EY Cyber Response Services. Plan. React. Recover.
|
|
|
- Barbra Farmer
- 5 years ago
- Views:
Transcription
1 EY Cyber Response Services Plan. React. Recover.
2 Insurance claim preparation Data recovery How EY can help Data privacy and GDPR compliance Cyber planning Our full suite of cyber capabilities Litigation support Investigation Investigation and incident and incident Digital forensics Cyber planning As part of their enterprise crisis management program, we help organizations develop plans and conduct simulation testing by taking into consideration of the magnitude and types of cybercrimes, data loss, customer privacy violation, regulatory compliance and infrastructure damage. Our team helps organizations establish an investigation framework and the forensic procedures to support the investigation. Forensic readiness is important if an organization is to be able to quickly respond to an incident and conduct investigations with efficiency and accuracy. It also helps to safeguard evidence collection and preservation in compliance with relevant regulations or laws, and with minimal interruption to business operations. We also work with organizations to form recovery plans that include containment and eradication, and leverage the broader business continuity plan. We take into account short-term measures to secure high-priority environments, restrict access or introduce barriers, while keeping our sights on a long-term mitigation strategy to reduce the risk of similar attacks happening again. 24/7/365 rapid Through managed services or preferred provider arrangements, we forge long-term relationships with our clients that enables us to gain deep knowledge of their IT and data environments so we can offer the speed and confidence they need to respond to cyber attacks, regardless of the level of complexity. With our global network, we have teams around the world who work together to forge a 24/7/365 incident intake process so we can respond to a cyber attack at any time of the day.
3 Investigation and incident Digital forensics Litigation support Our cyber team comprises investigators, formal regulators and law enforcement, as well as information security professionals who collaborate closely to pinpoint and contain the affected systems and data, conduct root cause analysis, perform eradication and mitigation activities, and liaise with government agencies as needed. Our cyber investigators combine computer forensic knowledge with traditional investigative approaches, including interviewing witnesses, interrogating data, and examining physical and digital evidence to uncover the facts pertaining to a cyber incident. We work with organizations to customize the investigation approach for each incident, taking into account potential litigation and regulatory inquiries, resource requirements, timing, desired work product and budget. As cybercrimes often span international borders with unique data privacy and state-secret laws, we tailor our procedures to the specific legal and regulatory requirements of each country involved in the investigation, including our work with counsel. Our global team is able to perform time-critical data mapping and forensically sound preservation and collection activities around the world simultaneously. In the event of an attack, we can quickly deploy resources around the world to collect investigative evidence, such as network traffic capture, log file and static host-system image. We analyze collected network log files and host information, and use internal cyber threat intelligence data, coupled with external threat intelligence data, to detect hostile activities and work toward attribution of the sources of the attack. We also utilize forensic data analytics to collect and fuse data from multiple logging and audit-trail systems to piece together the attack timeline and discover the original point of entry, as well as subsequent attacker activities. Almost all large cyber attacks lead to litigation, and, moreover, lead to different types of litigation handled by multiple law firms. We work with organizations and their counsel to develop work products consistent with litigation evidentiary requirements. Procedures for chain of custody, security of exhibits and contemporaneous note-taking practices are standard components of the methodology our professionals follow. Many national security-related cyber investigations involve complex liaison with government authorities. EY s cyber professionals are experienced in working with national security and law enforcement bodies, as well as management and counsel, to safeguard the organization s interests. Secure global infrastructure and consistent global methodology With numerous advanced security centers, forensic labs and data centers worldwide, all of which come with multiple layers of controls, we offer organizations the connectivity, scale and agility they need to respond to cyber attacks and to manage their data protection and privacy needs. Governed by a globally consistent methodology, we offer integrated services from one stage of the life cycle to the next, reducing the risks and costs of managing multiple service providers.
4 Data privacy and GDPR compliance Data recovery Insurance claim preparation Data privacy is an important consideration of cyber planning. We work with organizations to develop strategies and mechanisms to enable them to securely process and transfer the data needed for an investigation. Working with counsel, we develop written protocols that help them comply with applicable regulatory requirements. Companies often need to achieve a basic level of understanding of the scope of the breach to determine the appropriate notification procedures, as required by regulations such as the GDPR. We help organizations conduct swift and concise investigations in order to understand the scope of the breach and to determine the appropriate notification procedures. If cyber incidents result in destruction or corruption of data, EY can provide data recovery services and resources to support restoration from all types of deleted, corrupted, missing or inaccessible data that may have resulted from a cyber attack. This includes recovery of loss from any operating system environment and working with teams to restore services. We help organizations prepare and present a well-organized cyber claim with attendant supporting documentation. The goal during this part of the claim preparation process is to document and resolve as many components of the loss as possible. As organizations look to close out their cyber or network security claim, we help them to understand the calculations put forth by the adjusting team and develop alternative calculations for the resolution process. 8% of respondents describe their cyber plan as robust and spanning third parties and law enforcement. EY Global Information Security Survey Multidisciplinary team Our team includes cybersecurity professionals, investigators, data privacy professionals, digital forensics specialists, ediscovery professionals, forensic accountants, government contract analysts, economists and certified fraud examiners, as well as former ethics and compliance officers, former government auditors, and former prosecutors and regulators.
5 The wide-ranging business impacts and risks of cyber attacks It is only a matter of time before a business will suffer a cyber attack. The potential impact of cybercrime requires that cybersecurity be viewed as a business risk, rather than a simple IT issue. Fundamentally, an organization s reputation is on the line as a cyber attack may impact business operations, financial integrity, and legal exposure to its customers and partners. In addition, cyber risk has been increasingly linked to data protection and privacy regulatory compliance around the world. For example, the EU s General Data Protection Regulation (GDPR) that went into effect in May 2018 requires that supervisory authorities be notified, under certain circumstances, within 72 hours of a personal data breach. The EU Network and Information Security Directive incident notification requirements for digital service providers (DSP) dictate that DSPs notify the competent authority without undue delay of any incident having a substantial impact on the provision of a service. China s Cybersecurity Law became the first nationallevel law that addresses cybersecurity and data privacy protection in November The United States has approximately 20 sector-specific or medium-specific national privacy or data security laws, and hundreds of such laws among its 50 states and its territories such as the California Consumer Privacy Act of In order to adequately address the risks from large and complex cybercrimes that are likely to occur, it is critical that organizations develop a strong, centralized framework that is part of the enterprise risk management and crisis management strategies. Investigation Privacy Business continuity planning Litigation What would once have been considered large-scale cyber attacks are now becoming normal. The Global Risks Report 2018 World Economic Forum Public relations Cyber framework Compliance Cyber insurance claim Information security
6 Global presence Americas: Asia Pacific: EMEA: Africa: India: Atlanta Adelaide Belo Horizonte Auckland Bogota Bangkok Boston Beijing Buenos Aires Brisbane Charlotte Hanoi Chicago Hong Kong Cleveland Jakarta Curitiba Kuala Lumpur Dallas Manila Houston Melbourne Iselin Perth Lima Seoul Los Angeles Shanghai Mexico City Singapore New York Sydney Quito Taipei Rio de Janeiro San Antonio San Francisco San Jose Santiago São Paulo Secaucus Toronto Washington Metro DC Amsterdam Milan Belfast Moscow Brussels Oslo Bucharest Paris Budapest Prague Cologne Saarbrücken Copenhagen Stockholm Düsseldorf Stuttgart Frankfurt Vienna Istanbul Vilnius London Warsaw Madrid Zürich Manchester Abuja Cape Town Durban Johannesburg Nairobi Japan: Tokyo Chennai Hyderabad Mumbai New Delhi Middle East: Dubai Tel Aviv Countries with EY presence Forensic labs Advanced security centers Forensic data centers Managed Document Review centers Are you suspicious of a cyber attack? Contact us now! Global incident intake CyberResponse@ey.com Americas hotline: Contacts outside of Americas: ey.com/forensics EY Assurance Tax Transactions Advisory About EY EY is a global leader in assurance, tax, transaction and advisory services. The insights and quality services we deliver help build trust and confidence in the capital markets and in economies the world over. We develop outstanding leaders who team to deliver on our promises to all of our stakeholders. In so doing, we play a critical role in building a better working world for our people, for our clients and for our communities. EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients. For more information about our organization, please visit ey.com. About EY Forensic & Integrity Services Dealing with complex issues of fraud, regulatory compliance and business disputes can detract from efforts to succeed. Better management of fraud risk and compliance exposure is a critical business priority no matter the size or industry sector. With approximately 4,500 forensic professionals around the world, we will assemble the right multidisciplinary and culturally aligned team to work with you and your legal advisors. We work to give you the benefit of our broad sector experience, our deep subject-matter knowledge and the latest insights from our work worldwide Ernst & Young LLP. All Rights Reserved. EYG no Gbl BSC no ED None This material has been prepared for general informational purposes only and is not intended to be relied upon as accounting, tax or other professional advice. Please refer to your advisors for specific advice. ey.com
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services
 Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
Forensic Technology & Discovery Services Forensic analysis with leading technology: the intelligent connection Fraud Investigation & Dispute Services Forensic Technology & Discovery Services EY s Forensic
THE PLATFORM EQUINIX VISION
 THE PLATFORM EQUINIX VISION Build Here, and Go Anywhere SUMMARY Key trends are driving the need for a single interconnection platform for digital business On the Equinix global interconnection platform
THE PLATFORM EQUINIX VISION Build Here, and Go Anywhere SUMMARY Key trends are driving the need for a single interconnection platform for digital business On the Equinix global interconnection platform
THE PLATFORM EQUINIX VISION
 THE PLATFORM EQUINIX VISION Build Here, and Go Anywhere SUMMARY Key trends are driving the need for a single interconnection platform for digital business On the Equinix global interconnection platform
THE PLATFORM EQUINIX VISION Build Here, and Go Anywhere SUMMARY Key trends are driving the need for a single interconnection platform for digital business On the Equinix global interconnection platform
Introduction. When it comes to GDPR compliance, is OK for now enough? Minds made for protecting financial services
 When it comes to GDPR compliance, is OK for now enough? EY CertifyPoint s GDPR certification process will help you achieve and demonstrate compliance. Minds made for protecting financial services Introduction
When it comes to GDPR compliance, is OK for now enough? EY CertifyPoint s GDPR certification process will help you achieve and demonstrate compliance. Minds made for protecting financial services Introduction
Demonstrating data privacy for GDPR and beyond
 Demonstrating data privacy for GDPR and beyond EY data privacy assurance services Introduction The General Data Protection Regulation (GDPR) is ushering in a new era of data privacy in Europe. Organizations
Demonstrating data privacy for GDPR and beyond EY data privacy assurance services Introduction The General Data Protection Regulation (GDPR) is ushering in a new era of data privacy in Europe. Organizations
Is the answer to cybersecurity more technology, more people or more process?
 Is the answer to cybersecurity more technology, more people or more process? Cybersecurity can only be addressed by combining technology and business acumen with unique human insights. ey.com/betterworkingworld
Is the answer to cybersecurity more technology, more people or more process? Cybersecurity can only be addressed by combining technology and business acumen with unique human insights. ey.com/betterworkingworld
Safeguarding unclassified controlled technical information (UCTI)
 Safeguarding unclassified controlled technical information (UCTI) An overview Government Contract Services Bulletin Safeguarding UCTI An overview On November 18, 2013, the Department of Defense (DoD) issued
Safeguarding unclassified controlled technical information (UCTI) An overview Government Contract Services Bulletin Safeguarding UCTI An overview On November 18, 2013, the Department of Defense (DoD) issued
Association of Corporate Counsel
 Type in document reference # if needed Privacy protection in a Globalized World Association of Corporate Counsel New York, 24 March 2015 1 The plan Bringing out the main cross-border privacy issues for
Type in document reference # if needed Privacy protection in a Globalized World Association of Corporate Counsel New York, 24 March 2015 1 The plan Bringing out the main cross-border privacy issues for
Cloud Computing - Reaping the Benefits and Avoiding the Pitfalls. Stuart James & Delizia Diaz. Intellectual Property & Technology Webinar
 Intellectual Property & Technology Webinar Cloud Computing - Reaping the Benefits and Avoiding the Pitfalls Stuart James & Delizia Diaz 37 Offices in 18 Countries Birmingham Wednesday, 11 July 2012 Speakers
Intellectual Property & Technology Webinar Cloud Computing - Reaping the Benefits and Avoiding the Pitfalls Stuart James & Delizia Diaz 37 Offices in 18 Countries Birmingham Wednesday, 11 July 2012 Speakers
Protecting your data. EY s approach to data privacy and information security
 Protecting your data EY s approach to data privacy and information security Digital networks are a key enabler in the globalization of business. They dramatically enhance our ability to communicate, share
Protecting your data EY s approach to data privacy and information security Digital networks are a key enabler in the globalization of business. They dramatically enhance our ability to communicate, share
Cyber Risk Services Going beyond limits
 Cyber Risk Services Going beyond limits Current Threat Environment Security breaches: 318 Scanned websites with vulnerabilities: 78% Average identities exposed per breach: 1.3 Million Email malware rate
Cyber Risk Services Going beyond limits Current Threat Environment Security breaches: 318 Scanned websites with vulnerabilities: 78% Average identities exposed per breach: 1.3 Million Email malware rate
Canada Highlights. Cybersecurity: Do you know which protective measures will make your company cyber resilient?
 Canada Highlights Cybersecurity: Do you know which protective measures will make your company cyber resilient? 21 st Global Information Security Survey 2018 2019 1 Canada highlights According to the EY
Canada Highlights Cybersecurity: Do you know which protective measures will make your company cyber resilient? 21 st Global Information Security Survey 2018 2019 1 Canada highlights According to the EY
Bring Your Own Device Shakes Up IT Departments
 Bring Your Own Device Shakes Up IT Departments As employees quietly bring their personal devices to work, and forward-thinking companies respond, this win-win workplace revolution presents some challenges.
Bring Your Own Device Shakes Up IT Departments As employees quietly bring their personal devices to work, and forward-thinking companies respond, this win-win workplace revolution presents some challenges.
GDPR Privacy Webinar. Prioritizing Your Path towards GDPR Compliance Annika Sponselee and Nicole Vreeman 28 February 2018
 GDPR Privacy Webinar Prioritizing Your Path towards GDPR Compliance Annika Sponselee and Nicole Vreeman 28 February 2018 Prioritizing Your Path to GDPR Compliance Presented by Half-Day Workshops Online
GDPR Privacy Webinar Prioritizing Your Path towards GDPR Compliance Annika Sponselee and Nicole Vreeman 28 February 2018 Prioritizing Your Path to GDPR Compliance Presented by Half-Day Workshops Online
EY s data privacy service offering
 EY s data privacy service offering How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world Introduction Data privacy encompasses the rights and obligations
EY s data privacy service offering How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world Introduction Data privacy encompasses the rights and obligations
Big data privacy in Australia
 Five-article series Big data privacy in Australia Three actions you can take towards compliance Article 5 Big data and privacy Three actions you can take towards compliance There are three actions that
Five-article series Big data privacy in Australia Three actions you can take towards compliance Article 5 Big data and privacy Three actions you can take towards compliance There are three actions that
Developing your GDPR response for competitive advantage. EU General Data Protection Regulation (GDPR)
 Developing your GDPR response for competitive advantage EU General Data Protection Regulation (GDPR) Introduction In May 2018, the EU s new GDPR ushers in unprecedented levels of data protection for EU
Developing your GDPR response for competitive advantage EU General Data Protection Regulation (GDPR) Introduction In May 2018, the EU s new GDPR ushers in unprecedented levels of data protection for EU
Customer Breach Support A Deloitte managed service. Notifying, supporting and protecting your customers through a data breach
 Customer Breach Support A Deloitte managed service Notifying, supporting and protecting your customers through a data breach Customer Breach Support Client challenges Protecting your customers, your brand
Customer Breach Support A Deloitte managed service Notifying, supporting and protecting your customers through a data breach Customer Breach Support Client challenges Protecting your customers, your brand
LEVEL 3 SM WEBSITE ACCELERATION SERVICES
 LEVEL 3 SM WEBSITE ACCELERATION SERVICES WEBSITE CONSUMERS ARE IMPATIENT, which makes your website performance extremely critical. Whether you are delivering content to a desktop, tablet or mobile device,
LEVEL 3 SM WEBSITE ACCELERATION SERVICES WEBSITE CONSUMERS ARE IMPATIENT, which makes your website performance extremely critical. Whether you are delivering content to a desktop, tablet or mobile device,
HOT TOPICS IN DATA PRIVACY REGULATION IN RUSSIA
 HOT TOPICS IN DATA PRIVACY REGULATION IN RUSSIA Ksenia Andreeva Anastasia Dergacheva Vasilisa Strizh November 27, 2018 2018 Morgan, Lewis & Bockius 2017 Morgan, Lewis & Bockius Contents News from the Russian
HOT TOPICS IN DATA PRIVACY REGULATION IN RUSSIA Ksenia Andreeva Anastasia Dergacheva Vasilisa Strizh November 27, 2018 2018 Morgan, Lewis & Bockius 2017 Morgan, Lewis & Bockius Contents News from the Russian
EY Consulting. Is your strategy planning for the future or creating it? #TransformativeAge
 2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
2018 Ernst & Young Advisory. All rights reserved. Graphics studio France 1802SG1267. ED 04082018 EY Consulting Is your strategy planning for the future or creating it? #TransformativeAge The better the
ISACA Cincinnati Chapter March Meeting
 ISACA Cincinnati Chapter March Meeting Recent and Proposed Changes to SOC Reports Impacting Service and User Organizations. March 3, 2015 Presenters: Sayontan Basu-Mallick Lori Johnson Agenda SOCR Overview
ISACA Cincinnati Chapter March Meeting Recent and Proposed Changes to SOC Reports Impacting Service and User Organizations. March 3, 2015 Presenters: Sayontan Basu-Mallick Lori Johnson Agenda SOCR Overview
Cloud Computing: Overcoming the Legal and Regulatory Challenges. November
 Cloud Computing: Overcoming the Legal and Regulatory Challenges November 2011 2 Cloud Computing: Overcoming the Legal and Regulatory Challenges November 2011 Cloud Computing Overcoming the Legal and Regulatory
Cloud Computing: Overcoming the Legal and Regulatory Challenges November 2011 2 Cloud Computing: Overcoming the Legal and Regulatory Challenges November 2011 Cloud Computing Overcoming the Legal and Regulatory
What s new in EY Atlas. November 2018
 November 2018 EY tlas is regularly evolving and being enhanced to make your experience with the tool even better. This document highlights the new features and enhancements made since EY tlas was launched
November 2018 EY tlas is regularly evolving and being enhanced to make your experience with the tool even better. This document highlights the new features and enhancements made since EY tlas was launched
How to be cyber secure A practical guide for Australia s mid-size business
 How to be cyber secure A practical guide for Australia s mid-size business Introduction The digital age has bred opportunity for mid-size business. From ecommerce to social media, agile organisations have
How to be cyber secure A practical guide for Australia s mid-size business Introduction The digital age has bred opportunity for mid-size business. From ecommerce to social media, agile organisations have
EY s Data Privacy Services. January 2019
 EY s Data Privacy Services January 2019 Introduction Data privacy encompasses the rights and obligations of individuals and organizations with respect to the collection, use, disclosure, and retention
EY s Data Privacy Services January 2019 Introduction Data privacy encompasses the rights and obligations of individuals and organizations with respect to the collection, use, disclosure, and retention
Outsourcing: The Perspective of a Data Processor
 2008/SOM1/ECSG/SEM/010 Outsourcing: The Perspective of a Data Processor Submitted by: Hewlett-Packard Technical Assistance Seminar on International Implementation of the APEC Privacy Framework Lima, Peru
2008/SOM1/ECSG/SEM/010 Outsourcing: The Perspective of a Data Processor Submitted by: Hewlett-Packard Technical Assistance Seminar on International Implementation of the APEC Privacy Framework Lima, Peru
Enterprise Case Study
 REUTERS / Stefano Rellandini Enterprise Case Study The Future of Your WAN Dimitrios Voutsinas Head of Network Design and Development About Thomson Reuters We are the leading source of intelligent information
REUTERS / Stefano Rellandini Enterprise Case Study The Future of Your WAN Dimitrios Voutsinas Head of Network Design and Development About Thomson Reuters We are the leading source of intelligent information
Getting to Data Nirvana Data lakes and GDPR
 Getting to Data Nirvana Data lakes and GDPR A User's guide 1 Hogan Lovells Data lakes and GDPR: A User's guide 3 Copyright 2018. This report is the property of Hogan Lovells and may not be published or
Getting to Data Nirvana Data lakes and GDPR A User's guide 1 Hogan Lovells Data lakes and GDPR: A User's guide 3 Copyright 2018. This report is the property of Hogan Lovells and may not be published or
locuz.com SOC Services
 locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
locuz.com SOC Services 1 Locuz IT Security Lifecycle services combine people, processes and technologies to provide secure access to business applications, over any network and from any device. Our security
EY s data privacy service offering. How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world
 EY s data privacy service offering How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world In May 2018, the European Union s new General Data Protection
EY s data privacy service offering How to transform your data privacy capabilities for an EU General Data Protection Regulation (GDPR) world In May 2018, the European Union s new General Data Protection
Cybersecurity. The Board s Role
 Board Practice Cybersecurity The Board s Role There are two kinds of big companies in the United States. There are those who ve been hacked and those who don t know they ve been hacked. james comey former
Board Practice Cybersecurity The Board s Role There are two kinds of big companies in the United States. There are those who ve been hacked and those who don t know they ve been hacked. james comey former
2018 Data Security Incident Response Report Building Cyber Resilience: Compromise Response Intelligence in Action
 2018 Data Security Incident Response Report Building Cyber Resilience: Compromise Response Intelligence in Action April 11, 2018 Contact Information Casie D. Collignon Partner Denver 303.764.4037 ccollignon@bakerlaw.com
2018 Data Security Incident Response Report Building Cyber Resilience: Compromise Response Intelligence in Action April 11, 2018 Contact Information Casie D. Collignon Partner Denver 303.764.4037 ccollignon@bakerlaw.com
Dealing with Security and Security Breaches
 BEIJING BRUSSELS CHICAGO DALLAS FRANKFURT GENEVA HONG KONG LONDON LOS ANGELES NEW YORK PALO ALTO SAN FRANCISCO SHANGHAI SINGAPORE SYDNEY TOKYO WASHINGTON, D.C. Dealing with Security and Security Breaches
BEIJING BRUSSELS CHICAGO DALLAS FRANKFURT GENEVA HONG KONG LONDON LOS ANGELES NEW YORK PALO ALTO SAN FRANCISCO SHANGHAI SINGAPORE SYDNEY TOKYO WASHINGTON, D.C. Dealing with Security and Security Breaches
The Stakes Are Going Up: Hacking and the New Paradigm of Data Breaches
 The Stakes Are Going Up: Hacking and the New Paradigm of Data Breaches Edward McNicholas Global Co-Leader, Privacy, Data Security and Information Law Sidley Austin LLP The cyber threat is one of the most
The Stakes Are Going Up: Hacking and the New Paradigm of Data Breaches Edward McNicholas Global Co-Leader, Privacy, Data Security and Information Law Sidley Austin LLP The cyber threat is one of the most
The IBM Platform Computing HPC Cloud Service. Solution Overview
 The IBM Platform Computing HPC Cloud Service Solution Overview Industry-leading workload management 20 years managing distributed scale-out systems with 2000+ customers in many industries High performance
The IBM Platform Computing HPC Cloud Service Solution Overview Industry-leading workload management 20 years managing distributed scale-out systems with 2000+ customers in many industries High performance
Clarity on Cyber Security. Media conference 29 May 2018
 Clarity on Cyber Security Media conference 29 May 2018 Why this study? 2 Methodology Methodology of the study Online survey consisting of 33 questions 60 participants from C-Level (CISOs, CIOs, CTOs) 26
Clarity on Cyber Security Media conference 29 May 2018 Why this study? 2 Methodology Methodology of the study Online survey consisting of 33 questions 60 participants from C-Level (CISOs, CIOs, CTOs) 26
Why trading firms choose... Connexus Voice. For Traders
 Why trading firms choose... Connexus Voice For Traders Intelligent SIP based Voice Services Financial traders need instant connectivity to their counterparties, and private Connexus Voice circuits provide
Why trading firms choose... Connexus Voice For Traders Intelligent SIP based Voice Services Financial traders need instant connectivity to their counterparties, and private Connexus Voice circuits provide
EY Norwegian Cloud Maturity Survey Current and planned adoption of cloud services
 EY Norwegian Cloud Maturity Survey 2019 Current and planned adoption of cloud services Contents 01 Cloud maturity 4 02 Drivers and challenges 6 03 Current usage 10 04 Future plans 16 05 About the survey
EY Norwegian Cloud Maturity Survey 2019 Current and planned adoption of cloud services Contents 01 Cloud maturity 4 02 Drivers and challenges 6 03 Current usage 10 04 Future plans 16 05 About the survey
If you were under cyber attack would you ever know?
 If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
If you were under cyber attack would you ever know? EY and Los Alamos National Laboratory introduce a shift in cybersecurity strategy and bring behavioral analytics inside Asking behavioral questions inside
Building Interconnection 2017 Steps Taken & 2018 Plans
 Building Interconnection 2017 Steps Taken & 2018 Plans 2017 Equinix Inc. 2017 Key Highlights Expansion - new markets Launch - Flexible DataCentre Hyperscaler edge Rollout - IXEverywhere - SaaS, IoT & Ecosystems
Building Interconnection 2017 Steps Taken & 2018 Plans 2017 Equinix Inc. 2017 Key Highlights Expansion - new markets Launch - Flexible DataCentre Hyperscaler edge Rollout - IXEverywhere - SaaS, IoT & Ecosystems
Does someone else own your company s reputation? EY Global Information Security Survey 2018
 Does someone else own your company s reputation? EY Global Information Security Survey 2018 Perspectives for technology, media and entertainment, and telco companies Risking cyber reputations Are TMT companies
Does someone else own your company s reputation? EY Global Information Security Survey 2018 Perspectives for technology, media and entertainment, and telco companies Risking cyber reputations Are TMT companies
Certificate. Certificate number: a. Certified by EY CertifyPoint since: May 11, 2012
 Certificate Certificate number: 2012-001a Certified by EY CertifyPoint since: May 11, 2012 Based on certification examination in conformity with defined requirements in ISO/IEC 17021-1:2015 and ISO/IEC
Certificate Certificate number: 2012-001a Certified by EY CertifyPoint since: May 11, 2012 Based on certification examination in conformity with defined requirements in ISO/IEC 17021-1:2015 and ISO/IEC
HKTDC The World's Full-Service Trade Promotion Organisation
 HKTDC The World's Full-Service Trade Promotion Organisation The Hong Kong Trade Development Council (HKTDC) creates opportunity by promoting the global trade of goods and services, and connecting the world
HKTDC The World's Full-Service Trade Promotion Organisation The Hong Kong Trade Development Council (HKTDC) creates opportunity by promoting the global trade of goods and services, and connecting the world
Third-Party Cyber Risk Management Webinar May 23, 2017
 Third-Party Cyber Risk Management Webinar May 23, 2017 Today s speakers Nikole Davenport Senior Manager Deloitte & Touche LLP Nikole is a senior manager in Deloitte s Cyber Risk Services practice, specializing
Third-Party Cyber Risk Management Webinar May 23, 2017 Today s speakers Nikole Davenport Senior Manager Deloitte & Touche LLP Nikole is a senior manager in Deloitte s Cyber Risk Services practice, specializing
GDPR and digital advertising: Strategies and best practices for implementing GDPR compliance
 IP, Tech & Data GDPR and digital advertising: Strategies and best practices for implementing GDPR compliance Presented by: Gerard M. Stegmaier, Partner, Washington, D.C. October 17, 2018 What is GDPR,
IP, Tech & Data GDPR and digital advertising: Strategies and best practices for implementing GDPR compliance Presented by: Gerard M. Stegmaier, Partner, Washington, D.C. October 17, 2018 What is GDPR,
FDA Releases FSMA Final Rule on Accreditation of Third Party Certification Bodies
 Hogan Lovells US LLP Columbia Square 555 Thirteenth Street, NW Washington, DC 20004 T +1 202 637 5600 F +1 202 637 5910 www.hoganlovells.com MEMORANDUM From: Joseph A. Levitt Elizabeth Barr Fawell Maile
Hogan Lovells US LLP Columbia Square 555 Thirteenth Street, NW Washington, DC 20004 T +1 202 637 5600 F +1 202 637 5910 www.hoganlovells.com MEMORANDUM From: Joseph A. Levitt Elizabeth Barr Fawell Maile
Cybersecurity Protecting your crown jewels
 Cybersecurity Protecting your crown jewels Our cyber security services We view cybersecurity through a series of interconnected lenses. This rounded approach is designed to provide you with confidence:
Cybersecurity Protecting your crown jewels Our cyber security services We view cybersecurity through a series of interconnected lenses. This rounded approach is designed to provide you with confidence:
SEC Update. SEC issues new interpretive guidance on cybersecurity disclosures. March 5, Overview
 SEC Update March 5, 2018 This is a commercial communication from Hogan Lovells. See note below. SEC issues new interpretive guidance on cybersecurity disclosures On February 21, the Securities and Exchange
SEC Update March 5, 2018 This is a commercial communication from Hogan Lovells. See note below. SEC issues new interpretive guidance on cybersecurity disclosures On February 21, the Securities and Exchange
Robert Bond. Respecting Privacy, Securing Data and Enabling Trust a view from Europe
 Respecting Privacy, Securing Data and Enabling Trust a view from Europe Robert Bond, Partner & Notary Public Robert Bond Robert Bond has nearly 40 years' experience in advising national and international
Respecting Privacy, Securing Data and Enabling Trust a view from Europe Robert Bond, Partner & Notary Public Robert Bond Robert Bond has nearly 40 years' experience in advising national and international
2017 Data Security Incident Response Report. Be Compromise Ready: Go Back to the Basics
 2017 Data Security Incident Response Report Be Compromise Ready: Go Back to the Basics May 9, 2017 Contact Information Theodore J. Kobus, III Leader, Privacy and Data Protection Practice New York 212.271.1504
2017 Data Security Incident Response Report Be Compromise Ready: Go Back to the Basics May 9, 2017 Contact Information Theodore J. Kobus, III Leader, Privacy and Data Protection Practice New York 212.271.1504
Cyber Security Incident Response Fighting Fire with Fire
 Cyber Security Incident Response Fighting Fire with Fire Arun Perinkolam, Senior Manager Deloitte & Touche LLP Professional Techniques T21 CRISC CGEIT CISM CISA AGENDA Companies like yours What is the
Cyber Security Incident Response Fighting Fire with Fire Arun Perinkolam, Senior Manager Deloitte & Touche LLP Professional Techniques T21 CRISC CGEIT CISM CISA AGENDA Companies like yours What is the
Tax News Update: Global Edition (GTNU) User Guide
 Tax News Update: Global Edition (GTNU) User Guide Agenda GTNU introduction Highlights How to access GTNU How to set up email preferences Browsing for content Refinement panel Searching for content Page
Tax News Update: Global Edition (GTNU) User Guide Agenda GTNU introduction Highlights How to access GTNU How to set up email preferences Browsing for content Refinement panel Searching for content Page
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
MITIGATE CYBER ATTACK RISK
 SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
SOLUTION BRIEF MITIGATE CYBER ATTACK RISK CONNECTING SECURITY, RISK MANAGEMENT & BUSINESS TEAMS TO MINIMIZE THE WIDESPREAD IMPACT OF A CYBER ATTACK DIGITAL TRANSFORMATION CREATES NEW RISKS As organizations
Danish Cloud Maturity Survey 2018
 Danish Cloud Maturity Survey 2018 Current and planned adoption of cloud services Danish Cloud Maturity Survey 2018 1 Early days for cloud adoption with concerns for security and expertise, and complexity
Danish Cloud Maturity Survey 2018 Current and planned adoption of cloud services Danish Cloud Maturity Survey 2018 1 Early days for cloud adoption with concerns for security and expertise, and complexity
Workday s Robust Privacy Program
 Workday s Robust Privacy Program Workday s Robust Privacy Program Introduction Workday is a leading provider of enterprise cloud applications for human resources and finance. Founded in 2005 by Dave Duffield
Workday s Robust Privacy Program Workday s Robust Privacy Program Introduction Workday is a leading provider of enterprise cloud applications for human resources and finance. Founded in 2005 by Dave Duffield
Plan a Pragmatic Approach to the new EU Data Privacy Regulation
 AmChamDenmark event: EU Compliant & Cyber Resistant Plan a Pragmatic Approach to the new EU Data Privacy Regulation Janus Friis Bindslev, Partner Cyber Risk Services, Deloitte 4 February 2016 Agenda General
AmChamDenmark event: EU Compliant & Cyber Resistant Plan a Pragmatic Approach to the new EU Data Privacy Regulation Janus Friis Bindslev, Partner Cyber Risk Services, Deloitte 4 February 2016 Agenda General
Global Information Security Survey. A life sciences perspective
 Global Information Security Survey A life sciences perspective Introduction Welcome to the life sciences perspective on the results from Creating trust in the digital world: EY s Global Information Security
Global Information Security Survey A life sciences perspective Introduction Welcome to the life sciences perspective on the results from Creating trust in the digital world: EY s Global Information Security
December 10, Statement of the Securities Industry and Financial Markets Association. Senate Committee on Banking, Housing, and Urban Development
 December 10, 2014 Statement of the Securities Industry and Financial Markets Association Senate Committee on Banking, Housing, and Urban Development Hearing Entitled Cybersecurity: Enhancing Coordination
December 10, 2014 Statement of the Securities Industry and Financial Markets Association Senate Committee on Banking, Housing, and Urban Development Hearing Entitled Cybersecurity: Enhancing Coordination
Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK.
 Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK. In today s escalating cyber risk environment, you need to make sure you re focused on the right priorities by
Cyber Risk Program Maturity Assessment UNDERSTAND AND MANAGE YOUR ORGANIZATION S CYBER RISK. In today s escalating cyber risk environment, you need to make sure you re focused on the right priorities by
BUILT FOR THE STORM. AND THE NORM.
 BUILT FOR THE STORM. AND THE NORM. Data volumes are overwhelming. Stakes are sky-high. Time frames are shorter than ever. GET ANSWERS NOW. EM[URGENT]CY EXIT In a world where the routine can quickly become
BUILT FOR THE STORM. AND THE NORM. Data volumes are overwhelming. Stakes are sky-high. Time frames are shorter than ever. GET ANSWERS NOW. EM[URGENT]CY EXIT In a world where the routine can quickly become
Contact us What makes us different Dinesh Anand Our offices Forensic Bangalore Kolkata Cutting-edge technology to deliver more efficiently Services
 Forensic Services Who we are Pioneers Experienced innovators Thought leaders Pioneers of forensic services in India Partner group with 100+ person-years of forensic experience Handled some of the most
Forensic Services Who we are Pioneers Experienced innovators Thought leaders Pioneers of forensic services in India Partner group with 100+ person-years of forensic experience Handled some of the most
Coworking 2.0. Stavební Fórum October
 Stavební Fórum October 25-2018 The History Of Coworking 1995 1995 2005 2006 2008 2009 As hackerspaces can be considered as one of the first pre-form of spaces. Vienna's mother of spaces opened. The first
Stavební Fórum October 25-2018 The History Of Coworking 1995 1995 2005 2006 2008 2009 As hackerspaces can be considered as one of the first pre-form of spaces. Vienna's mother of spaces opened. The first
TIPS FOR FORGING A BETTER WORKING RELATIONSHIP BETWEEN COUNSEL AND IT TO IMPROVE CYBER-RESPONSE
 TIPS FOR FORGING A BETTER WORKING RELATIONSHIP BETWEEN COUNSEL AND IT TO IMPROVE CYBER-RESPONSE Association of Corporate Counsel NYC Chapter 11/1 NYC BDO USA, LLP, a Delaware limited liability partnership,
TIPS FOR FORGING A BETTER WORKING RELATIONSHIP BETWEEN COUNSEL AND IT TO IMPROVE CYBER-RESPONSE Association of Corporate Counsel NYC Chapter 11/1 NYC BDO USA, LLP, a Delaware limited liability partnership,
CCISO Blueprint v1. EC-Council
 CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
Professional Training Course - Cybercrime Investigation Body of Knowledge -
 Overview The expanded use of the Internet has facilitated rapid advances in communications, systems control, and information sharing. Those advances have created enormous opportunities for society, commerce
Overview The expanded use of the Internet has facilitated rapid advances in communications, systems control, and information sharing. Those advances have created enormous opportunities for society, commerce
SOLUTION BRIEF HELPING BREACH RESPONSE FOR GDPR WITH RSA SECURITY ADDRESSING THE TICKING CLOCK OF GDPR COMPLIANCE
 HELPING BREACH RESPONSE FOR GDPR WITH RSA SECURITY ADDRESSING THE TICKING CLOCK OF GDPR COMPLIANCE PREPARATION FOR GDPR IS ESSENTIAL The EU GDPR imposes interrelated obligations for organizations handling
HELPING BREACH RESPONSE FOR GDPR WITH RSA SECURITY ADDRESSING THE TICKING CLOCK OF GDPR COMPLIANCE PREPARATION FOR GDPR IS ESSENTIAL The EU GDPR imposes interrelated obligations for organizations handling
Step 1: Open browser to navigate to the data science challenge home page
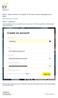 Step 1: Open browser to navigate to the data science challenge home page https://datascience.ey.com/ Step 2: Logging in You will need to create an account if you are a new user. Click the sign up button
Step 1: Open browser to navigate to the data science challenge home page https://datascience.ey.com/ Step 2: Logging in You will need to create an account if you are a new user. Click the sign up button
Governing cyber security risk: It s time to take it seriously Seven principles for Boards and Investors
 www.pwc.co.uk Governing cyber security risk: It s time to take it seriously Seven principles for Boards and Investors Dr. Richard Horne Cyber Security Partner PwC January 2017 Board governance is often
www.pwc.co.uk Governing cyber security risk: It s time to take it seriously Seven principles for Boards and Investors Dr. Richard Horne Cyber Security Partner PwC January 2017 Board governance is often
PROVIDING INVESTIGATIVE SOLUTIONS
 PROVIDING INVESTIGATIVE SOLUTIONS Experienced Professionals Northeast Intelligence Group, Inc. (NEIG) has been helping clients meet challenges for more than twenty years. By providing meaningful and timely
PROVIDING INVESTIGATIVE SOLUTIONS Experienced Professionals Northeast Intelligence Group, Inc. (NEIG) has been helping clients meet challenges for more than twenty years. By providing meaningful and timely
Fundamentals of Cybersecurity/CIIP. Building Capacity: Using a National Strategy & Self-Assessment
 Fundamentals of Cybersecurity/CIIP Building Capacity: Using a National Strategy & Self- Presented to: 2009 ITU Regional Cybersecurity Forum for Asia-Pacific Connecting the World Responsibly 23-25 25 September
Fundamentals of Cybersecurity/CIIP Building Capacity: Using a National Strategy & Self- Presented to: 2009 ITU Regional Cybersecurity Forum for Asia-Pacific Connecting the World Responsibly 23-25 25 September
Certificate. Certificate number: b. Certified by EY CertifyPoint since: April 15, 2016
 Certificate Certificate number: 2016-004b Certified by EY CertifyPoint since: April 15, 2016 Based on certification examination in conformity with defined requirements in ISO/IEC 17021-1:2015 and ISO/IEC
Certificate Certificate number: 2016-004b Certified by EY CertifyPoint since: April 15, 2016 Based on certification examination in conformity with defined requirements in ISO/IEC 17021-1:2015 and ISO/IEC
SOC 3 for Security and Availability
 SOC 3 for Security and Availability Independent Practioner s Trust Services Report For the Period October 1, 2015 through September 30, 2016 Independent SOC 3 Report for the Security and Availability Trust
SOC 3 for Security and Availability Independent Practioner s Trust Services Report For the Period October 1, 2015 through September 30, 2016 Independent SOC 3 Report for the Security and Availability Trust
Complete IP Video Security Solutions
 Complete IP Video Security Solutions www.indigovision.com About Us First security project Cameras using IndigoVision s encoding hardware are deployed. World s first NVR The IndigoVision Network Video Recorder
Complete IP Video Security Solutions www.indigovision.com About Us First security project Cameras using IndigoVision s encoding hardware are deployed. World s first NVR The IndigoVision Network Video Recorder
Incident Response Services to Help You Prepare for and Quickly Respond to Security Incidents
 Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
Services to Help You Prepare for and Quickly Respond to Security Incidents The Challenge The threat landscape is always evolving and adversaries are getting harder to detect; and with that, cyber risk
On the Radar: IBM Resilient applies incident response orchestration to GDPR data breaches
 On the Radar: IBM Resilient applies incident response orchestration to GDPR data breaches An incident response orchestration platform tailored to GDPR breach management needs Publication Date: 24 Oct 2018
On the Radar: IBM Resilient applies incident response orchestration to GDPR data breaches An incident response orchestration platform tailored to GDPR breach management needs Publication Date: 24 Oct 2018
Your Cloud Strategy Demands a Strong Network Strategy
 Your Cloud Strategy Demands a Strong Network Strategy An Executive Brief Sponsored by GTT January 2015 Roopashree (Roopa) Honnachari Industry Director Business Communication Services & Cloud Computing
Your Cloud Strategy Demands a Strong Network Strategy An Executive Brief Sponsored by GTT January 2015 Roopashree (Roopa) Honnachari Industry Director Business Communication Services & Cloud Computing
EU General Data Protection Regulation (GDPR) Achieving compliance
 EU General Data Protection Regulation (GDPR) Achieving compliance GDPR enhancing data protection and privacy The new EU General Data Protection Regulation (GDPR) will apply across all EU member states,
EU General Data Protection Regulation (GDPR) Achieving compliance GDPR enhancing data protection and privacy The new EU General Data Protection Regulation (GDPR) will apply across all EU member states,
EY Norwegian Cloud Maturity Survey 2018
 EY Norwegian Cloud Maturity Survey 2018 Current and planned adoption of cloud services EY Norwegian Cloud Maturity Survey 2018 1 It is still early days for cloud adoption in Norway, and the complexity
EY Norwegian Cloud Maturity Survey 2018 Current and planned adoption of cloud services EY Norwegian Cloud Maturity Survey 2018 1 It is still early days for cloud adoption in Norway, and the complexity
Sage Data Security Services Directory
 Sage Data Security Services Directory PROTECTING INFORMATION ASSETS ENSURING REGULATORY COMPLIANCE FIGHTING CYBERCRIME Discover the Sage Difference Protecting your business from cyber attacks is a full-time
Sage Data Security Services Directory PROTECTING INFORMATION ASSETS ENSURING REGULATORY COMPLIANCE FIGHTING CYBERCRIME Discover the Sage Difference Protecting your business from cyber attacks is a full-time
Digital trends in real estate, hospitality and construction. Building blocks for future growth. Brochure title RR. Brochure subtitle RR
 Digital trends in real estate, hospitality and construction Building blocks for future growth Brochure title RR Brochure subtitle RR 2 Digital trends in real estate, hospitality and construction: building
Digital trends in real estate, hospitality and construction Building blocks for future growth Brochure title RR Brochure subtitle RR 2 Digital trends in real estate, hospitality and construction: building
Are we breached? Deloitte's Cyber Threat Hunting
 Are we breached? Deloitte's Cyber Threat Hunting Brochure / report title goes here Section title goes here Have we been breached? Are we exposed? How do we proactively detect an attack and minimize the
Are we breached? Deloitte's Cyber Threat Hunting Brochure / report title goes here Section title goes here Have we been breached? Are we exposed? How do we proactively detect an attack and minimize the
Avanade s Approach to Client Data Protection
 White Paper Avanade s Approach to Client Data Protection White Paper The Threat Landscape Businesses today face many risks and emerging threats to their IT systems and data. To achieve sustainable success
White Paper Avanade s Approach to Client Data Protection White Paper The Threat Landscape Businesses today face many risks and emerging threats to their IT systems and data. To achieve sustainable success
New York Cybersecurity. New York Cybersecurity. Requirements for Financial Services Companies (23NYCRR 500) Solution Brief
 Publication Date: March 10, 2017 Requirements for Financial Services Companies (23NYCRR 500) Solution Brief EventTracker 8815 Centre Park Drive, Columbia MD 21045 About EventTracker EventTracker s advanced
Publication Date: March 10, 2017 Requirements for Financial Services Companies (23NYCRR 500) Solution Brief EventTracker 8815 Centre Park Drive, Columbia MD 21045 About EventTracker EventTracker s advanced
Cybersecurity: Considerations for Internal Audit. Gina Gondron Senior Manager Frazier & Deeter Geek Week August 10, 2016
 Cybersecurity: Considerations for Internal Audit Gina Gondron Senior Manager Frazier & Deeter Geek Week August 10, 2016 Agenda Key Risks Incorporating Internal Audit Resources Questions 2 San Francisco
Cybersecurity: Considerations for Internal Audit Gina Gondron Senior Manager Frazier & Deeter Geek Week August 10, 2016 Agenda Key Risks Incorporating Internal Audit Resources Questions 2 San Francisco
A Framework for Managing Crime and Fraud
 A Framework for Managing Crime and Fraud ASIS International Asia Pacific Security Forum & Exhibition Macau, December 4, 2013 Torsten Wolf, CPP Head of Group Security Operations Agenda Introduction Economic
A Framework for Managing Crime and Fraud ASIS International Asia Pacific Security Forum & Exhibition Macau, December 4, 2013 Torsten Wolf, CPP Head of Group Security Operations Agenda Introduction Economic
NetIQ User Conferentie NetIQ Update. Travis Greene Chief Service Management Strategist
 NetIQ Update Travis Greene Chief Service Strategist About NetIQ Strength, Leadership and Innovation NetIQ, An Attachmate Business One of the top 25 software companies in the world Thousands of customers,
NetIQ Update Travis Greene Chief Service Strategist About NetIQ Strength, Leadership and Innovation NetIQ, An Attachmate Business One of the top 25 software companies in the world Thousands of customers,
ADDRESSING CLIMATE FROM THE GROUND UP
 E2 Environmental Entrepreneurs ADDRESSING CLIMATE FROM THE GROUND UP Jamie Ponce Chicago City Director, C40 Cities Climate Leadership Group 21-February-2014 The C40 Cities Climate Leadership Group is a
E2 Environmental Entrepreneurs ADDRESSING CLIMATE FROM THE GROUND UP Jamie Ponce Chicago City Director, C40 Cities Climate Leadership Group 21-February-2014 The C40 Cities Climate Leadership Group is a
Data Privacy and Cybersecurity
 Data Privacy and Cybersecurity Key Contacts Timothy C. Blank Boston +1 617 728 7154 Dr. Olaf Fasshauer National Munich +49 89 21 21 63 28 Joshua H. Rawson New York +1 212 698 3862 Translate Page In an
Data Privacy and Cybersecurity Key Contacts Timothy C. Blank Boston +1 617 728 7154 Dr. Olaf Fasshauer National Munich +49 89 21 21 63 28 Joshua H. Rawson New York +1 212 698 3862 Translate Page In an
Emerging Technologies The risks they pose to your organisations
 Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
Emerging Technologies The risks they pose to your organisations 10 June 2016 Digital trends are fundamentally changing the way that customers behave and companies operate Mobile Connecting people and things
CYBERSECURITY RISK MANAGEMENT
 CYBERSECURITY RISK MANAGEMENT RETHINKING PROTECTION Cybersecurity is one of the most challenging risks confronting companies around the world. In today s interconnected world, virtually all companies and
CYBERSECURITY RISK MANAGEMENT RETHINKING PROTECTION Cybersecurity is one of the most challenging risks confronting companies around the world. In today s interconnected world, virtually all companies and
Stephanie Zierten Associate Counsel Federal Reserve Bank of Boston
 Stephanie Zierten Associate Counsel Federal Reserve Bank of Boston Cybersecurity Landscape Major Data Breaches (e.g., OPM, IRS) Data Breach Notification Laws Directors Derivative Suits Federal Legislation
Stephanie Zierten Associate Counsel Federal Reserve Bank of Boston Cybersecurity Landscape Major Data Breaches (e.g., OPM, IRS) Data Breach Notification Laws Directors Derivative Suits Federal Legislation
Val-EdTM. Valiant Technologies Education & Training Services. Workshop for CISM aspirants. All Trademarks and Copyrights recognized.
 Val-EdTM Valiant Technologies Education & Training Services Workshop for CISM aspirants All Trademarks and Copyrights recognized Page 1 of 8 Welcome to Valiant Technologies. We are a specialty consulting
Val-EdTM Valiant Technologies Education & Training Services Workshop for CISM aspirants All Trademarks and Copyrights recognized Page 1 of 8 Welcome to Valiant Technologies. We are a specialty consulting
GDPR: An Opportunity to Transform Your Security Operations
 GDPR: An Opportunity to Transform Your Security Operations McAfee SIEM solutions improve breach detection and response Is your security operations GDPR ready? General Data Protection Regulation (GDPR)
GDPR: An Opportunity to Transform Your Security Operations McAfee SIEM solutions improve breach detection and response Is your security operations GDPR ready? General Data Protection Regulation (GDPR)
CYBER THREATS, ACTIVE DEFENSE, AND THE BUSINESS AND LEGAL IMPACTS. October 20, Robert Silvers
 CYBER THREATS, ACTIVE DEFENSE, AND THE BUSINESS AND LEGAL IMPACTS October 20, 2017 Robert Silvers +1 202 551 1216 robertsilvers@paulhastings.com Haiyan Tang +86 21 6103 2722 haiyantang@paulhastings.com
CYBER THREATS, ACTIVE DEFENSE, AND THE BUSINESS AND LEGAL IMPACTS October 20, 2017 Robert Silvers +1 202 551 1216 robertsilvers@paulhastings.com Haiyan Tang +86 21 6103 2722 haiyantang@paulhastings.com
Cloud for Government: A Transformative Digital Tool to Better Serve Communities
 Cloud for Government: A Transformative Digital Tool to Better Serve Communities 1 005181004 From state to local agencies, government organizations crave access to the same cloud-based tools enabling digital
Cloud for Government: A Transformative Digital Tool to Better Serve Communities 1 005181004 From state to local agencies, government organizations crave access to the same cloud-based tools enabling digital
EU GDPR & NEW YORK CYBERSECURITY REQUIREMENTS 3 KEYS TO SUCCESS
 EU GDPR & NEW YORK CYBERSECURITY REQUIREMENTS 3 KEYS TO SUCCESS MEET THE EXPERTS DAVID O LEARY Director, Forsythe Security Solutions THOMAS ECK Director, Forsythe Security Solutions ALEX HANWAY Product
EU GDPR & NEW YORK CYBERSECURITY REQUIREMENTS 3 KEYS TO SUCCESS MEET THE EXPERTS DAVID O LEARY Director, Forsythe Security Solutions THOMAS ECK Director, Forsythe Security Solutions ALEX HANWAY Product

 A (soj
A (soj