Politecnico di Torino TSR/CNTS, PRL, PAR. Tutorial. User guide and helpful tips. Fulvio Risso and Marco Leogrande
|
|
|
- Candice Harris
- 5 years ago
- Views:
Transcription
1 Politecnico di Torino TSR/CNTS, PRL, PAR Tutorial User guide and helpful tips Fulvio Risso and Marco Leogrande November 28, 2018
2 Contents 1 Introduction How it works Network issues What do you need Connecting to Dyn@NG Dyn@NG servers Dyn@NG Politecnico di Torino Registration Dyn@NG Politecnico di Torino Login User Interface Overview File Menu Network Menu Device Library Network Window Console window Capture Window Load configuration from file Simulate your first topology Verify that the network operates correctly Make your first capture Simulate a more complex topology 16 5 IOS command line configuration tips Configuration modes Command shortening and online help Console timeout Connecting a router to a switch Troubleshooting Physical links appear not to be working
3 License This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License. You are free: to Share: to copy, distribute and transmit the work to Remix: to adapt the work Under the following conditions: Attribution: you must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). Noncommercial: you may not use this work for commercial purposes. Share Alike: if you alter, transform, or build upon this work, you may distribute the resulting work only under the same or similar license to this one. More information on the Creative Commons website ( Acknowledgments The authors would like to thank all the people who contributed to this project. Particularly, the authors would like to thank Marco Papa, Daniele Aramu, Matteo Avalle, Paolo Pettinato and Danilo Giordano. 3
4 1 Introduction This tutorial aims at providing an overview of the functionalities of the virtual networking laboratory. It will also present how to access the software functionalities and it will introduce users to the main features of the system. Server-side installation an some more details on the internals are available in separate documents enclosed in the source pack. From the end-user perspective, the main component is the web interface (the graphical network simulator), which enables the simulation of complex networks featuring some selected Cisco devices. In fact, the project is basically a front-end to Dynamips, Dynagen and Qemu and can emulate the behavior of some selected Cisco routers using adhoc virtual machines. Some of its features, mainly the ability to capture packets on every established link, make it an ideal instrument to learn how to deal with some issues of the real life devices without actually having access to them. Dyn@NG executes the virtual machines associated to Cisco routers leveraging the user from setting up and configuring such infrastructure. Moreover, Dyn@NG enables system administrators to set up a single, powerful server to be used by many users concurrently, each one simulating its own virtual network; users do not interfere with each other and do not have to own an extremely powerful computer to run their simulations on. 1.1 How it works The Dyn@NG system is based on tranforming network devices (e.g., routers) into Virtual Machines, executed in a virtualization environment, which emulates also the network connectivity between them. As a result we are able to emulate a network, including cables, switches and routers, in a single (powerful) PC. The emulated links will be crossed by the traffic generated by the routers, and those packets can be captured and shown on screen. The virtualization environment requires each router to be associated with an operating system image; when the step dedicated to the creation of the network topology has been completed, the user can turn on (manually) the router and start a new emulation session (more details in Section 2.4.2). 1.2 Network issues Being the Dyn@NG service completely based on web technologies, users are required to have an unfiltered connection to the TCP port the server listen at. Depending on the server installation, those ports are typically ports 80 or 8080 for HTTP, 443 for HTTPS 1. Even the connections 1 Currently Dyn@NG does not provide a special and secure mechanism for the user authentication phase. For instance, if the web server is configured to use HTTP only, the password is sent in clear to the server. In order to guarantee secure communications, it is strongly advised to configure the server to work only in HTTPS. 4
5 to the consoles of the routers are web-based, featuring a special web server configuration with rewriting rules and a proxy. The software backend interfaces with Dynamips and spawns different communication ports for each virtual router and user. All these operations are then presented to the user through a unified web interface, that therefore wraps all the connections (that usually would require access to arbitrary TCP/UDP ports) over HTTP. 1.3 What do you need Dyn@NG is a web-based application that requires no additional application to be installed on the client machine in addition to a modern web browser. All the installation is done once, serverside. However, you may want to install a network sniffer (e.g., Wireshark) to analyze capture files offline; in any case, a basic interface that can visualize network captures is integrated in the Dyn@NG web interface. Due to some inconsistencies in the different browsers, Firefox is the suggested choice. For instance, Chrome has the problem that the backspace key does not cancel the last character you typed in the console, but it will allow you to navigate backward on the page history, losing all the job you have done. 5
6 2 Connecting to 2.1 servers The service is available through a web URL. Unfortunately, due to the fact that Dyn@NG is in its early stages of development, each Dyn@NG instance is a standalone service, with its local database for users, etc. Hence, in order to guarantee better scalability, the administrator can install multiple servers and customize the initial web page with a set of links toward the secondary servers. Please refer to the local Dyn@NG service administrator to have the link for your Dyn@NG service Dyn@NG Politecnico di Torino The Dyn@NG Politecnico di Torino is available at the following addresses: Due to some limitations of our network, if the user connects from outside the University it has to use port 8080 when logging in into the secondary server: A screenshot of the main page on the primary server is depicted in Figure 1. Figure 1: Main page on the primary Dyn@NG PoliTO. 2.2 Registration Guest login is not allowed in Dyn@NG; users must be registered to access to the Dyn@NG service. To register an account you have to go to Dyn@NG website and press the register button. A new will appear (a screenshot is depicted in Figure 2) that will ask you to insert Username, Password and . 6
7 Figure 2: Registration form After that the server will send you a notification to your address with the instructions (basically, a web link) needed to activate your account. Registration is free, provided that your address belongs to a set of selected academic domains. The administrator can edit this list. At present, Dyn@NG use a local database, therefore you need an account on each Dyn@NG server in order to be able to log-in. 2.3 Login If you are already registered, you just need to insert your username and password that you provided for that server. 2.4 User Interface Overview This Section present the main Dyn@NG window and the commands that are available through this GUI. A typical screenshot of the main Dyn@NG window is shown in Figure 3. Figure 3: Dyn@NG interface File Menu The File menu is the first on the top-left side of the main window and it is shown in Figure 4. In this menu you can find four options: 7
8 Figure 4: File menu New Network Topology: with this button a new empty workspace will be loaded. WARNING: All the data present in the network panel will be erased. If you want to start a new topology without losing the one you have done, save it first. Save network topology: It is possible to save the network topology you created. You can save it in Local, i.e., on your local computer (e.g., your hard disk), or Remote, i.e., on the server that you are using, as shown in Figure 5. WARNING: the configuration of the router will be lost even if the Save current router configuration checkbox is selected; unfortunately that option does not work correctly. If you want to save and reload the configuration in the future, you will have to write a file with the router commands. (See better later) Open network topology (local/remote): you can load the configuration you saved from your local computer or the server you are using. WARNING: only the network topology will be loaded, while (due to a bug) the router configuration will not be loaded. Routers will boot with the standard default configuration. Figure 5: Save interface 8
9 2.4.2 Network Menu This menu (depicted in Figure 6) is used to start, stop and reboot the devices of your network topology. This menu features the following commands: Figure 6: Network menu Start: this button is used when you want to start the devices of your network topology after creating them. It is advised to save your network topology locally on your hard disk before starting the network, so in case of errors (e.g., the one depicted in Figure 7) you will be able to load it without have to create it again manually. Sometimes there can be some problems when starting your topology. Do not worry, unfortunately this happens (some bugs are still present around). First of all try using the Retry button several times to see if the problem gets solved. If this does not work, close the start network panel. Then go back to the network menu and use the Stop button and try again to Start the network. Figure 7: Error message Stop: this button is used if you want to stop the devices of your topology. It can be used also if the Start button does not work, to release some resources that the server reserved to you at a previous time. If by using the Start button the network does not start, either, you have to go to the top-right corner, where you find Logged as: and log off. After doing this, try logging-in again in order to help the server to release the resources. Restart: this button will stop your topology, and then using it again it will start the topology. 9
10 2.4.3 Device Library This is the place where you find the devices that you can use for your exercises. (a) Switch (b) Router Figure 8: Devices Switch: this is the simplest device you can use. It is a layer-2 switch with 8 Fast Ethernet interfaces. This switch is provided as is and cannot be configured. The icon representing the switch is depicted in Figure 8(a). Router Cisco 2691: This is the main device you will use. The icon representing the switch is depicted in Figure 8(b). The default configuration for this device includes two pre-defined linecards. If you need a different linecard, you need to configure the device and change the linecard in the second slot (formally, slot #1), choosing from one among the three available. To change the linecard you need to use the configuration panel of the router; it is available by rightclicking on the router and pressing the Configure button. This will open a new window (Figure 9) where you can modify the name of the router (changing the Label value) and change the linecard for slot number 1. The three available linecards are: GT96100-FE: this is a fast Ethernet adapter and has 2 interfaces. This is only a Level 2 adapter therefore you will not be able to configure an IP address. NM-1FE-TX: this is a fast Ethernet adapter with1 interface of Level 2 and Level 3. NM-16ESW: this is a fast Ethernet adapter with 16 interfaces of Level 2. Figure 9: Configuring the additional slots of a router 10
11 2.4.4 Network Window This is the area where you will create your topology. You will do it by drag-and-dropping the routers and switches from the Device Library to this area and then linking them with the proper connection. Section 3 will present how to create the topology in this window Console window In this area you will find the icons that are associated to the consoles, which are used to control anc configure the Cisco routers you added to your topology Capture Window Figure 10: Capture window This area, depicted in Figure 10 is dedicated to the capture and analysis of the traffic generated in your topology. This area includes the following columns: CR (Capture Ready): this indicates that the link is ready and available to capture traffic. If you started correctly the network they should be green. CP (Capture in Progress): this icon will become green as soon as the capture on that link begins. It is red in case the capture is not active. Name: is the name of the link where you will capture the traffic. Dyn@NG offers the possibility to capture the traffic either on a single link, or on the entire network (represented by the fist link in the Captures window, called, in fact network ). In the last case, the list of captured packets will be available by merging of all the packets captured on all the links present in the topology. Notice that we can capture the traffic from different links and then aggregate the captured packets within the same view by using the Aggregate captures on top of the Captures window. Action: this column includes five different buttons: Start: it starts the capture on the selected link. Notice that if you use the start button of the network link, all other links will start the capture too. Stop: it stops the capture on the selected link. If you use the stop button of the network link it will stop all other capture too. 11
12 Open Capture: it shows the currently captured packets in a new windows inside the browser. Due to a bug, this feature may not always work correctly, as the windows may not show up. In this case you can download the file on your hard disk and use WireShark to show it. Download: it downloads a file containing the captured packets on the local hard disk. Notice that if you download the capture from the network link you will get a single file containing the traffic of the entire network. Cancel: not yet implemented. 2.5 Load configuration from file There is the possibility to load the configuration of a router directly from a text file. To do that first of all you need to prepare a text file with all the commands necessary to make your own configuration. Write all the commands one for each line of the file, then save it. Prepare one file for each router you need to configure. After that open the Console of the router you want to configure. Specify that you want to configure the router manually answering no to the first question and press the Load Configuration button. Select the configuration file. After a couple of seconds your configuration will be loaded. NOTICE: Remember to write all the necessary command in order to configure your router, including the additional commands to enter in configuration mode (e.g., enable and configure terminal). 12
13 3 Simulate your first topology Figure 11: Our first network topology Now we can try to create a simple network topology with two routers directly connected through a link, as depicted in Figure 11. First of all we need to create our topology. Go to the Device Library and drag and drop the Cisco 2691 router to the network window. After inserting the routers we need to create a link that connects the two devices together. To do this select the first router as the source device and click on the second router as the destination device while holding the left CTRL key (just in case you do not remember which is the correct key, when you click on the first router an help pop-up appears on the left side of the window, reminding you how to complete this procedure). A window like the one depicted in Figure 12 will be opened. Select a network adapter from the Select a slot option (e.g., 0:GT96100-FE) for both devices and then a free interface (e.g., interface 0 ). Now that the two routers are connected they will be linked and we just need to activate the virtual machines associated to the routers, which translates into the start topology command. Routers can be configured through the console only when they are active, i.e., their associated virtual machine is up and running. For starting the topology (which is required in order to enable the console), we can go to the Network Menu and press the start button. Figure 12: Router Link Form Dyn@NG uses different icons to show the status of the router. For instance, a router that is switched off is shown with a blue icon, while an active router is shown with the green icon. When the router is active, we can open the associated console window and configure the device. To configure our topology, open the console of the router R0 and press the Enter key on your keyboard a couple of times; this is a known problem, as sometimes the router prompt does not appear if you do not press Enter. If everything is ok, after some seconds you should see the following prompt on the console: 13
14 Would you like to enter the initial configuration dialog? [yes/no] Answer no to the request. You will configure the machines manually. Wait until the Router> prompt appears in the console. You need now to: Enter in privileged-mode of the router using the command enable; Enter in configuration mode using the command configure terminal 2. Now we need to select the interface we want to configure. To do that we need to use the command interface FastEthernet x/y where x is the number of the slot you chose before, and y is the number of the interface (within that slot) you used. You can also use the shortcut in fa x/y. For instance, as we choose the slot 0 and interface 0, we write the command interface FastEthernet 0/0. Now we will configure the IP address with the following commands: Command ip address no shutdown end Description Configure the IP address /24 on the selected interface. This address will become immediately active. Turn on the interface. Some interfaces of the router are turned off by default, hence it is always better to type this command although this may not be always needed. Exit from the configuration mode. Obviously, a similar configuration must be repeated on the second router. On the console of R1 you can apply do the same commands, just changing the IP address into Here a brief summary of all the commands you typed in order to configure the address on the router, where the last digit of the IP address (written as z ) will be the actual IP address of the router: enable configure terminal interface FastEthernet0/0 ip address Z no shutdown end You have now configured the interfaces on the link. 2 Notice that you can also use shortcuts such ena and conf t for those commands. More details on command line shortcuts will be given in Section
15 3.1 Verify that the network operates correctly Now that you finished your configuration you can use the ping command in order to generate a stream of 5 ICMP Echo Request and ICMP Echo Reply to verify that the network topology works and that routers can exchange traffic between them. Open the console of the router R0. Assuming that the configuration of the router is the one suggested in previous section, you just need to use the command below to ping the router R1. ping You should see a similar text appearing on each console: Router# ping Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:.!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 4/4/20 ms Router# Please note that Cisco routers tend to miss the first reply to the ping command, while the remaining four are received correctly. A missing answer is shown with the dot sign., while a successful answer is shown with the exclamation mark (! ). Therefore, if you type the ping command for the first time and the first (or, in some cases, the first two) answers are missing, nothing is wrong on your side. Vice versa, if all the five answers are negative, something is wrong in your configuration. 3.2 Make your first capture Now we can try to capture the traffic generated by the ping command. Go to the capture window and press the on the start button associated to the link L0. This will start capturing the traffic generated on that link. Now come back to the router R0 and type again the ping command as we saw before. When the ping command terminates, go back to the capture window ad press the Stop button. Now download the file using the Download button or show the captured packets directly in the web browser. Opening the capture you will see the stream of packet generated between the two routers, i.e., most likely 5 ICMP Echo Requests and 5 ICMP Echo Replies. Some additional traffic may be present, which is generated by some protocols active on the router and that are used to exchange some data on the network. For instance, the Cisco Discovery Protocol (CDP) is active by default on a Cisco device and it is used to discovery the capabilities (e.g., installed hardware, software version, etc.) of the devices present on the network. 15
16 4 Simulate a more complex topology Now that we know how to create the topology, how configure terminals and how to capture traffic we can create a little bit more complex network composed by three routers (depicted in Figure 13) and see what kind of problems we can encounter. First, stop the previous topology (which translated into the stop network command), which in fact asks the Dyn@NG server to turn off the virtual machines associated to the routers and stop emulating the network. Then go to the File menu and select the new network topology command. Now create the topology depicted in Figure 13. Figure 13: Our second network topology In order to connect the routers together, use the interfaces depicted in Figure 11. For instance, use the interface 0/0 on router R1 to connect to the interface 0/0 of router R1, and so on. Notice that the number of the interface you select is completely independent on the two routers. Now we can start the network ( start network command in the main menu) and configure the routers through the consoles. Please note that routers R0 and R2 belong to different IP networks, therefore we need to configure the necessary static routes to enable the communication between them. Open the console panel and use the following commands: R0: enable configure terminal interface FastEthernet 0/0 ip address no shutdown exit ip route exit The command ip route specifies how to reach the remote destination. The syntax of this command is the following: ip route [network address ] [netmask of the network ] [next hop ] In this case we specify that the network configured on the left interface of router R2 (i.e., ) is reachable through the next hop represented by the rightmost interface of router R1 (i.e., ). After that we can move to the configuration of R1, which has two active interfaces. 16
17 R1: enable configure terminal in fa 0/0 ip address no shutdown exit in fa 0/1 ip address no shutdown exit exit Since R1 is directly connected to both IP networks present in our topology, we do not need to specify any static routing entry. Finally we can configure R2, with a set of commands that are definitely similar to R0. R2: enable configure terminal interface FastEthernet 0/0 ip address no shutdown exit ip route exit Now the topology is ready and configured. Go to the capture panel and press the Start button on the network layer. Then, using the console of router R0, ping the router R2 using the following command: ping When the ping command terminates, stop the capture of the network link, download the capture file of all the links (included the network one). Opening them you can see how the capture of the network layer contains all the packet generated on the network, ordered by timestamp. As we can imagine the ICMP packets on this capture are duplicated due to the two links passed through to arrive to the destination. However, there are some small differences in those packets: MAC addresses at the Ethernet level will change, and the Time To Live (TTL) field in the IP packets will be different, as the second packet is forwarded through a router and hence the value of that field is decremented. 17
18 Congratulations! You have completed this tutorial. You are now able to create a simple topology, start it, configure its devices, capture exchanged packets and analyze them in Wireshark. Before going further with other tutorials, you should read the other sections of this manual, especially Section 5, called IOS command line configuration tips. They will help you to learn how to make the system work as you want. 18
19 5 IOS command line configuration tips 5.1 Configuration modes The Cisco IOS command line interface has several configuration modes. The ones you will probably use most are listed in Table 1. EXEC-mode [Router>] In this mode you are allowed to use some of the available commands. However, you are not allowed to change the configuration. This is the default mode in which you enter after connecting to the router console. Privileged mode [Router#] This is the privileged, administration mode. You are allowed to execute all the commands that do not change the configuration. You enter this mode by typing enable in the exec-mode. Global configuration mode [Router(config)#] In this mode you are allowed to change the global configuration. Changes are applied immediately. You enter this mode by typing configure terminal in the privileged mode. Interface con- In this mode you can change the configuration of figuration mode [Router(config-if)#] a specific interface. You enter this mode by typing the interface keyword followed by the interface name, e.g., interface FastEthernet0/0, or interface Vlan1000 in the global configuration mode. Table 1: Main Cisco IOS command prompt modes You can go back to the previous mode (e.g., from the global configuration mode to the privileged mode) by typing exit. If you type exit in the EXEC mode, you will be logged off the console (not a big deal, just press RETURN to get back in). A command exists that allow you to exit from any configuration mode (including all the additional configuration modes, e.g., interface configuration mode). If you type end you will jump back to the privileged mode. 5.2 Command shortening and online help When there is no ambiguity you can shorten the commands by only typing their first letters. For example, the basic IP configuration of an interface can be typed as: en conf t in fa0/0 ip addr no shut end 19
20 which is equivalent to: enable configure terminal interface fastethernet0/0 ip address no shutdown end If you are not sure whether you can shorten a command or not, press TAB after the first letters. If the command self-completes, you can use just those letters instead of the full command; otherwise you have to provide a longer hint. If TAB does not complete your command, press? (a question mark) to have a list of alternatives. Also, if you press? after a space following a command, you will receive some help about the immediately following accepted parameters. 5.3 Console timeout If a router console is inactive, after some time you will be logged out. You can then press RETURN to get back in, and you will be brought back to the EXEC prompt. If you want to avoid this annoyance, you can disable the timeout by typing: configure terminal line console 0 exec-timeout 0 0 end 5.4 Connecting a router to a switch If you connect a routed 3 interface of one router to a switched interface of another router, you will get some CDP warning messages when turning up the routed interface (switched interfaces are up by default). In this case, the above interfaces will fail to negotiate a common speed and duplex setting; this seems to be a bug in the simulator. To solve this problem, you need to disable the auto-negotiation in the routed interface and set up speed and duplex mode manually: configure terminal interface FastEthernet0/X shutdown 3 A routed interface is an interface that can accept L3 configuration commands (e.g., IP addresses). A switched interface cannot accept L3 configuration command and it act as a pure data-link interface. The type of the interfaces depends on the particular linecard installed in the router. Please refer to the specification of the linecard to detect whether your interfaces are routed or switched. 20
21 speed 100 duplex full no shutdown end WARNING: it is important that the changes are made when the interface is down. 21
22 6 Troubleshooting 6.1 Physical links appear not to be working Sometimes it may happen that not all the links are working in the topology. To check for this problem, you may launch the following command in the privileged mode: show cdp neighbors CDP is a Cisco proprietary protocol used, among other things, to discover neighboring Cisco devices. Use it to check for connectivity between routers linked to each other. On a router connected to four other machines on the interfaces Fa1/0 - Fa1/3, for example, you should obtain: Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge S - Switch, H - Host, I - IGMP, r - Repeater Device ID Local Intrfce Holdtme Capability Platform Port ID Router Fas 1/3 174 R S I 2691 Fas 1/0 Router Fas 1/1 179 R S I 2691 Fas 0/0 Router Fas 1/0 175 R S I 2691 Fas 0/0 Router Fas 1/2 172 R S I 2691 Fas 1/0 If you find persistent anomalies, you can try to restart the simulation. 22
Introduction to lab assignments with GNS3
 Politecnico di Torino TSR/CNTS, PRL, PAR Introduction to lab assignments with GNS3 User guide and helpful tips Roberto Bonafiglia, Fulvio Risso October 27, 2017 Contents 1 Requirements 4 2 Access to GNS3
Politecnico di Torino TSR/CNTS, PRL, PAR Introduction to lab assignments with GNS3 User guide and helpful tips Roberto Bonafiglia, Fulvio Risso October 27, 2017 Contents 1 Requirements 4 2 Access to GNS3
LAB THREE STATIC ROUTING
 LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
Lab Establishing and Verifying a Telnet Connection Instructor Version 2500
 Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Wireless LAN Controller Module Configuration Examples
 Wireless LAN Controller Module Configuration Examples Document ID: 70530 Contents Introduction Prerequisites Requirements Components Used Conventions Basic Configuration Example 1 Basic Configuration with
Wireless LAN Controller Module Configuration Examples Document ID: 70530 Contents Introduction Prerequisites Requirements Components Used Conventions Basic Configuration Example 1 Basic Configuration with
Basics of GNS3 and Cisco IOS
 Lab00: Objectives: Basics of GNS3 and Cisco IOS IERG4090 Lab00 P.1 Upon completion of this lab, you will be able to: - Extract a given topology GNS3 archive - Start GNS3 - Open the given topology file
Lab00: Objectives: Basics of GNS3 and Cisco IOS IERG4090 Lab00 P.1 Upon completion of this lab, you will be able to: - Extract a given topology GNS3 archive - Start GNS3 - Open the given topology file
Basic Cisco Router Configuration: Multiple Routers
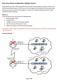 Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
CCNA 1 Chapter 2 v5.0 Exam Answers 2013
 CCNA 1 Chapter 2 v5.0 Exam Answers 2013 1. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same
CCNA 1 Chapter 2 v5.0 Exam Answers 2013 1. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same
Using Packet Tracer to Build a Network
 Using Packet Tracer to Build a Network We will be using Packet Tracer today to create the following network. This topology requires one 2811 router two 2960 switches and three workstations. Launch Packet
Using Packet Tracer to Build a Network We will be using Packet Tracer today to create the following network. This topology requires one 2811 router two 2960 switches and three workstations. Launch Packet
Exercises on IP Addressing
 Politecnico di Torino Exercises on IP Addressing Fulvio Risso November 14, 2017 License This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License. You are
Politecnico di Torino Exercises on IP Addressing Fulvio Risso November 14, 2017 License This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License. You are
Lab Troubleshooting Using traceroute Instructor Version 2500
 Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 4.2.5a Connectivity Tests Ping
 Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
CCNA 1 Chapter 2 v5.0 Exam Answers %
 CCNA 1 Chapter 2 v5.0 Exam Answers 2015 100% 1. Which two features are characteristics of flash memory? (Choose two.) Flash provides nonvolatile storage. Flash receives a copy of the IOS from RAM when
CCNA 1 Chapter 2 v5.0 Exam Answers 2015 100% 1. Which two features are characteristics of flash memory? (Choose two.) Flash provides nonvolatile storage. Flash receives a copy of the IOS from RAM when
Cisco Unified Serviceability
 Cisco Unified Serviceability Introduction, page 1 Installation, page 5 Introduction This document uses the following abbreviations to identify administration differences for these Cisco products: Unified
Cisco Unified Serviceability Introduction, page 1 Installation, page 5 Introduction This document uses the following abbreviations to identify administration differences for these Cisco products: Unified
Switch configuration. By the end of this session, you will be able to: Describe basic switch configuration methods. Configure a switch.
 By the end of this session, you will be able to: Describe basic switch configuration methods. Configure a switch. 4 SESSION OVERVIEW... 2 MANAGEMENT OPTIONS... 3 WHY CONFIGURE SWITCHES?... 4 CONSOLE PORT...
By the end of this session, you will be able to: Describe basic switch configuration methods. Configure a switch. 4 SESSION OVERVIEW... 2 MANAGEMENT OPTIONS... 3 WHY CONFIGURE SWITCHES?... 4 CONSOLE PORT...
Troubleshooting Network analysis Software communication tests and development Education. Protocols used for communication (10 seconds capture)
 Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab Capturing and Analyzing Network Traffic
 Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
Lab 1.2.2 Capturing and Analyzing Network Traffic Host Name IP Address Fa0/0 Subnet Mask IP Address S0/0/0 Subnet Mask Default Gateway RouterA 172.17.0.1 255.255.0.0 192.168.1.1 (DCE) 255.255.255.0 N/A
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Laboration 2 Troubleshooting Switching and First-Hop Redundancy
 Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Lab Configuring Static Routes Instructor Version 2500
 Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
IPv6 on routers. Computer Network Technologies and Services (CNTS) Tecnologie e Servizi di Rete (TSR)
 IPv6 on routers Computer Network Technologies and Services (CNTS) Tecnologie e Servizi di Rete (TSR) Preliminary note For this exercise you have to use the virtual routing environment prepared in a virtual
IPv6 on routers Computer Network Technologies and Services (CNTS) Tecnologie e Servizi di Rete (TSR) Preliminary note For this exercise you have to use the virtual routing environment prepared in a virtual
Configuring IP SLAs LSP Health Monitor Operations
 Configuring IP SLAs LSP Health Monitor Operations This module describes how to configure an IP Service Level Agreements (SLAs) label switched path (LSP) Health Monitor. LSP health monitors enable you to
Configuring IP SLAs LSP Health Monitor Operations This module describes how to configure an IP Service Level Agreements (SLAs) label switched path (LSP) Health Monitor. LSP health monitors enable you to
Using the Command-Line Interface
 Information About, page 1 How to Use the CLI to Configure Features, page 5 Information About Command Modes The Cisco IOS user interface is divided into many different modes. The commands available to you
Information About, page 1 How to Use the CLI to Configure Features, page 5 Information About Command Modes The Cisco IOS user interface is divided into many different modes. The commands available to you
Getting Started with CMS
 CHAPTER 3 This chapter provides these topics about the Cluster Management Suite (CMS) software: Features, page 3-2 Front Panel View, page 3-5 Topology View, page 3-11 Menus and Toolbar, page 3-16 Interaction
CHAPTER 3 This chapter provides these topics about the Cluster Management Suite (CMS) software: Features, page 3-2 Front Panel View, page 3-5 Topology View, page 3-11 Menus and Toolbar, page 3-16 Interaction
Lab Configure Cisco IOS Firewall CBAC
 Lab 3.8.3 Configure Cisco IOS Firewall CBAC Objective Scenario Topology Estimated Time: 50 minutes Number of Team Members: Two teams with four students per team. In this lab, students will complete the
Lab 3.8.3 Configure Cisco IOS Firewall CBAC Objective Scenario Topology Estimated Time: 50 minutes Number of Team Members: Two teams with four students per team. In this lab, students will complete the
Lab Troubleshooting LAN Connectivity
 Lab 9.2.4 Troubleshooting LAN Connectivity Device Host Name Interface IP Address Subnet Mask Default Gateway Switch Port R1 R1 Fast Ethernet 0/0 192.168.1.1 255.255.255.0 N/A Fast Ethernet 0/2 S1 S1 VLAN
Lab 9.2.4 Troubleshooting LAN Connectivity Device Host Name Interface IP Address Subnet Mask Default Gateway Switch Port R1 R1 Fast Ethernet 0/0 192.168.1.1 255.255.255.0 N/A Fast Ethernet 0/2 S1 S1 VLAN
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Lab - Using Wireshark to Examine TCP and UDP Captures
 Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Topology Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of a PC with Internet access. Topology Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session.
Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards
 Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards This document provides configuration tasks for the 4-port Cisco HWIC-4ESW and the 9-port Cisco HWIC-D-9ESW EtherSwitch high-speed WAN interface
Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards This document provides configuration tasks for the 4-port Cisco HWIC-4ESW and the 9-port Cisco HWIC-D-9ESW EtherSwitch high-speed WAN interface
LAB 3 Basic Switch Configuration Commands
 LAB 3 Basic Switch Configuration Commands This lab explains basic switch configuration commands in detail with examples. Configuration and commands explained in this tutorial are essential commands to
LAB 3 Basic Switch Configuration Commands This lab explains basic switch configuration commands in detail with examples. Configuration and commands explained in this tutorial are essential commands to
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
Lab 1. CLI Navigation. Scenario. Initial Configuration for R1
 Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
Using the Command-Line Interface
 CHAPTER 2 This chapter describes the Cisco IOS command-line interface (CLI) and how to use it to configure your Cisco ME 3400 Ethernet Access switch. It contains these sections: Understanding Command Modes,
CHAPTER 2 This chapter describes the Cisco IOS command-line interface (CLI) and how to use it to configure your Cisco ME 3400 Ethernet Access switch. It contains these sections: Understanding Command Modes,
Configuration and management of Networks LAB 1 Introduction to packet tracer
 LAB 1 Introduction to packet tracer Objectives: Learn Packet Tracer to design and simulate networks. Learn to create a simple LAN with two PCs using an Ethernet hub and two straight through cables to connect
LAB 1 Introduction to packet tracer Objectives: Learn Packet Tracer to design and simulate networks. Learn to create a simple LAN with two PCs using an Ethernet hub and two straight through cables to connect
NDPS Gateway PS012-02
 NDPS Gateway 2.5 4343-PS012-02 Foreword Welcome NDPS Gateway is software that controls printers and print jobs and checks their status in an NDPS (Novell Distributed Print Services) environment, the newest
NDPS Gateway 2.5 4343-PS012-02 Foreword Welcome NDPS Gateway is software that controls printers and print jobs and checks their status in an NDPS (Novell Distributed Print Services) environment, the newest
NETWORK LAB 2 Configuring Switch Desktop
 Configuring Switch 1. Select the switch tab and then add a switch from the list of switches we have to the workspace, we will choose (2950-24) switch. 2. Add a number of PCs next to the switch in order
Configuring Switch 1. Select the switch tab and then add a switch from the list of switches we have to the workspace, we will choose (2950-24) switch. 2. Add a number of PCs next to the switch in order
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
Classful Address Subnet Mask Number of Hosts per Subnet (2 x 2)
 LAB 1 Exercise 1- Subnetting exercises. Write the subnet, broadcast address, and valid host range for question 1 through question 6: 1. 192.168.100.25/30 2. 192.168.100.37/28 3. 192.168.100.66/27 4. 192.168.100.17/29
LAB 1 Exercise 1- Subnetting exercises. Write the subnet, broadcast address, and valid host range for question 1 through question 6: 1. 192.168.100.25/30 2. 192.168.100.37/28 3. 192.168.100.66/27 4. 192.168.100.17/29
Lab Zero: A First Experiment Using GENI and Jacks Tool
 GENIExperimenter/Tutorials/jacks/GettingStarted_PartI/Procedure GENI: geni 2/27/16, 14:35 Lab Zero: A First Experiment Using GENI and Jacks Tool These instructions are at: http://tinyurl.com/geni-labzero
GENIExperimenter/Tutorials/jacks/GettingStarted_PartI/Procedure GENI: geni 2/27/16, 14:35 Lab Zero: A First Experiment Using GENI and Jacks Tool These instructions are at: http://tinyurl.com/geni-labzero
Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards
 Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards First Published: May 17, 2005 Last Updated: July 28, 2010 This document provides configuration tasks for the 4-port Cisco HWIC-4ESW and the 9-port
Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards First Published: May 17, 2005 Last Updated: July 28, 2010 This document provides configuration tasks for the 4-port Cisco HWIC-4ESW and the 9-port
Before you start the lab exercises see the lab administrator or EEE3080F tutor to get assigned to your routers.
 EEE00F Lab Basics of the Network Lab Student Lab Manual Before you start the lab exercises see the lab administrator or EEE00F tutor to get assigned to your routers. Contents. Resources used in the labs...
EEE00F Lab Basics of the Network Lab Student Lab Manual Before you start the lab exercises see the lab administrator or EEE00F tutor to get assigned to your routers. Contents. Resources used in the labs...
Lab Zero: A First Experiment Using GENI and Jacks Tool
 Lab Zero: A First Experiment Using GENI and Jacks Tool These instructions are at: http://tinyurl.com/geni labzero Overview This is a first, simple experiment on GENI useful for familiarizing new experimenters
Lab Zero: A First Experiment Using GENI and Jacks Tool These instructions are at: http://tinyurl.com/geni labzero Overview This is a first, simple experiment on GENI useful for familiarizing new experimenters
Viewing System Status, page 404. Backing Up and Restoring a Configuration, page 416. Managing Certificates for Authentication, page 418
 This chapter describes how to maintain the configuration and firmware, reboot or reset the security appliance, manage the security license and digital certificates, and configure other features to help
This chapter describes how to maintain the configuration and firmware, reboot or reset the security appliance, manage the security license and digital certificates, and configure other features to help
Lab 2.8.1: Basic Static Route Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
IOS and Configuration Basics
 APPENDIX C This appendix contains basic information about the Cisco Internet Operating System (IOS) software and includes the following sections: Cisco IOS Modes of Operation Getting Context-Sensitive
APPENDIX C This appendix contains basic information about the Cisco Internet Operating System (IOS) software and includes the following sections: Cisco IOS Modes of Operation Getting Context-Sensitive
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Configuring VRRP. Finding Feature Information. The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns
 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual routers to the VRRP routers on a LAN, allowing several routers on a
The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual routers to the VRRP routers on a LAN, allowing several routers on a
Accessing Carolinas Healthcare System Resources Remotely
 Accessing Carolinas Healthcare System Resources Remotely Have you logged in remotely before? If not, please proceed to Step 1. If yes, please log in as normal or see FAQ section if you are having trouble
Accessing Carolinas Healthcare System Resources Remotely Have you logged in remotely before? If not, please proceed to Step 1. If yes, please log in as normal or see FAQ section if you are having trouble
Contents. Introduction
 Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces
Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces
Lab b Simple Extended Access Lists
 Lab 11.2.2b Simple Extended Access Lists 1-7 CCNA 2: Simple Extended Access Lists v 3.1 - Lab 11.2.2b Copyright 2003, Cisco Systems, Inc. Objective Scenario In this lab, configuring extended access lists
Lab 11.2.2b Simple Extended Access Lists 1-7 CCNA 2: Simple Extended Access Lists v 3.1 - Lab 11.2.2b Copyright 2003, Cisco Systems, Inc. Objective Scenario In this lab, configuring extended access lists
Table of Contents. isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ
 king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
Installing the Operating System or Hypervisor
 If you purchased E-Series Server or NCE Option 1 (E-Series Server or NCE without a preinstalled operating system or hypervisor), you must install an operating system or hypervisor. This chapter includes
If you purchased E-Series Server or NCE Option 1 (E-Series Server or NCE without a preinstalled operating system or hypervisor), you must install an operating system or hypervisor. This chapter includes
Network Security Laboratory 23 rd May STATEFUL FIREWALL LAB
 Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Network Security Laboratory 23 rd May 2016. STATEFUL FIREWALL LAB 1 CONTENTS INTRODUCTION I. What is Stateful Firewall II. Difference between Stateful and Stateless III. Example of Stateful firewall IV.
Sun VirtualBox Installation Tutorial
 Sun VirtualBox Installation Tutorial Installing Linux Mint 5 LTS Guest OS By Dennis Berry Welcome to the world of virtualization and Linux. This tutorial is intended to help users who are new to the world
Sun VirtualBox Installation Tutorial Installing Linux Mint 5 LTS Guest OS By Dennis Berry Welcome to the world of virtualization and Linux. This tutorial is intended to help users who are new to the world
VERTICAL HORIZON VH-2402S FAST ETHERNET SWITCH MANAGEMENT GUIDE
 VERTICAL HORIZON VH-2402S FAST ETHERNET SWITCH MANAGEMENT GUIDE 9033645-01 Notice Only qualified personnel should perform installation procedures. NOTICE Enterasys Networks reserves the right to make
VERTICAL HORIZON VH-2402S FAST ETHERNET SWITCH MANAGEMENT GUIDE 9033645-01 Notice Only qualified personnel should perform installation procedures. NOTICE Enterasys Networks reserves the right to make
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
Antonio Cianfrani. Packet Tracer
 Antonio Cianfrani Packet Tracer Packet Tracer (1/2) Packet Tracer? Cisco Packet Tracer is a software able to emulate CISCO networking devices. Packet Tracer features: Allows to create network topologies
Antonio Cianfrani Packet Tracer Packet Tracer (1/2) Packet Tracer? Cisco Packet Tracer is a software able to emulate CISCO networking devices. Packet Tracer features: Allows to create network topologies
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Cisco IOS Commands. abort CHAPTER
 CHAPTER 2 abort Use the abort VLAN database command to abandon the proposed new VLAN database, exit VLAN database mode, and return to privileged EXEC mode. abort This command has no arguments or keywords.
CHAPTER 2 abort Use the abort VLAN database command to abandon the proposed new VLAN database, exit VLAN database mode, and return to privileged EXEC mode. abort This command has no arguments or keywords.
Initial Configuration on ML-Series Card
 CHAPTER 3 This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
CHAPTER 3 This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
Agent and Agent Browser. Updated Friday, January 26, Autotask Corporation
 Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Lab 9: VPNs IPSec Remote Access VPN
 Lab 9: VPNs IPSec Remote Access VPN Rich Macfarlane 2015 Aim: Details The aim of this lab is to introduce Virtual Private Network (VPN) concepts, using an IPSec remote access VPN between a remote users
Lab 9: VPNs IPSec Remote Access VPN Rich Macfarlane 2015 Aim: Details The aim of this lab is to introduce Virtual Private Network (VPN) concepts, using an IPSec remote access VPN between a remote users
Configuring IDS TCP Reset Using VMS IDS MC
 Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Chapter 11. Configuring and Testing Your Network
 Chapter 11 Configuring and Testing Your Network CCNA1-1 Chapter 11 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario.
Chapter 11 Configuring and Testing Your Network CCNA1-1 Chapter 11 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario.
WLM1200-RMTS User s Guide
 WLM1200-RMTS User s Guide Copyright 2011, Juniper Networks, Inc. 1 WLM1200-RMTS User Guide Contents WLM1200-RMTS Publication Suite........................................ 2 WLM1200-RMTS Hardware Description....................................
WLM1200-RMTS User s Guide Copyright 2011, Juniper Networks, Inc. 1 WLM1200-RMTS User Guide Contents WLM1200-RMTS Publication Suite........................................ 2 WLM1200-RMTS Hardware Description....................................
Practice Labs User Guide
 Practice Labs User Guide This page is intentionally blank Contents Introduction... 3 Overview... 3 Accessing Practice Labs... 3 The Practice Labs Interface... 4 Minimum Browser Requirements... 5 The Content
Practice Labs User Guide This page is intentionally blank Contents Introduction... 3 Overview... 3 Accessing Practice Labs... 3 The Practice Labs Interface... 4 Minimum Browser Requirements... 5 The Content
Lab Catalyst 2950 and 3550 Series Intra-VLAN Security
 Lab 7.2.5.1 Catalyst 2950 and 3550 Series Intra-VLAN Security Objective Scenario Configure intra-vlan security with Access Control Lists (ACLs) using the command-line interface (CLI) mode. This lab will
Lab 7.2.5.1 Catalyst 2950 and 3550 Series Intra-VLAN Security Objective Scenario Configure intra-vlan security with Access Control Lists (ACLs) using the command-line interface (CLI) mode. This lab will
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Cisco Discovery Protocol Version 2
 Cisco Discovery Protocol (formerly known as CDP) is a Layer 2, media-independent, and network-independent protocol that runs on Cisco devices and enables networking applications to learn about directly
Cisco Discovery Protocol (formerly known as CDP) is a Layer 2, media-independent, and network-independent protocol that runs on Cisco devices and enables networking applications to learn about directly
Smart Install Concepts
 CHAPTER 1 Smart Install is a plug-and-play configuration and image-management feature that provides zero-touch deployment for new switches. This means that a customer can ship a switch to a location, place
CHAPTER 1 Smart Install is a plug-and-play configuration and image-management feature that provides zero-touch deployment for new switches. This means that a customer can ship a switch to a location, place
Lab Troubleshooting Routing Issues with debug Instructor Version 2500
 Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Using Cisco IOS Software
 Using Cisco IOS Software This chapter provides helpful tips for understanding and configuring Cisco IOS software using the command-line interface (CLI) It contains the following sections: Understanding
Using Cisco IOS Software This chapter provides helpful tips for understanding and configuring Cisco IOS software using the command-line interface (CLI) It contains the following sections: Understanding
MPLS router configuration
 MPLS router configuration Computer Network Technologies and Services (CNTS) Tecnologie e Servizi di Rete (TSR) Preliminary note For this exercise you have to use the virtual routing environment prepared
MPLS router configuration Computer Network Technologies and Services (CNTS) Tecnologie e Servizi di Rete (TSR) Preliminary note For this exercise you have to use the virtual routing environment prepared
PT Activity 5.6.1: Packet Tracer Skills Integration Challenge Topology Diagram
 Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 6 Addressing Table Device Interface IP Address Subnet Mask
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Lab 3: Basic Device Configuration
 Lab 3: Basic Device Configuration University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 2 Lab 3: Basic Device Configuration **Given
Lab 3: Basic Device Configuration University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 2 Lab 3: Basic Device Configuration **Given
Initial Configuration for the Switch
 Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Management Software AT-S79. User s Guide. For use with the AT-GS950/16 and AT-GS950/24 Smart Switches. Version Rev.
 Management Software AT-S79 User s Guide For use with the AT-GS950/16 and AT-GS950/24 Smart Switches Version 1.0.0 613-000207 Rev. A Copyright 2005 Allied Telesyn, Inc. All rights reserved. No part of this
Management Software AT-S79 User s Guide For use with the AT-GS950/16 and AT-GS950/24 Smart Switches Version 1.0.0 613-000207 Rev. A Copyright 2005 Allied Telesyn, Inc. All rights reserved. No part of this
HTTP 1.1 Web Server and Client
 The feature provides a consistent interface for users and applications by implementing support for HTTP 1.1 in Cisco IOS XE software-based devices. When combined with the HTTPS feature, the feature provides
The feature provides a consistent interface for users and applications by implementing support for HTTP 1.1 in Cisco IOS XE software-based devices. When combined with the HTTPS feature, the feature provides
Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies
 Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies Topology Objectives Background Configure EIGRP on multiple routers. Configure the bandwidth command to modify the EIGRP metric. Verify
Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies Topology Objectives Background Configure EIGRP on multiple routers. Configure the bandwidth command to modify the EIGRP metric. Verify
Net-Net EMS Quick Start Guide Release Version and 9000
 Net-Net EMS Quick Start Guide Release Version 6.0 4000 and 9000 Acme Packet, Inc. 71 Third Avenue Burlington, MA 01803 USA t 781-328-4400 f 781-425-5077 www.acmepacket.com Last updated: July 16, 2008 Document
Net-Net EMS Quick Start Guide Release Version 6.0 4000 and 9000 Acme Packet, Inc. 71 Third Avenue Burlington, MA 01803 USA t 781-328-4400 f 781-425-5077 www.acmepacket.com Last updated: July 16, 2008 Document
Open SDN Controller Applications
 The following topics describe the five applications that Open SDN Controller provides to facilitate the day-to-day administration of your network: BGPLS Manager, page 1 Inventory Manager, page 3 Model
The following topics describe the five applications that Open SDN Controller provides to facilitate the day-to-day administration of your network: BGPLS Manager, page 1 Inventory Manager, page 3 Model
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
Office and Express Print Release High Availability Setup Guide
 Office and Express Print Release High Availability Setup Guide Version 1.0 2017 EQ-HA-DCE-20170512 Print Release High Availability Setup Guide Document Revision History Revision Date May 12, 2017 September
Office and Express Print Release High Availability Setup Guide Version 1.0 2017 EQ-HA-DCE-20170512 Print Release High Availability Setup Guide Document Revision History Revision Date May 12, 2017 September
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Access Switch VLAN Y Y.1 /24
 Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Lab Applying a Logical Layered Model to a Physical Network
 Lab 3.1.1 Applying a Logical Layered Model to a Physical Network Objective In this exercise, you will use various Cisco IOS commands and a protocol analyzer to map the layers in the OSI model to the encapsulated
Lab 3.1.1 Applying a Logical Layered Model to a Physical Network Objective In this exercise, you will use various Cisco IOS commands and a protocol analyzer to map the layers in the OSI model to the encapsulated
CHAPTER 2 ACTIVITY
 CHAPTER 2 ACTIVITY 2.1.1.1 1. CLI stands for 2. GUI stands for 3. Write the step you used to go to CLI interface on Windows 4. The OS, normally loads from a disk drive, into RAM. 5. The portion of the
CHAPTER 2 ACTIVITY 2.1.1.1 1. CLI stands for 2. GUI stands for 3. Write the step you used to go to CLI interface on Windows 4. The OS, normally loads from a disk drive, into RAM. 5. The portion of the
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Lab 5: Basic VLAN Configuration
 Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Packet Tracer - Connect a Router to a LAN (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab)
 PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
MiPDF.COM. 3. Which procedure is used to access a Cisco 2960 switch when performing an initial configuration in a secure environment?
 CCNA1 v6.0 Chapter 2 Exam Answers 2017 (100%) MiPDF.COM 1. What is the function of the kernel of an operating software? It provides a user interface that allows users to request a specific task. The kernel
CCNA1 v6.0 Chapter 2 Exam Answers 2017 (100%) MiPDF.COM 1. What is the function of the kernel of an operating software? It provides a user interface that allows users to request a specific task. The kernel
NAT Routemaps Outside-to-Inside Support
 The feature enables you to configure a NAT routemap configuration that allows IP sessions to be initiated from outside the network to inside the network. This module explains how to configure the feature.
The feature enables you to configure a NAT routemap configuration that allows IP sessions to be initiated from outside the network to inside the network. This module explains how to configure the feature.
EXAM - HP0-Y52. Applying HP FlexNetwork Fundamentals. Buy Full Product.
 HP EXAM - HP0-Y52 Applying HP FlexNetwork Fundamentals Buy Full Product http://www.examskey.com/hp0-y52.html Examskey HP HP0-Y52 exam demo product is here for you to test the quality of the product. This
HP EXAM - HP0-Y52 Applying HP FlexNetwork Fundamentals Buy Full Product http://www.examskey.com/hp0-y52.html Examskey HP HP0-Y52 exam demo product is here for you to test the quality of the product. This
Catalyst 2960-X Switch Routing Configuration Guide, Cisco IOS Release 15.0(2)EX
 Catalyst 2960-X Switch Routing Configuration Guide, Cisco IOS Release 15.0(2)EX First Published: July 10, 2013 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Catalyst 2960-X Switch Routing Configuration Guide, Cisco IOS Release 15.0(2)EX First Published: July 10, 2013 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Initial Configuration
 3 CHAPTER This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
3 CHAPTER This chapter describes the initial configuration of the ML-Series card and contains the following major sections: Hardware Installation, page 3-1 Cisco IOS on the ML-Series Card, page 3-2 Startup
