P-907 t ' -July 26, 1956
|
|
|
- Adelia Wiggins
- 5 years ago
- Views:
Transcription
1 to <D O \0 IO ^ 1 <D s ^ No THE STORAOE ALLOCATION OF THE UNBAR PROGRAMMING CODE* H. A. Judd Internatlcnal Business Machines Corpcrati en / I P-907 t ' -July 26, 1956 J COPY. V-.~CF Prepared for The RAND Corporation Short / / /y bourse In Computational Aspects of Linear -T^^/^Progranmlng, Sept. 4-13, Approved toe 0T5 release DDC (13) CIRA I'OINIA
2 CLEARINGHOUSE FOR FEDERAL SCIENTIFIC AND TECHNICAL INFORMATION CFSTI DOCUMENT MANAGEMENT BRANCH LIMITATIONS IN REPRODUCTION QUALITY ACCESSION ~ A 7 ^ S olo^ 7 I. WE REGRET THAT LEGIBILITY OF THIS DOCUMENT IS IN PART UNSATISFACTORY REPRODUCTION HAS BEEN MADE FROM BEST AVAILABLE COPY. Q 2. A PORTION OF THE ORIGINAL DOCUMENT CONTAINS FINE DETAIL WHICH MAY MAKE READING OF PHOTOCOPY DIFFICULT. [3 3. THE ORIGINAL DOCUMENT CONTAINS COLOR. BUT DISTRIBUTION COPIES ARE AVAILABLE IN BLACK-AND-WHITE REPRODUCTION ONLY. Q 4. THE INITIAL DISTRIBUTION COPIES CONTAIN COLOR WHICH WILL BE SHOWN IN BLACK-AND-WHITE WHEN IT IS NECESSARY TO REPRINT. n 5. LIMITED SUPPLY ON HAND: WHEN EXHAUSTED, DOCUMENT WILL, - 1 BE AVAILABLE IN MICROFICHE ONLY. [I 6 LIMITED SUPPLY ON HAND: WHEN EXHAUSTED DOCUMENT WILL NOT BE AVAILABLE. 7 DOCUMENT IS AVAILABLE IN MICROFICHE ONLY. 8 DOCUMENT AVAILABLE ON LOAN FROM CFSTI ( TT DOCUMENTS ONLY). D» TSL-I07-I0 S4 PROCESSOR:
3 -11- SUMMARY The handling cf storage assignment and subroutine Interconnections for the 704 linear programming codes are discussed. The available storage of the machine Is divided Into two main parts -- code and data. Their layouts are fairly independent of one another and the programs Include routines for automatic "housekeeping" during leading and running of a Job. Flexibility Is provided for systematic modifications In the programs or for machines with various storage facilities.
4 -1- I have twc reasons for discussing the storage allocation that we used In the coding cf the Linear Programming problem. The foremost reason Is to Increase your understanding of the operation of the LP code, and secondly, I think It Is an excellent solution of the storage allocation problem for any big general program. The 704 code for solving the Transportation problem, which I worked on In New York,solves the Transportation problem admirably, but It lacks the tidiness that a good storage layout provides. To begin with, the LP code was denigned for a 704 with 409o words of magnetic core storage, one drum unit, five tape units, a card reader, a printer, and a punch. Only four tape units are necessary If no off-line printing Is desired. The code has already been modified to take advantage of the additional 409t) words of core storage which has been added to some of the 704^ now using the LP code. A more extensive modification Is planned for the 32,000 word core storage unit. The assembly of Input data Is, at present, completely separated both logically and physically from the LP main code. The data assembly program Is made up of many subroutines to accommodate the different options which are allowed. For example, the data may be loaded on a tape via the peripheral card-to-tape equipment Instead of the card reader. The Data Assembly code contains the necessary subroutines to accept the data either way. The layout Is somewhat similar in structure to the main code since we wanted to use the same
5 -2- data and constants regions. Since the Data Assembly code did not fit into the assigned space In high-speed storage, «re broke it in half storing the second half on a drum. After the first half is executed, the second half is read in from drums overwriting the first half. Control Is then returned to the beginning of the code and the second half is executed. This type of sleight of hand is very common where space is short and programs are long. It works best, however, when the pro- gram need be executed only once before it is destroyed, as in this case. For the main code, high-speed storage is divided up as follows during the execution of the code: COItlON MASTER CONTROL ROl/TINBS (MCR) ? UNIVERSAL SUBROUTINES (DPFADD, DPFMUL, DISTRB) SUBROUTINES UNIVERSAL CONSTANTS o H-REQION M+l V-REOION 2*f2 W-REOION 2Nf T-REOION 2048 The COMMON region is used for erasable storage by any MCR or subroutine at any time. The NCR region is used by the three different Master Control Routines which we have at the present time. Only one of these may be operating at a given time. In normal operation, the COMMON MCR is used until an optimal solution is reached, or until the operator decides to stop and invert the present basis. The INVERSION MCR must then be read into the MCR region from binary cards to perform the inversion. After the inversion is completed«the COMMON
6 -3- MCR would be read In again from binary cards and the coaputa- tlon could proceed. This manual switching of the MCR codes may be eliminated by saving the NCR's Internally, but at the time these NCR's are loaded«it may also be desirable to load part or all of the data In again since the restarts are handled In this way. In the near future some changes may be made In regard to the way restarts are handled so the MCR's will be saved Internally for more automatic changing. There are three universal subroutines, namely, Double Precision Floating Point Add, Double Precision Floating Point Multiply, and a subroutine called the Distributor. The functions of the first two are adequately explained by their titles. They are always available for use by any of the sub- routines (hence, they might be more aptly described as sub- subroutines). The Distributor Is a very short subroutine which contains a table of the number of Instructions and the drum address of the first Instruction of each subroutine In the code (with the exception of the Universal Subroutines). At present, there are Ik subroutines which may be used by the raaater codes. These subroutines do a great deal more than the ordinary macro-instruction type subroutines. The pricing operation, for example, is a single subroutine. When the MCR wants to execute this subroutine, it is only necessary to execute the two instructions CLA PRICE TSX DISTRB, C
7 The first Instruction places the code number corresponding to the desired subroutine In the accumulator register sc the Distributor can select the proper drum address from the table. The second Instruction places the 2'a complement of Its own location In Index register C and transfers control to the Distributor. First, the Distributor saves the contents of Index register C In a standard location. Then the drum address of the first Instruction and total number of Instructions In the subroutine are taken from the table. The Distributor reads the subroutine from the drum Into the standard subroutine region and transfers control to the first Instruction of that region (486). The subroutine Is then executed. Upon completion of the subroutine, Index register C Is reloaded from the standard location with the S's complement of the location of the TSX Instruction In the MCR. A TRA 1,C Is executed which returns control to the Instruction following the TSX Instruction In the MCR. In the 704, the effective address of a tagged TRA Instruction Is computed by subtracting the contents of the Indicated Index register from the stated address In the Instruction. The Index registers do not have an associated sign, hence, the subtraction Is done by taking the S's complement of the number In the Index register- and adding It to the stated address. The 2^ complement of the 2, B complement Is the number Itself. In the example above, we added one to the original location ana thus returned control to the Instruction following the TSX
8 -5- Instructlon In the MCR. If you are not confused by now, the rest will be easy. Since It Is possible to move 10,000 Instructions per second between drum and high-speed storage, very little time Is used by keeping all of the subroutines on drum and calling them In fresh each time they are to be executed. Thus, all of the "heavy" work was relegated to subroutines while decision making and control remained to the MCR's. Thus, to call a subroutine off the drum and execute It requires only two Instructions In the MCR, the Distributor routine, and a very short amount of time. Each of the subroutines must necessarily make certain assumptlcns concerning the disposition of the data which It uses. It Is the prime function of the MCB's to control the various activities and flow of data using the subroutines like the powerful tools they are. In the space allotted, you will note that a subroutine cannot exceed 21b words In length. Later on, I will show how we can fudge this number up a bit, but first I want to point cut the storage for constants and data. The Universal Constants contain the numbers 0, 1, 2, and other commonly uaed Integers. They also include all of the standard locations for parameters to Indicate which phase, which stage, which caption the print program will use, etc. Some of these constants are fixed by the Data Assembly program to define the storage layout for the particular problem being run such as M+l, 2M+2, VORION, WORIQN, etc.
9 -6- The H-REGION always contains M+l words and Is used to keep the names of the current activities which constitute the basis. The V and W regions are 2M^2 words In length and each may contain a double-precision vector. The solution vector. Beta«Is normally kept In V-reglon from where It Is used. The W-reglon la used for working storage In generating a /«x and l(t) IT) IT* ' while working with the transformation vectors In T-reglon. It Is used for several purposes> all of which require an expanded double precision vector. The transforma- tion vectors. Eta., are kept In ccndensed form In T-reglon when they are being used. At other times, they are stored on drum 3» or transferred to tape (end-of-stage procedure) if they exceed the capacity of T-reglon. The only difference between the code for the ^096 and the 8192 word core storage machines Is that T-reglon Is expanded to half of 2048 plus 4096, that Is from 2048 to Drum 3 Is not used at present In the 8192 word machine. In place of using the drum for temporary storage for the Eta vectors, the high-speed storage following T-reglon is used. This change has caused a considerable Increase In speed over the 4096 word machine. The T-reglon is also used for temporarily holding the matrix, or as much of it as possible, when it Is used. The tapes are used for permanent storage of the matrix (tape number 5)* for permanent storage of the transformation vectors (tapes numbered 2, 3, and 4), and tape 6 is used as output by the print program if peripheral printing is desired.
10 -7- Three tapes are needed for the transformation vectors for reliability and because they are used In both a forward and a backward direction. Tape 2 contains the vectors In the order In which they were generated providing, of course, that they exceed the capacity of T-reglon. Tapes 3 and 4 are used alternately to contain the transformation vectors In backward direction with respect to records only. That Is, at the first end-of-stage, the record Is written on tapes 2 and 3» At the second end-of-stage, the new record Is added to tape 2 and written on tape 4. Then the contents of tape 3 are written on tape 4 following the new record. Tapes 3 and h are alternated In this way as long as necessary. The drum layout Is straightforward and flexible enough so that It can be changed around If desired. There are four logical drums In a drum unit of the 704 with 20^8 words each. The first logical drum Is selected by the drum load button sequence which we use extensively for restart procedures. Thus, the program labeled DRBOOT, for drum bootstrap, has to be placed at the beginning of drum 1. The last 2H+2 words of drum 1 have been arbitrarily chosen to keep b, the original right-hand side. All of the other data Including the current MCR and constants are saved on drum 1 for the automatic restart. Drum 2 and the rest of drum 1 are used for sub-mcr's and all cf the subroutines. Drum 3 Is used for storing transformation vectors when T-reglon is being used for other purposes except when using an 8192 word
11 .ft machine. Drum 4 is used for other vectors generated during the runs which must be temporarily saved during the parametric programming. Now I would like to show the way In which we are able to cheat on the rigid storage layout of both the MCR region and the subroutine region. The Inversion MCR exceeds the 376 word limitation on the size of the NCR's. Here again, we use the sleight of hand technique of loading a part of the Inversion MCR as a subroutine with a code of zero. The main part of the Inversion MCR calls In this sub-mcr via the distributor. This sub-mcr knows a priori where the MCR gets stored on drum 2 so that It calls It In to the MCR region overwriting itself after It has finished Its function. The program which loads the subroutines, the sub-mcr's, and the current MCR Is known as the executive loader (EXECLD). This is a standard binary loading program which has been modified for our special needs. The standard binary loader reads cards and stores the words In storage getting the number of words on each card and the loading address of the first instruction from the left word in the ^'s row on the card. A hash check sum of the card Is in the right word in the 9'a row. Before it stores the instructions away, it tests the word count to see if it Is zero. When it finds a card with a count of zero, it uses this Indication to stop loading and transfers control to the location indicated in the address part of the left word in the 9'» row.
12 -9- The executive loader- uses the same Indlcatlcn, a ccunt of zero, and applies a detailed examination of the right word In the ^'s row. Per clarification, a card with a word count of zero Is called a TITLE card Instead of a transfer card in our write-ups. The number In the 9's right row of the title card indicates whether a subroutine, sub-mcr or MCR has Just been loaded. While the executive leader Is loading these sub-mcr's and subroutines. It stores them away first on drum 2 and then on drum 1 when drum 2 Is full. It keeps track of the first and last loading address of each code being loaded between successive title cards. Thus It computes the exact number of Instructions In the routine which It adds to a counter to keep track of the space left en the drum which It Is loading. Prior to loading each routine It places a return Jump (TRA 1, C) In the first location of the MCR region. This Is automatically destroyed by loading MCR's and also by some subroutines since we use another device for increasing the total length of subroutines. This Is to put a preface to some subroutines In the MCR region and execute this set of code before the executive loader tucks the subroutine away on a drum. The preface Is used to preset those addresses In each subroutine which depend en the particular problem the code Is working on. You may recall that M is variable for each problem and determines the limits of H, V, and W regions. Thus the executive loader always transfers control to the first
13 Inatructlon of the MCR where the preface Is executed. If there la one, and control returns to the executive loader after the subroutine Is Initialized. Then the executive loader Ignores the preface in the MCR region and tucks the condensed subroutine away on the drum, places the number of Instructions and first drum location \n the table of the Dis- tributor routine and proceeds to load the next subroutine or MCR. Thus, the order of loading Is determined to be: BASE routines (DRBOOT, Universal sub-routines, EXECLD, the CONSTANTS) SUBROUTINES SUB-MCR's DATA The Inherent beauty In this loading scheme Is that the program- mer does not have to know hew many Instructions are in each subroutine, sub-mcr, or MCR so long as the region boundaries are not violated. Again, we have allowed the 704 to do the housework of keeping track of the number of Instructions In each subroutine, store them away on drums efficiently, and bring them back again when they are called for by the MCR. The print subroutine exceeds the subroutine storage so badly that we have a pseudc-subroutine In Its place and the real print program Is loaded like a sub-mcr. The pseudo- subroutine gets called In and It In turn calls the real print program Into T region since that Is the only unoccupied space available which la large enough to accommodate the print program.
14 P-Q In ccncluslcn, let me pclnt out that data storage la a function of the number of equations In the system the code is working on. The storage of the LP code Is Independent of the problem and parts can be reassembled and Included as they are needed. If we had a 70^ with 32,000 words of core storage and no drum, we would use a block of core storage for the main subroutine storage. Any change like this affects only two routines, the executive loader and the distributor. If we get drums and 32,000 words of core storage, we would still keep the subroutines on drum and use all additional high-speed storage for transformation vectors.
GENERAL INFORMATION 7090 DATA PROCESSING SYSTEM
 7090 DATA PROCESSING SYSTEM GENERAL INFORMATION THE IBM 7090 Data Processing System, newest addition to IBM's family of data processing systems, includes the latest electronic component developments resulting
7090 DATA PROCESSING SYSTEM GENERAL INFORMATION THE IBM 7090 Data Processing System, newest addition to IBM's family of data processing systems, includes the latest electronic component developments resulting
Software. Lockheed Electronics
 Lockheed Electronics Software 0 Standard software for the Lockheed Electronics MAC Computers is designed to meet the varied requirements of different user systems. Lockheed has developed a set of system
Lockheed Electronics Software 0 Standard software for the Lockheed Electronics MAC Computers is designed to meet the varied requirements of different user systems. Lockheed has developed a set of system
COMPUTER ARITHMETIC (Part 1)
 Eastern Mediterranean University School of Computing and Technology ITEC255 Computer Organization & Architecture COMPUTER ARITHMETIC (Part 1) Introduction The two principal concerns for computer arithmetic
Eastern Mediterranean University School of Computing and Technology ITEC255 Computer Organization & Architecture COMPUTER ARITHMETIC (Part 1) Introduction The two principal concerns for computer arithmetic
CSCI 1800 Cybersecurity and International Relations. Computer Hardware & Software John E. Savage Brown University
 CSCI 1800 Cybersecurity and International Relations Computer Hardware & Software John E. Savage Brown University Overview Introduction computer design Central Processing Unit (CPU) Random Access Memory
CSCI 1800 Cybersecurity and International Relations Computer Hardware & Software John E. Savage Brown University Overview Introduction computer design Central Processing Unit (CPU) Random Access Memory
Chapter 3: Arithmetic for Computers
 Chapter 3: Arithmetic for Computers Objectives Signed and Unsigned Numbers Addition and Subtraction Multiplication and Division Floating Point Computer Architecture CS 35101-002 2 The Binary Numbering
Chapter 3: Arithmetic for Computers Objectives Signed and Unsigned Numbers Addition and Subtraction Multiplication and Division Floating Point Computer Architecture CS 35101-002 2 The Binary Numbering
indexing and subroutines; a full complement of logical, relational and control operators should be provided to enable efficient
 Chapter 9 Design of the B 5000 System^ William Lonergan /Paul King Computing systems have conventionally been designed via the "hardware" route. Subsequent to design, these systems have been handed over
Chapter 9 Design of the B 5000 System^ William Lonergan /Paul King Computing systems have conventionally been designed via the "hardware" route. Subsequent to design, these systems have been handed over
EAI 640 Digital Computing System.
 EAI 640 Digital Computing System. . - EAI@ 640 Digital Computing System -
EAI 640 Digital Computing System. . - EAI@ 640 Digital Computing System -
Issue 3 January Ferranti Mercury Computer X3. Instruction Sets and Instruction Times. Index
 Ferranti Mercury Computer X3. Instruction Sets and Instruction Times. Index D2 Power comparisons D5 Instruction sets Description of instructions References D2 Power comparisons 5,6. As Mercury was designed
Ferranti Mercury Computer X3. Instruction Sets and Instruction Times. Index D2 Power comparisons D5 Instruction sets Description of instructions References D2 Power comparisons 5,6. As Mercury was designed
Ferranti Atlas 1 & 2 Software & Sample Programs Version 1: 11 November 2003
 1. Available Software Ferranti Atlas 1 & 2 Software & Sample Programs Version 1: 11 November 2003 Contents 1. Available Software 2. Sample ABL 3. Job Descriptions 4. A Simple Program 5. References Atlas
1. Available Software Ferranti Atlas 1 & 2 Software & Sample Programs Version 1: 11 November 2003 Contents 1. Available Software 2. Sample ABL 3. Job Descriptions 4. A Simple Program 5. References Atlas
 Optional Equipment Optional Equipment The computing system... The Input Section feeds data and computer instructions into the system. This section receives data from a wide variety of sources, among which
Optional Equipment Optional Equipment The computing system... The Input Section feeds data and computer instructions into the system. This section receives data from a wide variety of sources, among which
COMPUTER ARCHITECTURE AND ORGANIZATION. Operation Add Magnitudes Subtract Magnitudes (+A) + ( B) + (A B) (B A) + (A B)
 Computer Arithmetic Data is manipulated by using the arithmetic instructions in digital computers. Data is manipulated to produce results necessary to give solution for the computation problems. The Addition,
Computer Arithmetic Data is manipulated by using the arithmetic instructions in digital computers. Data is manipulated to produce results necessary to give solution for the computation problems. The Addition,
The emulator represents a single 1103A machine word as the 36 least significant bits of a 64 bit unsigned integer.
 NAME atlas an 1103A emulator for UNIX systems SYNOPSIS atlas DESCRIPTION Atlas is an emulator for the Univac Scientific 1103A. In addition to implementing all 41 basic instructions of the CPU, including
NAME atlas an 1103A emulator for UNIX systems SYNOPSIS atlas DESCRIPTION Atlas is an emulator for the Univac Scientific 1103A. In addition to implementing all 41 basic instructions of the CPU, including
In this chapter you ll learn:
 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd Will you walk a little faster? said a whiting to a snail, There s a porpoise close behind us, and he s treading on
Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd Will you walk a little faster? said a whiting to a snail, There s a porpoise close behind us, and he s treading on
(Refer Slide Time: 1:40)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering, Indian Institute of Technology, Delhi Lecture - 3 Instruction Set Architecture - 1 Today I will start discussion
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering, Indian Institute of Technology, Delhi Lecture - 3 Instruction Set Architecture - 1 Today I will start discussion
THE LOGICAL STRUCTURE OF THE RC 4000 COMPUTER
 THE LOGICAL STRUCTURE OF THE RC 4000 COMPUTER PER BRINCH HANSEN (1967) This paper describes the logical structure of the RC 4000, a 24-bit, binary computer designed for multiprogramming operation. The
THE LOGICAL STRUCTURE OF THE RC 4000 COMPUTER PER BRINCH HANSEN (1967) This paper describes the logical structure of the RC 4000, a 24-bit, binary computer designed for multiprogramming operation. The
Module 5 - CPU Design
 Module 5 - CPU Design Lecture 1 - Introduction to CPU The operation or task that must perform by CPU is: Fetch Instruction: The CPU reads an instruction from memory. Interpret Instruction: The instruction
Module 5 - CPU Design Lecture 1 - Introduction to CPU The operation or task that must perform by CPU is: Fetch Instruction: The CPU reads an instruction from memory. Interpret Instruction: The instruction
DEC-08-LBAA-D IDENTIFICATION DEC-OO- LBAA-D. Product Code: Date Created: May 10, 1967 PDP-B LIBRARY
 IDENTIFICATION Product Code: Product Name: DEC-OO- LBAA-D Binary Loader Date Created: May 10, 1967 Maintainer: Software Services Group PDP-B LIBRARY 1. ABSTRACT The Binary Loader is a short routine for
IDENTIFICATION Product Code: Product Name: DEC-OO- LBAA-D Binary Loader Date Created: May 10, 1967 Maintainer: Software Services Group PDP-B LIBRARY 1. ABSTRACT The Binary Loader is a short routine for
The Atlas scheduling system
 The By D. J. Howarth, P. D. Jones and M. T. Wyld Introduction Atlas is the name given to a comprehensive computer system which has its origin in the Computing Machine Laboratory under Professor T. Kilburn
The By D. J. Howarth, P. D. Jones and M. T. Wyld Introduction Atlas is the name given to a comprehensive computer system which has its origin in the Computing Machine Laboratory under Professor T. Kilburn
A microcomputer system for mass spectrometer control and data acquisition
 Proc. Indian Acad. Sci. (Chem. Sci.), Vol. 93, No. 2, March 1984, plx 189-193. 9 Printed in India. A microcomputer system for mass spectrometer control and data acquisition P G OZA, H S MAZUMDAR, A K CHOUDHARY
Proc. Indian Acad. Sci. (Chem. Sci.), Vol. 93, No. 2, March 1984, plx 189-193. 9 Printed in India. A microcomputer system for mass spectrometer control and data acquisition P G OZA, H S MAZUMDAR, A K CHOUDHARY
Darshan Institute of Engineering & Technology for Diploma Studies Unit - 1
 Darshan Institute of Engineering & Technology for Diploma Studies Unit - 1 1. Draw and explain 4 bit binary arithmetic or adder circuit diagram. A binary parallel adder is digital function that produces
Darshan Institute of Engineering & Technology for Diploma Studies Unit - 1 1. Draw and explain 4 bit binary arithmetic or adder circuit diagram. A binary parallel adder is digital function that produces
19 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd
 19 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd Will you walk a little faster? said a whiting to a snail, There s a porpoise close behind us, and he s treading
19 Much that I bound, I could not free; Much that I freed returned to me. Lee Wilson Dodd Will you walk a little faster? said a whiting to a snail, There s a porpoise close behind us, and he s treading
COLUMN GENERATION IN LINEAR PROGRAMMING
 COLUMN GENERATION IN LINEAR PROGRAMMING EXAMPLE: THE CUTTING STOCK PROBLEM A certain material (e.g. lumber) is stocked in lengths of 9, 4, and 6 feet, with respective costs of $5, $9, and $. An order for
COLUMN GENERATION IN LINEAR PROGRAMMING EXAMPLE: THE CUTTING STOCK PROBLEM A certain material (e.g. lumber) is stocked in lengths of 9, 4, and 6 feet, with respective costs of $5, $9, and $. An order for
Describe the layers of a computer system
 Chapter 1 The Big Picture Chapter Goals Describe the layers of a computer system Describe the concept of abstraction and its relationship to computing Describe the history of computer hardware and software
Chapter 1 The Big Picture Chapter Goals Describe the layers of a computer system Describe the concept of abstraction and its relationship to computing Describe the history of computer hardware and software
ORG ; TWO. Assembly Language Programming
 Dec 2 Hex 2 Bin 00000010 ORG ; TWO Assembly Language Programming OBJECTIVES this chapter enables the student to: Explain the difference between Assembly language instructions and pseudo-instructions. Identify
Dec 2 Hex 2 Bin 00000010 ORG ; TWO Assembly Language Programming OBJECTIVES this chapter enables the student to: Explain the difference between Assembly language instructions and pseudo-instructions. Identify
Chapter 13. The ISA of a simplified DLX Why use abstractions?
 Chapter 13 The ISA of a simplified DLX In this chapter we describe a specification of a simple microprocessor called the simplified DLX. The specification is called an instruction set architecture (ISA).
Chapter 13 The ISA of a simplified DLX In this chapter we describe a specification of a simple microprocessor called the simplified DLX. The specification is called an instruction set architecture (ISA).
UNIT III LOADERS AND LINKERS
 UNIT III LOADERS AND LINKERS INTRODUCTION Loader is a system program that performs the loading function. Many loaders also support relocation and linking. Some systems have a linker (linkage editor) to
UNIT III LOADERS AND LINKERS INTRODUCTION Loader is a system program that performs the loading function. Many loaders also support relocation and linking. Some systems have a linker (linkage editor) to
Coach s Office Playbook Tutorial Playbook i
 Playbook i The Playbook... 1 Overview... 1 Open the Playbook... 1 The Playbook Window... 2 Name the Chapter... 2 Insert the First Page... 3 Page Templates... 3 Define the Template Boxes... 4 Text on the
Playbook i The Playbook... 1 Overview... 1 Open the Playbook... 1 The Playbook Window... 2 Name the Chapter... 2 Insert the First Page... 3 Page Templates... 3 Define the Template Boxes... 4 Text on the
ZEBRA, a simple binary computer 1
 Chapter 12 ZEBRA, a simple binary computer 1 W. L. van der Poel Summary The computer ZEBRA a computer based on the following ideas: and 1. The logical structure of the arithmetic control units of the machine
Chapter 12 ZEBRA, a simple binary computer 1 W. L. van der Poel Summary The computer ZEBRA a computer based on the following ideas: and 1. The logical structure of the arithmetic control units of the machine
CSCE 5610: Computer Architecture
 HW #1 1.3, 1.5, 1.9, 1.12 Due: Sept 12, 2018 Review: Execution time of a program Arithmetic Average, Weighted Arithmetic Average Geometric Mean Benchmarks, kernels and synthetic benchmarks Computing CPI
HW #1 1.3, 1.5, 1.9, 1.12 Due: Sept 12, 2018 Review: Execution time of a program Arithmetic Average, Weighted Arithmetic Average Geometric Mean Benchmarks, kernels and synthetic benchmarks Computing CPI
Computer Organisation CS303
 Computer Organisation CS303 Module Period Assignments 1 Day 1 to Day 6 1. Write a program to evaluate the arithmetic statement: X=(A-B + C * (D * E-F))/G + H*K a. Using a general register computer with
Computer Organisation CS303 Module Period Assignments 1 Day 1 to Day 6 1. Write a program to evaluate the arithmetic statement: X=(A-B + C * (D * E-F))/G + H*K a. Using a general register computer with
16 Sharing Main Memory Segmentation and Paging
 Operating Systems 64 16 Sharing Main Memory Segmentation and Paging Readings for this topic: Anderson/Dahlin Chapter 8 9; Siberschatz/Galvin Chapter 8 9 Simple uniprogramming with a single segment per
Operating Systems 64 16 Sharing Main Memory Segmentation and Paging Readings for this topic: Anderson/Dahlin Chapter 8 9; Siberschatz/Galvin Chapter 8 9 Simple uniprogramming with a single segment per
MICROPROCESSOR AND MICROCONTROLLER BASED SYSTEMS
 MICROPROCESSOR AND MICROCONTROLLER BASED SYSTEMS UNIT I INTRODUCTION TO 8085 8085 Microprocessor - Architecture and its operation, Concept of instruction execution and timing diagrams, fundamentals of
MICROPROCESSOR AND MICROCONTROLLER BASED SYSTEMS UNIT I INTRODUCTION TO 8085 8085 Microprocessor - Architecture and its operation, Concept of instruction execution and timing diagrams, fundamentals of
CHAPTER SEVEN PROGRAMMING THE BASIC COMPUTER
 CHAPTER SEVEN 71 Introduction PROGRAMMING THE BASIC COMPUTER A computer system as it was mentioned before in chapter 1, it is subdivided into two functional parts: 1 Hardware, which consists of all physical
CHAPTER SEVEN 71 Introduction PROGRAMMING THE BASIC COMPUTER A computer system as it was mentioned before in chapter 1, it is subdivided into two functional parts: 1 Hardware, which consists of all physical
CSC 553 Operating Systems
 CSC 553 Operating Systems Lecture 12 - File Management Files Data collections created by users The File System is one of the most important parts of the OS to a user Desirable properties of files: Long-term
CSC 553 Operating Systems Lecture 12 - File Management Files Data collections created by users The File System is one of the most important parts of the OS to a user Desirable properties of files: Long-term
GENERAL REFERENCE MANUAL. From the original English Manual - (L.C. Sept 2017)
 GENERAL REFERENCE MANUAL Preface Programma 101 is a completely self-contained desktop machine capable of operating in manual mode as a high speed electronic printing calculator, in program mode as an
GENERAL REFERENCE MANUAL Preface Programma 101 is a completely self-contained desktop machine capable of operating in manual mode as a high speed electronic printing calculator, in program mode as an
CHAPTER-1: INTRODUCTION TO OPERATING SYSTEM:
 CHAPTER-1: INTRODUCTION TO OPERATING SYSTEM: TOPICS TO BE COVERED 1.1 Need of Operating System 1.2 Evolution of os 1.3 operating system i. Batch ii. iii. iv. Multiprogramming Time sharing Real time v.
CHAPTER-1: INTRODUCTION TO OPERATING SYSTEM: TOPICS TO BE COVERED 1.1 Need of Operating System 1.2 Evolution of os 1.3 operating system i. Batch ii. iii. iv. Multiprogramming Time sharing Real time v.
INITIALIZE CLEAR beneath COUNT
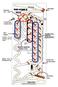 INITIALIZE Strictly speaking, the Digi-Comp II does not have an "INITIALIZE" function- it is a task that the human operator must perform, before most computations, to prepare the wooden "circuitry" for
INITIALIZE Strictly speaking, the Digi-Comp II does not have an "INITIALIZE" function- it is a task that the human operator must perform, before most computations, to prepare the wooden "circuitry" for
Specification ttfattr Mark HA ENGLISH ELECTRIC'
 Specification ttfattr Mark HA ENGLISH ELECTRIC' V $ i Contents 1.0 INTRODUCTION... 3 «2.0 GENERAL INFORMATION... 3 3.0 PHYSICAL FORM OF THE COMPUTER... 4 3.1 Electronic Units, Magnetic Store... 4 3.2 Control
Specification ttfattr Mark HA ENGLISH ELECTRIC' V $ i Contents 1.0 INTRODUCTION... 3 «2.0 GENERAL INFORMATION... 3 3.0 PHYSICAL FORM OF THE COMPUTER... 4 3.1 Electronic Units, Magnetic Store... 4 3.2 Control
Chapter 3. Errors and numerical stability
 Chapter 3 Errors and numerical stability 1 Representation of numbers Binary system : micro-transistor in state off 0 on 1 Smallest amount of stored data bit Object in memory chain of 1 and 0 10011000110101001111010010100010
Chapter 3 Errors and numerical stability 1 Representation of numbers Binary system : micro-transistor in state off 0 on 1 Smallest amount of stored data bit Object in memory chain of 1 and 0 10011000110101001111010010100010
MIPS (SPIM) Assembler Syntax
 MIPS (SPIM) Assembler Syntax Comments begin with # Everything from # to the end of the line is ignored Identifiers are a sequence of alphanumeric characters, underbars (_), and dots () that do not begin
MIPS (SPIM) Assembler Syntax Comments begin with # Everything from # to the end of the line is ignored Identifiers are a sequence of alphanumeric characters, underbars (_), and dots () that do not begin
ETSI TS V6.2.0 ( )
 TS 100 508 V6.2.0 (2000-07) Technical Specification Digital cellular telecommunications system (Phase 2+); International Mobile station Equipment Identities (IMEI) (GSM 02.16 version 6.2.0 Release 1997)
TS 100 508 V6.2.0 (2000-07) Technical Specification Digital cellular telecommunications system (Phase 2+); International Mobile station Equipment Identities (IMEI) (GSM 02.16 version 6.2.0 Release 1997)
Chapter 3 Loaders and Linkers
 Chapter 3 Loaders and Linkers Three fundamental processes: Loading brings the object program into memory for execution. Relocation modifies the object program so that it can be loaded at an address different
Chapter 3 Loaders and Linkers Three fundamental processes: Loading brings the object program into memory for execution. Relocation modifies the object program so that it can be loaded at an address different
8.7 TM: A SIMPLE TARGET MACHINE
 8.7 TM: A SIMPLE TARGET MACHINE In the section following this one we will present a code generator for the TINY language. In order to make this a meaningful task, we generate target code directly for a
8.7 TM: A SIMPLE TARGET MACHINE In the section following this one we will present a code generator for the TINY language. In order to make this a meaningful task, we generate target code directly for a
Chapter 10 - Computer Arithmetic
 Chapter 10 - Computer Arithmetic Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 10 - Computer Arithmetic 1 / 126 1 Motivation 2 Arithmetic and Logic Unit 3 Integer representation
Chapter 10 - Computer Arithmetic Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 10 - Computer Arithmetic 1 / 126 1 Motivation 2 Arithmetic and Logic Unit 3 Integer representation
CHETTINAD COLLEGE OF ENGINEERING AND TECHNOLOGY COMPUTER ARCHITECURE- III YEAR EEE-6 TH SEMESTER 16 MARKS QUESTION BANK UNIT-1
 CHETTINAD COLLEGE OF ENGINEERING AND TECHNOLOGY COMPUTER ARCHITECURE- III YEAR EEE-6 TH SEMESTER 16 MARKS QUESTION BANK UNIT-1 Data representation: (CHAPTER-3) 1. Discuss in brief about Data types, (8marks)
CHETTINAD COLLEGE OF ENGINEERING AND TECHNOLOGY COMPUTER ARCHITECURE- III YEAR EEE-6 TH SEMESTER 16 MARKS QUESTION BANK UNIT-1 Data representation: (CHAPTER-3) 1. Discuss in brief about Data types, (8marks)
Programming at different levels
 CS2214 COMPUTER ARCHITECTURE & ORGANIZATION SPRING 2014 EMY MNEMONIC MACHINE LANGUAGE PROGRAMMING EXAMPLES Programming at different levels CS1114 Mathematical Problem : a = b + c CS2214 CS2214 The C-like
CS2214 COMPUTER ARCHITECTURE & ORGANIZATION SPRING 2014 EMY MNEMONIC MACHINE LANGUAGE PROGRAMMING EXAMPLES Programming at different levels CS1114 Mathematical Problem : a = b + c CS2214 CS2214 The C-like
Grace E, Mitchell. International Business Machines Corporation Research Center Yorktown Heights, New York
 THE 704 FORTRAN 1 AUTOMATC CODNG SYSTEM Grace E, Mitchell. nternational Business Machines Corporation Research Center Yorktown Heights, New York ABSTRACT: This paper discusses the addition made in the
THE 704 FORTRAN 1 AUTOMATC CODNG SYSTEM Grace E, Mitchell. nternational Business Machines Corporation Research Center Yorktown Heights, New York ABSTRACT: This paper discusses the addition made in the
In examining performance Interested in several things Exact times if computable Bounded times if exact not computable Can be measured
 System Performance Analysis Introduction Performance Means many things to many people Important in any design Critical in real time systems 1 ns can mean the difference between system Doing job expected
System Performance Analysis Introduction Performance Means many things to many people Important in any design Critical in real time systems 1 ns can mean the difference between system Doing job expected
Specification Illicit Mark I ENGLISH ELECTRIC'
 Specification Illicit Mark I ENGLISH ELECTRIC' Contents Page 1.0 INTRODUCTION. 3 2.0 GENERAL INFORMATION.. 3 3.0 PHYSICAL FORM OF THE COMFUTER. 4 3. 1 Electronic Units, Magnetic Store & Control Desk.
Specification Illicit Mark I ENGLISH ELECTRIC' Contents Page 1.0 INTRODUCTION. 3 2.0 GENERAL INFORMATION.. 3 3.0 PHYSICAL FORM OF THE COMFUTER. 4 3. 1 Electronic Units, Magnetic Store & Control Desk.
User. Application program. Interfaces. Operating system. Hardware
 Operating Systems Introduction to Operating Systems and Computer Hardware Introduction and Overview The operating system is a set of system software routines that interface between an application program
Operating Systems Introduction to Operating Systems and Computer Hardware Introduction and Overview The operating system is a set of system software routines that interface between an application program
CS 61C: Great Ideas in Computer Architecture MIPS Instruction Formats
 CS 61C: Great Ideas in Computer Architecture MIPS Instruction Formats Instructors: Vladimir Stojanovic and Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/sp16 1 Machine Interpretation Levels of Representation/Interpretation
CS 61C: Great Ideas in Computer Architecture MIPS Instruction Formats Instructors: Vladimir Stojanovic and Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/sp16 1 Machine Interpretation Levels of Representation/Interpretation
Special Section: Building Your Own Compiler
 cshtp6_19_datastructures_compiler.fm Page 1 Tuesday, February 14, 2017 10:31 AM 1 Chapter 19 Special Section: Building Your Own Compiler In Exercises8.31 8.33, we introduced Simpletron Machine Language
cshtp6_19_datastructures_compiler.fm Page 1 Tuesday, February 14, 2017 10:31 AM 1 Chapter 19 Special Section: Building Your Own Compiler In Exercises8.31 8.33, we introduced Simpletron Machine Language
Chapter 5: Computer Arithmetic. In this chapter you will learn about:
 Slide 1/29 Learning Objectives In this chapter you will learn about: Reasons for using binary instead of decimal numbers Basic arithmetic operations using binary numbers Addition (+) Subtraction (-) Multiplication
Slide 1/29 Learning Objectives In this chapter you will learn about: Reasons for using binary instead of decimal numbers Basic arithmetic operations using binary numbers Addition (+) Subtraction (-) Multiplication
1.3 Data processing; data storage; data movement; and control.
 CHAPTER 1 OVERVIEW ANSWERS TO QUESTIONS 1.1 Computer architecture refers to those attributes of a system visible to a programmer or, put another way, those attributes that have a direct impact on the logical
CHAPTER 1 OVERVIEW ANSWERS TO QUESTIONS 1.1 Computer architecture refers to those attributes of a system visible to a programmer or, put another way, those attributes that have a direct impact on the logical
Loaders. Systems Programming. Outline. Basic Loader Functions
 Loaders Systems Programming Chapter 3 Linkers and Loaders A loader is a system program that performs the loading function. many also support relocation & linking others have a separate linker and loader
Loaders Systems Programming Chapter 3 Linkers and Loaders A loader is a system program that performs the loading function. many also support relocation & linking others have a separate linker and loader
Chapter 03: Computer Arithmetic. Lesson 09: Arithmetic using floating point numbers
 Chapter 03: Computer Arithmetic Lesson 09: Arithmetic using floating point numbers Objective To understand arithmetic operations in case of floating point numbers 2 Multiplication of Floating Point Numbers
Chapter 03: Computer Arithmetic Lesson 09: Arithmetic using floating point numbers Objective To understand arithmetic operations in case of floating point numbers 2 Multiplication of Floating Point Numbers
UNIT-II. Part-2: CENTRAL PROCESSING UNIT
 Page1 UNIT-II Part-2: CENTRAL PROCESSING UNIT Stack Organization Instruction Formats Addressing Modes Data Transfer And Manipulation Program Control Reduced Instruction Set Computer (RISC) Introduction:
Page1 UNIT-II Part-2: CENTRAL PROCESSING UNIT Stack Organization Instruction Formats Addressing Modes Data Transfer And Manipulation Program Control Reduced Instruction Set Computer (RISC) Introduction:
Lecture 2 Microcomputer Organization: Fig.1.1 Basic Components of Microcomputer
 Lecture 2 Microcomputer Organization: As discussed in previous lecture microprocessor is a central processing unit (CPU) with its related timing functions on a single chip. A microprocessor combined with
Lecture 2 Microcomputer Organization: As discussed in previous lecture microprocessor is a central processing unit (CPU) with its related timing functions on a single chip. A microprocessor combined with
Learning Objectives. Binary over Decimal. In this chapter you will learn about:
 Ref Page Slide 1/29 Learning Objectives In this chapter you will learn about: Reasons for using binary instead of decimal numbers Basic arithmetic operations using binary numbers Addition (+) Subtraction
Ref Page Slide 1/29 Learning Objectives In this chapter you will learn about: Reasons for using binary instead of decimal numbers Basic arithmetic operations using binary numbers Addition (+) Subtraction
EE 361 University of Hawaii Fall
 C functions Road Map Computation flow Implementation using MIPS instructions Useful new instructions Addressing modes Stack data structure 1 EE 361 University of Hawaii Implementation of C functions and
C functions Road Map Computation flow Implementation using MIPS instructions Useful new instructions Addressing modes Stack data structure 1 EE 361 University of Hawaii Implementation of C functions and
CS401 - Computer Architecture and Assembly Language Programming Glossary By
 CS401 - Computer Architecture and Assembly Language Programming Glossary By absolute address : A virtual (not physical) address within the process address space that is computed as an absolute number.
CS401 - Computer Architecture and Assembly Language Programming Glossary By absolute address : A virtual (not physical) address within the process address space that is computed as an absolute number.
Memory Management. Memory Management
 Memory Management Most demanding di aspect of an operating system Cost has dropped. Consequently size of main memory has expanded enormously. Can we say that we have enough still. Swapping in/out. Memory
Memory Management Most demanding di aspect of an operating system Cost has dropped. Consequently size of main memory has expanded enormously. Can we say that we have enough still. Swapping in/out. Memory
CSE 3101 Design and Analysis of Algorithms Practice Test for Unit 1 Loop Invariants and Iterative Algorithms
 CSE 0 Design and Analysis of Algorithms Practice Test for Unit Loop Invariants and Iterative Algorithms Jeff Edmonds First learn the steps. Then try them on your own. If you get stuck only look at a little
CSE 0 Design and Analysis of Algorithms Practice Test for Unit Loop Invariants and Iterative Algorithms Jeff Edmonds First learn the steps. Then try them on your own. If you get stuck only look at a little
Notes: The Marie Simulator
 The Accumulator (AC) is the register where calculations are performed. To add two numbers together, a) load the first number into the accumulator with a Load instruction b) Add the second number to the
The Accumulator (AC) is the register where calculations are performed. To add two numbers together, a) load the first number into the accumulator with a Load instruction b) Add the second number to the
Computer Science 61C Spring Friedland and Weaver. Instruction Encoding
 Instruction Encoding 1 Instruction Formats I-format: used for instructions with immediates, lw and sw (since offset counts as an immediate), and branches (beq and bne) since branches are "relative" to
Instruction Encoding 1 Instruction Formats I-format: used for instructions with immediates, lw and sw (since offset counts as an immediate), and branches (beq and bne) since branches are "relative" to
AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30]
![AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30]](/thumbs/80/81792243.jpg) AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] Note: Question Number 1 is compulsory. Marks : 10X1
AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] Note: Question Number 1 is compulsory. Marks : 10X1
TEMPORARY CUSTODY WHAT IS TEMPORARY CUSTODY?
 4 TEMPORARY CUSTODY WHAT IS TEMPORARY CUSTODY? An accession is defined as one or more objects acquired at one time from one source constituting a single transaction between a museum and a source (Burcaw
4 TEMPORARY CUSTODY WHAT IS TEMPORARY CUSTODY? An accession is defined as one or more objects acquired at one time from one source constituting a single transaction between a museum and a source (Burcaw
Systems Reference Library
 File Number GENL-34 Form C24-3185-2 Systems Reference Library Disk Pile Organization Routines Specifications BM 1401, 1440, 1460 (1311 and 1301) This publication contains the specifications of two separate
File Number GENL-34 Form C24-3185-2 Systems Reference Library Disk Pile Organization Routines Specifications BM 1401, 1440, 1460 (1311 and 1301) This publication contains the specifications of two separate
Chapter 9 Memory Management Main Memory Operating system concepts. Sixth Edition. Silberschatz, Galvin, and Gagne 8.1
 Chapter 9 Memory Management Main Memory Operating system concepts. Sixth Edition. Silberschatz, Galvin, and Gagne 8.1 Chapter 9: Memory Management Background Swapping Contiguous Memory Allocation Segmentation
Chapter 9 Memory Management Main Memory Operating system concepts. Sixth Edition. Silberschatz, Galvin, and Gagne 8.1 Chapter 9: Memory Management Background Swapping Contiguous Memory Allocation Segmentation
OLIVETTI PROGRAMMA 101 QUICK GUIDE adapted by L.C. Sep from Computer Structures: Readings and Examples C.G. Bell, McGraw Hill 1971
 OLIVETTI PROGRAMMA 101 QUICK GUIDE adapted by L.C. Sep. 2017 from Computer Structures: Readings and Examples C.G. Bell, McGraw Hill 1971 - 2 - The OLIVETTI Programma 101 desk calculator 1 The Programma
OLIVETTI PROGRAMMA 101 QUICK GUIDE adapted by L.C. Sep. 2017 from Computer Structures: Readings and Examples C.G. Bell, McGraw Hill 1971 - 2 - The OLIVETTI Programma 101 desk calculator 1 The Programma
15 Sharing Main Memory Segmentation and Paging
 Operating Systems 58 15 Sharing Main Memory Segmentation and Paging Readings for this topic: Anderson/Dahlin Chapter 8 9; Siberschatz/Galvin Chapter 8 9 Simple uniprogramming with a single segment per
Operating Systems 58 15 Sharing Main Memory Segmentation and Paging Readings for this topic: Anderson/Dahlin Chapter 8 9; Siberschatz/Galvin Chapter 8 9 Simple uniprogramming with a single segment per
Module 1: Introduction
 Module 1: Introduction What is an operating system? Simple Batch Systems Multiprogramming Batched Systems Time-Sharing Systems Personal-Computer Systems Parallel Systems Distributed Systems Real-Time Systems
Module 1: Introduction What is an operating system? Simple Batch Systems Multiprogramming Batched Systems Time-Sharing Systems Personal-Computer Systems Parallel Systems Distributed Systems Real-Time Systems
H. W. Kuhn. Bryn Mawr College
 VARIANTS OF THE HUNGARIAN METHOD FOR ASSIGNMENT PROBLEMS' H. W. Kuhn Bryn Mawr College The author presents a geometrical modelwhich illuminates variants of the Hungarian method for the solution of the
VARIANTS OF THE HUNGARIAN METHOD FOR ASSIGNMENT PROBLEMS' H. W. Kuhn Bryn Mawr College The author presents a geometrical modelwhich illuminates variants of the Hungarian method for the solution of the
ESSSg^Pi»ter. The most important features of MULBY 3 at a glance
 ESSSg^Pi»ter 0 The most important features of MULBY 3 at a glance # I The most important features of MULBY 3 This brochure shall provide a quick survey about the MULBY 3 central processor unit, standard
ESSSg^Pi»ter 0 The most important features of MULBY 3 at a glance # I The most important features of MULBY 3 This brochure shall provide a quick survey about the MULBY 3 central processor unit, standard
Prepared By : Ms. Sanchari Saha ( Asst. Professor) Department : Computer Science & Engineering
 Subject Name: System Software Subject Code: 10CS52 Prepared By : Ms. Sanchari Saha ( Asst. Professor) Department : Computer Science & Engineering Date : 20-10-2014 UNIT-4 LOADERS & LINKERS Engineered for
Subject Name: System Software Subject Code: 10CS52 Prepared By : Ms. Sanchari Saha ( Asst. Professor) Department : Computer Science & Engineering Date : 20-10-2014 UNIT-4 LOADERS & LINKERS Engineered for
Bentonville School District Print Services
 Bentonville School District Print Services Guidelines and Price List 2017-2018 Phone: 479-696-3426 Email: bpsprintservices@bentonvillek12.org bwhsprintservices@bentonvillek12.org The concept of centralized
Bentonville School District Print Services Guidelines and Price List 2017-2018 Phone: 479-696-3426 Email: bpsprintservices@bentonvillek12.org bwhsprintservices@bentonvillek12.org The concept of centralized
MODULE 5 LINKERS AND LOADERS
 MODULE 5 LINKERS AND LOADERS Execution phases The execution of a program involves 4 steps:- 1) Translation Converting source program to object modules. The assemblers and compilers fall under the category
MODULE 5 LINKERS AND LOADERS Execution phases The execution of a program involves 4 steps:- 1) Translation Converting source program to object modules. The assemblers and compilers fall under the category
OPERATING SYSTEM SUPPORT (Part 1)
 Eastern Mediterranean University School of Computing and Technology ITEC255 Computer Organization & Architecture OPERATING SYSTEM SUPPORT (Part 1) Introduction The operating system (OS) is the software
Eastern Mediterranean University School of Computing and Technology ITEC255 Computer Organization & Architecture OPERATING SYSTEM SUPPORT (Part 1) Introduction The operating system (OS) is the software
ASSIST Assembler Replacement User s Guide
 ASSIST Assembler Replacement User s Guide Program&Documentation: John R. Mashey Pro ject Supervision : Graham Campbell PSU Computer Science Department Preface This manual is the key reference source for
ASSIST Assembler Replacement User s Guide Program&Documentation: John R. Mashey Pro ject Supervision : Graham Campbell PSU Computer Science Department Preface This manual is the key reference source for
Objective: Find areas by decomposing into rectangles or completing composite figures to form rectangles.
 Lesson 13 3 4 Lesson 13 Objective: Find areas by decomposing into rectangles or completing composite Suggested Lesson Structure Fluency Practice Application Problem Concept Development Student Debrief
Lesson 13 3 4 Lesson 13 Objective: Find areas by decomposing into rectangles or completing composite Suggested Lesson Structure Fluency Practice Application Problem Concept Development Student Debrief
File System Interface: Overview. Objective. File Concept UNIT-IV FILE SYSTEMS
 UNIT-IV FILE SYSTEMS File System Interface: File Concept Access Methods Directory Structure File System Mounting Protection Overview For most users, the file system is the most visible aspect of an operating
UNIT-IV FILE SYSTEMS File System Interface: File Concept Access Methods Directory Structure File System Mounting Protection Overview For most users, the file system is the most visible aspect of an operating
The 80C186XL 80C188XL Integrated Refresh Control Unit
 APPLICATION BRIEF The 80C186XL 80C188XL Integrated Refresh Control Unit GARRY MION ECO SENIOR APPLICATIONS ENGINEER November 1994 Order Number 270520-003 Information in this document is provided in connection
APPLICATION BRIEF The 80C186XL 80C188XL Integrated Refresh Control Unit GARRY MION ECO SENIOR APPLICATIONS ENGINEER November 1994 Order Number 270520-003 Information in this document is provided in connection
FAST CALCULATION OF INVERSE MATRICES OCCURRING IN SQUARED-RECTANGLE CALCULATION
 R911 Philips Res. Repts 30, 329*-336*, 1975 Issue in honour of C. J. Bouwkamp FAST CALCULATION OF INVERSE MATRICES OCCURRING IN SQUARED-RECTANGLE CALCULATION 1. Introduction by A. J. W. DUIJVESTIJN Technological
R911 Philips Res. Repts 30, 329*-336*, 1975 Issue in honour of C. J. Bouwkamp FAST CALCULATION OF INVERSE MATRICES OCCURRING IN SQUARED-RECTANGLE CALCULATION 1. Introduction by A. J. W. DUIJVESTIJN Technological
Solutions for Operations Research Final Exam
 Solutions for Operations Research Final Exam. (a) The buffer stock is B = i a i = a + a + a + a + a + a 6 + a 7 = + + + + + + =. And the transportation tableau corresponding to the transshipment problem
Solutions for Operations Research Final Exam. (a) The buffer stock is B = i a i = a + a + a + a + a + a 6 + a 7 = + + + + + + =. And the transportation tableau corresponding to the transshipment problem
CS 2150 (fall 2010) Midterm 2
 Name: Userid: CS 2150 (fall 2010) Midterm 2 You MUST write your name and e-mail ID on EACH page and bubble in your userid at the bottom of EACH page, including this page. If you are still writing when
Name: Userid: CS 2150 (fall 2010) Midterm 2 You MUST write your name and e-mail ID on EACH page and bubble in your userid at the bottom of EACH page, including this page. If you are still writing when
Chapter 8. Operating System Support. Yonsei University
 Chapter 8 Operating System Support Contents Operating System Overview Scheduling Memory Management Pentium II and PowerPC Memory Management 8-2 OS Objectives & Functions OS is a program that Manages the
Chapter 8 Operating System Support Contents Operating System Overview Scheduling Memory Management Pentium II and PowerPC Memory Management 8-2 OS Objectives & Functions OS is a program that Manages the
Chapter 5 : Computer Arithmetic
 Chapter 5 Computer Arithmetic Integer Representation: (Fixedpoint representation): An eight bit word can be represented the numbers from zero to 255 including = 1 = 1 11111111 = 255 In general if an nbit
Chapter 5 Computer Arithmetic Integer Representation: (Fixedpoint representation): An eight bit word can be represented the numbers from zero to 255 including = 1 = 1 11111111 = 255 In general if an nbit
REPORT ON MESSAGE SWITCHING WITH THE UNIVAC REAL-TIME COMPUTER
 REPORT ON MESSAGE SWITCHING WITH THE UNIVAC 490 REAL-TIME COMPUTER REPORT ON MESSAGE SWITCHING WITH THE UNIVAC 490 REAL-TIME COMPUTER PX 1792 APRIL, 1961 MILITARY DEPARTMENT ~7I.nd~ DIVISION OF SPERRY
REPORT ON MESSAGE SWITCHING WITH THE UNIVAC 490 REAL-TIME COMPUTER REPORT ON MESSAGE SWITCHING WITH THE UNIVAC 490 REAL-TIME COMPUTER PX 1792 APRIL, 1961 MILITARY DEPARTMENT ~7I.nd~ DIVISION OF SPERRY
Instructions: Assembly Language
 Chapter 2 Instructions: Assembly Language Reading: The corresponding chapter in the 2nd edition is Chapter 3, in the 3rd edition it is Chapter 2 and Appendix A and in the 4th edition it is Chapter 2 and
Chapter 2 Instructions: Assembly Language Reading: The corresponding chapter in the 2nd edition is Chapter 3, in the 3rd edition it is Chapter 2 and Appendix A and in the 4th edition it is Chapter 2 and
Chapter 5. Digital Design and Computer Architecture, 2 nd Edition. David Money Harris and Sarah L. Harris. Chapter 5 <1>
 Chapter 5 Digital Design and Computer Architecture, 2 nd Edition David Money Harris and Sarah L. Harris Chapter 5 Chapter 5 :: Topics Introduction Arithmetic Circuits umber Systems Sequential Building
Chapter 5 Digital Design and Computer Architecture, 2 nd Edition David Money Harris and Sarah L. Harris Chapter 5 Chapter 5 :: Topics Introduction Arithmetic Circuits umber Systems Sequential Building
Module 1: Introduction. What is an Operating System?
 Module 1: Introduction What is an operating system? Simple Batch Systems Multiprogramming Batched Systems Time-Sharing Systems Personal-Computer Systems Parallel Systems Distributed Systems Real-Time Systems
Module 1: Introduction What is an operating system? Simple Batch Systems Multiprogramming Batched Systems Time-Sharing Systems Personal-Computer Systems Parallel Systems Distributed Systems Real-Time Systems
DLD VIDYA SAGAR P. potharajuvidyasagar.wordpress.com. Vignana Bharathi Institute of Technology UNIT 1 DLD P VIDYA SAGAR
 UNIT I Digital Systems: Binary Numbers, Octal, Hexa Decimal and other base numbers, Number base conversions, complements, signed binary numbers, Floating point number representation, binary codes, error
UNIT I Digital Systems: Binary Numbers, Octal, Hexa Decimal and other base numbers, Number base conversions, complements, signed binary numbers, Floating point number representation, binary codes, error
Computer Systems. Binary Representation. Binary Representation. Logical Computation: Boolean Algebra
 Binary Representation Computer Systems Information is represented as a sequence of binary digits: Bits What the actual bits represent depends on the context: Seminar 3 Numerical value (integer, floating
Binary Representation Computer Systems Information is represented as a sequence of binary digits: Bits What the actual bits represent depends on the context: Seminar 3 Numerical value (integer, floating
CUARINGHOUSE FOR FEDERAL SCIENTIFIC AND TECHNICAL INFORMATION OFSTI DOCUMENT MANAGEMENT BRANCH LIMITATIONS IN REPRODUCTION QUALITY
 CUARINGHOUSE FOR FEDERAL SCIENTIFIC AND TECHNICAL INFORMATION OFSTI DOCUMENT MANAGEMENT BRANCH 410.11 LIMITATIONS IN REPRODUCTION QUALITY ACCESSION «ftß bo^rollz ET I. «E REGRET THAT LEGIBILITY OF THIS
CUARINGHOUSE FOR FEDERAL SCIENTIFIC AND TECHNICAL INFORMATION OFSTI DOCUMENT MANAGEMENT BRANCH 410.11 LIMITATIONS IN REPRODUCTION QUALITY ACCESSION «ftß bo^rollz ET I. «E REGRET THAT LEGIBILITY OF THIS
COSC 6385 Computer Architecture. Instruction Set Architectures
 COSC 6385 Computer Architecture Instruction Set Architectures Spring 2012 Instruction Set Architecture (ISA) Definition on Wikipedia: Part of the Computer Architecture related to programming Defines set
COSC 6385 Computer Architecture Instruction Set Architectures Spring 2012 Instruction Set Architecture (ISA) Definition on Wikipedia: Part of the Computer Architecture related to programming Defines set
Number Systems (2.1.1)
 Number Systems (2.1.1) Concept of a register. Operations of register, Complementation, Ranges, Left and right shifts, Addition of two binary number, Numerical overflow, 2 s complement representation, Binary
Number Systems (2.1.1) Concept of a register. Operations of register, Complementation, Ranges, Left and right shifts, Addition of two binary number, Numerical overflow, 2 s complement representation, Binary
OPERATING SYSTEMS. Deadlocks
 OPERATING SYSTEMS CS3502 Spring 2018 Deadlocks Chapter 7 Resource Allocation and Deallocation When a process needs resources, it will normally follow the sequence: 1. Request a number of instances of one
OPERATING SYSTEMS CS3502 Spring 2018 Deadlocks Chapter 7 Resource Allocation and Deallocation When a process needs resources, it will normally follow the sequence: 1. Request a number of instances of one
Divide: Paper & Pencil
 Divide: Paper & Pencil 1001 Quotient Divisor 1000 1001010 Dividend -1000 10 101 1010 1000 10 Remainder See how big a number can be subtracted, creating quotient bit on each step Binary => 1 * divisor or
Divide: Paper & Pencil 1001 Quotient Divisor 1000 1001010 Dividend -1000 10 101 1010 1000 10 Remainder See how big a number can be subtracted, creating quotient bit on each step Binary => 1 * divisor or
Functions. Ray Seyfarth. August 4, Bit Intel Assembly Language c 2011 Ray Seyfarth
 Functions Ray Seyfarth August 4, 2011 Functions We will write C compatible function C++ can also call C functions using extern "C" {...} It is generally not sensible to write complete assembly programs
Functions Ray Seyfarth August 4, 2011 Functions We will write C compatible function C++ can also call C functions using extern "C" {...} It is generally not sensible to write complete assembly programs
A Linear-Time Heuristic for Improving Network Partitions
 A Linear-Time Heuristic for Improving Network Partitions ECE 556 Project Report Josh Brauer Introduction The Fiduccia-Matteyses min-cut heuristic provides an efficient solution to the problem of separating
A Linear-Time Heuristic for Improving Network Partitions ECE 556 Project Report Josh Brauer Introduction The Fiduccia-Matteyses min-cut heuristic provides an efficient solution to the problem of separating
