BCS-FACS 7th Refinement Workshop
|
|
|
- Sydney Dennis
- 5 years ago
- Views:
Transcription
1 ELECTRONIC WORKSHOPS IN COMPUTING Series edited by Professor C.J. van Rijsbergen He Jifeng, Oxford University Computing Laboratory, UK, John Cooke, Loughborough University, UK, and Peter Wallis, University of Bath, UK (Eds) BCS-FACS 7th Refinement Workshop Proceedings of the BCS-FACS 7th Refinement Workshop, Bath, 3-5 July 1996 Interpreting Nondeterminism in the Refinement Calculus (Invited Lecture) R.J.R. Back and J. von Wright Published in Collaboration with the British Computer Society Copyright in this paper belongs to the author(s) ISBN
2 Ralph-Johan Back Department of Computer Science, Abo Akademi University Turku, Finland Joakim von Wright Department of Computer Science, Abo Akademi University Turku, Finland Abstract We introduce a simple programming language and ine its predicate transformer semantics. We motivate the choice of the constructs for the language by algebraic arguments, showing that the constructs are essentially the basic algebraic operations that are available for predicate transformers, when these are viewed as forming a complete lattice enriched category. We then show that the statements in the language can be given a simple operational interpretation, as describing the interaction between a user and a computing system. This gives a general intuitive interpretation of angelic and demonic nondeterminism. We also consider the notion of correctness and refinement of program statements that this intuitive interpretation gives rise to, and show the connection between the user-system interpretation and the interpretation of program execution as a game. 1 Introduction We will ine a simple programming language, intended to capture the interaction between a computing system and its user. We first describe the language formally (syntax and semantics) and motivate the choice of the language constructs by appealing to their fundamental algebraic properties. Our main interest here is, however, to give a simple intuitive interpretation of the programming language, and to motivate the notions of correctness and refinement for this language. Consider the following simple language of (program) statements: S ::= abort skip magic {p} [p] f {Q} [Q] (Basic statements) S 1 ; S 2 S 1 S 2 S 1 S 2 ( i I.S i ) ( i I.S i ) (Compound statements) A program statement is always associated with an initial state space Σ and a final state space Γ. These state spaces are types (we will later be more specific about what the state spaces are). The intuition is that execution of S always starts in some state σ :Σand if it terminates normally, then it terminates in a final state γ :Γ. In the syntax above, p :Σ Bool is a state predicate that assigns a truth value to each state, f :Σ Γis a state transformer (a total function) that maps every state in Σ to a new state in Γ, while Q :Σ Γ Bool is a state relation that relates a state in Σ to zero, one or more new states in Γ. The statements abort, skip and magic are special constants of the language. The compound constructs express a statement S in terms of component statements S 1, S 2 or in terms of a set {S i i I} of statements. 1.1 Predicate transformer interpretation Following Dijkstra [5], the statements are interpreted as predicate transformers, i.e., as functions that map a postcondition (a predicate on the final state space) to a precondition (a predicate on the initial state space). A predicate can be seen either as a function from states to truth values, or we can interpret it as a set of states (i.e., the set of states that are mapped to truth by the predicate). Below, we use the latter interpretation. BCS-FACS 7th Refinement Workshop 1
3 Let q be a predicate over the final state space Γ, and let σ be a state in the initial state space Σ. Furthermore, let true stand for the identically true predicate, i.e., the universal set Σ, and let false stand for the identically false predicate, i.e., the empty set. We have the following initions for the basic statements: abort q skip q magic q {p} q [p] q f q {Q} q [Q]q = false = q = true = p q = p q = f 1 q = {σ Qσ q} = {σ Qσ q }. For the compound statements, we ine (S 1 ; S 2 ) q (S 1 S 2 ) q (S 1 S 2 )q ( i I.S i )q ( i I.S i )q = S 1 (S 2 q) = (S 1 q) (S 2 q) = (S 1 q) (S 2 q) = ( i I.S i q) = ( i I.S i q). 1.2 Algebraic interpretation The predicate transformers form a category, where the state spaces Σ, Γ,... are the objects of the category, and the morphisms S :Σ Γ are predicate transformers (we will write Σ Γ for the predicate transformers with initial state space Σ and final state space Γ). The identity morphisms in this category are the statement skip :Σ Σ while sequential composition is the composition of morphisms. The predicates on a state space Σ form the powerset of Σ, which is a complete boolean lattice with set inclusion as the ordering. The empty set (false) is the bottom of this lattice, while the universal set (true) is the top of the lattice. Intersection is lattice meet, union is lattice join, and complement (negation) is lattice complement. The predicate transformers Σ Γ are ordered by the refinement relation (originally introduced by Back [1]), ined by S S = ( q. S q S q). The predicate transformers Σ Γ also form a complete boolean lattice with respect to the refinement relation. The statement abort is the bottom of this lattice, while magic is the top of the lattice. Meet is S 1 S 2 and join is S 1 S 2. Statement ( i I.S i ) is the meet of the set of statements {S i i I}, while ( i I.S i ) is the join of this set of statements. Both exist, because the lattice of predicate transformers is complete. Finally, we can consider the statements {p} and [p] as two different embeddings of the lattice of predicates over Σ into the lattice Σ Σ of predicate transformers. Similarly, we can consider f as an embedding of functions f :Σ Γinto predicate transformers f :Σ Γ, and {Q} and [Q] as two different embeddings of relations Q :Σ Γ Bool into predicate transformers Σ Γ. One can show that these embeddings are in fact quite regular, in the sense that they preserve much of the lattice and category structure of the domain. For instance, we have that {p q} = {p} {q}, so that meets in the predicate lattice are mapped to meets in the predicate transformer lattice, and we have similarly that {p q} = {p} {q}. Also, we have {false} = abort, so the bottom of the predicate lattice is mapped to the bottom of the predicate transformer lattice. However, {true} magic, so the top of the predicate BCS-FACS 7th Refinement Workshop 2
4 lattice is not mapped to the top of the predicate transformer lattice. From a category theoretic view, we can show that all these embeddings are in fact functors, when state predicates, state transformers and state relations are viewed as categories of the appropriate kind. For more detailed investigations of predicate transformers in the light of category theory we refer to Naumann [9] and Martin [7]. 1.3 Monotonicity A predicate transformer S is monotonic,ifp qimplies that Sp Sq. The set of monotonic predicate transformers with initial state space Σ and final state space Γ form a complete (but not boolean) lattice, with the same top, bottom, meet and join as the lattice of all predicate transformers. Sequential composition is monotonic with respect to the refinement ordering, when we restrict ourselves to monotonic predicate transformers: (S S ) (T T ) S; T S ; T. ( ) The monotonic predicate transformers form a subcategory of the predicate transformer category, with same identity element and same composition operation. This category is a complete lattice enriched category, because the morphisms (monotonic predicate transformers) from Σ to Γ form a complete lattice and the property ( ) holds. The program statements are all monotonic, when interpreted as predicate transformers. On the other hand, we can show that any monotonic predicate transformers can be expressed as statements, so the statements form a normal form for the monotonic predicate transformers. In fact, any monotonic predicate transformer S can be expressed as a statement {P };[Q], for some choice of relations P and Q (that depends on the predicate transformer S). The program statements are thus built using basic algebraic constructs that have very regular mathematical properties. We can argue that the statement constructs are not introduced ad hoc but each one is a basic lattice theoretic or category theoretic construct, or justified by the embedding of predicates, state transformers and relations into the predicate transformers. The question now is whether these constructs also make sense operationally, i.e., do we have a good informal and operational interpretation of statements, so that the language can be used in the design of computing systems. Below we show that this is indeed the case. 2 Operational interpretation of statements We consider a situation where a user interacts with a computing system through a common interface consisting of global, shared variables. Both the user and the system can read and write the global variables. A program statement describes the way in which the interaction between the user and system takes place. Essentially, it describes the interaction as a sequence of small incremental changes to the global state determined by the global variables. Below, we will go through the constructs of our language one by one, and explain informally how they would be executed. 2.1 Changing the state The skip statement skip is a dummy statement, that does not change the state. Hence, it is very easy to execute. The deterministic update f computes a new state f(σ) from the present state σ. The skip statement is a special case of the deterministic update where f is the identity function on the state, i.e., skip = id). An assignment statement like x := x +1, which increments state component x by one, is a special kind of deterministic update, as is a multiple assignment statement like x, y := x + y, x y, which assigns the sum of x and y to state component x and their difference to state component y. The assignment statement is expressed in terms of program variables x and y, that denote components of the state space, which we assume here to be a product of simpler types. We can use a program variable declaration, like var x, y, z : Nat to indicate that the state space has three components, which are called x, y, z, respectively, in this case all of type Nat. This declaration is a convenient shorthand that permits us to leave out the explicit lambda abstraction for state BCS-FACS 7th Refinement Workshop 3
5 predicates, state transformations and state relations. The first assignment statement can then be expressed as x := x +1 (or λx,y,z. x := x +1 if we use explicit lambda notation). The second assignment is expressed as the deterministic update x, y := x + y, x y (or λx,y,z. x,y := x + y, x y if we again write out the lambda abstraction explicitly). The angular brackets are usually omitted around assignment statements like this, but are needed for updates with arbitrary state transformers. 2.2 Sequential composition Sequential composition S 1 ; S 2 also has the usual meaning: it describes the order of progression in the computation. It permits us to describe a big computation as a sequence of smaller computation steps. Thus x := x +1 ; x, y := x + y, x y carries out the two assignments in succession. 2.3 Failure The aborting statement abort stands for a completely unined computation. That is, we do not know what can happen if we execute this statement. The system may suddenly terminate in some inconsistent state, it might become completely unresponsive because it is stuck in an infinite loop, or any other nasty things may happen. It is also possible that the system just does some normal computation, but we do not know what. The main point is that we, as the user of the system, completely lose control of the computation. Executing an abort statement is thus a failure, and is something the user wants to avoid at all cost. Programs should therefore be designed in such a way that the abort statement is never executed. The assert statement {g} qualifies the aborting statement, so that aborting only occurs when condition g does not hold. For instance, the assertion {x y} will abort the program execution in a state where x y does not hold, but otherwise the statement has no effect. Abortion and skip are both special cases of the assert statement: {false} = abort and {true} = skip (remember that false is never satisfied while true is always satisfied in a state). 2.4 Selecting alternatives The angelic choice statement S 1 S 2 is interpreted as a request to the user to choose one of the two alternative statements. Execution is halted at this statement and the user is informed that he needs to make a choice. The user then has to indicate which of the statements S 1 or S 2 that he wants to continue with. Once he has done this, execution continues with the selected statement. Selections with more than two alternatives are ined by repeated selection, so that, e.g., S 1 S 2 S 3 =(S 1 S 2 ) S 3. Selection is associative, so it does not really matter how the expression is parenthesized. The alternatives can be presented to the user in different ways. They can be given in a menu, the user may be asked for the number that identifies the selected alternative, or the alternatives may be associated with buttons on the screen. Other schemes for arranging the selection are also conceivable. An angelic choice operator (the join operator for predicate transformer lattices) was introduced independently by Gardiner and Morgan [6] (as a conjunction operator ) and by Back and von Wright [2]. The operator was called angelic because the choice is made in such a way that the postcondition is established, if possible. 2.5 Input statement The angelic update statement {Q} also has a very familiar meaning in programs. It is a request for an input value. Executing this statement in state σ means that the system asks the user to choose a next state σ, from which to continue the execution. The choice must be such that relation Qσσ holds. If there is no σ that satisfies the condition, then the execution aborts. An input statement will usually not ask the user to determine a completely new state, but only to select the value for some specific state component. An angelic assignment is an angelic update of the form {x := x Q}, where the user only needs to select a value for the state component(s) x, while all other state components retain their old values. For instance, a program to compute the square root could contain the statement {x, e := x 0,e 0 x 0 0 e 0 >0}, where x and e are two program variables. The statement asks the user to select a specific value x 0 0 for x and e 0 > 0 for BCS-FACS 7th Refinement Workshop 4
6 e (we will later use x as a value for which the square root is computed and e as the precision). The angelic assignment statement thus indicates which components should be given new input values, and also describes the legal inputs for these. The assert statement is a special case of the angelic update where the state is not changed: {p} = { p }, where p σσ (pσ σ =σ ). 2.6 Waiting The statement magic is known as a miracle [8]. The system cannot, of course, do a miracle, so it has to do what everybody else does: it has to wait for a miracle (which will never happen). In other words, the magic statement is really a wait statement. It can also be understood as a deadlock statement, because it simply prevents the execution from proceeding. A deadlock is not the same as an abortion, because it is not considered to be an error. On the contrary, it is an extreme safeguard against an error: rather than taking the risk of making an error, we do nothing. The guard statement [g] is a qualified wait statement, which will only wait when the condition g is not true. In this way, the guard g is a real guard: it permits execution to proceed when g holds, and forces the execution to wait when g does not hold. The guard can be understood as an enabling condition, which states under which condition it is permitted to execute the statement following the guard. For instance, the guard [x <y]permits execution to proceed if x<y. The guard is mostly used in the composition [g]; S, which is abbreviated as g S, a so called (naked) guarded command. Miracle and skip are both special cases of the guard statement: [false] =magic and [true] =skip. 2.7 Uncertainty The demonic choice statement S 1 S 2 reflects our uncertainty as to how the execution will proceed. We (the user of the program) do not know which one of the alternatives S 1 or S 2 will actually be chosen by the system. Since we do not have this information, we need to guard against either choice if we want to be certain to achieve some specific final state with our program (this justifies calling the choice demonic ). Again, we can generalize the demonic choice to an arbitrary number of alternatives S 1 S 2... S n by repeated choice. Why would we, as program designers, want to permit this kind of uncertainty in our programs? Would it not be simpler to state explicitly which way the execution will proceed, and thus save ourselves the trouble of considering a number of different alternatives? In many situations we do not really have a choice, because we do not know which alternative will be chosen. In other situations, we do not really need to be completely explicit about what the program should do, it is sufficient that the statement behaves in a certain way for us to achieve the goals that we want to. It is better to leave ourselves some freedom to be more inite about the appropriate alternative later on, when we need to improve the program s time or space efficiency, or make it better with respect to some other criteria. The system is assumed to be eager to proceed, and will thus avoid waiting whenever possible. If one of the statements S i in a demonic choice leads to a miracle and hence to a forced wait, then the system will not choose this one, if there is another choice that allows it to proceed. Consider as an example the statement (x >0 x:= x +1) (x<0 x:= x 1) In an initial state where x =3the system would choose the first alternative, because the second alternative would lead to deadlock. In initial state x = 3, the second alternative would again be chosen. In initial state x =0the only choice is to wait. 2.8 Specification The demonic update statement [Q] (originally introduced by Back [1] as a nondeterministic assignment) describes a state change where the result may be uncertain. Executing [Q] in an initial state σ, we know that execution will continue with some σ such that Qσσ holds, if possible, but we do not know exactly which state σ will be selected, if there is more than one candidate. If there is no σ such that Qσσ holds, then the system must wait. The demonic update statement is a specification of what is actually done by the system during execution. An example is provided by a BCS-FACS 7th Refinement Workshop 5
7 demonic assignment [x := x 1 e x x 2 1 e], which assigns to x some new value x 1 which is the square root of x with precision e. Two successive executions of the same demonic update statement do not have to give the same final state. The reasons for this could be many. It could be that the actual implementation of the statement is based on some random natural phenomena and hence cannot be repeated. The implementation can be pseudo-random, in the sense that a random number generator is used to choose among the possible final states. Often the implementation has a hidden state that is preserved from one invocation of the statement to next, and this influences the choice the next time around. It is also possible that the same program is intended to run with different implementation versions of the specification and that these versions differ in some unimportant ways in how the new state is chosen. We are not allowed to know which version is actually being used, because the two versions should be mutually interchangeable. The specification statement is a device by which we can control the information made available about program components. It allows us to postpone decision about details in the design until later. Only the information that is absolutely needed for successful use of a component should be given, and the rest is best hidden from the user. This gives the biggest possible freedom for the implementer of the component, to find a good implementation and to change the implementation when necessary, without affecting the other components in the program that use it. The demonic update statement is the basic construct for achieving this kind of information hiding. 3 Derived statements Composing the basic statements in specific ways gives rise to a large selection of interesting and useful constructs. For instance, the statement {x, e := x 0,e 0 x 0 0 e 0 >0}; [x:= x 1 e x x 2 1 e] is a very general specification for a square root program: first the user is asked to select the value for which the square root is to be computed and the precision with which it is computed, and then the system computes an approximation of the square root with this precision. Some statement constructs are so useful that it is motivated to give them a syntax of their own. We refer to these as derived statements. In practice, we usually work with the derived statements directly and can forget about how they were ined, provided that we have established enough useful properties of the derived statements. As a simple example of this, we will look at how to ine conditional statements and while-loops as derived statements. 3.1 Conditional statements The usual guarded conditional statement, introduced by Dijkstra [5], is ined by if g 1 S 1 []...[] g n S n fi = {g 1... g n };([g 1 ]; S 1... [g n ]; S n ). Thus, the conditional statement aborts if none of the guards g i is satisfied. If at least one guard is satisfied, then one of the enabled statements is chosen for execution. The choice is demonic, so we do not know which one is chosen when two or more alternatives are enabled. However, as the system is eager to proceed, it will not choose an alternative that is not enabled, if there are enabled alternatives available. If the guards are mutually exclusive, the conditional statement is really deterministic, and there is no uncertainty associated with the outcome of the statement. This is the way conditional statements are usually ined in existing programming languages. An example of a guarded command is if x y x := y[] x y skip fi which sets x to the minimum of x and y. BCS-FACS 7th Refinement Workshop 6
8 A variant of the conditional statement would be the following statement await g 1 S 1 []...[] g n S n end = [g 1 ]; S 1... [g n ]; S n. This statement chooses to wait rather than abort, when none of the conditions is satisfied. In other words, the statements awaits the fulfillment of one of the enabling conditions. A construct like this could be used to synchronize the execution of parallel processes. A further variant of the conditional statement is choose g 1 : S 1 []...[] g n : S n end = {g 1 }; S 1... {g n };S n. In this case, the alternatives are given as selections. The assert statements g i are evaluated in the current state, and those alternatives for which the conditions holds are presented to the user to choose from. The expectation is that one of the conditions is true (if not, then execution will abort). Thus, we have a context dependent selection. If the conditions are mutually exclusive, then the choice is deterministic, and there is no need to bother the user with making a selection. In this case, this construct and the guarded conditional statement have exactly the same behavior. Finally, we have the variant select g 1 : S 1 []...[] g n : S n end = [g 1... g n ]; ({g 1 }; S 1... {g n };S n ). In this case execution may only proceed if we know that there is at least one alternative that can actually be selected. In other words, the system waits rather than aborts if no alternative is enabled. 3.2 Iteration and recursion There are two statement constructs that we have not yet considered, the general angelic choice ( i I.S i ) and the general demonic choice ( i I.S i ). These are just the generalizations of the angelic and demonic choice statements so that the choice can be made among an arbitrary, even infinite, set of statements {S i i I}. In the special case that I is empty, the general angelic choice is ined to be abort and the general demonic choice is ined to be magic. We will illustrate the angelic choice by ining the traditional while loop in terms of it. We ine the while loop by where while g do S od = ( i Nat. Do i), Do 0 = abort Do (i +1) = if g S; Do i [] g skip fi, i 0. We assume here for simplicity that the statement S is deterministic, to avoid problems involving unbounded nondeterminism. In other words, Do 0 will abort immediately, Do will terminate normally if g holds, otherwise it will execute S and then it will abort, Do 2 will try one more iteration before aborting, and so on. In general, the statement Do (i+1) will execute statement S at most i times. If the loop would terminate within i iterations, then Do (i +1)will also terminate, with the same result. If more iterations would be required, then the statement Do (i +1)will abort instead. Thus, Do i is the ith approximation of the loop. The infinite angelic choice describes the execution of the loop. The user tries to avoid aborting, so in each state, he will choose an approximation Do i that is big enough so that the loop will terminate, if this is possible. If there is no such i, then the loop would also not terminate. The user is then forced to choose one of the aborting alternatives (which one does not matter, as the computation will fail anyway). BCS-FACS 7th Refinement Workshop 7
9 In programming languages, the iteration is usually implemented in a different way, but the effect is the same. Rather than letting the user make the choice, the system tries the approximations Do 0, Do 1, Do 2,...one by one, by at each stage iterating once more, if termination was not achieved with the previous choice. If there is a greatest number i of iterations required, then the effect will be exactly the same as if the user would have made the (right) choice Do (i +1) directly. If, however, the loop does not terminate, then the system will actually be stuck an infinite loop. Both situations are equally bad, and in the Refinement Calculus, these two possibilities are identified, because in both cases, the user has lost control over the computation. Recursive statements can be ined in the same way, in terms of infinite angelic choice among approximation. The main point here is that we do not need to postulate an explicit iteration (or recursion) construct, because essentially the same computational behavior can be described with infinite angelic choice. We choose the latter as a basic statement constructor in our language, because it has much nicer mathematical properties than an explicit loop or recursion construct. The infinite demonic choice is also useful for describing programming notions, but we will not go into details of this here. 4 Correctness Having introduced a notation for program statements, we next need to decide what to do with them. Basically, we use program statements to describe how computations are to be performed. A central question is then whether the statement that we have ined can be used for what we need, i.e., whether the statement is correct with respect to some given specification. The other central question is how to improve on the statement, in a way that preserves correctness, i.e., how to refine it. Let us first consider what it means for a program statement to be correct. For statements that do not contain any choice constructs, the question is quite easy to answer. First, we specify what the program is supposed to do by giving a precondition p that may be assumed to hold for the initial state and a postcondition q that is required to hold for the final state. The program S is then correct with respect to this specification, if the final value computed by the program satisfies q whenever the initial value satisfies p. This is denoted p { S } q. As an example, we have that x =0{ x := x +1 }x=1. In other words, if x =0initially, then the assignment statement will change the state so that x =1. Consider now what it means for S to be correct when the statement exhibits angelic nondeterminism. In this case, the user is given different choices for how to proceed during the computation. The statement S can be considered correct if the user can always make his choices so that q is established when S is started in an initial state that satisfies p. In other words, the user can establish postcondition q. An example is x =0{ x := x +1 x:= x +2 }x=1. In this case, the user can make his choice so that in the final state x =1. When our statement S exhibits demonic nondeterminism, then we require that q must be established by S when started in an initial state that satisfies p, no matter how the nondeterminism is resolved by the system during execution. In other words, the system cannot avoid establishing q. As an example, we have that x =0{ x := x +1 x:= x +2 }(x=1 x=2). The system must choose either statement, so it cannot avoid setting establishing the required postcondition. However, x =0{ x := x +1 x:= x +2 }x=1does not hold, because the system might choose the second alternative. The execution of a program can now be seen as a game between the user and the system. The rules of the game are given by the statement S as we have explained above, the possible initial positions of the game by the precondition p, and the winning positions for the user are determined by the postcondition q. Correctness of S with respect to precondition p and postcondition q, p { S } q, will then mean that the user has a winning strategy for reaching q from any initial state in p. In other words, the user can always win the game, no matter how the system plays [3]. BCS-FACS 7th Refinement Workshop 8
10 5 Refinement of statements Once we have a statement that is correct in the sense above, how can we make it better (more efficient, more portable, less space hungry etc.) without losing the correctness. In other words, how do we refine the program to better suit our purposes. Intuitively, program refinement means modifying a program while preserving correctness. This means that the refinement S of S must be correct with respect to any pre-postcondition pair (p, q) for which S is correct. Thus, S is refined by S if ( p, q. p { S } q p { S } q) ( ) We can show that this condition is equivalent to S S as we ined it earlier. Hence, the refinement relation captures the notion of a correctness preserving refinement. For angelic constructs, the notion of refinement that we have chosen implies that adding new alternatives to an angelic program is a refinement. Thus, S 1 S 2 is refined by S 1 S 2 S 3, for any S 3. Given the intuitive explanation of angelic choice above, it should be clear that this does indeed preserve correctness. In the refined program, we will be offered more choices than we had in the original program. However, the old alternatives remain, and we may select these to achieve whatever we wanted to achieve with the original program. The refined program has then more capabilities, because there may be things we can achieve (final states that we can reach) that we could not achieve before. In this sense, refinement increases the power of the statement. A particular case of refinement is when we replace abort with a statement that does not abort. In this case, the capabilities of the statement are also increased, because where earlier abortion was unavoidable, it may now be possible to continue execution and reach some interesting final state. This refinement could be interpreted as fixing a component that was broken. Refining an assert statement means making the condition more permissive, so that less states will cause abortion. We are thus improving this component by making it work properly in situations where it would not work before. An example of refinement of an angelic statement is {x, e := x 0,e 0 x 0 0 e } {x, e := x 0,e 0 x 0 0 e }. In this case, the user of the refined angelic assignment has more choices for the precision e than what he had in the original program. Refinement of a demonic program statement is quite different from refinement of an angelic statement. Refinement for demonic statements means decreasing the uncertainty about the effect of executing the statement. A demonic choice S 1 S 2 S 3 is, e.g., refined by the choice S 1 S 2. In this case, we have removed one possible option that the system could choose. If the program worked correctly no matter which of the alternatives S 1, S 2 or S 3 was selected by the system, it obviously has to work correctly if the system has less alternatives to choose from. We will know more about what could happen when the statement is executed. In other words, refinement means that the uncertainty is decreased and information is increased. For a specification [Q], refinement means that the choice of the next state is more deterministic. This usually means that the specification is closer to an actual implementation in a programming language. Program construction often proceeds in a stepwise manner from a very general specification to a very specific and deterministic implementation, intended to be a refinement of the original specification. A deterministic statement S can in fact be refined even further. One possibility is to refine it to g S, i.e., associate a nontrivial enabledness condition with it. The statement S itself is equivalent to true S, so refinement here just means tightening the conditions for enabledness. In this case, we consider the introduction of a deadlock as an improvement of the original program which did not deadlock. This might seem paradoxical, but it can be justified as follows: The statement S itself could lead to an abortion, and hence the whole execution would fail. However, the statement g S might be disabled in the situation where S would abort. In this sense, we prefer waiting (delayed execution) to explicit failure. An example of refinement of a demonic statement is the following: [x := x 1 e x x 2 1 e] BCS-FACS 7th Refinement Workshop 9
11 [x := x 1 e/2 x x 2 1 e/2]. In this case, the precision with which the square root is computed has been doubled, and hence, the user has more information about what the final value of x will be. In general, we see that refinement of program statements amounts to improving the user s control of how the program is executed, either by decreasing the uncertainty of how a statement is actually executed, or by adding explicit new alternative ways for the user to choose. In the game theoretic interpretation, refinement means changing the program so that the user s possibilities of winning are increased (or at least, not decreased). By the monotonicity of sequential composition, we can combine the above two refinements: {x, e := x 0,e 0 x 0 0 e }; [x:= x 1 e x x 2 1 e] {x, e := x 0,e 0 x 0 0 e }; [x:= x 1 e/2 x x 2 1 e/2]. The refined program gives both more choices to the user, and computes the square root with greater precision than the original program. 6 Conclusions We have above described a simple language for describing the interaction between a user and a system. The basic constructs of the language are motivated by their fundamental algebraic properties. We gave a rather simple reading of the program constructs used in the refinement calculus, including such constructs as miracles, angelic choices and angelic updates, which have traditionally been considered quite exotic. We showed that a reasonable interpretation of such constructs is obtained by not only considering what the computing system can do, but also taken into account what the user of the system can do. This interpretation will also give a rather straightforward interpretation of correctness and refinement of programs with angelic and demonic nondeterminism. We will The themes treated in this paper are investigated in more detail in a book [4]. The results above can also be seen as an argument against the standard collection of fundamental statements in programming logics. Constructs like conditional statements and while loops, which are usually taken to be fundamental, are in fact much less regular than the basic lattice and category theoretic operations that we propose here. Similarly, the discussion above can be seen as a motivation for working in the full lattices of predicate transformers, rather than restricting oneself to weaker structures like complete partial orders. References [1] R.J. Back. Correctness Preserving Program Refinements: Proof Theory and Applications, volume 131 of Mathematical Center Tracts. Mathematical Centre, Amsterdam, [2] R.J. Back and J. von Wright. Duality in specification languages: a lattice-theoretical approach. Acta Informatica, 27: , [3] R.J. Back and J. von Wright. Games and winning strategies. Information Processing Letters, 53: , [4] R.J. Back and J. von Wright. Refinement Calculus. Book in preparation. [5] E.W. Dijkstra. A Discipline of Programming. Prentice Hall International, [6] P.H. Gardiner and C.C. Morgan. Data refinement of predicate transformers. Theoretical Computer Science, 87(1): , [7] C.E. Martin. Preordered Categories and Predicate Transformers. PhD thesis, Oxford University, [8] C.C. Morgan. The specification statement. ACM Transactions on Programming Languages and Systems, 10(3): , July BCS-FACS 7th Refinement Workshop 10
12 [9] D.A. Naumann. Two-Categories and Program Structure: Data Types, Refinement Calculi and Predicate Transformers. PhD thesis, University of Texas at Austin, BCS-FACS 7th Refinement Workshop 11
6.001 Notes: Section 6.1
 6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
6.001 Notes: Section 8.1
 6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
6.001 Notes: Section 8.1 Slide 8.1.1 In this lecture we are going to introduce a new data type, specifically to deal with symbols. This may sound a bit odd, but if you step back, you may realize that everything
Programming Languages Third Edition
 Programming Languages Third Edition Chapter 12 Formal Semantics Objectives Become familiar with a sample small language for the purpose of semantic specification Understand operational semantics Understand
Programming Languages Third Edition Chapter 12 Formal Semantics Objectives Become familiar with a sample small language for the purpose of semantic specification Understand operational semantics Understand
3.7 Denotational Semantics
 3.7 Denotational Semantics Denotational semantics, also known as fixed-point semantics, associates to each programming language construct a well-defined and rigorously understood mathematical object. These
3.7 Denotational Semantics Denotational semantics, also known as fixed-point semantics, associates to each programming language construct a well-defined and rigorously understood mathematical object. These
Chapter 3. Set Theory. 3.1 What is a Set?
 Chapter 3 Set Theory 3.1 What is a Set? A set is a well-defined collection of objects called elements or members of the set. Here, well-defined means accurately and unambiguously stated or described. Any
Chapter 3 Set Theory 3.1 What is a Set? A set is a well-defined collection of objects called elements or members of the set. Here, well-defined means accurately and unambiguously stated or described. Any
Formalizing Dijkstra
 Formalizing Dijkstra 1 Formalizing Dijkstra John Harrison Intel Corporation A Discipline of Programming Mechanizing programming logics Relational semantics Weakest preconditions Guarded commands Theorems
Formalizing Dijkstra 1 Formalizing Dijkstra John Harrison Intel Corporation A Discipline of Programming Mechanizing programming logics Relational semantics Weakest preconditions Guarded commands Theorems
[Ch 6] Set Theory. 1. Basic Concepts and Definitions. 400 lecture note #4. 1) Basics
![[Ch 6] Set Theory. 1. Basic Concepts and Definitions. 400 lecture note #4. 1) Basics [Ch 6] Set Theory. 1. Basic Concepts and Definitions. 400 lecture note #4. 1) Basics](/thumbs/82/86066673.jpg) 400 lecture note #4 [Ch 6] Set Theory 1. Basic Concepts and Definitions 1) Basics Element: ; A is a set consisting of elements x which is in a/another set S such that P(x) is true. Empty set: notated {
400 lecture note #4 [Ch 6] Set Theory 1. Basic Concepts and Definitions 1) Basics Element: ; A is a set consisting of elements x which is in a/another set S such that P(x) is true. Empty set: notated {
Meeting13:Denotations
 Meeting13:Denotations Announcements Homework 3 due next week Friday at 6:00pm Homework2Comments Time: 29.2 hours avg Difficulty: 5.4 avg Issues Length? (Part 2 out Wed instead of Mon) Misunderstanding
Meeting13:Denotations Announcements Homework 3 due next week Friday at 6:00pm Homework2Comments Time: 29.2 hours avg Difficulty: 5.4 avg Issues Length? (Part 2 out Wed instead of Mon) Misunderstanding
Induction and Semantics in Dafny
 15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
A Formal Approach to Program Modification. Lindsay Groves
 A Formal Approach to Program Modication Lindsay Groves School of Mathematical and Computing Sciences Victoria University of Wellington, New Zealand lindsay@mcs.vuw.ac.nz Abstract This paper presents a
A Formal Approach to Program Modication Lindsay Groves School of Mathematical and Computing Sciences Victoria University of Wellington, New Zealand lindsay@mcs.vuw.ac.nz Abstract This paper presents a
Dependent Object Types - A foundation for Scala s type system
 Dependent Object Types - A foundation for Scala s type system Draft of September 9, 2012 Do Not Distrubute Martin Odersky, Geoffrey Alan Washburn EPFL Abstract. 1 Introduction This paper presents a proposal
Dependent Object Types - A foundation for Scala s type system Draft of September 9, 2012 Do Not Distrubute Martin Odersky, Geoffrey Alan Washburn EPFL Abstract. 1 Introduction This paper presents a proposal
On the Definition of Sequential Consistency
 On the Definition of Sequential Consistency Ali Sezgin Ganesh Gopalakrishnan Abstract The definition of sequential consistency is compared with an intuitive notion of correctness. A relation between what
On the Definition of Sequential Consistency Ali Sezgin Ganesh Gopalakrishnan Abstract The definition of sequential consistency is compared with an intuitive notion of correctness. A relation between what
Handout 9: Imperative Programs and State
 06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 9: Imperative Programs and State Imperative
Discrete Mathematics Lecture 4. Harper Langston New York University
 Discrete Mathematics Lecture 4 Harper Langston New York University Sequences Sequence is a set of (usually infinite number of) ordered elements: a 1, a 2,, a n, Each individual element a k is called a
Discrete Mathematics Lecture 4 Harper Langston New York University Sequences Sequence is a set of (usually infinite number of) ordered elements: a 1, a 2,, a n, Each individual element a k is called a
Meeting14:Denotations
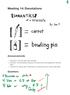 Meeting14:Denotations Announcements Homework 3 due next week Friday at 6:00pm Reminder: 5-minute feedback discussion with Sean is part of the assignment ("interview light") Talk (with me, with the class
Meeting14:Denotations Announcements Homework 3 due next week Friday at 6:00pm Reminder: 5-minute feedback discussion with Sean is part of the assignment ("interview light") Talk (with me, with the class
Lists. Michael P. Fourman. February 2, 2010
 Lists Michael P. Fourman February 2, 2010 1 Introduction The list is a fundamental datatype in most functional languages. ML is no exception; list is a built-in ML type constructor. However, to introduce
Lists Michael P. Fourman February 2, 2010 1 Introduction The list is a fundamental datatype in most functional languages. ML is no exception; list is a built-in ML type constructor. However, to introduce
axiomatic semantics involving logical rules for deriving relations between preconditions and postconditions.
 CS 6110 S18 Lecture 18 Denotational Semantics 1 What is Denotational Semantics? So far we have looked at operational semantics involving rules for state transitions, definitional semantics involving translations
CS 6110 S18 Lecture 18 Denotational Semantics 1 What is Denotational Semantics? So far we have looked at operational semantics involving rules for state transitions, definitional semantics involving translations
Lecture Notes on Contracts
 Lecture Notes on Contracts 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 30, 2012 1 Introduction For an overview the course goals and the mechanics and schedule of the course,
Lecture Notes on Contracts 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 30, 2012 1 Introduction For an overview the course goals and the mechanics and schedule of the course,
Denotational Semantics of a Simple Imperative Language Using Intensional Logic
 Denotational Semantics of a Simple Imperative Language Using Intensional Logic Marc Bender bendermm@mcmaster.ca CAS 706 - Programming Languages Instructor: Dr. Jacques Carette Dept. of Computing and Software
Denotational Semantics of a Simple Imperative Language Using Intensional Logic Marc Bender bendermm@mcmaster.ca CAS 706 - Programming Languages Instructor: Dr. Jacques Carette Dept. of Computing and Software
Goals: Define the syntax of a simple imperative language Define a semantics using natural deduction 1
 Natural Semantics Goals: Define the syntax of a simple imperative language Define a semantics using natural deduction 1 1 Natural deduction is an instance of first-order logic; that is, it is the formal
Natural Semantics Goals: Define the syntax of a simple imperative language Define a semantics using natural deduction 1 1 Natural deduction is an instance of first-order logic; that is, it is the formal
6. Hoare Logic and Weakest Preconditions
 6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
Shared Variables and Interference
 Illinois Institute of Technology Lecture 24 Shared Variables and Interference CS 536: Science of Programming, Spring 2018 A. Why Parallel programs can coordinate their work using shared variables, but
Illinois Institute of Technology Lecture 24 Shared Variables and Interference CS 536: Science of Programming, Spring 2018 A. Why Parallel programs can coordinate their work using shared variables, but
Semantics via Syntax. f (4) = if define f (x) =2 x + 55.
 1 Semantics via Syntax The specification of a programming language starts with its syntax. As every programmer knows, the syntax of a language comes in the shape of a variant of a BNF (Backus-Naur Form)
1 Semantics via Syntax The specification of a programming language starts with its syntax. As every programmer knows, the syntax of a language comes in the shape of a variant of a BNF (Backus-Naur Form)
Lecture Notes on Program Equivalence
 Lecture Notes on Program Equivalence 15-312: Foundations of Programming Languages Frank Pfenning Lecture 24 November 30, 2004 When are two programs equal? Without much reflection one might say that two
Lecture Notes on Program Equivalence 15-312: Foundations of Programming Languages Frank Pfenning Lecture 24 November 30, 2004 When are two programs equal? Without much reflection one might say that two
Propositional Logic. Part I
 Part I Propositional Logic 1 Classical Logic and the Material Conditional 1.1 Introduction 1.1.1 The first purpose of this chapter is to review classical propositional logic, including semantic tableaux.
Part I Propositional Logic 1 Classical Logic and the Material Conditional 1.1 Introduction 1.1.1 The first purpose of this chapter is to review classical propositional logic, including semantic tableaux.
Nano-Lisp The Tutorial Handbook
 Nano-Lisp The Tutorial Handbook Francis Sergeraert March 4, 2006 1 Various types of Nano-Lisp objects. There are several type notions and in this documentation only the notion of implementation type (itype
Nano-Lisp The Tutorial Handbook Francis Sergeraert March 4, 2006 1 Various types of Nano-Lisp objects. There are several type notions and in this documentation only the notion of implementation type (itype
(Refer Slide Time: 4:00)
 Principles of Programming Languages Dr. S. Arun Kumar Department of Computer Science & Engineering Indian Institute of Technology, Delhi Lecture - 38 Meanings Let us look at abstracts namely functional
Principles of Programming Languages Dr. S. Arun Kumar Department of Computer Science & Engineering Indian Institute of Technology, Delhi Lecture - 38 Meanings Let us look at abstracts namely functional
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5
 Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
Formal Methods of Software Design, Eric Hehner, segment 1 page 1 out of 5 [talking head] Formal Methods of Software Engineering means the use of mathematics as an aid to writing programs. Before we can
Application: Programming Language Semantics
 Chapter 8 Application: Programming Language Semantics Prof. Dr. K. Madlener: Specification and Verification in Higher Order Logic 527 Introduction to Programming Language Semantics Programming Language
Chapter 8 Application: Programming Language Semantics Prof. Dr. K. Madlener: Specification and Verification in Higher Order Logic 527 Introduction to Programming Language Semantics Programming Language
RSL Reference Manual
 RSL Reference Manual Part No.: Date: April 6, 1990 Original Authors: Klaus Havelund, Anne Haxthausen Copyright c 1990 Computer Resources International A/S This document is issued on a restricted basis
RSL Reference Manual Part No.: Date: April 6, 1990 Original Authors: Klaus Havelund, Anne Haxthausen Copyright c 1990 Computer Resources International A/S This document is issued on a restricted basis
Formal Methods. CITS5501 Software Testing and Quality Assurance
 Formal Methods CITS5501 Software Testing and Quality Assurance Pressman, R. Software Engineering: A Practitioner s Approach. Chapter 28. McGraw-Hill, 2005 The Science of Programming, David Gries, 1981
Formal Methods CITS5501 Software Testing and Quality Assurance Pressman, R. Software Engineering: A Practitioner s Approach. Chapter 28. McGraw-Hill, 2005 The Science of Programming, David Gries, 1981
Shared Variables and Interference
 Solved Shared Variables and Interference CS 536: Science of Programming, Fall 2018 A. Why Parallel programs can coordinate their work using shared variables, but it s important for threads to not interfere
Solved Shared Variables and Interference CS 536: Science of Programming, Fall 2018 A. Why Parallel programs can coordinate their work using shared variables, but it s important for threads to not interfere
Negations in Refinement Type Systems
 Negations in Refinement Type Systems T. Tsukada (U. Tokyo) 14th March 2016 Shonan, JAPAN This Talk About refinement intersection type systems that refute judgements of other type systems. Background Refinement
Negations in Refinement Type Systems T. Tsukada (U. Tokyo) 14th March 2016 Shonan, JAPAN This Talk About refinement intersection type systems that refute judgements of other type systems. Background Refinement
Z Notation. June 21, 2018
 Z Notation June 21, 2018 1 Definitions There are many different ways to introduce an object in a Z specification: declarations, abbreviations, axiomatic definitions, and free types. Keep in mind that the
Z Notation June 21, 2018 1 Definitions There are many different ways to introduce an object in a Z specification: declarations, abbreviations, axiomatic definitions, and free types. Keep in mind that the
A Small Interpreted Language
 A Small Interpreted Language What would you need to build a small computing language based on mathematical principles? The language should be simple, Turing equivalent (i.e.: it can compute anything that
A Small Interpreted Language What would you need to build a small computing language based on mathematical principles? The language should be simple, Turing equivalent (i.e.: it can compute anything that
Denotational Semantics. Domain Theory
 Denotational Semantics and Domain Theory 1 / 51 Outline Denotational Semantics Basic Domain Theory Introduction and history Primitive and lifted domains Sum and product domains Function domains Meaning
Denotational Semantics and Domain Theory 1 / 51 Outline Denotational Semantics Basic Domain Theory Introduction and history Primitive and lifted domains Sum and product domains Function domains Meaning
Denotational semantics
 1 Denotational semantics 2 What we're doing today We're looking at how to reason about the effect of a program by mapping it into mathematical objects Specifically, answering the question which function
1 Denotational semantics 2 What we're doing today We're looking at how to reason about the effect of a program by mapping it into mathematical objects Specifically, answering the question which function
Lecture 5. Logic I. Statement Logic
 Ling 726: Mathematical Linguistics, Logic. Statement Logic V. Borschev and B. Partee, September 27, 2 p. Lecture 5. Logic I. Statement Logic. Statement Logic...... Goals..... Syntax of Statement Logic....2.
Ling 726: Mathematical Linguistics, Logic. Statement Logic V. Borschev and B. Partee, September 27, 2 p. Lecture 5. Logic I. Statement Logic. Statement Logic...... Goals..... Syntax of Statement Logic....2.
Joint Entity Resolution
 Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
Joint Entity Resolution Steven Euijong Whang, Hector Garcia-Molina Computer Science Department, Stanford University 353 Serra Mall, Stanford, CA 94305, USA {swhang, hector}@cs.stanford.edu No Institute
LOGIC AND DISCRETE MATHEMATICS
 LOGIC AND DISCRETE MATHEMATICS A Computer Science Perspective WINFRIED KARL GRASSMANN Department of Computer Science University of Saskatchewan JEAN-PAUL TREMBLAY Department of Computer Science University
LOGIC AND DISCRETE MATHEMATICS A Computer Science Perspective WINFRIED KARL GRASSMANN Department of Computer Science University of Saskatchewan JEAN-PAUL TREMBLAY Department of Computer Science University
Fundamental Concepts. Chapter 1
 Chapter 1 Fundamental Concepts This book is about the mathematical foundations of programming, with a special attention on computing with infinite objects. How can mathematics help in programming? There
Chapter 1 Fundamental Concepts This book is about the mathematical foundations of programming, with a special attention on computing with infinite objects. How can mathematics help in programming? There
STABILITY AND PARADOX IN ALGORITHMIC LOGIC
 STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
STABILITY AND PARADOX IN ALGORITHMIC LOGIC WAYNE AITKEN, JEFFREY A. BARRETT Abstract. Algorithmic logic is the logic of basic statements concerning algorithms and the algorithmic rules of deduction between
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages
 Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Lecture 19 Tuesday, April 3, 2018 1 Introduction to axiomatic semantics The idea in axiomatic semantics is to give specifications
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Lecture 19 Tuesday, April 3, 2018 1 Introduction to axiomatic semantics The idea in axiomatic semantics is to give specifications
Mechanised Formal Reasoning About Modular Programs
 Mechanised Formal Reasoning About Modular Programs Linas Laibinis To be presented with the permission of the Faculty of Mathematics and Natural Sciences at Åbo Akademi University for public criticism in
Mechanised Formal Reasoning About Modular Programs Linas Laibinis To be presented with the permission of the Faculty of Mathematics and Natural Sciences at Åbo Akademi University for public criticism in
An Evolution of Mathematical Tools
 An Evolution of Mathematical Tools From Conceptualization to Formalization Here's what we do when we build a formal model (or do a computation): 0. Identify a collection of objects/events in the real world.
An Evolution of Mathematical Tools From Conceptualization to Formalization Here's what we do when we build a formal model (or do a computation): 0. Identify a collection of objects/events in the real world.
SOFTWARE ENGINEERING DESIGN I
 2 SOFTWARE ENGINEERING DESIGN I 3. Schemas and Theories The aim of this course is to learn how to write formal specifications of computer systems, using classical logic. The key descriptional technique
2 SOFTWARE ENGINEERING DESIGN I 3. Schemas and Theories The aim of this course is to learn how to write formal specifications of computer systems, using classical logic. The key descriptional technique
PROPER TECHNIQUE OF SOFTWARE INSPECTION USING GUARDED COMMAND LANGUAGE
 International Journal of Computer Science and Communication Vol. 2, No. 1, January-June 2011, pp. 153-157 PROPER TECHNIQUE OF SOFTWARE INSPECTION USING GUARDED COMMAND LANGUAGE Neeraj Kumar Singhania University,
International Journal of Computer Science and Communication Vol. 2, No. 1, January-June 2011, pp. 153-157 PROPER TECHNIQUE OF SOFTWARE INSPECTION USING GUARDED COMMAND LANGUAGE Neeraj Kumar Singhania University,
The University of Nottingham SCHOOL OF COMPUTER SCIENCE A LEVEL 4 MODULE, SPRING SEMESTER MATHEMATICAL FOUNDATIONS OF PROGRAMMING ANSWERS
 The University of Nottingham SCHOOL OF COMPUTER SCIENCE A LEVEL 4 MODULE, SPRING SEMESTER 2012 2013 MATHEMATICAL FOUNDATIONS OF PROGRAMMING ANSWERS Time allowed TWO hours Candidates may complete the front
The University of Nottingham SCHOOL OF COMPUTER SCIENCE A LEVEL 4 MODULE, SPRING SEMESTER 2012 2013 MATHEMATICAL FOUNDATIONS OF PROGRAMMING ANSWERS Time allowed TWO hours Candidates may complete the front
CS152: Programming Languages. Lecture 11 STLC Extensions and Related Topics. Dan Grossman Spring 2011
 CS152: Programming Languages Lecture 11 STLC Extensions and Related Topics Dan Grossman Spring 2011 Review e ::= λx. e x e e c v ::= λx. e c τ ::= int τ τ Γ ::= Γ, x : τ (λx. e) v e[v/x] e 1 e 1 e 1 e
CS152: Programming Languages Lecture 11 STLC Extensions and Related Topics Dan Grossman Spring 2011 Review e ::= λx. e x e e c v ::= λx. e c τ ::= int τ τ Γ ::= Γ, x : τ (λx. e) v e[v/x] e 1 e 1 e 1 e
(Refer Slide Time: 0:19)
 Theory of Computation. Professor somenath Biswas. Department of Computer Science & Engineering. Indian Institute of Technology, Kanpur. Lecture-15. Decision Problems for Regular Languages. (Refer Slide
Theory of Computation. Professor somenath Biswas. Department of Computer Science & Engineering. Indian Institute of Technology, Kanpur. Lecture-15. Decision Problems for Regular Languages. (Refer Slide
Overview. Probabilistic Programming. Dijkstra s guarded command language: Syntax. Elementary pgcl ingredients. Lecture #4: Probabilistic GCL
 Overview Lecture #4: Probabilistic GCL 1 Joost-Pieter Katoen 2 3 Recursion RWTH Lecture Series on 2018 Joost-Pieter Katoen 1/31 Joost-Pieter Katoen 2/31 Dijkstra s guarded command language: Syntax Elementary
Overview Lecture #4: Probabilistic GCL 1 Joost-Pieter Katoen 2 3 Recursion RWTH Lecture Series on 2018 Joost-Pieter Katoen 1/31 Joost-Pieter Katoen 2/31 Dijkstra s guarded command language: Syntax Elementary
(Refer Slide Time 6:48)
 Digital Circuits and Systems Prof. S. Srinivasan Department of Electrical Engineering Indian Institute of Technology Madras Lecture - 8 Karnaugh Map Minimization using Maxterms We have been taking about
Digital Circuits and Systems Prof. S. Srinivasan Department of Electrical Engineering Indian Institute of Technology Madras Lecture - 8 Karnaugh Map Minimization using Maxterms We have been taking about
A Partial Correctness Proof for Programs with Decided Specifications
 Applied Mathematics & Information Sciences 1(2)(2007), 195-202 An International Journal c 2007 Dixie W Publishing Corporation, U. S. A. A Partial Correctness Proof for Programs with Decided Specifications
Applied Mathematics & Information Sciences 1(2)(2007), 195-202 An International Journal c 2007 Dixie W Publishing Corporation, U. S. A. A Partial Correctness Proof for Programs with Decided Specifications
Lecture 5: The Halting Problem. Michael Beeson
 Lecture 5: The Halting Problem Michael Beeson Historical situation in 1930 The diagonal method appears to offer a way to extend just about any definition of computable. It appeared in the 1920s that it
Lecture 5: The Halting Problem Michael Beeson Historical situation in 1930 The diagonal method appears to offer a way to extend just about any definition of computable. It appeared in the 1920s that it
3.1 Constructions with sets
 3 Interlude on sets Sets and functions are ubiquitous in mathematics. You might have the impression that they are most strongly connected with the pure end of the subject, but this is an illusion: think
3 Interlude on sets Sets and functions are ubiquitous in mathematics. You might have the impression that they are most strongly connected with the pure end of the subject, but this is an illusion: think
Lecture Transcript While and Do While Statements in C++
 Lecture Transcript While and Do While Statements in C++ Hello and welcome back. In this lecture we are going to look at the while and do...while iteration statements in C++. Here is a quick recap of some
Lecture Transcript While and Do While Statements in C++ Hello and welcome back. In this lecture we are going to look at the while and do...while iteration statements in C++. Here is a quick recap of some
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2002 Vol. 1, No. 2, July-August 2002 The Theory of Classification Part 2: The Scratch-Built
JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2002 Vol. 1, No. 2, July-August 2002 The Theory of Classification Part 2: The Scratch-Built
(Refer Slide Time 3:31)
 Digital Circuits and Systems Prof. S. Srinivasan Department of Electrical Engineering Indian Institute of Technology Madras Lecture - 5 Logic Simplification In the last lecture we talked about logic functions
Digital Circuits and Systems Prof. S. Srinivasan Department of Electrical Engineering Indian Institute of Technology Madras Lecture - 5 Logic Simplification In the last lecture we talked about logic functions
Order from Chaos. University of Nebraska-Lincoln Discrete Mathematics Seminar
 Order from Chaos University of Nebraska-Lincoln Discrete Mathematics Seminar Austin Mohr Department of Mathematics Nebraska Wesleyan University February 8, 20 The (, )-Puzzle Start by drawing six dots
Order from Chaos University of Nebraska-Lincoln Discrete Mathematics Seminar Austin Mohr Department of Mathematics Nebraska Wesleyan University February 8, 20 The (, )-Puzzle Start by drawing six dots
INCREMENTAL SOFTWARE CONSTRUCTION WITH REFINEMENT DIAGRAMS
 INCREMENTAL SOFTWARE CONSTRUCTION WITH REFINEMENT DIAGRAMS Ralph-Johan Back Abo Akademi University July 6, 2006 Home page: www.abo.fi/~backrj Research / Current research / Incremental Software Construction
INCREMENTAL SOFTWARE CONSTRUCTION WITH REFINEMENT DIAGRAMS Ralph-Johan Back Abo Akademi University July 6, 2006 Home page: www.abo.fi/~backrj Research / Current research / Incremental Software Construction
Lambda Calculus. Type Systems, Lectures 3. Jevgeni Kabanov Tartu,
 Lambda Calculus Type Systems, Lectures 3 Jevgeni Kabanov Tartu, 13.02.2006 PREVIOUSLY ON TYPE SYSTEMS Arithmetical expressions and Booleans Evaluation semantics Normal forms & Values Getting stuck Safety
Lambda Calculus Type Systems, Lectures 3 Jevgeni Kabanov Tartu, 13.02.2006 PREVIOUSLY ON TYPE SYSTEMS Arithmetical expressions and Booleans Evaluation semantics Normal forms & Values Getting stuck Safety
AXIOMS OF AN IMPERATIVE LANGUAGE PARTIAL CORRECTNESS WEAK AND STRONG CONDITIONS. THE AXIOM FOR nop
 AXIOMS OF AN IMPERATIVE LANGUAGE We will use the same language, with the same abstract syntax that we used for operational semantics. However, we will only be concerned with the commands, since the language
AXIOMS OF AN IMPERATIVE LANGUAGE We will use the same language, with the same abstract syntax that we used for operational semantics. However, we will only be concerned with the commands, since the language
6.001 Notes: Section 15.1
 6.001 Notes: Section 15.1 Slide 15.1.1 Our goal over the next few lectures is to build an interpreter, which in a very basic sense is the ultimate in programming, since doing so will allow us to define
6.001 Notes: Section 15.1 Slide 15.1.1 Our goal over the next few lectures is to build an interpreter, which in a very basic sense is the ultimate in programming, since doing so will allow us to define
Hoare logic. WHILE p, a language with pointers. Introduction. Syntax of WHILE p. Lecture 5: Introduction to separation logic
 Introduction Hoare logic Lecture 5: Introduction to separation logic In the previous lectures, we have considered a language, WHILE, where mutability only concerned program variables. Jean Pichon-Pharabod
Introduction Hoare logic Lecture 5: Introduction to separation logic In the previous lectures, we have considered a language, WHILE, where mutability only concerned program variables. Jean Pichon-Pharabod
Order from Chaos. Nebraska Wesleyan University Mathematics Circle
 Order from Chaos Nebraska Wesleyan University Mathematics Circle Austin Mohr Department of Mathematics Nebraska Wesleyan University February 2, 20 The (, )-Puzzle Start by drawing six dots at the corners
Order from Chaos Nebraska Wesleyan University Mathematics Circle Austin Mohr Department of Mathematics Nebraska Wesleyan University February 2, 20 The (, )-Puzzle Start by drawing six dots at the corners
Lecture Notes on Binary Decision Diagrams
 Lecture Notes on Binary Decision Diagrams 15-122: Principles of Imperative Computation William Lovas Notes by Frank Pfenning Lecture 25 April 21, 2011 1 Introduction In this lecture we revisit the important
Lecture Notes on Binary Decision Diagrams 15-122: Principles of Imperative Computation William Lovas Notes by Frank Pfenning Lecture 25 April 21, 2011 1 Introduction In this lecture we revisit the important
Hardware versus software
 Logic 1 Hardware versus software 2 In hardware such as chip design or architecture, designs are usually proven to be correct using proof tools In software, a program is very rarely proved correct Why?
Logic 1 Hardware versus software 2 In hardware such as chip design or architecture, designs are usually proven to be correct using proof tools In software, a program is very rarely proved correct Why?
MA651 Topology. Lecture 4. Topological spaces 2
 MA651 Topology. Lecture 4. Topological spaces 2 This text is based on the following books: Linear Algebra and Analysis by Marc Zamansky Topology by James Dugundgji Fundamental concepts of topology by Peter
MA651 Topology. Lecture 4. Topological spaces 2 This text is based on the following books: Linear Algebra and Analysis by Marc Zamansky Topology by James Dugundgji Fundamental concepts of topology by Peter
This is already grossly inconvenient in present formalisms. Why do we want to make this convenient? GENERAL GOALS
 1 THE FORMALIZATION OF MATHEMATICS by Harvey M. Friedman Ohio State University Department of Mathematics friedman@math.ohio-state.edu www.math.ohio-state.edu/~friedman/ May 21, 1997 Can mathematics be
1 THE FORMALIZATION OF MATHEMATICS by Harvey M. Friedman Ohio State University Department of Mathematics friedman@math.ohio-state.edu www.math.ohio-state.edu/~friedman/ May 21, 1997 Can mathematics be
Recursively Enumerable Languages, Turing Machines, and Decidability
 Recursively Enumerable Languages, Turing Machines, and Decidability 1 Problem Reduction: Basic Concepts and Analogies The concept of problem reduction is simple at a high level. You simply take an algorithm
Recursively Enumerable Languages, Turing Machines, and Decidability 1 Problem Reduction: Basic Concepts and Analogies The concept of problem reduction is simple at a high level. You simply take an algorithm
Lecture 1 Contracts : Principles of Imperative Computation (Fall 2018) Frank Pfenning
 Lecture 1 Contracts 15-122: Principles of Imperative Computation (Fall 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Lecture 1 Contracts 15-122: Principles of Imperative Computation (Fall 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
UNIVERSITY OF EDINBURGH COLLEGE OF SCIENCE AND ENGINEERING SCHOOL OF INFORMATICS INFR08008 INFORMATICS 2A: PROCESSING FORMAL AND NATURAL LANGUAGES
 UNIVERSITY OF EDINBURGH COLLEGE OF SCIENCE AND ENGINEERING SCHOOL OF INFORMATICS INFR08008 INFORMATICS 2A: PROCESSING FORMAL AND NATURAL LANGUAGES Saturday 10 th December 2016 09:30 to 11:30 INSTRUCTIONS
UNIVERSITY OF EDINBURGH COLLEGE OF SCIENCE AND ENGINEERING SCHOOL OF INFORMATICS INFR08008 INFORMATICS 2A: PROCESSING FORMAL AND NATURAL LANGUAGES Saturday 10 th December 2016 09:30 to 11:30 INSTRUCTIONS
Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122
 Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122 I. Logic 101 In logic, a statement or proposition is a sentence that can either be true or false. A predicate is a sentence in
Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122 I. Logic 101 In logic, a statement or proposition is a sentence that can either be true or false. A predicate is a sentence in
Verification of Selection and Heap Sort Using Locales
 Verification of Selection and Heap Sort Using Locales Danijela Petrović September 19, 2015 Abstract Stepwise program refinement techniques can be used to simplify program verification. Programs are better
Verification of Selection and Heap Sort Using Locales Danijela Petrović September 19, 2015 Abstract Stepwise program refinement techniques can be used to simplify program verification. Programs are better
Polymorphic lambda calculus Princ. of Progr. Languages (and Extended ) The University of Birmingham. c Uday Reddy
 06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 6: Polymorphic Type Systems 1. Polymorphic
06-02552 Princ. of Progr. Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 6: Polymorphic Type Systems 1. Polymorphic
Hoare logic. Lecture 5: Introduction to separation logic. Jean Pichon-Pharabod University of Cambridge. CST Part II 2017/18
 Hoare logic Lecture 5: Introduction to separation logic Jean Pichon-Pharabod University of Cambridge CST Part II 2017/18 Introduction In the previous lectures, we have considered a language, WHILE, where
Hoare logic Lecture 5: Introduction to separation logic Jean Pichon-Pharabod University of Cambridge CST Part II 2017/18 Introduction In the previous lectures, we have considered a language, WHILE, where
Distributed Systems Programming (F21DS1) Formal Verification
 Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
Distributed Systems Programming (F21DS1) Formal Verification Andrew Ireland Department of Computer Science School of Mathematical and Computer Sciences Heriot-Watt University Edinburgh Overview Focus on
Virtual World Development
 ALGEBRAIC SPECIFICATION LANGUAGE The algebraic specification language (ASL) is intended to provide the formal structure needed for modular programming and the flexibility needed for unencumbered design.
ALGEBRAIC SPECIFICATION LANGUAGE The algebraic specification language (ASL) is intended to provide the formal structure needed for modular programming and the flexibility needed for unencumbered design.
Checks and Balances - Constraint Solving without Surprises in Object-Constraint Programming Languages: Full Formal Development
 Checks and Balances - Constraint Solving without Surprises in Object-Constraint Programming Languages: Full Formal Development Tim Felgentreff, Todd Millstein, Alan Borning and Robert Hirschfeld Viewpoints
Checks and Balances - Constraint Solving without Surprises in Object-Constraint Programming Languages: Full Formal Development Tim Felgentreff, Todd Millstein, Alan Borning and Robert Hirschfeld Viewpoints
Sets. Sets. Subset, universe. Specifying sets, membership. Examples: Specifying a set using a predicate. Examples
 Sets 2/36 We will not give a precise definition of what is a set, but we will say precisely what you can do with it. Sets Lectures 7 and 8 (hapter 16) (Think of a set as a collection of things of which
Sets 2/36 We will not give a precise definition of what is a set, but we will say precisely what you can do with it. Sets Lectures 7 and 8 (hapter 16) (Think of a set as a collection of things of which
Programming Languages and Compilers Qualifying Examination. Answer 4 of 6 questions.
 Programming Languages and Compilers Qualifying Examination Fall 2017 Answer 4 of 6 questions. GENERAL INSTRUCTIONS 1. Answer each question in a separate book. 2. Indicate on the cover of each book the
Programming Languages and Compilers Qualifying Examination Fall 2017 Answer 4 of 6 questions. GENERAL INSTRUCTIONS 1. Answer each question in a separate book. 2. Indicate on the cover of each book the
Lecture Notes on Data Representation
 Lecture Notes on Data Representation 15-814: Types and Programming Languages Frank Pfenning Lecture 9 Tuesday, October 2, 2018 1 Introduction In this lecture we ll see our type system in action. In particular
Lecture Notes on Data Representation 15-814: Types and Programming Languages Frank Pfenning Lecture 9 Tuesday, October 2, 2018 1 Introduction In this lecture we ll see our type system in action. In particular
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute. Week 02 Module 06 Lecture - 14 Merge Sort: Analysis
 Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Week 02 Module 06 Lecture - 14 Merge Sort: Analysis So, we have seen how to use a divide and conquer strategy, we
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Week 02 Module 06 Lecture - 14 Merge Sort: Analysis So, we have seen how to use a divide and conquer strategy, we
Introduction to Denotational Semantics. Class Likes/Dislikes Survey. Dueling Semantics. Denotational Semantics Learning Goals. You re On Jeopardy!
 Introduction to Denotational Semantics Class Likes/Dislikes Survey would change [the bijection question] to be one that still tested students' recollection of set theory but that didn't take as much time
Introduction to Denotational Semantics Class Likes/Dislikes Survey would change [the bijection question] to be one that still tested students' recollection of set theory but that didn't take as much time
Lecture Notes on Arrays
 Lecture Notes on Arrays 15-122: Principles of Imperative Computation July 2, 2013 1 Introduction So far we have seen how to process primitive data like integers in imperative programs. That is useful,
Lecture Notes on Arrays 15-122: Principles of Imperative Computation July 2, 2013 1 Introduction So far we have seen how to process primitive data like integers in imperative programs. That is useful,
Relational Database: The Relational Data Model; Operations on Database Relations
 Relational Database: The Relational Data Model; Operations on Database Relations Greg Plaxton Theory in Programming Practice, Spring 2005 Department of Computer Science University of Texas at Austin Overview
Relational Database: The Relational Data Model; Operations on Database Relations Greg Plaxton Theory in Programming Practice, Spring 2005 Department of Computer Science University of Texas at Austin Overview
1. true / false By a compiler we mean a program that translates to code that will run natively on some machine.
 1. true / false By a compiler we mean a program that translates to code that will run natively on some machine. 2. true / false ML can be compiled. 3. true / false FORTRAN can reasonably be considered
1. true / false By a compiler we mean a program that translates to code that will run natively on some machine. 2. true / false ML can be compiled. 3. true / false FORTRAN can reasonably be considered
Handout 10: Imperative programs and the Lambda Calculus
 06-02552 Princ of Progr Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 10: Imperative programs and the Lambda Calculus
06-02552 Princ of Progr Languages (and Extended ) The University of Birmingham Spring Semester 2016-17 School of Computer Science c Uday Reddy2016-17 Handout 10: Imperative programs and the Lambda Calculus
P Is Not Equal to NP. ScholarlyCommons. University of Pennsylvania. Jon Freeman University of Pennsylvania. October 1989
 University of Pennsylvania ScholarlyCommons Technical Reports (CIS) Department of Computer & Information Science October 1989 P Is Not Equal to NP Jon Freeman University of Pennsylvania Follow this and
University of Pennsylvania ScholarlyCommons Technical Reports (CIS) Department of Computer & Information Science October 1989 P Is Not Equal to NP Jon Freeman University of Pennsylvania Follow this and
How invariants help writing loops Author: Sander Kooijmans Document version: 1.0
 How invariants help writing loops Author: Sander Kooijmans Document version: 1.0 Why this document? Did you ever feel frustrated because of a nasty bug in your code? Did you spend hours looking at the
How invariants help writing loops Author: Sander Kooijmans Document version: 1.0 Why this document? Did you ever feel frustrated because of a nasty bug in your code? Did you spend hours looking at the
Introduction to Denotational Semantics. Brutus Is An Honorable Man. Class Likes/Dislikes Survey. Dueling Semantics
 Brutus Is An Honorable Man HW2 will not be due today. Homework X+1 will never be due until after I have returned Homework X to you. Normally this is never an issue, but I was sick yesterday and was hosting
Brutus Is An Honorable Man HW2 will not be due today. Homework X+1 will never be due until after I have returned Homework X to you. Normally this is never an issue, but I was sick yesterday and was hosting
FreePascal changes: user documentation
 FreePascal changes: user documentation Table of Contents Jochem Berndsen February 2007 1Introduction...1 2Accepted syntax...2 Declarations...2 Statements...3 Class invariants...3 3Semantics...3 Definitions,
FreePascal changes: user documentation Table of Contents Jochem Berndsen February 2007 1Introduction...1 2Accepted syntax...2 Declarations...2 Statements...3 Class invariants...3 3Semantics...3 Definitions,
Distributed minimum spanning tree problem
 Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
Distributed minimum spanning tree problem Juho-Kustaa Kangas 24th November 2012 Abstract Given a connected weighted undirected graph, the minimum spanning tree problem asks for a spanning subtree with
CS2 Algorithms and Data Structures Note 10. Depth-First Search and Topological Sorting
 CS2 Algorithms and Data Structures Note 10 Depth-First Search and Topological Sorting In this lecture, we will analyse the running time of DFS and discuss a few applications. 10.1 A recursive implementation
CS2 Algorithms and Data Structures Note 10 Depth-First Search and Topological Sorting In this lecture, we will analyse the running time of DFS and discuss a few applications. 10.1 A recursive implementation
Algebra of Sets. Aditya Ghosh. April 6, 2018 It is recommended that while reading it, sit with a pen and a paper.
 Algebra of Sets Aditya Ghosh April 6, 2018 It is recommended that while reading it, sit with a pen and a paper. 1 The Basics This article is only about the algebra of sets, and does not deal with the foundations
Algebra of Sets Aditya Ghosh April 6, 2018 It is recommended that while reading it, sit with a pen and a paper. 1 The Basics This article is only about the algebra of sets, and does not deal with the foundations
Computer Science Technical Report
 Computer Science Technical Report Feasibility of Stepwise Addition of Multitolerance to High Atomicity Programs Ali Ebnenasir and Sandeep S. Kulkarni Michigan Technological University Computer Science
Computer Science Technical Report Feasibility of Stepwise Addition of Multitolerance to High Atomicity Programs Ali Ebnenasir and Sandeep S. Kulkarni Michigan Technological University Computer Science
Consider a description of arithmetic. It includes two equations that define the structural types of digit and operator:
 Syntax A programming language consists of syntax, semantics, and pragmatics. We formalize syntax first, because only syntactically correct programs have semantics. A syntax definition of a language lists
Syntax A programming language consists of syntax, semantics, and pragmatics. We formalize syntax first, because only syntactically correct programs have semantics. A syntax definition of a language lists
CITS5501 Software Testing and Quality Assurance Formal methods
 CITS5501 Software Testing and Quality Assurance Formal methods Unit coordinator: Arran Stewart May 1, 2018 1 / 49 Sources Pressman, R., Software Engineering: A Practitioner s Approach, McGraw-Hill, 2005
CITS5501 Software Testing and Quality Assurance Formal methods Unit coordinator: Arran Stewart May 1, 2018 1 / 49 Sources Pressman, R., Software Engineering: A Practitioner s Approach, McGraw-Hill, 2005
Operational Semantics
 15-819K: Logic Programming Lecture 4 Operational Semantics Frank Pfenning September 7, 2006 In this lecture we begin in the quest to formally capture the operational semantics in order to prove properties
15-819K: Logic Programming Lecture 4 Operational Semantics Frank Pfenning September 7, 2006 In this lecture we begin in the quest to formally capture the operational semantics in order to prove properties
Implementing Continuations
 Implementing Continuations sk and dbtucker 2002-10-18 1 Changing Representations Now that we ve seen how continuations work, let s study how to implement them in an interpreter. For this lecture onward,
Implementing Continuations sk and dbtucker 2002-10-18 1 Changing Representations Now that we ve seen how continuations work, let s study how to implement them in an interpreter. For this lecture onward,
