Introduction to Medical Computing
|
|
|
- Monica Mason
- 6 years ago
- Views:
Transcription
1 CS 2125 Introduction to Medical Computing Stephen M. Watt
2 Embedded Software Embedded software is computer software that makes a device perform its function without presenting it as a general purpose computer.
3 Examples o MP3 player o Digital camera o The braking system in a car o GPS navigation device o Flight control o Cable box o DVD player o Printer o Mobile phone o Video game console o Microwave oven o CT imaging device o Blood pressure monitor o Defibrillator o Pacemaker
4 What is in Common Don t think of it as a computer No screen/keyboard/mouse Take input signals from sensors/buttons/etc Gives output signals/actuators/switches/etc Often controls something Real-time response needed Need to be able to turn on/off/reset Reliability is essential
5 Some Resources embsoftwre.pdf
6 Key Ideas Concurrency Real time response Correctness
7 Concurrency Processors, Processes, Threads. Process state. Context switching. Pre-emptive vs non-pre-emptive scheduling.
8 Real-Time Response Real-time response does not just mean fast response. It means the response is predictable and guaranteed to be within certain limits. This means that the worst-case execution time can be proven to always be within the required limit. E.g. anti-lock braking system must control the brakes before the car slides off the road.
9 Consequences of R-T constraints All libraries used in a software system have to have real-time guarantees. Concurrency must be r-t aware, or controllable. Memory management usually done statically.
10 Hard RT vs Soft RT Property Hart RT Soft RT Response time Required Desired Peak-load performance Predictable Degraded Control of pace Environment Computer Safety Often critical Non-critical Size of data Small/medium Any Redunancy type Active Checkpoint-recovery Data integrity Short term Long term Error detection Autonomous User Assisted *Adapted from Real-Time Systems, Kanaka Juvva
11 Real-Time Scheduling *Adapted from Real-Time Systems, Kanaka Juvva
12 Correctness Want correct software No, really.
13 Correctness Really want correct software. Cannot have if (! isasexpected(v1)) { } fprintf(stderr, Error: unexpected value %d\n, v1); exit(exit_failure);
14 How to Achieve Correctness Correctness proofs. Prove: The program computes the right thing. Prove: No variables overflow, no division by zero, etc.
15 Proving Programs Correct Not just a convincing argument. Mathematical proof of some precise statement about the execution and computed quantities. Typically annotate program with assertions Prove that if the input conditions are met, then the assertions are true. Assertions may be pre-conditions, post-conditions or invariants.
16 Proving Programs Correct A change-making algorithm Pre-condition Post-condition * From Essays on Algorithm Analysis, F. D. Lewis
17 Proving Programs Correct Pre-condition: what is true before a block Invariant: what is always true at this point (usually a loop invariant) Post-condition: what is true after a block Some programming langauges (e.g. Eiffel) have native support for these.
18 Inductive Assertions Flow Chart: diagramatic representation of program execution. Basic blocks have predecessors and successors. Assertions can be attached to the arrows. Start with validity of starting precondition as true and all assertions as unknown. Prove assertions based on validity of predecessor assertions.
19 Proving Programs Correct Break program into sequential parts with assertions inserted between. For loops, write a loop invariant that expresses the purpose of the loop. Write it so Inv(n) is true after n iterations of the loop. Show the pre-condition guarantees Inv(0) is true. (Basis step) Show that if Inv(k) is true and the loop test L is true, then Inv(k+1) is true. (Inductive step) Show that after the loop iterates the required number of times, the post-condition of the loop is guaranteed.
20 Proving Programs Correct An Introduction to Proving the Correctness of Programs, Sidney L. Hantler and James C. King, Computing Surveys, Vol 9, No 3, Sept Program correctness: on inductive assertion methods, J.C. King, IEEE Transactions on Software Engineering, Vol SE-6, Issue 5, pp
21
Real-Time Systems 1. Basic Concepts
 Real-Time Systems 1 Basic Concepts Typical RTS 2 Example: Car 3 Mission: Reaching the destination safely. Controlled System: Car. Operating environment: Road conditions and other cars. Controlling System
Real-Time Systems 1 Basic Concepts Typical RTS 2 Example: Car 3 Mission: Reaching the destination safely. Controlled System: Car. Operating environment: Road conditions and other cars. Controlling System
Syllabus Instructors:
 Introduction to Real-Time Systems Embedded Real-Time Software Lecture 1 Syllabus Instructors: Dongsoo S. Kim Office : Room 83345 (031-299-4642) E-mail : dskim@iupui.edu Office Hours: by appointment 2 Syllabus
Introduction to Real-Time Systems Embedded Real-Time Software Lecture 1 Syllabus Instructors: Dongsoo S. Kim Office : Room 83345 (031-299-4642) E-mail : dskim@iupui.edu Office Hours: by appointment 2 Syllabus
EMBEDDED SYSTEMS INTRODUCTION
 EMBEDDED SYSTEMS INTRODUCTION UPDATED TLH Copyright 2000, EXAMPLE PRODUCTS & PROJECTS FOR THE PROJECT SELECT AN EMBEDDED SYSTEM DESIGN IT OR DESCRIBE IT IN DETAIL SEE THE PROJECT REQUIREMENTS SHEET FOR
EMBEDDED SYSTEMS INTRODUCTION UPDATED TLH Copyright 2000, EXAMPLE PRODUCTS & PROJECTS FOR THE PROJECT SELECT AN EMBEDDED SYSTEM DESIGN IT OR DESCRIBE IT IN DETAIL SEE THE PROJECT REQUIREMENTS SHEET FOR
An Annotated Language
 Hoare Logic An Annotated Language State and Semantics Expressions are interpreted as functions from states to the corresponding domain of interpretation Operators have the obvious interpretation Free of
Hoare Logic An Annotated Language State and Semantics Expressions are interpreted as functions from states to the corresponding domain of interpretation Operators have the obvious interpretation Free of
Outline. Introduction. 2 Proof of Correctness. 3 Final Notes. Precondition P 1 : Inputs include
 Outline Computer Science 331 Correctness of Algorithms Mike Jacobson Department of Computer Science University of Calgary Lectures #2-4 1 What is a? Applications 2 Recursive Algorithms 3 Final Notes Additional
Outline Computer Science 331 Correctness of Algorithms Mike Jacobson Department of Computer Science University of Calgary Lectures #2-4 1 What is a? Applications 2 Recursive Algorithms 3 Final Notes Additional
CS 161 Computer Security
 Wagner Spring 2014 CS 161 Computer Security 1/27 Reasoning About Code Often functions make certain assumptions about their arguments, and it is the caller s responsibility to make sure those assumptions
Wagner Spring 2014 CS 161 Computer Security 1/27 Reasoning About Code Often functions make certain assumptions about their arguments, and it is the caller s responsibility to make sure those assumptions
Hardware versus software
 Logic 1 Hardware versus software 2 In hardware such as chip design or architecture, designs are usually proven to be correct using proof tools In software, a program is very rarely proved correct Why?
Logic 1 Hardware versus software 2 In hardware such as chip design or architecture, designs are usually proven to be correct using proof tools In software, a program is very rarely proved correct Why?
Reasoning about programs
 Reasoning about programs Last time Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Reasoning about programs Last time Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Last time. Reasoning about programs. Coming up. Project Final Presentations. This Thursday, Nov 30: 4 th in-class exercise
 Last time Reasoning about programs Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Last time Reasoning about programs Coming up This Thursday, Nov 30: 4 th in-class exercise sign up for group on moodle bring laptop to class Final projects: final project presentations: Tue Dec 12, in
Embedded Software Engineering
 Embedded Software Engineering 3 Unit Course, Spring 2002 EECS Department, UC Berkeley Christoph Kirsch www.eecs.berkeley.edu/~fresco/giotto/course-2002 It s significant $4 billion development effort >
Embedded Software Engineering 3 Unit Course, Spring 2002 EECS Department, UC Berkeley Christoph Kirsch www.eecs.berkeley.edu/~fresco/giotto/course-2002 It s significant $4 billion development effort >
Embedded Systems. Octav Chipara. Thursday, September 13, 12
 Embedded Systems Octav Chipara Caught between two worlds Embedded systems PC world 2 What are embedded systems? Any device that includes a computer (but you don t think of it as a computer) iphone digital
Embedded Systems Octav Chipara Caught between two worlds Embedded systems PC world 2 What are embedded systems? Any device that includes a computer (but you don t think of it as a computer) iphone digital
Local Verification of Global Invariants in
 Local Verification of Global Invariants in 1 Local Verification of Global Invariants in Concurrent Programs Ernie Cohen 1, Michal Moskal 2, Wolfram Schulte 2, Stephan Tobies 1 1 European Microsoft Innovation
Local Verification of Global Invariants in 1 Local Verification of Global Invariants in Concurrent Programs Ernie Cohen 1, Michal Moskal 2, Wolfram Schulte 2, Stephan Tobies 1 1 European Microsoft Innovation
(Refer Slide Time: 00:18)
 Programming, Data Structures and Algorithms Prof. N. S. Narayanaswamy Department of Computer Science and Engineering Indian Institute of Technology, Madras Module 11 Lecture 58 Problem: single source shortest
Programming, Data Structures and Algorithms Prof. N. S. Narayanaswamy Department of Computer Science and Engineering Indian Institute of Technology, Madras Module 11 Lecture 58 Problem: single source shortest
CS158 Section B Exam 1 Key
 CS158 Section B Exam 1 Key Name This is a closed-book exam. The only items not supplied that you are allowed to use are writing implements. You have 50 minutes to complete this exam. The total amount of
CS158 Section B Exam 1 Key Name This is a closed-book exam. The only items not supplied that you are allowed to use are writing implements. You have 50 minutes to complete this exam. The total amount of
HARDWARE SOFTWARE CO-DESIGN
 HARDWARE SOFTWARE CO-DESIGN BITS Pilani Dubai Campus Dr Jagadish Nayak Introduction BITS Pilani Dubai Campus What is this? Hardware/Software codesign investigates the concurrent design of hardware and
HARDWARE SOFTWARE CO-DESIGN BITS Pilani Dubai Campus Dr Jagadish Nayak Introduction BITS Pilani Dubai Campus What is this? Hardware/Software codesign investigates the concurrent design of hardware and
Program Verification. Aarti Gupta
 Program Verification Aarti Gupta 1 Agenda Famous bugs Common bugs Testing (from lecture 6) Reasoning about programs Techniques for program verification 2 Famous Bugs The first bug: A moth in a relay (1945)
Program Verification Aarti Gupta 1 Agenda Famous bugs Common bugs Testing (from lecture 6) Reasoning about programs Techniques for program verification 2 Famous Bugs The first bug: A moth in a relay (1945)
Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122
 Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122 I. Logic 101 In logic, a statement or proposition is a sentence that can either be true or false. A predicate is a sentence in
Foundations, Reasoning About Algorithms, and Design By Contract CMPSC 122 I. Logic 101 In logic, a statement or proposition is a sentence that can either be true or false. A predicate is a sentence in
Lecture 1 Contracts : Principles of Imperative Computation (Fall 2018) Frank Pfenning
 Lecture 1 Contracts 15-122: Principles of Imperative Computation (Fall 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Lecture 1 Contracts 15-122: Principles of Imperative Computation (Fall 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Data & Procedure Reasoning about correctness
 Data & Procedure Reasoning about correctness Although this book focuses primarily on the data side of computation, its study cannot truly be separated from the study of procedure. The next two chapters
Data & Procedure Reasoning about correctness Although this book focuses primarily on the data side of computation, its study cannot truly be separated from the study of procedure. The next two chapters
IN4343 Real-Time Systems
 IN4343 Real-Time Systems Koen Langendoen, TA (TBD) 2017-2018 Delft University of Technology Challenge the future Course outline Real-time systems Lectures theory instruction Exam Reinder Bril TU/e Practicum
IN4343 Real-Time Systems Koen Langendoen, TA (TBD) 2017-2018 Delft University of Technology Challenge the future Course outline Real-time systems Lectures theory instruction Exam Reinder Bril TU/e Practicum
AXIOMS OF AN IMPERATIVE LANGUAGE PARTIAL CORRECTNESS WEAK AND STRONG CONDITIONS. THE AXIOM FOR nop
 AXIOMS OF AN IMPERATIVE LANGUAGE We will use the same language, with the same abstract syntax that we used for operational semantics. However, we will only be concerned with the commands, since the language
AXIOMS OF AN IMPERATIVE LANGUAGE We will use the same language, with the same abstract syntax that we used for operational semantics. However, we will only be concerned with the commands, since the language
CITS5501 Software Testing and Quality Assurance Formal methods
 CITS5501 Software Testing and Quality Assurance Formal methods Unit coordinator: Arran Stewart May 1, 2018 1 / 49 Sources Pressman, R., Software Engineering: A Practitioner s Approach, McGraw-Hill, 2005
CITS5501 Software Testing and Quality Assurance Formal methods Unit coordinator: Arran Stewart May 1, 2018 1 / 49 Sources Pressman, R., Software Engineering: A Practitioner s Approach, McGraw-Hill, 2005
Real-Time Garbage Collection Panel JTRES 2007
 Real-Time Garbage Collection Panel JTRES 2007 Bertrand Delsart, Sun Sean Foley, IBM Kelvin Nilsen, Aonix Sven Robertz, Lund Univ Fridtjof Siebert, aicas Feedback from our customers Is it fast enough to
Real-Time Garbage Collection Panel JTRES 2007 Bertrand Delsart, Sun Sean Foley, IBM Kelvin Nilsen, Aonix Sven Robertz, Lund Univ Fridtjof Siebert, aicas Feedback from our customers Is it fast enough to
Lecture 1 Contracts. 1 A Mysterious Program : Principles of Imperative Computation (Spring 2018) Frank Pfenning
 Lecture 1 Contracts 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Lecture 1 Contracts 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning In these notes we review contracts, which we use to collectively denote function contracts, loop invariants,
Real-time Support in Operating Systems
 Real-time Support in Operating Systems Colin Perkins teaching/2003-2004/rtes4/lecture11.pdf Lecture Outline Overview of the rest of the module Real-time support in operating systems Overview of concepts
Real-time Support in Operating Systems Colin Perkins teaching/2003-2004/rtes4/lecture11.pdf Lecture Outline Overview of the rest of the module Real-time support in operating systems Overview of concepts
ECE 1161/2161 Embedded Computer System Design 2. Introduction. Wei Gao. Spring
 ECE 1161/2161 Embedded Computer System Design 2 Introduction Wei Gao Spring 2018 1 Course Information Class time: 4:30pm 5:45pm TuTh Instructor: Wei Gao, weigao@pitt.edu Office: 1205 Benedum Office hour:
ECE 1161/2161 Embedded Computer System Design 2 Introduction Wei Gao Spring 2018 1 Course Information Class time: 4:30pm 5:45pm TuTh Instructor: Wei Gao, weigao@pitt.edu Office: 1205 Benedum Office hour:
Writing better code Loop invariants Correctness. John Edgar 2
 Writing better code Loop invariants Correctness John Edgar 2 Not all code is equal Correct and reliable code is one of our goals Is a new car correct or reliable? Other characteristics of good code Affordable
Writing better code Loop invariants Correctness John Edgar 2 Not all code is equal Correct and reliable code is one of our goals Is a new car correct or reliable? Other characteristics of good code Affordable
ICS 180 Spring Embedded Systems. Introduction: What are Embedded Systems and what is so interesting about them?
 ICS 180 Spring 1999 Embedded Systems Introduction: What are Embedded Systems and what is so interesting about them? A. Veidenbaum Information and Computer Science University of California, Irvine. Outline
ICS 180 Spring 1999 Embedded Systems Introduction: What are Embedded Systems and what is so interesting about them? A. Veidenbaum Information and Computer Science University of California, Irvine. Outline
Introduction to Real-time Systems. Advanced Operating Systems (M) Lecture 2
 Introduction to Real-time Systems Advanced Operating Systems (M) Lecture 2 Introduction to Real-time Systems Real-time systems deliver services while meeting some timing constraints Not necessarily fast,
Introduction to Real-time Systems Advanced Operating Systems (M) Lecture 2 Introduction to Real-time Systems Real-time systems deliver services while meeting some timing constraints Not necessarily fast,
Algorithms in Systems Engineering ISE 172. Lecture 3. Dr. Ted Ralphs
 Algorithms in Systems Engineering ISE 172 Lecture 3 Dr. Ted Ralphs ISE 172 Lecture 3 1 References for Today s Lecture Required reading Chapter 2 References D.E. Knuth, The Art of Computer Programming,
Algorithms in Systems Engineering ISE 172 Lecture 3 Dr. Ted Ralphs ISE 172 Lecture 3 1 References for Today s Lecture Required reading Chapter 2 References D.E. Knuth, The Art of Computer Programming,
Lesson 13: The Graph of a Linear Equation in Two Variables
 Student Outcomes Students predict the shape of a graph of a linear equation by finding and plotting solutions on a coordinate plane. Students informally explain why the graph of a linear equation is not
Student Outcomes Students predict the shape of a graph of a linear equation by finding and plotting solutions on a coordinate plane. Students informally explain why the graph of a linear equation is not
Lectures 20, 21: Axiomatic Semantics
 Lectures 20, 21: Axiomatic Semantics Polyvios Pratikakis Computer Science Department, University of Crete Type Systems and Static Analysis Based on slides by George Necula Pratikakis (CSD) Axiomatic Semantics
Lectures 20, 21: Axiomatic Semantics Polyvios Pratikakis Computer Science Department, University of Crete Type Systems and Static Analysis Based on slides by George Necula Pratikakis (CSD) Axiomatic Semantics
Specifications and Modeling
 12 Specifications and Modeling Peter Marwedel TU Dortmund, Informatik 12 Springer, 2010 2012 年 10 月 17 日 These slides use Microsoft clip arts. Microsoft copyright restrictions apply. Hypothetical design
12 Specifications and Modeling Peter Marwedel TU Dortmund, Informatik 12 Springer, 2010 2012 年 10 月 17 日 These slides use Microsoft clip arts. Microsoft copyright restrictions apply. Hypothetical design
6. Hoare Logic and Weakest Preconditions
 6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
6. Hoare Logic and Weakest Preconditions Program Verification ETH Zurich, Spring Semester 07 Alexander J. Summers 30 Program Correctness There are many notions of correctness properties for a given program
Correctness of specifications. Correctness. Correctness of specifications (2) Example of a Correctness Proof. Testing versus Correctness Proofs
 CS 390 Lecture 17 Correctness A product is correct if it satisfies its output specifications when operated under permitted conditions Correctness of specifications Incorrect specification for a sort (Figure
CS 390 Lecture 17 Correctness A product is correct if it satisfies its output specifications when operated under permitted conditions Correctness of specifications Incorrect specification for a sort (Figure
CHAPTER 1: REAL TIME COMPUTER CONTROL
 CHAPTER 1 Page 1 ENGG4420 LECTURE 2 September 08 10 12:49 PM CHAPTER 1: REAL TIME COMPUTER CONTROL REFERENCES: G. F. Franklin et al., ``Feedback Control of Dynamic Systems,`` 5th Edition, Pearson, 2006.
CHAPTER 1 Page 1 ENGG4420 LECTURE 2 September 08 10 12:49 PM CHAPTER 1: REAL TIME COMPUTER CONTROL REFERENCES: G. F. Franklin et al., ``Feedback Control of Dynamic Systems,`` 5th Edition, Pearson, 2006.
Classification of RTS. RTS Definitions. RTS Definitions
 Classification of RTS Dr. Hugh Melvin, Dept. of IT, NUI,G 1 Precise definition of RTS? Difficult due to the extent and scope of RTS System where a substantial fraction of the design effort goes into making
Classification of RTS Dr. Hugh Melvin, Dept. of IT, NUI,G 1 Precise definition of RTS? Difficult due to the extent and scope of RTS System where a substantial fraction of the design effort goes into making
Chapter 3 (part 3) Describing Syntax and Semantics
 Chapter 3 (part 3) Describing Syntax and Semantics Chapter 3 Topics Introduction The General Problem of Describing Syntax Formal Methods of Describing Syntax Attribute Grammars Describing the Meanings
Chapter 3 (part 3) Describing Syntax and Semantics Chapter 3 Topics Introduction The General Problem of Describing Syntax Formal Methods of Describing Syntax Attribute Grammars Describing the Meanings
Complexity, Induction, and Recurrence Relations. CSE 373 Help Session 4/7/2016
 Complexity, Induction, and Recurrence Relations CSE 373 Help Session 4/7/2016 Big-O Definition Definition: g(n) is in O( f(n) ) if there exist positive constants c and n0 such that g(n) c f(n) for all
Complexity, Induction, and Recurrence Relations CSE 373 Help Session 4/7/2016 Big-O Definition Definition: g(n) is in O( f(n) ) if there exist positive constants c and n0 such that g(n) c f(n) for all
Operating Systems. Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) alphapeeler.sf.net/pubkeys/pkey.htm
 Operating Systems Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) armahmood786@yahoo.com alphasecure@gmail.com alphapeeler.sf.net/pubkeys/pkey.htm http://alphapeeler.sourceforge.net pk.linkedin.com/in/armahmood
Operating Systems Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) armahmood786@yahoo.com alphasecure@gmail.com alphapeeler.sf.net/pubkeys/pkey.htm http://alphapeeler.sourceforge.net pk.linkedin.com/in/armahmood
Verification of Parameterized Concurrent Programs By Modular Reasoning about Data and Control
 Verification of Parameterized Concurrent Programs By Modular Reasoning about Data and Control Zachary Kincaid Azadeh Farzan University of Toronto January 18, 2013 Z. Kincaid (U. Toronto) Modular Reasoning
Verification of Parameterized Concurrent Programs By Modular Reasoning about Data and Control Zachary Kincaid Azadeh Farzan University of Toronto January 18, 2013 Z. Kincaid (U. Toronto) Modular Reasoning
More Complicated Recursion CMPSC 122
 More Complicated Recursion CMPSC 122 Now that we've gotten a taste of recursion, we'll look at several more examples of recursion that are special in their own way. I. Example with More Involved Arithmetic
More Complicated Recursion CMPSC 122 Now that we've gotten a taste of recursion, we'll look at several more examples of recursion that are special in their own way. I. Example with More Involved Arithmetic
Spark verification features
 Spark verification features Paul Jackson School of Informatics University of Edinburgh Formal Verification Spring 2018 Adding specification information to programs Verification concerns checking whether
Spark verification features Paul Jackson School of Informatics University of Edinburgh Formal Verification Spring 2018 Adding specification information to programs Verification concerns checking whether
4/6/2011. Informally, scheduling is. Informally, scheduling is. More precisely, Periodic and Aperiodic. Periodic Task. Periodic Task (Contd.
 So far in CS4271 Functionality analysis Modeling, Model Checking Timing Analysis Software level WCET analysis System level Scheduling methods Today! erformance Validation Systems CS 4271 Lecture 10 Abhik
So far in CS4271 Functionality analysis Modeling, Model Checking Timing Analysis Software level WCET analysis System level Scheduling methods Today! erformance Validation Systems CS 4271 Lecture 10 Abhik
Lecture 10 Design by Contract
 CS 5959 Writing Solid Code Fall 2015 Nov-23 Lecture 10 Design by Contract Zvonimir Rakamarić University of Utah Design by Contract Also called assume-guarantee reasoning Developers annotate software components
CS 5959 Writing Solid Code Fall 2015 Nov-23 Lecture 10 Design by Contract Zvonimir Rakamarić University of Utah Design by Contract Also called assume-guarantee reasoning Developers annotate software components
Lecture 5 - Axiomatic semantics
 Program Verification March 2014 Lecture 5 - Axiomatic semantics Lecturer: Noam Rinetzky Scribes by: Nir Hemed 1.1 Axiomatic semantics The development of the theory is contributed to Robert Floyd, C.A.R
Program Verification March 2014 Lecture 5 - Axiomatic semantics Lecturer: Noam Rinetzky Scribes by: Nir Hemed 1.1 Axiomatic semantics The development of the theory is contributed to Robert Floyd, C.A.R
Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]:
![Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]: Analyze the obvious algorithm, 5 points Here is the most obvious algorithm for this problem: (LastLargerElement[A[1..n]:](/thumbs/90/104324109.jpg) CSE 101 Homework 1 Background (Order and Recurrence Relations), correctness proofs, time analysis, and speeding up algorithms with restructuring, preprocessing and data structures. Due Thursday, April
CSE 101 Homework 1 Background (Order and Recurrence Relations), correctness proofs, time analysis, and speeding up algorithms with restructuring, preprocessing and data structures. Due Thursday, April
Lecture Notes on Contracts
 Lecture Notes on Contracts 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 30, 2012 1 Introduction For an overview the course goals and the mechanics and schedule of the course,
Lecture Notes on Contracts 15-122: Principles of Imperative Computation Frank Pfenning Lecture 2 August 30, 2012 1 Introduction For an overview the course goals and the mechanics and schedule of the course,
Overview. Rationale Division of labour between script and C++ Choice of language(s) Interfacing to C++ Performance, memory
 SCRIPTING Overview Rationale Division of labour between script and C++ Choice of language(s) Interfacing to C++ Reflection Bindings Serialization Performance, memory Rationale C++ isn't the best choice
SCRIPTING Overview Rationale Division of labour between script and C++ Choice of language(s) Interfacing to C++ Reflection Bindings Serialization Performance, memory Rationale C++ isn't the best choice
RE for Embedded Systems - Part 1
 REQUIREMENTS ENGINEERING LECTURE 2017/2018 Dr. Jörg Dörr RE for Embedded Systems - Part 1 Fraunhofer IESE Lecture Outline Embedded systems and their characteristics Requirements specifications (for embedded
REQUIREMENTS ENGINEERING LECTURE 2017/2018 Dr. Jörg Dörr RE for Embedded Systems - Part 1 Fraunhofer IESE Lecture Outline Embedded systems and their characteristics Requirements specifications (for embedded
introduction to Programming in C Department of Computer Science and Engineering Lecture No. #40 Recursion Linear Recursion
 introduction to Programming in C Department of Computer Science and Engineering Lecture No. #40 Recursion Linear Recursion Today s video will talk about an important concept in computer science which is
introduction to Programming in C Department of Computer Science and Engineering Lecture No. #40 Recursion Linear Recursion Today s video will talk about an important concept in computer science which is
CS Lecture 19: Loop invariants
 CS 1110 Lecture 19: Loop invariants Announcements Prelim 2 conflicts Today (April 2) is two weeks before the prelim, and the deadline for submitting prelim conflicts. Instructor travel This week and the
CS 1110 Lecture 19: Loop invariants Announcements Prelim 2 conflicts Today (April 2) is two weeks before the prelim, and the deadline for submitting prelim conflicts. Instructor travel This week and the
n Specifying what each method does q Specify it in a comment before method's header n Precondition q Caller obligation n Postcondition
 Programming as a contract Assertions, pre/postconditions and invariants Assertions: Section 4.2 in Savitch (p. 239) Loop invariants: Section 4.5 in Rosen Specifying what each method does q Specify it in
Programming as a contract Assertions, pre/postconditions and invariants Assertions: Section 4.2 in Savitch (p. 239) Loop invariants: Section 4.5 in Rosen Specifying what each method does q Specify it in
Default arguments, documentation
 , documentation Comp Sci 1570 Introduction to C++ Outline 1 2 to functions A default parameter (also called an optional parameter or a default argument) is a function parameter that has a default value
, documentation Comp Sci 1570 Introduction to C++ Outline 1 2 to functions A default parameter (also called an optional parameter or a default argument) is a function parameter that has a default value
Safety SPL/2010 SPL/20 1
 Safety 1 system designing for concurrent execution environments system: collection of objects and their interactions system properties: Safety - nothing bad ever happens Liveness - anything ever happens
Safety 1 system designing for concurrent execution environments system: collection of objects and their interactions system properties: Safety - nothing bad ever happens Liveness - anything ever happens
Memory Safety (cont d) Software Security
 Memory Safety (cont d) Software Security CS 161: Computer Security Prof. Raluca Ada Popa January 17, 2016 Some slides credit to David Wagner and Nick Weaver Announcements Discussion sections and office
Memory Safety (cont d) Software Security CS 161: Computer Security Prof. Raluca Ada Popa January 17, 2016 Some slides credit to David Wagner and Nick Weaver Announcements Discussion sections and office
Softwaretechnik. Program verification. Albert-Ludwigs-Universität Freiburg. June 28, Softwaretechnik June 28, / 24
 Softwaretechnik Program verification Albert-Ludwigs-Universität Freiburg June 28, 2012 Softwaretechnik June 28, 2012 1 / 24 Road Map Program verification Automatic program verification Programs with loops
Softwaretechnik Program verification Albert-Ludwigs-Universität Freiburg June 28, 2012 Softwaretechnik June 28, 2012 1 / 24 Road Map Program verification Automatic program verification Programs with loops
SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION
 CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Alessandro Artale UniBZ - http://www.inf.unibz.it/ artale/ SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All
CHAPTER 5 SEQUENCES, MATHEMATICAL INDUCTION, AND RECURSION Alessandro Artale UniBZ - http://www.inf.unibz.it/ artale/ SECTION 5.5 Application: Correctness of Algorithms Copyright Cengage Learning. All
Softwaretechnik. Program verification. Software Engineering Albert-Ludwigs-University Freiburg. June 30, 2011
 Softwaretechnik Program verification Software Engineering Albert-Ludwigs-University Freiburg June 30, 2011 (Software Engineering) Softwaretechnik June 30, 2011 1 / 28 Road Map Program verification Automatic
Softwaretechnik Program verification Software Engineering Albert-Ludwigs-University Freiburg June 30, 2011 (Software Engineering) Softwaretechnik June 30, 2011 1 / 28 Road Map Program verification Automatic
CS510 \ Lecture Ariel Stolerman
 CS510 \ Lecture02 2012-10-03 1 Ariel Stolerman Midterm Evan will email about that after the lecture, at least 2 lectures from now. The exam will be given in a regular PDF (not an online form). We will
CS510 \ Lecture02 2012-10-03 1 Ariel Stolerman Midterm Evan will email about that after the lecture, at least 2 lectures from now. The exam will be given in a regular PDF (not an online form). We will
Lecture Notes on Linear Search
 Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 28, 2014 1 Introduction One of the fundamental and recurring problems in computer science is
Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 28, 2014 1 Introduction One of the fundamental and recurring problems in computer science is
Backward Reasoning: Rule for Assignment. Backward Reasoning: Rule for Sequence. Simple Example. Hoare Logic, continued Reasoning About Loops
 Backward Reasoning: Rule for Assignment Hoare Logic, continued Reasoning About Loops { wp( x=expression,q) x = expression; { Q Rule: the weakest precondition wp( x=expression,q) is Q with all occurrences
Backward Reasoning: Rule for Assignment Hoare Logic, continued Reasoning About Loops { wp( x=expression,q) x = expression; { Q Rule: the weakest precondition wp( x=expression,q) is Q with all occurrences
Lecture 4 Searching Arrays
 Lecture 4 Searching Arrays 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning One of the fundamental and recurring problems in computer science is to find elements in collections,
Lecture 4 Searching Arrays 15-122: Principles of Imperative Computation (Spring 2018) Frank Pfenning One of the fundamental and recurring problems in computer science is to find elements in collections,
Software Security: Vulnerability Analysis
 Computer Security Course. Software Security: Vulnerability Analysis Program Verification Program Verification How to prove a program free of buffer overflows? Precondition Postcondition Loop invariants
Computer Security Course. Software Security: Vulnerability Analysis Program Verification Program Verification How to prove a program free of buffer overflows? Precondition Postcondition Loop invariants
PLC Fundamentals. Module 1: Introduction to PLC. Academic Services Unit PREPARED BY. August 2011
 PLC Fundamentals PREPARED BY Academic Services Unit August 2011 Applied Technology High Schools, 2011 ATE1212 PLC Fundamentals Module Objectives Upon successful completion of this module, students will
PLC Fundamentals PREPARED BY Academic Services Unit August 2011 Applied Technology High Schools, 2011 ATE1212 PLC Fundamentals Module Objectives Upon successful completion of this module, students will
Overview. Rationale Division of labour between script and C++ Choice of language(s) Interfacing to C++
 Scripting 1 Overview Rationale Division of labour between script and C++ Choice of language(s) Interfacing to C++ Rationale C++ isn't the best choice for all problems Complicated feature set, syntax Low-level,
Scripting 1 Overview Rationale Division of labour between script and C++ Choice of language(s) Interfacing to C++ Rationale C++ isn't the best choice for all problems Complicated feature set, syntax Low-level,
Real-Time Systems and their Programming Languages
 Real-Time Systems and their Programming Languages Prerequisites Basic understanding of Ada and C Basic understanding of computer architectures. Basic understanding of Operating Systems Course Aims: Understanding
Real-Time Systems and their Programming Languages Prerequisites Basic understanding of Ada and C Basic understanding of computer architectures. Basic understanding of Operating Systems Course Aims: Understanding
8051 Microcontroller memory Organization and its Applications
 8051 Microcontroller memory Organization and its Applications Memory mapping in 8051 ROM memory map in 8051 family 0000H 4k 0000H 8k 0000H 32k 0FFFH DS5000-32 8051 1FFFH 8752 7FFFH from Atmel Corporation
8051 Microcontroller memory Organization and its Applications Memory mapping in 8051 ROM memory map in 8051 family 0000H 4k 0000H 8k 0000H 32k 0FFFH DS5000-32 8051 1FFFH 8752 7FFFH from Atmel Corporation
Consumer Vehicle Interface Design and Assessment. Paul Green
 Consumer Vehicle Interface Design and Assessment Paul Green Research Professor UMTRI Driver Interface Group Adjunct Associate Professor Industrial & Operations Engrg. 5th Annual University of Michigan
Consumer Vehicle Interface Design and Assessment Paul Green Research Professor UMTRI Driver Interface Group Adjunct Associate Professor Industrial & Operations Engrg. 5th Annual University of Michigan
Teaching KS3 Computing. Session 7 Theory: How computers work Practical: Building on programming skills
 Teaching KS3 Computing Session 7 Theory: How computers work Practical: Building on programming skills Today s session 5:00 6:00 How computers work 6.00 7.00 Building on programming skills From the national
Teaching KS3 Computing Session 7 Theory: How computers work Practical: Building on programming skills Today s session 5:00 6:00 How computers work 6.00 7.00 Building on programming skills From the national
Lecture 1: Overview
 15-150 Lecture 1: Overview Lecture by Stefan Muller May 21, 2018 Welcome to 15-150! Today s lecture was an overview that showed the highlights of everything you re learning this semester, which also meant
15-150 Lecture 1: Overview Lecture by Stefan Muller May 21, 2018 Welcome to 15-150! Today s lecture was an overview that showed the highlights of everything you re learning this semester, which also meant
Outline. Petri nets. Introduction Examples Properties Analysis techniques. 1 EE249Fall04
 Outline Petri nets Introduction Examples Properties Analysis techniques 1 Petri Nets (PNs) Model introduced by C.A. Petri in 1962 Ph.D. Thesis: Communication with Automata Applications: distributed computing,
Outline Petri nets Introduction Examples Properties Analysis techniques 1 Petri Nets (PNs) Model introduced by C.A. Petri in 1962 Ph.D. Thesis: Communication with Automata Applications: distributed computing,
Half full or half empty? William Gropp Mathematics and Computer Science
 Half full or half empty? William Gropp Mathematics and Computer Science www.mcs.anl.gov/~gropp MPI on Multicore Processors Work of Darius Buntinas and Guillaume Mercier 340 ns MPI ping/pong latency More
Half full or half empty? William Gropp Mathematics and Computer Science www.mcs.anl.gov/~gropp MPI on Multicore Processors Work of Darius Buntinas and Guillaume Mercier 340 ns MPI ping/pong latency More
CS 101 Randomness. Lecture 21
 CS 101 Randomness Lecture 21 1 Randomness In most programming languages (Processing included) there are ways to generate random numbers 2 Randomness In most programming languages (Processing included)
CS 101 Randomness Lecture 21 1 Randomness In most programming languages (Processing included) there are ways to generate random numbers 2 Randomness In most programming languages (Processing included)
Introduction to Concurrency (Processes, Threads, Interrupts, etc.)
 Introduction to Concurrency (Processes, Threads, Interrupts, etc.) CS-3013 Operating Systems Hugh C. Lauer (Slides include materials from Slides include materials from Modern Operating Systems, 3 rd ed.,
Introduction to Concurrency (Processes, Threads, Interrupts, etc.) CS-3013 Operating Systems Hugh C. Lauer (Slides include materials from Slides include materials from Modern Operating Systems, 3 rd ed.,
Real Time Operating Systems and Middleware
 Real Time Operating Systems and Middleware Introduction to Real-Time Systems Luca Abeni abeni@disi.unitn.it Credits: Luigi Palopoli, Giuseppe Lipari, Marco Di Natale, and Giorgio Buttazzo Scuola Superiore
Real Time Operating Systems and Middleware Introduction to Real-Time Systems Luca Abeni abeni@disi.unitn.it Credits: Luigi Palopoli, Giuseppe Lipari, Marco Di Natale, and Giorgio Buttazzo Scuola Superiore
e-pg Pathshala Subject : Computer Science Paper: Embedded System Module: Microcontrollers and Embedded Processors Module No: CS/ES/2 Quadrant 1 e-text
 e-pg Pathshala Subject : Computer Science Paper: Embedded System Module: Microcontrollers and Embedded Processors Module No: CS/ES/2 Quadrant 1 e-text In this module, microcontrollers and embedded processors
e-pg Pathshala Subject : Computer Science Paper: Embedded System Module: Microcontrollers and Embedded Processors Module No: CS/ES/2 Quadrant 1 e-text In this module, microcontrollers and embedded processors
Hoare Logic and Model Checking
 Hoare Logic and Model Checking Kasper Svendsen University of Cambridge CST Part II 2016/17 Acknowledgement: slides heavily based on previous versions by Mike Gordon and Alan Mycroft Introduction In the
Hoare Logic and Model Checking Kasper Svendsen University of Cambridge CST Part II 2016/17 Acknowledgement: slides heavily based on previous versions by Mike Gordon and Alan Mycroft Introduction In the
Algorithms 1 / 24. Algorithms Sequential Search
 Algorithm: a well-ordered collection of unambiguous and effectively computable operations, that, when executed, produces a result in a finite amount of time. 1 / 24 Algorithm: a well-ordered collection
Algorithm: a well-ordered collection of unambiguous and effectively computable operations, that, when executed, produces a result in a finite amount of time. 1 / 24 Algorithm: a well-ordered collection
PROGRAMMING IN HASKELL. CS Chapter 6 - Recursive Functions
 PROGRAMMING IN HASKELL CS-205 - Chapter 6 - Recursive Functions 0 Introduction As we have seen, many functions can naturally be defined in terms of other functions. factorial :: Int Int factorial n product
PROGRAMMING IN HASKELL CS-205 - Chapter 6 - Recursive Functions 0 Introduction As we have seen, many functions can naturally be defined in terms of other functions. factorial :: Int Int factorial n product
Review of distracted driving factors. George Yannis, Associate Professor, NTUA
 Review of distracted driving factors George Yannis, Associate Professor, NTUA www.nrso.ntua.gr/geyannis Research Objectives Presentation Structure Research Objectives To provide a comprehensive picture
Review of distracted driving factors George Yannis, Associate Professor, NTUA www.nrso.ntua.gr/geyannis Research Objectives Presentation Structure Research Objectives To provide a comprehensive picture
To illustrate what is intended the following are three write ups by students. Diagonalization
 General guidelines: You may work with other people, as long as you write up your solution in your own words and understand everything you turn in. Make sure to justify your answers they should be clear
General guidelines: You may work with other people, as long as you write up your solution in your own words and understand everything you turn in. Make sure to justify your answers they should be clear
P1 Engineering Computation
 1EC 2001 1 / 1 P1 Engineering Computation David Murray david.murray@eng.ox.ac.uk www.robots.ox.ac.uk/ dwm/courses/1ec Hilary 2001 1EC 2001 2 / 1 Algorithms: Design, Constructs and Correctness 1EC 2001
1EC 2001 1 / 1 P1 Engineering Computation David Murray david.murray@eng.ox.ac.uk www.robots.ox.ac.uk/ dwm/courses/1ec Hilary 2001 1EC 2001 2 / 1 Algorithms: Design, Constructs and Correctness 1EC 2001
Learning Outcomes. Scheduling. Is scheduling important? What is Scheduling? Application Behaviour. Is scheduling important?
 Learning Outcomes Scheduling Understand the role of the scheduler, and how its behaviour influences the performance of the system. Know the difference between I/O-bound and CPU-bound tasks, and how they
Learning Outcomes Scheduling Understand the role of the scheduler, and how its behaviour influences the performance of the system. Know the difference between I/O-bound and CPU-bound tasks, and how they
Hoare Logic and Model Checking. A proof system for Separation logic. Introduction. Separation Logic
 Introduction Hoare Logic and Model Checking In the previous lecture we saw the informal concepts that Separation Logic is based on. Kasper Svendsen University of Cambridge CST Part II 2016/17 This lecture
Introduction Hoare Logic and Model Checking In the previous lecture we saw the informal concepts that Separation Logic is based on. Kasper Svendsen University of Cambridge CST Part II 2016/17 This lecture
Unit #3: Recursion, Induction, and Loop Invariants
 Unit #3: Recursion, Induction, and Loop Invariants CPSC 221: Basic Algorithms and Data Structures Jan Manuch 2017S1: May June 2017 Unit Outline Thinking Recursively Recursion Examples Analyzing Recursion:
Unit #3: Recursion, Induction, and Loop Invariants CPSC 221: Basic Algorithms and Data Structures Jan Manuch 2017S1: May June 2017 Unit Outline Thinking Recursively Recursion Examples Analyzing Recursion:
Introduction. Definition. What is an embedded system? What are embedded systems? Challenges in embedded computing system design. Design methodologies.
 Introduction What are embedded systems? Challenges in embedded computing system design. Design methodologies. What is an embedded system? Communication Avionics Automobile Consumer Electronics Office Equipment
Introduction What are embedded systems? Challenges in embedded computing system design. Design methodologies. What is an embedded system? Communication Avionics Automobile Consumer Electronics Office Equipment
Modules and Representation Invariants
 Modules and Representation Invariants COS 326 Andrew W. Appel Princeton University slides copyright 2013-2015 David Walker and Andrew W. Appel In previous classes: Reasoning about individual OCaml expressions.
Modules and Representation Invariants COS 326 Andrew W. Appel Princeton University slides copyright 2013-2015 David Walker and Andrew W. Appel In previous classes: Reasoning about individual OCaml expressions.
AXIOMS FOR THE INTEGERS
 AXIOMS FOR THE INTEGERS BRIAN OSSERMAN We describe the set of axioms for the integers which we will use in the class. The axioms are almost the same as what is presented in Appendix A of the textbook,
AXIOMS FOR THE INTEGERS BRIAN OSSERMAN We describe the set of axioms for the integers which we will use in the class. The axioms are almost the same as what is presented in Appendix A of the textbook,
A - 1. CS 494 Object-Oriented Analysis & Design. UML Class Models. Overview. Class Model Perspectives (cont d) Developing Class Models
 CS 494 Object-Oriented Analysis & Design UML Class Models Overview How class models are used? Perspectives Classes: attributes and operations Associations Multiplicity Generalization and Inheritance Aggregation
CS 494 Object-Oriented Analysis & Design UML Class Models Overview How class models are used? Perspectives Classes: attributes and operations Associations Multiplicity Generalization and Inheritance Aggregation
Supervised Learning with Neural Networks. We now look at how an agent might learn to solve a general problem by seeing examples.
 Supervised Learning with Neural Networks We now look at how an agent might learn to solve a general problem by seeing examples. Aims: to present an outline of supervised learning as part of AI; to introduce
Supervised Learning with Neural Networks We now look at how an agent might learn to solve a general problem by seeing examples. Aims: to present an outline of supervised learning as part of AI; to introduce
Them Threads, Them Threads, Them Useless Threads
 Them Threads, Them Threads, Them Useless Threads Dr Russel Winder Partner, Concertant LLP russel.winder@concertant.com Copyright 2008 Russel Winder 1 Aims and Objectives of the Session Raise awareness
Them Threads, Them Threads, Them Useless Threads Dr Russel Winder Partner, Concertant LLP russel.winder@concertant.com Copyright 2008 Russel Winder 1 Aims and Objectives of the Session Raise awareness
Areas related to SW verif. Trends in Software Validation. Your Expertise. Research Trends High level. Research Trends - Ex 2. Research Trends Ex 1
 Areas related to SW verif. Trends in Software Validation Abhik Roychoudhury CS 6214 Formal Methods Model based techniques Proof construction techniques Program Analysis Static Analysis Abstract Interpretation
Areas related to SW verif. Trends in Software Validation Abhik Roychoudhury CS 6214 Formal Methods Model based techniques Proof construction techniques Program Analysis Static Analysis Abstract Interpretation
Programming Language Abstractions for Modularly Verified Distributed Systems. James R. Wilcox Zach Tatlock Ilya Sergey
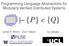 Programming Language Abstractions for Modularly Verified Distributed Systems ` {P } c {Q} James R. Wilcox Zach Tatlock Ilya Sergey Distributed Systems Distributed Infrastructure Distributed Applications
Programming Language Abstractions for Modularly Verified Distributed Systems ` {P } c {Q} James R. Wilcox Zach Tatlock Ilya Sergey Distributed Systems Distributed Infrastructure Distributed Applications
You should get the following:
 Index Index... 2 Engineering Mode... 3 Hidden Menu within engineering mode... 4 Driver distraction Menu... 5 Region Code Menu... 6 Backdoor Menu... 7 Navigation Hidden Menu... 8 Page -2- Engineering Mode
Index Index... 2 Engineering Mode... 3 Hidden Menu within engineering mode... 4 Driver distraction Menu... 5 Region Code Menu... 6 Backdoor Menu... 7 Navigation Hidden Menu... 8 Page -2- Engineering Mode
"Secure" Coding Practices Nicholas Weaver
 "Secure" Coding Practices based on David Wagner s slides from Sp 2016 1 Administrivia Computer Science 161 Fall 2016 2 3 This is a Remarkably Typical C Problem Computer Science 161 Fall 2016 if ((options
"Secure" Coding Practices based on David Wagner s slides from Sp 2016 1 Administrivia Computer Science 161 Fall 2016 2 3 This is a Remarkably Typical C Problem Computer Science 161 Fall 2016 if ((options
Thread Synchronization: Foundations. Properties. Safety properties. Edsger s perspective. Nothing bad happens
 Edsger s perspective Testing can only prove the presence of bugs Thread Synchronization: Foundations Properties Property: a predicate that is evaluated over a run of the program (a trace) every message
Edsger s perspective Testing can only prove the presence of bugs Thread Synchronization: Foundations Properties Property: a predicate that is evaluated over a run of the program (a trace) every message
Lectures 24 and 25: Scheduling; Introduction to Effects
 15-150 Lectures 24 and 25: Scheduling; Introduction to Effects Lectures by Dan Licata April 12 and 17, 2011 1 Brent s Principle In lectures 17 and 18, we discussed cost graphs, which can be used to reason
15-150 Lectures 24 and 25: Scheduling; Introduction to Effects Lectures by Dan Licata April 12 and 17, 2011 1 Brent s Principle In lectures 17 and 18, we discussed cost graphs, which can be used to reason
Design of Embedded Systems
 Design of Embedded Systems José Costa Software for Embedded Systems Departamento de Engenharia Informática (DEI) Instituto Superior Técnico 2015-01-02 José Costa (DEI/IST) Design of Embedded Systems 1
Design of Embedded Systems José Costa Software for Embedded Systems Departamento de Engenharia Informática (DEI) Instituto Superior Técnico 2015-01-02 José Costa (DEI/IST) Design of Embedded Systems 1
Part II. Hoare Logic and Program Verification. Why specify programs? Specification and Verification. Code Verification. Why verify programs?
 Part II. Hoare Logic and Program Verification Part II. Hoare Logic and Program Verification Dilian Gurov Props: Models: Specs: Method: Tool: safety of data manipulation source code logic assertions Hoare
Part II. Hoare Logic and Program Verification Part II. Hoare Logic and Program Verification Dilian Gurov Props: Models: Specs: Method: Tool: safety of data manipulation source code logic assertions Hoare
