SQL INJECTION IN WEB APPLICATIONS By Roshmi Choudhury,Officer (IT) Numaligarh Refinery Limited
|
|
|
- Lizbeth Chambers
- 6 years ago
- Views:
Transcription
1 SQL INJECTION IN WEB APPLICATIONS By Roshmi Choudhury,Officer (IT) Numaligarh Refinery Limited Abstract It may be too late to shut the stable door after the horse has been stolen. Most companies in the world only react to security breakthroughs and too often after the damage has already occurred. While other systems in a company are quite secured enough, a web site is vulnerable to attacks usually by what is known as SQL Injection. SQL injection is a method for exploiting web applications that uses user-supplied data to form SQL queries, which is then sent to the database for retrieving data. The objective of this paper is to apprise about the different techniques in SQL Injection and the mechanisms that should be employed to prevent it from happening. What is SQL Injection? SQL injection is the manipulation of SQL code that will be sent to the database. It is possible in web-based applications that form dynamic SQL statements for retrieving data from the database. The hacker appends executable code to a text field that provides input for a query. This could allow the hacker obtain information from the database other than what was intended by the web application. SQL Injection Techniques The commonly used SQL injection techniques are: Bypassing Authorization Using the SELECT & UNION statements Using SQL server stored procedures. Bypassing Authorization The easiest SQL injection is to bypass the logon forms where the user is authenticated against a password supplied by the user. This is how login form looks like Login Name: Password: SUBMIT And this how the authorization script in the web page will look like: txtuser = request ( User ) txtpassword = request ( Password )
2 set conn = Server.CreateObject ( ADODB.Connection ) set rs = Server.CreateObject ( ADODB.Recordset ) Conn.open dsn SQLQuery = select * from users where password = & txtpassword & and user = & txtuser & Rs.open SQLQuery, Conn If rs.eof and rs.bof then Access Denied Else Access Allowed End if To bypass this authorization, the user will have to enter the following: Login Name: Password: or 1 = 1 test SUBMIT The query is built using server-side script languages such as ASP, JSP and CGI, and is then sent to the database server as a single SQL statement. The SQL query that will be sent to the database will look like: Select * from users where password = test and user = or 1 = 1 This SQL query will go through without any errors and will return a record set. So the hacker can login and get access to other web pages and more importantly the database. SELECT and UNION Statements Most web applications will retrieve data from the database using a SELECT statement with a WHERE clause. To make a server return records other than those intended, the WHERE clause should be modified by injecting a UNION SELECT. Let us consider a web page that returns employee information when a city is entered. The SQL query in the web page will look like this
3 SELECT first_name, last_name, designation FROM employees WHERE city = & txtcity & The major problem encountered here is that we do not know other tables to make a UNION statement. However, for an experienced hacker this is not much of a problem. Because he will have adequate knowledge of the SQL server and the tables from where he can gather this information. The tables are sysobjects for the table names and syscolumns for the fields. To make a UNION statement successful, the number of columns in the two SELECT statement and their field types should match. The following injection string can be used: UNION ALL SELECT name, 4 FROM sysobjects WHERE xtype = U The SQL query that will be formed will look like this: WHERE city = UNION ALL SELECT name, id, 4 FROM sysobjects WHERE xtype = U Error messages are very important for a successful attack. The error from the server is Server: Msg 205, Level 16, State 1, Line 1 All queries in an SQL statement containing a UNION operator must have an equal number of expressions in their target lists. The user can add another field so that the SQL query passed to the database will be: WHERE city = UNION ALL SELECT name, id, 4, 4 FROM sysobjects WHERE xtype = U Since the number of columns in the two SELECT statements match and the column type matches, the attacker will get a valid output which will lists all the tables in the database with their ID number. He can select one such table and its corresponding ID and form another SQL injection string: UNION ALL SELECT name, 4, 4, 4 FROM syscolumns WHERE id = The SQL query that will be executed on the server will be: WHERE city = UNION ALL SELECT name, 4, 4, 4 FROM syscolumns WHERE id = 14243
4 The user gets all the fields of the table; he can then extract any information from the table using the same procedure. Stored Procedures If the ASP page uses stored procedures and the user-supplied parameters are passed to a stored procedure, then SQL injection is typically impossible because the user simply adds characters that are meaningless to the string. However, if dynamic SQL is used in the stored procedure, it would end up reintroducing SQL injection. ---Not vulnerable to SQL injection CREATE PROC varchar (200) AS BEGIN SELECT last_name, first_name FROM authors WHERE city END ---Vulnerable to SQL injection CREATE proc varchar(200) AS BEGIN nvarchar(2000) = replace(@city, '''', '''''') = 'SELECT last_name, first_name FROM authors where city=''' + '''' EXEC (@cmd) RETURN END The attacker can also take advantage of system supplied stored procedures such as the xp_cmdshell which executes operating system commands in the context of the Microsoft SQL server. He can use the following injection string and can get the list of files in the current directory of the SQL process. ' EXEC master..xp_cmdshell dir - -' Preventing SQL injection Input validation with parameter filtering and sizing; and detection of SQL signatures like UNION SELECT & XP_CMDSHELL Stored procedures without any dynamic SQL embedded in it.
5 Providing limited database access to the user. Restricting error messages from appearing on the screen by using error handlers. References 1. SQL Injection- Are your web applications vulnerable? by Kevin Spatt 2. Advanced SQL Injection in SQL Server Applications by Chris Anley
Module 14: SQL Injection
 Module 14: SQL Injection Objective The objective of this lab is to provide expert knowledge on SQL Injection attacks and other responsibilities that include: Understanding when and how web application
Module 14: SQL Injection Objective The objective of this lab is to provide expert knowledge on SQL Injection attacks and other responsibilities that include: Understanding when and how web application
Secure Web App. 제목 : Secure Web Application v1.0 ( 채수민책임 ) Copyright 2008 Samsung SDS Co., Ltd. All rights reserved - 1 -
 Secure Web App. Copyright 2008 Samsung SDS Co., Ltd. All rights reserved - 1 - Building & Testing Secure Web Applications By Aspect Security Copyright 2008 Samsung SDS Co., Ltd. All rights reserved - 2
Secure Web App. Copyright 2008 Samsung SDS Co., Ltd. All rights reserved - 1 - Building & Testing Secure Web Applications By Aspect Security Copyright 2008 Samsung SDS Co., Ltd. All rights reserved - 2
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma
 Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Overview of Professional Quest Technologies
 Overview of Professional Quest Technologies Professional Quest Web Architecture Professional Quest's utilizes a number of industry standard components in its web architecture. Server Web Pages For the
Overview of Professional Quest Technologies Professional Quest Web Architecture Professional Quest's utilizes a number of industry standard components in its web architecture. Server Web Pages For the
Webapps Vulnerability Report
 Webapps Vulnerability Report Tuesday, January 12, 2010 Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE IMPACT during this
Webapps Vulnerability Report Tuesday, January 12, 2010 Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE IMPACT during this
SQL Injection SPRING 2018: GANG WANG
 SQL Injection SPRING 2018: GANG WANG SQL Injection Another reason to validate user input data Slides credit to Neil Daswani and Adam Doupé 2 3 http://xkcd.com/327/ Produce More Secure Code Operating system
SQL Injection SPRING 2018: GANG WANG SQL Injection Another reason to validate user input data Slides credit to Neil Daswani and Adam Doupé 2 3 http://xkcd.com/327/ Produce More Secure Code Operating system
The ADO Connection Object is used to create an open connection to a data source. Through this connection, you can access and manipulate a database.
 Unit 5: Accessing Databases with ASP and ADO Active Database Object(ADO) ADO represents a collection of objects that, via ASP, you can easily manipulate to gain incredible control over the information
Unit 5: Accessing Databases with ASP and ADO Active Database Object(ADO) ADO represents a collection of objects that, via ASP, you can easily manipulate to gain incredible control over the information
SPOOFING. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
SPOOFING Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Determine relevance of
Web Security. Attacks on Servers 11/6/2017 1
 Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
Web Security Attacks on Servers 11/6/2017 1 Server side Scripting Javascript code is executed on the client side on a user s web browser Server side code is executed on the server side. The server side
Hack-Proofing Your ASP.NET Applications
 Note: Article is mapped toe ACCP Trim 4 and ACCP-Pro Term III Introduction Almost every day, the mainstream media reports that another site has been hacked. These constant intrusions by prominent hacker
Note: Article is mapped toe ACCP Trim 4 and ACCP-Pro Term III Introduction Almost every day, the mainstream media reports that another site has been hacked. These constant intrusions by prominent hacker
Secure Programming Lecture 8++: SQL Injection
 Secure Programming Lecture 8++: SQL Injection David Aspinall, Informatics @ Edinburgh 9th February 2016 Outline Overview Other past attacks More examples Classification Injection route and motive Forms
Secure Programming Lecture 8++: SQL Injection David Aspinall, Informatics @ Edinburgh 9th February 2016 Outline Overview Other past attacks More examples Classification Injection route and motive Forms
Application vulnerabilities and defences
 Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Security Course. WebGoat Lab sessions
 Security Course WebGoat Lab sessions WebGoat Lab sessions overview Initial Setup Tamper Data Web Goat Lab Session 4 Access Control, session information stealing Lab Session 2 HTTP Basics Sniffing Parameter
Security Course WebGoat Lab sessions WebGoat Lab sessions overview Initial Setup Tamper Data Web Goat Lab Session 4 Access Control, session information stealing Lab Session 2 HTTP Basics Sniffing Parameter
Assignment 6. This lab should be performed under the Oracle Linux VM provided in the course.
 Assignment 6 This assignment includes hands-on exercises in the Oracle VM. It has two Parts. Part 1 is SQL Injection Lab and Part 2 is Encryption Lab. Deliverables You will be submitting evidence that
Assignment 6 This assignment includes hands-on exercises in the Oracle VM. It has two Parts. Part 1 is SQL Injection Lab and Part 2 is Encryption Lab. Deliverables You will be submitting evidence that
Dynamically build connection objects for Microsoft Access databases in SQL Server Integration Services SSIS
 Dynamically build connection objects for Microsoft Access databases in SQL Server Integration Services SSIS Problem As a portion of our daily data upload process, we receive data in the form of Microsoft
Dynamically build connection objects for Microsoft Access databases in SQL Server Integration Services SSIS Problem As a portion of our daily data upload process, we receive data in the form of Microsoft
Locate your Advanced Tools and Applications
 MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
MySQL Manager is a web based MySQL client that allows you to create and manipulate a maximum of two MySQL databases. MySQL Manager is designed for advanced users.. 1 Contents Locate your Advanced Tools
Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion
 IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
ATTACKING SYSTEM & WEB Desmond Alexander CISSP / GIAC/ GPEN CEO FORESEC
 ATTACKING SYSTEM & WEB Desmond Alexander CISSP / GIAC/ GPEN CEO FORESEC AGENDA VULNERABILITIES OF WEB EXPLOIT METHODS COUNTERMEASURE About Me DIRECTOR OF FORESEC COUNTER TERRORIST ACTION TEAM RESEARCH
ATTACKING SYSTEM & WEB Desmond Alexander CISSP / GIAC/ GPEN CEO FORESEC AGENDA VULNERABILITIES OF WEB EXPLOIT METHODS COUNTERMEASURE About Me DIRECTOR OF FORESEC COUNTER TERRORIST ACTION TEAM RESEARCH
Injection attacks use specially crafted inputs to subvert the intended operation of applications.
 Secure Programming Lecture 8: SQL Injection David Aspinall, Informatics @ Edinburgh 8th February 2018 Recap Injection attacks use specially crafted inputs to subvert the intended operation of applications.
Secure Programming Lecture 8: SQL Injection David Aspinall, Informatics @ Edinburgh 8th February 2018 Recap Injection attacks use specially crafted inputs to subvert the intended operation of applications.
CSCE 548 Building Secure Software SQL Injection Attack
 CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
Chapter 5: Database Security
 i Chapter 5: Comp Sci 3600 Outline i 1 2 i 3 4 5 Outline i 1 2 i 3 4 5 What is a i Structured collection of data stored for use by one or more applications Contains the relationships between data items
i Chapter 5: Comp Sci 3600 Outline i 1 2 i 3 4 5 Outline i 1 2 i 3 4 5 What is a i Structured collection of data stored for use by one or more applications Contains the relationships between data items
Building a Web-based Health Promotion Database
 6 th International Conference on Applied Informatics Eger, Hungary, January 27 31, 2004. Building a Web-based Health Promotion Database Ádám Rutkovszky University of Debrecen, Faculty of Economics Department
6 th International Conference on Applied Informatics Eger, Hungary, January 27 31, 2004. Building a Web-based Health Promotion Database Ádám Rutkovszky University of Debrecen, Faculty of Economics Department
Web Application Security. Philippe Bogaerts
 Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
DumpsTorrent. Latest dumps torrent provider, real dumps
 DumpsTorrent http://www.dumpstorrent.com Latest dumps torrent provider, real dumps Exam : GCIH Title : GIAC Certified Incident Handler Vendor : GIAC Version : DEMO Get Latest & Valid GCIH Exam's Question
DumpsTorrent http://www.dumpstorrent.com Latest dumps torrent provider, real dumps Exam : GCIH Title : GIAC Certified Incident Handler Vendor : GIAC Version : DEMO Get Latest & Valid GCIH Exam's Question
Injection vulnerabilities: command injection and SQL injection
 Injection vulnerabilities: command injection and SQL injection Questões de Segurança em Engenharia de Software (QSES) Departamento de Ciência de Computadores Faculdade de Ciências da Universidade do Porto
Injection vulnerabilities: command injection and SQL injection Questões de Segurança em Engenharia de Software (QSES) Departamento de Ciência de Computadores Faculdade de Ciências da Universidade do Porto
Engineering Your Software For Attack
 Engineering Your Software For Attack Robert A. Martin Senior Principal Engineer Cyber Security Center Center for National Security The MITRE Corporation 2013 The MITRE Corporation. All rights reserved.
Engineering Your Software For Attack Robert A. Martin Senior Principal Engineer Cyber Security Center Center for National Security The MITRE Corporation 2013 The MITRE Corporation. All rights reserved.
Step-by-Step Guide to Ansur Executive 3.0 Installation With or without Electronic Signatures
 Step-by-Step Guide to Ansur Executive 3.0 Installation With or without Electronic Signatures Ansur with Electronic Signatures Background: Electronic signature is a new feature that is implemented in Ansur
Step-by-Step Guide to Ansur Executive 3.0 Installation With or without Electronic Signatures Ansur with Electronic Signatures Background: Electronic signature is a new feature that is implemented in Ansur
This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in
 1 This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in terms of prevalence (how much the vulnerability is widespread),
1 This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in terms of prevalence (how much the vulnerability is widespread),
Detecting SQLIA using execution plans
 Graduate Theses and Dissertations Graduate College 2016 Detecting SQLIA using execution plans Sriram Nagarajan Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/etd Part
Graduate Theses and Dissertations Graduate College 2016 Detecting SQLIA using execution plans Sriram Nagarajan Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/etd Part
INF 102 CONCEPTS OF PROG. LANGS ADVERSITY. Instructors: James Jones Copyright Instructors.
 INF 102 CONCEPTS OF PROG. LANGS ADVERSITY Instructors: James Jones Copyright Instructors. Approaches to failure Let it fail Good in development: understand failure mode Defend against the possible and
INF 102 CONCEPTS OF PROG. LANGS ADVERSITY Instructors: James Jones Copyright Instructors. Approaches to failure Let it fail Good in development: understand failure mode Defend against the possible and
Tautology based Advanced SQL Injection Technique A Peril to Web Application
 IJIRST National Conference on Latest Trends in Networking and Cyber Security March 2017 Tautology based Advanced SQL Injection Technique A Peril to Web Application Kritarth Jhala 1 Shukla Umang D 2 2 Department
IJIRST National Conference on Latest Trends in Networking and Cyber Security March 2017 Tautology based Advanced SQL Injection Technique A Peril to Web Application Kritarth Jhala 1 Shukla Umang D 2 2 Department
Ruby on Rails Secure Coding Recommendations
 Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
COMP 430 Intro. to Database Systems. Encapsulating SQL code
 COMP 430 Intro. to Database Systems Encapsulating SQL code Want to bundle SQL into code blocks Like in every other language Encapsulation Abstraction Code reuse Maintenance DB- or application-level? DB:
COMP 430 Intro. to Database Systems Encapsulating SQL code Want to bundle SQL into code blocks Like in every other language Encapsulation Abstraction Code reuse Maintenance DB- or application-level? DB:
Advanced Web Technology 10) XSS, CSRF and SQL Injection
 Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 1 Table of Contents Cross Site Request Forgery - CSRF Presentation
Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 1 Table of Contents Cross Site Request Forgery - CSRF Presentation
SQL Injection Attack & Its Prevention
 e-issn 2455 1392 Volume 2 Issue 6, June 2016 pp. 349 354 Scientific Journal Impact Factor : 3.468 http://www.ijcter.com SQL Injection Attack & Its Prevention Amey Anil Patil L.B.H.S.S.T s Institute Of
e-issn 2455 1392 Volume 2 Issue 6, June 2016 pp. 349 354 Scientific Journal Impact Factor : 3.468 http://www.ijcter.com SQL Injection Attack & Its Prevention Amey Anil Patil L.B.H.S.S.T s Institute Of
Security issues. Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith
 Security issues Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith Criteria D3 D3 Recommend ways to improve web security when using web server scripting Clean browser input Don
Security issues Unit 27 Web Server Scripting Extended Diploma in ICT 2016 Lecture: Phil Smith Criteria D3 D3 Recommend ways to improve web security when using web server scripting Clean browser input Don
Unit Level Secure by Design Approach
 Unit Level Secure by Design Approach Abstract Authors: Vasantharaju MS & Joshua Cajetan Rebelo Vasantharaju_MS@McAfee.com Joshua.Rebelo@Siemens.com With cyber-attacks on the rise and high-profile breaches
Unit Level Secure by Design Approach Abstract Authors: Vasantharaju MS & Joshua Cajetan Rebelo Vasantharaju_MS@McAfee.com Joshua.Rebelo@Siemens.com With cyber-attacks on the rise and high-profile breaches
Web Application Attacks
 Web Application Attacks What can an attacker do and just how hard is it? By Damon P. Cortesi IOActive, Inc. Comprehensive Computer Security Services www.ioactive.com cortesi:~
Web Application Attacks What can an attacker do and just how hard is it? By Damon P. Cortesi IOActive, Inc. Comprehensive Computer Security Services www.ioactive.com cortesi:~
Domain System Threat Landscape. Pablo Rodriguez Nic.pr Janelle McAlister - MarkMonitor
 Domain System Threat Landscape Pablo Rodriguez Nic.pr Janelle McAlister - MarkMonitor Agenda n History n Nic.PR Case Study q Registrar Perspective q Registry Perspective n Future solutions History n Over
Domain System Threat Landscape Pablo Rodriguez Nic.pr Janelle McAlister - MarkMonitor Agenda n History n Nic.PR Case Study q Registrar Perspective q Registry Perspective n Future solutions History n Over
SANS SEC504. Hacker Tools, Techniques, Exploits and Incident Handling.
 SANS SEC504 Hacker Tools, Techniques, Exploits and Incident Handling http://killexams.com/exam-detail/sec504 QUESTION: 315 Which of the following techniques can be used to map 'open' or 'pass through'
SANS SEC504 Hacker Tools, Techniques, Exploits and Incident Handling http://killexams.com/exam-detail/sec504 QUESTION: 315 Which of the following techniques can be used to map 'open' or 'pass through'
Detecting Insider Attacks on Databases using Blockchains
 Detecting Insider Attacks on Databases using Blockchains Shubham Sharma, Rahul Gupta, Shubham Sahai Srivastava and Sandeep K. Shukla Department of Computer Science and Engineering Indian Institute of Technology,
Detecting Insider Attacks on Databases using Blockchains Shubham Sharma, Rahul Gupta, Shubham Sahai Srivastava and Sandeep K. Shukla Department of Computer Science and Engineering Indian Institute of Technology,
Injection. CSC 482/582: Computer Security Slide #1
 Injection Slide #1 Topics 1. Injection Attacks 2. SQL Injection 3. Mitigating SQL Injection 4. XML Injection Slide #2 Injection Injection attacks trick an application into including unintended commands
Injection Slide #1 Topics 1. Injection Attacks 2. SQL Injection 3. Mitigating SQL Injection 4. XML Injection Slide #2 Injection Injection attacks trick an application into including unintended commands
The INSERT INTO Method
 Article: Transferring Data from One Table to Another Date: 20/03/2012 Posted by: HeelpBook Staff Source: Link Permalink: Link SQL SERVER TRANSFERRING DATA FROM ONE TABLE TO ANOTHER Every DBA needs to transfer
Article: Transferring Data from One Table to Another Date: 20/03/2012 Posted by: HeelpBook Staff Source: Link Permalink: Link SQL SERVER TRANSFERRING DATA FROM ONE TABLE TO ANOTHER Every DBA needs to transfer
Design and Implement of Laboratory Management System based Web Zheng-Bo LI School of Economic Management, Beihua University, Jilin , China.
 Advances in Engineering Research (AER), volume 82 2016 International Conference on Engineering and Advanced Technology (ICEAT-16) Design and Implement of Laboratory Management System based Web Zheng-Bo
Advances in Engineering Research (AER), volume 82 2016 International Conference on Engineering and Advanced Technology (ICEAT-16) Design and Implement of Laboratory Management System based Web Zheng-Bo
CSC 405 Computer Security. Web Security
 CSC 405 Computer Security Web Security Alexandros Kapravelos akaprav@ncsu.edu (Derived from slides by Giovanni Vigna and Adam Doupe) 1 source: https://xkcd.com/327/ 2 source: https://xkcd.com/327/ 3 source:
CSC 405 Computer Security Web Security Alexandros Kapravelos akaprav@ncsu.edu (Derived from slides by Giovanni Vigna and Adam Doupe) 1 source: https://xkcd.com/327/ 2 source: https://xkcd.com/327/ 3 source:
Risk Analysis and Measurement with CWRAF
 Risk Analysis and Measurement with CWRAF - Common Weakness Risk Analysis Framework - April 4, 2012 Making Security Measurable (MSM) Software Assurance Enterprise Security Management Threat Management Design
Risk Analysis and Measurement with CWRAF - Common Weakness Risk Analysis Framework - April 4, 2012 Making Security Measurable (MSM) Software Assurance Enterprise Security Management Threat Management Design
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
AN-016 Protégé Server ODBC Database Connectivity
 AN-016 Protégé Server ODBC Database Connectivity PUBLICATION INFORMATION This application note covers the use of the protégé system to perform a specific function and may be used in conjunction with other
AN-016 Protégé Server ODBC Database Connectivity PUBLICATION INFORMATION This application note covers the use of the protégé system to perform a specific function and may be used in conjunction with other
A SURVEY OF ATTACKS ON PHP AND WEB VULNERABILITIES
 INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 A SURVEY OF ATTACKS ON PHP AND WEB VULNERABILITIES Venkatesh Yerram 1, Dr G.Venkat Rami Reddy 2 ¹Computer Networks
INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 A SURVEY OF ATTACKS ON PHP AND WEB VULNERABILITIES Venkatesh Yerram 1, Dr G.Venkat Rami Reddy 2 ¹Computer Networks
CSE 127 Computer Security
 CSE 127 Computer Security Fall 2015 Web Security I: SQL injection Stefan Savage The Web creates new problems Web sites are programs Partially implemented in browser» Javascript, Java, Flash Partially implemented
CSE 127 Computer Security Fall 2015 Web Security I: SQL injection Stefan Savage The Web creates new problems Web sites are programs Partially implemented in browser» Javascript, Java, Flash Partially implemented
Create a Login System in Visual Basic. Creating a login system. Start a new visual basic Windows Forms application project. Call it Login System
 Creating a login system Start a new visual basic Windows Forms application project Call it Login System Change the form TITLE from Form1 to Login System Add the following to the form Component Text Name
Creating a login system Start a new visual basic Windows Forms application project Call it Login System Change the form TITLE from Form1 to Login System Add the following to the form Component Text Name
SQL Injection Attacks and Defense
 SQL Injection Attacks and Defense Justin Clarke Lead Author and Technical Editor Rodrigo Marcos Alvarez Dave Hartley Joseph Hemler Alexander Kornbrust Haroon Meer Gary O'Leary-Steele Alberto Revelli Marco
SQL Injection Attacks and Defense Justin Clarke Lead Author and Technical Editor Rodrigo Marcos Alvarez Dave Hartley Joseph Hemler Alexander Kornbrust Haroon Meer Gary O'Leary-Steele Alberto Revelli Marco
Server-side web security (part 2 - attacks and defences)
 Server-side web security (part 2 - attacks and defences) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Basic injections $query = "SELECT name, lastname,
Server-side web security (part 2 - attacks and defences) Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Basic injections $query = "SELECT name, lastname,
Infotek Solutions Inc.
 Infotek Solutions Inc. Read Data from Database and input in Flight Reservation login logout and add Check point in QTP: In this tutorial we will read data from mysql database and give the input to login
Infotek Solutions Inc. Read Data from Database and input in Flight Reservation login logout and add Check point in QTP: In this tutorial we will read data from mysql database and give the input to login
Views in SQL Server 2000
 Views in SQL Server 2000 By: Kristofer Gafvert Copyright 2003 Kristofer Gafvert 1 Copyright Information Copyright 2003 Kristofer Gafvert (kgafvert@ilopia.com). No part of this publication may be transmitted,
Views in SQL Server 2000 By: Kristofer Gafvert Copyright 2003 Kristofer Gafvert 1 Copyright Information Copyright 2003 Kristofer Gafvert (kgafvert@ilopia.com). No part of this publication may be transmitted,
SECURITY TESTING. Towards a safer web world
 SECURITY TESTING Towards a safer web world AGENDA 1. 3 W S OF SECURITY TESTING 2. SECURITY TESTING CONCEPTS 3. SECURITY TESTING TYPES 4. TOP 10 SECURITY RISKS ate: 2013-14 Few Security Breaches September
SECURITY TESTING Towards a safer web world AGENDA 1. 3 W S OF SECURITY TESTING 2. SECURITY TESTING CONCEPTS 3. SECURITY TESTING TYPES 4. TOP 10 SECURITY RISKS ate: 2013-14 Few Security Breaches September
Using OpenESQL to Map COBOL to DBMS Data Types
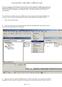 There is an easy way in Net Express to determine the correct mapping of COBOL data types to the appropriate DBMS's data types. This issue arises frequently and by using the OpenESQL assistant tool the
There is an easy way in Net Express to determine the correct mapping of COBOL data types to the appropriate DBMS's data types. This issue arises frequently and by using the OpenESQL assistant tool the
Bruce Moore Fall 99 Internship September 23, 1999 Supervised by Dr. John P.
 Bruce Moore Fall 99 Internship September 23, 1999 Supervised by Dr. John P. Russo Active Server Pages Active Server Pages are Microsoft s newest server-based technology for building dynamic and interactive
Bruce Moore Fall 99 Internship September 23, 1999 Supervised by Dr. John P. Russo Active Server Pages Active Server Pages are Microsoft s newest server-based technology for building dynamic and interactive
Oracle Database 10g Express
 Oracle Database 10g Express This tutorial prepares the Oracle Database 10g Express Edition Developer to perform common development and administrative tasks of Oracle Database 10g Express Edition. Objectives
Oracle Database 10g Express This tutorial prepares the Oracle Database 10g Express Edition Developer to perform common development and administrative tasks of Oracle Database 10g Express Edition. Objectives
SQL Server Security Checklist
 Page 1 of 5 SQL Server Security Checklist http:// www.sqlsecurity.com 1. Make sure the latest NT and SQL Server Service Packs are applied. This goes without saying but I'll say it anyway for completeness.
Page 1 of 5 SQL Server Security Checklist http:// www.sqlsecurity.com 1. Make sure the latest NT and SQL Server Service Packs are applied. This goes without saying but I'll say it anyway for completeness.
Security and social engineering
 Focused on Security. Committed to Success. Security and social engineering Fcis,Mansoura University,Egtpt What is social engineer? Social engineering is satisfied attack from end user who behave confidence
Focused on Security. Committed to Success. Security and social engineering Fcis,Mansoura University,Egtpt What is social engineer? Social engineering is satisfied attack from end user who behave confidence
Notification Service for e-commerce Systems
 Notification Service for e-commerce Systems By Johan Sandberg 2003-10-23 Examiner: Vladimir Vlassov Abstract The objective of this thesis was to construct and analyze scalability of a system that handles
Notification Service for e-commerce Systems By Johan Sandberg 2003-10-23 Examiner: Vladimir Vlassov Abstract The objective of this thesis was to construct and analyze scalability of a system that handles
Private Institute of Aga NETWORK DATABASE LECTURER NIYAZ M. SALIH
 Private Institute of Aga 2018 NETWORK DATABASE LECTURER NIYAZ M. SALIH Data Definition Language (DDL): String data Types: Data Types CHAR(size) NCHAR(size) VARCHAR2(size) Description A fixed-length character
Private Institute of Aga 2018 NETWORK DATABASE LECTURER NIYAZ M. SALIH Data Definition Language (DDL): String data Types: Data Types CHAR(size) NCHAR(size) VARCHAR2(size) Description A fixed-length character
DEFENSIVE PROGRAMMING. Lecture for EDA 263 Magnus Almgren Department of Computer Science and Engineering Chalmers University of Technology
 DEFENSIVE PROGRAMMING Lecture for EDA 263 Magnus Almgren Department of Computer Science and Engineering Chalmers University of Technology Traditional Programming When writing a program, programmers typically
DEFENSIVE PROGRAMMING Lecture for EDA 263 Magnus Almgren Department of Computer Science and Engineering Chalmers University of Technology Traditional Programming When writing a program, programmers typically
Hacking Terminology. Mark R. Adams, CISSP KPMG LLP
 Hacking Terminology Mark R. Adams, CISSP KPMG LLP Backdoor Also referred to as a trap door. A hole in the security of a system deliberately left in place by designers or maintainers. Hackers may also leave
Hacking Terminology Mark R. Adams, CISSP KPMG LLP Backdoor Also referred to as a trap door. A hole in the security of a system deliberately left in place by designers or maintainers. Hackers may also leave
Using MySQL on the Winthrop Linux Systems
 Using MySQL on the Winthrop Linux Systems by Dr. Kent Foster adapted for CSCI 297 Scripting Languages by Dr. Dannelly updated March 2017 I. Creating your MySQL password: Your mysql account username has
Using MySQL on the Winthrop Linux Systems by Dr. Kent Foster adapted for CSCI 297 Scripting Languages by Dr. Dannelly updated March 2017 I. Creating your MySQL password: Your mysql account username has
IS 2150 / TEL 2810 Introduction to Security
 IS 2150 / TEL 2810 Introduction to Security James Joshi Professor, SIS Lecture 15 April 20, 2016 SQL Injection Cross-Site Scripting 1 Goals Overview SQL Injection Attacks Cross-Site Scripting Attacks Some
IS 2150 / TEL 2810 Introduction to Security James Joshi Professor, SIS Lecture 15 April 20, 2016 SQL Injection Cross-Site Scripting 1 Goals Overview SQL Injection Attacks Cross-Site Scripting Attacks Some
CSE361 Web Security. Attacks against the server-side of web applications. Nick Nikiforakis
 CSE361 Web Security Attacks against the server-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Threat model In these scenarios: The server is benign The client is malicious The client
CSE361 Web Security Attacks against the server-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Threat model In these scenarios: The server is benign The client is malicious The client
Acknowledgments Introduction. Part I: Programming Access Applications 1. Chapter 1: Overview of Programming for Access 3
 74029ftoc.qxd:WroxPro 9/27/07 1:40 PM Page xiii Acknowledgments Introduction x xxv Part I: Programming Access Applications 1 Chapter 1: Overview of Programming for Access 3 Writing Code for Access 3 The
74029ftoc.qxd:WroxPro 9/27/07 1:40 PM Page xiii Acknowledgments Introduction x xxv Part I: Programming Access Applications 1 Chapter 1: Overview of Programming for Access 3 Writing Code for Access 3 The
SQL Injection Protector
 2011 International Conference on Modeling, Simulation and Control IPCSIT vol.10 (2011) (2011) IACSIT Press, Singapore SQL Injection Protector Wiwat Sriphum, Thawatchai Chomsiri, Ponlawat Attanak, Panuwat
2011 International Conference on Modeling, Simulation and Control IPCSIT vol.10 (2011) (2011) IACSIT Press, Singapore SQL Injection Protector Wiwat Sriphum, Thawatchai Chomsiri, Ponlawat Attanak, Panuwat
jk0-022 Exam Questions Demo CompTIA Exam Questions jk0-022
 CompTIA Exam Questions jk0-022 CompTIA Academic/E2C Security+ Certification Exam Voucher Only Version:Demo 1.An attacker used an undocumented and unknown application exploit to gain access to a file server.
CompTIA Exam Questions jk0-022 CompTIA Academic/E2C Security+ Certification Exam Voucher Only Version:Demo 1.An attacker used an undocumented and unknown application exploit to gain access to a file server.
Excerpts of Web Application Security focusing on Data Validation. adapted for F.I.S.T. 2004, Frankfurt
 Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Practical Automated Web Application Attack Techniques Justin Clarke Gotham Digital Science Gotham Digital Science Ltd
 Practical Automated Web Application Attack Techniques Justin Clarke Gotham Digital Science Why this talk? The techniques are well known, but how about some way of applying ppy them? Commercial tools are
Practical Automated Web Application Attack Techniques Justin Clarke Gotham Digital Science Why this talk? The techniques are well known, but how about some way of applying ppy them? Commercial tools are
Database Systems. Answers
 Database Systems Question @ Answers Question 1 What are the most important directories in the MySQL installation? Bin Executable Data Database data Docs Database documentation Question 2 What is the primary
Database Systems Question @ Answers Question 1 What are the most important directories in the MySQL installation? Bin Executable Data Database data Docs Database documentation Question 2 What is the primary
ANALYSIS OF VARIOUS LEVELS OF PENETRATION BY SQL INJECTION TECHNIQUE THROUGH DVWA
 ANALYSIS OF VARIOUS LEVELS OF PENETRATION BY SQL INJECTION TECHNIQUE THROUGH DVWA By Ashish Kumar, Dr. Swapnesh Taterh 1st AIIT, Amity University, Rajasthan. 2nd Asst Prof, AIIT, Amity University, Rajasthan.
ANALYSIS OF VARIOUS LEVELS OF PENETRATION BY SQL INJECTION TECHNIQUE THROUGH DVWA By Ashish Kumar, Dr. Swapnesh Taterh 1st AIIT, Amity University, Rajasthan. 2nd Asst Prof, AIIT, Amity University, Rajasthan.
BraindumpsVCE. Best vce braindumps-exam vce pdf free download
 BraindumpsVCE http://www.braindumpsvce.com Best vce braindumps-exam vce pdf free download Exam : 312-50v8 Title : Certified Ethical Hacker v8 Vendors : ECCouncil Version : DEMO 1 / 4 Get Latest & Valid
BraindumpsVCE http://www.braindumpsvce.com Best vce braindumps-exam vce pdf free download Exam : 312-50v8 Title : Certified Ethical Hacker v8 Vendors : ECCouncil Version : DEMO 1 / 4 Get Latest & Valid
WELCOME. APEX Security Primer. About Enkitec. About the Presenter. ! Oracle Platinum Partner! Established in 2004
 WELCOME APEX Security Primer Scott Spendolini Executive Director!1!2 About the Presenter About Enkitec! Scott Spendolini! Oracle Platinum Partner! scott.spendolini@enkitec.com! Established in 2004! @sspendol!
WELCOME APEX Security Primer Scott Spendolini Executive Director!1!2 About the Presenter About Enkitec! Scott Spendolini! Oracle Platinum Partner! scott.spendolini@enkitec.com! Established in 2004! @sspendol!
Remote Administration
 Windows Remote Desktop, on page 1 pcanywhere, on page VNC, on page 6 Windows Remote Desktop Remote Desktop permits users to remotely execute applications on Windows Server 2012 R2 from a range of devices
Windows Remote Desktop, on page 1 pcanywhere, on page VNC, on page 6 Windows Remote Desktop Remote Desktop permits users to remotely execute applications on Windows Server 2012 R2 from a range of devices
Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE. s3security.com
 Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE s3security.com Security Professional Services S3 offers security services through its Security Professional Services (SPS) group, the security-consulting
Specialized Security Services, Inc. REDUCE RISK WITH CONFIDENCE s3security.com Security Professional Services S3 offers security services through its Security Professional Services (SPS) group, the security-consulting
Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary Attack
 P3 - Explain the security risks and protection mechanisms involved in website performance Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary
P3 - Explain the security risks and protection mechanisms involved in website performance Assessment 1 Task 3 Explain the following security risks SQL Injection Cross Site Scripting XSS Brute Force Attack/Dictionary
Lab # 1. You will be using MySQL as a database management system during the labs. The goal of this first lab is to familiarize you with MySQL.
 DDB Spring 2006 Lab # 1 You will be using MySQL as a database management system during the labs. The goal of this first lab is to familiarize you with MySQL. The reason you are using MySQL is twofolds.
DDB Spring 2006 Lab # 1 You will be using MySQL as a database management system during the labs. The goal of this first lab is to familiarize you with MySQL. The reason you are using MySQL is twofolds.
Introduction to Ethical Hacking
 Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
(more) Advanced SQL Injection
 (more) Advanced SQL Injection Chris Anley [chris@ngssoftware.com] 18/06/2002 An NGSSoftware Insight Security Research (NISR) Publication 2002 Next Generation Security Software Ltd http://www.ngssoftware.com
(more) Advanced SQL Injection Chris Anley [chris@ngssoftware.com] 18/06/2002 An NGSSoftware Insight Security Research (NISR) Publication 2002 Next Generation Security Software Ltd http://www.ngssoftware.com
A (sample) computerized system for publishing the daily currency exchange rates
 A (sample) computerized system for publishing the daily currency exchange rates The Treasury Department has constructed a computerized system that publishes the daily exchange rates of the local currency
A (sample) computerized system for publishing the daily currency exchange rates The Treasury Department has constructed a computerized system that publishes the daily exchange rates of the local currency
Penetration Testing following OWASP. Boyan Yanchev Chief Technology Ofcer Peter Dimkov IS Consultant
 Penetration Testing following OWASP Boyan Yanchev Chief Technology Ofcer Peter Dimkov IS Consultant За Лирекс Penetration testing A method of compromising the security of a computer system or network by
Penetration Testing following OWASP Boyan Yanchev Chief Technology Ofcer Peter Dimkov IS Consultant За Лирекс Penetration testing A method of compromising the security of a computer system or network by
Karthik Bharathy Program Manager, SQL Server Microsoft
 Karthik Bharathy Program Manager, SQL Server Microsoft Key Session takeaways Understand the many views of SQL Server Look at hardening SQL Server At the network level At the access level At the data level
Karthik Bharathy Program Manager, SQL Server Microsoft Key Session takeaways Understand the many views of SQL Server Look at hardening SQL Server At the network level At the access level At the data level
SECURE CODING PART 1 MAGDA LILIA CHELLY ENTREPRENEUR CISO ADVISOR CYBERFEMINIST PEERLYST BRAND AMBASSADOR TOP 50 CYBER CYBER
 SECURE CODING PART 1 MAGDA LILIA CHELLY ENTREPRENEUR CISO ADVISOR CYBERFEMINIST PEERLYST BRAND AMBASSADOR TOP 50 CYBER INFLUENCER @RESPONSIBLE CYBER 1 AGENDA 1. Introduction: What is security? How much
SECURE CODING PART 1 MAGDA LILIA CHELLY ENTREPRENEUR CISO ADVISOR CYBERFEMINIST PEERLYST BRAND AMBASSADOR TOP 50 CYBER INFLUENCER @RESPONSIBLE CYBER 1 AGENDA 1. Introduction: What is security? How much
Installing PostgreSQL on Windows Server 2003
 Installing on Windows Server 2003 This Article covers installation of Version 9.3 32- bit on Windows Server 2003 32-bit OS Preflight Windows Server 9.3 32-bit Username :postgres Item Description 2003 R2
Installing on Windows Server 2003 This Article covers installation of Version 9.3 32- bit on Windows Server 2003 32-bit OS Preflight Windows Server 9.3 32-bit Username :postgres Item Description 2003 R2
Injectable Exploits. New Tools for Pwning Web Apps and Browsers
 Injectable Exploits New Tools for Pwning Web Apps and Browsers Kevin Johnson kevin@inguardians.com Justin Searle justin@inguardians.com Frank DiMaggio frank@secureideas.net 1 Who are we? Kevin Johnson
Injectable Exploits New Tools for Pwning Web Apps and Browsers Kevin Johnson kevin@inguardians.com Justin Searle justin@inguardians.com Frank DiMaggio frank@secureideas.net 1 Who are we? Kevin Johnson
Creating SQL Server Stored Procedures CDS Brownbag Series CDS
 Creating SQL Server Stored Procedures Paul Litwin FHCRC Collaborative Data Services CDS Brownbag Series This is the 11th in a series of seminars Materials for the series can be downloaded from www.deeptraining.com/fhcrc
Creating SQL Server Stored Procedures Paul Litwin FHCRC Collaborative Data Services CDS Brownbag Series This is the 11th in a series of seminars Materials for the series can be downloaded from www.deeptraining.com/fhcrc
Content-Based Assessments
 A and B skills GO! Fix it Project H Annual Dinner For Project H, you will need the following database: ah_annual_dinner Lastname_Firstname_H_Annual_Dinner Lastname_Firstname_H_Screens Lastname_Firstname_H_ACCDE
A and B skills GO! Fix it Project H Annual Dinner For Project H, you will need the following database: ah_annual_dinner Lastname_Firstname_H_Annual_Dinner Lastname_Firstname_H_Screens Lastname_Firstname_H_ACCDE
CHAPTER 2 THEORETICAL FOUNDATION
 5 CHAPTER 2 THEORETICAL FOUNDATION 2.1 Theoretical Foundation This chapter covers about the appropriate theories that needed to be clarified in order to support the technique used to introduce network
5 CHAPTER 2 THEORETICAL FOUNDATION 2.1 Theoretical Foundation This chapter covers about the appropriate theories that needed to be clarified in order to support the technique used to introduce network
OWASP Broken Web Application Project. When Bad Web Apps are Good
 OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
FRAMEWORK VERSION 3.0 NETWORK INSTALLATION INSTALLING MICROSOFT STEP BY STEP INTERACTIVE TRAINING SOFTWARE
 FRAMEWORK VERSION 3.0 NETWORK INSTALLATION INSTALLING MICROSOFT STEP BY STEP INTERACTIVE TRAINING SOFTWARE The purpose of this document is to: Describe the components of Microsoft Interactive Training
FRAMEWORK VERSION 3.0 NETWORK INSTALLATION INSTALLING MICROSOFT STEP BY STEP INTERACTIVE TRAINING SOFTWARE The purpose of this document is to: Describe the components of Microsoft Interactive Training
Ebook : Overview of application development. All code from the application series books listed at:
 Ebook : Overview of application development. All code from the application series books listed at: http://www.vkinfotek.com with permission. Publishers: VK Publishers Established: 2001 Type of books: Develop
Ebook : Overview of application development. All code from the application series books listed at: http://www.vkinfotek.com with permission. Publishers: VK Publishers Established: 2001 Type of books: Develop
Book IX. Developing Applications Rapidly
 Book IX Developing Applications Rapidly Contents at a Glance Chapter 1: Building Master and Detail Pages Chapter 2: Creating Search and Results Pages Chapter 3: Building Record Insert Pages Chapter 4:
Book IX Developing Applications Rapidly Contents at a Glance Chapter 1: Building Master and Detail Pages Chapter 2: Creating Search and Results Pages Chapter 3: Building Record Insert Pages Chapter 4:
Engineering, Built Environment and IT Department of Computer Science MIT C Projects Portal User Manual
 Engineering, Built Environment and IT Department of Computer Science MIT C Projects Portal User Manual Last Update: 24 August 2017 1 Requesting an Account This section highlights the steps that are required
Engineering, Built Environment and IT Department of Computer Science MIT C Projects Portal User Manual Last Update: 24 August 2017 1 Requesting an Account This section highlights the steps that are required
Principles of Designing Secure Systems
 T H E U N I V E R S I T Y O F B R I T I S H C O L U M B I A Principles of Designing Secure Systems CPEN 442 learning objectives explain the principles recognize the principles in real-world designs explain
T H E U N I V E R S I T Y O F B R I T I S H C O L U M B I A Principles of Designing Secure Systems CPEN 442 learning objectives explain the principles recognize the principles in real-world designs explain
Stored Procedures and Functions. Rose-Hulman Institute of Technology Curt Clifton
 Stored Procedures and Functions Rose-Hulman Institute of Technology Curt Clifton Outline Stored Procedures or Sprocs Functions Statements Reference Defining Stored Procedures Named Collections of Transact-SQL
Stored Procedures and Functions Rose-Hulman Institute of Technology Curt Clifton Outline Stored Procedures or Sprocs Functions Statements Reference Defining Stored Procedures Named Collections of Transact-SQL
Database Table Editor for Excel. by Brent Larsen
 Database Table Editor for Excel by Brent Larsen Executive Summary This project is a database table editor that is geared toward those who use databases heavily, and in particular those who frequently insert,
Database Table Editor for Excel by Brent Larsen Executive Summary This project is a database table editor that is geared toward those who use databases heavily, and in particular those who frequently insert,
