My Health, My Data (and other related projects) Yannis Ioannidis ATHENA Research Center & University of Athens
|
|
|
- Chad Mosley
- 5 years ago
- Views:
Transcription
1 My Health, My Data (and other related projects) Yannis Ioannidis ATHENA Research Center & University of Athens
2 My Health, My Data! 1 / 11 / / 10 / 2019 ~3M ( ~420K for ARC)
3
4 Age ParCHD Procedures ExIntoler Cyanosis CPBP CPArrhy CPConcl CPTermRsn BSA TPVRegurg TriRegurg RVD RedRV PSMotion RestrPatt AVBlock SupravArrhy VentricArrhy Final DAG (based on MCMC&DP, threshold=0.5) Unknown / missing data Multiple pipelines personalized data acquisition (e.g., feature extraction from images) Diagnostic p. medicine flow Biomarkers Clinical Workflows (medical protocols) Precision Medicine Support Reasoning, Simulation & DSS For a particular patient Predict value of missing variable Individualized diagnosis, prognosis & treatment plan Data Management & Harmonisation Data modelling, ETL, enrichment & curation DOWNSTREAM Phenotype & Clinical data Data Exploration & cohort selection Explore, select and prepare for analysis Domain knowledge & assumptions TOP-DOWN BOTTOM-UP Data Analysis & Modelling Knowledge Discovery & Model training UPSTREAM Age ParCHD Procedures ExIntoler Cyanosis CPBP CPArrhy CPConcl CPTermRsn BSA TPVRegurg TriRegurg RVD RedRV PSMotion RestrPatt AVBlock SupravArrhy VentricArrhy External Data sources (dbsnp, PharmGB, DrugBank ) Integrated, curated and annotated data Dataset for analysis Disease signatures & patient groups Variables dependencies & prediction models Research data analysis and modelling flow for p. medicine
5 WHAT WHERE HOW WHY Quality Assurance, Quality of Service, Compliance & Dissemination HES-SO [WP1]: Requirements Analysis CNR [WP9]: Penetration & Re-Identification Challenge LYN [WP7]: Platform-driven Assessment Application Layer (WEB & Apps) SIEMENS, ATHENA, HES-SO [WP2, WP8] Data Exploration, Analytics & Cohort Builder based on advanced Similarity & Semantic Search LYN [WP11]: Coordination & Management NCTM [WP2]: Regulatory and Compliance Study LYN [WP10]: Dissemination and Exploitation HWC, DigiMe [WP3] Personal Data Account (PDA) & Dynamic consent management API (for SaaS applications) ATHENA, GNUBILA (WP5, WP6) Privacy by design middleware Layer ATHENA, GNUBILA [WP5] Privacy preserving distributed data processing GNUBILA, ATHENA, HWC [WP6, WP3] Blockchain Integration & Smart contracts management DigiMe, HWC [WP3] Personal Data acquisition and management Federated Data Management & Data Harmonisation Layer ATHENA [WP5]: Data Profiling & curation (quality, privacy & analysis) HES-SO, ATHENA [WP4] : Semantic Modeling and data integration HES-SO, GNUBILA [WP4]: Persistent Identifiers Cataloguing (PID) Private Data Sources Hospitals Electronic Medical Records Personal Data Subjects social media accounts, clinical data repositories, personal drives, wearable devices
6 WHAT WHERE HOW WHY Quality Assurance, Quality of Service, Compliance & Dissemination HES-SO [WP1]: Requirements Analysis CNR [WP9]: Penetration & Re-Identification Challenge LYN [WP7]: Platform-driven Assessment Application Layer (WEB & Apps) SIEMENS, ATHENA, HES-SO [WP2, WP8] Data Exploration, Analytics & Cohort Builder based on advanced Similarity & Semantic Search LYN [WP11]: Coordination & Management NCTM [WP2]: Regulatory and Compliance Study LYN [WP10]: Dissemination and Exploitation HWC, DigiMe [WP3] Personal Data Account (PDA) & Dynamic consent management API (for SaaS applications) ATHENA, GNUBILA (WP5, WP6) Privacy by design middleware Layer ATHENA, GNUBILA [WP5] Privacy preserving distributed data processing GNUBILA, ATHENA, HWC [WP6, WP3] Blockchain Integration & Smart contracts management DigiMe, HWC [WP3] Personal Data acquisition and management Federated Data Management & Data Harmonisation Layer ATHENA [WP5]: Data Profiling & curation (quality, privacy & analysis) HES-SO, ATHENA [WP4] : Semantic Modeling and data integration HES-SO, GNUBILA [WP4]: Persistent Identifiers Cataloguing (PID) Private Data Sources Hospitals Electronic Medical Records Personal Data Subjects social media accounts, clinical data repositories, personal drives, wearable devices
7 Data Collection and Management Data collection / origin Pseudonymised (de-identified) clinical (routine) data Personal data including machine-generated data from Internet of Things (IoT) Derived data related to the usage and the processing of the data Data storage & preservation Federated data management for clinical data ETL, pre-processing and pseudo-anonymization flow DIGI.me Personal Data Account (PDA) application retrieve personal data to an encrypted local library, which the users can then add to a personal cloud Data Modelling, Harmonisation, Cataloguing and Integration Global dynamic Subjective-Objective-Assessment-Plan (SOAP) model Use biomedical taxonomies and ontologies such as LOINC, SNOMED CT, ICD-10-CM, CPT, MESH Persistent Identifiers (PIDs) Secure data access, sharing and processing in line with GDPR legislation
8 Hospitals OPBG - Vatican UCL/GOSH London DH Berlin IGG Genova KU - Leuven CHUV Lausanne
9 WHAT WHERE HOW WHY Quality Assurance, Quality of Service, Compliance & Dissemination HES-SO [WP1]: Requirements Analysis CNR [WP9]: Penetration & Re-Identification Challenge LYN [WP7]: Platform-driven Assessment Application Layer (WEB & Apps) SIEMENS, ATHENA, HES-SO [WP2, WP8] Data Exploration, Analytics & Cohort Builder based on advanced Similarity & Semantic Search LYN [WP11]: Coordination & Management NCTM [WP2]: Regulatory and Compliance Study LYN [WP10]: Dissemination and Exploitation HWC, DigiMe [WP3] Personal Data Account (PDA) & Dynamic consent management API (for SaaS applications) ATHENA, GNUBILA (WP5, WP6) Privacy by design middleware Layer ATHENA, GNUBILA [WP5] Privacy preserving distributed data processing GNUBILA, ATHENA, HWC [WP6, WP3] Blockchain Integration & Smart contracts management DigiMe, HWC [WP3] Personal Data acquisition and management Federated Data Management & Data Harmonisation Layer ATHENA [WP5]: Data Profiling & curation (quality, privacy & analysis) HES-SO, ATHENA [WP4] : Semantic Modeling and data integration HES-SO, GNUBILA [WP4]: Persistent Identifiers Cataloguing (PID) Private Data Sources Hospitals Electronic Medical Records Personal Data Subjects social media accounts, clinical data repositories, personal drives, wearable devices
10 Data access & Privacy preservation Security / privacy breaches: avoid a single point of failure (i.e., datawarehouse, TTP): decentralize data (transactions, patient data) and control using federation and blockchain offer multiple levels of privacy preservation Ownership: Users should control their data, easily join or leave Transparency: Users should audit the usage of their data Privacy is important
11 PIDs PIDs PIDs consent Sharing Blockchain MHMD Data processors Output (WHAT) Bio-medical model (Anonymous) Medical Data Methods (HOW) PI (1) Initiates a Data Access request consent (3c) Execute a privacy Preserving computation Data (WHAT) Functions (WHY) (3a,b) Sharing of (Anonymous) EHRs consent Data subjects Data controllers (2) Re-identification & consent request Transaction Smart Contract a decentralized personal Blockchain as data an access-control management manager platform focused on privacy Actors (WHO) combine blockchain and off-blockchain storage users own, control and monitor their data and data usage Privacy preserving Privacy distributed preserving data Patient complex data utilize blockchain & smart contracts as an automated access- publishing flow execution control manager does not require trust in a third party Data controllers pointers to de-identified Digital data Object Architecture suitable (DOA) for random queries support full data processing through PPDM New cohort Request (2) consent request SeC MDP CDP
12 Blockchain integration Smart Contract WHO subjects & controllers processors & requesters WHAT & WHY Data Functions Output DMP & (privacy) profiling Publishing (external parties) Mining (within MHMD) Personal data access Models EHR data Predictions HOW Publishing: Anonymization & Watermarking Blockchain & Smart contracts (control & trace data usage) PPDM: MPC, DP, Encryption (on pseudoanonymized data)
13 Encryption and privacy preserving policies Three main use cases: Personal Data Access (no privacy) Patient accessing his/her EHR Static Data publishing Research VS other purposes Anonymization requirements (AMNESIA) Watermarking Privacy Preserving Data Mining (within platform) Move data (authorized applications get and process the data i.e., MDP / Cardioproof) Move computation to data: secure multiparty computation (SMC, DP) on federated data / distrustful parties (MHMD, HBP) Other encryption techniques (homomorphic)
14 Encryption and privacy preserving policies static data publishing: Sanitization (Anonymization) secure multi party computation: Only overall aggregated data are transferred between nodes interactive anonymization: Differential Privacy & Crowd-Blending privacy encryption: Fully/Partially Homomorphic Encryption (FHE) decentralization: Use Blockchain to Protect Personal Data
15 Efficiency Encryption and privacy preserving policies Privacy & Sensitivity Data Profiling: Define privacy profiles per data type & usage scenario Trade-offs among efficiency, accuracy & privacy Define a formal methodology to describe privacy budget in terms of expected accuracy Automate privacy preserving method selection based on privacy & sensitivity profile and efficiency / accuracy trade-offs
16 Secure Data publishing Sanitization (Anonymisation) hiding individual information (ensuring k-anonymity) but preserving aggregated (sufficient) statistics Different dangers Identity leakage Attribute leakage Participation leakage Different transformations Generalization Suppression Perturbation Partitioning Noise addition
17 Secure Data publishing Amnesia anonymization tool It offers several versions of k-anonymity It allows the user to select and customize possible solutions It offers graphical tools that allow the user to analyze the anonymized dataset It is scalable and uses all available CPU cores in the anonymization process Watermarking techniques
18 Privacy Preserving Data Mining The setting: Data is horizontally distributed at different sites on a Private Data Network (PDN) of mutually distrustfully parties The aim: Compute the data mining algorithm on the data so that nothing but the output is learned Use secure computation using SMPC, encryption, DP etc Assume Semi-honest types of adversaries that follow the protocol Makes sense where the participating parties really trust each other (e.g., hospitals) Training (learning) vs Reasoning: different requirements and privacy related issues training: needs access to patient records reasoning: needs only the model and new data subjects but Inference from the results: One can break privacy using well specified queries and analyzing the results
19 Distributed Privacy Preserving Data Mining: EXAREME Distributed elastic execution Iterative dataflow execution: Support ML algorithms Powerful data programming paradigm: SQL with User Defined Functions Privacy-aware query processing
20 Dataflow Execution Example L: Σx, Decompose Σx 2, N query into N, Run avg, global std G: N, local avg, and std global parts queries Partial aggregated results m-name Σx Σx 2 N Federatio n count, Query avg, std m-name N avg std Partial aggregated results m-name Σx Σx 2 N Local queries Local queries 1 N Σx,Σx Run 2 local,n Run local id m-name m-value Σx,Σx queries 2,N queries id m-name m-value
21
22 THANK YOU
Click to edit Master title style
 Click to edit Master title style HBP Period 1 Review (Oct 2013 Sep 2014) Human Brain Project Vasilis Vassalos vassalos@aueb.gr Click Human to edit Brain Master Project title style Goal What makes us human?
Click to edit Master title style HBP Period 1 Review (Oct 2013 Sep 2014) Human Brain Project Vasilis Vassalos vassalos@aueb.gr Click Human to edit Brain Master Project title style Goal What makes us human?
Accountability in Privacy-Preserving Data Mining
 PORTIA Privacy, Obligations, and Rights in Technologies of Information Assessment Accountability in Privacy-Preserving Data Mining Rebecca Wright Computer Science Department Stevens Institute of Technology
PORTIA Privacy, Obligations, and Rights in Technologies of Information Assessment Accountability in Privacy-Preserving Data Mining Rebecca Wright Computer Science Department Stevens Institute of Technology
Executive Summary for deliverable D6.1: Definition of the PFS services (requirements, initial design)
 Electronic Health Records for Clinical Research Executive Summary for deliverable D6.1: Definition of the PFS services (requirements, initial design) Project acronym: EHR4CR Project full title: Electronic
Electronic Health Records for Clinical Research Executive Summary for deliverable D6.1: Definition of the PFS services (requirements, initial design) Project acronym: EHR4CR Project full title: Electronic
Employing the principles of My Data and blockchain in building trust in farm data sharing
 Employing the principles of My Data and blockchain in building trust in farm data sharing Linked Open Data in Agriculture MACS-G20 workshop, Berlin Liisa Pesonen and Markku Koistinen Natural Resources
Employing the principles of My Data and blockchain in building trust in farm data sharing Linked Open Data in Agriculture MACS-G20 workshop, Berlin Liisa Pesonen and Markku Koistinen Natural Resources
Computer-based Tracking Protocols: Improving Communication between Databases
 Computer-based Tracking Protocols: Improving Communication between Databases Amol Deshpande Database Group Department of Computer Science University of Maryland Overview Food tracking and traceability
Computer-based Tracking Protocols: Improving Communication between Databases Amol Deshpande Database Group Department of Computer Science University of Maryland Overview Food tracking and traceability
Void main Technologies
 Sno Title Domain 1. A Cross Tenant Access Control (CTAC) Model for Cloud Computing: Formal Specification and Verification 2. A Lightweight Secure Data Sharing Scheme for Mobile Cloud Computing 3. A Modified
Sno Title Domain 1. A Cross Tenant Access Control (CTAC) Model for Cloud Computing: Formal Specification and Verification 2. A Lightweight Secure Data Sharing Scheme for Mobile Cloud Computing 3. A Modified
Data Replication: Automated move and copy of data. PRACE Advanced Training Course on Data Staging and Data Movement Helsinki, September 10 th 2013
 Data Replication: Automated move and copy of data PRACE Advanced Training Course on Data Staging and Data Movement Helsinki, September 10 th 2013 Claudio Cacciari c.cacciari@cineca.it Outline The issue
Data Replication: Automated move and copy of data PRACE Advanced Training Course on Data Staging and Data Movement Helsinki, September 10 th 2013 Claudio Cacciari c.cacciari@cineca.it Outline The issue
Statistical and Synthetic Data Sharing with Differential Privacy
 pscanner and idash Data Sharing Symposium UCSD, Sept 30 Oct 2, 2015 Statistical and Synthetic Data Sharing with Differential Privacy Li Xiong Department of Mathematics and Computer Science Department of
pscanner and idash Data Sharing Symposium UCSD, Sept 30 Oct 2, 2015 Statistical and Synthetic Data Sharing with Differential Privacy Li Xiong Department of Mathematics and Computer Science Department of
Fujitsu World Tour 2018
 Fujitsu World Tour 2018 May 30, 2018 #FujitsuWorldTour 1 Copyright 2018 FUJITSU Security and Privacy of Big Data A NIST Perspective Arnab Roy Fujitsu Laboratories of America Co-Chair, NIST Big Data WG:
Fujitsu World Tour 2018 May 30, 2018 #FujitsuWorldTour 1 Copyright 2018 FUJITSU Security and Privacy of Big Data A NIST Perspective Arnab Roy Fujitsu Laboratories of America Co-Chair, NIST Big Data WG:
Privacy-Preserving Distributed Linear Regression on High-Dimensional Data
 Privacy-Preserving Distributed Linear Regression on High-Dimensional Data Borja Balle Amazon Research Cambridge (work done at Lancaster University) Based on joint work with Adria Gascon, Phillipp Schoppmann,
Privacy-Preserving Distributed Linear Regression on High-Dimensional Data Borja Balle Amazon Research Cambridge (work done at Lancaster University) Based on joint work with Adria Gascon, Phillipp Schoppmann,
ETL is No Longer King, Long Live SDD
 ETL is No Longer King, Long Live SDD How to Close the Loop from Discovery to Information () to Insights (Analytics) to Outcomes (Business Processes) A presentation by Brian McCalley of DXC Technology,
ETL is No Longer King, Long Live SDD How to Close the Loop from Discovery to Information () to Insights (Analytics) to Outcomes (Business Processes) A presentation by Brian McCalley of DXC Technology,
Health Data & Blockchain: The New Sharing Frontier. Michael Dillhyon, CCO, Graftworx
 Health Data & Blockchain: The New Sharing Frontier Michael Dillhyon, CCO, Graftworx Twitter: @SwissGator Overview Who? Background Why? Enterprise & Consumer Benefit What? (Blockchain of course) Value Prop
Health Data & Blockchain: The New Sharing Frontier Michael Dillhyon, CCO, Graftworx Twitter: @SwissGator Overview Who? Background Why? Enterprise & Consumer Benefit What? (Blockchain of course) Value Prop
Using Blockchain for Consent and Access to Private and Sensitive Data in the GDPR Environment
 Using Blockchain for Consent and Access to Private and Sensitive Data in the GDPR Environment Gary Leeming, Chief Technology Officer Connected Health Cities, University of Manchester 1 Connected Health
Using Blockchain for Consent and Access to Private and Sensitive Data in the GDPR Environment Gary Leeming, Chief Technology Officer Connected Health Cities, University of Manchester 1 Connected Health
A scalable AI Knowledge Graph Solution for Healthcare (and many other industries) Dr. Jans Aasman
 A scalable AI Knowledge Graph Solution for Healthcare (and many other industries) Dr. Jans Aasman About Franz Inc. Privately held, Self-funded, Profitable since 1984 Headquartered: Oakland, CA Flagship
A scalable AI Knowledge Graph Solution for Healthcare (and many other industries) Dr. Jans Aasman About Franz Inc. Privately held, Self-funded, Profitable since 1984 Headquartered: Oakland, CA Flagship
The Emerging Data Lake IT Strategy
 The Emerging Data Lake IT Strategy An Evolving Approach for Dealing with Big Data & Changing Environments bit.ly/datalake SPEAKERS: Thomas Kelly, Practice Director Cognizant Technology Solutions Sean Martin,
The Emerging Data Lake IT Strategy An Evolving Approach for Dealing with Big Data & Changing Environments bit.ly/datalake SPEAKERS: Thomas Kelly, Practice Director Cognizant Technology Solutions Sean Martin,
On the design of a Blockchain-based system to facilitate Healthcare Data Sharing
 On the design of a Blockchain-based system to facilitate Healthcare Data Sharing Anastasia Theodouli, Stelios Arakliotis, Konstantinos Moschou, Konstantinos Votis, Dimitrios Tzovaras CERTH / ITI Thessaloniki,
On the design of a Blockchain-based system to facilitate Healthcare Data Sharing Anastasia Theodouli, Stelios Arakliotis, Konstantinos Moschou, Konstantinos Votis, Dimitrios Tzovaras CERTH / ITI Thessaloniki,
IEEE 2013 JAVA PROJECTS Contact No: KNOWLEDGE AND DATA ENGINEERING
 IEEE 2013 JAVA PROJECTS www.chennaisunday.com Contact No: 9566137117 KNOWLEDGE AND DATA ENGINEERING (DATA MINING) 1. A Fast Clustering-Based Feature Subset Selection Algorithm for High Dimensional Data
IEEE 2013 JAVA PROJECTS www.chennaisunday.com Contact No: 9566137117 KNOWLEDGE AND DATA ENGINEERING (DATA MINING) 1. A Fast Clustering-Based Feature Subset Selection Algorithm for High Dimensional Data
Powering Knowledge Discovery. Insights from big data with Linguamatics I2E
 Powering Knowledge Discovery Insights from big data with Linguamatics I2E Gain actionable insights from unstructured data The world now generates an overwhelming amount of data, most of it written in natural
Powering Knowledge Discovery Insights from big data with Linguamatics I2E Gain actionable insights from unstructured data The world now generates an overwhelming amount of data, most of it written in natural
The SHARPn phenotyping funnel. Phenotype specific patient cohorts
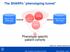 The SHARPn phenotyping funnel Mayo Clinic EHR data QDMs CEMs Intermountain EHR data DRLs Phenotype specific patient cohorts [Welch et al., JBI 2012; 45(4):763-71] 2012 MFMER slide-1 Algorithm Development
The SHARPn phenotyping funnel Mayo Clinic EHR data QDMs CEMs Intermountain EHR data DRLs Phenotype specific patient cohorts [Welch et al., JBI 2012; 45(4):763-71] 2012 MFMER slide-1 Algorithm Development
Reproducible Workflows Biomedical Research. P Berlin, Germany
 Reproducible Workflows Biomedical Research P11 2018 Berlin, Germany Contributors Leslie McIntosh Research Data Alliance, U.S., Executive Director Oya Beyan Aachen University, Germany Anthony Juehne RDA,
Reproducible Workflows Biomedical Research P11 2018 Berlin, Germany Contributors Leslie McIntosh Research Data Alliance, U.S., Executive Director Oya Beyan Aachen University, Germany Anthony Juehne RDA,
Void main Technologies
 SNO TITLE Domain 1. A Hybrid Approach for Detecting Automated Spammers in Twitter Data mining 2. A Key-Policy Attribute-Based Temporary Keyword Search scheme for Secure Storage 3. A Lightweight Secure
SNO TITLE Domain 1. A Hybrid Approach for Detecting Automated Spammers in Twitter Data mining 2. A Key-Policy Attribute-Based Temporary Keyword Search scheme for Secure Storage 3. A Lightweight Secure
Preserving Data Privacy in the IoT World
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY Preserving Data Privacy in the IoT World Thomas Hardjono Alex Sandy Pentland Connection Science & Engineering Massachusetts Institute of Technology July 2016 connection.mit.edu
MASSACHUSETTS INSTITUTE OF TECHNOLOGY Preserving Data Privacy in the IoT World Thomas Hardjono Alex Sandy Pentland Connection Science & Engineering Massachusetts Institute of Technology July 2016 connection.mit.edu
Evolving IoT with Smart Objects
 Evolving IoT with Smart Objects John Soldatos (jsol@ait.gr) Associate Professor Athens Information Technology isprint Workshop, Brussels, September 19th, 2017 Monolithic IoT applications (2005-2010) IoT
Evolving IoT with Smart Objects John Soldatos (jsol@ait.gr) Associate Professor Athens Information Technology isprint Workshop, Brussels, September 19th, 2017 Monolithic IoT applications (2005-2010) IoT
Contractual Approaches to Data Protection in Clinical Research Projects
 Contractual Approaches to Data Protection in Clinical Research Projects EICAR, 24th Annual Conference Nürnberg, October 2016 Dr. jur. Marc Stauch Institute for Legal Informatics Leibniz Universität Hannover
Contractual Approaches to Data Protection in Clinical Research Projects EICAR, 24th Annual Conference Nürnberg, October 2016 Dr. jur. Marc Stauch Institute for Legal Informatics Leibniz Universität Hannover
Workshop 2. > Interoperability <
 Workshop 2 21 / 08 / 2011 > Interoperability < Heiko Zimmermann R&D Engineer, AHI CR Santec Heiko.Zimmermann@tudor.lu Interoperability definition Picture from NCI-Wiki (https://wiki.nci.nih.gov) 2 Interoperability
Workshop 2 21 / 08 / 2011 > Interoperability < Heiko Zimmermann R&D Engineer, AHI CR Santec Heiko.Zimmermann@tudor.lu Interoperability definition Picture from NCI-Wiki (https://wiki.nci.nih.gov) 2 Interoperability
SNOMED CT Implementation Approaches. National Resource Centre for EHR Standards (NRCeS) C-DAC, Pune
 SNOMED CT Implementation Approaches National Resource Centre for EHR Standards (NRCeS) C-DAC, Pune SNOMED CT with no Health Record SNOMED CT is a powerful modern clinical terminology Comprehensive scope
SNOMED CT Implementation Approaches National Resource Centre for EHR Standards (NRCeS) C-DAC, Pune SNOMED CT with no Health Record SNOMED CT is a powerful modern clinical terminology Comprehensive scope
On health data architecture design
 Subhashis Banerjee Computer Science and Engineering IIT Delhi Law Economics Policy Conference, Delhi November 27, 2018 Why do we need it? Electronic Health Records and individual health. Public health
Subhashis Banerjee Computer Science and Engineering IIT Delhi Law Economics Policy Conference, Delhi November 27, 2018 Why do we need it? Electronic Health Records and individual health. Public health
Fair data and open data: differences and consequences
 Fair data and open data: differences and consequences 1. To share or not to share: what is fair? Alex Burdorf, Erasmus MC Rotterdam 2. Data sharing: consequences for informed consent Marie-José Bonthuis,
Fair data and open data: differences and consequences 1. To share or not to share: what is fair? Alex Burdorf, Erasmus MC Rotterdam 2. Data sharing: consequences for informed consent Marie-José Bonthuis,
IBM Cloud Security for the Cloud. Amr Ismail Security Solutions Sales Leader Middle East & Pakistan
 IBM Cloud Security for the Cloud Amr Ismail Security Solutions Sales Leader Middle East & Pakistan Today s Drivers for Cloud Adoption ELASTIC LOWER COST SOLVES SKILLS SHORTAGE RAPID INNOVATION GREATER
IBM Cloud Security for the Cloud Amr Ismail Security Solutions Sales Leader Middle East & Pakistan Today s Drivers for Cloud Adoption ELASTIC LOWER COST SOLVES SKILLS SHORTAGE RAPID INNOVATION GREATER
The NIH Collaboratory Distributed Research Network: A Privacy Protecting Method for Sharing Research Data Sets
 The NIH Collaboratory Distributed Research Network: A Privacy Protecting Method for Sharing Research Data Sets Jeffrey Brown, Lesley Curtis, and Rich Platt June 13, 2014 Previously The NIH Collaboratory:
The NIH Collaboratory Distributed Research Network: A Privacy Protecting Method for Sharing Research Data Sets Jeffrey Brown, Lesley Curtis, and Rich Platt June 13, 2014 Previously The NIH Collaboratory:
Helping you to be GDPR compliant
 Helping you to be GDPR compliant Helping you to be GDPR compliant 01 Privacy Compliance Dashboard Your campaign Privacy Compliance Dashboard is a transparent view where you identify the contact information
Helping you to be GDPR compliant Helping you to be GDPR compliant 01 Privacy Compliance Dashboard Your campaign Privacy Compliance Dashboard is a transparent view where you identify the contact information
SOLUTION ARCHITECTURE AND TECHNICAL OVERVIEW. Decentralized platform for coordination and administration of healthcare and benefits
 SOLUTION ARCHITECTURE AND TECHNICAL OVERVIEW Decentralized platform for coordination and administration of healthcare and benefits ENABLING TECHNOLOGIES Blockchain Distributed ledgers Smart Contracts Relationship
SOLUTION ARCHITECTURE AND TECHNICAL OVERVIEW Decentralized platform for coordination and administration of healthcare and benefits ENABLING TECHNOLOGIES Blockchain Distributed ledgers Smart Contracts Relationship
CIAM: Need for Identity Governance & Assurance. Yash Prakash VP of Products
 CIAM: Need for Identity Governance & Assurance Yash Prakash VP of Products Key Tenets of CIAM Solution Empower consumers, CSRs & administrators Scale to millions of entities, cloud based service Security
CIAM: Need for Identity Governance & Assurance Yash Prakash VP of Products Key Tenets of CIAM Solution Empower consumers, CSRs & administrators Scale to millions of entities, cloud based service Security
IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT)
 Page 1 of 6 IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT) I. Understanding the need for privacy in the IT environment A. Evolving
Page 1 of 6 IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT) I. Understanding the need for privacy in the IT environment A. Evolving
Data Management Glossary
 Data Management Glossary A Access path: The route through a system by which data is found, accessed and retrieved Agile methodology: An approach to software development which takes incremental, iterative
Data Management Glossary A Access path: The route through a system by which data is found, accessed and retrieved Agile methodology: An approach to software development which takes incremental, iterative
Privacy-Preserving. Introduction to. Data Publishing. Concepts and Techniques. Benjamin C. M. Fung, Ke Wang, Chapman & Hall/CRC. S.
 Chapman & Hall/CRC Data Mining and Knowledge Discovery Series Introduction to Privacy-Preserving Data Publishing Concepts and Techniques Benjamin C M Fung, Ke Wang, Ada Wai-Chee Fu, and Philip S Yu CRC
Chapman & Hall/CRC Data Mining and Knowledge Discovery Series Introduction to Privacy-Preserving Data Publishing Concepts and Techniques Benjamin C M Fung, Ke Wang, Ada Wai-Chee Fu, and Philip S Yu CRC
Privacy Challenges in Big Data and Industry 4.0
 Privacy Challenges in Big Data and Industry 4.0 Jiannong Cao Internet & Mobile Computing Lab Department of Computing Hong Kong Polytechnic University Email: csjcao@comp.polyu.edu.hk http://www.comp.polyu.edu.hk/~csjcao/
Privacy Challenges in Big Data and Industry 4.0 Jiannong Cao Internet & Mobile Computing Lab Department of Computing Hong Kong Polytechnic University Email: csjcao@comp.polyu.edu.hk http://www.comp.polyu.edu.hk/~csjcao/
Connected Medical Devices
 Connected Medical Devices How to Reduce Risks Inherent in an Internet of Things that Can Help or Harm Laura Clark Fey, Esq., Principal, Fey LLC Agenda Overview of the Internet of Things for Healthcare
Connected Medical Devices How to Reduce Risks Inherent in an Internet of Things that Can Help or Harm Laura Clark Fey, Esq., Principal, Fey LLC Agenda Overview of the Internet of Things for Healthcare
Partition Based Perturbation for Privacy Preserving Distributed Data Mining
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 17, No 2 Sofia 2017 Print ISSN: 1311-9702; Online ISSN: 1314-4081 DOI: 10.1515/cait-2017-0015 Partition Based Perturbation
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 17, No 2 Sofia 2017 Print ISSN: 1311-9702; Online ISSN: 1314-4081 DOI: 10.1515/cait-2017-0015 Partition Based Perturbation
Examples for best practices in ehealth
 Examples for best practices in ehealth Karl P. Pfeiffer *) Rector / Managing Director FH JOANNEUM University of Applied Sciences Graz, Austria Brussels 20170315 *) ehealth coordinator for the province
Examples for best practices in ehealth Karl P. Pfeiffer *) Rector / Managing Director FH JOANNEUM University of Applied Sciences Graz, Austria Brussels 20170315 *) ehealth coordinator for the province
Request for Information Technical Response White Paper for Joint Operational Medicine Information Systems (JOMIS)
 Request for Information Technical Response White Paper for Joint Operational Medicine Information Systems (JOMIS) Ensuring Continuity of Data 5 May 2017 Prepared by: Northrop Grumman Systems Corporation
Request for Information Technical Response White Paper for Joint Operational Medicine Information Systems (JOMIS) Ensuring Continuity of Data 5 May 2017 Prepared by: Northrop Grumman Systems Corporation
Research Incentive Fund (RIF) Grant Proposal APPLICATION FORM
 Research Incentive Fund (RIF) Grant Proposal APPLICATION FORM Please read the RIF Faculty Handbook before completing this application, or visit the Research Website. All fields will expand as needed. Submit
Research Incentive Fund (RIF) Grant Proposal APPLICATION FORM Please read the RIF Faculty Handbook before completing this application, or visit the Research Website. All fields will expand as needed. Submit
IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT)
 Page 1 of 6 IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT) I. Understanding the need for privacy in the IT environment A. Evolving
Page 1 of 6 IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT) I. Understanding the need for privacy in the IT environment A. Evolving
NPP & Blockchain Have you thought about the data? Ken Krupa, CTO, MarkLogic
 NPP & Blockchain Have you thought about the data? Ken Krupa, CTO, MarkLogic Hello SLIDE: 2 14 COPYRIGHT November 2017 MARKLOGIC CORPORATION. ALL RIGHTS RESERVED. A QUICK LOOK New Payments Platform Open
NPP & Blockchain Have you thought about the data? Ken Krupa, CTO, MarkLogic Hello SLIDE: 2 14 COPYRIGHT November 2017 MARKLOGIC CORPORATION. ALL RIGHTS RESERVED. A QUICK LOOK New Payments Platform Open
Privacy-Preserving Machine Learning
 Privacy-Preserving Machine Learning CS 760: Machine Learning Spring 2018 Mark Craven and David Page www.biostat.wisc.edu/~craven/cs760 1 Goals for the Lecture You should understand the following concepts:
Privacy-Preserving Machine Learning CS 760: Machine Learning Spring 2018 Mark Craven and David Page www.biostat.wisc.edu/~craven/cs760 1 Goals for the Lecture You should understand the following concepts:
Terminology Harmonization
 Terminology Harmonization Rob McClure, MD; Lisa Anderson, MSN, RN-BC; Angie Glotstein, BSN, RN November 14-15, 2018 Washington, DC Table of contents OVERVIEW OF CODE SYSTEMS AND TERMINOLOGY TOOLS USING
Terminology Harmonization Rob McClure, MD; Lisa Anderson, MSN, RN-BC; Angie Glotstein, BSN, RN November 14-15, 2018 Washington, DC Table of contents OVERVIEW OF CODE SYSTEMS AND TERMINOLOGY TOOLS USING
Juliusz Pukacki OGF25 - Grid technologies in e-health Catania, 2-6 March 2009
 Grid Technologies for Cancer Research in the ACGT Project Juliusz Pukacki (pukacki@man.poznan.pl) OGF25 - Grid technologies in e-health Catania, 2-6 March 2009 Outline ACGT project ACGT architecture Layers
Grid Technologies for Cancer Research in the ACGT Project Juliusz Pukacki (pukacki@man.poznan.pl) OGF25 - Grid technologies in e-health Catania, 2-6 March 2009 Outline ACGT project ACGT architecture Layers
Towards an integrated regulation platform in Luxembourg. Information Security Education Day th of april
 Towards an integrated regulation platform in Luxembourg Information Security Education Day 2017-28 th of april Context A complex and inter-connected digital ecosystem contributing to all sectors A set
Towards an integrated regulation platform in Luxembourg Information Security Education Day 2017-28 th of april Context A complex and inter-connected digital ecosystem contributing to all sectors A set
From IHE Audit Trails to XES Event Logs Facilitating Process Mining
 40 Digital Healthcare Empowering Europeans R. Cornet et al. (Eds.) 2015 European Federation for Medical Informatics (EFMI). This article is published online with Open Access by IOS Press and distributed
40 Digital Healthcare Empowering Europeans R. Cornet et al. (Eds.) 2015 European Federation for Medical Informatics (EFMI). This article is published online with Open Access by IOS Press and distributed
CA ERwin Data Modeler s Role in the Relational Cloud. Nuccio Piscopo.
 CA ERwin Data Modeler s Role in the Relational Cloud Nuccio Piscopo Table of Contents Abstract.....3 Introduction........3 Daas requirements through CA ERwin Data Modeler..3 CA ERwin in the Relational
CA ERwin Data Modeler s Role in the Relational Cloud Nuccio Piscopo Table of Contents Abstract.....3 Introduction........3 Daas requirements through CA ERwin Data Modeler..3 CA ERwin in the Relational
Privacy Preserving Data Mining: An approach to safely share and use sensible medical data
 Privacy Preserving Data Mining: An approach to safely share and use sensible medical data Gerhard Kranner, Viscovery Biomax Symposium, June 24 th, 2016, Munich www.viscovery.net Privacy protection vs knowledge
Privacy Preserving Data Mining: An approach to safely share and use sensible medical data Gerhard Kranner, Viscovery Biomax Symposium, June 24 th, 2016, Munich www.viscovery.net Privacy protection vs knowledge
THE NEW EU DATA PROTECTION REGULATION: WHAT IS IT AND WHAT DO WE NEED TO DO? KALLIOPI SPYRIDAKI CHIEF PRIVACY STRATEGIST, EUROPE
 THE NEW EU DATA PROTECTION REGULATION: WHAT IS IT AND WHAT DO WE NEED TO DO? KALLIOPI SPYRIDAKI CHIEF PRIVACY STRATEGIST, EUROPE EU DATA PROTECTION REGULATION Kalliopi Spyridaki Chief Privacy Strategist,
THE NEW EU DATA PROTECTION REGULATION: WHAT IS IT AND WHAT DO WE NEED TO DO? KALLIOPI SPYRIDAKI CHIEF PRIVACY STRATEGIST, EUROPE EU DATA PROTECTION REGULATION Kalliopi Spyridaki Chief Privacy Strategist,
Cyber-Physical Chain (CPChain) Light Paper
 Cyber-Physical Chain (CPChain) Light Paper Decentralized Infrastructure for Next Generation Internet of Things Cyber-Physical Chain (CPChain) Team December 10, 2017 Abstract Deeply integrating blockchain
Cyber-Physical Chain (CPChain) Light Paper Decentralized Infrastructure for Next Generation Internet of Things Cyber-Physical Chain (CPChain) Team December 10, 2017 Abstract Deeply integrating blockchain
International Journal of Advance Engineering and Research Development
 Scientific Journal of Impact Factor (SJIF): 5.71 e-issn (O): 2348-4470 p-issn (P): 2348-6406 International Journal of Advance Engineering and Research Development Volume 5, Issue 03, March -2018 A SURVEY
Scientific Journal of Impact Factor (SJIF): 5.71 e-issn (O): 2348-4470 p-issn (P): 2348-6406 International Journal of Advance Engineering and Research Development Volume 5, Issue 03, March -2018 A SURVEY
DISCLOSURE PROTECTION OF SENSITIVE ATTRIBUTES IN COLLABORATIVE DATA MINING V. Uma Rani *1, Dr. M. Sreenivasa Rao *2, V. Theresa Vinayasheela *3
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 5 May, 2014 Page No. 5594-5599 DISCLOSURE PROTECTION OF SENSITIVE ATTRIBUTES IN COLLABORATIVE DATA MINING
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 3 Issue 5 May, 2014 Page No. 5594-5599 DISCLOSURE PROTECTION OF SENSITIVE ATTRIBUTES IN COLLABORATIVE DATA MINING
Humboldt-University of Berlin
 Humboldt-University of Berlin Exploiting Link Structure to Discover Meaningful Associations between Controlled Vocabulary Terms exposé of diploma thesis of Andrej Masula 13th October 2008 supervisor: Louiqa
Humboldt-University of Berlin Exploiting Link Structure to Discover Meaningful Associations between Controlled Vocabulary Terms exposé of diploma thesis of Andrej Masula 13th October 2008 supervisor: Louiqa
Mobile and Secure Healthcare: Encrypted Objects and Access Control Delegation
 Mobile and Secure Healthcare: Encrypted Objects and Access Control Delegation PRESENTATION TITLE GOES HERE January 28, 206 SNIA Presenters Alex McDonald Chair - SNIA Cloud Storage NetApp Martin Rosner
Mobile and Secure Healthcare: Encrypted Objects and Access Control Delegation PRESENTATION TITLE GOES HERE January 28, 206 SNIA Presenters Alex McDonald Chair - SNIA Cloud Storage NetApp Martin Rosner
PPKM: Preserving Privacy in Knowledge Management
 PPKM: Preserving Privacy in Knowledge Management N. Maheswari (Corresponding Author) P.G. Department of Computer Science Kongu Arts and Science College, Erode-638-107, Tamil Nadu, India E-mail: mahii_14@yahoo.com
PPKM: Preserving Privacy in Knowledge Management N. Maheswari (Corresponding Author) P.G. Department of Computer Science Kongu Arts and Science College, Erode-638-107, Tamil Nadu, India E-mail: mahii_14@yahoo.com
OpenAIRE. Fostering the social and technical links that enable Open Science in Europe and beyond
 Alessia Bardi and Paolo Manghi, Institute of Information Science and Technologies CNR Katerina Iatropoulou, ATHENA, Iryna Kuchma and Gwen Franck, EIFL Pedro Príncipe, University of Minho OpenAIRE Fostering
Alessia Bardi and Paolo Manghi, Institute of Information Science and Technologies CNR Katerina Iatropoulou, ATHENA, Iryna Kuchma and Gwen Franck, EIFL Pedro Príncipe, University of Minho OpenAIRE Fostering
Towards a Long Term Research Agenda for Digital Library Research. Yannis Ioannidis University of Athens
 Towards a Long Term Research Agenda for Digital Library Research Yannis Ioannidis University of Athens yannis@di.uoa.gr DELOS Project Family Tree BRICKS IP DELOS NoE DELOS NoE DILIGENT IP FP5 FP6 2 DL
Towards a Long Term Research Agenda for Digital Library Research Yannis Ioannidis University of Athens yannis@di.uoa.gr DELOS Project Family Tree BRICKS IP DELOS NoE DELOS NoE DILIGENT IP FP5 FP6 2 DL
Interoperability and Semantics in Use- Application of UML, XMI and MDA to Precision Medicine and Cancer Research
 Interoperability and Semantics in Use- Application of UML, XMI and MDA to Precision Medicine and Cancer Research Ian Fore, D.Phil. Associate Director, Biorepository and Pathology Informatics Senior Program
Interoperability and Semantics in Use- Application of UML, XMI and MDA to Precision Medicine and Cancer Research Ian Fore, D.Phil. Associate Director, Biorepository and Pathology Informatics Senior Program
Martijn Loderus. Merritt Maxim. Principal Analyst Forrester. Director & Global Practice Partner for Advisory Consulting Janrain
 Merritt Maxim Principal Analyst Forrester Martijn Loderus Director & Global Practice Partner for Advisory Consulting Janrain Merritt and Martijn will share insights on Digital Transformation & Drivers
Merritt Maxim Principal Analyst Forrester Martijn Loderus Director & Global Practice Partner for Advisory Consulting Janrain Merritt and Martijn will share insights on Digital Transformation & Drivers
2017 GridGain Systems, Inc. In-Memory Performance Durability of Disk
 In-Memory Performance Durability of Disk Meeting the Challenges of Fast Data in Healthcare with In-Memory Technologies Akmal Chaudhri Technology Evangelist GridGain Agenda Introduction Fast Data in Healthcare
In-Memory Performance Durability of Disk Meeting the Challenges of Fast Data in Healthcare with In-Memory Technologies Akmal Chaudhri Technology Evangelist GridGain Agenda Introduction Fast Data in Healthcare
Developing a national disease registry: the German approach to a rare disease registry
 Developing a national disease registry: the German approach to a rare disease registry T. Hartz @tobgerm University Medical Center Mainz, Germany Institute for Medical Biometry, Epidemiology and Informatics
Developing a national disease registry: the German approach to a rare disease registry T. Hartz @tobgerm University Medical Center Mainz, Germany Institute for Medical Biometry, Epidemiology and Informatics
SHOW ME THE MONEY SOCIETAL CHALLENGE 1 [ ] 2 nd Oct 2017
![SHOW ME THE MONEY SOCIETAL CHALLENGE 1 [ ] 2 nd Oct 2017 SHOW ME THE MONEY SOCIETAL CHALLENGE 1 [ ] 2 nd Oct 2017](/thumbs/74/70479101.jpg) SHOW ME THE MONEY SOCIETAL CHALLENGE 1 [2018-2020] 2 nd Oct 2017 H2020 SC1-eHealth Calls (2018). Agenda Appendix A. Lessons Learned From ESRs. Appendix B. A Quick Guide How To Make A Proposal. Appendix
SHOW ME THE MONEY SOCIETAL CHALLENGE 1 [2018-2020] 2 nd Oct 2017 H2020 SC1-eHealth Calls (2018). Agenda Appendix A. Lessons Learned From ESRs. Appendix B. A Quick Guide How To Make A Proposal. Appendix
Biomedical and Healthcare Applications for Blockchain. Tiffany J. Callahan Computational Bioscience Program Hunter/Kahn Labs
 Biomedical and Healthcare Applications for Blockchain Tiffany J. Callahan Computational Bioscience Program Hunter/Kahn Labs Network Analysis Working Group 01.25.2018 Outline Introduction to bitcoin + blockchain
Biomedical and Healthcare Applications for Blockchain Tiffany J. Callahan Computational Bioscience Program Hunter/Kahn Labs Network Analysis Working Group 01.25.2018 Outline Introduction to bitcoin + blockchain
Birgit Morlion. DG Communications Networks, Content and Technology (DG CONNECT)
 Digital transformation of health and care in the Digital Single Market Harnessing the potential of data to empower citizens and build a healthier society DG Communications Networks, Content and Technology
Digital transformation of health and care in the Digital Single Market Harnessing the potential of data to empower citizens and build a healthier society DG Communications Networks, Content and Technology
TEXT MINING: THE NEXT DATA FRONTIER
 TEXT MINING: THE NEXT DATA FRONTIER An Infrastructural Approach Dr. Petr Knoth CORE (core.ac.uk) Knowledge Media institute, The Open University United Kingdom 2 OpenMinTeD Establish an open and sustainable
TEXT MINING: THE NEXT DATA FRONTIER An Infrastructural Approach Dr. Petr Knoth CORE (core.ac.uk) Knowledge Media institute, The Open University United Kingdom 2 OpenMinTeD Establish an open and sustainable
IEEE-SA Internet of Things - Security & Standards
 IEEE-SA Internet of Things - Security & Standards Srikanth Chandrasekaran IEEE Standards Association MOBILE WORLD CONGRESS, SHANGHAI JUNE 2018 What does the IEEE Standards Association (IEEE-SA) do? Vision:
IEEE-SA Internet of Things - Security & Standards Srikanth Chandrasekaran IEEE Standards Association MOBILE WORLD CONGRESS, SHANGHAI JUNE 2018 What does the IEEE Standards Association (IEEE-SA) do? Vision:
Understanding the workplace of the future. Artificial Intelligence series
 Understanding the workplace of the future Artificial Intelligence series Konica Minolta Inc. 02 Cognitive Hub and the Semantic Platform Within today s digital workplace, there is a growing need for different
Understanding the workplace of the future Artificial Intelligence series Konica Minolta Inc. 02 Cognitive Hub and the Semantic Platform Within today s digital workplace, there is a growing need for different
From Integration to Interoperability: The Role of Public Health Systems in the Emerging World of Health Information Exchange
 From Integration to Interoperability: The Role of Public Health Systems in the Emerging World of Health Information Exchange Noam H. Arzt, PhD American Public Health Association Annual Meeting Session
From Integration to Interoperability: The Role of Public Health Systems in the Emerging World of Health Information Exchange Noam H. Arzt, PhD American Public Health Association Annual Meeting Session
Security Control Methods for Statistical Database
 Security Control Methods for Statistical Database Li Xiong CS573 Data Privacy and Security Statistical Database A statistical database is a database which provides statistics on subsets of records OLAP
Security Control Methods for Statistical Database Li Xiong CS573 Data Privacy and Security Statistical Database A statistical database is a database which provides statistics on subsets of records OLAP
H2020-LEIT-ICT WP European Data Infrastructure ICT-13 Supporting the emergence of data markets and the data economy
 H2020-LEIT-ICT WP2018-2020 European Data Infrastructure ICT-13 Supporting the emergence of data markets and the data economy Kimmo Rossi DG CNECT.G1 Data Policy and Innovation Unit Problem statement Sharing
H2020-LEIT-ICT WP2018-2020 European Data Infrastructure ICT-13 Supporting the emergence of data markets and the data economy Kimmo Rossi DG CNECT.G1 Data Policy and Innovation Unit Problem statement Sharing
GDPR: A technical perspective from Arkivum
 GDPR: A technical perspective from Arkivum Under the GDPR, you have a general obligation to implement technical and organisational measures to show that you have considered and integrated data protection
GDPR: A technical perspective from Arkivum Under the GDPR, you have a general obligation to implement technical and organisational measures to show that you have considered and integrated data protection
A Review on Privacy Preserving Data Mining Approaches
 A Review on Privacy Preserving Data Mining Approaches Anu Thomas Asst.Prof. Computer Science & Engineering Department DJMIT,Mogar,Anand Gujarat Technological University Anu.thomas@djmit.ac.in Jimesh Rana
A Review on Privacy Preserving Data Mining Approaches Anu Thomas Asst.Prof. Computer Science & Engineering Department DJMIT,Mogar,Anand Gujarat Technological University Anu.thomas@djmit.ac.in Jimesh Rana
mhealth & integrated care
 mhealth & integrated care 2nd Shiraz International mhealth Congress February 22th, 23th 2017, Shiraz - Iran Nick Guldemond Associate Professor Integrated Care & Technology Roadmap 1 Healthcare paradigm
mhealth & integrated care 2nd Shiraz International mhealth Congress February 22th, 23th 2017, Shiraz - Iran Nick Guldemond Associate Professor Integrated Care & Technology Roadmap 1 Healthcare paradigm
MAPR DATA GOVERNANCE WITHOUT COMPROMISE
 MAPR TECHNOLOGIES, INC. WHITE PAPER JANUARY 2018 MAPR DATA GOVERNANCE TABLE OF CONTENTS EXECUTIVE SUMMARY 3 BACKGROUND 4 MAPR DATA GOVERNANCE 5 CONCLUSION 7 EXECUTIVE SUMMARY The MapR DataOps Governance
MAPR TECHNOLOGIES, INC. WHITE PAPER JANUARY 2018 MAPR DATA GOVERNANCE TABLE OF CONTENTS EXECUTIVE SUMMARY 3 BACKGROUND 4 MAPR DATA GOVERNANCE 5 CONCLUSION 7 EXECUTIVE SUMMARY The MapR DataOps Governance
ClinVar. Jennifer Lee, PhD, NCBI/NLM/NIH ClinVar
 ClinVar What is ClinVar ClinVar is a freely available, central archive for associating observed variation with supporting clinical and experimental evidence for a wide range of disorders. The database
ClinVar What is ClinVar ClinVar is a freely available, central archive for associating observed variation with supporting clinical and experimental evidence for a wide range of disorders. The database
The NeuroLOG Platform Federating multi-centric neuroscience resources
 Software technologies for integration of process and data in medical imaging The Platform Federating multi-centric neuroscience resources Johan MONTAGNAT Franck MICHEL Vilnius, Apr. 13 th 2011 ANR-06-TLOG-024
Software technologies for integration of process and data in medical imaging The Platform Federating multi-centric neuroscience resources Johan MONTAGNAT Franck MICHEL Vilnius, Apr. 13 th 2011 ANR-06-TLOG-024
SmartData Fabric distributed virtual data, graph data and master data management, analytics and security. Solutions and Key Features Revision 2.
 s and Key Features Revision 2.5 Page 1 of 7 www.whamtech.com (972) 991-5700 info@whamtech.com March 2018 ID SOL1 Automated Data Discovery and Classification (ADDC) Key Feature ID KF01 KF02 KF03 Key Feature
s and Key Features Revision 2.5 Page 1 of 7 www.whamtech.com (972) 991-5700 info@whamtech.com March 2018 ID SOL1 Automated Data Discovery and Classification (ADDC) Key Feature ID KF01 KF02 KF03 Key Feature
Big Data - Security with Privacy
 Big Data - Security with Privacy Elisa Bertino CS Department, Cyber Center, and CERIAS Purdue University Cyber Center Today we have technologies for Acquiring and sensing data Transmitting data Storing,
Big Data - Security with Privacy Elisa Bertino CS Department, Cyber Center, and CERIAS Purdue University Cyber Center Today we have technologies for Acquiring and sensing data Transmitting data Storing,
All of Us Research Program
 An Introduction to the All of Us Research Program October, 2017 @AllofUsResearch #JoinAllofUs Presented on behalf of NIH All of Us by Petra Kaufmann, Director of Office of Rare Diseases Research, NCATS/NIH
An Introduction to the All of Us Research Program October, 2017 @AllofUsResearch #JoinAllofUs Presented on behalf of NIH All of Us by Petra Kaufmann, Director of Office of Rare Diseases Research, NCATS/NIH
In-Memory Technology in Life Sciences
 in Life Sciences Dr. Matthieu-P. Schapranow In-Memory Database Applications in Healthcare 2016 Apr Intelligent Healthcare Networks in the 21 st Century? Hospital Research Center Laboratory Researcher Clinician
in Life Sciences Dr. Matthieu-P. Schapranow In-Memory Database Applications in Healthcare 2016 Apr Intelligent Healthcare Networks in the 21 st Century? Hospital Research Center Laboratory Researcher Clinician
Privacy Preserving Data Publishing: From k-anonymity to Differential Privacy. Xiaokui Xiao Nanyang Technological University
 Privacy Preserving Data Publishing: From k-anonymity to Differential Privacy Xiaokui Xiao Nanyang Technological University Outline Privacy preserving data publishing: What and Why Examples of privacy attacks
Privacy Preserving Data Publishing: From k-anonymity to Differential Privacy Xiaokui Xiao Nanyang Technological University Outline Privacy preserving data publishing: What and Why Examples of privacy attacks
Privacy Preserving Ranked Multi-Keyword Search for Multiple Data Owners in Cloud Computing
 S.NO PROJECT CODE IEEE JAVA PROJECT TITLES DOMAIN 1 NEO1501 A Hybrid Cloud Approach for Secure Authorized Deduplication 2 NEO1502 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud
S.NO PROJECT CODE IEEE JAVA PROJECT TITLES DOMAIN 1 NEO1501 A Hybrid Cloud Approach for Secure Authorized Deduplication 2 NEO1502 A Profit Maximization Scheme with Guaranteed Quality of Service in Cloud
A Machine Learning Approach to Privacy-Preserving Data Mining Using Homomorphic Encryption
 A Machine Learning Approach to Privacy-Preserving Data Mining Using Homomorphic Encryption Seiichi Ozawa Center for Mathematical Data Science Graduate School of Engineering Kobe University 2 What is PPDM?
A Machine Learning Approach to Privacy-Preserving Data Mining Using Homomorphic Encryption Seiichi Ozawa Center for Mathematical Data Science Graduate School of Engineering Kobe University 2 What is PPDM?
Secure Multi-party Computation
 Secure Multi-party Computation What it is, and why you d care Manoj Prabhakaran University of Illinois, Urbana-Champaign SMC SMC SMC conceived more than 30 years back SMC SMC conceived more than 30 years
Secure Multi-party Computation What it is, and why you d care Manoj Prabhakaran University of Illinois, Urbana-Champaign SMC SMC SMC conceived more than 30 years back SMC SMC conceived more than 30 years
national ehealth platform Dr. Marcos DA SILVEIRA
 Challenges to define a national ehealth platform Dr. Marcos DA SILVEIRA marcos.dasilveira@tudor.lu CR SANTEC General view Guidelines Doctor center X Patient center architecture Requirements and constraints
Challenges to define a national ehealth platform Dr. Marcos DA SILVEIRA marcos.dasilveira@tudor.lu CR SANTEC General view Guidelines Doctor center X Patient center architecture Requirements and constraints
The New Healthcare Economy is rising up
 The New Healthcare Economy is rising up February 2017 The ever-rising costs of healthcare are fostering innovative solutions and disruptive business models Cybersecurity concerns come to medical technology
The New Healthcare Economy is rising up February 2017 The ever-rising costs of healthcare are fostering innovative solutions and disruptive business models Cybersecurity concerns come to medical technology
IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT)
 Page 1 of 6 IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT) I. Understanding the need for privacy in the IT environment A. Evolving
Page 1 of 6 IT Privacy Certification Outline of the Body of Knowledge (BOK) for the Certified Information Privacy Technologist (CIPT) I. Understanding the need for privacy in the IT environment A. Evolving
Research Trends in Privacy Preserving in Association Rule Mining (PPARM) On Horizontally Partitioned Database
 204 IJEDR Volume 2, Issue ISSN: 232-9939 Research Trends in Privacy Preserving in Association Rule Mining (PPARM) On Horizontally Partitioned Database Rachit Adhvaryu, 2 Nikunj Domadiya PG Student, 2 Professor
204 IJEDR Volume 2, Issue ISSN: 232-9939 Research Trends in Privacy Preserving in Association Rule Mining (PPARM) On Horizontally Partitioned Database Rachit Adhvaryu, 2 Nikunj Domadiya PG Student, 2 Professor
Privacy and Security Aspects Related to the Use of Big Data Progress of work in the ESS. Pascal Jacques Eurostat Local Security Officer 1
 Privacy and Security Aspects Related to the Use of Big Data Progress of work in the ESS Pascal Jacques Eurostat Local Security Officer 1 Current work on privacy and ethics in Big data Privacy Confidentiality
Privacy and Security Aspects Related to the Use of Big Data Progress of work in the ESS Pascal Jacques Eurostat Local Security Officer 1 Current work on privacy and ethics in Big data Privacy Confidentiality
Page 1. Oracle9i OLAP. Agenda. Mary Rehus Sales Consultant Patrick Larkin Vice President, Oracle Consulting. Oracle Corporation. Business Intelligence
 Oracle9i OLAP A Scalable Web-Base Business Intelligence Platform Mary Rehus Sales Consultant Patrick Larkin Vice President, Oracle Consulting Agenda Business Intelligence Market Oracle9i OLAP Business
Oracle9i OLAP A Scalable Web-Base Business Intelligence Platform Mary Rehus Sales Consultant Patrick Larkin Vice President, Oracle Consulting Agenda Business Intelligence Market Oracle9i OLAP Business
Accumulative Privacy Preserving Data Mining Using Gaussian Noise Data Perturbation at Multi Level Trust
 Accumulative Privacy Preserving Data Mining Using Gaussian Noise Data Perturbation at Multi Level Trust G.Mareeswari 1, V.Anusuya 2 ME, Department of CSE, PSR Engineering College, Sivakasi, Tamilnadu,
Accumulative Privacy Preserving Data Mining Using Gaussian Noise Data Perturbation at Multi Level Trust G.Mareeswari 1, V.Anusuya 2 ME, Department of CSE, PSR Engineering College, Sivakasi, Tamilnadu,
EUDAT - Open Data Services for Research
 EUDAT - Open Data Services for Research Johannes Reetz EUDAT operations Max Planck Computing & Data Centre Science Operations Workshop 2015 ESO, Garching 24-27th November 2015 EUDAT receives funding from
EUDAT - Open Data Services for Research Johannes Reetz EUDAT operations Max Planck Computing & Data Centre Science Operations Workshop 2015 ESO, Garching 24-27th November 2015 EUDAT receives funding from
The NIS Directive and Cybersecurity in
 The NIS Directive and Cybersecurity in ehealth Dr. Athanasios Drougkas Officer in NIS Belgian Hospitals Meeting on Security Brussels 13 th October European Union Agency For Network And Information Security
The NIS Directive and Cybersecurity in ehealth Dr. Athanasios Drougkas Officer in NIS Belgian Hospitals Meeting on Security Brussels 13 th October European Union Agency For Network And Information Security
Privacy Preserving Data Mining. Danushka Bollegala COMP 527
 Privacy Preserving ata Mining anushka Bollegala COMP 527 Privacy Issues ata mining attempts to ind mine) interesting patterns rom large datasets However, some o those patterns might reveal inormation that
Privacy Preserving ata Mining anushka Bollegala COMP 527 Privacy Issues ata mining attempts to ind mine) interesting patterns rom large datasets However, some o those patterns might reveal inormation that
Co-clustering for differentially private synthetic data generation
 Co-clustering for differentially private synthetic data generation Tarek Benkhelif, Françoise Fessant, Fabrice Clérot and Guillaume Raschia January 23, 2018 Orange Labs & LS2N Journée thématique EGC &
Co-clustering for differentially private synthetic data generation Tarek Benkhelif, Françoise Fessant, Fabrice Clérot and Guillaume Raschia January 23, 2018 Orange Labs & LS2N Journée thématique EGC &
CONSOLIDATING RISK MANAGEMENT AND REGULATORY COMPLIANCE APPLICATIONS USING A UNIFIED DATA PLATFORM
 CONSOLIDATING RISK MANAGEMENT AND REGULATORY COMPLIANCE APPLICATIONS USING A UNIFIED PLATFORM Executive Summary Financial institutions have implemented and continue to implement many disparate applications
CONSOLIDATING RISK MANAGEMENT AND REGULATORY COMPLIANCE APPLICATIONS USING A UNIFIED PLATFORM Executive Summary Financial institutions have implemented and continue to implement many disparate applications
BHConsulting. Your trusted cybersecurity partner
 Your trusted cybersecurity partner BH Consulting Securing your business BH Consulting is an award-winning, independent provider of cybersecurity consulting and information security advisory services. Recognised
Your trusted cybersecurity partner BH Consulting Securing your business BH Consulting is an award-winning, independent provider of cybersecurity consulting and information security advisory services. Recognised
