Security Router Pod Planning and Installation Guide
|
|
|
- Kerrie Sims
- 6 years ago
- Views:
Transcription
1 Security Router Pod Planning and Installation Guide For Cisco Networking Academy FNSR Curriculum Document Version: Copyright 2005, Network Development Group, Inc. NETLAB Academy Edition and NETLAB+ are registered trademarks of Network Development Group, Inc. Cisco, IOS, Cisco IOS, Networking Academy, CCNA, CCNP, and PIX are registered trademarks of Cisco Systems, Inc.
2 1 Introduction Lab Orientation Full Pod Limited Pod Deviations Remote PC Support Client-to-IOS-Firewall Topology Lab Device Requirements ROUTER1 and ROUTER Router Backbone (RBB) Backbone Server / VPN Client PC PCs and Servers Control Device Requirements Control Switch Overview Access Server Switched Outlets Pre-requisites Setup Control Devices Upload IOS Images Disable User Logins (optional) Adding the Pod Start the New Pod Wizard Add a Security Router Pod Select Control Switch and Ports Select Access Server(s) and Ports Select Switched Outlets Select Router Types Select Software Images and Recovery Options Select PC Options Select a Pod ID Select a Pod Name Verify Your Settings Cable the Pod Configuring PCs Assign IP Addresses Test the Control Path Load Remote PC Software Load Curriculum Specific Software Secure the PC Configuring RBB Determine VLANs Option 1 - Separate RBB for Each Security Router Pod Option 2 Using Multi-VRF CE on a Separate Physical Router to Simulate Several RBB Routers Testing the Pod Finishing Up /29/2005 Page 2 of 47
3 10.1 Bring the Pod(s) Back Online Enable Security Router Pod and FNSR Exercises Schedule a Lab Reservation for Your New Pod Appendix A - FNSR Supported Labs /29/2005 Page 3 of 47
4 PART 1 PLANNING 1 Introduction NETLAB Academy Edition features two pods for use with the Fundamentals of Network Security (FNS) curriculum. This guide documents the NETLAB AE Security Router Pod, used with FNS: Router (FNSR) labs. You may have up to two Security Router Pods per NETLAB AE system. The NETLAB AE Security Router Pod features direct access the console of ROUTER1 and ROUTER2. Depending on your settings, NETLAB AE can also provide remote access to the keyboard, video, and mouse of PCs and servers in the pod. 4/29/2005 Page 4 of 47
5 1.1 Lab Orientation This document assumes that you are familiar with the FNS curriculum and labs. In particular, you should review the Student Lab Orientation exercise. This lab provides an overview of the pod, labs, objectives, and general requirements. 1.2 Full Pod The FNSR labs are designed around a two-team model. One team of students configures the left side of the pod, while another team configures the right side. In this scenario, all the devices should be implemented. 1.3 Limited Pod In additional to supporting the full pod (see 1.2), NETLAB AE also offers support for a limited pod. NETLAB AE users in a team or instructor-led class can share access to a router console or PC. Therefore, all users can work from the left side of the pod (ROUTER1, PC_1, and IS_1) to accomplish the lesson objective while using the right side of pod only for verification (i.e. pings, traces, VPN client, etc). To reduce operating costs, NETLAB AE does not mandate that you implement every PC and server, nor does it require any particular operating system. You can easily reconfigure the pod settings at any time during the semester, making adjustments and repositioning PCs as needed. Although NETLAB AE provides this flexibility, certain choices may be required by the curriculum and by NETLAB AE. 1.4 Deviations Users often contact our technical support team for lab-related problems. Users are typically not aware that there are many NETLAB AE servers and are easily confused by local deviations from the standard curriculum and labs. The FNS curriculum is relatively complex and offers many opportunities to make adjustments to the labs. If your NETLAB AE pods will be made accessible outside your local Academy, you should carefully consider the impact of deviations and substitutions. Even if your user community is local or relatively small, we recommend that you (1) document the specifics of your pods and (2) use the NETLAB AE News and Announcements feature to point users to your documentation. 4/29/2005 Page 5 of 47
6 1.5 Remote PC Support The Security Router Pod includes placeholders for 5 remote PCs. You have several options for each PC. Direct/VMware. The PC is implemented as a VMware GSX virtual machine. o Users can control the keyboard, video, and mouse. o Users can power on, shutdown, reboot, and revert to a clean state. o Users can have administrator rights. Direct/Standalone. The PC is implemented on a standalone machine, or a virtual product emulating a standalone machine. o Users can control the keyboard, video, and mouse. o Users can revert to a clean state by rebooting. o Users have limited rights (administrative access not recommended). Indirect. The PC is implemented, but not managed by NETLAB AE. o Users may be able to interact with the PC, but cannot access the keyboard, video, or mouse through NETLAB AE. Absent. The PC is not implemented. These options are fully explained in the NETLAB+ Remote PC Guide. Most of the FNSR labs do not require administrative rights on the PC. Therefore, Direct/Standalone PCs can be used effectively with FNSR. Direct/VMware offers complete administrative access on the remote PC and offers the greatest support for FNSR labs. 4/29/2005 Page 6 of 47
7 1.6 Client-to-IOS-Firewall Topology The FNSR curriculum contains labs that use a Client-to-IOS Firewall topology. NETLAB AE does not implement a separate pod type for these labs. You may optionally configure the Backbone Server (BB) for direct access by users, and use BB for VPN client exercises. By enabling direct access, BB can also be used as an external PC for labs that require testing from an outside network (i.e. simulating a host on the Internet). 4/29/2005 Page 7 of 47
8 2 Lab Device Requirements This section describes the requirements for each lab device. Lab devices are part of the topology and users can interact with them either directly or indirectly. 2.1 ROUTER1 and ROUTER2 Both routers in the Security Router Pod have the same requirements. NETLAB AE Supported Devices Ethernet Ports Required IOS Release Images (in order of preference) 2611XM 2621XM 2651XM (4)T Advanced IP Services 12.3(4)T Advanced Security C266-advipservicesk9-mz T6 (128/32) C2600-advsecurityk9-mz T6 (96/32) VPN Router bundles ship by default with 12.3(4)T or later. Do not go above the 12.3(7)T image, as the IOS Intrusion Detection commands have changed significantly in version 12.3(8)T. If the router has 12.3(8)T or later, the image must be downgraded. Security Device Manager (SDM) version 1.2 or later will be required for labs in Modules 2 through 7. VPN router bundles ship by default with SDM. 1 The 2621 model router will work for all labs excluding SDM labs once they have been upgraded from 16F/32DRAM to 16F/64DRAM. 2.2 Router Backbone (RBB) RBB is a static router. It is not accessible or configurable by users. However, it is part of the topology so users can indirectly interact with it (i.e. ping, trace, RIP, etc.). You can implement RBB in one of two ways: (1) A separate standalone RBB router for each Security Router Pod (2) Simulating RBB for two or more security pods by utilizing multi-vrf on one physical router. Configuration of each option is covered in detail in section 8. 4/29/2005 Page 8 of 47
9 2.3 Backbone Server / VPN Client PC The Backbone Server (BB) provides services that are typically provided by Internet servers. The FNS curriculum provides two options for the backbone server (BB): Option 1 a dedicated BB server. Option 2 - one SuperServer with Intel Pro Server NIC with VLAN support, serving as several PCs in the pod. NETLAB AE currently does not support the SuperServer (option 2). You should use VMware GSX (or other virtualization) products to simulate several machines. Virtual machines have their own routing tables, which avoids asymmetric routing problems in the pod. FNSR refers to a Client-to-IOS Firewall configuration. NETLAB AE does not have a pod type for this topology. However, you may also configure the Backbone Server (BB) for direct access, which means that users can login and interact with the Windows interface. By loading the Cisco VPN client software on BB, users can use the NETLAB AE Security Router Pod for client-to-ios firewall labs. Direct access also allows BB to be used as an external PC for labs that require testing from an outside network (i.e. simulating the Internet). 2.4 PCs and Servers The Security Router Pod includes placeholders for 5 remote PCs. Please refer to section 1.5 and the NETLAB+ Remote PC guide. 4/29/2005 Page 9 of 47
10 3 Control Device Requirements NETLAB AE control devices provide internal connectivity, console access, and managed power. Control devices are dynamically managed by NETLAB AE and are not accessible or configurable by end users. Management of control devices is covered in the NETLAB+ Administrator Guide. The Security Router Pod requires the following control device resources: Control Device Resource Control Switch Access Server Switched Outlet Devices Quantity Required 10 consecutive ports + Up to 5 Reserved Ports 2 lines 2 outlets 3.1 Control Switch Overview NETLAB AE uses a control switch to provide connectivity between devices in the Security Router Pod. CONTROL SWITCH A C C C D F F F G T R R R FA0/1 FA0/0 ROUTER1 IS1 FA0/1 FA0/0 ROUTER2 IS2 BB TRUNK CONTROL PATH PC1 PC2 CONTROL PATH RBB CONTROL PATH The actual FNS labs refer to SW0. This device is not implemented in NETLAB AE. In addition, the NETLAB AE cable scheme (depicted above) is different from SW0. The Security Router Pod requires 10 consecutive ports on a supported control switch (other than a Catalyst 1900 series). 4/29/2005 Page 10 of 47
11 You cannot use a Catalyst 1900 series control switch because 802.lq trunking is not supported. Ports are labeled +0 to +9 in the diagram and are relative to the base port of your choice. As with all pods, you choose a base port for the Security Router Pod. To determine the actual port numbers, simply add the base port number chosen for this pod to the depicted relative port numbers. For example, if the base port is 5, the actual port numbers will be 5 to 14. Using SNMP, NETLAB AE will automatically assign and program VLANs on ports +0 to +8. These VLANs are depicted as letters A, C, D, F, and G and represent a subnet in the topology (B and E are reserved for future DMZ segments and compatibility with the Security PIX Pod). Each NETLAB AE pod has a unique VLAN pool and the actual VLAN numbers will be unique for each NETLAB AE pod. This is to avoid conflict between pods. Port +9 provides a trunk port if you choose to implement RBB as a separate router (see 8.2). Alternatively, you can use this port to provide trunking for multiple security pods in conjunction with the multi-vrf approach outlined in section 8.3. You also need a reserved control switch port for each Direct/Standalone remote PC. These ports (depicted as R) connect to the PCs 2 nd interface and provide a control path for NETLAB AE Remote PC software functions. The control path (1) allows users to access the keyboard, video, and mouse and (2) allows NETLAB AE to communicate with the PC through an API. 3.2 Access Server Access servers provide console connections to lab routers, lab switches, and lab firewall devices so that users can access these devices from NETLAB AE. The Security Router Pod requires two access server ports. These ports provide console access to ROUTER1 and ROUTER Switched Outlets Switched outlets provide managed electrical power, allowing NETLAB AE and users to turn lab equipment on and off. The Security Router Pod requires a switched outlet for ROUTER1 and ROUTER2. 4/29/2005 Page 11 of 47
12 PART 2 - IMPLEMENTATION 4 Pre-requisites This section covers tasks that should be executed prior to adding a Security Router Pod. 4.1 Setup Control Devices Using the guidelines in section 3, decide which control switch ports, access server ports, and switched outlets you will use for your Security Router Pod. Add control devices if necessary. Control device configuration is documented in the NETLAB+ Administrator Guide. 4.2 Upload IOS Images Upload the IOS images for ROUTER1 and ROUTER2. NETLAB AE will recover these images on the router if they are erased from flash. 4.3 Disable User Logins (optional) You must take all equipment pods offline to add pods or configure control devices. You may wish to disable user logins during this time. 4/29/2005 Page 12 of 47
13 5 Adding the Pod This section walks you through the process of adding a Security Router Pod using the NETLAB AE New Pod Wizard. 5.1 Start the New Pod Wizard Login to the administrator account. Select Equipment Pods. Select Take All OFFLINE if any of the pods are online. Caution: this will cancel any reservations in progress. Select Add a Pod. The New Pod Wizard will now help you add an equipment pod to your system. 5.2 Add a Security Router Pod When prompted, select Security Router Pod. 5.3 Select Control Switch and Ports A Security Router Pod requires 10 consecutive control switch ports. NETLAB AE will present a list of the control switches on your system. Switches that meet the port requirement can be selected. Choose one control switch for your new pod. Next, select the ports you want to use. 4/29/2005 Page 13 of 47
14 5.4 Select Access Server(s) and Ports A Security Router Pod requires 2 access server ports. It is a good idea to use consecutive ports on one access server if possible. This practice will make it easier to cable and troubleshoot. If consecutive ports are not available, you can use non-consecutive ports, on different access servers if necessary. When specifying ports, use the port numbers shown on the access server itself. Some models start at port 1 (Cisco 2509 and 2511) and others start at port 0 (Cisco NM-16A and NM-32A modules). NETLAB AE allows you to choose consecutive ports on one access server, or you can choose Let me pick to select an access server and port for each router. Let me pick, allows you to make granular selections. 4/29/2005 Page 14 of 47
15 5.5 Select Switched Outlets A Security Router Pod requires 2 switched outlets. It is a good idea to use consecutive outlets on one switched outlet device (SOD) if possible. This practice will make it easier to cable and troubleshoot. If consecutive outlets are not available, you may use non-consecutive outlets, spanning multiple SODs if necessary. Let me Pick, will allow you to make granular selections. 4/29/2005 Page 15 of 47
16 5.6 Select Router Types Please specify a router model for ROUTER1 and ROUTER2. RBB is a statically configured router, so it does not appear in the router selection process Your selections are used to assign the appropriate NETLAB AE device driver. Improper selections may cause errors. NETLAB AE may offer selections that meet the port requirements, but do not support the curriculum. See section 2.1 for a list of supported routers. 4/29/2005 Page 16 of 47
17 5.7 Select Software Images and Recovery Options NETLAB AE scrubs ROUTER1 and ROUTER2 at the end of lab reservation or upon request. During a scrub, NETLAB AE can recover an IOS image if it has been erased from flash. You have three choices for flash recovery: Recovery Using Specified Image If specified image not in flash If no image in flash (erased) Never (device may become unusable) During A Scrub Operation Restores the selected software image if that image is not in flash. Restores the selected software image if there are no.bin images in flash. No action is taken if flash contains a.bin image (even if it is not the specified one). NETLAB AE will take no action if the flash does not contain a bootable image. In this case, NETLAB AE automated boot process will fail and manual restoration of IOS will be required. If you select an automatic recovery option, you must also select a software image supported by the curriculum (see 2.1). 4/29/2005 Page 17 of 47
18 5.8 Select PC Options Section 2.4 discussed various options for your pod s PCs and servers. In this task, you will select an ID, type, access method, and operating system for your PCs and servers. Figure Typical PC settings for a full pod (discussed in 1.2) Figure Typical PC settings for a limited pod (discussed in 1.3) The following table describes the four most common settings as described in section 1.5: To implement Set TYPE to Set ACCESS to Direct/VMware VMWARE VNC Direct/Standalone STANDALONE VNC Indirect (any) INDIRECT Absent (no PC) ABSENT n/a 4/29/2005 Page 18 of 47
19 5.9 Select a Pod ID Each pod is assigned a unique numeric ID Select a Pod Name Each pod can have a unique name. This name will appear in the scheduler, along with the pod type Verify Your Settings At this point NETLAB AE has added the pod to its database. However, the pod has not been brought online yet. You will want to cable up the pod, configure PCs, configure router RBB, and run a pod test before bringing the pod online. These tasks are discussed in the remaining sections. After you click OK, the new pod will appear in the list of equipment pods. Click on the magnifier button or pod ID to manage you new pod. 4/29/2005 Page 19 of 47
20 4/29/2005 Page 20 of 47
21 NETLAB AE will display the status of the pod and the high-level settings for each device, PC, and control switch. 4/29/2005 Page 21 of 47
22 6 Cable the Pod Use the NETLAB AE cable chart feature to help you connect the lab devices in your pod. The chart is generated in real-time and contains port-specific information based on your current lab device and control device settings. The cable chart function is accessed from the pod management page. 4/29/2005 Page 22 of 47
23 7 Configuring PCs This section describes the basic tasks required to setup your PCs. Detailed guidance, such as securing the operating system and restoring the PC to a clean state is covered in the NETLAB+ Remote PC Guide. Caution: Connect your PCs and servers to a surge protector, not a NETLAB AE switched outlet device (i.e. APC). Even though an unused outlet may currently be ON, NETLAB AE may turn the outlet OFF during certain tests. 7.1 Assign IP Addresses Standalone/Direct remote PCs have two network interfaces and have two IP addresses. One interface faces the pod, and the other to any reserved control switch port. Reserved control switch ports reside in VLAN 1 and provide a path to the inside interface of the NETLAB AE server. The control path IP addresses will be based on the PC ID assigned in the new pod wizard (see below). Do not set a default gateway on the control path interfaces. CONTROL SWITCH A C C C D F F F G T R R R PC1 IS_1 PC2 IS_2 BB <id> no gateway <id> no gateway <id> no gateway CONTROL PATH CONTROL PATH CONTROL PATH 4/29/2005 Page 23 of 47
24 The following table shows the correct IP parameters for each PC and server. Primary Interface To Pod Secondary Interface (Direct/Standalone PCs ONLY) IP Address Mask Gateway IP Address Mask Gateway PC_ / <pc_id> /24 None PC_ / <pc_id> /24 None BB / <pc_id> /24 None IS_ / <pc_id> /24 None IS_ / <pc_id> /24 None The secondary IP addresses for Direct/Standalone PCs are derived from the unique PC ID. The actual addresses are listed on the pod management page. This is a sample 7.2 Test the Control Path For each Direct/Standalone remote PC, verify the control path between the PC secondary interface and the NETLAB AE server inside interface. All interfaces and switch ports in the control path should be administratively enabled and should have a green link light. Open a command window and ping the NETLAB AE server inside address NETLAB AE also binds on its inside interface, but you will not be able to ping this address from a properly configured remote PC. 4/29/2005 Page 24 of 47
25 7.3 Load Remote PC Software You must load the NETLAB AE Remote PC software package on Direct/Standalone remote PCs. The installation package is stored on the NETLAB AE server and is downloaded using a web browser on the PC. This software is only installed on direct access PCs (PC_1, PC_2 and BB). It should not be installed on IS_1, IS_2 or the users PCs. 1) Open a web browser on the remote PC. 2) Enter the case-sensitive URL exactly as shown: 3) Click Open to install the package. 4/29/2005 Page 25 of 47
26 4) Answer Yes at the Security Warning. 4/29/2005 Page 26 of 47
27 5) Agree to the license. 6) Read the README file. 7.4 Load Curriculum Specific Software Install the software on the PC outlined in the FNSR curriculum and Student Orientation Lab. 7.5 Secure the PC NETLAB AE does not prescribe any specific security policies for your PCs. However, you should implement a policy appropriate for your user community. For Direct/Standalone PCs, we recommend that you: 1) Setup the guest account for casual user access. You should only allow very trusted users access to the administrator account (or equivalent), if you allow this at all. Appendix A highlights the few labs that may require admin privileges. 2) Use the policy editor to remove the system Shutdown option from the guest account. If a user shuts down a PC, that PC is unusable until someone physically powers it on. 3) Install and activate image restoration software such as Horizon DataSys Drive Vaccine. NETLAB AE will reboot the PC between lab reservations so that Drive Vaccine (or equivalent) can restore the PC to a clean state. Please see the NETLAB+ Remote PC Guide for additional security tips. 4/29/2005 Page 27 of 47
28 8 Configuring RBB RBB is a statically configured router. It is not accessible or configurable by users. However, it is part of the topology so users can indirectly interact with it (i.e. ping, trace, RIP, etc.). 1 You can implement RBB in one of two ways: (1) Deploy a separate standalone RBB router for each Security Router Pod. (2) Simulate RBB for two or more security pods by utilizing multi-vrf CE on one physical router. The following diagram shows how the networks in the Security Router Pod are implemented as VLANs on the control switch. For illustration, each VLAN is given a letter and color. To avoid conflicts between pods, the actual pool of VLAN numbers selected for each pod is different. CONTROL SWITCH A C C C D F F F G T R R R Router1 IS1 Router2 IS2 BB TRUNK CONTROL PATH PC1 PC2 IF NOT USING 3550 AND MULTI-VRF RBB CONTROL PATH CONTROL PATH 4/29/2005 Page 28 of 47
29 In the Security Router Pod, RBB performs routing between network A, D, and G. RBB advertises routes to its peers using both EIGRP and RIP version 2. EIGRP is used in most of the FNSR labs. RIPv2 is used in the Route Authentication and Filtering lab. 8.1 Determine VLANs Recall that each pod is automatically assigned a pool of unique VLAN numbers. Regardless of how you choose to implement RBB routing, you will need to determine what VLAN numbers are actually used for network A, D, and G. First, determine the base VLAN for the pod you are setting up. This is shown on the pod management page. From the administrative account, go to Equipment Pods and select the pod from the list. Obtain the BASE VLAN from the CONTROL SWITCH table. In this example, pod 5 uses VLANs The base VLAN is 140. Now compute the actual VLANs by adding the base VLAN to the offset values listed below for each network. Record your results for future reference. Network Offset (add to base VLAN) Actual VLAN Example A + 0 = = 140 D + 3 = = 143 G + 6 = = 146 4/29/2005 Page 29 of 47
30 8.2 Option 1 - Separate RBB for Each Security Router Pod The most basic way to provide RBB routing is to a separate RBB router for each Security Pod. RBB will need at least one 802.1q capable FastEthernet port. Refer to the same CONTROL SWITCH table from section 8.1. Connect RBB to the last control switch port assigned to the pod (base port + 9). Next, connect to the console of the control switch. Configure RBB s control switch port as a trunk. Limit allowed VLANs to those computed in the VLAN table (see 8.1). Sample configuration for RBB control switch port items in blue will vary. interface FastEthernet0/10 switchport mode trunk switchport trunk allowed vlan 140,143,146 switchport nonegotiate no switchport access vlan no shutdown 4/29/2005 Page 30 of 47
31 Connect and configure RBB via the console port. Since RBB is static and not managed by NETLAB AE, you may want to use a different enable password than the one used for hands on lab routers. You may also wish to disable login on VTY lines. Sample RBB configuration items in blue will vary by pod and admin preference. hostname RBB! normal enable secret not recommended enable secret different key chain RTRAUTH key 1 key-string interface FastEthernet0/0.140 description to ROUTER1 segment encapsulation dot1q 140 ip address ip rip authentication mode md5 ip rip authentication key-chain RTRAUTH no shutdown interface FastEthernet0/0.143 description to ROUTER2 segment encapsulation dot1q 143 ip address ip rip authentication mode md5 ip rip authentication key-chain RTRAUTH no shutdown interface FastEthernet0/0.146 description to BB segment encapsulation dot1q 146 ip address no shutdown! routing protocol for most labs router eigrp 1 network network no auto-summary! routing protocol for rip / authentication lab router rip version 2 network network /29/2005 Page 31 of 47
32 8.3 Option 2 Using Multi-VRF CE on a Separate Physical Router to Simulate Several RBB Routers You can leverage Cisco s Multi-VRF CE feature (also known as VRF Lite) to provide an RBB routing function for two or more NETLAB AE security pods (Router or PIX) using only one physical router. Multi-VRF stands for Multiple Virtual Routing and Forwarding. As the name implies, this feature allows you to have multiple routing tables in one router. Frame Relay or VLAN interfaces can be mapped to a specific routing table (VRF). In essence, you are simulating multiple virtual routers with one physical router. The router and IOS must support both 802.1q trunking and Mutli-VRF CE. Cisco s Feature Navigator can help with this task. FNSR labs use EIGRP. EIGRP support for Multi-VRF CE is very recent and can be found in some IOS 12.3 releases. Building on option 1 (see 8.2), the physical router is connected to the T control switch port, designated for RBB on any one of the security pods. The security pods do not need to be on the same control switch, as long as all control switches are interconnected on trunking ports and all VLANs are permitted between control switches. NETLAB AE manages the VLAN database on each control switch using SNMP. During control switch configuration, NETLAB AE sets the control switch to VTP transparent mode. You should not change the control switches to VTP Server or VTP Client mode. In lieu of VTP, NETLAB AE will maintain an identical VLAN database on each control switch. 4/29/2005 Page 32 of 47
33 In the example to follow, we will use a Cisco 2621 running Multi-VRF CE to provide a virtual RBB for a Security Router Pod (POD_5) and a Security Pix Pod (POD_6). The physical router is a Cisco 2621 running 12.3(6c) Telco (c2600-telco-mz.123-6c.bin). Both Security Router Pod and Security Pix Pod share a similar VLAN layout. This is by design. RBB provides routing between networks A, D, and G depicted below. RBB in the Security Router Pod RBB in the Security PIX Pod Similar to section 8.2, we determine that the BASE VLAN for POD_5 and POD_6 is 140 and 150 respectively. We compute the VLANs for network A, D, and G by adding the base VLAN for each pod to the offsets shown below. Figure RBB routed VLANS for POD_5 and POD_6 Network Offset (add to base VLAN) POD_5 POD_6 A = = 150 D = = 153 G = = 156 You can connect the physical router to the designated T port on either security pod. In this case, we will use POD_5, a Security Router Pod. 4/29/2005 Page 33 of 47
34 CONTROL SWITCH A C C C D F F F G T R R R Router1 IS1 Router2 IS2 BB TRUNK CONTROL PATH PC1 PC2 IF NOT USING 3550 AND MULTI-VRF RBB CONTROL PATH CONTROL PATH POD_5 is using ports 1 to 10 on control switch 3. Therefore, the T port is FastEthernet0/10. We want to provide routing for all the VLANs computed in Figure above. Therefore, we will configure FastEthernet0/10 for 802.1q and permit the VLANs for both pods. Sample configuration for RBB control switch port items in blue will vary. interface FastEthernet0/10 switchport mode trunk switchport trunk allowed vlan 140,143,146,150,153,156 switchport nonegotiate no switchport access vlan no shutdown 4/29/2005 Page 34 of 47
35 Our two security pods will actually be connected to two different control switches. Recall that NETLAB AE maintains an identical VLAN database on each control switch (similar to VTP). As long as trunking is enabled between control switches, no additional switch setup is required. CONTROL SWITCH 3 SECURITY PIX POD CONTROL SWITCH 2 SECURITY ROUTER POD RBB Make sure this link is configured for trunking. Make sure this link is configured for trunking. VLANS 150, 153, 156 NETLAB SERVER CONTROL SWITCH 1 Next, we configure the physical RBB router. Begin by creating a virtual routing and forwarding instance for POD_5 and POD_6. Each VRF will represent a virtual RBB router. Each VRF requires a unique route descriptor in the form rd:rd. We will use the pod ID for the rd values. hostname multi-rbb! ip vrf POD_5 rd 5:5! ip vrf POD_6 rd 6:6 Create a MD5 key chain for the RIPv2 lab. We will apply this to two networks in the Security Router Pod. 4/29/2005 Page 35 of 47
36 key chain RTRAUTH key 1 key-string Next, configure sub-interfaces for networks A, D, and G in POD_5. Apply the ip vrf forwarding command before assigning the IP address. This command assigns the VLAN sub-interface to a VRF. The two sub-interfaces facing network A and D will be configured for RIP MD5 authentication, in support of one of the lab exercises. Now create sub-interfaces for POD_6. interface FastEthernet0/0.150 description POD_6 net A to PIX1 encapsulation dot1q 150 ip vrf forwarding POD_6 ip address ! interface FastEthernet0/0.153 description POD_5 net D to PIX2 encapsulation dot1q 153 ip vrf forwarding POD_6 ip address ! interface FastEthernet0/0.156 description POD_5 net G to BB encapsulation dot1q 156 ip vrf forwarding POD_6 ip address Next, we create an EIGRP and RIPv2 routing instance and assign them to the POD_5 VRF using the address-family ipv4 vrf command. EIGRP requires an autonomous-system 1 command within the address family. POD_6 is the PIX pod and does not use EIGRP or RIP. If POD_6 was another Router pod, you would configure address families POD_6 for EIGRP and RIP similar to POD_5. 4/29/2005 Page 36 of 47
37 router eigrp 1 auto-summary! address-family ipv4 vrf POD_5 autonomous-system 1 network network no auto-summary! router rip version 2! address-family ipv4 vrf POD_5 network network no auto-summary Because the PIX pod uses NAT on the outside interfaces, no routing protocols or static routes are required for the PIX pod s VRF. Exit configuration mode and save the configuration. 4/29/2005 Page 37 of 47
38 Once your pods are running and configs are loaded into ROUTER1 and ROUTER2, you can verify your VRF routing using the show ip route vrf command. multi_rbb# show ip route vrf POD_5 Routing Table: POD_5 Gateway of last resort is not set C C C D D /24 is subnetted, 1 subnets is directly connected, FastEthernet0/ /24 is subnetted, 2 subnets is directly connected, FastEthernet0/ is directly connected, FastEthernet0/ /24 is subnetted, 2 subnets [90/30720] via , 00:00:27, FastEthernet0/ [90/30720] via , 00:00:12, FastEthernet0/ /29/2005 Page 38 of 47
39 9 Testing the Pod After all routers and PCs have been installed, you should run a pod test to verify that your pod is working. The pod test will detect common configuration and cabling problems. Some tests may take a long time. During the BOOTIOS test, NETLAB AE may have to load the specified IOS image if it is not in flash. Some images are very large and can take up to 30 minutes to program into flash memory. If you cannot resolve an issue and decide to contact technical support, please cut and paste the text from the POD TEST LOG and include with your . 4/29/2005 Page 39 of 47
40 Finishing Up Bring the Pod(s) Back Online Now you can bring the pod online and make it available for lab reservations. You can bring just this pod online by clicking the Online button under Management Options. Alternatively, you can click Bring All ONLINE on the Equipment Pods page. Choose this option when you have no more additions or modifications to pods or control devices and you wish to put all pods into service. 4/29/2005 Page 40 of 47
41 10.2 Enable Security Router Pod and FNSR Exercises To make the Security Router Pod and FNSR lab exercises available to classes and students, you must first enable FNS/Router in a new or existing class. To add or edit class information, log into NETLAB AE using your instructor account. See the Instructor Accounts section of the NETLAB+ Administrator Guide for details. Select Class from the menu bar at the top of the MyNETLAB page, or the link in the body of the page. The Class Manager page will be displayed. Select to add a new class or select an existing class from the class list by clicking on a class name. 4/29/2005 Page 41 of 47
42 You may now enable more than one set of content. Previous NETLAB AE versions only allowed one content selection. 4/29/2005 Page 42 of 47
43 10.3 Schedule a Lab Reservation for Your New Pod. To schedule a lab reservation, select Scheduler from the menu bar or the link on the body of the MyNETLAB page. The Scheduler Options screen will be displayed. Detailed descriptions of the scheduler options are available by selecting Help on the menu bar. In this example, we will reserve an equipment pod for your own use. Select OK to proceed to the reservation calendar. Please Note: The selection of pods depicted may be different from the pods available at your site. 4/29/2005 Page 43 of 47
44 The reservation time area may be scrolled up and down. Scroll to the bottom to display the color legend. Select an available time, and the Reserve Instructor Access Time page will be displayed. 4/29/2005 Page 44 of 47
45 Review the details of the reservation and select Confirm Reservation. You can return to the reservation calendar to see your lab reservation on the time reservation portion. Remember, you may need to scroll the page to see your information. For more information on scheduling reservations, see the Scheduler section of the NETLAB+ Instructor Guide. 4/29/2005 Page 45 of 47
46 11 Appendix A - FNSR Supported Labs LAB Name NETLAB AE Support Comments Student Lab Orientation Yes This lab describes the basics of cabling and configuring the standard lab topology for this course. Students will become familiar with the physical and logical topology that will be used throughout the course. Vulnerabilities and Exploits Caution* The use of common network mapping tools, hacking programs, and scripts on a LAN and across a WAN. *Requires administrator access on the PCs. Only recommended for Direct/VMware PCs.. Configure SSH Yes Configure SSH access. Controlling TCP/IP Services Yes In this lab, students will complete the following objectives: Begin the process of implementing a secure perimeter router Explicitly deny common TCP/IP services Verify TCP/IP services have been disabled Configure Routing Authentication and Filtering Yes In this lab, students will demonstrate the use of authentication and filters to control route updates from peer routers. General Router Security Yes Configure basic router security features. Configure Basic Security using Security Caution* Device Manager Copy the SDM files to router Flash memory. *You must manually load SDM files in flash. NETLAB AE does not automatically manage SDM images. Lock-and-Key ACLs Yes In this lab, students will configure a dynamic ACL for lock-and-key security. Time-Based ACLs Yes Time-based ACLs allow administrators to control when users are permitted or denied access to network resources. Time-based ACLs can be applied to NAT, interfaces, lines, and virtually all other ACL scenarios. In this lab, students will control web access Configure Cisco IOS Firewall CBAC on a Yes Context-based Access Control (CBAC). Cisco Router Configure AAA on Cisco Router Yes In this exercise, students will protect the network access server (NAS), or pod router, by securing access using simple passwords without authentication, authorization, and accounting (AAA). Then students will configure the NAS to perform AAA authentication Install and Configure CSACS 3.0 for Windows Caution* Install CSACS on Windows. *Requires Window's administrator access and overwrite of CSACS. Only recommended for Direct/VMware PCs. Configure Authentication Proxy Yes In this lab, students will configure authentication proxy on a Cisco router. Configure IOS Firewall IDS Yes The Intrusion Detection Systems provide a level of protection beyond the firewall by protecting the network from internal and external attacks and threats. Configure Logging Yes In this lab, students will use logging to monitor network events. 4/29/2005 Page 46 of 47
47 Configure SNMP Caution* Configure SNMP. *We recommend that you preload Trap Watcher to avoid administrative access by users. Setting Time and NTP Yes All Cisco routers provide an array of time-of-day services. These services allow the products to accurately keep track of the current time and date, to synchronize multiple products to the same time, and to provide time services to other systems. Configuring Cisco IOS IPSec using Pre- Shared Keys Configuring Cisco IOS IPSec with Pre- Shared Keys using SDM Configuring Cisco GRE IPSec Tunnel using SDM Yes Yes Yes The XYZ Company has purchased Cisco routers and wants to create a secure VPN over the Internet between two sites. The company wants to configure a secure VPN gateway using IPSec between two Cisco routers to use pre-shared keys for authentication. In this lab, the student will learn the following objectives: Prepare to configure Virtual Private Network (VPN) Support, Configure VPN tunnel using SDM VPN Wizard, Modify IKE and IP Security (IPSec) configuration, Verify and test IPSec configuration In this lab, the student will learn the following objectives: Prepare to configure Virtual Private Network (VPN) Support, Configure GRE/IPSec tunnel using SDM VPN Wizard, Modify GRE/IPSec configuration, Verify and test GRE/IPSec configuration. Configure IPSec using Digital Certificates Yes* The XYZ Company has purchased Cisco routers and wants to create a secure Virtual Private Network (VPN) over the Internet between two sites. The company wants to configure a secure VPN gateway using IPSec between two Cisco routers using a certificate authority. *A supported CA server must be loaded on Backbone Server or other PC. Depending on the CA product used, you might have to run Windows 2000 or Windows 2003 server to support this exercise. Configure Remote Access Using Cisco Easy VPN Yes* In this lab exercise, the team will configure a Cisco Easy VPN Server given a Cisco 2600 Series router, and a Cisco VPN Client 3.5 given a PC running Windows Upon completion of these configuration tasks, the group will test the connectivity between. *BB must be configured for direct access to support this lab. Configure Cisco Easy VPN Server with NAT Yes In this lab, students will use the Network Address Translation (NAT) and Port Address Translation (PAT) to hide internal addresses. 4/29/2005 Page 47 of 47
Basic Router Pod Version 2 BETA
 Basic Router Pod Version 2 BETA Planning and Installation Guide For Cisco Networking Academy CCNA & CCNP Curriculum Document Version: 2005-11-26 NETLAB Academy Edition features two variations of the Basic
Basic Router Pod Version 2 BETA Planning and Installation Guide For Cisco Networking Academy CCNA & CCNP Curriculum Document Version: 2005-11-26 NETLAB Academy Edition features two variations of the Basic
Basic Switch Pod Version 2
 Basic Switch Pod Version 2 Planning and Installation Guide For Cisco Networking Academy CCNA Curriculum Document Version: 2008.10.07 NETLAB Academy Edition features two variations of the Basic Switch Pod.
Basic Switch Pod Version 2 Planning and Installation Guide For Cisco Networking Academy CCNA Curriculum Document Version: 2008.10.07 NETLAB Academy Edition features two variations of the Basic Switch Pod.
Basic Router Pod Planning and Installation Guide
 Basic Router Pod Planning and Installation Guide For Cisco Networking Academy CCNA 3.x Curriculum Document Version: 2005-09-03 Copyright 2005, Network Development Group, Inc. NETLAB Academy Edition and
Basic Router Pod Planning and Installation Guide For Cisco Networking Academy CCNA 3.x Curriculum Document Version: 2005-09-03 Copyright 2005, Network Development Group, Inc. NETLAB Academy Edition and
Advanced Router Pod Planning and Installation Guide
 Advanced Router Pod Planning and Installation Guide For Cisco Networking Academy CCNA 3.x/CCNP 3.x Curriculums Document Version: 2005-06-03 Copyright 2005, Network Development Group, Inc. NETLAB Academy
Advanced Router Pod Planning and Installation Guide For Cisco Networking Academy CCNA 3.x/CCNP 3.x Curriculums Document Version: 2005-06-03 Copyright 2005, Network Development Group, Inc. NETLAB Academy
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab Troubleshooting VTP Configuration
 Lab 4.4.3 Troubleshooting VTP Configuration Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask S1 VLAN 99 172.17.99.11 255.255.255.0 S2 VLAN 99 172.17.99.12 255.255.255.0
Lab 4.4.3 Troubleshooting VTP Configuration Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask S1 VLAN 99 172.17.99.11 255.255.255.0 S2 VLAN 99 172.17.99.12 255.255.255.0
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Lab Configure Routing Authentication and Filtering
 Lab 2.5.7 Configure Routing Authentication and Filtering Objective Scenario Topology In this lab, the students will complete the following tasks: Configure routing protocol authentication Configure route
Lab 2.5.7 Configure Routing Authentication and Filtering Objective Scenario Topology In this lab, the students will complete the following tasks: Configure routing protocol authentication Configure route
Lab 6.4.2: Challenge Inter-VLAN Routing
 Lab 6.4.2: Challenge Inter-VLAN Routing Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.99.11 255.255.255.0 192.168.99.1 S2 VLAN
Lab 6.4.2: Challenge Inter-VLAN Routing Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.99.11 255.255.255.0 192.168.99.1 S2 VLAN
CCNA Security 1.0 Student Packet Tracer Manual
 1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
Case Study. Routing & Switching. Cisco Networking Academy Routing and Switching: Scaling Network Case Study
 Case Study Routing & Switching Cisco Networking Academy Routing and Switching: Scaling Network Case Study Overview and Objectives This case study allows students to build and configure a complex network
Case Study Routing & Switching Cisco Networking Academy Routing and Switching: Scaling Network Case Study Overview and Objectives This case study allows students to build and configure a complex network
Skills Assessment Student Training
 Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
The primary audience for this course includes Network Administrators, Network Engineers,
 CCNA COURSE DESCRIPTION: Cisco Certified Network Associate (CCNA) validates the ability to install, configure, operate, and troubleshoot medium-size route and switched networks, including implementation
CCNA COURSE DESCRIPTION: Cisco Certified Network Associate (CCNA) validates the ability to install, configure, operate, and troubleshoot medium-size route and switched networks, including implementation
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Case Study. Routing & Switching. Cisco Networking Academy Routing and Switching: Scaling Network Case Study
 Case Study Routing & Switching Cisco Networking Academy Routing and Switching: Scaling Network Case Study Overview and Objectives This case study allows students to build and configure a complex network
Case Study Routing & Switching Cisco Networking Academy Routing and Switching: Scaling Network Case Study Overview and Objectives This case study allows students to build and configure a complex network
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Correcting RIPv2 Routing Problems
 Lab 9.4.2 Correcting RIPv2 Routing Problems e Interface IP Address Subnet Mask Default Gateway Device Host Name Interface IP Address Subnet Mask Default Gateway R1 BRANCH1 Fast Ethernet 0/0 172.16.0.1
Lab 9.4.2 Correcting RIPv2 Routing Problems e Interface IP Address Subnet Mask Default Gateway Device Host Name Interface IP Address Subnet Mask Default Gateway R1 BRANCH1 Fast Ethernet 0/0 172.16.0.1
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Chapter 4. Network Security. Part II
 Chapter 4 Network Security Part II CCNA4-1 Chapter 4-2 Introducing Network Security Securing Cisco Routers CCNA4-2 Chapter 4-2 Router Security Issues The Role of Routers in Network Security: Router security
Chapter 4 Network Security Part II CCNA4-1 Chapter 4-2 Introducing Network Security Securing Cisco Routers CCNA4-2 Chapter 4-2 Router Security Issues The Role of Routers in Network Security: Router security
Lab 7.5.1: Basic Wireless Configuration
 Topology Diagram Learning Objectives Configure options in the Linksys Setup tab. Configure options in the Linksys Wireless tab. Configure options in the Linksys Administration tab. Configure options in
Topology Diagram Learning Objectives Configure options in the Linksys Setup tab. Configure options in the Linksys Wireless tab. Configure options in the Linksys Administration tab. Configure options in
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
CCNA Boot Camp. Course Description
 CCNA Boot Camp Course Description CCNA Boot Camp combines both the Interconnecting Cisco Network Devices Part 1 (ICND1) course and the Interconnecting Cisco Network Devices Part 2 (ICND2) course into one
CCNA Boot Camp Course Description CCNA Boot Camp combines both the Interconnecting Cisco Network Devices Part 1 (ICND1) course and the Interconnecting Cisco Network Devices Part 2 (ICND2) course into one
CCNA DISCOVERY V4.0 WORKING AT A SMALL-TO-MEDIUM BUSINESS OR ISP INSTRUCTOR REFERENCE GUIDE. Prepared by Cisco Learning Institute
 CCNA DISCOVERY V4.0 WORKING AT A SMALL-TO-MEDIUM BUSINESS OR ISP COMPARISON OF NEW CURRICULA WITH EXISTING CURRICULA Prepared by Cisco Learning Institute June 25, 2007 Working for a Small-to-Medium Business
CCNA DISCOVERY V4.0 WORKING AT A SMALL-TO-MEDIUM BUSINESS OR ISP COMPARISON OF NEW CURRICULA WITH EXISTING CURRICULA Prepared by Cisco Learning Institute June 25, 2007 Working for a Small-to-Medium Business
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Chapter 2 Lab 2-1, Static VLANS, VLAN Trunking, and VTP Domains and Modes
 Chapter 2 Lab 2-1, Static VLANS, VLAN Trunking, and VTP Domains and Modes Topology Objectives Background Set up a VTP domain. Create and maintain VLANs. Configure ISL and 802.1Q trunking. VLANs logically
Chapter 2 Lab 2-1, Static VLANS, VLAN Trunking, and VTP Domains and Modes Topology Objectives Background Set up a VTP domain. Create and maintain VLANs. Configure ISL and 802.1Q trunking. VLANs logically
Interconnecting Cisco Networking Devices Part 1 ICND1
 Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
CCNA Exploration Network Fundamentals
 CCNA Exploration 4.0 1. Network Fundamentals The goal of this course is to introduce you to fundamental networking concepts and technologies. These online course materials will assist you in developing
CCNA Exploration 4.0 1. Network Fundamentals The goal of this course is to introduce you to fundamental networking concepts and technologies. These online course materials will assist you in developing
Objectives. Classes of threats to networks. Network Security. Common types of network attack. Mitigation techniques to protect against threats
 ITE I Chapter 6 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 1 Objectives Enterprise Network Security Describe the general methods used to mitigate security threats to Enterprise networks
ITE I Chapter 6 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 1 Objectives Enterprise Network Security Describe the general methods used to mitigate security threats to Enterprise networks
TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE. Modified
 TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE Modified 2017-07-10 TestOut Routing and Switching Pro Outline- English 6.0.x Videos: 133 (15:42:34) Demonstrations: 78 (7:22:19) Simulations:
TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE Modified 2017-07-10 TestOut Routing and Switching Pro Outline- English 6.0.x Videos: 133 (15:42:34) Demonstrations: 78 (7:22:19) Simulations:
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
Lab Configuring an ISR with SDM Express
 Lab 5.2.3 Configuring an ISR with SDM Express Objectives Configure basic router global settings router name, users, and login passwords using Cisco SDM Express. Configure LAN and Internet connections on
Lab 5.2.3 Configuring an ISR with SDM Express Objectives Configure basic router global settings router name, users, and login passwords using Cisco SDM Express. Configure LAN and Internet connections on
Lab - Troubleshooting VLAN Configurations (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
CCNA. Course Catalog
 CCNA Course Catalog 2012-2013 This course is intended for the following audience: Network Administrator Network Engineer Systems Engineer CCNA Exam Candidates Cisco Certified Network Associate (CCNA 640-802)
CCNA Course Catalog 2012-2013 This course is intended for the following audience: Network Administrator Network Engineer Systems Engineer CCNA Exam Candidates Cisco Certified Network Associate (CCNA 640-802)
Remote PC Guide for VMware Implementation Using ESXi Version 3.5/4.01
 Remote PC Guide for VMware Implementation Using ESXi Version 3.5/4.01 Document Version: 2010-10-22 This guide is a primer for adding remotely accessible PC or servers into your NETLAB Academy Edition or
Remote PC Guide for VMware Implementation Using ESXi Version 3.5/4.01 Document Version: 2010-10-22 This guide is a primer for adding remotely accessible PC or servers into your NETLAB Academy Edition or
Lab Configuring Dynamic and Static NAT (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 7 Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1.1 192.168.1.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 7 Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1.1 192.168.1.1
VMware Server. Virtual PC Basics. VMware is a registered trademark of VMware, Inc. (an EMC company).
 VMware Server Virtual PC Basics VMware is a registered trademark of VMware, Inc. (an EMC company). NDG Customer Support Kaan Uzun, NDG Support Manager Email: support@netdevgroup.com Customers Receive Software
VMware Server Virtual PC Basics VMware is a registered trademark of VMware, Inc. (an EMC company). NDG Customer Support Kaan Uzun, NDG Support Manager Email: support@netdevgroup.com Customers Receive Software
Lab 9.6.3: EIGRP Troubleshooting Lab
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 172.18.64.1 255.255.192.0 N/A HQ S0/0/0 209.165.202.129 255.255.255.252 N/A S0/0/1 209.165.202.133 255.255.255.252
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 172.18.64.1 255.255.192.0 N/A HQ S0/0/0 209.165.202.129 255.255.255.252 N/A S0/0/1 209.165.202.133 255.255.255.252
Configuring High Availability (HA)
 4 CHAPTER This chapter covers the following topics: Adding High Availability Cisco NAC Appliance To Your Network, page 4-1 Installing a Clean Access Manager High Availability Pair, page 4-3 Installing
4 CHAPTER This chapter covers the following topics: Adding High Availability Cisco NAC Appliance To Your Network, page 4-1 Installing a Clean Access Manager High Availability Pair, page 4-3 Installing
Lab Configuring EtherChannel
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask S1 VLAN 99 192.168.99.11 255.255.255.0 S2 VLAN 99 192.168.99.12 255.255.255.0 S3 VLAN 99 192.168.99.13 255.255.255.0 PC-A NIC
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask S1 VLAN 99 192.168.99.11 255.255.255.0 S2 VLAN 99 192.168.99.12 255.255.255.0 S3 VLAN 99 192.168.99.13 255.255.255.0 PC-A NIC
Case Study. WANs. Cisco Networking Academy Program CCNA 4: WAN Technologies v3.0
 Case Study WANs Cisco Networking Academy Program CCNA 4: WAN Technologies v3.0 Overview and Objectives This final case study shows you how to build and configure a complex network using the skills you
Case Study WANs Cisco Networking Academy Program CCNA 4: WAN Technologies v3.0 Overview and Objectives This final case study shows you how to build and configure a complex network using the skills you
Interconnecting Cisco Networking Devices: Accelerated
 Interconnecting Cisco Networking Devices: Accelerated CCNAX v3.0; 5 days, Instructor-led Course Description The Cisco CCNA curriculum includes a third course, Interconnecting Cisco Networking Devices:
Interconnecting Cisco Networking Devices: Accelerated CCNAX v3.0; 5 days, Instructor-led Course Description The Cisco CCNA curriculum includes a third course, Interconnecting Cisco Networking Devices:
Skills Assessment Student Training Exam
 Skills Assessment Student Training Exam Topology Assessment Objectives Part 1: Initialize Devices (2 points, 5 minutes) Part 2: Configure Device Basic Settings (18 points, 20 minutes) Part 3: Configure
Skills Assessment Student Training Exam Topology Assessment Objectives Part 1: Initialize Devices (2 points, 5 minutes) Part 2: Configure Device Basic Settings (18 points, 20 minutes) Part 3: Configure
Scenario Labs NETSIM FOR CCNA LAB MANUAL. Scenario Labs. Boson NetSim for CCNA Lab Manual
 NETSIM FOR CCNA LAB MANUAL Welcome to the NetSim. The goal of these labs is to introduce you to the limited number of commands needed to enable a technology, without addressing extra commands that could
NETSIM FOR CCNA LAB MANUAL Welcome to the NetSim. The goal of these labs is to introduce you to the limited number of commands needed to enable a technology, without addressing extra commands that could
Lab Using the CLI to Gather Network Device Information Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System. Proposed by Jedadiah Casey. Introduction
 Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview
 Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview This course will teach students about building a simple network, establishing internet connectivity, managing network device security,
Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview This course will teach students about building a simple network, establishing internet connectivity, managing network device security,
COPYRIGHTED MATERIAL. Table of Contents. Assessment Test
 10089.book Page xi Monday, July 23, 2007 3:17 PM Introduction Assessment Test xxiii xxxiii Chapter 1 Internetworking 1 Internetworking Basics 4 Internetworking Models 11 The Layered Approach 12 Advantages
10089.book Page xi Monday, July 23, 2007 3:17 PM Introduction Assessment Test xxiii xxxiii Chapter 1 Internetworking 1 Internetworking Basics 4 Internetworking Models 11 The Layered Approach 12 Advantages
"Charting the Course... Interconnecting Cisco Networking Devices Accelerated 3.0 (CCNAX) Course Summary
 Description Course Summary The Cisco CCNA curriculum includes a third course, Interconnecting Cisco Networking Devices: Accelerated (CCNAX), consisting of Interconnecting Cisco Networking Devices, Part
Description Course Summary The Cisco CCNA curriculum includes a third course, Interconnecting Cisco Networking Devices: Accelerated (CCNAX), consisting of Interconnecting Cisco Networking Devices, Part
CCNA Routing and Switching (NI )
 CCNA Routing and Switching (NI400+401) 150 Hours ` Outline The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that is
CCNA Routing and Switching (NI400+401) 150 Hours ` Outline The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that is
Cisco Certified Network Associate ( )
 Cisco Certified Network Associate (200-125) Exam Description: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that
Cisco Certified Network Associate (200-125) Exam Description: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment that
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3
 Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Deploying Cisco ASA Firewall Solutions (FIREWALL) v2.0. Global Knowledge European Remote Labs Instructor Guide
 Deploying Cisco ASA Firewall Solutions (FIREWALL) v2.0 Global Knowledge European Remote Labs Instructor Guide 1. Contents 1. Contents... 2 2. Introduction... 3 3. Remote Labs Topology, Connections and
Deploying Cisco ASA Firewall Solutions (FIREWALL) v2.0 Global Knowledge European Remote Labs Instructor Guide 1. Contents 1. Contents... 2 2. Introduction... 3 3. Remote Labs Topology, Connections and
CCNA Security PT Practice SBA
 A few things to keep in mind while completing this activity: 1. Do not use the browser Back button or close or reload any Exam windows during the exam. 2. Do not close Packet Tracer when you are done.
A few things to keep in mind while completing this activity: 1. Do not use the browser Back button or close or reload any Exam windows during the exam. 2. Do not close Packet Tracer when you are done.
UniNets CCNA Security LAB MANUAL UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL UniNets CCNA LAB MANUAL
 UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
Scope and Sequence: CCNA Exploration v4.0
 Scope and Sequence: CCNA Exploration v4.0 Last Updated August 30, 2007 The course objectives and outline for the final two CCNA Exploration courses, LAN Switching and Wireless and Accessing the WAN, are
Scope and Sequence: CCNA Exploration v4.0 Last Updated August 30, 2007 The course objectives and outline for the final two CCNA Exploration courses, LAN Switching and Wireless and Accessing the WAN, are
RealCiscoLAB.com. Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions
 RealCiscoLAB.com CCNPv6 SWITCH Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions Topology Objective Background Route between VLANs using a 3560 switch with an internal route
RealCiscoLAB.com CCNPv6 SWITCH Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions Topology Objective Background Route between VLANs using a 3560 switch with an internal route
Lab - Configuring VLANs and Trunking (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3
Lecture (06) Design and Configuration LAN Practicing, working on CISCO equipment. By: Dr. Ahmed ElShafee
 Lecture (06) Design and Configuration LAN Practicing, working on CISCO equipment By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2015, Practical App. Networks II Part I ٢ ٣ SW01 steps firstly connect
Lecture (06) Design and Configuration LAN Practicing, working on CISCO equipment By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2015, Practical App. Networks II Part I ٢ ٣ SW01 steps firstly connect
VMware vsphere 5.5: Install, Configure, Manage Lab Addendum. Lab 3: Configuring VMware ESXi
 VMware vsphere 5.5: Install, Configure, Manage Lab Addendum Lab 3: Configuring VMware ESXi Document Version: 2014-07-08 Copyright Network Development Group, Inc. www.netdevgroup.com NETLAB Academy Edition,
VMware vsphere 5.5: Install, Configure, Manage Lab Addendum Lab 3: Configuring VMware ESXi Document Version: 2014-07-08 Copyright Network Development Group, Inc. www.netdevgroup.com NETLAB Academy Edition,
Lab - Configuring VLANs and Trunking
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3 255.255.255.0
Scope and Sequence: CCNA Discovery
 Scope and Sequence: CCNA Discovery Last updated April 22, 2008 Target Audience CCNA Discovery is primarily designed for Cisco Networking Academy students who are looking for career-oriented, information
Scope and Sequence: CCNA Discovery Last updated April 22, 2008 Target Audience CCNA Discovery is primarily designed for Cisco Networking Academy students who are looking for career-oriented, information
Lab 5.6.2: Challenge RIP Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
Lab - Configuring VLANs and Trunking
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3 255.255.255.0
Chapter 8: Lab B: Configuring a Remote Access VPN Server and Client
 Chapter 8: Lab B: Configuring a Remote Access VPN Server and Client Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 FA0/1 192.168.1.1 255.255.255.0 N/A
Chapter 8: Lab B: Configuring a Remote Access VPN Server and Client Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 FA0/1 192.168.1.1 255.255.255.0 N/A
Lab 3.4.6a Configure the PIX Security Appliance using Setup Mode and ASDM Startup Wizard
 Lab 3.4.6a Configure the PIX Security Appliance using Setup Mode and ASDM Startup Wizard Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Verify that the
Lab 3.4.6a Configure the PIX Security Appliance using Setup Mode and ASDM Startup Wizard Objective Scenario Topology In this lab exercise, the students will complete the following tasks: Verify that the
Note: Use two 2960 switches for ALS1 and ALS2 and two 3560 switches for DLS1 and DLS2
 LAB 2 - Part I - VLANs, VLAN Trunking, and VTP Domains Topology: Objectives Set up a VTP domain. Create and maintain VLANs. Configure 802.1Q trunking. Background VLANs logically segment a network by function,
LAB 2 - Part I - VLANs, VLAN Trunking, and VTP Domains Topology: Objectives Set up a VTP domain. Create and maintain VLANs. Configure 802.1Q trunking. Background VLANs logically segment a network by function,
Device Interface IP Address Subnet Mask Default Gateway
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP Fa0/0 172.20.1.129 255.255.255.128 N/A S0/0/0 172.20.1.1 255.255.255.128 N/A Fa0/0 172.20.0.129 255.255.255.128
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP Fa0/0 172.20.1.129 255.255.255.128 N/A S0/0/0 172.20.1.1 255.255.255.128 N/A Fa0/0 172.20.0.129 255.255.255.128
PT Activity 8.6.1: CCNA Skills Integration Challenge Topology Diagram
 Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 Addressing Table for HQ Device Interface IP Address Subnet
Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 Addressing Table for HQ Device Interface IP Address Subnet
Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools
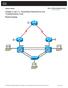 Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools Physical Topology All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools Physical Topology All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
ASM Educational Center (ASM) Est Cisco CCNA Routing and Switching Certification
 Cisco CCNA Routing and Switching Certification Course Outline Module 1: Building a Simple Network Objective: Describe network fundamentals and implement a simple LAN. Lesson 1: Exploring the Functions
Cisco CCNA Routing and Switching Certification Course Outline Module 1: Building a Simple Network Objective: Describe network fundamentals and implement a simple LAN. Lesson 1: Exploring the Functions
Course Outline. CCNA - Interconnecting Cisco Networking Devices Part 1 and 2.
 Course Outline CCNA - Interconnecting Cisco Networking Devices Part 1 17 Oct 2018 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert
Course Outline CCNA - Interconnecting Cisco Networking Devices Part 1 17 Oct 2018 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert
CCNA Routing and Switching ucertify Network Simulator. Course Outline. 30 Oct ( Add-On )
 Course Outline CCNA Routing and Switching 200125 ucertify Network 30 Oct 2018 ( Add-On ) Contents 1. Course Objective 2. Expert Instructor-Led Training 3. ADA Compliant & JAWS Compatible Platform 4. State
Course Outline CCNA Routing and Switching 200125 ucertify Network 30 Oct 2018 ( Add-On ) Contents 1. Course Objective 2. Expert Instructor-Led Training 3. ADA Compliant & JAWS Compatible Platform 4. State
Lab 6-1 Configuring a WLAN Controller
 Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario Step 1 In the next two labs, you will configure a wireless solution involving a WLAN controller, two lightweight wireless access points,
Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario Step 1 In the next two labs, you will configure a wireless solution involving a WLAN controller, two lightweight wireless access points,
Lab 1. CLI Navigation. Scenario. Initial Configuration for R1
 Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
CCNA Semester 3 labs. Labs for chapters 2 10
 CCNA Semester 3 labs Labs for chapters 2 10 2.1.4.5 Lab - Configure Extended VLANs, VTP, and DTP 2.2.2.5 Lab - Troubleshooting Inter-VLAN Routing 3.1.2.12 Lab - Building a Switched Network with Redundant
CCNA Semester 3 labs Labs for chapters 2 10 2.1.4.5 Lab - Configure Extended VLANs, VTP, and DTP 2.2.2.5 Lab - Troubleshooting Inter-VLAN Routing 3.1.2.12 Lab - Building a Switched Network with Redundant
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example
 LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Scope and Sequence: CCNA Discovery v4.0
 Scope and Sequence: CCNA Discovery v4.0 Last Updated August 30, 2007 The course objectives and outline for the final two CCNA Discovery courses, Introducing Routing and Switching in the Enterprise and
Scope and Sequence: CCNA Discovery v4.0 Last Updated August 30, 2007 The course objectives and outline for the final two CCNA Discovery courses, Introducing Routing and Switching in the Enterprise and
Device Interface IP Address Subnet Mask R1 G0/ N/A
 CSNB214 Packet Tracer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Objectives R1 G0/0 192.168.20.1 255.255.255.0 N/A S1 VLAN 10 S2 VLAN 10 G0/1 192.168.10.1 255.255.255.0
CSNB214 Packet Tracer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Objectives R1 G0/0 192.168.20.1 255.255.255.0 N/A S1 VLAN 10 S2 VLAN 10 G0/1 192.168.10.1 255.255.255.0
Cisco CCNA (ICND1, ICND2) Bootcamp
 Cisco CCNA (ICND1, ICND2) Bootcamp Course Duration: 5 Days Course Overview This five-day course covers the essential topics of ICND1 and ICND2 in an intensive Bootcamp format. It teaches students the skills
Cisco CCNA (ICND1, ICND2) Bootcamp Course Duration: 5 Days Course Overview This five-day course covers the essential topics of ICND1 and ICND2 in an intensive Bootcamp format. It teaches students the skills
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Skills Assessment (EIGRP) Student Training Exam
 Skills Assessment (EIGRP) Student Training Exam Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 16 Addressing Table Assessment Objectives Device
Skills Assessment (EIGRP) Student Training Exam Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 16 Addressing Table Assessment Objectives Device
CCNA. Murlisona App. Hiralal Lane, Ravivar Karanja, Near Pethe High-School, ,
 CCNA Cisco Certified Network Associate (200-125) Exam DescrIPtion: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment
CCNA Cisco Certified Network Associate (200-125) Exam DescrIPtion: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50 60 question assessment
CISCO QUAD Cisco CCENT/CCNA/CCDA/CCNA Security (QUAD)
 Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Our Learning Exclusive Custom exam prep software and materials Exam delivery in classroom with 98% success Course specific thinqtank Learning publications to promote fun exciting learning Extended hours
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab 1-2Connecting to a Cisco Router or Switch via Console. Lab 1-6Basic Graphic Network Simulator v3 Configuration
 MODULE1 GETTING STARTED WITH YOUR CISCO LAB Lab 1-1Identifying Router Components and Accessories Lab 1-2Connecting to a Cisco Router or Switch via Console Lab 1-3Identifying Router & Switch IOS Software
MODULE1 GETTING STARTED WITH YOUR CISCO LAB Lab 1-1Identifying Router Components and Accessories Lab 1-2Connecting to a Cisco Router or Switch via Console Lab 1-3Identifying Router & Switch IOS Software
Laboration 1 Examine the Topology and Basic Troubleshooting Commands
 Laboration 1 Examine the Topology and Basic Troubleshooting Commands Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page
Laboration 1 Examine the Topology and Basic Troubleshooting Commands Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page
ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch
 ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco
ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco
CWT Hands-On Summation Lab 1 Checkpoints 1-8
 CWT Hands-On Summation Lab 1 Checkpoints 1-8 Clear devices prior to starting summation 1. Erase any existing configuration on the routers and switches. On routers (repeat for all routers): R1#erase startup-config
CWT Hands-On Summation Lab 1 Checkpoints 1-8 Clear devices prior to starting summation 1. Erase any existing configuration on the routers and switches. On routers (repeat for all routers): R1#erase startup-config
Installation and Configuration Guide
 Installation and Configuration Guide h-series 800-782-3762 www.edgewave.com 2001 2011 EdgeWave Inc. (formerly St. Bernard Software). All rights reserved. The EdgeWave logo, iprism and iguard are trademarks
Installation and Configuration Guide h-series 800-782-3762 www.edgewave.com 2001 2011 EdgeWave Inc. (formerly St. Bernard Software). All rights reserved. The EdgeWave logo, iprism and iguard are trademarks
