TERNARY TREES USAGE FOR COMPUTATIONAL EXPERIMENT DATA STORAGE
|
|
|
- Cornelius Daniels
- 5 years ago
- Views:
Transcription
1 TERNARY TREES USAGE FOR COMPUTATIONAL EXPERIMENT DATA STORAGE A.N. Kovartsev 1, D.A. Popova-Kovartseva 1, E.E. Gorshkova 1 1 Samara National Research University, Samara, Russia Abstract. Repository for a great number of the suspected function runs must often be organized during the realization of numerical global optimization method or program modules testing methods. In this connection the problem of a fastaccess search of required element arises. A way to solve the problem can be found through the organization of an effective data repository, which allows for rapid implementation of the search and insertion of new elements. The binary and ternary trees storage options are considered in the paper, their comparison is made, recommendations for use of analyzed data models are reported. Keywords: binary trees, ternary trees, data structures, global optimization. Citation: Kovartsev AN, Popova-Kovartseva DA, Gorshkova ЕЕ. Ternary trees usage for computational experiment data storage. CEUR Workshop Proceedings, 2016; 1638: DOI: / Introduction Considerable volume of function "runs" must be stored during application of numerical global optimization method (GO) [1, 2] or program modules testing methods [3, 4]. The main requirement for GO algorithms and program modules testing methods is the speed of the algorithm. Let us assume that the computation time of function f (x) is sufficiently large. This situation is typical for solving optimization problems in technical systems design process, such as gas turbine engines, aircraft, etc. Some tests in the known GO algorithms are repeated in increments (for example, in bisection method or its modified version [5]) and that leads to redundant computation of f (x). A way to solve this problem can be found through the organization of an effective data repository allowing for rapid implementation of the search and insertion operations of new elements. 1 Disadvantages of traditional binary trees usage Let us agree, that by the test we mean function f (x) calculation at the point specified by optimization algorithm or function testing algorithm. Optimization methods Information Technology and Nanotechnology (ITNT-2016) 820
2 complexity is the total number of algorithm steps [6]. However, taking into account the high advanced computers performance, by optimization algorithms complexity it's more accurate to mean the total number of calls to the optimizable function, since the algorithm steps can have different complexity, and each function call takes the same amount of time for any algorithm. On the other hand, the number of function calls is independent of the computer processing power that allows comparing algorithms to be implemented on computers with different performance. At the same time, each function call may require significant computing time depending on the complexity of the test function. This article deals with the problem of data repository organizing for GO algorithm based on the modified bisection method (BM) [5]. In the BM algorithm the search space partitioning strategy may be defined as non-uniform space division with the use of regular structures (see [1]). However, it is necessary to compute the function at the same points of independent variables set. In order to avoid repeated calculations, it is expedient to store the point coordinates and function values at them in a separate data repository. Thus the data array may have considerable size. In this case there is the problem of finding an element in the array. For example, the average complexity of sequential search in an unordered and in an ordered array is O(n) [7]. Practically, binary trees (b-trees) are generally used to increase the efficiency of the search algorithm [8, 9]. Binary search for balanced binary trees [10] has an average complexity proportional to O (log 2 n) and depends on the depth of a binary tree. By the depth of a binary tree is generally understood [10] the number of nodes on the longest path from the root of the tree to its leaves. However, usage of binary trees for data storing at the test points of the tested or optimized function has its own aspects. In particular, a certain procedure of data entry or additional sorting of data is required to build an optimal balanced binary tree even for regular grids. For the irregular grids of experiment data sorting is essential. Figure 2 shows the balanced binary tree built for the regular grid (see. Fig. 1) using one of the rational methods of construction of the balanced binary tree. Fig. 1. Strategy of the balanced binary tree building on a regular grid In addition, computational experiment must comply with the sequence shown in Figure 1. The calculations start from a point with coordinates (2, 2). A binary tree shown in Figure 2 corresponds to this plan. Information Technology and Nanotechnology (ITNT-2016) 821
3 However, the gradual detalization of the search area is peculiar for BM, and it starts from a large sample spacing with a gradual decrease in specific fragments in the searching range. The range of search "densifies" nonuniformly here. In this case, it's impractical to achieve the balance of the binary tree, and this leads to efficiency loss of search algorithms. Figure 3 shows a binary tree corresponding to the experiment shown in Figure 4. Fig. 2. Balanced binary tree for 5*5 experiment grid Fig. 3. Binary tree for BM As can be seen from the figure binary tree becomes not balanced for irregular grid. One way to improve the efficiency of the search algorithm is to use more complex data structures, such as ternary trees (t-trees). Fig. 4. Construction of the balanced binary tree Information Technology and Nanotechnology (ITNT-2016) 822
4 2 Ternary trees Two ordering relationships ("<" and "> =" or "<=" and ">") are used to build a binary tree that allow to implement a procedure of binary division of the ordered set. Three conditions are required for the ternary tree construction which allow to split an ordered set into three parts. As such, will be the following conditions "<", "=" and ">". Points of the experiment will be organized by the following criterion z x y, i.e. by the sum of the experimental points coordinates. In general, points with coordinates that correspond to the condition of equality, not often encountered; in this case, a ternary tree is converted into binary. However, there is a fair amount of such points for regular grids. Points that satisfy the condition of equality are located on the diagonals ( x y const ) for 5 * 5 grid in figure 5. Fig. 5. Construction of the ternary tree The result is a t-tree, shown in Figure 6. The comparison between an average efficiency of search for b- and t-trees for different regular grids of partitioning the search space is of some interest. 2 Let n be a number of nodes of a regular grid for each coordinate, N n - the total number of grid nodes, k - the depth of a complete binary tree [10]. Fig. 6. Ternary tree for 5*5 experiment grid A binary tree is "complete" if both subtrees of all nodes are "balanced", i.e. they have approximately the same number of nodes [10]. The total number of nodes for a "complete" (balanced) b-tree can be calculated from k the formula [7] 2 1. Information Technology and Nanotechnology (ITNT-2016) 823
5 Suppose that the complete balanced tree is constructed for each regular grid, so that the first few levels except the last one are completely filled with nodes. Basically, it is impossible to build completely filled "balanced" trees for n n grid, because the number of elements in the grid and in complete binary tree does not match. For any number of elements (in this case the n n grid) the "complete" tree depth can be calculated from the formula: log 2 N, if log 2 N log 2 N, k log 2 N 1, else. On the assumption of equally probable binary tree filling with the information in the grid nodes we calculate the average complexity of the search on the "complete" b- 2 tree. For a grid with the number of elements N n, the elements of the "complete" k tree up to the depth k 1 will be completely filled. 2 elements are located on each k level of the binary tree. It is easy to show that for equally probable distribution of nodes of a regular grid in a binary tree the average complexity of search can be calculated using the following formula: 1 2 k B( N) ( k n ( k 1) 2 ). 2 n Unfortunately, "complete" balanced b-tree is generated only when the inclusion of grid elements into a binary tree has a certain order. In general, the search process can form linear structure with greater depth than the "complete" b-tree. Knuth [11] has shown that, if all possible options of elements inclusion (N!) into the binary tree are assumed to be equally probable, then the average depth of a binary search is N and averagely log 2 N comparisons are required per search. Figure 7 shows graphs of average search complexity. It can be seen, that the average complexity of the search of the "complete" binary tree is much smaller than in case of arbitrary filling of b-tree with grid elements. The ternary tree depth is almost the same as the dimension of the grid, as the tree depth cannot be less than the number of nodes on the grid diagonal because of the equality operation. It is much more difficult to calculate the average complexity of the search T(N) for a ternary tree. Figure 7 shows a graph of behavior T(N) of the number of grid elements resulted from the computing experiment for quasioptimal t-trees. Fig. 7. Comparison of the average complexity of the search on the b and t trees Information Technology and Nanotechnology (ITNT-2016) 824
6 As can be seen from the figure a ternary tree has disadvantages in the description of the regular grid of the experiment in comparison with optimal binary tree. However, a margin of free branches in the tree that can be filled with new grid nodes is very important in the nonlinear search space partitioning method when changing the sample spacing of the search space. In this regard, the binary tree loses much to t-tree, since b-tree branches are located at the last level of the tree. The reservation availability for new experimental points occurs in the t-tree, which do not increase the depth of search long enough. The latter happens because the operation of the equality "=" implements the partition of the grid points set into equivalence classes. All classes are comparable to operations "<" and ">" and form "branches" of equivalence. Grid densifying in separate squares leads to the appearance of new branches, that quickly find an empty place on a tree. The upper levels of binary trees tend to be already completed by this time and further development is possible only by increasing the depth of the tree. It is inappropriate to sort b-tree in order to improve its structure when the operations of element inserting and searching for an item in the tree are made at the same time. The fastest sorting algorithms require N log 2 N operations to improve the tree structure [12]. In this case, the efficiency of the dichotomous search on balanced b-tree will be lost due to the sort operations. Thus, ternary tree can be used as the data model of experimental points placement during software module testing. 3 The efficiency of the search algorithm in ternary tree research The efficiency of the search algorithm in ternary tree depends on the properties of the test function. We used 6 test functions with different topologies in the computational experiments and, therefore, different computational complexity in terms of solving the problem of GO. The functions are different: from relatively simple rational functions, more complex ravine functions, multiextremal functions (including discontinuous functions) to ROOT standard test functions offered on the site [13]. Figure 8 shows the results of computational experiments of the efficiency of the search algorithm in ternary tree research for the considered test functions. For clarity, dependency graphs of the average search length of optimal "complete" binary tree and evaluation of the same values for equally probable way of filling b-tree proposed by Knuth [11] are shown below. As can be seen from the figure, in most cases, the efficiency of the search on the t-tree is comparable with the average complexity of the search at the optimal binary tree. The latter is achieved due to the large number of ternary tree free connections, located on the upper levels. In general, the average search length of t-tree has an acceptable value for large volumes of stored data. In comparison it should be noted that t-tree was discussed in unsorted form, while b-tree, for the same amount of information was optimal and balanced. The latter means the high efficiency of the search on t-trees. Information Technology and Nanotechnology (ITNT-2016) 825
7 If we consider the relative average search length (ratio of the average search length to the total number of elements of the tree), then with increasing of the size of t-tree search efficiency only increases (see Fig. 9). Fig. 8. The efficiency of the search on the t-trees Fig. 9. The relative efficiency of the search on the t-trees Conclusion In this article, we considered the problem of data repository organization and data search algorithm on ternary trees, designed to serve the global optimization methods and function tests that require processing of large volumes of information. Using of ternary trees gives a number of advantages in comparison with traditional binary trees, as it does not require to perform a sort operation or balance the tree in order to improve the efficiency of the search on ternary trees, and the average complexity of the search is comparable to the efficiency of search on the binary optimal balanced tree. Information Technology and Nanotechnology (ITNT-2016) 826
8 Acknowledgements This work was supported by the state Ministry of Education and Science of the Russian Federation as part of the activities of the Program of competitiveness improving of SSAU among the world's leading research and education centers for References 1. Kovartsev AN, Popova-Kovartseva DA. On efficiency of parallel algorithms for global optimization of functions of several variables. Computer Optics, 2011; 35(2): [in Russian] 2. Kovartsev АN. A deterministic evolutionary algorithm for the global optimization of morse cluster. Computer Optics, 2014; 39(2): [in Russian] 3. Kovartsev AN, Popova-Kovartseva DA, Abolmasov PV. Efficiency study of global parallel optimization for multivariable function. Vestnik NNGU, 2013; 3(1): [in Russian] 4. Kovartsev АN. An efficient algorithm for testing the truth of assertions for real numbers expressed in relational signatures. Computer Optics, 2014; 38(3): [in Russian] 5. Kovartsev AN, Popova-Kovartseva DA, Gorshkova EE. Software testing based on global search of several variables functions discontinuity. Proceedings of International Conference Information Technology and Nanotechnology (ITNT-2015), 2015: Nemirovskij AS, Yudin DB. The complexity of the problems and the effectiveness of optimization methods. Moscow: Nauka, 1979; 384 p. [in Russian] 7. Makkonel J. Analysis of algorithms. Introductory course. Moscow: Tekhnosfera, 2002; 304 p. [in Russian] 8. Adamenko AN, Kuchukov AM. Logic programming and Visual Prolog. St. Petersburg: BHV- Peterburg, 2003; 992 p. [in Russian] 9. Ivanov BN. Discrete mathematics. Algoritms and programs. Moscow: Laboratoriya bazovyh znanij, 2001; 288 p. [in Russian] 10. Meyer B, Baldwin K. Programming methods. V. 2 (3). Moscow: Mir, 1982; 386 p. 11. Knuth D. Art of Computer Programming. Sorting and searching. V. 3. Moscow: Mir, 1978; 848 p. 12. Holl P. Computational structure. Introduction to nonnumerical programming. Moscow: Mir, 1978; 216 p. 13. Global optimization algorithms. Sourse: < Information Technology and Nanotechnology (ITNT-2016) 827
DEVELOPMENT OF THE EFFECTIVE SET OF FEATURES CONSTRUCTION TECHNOLOGY FOR TEXTURE IMAGE CLASSES DISCRIMINATION
 DEVELOPMENT OF THE EFFECTIVE SET OF FEATURES CONSTRUCTION TECHNOLOGY FOR TEXTURE IMAGE CLASSES DISCRIMINATION E. Biryukova 1, R. Paringer 1,2, A.V. Kupriyanov 1,2 1 Samara National Research University,
DEVELOPMENT OF THE EFFECTIVE SET OF FEATURES CONSTRUCTION TECHNOLOGY FOR TEXTURE IMAGE CLASSES DISCRIMINATION E. Biryukova 1, R. Paringer 1,2, A.V. Kupriyanov 1,2 1 Samara National Research University,
DIFFERENTIAL IMAGE COMPRESSION BASED ON ADAPTIVE PREDICTION
 DIFFERENTIAL IMAGE COMPRESSION BASED ON ADAPTIVE PREDICTION M.V. Gashnikov Samara National Research University, Samara, Russia Abstract. The paper describes the adaptive prediction algorithm for differential
DIFFERENTIAL IMAGE COMPRESSION BASED ON ADAPTIVE PREDICTION M.V. Gashnikov Samara National Research University, Samara, Russia Abstract. The paper describes the adaptive prediction algorithm for differential
IMPULSE RESPONSE IDENTIFICATION BY ENERGY SPECTRUM METHOD USING GEOINFORMATION DATA IN CASE OF REMOTE SENSING IMAGES
 IMPULSE RESPONSE IDENTIFICATION BY ENERGY SPECTRUM METHOD USING GEOINFORMATION DATA IN CASE OF REMOTE SENSING IMAGES A.Y. Denisova, V.V. Sergeyev Samara National Research University, Samara, Russia Abstract.
IMPULSE RESPONSE IDENTIFICATION BY ENERGY SPECTRUM METHOD USING GEOINFORMATION DATA IN CASE OF REMOTE SENSING IMAGES A.Y. Denisova, V.V. Sergeyev Samara National Research University, Samara, Russia Abstract.
REAL-TIME ROAD SIGNS RECOGNITION USING MOBILE GPU
 High-Performance Сomputing REAL-TIME ROAD SIGNS RECOGNITION USING MOBILE GPU P.Y. Yakimov Samara National Research University, Samara, Russia Abstract. This article shows an effective implementation of
High-Performance Сomputing REAL-TIME ROAD SIGNS RECOGNITION USING MOBILE GPU P.Y. Yakimov Samara National Research University, Samara, Russia Abstract. This article shows an effective implementation of
Optimization of thread affinity and memory affinity for remote core locking synchronization in multithreaded programs for multicore computer systems
 Optimization of thread affinity and memory affinity for remote core locking synchronization in multithreaded programs for multicore computer systems Alexey Paznikov Saint Petersburg Electrotechnical University
Optimization of thread affinity and memory affinity for remote core locking synchronization in multithreaded programs for multicore computer systems Alexey Paznikov Saint Petersburg Electrotechnical University
Data Structures And Algorithms
 Data Structures And Algorithms Hashing Eng. Anis Nazer First Semester 2017-2018 Searching Search: find if a key exists in a given set Searching algorithms: linear (sequential) search binary search Search
Data Structures And Algorithms Hashing Eng. Anis Nazer First Semester 2017-2018 Searching Search: find if a key exists in a given set Searching algorithms: linear (sequential) search binary search Search
Genetic algorithms for the synthesis optimization of a set of irredundant diagnostic tests in the intelligent system
 Computer Science Journal of Moldova, vol.9, no.3(27), 2001 Genetic algorithms for the synthesis optimization of a set of irredundant diagnostic tests in the intelligent system Anna E. Yankovskaya Alex
Computer Science Journal of Moldova, vol.9, no.3(27), 2001 Genetic algorithms for the synthesis optimization of a set of irredundant diagnostic tests in the intelligent system Anna E. Yankovskaya Alex
Chapter 11: Indexing and Hashing
 Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 11: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Hashing Techniques. Material based on slides by George Bebis
 Hashing Techniques Material based on slides by George Bebis https://www.cse.unr.edu/~bebis/cs477/lect/hashing.ppt The Search Problem Find items with keys matching a given search key Given an array A, containing
Hashing Techniques Material based on slides by George Bebis https://www.cse.unr.edu/~bebis/cs477/lect/hashing.ppt The Search Problem Find items with keys matching a given search key Given an array A, containing
Probability-theoretical model for product assembly parameters assessment
 Probability-theoretical model for product assembly parameters assessment N.V. Ruzanov, М.А. Bolotov, V.А. Pechenin Samara National Research University, 34 Moskovskoe Shosse, 443086, Samara, Russia Abstract
Probability-theoretical model for product assembly parameters assessment N.V. Ruzanov, М.А. Bolotov, V.А. Pechenin Samara National Research University, 34 Moskovskoe Shosse, 443086, Samara, Russia Abstract
and Photonics" of Russian Academy of Sciences, Samara, Russia
 APPLICATION OF THE METHOD OF PYRAMID FOR SYNTHESIS OF PARALLEL ALGORITHM FOR DIFFERENCE SOLUTION OF THE TWO- DIMENSIONAL PARTIAL DIFFERENTIALS EQUATION D.L. Golovashkin 1,2, L.V. Yablokova 1, E.V. Belova
APPLICATION OF THE METHOD OF PYRAMID FOR SYNTHESIS OF PARALLEL ALGORITHM FOR DIFFERENCE SOLUTION OF THE TWO- DIMENSIONAL PARTIAL DIFFERENTIALS EQUATION D.L. Golovashkin 1,2, L.V. Yablokova 1, E.V. Belova
TABLES AND HASHING. Chapter 13
 Data Structures Dr Ahmed Rafat Abas Computer Science Dept, Faculty of Computer and Information, Zagazig University arabas@zu.edu.eg http://www.arsaliem.faculty.zu.edu.eg/ TABLES AND HASHING Chapter 13
Data Structures Dr Ahmed Rafat Abas Computer Science Dept, Faculty of Computer and Information, Zagazig University arabas@zu.edu.eg http://www.arsaliem.faculty.zu.edu.eg/ TABLES AND HASHING Chapter 13
Module 5: Hashing. CS Data Structures and Data Management. Reza Dorrigiv, Daniel Roche. School of Computer Science, University of Waterloo
 Module 5: Hashing CS 240 - Data Structures and Data Management Reza Dorrigiv, Daniel Roche School of Computer Science, University of Waterloo Winter 2010 Reza Dorrigiv, Daniel Roche (CS, UW) CS240 - Module
Module 5: Hashing CS 240 - Data Structures and Data Management Reza Dorrigiv, Daniel Roche School of Computer Science, University of Waterloo Winter 2010 Reza Dorrigiv, Daniel Roche (CS, UW) CS240 - Module
PARTICLE SWARM OPTIMIZATION FOR MULTIDIMENSIONAL CLUSTERING OF NATURAL LANGUAGE DATA
 International Journal of Civil Engineering and Technology (IJCIET) Volume 9, Issue 11, November 2018, pp. 139 149, Article ID: IJCIET_09_11_014 Available online at http://www.iaeme.com/ijciet/issues.asp?jtype=ijciet&vtype=9&itype=11
International Journal of Civil Engineering and Technology (IJCIET) Volume 9, Issue 11, November 2018, pp. 139 149, Article ID: IJCIET_09_11_014 Available online at http://www.iaeme.com/ijciet/issues.asp?jtype=ijciet&vtype=9&itype=11
Final drive lubrication modeling
 Final drive lubrication modeling E. Avdeev a,b 1, V. Ovchinnikov b a Samara University, b Laduga Automotive Engineering Abstract. In this paper we describe the method, which is the composition of finite
Final drive lubrication modeling E. Avdeev a,b 1, V. Ovchinnikov b a Samara University, b Laduga Automotive Engineering Abstract. In this paper we describe the method, which is the composition of finite
Quick-Sort. Quick-Sort 1
 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Quick-Sort 1 Outline and Reading Quick-sort ( 4.3) Algorithm Partition step Quick-sort tree Execution example Analysis of quick-sort (4.3.1) In-place
Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Quick-Sort 1 Outline and Reading Quick-sort ( 4.3) Algorithm Partition step Quick-sort tree Execution example Analysis of quick-sort (4.3.1) In-place
QuickSort
 QuickSort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 1 QuickSort QuickSort on an input sequence S with n elements consists of three steps: n n n Divide: partition S into two sequences S 1 and S 2 of about
QuickSort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 1 QuickSort QuickSort on an input sequence S with n elements consists of three steps: n n n Divide: partition S into two sequences S 1 and S 2 of about
Fundamental mathematical techniques reviewed: Mathematical induction Recursion. Typically taught in courses such as Calculus and Discrete Mathematics.
 Fundamental mathematical techniques reviewed: Mathematical induction Recursion Typically taught in courses such as Calculus and Discrete Mathematics. Techniques introduced: Divide-and-Conquer Algorithms
Fundamental mathematical techniques reviewed: Mathematical induction Recursion Typically taught in courses such as Calculus and Discrete Mathematics. Techniques introduced: Divide-and-Conquer Algorithms
A Secondary storage Algorithms and Data Structures Supplementary Questions and Exercises
 308-420A Secondary storage Algorithms and Data Structures Supplementary Questions and Exercises Section 1.2 4, Logarithmic Files Logarithmic Files 1. A B-tree of height 6 contains 170,000 nodes with an
308-420A Secondary storage Algorithms and Data Structures Supplementary Questions and Exercises Section 1.2 4, Logarithmic Files Logarithmic Files 1. A B-tree of height 6 contains 170,000 nodes with an
Question Bank Subject: Advanced Data Structures Class: SE Computer
 Question Bank Subject: Advanced Data Structures Class: SE Computer Question1: Write a non recursive pseudo code for post order traversal of binary tree Answer: Pseudo Code: 1. Push root into Stack_One.
Question Bank Subject: Advanced Data Structures Class: SE Computer Question1: Write a non recursive pseudo code for post order traversal of binary tree Answer: Pseudo Code: 1. Push root into Stack_One.
Fast algorithm for generating ascending compositions
 manuscript No. (will be inserted by the editor) Fast algorithm for generating ascending compositions Mircea Merca Received: date / Accepted: date Abstract In this paper we give a fast algorithm to generate
manuscript No. (will be inserted by the editor) Fast algorithm for generating ascending compositions Mircea Merca Received: date / Accepted: date Abstract In this paper we give a fast algorithm to generate
6. Parallel Volume Rendering Algorithms
 6. Parallel Volume Algorithms This chapter introduces a taxonomy of parallel volume rendering algorithms. In the thesis statement we claim that parallel algorithms may be described by "... how the tasks
6. Parallel Volume Algorithms This chapter introduces a taxonomy of parallel volume rendering algorithms. In the thesis statement we claim that parallel algorithms may be described by "... how the tasks
UNIT-2. Problem of size n. Sub-problem 1 size n/2. Sub-problem 2 size n/2. Solution to the original problem
 Divide-and-conquer method: Divide-and-conquer is probably the best known general algorithm design technique. The principle behind the Divide-and-conquer algorithm design technique is that it is easier
Divide-and-conquer method: Divide-and-conquer is probably the best known general algorithm design technique. The principle behind the Divide-and-conquer algorithm design technique is that it is easier
4.1.2 Merge Sort Sorting Lower Bound Counting Sort Sorting in Practice Solving Problems by Sorting...
 Contents 1 Introduction... 1 1.1 What is Competitive Programming?... 1 1.1.1 Programming Contests.... 2 1.1.2 Tips for Practicing.... 3 1.2 About This Book... 3 1.3 CSES Problem Set... 5 1.4 Other Resources...
Contents 1 Introduction... 1 1.1 What is Competitive Programming?... 1 1.1.1 Programming Contests.... 2 1.1.2 Tips for Practicing.... 3 1.2 About This Book... 3 1.3 CSES Problem Set... 5 1.4 Other Resources...
[10] Industrial DataMatrix barcodes recognition with a random tilt and rotating the camera
![[10] Industrial DataMatrix barcodes recognition with a random tilt and rotating the camera [10] Industrial DataMatrix barcodes recognition with a random tilt and rotating the camera](/thumbs/84/90637441.jpg) [10] Industrial DataMatrix barcodes recognition with a random tilt and rotating the camera Image processing, pattern recognition 865 Kruchinin A.Yu. Orenburg State University IntBuSoft Ltd Abstract The
[10] Industrial DataMatrix barcodes recognition with a random tilt and rotating the camera Image processing, pattern recognition 865 Kruchinin A.Yu. Orenburg State University IntBuSoft Ltd Abstract The
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 2015 Goodrich and Tamassia
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 2015 Goodrich and Tamassia
Sorting Goodrich, Tamassia Sorting 1
 Sorting Put array A of n numbers in increasing order. A core algorithm with many applications. Simple algorithms are O(n 2 ). Optimal algorithms are O(n log n). We will see O(n) for restricted input in
Sorting Put array A of n numbers in increasing order. A core algorithm with many applications. Simple algorithms are O(n 2 ). Optimal algorithms are O(n log n). We will see O(n) for restricted input in
Optical Microscopy and Metallography: Recognition of Metal Structures using Customizable Automatic Qualifiers
 ECNDT 2006 - Poster 68 Optical Microscopy and Metallography: Recognition of Metal Structures using Customizable Automatic Qualifiers Mikhail V. FILINOV, Andrey S. FURSOV, Association SPEKTR_GROUP, Moscow,
ECNDT 2006 - Poster 68 Optical Microscopy and Metallography: Recognition of Metal Structures using Customizable Automatic Qualifiers Mikhail V. FILINOV, Andrey S. FURSOV, Association SPEKTR_GROUP, Moscow,
University of Waterloo Department of Electrical and Computer Engineering ECE 250 Data Structures and Algorithms. Final Examination T09:00
 University of Waterloo Department of Electrical and Computer Engineering ECE 250 Data Structures and Algorithms Instructor: Douglas Wilhelm Harder Time: 2.5 hours Aides: none 18 pages Final Examination
University of Waterloo Department of Electrical and Computer Engineering ECE 250 Data Structures and Algorithms Instructor: Douglas Wilhelm Harder Time: 2.5 hours Aides: none 18 pages Final Examination
Data Mining. 3.3 Rule-Based Classification. Fall Instructor: Dr. Masoud Yaghini. Rule-Based Classification
 Data Mining 3.3 Fall 2008 Instructor: Dr. Masoud Yaghini Outline Using IF-THEN Rules for Classification Rules With Exceptions Rule Extraction from a Decision Tree 1R Algorithm Sequential Covering Algorithms
Data Mining 3.3 Fall 2008 Instructor: Dr. Masoud Yaghini Outline Using IF-THEN Rules for Classification Rules With Exceptions Rule Extraction from a Decision Tree 1R Algorithm Sequential Covering Algorithms
CPSC 311: Analysis of Algorithms (Honors) Exam 1 October 11, 2002
 CPSC 311: Analysis of Algorithms (Honors) Exam 1 October 11, 2002 Name: Instructions: 1. This is a closed book exam. Do not use any notes or books, other than your 8.5-by-11 inch review sheet. Do not confer
CPSC 311: Analysis of Algorithms (Honors) Exam 1 October 11, 2002 Name: Instructions: 1. This is a closed book exam. Do not use any notes or books, other than your 8.5-by-11 inch review sheet. Do not confer
Hashing. Dr. Ronaldo Menezes Hugo Serrano. Ronaldo Menezes, Florida Tech
 Hashing Dr. Ronaldo Menezes Hugo Serrano Agenda Motivation Prehash Hashing Hash Functions Collisions Separate Chaining Open Addressing Motivation Hash Table Its one of the most important data structures
Hashing Dr. Ronaldo Menezes Hugo Serrano Agenda Motivation Prehash Hashing Hash Functions Collisions Separate Chaining Open Addressing Motivation Hash Table Its one of the most important data structures
Quick-Sort fi fi fi 7 9. Quick-Sort Goodrich, Tamassia
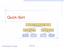 Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
Chapter 12: Indexing and Hashing. Basic Concepts
 Chapter 12: Indexing and Hashing! Basic Concepts! Ordered Indices! B+-Tree Index Files! B-Tree Index Files! Static Hashing! Dynamic Hashing! Comparison of Ordered Indexing and Hashing! Index Definition
Chapter 12: Indexing and Hashing! Basic Concepts! Ordered Indices! B+-Tree Index Files! B-Tree Index Files! Static Hashing! Dynamic Hashing! Comparison of Ordered Indexing and Hashing! Index Definition
ANALYSIS OF THE FEATURES OF THE OPTIMAL LOGICAL STRUCTURE OF DISTRIBUTED DATABASES
 ANALYSIS OF THE FEATURES OF THE OPTIMAL LOGICAL STRUCTURE OF DISTRIBUTED DATABASES E.V. Nurmatova 1,a, V.V. Gusev 2, V.V. Kotliar 2 1 «MIREA Russian Technological University», Moscow 2 NRC "Kurchatov Institute"
ANALYSIS OF THE FEATURES OF THE OPTIMAL LOGICAL STRUCTURE OF DISTRIBUTED DATABASES E.V. Nurmatova 1,a, V.V. Gusev 2, V.V. Kotliar 2 1 «MIREA Russian Technological University», Moscow 2 NRC "Kurchatov Institute"
Hash Tables. CS 311 Data Structures and Algorithms Lecture Slides. Wednesday, April 22, Glenn G. Chappell
 Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
Hash Tables CS 311 Data Structures and Algorithms Lecture Slides Wednesday, April 22, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005
CSE548, AMS542: Analysis of Algorithms, Fall 2012 Date: October 16. In-Class Midterm. ( 11:35 AM 12:50 PM : 75 Minutes )
 CSE548, AMS542: Analysis of Algorithms, Fall 2012 Date: October 16 In-Class Midterm ( 11:35 AM 12:50 PM : 75 Minutes ) This exam will account for either 15% or 30% of your overall grade depending on your
CSE548, AMS542: Analysis of Algorithms, Fall 2012 Date: October 16 In-Class Midterm ( 11:35 AM 12:50 PM : 75 Minutes ) This exam will account for either 15% or 30% of your overall grade depending on your
CSC Design and Analysis of Algorithms. Lecture 5. Decrease and Conquer Algorithm Design Technique. Decrease-and-Conquer
 CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conquer Algorithm Design Technique Decrease-and-Conquer This algorithm design technique is based on exploiting a relationship between
CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conquer Algorithm Design Technique Decrease-and-Conquer This algorithm design technique is based on exploiting a relationship between
ASSOCIATIVE COPROCESSOR BLOCK BASED ON PLD FOR DIFFERENT COMPUTER SYSTEMS
 ASSOCIATIVE COPROCESSOR BLOCK BASED ON PLD FOR DIFFERENT COMPUTER SYSTEMS Martyshkin A. I. Penza State Technological University, Russia, Baydukov Proyezd / Gagarin Street, 1a/11, Penza, Penza Region, Russia
ASSOCIATIVE COPROCESSOR BLOCK BASED ON PLD FOR DIFFERENT COMPUTER SYSTEMS Martyshkin A. I. Penza State Technological University, Russia, Baydukov Proyezd / Gagarin Street, 1a/11, Penza, Penza Region, Russia
Chapter 12: Indexing and Hashing
 Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition in SQL
Chapter 12: Indexing and Hashing
 Chapter 12: Indexing and Hashing Database System Concepts, 5th Ed. See www.db-book.com for conditions on re-use Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree
Chapter 12: Indexing and Hashing Database System Concepts, 5th Ed. See www.db-book.com for conditions on re-use Chapter 12: Indexing and Hashing Basic Concepts Ordered Indices B + -Tree Index Files B-Tree
Decision tree learning
 Decision tree learning Andrea Passerini passerini@disi.unitn.it Machine Learning Learning the concept Go to lesson OUTLOOK Rain Overcast Sunny TRANSPORTATION LESSON NO Uncovered Covered Theoretical Practical
Decision tree learning Andrea Passerini passerini@disi.unitn.it Machine Learning Learning the concept Go to lesson OUTLOOK Rain Overcast Sunny TRANSPORTATION LESSON NO Uncovered Covered Theoretical Practical
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute. Week 02 Module 06 Lecture - 14 Merge Sort: Analysis
 Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Week 02 Module 06 Lecture - 14 Merge Sort: Analysis So, we have seen how to use a divide and conquer strategy, we
Design and Analysis of Algorithms Prof. Madhavan Mukund Chennai Mathematical Institute Week 02 Module 06 Lecture - 14 Merge Sort: Analysis So, we have seen how to use a divide and conquer strategy, we
Digital Halftoning Algorithm Based o Space-Filling Curve
 JAIST Reposi https://dspace.j Title Digital Halftoning Algorithm Based o Space-Filling Curve Author(s)ASANO, Tetsuo Citation IEICE TRANSACTIONS on Fundamentals o Electronics, Communications and Comp Sciences,
JAIST Reposi https://dspace.j Title Digital Halftoning Algorithm Based o Space-Filling Curve Author(s)ASANO, Tetsuo Citation IEICE TRANSACTIONS on Fundamentals o Electronics, Communications and Comp Sciences,
Symbol Table. Symbol table is used widely in many applications. dictionary is a kind of symbol table data dictionary is database management
 Hashing Symbol Table Symbol table is used widely in many applications. dictionary is a kind of symbol table data dictionary is database management In general, the following operations are performed on
Hashing Symbol Table Symbol table is used widely in many applications. dictionary is a kind of symbol table data dictionary is database management In general, the following operations are performed on
Matching on Graphs II. STATEMENT OF THE TASK. GENERAL IDEA OF THE ALGORITHM OF SEARCH OF MATCHING
 Matching on Graphs Shut V N ), Svirski V M ), Solomiyuk K S ), Gryazev E V 4) ) Brest State Technical University, Belarus Moskowskaja 67, 407 Brest, Belarus rolly@mailru ) Brest State Technical University,Belarus
Matching on Graphs Shut V N ), Svirski V M ), Solomiyuk K S ), Gryazev E V 4) ) Brest State Technical University, Belarus Moskowskaja 67, 407 Brest, Belarus rolly@mailru ) Brest State Technical University,Belarus
Determination of an Unmanned Mobile Object Orientation by Natural Landmarks
 Determination of an Unmanned Mobile Object Orientation by Natural Landmarks Anton M. Korsakov, Ivan S. Fomin, Dmitry A. Gromoshinsky, Alexandr V. Bakhshiev, Dmitrii N. Stepanov, EkaterinaY. Smirnova 1
Determination of an Unmanned Mobile Object Orientation by Natural Landmarks Anton M. Korsakov, Ivan S. Fomin, Dmitry A. Gromoshinsky, Alexandr V. Bakhshiev, Dmitrii N. Stepanov, EkaterinaY. Smirnova 1
1 The range query problem
 CS268: Geometric Algorithms Handout #12 Design and Analysis Original Handout #12 Stanford University Thursday, 19 May 1994 Original Lecture #12: Thursday, May 19, 1994 Topics: Range Searching with Partition
CS268: Geometric Algorithms Handout #12 Design and Analysis Original Handout #12 Stanford University Thursday, 19 May 1994 Original Lecture #12: Thursday, May 19, 1994 Topics: Range Searching with Partition
Algorithms in Systems Engineering ISE 172. Lecture 12. Dr. Ted Ralphs
 Algorithms in Systems Engineering ISE 172 Lecture 12 Dr. Ted Ralphs ISE 172 Lecture 12 1 References for Today s Lecture Required reading Chapter 5 References CLRS Chapter 11 D.E. Knuth, The Art of Computer
Algorithms in Systems Engineering ISE 172 Lecture 12 Dr. Ted Ralphs ISE 172 Lecture 12 1 References for Today s Lecture Required reading Chapter 5 References CLRS Chapter 11 D.E. Knuth, The Art of Computer
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK ENHANCED DATA REPLICATION TECHNIQUES FOR DISTRIBUTED DATABASES SANDIP PANDURANG
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK ENHANCED DATA REPLICATION TECHNIQUES FOR DISTRIBUTED DATABASES SANDIP PANDURANG
Decision trees. Decision trees are useful to a large degree because of their simplicity and interpretability
 Decision trees A decision tree is a method for classification/regression that aims to ask a few relatively simple questions about an input and then predicts the associated output Decision trees are useful
Decision trees A decision tree is a method for classification/regression that aims to ask a few relatively simple questions about an input and then predicts the associated output Decision trees are useful
15 Data Compression 2014/9/21. Objectives After studying this chapter, the student should be able to: 15-1 LOSSLESS COMPRESSION
 15 Data Compression Data compression implies sending or storing a smaller number of bits. Although many methods are used for this purpose, in general these methods can be divided into two broad categories:
15 Data Compression Data compression implies sending or storing a smaller number of bits. Although many methods are used for this purpose, in general these methods can be divided into two broad categories:
CSE 100: B+ TREE, 2-3 TREE, NP- COMPLETNESS
 CSE 100: B+ TREE, 2-3 TREE, NP- COMPLETNESS Analyzing find in B-trees Since the B-tree is perfectly height-balanced, the worst case time cost for find is O(logN) Best case: If every internal node is completely
CSE 100: B+ TREE, 2-3 TREE, NP- COMPLETNESS Analyzing find in B-trees Since the B-tree is perfectly height-balanced, the worst case time cost for find is O(logN) Best case: If every internal node is completely
Lecture 1. 1 Notation
 Lecture 1 (The material on mathematical logic is covered in the textbook starting with Chapter 5; however, for the first few lectures, I will be providing some required background topics and will not be
Lecture 1 (The material on mathematical logic is covered in the textbook starting with Chapter 5; however, for the first few lectures, I will be providing some required background topics and will not be
Dr. Amotz Bar-Noy s Compendium of Algorithms Problems. Problems, Hints, and Solutions
 Dr. Amotz Bar-Noy s Compendium of Algorithms Problems Problems, Hints, and Solutions Chapter 1 Searching and Sorting Problems 1 1.1 Array with One Missing 1.1.1 Problem Let A = A[1],..., A[n] be an array
Dr. Amotz Bar-Noy s Compendium of Algorithms Problems Problems, Hints, and Solutions Chapter 1 Searching and Sorting Problems 1 1.1 Array with One Missing 1.1.1 Problem Let A = A[1],..., A[n] be an array
Outline. The History of Histograms. Yannis Ioannidis University of Athens, Hellas
 The History of Histograms Yannis Ioannidis University of Athens, Hellas Outline Prehistory Definitions and Framework The Early Past 10 Years Ago The Recent Past Industry Competitors The Future Prehistory
The History of Histograms Yannis Ioannidis University of Athens, Hellas Outline Prehistory Definitions and Framework The Early Past 10 Years Ago The Recent Past Industry Competitors The Future Prehistory
Review: Final Exam CPSC Artificial Intelligence Michael M. Richter
 Review: Final Exam Model for a Learning Step Learner initially Environm ent Teacher Compare s pe c ia l Information Control Correct Learning criteria Feedback changed Learner after Learning Learning by
Review: Final Exam Model for a Learning Step Learner initially Environm ent Teacher Compare s pe c ia l Information Control Correct Learning criteria Feedback changed Learner after Learning Learning by
NUMERICAL METHODS PERFORMANCE OPTIMIZATION IN ELECTROLYTES PROPERTIES MODELING
 NUMERICAL METHODS PERFORMANCE OPTIMIZATION IN ELECTROLYTES PROPERTIES MODELING Dmitry Potapov National Research Nuclear University MEPHI, Russia, Moscow, Kashirskoe Highway, The European Laboratory for
NUMERICAL METHODS PERFORMANCE OPTIMIZATION IN ELECTROLYTES PROPERTIES MODELING Dmitry Potapov National Research Nuclear University MEPHI, Russia, Moscow, Kashirskoe Highway, The European Laboratory for
Generalized Coordinates for Cellular Automata Grids
 Generalized Coordinates for Cellular Automata Grids Lev Naumov Saint-Peterburg State Institute of Fine Mechanics and Optics, Computer Science Department, 197101 Sablinskaya st. 14, Saint-Peterburg, Russia
Generalized Coordinates for Cellular Automata Grids Lev Naumov Saint-Peterburg State Institute of Fine Mechanics and Optics, Computer Science Department, 197101 Sablinskaya st. 14, Saint-Peterburg, Russia
Friday Four Square! 4:15PM, Outside Gates
 Binary Search Trees Friday Four Square! 4:15PM, Outside Gates Implementing Set On Monday and Wednesday, we saw how to implement the Map and Lexicon, respectively. Let's now turn our attention to the Set.
Binary Search Trees Friday Four Square! 4:15PM, Outside Gates Implementing Set On Monday and Wednesday, we saw how to implement the Map and Lexicon, respectively. Let's now turn our attention to the Set.
SHARED MEMORY VS DISTRIBUTED MEMORY
 OVERVIEW Important Processor Organizations 3 SHARED MEMORY VS DISTRIBUTED MEMORY Classical parallel algorithms were discussed using the shared memory paradigm. In shared memory parallel platform processors
OVERVIEW Important Processor Organizations 3 SHARED MEMORY VS DISTRIBUTED MEMORY Classical parallel algorithms were discussed using the shared memory paradigm. In shared memory parallel platform processors
Comparison Sorts. Chapter 9.4, 12.1, 12.2
 Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Parallel Sorting Algorithms
 CSC 391/691: GPU Programming Fall 015 Parallel Sorting Algorithms Copyright 015 Samuel S. Cho Sorting Algorithms Review Bubble Sort: O(n ) Insertion Sort: O(n ) Quick Sort: O(n log n) Heap Sort: O(n log
CSC 391/691: GPU Programming Fall 015 Parallel Sorting Algorithms Copyright 015 Samuel S. Cho Sorting Algorithms Review Bubble Sort: O(n ) Insertion Sort: O(n ) Quick Sort: O(n log n) Heap Sort: O(n log
Parallel and Sequential Data Structures and Algorithms Lecture (Spring 2012) Lecture 16 Treaps; Augmented BSTs
 Lecture 16 Treaps; Augmented BSTs Parallel and Sequential Data Structures and Algorithms, 15-210 (Spring 2012) Lectured by Margaret Reid-Miller 8 March 2012 Today: - More on Treaps - Ordered Sets and Tables
Lecture 16 Treaps; Augmented BSTs Parallel and Sequential Data Structures and Algorithms, 15-210 (Spring 2012) Lectured by Margaret Reid-Miller 8 March 2012 Today: - More on Treaps - Ordered Sets and Tables
Hashing for searching
 Hashing for searching Consider searching a database of records on a given key. There are three standard techniques: Searching sequentially start at the first record and look at each record in turn until
Hashing for searching Consider searching a database of records on a given key. There are three standard techniques: Searching sequentially start at the first record and look at each record in turn until
Radix Searching. The insert procedure for digital search trees also derives directly from the corresponding procedure for binary search trees:
 Radix Searching The most simple radix search method is digital tree searching - the binary search tree with the branch in the tree according to the bits of keys: at the first level the leading bit is used,
Radix Searching The most simple radix search method is digital tree searching - the binary search tree with the branch in the tree according to the bits of keys: at the first level the leading bit is used,
MID TERM MEGA FILE SOLVED BY VU HELPER Which one of the following statement is NOT correct.
 MID TERM MEGA FILE SOLVED BY VU HELPER Which one of the following statement is NOT correct. In linked list the elements are necessarily to be contiguous In linked list the elements may locate at far positions
MID TERM MEGA FILE SOLVED BY VU HELPER Which one of the following statement is NOT correct. In linked list the elements are necessarily to be contiguous In linked list the elements may locate at far positions
Some questions of consensus building using co-association
 Some questions of consensus building using co-association VITALIY TAYANOV Polish-Japanese High School of Computer Technics Aleja Legionow, 4190, Bytom POLAND vtayanov@yahoo.com Abstract: In this paper
Some questions of consensus building using co-association VITALIY TAYANOV Polish-Japanese High School of Computer Technics Aleja Legionow, 4190, Bytom POLAND vtayanov@yahoo.com Abstract: In this paper
Quick-Sort. Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm:
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9
Algorithm for encoding nd spatial objects into GIS
 Algorithm for encoding nd spatial objects into GIS D E Andrianov 1, S V Eremeev 1, Y A Kovalev 1 and K V Kuptsov 1 1 State University named after Alexander Grigorievich and Nikolai Grigorievich Stoletov,
Algorithm for encoding nd spatial objects into GIS D E Andrianov 1, S V Eremeev 1, Y A Kovalev 1 and K V Kuptsov 1 1 State University named after Alexander Grigorievich and Nikolai Grigorievich Stoletov,
INF2220: algorithms and data structures Series 1
 Universitetet i Oslo Institutt for Informatikk I. Yu, D. Karabeg INF2220: algorithms and data structures Series 1 Topic Function growth & estimation of running time, trees Issued: 24. 08. 2016 Exercise
Universitetet i Oslo Institutt for Informatikk I. Yu, D. Karabeg INF2220: algorithms and data structures Series 1 Topic Function growth & estimation of running time, trees Issued: 24. 08. 2016 Exercise
UNIT III BALANCED SEARCH TREES AND INDEXING
 UNIT III BALANCED SEARCH TREES AND INDEXING OBJECTIVE The implementation of hash tables is frequently called hashing. Hashing is a technique used for performing insertions, deletions and finds in constant
UNIT III BALANCED SEARCH TREES AND INDEXING OBJECTIVE The implementation of hash tables is frequently called hashing. Hashing is a technique used for performing insertions, deletions and finds in constant
Innovating R Tree for Message Forwarding Technique and Hierarchical Network Clustering in Service Based Routing
 Internet of Things and Cloud Computing 2015; 3(3): 59-65 Published online October 11, 2015 (http://www.sciencepublishinggroup.com/j/iotcc) doi: 10.11648/j.iotcc.s.2015030601.17 ISSN: 2376-7715 (Print);
Internet of Things and Cloud Computing 2015; 3(3): 59-65 Published online October 11, 2015 (http://www.sciencepublishinggroup.com/j/iotcc) doi: 10.11648/j.iotcc.s.2015030601.17 ISSN: 2376-7715 (Print);
Available online at ScienceDirect. Procedia Computer Science 103 (2017 )
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 103 (2017 ) 505 510 XIIth International Symposium «Intelligent Systems», INTELS 16, 5-7 October 2016, Moscow, Russia Network-centric
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 103 (2017 ) 505 510 XIIth International Symposium «Intelligent Systems», INTELS 16, 5-7 October 2016, Moscow, Russia Network-centric
CS61B Spring 2016 Guerrilla Section 6 Worksheet
 Spring 2016 5 May 2016 Directions: In groups of 4-5, work on the following exercises. Do not proceed to the next exercise until everyone in your group has the answer and understands why the answer is what
Spring 2016 5 May 2016 Directions: In groups of 4-5, work on the following exercises. Do not proceed to the next exercise until everyone in your group has the answer and understands why the answer is what
Chapter 12: Indexing and Hashing (Cnt(
 Chapter 12: Indexing and Hashing (Cnt( Cnt.) Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition
Chapter 12: Indexing and Hashing (Cnt( Cnt.) Basic Concepts Ordered Indices B+-Tree Index Files B-Tree Index Files Static Hashing Dynamic Hashing Comparison of Ordered Indexing and Hashing Index Definition
Parallel Hybrid Monte Carlo Algorithms for Matrix Computations
 Parallel Hybrid Monte Carlo Algorithms for Matrix Computations V. Alexandrov 1, E. Atanassov 2, I. Dimov 2, S.Branford 1, A. Thandavan 1 and C. Weihrauch 1 1 Department of Computer Science, University
Parallel Hybrid Monte Carlo Algorithms for Matrix Computations V. Alexandrov 1, E. Atanassov 2, I. Dimov 2, S.Branford 1, A. Thandavan 1 and C. Weihrauch 1 1 Department of Computer Science, University
Hierarchical Multi level Approach to graph clustering
 Hierarchical Multi level Approach to graph clustering by: Neda Shahidi neda@cs.utexas.edu Cesar mantilla, cesar.mantilla@mail.utexas.edu Advisor: Dr. Inderjit Dhillon Introduction Data sets can be presented
Hierarchical Multi level Approach to graph clustering by: Neda Shahidi neda@cs.utexas.edu Cesar mantilla, cesar.mantilla@mail.utexas.edu Advisor: Dr. Inderjit Dhillon Introduction Data sets can be presented
Algorithm of correction of error caused by perspective distortions of measuring mark images
 Mechanics & Industry 7, 73 (206) c AFM, EDP Sciences 206 DOI: 0.05/meca/206077 www.mechanics-industry.org Mechanics & Industry Algorithm of correction of error caused by perspective distortions of measuring
Mechanics & Industry 7, 73 (206) c AFM, EDP Sciences 206 DOI: 0.05/meca/206077 www.mechanics-industry.org Mechanics & Industry Algorithm of correction of error caused by perspective distortions of measuring
B553 Lecture 12: Global Optimization
 B553 Lecture 12: Global Optimization Kris Hauser February 20, 2012 Most of the techniques we have examined in prior lectures only deal with local optimization, so that we can only guarantee convergence
B553 Lecture 12: Global Optimization Kris Hauser February 20, 2012 Most of the techniques we have examined in prior lectures only deal with local optimization, so that we can only guarantee convergence
Analysis of Algorithms and Presentation of Algorithm Graph in a Line-Parallel Form
 Analysis of Algorithms and Presentation of Algorithm Graph in a Line-Parallel Form D.M. Okhunov, M.H.Okhunov Cand.Econ.Sci., the senior lecturer of the Fergana Branch of the Tashkent University of Information
Analysis of Algorithms and Presentation of Algorithm Graph in a Line-Parallel Form D.M. Okhunov, M.H.Okhunov Cand.Econ.Sci., the senior lecturer of the Fergana Branch of the Tashkent University of Information
An Efficient Algorithm to Test Forciblyconnectedness of Graphical Degree Sequences
 Theory and Applications of Graphs Volume 5 Issue 2 Article 2 July 2018 An Efficient Algorithm to Test Forciblyconnectedness of Graphical Degree Sequences Kai Wang Georgia Southern University, kwang@georgiasouthern.edu
Theory and Applications of Graphs Volume 5 Issue 2 Article 2 July 2018 An Efficient Algorithm to Test Forciblyconnectedness of Graphical Degree Sequences Kai Wang Georgia Southern University, kwang@georgiasouthern.edu
Motivation for B-Trees
 1 Motivation for Assume that we use an AVL tree to store about 20 million records We end up with a very deep binary tree with lots of different disk accesses; log2 20,000,000 is about 24, so this takes
1 Motivation for Assume that we use an AVL tree to store about 20 million records We end up with a very deep binary tree with lots of different disk accesses; log2 20,000,000 is about 24, so this takes
Using the Best of Both!
 Using the Best of Both! A Guide to Using Connected Mathematics 2 with Prentice Hall Mathematics Courses 1, 2, 3 2012, and Algebra Readiness MatBro111707BestOfBothPH10&CMP2.indd 1 6/7/11 11:59 AM Using
Using the Best of Both! A Guide to Using Connected Mathematics 2 with Prentice Hall Mathematics Courses 1, 2, 3 2012, and Algebra Readiness MatBro111707BestOfBothPH10&CMP2.indd 1 6/7/11 11:59 AM Using
A New Distance Independent Localization Algorithm in Wireless Sensor Network
 A New Distance Independent Localization Algorithm in Wireless Sensor Network Siwei Peng 1, Jihui Li 2, Hui Liu 3 1 School of Information Science and Engineering, Yanshan University, Qinhuangdao 2 The Key
A New Distance Independent Localization Algorithm in Wireless Sensor Network Siwei Peng 1, Jihui Li 2, Hui Liu 3 1 School of Information Science and Engineering, Yanshan University, Qinhuangdao 2 The Key
Particular experience in design and implementation of a Current Research Information System in Russia: national specificity
 Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 00 (2014) 000 000 www.elsevier.com/locate/procedia CRIS 2014 Particular experience in design and implementation of a Current
Available online at www.sciencedirect.com ScienceDirect Procedia Computer Science 00 (2014) 000 000 www.elsevier.com/locate/procedia CRIS 2014 Particular experience in design and implementation of a Current
9. Which situation is true regarding a cascading cut that produces c trees for a Fibonacci heap?
 1 1 Name Test 1 - Closed Book Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each 1. During which operation on a leftist heap may subtree swaps be needed? A. DECREASE-KEY
1 1 Name Test 1 - Closed Book Student ID # Multiple Choice. Write your answer to the LEFT of each problem. points each 1. During which operation on a leftist heap may subtree swaps be needed? A. DECREASE-KEY
A Linear-Time Heuristic for Improving Network Partitions
 A Linear-Time Heuristic for Improving Network Partitions ECE 556 Project Report Josh Brauer Introduction The Fiduccia-Matteyses min-cut heuristic provides an efficient solution to the problem of separating
A Linear-Time Heuristic for Improving Network Partitions ECE 556 Project Report Josh Brauer Introduction The Fiduccia-Matteyses min-cut heuristic provides an efficient solution to the problem of separating
File Structures and Indexing
 File Structures and Indexing CPS352: Database Systems Simon Miner Gordon College Last Revised: 10/11/12 Agenda Check-in Database File Structures Indexing Database Design Tips Check-in Database File Structures
File Structures and Indexing CPS352: Database Systems Simon Miner Gordon College Last Revised: 10/11/12 Agenda Check-in Database File Structures Indexing Database Design Tips Check-in Database File Structures
Sorting. Data structures and Algorithms
 Sorting Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and Mount (Wiley, 2004) Outline Bubble
Sorting Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and Mount (Wiley, 2004) Outline Bubble
NET/JRF-COMPUTER SCIENCE & APPLICATIONS. Time: 01 : 00 Hour Date : M.M. : 50
 1 NET/JRF-COMPUTER SCIENCE & APPLICATIONS UNIT TEST : DATA STRUCTURE Time: 01 : 00 Hour Date : 02-06-2017 M.M. : 50 INSTRUCTION: Attempt all the 25 questions. Each question carry TWO marks. 1. Consider
1 NET/JRF-COMPUTER SCIENCE & APPLICATIONS UNIT TEST : DATA STRUCTURE Time: 01 : 00 Hour Date : 02-06-2017 M.M. : 50 INSTRUCTION: Attempt all the 25 questions. Each question carry TWO marks. 1. Consider
Range searching. with Range Trees
 Range searching Computational Geometry [csci 3250] Range searching with Range Trees Given a set of points, preprocess them into a data structure to support fast range queries. 2D Laura Toma Bowdoin College
Range searching Computational Geometry [csci 3250] Range searching with Range Trees Given a set of points, preprocess them into a data structure to support fast range queries. 2D Laura Toma Bowdoin College
17/05/2018. Outline. Outline. Divide and Conquer. Control Abstraction for Divide &Conquer. Outline. Module 2: Divide and Conquer
 Module 2: Divide and Conquer Divide and Conquer Control Abstraction for Divide &Conquer 1 Recurrence equation for Divide and Conquer: If the size of problem p is n and the sizes of the k sub problems are
Module 2: Divide and Conquer Divide and Conquer Control Abstraction for Divide &Conquer 1 Recurrence equation for Divide and Conquer: If the size of problem p is n and the sizes of the k sub problems are
Sorting is ordering a list of objects. Here are some sorting algorithms
 Sorting Sorting is ordering a list of objects. Here are some sorting algorithms Bubble sort Insertion sort Selection sort Mergesort Question: What is the lower bound for all sorting algorithms? Algorithms
Sorting Sorting is ordering a list of objects. Here are some sorting algorithms Bubble sort Insertion sort Selection sort Mergesort Question: What is the lower bound for all sorting algorithms? Algorithms
Algorithms and Data Structures
 Algorithms and Data Structures Spring 2019 Alexis Maciel Department of Computer Science Clarkson University Copyright c 2019 Alexis Maciel ii Contents 1 Analysis of Algorithms 1 1.1 Introduction.................................
Algorithms and Data Structures Spring 2019 Alexis Maciel Department of Computer Science Clarkson University Copyright c 2019 Alexis Maciel ii Contents 1 Analysis of Algorithms 1 1.1 Introduction.................................
A Fast Algorithm for Optimal Alignment between Similar Ordered Trees
 Fundamenta Informaticae 56 (2003) 105 120 105 IOS Press A Fast Algorithm for Optimal Alignment between Similar Ordered Trees Jesper Jansson Department of Computer Science Lund University, Box 118 SE-221
Fundamenta Informaticae 56 (2003) 105 120 105 IOS Press A Fast Algorithm for Optimal Alignment between Similar Ordered Trees Jesper Jansson Department of Computer Science Lund University, Box 118 SE-221
FUTURE communication networks are expected to support
 1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
1146 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL 13, NO 5, OCTOBER 2005 A Scalable Approach to the Partition of QoS Requirements in Unicast and Multicast Ariel Orda, Senior Member, IEEE, and Alexander Sprintson,
Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of C
 Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of California, San Diego CA 92093{0114, USA Abstract. We
Optimum Alphabetic Binary Trees T. C. Hu and J. D. Morgenthaler Department of Computer Science and Engineering, School of Engineering, University of California, San Diego CA 92093{0114, USA Abstract. We
CSC Design and Analysis of Algorithms. Lecture 5. Decrease and Conquer Algorithm Design Technique. Decrease-and-Conquer
 CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conuer Algorithm Design Techniue Decrease-and-Conuer This algorithm design techniue is based on exploiting a relationship between a solution
CSC 8301- Design and Analysis of Algorithms Lecture 5 Decrease and Conuer Algorithm Design Techniue Decrease-and-Conuer This algorithm design techniue is based on exploiting a relationship between a solution
Lecture 3: Sorting 1
 Lecture 3: Sorting 1 Sorting Arranging an unordered collection of elements into monotonically increasing (or decreasing) order. S = a sequence of n elements in arbitrary order After sorting:
Lecture 3: Sorting 1 Sorting Arranging an unordered collection of elements into monotonically increasing (or decreasing) order. S = a sequence of n elements in arbitrary order After sorting:
