS Remotely Over VPN Web: www.interiorhealth.ca 2 Getting Started Please ensure that your PACS administrator has setup your McKesson account for access to the McKesson
Accessing McKesson Radiology 12.3 PACS Remotely Over VPN Web: www.interiorhealth.ca 2 Getting Started Please ensure that your PACS administrator has setup your McKesson account for access to the McKesson
AMP User Manual Tools Dropdown
 AMP User Manual Tools Dropdown Clicking on Tools allows all users to access the following functionalities: Language, Workspace Info, Search and Address Book. For workspace managers, the tools dropdown
AMP User Manual Tools Dropdown Clicking on Tools allows all users to access the following functionalities: Language, Workspace Info, Search and Address Book. For workspace managers, the tools dropdown
Ekran System v.6.1 Troubleshooting
 Ekran System v.6.1 Troubleshooting Quick Access to Log Files Table of Contents Quick Access to Log Files... 3 Database/Server... 4 Database/Server Related Issues... 4 Database/Server Related Error Messages...
Ekran System v.6.1 Troubleshooting Quick Access to Log Files Table of Contents Quick Access to Log Files... 3 Database/Server... 4 Database/Server Related Issues... 4 Database/Server Related Error Messages...
Webroot SecureAnywhere Business Endpoint Protection
 Single Product Test Head-to-Head Comparison VIPRE Endpoint Security - Cloud Edition Webroot SecureAnywhere Business Endpoint Protection Language: English October 2017 Last revision: 3 rd November 2017-1
Single Product Test Head-to-Head Comparison VIPRE Endpoint Security - Cloud Edition Webroot SecureAnywhere Business Endpoint Protection Language: English October 2017 Last revision: 3 rd November 2017-1
Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9
 Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9 If you are not working from a Windows 7 or 8 computer, you will need to update: Windows XP to Service Pack 3 Windows Vista
Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9 If you are not working from a Windows 7 or 8 computer, you will need to update: Windows XP to Service Pack 3 Windows Vista
Osteoporosis Assessment LORAD Breast Cancer Detection DirectRay Digital Imaging FLUOROSCAN C-arm Imaging TITLE DOCUMENT NUMBER REV
 Artwork consists of: Ten pages, 8.5 11 inch, attached. REV AUTHORED BY DATE C. LUU 12/18/13 REV DRAFTED BY DATE C. LUU 12/18/13 PROPRIETARY: This document contains proprietary data of Hologic, Inc. No
Artwork consists of: Ten pages, 8.5 11 inch, attached. REV AUTHORED BY DATE C. LUU 12/18/13 REV DRAFTED BY DATE C. LUU 12/18/13 PROPRIETARY: This document contains proprietary data of Hologic, Inc. No
INTRODUCTION... 2 GETTING STARTED...
 Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Controls to be activated with the mouse will be shown as Start button > Settings > System > About.
Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Controls to be activated with the mouse will be shown as Start button > Settings > System > About.
ishipdocs User Guide
 ishipdocs User Guide 11/8/2016 Disclaimer This guide has been validated and reviewed for accuracy. The instructions and descriptions it contains are accurate for ishipdocs. However, succeeding versions
ishipdocs User Guide 11/8/2016 Disclaimer This guide has been validated and reviewed for accuracy. The instructions and descriptions it contains are accurate for ishipdocs. However, succeeding versions
QUICK START GUIDE. Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server Click here to download the most recent version of this document
 QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET INTERNET SECURITY IS ALL-IN-ONE INTERNET SECURITY SOFTWARE.
QUICK START GUIDE Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / Home Server 2011 Click here to download the most recent version of this document ESET INTERNET SECURITY IS ALL-IN-ONE INTERNET SECURITY SOFTWARE.
Table of Contents. HotSpot Installation. Windows 7, 8.1 and 10. Windows Server OS. DNS Web Filter Setup. Windows Configuration. Antamedia HotSpot?
 Contents Table of Contents Part 1 1 Part 2 1 2 3 1 Introduction 1 What is... Antamedia HotSpot? 2 Requirements... 3 Pre-installation Steps... 4 Network Adapters Setup... 9 Network Topology Examples Part
Contents Table of Contents Part 1 1 Part 2 1 2 3 1 Introduction 1 What is... Antamedia HotSpot? 2 Requirements... 3 Pre-installation Steps... 4 Network Adapters Setup... 9 Network Topology Examples Part
Guide to fix the problem with Problets
 Guide to fix the problem with Problets COP 2512 - IT Programming Fundamentals In order to fix the problem of not being able to run Problets on your web browser, please follow the following steps: 1. Make
Guide to fix the problem with Problets COP 2512 - IT Programming Fundamentals In order to fix the problem of not being able to run Problets on your web browser, please follow the following steps: 1. Make
Avira Free Mac Security Version HowTo
 Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Avira Free Mac Security Version 2.0.4 HowTo Table of contents 1. Introduction... 3 1.1 Features... 3 1.2 System Requirements...4 2. Installation...4 2.1 Installation with the install wizard...4 2.2 Installation
Fiery PRO 80 /S450 65C-KM Color Server. Printing from Windows
 Fiery PRO 80 /S450 65C-KM Color Server Printing from Windows 2007 Electronics for Imaging, Inc. The information in this publication is covered under Legal Notices for this product. 45067315 01 November
Fiery PRO 80 /S450 65C-KM Color Server Printing from Windows 2007 Electronics for Imaging, Inc. The information in this publication is covered under Legal Notices for this product. 45067315 01 November
ValuePRO Tutorial Internet Explorer 8 Configuration
 ValuePRO Tutorial Internet Explorer 8 Configuration Table of Contents Contents 1. Adding ValuePRO to Trusted Sites... 1 1. Overview... 1 2. Changes Required... 1 2. Enabling Cross Site Scripting... 3 1.
ValuePRO Tutorial Internet Explorer 8 Configuration Table of Contents Contents 1. Adding ValuePRO to Trusted Sites... 1 1. Overview... 1 2. Changes Required... 1 2. Enabling Cross Site Scripting... 3 1.
Outlook 2010 Setup Guide (POP3 Transmailaccess)
 Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
How to Add and Configure Yahoo! Mail in Outlook 2010/2007
 How to Add and Configure Yahoo! Mail in Outlook 2010/2007 Submitted by Jess on Wed, 12/18/2013-22:18 There is a big change in Yahoo Mail that came with the changes that Yahoo made with their interface
How to Add and Configure Yahoo! Mail in Outlook 2010/2007 Submitted by Jess on Wed, 12/18/2013-22:18 There is a big change in Yahoo Mail that came with the changes that Yahoo made with their interface
How to Use WindowsUpdate.Com
 Sunny Solutions Page 1 of 12 How to Use WindowsUpdate.Com (Last Update: 01/29/2010, 03:09 AM, Version 1.027) Microsoft (Microsoft) has created a website called WindowsUpdate.Com. This website distributes
Sunny Solutions Page 1 of 12 How to Use WindowsUpdate.Com (Last Update: 01/29/2010, 03:09 AM, Version 1.027) Microsoft (Microsoft) has created a website called WindowsUpdate.Com. This website distributes
Installation Manual. and User Guide
 Installation Manual and User Guide ESET Mobile Antivirus For Windows Mobile Copyright 2009 by ESET, spol. s r. o. ESET Mobile Antivirus For Windows Mobile was developed by ESET, spol. s r.o. For more information
Installation Manual and User Guide ESET Mobile Antivirus For Windows Mobile Copyright 2009 by ESET, spol. s r. o. ESET Mobile Antivirus For Windows Mobile was developed by ESET, spol. s r.o. For more information
Copyright 2018 PC Pitstop, Inc. User Guide v
 Copyright 2018 PC Pitstop, Inc User Guide v 3.0.2 2018 Table of Contents Introduction 1 Optimal System Requirements 1 Scan Components 1 Where to Purchase PC Matic 2 Installation Options 3 Launching PC
Copyright 2018 PC Pitstop, Inc User Guide v 3.0.2 2018 Table of Contents Introduction 1 Optimal System Requirements 1 Scan Components 1 Where to Purchase PC Matic 2 Installation Options 3 Launching PC
User Manual. Document revision AVG.11 ( )
 AVG AntiVirus User Manual Document revision AVG.11 (12.1.2016) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents 1.
AVG AntiVirus User Manual Document revision AVG.11 (12.1.2016) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners. Contents 1.
Download firefox with virus protection
 P ford residence southampton, ny Download firefox with virus protection 3-11-2015 Protect your devices with the best free antivirus on the market. Download Avast antivirus and anti-spyware protection for
P ford residence southampton, ny Download firefox with virus protection 3-11-2015 Protect your devices with the best free antivirus on the market. Download Avast antivirus and anti-spyware protection for
Purchasing Portal Supplier s technical requirements FULLSTEP PORTAL VS
 Purchasing Portal Supplier s technical requirements FULLSTEP PORTAL VS. 31600 FULLSTEP NETWORKS 2008 Document services cap/ 26/02/2008 Table of Contents 1 Introduction 3 2 Requirements 3 2.1 Internet connection
Purchasing Portal Supplier s technical requirements FULLSTEP PORTAL VS. 31600 FULLSTEP NETWORKS 2008 Document services cap/ 26/02/2008 Table of Contents 1 Introduction 3 2 Requirements 3 2.1 Internet connection
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
PISA 2018 COMPUTER-BASED SCHOOL QUESTIONNAIRE: PRINCIPAL S MANUAL
 P 2 I S A 0 1 8 PISA 2018 COMPUTER-BASED SCHOOL QUESTIONNAIRE: PRINCIPAL S MANUAL Doc.: CY7_CBA_ScQPrincipalManual.docx Produced by ETS, Core A Contractor TABLE OF CONTENTS Part 1 Introduction Introduction
P 2 I S A 0 1 8 PISA 2018 COMPUTER-BASED SCHOOL QUESTIONNAIRE: PRINCIPAL S MANUAL Doc.: CY7_CBA_ScQPrincipalManual.docx Produced by ETS, Core A Contractor TABLE OF CONTENTS Part 1 Introduction Introduction
Hal Documentation. Release 1.0. Dan Ryan
 Hal Documentation Release 1.0 Dan Ryan July 16, 2016 Contents 1 Configuration 3 2 Adapters 5 2.1 Campfire................................................. 5 2.2 Hipchat..................................................
Hal Documentation Release 1.0 Dan Ryan July 16, 2016 Contents 1 Configuration 3 2 Adapters 5 2.1 Campfire................................................. 5 2.2 Hipchat..................................................
Cisdem AppCrypt Tutorial
 Cisdem AppCrypt Tutorial 1 Table of Contents I. About Cisdem AppCrypt... 3 II. Activating this Application... 4 III. Application Operating... 5 I. Get Started... 5 II. Add & Remove Applications... 6 III.
Cisdem AppCrypt Tutorial 1 Table of Contents I. About Cisdem AppCrypt... 3 II. Activating this Application... 4 III. Application Operating... 5 I. Get Started... 5 II. Add & Remove Applications... 6 III.
Remove Trend Micro Titanium Internet Security Without Password
 Remove Trend Micro Titanium Internet Security Without Password Uninstall Titanium Internet Security for Mac using the installer. Open the Trend Click Uninstall. Type the administrator name and password,
Remove Trend Micro Titanium Internet Security Without Password Uninstall Titanium Internet Security for Mac using the installer. Open the Trend Click Uninstall. Type the administrator name and password,
OUTLOOK ANYWHERE CONNECTION GUIDE FOR USERS OF OUTLOOK 2007
 OUTLOOK ANYWHERE CONNECTION GUIDE FOR USERS OF OUTLOOK 2007 CONTENTS What is Outlook Anywhere? Before you begin How do I configure Outlook Anywhere with Outlook 2007? How do I use Outlook Anywhere? I already
OUTLOOK ANYWHERE CONNECTION GUIDE FOR USERS OF OUTLOOK 2007 CONTENTS What is Outlook Anywhere? Before you begin How do I configure Outlook Anywhere with Outlook 2007? How do I use Outlook Anywhere? I already
Using Antivirus Software in an Interplay Environment
 Using Antivirus Software in an Interplay Environment Support for Symantec Endpoint v12.1 Overview Avid Interplay v2.x supports the following components of Symantec Endpoint v12.1: Antivirus Antispyware
Using Antivirus Software in an Interplay Environment Support for Symantec Endpoint v12.1 Overview Avid Interplay v2.x supports the following components of Symantec Endpoint v12.1: Antivirus Antispyware
section.es PUBLISHER MANUAL
 section.es PUBLISHER MANUAL Table of Content TABLE OF CONTENT 1 LOGIN 1 EDIT EXISTING ARTICLE ON YOUR WEBSITE 2 CREATE A NEW ARTICLE 3 INSERT A FILE 5 INSERT AN ALBUM WITH PHOTOS 6 Login 1) go to - http://section.es
section.es PUBLISHER MANUAL Table of Content TABLE OF CONTENT 1 LOGIN 1 EDIT EXISTING ARTICLE ON YOUR WEBSITE 2 CREATE A NEW ARTICLE 3 INSERT A FILE 5 INSERT AN ALBUM WITH PHOTOS 6 Login 1) go to - http://section.es
