The HOL-SPARK Program Verification Environment. Stefan Berghofer secunet Security Networks AG
|
|
|
- Jemimah Nicholson
- 5 years ago
- Views:
Transcription
1 The HOL-SPARK Program Verification Environment Stefan Berghofer secunet Security Networks AG August 15, 2018
2 Contents 1 Introduction SPARK HOL-SPARK Verifying an Example Program Importing SPARK VCs into Isabelle Proving the VCs Optimizing the proof Principles of VC generation 13 4 HOL-SPARK Reference Commands Types Integers Enumeration types Records Arrays User-defined proof functions and types
3 Chapter 1 Introduction This document describes a link between Isabelle/HOL and the SPARK/Ada tool suite for the verification of high-integrity software. Using this link, verification problems can be tackled that are beyond reach of the proof tools currently available for SPARK. A number of examples can be found in the directory HOL/SPARK/Examples in the Isabelle distribution. An opensource version of the SPARK tool suite is available free of charge from libre.adacore.com. In the remainder of 1, we give an introduction to SPARK and the HOL- SPARK link. The verification of an example program is described in 2. In 3, we explain the principles underlying the generation of verification conditions for SPARK programs. Finally, 4 describes the commands provided by the HOL-SPARK link, as well as the encoding of SPARK types in HOL. 1.1 SPARK SPARK [1] is a subset of the Ada language that has been designed to allow verification of high-integrity software. It is missing certain features of Ada that can make programs difficult to verify, such as access types, dynamic data structures, and recursion. SPARK allows to prove absence of runtime exceptions, as well as partial correctness using pre- and postconditions. Loops can be annotated with invariants, and each procedure must have a dataflow annotation, specifying the dependencies of the output parameters on the input parameters of the procedure. Since SPARK annotations are just written as comments, SPARK programs can be compiled by an ordinary Ada compiler such as GNAT. SPARK comes with a number of tools, notably the Examiner that, given a SPARK program as an input, performs a dataflow 2
4 analysis and generates verification conditions (VCs) that must be proved in order for the program to be exception-free and partially correct. The VCs generated by the Examiner are formulae expressed in a language called FDL, which is first-order logic extended with arithmetic operators, arrays, records, and enumeration types. For example, the FDL expression for_all(i: integer, ((i >= min) and (i <= max)) -> (element(a, [i]) = 0)) states that all elements of the array a with indices greater or equal to min and smaller or equal to max are 0. VCs are processed by another SPARK tool called the Simplifier that either completely solves VCs or transforms them into simpler, equivalent conditions. The latter VCs can then be processed using another tool called the Proof Checker. While the Simplifier tries to prove VCs in a completely automatic way, the Proof Checker requires user interaction, which enables it to prove formulae that are beyond the scope of the Simplifier. The steps that are required to manually prove a VC are recorded in a log file by the Proof Checker. Finally, this log file, together with the output of the other SPARK tools mentioned above, is read by a tool called POGS (Proof ObliGation Summariser) that produces a table mentioning for each VC the method by which it has been proved. In order to overcome the limitations of FDL and to express complex specifications, SPARK allows the user to declare so-called proof functions. The desired properties of such functions are described by postulating a set of rules that can be used by the Simplifier and Proof Checker [1, 11.7]. An obvious drawback of this approach is that incorrect rules can easily introduce inconsistencies. 1.2 HOL-SPARK The HOL-SPARK verification environment, which is built on top of Isabelle s object logic HOL, is intended as an alternative to the SPARK Proof Checker, and improves on it in a number of ways. HOL-SPARK allows Isabelle to directly parse files generated by the Examiner and Simplifier, and provides a special proof command to conduct proofs of VCs, which can make use of the full power of Isabelle s rich collection of proof methods. Proofs can be conducted using Isabelle s graphical user interface, which makes it easy to navigate through larger proof scripts. Moreover, proof functions can be introduced in a definitional way, for example by using Isabelle s package for recursive functions, rather than by just stating their properties as axioms, which avoids introducing inconsistencies. 3
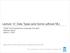
5 Source files (*.ads, *.adb) Examiner FDL declarations (*.fdl) VCs (*.vcg) Rules (*.rls) Simplifier Simplified VCs (*.siv) HOL-SPARK Theory files (*.thy) Proof review files (*.prv) POGS Summary file (*.sum) Figure 1.1: SPARK program verification tool chain 4
6 Figure 1.1 shows the integration of HOL-SPARK into the tool chain for the verification of SPARK programs. HOL-SPARK processes declarations (*.fdl) and rules (*.rls) produced by the Examiner, as well as simplified VCs (*.siv) produced by the SPARK Simplifier. Alternatively, the original unsimplified VCs (*.vcg) produced by the Examiner can be used as well. Processing of the SPARK files is triggered by an Isabelle theory file (*.thy), which also contains the proofs for the VCs contained in the *.siv or *.vcg files. Once that all verification conditions have been successfully proved, Isabelle generates a proof review file (*.prv) notifying the POGS tool of the VCs that have been discharged. 5
7 Chapter 2 Verifying an Example Program We will now explain the usage of the SPARK verification environment by proving the correctness of an example program. As an example, we use a program for computing the greatest common divisor of two natural numbers shown in Fig. 2.1, which has been taken from the book about SPARK by Barnes [1, 11.6]. 2.1 Importing SPARK VCs into Isabelle In order to specify that the SPARK procedure G C D behaves like its mathematical counterpart, Barnes introduces a proof function Gcd in the package specification. Invoking the SPARK Examiner and Simplifier on this program yields a file g c d.siv containing the simplified VCs, as well as files g c d.fdl and g c d.rls, containing FDL declarations and rules, respectively. The files generated by SPARK are assumed to reside in the subdirectory greatest common divisor. For G C D the Examiner generates ten VCs, eight of which are proved automatically by the Simplifier. We now show how to prove the remaining two VCs interactively using HOL-SPARK. For this purpose, we create a theory Greatest Common Divisor, which is shown in Fig A theory file always starts with the keyword theory followed by the name of the theory, which must be the same as the file name. The theory name is followed by the keyword imports and a list of theories imported by the current theory. All theories using the HOL-SPARK verification environment must import the theory SPARK. In addition, we also include the GCD theory. The list of imported theories is followed by the begin keyword. In order to interactively process the theory shown in Fig. 2.2, we start Isabelle with the command isabelle jedit -l HOL-SPARK Greatest_Common_Divisor.thy 6
8 package Greatest_Common_Divisor is --# function Gcd(A, B: Natural) return Natural; procedure G_C_D(M, N: in Natural; G: out Natural); --# derives G from M, N; --# pre M >= 0 and N > 0; --# post G = Gcd(M,N); end Greatest_Common_Divisor; package body Greatest_Common_Divisor is procedure G_C_D(M, N: in Natural; G: out Natural) is C, D, R: Integer; begin C := M; D := N; while D /= 0 loop --# assert C >= 0 and D > 0 and Gcd(C, D) = Gcd(M, N); R := C rem D; C := D; D := R; end loop; G := C; end G_C_D; end Greatest_Common_Divisor; Figure 2.1: SPARK program for computing the greatest common divisor Figure 2.2: Correctness proof for the greatest common divisor program 7
9 The option -l HOL-SPARK instructs Isabelle to load the right object logic image containing the verification environment. Each proof function occurring in the specification of a SPARK program must be linked with a corresponding Isabelle function. This is accomplished by the command spark proof functions, which expects a list of equations of the form name = term, where name is the name of the proof function and term is the corresponding Isabelle term. In the case of gcd, both the SPARK proof function and its Isabelle counterpart happen to have the same name. Isabelle checks that the type of the term linked with a proof function agrees with the type of the function declared in the *.fdl file. It is worth noting that the spark proof functions command can be invoked both outside, i.e. before spark open, and inside the environment, i.e. after spark open, but before any spark vc command. The former variant is useful when having to declare proof functions that are shared by several procedures, whereas the latter has the advantage that the type of the proof function can be checked immediately, since the VCs, and hence also the declarations of proof functions in the *.fdl file have already been loaded. We now instruct Isabelle to open a new verification environment and load a set of VCs. This is done using the command spark open, which must be given the name of a *.siv file as an argument. Behind the scenes, Isabelle parses this file and the corresponding *.fdl and *.rls files, and converts the VCs to Isabelle terms. Using the command spark status, the user can display the current VCs together with their status (proved, unproved). The variants spark status (proved) and spark status (unproved) show only proved and unproved VCs, respectively. For g c d.siv, the output of spark status is shown in Fig To minimize the number of assumptions, and hence the size of the VCs, FDL rules of the form... may be replaced by... are turned into native Isabelle definitions, whereas other rules are modelled as assumptions. 2.2 Proving the VCs The two open VCs are procedure_g_c_d_4 and procedure_g_c_d_11, both of which contain the gcd proof function that the SPARK Simplifier does not know anything about. The proof of a particular VC can be started with the spark vc command, which is similar to the standard lemma and theorem commands, with the difference that it only takes a name of a VC but no formula as an argument. A VC can have several conclusions that can be referenced by the identifiers?c1,?c2, etc. If there is just one conclusion, it can also be referenced by?thesis. It is important to note 8
10 Context: fixes m :: "int" and n :: "int" and c :: "int" and d :: "int" assumes g_c_d_rules1: "0 integer size" and g_c_d_rules6: "0 natural size" notes definition defns = integer first = integer last = Definitions: g_c_d_rules2: integer first = g_c_d_rules3: integer last = Verification conditions: path(s) from assertion of line 10 to assertion of line 10 procedure_g_c_d_4 (unproved) assumes H1: "0 c" and H2: "0 < d" and H3: "gcd c d = gcd m n"... shows "0 < c - c sdiv d * d" and "gcd d (c - c sdiv d * d) = gcd m n path(s) from assertion of line 10 to finish procedure_g_c_d_11 (unproved) assumes H1: "0 c" and H2: "0 < d" and H3: "gcd c d = gcd m n"... shows "d = gcd m n" Figure 2.3: Output of spark status for g c d.siv 9
11 that the div operator of FDL behaves differently from the div operator of Isabelle/HOL on negative numbers. The former always truncates towards zero, whereas the latter truncates towards minus infinity. This is why the FDL div operator is mapped to the sdiv operator in Isabelle/HOL, which is defined as a sdiv b = sgn a * sgn b * ( a div b ) For example, we have that - 5 sdiv 4 = - 1, but - 5 div 4 = - 2. For non-negative dividend and divisor, sdiv is equivalent to div, as witnessed by theorem sdiv_pos_pos: 0 a = 0 b = a sdiv b = a div b In contrast, the behaviour of the FDL mod operator is equivalent to the one of Isabelle/HOL. Moreover, since FDL has no counterpart of the SPARK operator rem, the SPARK expression c rem d just becomes c - c sdiv d * d in Isabelle. The first conclusion of procedure_g_c_d_4 requires us to prove that the remainder of c and d is greater than 0. To do this, we use the theorem minus_div_mult_eq_mod [symmetric] describing the correspondence between div and mod a mod b = a - a div b * b together with the theorem pos_mod_sign saying that the result of the mod operator is non-negative when applied to a non-negative divisor: (0:: a) < b = (0:: a) a mod b We will also need the aforementioned theorem sdiv_pos_pos in order for the standard Isabelle/HOL theorems about div to be applicable to the VC, which is formulated using sdiv rather that div. Note that the proof uses 0 c and 0 < d rather than H1 and H2 to refer to the hypotheses of the current VC. While the latter variant seems more compact, it is not particularly robust, since the numbering of hypotheses can easily change if the corresponding program is modified, making the proof script hard to adjust when there are many hypotheses. Moreover, proof scripts using abbreviations like H1 and H2 are hard to read without assistance from Isabelle. The second conclusion of procedure_g_c_d_4 requires us to prove that the gcd of d and the remainder of c and d is equal to the gcd of the original input values m and n, which is the actual invariant of the procedure. This is a consequence of theorem gcd_non_0_int 0 < y = gcd x y = gcd y (x mod y) 10
12 Again, we also need theorems minus_div_mult_eq_mod [symmetric] and sdiv_pos_pos to justify that SPARK s rem operator is equivalent to Isabelle s mod operator for non-negative operands. The VC procedure_g_c_d_11 says that if the loop invariant holds before the last iteration of the loop, the postcondition of the procedure will hold after execution of the loop body. To prove this, we observe that the remainder of c and d, and hence c mod d is 0 when exiting the loop. This implies that gcd c d = d, since c is divisible by d, so the conclusion follows using the assumption gcd c d = gcd m n. This concludes the proofs of the open VCs, and hence the SPARK verification environment can be closed using the command spark end. This command checks that all VCs have been proved and issues an error message if there are remaining unproved VCs. Moreover, Isabelle checks that there is no open SPARK verification environment when the final end command of a theory is encountered. 2.3 Optimizing the proof When looking at the program from Fig. 2.1 once again, several optimizations come to mind. First of all, like the input parameters of the procedure, the local variables C, D, and R can be declared as Natural rather than Integer. Since natural numbers are non-negative by construction, the values computed by the algorithm are trivially proved to be non-negative. Since we are working with non-negative numbers, we can also just use SPARK s mod operator instead of rem, which spares us an application of theorems minus_div_mult_eq_mod [symmetric] and sdiv_pos_pos. Finally, as noted by Barnes [1, 11.5], we can simplify matters by placing the assert statement between while and loop rather than directly after the loop. In the former case, the loop invariant has to be proved only once, whereas in the latter case, it has to be proved twice: since the assert occurs after the check of the exit condition, the invariant has to be proved for the path from the assert statement to the assert statement, and for the path from the assert statement to the postcondition. In the case of the G C D procedure, this might not seem particularly problematic, since the proof of the invariant is very simple, but it can unnecessarily complicate matters if the proof of the invariant is non-trivial. The simplified program for computing the greatest common divisor, together with its correctness proof, is shown in Fig Since the package specification has not changed, we only show the body of the packages. The two VCs can now be proved by a single application of Isabelle s proof method simp. 11
13 package body Simple_Greatest_Common_Divisor is procedure G_C_D (M, N : in Natural; G : out Natural) is C, D, R : Natural; begin C := M; D := N; while D /= 0 --# assert Gcd (C, D) = Gcd (M, N); loop R := C mod D; C := D; D := R; end loop; G := C; end G_C_D; end Simple_Greatest_Common_Divisor; theory Simple_Greatest_Common_Divisor imports "HOL-SPARK.SPARK" begin spark proof functions gcd = "gcd :: int int int" spark open "simple_greatest_common_divisor/g_c_d" spark vc procedure_g_c_d_4 using 0 < d gcd c d = gcd m n by (simp add: gcd_non_0_int) spark vc procedure_g_c_d_9 using 0 c gcd c 0 = gcd m n by simp spark end end Figure 2.4: Simplified greatest common divisor program and proof 12
14 Chapter 3 Principles of VC generation In this section, we will discuss some aspects of VC generation that are useful for understanding and optimizing the VCs produced by the SPARK Examiner. As explained by Barnes [1, 11.5], the SPARK Examiner unfolds the loop for I in T range L.. U loop --# assert P (I); S; end loop; to if L <= U then I := L; loop --# assert P (I); S; exit when I = U; I := I + 1; end loop; end if; Due to this treatment of for-loops, the user essentially has to prove twice that S preserves the invariant P, namely for the path from the assertion to the assertion and from the assertion to the next cut point following the loop. The preservation of the invariant has to be proved even more often when the loop is followed by an if-statement. For trivial invariants, this might not seem like a big problem, but in realistic applications, where invariants are complex, this can be a major inconvenience. Often, the proofs of the invariant differ only in a few variables, so it is tempting to just copy and modify existing proof scripts, but this leads to proofs that are hard to 13
15 package Loop_Invariant is type Word32 is mod 2 ** 32; procedure Proc1 (A : in Natural; B : in Word32; C : out Word32); --# derives C from A, B; --# post Word32 (A) * B = C; procedure Proc2 (A : in Natural; B : in Word32; C : out Word32); --# derives C from A, B; --# post Word32 (A) * B = C; end Loop_Invariant; package body Loop_Invariant is procedure Proc1 (A : in Natural; B : in Word32; C : out Word32) is begin C := 0; for I in Natural range 1.. A --# assert Word32 (I - 1) * B = C; loop C := C + B; end loop; end Proc1; procedure Proc2 (A : in Natural; B : in Word32; C : out Word32) is begin C := 0; for I in Natural range 1.. A --# assert Word32 (I - 1) * B = C; loop C := C + B; --# assert Word32 (I) * B = C; end loop; end Proc2; end Loop_Invariant; Figure 3.1: Assertions in for-loops 14
16 precondition (1 1) b mod 2 32 = 0 1 a a b mod 2 32 = 0 assertion (i 1) b mod 2 32 = c (i + 1 1) b mod 2 32 = (c + b) mod 2 32 (a 1) b mod 2 32 = c a b mod 2 32 = (c + b) mod 2 32 postcondition Figure 3.2: Control flow graph for procedure Proc1 precondition 1 a a b mod 2 32 = 0 (1 1) b mod 2 32 = 0 assertion 1 (i 1) b mod 2 32 = c i b mod 2 32 = (c + b) mod 2 32 i b mod 2 32 = c (i + 1 1) b mod 2 32 = c assertion 2 a b mod 2 32 = c a b mod 2 32 = c postcondition Figure 3.3: Control flow graph for procedure Proc2 15
17 maintain. The problem of having to prove the invariant several times can be avoided by rephrasing the above for-loop to for I in T range L.. U loop --# assert P (I); S; --# assert P (I + 1) end loop; The VC for the path from the second assertion to the first assertion is trivial and can usually be proved automatically by the SPARK Simplifier, whereas the VC for the path from the first assertion to the second assertion actually expresses the fact that S preserves the invariant. We illustrate this technique using the example package shown in Fig It contains two procedures Proc1 and Proc2, both of which implement multiplication via addition. The procedures have the same specification, but in Proc1, only one assert statement is placed at the beginning of the loop, whereas Proc2 employs the trick explained above. After applying the SPARK Simplifier to the VCs generated for Proc1, two very similar VCs loop 1 i * b mod 2 32 = ((loop 1 i - 1) * b mod b) mod 2 32 and a * b mod 2 32 = ((a - 1) * b mod b) mod 2 32 remain, whereas for Proc2, only the first of the above VCs remains. Why placing assert statements both at the beginning and at the end of the loop body simplifies the proof of the invariant should become obvious when looking at Fig. 3.2 and Fig. 3.3 showing the control flow graphs for Proc1 and Proc2, respectively. The nodes in the graph correspond to cut points in the program, and the paths between the cut points are annotated with the corresponding VCs. To reduce the size of the graphs, we do not show nodes and edges corresponding to runtime checks. The VCs for the path bypassing the loop and for the path from the precondition to the (first) assertion are the same for both procedures. The graph for Proc1 contains two VCs expressing that the invariant is preserved by the execution of the loop body: one for the path from the assertion to the assertion, and another one for the path from the assertion to the conclusion, which corresponds to the last iteration of the loop. The latter VC can be obtained from the former by simply replacing i by a. In contrast, the graph for Proc2 contains only one such VC for the path from assertion 1 to assertion 2. The VC for the path from assertion 2 to assertion 1 is trivial, and so is the VC for the path 16
18 from assertion 2 to the postcondition, expressing that the loop invariant implies the postcondition when the loop has terminated. 17
19 Chapter 4 HOL-SPARK Reference This section is intended as a quick reference for the HOL-SPARK verification environment. In 4.1, we give a summary of the commands provided by the HOL-SPARK, while 4.2 contains a description of how particular types of SPARK and FDL are modelled in Isabelle. 4.1 Commands This section describes the syntax and effect of each of the commands provided by HOL-SPARK. spark open name ( name ) Opens a new SPARK verification environment and loads a *.siv file with VCs. Alternatively, *.vcg files can be loaded using spark open vcg. The corresponding *.fdl and *.rls files must reside in the same directory as the file given as an argument to the command. This command also generates records and datatypes for the types specified in the *.fdl file, unless they have already been associated with user-defined Isabelle types (see below). Since the full package name currently cannot be determined from the files generated by the SPARK Examiner, the command also allows to specify an optional package prefix in the format p 1... p n. When working with projects consisting of several packages, this is necessary in order for the verification environment to be able to map proof functions and types defined in Isabelle to their SPARK counterparts. 18
20 spark proof functions name = term Associates a proof function with the given name to a term. The name should be the full name of the proof function as it appears in the *.fdl file, including the package prefix. This command can be used both inside and outside a verification environment. The latter variant is useful for introducing proof functions that are shared by several procedures or packages, whereas the former allows the given term to refer to the types generated by spark open for record or enumeration types specified in the *.fdl file. spark types name = type mapping mapping ( name = name, ) Associates a SPARK type with the given name with an Isabelle type. This command can only be used outside a verification environment. The given type must be either a record or a datatype, where the names of fields or constructors must either match those of the corresponding SPARK types (modulo casing), or a mapping from SPARK to Isabelle names has to be provided. This command is useful when having to define proof functions referring to record or enumeration types that are shared by several procedures or packages. First, the types required by the proof functions can be introduced using Isabelle s commands for defining records or datatypes. Having introduced the types, the proof functions can be defined in Isabelle. Finally, both the proof functions and the types can be associated with their SPARK counterparts. 19
21 spark status (proved) (unproved) Outputs the variables declared in the *.fdl file, the rules declared in the *.rls file, and all VCs, together with their status (proved, unproved). The output can be restricted to the proved or unproved VCs by giving the corresponding option to the command. spark vc name Initiates the proof of the VC with the given name. Similar to the standard lemma or theorem commands, this command must be followed by a sequence of proof commands. The command introduces the hypotheses H1... Hn, as well as the identifiers?c1...?cm corresponding to the conclusions of the VC. spark end (incomplete) Closes the current verification environment. Unless the incomplete option is given, all VCs must have been proved, otherwise the command issues an error message. As a side effect, the command generates a proof review (*.prv) file to inform POGS of the proved VCs. 4.2 Types The main types of FDL are integers, enumeration types, records, and arrays. In the following sections, we describe how these types are modelled in Isabelle Integers The FDL type integer is modelled by the Isabelle type int. While the FDL mod operator behaves in the same way as its Isabelle counterpart, this is 20
22 sdiv_def: a sdiv b = sgn a * sgn b * ( a div b ) sdiv_minus_dividend: - a sdiv b = - (a sdiv b) sdiv_minus_divisor: a sdiv - b = - (a sdiv b) sdiv_pos_pos: 0 a = 0 b = a sdiv b = a div b sdiv_pos_neg: 0 a = b < 0 = a sdiv b = - (a div - b) sdiv_neg_pos: a < 0 = 0 b = a sdiv b = - (- a div b) sdiv_neg_neg: a < 0 = b < 0 = a sdiv b = - a div - b Figure 4.1: Characteristic properties of sdiv AND_lower: OR_lower: XOR_lower: AND_upper1: AND_upper2: OR_upper: XOR_upper: AND_mod: 0 x = 0 x AND y 0 x = 0 y = 0 x OR y 0 x = 0 y = 0 x XOR y 0 x = x AND y x 0 y = x AND y y 0 x = x < 2 n = y < 2 n = x OR y < 2 n 0 x = x < 2 n = y < 2 n = x XOR y < 2 n x AND 2 n - 1 = x mod 2 n Figure 4.2: Characteristic properties of bitwise operators not the case for the div operator. As has already been mentioned in 2.2, the div operator of SPARK always truncates towards zero, whereas the div operator of Isabelle truncates towards minus infinity. Therefore, the FDL div operator is mapped to the sdiv operator in Isabelle. The characteristic theorems of sdiv, in particular those describing the relationship with the standard div operator, are shown in Fig. 4.1 The bitwise logical operators of SPARK and FDL are modelled by the operators AND, OR and XOR from Isabelle s Word library, all of which have type int int int. A list of properties of these operators that are useful in proofs about SPARK programs are shown in Fig Enumeration types The FDL enumeration type type t = (e 1, e 2,..., e n ); is modelled by the Isabelle datatype datatype t = e 1 e 2... e n 21
23 range_pos: range pos = {0..<int CARD( a)} less_pos: (x < y) = (pos x < pos y) less_eq_pos: (x y) = (pos x pos y) val_def: val = inv pos succ_def: succ x = val (pos x + 1) pred_def: pred x = val (pos x - 1) first_el_def: first_el = val 0 last_el_def: last_el = val (int CARD( a) - 1) inj_pos: inj pos val_pos: val (pos x) = x pos_val: z range pos = pos (val z) = z first_el_smallest: first_el x last_el_greatest: x last_el pos_succ: x last_el = pos (succ x) = pos x + 1 pos_pred: x first_el = pos (pred x) = pos x - 1 succ_val: x range pos = succ (val x) = val (x + 1) pred_val: x range pos = pred (val x) = val (x - 1) Figure 4.3: Generic properties of functions on enumeration types The HOL-SPARK environment defines a type class spark_enum that captures the characteristic properties of all enumeration types. It provides the following polymorphic functions and constants for all types a of this type class: pos :: a int val :: int a succ :: a a pred :: a a first_el :: a last_el :: a In addition, spark_enum is a subclass of the linorder type class, which allows the comparison operators < and to be used on enumeration types. The polymorphic operations shown above enjoy a number of generic properties that hold for all enumeration types. These properties are listed in Fig Moreover, Fig. 4.4 shows a list of properties that are specific to each enumeration type t, such as the characteristic equations for val and pos. 22
24 t val: val 0 = e 1 t pos: pos e 1 = 0 val 1 = e 2 pos e 2 = 1.. val (n 1) = e n pos e n = n 1 t card: card(t) = n t first el: first el = e 1 t last el: last el = e n Figure 4.4: Type-specific properties of functions on enumeration types Records The FDL record type type t = record f 1 : t 1 ;. f n end; : t n is modelled by the Isabelle record type record t = f 1 :: t 1. f n :: t n Records are constructed using the notation ( f 1 = v 1,..., f n = v n ), a field f i of a record r is selected using the notation f i r, and the fields f and f of a record r can be updated using the notation r ( f := v, f := v ) Arrays The FDL array type type t = array [t 1,..., t n ] of u; is modelled by the Isabelle function type t 1 t n u. Array updates are written as A(x 1 := y 1,..., x n := y n ). To allow updating an array at a set of indices, HOL-SPARK provides the notation... [:=]..., which can be combined with... :=... and has the properties 23
25 z xs = (f(xs [:=] y)) z = y z / xs = (f(xs [:=] y)) z = f z f({x} [:=] y) = f(x := y) Thus, we can write expressions like A({0..9} [:=] 42, 15 := 99, {20..29} [:=] 0) that would be cumbersome to write using single updates. 4.3 User-defined proof functions and types To illustrate the interplay between the commands for introducing userdefined proof functions and types mentioned in 4.1, we now discuss a larger example involving the definition of proof functions on complex types. Assume we would like to define an array type, whose elements are records that themselves contain arrays. Moreover, assume we would like to initialize all array elements and record fields of type Integer in an array of this type with the value 0. The specification of package Complex Types containing the definition of the array type, which we call Array Type2, is shown in Fig It also contains the declaration of a proof function Initialized that is used to express that the array has been initialized. The two other proof functions Initialized2 and Initialized3 are used to reason about the initialization of the inner array. Since the array types and proof functions may be used by several packages, such as the one shown in Fig. 4.6, it is advantageous to define the proof functions in a central theory that can be included by other theories containing proofs about packages using Complex Types. We show this theory in Fig Since the proof functions refer to the enumeration and record types defined in Complex Types, we need to define the Isabelle counterparts of these types using the datatype and record commands in order to be able to write down the definition of the proof functions. These types are linked to the corresponding SPARK types using the spark types command. Note that we have to specify the full name of the SPARK functions including the package prefix. Using the logic of Isabelle, we can then define functions involving the enumeration and record types introduced above, and link them to the corresponding SPARK proof functions. It is important that the definition commands are preceeded by the spark types command, since the definition of initialized3 uses the val function for enumeration types that is only available once that day has been declared as a SPARK type. 24
26 package Complex_Types is type Day is (Mon, Tue, Wed, Thu, Fri, Sat, Sun); subtype Array_Index is Natural range 0.. 9; type Array_Type1 is array (Array_Index, Day) of Integer; type Record_Type is record Field1 : Array_Type1; Field2 : Integer; end record; type Array_Type2 is array (Array_Index) of Record_Type; --# function Initialized --# (A: Array_Type2; I : Natural) return Boolean; --# function Initialized2 --# (A: Array_Type1; I : Natural) return Boolean; --# function Initialized3 --# (A: Array_Type1; I : Natural; K : Natural) return Boolean; end Complex_Types; Figure 4.5: Nested array and record types 25
27 with Complex_Types; --# inherit Complex_Types; package Complex_Types_App is procedure Initialize (A : in out Complex_Types.Array_Type2); --# derives A from A; --# post Complex_Types.Initialized (A, 10); end Complex_Types_App; package body Complex_Types_App is procedure Initialize (A : in out Complex_Types.Array_Type2) is begin for I in Complex_Types.Array_Index --# assert Complex_Types.Initialized (A, I); loop for J in Complex_Types.Array_Index --# assert --# Complex_Types.Initialized (A, I) and --# Complex_Types.Initialized2 (A (I).Field1, J); loop for K in Complex_Types.Day --# assert --# Complex_Types.Initialized (A, I) and --# Complex_Types.Initialized2 (A (I).Field1, J) and --# Complex_Types.Initialized3 --# (A (I).Field1, J, Complex_Types.Day Pos (K)); loop A (I).Field1 (J, K) := 0; end loop; end loop; A (I).Field2 := 0; end loop; end Initialize; end Complex_Types_App; Figure 4.6: Application of Complex Types package 26
28 theory Complex_Types imports "HOL-SPARK.SPARK" begin datatype day = Mon Tue Wed Thu Fri Sat Sun record two_fields = Field1 :: "int day int" Field2 :: int spark types complex_types day = day complex_types record_type = two_fields definition initialized3 :: "(int day int) int int bool" where "initialized3 A i k = ( j {0..<k}. A (i, val j) = 0)" definition initialized2 :: "(int day int) int bool" where "initialized2 A i = ( j {0..<i}. initialized3 A j 7)" definition initialized :: "(int two_fields) int bool" where "initialized A i = ( j {0..<i}. initialized2 (Field1 (A j)) 10 Field2 (A j) = 0)" spark proof functions complex_types initialized = initialized complex_types initialized2 = initialized2 complex_types initialized3 = initialized3 end Figure 4.7: Theory defining proof functions for complex types 27
29 Bibliography [1] J. Barnes. The SPARK Approach to Safety and Security. Addison-Wesley,
Lecture Notes on Contracts
 Lecture Notes on Contracts 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 30, 2012 1 Introduction For an overview the course goals and the mechanics and schedule of the course,
Lecture Notes on Contracts 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 30, 2012 1 Introduction For an overview the course goals and the mechanics and schedule of the course,
CIS 890: Safety Critical Systems
 CIS 890: Safety Critical Systems Lecture: SPARK -- Analysis Tools Copyright 2007, John Hatcliff. The syllabus and all lectures for this course are copyrighted materials and may not be used in other course
CIS 890: Safety Critical Systems Lecture: SPARK -- Analysis Tools Copyright 2007, John Hatcliff. The syllabus and all lectures for this course are copyrighted materials and may not be used in other course
Induction and Semantics in Dafny
 15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
15-414 Lecture 11 1 Instructor: Matt Fredrikson Induction and Semantics in Dafny TA: Ryan Wagner Encoding the syntax of Imp Recall the abstract syntax of Imp: a AExp ::= n Z x Var a 1 + a 2 b BExp ::=
Verification Condition Generation
 Verification Condition Generation Jorge Sousa Pinto Departamento de Informática / Universidade do Minho jsp@di.uminho.pt www.di.uminho.pt/~jsp Outline (1) - From Hoare Logic to VCGen algorithms: an architecture
Verification Condition Generation Jorge Sousa Pinto Departamento de Informática / Universidade do Minho jsp@di.uminho.pt www.di.uminho.pt/~jsp Outline (1) - From Hoare Logic to VCGen algorithms: an architecture
Lecture Notes on Ints
 Lecture Notes on Ints 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 26, 2010 1 Introduction Two fundamental types in almost any programming language are booleans and integers.
Lecture Notes on Ints 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 26, 2010 1 Introduction Two fundamental types in almost any programming language are booleans and integers.
Program Verification (6EC version only)
 Program Verification (6EC version only) Erik Poll Digital Security Radboud University Nijmegen Overview Program Verification using Verification Condition Generators JML a formal specification language
Program Verification (6EC version only) Erik Poll Digital Security Radboud University Nijmegen Overview Program Verification using Verification Condition Generators JML a formal specification language
An Annotated Language
 Hoare Logic An Annotated Language State and Semantics Expressions are interpreted as functions from states to the corresponding domain of interpretation Operators have the obvious interpretation Free of
Hoare Logic An Annotated Language State and Semantics Expressions are interpreted as functions from states to the corresponding domain of interpretation Operators have the obvious interpretation Free of
GNATprove a Spark2014 verifying compiler Florian Schanda, Altran UK
 1 GNATprove a Spark2014 verifying compiler Florian Schanda, Altran UK Tool architecture User view Source gnatprove Verdict 2 Tool architecture More detailed view... Source Encoding CVC4 gnat2why gnatwhy3
1 GNATprove a Spark2014 verifying compiler Florian Schanda, Altran UK Tool architecture User view Source gnatprove Verdict 2 Tool architecture More detailed view... Source Encoding CVC4 gnat2why gnatwhy3
Lecture 1 Contracts : Principles of Imperative Computation (Fall 2018) Frank Pfenning
 Lecture 1 Contracts 15-122: Principles of Imperative Computation (Fall 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Lecture 1 Contracts 15-122: Principles of Imperative Computation (Fall 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Integers and Mathematical Induction
 IT Program, NTUT, Fall 07 Integers and Mathematical Induction Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology TAIWAN 1 Learning Objectives Learn about
IT Program, NTUT, Fall 07 Integers and Mathematical Induction Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology TAIWAN 1 Learning Objectives Learn about
Assertions & Verification Example Exam Questions
 2009 November 23 Assertions & Verification Example Exam Questions 1. 2. A B C Give a general template for refining an operation into a sequence and state what questions a designer must answer to verify
2009 November 23 Assertions & Verification Example Exam Questions 1. 2. A B C Give a general template for refining an operation into a sequence and state what questions a designer must answer to verify
Lecture 1 Contracts. 1 A Mysterious Program : Principles of Imperative Computation (Spring 2018) Frank Pfenning
 Lecture 1 Contracts 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Lecture 1 Contracts 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Verification Condition Generation via Theorem Proving
 Verification Condition Generation via Theorem Proving John Matthews Galois Connections Inc. J Strother Moore University of Texas at Austin Sandip Ray University of Texas at Austin Daron Vroon Georgia Institute
Verification Condition Generation via Theorem Proving John Matthews Galois Connections Inc. J Strother Moore University of Texas at Austin Sandip Ray University of Texas at Austin Daron Vroon Georgia Institute
From Types to Sets in Isabelle/HOL
 From Types to Sets in Isabelle/HOL Extented Abstract Ondřej Kunčar 1 and Andrei Popescu 1,2 1 Fakultät für Informatik, Technische Universität München, Germany 2 Institute of Mathematics Simion Stoilow
From Types to Sets in Isabelle/HOL Extented Abstract Ondřej Kunčar 1 and Andrei Popescu 1,2 1 Fakultät für Informatik, Technische Universität München, Germany 2 Institute of Mathematics Simion Stoilow
Declaring Numbers. Bernd Braßel, Frank Huch and Sebastian Fischer. Department of Computer Science, University of Kiel, Germany
 Declaring Numbers Bernd Braßel, Frank Huch and Sebastian Fischer Department of Computer Science, University of Kiel, Germany WFLP 2007, Paris, France I m going to present joint work with my colleagues
Declaring Numbers Bernd Braßel, Frank Huch and Sebastian Fischer Department of Computer Science, University of Kiel, Germany WFLP 2007, Paris, France I m going to present joint work with my colleagues
Assertions & Verification & Example Loop Invariants Example Exam Questions
 2014 November 27 1. Assertions & Verification & Example Loop Invariants Example Exam Questions 2. A B C Give a general template for refining an operation into a sequence and state what questions a designer
2014 November 27 1. Assertions & Verification & Example Loop Invariants Example Exam Questions 2. A B C Give a general template for refining an operation into a sequence and state what questions a designer
CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer Science (Arkoudas and Musser) Section 17.2
 CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer Science (Arkoudas and Musser) Section 17.2 Instructor: Carlos Varela Rensselaer Polytechnic Institute Spring 2018 CSCI.6962/4962
CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer Science (Arkoudas and Musser) Section 17.2 Instructor: Carlos Varela Rensselaer Polytechnic Institute Spring 2018 CSCI.6962/4962
15-122: Principles of Imperative Computation (Section G)
 15-122: Principles of Imperative Computation (Section G) Document 2 Solutions 0. Contracts This lecture was mainly about contracts and ensuring correctness of code. Josh Zimmerman There are 4 types of
15-122: Principles of Imperative Computation (Section G) Document 2 Solutions 0. Contracts This lecture was mainly about contracts and ensuring correctness of code. Josh Zimmerman There are 4 types of
Bits, Words, and Integers
 Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer Science (Arkoudas and Musser) Sections p.
 CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer Science (Arkoudas and Musser) Sections 10.1-10.3 p. 1/106 CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer
CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer Science (Arkoudas and Musser) Sections 10.1-10.3 p. 1/106 CSCI.6962/4962 Software Verification Fundamental Proof Methods in Computer
SPARK Examiner with Run-time Checker Generation of VCs for SPARK Programs
 Status: Definitive 22 November 2005 Originator Team Approver Team Line Manager Copyright The contents of this manual are the subject of copyright and all rights in it are reserved. The manual may not be
Status: Definitive 22 November 2005 Originator Team Approver Team Line Manager Copyright The contents of this manual are the subject of copyright and all rights in it are reserved. The manual may not be
Chapter 3 (part 3) Describing Syntax and Semantics
 Chapter 3 (part 3) Describing Syntax and Semantics Chapter 3 Topics Introduction The General Problem of Describing Syntax Formal Methods of Describing Syntax Attribute Grammars Describing the Meanings
Chapter 3 (part 3) Describing Syntax and Semantics Chapter 3 Topics Introduction The General Problem of Describing Syntax Formal Methods of Describing Syntax Attribute Grammars Describing the Meanings
Lecture Notes on Arrays
 Lecture Notes on Arrays 15-122: Principles of Imperative Computation July 2, 2013 1 Introduction So far we have seen how to process primitive data like integers in imperative programs. That is useful,
Lecture Notes on Arrays 15-122: Principles of Imperative Computation July 2, 2013 1 Introduction So far we have seen how to process primitive data like integers in imperative programs. That is useful,
Math Introduction to Advanced Mathematics
 Math 215 - Introduction to Advanced Mathematics Number Theory Fall 2017 The following introductory guide to number theory is borrowed from Drew Shulman and is used in a couple of other Math 215 classes.
Math 215 - Introduction to Advanced Mathematics Number Theory Fall 2017 The following introductory guide to number theory is borrowed from Drew Shulman and is used in a couple of other Math 215 classes.
SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION
 CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Copyright Cengage Learning. All rights reserved. SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All rights reserved.
CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Copyright Cengage Learning. All rights reserved. SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All rights reserved.
COMPUTER SCIENCE TRIPOS
 CST.2000.1.1 COMPUTER SCIENCE TRIPOS Part IA Monday 5 June 2000 1.30 to 4.30 Paper 1 Answer two questions from Section A, and one question from each of Sections B, C, D and E. Submit the answers in six
CST.2000.1.1 COMPUTER SCIENCE TRIPOS Part IA Monday 5 June 2000 1.30 to 4.30 Paper 1 Answer two questions from Section A, and one question from each of Sections B, C, D and E. Submit the answers in six
Functional Programming and Modeling
 Chapter 2 2. Functional Programming and Modeling 2.0 2. Functional Programming and Modeling 2.0 Overview of Chapter Functional Programming and Modeling 2. Functional Programming and Modeling 2.1 Overview
Chapter 2 2. Functional Programming and Modeling 2.0 2. Functional Programming and Modeling 2.0 Overview of Chapter Functional Programming and Modeling 2. Functional Programming and Modeling 2.1 Overview
FreePascal changes: user documentation
 FreePascal changes: user documentation Table of Contents Jochem Berndsen February 2007 1Introduction...1 2Accepted syntax...2 Declarations...2 Statements...3 Class invariants...3 3Semantics...3 Definitions,
FreePascal changes: user documentation Table of Contents Jochem Berndsen February 2007 1Introduction...1 2Accepted syntax...2 Declarations...2 Statements...3 Class invariants...3 3Semantics...3 Definitions,
Computing Fundamentals 2 Introduction to CafeOBJ
 Computing Fundamentals 2 Introduction to CafeOBJ Lecturer: Patrick Browne Lecture Room: K408 Lab Room: A308 Based on work by: Nakamura Masaki, João Pascoal Faria, Prof. Heinrich Hußmann. See notes on slides
Computing Fundamentals 2 Introduction to CafeOBJ Lecturer: Patrick Browne Lecture Room: K408 Lab Room: A308 Based on work by: Nakamura Masaki, João Pascoal Faria, Prof. Heinrich Hußmann. See notes on slides
6. Hoare Logic and Weakest Preconditions
 6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
CS152: Programming Languages. Lecture 11 STLC Extensions and Related Topics. Dan Grossman Spring 2011
 CS152: Programming Languages Lecture 11 STLC Extensions and Related Topics Dan Grossman Spring 2011 Review e ::= λx. e x e e c v ::= λx. e c τ ::= int τ τ Γ ::= Γ, x : τ (λx. e) v e[v/x] e 1 e 1 e 1 e
CS152: Programming Languages Lecture 11 STLC Extensions and Related Topics Dan Grossman Spring 2011 Review e ::= λx. e x e e c v ::= λx. e c τ ::= int τ τ Γ ::= Γ, x : τ (λx. e) v e[v/x] e 1 e 1 e 1 e
Specification, Verification, and Interactive Proof
 Specification, Verification, and Interactive Proof SRI International May 23, 2016 PVS PVS - Prototype Verification System PVS is a verification system combining language expressiveness with automated tools.
Specification, Verification, and Interactive Proof SRI International May 23, 2016 PVS PVS - Prototype Verification System PVS is a verification system combining language expressiveness with automated tools.
THE AGDA STANDARD LIBRARY
 THE AGDA STANDARD LIBRARY N. P. STRICKLAND 1. Introduction In this document we give a survey of the structure, organisation and contents of the Agda standard library. We will mostly ignore foundational
THE AGDA STANDARD LIBRARY N. P. STRICKLAND 1. Introduction In this document we give a survey of the structure, organisation and contents of the Agda standard library. We will mostly ignore foundational
Axiomatic Specification. Al-Said, Apcar, Jerejian
 Axiomatic Specification Al-Said, Apcar, Jerejian 1 Axioms: Wffs that can be written down without any reference to any other Wffs. Wffs that are stipulated as unproved premises for the proof of other wffs
Axiomatic Specification Al-Said, Apcar, Jerejian 1 Axioms: Wffs that can be written down without any reference to any other Wffs. Wffs that are stipulated as unproved premises for the proof of other wffs
1 Elementary number theory
 Math 215 - Introduction to Advanced Mathematics Spring 2019 1 Elementary number theory We assume the existence of the natural numbers and the integers N = {1, 2, 3,...} Z = {..., 3, 2, 1, 0, 1, 2, 3,...},
Math 215 - Introduction to Advanced Mathematics Spring 2019 1 Elementary number theory We assume the existence of the natural numbers and the integers N = {1, 2, 3,...} Z = {..., 3, 2, 1, 0, 1, 2, 3,...},
SECTION II: LANGUAGE BASICS
 Chapter 5 SECTION II: LANGUAGE BASICS Operators Chapter 04: Basic Fundamentals demonstrated declaring and initializing variables. This chapter depicts how to do something with them, using operators. Operators
Chapter 5 SECTION II: LANGUAGE BASICS Operators Chapter 04: Basic Fundamentals demonstrated declaring and initializing variables. This chapter depicts how to do something with them, using operators. Operators
Lecture Notes: Hoare Logic
 Lecture Notes: Hoare Logic 17-654/17-754: Analysis of Software Artifacts Jonathan Aldrich (jonathan.aldrich@cs.cmu.edu) Lecture 3 1 Hoare Logic The goal of Hoare logic is to provide a formal system for
Lecture Notes: Hoare Logic 17-654/17-754: Analysis of Software Artifacts Jonathan Aldrich (jonathan.aldrich@cs.cmu.edu) Lecture 3 1 Hoare Logic The goal of Hoare logic is to provide a formal system for
COE428 Lecture Notes Week 1 (Week of January 9, 2017)
 COE428 Lecture Notes: Week 1 1 of 10 COE428 Lecture Notes Week 1 (Week of January 9, 2017) Table of Contents COE428 Lecture Notes Week 1 (Week of January 9, 2017)...1 Announcements...1 Topics...1 Informal
COE428 Lecture Notes: Week 1 1 of 10 COE428 Lecture Notes Week 1 (Week of January 9, 2017) Table of Contents COE428 Lecture Notes Week 1 (Week of January 9, 2017)...1 Announcements...1 Topics...1 Informal
Lecture 7: General Loops (Chapter 7)
 CS 101: Computer Programming and Utilization Jul-Nov 2017 Umesh Bellur (cs101@cse.iitb.ac.in) Lecture 7: General Loops (Chapter 7) The Need for a More General Loop Read marks of students from the keyboard
CS 101: Computer Programming and Utilization Jul-Nov 2017 Umesh Bellur (cs101@cse.iitb.ac.in) Lecture 7: General Loops (Chapter 7) The Need for a More General Loop Read marks of students from the keyboard
Status: Informal Type: Technical. This document gives an example of the Compliance Notation.
 Project: Title: Status: Informal Type: Technical Author: Name Location Signature Date R.D. Arthan Abstract: WIN01 This document gives an example of the. Distribution: Library Copyright c : Lemma 1 Ltd
Project: Title: Status: Informal Type: Technical Author: Name Location Signature Date R.D. Arthan Abstract: WIN01 This document gives an example of the. Distribution: Library Copyright c : Lemma 1 Ltd
Lecture 3 Notes Arrays
 Lecture 3 Notes Arrays 15-122: Principles of Imperative Computation (Summer 1 2015) Frank Pfenning, André Platzer 1 Introduction So far we have seen how to process primitive data like integers in imperative
Lecture 3 Notes Arrays 15-122: Principles of Imperative Computation (Summer 1 2015) Frank Pfenning, André Platzer 1 Introduction So far we have seen how to process primitive data like integers in imperative
Integration of SMT Solvers with ITPs There and Back Again
 Integration of SMT Solvers with ITPs There and Back Again Sascha Böhme and University of Sheffield 7 May 2010 1 2 Features: SMT-LIB vs. Yices Translation Techniques Caveats 3 4 Motivation Motivation System
Integration of SMT Solvers with ITPs There and Back Again Sascha Böhme and University of Sheffield 7 May 2010 1 2 Features: SMT-LIB vs. Yices Translation Techniques Caveats 3 4 Motivation Motivation System
CSCE 314 Programming Languages
 CSCE 314 Programming Languages Haskell: Declaring Types and Classes Dr. Hyunyoung Lee 1 Outline Declaring Data Types Class and Instance Declarations 2 Defining New Types Three constructs for defining types:
CSCE 314 Programming Languages Haskell: Declaring Types and Classes Dr. Hyunyoung Lee 1 Outline Declaring Data Types Class and Instance Declarations 2 Defining New Types Three constructs for defining types:
VS 3 : SMT Solvers for Program Verification
 VS 3 : SMT Solvers for Program Verification Saurabh Srivastava 1,, Sumit Gulwani 2, and Jeffrey S. Foster 1 1 University of Maryland, College Park, {saurabhs,jfoster}@cs.umd.edu 2 Microsoft Research, Redmond,
VS 3 : SMT Solvers for Program Verification Saurabh Srivastava 1,, Sumit Gulwani 2, and Jeffrey S. Foster 1 1 University of Maryland, College Park, {saurabhs,jfoster}@cs.umd.edu 2 Microsoft Research, Redmond,
Recursion. Lars-Henrik Eriksson. Functional Programming 1. Based on a presentation by Tjark Weber and notes by Sven-Olof Nyström
 Lars-Henrik Eriksson Functional Programming 1 Based on a presentation by Tjark Weber and notes by Sven-Olof Nyström Tjark Weber (UU) Recursion 1 / 41 Comparison: Imperative/Functional Programming Comparison:
Lars-Henrik Eriksson Functional Programming 1 Based on a presentation by Tjark Weber and notes by Sven-Olof Nyström Tjark Weber (UU) Recursion 1 / 41 Comparison: Imperative/Functional Programming Comparison:
Abstract Interpretation
 Abstract Interpretation Ranjit Jhala, UC San Diego April 22, 2013 Fundamental Challenge of Program Analysis How to infer (loop) invariants? Fundamental Challenge of Program Analysis Key issue for any analysis
Abstract Interpretation Ranjit Jhala, UC San Diego April 22, 2013 Fundamental Challenge of Program Analysis How to infer (loop) invariants? Fundamental Challenge of Program Analysis Key issue for any analysis
Proving SPARK Verification Conditions with SMT solvers
 manuscript No. (will be inserted by the editor) Proving SPARK Verification Conditions with SMT solvers Paul B. Jackson Grant Olney Passmore Received: date / Accepted: date Abstract We have constructed
manuscript No. (will be inserted by the editor) Proving SPARK Verification Conditions with SMT solvers Paul B. Jackson Grant Olney Passmore Received: date / Accepted: date Abstract We have constructed
Lecture 6: Arithmetic and Threshold Circuits
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 6: Arithmetic and Threshold Circuits David Mix Barrington and Alexis Maciel July
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 6: Arithmetic and Threshold Circuits David Mix Barrington and Alexis Maciel July
Typed Racket: Racket with Static Types
 Typed Racket: Racket with Static Types Version 5.0.2 Sam Tobin-Hochstadt November 6, 2010 Typed Racket is a family of languages, each of which enforce that programs written in the language obey a type
Typed Racket: Racket with Static Types Version 5.0.2 Sam Tobin-Hochstadt November 6, 2010 Typed Racket is a family of languages, each of which enforce that programs written in the language obey a type
Isabelle/jEdit as IDE for domain-specific formal languages and informal text documents
 Isabelle/jEdit as IDE for domain-specific formal languages and informal text documents Makarius Wenzel http://sketis.net June 2018 λ = Isabelle β PIDE α Isabelle/jEdit as Formal IDE Abstract Isabelle/jEdit
Isabelle/jEdit as IDE for domain-specific formal languages and informal text documents Makarius Wenzel http://sketis.net June 2018 λ = Isabelle β PIDE α Isabelle/jEdit as Formal IDE Abstract Isabelle/jEdit
The Typed Racket Guide
 The Typed Racket Guide Version 5.3.6 Sam Tobin-Hochstadt and Vincent St-Amour August 9, 2013 Typed Racket is a family of languages, each of which enforce
The Typed Racket Guide Version 5.3.6 Sam Tobin-Hochstadt and Vincent St-Amour August 9, 2013 Typed Racket is a family of languages, each of which enforce
Overloading, Type Classes, and Algebraic Datatypes
 Overloading, Type Classes, and Algebraic Datatypes Delivered by Michael Pellauer Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. September 28, 2006 September 28, 2006 http://www.csg.csail.mit.edu/6.827
Overloading, Type Classes, and Algebraic Datatypes Delivered by Michael Pellauer Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. September 28, 2006 September 28, 2006 http://www.csg.csail.mit.edu/6.827
Formalization of Incremental Simplex Algorithm by Stepwise Refinement
 Formalization of Incremental Simplex Algorithm by Stepwise Refinement Mirko Spasić, Filip Marić Faculty of Mathematics, University of Belgrade FM2012, 30. August 2012. Overview 1 Introduction 2 Approach
Formalization of Incremental Simplex Algorithm by Stepwise Refinement Mirko Spasić, Filip Marić Faculty of Mathematics, University of Belgrade FM2012, 30. August 2012. Overview 1 Introduction 2 Approach
Types and Type Inference
 CS 242 2012 Types and Type Inference Notes modified from John Mitchell and Kathleen Fisher Reading: Concepts in Programming Languages, Revised Chapter 6 - handout on Web!! Outline General discussion of
CS 242 2012 Types and Type Inference Notes modified from John Mitchell and Kathleen Fisher Reading: Concepts in Programming Languages, Revised Chapter 6 - handout on Web!! Outline General discussion of
Why. an intermediate language for deductive program verification
 Why an intermediate language for deductive program verification Jean-Christophe Filliâtre CNRS Orsay, France AFM workshop Grenoble, June 27, 2009 Jean-Christophe Filliâtre Why tutorial AFM 09 1 / 56 Motivations
Why an intermediate language for deductive program verification Jean-Christophe Filliâtre CNRS Orsay, France AFM workshop Grenoble, June 27, 2009 Jean-Christophe Filliâtre Why tutorial AFM 09 1 / 56 Motivations
ELEMENTARY NUMBER THEORY AND METHODS OF PROOF
 CHAPTER 4 ELEMENTARY NUMBER THEORY AND METHODS OF PROOF Copyright Cengage Learning. All rights reserved. SECTION 4.8 Application: Algorithms Copyright Cengage Learning. All rights reserved. Application:
CHAPTER 4 ELEMENTARY NUMBER THEORY AND METHODS OF PROOF Copyright Cengage Learning. All rights reserved. SECTION 4.8 Application: Algorithms Copyright Cengage Learning. All rights reserved. Application:
3.7 Denotational Semantics
 3.7 Denotational Semantics Denotational semantics, also known as fixed-point semantics, associates to each programming language construct a well-defined and rigorously understood mathematical object. These
3.7 Denotational Semantics Denotational semantics, also known as fixed-point semantics, associates to each programming language construct a well-defined and rigorously understood mathematical object. These
Exercise 1 ( = 22 points)
 1 Exercise 1 (4 + 3 + 4 + 5 + 6 = 22 points) The following data structure represents polymorphic lists that can contain values of two types in arbitrary order: data DuoList a b = C a (DuoList a b) D b
1 Exercise 1 (4 + 3 + 4 + 5 + 6 = 22 points) The following data structure represents polymorphic lists that can contain values of two types in arbitrary order: data DuoList a b = C a (DuoList a b) D b
A CRASH COURSE IN SEMANTICS
 LAST TIME Recdef More induction NICTA Advanced Course Well founded orders Slide 1 Theorem Proving Principles, Techniques, Applications Slide 3 Well founded recursion Calculations: also/finally {P}... {Q}
LAST TIME Recdef More induction NICTA Advanced Course Well founded orders Slide 1 Theorem Proving Principles, Techniques, Applications Slide 3 Well founded recursion Calculations: also/finally {P}... {Q}
Excerpt from "Art of Problem Solving Volume 1: the Basics" 2014 AoPS Inc.
 Chapter 5 Using the Integers In spite of their being a rather restricted class of numbers, the integers have a lot of interesting properties and uses. Math which involves the properties of integers is
Chapter 5 Using the Integers In spite of their being a rather restricted class of numbers, the integers have a lot of interesting properties and uses. Math which involves the properties of integers is
Provably Correct Software
 Provably Correct Software Max Schäfer Institute of Information Science/Academia Sinica September 17, 2007 1 / 48 The Need for Provably Correct Software BUT bugs are annoying, embarrassing, and cost gazillions
Provably Correct Software Max Schäfer Institute of Information Science/Academia Sinica September 17, 2007 1 / 48 The Need for Provably Correct Software BUT bugs are annoying, embarrassing, and cost gazillions
Part II. Hoare Logic and Program Verification. Why specify programs? Specification and Verification. Code Verification. Why verify programs?
 Part II. Hoare Logic and Program Verification Part II. Hoare Logic and Program Verification Dilian Gurov Props: Models: Specs: Method: Tool: safety of data manipulation source code logic assertions Hoare
Part II. Hoare Logic and Program Verification Part II. Hoare Logic and Program Verification Dilian Gurov Props: Models: Specs: Method: Tool: safety of data manipulation source code logic assertions Hoare
Algorithm Analysis. (Algorithm Analysis ) Data Structures and Programming Spring / 48
 Algorithm Analysis (Algorithm Analysis ) Data Structures and Programming Spring 2018 1 / 48 What is an Algorithm? An algorithm is a clearly specified set of instructions to be followed to solve a problem
Algorithm Analysis (Algorithm Analysis ) Data Structures and Programming Spring 2018 1 / 48 What is an Algorithm? An algorithm is a clearly specified set of instructions to be followed to solve a problem
Chapter 3. Describing Syntax and Semantics
 Chapter 3 Describing Syntax and Semantics Chapter 3 Topics Introduction The General Problem of Describing Syntax Formal Methods of Describing Syntax Attribute Grammars Describing the Meanings of Programs:
Chapter 3 Describing Syntax and Semantics Chapter 3 Topics Introduction The General Problem of Describing Syntax Formal Methods of Describing Syntax Attribute Grammars Describing the Meanings of Programs:
Softwaretechnik. Program verification. Albert-Ludwigs-Universität Freiburg. June 28, Softwaretechnik June 28, / 24
 Softwaretechnik Program verification Albert-Ludwigs-Universität Freiburg June 28, 2012 Softwaretechnik June 28, 2012 1 / 24 Road Map Program verification Automatic program verification Programs with loops
Softwaretechnik Program verification Albert-Ludwigs-Universität Freiburg June 28, 2012 Softwaretechnik June 28, 2012 1 / 24 Road Map Program verification Automatic program verification Programs with loops
AXIOMS FOR THE INTEGERS
 AXIOMS FOR THE INTEGERS BRIAN OSSERMAN We describe the set of axioms for the integers which we will use in the class. The axioms are almost the same as what is presented in Appendix A of the textbook,
AXIOMS FOR THE INTEGERS BRIAN OSSERMAN We describe the set of axioms for the integers which we will use in the class. The axioms are almost the same as what is presented in Appendix A of the textbook,
Softwaretechnik. Program verification. Software Engineering Albert-Ludwigs-University Freiburg. June 30, 2011
 Softwaretechnik Program verification Software Engineering Albert-Ludwigs-University Freiburg June 30, 2011 (Software Engineering) Softwaretechnik June 30, 2011 1 / 28 Road Map Program verification Automatic
Softwaretechnik Program verification Software Engineering Albert-Ludwigs-University Freiburg June 30, 2011 (Software Engineering) Softwaretechnik June 30, 2011 1 / 28 Road Map Program verification Automatic
Mathematical Induction
 Mathematical Induction Victor Adamchik Fall of 2005 Lecture 3 (out of three) Plan 1. Recursive Definitions 2. Recursively Defined Sets 3. Program Correctness Recursive Definitions Sometimes it is easier
Mathematical Induction Victor Adamchik Fall of 2005 Lecture 3 (out of three) Plan 1. Recursive Definitions 2. Recursively Defined Sets 3. Program Correctness Recursive Definitions Sometimes it is easier
Theorem proving. PVS theorem prover. Hoare style verification PVS. More on embeddings. What if. Abhik Roychoudhury CS 6214
 Theorem proving PVS theorem prover Abhik Roychoudhury National University of Singapore Both specification and implementation can be formalized in a suitable logic. Proof rules for proving statements in
Theorem proving PVS theorem prover Abhik Roychoudhury National University of Singapore Both specification and implementation can be formalized in a suitable logic. Proof rules for proving statements in
Contents. Program 1. Java s Integral Types in PVS (p.4 of 37)
 Java s Integral Types in PVS Bart Jacobs bart@cs.kun.nl www.cs.kun.nl/ bart www.verificard.org. Dep. Computer Science, Univ. Nijmegen, NL Contents I. Example programs II. Integral types in Java (implementations)
Java s Integral Types in PVS Bart Jacobs bart@cs.kun.nl www.cs.kun.nl/ bart www.verificard.org. Dep. Computer Science, Univ. Nijmegen, NL Contents I. Example programs II. Integral types in Java (implementations)
Isabelle s meta-logic. p.1
 Isabelle s meta-logic p.1 Basic constructs Implication = (==>) For separating premises and conclusion of theorems p.2 Basic constructs Implication = (==>) For separating premises and conclusion of theorems
Isabelle s meta-logic p.1 Basic constructs Implication = (==>) For separating premises and conclusion of theorems p.2 Basic constructs Implication = (==>) For separating premises and conclusion of theorems
SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION
 CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Alessandro Artale UniBZ - http://www.inf.unibz.it/ artale/ SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All
CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Alessandro Artale UniBZ - http://www.inf.unibz.it/ artale/ SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All
Introduction. chapter Functions
 chapter 1 Introduction In this chapter we set the stage for the rest of the book. We start by reviewing the notion of a function, then introduce the concept of functional programming, summarise the main
chapter 1 Introduction In this chapter we set the stage for the rest of the book. We start by reviewing the notion of a function, then introduce the concept of functional programming, summarise the main
Lecture 12: Data Types (and Some Leftover ML)
 Lecture 12: Data Types (and Some Leftover ML) COMP 524 Programming Language Concepts Stephen Olivier March 3, 2009 Based on slides by A. Block, notes by N. Fisher, F. Hernandez-Campos, and D. Stotts Goals
Lecture 12: Data Types (and Some Leftover ML) COMP 524 Programming Language Concepts Stephen Olivier March 3, 2009 Based on slides by A. Block, notes by N. Fisher, F. Hernandez-Campos, and D. Stotts Goals
AXIOMS OF AN IMPERATIVE LANGUAGE PARTIAL CORRECTNESS WEAK AND STRONG CONDITIONS. THE AXIOM FOR nop
 AXIOMS OF AN IMPERATIVE LANGUAGE We will use the same language, with the same abstract syntax that we used for operational semantics. However, we will only be concerned with the commands, since the language
AXIOMS OF AN IMPERATIVE LANGUAGE We will use the same language, with the same abstract syntax that we used for operational semantics. However, we will only be concerned with the commands, since the language
Content Development for Distance Education in Advanced University Mathematics Using Mizar
 Content Development for Distance Education in Advanced University Mathematics Using Mizar Takaya IDO 1, Hiroyuki OKAZAKI 1, Hiroshi YAMAZAKI 1, Pauline Naomi KAWAMOTO 1, Katsumi WASAKI 1, and Yasunari
Content Development for Distance Education in Advanced University Mathematics Using Mizar Takaya IDO 1, Hiroyuki OKAZAKI 1, Hiroshi YAMAZAKI 1, Pauline Naomi KAWAMOTO 1, Katsumi WASAKI 1, and Yasunari
Softwaretechnik. Lecture 03: Types and Type Soundness. Peter Thiemann. University of Freiburg, Germany SS 2008
 Softwaretechnik Lecture 03: Types and Type Soundness Peter Thiemann University of Freiburg, Germany SS 2008 Peter Thiemann (Univ. Freiburg) Softwaretechnik SWT 1 / 35 Table of Contents Types and Type correctness
Softwaretechnik Lecture 03: Types and Type Soundness Peter Thiemann University of Freiburg, Germany SS 2008 Peter Thiemann (Univ. Freiburg) Softwaretechnik SWT 1 / 35 Table of Contents Types and Type correctness
CSC313 High Integrity Systems/CSCM13 Critical Systems. CSC313/CSCM13 Chapter 2 1/ 221
 CSC313 High Integrity Systems/CSCM13 Critical Systems CSC313/CSCM13 Chapter 2 1/ 221 CSC313 High Integrity Systems/ CSCM13 Critical Systems Course Notes Chapter 2: SPARK Ada Sect. 2 (f) Anton Setzer Dept.
CSC313 High Integrity Systems/CSCM13 Critical Systems CSC313/CSCM13 Chapter 2 1/ 221 CSC313 High Integrity Systems/ CSCM13 Critical Systems Course Notes Chapter 2: SPARK Ada Sect. 2 (f) Anton Setzer Dept.
COP4020 Programming Assignment 1 - Spring 2011
 COP4020 Programming Assignment 1 - Spring 2011 In this programming assignment we design and implement a small imperative programming language Micro-PL. To execute Mirco-PL code we translate the code to
COP4020 Programming Assignment 1 - Spring 2011 In this programming assignment we design and implement a small imperative programming language Micro-PL. To execute Mirco-PL code we translate the code to
XACML Function Annotations
 XACML Function Annotations Prathima Rao Dan Lin Elisa Bertino Department of Computer Science Purdue University {prao,lindan,bertino}@cs.purdue.edu Abstract XACML is being increasingly adopted in large
XACML Function Annotations Prathima Rao Dan Lin Elisa Bertino Department of Computer Science Purdue University {prao,lindan,bertino}@cs.purdue.edu Abstract XACML is being increasingly adopted in large
MITOCW watch?v=kvtlwgctwn4
 MITOCW watch?v=kvtlwgctwn4 PROFESSOR: The idea of congruence was introduced to the world by Gauss in the early 18th century. You've heard of him before, I think. He's responsible for some work on magnetism
MITOCW watch?v=kvtlwgctwn4 PROFESSOR: The idea of congruence was introduced to the world by Gauss in the early 18th century. You've heard of him before, I think. He's responsible for some work on magnetism
Unit 3. Operators. School of Science and Technology INTRODUCTION
 INTRODUCTION Operators Unit 3 In the previous units (unit 1 and 2) you have learned about the basics of computer programming, different data types, constants, keywords and basic structure of a C program.
INTRODUCTION Operators Unit 3 In the previous units (unit 1 and 2) you have learned about the basics of computer programming, different data types, constants, keywords and basic structure of a C program.
1.3. Conditional expressions To express case distinctions like
 Introduction Much of the theory developed in the underlying course Logic II can be implemented in a proof assistant. In the present setting this is interesting, since we can then machine extract from a
Introduction Much of the theory developed in the underlying course Logic II can be implemented in a proof assistant. In the present setting this is interesting, since we can then machine extract from a
Programming Lecture 3
 Programming Lecture 3 Expressions (Chapter 3) Primitive types Aside: Context Free Grammars Constants, variables Identifiers Variable declarations Arithmetic expressions Operator precedence Assignment statements
Programming Lecture 3 Expressions (Chapter 3) Primitive types Aside: Context Free Grammars Constants, variables Identifiers Variable declarations Arithmetic expressions Operator precedence Assignment statements
From Event-B Models to Dafny Code Contracts
 From Event-B Models to Dafny Code Contracts Mohammadsadegh Dalvandi, Michael Butler, Abdolbaghi Rezazadeh Electronic and Computer Science School, University of Southampton Southampton, United Kingdom {md5g11,mjb,ra3}@ecs.soton.ac.uk
From Event-B Models to Dafny Code Contracts Mohammadsadegh Dalvandi, Michael Butler, Abdolbaghi Rezazadeh Electronic and Computer Science School, University of Southampton Southampton, United Kingdom {md5g11,mjb,ra3}@ecs.soton.ac.uk
Chapter 15. Functional Programming. Topics. Currying. Currying: example. Currying: example. Reduction
 Topics Chapter 15 Functional Programming Reduction and Currying Recursive definitions Local definitions Type Systems Strict typing Polymorphism Classes Booleans Characters Enumerations Tuples Strings 2
Topics Chapter 15 Functional Programming Reduction and Currying Recursive definitions Local definitions Type Systems Strict typing Polymorphism Classes Booleans Characters Enumerations Tuples Strings 2
Lecture Notes on Linear Search
 Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 28, 2014 1 Introduction One of the fundamental and recurring problems in computer science is
Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 28, 2014 1 Introduction One of the fundamental and recurring problems in computer science is
1 Introduction. 3 Syntax
 CS 6110 S18 Lecture 19 Typed λ-calculus 1 Introduction Type checking is a lightweight technique for proving simple properties of programs. Unlike theorem-proving techniques based on axiomatic semantics,
CS 6110 S18 Lecture 19 Typed λ-calculus 1 Introduction Type checking is a lightweight technique for proving simple properties of programs. Unlike theorem-proving techniques based on axiomatic semantics,
Reasoning about programs
 Reasoning about programs Last time Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Reasoning about programs Last time Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Last time. Reasoning about programs. Coming up. Project Final Presentations. This Thursday, Nov 30: 4 th in-class exercise
 Last time Reasoning about programs Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Last time Reasoning about programs Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
CS 161 Computer Security
 Wagner Spring 2014 CS 161 Computer Security 1/27 Reasoning About Code Often functions make certain assumptions about their arguments, and it is the caller s responsibility to make sure those assumptions
Wagner Spring 2014 CS 161 Computer Security 1/27 Reasoning About Code Often functions make certain assumptions about their arguments, and it is the caller s responsibility to make sure those assumptions
Data types for mcrl2
 Data types for mcrl2 Aad Mathijssen April 5, 2018 We provide a syntax for the standard data types of the mcrl2 language. This syntax is intended to be a practical mix between standard mathematical notation
Data types for mcrl2 Aad Mathijssen April 5, 2018 We provide a syntax for the standard data types of the mcrl2 language. This syntax is intended to be a practical mix between standard mathematical notation
Calculation of extended gcd by normalization
 SCIREA Journal of Mathematics http://www.scirea.org/journal/mathematics August 2, 2018 Volume 3, Issue 3, June 2018 Calculation of extended gcd by normalization WOLF Marc, WOLF François, LE COZ Corentin
SCIREA Journal of Mathematics http://www.scirea.org/journal/mathematics August 2, 2018 Volume 3, Issue 3, June 2018 Calculation of extended gcd by normalization WOLF Marc, WOLF François, LE COZ Corentin
Problem Solving with C++
 GLOBAL EDITION Problem Solving with C++ NINTH EDITION Walter Savitch Kendrick Mock Ninth Edition PROBLEM SOLVING with C++ Problem Solving with C++, Global Edition Cover Title Copyright Contents Chapter
GLOBAL EDITION Problem Solving with C++ NINTH EDITION Walter Savitch Kendrick Mock Ninth Edition PROBLEM SOLVING with C++ Problem Solving with C++, Global Edition Cover Title Copyright Contents Chapter
Discrete Mathematics Lecture 4. Harper Langston New York University
 Discrete Mathematics Lecture 4 Harper Langston New York University Sequences Sequence is a set of (usually infinite number of) ordered elements: a 1, a 2,, a n, Each individual element a k is called a
Discrete Mathematics Lecture 4 Harper Langston New York University Sequences Sequence is a set of (usually infinite number of) ordered elements: a 1, a 2,, a n, Each individual element a k is called a
COMP 122/L Lecture 2. Kyle Dewey
 COMP 122/L Lecture 2 Kyle Dewey Outline Operations on binary values AND, OR, XOR, NOT Bit shifting (left, two forms of right) Addition Subtraction Twos complement Bitwise Operations Bitwise AND Similar
COMP 122/L Lecture 2 Kyle Dewey Outline Operations on binary values AND, OR, XOR, NOT Bit shifting (left, two forms of right) Addition Subtraction Twos complement Bitwise Operations Bitwise AND Similar
A Partial Correctness Proof for Programs with Decided Specifications
 Applied Mathematics & Information Sciences 1(2)(2007), 195-202 An International Journal c 2007 Dixie W Publishing Corporation, U. S. A. A Partial Correctness Proof for Programs with Decided Specifications
Applied Mathematics & Information Sciences 1(2)(2007), 195-202 An International Journal c 2007 Dixie W Publishing Corporation, U. S. A. A Partial Correctness Proof for Programs with Decided Specifications
Chapter 4. Number Theory. 4.1 Factors and multiples
 Chapter 4 Number Theory We ve now covered most of the basic techniques for writing proofs. So we re going to start applying them to specific topics in mathematics, starting with number theory. Number theory
Chapter 4 Number Theory We ve now covered most of the basic techniques for writing proofs. So we re going to start applying them to specific topics in mathematics, starting with number theory. Number theory
CSE 331 Summer 2016 Final Exam. Please wait to turn the page until everyone is told to begin.
 Name The exam is closed book, closed notes, and closed electronics. Please wait to turn the page until everyone is told to begin. Score / 54 1. / 12 2. / 12 3. / 10 4. / 10 5. / 10 Bonus: 1. / 6 2. / 4
Name The exam is closed book, closed notes, and closed electronics. Please wait to turn the page until everyone is told to begin. Score / 54 1. / 12 2. / 12 3. / 10 4. / 10 5. / 10 Bonus: 1. / 6 2. / 4
This is already grossly inconvenient in present formalisms. Why do we want to make this convenient? GENERAL GOALS
 1 THE FORMALIZATION OF MATHEMATICS by Harvey M. Friedman Ohio State University Department of Mathematics friedman@math.ohio-state.edu www.math.ohio-state.edu/~friedman/ May 21, 1997 Can mathematics be
1 THE FORMALIZATION OF MATHEMATICS by Harvey M. Friedman Ohio State University Department of Mathematics friedman@math.ohio-state.edu www.math.ohio-state.edu/~friedman/ May 21, 1997 Can mathematics be
