1.264 FINAL EXAM FALL 2012 NAME. Exam guidelines:
|
|
|
- Richard Crawford
- 6 years ago
- Views:
Transcription
1 1.264 FINAL EXAM FALL 2012 NAME Exam guidelines: 1) 80 minutes are allowed to complete the exam. 2) Open notes; open book. a. You may use a web browser on a laptop computer to access the online course texts. No other web pages may be accessed and no other applications may be open at any point during the exam. 3) There are 4 questions (100 points) and 8 pages (including this one) in the exam booklet. 4) Laptops are allowed to access online course books. No cell phones or messaging devices are allowed. Please turn off any that you have brought. 5) Calculators are allowed. 6) Please write legibly you are welcome to use both sides of the paper; we can provide additional paper if necessary. 1
2 PART I: WEB SERVICES AND TELECOM (60 POINTS; SUGGESTED TIME: 50 MINUTES) An ai rline operates a set of flights. A flight has a flight numb er, an origin a irport and a destination airport. All flig hts oper ate da ily. When a passenger books a ti cket, the airline registers t heir name, and assigns the m a specif ic seat o n a flight o n a departure date. Assume al l si mple t ypes are #PCD ATA, except ai rports, whi ch are ei ther BOS, SJU, SFO, JFK, DCA or MAD. 1. Write a DTD file for the airline s set of flights and passenger info. The first line is provided. You may wish to draw a data model and write the XML file (part 2) first. (15 points) <?xml version = "1.0" encoding = "iso "?> (PROVIDED) 2
3 2. Write an XML file that conforms to the DTD that you created in the previous step. Create 2 flights on 2 dates with 2 passengers per flight. (15 points) a. XML File 3
4 b. How will the airline alter the tag names when sending XML to a partner airline, if a partner s XSD or DTD is slightly different for a request or response? (2 points) c. Can the XML file be sent as a Web service response to a request? What are the parameters in the request? (2 points) d. Your airline sends just XML documents to each gate at each airport. What XML standard must a manager at an airport use to display the XML that is sent, so he or she can read it formatted well in a browser? (3 points) e. Your airline is expanding to several airports in Africa, each served by a VSAT terminal with a bandwidth of 9.6 kbps. You send 500 XML messages per hour to each airport; there are many changes in reservations and connections. The XML messages use the format you defined in part (2a) above, and contain 1200 characters (bytes) on average. This XML message traffic is 90% of the traffic on these VSAT links. Will a VSAT link provide sufficient bandwidth to an airport? If not, suggest changes that would make this workable. (4 points) f. Should your African airports validate each XML message against the DTD published on your Web site, by getting the DTD from the Web site for each message received, or is there a simpler procedure that is acceptable? (3 points) 4
5 g. What technology would you use if you were in the same city as the VSAT carrier and you wanted to do this at lowest cost? The VSAT carrier has access to the open Internet and also subscribes to a carrier s Metro Ethernet service, which would cost you $3,000 per month to use and provides 1 Gbps. You are two miles from a central office that offers a wide range of data services, and you are served by a CATV company that offers data services at your location. The telco (central office), CATV and open Internet services cost about $300 per month for 1.5 Mbps (3 points). h. In question (g), what security measures would you use? Briefly justify. (3 points) i. Does each African airport need a Web server for its end of these transactions? An app server? A database server? Explain why or why not. All applications used by any airport are provided from the airline s main data center and are accessed via Web browsers. (3 points) 5
6 j. Does each African airport need a load balancer? A firewall? A router? Explain why or why not. (3 points) k. The CATV carrier serving one of the African airports offers you dedicated use of one 6 MHz CATV channel over which you can run Ethernet between the airport terminal and your maintenance facility on the other side of the airport. The signal-to-noise ratio of this channel is 27; the maximum utilization for Ethernet is 50%. What is the bandwidth, in megabits per second (Mbps), of this channel? Would this be sufficient to stream 4 MPEG-2 (6 Mbps) high-quality security video feeds between the terminal and the maintenance facility? (4 points) 6
7 PART II: SECURITY (40 POINTS; SUGGESTED TIME: 30 MINUTES) 3. Medical Supply Chain Security (20 points) a. Outline how an attack can be launched against a user with a laptop at an Internet café who logs into a medical supply chain Web site from an http (not https) home page, even if all subsequent pages are https (SSL) pages. (7 points) b. Suppose the supply chain companies form a consortium to issue password generator cards that create a new 8 digit passcode every 30 seconds (e.g., Secure-ID) to all their employees. The employee must enter this 8 digit code as part of their password. (There is also a fixed password that the employee chooses and enters, as usual.) They leave their home pages as before (http, but with all pages after login as https). Does this combat the attack in part a above? (7 points) c. What new vulnerability, if any, has the consortium introduced in part b above? (3 points) 7
8 d. Some of the password generator cards are stolen, or not returned by employees who leave their companies. Is this a security risk? Briefly give your reasons pro or con. If it is a risk, describe at least one attack that can be executed with a stolen password generator card. (3 points) 4. Truck at a Security Gate (20 points) a. Write the protocol notation for the following security system: (5 points) Truck pulls up to gate at terminal Truck electronic card sends its id and a nonce (sequential number) to gate, encrypted with gate public key Gate checks its database, opens if ID is valid and nonce is greater than the last nonce sent, unless last nonce sent and stored in database was largest number possible. In that case, any nonce is accepted b. List at least two possible attacks against this protocol that may succeed. (10 points) c. List one possible attack against security protocols that this protocol can usually withstand. (5 points) 8
9 MIT OpenCourseWare J / ESD.264J Database, Internet, and Systems Integration Technologies Fall 2013 For information about citing these materials or our Terms of Use, visit:
1.264 FINAL EXAM FALL 2012 NAME. Exam guidelines:
 1.264 FINAL EXAM FALL 2012 NAME Exam guidelines: 1) 80 minutes are allowed to complete the exam. 2) Open notes; open book. a. You may use a web browser on a laptop computer to access the online course
1.264 FINAL EXAM FALL 2012 NAME Exam guidelines: 1) 80 minutes are allowed to complete the exam. 2) Open notes; open book. a. You may use a web browser on a laptop computer to access the online course
1.204 Quiz 1. Spring Name. Exam guidelines:
 1.204 Quiz 1 Spring 2008 Name Exam guidelines: 1) 80 minutes are allowed to complete the quiz. 2) Open notes; open book. 3) There are 4 questions (100 points) and 7 pages (including this one) in the exam
1.204 Quiz 1 Spring 2008 Name Exam guidelines: 1) 80 minutes are allowed to complete the quiz. 2) Open notes; open book. 3) There are 4 questions (100 points) and 7 pages (including this one) in the exam
IP PBXs (private branch exchanges) (page 7) are branch phone switches that handle voice over IP: voice calls go over the data network.
 Homework 10 1.264, Fall 2013 Communications, and software process Due: Friday, December 6 A. Communications Read the Qwest response to the Request for Information (RFI) on Carrier Ethernet, which is posted
Homework 10 1.264, Fall 2013 Communications, and software process Due: Friday, December 6 A. Communications Read the Qwest response to the Request for Information (RFI) on Carrier Ethernet, which is posted
1.264 Lecture 32 (Solutions)
 1.264 Lecture 32 (Solutions) Telecom: Basic technology Next class: Green chapter 4, 6, 7, 10. Exercise due before class 1 Exercise 1 Communications at warehouse A warehouse scans its inventory with RFID
1.264 Lecture 32 (Solutions) Telecom: Basic technology Next class: Green chapter 4, 6, 7, 10. Exercise due before class 1 Exercise 1 Communications at warehouse A warehouse scans its inventory with RFID
c. Is the VPN running over the open Internet? Yes. This is why the VPN encryption/security is required.
 Homework 10 1.264, Fall 2013 Communications, and software process A. Communications 1. VPN a. What bandwidth is provided over the IPsec VPN DSL links from Green Bay, WI and Chicago IL? Look up the typical
Homework 10 1.264, Fall 2013 Communications, and software process A. Communications 1. VPN a. What bandwidth is provided over the IPsec VPN DSL links from Green Bay, WI and Chicago IL? Look up the typical
CSCI 466 Midterm Networks Fall 2013
 CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
White Paper Broadband Multimedia Servers for IPTV Design options with ATCA
 Internet channels provide individual audiovisual content on demand. Such applications are frequently summarized as IPTV. Applications include the traditional programmed Video on Demand from a library of
Internet channels provide individual audiovisual content on demand. Such applications are frequently summarized as IPTV. Applications include the traditional programmed Video on Demand from a library of
THE INFORMATION CONTAINED IN THIS DOCUMENT IS CONFIDENTIAL AND PROPRIETARY TO TRAVELPORT.
 September 2013 THE INFORMATION CONTAINED IN THIS DOCUMENT IS CONFIDENTIAL AND PROPRIETARY TO TRAVELPORT. Copyright Copyright 2013 Travelport and/or its subsidiaries. All rights reserved. Travelport provides
September 2013 THE INFORMATION CONTAINED IN THIS DOCUMENT IS CONFIDENTIAL AND PROPRIETARY TO TRAVELPORT. Copyright Copyright 2013 Travelport and/or its subsidiaries. All rights reserved. Travelport provides
On the Web and the BlackBerry
 TripIt and TripIt Pro On the Web and the BlackBerry March 26 2013 Use TripIt to manage your entire trip flight, rental car, hotel, dining, meetings, and events in a single master itinerary. TripIt lets
TripIt and TripIt Pro On the Web and the BlackBerry March 26 2013 Use TripIt to manage your entire trip flight, rental car, hotel, dining, meetings, and events in a single master itinerary. TripIt lets
Authentication & Authorization
 Authentication & Authorization Anuj Gupta 1, 1 M.Tech Scholar, Department of C.F.I.S, G.I.T.A.M, Kablana, Jhajjar Ashish Kumar Sharma 2 2 Assistant Professor, Department of C.F.I.S & C.S.E, G.I.T.A.M,
Authentication & Authorization Anuj Gupta 1, 1 M.Tech Scholar, Department of C.F.I.S, G.I.T.A.M, Kablana, Jhajjar Ashish Kumar Sharma 2 2 Assistant Professor, Department of C.F.I.S & C.S.E, G.I.T.A.M,
EECS 122: Introduction to Communication Networks Final Exam Solutions
 EECS 22: Introduction to Communication Networks Final Exam Solutions Problem. (6 points) How long does it take for a 3000-byte IP packet to go from host A to host B in the figure below. Assume the overhead
EECS 22: Introduction to Communication Networks Final Exam Solutions Problem. (6 points) How long does it take for a 3000-byte IP packet to go from host A to host B in the figure below. Assume the overhead
Scholastic Learning Zone User s Guide
 Scholastic Learning Zone User s Guide Copyright 2016 by Scholastic Inc. All rights reserved. Published by Scholastic Inc. SCHOLASTIC, SCHOLASTIC LEARNING ZONE, TRUEFLIX, BOOKFLIX, and associated logos
Scholastic Learning Zone User s Guide Copyright 2016 by Scholastic Inc. All rights reserved. Published by Scholastic Inc. SCHOLASTIC, SCHOLASTIC LEARNING ZONE, TRUEFLIX, BOOKFLIX, and associated logos
1.264 Lecture 27. Security protocols Symmetric cryptography. Next class: Anderson chapter 10. Exercise due after class
 1.264 Lecture 27 Security protocols Symmetric cryptography Next class: Anderson chapter 10. Exercise due after class 1 Exercise: hotel keys What is the protocol? What attacks are possible? Copy Cut and
1.264 Lecture 27 Security protocols Symmetric cryptography Next class: Anderson chapter 10. Exercise due after class 1 Exercise: hotel keys What is the protocol? What attacks are possible? Copy Cut and
PLEASE WRITE NEATLY I need to be able to read your answers! (seemingly encrypted solutions can not be decrypted!)
 FINAL Exam: Off campus students (same exam as for on campus students) CMPSCI 453/591 ST550A: Computer Networks Spring 2002 Prof. Jim Kurose Instructions: Put your name and student number on the exam books
FINAL Exam: Off campus students (same exam as for on campus students) CMPSCI 453/591 ST550A: Computer Networks Spring 2002 Prof. Jim Kurose Instructions: Put your name and student number on the exam books
Agenda. Live Demo of TripCase. I. TripCase overview II. III. Invoice retrieval. IV. Mobile App V. FAQ VI. Q & A
 TripCase 1 Agenda I. TripCase overview II. Live Demo of TripCase III. Invoice retrieval IV. Mobile App V. FAQ VI. Q & A 2 Overview Your Travel Itinerary is Changing, and for the Better! Major Enhancements:
TripCase 1 Agenda I. TripCase overview II. Live Demo of TripCase III. Invoice retrieval IV. Mobile App V. FAQ VI. Q & A 2 Overview Your Travel Itinerary is Changing, and for the Better! Major Enhancements:
CS 640: Introduction to Computer Networks
 CS 640: Introduction to Computer Networks Midterm II 12/14/2006 Allotted time: 11:00AM to 12:40 PM (100 minutes) Name: UW -ID Number: 1. There are 7 questions in this mid-term. All 7 must be answered for
CS 640: Introduction to Computer Networks Midterm II 12/14/2006 Allotted time: 11:00AM to 12:40 PM (100 minutes) Name: UW -ID Number: 1. There are 7 questions in this mid-term. All 7 must be answered for
Scholastic Learning Zone User s Guide
 Scholastic Learning Zone User s Guide Copyright 2015 by Scholastic Inc. All rights reserved. Published by Scholastic Inc. SCHOLASTIC, SCHOLASTIC LEARNING ZONE, TRUEFLIX, BOOKFLIX, and associated logos
Scholastic Learning Zone User s Guide Copyright 2015 by Scholastic Inc. All rights reserved. Published by Scholastic Inc. SCHOLASTIC, SCHOLASTIC LEARNING ZONE, TRUEFLIX, BOOKFLIX, and associated logos
1.264 Lecture 23. Telecom Enterprise networks MANs, WANs
 1.264 Lecture 23 Telecom Enterprise networks MANs, WANs Enterprise networks Connections within enterprise External connections Remote offices Employees Customers Business partners, supply chain partners
1.264 Lecture 23 Telecom Enterprise networks MANs, WANs Enterprise networks Connections within enterprise External connections Remote offices Employees Customers Business partners, supply chain partners
1.264 Lecture 26. Security protocols. Next class: Anderson chapter 4. Exercise due before class
 1.264 Lecture 26 Security protocols Next class: Anderson chapter 4. Exercise due before class 1 Encryption Encryption is the process of: Transforming information (referred to as plaintext) Using an algorithm
1.264 Lecture 26 Security protocols Next class: Anderson chapter 4. Exercise due before class 1 Encryption Encryption is the process of: Transforming information (referred to as plaintext) Using an algorithm
Router Router Microprocessor controlled traffic direction home router DSL modem Computer Enterprise routers Core routers
 Router Router is a Microprocessor controlled device that forwards data packets across the computer network. It is used to connect two or more data lines from different net works. The function of the router
Router Router is a Microprocessor controlled device that forwards data packets across the computer network. It is used to connect two or more data lines from different net works. The function of the router
The Internet and the World Wide Web
 Technology Briefing The Internet and the World Wide Web TB5-1 Learning Objectives TB5-2 Learning Objectives TB5-3 How Did the Internet Get Started? Internet derived from internetworking 1960s U.S. Defense
Technology Briefing The Internet and the World Wide Web TB5-1 Learning Objectives TB5-2 Learning Objectives TB5-3 How Did the Internet Get Started? Internet derived from internetworking 1960s U.S. Defense
CSci530 Final Exam. Fall 2011
 CSci530 Final Exam Fall 2011 Instructions: Show all work. No electronic devices are allowed. This exam is open book, open notes. You have 120 minutes to complete the exam. Please prepare your answers on
CSci530 Final Exam Fall 2011 Instructions: Show all work. No electronic devices are allowed. This exam is open book, open notes. You have 120 minutes to complete the exam. Please prepare your answers on
Mobile App. User Manual v1.0. Satish Pandit PLEXITECH SOLUTIONS LLP.
 Mobile App User Manual v1.0 Satish Pandit PLEXITECH SOLUTIONS LLP. Revision History Note: The revision history cycle begins once changes or enhancements are requested after the initial version of the User
Mobile App User Manual v1.0 Satish Pandit PLEXITECH SOLUTIONS LLP. Revision History Note: The revision history cycle begins once changes or enhancements are requested after the initial version of the User
Concur Cliqbook Travel New User Interface
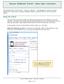 The enhanced User Interface (UI) known as Hooville was designed to improve the user experience in many ways, including increased usability, improved filtering, and more search results. Using the wizard
The enhanced User Interface (UI) known as Hooville was designed to improve the user experience in many ways, including increased usability, improved filtering, and more search results. Using the wizard
1. What is a Computer Network? interconnected collection of autonomous computers connected by a communication technology
 Review Questions for exam Preparation (22-07-2017) 1. What is a Computer Network? interconnected collection of autonomous computers connected by a communication technology 2. What is the Internet? "network
Review Questions for exam Preparation (22-07-2017) 1. What is a Computer Network? interconnected collection of autonomous computers connected by a communication technology 2. What is the Internet? "network
ALTITUDE DOESN T MAKE YOU SAFE. Satcom Direct s Comprehensive Cyber Security Portfolio for Business Aviation
 ALTITUDE DOESN T MAKE YOU SAFE Satcom Direct s Comprehensive Cyber Security Portfolio for Business Aviation CYBER SECURITY IS THE GREATEST THREAT TO EVERY COMPANY IN THE WORLD. IBM CEO GINNI ROMETTY SD
ALTITUDE DOESN T MAKE YOU SAFE Satcom Direct s Comprehensive Cyber Security Portfolio for Business Aviation CYBER SECURITY IS THE GREATEST THREAT TO EVERY COMPANY IN THE WORLD. IBM CEO GINNI ROMETTY SD
Table of Contents. Page 1 of 17
 Table of Contents Accessing Your Concur Site... 2 Updating Your Travel Profile (You must do this before booking travel)... 2 Reviewing the Home Page... 4 Tulane Travel Site and Policy... 4 Company Notes...
Table of Contents Accessing Your Concur Site... 2 Updating Your Travel Profile (You must do this before booking travel)... 2 Reviewing the Home Page... 4 Tulane Travel Site and Policy... 4 Company Notes...
Vivada Empowering Rural Telephony in Africa.
 Empowering Rural Telephony in Africa Africa Today Only about 30% of Africa is covered by telephony services Due to the remoteness and lack of ROI, traditional operators are ignoring the rural African markets
Empowering Rural Telephony in Africa Africa Today Only about 30% of Africa is covered by telephony services Due to the remoteness and lack of ROI, traditional operators are ignoring the rural African markets
RSA SecurID Implementation
 Partner Information Partner Name Website Product Name Barracuda Networks Version & Platform x60 Series Product Description Product Category Solution Summary www.barracudanetworks.com Product Information
Partner Information Partner Name Website Product Name Barracuda Networks Version & Platform x60 Series Product Description Product Category Solution Summary www.barracudanetworks.com Product Information
The Applications and Gaming Tab - Port Range Forward
 The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
70 CHAPTER 1 COMPUTER NETWORKS AND THE INTERNET
 70 CHAPTER 1 COMPUTER NETWORKS AND THE INTERNET one of these packets arrives to a packet switch, what information in the packet does the switch use to determine the link onto which the packet is forwarded?
70 CHAPTER 1 COMPUTER NETWORKS AND THE INTERNET one of these packets arrives to a packet switch, what information in the packet does the switch use to determine the link onto which the packet is forwarded?
Booking vacation packages (general)
 Outrigger Hotels and Resorts Vacations FAQs: Booking vacation packages (general) Am I booking my vacation package directly with Outrigger Hotels and Resorts? No, your booking is handled through Global
Outrigger Hotels and Resorts Vacations FAQs: Booking vacation packages (general) Am I booking my vacation package directly with Outrigger Hotels and Resorts? No, your booking is handled through Global
Making life simpler for remote and mobile workers
 : Technology GoToMyPC Technology Making life simpler for remote and mobile workers Learn why GoToMyPC is the most secure, cost-effective and easy-to-use solution for providing remote access to the desktop.
: Technology GoToMyPC Technology Making life simpler for remote and mobile workers Learn why GoToMyPC is the most secure, cost-effective and easy-to-use solution for providing remote access to the desktop.
Lecture 2: Internet Structure
 Lecture 2: Internet Structure COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016, J.F Kurose and K.W. Ross,
Lecture 2: Internet Structure COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016, J.F Kurose and K.W. Ross,
Technology in Action. Chapter Topics. Participation Question. Participation Question 8/17/11. Chapter 7 Networking: Connecting Computing Devices
 Technology in Action Chapter 7 Networking: Connecting Computing Devices 1 2 Chapter Topics Networking fundamentals Network architecture Network components Peer-to-peer networks Ethernet networks Power-line
Technology in Action Chapter 7 Networking: Connecting Computing Devices 1 2 Chapter Topics Networking fundamentals Network architecture Network components Peer-to-peer networks Ethernet networks Power-line
Point to Multi-point Link: Bridge Mode
 u n w i r i n g o u r w o r l d T M Point to Multi-point Link: Bridge Mode airpoint Nexus PRO TOTAL (sb 3212) & airclient Nexus PRO TOTAL (sb 3412) Configuration Guide Version 1.0 Copyright smartbridges
u n w i r i n g o u r w o r l d T M Point to Multi-point Link: Bridge Mode airpoint Nexus PRO TOTAL (sb 3212) & airclient Nexus PRO TOTAL (sb 3412) Configuration Guide Version 1.0 Copyright smartbridges
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key. Fall 2008
 ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
ITEC 350: Introduction To Computer Networking Midterm Exam #2 Key Closed book and closed notes. Fall 2008 No electronic devices allowed, e.g., calculator, laptop, PDA. Show your work. No work, no credit.
INSTRUCTIONS FOR THE 2018 ADVANCED SERVICES DEMAND DATA REQUEST
 INSTRUCTIONS FOR THE 2018 ADVANCED SERVICES DEMAND DATA REQUEST Monday 22, January 2018 Wednesday 28, February 2018 Study Contacts Kiwan Lee NECA Special Access Rate Development & Quantitative Analysis
INSTRUCTIONS FOR THE 2018 ADVANCED SERVICES DEMAND DATA REQUEST Monday 22, January 2018 Wednesday 28, February 2018 Study Contacts Kiwan Lee NECA Special Access Rate Development & Quantitative Analysis
CLIENT MANUAL USER MANUAL. Sky Travellers Page 1. Dubai, UAE. Skytravellers.com
 http://partner.skytravellers.com/ CLIENT MANUAL Dubai, UAE Skytravellers.com P.O. Box: 89634, Office No. 109, Business Point, Port Saeed, Deira, Dubai, UAE, Tel: +971 4 2989880 Fax: + 971 4 2941413 e-mail:
http://partner.skytravellers.com/ CLIENT MANUAL Dubai, UAE Skytravellers.com P.O. Box: 89634, Office No. 109, Business Point, Port Saeed, Deira, Dubai, UAE, Tel: +971 4 2989880 Fax: + 971 4 2941413 e-mail:
Birkbeck (University of London)
 Birkbeck (University of London) MSc Examination for Internal Students School of Computer Science and Information Systems Internet and Web Technologies () Credit Value: 15 Date of Examination: Monday 1
Birkbeck (University of London) MSc Examination for Internal Students School of Computer Science and Information Systems Internet and Web Technologies () Credit Value: 15 Date of Examination: Monday 1
Lotus IBM Lotus Notes Domino 8 Developing Web Applications. Download Full Version :
 Lotus 190-836 IBM Lotus Notes Domino 8 Developing Web Applications Download Full Version : http://killexams.com/pass4sure/exam-detail/190-836 A. Create a WebQuerySave agent that writes the message to the
Lotus 190-836 IBM Lotus Notes Domino 8 Developing Web Applications Download Full Version : http://killexams.com/pass4sure/exam-detail/190-836 A. Create a WebQuerySave agent that writes the message to the
PLEASE READ CAREFULLY BEFORE YOU START
 MIDTERM EXAMINATION #1 NETWORKING CONCEPTS 03-60-367-01 U N I V E R S I T Y O F W I N D S O R - S c h o o l o f C o m p u t e r S c i e n c e Intersession 2009 Question Paper NOTE: Students may take this
MIDTERM EXAMINATION #1 NETWORKING CONCEPTS 03-60-367-01 U N I V E R S I T Y O F W I N D S O R - S c h o o l o f C o m p u t e r S c i e n c e Intersession 2009 Question Paper NOTE: Students may take this
Quick Start Guide. Intermedia Unite Cisco SPA112
 Quick Start Guide Intermedia Unite Cisco SPA112 2 Welcome to Intermedia Unite. What s in the box? Cisco SPA112 A. SPA112 ATA B. Ethernet cable C. Power adapter D. Plug end A. C. B. D. 3 Guided Setup Your
Quick Start Guide Intermedia Unite Cisco SPA112 2 Welcome to Intermedia Unite. What s in the box? Cisco SPA112 A. SPA112 ATA B. Ethernet cable C. Power adapter D. Plug end A. C. B. D. 3 Guided Setup Your
Service Description Safecom Customer Connection Version 3.5
 Service Description Safecom Customer Connection Version 3.5 2006 Telecom NZ Ltd Commercial in Confidence CONTENTS 1 INTRODUCTION...3 2 SERVICE DEFINITION...3 2.1 SERVICE OVERVIEW... 3 2.2 SERVICE FEATURES...
Service Description Safecom Customer Connection Version 3.5 2006 Telecom NZ Ltd Commercial in Confidence CONTENTS 1 INTRODUCTION...3 2 SERVICE DEFINITION...3 2.1 SERVICE OVERVIEW... 3 2.2 SERVICE FEATURES...
Switched Multimegabit Data Service (SMDS)
 CHAPTER 14 Switched Multimegabit Data Service (SMDS) Background Switched Multimegabit Data Service (SMDS) is a high-speed, packet-switched, datagram-based WAN networking technology used for communication
CHAPTER 14 Switched Multimegabit Data Service (SMDS) Background Switched Multimegabit Data Service (SMDS) is a high-speed, packet-switched, datagram-based WAN networking technology used for communication
Cerberus IVR (interactive voice response) User Operation
 User Manual Cerberus User Manual Congratulations on subscribing to the most advanced Home/Office Security system available in the market today, featuring real time Video Verification. Cerberus is easy
User Manual Cerberus User Manual Congratulations on subscribing to the most advanced Home/Office Security system available in the market today, featuring real time Video Verification. Cerberus is easy
Switched Multimegabit Data Service
 CHAPTER 14 Chapter Goals Tell how SMDS works, and describe its components. Describe the operational elements of the SMDS environment, and outline its underlying protocol. Discuss related technologies.
CHAPTER 14 Chapter Goals Tell how SMDS works, and describe its components. Describe the operational elements of the SMDS environment, and outline its underlying protocol. Discuss related technologies.
EECS 3214 Final Exam Winter 2017 April 19, 2017 Instructor: S. Datta. 3. You have 180 minutes to complete the exam. Use your time judiciously.
 EECS 3214 Final Exam Winter 2017 April 19, 2017 Instructor: S. Datta Name (LAST, FIRST): Student number: Instructions: 1. If you have not done so, put away all books, papers, and electronic communication
EECS 3214 Final Exam Winter 2017 April 19, 2017 Instructor: S. Datta Name (LAST, FIRST): Student number: Instructions: 1. If you have not done so, put away all books, papers, and electronic communication
Updating Your Travel Profile... 3 Travel Arranger... 3 Access... 3 Obtain Airfare Quote.. 5. Obtain Car Rental Quote.. 8. Obtain Hotel Room Quote 10
 Table of Contents Updating Your Travel Profile... 3 Travel Arranger... 3 Access... 3 Obtain Airfare Quote.. 5 Obtain Car Rental Quote.. 8 Obtain Hotel Room Quote 10 Book a Flight... 13 Book a Car... 17
Table of Contents Updating Your Travel Profile... 3 Travel Arranger... 3 Access... 3 Obtain Airfare Quote.. 5 Obtain Car Rental Quote.. 8 Obtain Hotel Room Quote 10 Book a Flight... 13 Book a Car... 17
UTM Firewall Registration & Activation Manual DFL-260/ 860. Ver 1.00 Network Security Solution
 UTM Firewall Registration & Activation Manual DFL-260/ 860 Ver 1.00 curitycu Network Security Solution http://security.dlink.com.tw 1.Introduction...02 2.Apply for a D-Link Membership...03 3.D-Link NetDefend
UTM Firewall Registration & Activation Manual DFL-260/ 860 Ver 1.00 curitycu Network Security Solution http://security.dlink.com.tw 1.Introduction...02 2.Apply for a D-Link Membership...03 3.D-Link NetDefend
Data Center Operations Guide
 Data Center Operations Guide SM When you utilize Dude Solutions Software as a Service (SaaS) applications, your data is hosted in an independently audited data center certified to meet the highest standards
Data Center Operations Guide SM When you utilize Dude Solutions Software as a Service (SaaS) applications, your data is hosted in an independently audited data center certified to meet the highest standards
Boost your Business Internet Access with Chess
 DATASHEET MIKE Making Internet Access Simple Boost your Business Internet Access with Chess BETTER COMMUNICATION, SIMPLIFIED SUPPORT AND REDUCED COST. BRING YOUR BUSINESS INTO THE DIGITAL AGE WITH AN INTERNET
DATASHEET MIKE Making Internet Access Simple Boost your Business Internet Access with Chess BETTER COMMUNICATION, SIMPLIFIED SUPPORT AND REDUCED COST. BRING YOUR BUSINESS INTO THE DIGITAL AGE WITH AN INTERNET
Citrix Receiver for Universal Windows Platform
 Citrix Receiver for Universal Windows Platform Jul 18, 2017 Citrix Receiver for Universal Windows Platform (UWP) is client software available for download from the Microsoft store. It enables users to
Citrix Receiver for Universal Windows Platform Jul 18, 2017 Citrix Receiver for Universal Windows Platform (UWP) is client software available for download from the Microsoft store. It enables users to
CCNA 1 Chapter 7 v5.0 Exam Answers 2013
 CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
Concur Travel User Guide
 Concur Travel User Guide 1 Table of Contents What is Concur?... 3 Concur Modules... 3 Logging on to Concur... 5 Exploring the Home Page... 6 Updating Your Travel Profile... 7 Personal Information... 7
Concur Travel User Guide 1 Table of Contents What is Concur?... 3 Concur Modules... 3 Logging on to Concur... 5 Exploring the Home Page... 6 Updating Your Travel Profile... 7 Personal Information... 7
EL Wireless and Mobile Networking Spring 2002 Mid-Term Exam Solution - March 6, 2002
 Instructions: EL 604 - Wireless and Mobile Networking Spring 2002 Mid-Term Exam Solution - March 6, 2002 Be sure to write your name on your submission. This is an open book test. Use your class notes,
Instructions: EL 604 - Wireless and Mobile Networking Spring 2002 Mid-Term Exam Solution - March 6, 2002 Be sure to write your name on your submission. This is an open book test. Use your class notes,
Business travel made simple and rewarding. USER GUIDE
 Business travel made simple and rewarding. USER GUIDE TABLE OF CONTENTS 1. GETTING STARTED...3 PROGRAM USERS...3 ENROLLING YOUR COMPANY...5 SIGNING IN...5 TOOL OVERVIEW...6 2. THE PROGRAM ADMINISTRATOR
Business travel made simple and rewarding. USER GUIDE TABLE OF CONTENTS 1. GETTING STARTED...3 PROGRAM USERS...3 ENROLLING YOUR COMPANY...5 SIGNING IN...5 TOOL OVERVIEW...6 2. THE PROGRAM ADMINISTRATOR
Corporate Private Networks Applications
 Corporate communication networks are critical in ensuring day-to-day business operations flow smoothly. With deficiencies in telephone networks and terrestrial infrastructure in developing regions, a modern,
Corporate communication networks are critical in ensuring day-to-day business operations flow smoothly. With deficiencies in telephone networks and terrestrial infrastructure in developing regions, a modern,
Copyright 2011 Nomadix, Inc. All Rights Reserved Agoura Road Suite 102 Agoura Hills CA USA White Paper
 Nomadix Service Engine Access in Large Public Venues Copyright 2011 Nomadix, Inc. All Rights Reserved. 30851 Agoura Road Suite 102 Agoura Hills CA 91301 USA www.nomadix.com 230-1026-001 Sheet 2 of 9 Introduction
Nomadix Service Engine Access in Large Public Venues Copyright 2011 Nomadix, Inc. All Rights Reserved. 30851 Agoura Road Suite 102 Agoura Hills CA 91301 USA www.nomadix.com 230-1026-001 Sheet 2 of 9 Introduction
Accessing Online Mutual Fund Information from Schwab
 Accessing Online Mutual Fund Information from Schwab Accessing the Internet Standards World Wide Web (WWW) Internet, Intranet, Extranet Schwab Web-enabled Database How Do You Reach Schwab From Charlottesville
Accessing Online Mutual Fund Information from Schwab Accessing the Internet Standards World Wide Web (WWW) Internet, Intranet, Extranet Schwab Web-enabled Database How Do You Reach Schwab From Charlottesville
Part 1. Lecturer: Prof. Mohamed Bettaz Coordinator: Prof. Mohamed Bettaz Internal Examiner: Dr. Mourad Maouche. Examination Paper
 Philadelphia University Lecturer: Prof. Mohamed Bettaz Coordinator: Prof. Mohamed Bettaz Internal Examiner: Dr. Mourad Maouche Faculty of Information Technology Department of Computer Science Examination
Philadelphia University Lecturer: Prof. Mohamed Bettaz Coordinator: Prof. Mohamed Bettaz Internal Examiner: Dr. Mourad Maouche Faculty of Information Technology Department of Computer Science Examination
Welcome to United Bank - Mobile Banking!
 Questions Welcome to United Bank - Mobile Banking! General Questions How much does this service cost? Is it secure? Which wireless carriers are supported? Do I need a text message or data plan? I'm not
Questions Welcome to United Bank - Mobile Banking! General Questions How much does this service cost? Is it secure? Which wireless carriers are supported? Do I need a text message or data plan? I'm not
Using the AETA Remote Access service
 Using the AETA Remote Access service 1. Background AETA codecs can all be controlled via an IP interface, and for instance a computer can easily take control over a codec when it is connected on the same
Using the AETA Remote Access service 1. Background AETA codecs can all be controlled via an IP interface, and for instance a computer can easily take control over a codec when it is connected on the same
SECURING INFORMATION SYSTEMS
 SECURING INFORMATION SYSTEMS (November 7, 2016) BUS3500 - Abdou Illia - Fall 2016 1 LEARNING GOALS Understand security attacks preps Discuss the major threats to information systems. Discuss protection
SECURING INFORMATION SYSTEMS (November 7, 2016) BUS3500 - Abdou Illia - Fall 2016 1 LEARNING GOALS Understand security attacks preps Discuss the major threats to information systems. Discuss protection
CPSC 441 COMPUTER COMMUNICATIONS MIDTERM EXAM
 CPSC 441 COMPUTER COMMUNICATIONS MIDTERM EXAM Department of Computer Science University of Calgary Professor: Carey Williamson November 1, 2005 This is a CLOSED BOOK exam. Textbooks, notes, laptops, personal
CPSC 441 COMPUTER COMMUNICATIONS MIDTERM EXAM Department of Computer Science University of Calgary Professor: Carey Williamson November 1, 2005 This is a CLOSED BOOK exam. Textbooks, notes, laptops, personal
Cisco SR 520-T1 Secure Router
 Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Security Statement Revision Date: 23 April 2009
 Security Statement Revision Date: 23 April 2009 ISL Online, ISL Light, ISL AlwaysOn, ISL Pronto, and ISL Groop are registered trademarks of XLAB d.o.o. Copyright (c) 2003-2009 XLAB d.o.o. Ljubljana. All
Security Statement Revision Date: 23 April 2009 ISL Online, ISL Light, ISL AlwaysOn, ISL Pronto, and ISL Groop are registered trademarks of XLAB d.o.o. Copyright (c) 2003-2009 XLAB d.o.o. Ljubljana. All
Questions & Answers From Thursday, September 16 Webinar Alternatives Case Examples Frequency and Spectrum Planning Security WiMAX Capabilities
 Questions & Answers From Thursday, September 16 Webinar Alternatives Case Examples Frequency and Spectrum Planning Security WiMAX Capabilities Alternatives Q: How about PLC? Is it a viable alternative
Questions & Answers From Thursday, September 16 Webinar Alternatives Case Examples Frequency and Spectrum Planning Security WiMAX Capabilities Alternatives Q: How about PLC? Is it a viable alternative
Accessing Skyward Mobile Access App
 Accessing Skyward Mobile Access App Previous: Keyboard Shortcuts Parent: General Navigation Additional... The Skyward Mobile Access app is available for free download on Android and ios devices. Once you
Accessing Skyward Mobile Access App Previous: Keyboard Shortcuts Parent: General Navigation Additional... The Skyward Mobile Access app is available for free download on Android and ios devices. Once you
BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS
 BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Prof. Dr. Hasan Hüseyin BALIK (1 st Week) Outline Course Information and Policies Course Syllabus 1. Data Communications, Data Networks, and the Internet
BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Prof. Dr. Hasan Hüseyin BALIK (1 st Week) Outline Course Information and Policies Course Syllabus 1. Data Communications, Data Networks, and the Internet
CSCI315 Database Design and Implementation Singapore Assignment 2 11 January 2018
 School of Computer Science & Software Engineering Session: 1, January 2017 University of Wollongong Lecturer: Janusz R. Getta CSCI315 Database Design and Implementation Singapore 2018-1 Assignment 2 11
School of Computer Science & Software Engineering Session: 1, January 2017 University of Wollongong Lecturer: Janusz R. Getta CSCI315 Database Design and Implementation Singapore 2018-1 Assignment 2 11
2 DIVAR hybrid 3000/5000 firmware v1.3.0 ( )
 Video Recorder recorder 1 General Notices Notice! Bosch strongly recommends upgrading to the latest firmware for the best possible functionality, compatibility, performance and security. Check http://downloadstore.boschsecurity.com/
Video Recorder recorder 1 General Notices Notice! Bosch strongly recommends upgrading to the latest firmware for the best possible functionality, compatibility, performance and security. Check http://downloadstore.boschsecurity.com/
Sandbox Parent Portal Quick Start Guide
 Sandbox Parent Portal Quick Start Guide Your childcare provider uses Sandbox Software to help manage their center. Sandbox Software has a Parent Portal that enables parents to manage information for their
Sandbox Parent Portal Quick Start Guide Your childcare provider uses Sandbox Software to help manage their center. Sandbox Software has a Parent Portal that enables parents to manage information for their
5 Tips to Fortify your Wireless Network
 Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
Article ID: 5035 5 Tips to Fortify your Wireless Network Objective Although Wi-Fi networks are convenient for you and your employees, there may be unwanted clients using up the bandwidth you pay for. In
T e l e c o m m u n i c a t i o n s, t h e i n t e r n e t, a n d W i r e l e s s t e c h n o l o g y
 T e l e c o m m u n i c a t i o n s, t h e i n t e r n e t, a n d W i r e l e s s t e c h n o l o g y C h a p t e r 7 Jun Akizaki The Power of PowerPoint WELCOME group members: 1. Dewi Setyani 16808144017
T e l e c o m m u n i c a t i o n s, t h e i n t e r n e t, a n d W i r e l e s s t e c h n o l o g y C h a p t e r 7 Jun Akizaki The Power of PowerPoint WELCOME group members: 1. Dewi Setyani 16808144017
Protocol Layers, Security Sec: Application Layer: Sec 2.1 Prof Lina Battestilli Fall 2017
 CSC 401 Data and Computer Communications Networks Protocol Layers, Security Sec:1.5-1.6 Application Layer: Sec 2.1 Prof Lina Battestilli Fall 2017 Outline Computer Networks and the Internet (Ch 1) 1.1
CSC 401 Data and Computer Communications Networks Protocol Layers, Security Sec:1.5-1.6 Application Layer: Sec 2.1 Prof Lina Battestilli Fall 2017 Outline Computer Networks and the Internet (Ch 1) 1.1
Network Connectivity and Mobility
 Network Connectivity and Mobility BSAD 141 Dave Novak Topics Covered Lecture is structured based on the five elements of creating a connected world from the text book (with additional content) 1. Network
Network Connectivity and Mobility BSAD 141 Dave Novak Topics Covered Lecture is structured based on the five elements of creating a connected world from the text book (with additional content) 1. Network
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER
 DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
COSC 6377 Mid-Term #2 Fall 2000
 Name: SSN: Signature: Open book, open notes. Your work must be your own. Assigned seating. Test time: 7:05pm to 8:05pm. You may not use a calculator or PalmPilot to calculate subnetting/host/netid information.
Name: SSN: Signature: Open book, open notes. Your work must be your own. Assigned seating. Test time: 7:05pm to 8:05pm. You may not use a calculator or PalmPilot to calculate subnetting/host/netid information.
Reports Demo Infrastructure Report
 Partner: Advocate IT Services 123 Elm Street Nowhere, UT US Reports Demo Infrastructure Report Customer: Reports Demo Street: 123 City: 123 State/Prov: AZ Country: United States Device Summary: Device
Partner: Advocate IT Services 123 Elm Street Nowhere, UT US Reports Demo Infrastructure Report Customer: Reports Demo Street: 123 City: 123 State/Prov: AZ Country: United States Device Summary: Device
System User Guide. Contents. Login and Welcome. Creating your booking: Availability Search. Availability response. Filters. Selecting your Flights
 System User Guide Contents Login and Welcome Creating your booking: Availability Search Availability response Filters Selecting your Flights Quote Confirmation Book Reminders Pre-ticket Amendments Pay
System User Guide Contents Login and Welcome Creating your booking: Availability Search Availability response Filters Selecting your Flights Quote Confirmation Book Reminders Pre-ticket Amendments Pay
Configuring System using Startup Wizard
 Configuring System using Startup Wizard Release 1.0 Password Configuration When using a CCTV Security Pros system for the first time, you are required to set a login password for the admin account (system
Configuring System using Startup Wizard Release 1.0 Password Configuration When using a CCTV Security Pros system for the first time, you are required to set a login password for the admin account (system
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY Fall Quiz II
 Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.858 Fall 2014 Quiz II You have 80 minutes to answer the questions in this quiz. In order to receive credit
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.858 Fall 2014 Quiz II You have 80 minutes to answer the questions in this quiz. In order to receive credit
Examen final de Xarxes de Computadors (XC) 6/6/2011 NAME: SURNAME DNI:
 Examen final de Xarxes de Computadors (XC) 6/6/2011 NAME: SURNAME DNI: Answer problems 1 amd 2 in the same questions sheet, and problem 3 en exams sheets.justify your answers. N2 N3 N1 f2 f4 N4 N7 f1 R1
Examen final de Xarxes de Computadors (XC) 6/6/2011 NAME: SURNAME DNI: Answer problems 1 amd 2 in the same questions sheet, and problem 3 en exams sheets.justify your answers. N2 N3 N1 f2 f4 N4 N7 f1 R1
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
Do not open this examination paper until instructed to do so. Answer all the questions.
 M11/5/COMSC/HP2/ENG/TZ0/XX 22117012 Computer science HIGHER level Paper 2 Friday 20 May 2011 (morning) 2 hours 15 minutes INSTRUCTIONS TO CANDIDATES Do not open this examination paper until instructed
M11/5/COMSC/HP2/ENG/TZ0/XX 22117012 Computer science HIGHER level Paper 2 Friday 20 May 2011 (morning) 2 hours 15 minutes INSTRUCTIONS TO CANDIDATES Do not open this examination paper until instructed
CSC 401 Data and Computer Communications Networks
 CSC 401 Data and Computer Communications Networks Link Layer, Switches, VLANS, MPLS, Data Centers Sec 6.4 to 6.7 Prof. Lina Battestilli Fall 2017 Chapter 6 Outline Link layer and LANs: 6.1 introduction,
CSC 401 Data and Computer Communications Networks Link Layer, Switches, VLANS, MPLS, Data Centers Sec 6.4 to 6.7 Prof. Lina Battestilli Fall 2017 Chapter 6 Outline Link layer and LANs: 6.1 introduction,
Data Communications and Networks
 Data Communications and Networks CSCI-GA.2262-001 Spring 2016 Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences Midterm Examination Solutions
Data Communications and Networks CSCI-GA.2262-001 Spring 2016 Dr. Jean-Claude Franchitti New York University Computer Science Department Courant Institute of Mathematical Sciences Midterm Examination Solutions
CPS 706 Computer Networks (Fall 2011)
 CPS 706 Computer Networks (all 2011) Midterm Exam 1 Solutions Date: October 21, 2011, ime: 14:00 16:00pm, Instructor: Dr. J. Misic Name: Student ID: Email: Instructions: 1. his is a closed book exam 2.
CPS 706 Computer Networks (all 2011) Midterm Exam 1 Solutions Date: October 21, 2011, ime: 14:00 16:00pm, Instructor: Dr. J. Misic Name: Student ID: Email: Instructions: 1. his is a closed book exam 2.
Securing Wireless Networks by By Joe Klemencic Mon. Apr
 http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
Network Installation Guide: ICM7100SE [ This note applies to the ICM7100SE VMS Server] [ 28-Jun-17] Contents. Materials needed.
![Network Installation Guide: ICM7100SE [ This note applies to the ICM7100SE VMS Server] [ 28-Jun-17] Contents. Materials needed. Network Installation Guide: ICM7100SE [ This note applies to the ICM7100SE VMS Server] [ 28-Jun-17] Contents. Materials needed.](/thumbs/83/87610164.jpg) Network Installation Guide: ICM7100SE [ This note applies to the ICM7100SE VMS Server] [ 28-Jun-17] Contents Materials needed... 1 Overview... 1 Initial System Config... 2 Troubleshooting... 9 Materials
Network Installation Guide: ICM7100SE [ This note applies to the ICM7100SE VMS Server] [ 28-Jun-17] Contents Materials needed... 1 Overview... 1 Initial System Config... 2 Troubleshooting... 9 Materials
CPS221 Lecture: Layered Network Architecture
 CPS221 Lecture: Layered Network Architecture Objectives last revised 9/8/14 1. To discuss the OSI layered architecture model 2. To discuss the specific implementation of this model in TCP/IP Materials:
CPS221 Lecture: Layered Network Architecture Objectives last revised 9/8/14 1. To discuss the OSI layered architecture model 2. To discuss the specific implementation of this model in TCP/IP Materials:
Access to the Online Booking Tool
 Welcome to KDS Corporate Start-up Guide This leaflet shows you the main features of the travel module. The information in this leaflet corresponds to the tool s generic features and depends on your company
Welcome to KDS Corporate Start-up Guide This leaflet shows you the main features of the travel module. The information in this leaflet corresponds to the tool s generic features and depends on your company
Chapter 1 Introduction
 Chapter 1 Introduction A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you can add, modify, and delete
Chapter 1 Introduction A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you can add, modify, and delete
CS244a: An Introduction to Computer Networks
 Grade: MC: 7: 8: 9: 10: 11: 12: 13: 14: Total: CS244a: An Introduction to Computer Networks Final Exam: Wednesday You are allowed 2 hours to complete this exam. (i) This exam is closed book and closed
Grade: MC: 7: 8: 9: 10: 11: 12: 13: 14: Total: CS244a: An Introduction to Computer Networks Final Exam: Wednesday You are allowed 2 hours to complete this exam. (i) This exam is closed book and closed
Quick Start Guide. GV-Recording Server. 1 Introduction. Packing List
 1 Introduction Quick Start Guide GV-Recording Server Welcome to the GV-Recording Server Quick Start Guide. This quick guide will guide you through the basic installation of GV-Recording Server, connecting
1 Introduction Quick Start Guide GV-Recording Server Welcome to the GV-Recording Server Quick Start Guide. This quick guide will guide you through the basic installation of GV-Recording Server, connecting
Network Guide for Listen Everywhere
 Network Guide for Listen Everywhere Overview: The Listen Everywhere (LE) System is designed to be used on pre-existing wireless networks and to be plug and play. However, it may be necessary to have an
Network Guide for Listen Everywhere Overview: The Listen Everywhere (LE) System is designed to be used on pre-existing wireless networks and to be plug and play. However, it may be necessary to have an
Network Programming I Computer Network Design
 Network Programming I Computer Network Design Flavio Esposito http://cs.slu.edu/~esposito/teaching/3650/ Lecture 2 Lecture Goals Get feel and terminology of some components of real nets More depth & details
Network Programming I Computer Network Design Flavio Esposito http://cs.slu.edu/~esposito/teaching/3650/ Lecture 2 Lecture Goals Get feel and terminology of some components of real nets More depth & details
B E T A. New Mobile Interface (2015) User Guide
 B E T A New Mobile Interface (2015) User Guide Application Account Setup & Maintenance Initial Account Setup Account Maintenance New Skyward Mobile Navigation User Main Menu Recent Favorite Application
B E T A New Mobile Interface (2015) User Guide Application Account Setup & Maintenance Initial Account Setup Account Maintenance New Skyward Mobile Navigation User Main Menu Recent Favorite Application
CS244a: An Introduction to Computer Networks
 Name: Student ID #: Campus/SITN-Local/SITN-Remote? MC MC Long 18 19 TOTAL /20 /20 CS244a: An Introduction to Computer Networks Final Exam: Thursday February 16th, 2000 You are allowed 2 hours to complete
Name: Student ID #: Campus/SITN-Local/SITN-Remote? MC MC Long 18 19 TOTAL /20 /20 CS244a: An Introduction to Computer Networks Final Exam: Thursday February 16th, 2000 You are allowed 2 hours to complete
