Network Dimensioning Based on Percentage of Access Link Capacity Carrying Premium Traffic
|
|
|
- Brittney Park
- 5 years ago
- Views:
Transcription
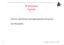
1 Network Dimensioning Based on Percentage of Access Link Capacity Carrying Premium Traffic Vasilios A. Siris and Georgios I. Fotiadis Foundation for Research and Technology - Hellas (FORTH), Institute of Computer Science and University of Crete, Department of Computer Science P.O. Box 1385, GR Heraklion, Crete, Greece Tel.: , fax: {vsiris,fotiadis}@ics.forth.gr Abstract Network dimensioning is typically based on a traffic matrix that contains the bandwidth demand for each sourcedestination pair. We consider a different approach, which assumes that only the maximum amount of premium traffic that can be carried across each access link is known. Based on this information, we present three algorithms for determining the bandwidth required for premium traffic in the core network. The first algorithm intermediately estimates the traffic matrix based on the gravity model. The other two algorithms compute the worst-case requirements for premium traffic when there are no link failures and fixed routing is used (second algorithm), and when there are link failures and alternative routing paths are available (third algorithm). An important feature of the two worst-case algorithms is that they allow admission control decisions to be based solely on the availability of bandwidth for premium traffic at the access links. We apply and compare the three algorithms for the Greek Research and Technology Network (GRNET), which currently uses the third algorithm for its premium IP service. I. INTRODUCTION Quality of Service (QoS) has become a reality in most of today s packet switched networks. QoS defines the mechanisms used to provide bandwidth and delay/jitter guarantees to the subscribers of a multi-service communication network, which can simultaneously accommodate different types of traffic flows, such as voice-over-ip (VoIP), streaming video, and legacy best-effort Internet traffic (file transfer, and web traffic). The DiffServ model [1] is the most common approach for QoS provision. DiffServ introduces the notion of Per-Hop-Behavior (PHB) where each aggregate traffic flow is mapped to a traffic class, whose packets are treated equally. Each traffic class can represent a different service offered by the network provider. PHBs are implemented at routers using priority queuing and scheduling mechanisms. Providing guarantees in large-scale DiffServ networks can be a complex task mainly due to the heterogeneity of the participating subscriber and provider networks, whose capacity can range from several Gbps to under one Mbps, as in the case of low-speed DSL links. This capacity mismatch can result in congestion at the network core and, more likely, at the network edge. One approach to address this problem is to This work has been supported in part by the Greek Research and Technology Network (GRNET). limit the amount of premium traffic that can be carried over the access links, and implement an appropriate dimensioning and provisioning scheme for ensuring the guarantees for premium traffic; such an approach also avoids premium IP traffic from starving best-effort traffic. The maximum percentage of each access link that can be used for premium traffic can depend on the provider s service policy. Hence, in the case of a nonprofit NREN (National Research and Educational Network), as is the case of the Greek Research and Technology Network (GRNET), subscribers with the same access link capacity can be allowed to use up to the same maximum percentage of the access link s capacity for carrying premium traffic, hence ensuring fairness in using the premium IP service. On the other hand, a provider selling network access services can offer different pricing options that correspond to a different percentage of premium IP traffic that can be sent across the access link. In this paper we present and investigate three dimensioning algorithms that estimate the required premium IP bandwidth in the core network, taking as input the maximum percentage of each access link s capacity that can carry premium traffic. The first algorithm intermediately estimates the traffic matrix based on the so-called gravity model [2], [3]. The other two algorithms compute the worst-case bandwidth requirements when there are no link failures and fixed routing is applied (second algorithm), and when there are link failures and alternative routing paths are available (third algorithm). An important advantage of the latter two algorithms is that admission control decisions can be based solely on the availability of bandwidth for premium traffic at the access links. This greatly simplifies the core network, which only requires to give higher priority to premium traffic, through the provision of appropriate PHB mechanisms. Additionally, the three algorithms are independent of the particular routing algorithm implemented in the core network: the first and second algorithm assumes that the routing paths are known, whereas the third algorithm computes the worst-case bandwidth requirements when alternate routing paths can bypass failed links. The third algorithm is currently used for GRNET s premium IP service [4], where requests for premium connections are made through a web-based tool that takes admission control decisions based solely on the access
2 link capacities, their maximum percentage that can be used for premium traffic, and the active premium IP connections. The remainder of this paper is organized as follows. Section II identifies related work in the field of network dimensioning and capacity planning. Section III provides the network definitions and the provisioning mechanisms used, while Section IV presents the three dimensioning algorithms we investigate. Section V presents the results from the application of the algorithms to the GRNET 1 network and, finally, Section VI concludes the paper. II. RELATED WORK Several methods have been proposed in the literature for estimating the traffic demand over a network s backbone in order to efficiently dimension network capacity. The traffic demand is typically expressed using a two-dimension traffic matrix that quantifies the demand between all source and destination pairs in the network; e.g. see [3], [5] and the references therein. The computation requires measurements of the actual traffic, e.g. at the ingress and egress interfaces. Rather than considering the point-to-point demand, the work of [6] considers the traffic demand originating from an ingress router to a set of egress routers; such a model is appropriate for transit domains, where a destination is reachable from multiple egress routers. The above approaches cannot be applied to premium IP services, which have not been offered before, hence for which no usage data is available. One approach for network dimensioning of premium IP services involves the formulation of an optimization problem involving link costs. However, consideration of delay and loss constraints lead to an NP-complete problem, whose solution requires various heuristic assumptions [7]. Optimization objectives involving link costs can also be considered when premium IP traffic co-exists with best-effort traffic [8], [9]. Unlike the above works, the dimensioning approach we consider does not require knowledge of a traffic matrix between source-destination pairs, but only the maximum percentage of the access link capacity that can be used for premium IP traffic; moreover, the second and third algorithm we present find the worst-case bandwidth requirements, independent of the underlying routing algorithm. On the other hand, the works of [7], [8], [9] consider the capacity dimensioning problem in conjunction with routing. Such joint consideration would lead to more optimal dimensioning; however, in current networks that typically over-dimension some of the core network links carrying both best-effort and premium traffic, the added complexity required to modify the routing algorithm is likely to outweigh the increased efficiency. III. DEFINITIONS AND MECHANISMS In this section we provide the definitions used in the remaining sections, and describe the provisioning mechanisms used at the core and the edge of the network to meet the guarantees for premium traffic. 1 The Greek Research and Technology Network (GRNET), c r,kr, a + r,kr, a r,kr c r,1, a + r,1, a r,1 router r Provider Network router j c j,kj, a + j,k j, a j,k j c j,1, a + j,1, a j,1 Fig. 1. A provider s edge router r is connected to K r subscriber networks. The k th subscriber network connected to router r has capacity c r,k. A maximum percentage a + r,k, a r,k of this access link capacity can carry premium IP traffic in the ingress, egress direction, respectively. A. Definitions Let G = (R, L) be a directed graph representing the network topology, where R is the set of routers and L is the set of links in the network interconnecting the routers in R. The capacity of link l is C l. Every router r R of the provider network has a number K r of subscriber networks connected to it, Figure 1. Each subscriber network is connected to the provider s edge router through an access link with capacity c r,k, where r R and 1 k K r. A maximum percentage of this access link capacity can be used to carry premium traffic. Let this percentage be a + r,k in the ingress direction (from the subscriber to the provider) and a r,k in the egress direction (from the provider to the subscriber). For each edge router r we define I(r) as the maximum aggregate rate of premium traffic that can be inserted to the provider s network through router r from all its subscriber networks, and O(r) as the maximum aggregate rate of premium traffic that can be ejected from the provider s network through router r to all its subscriber networks. Hence, K r I(r) = a + r,k c K r r,k, O(r) = a r,k c r,k. (1) k=1 k=1 If the network does not contain any servers that only produce or consume premium IP traffic, we will have a + r,k = a r,k, hence I(r) = O(r), r R. Note, however, that the algorithms presented in Section IV do not require this assumption. B. Provisioning mechanisms In order to satisfy the requirements for premium IP services appropriate mechanisms have to be implemented both at the edge and the core of the network. These mechanisms include admission control, policing, and queueing. The objective of admission control is to ensure that requests for premium IP connections are accepted only if there is available bandwidth. Note that admission control is applied in addition to defining a maximum percentage of each access link s capacity that can be used for premium traffic. Hence, it is not enough to check that the access link of a subscriber requesting a premium connection has enough bandwidth to accept the request. With the application of the second and
3 third dimensioning algorithms, which estimate the worst-case bandwidth requirements when there are no link failures and fixed routing is applied (second algorithm), and when there are link failures and alternative routing paths are available (third algorithm), the admission control decision needs to involve only the ingress and egress access links that the requested premium IP connection will traverse. The second provisioning mechanism is policing, whose objective is to ensure that the traffic entering the network conforms to the maximum amount of traffic allowed for the particular connection. Policing is applied solely at the ingress router of the provider network, and is based on the source and destination subscriber network of the premium IP connection. The third provisioning mechanism involves queueing, whose objective is to give higher priority to premium IP traffic. In a DiffServ network this is achieved through the Expedited Forwarding (EF) PHB mechanism. Recall that starvation of best-effort traffic is avoided by limiting the amount of premium IP traffic at the access links. IV. NETWORK DIMENSIONING ALGORITHMS In this section we present three dimensioning algorithms whose input is the maximum amount of premium traffic that can be carried across each access link. A. Gravity-based Traffic Matrix (GTM) Dimensioning Algorithm The Gravity-based Traffic Matrix (GTM) dimensioning algorithm uses the maximum amount of premium traffic carried across each access link to estimate a traffic matrix using the socalled gravity model. The gravity model originated in social science, but has been successfully applied in telephony to accurately model the telephone traffic exchanged between two cities based on their number of area codes, and in IP networks to estimate the traffic matrix from network measurements; e.g. see [2], [3], [5] and the references therein. According to this model the amount of premium traffic M(s,d) originating from router s and destined to router d is proportional to the amount of premium traffic that can be accepted by router d, hence M(s,d) = I(s) O(d) x R O(x). If we define P(s,d) to be the path from s to d, then the bandwidth requirement for premium IP traffic B(l) at each link l L can be computed using the following Algorithm 1: Algorithm 1 Gravity-based Traffic Matrix (GTM) Algorithm for all s R do for all d R do for all l P(s,d) do B(l)+ = M(s,d) Algorithm 1 adds to each link belonging to the path from router s to d the amount of traffic M(s,d) estimated using the gravity model assumption. In Section V where we apply the proposed algorithms to the GRNET network, the GTM algorithm will be used as a baseline comparison since it represents an accurate estimate of the bandwidth requirements for premium IP traffic, if the gravity model s proportionality assumption used for estimating the traffic matrix is accurate. B. Worst-Case (WC) Dimensioning Algorithm with no Link Failures and Fixed Routing This worst-case (WC) dimensioning algorithm defines an upper bound for the bandwidth required for premium traffic on all network links, when no link failures occur and fixed routing is assumed. The algorithm s input are variables I and O, defined in (1). The algorithm assumes the path P(s,d) between each source-destination pair is static and known. The WC algorithm relies on the calculation of two variables: B I (l) denotes the aggregate traffic that can be injected from all upstream routers to link l (recall that links are directed), and is given by B I (l) = I(s). s: d R:l P(s,d) Similarly, B O (l) denotes the aggregate traffic that can be ejected to routers that are downstream of link l. So: B O (l) = O(d). d: s R:l P(s,d) The bandwidth allocations for every link is determined through the following lemma. Lemma 1: The maximum bandwidth requirements for premium IP traffic on link l L is given by the minimum of B I (l) and B O (l). Proof: Suppose that l L with B I (l) = a and B O (l) = b, and a > b. It is not possible for link l to carry premium traffic with rate a, even though upstream routers can inject such an amount traffic, because downstream routers can only accept traffic with maximum rate b < a. Hence, the maximum amount of premium traffic that can flow through link l is b. Similarly, if a < b then the maximum premium traffic is limited by the amount of traffic that can be injected in the link by its upstream routers, which is a. The pseudocode for the worst-case (WC) dimensioning algorithm is shown in Algorithm 2. C. Worst-Case Dimensioning Algorithm with Link Failures (WC-LF) Next we present a worst-case dimensioning algorithm that considers link failures and assumes alternate routes exist; this is the case when the network contains loops, i.e. a set of links whose endpoints form a closed loop. Let T be a spanning tree of the directed graph representing the network topology; T contains a single path from any source router to any destination router. The algorithm presented in the previous subsection can be used to calculate the maximum bandwidth requirements B T (l) for each link l belonging to the spanning tree T. The overall worst-case
4 Algorithm 2 Worst-Case (WC) Dimensioning Algorithm for all s R do if d R such that l in P(s,d) then B I (l)+ = I(s) end if for all d R do if s R such that l in P(s,d) then B O (l)+ = O(d) end if B(l) = min{b I (l),b O (l)} bandwidth requirement B (l) for link l can be found by taking the maximum of B T (l) over all spanning trees T ; this considers all possible link failures and alternate routes. The correctness of this approach for finding the worst-case bandwidth requirements follows directly from Lemma 1. Let V be the set of loops, and V = {l : l v,v V } the set of all links belonging to loops. Next we propose an algorithm for calculating the worst-case bandwidth requirements on all links. We will initially assume that the loops in the network are disjoint, i.e. they do not share common links. We consider this special case since many wide-area networks, such as GRNET, have such a topology. Later we will present a more general algorithm for the general case. In the simple case of disjoint loops, all the different spanning trees can be found by sequentially marking each link in a loop as down, and applying the worst-case Algorithm 2. The resulting pseudocode is shown in Algorithm 3. At the end of the algorithm, the maximum bandwidth requirement for link l is given by B (l). Algorithm 3 Worst-Case Dimensioning Algorithm with Link Failures (WC-LF) while l V : l not processed do for all v V do if l v : l not processed then mark l as down mark l as processed end if run WC Algorithm 2 B (l) = max{b(l),b (l)} mark all links as up end while D. WC-LF+ Algorithm Next we extend Algorithm 3 to the case of network topologies that contain loops which share common links. The approach followed by this algorithm extends the WC- LF algorithm by marking more than one links in the original graph as down, such that the remaining links create a single path between the different router pairs. We define P (s,d) = {P(s,d)} to be all the possible paths from router s to d, and as before V = {l : l v,v V } the set of all links belonging to loops. The pseudocode for the WC-LF+ algorithm is shown below. At the end of the algorithm, the maximum bandwidth requirement for link l is given by B (l). Algorithm 4 WC-LF+ Dimensioning Algorithm for all s R do for all d R do for all p P (s,d) do mark one link l from every p P (s,d) {p} as down, s.t. l V and l belongs to a single loop run WC Algorithm 2 B (l) = max{b(l),b (l)} It is worth noting that the two worst-case algorithms are equivalent to finding for each link l, the worst-case bandwidth requirements over all cuts of the network graph that divide it into two disjoint subgraphs, and the two end-points of link l are contained in different subgraphs [4]. V. APPLICATION TO THE GREEK RESEARCH AND TECHNOLOGY NETWORK (GRNET) In this section we present and discuss results from the application of the three dimensioning algorithms described in the previous section to the GRNET network, whose premium IP service is used for VoIP and other delay-sensitive traffic. The Gravity-based Traffic Matrix (GTM) algorithm yields an accurate estimate of the bandwidth requirements for premium traffic, if the gravity model s proportionality assumption used for estimating the traffic matrix is accurate. Hence, comparison of the GTM algorithm with the two worst-case dimensioning algorithms (Algorithm 2 - WC, and Algorithm 3 - WC-LF) will show when and by how much these two algorithms overestimate the required bandwidth for premium traffic. Note that since the GRNET network does not contain loops with common links, we apply Algorithm 3 for estimating the worstcase premium IP bandwidth requirements in the case of link failures. Also, because loops do not share common links, there are two routes between routers belonging to loops. The GRNET network is shown in Figure 2. The rectangular nodes represent core routers with high speed interfaces (up to 2.5 Gbps) that typically contain a large number of subscriber networks, while the round nodes are routers with lower speed
5 Ioannina (13) Patra (9) Ioannina-2 (12) Patra-2 (8) 2.5 Gbps 1Gbps Acropolis (3) 100 Mbps 34 Mbps Fig. 2. Thessaloniki-2 (14) Larissa-2 (10) Athens-3 (1) Ilissos (2) Thessaloniki (15) Larissa (11) Athens (4) Syros (5) Herakleio-2 (6) The GRNET Network Herakleio (7) Xanthi (16) interfaces (up to 100 Mbps, except the Athens router that has a 1 Gbps interface). The access links of subscriber networks are highly heterogenous, ranging from speeds of 1 Gbps (University of Athens, connected to the Acropolis router) to 2 Mbps (Institute of Molecular Biology Crete - IMBC, connected to the Herakleio router). The maximum percentage of the access link s capacity that can be used to carry premium traffic is shown in Table I; we assume that the percentage is the same in the ingress and egress direction. Table II shows the subscriber networks of router Herakleio and their corresponding access link capacities. The aggregate amount of traffic that can be injected in the network, I, and ejected from the network, O, from the Herakleio router can be calculated using (1) and Table II. Hence, I(Herakleio) = O(Herakleio) = = 14.8 Mbps. The values of the variables I and O for the other routers in GRNET are shown in Table III; for all routers, I is equal to O since we have assumed that the percentage of the access link that can be used for premium traffic is the same in the ingress and egress direction. Table III also shows each router s ID that appears in the notation link a b, which represents the link connecting routers with ID a and b. TABLE I ACCESS LINK PERCENTAGES FOR PREMIUM IP TRAFFIC Access Link Capacity c Percentage Reserved 1 Gbps 1% 100 Mbps 10% 34 Mbps 20% TABLE II SUBSCRIBER NETWORKS AT NODE Herakleio Subscriber Network Access Link Capacity (Mbps) UoC 34 FORTH 34 TEIHER 4 IMBC 2 TABLE III GRNET ROUTERS Router Name Router ID I, O (Mbps) Athens Ilissos Acropolis Athens Syros Herakleio Herakleio Patra Patra Larissa Larissa Ioannina Ioannina Thessaloniki Thessaloniki Xanthi TABLE IV PREMIUM IP BANDWIDTH REQUIREMENTS Link ID GTM (%) WC (%) WC-LF (%) Results from the application of the three dimensioning algorithms appear in Table IV, which shows the maximum amount of bandwidth and the corresponding percentage of each link s capacity required for premium traffic that is estimated by the three dimensioning algorithms. Because the percentage of the access link capacity used for premium traffic is the same in the ingress and egress direction, the bandwidth requirements are symmetric, hence the maximum premium IP bandwidth for link a b is equal to that of link b a. As expected, the bandwidth requirements for premium IP traffic estimated by the Gravity-based Traffic Matrix (GTM) algorithm are smaller than the two worst-case dimensioning algorithms WC and WC-LF. Additionally, the bandwidth estimates for the WC-LF algorithm are equal to or higher than the other two algorithms; this is expected since the WC-LF algorithm considers alternate routes to bypass link failures, whereas the other two algorithms assume that links do not fail and consider fixed routes. The percentage by which the two worst-case algorithms overestimate, compared to the GTM algorithm, the premium IP traffic bandwidth requirements is not the same for all links. In particular, the overestimation for links that do not belong to a network loop is up to approximately 14% (for link 14 15).
6 Additionally, for these links the estimate by the two worstcase dimensioning algorithms is the same; this occurs because for links that do not belong to loops there are no alternate routes. Finally, note that except for links and 15 16, the estimated percentage of premium IP traffic on all links not belonging to a loop are under 15%, which is less than the maximum percentage of 25% premium traffic typically suggested for supporting low loss and jitter [10]. On the other hand, for links and the estimated bandwidth for premium IP traffic is above 35% for all three dimensioning algorithms; this suggests that the capacity for these two links should be increased in order to effectively accommodate the full demand for premium IP services. For the links that belong to loops, the overestimation for premium IP bandwidth by the two worst-case algorithms is higher. However, the overestimation is not the same for all links. Hence, the overestimation of the WC algorithm for links 1 10, 10 14, and 1 8 is lower (up to 80% for link 10 14) than for links 8 12 and (up to 380% for link 8 12). This is attributed to the fact that routers 8 and 12 contain a small aggregate subscriber rate, and the premium IP bandwidth estimates of the GTM algorithm for links 8 12 and are small because these links are not contained in many routing paths, as is the case of links 1 10, 10 14, and 1 8. The latter observation also explains why the overestimation for link 2 3 (570%), which is contained only in the path from router 2 to 3, is larger than for links 1 2 and 2 3 (42%). Also, note that for these links the WC-LF algorithm overestimates the premium IP bandwidth compared to the WC algorithm by 100%; this is to be expected since, unlike the WC algorithm, the WC-LF algorithm considers the case of link failures and there are two routes between routers belonging to a loop. It is important to note that for all the above links the estimated premium IP bandwidth by all three algorithms is less than 8%, which is less than the percentage 25% mentioned above for supporting low loss and jitter. From the above results we can conclude that the maximum percentage of the access link capacities for premium IP traffic shown in Table I can be supported on the core links of GRNET s network, except for links and where the percentage required for premium IP traffic even with the Gravity-based Traffic Matrix (GTM) algorithm is above 35%, which is rather too high; this result suggests that the capacity for these two links should be increased. The discussion in this section shows how the proposed dimensioning algorithms can be used in practise, to determine if the capacity of core links in a wide-area network needs to be increased, and by how much, or to estimate the minimum amount of capacity that is available for best-effort traffic with and without link failures. VI. CONCLUDING REMARKS We presented three algorithms for dimensioning a network supporting premium IP traffic, when only the maximum amount of premium traffic that can be carried across each access link is known. The Gravity-based Traffic Matrix (GTM) algorithm is expected to be accurate if the proportionality assumption of the gravity model is accurate; other works have shown that it is quite accurate for telephony and besteffort traffic. The other two dimensioning algorithms estimate the worst-case bandwidth requirements, hence can be more appropriate when premium services are first rolled out and enable a provider to offer a higher level of assurances for premium IP traffic compared to the GTM algorithm. Moreover, they allow admission control decisions to be based solely on the availability of bandwidth at the access links. Which of the two worst-case dimensioning algorithms should be used will depend on the probability of link failures, since only the WC- LF (Worst-Case with Link Failures) dimensioning algorithm considers link failures, hence its bandwidth estimates can support guarantees in such cases. We compared the estimates of the three algorithms through their application to an actual wide-area network, the Greek Research and Technology Network (GRNET). The comparison gives intuition of when the worst-case algorithms overestimate the required premium IP bandwidth, and demonstrate how the algorithms can be used to determine if the capacity in core network links needs to be increased, and for estimating the minimum bandwidth for best-effort traffic with and without link failures. The worst-case dimensioning algorithms assumed that traffic from a particular source router can be destined to any destination router. It would be interesting to adapt the algorithms in this paper to the case where the traffic from a source router can be destined to a set of destination routers, rather than to all routers; such a model is appropriate for transit networks. Another area for further work is the application of the proposed dimensioning algorithms to more complex network topologies, such as the European-wide GEANT network 2. REFERENCES [1] S. Blake, D. Black, M. Carlson, E. Davies, Z. Wang, and W. Weiss, An Architecture for Differentiated Services, RFC 2475, December [2] D. Lam, D. Cox, and J. Widom, Teletraffic Modeling for Personal Communications Services, IEEE Commun., vol. 35, no. 2, Feb [3] Y. Zhang, M. Roughan, N. Duffield, and A. Greenberg, Fast accurate computation of large-scale IP traffic matrices from link loads, in Proc. of ACM SIGMETRICS 03. [4] A. Varvitsiotis, V. A. Siris, D. N. Primpas, G. I. Fotiadis, A. C. Liakopoulos, and C. J. Bouras, Techniques for DiffServ-based QoS in Hierarchically Federated MAN Networks: the GRNET Case, in Proc. of IEEE LANMAN [5] A. Gunnar, M. Johansson, and T. Telkamp, Traffic Matrix Estimation on a Large IP Backbone - A Comparison on Real Data, in Proc. of Internet Measurement Conference 2004, October [6] A. Feldmann, A. Greenberg, C. Lund, N. Reingold, J. Rexford, and F. True, Deriving Traffic Demand for Operational IP Networks: Methodology and Experience, in Proc. of ACM SIGCOMM 00. [7] P. Trimintzios, T. Bauge, G. Pavlou, L. Georgiadis, R. Egan, and P. Flegkas, Quality of Service Provisioning for Supporting Premium Services in IP Networks, in Proc. of IEEE Globecom [8] K. Wu and D. Reeves, Capacity Planning of DiffServ Networks with Best-Effort and Expedited Forwarding Traffic, Telecommunication Systems, vol. 25, pp , [9], Link Dimensioning and LSP Optimization for MPLS Networks Supporting DiffServ EF and BE traffic classes, 18th International Teletraffic Congress, [10] C. Filsfils and J. Evans, Engineering a multiservice IP backbone to support tight SLAs, Computer Networks, vol. 40, pp , The European Academic and Research Backbone GEANT,
Extending the QoS provisioning in GRNET
 Extending the QoS provisioning in GRNET Christos Bouras Vaggelis Kapoulas Dimitris Primpas Leonidas Poulopoulos Research Academic Computer Technology Institute, N. Kazantzaki str., University Campus, GR-26500
Extending the QoS provisioning in GRNET Christos Bouras Vaggelis Kapoulas Dimitris Primpas Leonidas Poulopoulos Research Academic Computer Technology Institute, N. Kazantzaki str., University Campus, GR-26500
A Framework for dynamic and on-demand QoS to Videoconference Session
 A Framework for dynamic and on-demand QoS to Videoconference Session Christos Bouras Research Academic Computer Technology Institute and Computer Engineering and Informatics Department, University of Patras
A Framework for dynamic and on-demand QoS to Videoconference Session Christos Bouras Research Academic Computer Technology Institute and Computer Engineering and Informatics Department, University of Patras
A Framework for dynamic and on-demand QoS to Videoconference Session
 A Framework for dynamic and on-demand QoS to Videoconference Session Christos Bouras, Apostolos Gkamas and Dimitris Primpas Research Academic Computer Technology Institute, N. Kazantzaki Str., University
A Framework for dynamic and on-demand QoS to Videoconference Session Christos Bouras, Apostolos Gkamas and Dimitris Primpas Research Academic Computer Technology Institute, N. Kazantzaki Str., University
Extending QoS support from Layer 3 to Layer 2
 Extending QoS support from Layer 3 to Layer 2 Christos Bouras Vaggelis Kapoulas Vassilis Papapanagiotou Leonidas Poulopoulos Dimitris Primpas Kostas Stamos Research Academic Computer Technology Institute,
Extending QoS support from Layer 3 to Layer 2 Christos Bouras Vaggelis Kapoulas Vassilis Papapanagiotou Leonidas Poulopoulos Dimitris Primpas Kostas Stamos Research Academic Computer Technology Institute,
Christos Bouras 1,2, Vaggelis Kapoulas 1, Vassilis Papapanagiotou 1,2, Leonidas Poulopoulos 2,3, Dimitris Primpas 1,2, Kostas Stamos 1,2
 Layer 2 Quality of Service Architectures 1 1 X Layer 2 Quality of Service Architectures Christos Bouras 1,2, Vaggelis Kapoulas 1, Vassilis Papapanagiotou 1,2, Leonidas Poulopoulos 2,3, Dimitris Primpas
Layer 2 Quality of Service Architectures 1 1 X Layer 2 Quality of Service Architectures Christos Bouras 1,2, Vaggelis Kapoulas 1, Vassilis Papapanagiotou 1,2, Leonidas Poulopoulos 2,3, Dimitris Primpas
Investigating Bandwidth Broker s inter-domain operation for dynamic and automatic end to end provisioning
 Investigating Bandwidth Broker s inter-domain operation for dynamic and automatic end to end provisioning Christos Bouras and Dimitris Primpas Research Academic Computer Technology Institute, N.Kazantzaki
Investigating Bandwidth Broker s inter-domain operation for dynamic and automatic end to end provisioning Christos Bouras and Dimitris Primpas Research Academic Computer Technology Institute, N.Kazantzaki
Quality of Service II
 Quality of Service II Patrick J. Stockreisser p.j.stockreisser@cs.cardiff.ac.uk Lecture Outline Common QoS Approaches Best Effort Integrated Services Differentiated Services Integrated Services Integrated
Quality of Service II Patrick J. Stockreisser p.j.stockreisser@cs.cardiff.ac.uk Lecture Outline Common QoS Approaches Best Effort Integrated Services Differentiated Services Integrated Services Integrated
IPv6 QoS Testing on Dual Stack Network
 IPv6 QoS Testing on Dual Stack Network Christos Bouras Dimitris Primpas Kostas Stamos Research Academic Computer Technology Institute, N.Kazantzaki Str., 26500, University Of Patras Campus, Rio, Patras,
IPv6 QoS Testing on Dual Stack Network Christos Bouras Dimitris Primpas Kostas Stamos Research Academic Computer Technology Institute, N.Kazantzaki Str., 26500, University Of Patras Campus, Rio, Patras,
DiffServ Architecture: Impact of scheduling on QoS
 DiffServ Architecture: Impact of scheduling on QoS Abstract: Scheduling is one of the most important components in providing a differentiated service at the routers. Due to the varying traffic characteristics
DiffServ Architecture: Impact of scheduling on QoS Abstract: Scheduling is one of the most important components in providing a differentiated service at the routers. Due to the varying traffic characteristics
QoS support in IPv6 environments
 QoS support in IPv6 environments Location, country Date Speaker name (or email address) Copy Rights This slide set is the ownership of the 6DISS project via its partners The Powerpoint version of this
QoS support in IPv6 environments Location, country Date Speaker name (or email address) Copy Rights This slide set is the ownership of the 6DISS project via its partners The Powerpoint version of this
DiffServ Architecture: Impact of scheduling on QoS
 DiffServ Architecture: Impact of scheduling on QoS Introduction: With the rapid growth of the Internet, customers are demanding multimedia applications such as telephony and video on demand, to be available
DiffServ Architecture: Impact of scheduling on QoS Introduction: With the rapid growth of the Internet, customers are demanding multimedia applications such as telephony and video on demand, to be available
DIFFSERV-AWARE FLOW ADMISSION CONTROL AND RESOURCE ALLOCATION MODELING
 EuroFGI Workshop on IP QoS and Traffic Control P. Pereira (Ed.) Lisbon, Portugal, December 6-7, 7 DIFFSERV-AWARE FLOW ADMISSION CONTROL AND RESOURCE ALLOCATION MODELING Gilles Bertrand, Géraldine Texier
EuroFGI Workshop on IP QoS and Traffic Control P. Pereira (Ed.) Lisbon, Portugal, December 6-7, 7 DIFFSERV-AWARE FLOW ADMISSION CONTROL AND RESOURCE ALLOCATION MODELING Gilles Bertrand, Géraldine Texier
A Preferred Service Architecture for Payload Data Flows. Ray Gilstrap, Thom Stone, Ken Freeman
 A Preferred Service Architecture for Payload Data Flows Ray Gilstrap, Thom Stone, Ken Freeman NASA Research and Engineering Network NASA Advanced Supercomputing Division NASA Ames Research Center Outline
A Preferred Service Architecture for Payload Data Flows Ray Gilstrap, Thom Stone, Ken Freeman NASA Research and Engineering Network NASA Advanced Supercomputing Division NASA Ames Research Center Outline
THE Differentiated Services (DiffServ) architecture [1] has been
![THE Differentiated Services (DiffServ) architecture [1] has been THE Differentiated Services (DiffServ) architecture [1] has been](/thumbs/83/87098944.jpg) Efficient Resource Management for End-to-End QoS Guarantees in DiffServ Networks Spiridon Bakiras and Victor O.K. Li Department of Electrical & Electronic Engineering The University of Hong Kong Pokfulam
Efficient Resource Management for End-to-End QoS Guarantees in DiffServ Networks Spiridon Bakiras and Victor O.K. Li Department of Electrical & Electronic Engineering The University of Hong Kong Pokfulam
An Admission Control and Deployment Optimization Algorithm for an Implemented Distributed Bandwidth Broker in a Simulation Environment
 An Admission Control and Deployment Optimization Algorithm for an Implemented Distributed Bandwidth Broker in a Simulation Environment Christos Bouras and Dimitris Primpas Research Academic Computer Technology
An Admission Control and Deployment Optimization Algorithm for an Implemented Distributed Bandwidth Broker in a Simulation Environment Christos Bouras and Dimitris Primpas Research Academic Computer Technology
QoS and IP Premium service specification and implementation. Slide Show
 QoS and IP Premium service specification and implementation Presentation given by Mauro Campanella (GARR) at the TERENA Networking Conference 2001, May 2001 Slide Show Table of Contents Slide 1 Slide 2
QoS and IP Premium service specification and implementation Presentation given by Mauro Campanella (GARR) at the TERENA Networking Conference 2001, May 2001 Slide Show Table of Contents Slide 1 Slide 2
Lecture 13. Quality of Service II CM0256
 Lecture 13 Quality of Service II CM0256 Types of QoS Best Effort Services Integrated Services -- resource reservation network resources are assigned according to the application QoS request and subject
Lecture 13 Quality of Service II CM0256 Types of QoS Best Effort Services Integrated Services -- resource reservation network resources are assigned according to the application QoS request and subject
A Bandwidth-Broker Based Inter-Domain SLA Negotiation
 A Bandwidth-Broker Based Inter-Domain SLA Negotiation Haci A. Mantar θ, Ibrahim T. Okumus, Junseok Hwang +, Steve Chapin β θ Department of Computer Engineering, Gebze Institute of Technology, Turkey β
A Bandwidth-Broker Based Inter-Domain SLA Negotiation Haci A. Mantar θ, Ibrahim T. Okumus, Junseok Hwang +, Steve Chapin β θ Department of Computer Engineering, Gebze Institute of Technology, Turkey β
EE 122: Differentiated Services
 What is the Problem? EE 122: Differentiated Services Ion Stoica Nov 18, 2002 Goal: provide support for wide variety of applications: - Interactive TV, IP telephony, on-line gamming (distributed simulations),
What is the Problem? EE 122: Differentiated Services Ion Stoica Nov 18, 2002 Goal: provide support for wide variety of applications: - Interactive TV, IP telephony, on-line gamming (distributed simulations),
DiffServ over MPLS: Tuning QOS parameters for Converged Traffic using Linux Traffic Control
 1 DiffServ over MPLS: Tuning QOS parameters for Converged Traffic using Linux Traffic Control Sundeep.B.Singh, Girish.P.Saraph, Chetan.P.Bhadricha and Girish.K.Dadhich Indian Institute of Technology Bombay,
1 DiffServ over MPLS: Tuning QOS parameters for Converged Traffic using Linux Traffic Control Sundeep.B.Singh, Girish.P.Saraph, Chetan.P.Bhadricha and Girish.K.Dadhich Indian Institute of Technology Bombay,
DiffServ over MPLS: Tuning QOS parameters for Converged Traffic using Linux Traffic Control
 1 DiffServ over MPLS: Tuning QOS parameters for Converged Traffic using Linux Traffic Control Sundeep.B.Singh and Girish.P.Saraph Indian Institute of Technology Bombay, Powai, Mumbai-400076, India Abstract
1 DiffServ over MPLS: Tuning QOS parameters for Converged Traffic using Linux Traffic Control Sundeep.B.Singh and Girish.P.Saraph Indian Institute of Technology Bombay, Powai, Mumbai-400076, India Abstract
IP Differentiated Services
 Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. 7. IP Diffserv introduction Pag. 1 IP Differentiated Services Providing differentiated services in IP networks
Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. 7. IP Diffserv introduction Pag. 1 IP Differentiated Services Providing differentiated services in IP networks
Real-Time Applications. Delay-adaptive: applications that can adjust their playback point (delay or advance over time).
 Real-Time Applications Tolerant: can tolerate occasional loss of data. Intolerant: cannot tolerate such losses. Delay-adaptive: applications that can adjust their playback point (delay or advance over
Real-Time Applications Tolerant: can tolerate occasional loss of data. Intolerant: cannot tolerate such losses. Delay-adaptive: applications that can adjust their playback point (delay or advance over
Request for Comments: K. Poduri Bay Networks June 1999
 Network Working Group Request for Comments: 2598 Category: Standards Track V. Jacobson K. Nichols Cisco Systems K. Poduri Bay Networks June 1999 An Expedited Forwarding PHB Status of this Memo This document
Network Working Group Request for Comments: 2598 Category: Standards Track V. Jacobson K. Nichols Cisco Systems K. Poduri Bay Networks June 1999 An Expedited Forwarding PHB Status of this Memo This document
Advanced Computer Networks
 Advanced Computer Networks QoS in IP networks Prof. Andrzej Duda duda@imag.fr Contents QoS principles Traffic shaping leaky bucket token bucket Scheduling FIFO Fair queueing RED IntServ DiffServ http://duda.imag.fr
Advanced Computer Networks QoS in IP networks Prof. Andrzej Duda duda@imag.fr Contents QoS principles Traffic shaping leaky bucket token bucket Scheduling FIFO Fair queueing RED IntServ DiffServ http://duda.imag.fr
Congestion Control and Resource Allocation
 Problem: allocating resources Congestion control Quality of service Congestion Control and Resource Allocation Hongwei Zhang http://www.cs.wayne.edu/~hzhang The hand that hath made you fair hath made you
Problem: allocating resources Congestion control Quality of service Congestion Control and Resource Allocation Hongwei Zhang http://www.cs.wayne.edu/~hzhang The hand that hath made you fair hath made you
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 Voice and Video over IP Slides derived from those available on the Web site of the book Computer Networking, by Kurose and Ross, PEARSON 2 Multimedia networking:
Mohammad Hossein Manshaei manshaei@gmail.com 1393 Voice and Video over IP Slides derived from those available on the Web site of the book Computer Networking, by Kurose and Ross, PEARSON 2 Multimedia networking:
1188 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 13, NO. 5, OCTOBER Wei Sun, Student Member, IEEE, and Kang G. Shin, Fellow, IEEE
 1188 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 13, NO. 5, OCTOBER 2005 End-to-End Delay Bounds for Traffic Aggregates Under Guaranteed-Rate Scheduling Algorithms Wei Sun, Student Member, IEEE, and Kang
1188 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 13, NO. 5, OCTOBER 2005 End-to-End Delay Bounds for Traffic Aggregates Under Guaranteed-Rate Scheduling Algorithms Wei Sun, Student Member, IEEE, and Kang
Comparison of Shaping and Buffering for Video Transmission
 Comparison of Shaping and Buffering for Video Transmission György Dán and Viktória Fodor Royal Institute of Technology, Department of Microelectronics and Information Technology P.O.Box Electrum 229, SE-16440
Comparison of Shaping and Buffering for Video Transmission György Dán and Viktória Fodor Royal Institute of Technology, Department of Microelectronics and Information Technology P.O.Box Electrum 229, SE-16440
PERFORMANCE OF PREMIUM SERVICE IN QOS IP NETWORK
 PERFORMANCE OF PREMIUM SERVICE IN QOS IP NETWORK Wojciech Burakowski Monika Fudala Halina Tarasiuk Institute of Telecommunications, Warsaw University of Technology ul. Nowowiejska 15/19, 00-665 Warsaw,
PERFORMANCE OF PREMIUM SERVICE IN QOS IP NETWORK Wojciech Burakowski Monika Fudala Halina Tarasiuk Institute of Telecommunications, Warsaw University of Technology ul. Nowowiejska 15/19, 00-665 Warsaw,
Network Protection Design for MPLS Networks
 Network Protection Design for MPLS Networks Gaurav Agrawal, Dijiang Huang, Deep Medhi Computer Science and Electrical Engineering Department University of Missouri-Kansas City, MO 64110, USA Computer Science
Network Protection Design for MPLS Networks Gaurav Agrawal, Dijiang Huang, Deep Medhi Computer Science and Electrical Engineering Department University of Missouri-Kansas City, MO 64110, USA Computer Science
PERFORMANCE ANALYSIS OF AF IN CONSIDERING LINK UTILISATION BY SIMULATION WITH DROP-TAIL
 I.J.E.M.S., VOL.2 (4) 2011: 221-228 ISSN 2229-600X PERFORMANCE ANALYSIS OF AF IN CONSIDERING LINK UTILISATION BY SIMULATION WITH DROP-TAIL Jai Kumar, Jaiswal Umesh Chandra Department of Computer Science
I.J.E.M.S., VOL.2 (4) 2011: 221-228 ISSN 2229-600X PERFORMANCE ANALYSIS OF AF IN CONSIDERING LINK UTILISATION BY SIMULATION WITH DROP-TAIL Jai Kumar, Jaiswal Umesh Chandra Department of Computer Science
Call Admission Control in IP networks with QoS support
 Call Admission Control in IP networks with QoS support Susana Sargento, Rui Valadas and Edward Knightly Instituto de Telecomunicações, Universidade de Aveiro, P-3810 Aveiro, Portugal ECE Department, Rice
Call Admission Control in IP networks with QoS support Susana Sargento, Rui Valadas and Edward Knightly Instituto de Telecomunicações, Universidade de Aveiro, P-3810 Aveiro, Portugal ECE Department, Rice
A host selection model for a distributed bandwidth broker
 A host selection model for a distributed bandwidth broker Christos Bouras Dimitris Primpas Research Academic Computer Technology Institute, Ν.Κazantzaki Str., Patras University 26500 Rion, Patras, Greece
A host selection model for a distributed bandwidth broker Christos Bouras Dimitris Primpas Research Academic Computer Technology Institute, Ν.Κazantzaki Str., Patras University 26500 Rion, Patras, Greece
Adaptive-Weighted Packet Scheduling for Premium Service
 -Weighted Packet Scheduling for Premium Service Haining Wang Chia Shen Kang G. Shin The University of Michigan Mitsubishi Electric Research Laboratory Ann Arbor, MI 489 Cambridge, MA 239 hxw,kgshin @eecs.umich.edu
-Weighted Packet Scheduling for Premium Service Haining Wang Chia Shen Kang G. Shin The University of Michigan Mitsubishi Electric Research Laboratory Ann Arbor, MI 489 Cambridge, MA 239 hxw,kgshin @eecs.umich.edu
A DiffServ IntServ Integrated QoS Provision Approach in BRAHMS Satellite System
 A DiffServ IntServ Integrated QoS Provision Approach in BRAHMS Satellite System Guido Fraietta 1, Tiziano Inzerilli 2, Valerio Morsella 3, Dario Pompili 4 University of Rome La Sapienza, Dipartimento di
A DiffServ IntServ Integrated QoS Provision Approach in BRAHMS Satellite System Guido Fraietta 1, Tiziano Inzerilli 2, Valerio Morsella 3, Dario Pompili 4 University of Rome La Sapienza, Dipartimento di
Analysis of the interoperation of the Integrated Services and Differentiated Services Architectures
 Analysis of the interoperation of the Integrated Services and Differentiated Services Architectures M. Fabiano P.S. and M.A. R. Dantas Departamento da Ciência da Computação, Universidade de Brasília, 70.910-970
Analysis of the interoperation of the Integrated Services and Differentiated Services Architectures M. Fabiano P.S. and M.A. R. Dantas Departamento da Ciência da Computação, Universidade de Brasília, 70.910-970
Grandstream Networks, Inc. GWN7000 QoS - VoIP Traffic Management
 Grandstream Networks, Inc. GWN7000 QoS - VoIP Traffic Management Table of Contents INTRODUCTION... 4 DSCP CLASSIFICATION... 5 QUALITY OF SERVICE ON GWN7000... 6 USING QOS TO PRIORITIZE VOIP TRAFFIC...
Grandstream Networks, Inc. GWN7000 QoS - VoIP Traffic Management Table of Contents INTRODUCTION... 4 DSCP CLASSIFICATION... 5 QUALITY OF SERVICE ON GWN7000... 6 USING QOS TO PRIORITIZE VOIP TRAFFIC...
HSCN Quality of Service (QoS) Policy
 HSCN Quality of Service (QoS) Policy Published March 2018 Copyright 2018 Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
HSCN Quality of Service (QoS) Policy Published March 2018 Copyright 2018 Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Ahmed Benallegue RMDCN workshop on the migration to IP/VPN 1/54
 MPLS Technology Overview Ahmed Benallegue A.Benallegue@ecmwf.int RMDCN workshop on the migration to IP/VPN 1/54 Plan 1. MPLS basics 2. The MPLS approach 3. Label distribution RSVP-TE 4. Traffic Engineering
MPLS Technology Overview Ahmed Benallegue A.Benallegue@ecmwf.int RMDCN workshop on the migration to IP/VPN 1/54 Plan 1. MPLS basics 2. The MPLS approach 3. Label distribution RSVP-TE 4. Traffic Engineering
Quality of Service in Ultrabroadband models
 Quality of Service in Ultrabroadband models Elias Aravantinos ICT Consultant, CITI Managing Director, Exelixisnet earavantinos@exelixisnet.com April 4, 2008 TELECOM ParisTech Contents 1 2 3 4 UBB & QoS
Quality of Service in Ultrabroadband models Elias Aravantinos ICT Consultant, CITI Managing Director, Exelixisnet earavantinos@exelixisnet.com April 4, 2008 TELECOM ParisTech Contents 1 2 3 4 UBB & QoS
Resilience-Differentiated QoS Extensions to RSVP and DiffServ to Signal End-to-End IP Resilience Requirements
 Resilience-Differentiated QoS Extensions to RSVP and DiffServ to Signal End-to-End IP Resilience Requirements Achim Autenrieth (1) *, Andreas Kirstädter (2) (1) Munich University of Technology Institute
Resilience-Differentiated QoS Extensions to RSVP and DiffServ to Signal End-to-End IP Resilience Requirements Achim Autenrieth (1) *, Andreas Kirstädter (2) (1) Munich University of Technology Institute
Problems with IntServ. EECS 122: Introduction to Computer Networks Differentiated Services (DiffServ) DiffServ (cont d)
 Problems with IntServ EECS 122: Introduction to Computer Networks Differentiated Services (DiffServ) Computer Science Division Department of Electrical Engineering and Computer Sciences University of California,
Problems with IntServ EECS 122: Introduction to Computer Networks Differentiated Services (DiffServ) Computer Science Division Department of Electrical Engineering and Computer Sciences University of California,
Internetworking with Different QoS Mechanism Environments
 Internetworking with Different QoS Mechanism Environments ERICA BUSSIKI FIGUEIREDO, PAULO ROBERTO GUARDIEIRO Laboratory of Computer Networks, Faculty of Electrical Engineering Federal University of Uberlândia
Internetworking with Different QoS Mechanism Environments ERICA BUSSIKI FIGUEIREDO, PAULO ROBERTO GUARDIEIRO Laboratory of Computer Networks, Faculty of Electrical Engineering Federal University of Uberlândia
MQC Hierarchical Queuing with 3 Level Scheduler
 MQC Hierarchical Queuing with 3 Level Scheduler The MQC Hierarchical Queuing with 3 Level Scheduler feature provides a flexible packet scheduling and queuing system in which you can specify how excess
MQC Hierarchical Queuing with 3 Level Scheduler The MQC Hierarchical Queuing with 3 Level Scheduler feature provides a flexible packet scheduling and queuing system in which you can specify how excess
IP Premium Agenda. - Status of IP Premium definition. - open issues - general - technical. - What s next. M. Campanella - TF-TNG - Prague - 2 Apr 2001
 IP Premium Agenda - Status of IP Premium definition - open issues - general - technical - What s next 1 IP Premium status - Diffserv Architecture - Expedited Forwarding Per Hop Behavior - manual provisioning
IP Premium Agenda - Status of IP Premium definition - open issues - general - technical - What s next 1 IP Premium status - Diffserv Architecture - Expedited Forwarding Per Hop Behavior - manual provisioning
Basics (cont.) Characteristics of data communication technologies OSI-Model
 48 Basics (cont.) Characteristics of data communication technologies OSI-Model Topologies Packet switching / Circuit switching Medium Access Control (MAC) mechanisms Coding Quality of Service (QoS) 49
48 Basics (cont.) Characteristics of data communication technologies OSI-Model Topologies Packet switching / Circuit switching Medium Access Control (MAC) mechanisms Coding Quality of Service (QoS) 49
Real-Time Protocol (RTP)
 Real-Time Protocol (RTP) Provides standard packet format for real-time application Typically runs over UDP Specifies header fields below Payload Type: 7 bits, providing 128 possible different types of
Real-Time Protocol (RTP) Provides standard packet format for real-time application Typically runs over UDP Specifies header fields below Payload Type: 7 bits, providing 128 possible different types of
Quality of Service Mechanism for MANET using Linux Semra Gulder, Mathieu Déziel
 Quality of Service Mechanism for MANET using Linux Semra Gulder, Mathieu Déziel Semra.gulder@crc.ca, mathieu.deziel@crc.ca Abstract: This paper describes a QoS mechanism suitable for Mobile Ad Hoc Networks
Quality of Service Mechanism for MANET using Linux Semra Gulder, Mathieu Déziel Semra.gulder@crc.ca, mathieu.deziel@crc.ca Abstract: This paper describes a QoS mechanism suitable for Mobile Ad Hoc Networks
An Efficient Dynamic Bandwidth Allocation Algorithm for Quality of Service Networks
 An Efficient Dynamic Bandwidth Allocation Algorithm for Quality of Service Networks J. Elias 1, F. Martignon 2, and A. Capone 3 1 University of Paris 6, LIP6 Laboratory, 8 rue du Capitaine Scott, 75015,
An Efficient Dynamic Bandwidth Allocation Algorithm for Quality of Service Networks J. Elias 1, F. Martignon 2, and A. Capone 3 1 University of Paris 6, LIP6 Laboratory, 8 rue du Capitaine Scott, 75015,
QoS experiences in native IPv6 networks
 INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT Int. J. Network Mgmt (2008) Published online in Wiley InterScience ().695 QoS experiences in native IPv6 networks Athanassios Liakopoulos 1,2, Dimitrios Kalogeras
INTERNATIONAL JOURNAL OF NETWORK MANAGEMENT Int. J. Network Mgmt (2008) Published online in Wiley InterScience ().695 QoS experiences in native IPv6 networks Athanassios Liakopoulos 1,2, Dimitrios Kalogeras
CSE 461 Quality of Service. David Wetherall
 CSE 461 Quality of Service David Wetherall djw@cs.washington.edu QOS Focus: How to provide better than best effort Fair queueing Application Application needs Transport Traffic shaping Guarantees IntServ
CSE 461 Quality of Service David Wetherall djw@cs.washington.edu QOS Focus: How to provide better than best effort Fair queueing Application Application needs Transport Traffic shaping Guarantees IntServ
QoS Performance Analysis in Deployment of DiffServ-aware MPLS Traffic Engineering
 Eighth ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing QoS Performance Analysis in Deployment of DiffServ-aware MPLS Traffic
Eighth ACIS International Conference on Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing QoS Performance Analysis in Deployment of DiffServ-aware MPLS Traffic
QoS Experience on European Backbone
 QoS Experience on European Backbone TNC 2003, Zabgreb (Croatia), 20-05-2003 Nicolas Simar, Network Engineer DANTE Agenda GÉANT Services on GÉANT Premium IP Less than Best Effort Queuing on GÉANT and status
QoS Experience on European Backbone TNC 2003, Zabgreb (Croatia), 20-05-2003 Nicolas Simar, Network Engineer DANTE Agenda GÉANT Services on GÉANT Premium IP Less than Best Effort Queuing on GÉANT and status
QoS Technology White Paper
 QoS Technology White Paper Keywords: QoS, service model, IntServ, DiffServ, congestion management, congestion avoidance, queuing technology, traffic policing, traffic shaping, link efficiency mechanism.
QoS Technology White Paper Keywords: QoS, service model, IntServ, DiffServ, congestion management, congestion avoidance, queuing technology, traffic policing, traffic shaping, link efficiency mechanism.
Multimedia Networking. Network Support for Multimedia Applications
 Multimedia Networking Network Support for Multimedia Applications Protocols for Real Time Interactive Applications Differentiated Services (DiffServ) Per Connection Quality of Services Guarantees (IntServ)
Multimedia Networking Network Support for Multimedia Applications Protocols for Real Time Interactive Applications Differentiated Services (DiffServ) Per Connection Quality of Services Guarantees (IntServ)
Internet Services & Protocols. Quality of Service Architecture
 Department of Computer Science Institute for System Architecture, Chair for Computer Networks Internet Services & Protocols Quality of Service Architecture Dr.-Ing. Stephan Groß Room: INF 3099 E-Mail:
Department of Computer Science Institute for System Architecture, Chair for Computer Networks Internet Services & Protocols Quality of Service Architecture Dr.-Ing. Stephan Groß Room: INF 3099 E-Mail:
Topic 4b: QoS Principles. Chapter 9 Multimedia Networking. Computer Networking: A Top Down Approach
 Topic 4b: QoS Principles Chapter 9 Computer Networking: A Top Down Approach 7 th edition Jim Kurose, Keith Ross Pearson/Addison Wesley April 2016 9-1 Providing multiple classes of service thus far: making
Topic 4b: QoS Principles Chapter 9 Computer Networking: A Top Down Approach 7 th edition Jim Kurose, Keith Ross Pearson/Addison Wesley April 2016 9-1 Providing multiple classes of service thus far: making
CSE 123b Communications Software
 CSE 123b Communications Software Spring 2002 Lecture 10: Quality of Service Stefan Savage Today s class: Quality of Service What s wrong with Best Effort service? What kinds of service do applications
CSE 123b Communications Software Spring 2002 Lecture 10: Quality of Service Stefan Savage Today s class: Quality of Service What s wrong with Best Effort service? What kinds of service do applications
IP Premium Agenda. - Services specification and implementation discussion. - Qos Parameters. M. Campanella - TF-TNG - Münster 7 feb 2001
 IP Premium Agenda - Services specification and implementation discussion - Qos Parameters 1 Géant QoS Services Specifications Mauro Campanella Tiziana Ferrari Mauro.Campanella@mi.infn.it Tiziana.Ferrari@cnaf.infn.it
IP Premium Agenda - Services specification and implementation discussion - Qos Parameters 1 Géant QoS Services Specifications Mauro Campanella Tiziana Ferrari Mauro.Campanella@mi.infn.it Tiziana.Ferrari@cnaf.infn.it
Differentiated Services
 Diff-Serv 1 Differentiated Services QoS Problem Diffserv Architecture Per hop behaviors Diff-Serv 2 Problem: QoS Need a mechanism for QoS in the Internet Issues to be resolved: Indication of desired service
Diff-Serv 1 Differentiated Services QoS Problem Diffserv Architecture Per hop behaviors Diff-Serv 2 Problem: QoS Need a mechanism for QoS in the Internet Issues to be resolved: Indication of desired service
PERFORMANCE ANALYSIS OF AF IN CONSIDERING LINK
 I.J.E.M.S., VOL.2 (3) 211: 163-171 ISSN 2229-6X PERFORMANCE ANALYSIS OF AF IN CONSIDERING LINK UTILISATION BY SIMULATION Jai Kumar and U.C. Jaiswal Department of Computer Science and Engineering, Madan
I.J.E.M.S., VOL.2 (3) 211: 163-171 ISSN 2229-6X PERFORMANCE ANALYSIS OF AF IN CONSIDERING LINK UTILISATION BY SIMULATION Jai Kumar and U.C. Jaiswal Department of Computer Science and Engineering, Madan
Differentiated Services
 1 Differentiated Services QoS Problem Diffserv Architecture Per hop behaviors 2 Problem: QoS Need a mechanism for QoS in the Internet Issues to be resolved: Indication of desired service Definition of
1 Differentiated Services QoS Problem Diffserv Architecture Per hop behaviors 2 Problem: QoS Need a mechanism for QoS in the Internet Issues to be resolved: Indication of desired service Definition of
4A0-107 Q&As. Alcatel-Lucent Quality of Service. Pass Alcatel-Lucent 4A0-107 Exam with 100% Guarantee
 4A0-107 Q&As Alcatel-Lucent Quality of Service Pass Alcatel-Lucent 4A0-107 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money Back
4A0-107 Q&As Alcatel-Lucent Quality of Service Pass Alcatel-Lucent 4A0-107 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money Back
Peer to Peer Infrastructure : QoS enabled traffic prioritization. Mary Barnes Bill McCormick
 Peer to Peer Infrastructure : QoS enabled traffic prioritization Mary Barnes (mary.barnes@nortel.com) Bill McCormick (billmcc@nortel.com) p2pi - QoS 1/24/09 1 Overview!! Discuss the mechanisms and implications
Peer to Peer Infrastructure : QoS enabled traffic prioritization Mary Barnes (mary.barnes@nortel.com) Bill McCormick (billmcc@nortel.com) p2pi - QoS 1/24/09 1 Overview!! Discuss the mechanisms and implications
QoS Services with Dynamic Packet State
 QoS Services with Dynamic Packet State Ion Stoica Carnegie Mellon University (joint work with Hui Zhang and Scott Shenker) Today s Internet Service: best-effort datagram delivery Architecture: stateless
QoS Services with Dynamic Packet State Ion Stoica Carnegie Mellon University (joint work with Hui Zhang and Scott Shenker) Today s Internet Service: best-effort datagram delivery Architecture: stateless
Active Resource Management for The Differentiated Services Environment
 Abstract Active Resource Management for The Differentiated Services Environment Ananthanarayanan Ramanathan, Manish Parashar The Applied Software Systems Laboratory Department of Electrical And Computer
Abstract Active Resource Management for The Differentiated Services Environment Ananthanarayanan Ramanathan, Manish Parashar The Applied Software Systems Laboratory Department of Electrical And Computer
Dynamic Fair Bandwidth Allocation for DiffServ Classes
 Dynamic Fair Bandwidth Allocation for DiffServ Classes Hideyuki Shimonishi Ichinoshin Maki Tutomu Murase Masayuki Murata Networking Research Labs, NEC Corporation Graduate School of Engineering Science,
Dynamic Fair Bandwidth Allocation for DiffServ Classes Hideyuki Shimonishi Ichinoshin Maki Tutomu Murase Masayuki Murata Networking Research Labs, NEC Corporation Graduate School of Engineering Science,
Deploying MPLS & DiffServ
 Deploying MPLS & DiffServ Thomas Telkamp Director, Data Architecture & Technology Global Crossing Telecommunications, Inc. telkamp@gblx.net MPLS and DiffServ technologies are getting a lot of attention
Deploying MPLS & DiffServ Thomas Telkamp Director, Data Architecture & Technology Global Crossing Telecommunications, Inc. telkamp@gblx.net MPLS and DiffServ technologies are getting a lot of attention
Advanced Mechanisms for Available Rate Usage in ATM and Differentiated Services Networks
 Advanced Mechanisms for Available Rate Usage in ATM and Differentiated Services Networks Roland Bless, Dirk Holzhausen, Hartmut Ritter, Klaus Wehrle Institute of Telematics, University of Karlsruhe Zirkel
Advanced Mechanisms for Available Rate Usage in ATM and Differentiated Services Networks Roland Bless, Dirk Holzhausen, Hartmut Ritter, Klaus Wehrle Institute of Telematics, University of Karlsruhe Zirkel
Core-Stateless Proportional Fair Queuing for AF Traffic
 Core-Stateless Proportional Fair Queuing for AF Traffic Gang Cheng, Kai Xu, Ye Tian, and Nirwan Ansari Advanced Networking Laboratory, Department of Electrical and Computer Engineering, New Jersey Institute
Core-Stateless Proportional Fair Queuing for AF Traffic Gang Cheng, Kai Xu, Ye Tian, and Nirwan Ansari Advanced Networking Laboratory, Department of Electrical and Computer Engineering, New Jersey Institute
A scalable architecture for end-to-end QoS provisioning
 Computer Communications 27 (2004) 1330 1340 www.elsevier.com/locate/comcom A scalable architecture for end-to-end QoS provisioning Spiridon Bakiras*, Victor O.K. Li Department of Electrical and Electronic
Computer Communications 27 (2004) 1330 1340 www.elsevier.com/locate/comcom A scalable architecture for end-to-end QoS provisioning Spiridon Bakiras*, Victor O.K. Li Department of Electrical and Electronic
A DiffServ transport network to bring 3G access to villages in the Amazon forest: a case study
 A DiffServ transport network to bring 3G access to villages in the Amazon forest: a case study based on the EC FP7 project Wireless Technologies for isolated rural communities in developing countries based
A DiffServ transport network to bring 3G access to villages in the Amazon forest: a case study based on the EC FP7 project Wireless Technologies for isolated rural communities in developing countries based
Telecommunication Services Engineering Lab. Roch H. Glitho
 1 Quality of Services 1. Terminology 2. Technologies 2 Terminology Quality of service Ability to control network performance in order to meet application and/or end-user requirements Examples of parameters
1 Quality of Services 1. Terminology 2. Technologies 2 Terminology Quality of service Ability to control network performance in order to meet application and/or end-user requirements Examples of parameters
Virtual Time Reference System: A Unifying Scheduling Framework for Scalable Support of Guaranteed Services
 2684 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 18, NO. 12, DECEMBER 2000 Virtual Time Reference System: A Unifying Scheduling Framework for Scalable Support of Guaranteed Services Zhi-Li Zhang,
2684 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 18, NO. 12, DECEMBER 2000 Virtual Time Reference System: A Unifying Scheduling Framework for Scalable Support of Guaranteed Services Zhi-Li Zhang,
INTEGRATED SERVICES AND DIFFERENTIATED SERVICES: A FUNCTIONAL COMPARISON
 INTEGRATED SERVICES AND DIFFERENTIATED SERVICES: A FUNCTIONAL COMPARON Franco Tommasi, Simone Molendini Faculty of Engineering, University of Lecce, Italy e-mail: franco.tommasi@unile.it, simone.molendini@unile.it
INTEGRATED SERVICES AND DIFFERENTIATED SERVICES: A FUNCTIONAL COMPARON Franco Tommasi, Simone Molendini Faculty of Engineering, University of Lecce, Italy e-mail: franco.tommasi@unile.it, simone.molendini@unile.it
Traffic Engineering 2: Layer 2 Prioritisation - CoS (Class of Service)
 Published on Jisc community (https://community.jisc.ac.uk) Home > Network and technology service docs > Vscene > Technical details > Products > H.323 > Guide to reliable H.323 campus networks > Traffic
Published on Jisc community (https://community.jisc.ac.uk) Home > Network and technology service docs > Vscene > Technical details > Products > H.323 > Guide to reliable H.323 campus networks > Traffic
BW Protection. 2002, Cisco Systems, Inc. All rights reserved.
 BW Protection 2002, Cisco Systems, Inc. All rights reserved. 1 Cisco MPLS - Traffic Engineering for VPNs Amrit Hanspal Sr. Product Manager MPLS & QoS Internet Technologies Division 2 Agenda MPLS Fundamentals
BW Protection 2002, Cisco Systems, Inc. All rights reserved. 1 Cisco MPLS - Traffic Engineering for VPNs Amrit Hanspal Sr. Product Manager MPLS & QoS Internet Technologies Division 2 Agenda MPLS Fundamentals
Best Practices for Determining the Traffic Matrix in IP Networks
 Best Practices for Determining the Traffic Matrix in IP Networks Apricot 2005 - Kyoto, Japan Thursday February 24, 2005 Internet Routing and Backbone Operations Session C5-4 Thomas Telkamp, Cariden Technologies,
Best Practices for Determining the Traffic Matrix in IP Networks Apricot 2005 - Kyoto, Japan Thursday February 24, 2005 Internet Routing and Backbone Operations Session C5-4 Thomas Telkamp, Cariden Technologies,
Internet QoS : A Big Picture
 Internet QoS : A Big Picture Xipeng Xiao and Lionel M. Ni, M, Michigan State University IEEE Network, March/April 1999 Oct 25, 2006 Jaekyu Cho Outline Introduction IntServ/RSVP DiffServ MPLS Traffic Engineering/CBR
Internet QoS : A Big Picture Xipeng Xiao and Lionel M. Ni, M, Michigan State University IEEE Network, March/April 1999 Oct 25, 2006 Jaekyu Cho Outline Introduction IntServ/RSVP DiffServ MPLS Traffic Engineering/CBR
Several issues and problems need to be addressed prior to implementing differentiated services for offering real QoS based IP services. Traffic engine
 Modeling and Analysis of Internet Differentiated Services Traffic Muckai K Girish a and Jian-Qiang Hu b asbc Technology Resources, Inc. 4698 Willow Woad Pleasanton, California 94588, USA bdepartment of
Modeling and Analysis of Internet Differentiated Services Traffic Muckai K Girish a and Jian-Qiang Hu b asbc Technology Resources, Inc. 4698 Willow Woad Pleasanton, California 94588, USA bdepartment of
Integrating Network QoS and Web QoS to Provide End-to-End QoS
 Integrating Network QoS and Web QoS to Provide End-to-End QoS Wang Fei Wang Wen-dong Li Yu-hong Chen Shan-zhi State Key Lab of Networking and Switching, Beijing University of Posts & Telecommunications,
Integrating Network QoS and Web QoS to Provide End-to-End QoS Wang Fei Wang Wen-dong Li Yu-hong Chen Shan-zhi State Key Lab of Networking and Switching, Beijing University of Posts & Telecommunications,
Lesson 14: QoS in IP Networks: IntServ and DiffServ
 Slide supporting material Lesson 14: QoS in IP Networks: IntServ and DiffServ Giovanni Giambene Queuing Theory and Telecommunications: Networks and Applications 2nd edition, Springer All rights reserved
Slide supporting material Lesson 14: QoS in IP Networks: IntServ and DiffServ Giovanni Giambene Queuing Theory and Telecommunications: Networks and Applications 2nd edition, Springer All rights reserved
A. Charny Delay Bounds In a Network with Aggregate Scheduling. Draft Version 4. 2/29/00. Delay Bounds In a Network With Aggregate Scheduling 1
 A. Charny Delay Bounds In a Network with Aggregate Scheduling. Version 4. 2/29/00 Delay Bounds In a Network With Aggregate Scheduling Anna Charny acharny@cisco.com Abstract A large number of products implementing
A. Charny Delay Bounds In a Network with Aggregate Scheduling. Version 4. 2/29/00 Delay Bounds In a Network With Aggregate Scheduling Anna Charny acharny@cisco.com Abstract A large number of products implementing
Service-to-Service Mapping of Differentiated Services to the ABR Service of ATM in Edge/Core Networks
 Service-to-Service Mapping of Differentiated Services to the ABR Service of ATM in Edge/Core Networks Deepak Sreenivasamurthy Masters Thesis M.S. Computer Engineering University of Kansas October 22, 1999
Service-to-Service Mapping of Differentiated Services to the ABR Service of ATM in Edge/Core Networks Deepak Sreenivasamurthy Masters Thesis M.S. Computer Engineering University of Kansas October 22, 1999
Cross-Layer QoS Support in the IEEE Mesh Network
 Cross-Layer QoS Support in the IEEE 802.16 Mesh Network Chun-Chuan Yang, Yi-Ting Mai and Liang-Chi Tsai Multimedia and Communications Laboratory Department of Computer Science and Information Engineering
Cross-Layer QoS Support in the IEEE 802.16 Mesh Network Chun-Chuan Yang, Yi-Ting Mai and Liang-Chi Tsai Multimedia and Communications Laboratory Department of Computer Science and Information Engineering
Principles. IP QoS DiffServ. Agenda. Principles. L74 - IP QoS Differentiated Services Model. L74 - IP QoS Differentiated Services Model
 Principles IP QoS DiffServ Differentiated Services Architecture DSCP, CAR Integrated Services Model does not scale well flow based traffic overhead (RSVP messages) routers must maintain state information
Principles IP QoS DiffServ Differentiated Services Architecture DSCP, CAR Integrated Services Model does not scale well flow based traffic overhead (RSVP messages) routers must maintain state information
Quality of Service In Data Networks
 Quality of Service In Data Networks The Ohio State University Columbus, OH 43210 Jain@CIS.Ohio-State.Edu These slides are available on-line at http://www.cis.ohio-state.edu/~jain/cis788-99/ 1 Overview
Quality of Service In Data Networks The Ohio State University Columbus, OH 43210 Jain@CIS.Ohio-State.Edu These slides are available on-line at http://www.cis.ohio-state.edu/~jain/cis788-99/ 1 Overview
Multicast and Quality of Service. Internet Technologies and Applications
 Multicast and Quality of Service Internet Technologies and Applications Aims and Contents Aims Introduce the multicast and the benefits it offers Explain quality of service and basic techniques for delivering
Multicast and Quality of Service Internet Technologies and Applications Aims and Contents Aims Introduce the multicast and the benefits it offers Explain quality of service and basic techniques for delivering
Trafffic Engineering 2015/16 1
 Traffic Engineering 2015/2016 Traffic Engineering: from ATM to MPLS fernando.silva@tecnico.ulisboa.pt Instituto Superior Técnico Trafffic Engineering 2015/16 1 Outline Traffic Engineering revisited Traffic
Traffic Engineering 2015/2016 Traffic Engineering: from ATM to MPLS fernando.silva@tecnico.ulisboa.pt Instituto Superior Técnico Trafffic Engineering 2015/16 1 Outline Traffic Engineering revisited Traffic
Configuring Modular QoS on Link Bundles
 A link bundle is a group of one or more ports that are aggregated together and treated as a single link. This module describes QoS on link bundles. Line Card, SIP, and SPA Support Feature ASR 9000 Ethernet
A link bundle is a group of one or more ports that are aggregated together and treated as a single link. This module describes QoS on link bundles. Line Card, SIP, and SPA Support Feature ASR 9000 Ethernet
VoIP Protocols and QoS
 Announcements I. Times have been posted for demo slots VoIP Protocols and QoS II. HW5 and HW6 solutions have been posted HW6 being graded Internet Protocols CSC / ECE 573 Fall, 2005 N. C. State University
Announcements I. Times have been posted for demo slots VoIP Protocols and QoS II. HW5 and HW6 solutions have been posted HW6 being graded Internet Protocols CSC / ECE 573 Fall, 2005 N. C. State University
Minimum Interference Routing of Bandwidth Guaranteed Tunnels with MPLS Traffic Engineering Applications
 2566 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 18, NO. 12, DECEMBER 2000 Minimum Interference Routing of Bandwidth Guaranteed Tunnels with MPLS Traffic Engineering Applications Koushik Kar,
2566 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 18, NO. 12, DECEMBER 2000 Minimum Interference Routing of Bandwidth Guaranteed Tunnels with MPLS Traffic Engineering Applications Koushik Kar,
Modular Quality of Service Overview on Cisco IOS XR Software
 Modular Quality of Service Overview on Cisco IOS XR Software Quality of Service (QoS) is the technique of prioritizing traffic flows and providing preferential forwarding for higher-priority packets. The
Modular Quality of Service Overview on Cisco IOS XR Software Quality of Service (QoS) is the technique of prioritizing traffic flows and providing preferential forwarding for higher-priority packets. The
CSCD 433/533 Advanced Networks Spring Lecture 22 Quality of Service
 CSCD 433/533 Advanced Networks Spring 2016 Lecture 22 Quality of Service 1 Topics Quality of Service (QOS) Defined Properties Integrated Service Differentiated Service 2 Introduction Problem Overview Have
CSCD 433/533 Advanced Networks Spring 2016 Lecture 22 Quality of Service 1 Topics Quality of Service (QOS) Defined Properties Integrated Service Differentiated Service 2 Introduction Problem Overview Have
Distributed QoS Routing for Backbone Overlay Networks
 Distributed QoS Routing for Backbone Overlay Networks Li Lao 1, Swapna S. Gokhale 2, and Jun-Hong Cui 2 1 Computer Science Dept., University of California, Los Angeles, CA 90095 2 Computer Science & Engineering
Distributed QoS Routing for Backbone Overlay Networks Li Lao 1, Swapna S. Gokhale 2, and Jun-Hong Cui 2 1 Computer Science Dept., University of California, Los Angeles, CA 90095 2 Computer Science & Engineering
Quality of Service Provisioning for Supporting Premium Services in IP Networks
 Quality of Service Provisioning for Supporting Premium Services in IP Networks P. Trimintzios, T. Baugé, G. Pavlou, L. Georgiadis, R. Egan and P. Flegkas Centre for Communication Systems Research, University
Quality of Service Provisioning for Supporting Premium Services in IP Networks P. Trimintzios, T. Baugé, G. Pavlou, L. Georgiadis, R. Egan and P. Flegkas Centre for Communication Systems Research, University
Quality of Service (QoS)
 Quality of Service (QoS) What you will learn Techniques for QoS Integrated Service (IntServ) Differentiated Services (DiffServ) MPLS QoS Design Principles 1/49 QoS in the Internet Paradigm IP over everything
Quality of Service (QoS) What you will learn Techniques for QoS Integrated Service (IntServ) Differentiated Services (DiffServ) MPLS QoS Design Principles 1/49 QoS in the Internet Paradigm IP over everything
Providing Bandwidth Guarantees with OpenFlow
 Providing Bandwidth Guarantees with OpenFlow Hedi Krishna, Niels L. M. van Adrichem, and Fernando A. Kuipers Network Architectures and Services, Delft University of Technology Mekelweg 4, 2628 CD Delft,
Providing Bandwidth Guarantees with OpenFlow Hedi Krishna, Niels L. M. van Adrichem, and Fernando A. Kuipers Network Architectures and Services, Delft University of Technology Mekelweg 4, 2628 CD Delft,
Improving QOS in IP Networks. Principles for QOS Guarantees
 Improving QOS in IP Networks Thus far: making the best of best effort Future: next generation Internet with QoS guarantees RSVP: signaling for resource reservations Differentiated Services: differential
Improving QOS in IP Networks Thus far: making the best of best effort Future: next generation Internet with QoS guarantees RSVP: signaling for resource reservations Differentiated Services: differential
