XCOLD Information Leak
|
|
|
- Tracey Bishop
- 5 years ago
- Views:
Transcription
1 XCOLD Information Leak New Functionality for Developers, New Security Concerns Based on my original article: uk/2016/01/zap-newsletter-2016-january.html#feature
2 Intro Ottawa ended up with an uncharacteristically green Christmas this year, but finally got snow as I m drafting this (Dec 29th), so I'm going to dub this the XCOLD Info Leak (X-ChrOmeLogger-Data).
3 Intro
4 Functional Summary Basically it boils down as follows: Decide you want server side messages available to clients. Stick some code into your web app. Support seems to be quite extensive: Python, PHP, Ruby, Node.js,.NET, ColdFusion, Go, Java, and Perl. Though the majority of the existing install/usage seems to be PHP. Boom get messages in the browser (Chrome requires an extension, while Firefox now has native support). Messages are returned as Base64 encoded JSON via the response header XChromeLogger-Data. Browsing one can also learn that older or alternate implementations use(d) X-ChromePhp-Data.
5 Use? Ok so X-ChromeLogger-Data is in use. Not extensively but the numbers are increasing. The image here is from , I had previously poked around on this topic around the 18th. Though I don t remember the specific number I d previously queried there seems to have been an increase in a short period and over the holidays.
6 Use? It also seems that X-ChromePhpData is in use to a much lesser extent. So off I go to see what kind of data people might be exposing.
7 Looking around... Keep in mind the following findings are based on public data, I m not revealing anything here that the site(s) haven t already revealed to the world. Below I ve just copied the Base64 encoded header values from the Shodan results and run them through the handy online decoder at
8 Looking around... Alternative 1: Proxy your shodan result browsing through ZAP, select the base64 string and use the Encode / Decode / Hash context menu:
9 Looking around... Alternative 2: You could also pop the dev tools console (F12) and do a atob( <some base64 string> ); and hit enter. For example atob( ZW5jb2RlIHRoaXM= ); returns encode this. I used the online service below since the dev tools console doesn t line wrap :(
10 How Bad Is It? Meh Picking the first X-ChromePhp-Data shodan result I got the following: Ok not terribly revealing, however it does give the entire disk location of AppController.php. Might be able to leverage that in other attacks or use the knowledge to social engineer something.
11 How Bad Is It?...Warming Up. Here s another example that s really verbose, note Undefined index: admin references:
12 How Bad Is It?...Warmer Still. Here s another, note the failures in processing various tokens, PREBODY, and HTTP_USER_AGENT. Those details might lead a pentester to another useful finding such as UA specific response or UA injection of some sort.
13 How Bad Is It?...Hot in here? Here s one that appears to be a WordPress plugin. And, another that seems to be a Windows host running some WordPress gallery.
14 How Bad Is It?...Smoke...Fire? To top it off, here s an example leaking raw SQL details:
15 Now What? While the benefits to a developer are obvious I would suggest that the following considerations or implementation choices be made if using the functionality: 1. Do you want this turned on for Production use? 2. If you do want it on for Production use can you ensure that you don t leak information that might be leveraged by an attacker or malicious individual? 3. Can you tie it to your authorization framework so that the information (header + content) is returned only to admins and support personnel not all users?
16 Scanner Support... Curious if your app or site is exposing anything similar to the examples above? Do you have the XCOLD Info Leak? Checkout the new ZAP passive plugin that looks for and identifies information leaks via X-ChromeLogger-Data and XChromePhp-Data. Available via the ZAP Market Place as of 'Passive Scan Rules Alpha' version 8.
17 Updates That s +113 occurrences at the top (Sweden) in 3 wks That s +134 on the HTTPS service counts in 3 wks.
18 Updates That s +6 occurrences at the top (US) in 3 wks That s +7 on the HTTPS service counts in 3 wks.
Metasploit. Installation Guide Release 4.4
 Metasploit Installation Guide Release 4.4 TABLE OF CONTENTS About this Guide Target Audience...1 Organization...1 Document Conventions...1 Support...2 Support for Metasploit Pro and Metasploit Express...2
Metasploit Installation Guide Release 4.4 TABLE OF CONTENTS About this Guide Target Audience...1 Organization...1 Document Conventions...1 Support...2 Support for Metasploit Pro and Metasploit Express...2
I was given the following web application: and the instruction could be found on the first page.
 I was given the following web application: http://159.203.178.9/ and the instruction could be found on the first page. So, I had to find the path for the application that stores notes and try to exploit
I was given the following web application: http://159.203.178.9/ and the instruction could be found on the first page. So, I had to find the path for the application that stores notes and try to exploit
I started off with a quick nmap scan, which showed both port 80 and 443 open.
 Mr-Robot: 1 Walkthrough Author: mrb3n Download location: https://download.vulnhub.com/mrrobot/mrrobot.ova Goal: Find 3 keys hidden in different locations -----------------------------------------------------------------------------------------------------------------
Mr-Robot: 1 Walkthrough Author: mrb3n Download location: https://download.vulnhub.com/mrrobot/mrrobot.ova Goal: Find 3 keys hidden in different locations -----------------------------------------------------------------------------------------------------------------
Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013
 Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013 Welcome Back! A Quick Recap of the Last Presentation: Overview of web technologies. What it is. How it works. Why it s attractive
Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013 Welcome Back! A Quick Recap of the Last Presentation: Overview of web technologies. What it is. How it works. Why it s attractive
Sucuri Webinar Q&A HOW TO IDENTIFY AND FIX A HACKED WORDPRESS WEBSITE. Ben Martin - Remediation Team Lead
 Sucuri Webinar Q&A HOW TO IDENTIFY AND FIX A HACKED WORDPRESS WEBSITE. Ben Martin - Remediation Team Lead 1 Question #1: What is the benefit to spammers for using someone elses UA code and is there a way
Sucuri Webinar Q&A HOW TO IDENTIFY AND FIX A HACKED WORDPRESS WEBSITE. Ben Martin - Remediation Team Lead 1 Question #1: What is the benefit to spammers for using someone elses UA code and is there a way
ZAP Innovations. OWASP Zed Attack Proxy. Simon Bennetts. OWASP AppSec EU Hamburg The OWASP Foundation
 OWASP AppSec EU Hamburg 2013 The OWASP Foundation http://www.owasp.org ZAP Innovations OWASP Zed Attack Proxy Simon Bennetts OWASP ZAP Project Lead Mozilla Security Team psiinon@gmail.com Copyright The
OWASP AppSec EU Hamburg 2013 The OWASP Foundation http://www.owasp.org ZAP Innovations OWASP Zed Attack Proxy Simon Bennetts OWASP ZAP Project Lead Mozilla Security Team psiinon@gmail.com Copyright The
Version Release Date: September 5, Release Client Version: Release Overview 7 Resolved Issues 8 Known Issues 8
 SpringCM Edit for Windows Version 1.5 Release Notes January 2015 Table of Contents Version 1.5 5 Release Date: January 19, 2015 5 Release Client Version: 1.5.16 5 Release Overview 5 Enhancements 5 Silent
SpringCM Edit for Windows Version 1.5 Release Notes January 2015 Table of Contents Version 1.5 5 Release Date: January 19, 2015 5 Release Client Version: 1.5.16 5 Release Overview 5 Enhancements 5 Silent
DATABASE SYSTEMS. Database programming in a web environment. Database System Course,
 DATABASE SYSTEMS Database programming in a web environment Database System Course, 2016-2017 AGENDA FOR TODAY The final project Advanced Mysql Database programming Recap: DB servers in the web Web programming
DATABASE SYSTEMS Database programming in a web environment Database System Course, 2016-2017 AGENDA FOR TODAY The final project Advanced Mysql Database programming Recap: DB servers in the web Web programming
Application Extender 16.3 Web Access
 Application Extender 16.3 Web Access Pre-requisites for WebXtender client Firefox, Chrome or Edge browser For scanning, your friendly neighborhood desktop support person will need to install the specific
Application Extender 16.3 Web Access Pre-requisites for WebXtender client Firefox, Chrome or Edge browser For scanning, your friendly neighborhood desktop support person will need to install the specific
Intro to Couchbase Server for ColdFusion - Clustered NoSQL and Caching at its Finest
 Tweet Intro to Couchbase Server for ColdFusion - Clustered NoSQL and Caching at its Finest Brad Wood Jul 26, 2013 Today we are starting a new blogging series on how to leverage Couchbase NoSQL from ColdFusion
Tweet Intro to Couchbase Server for ColdFusion - Clustered NoSQL and Caching at its Finest Brad Wood Jul 26, 2013 Today we are starting a new blogging series on how to leverage Couchbase NoSQL from ColdFusion
Reading How the Web Works
 Reading 1.3 - How the Web Works By Jonathan Lane Introduction Every so often, you get offered a behind-the-scenes look at the cogs and fan belts behind the action. Today is your lucky day. In this article
Reading 1.3 - How the Web Works By Jonathan Lane Introduction Every so often, you get offered a behind-the-scenes look at the cogs and fan belts behind the action. Today is your lucky day. In this article
Manual Html Image Src Url Path Not Working
 Manual Html Image Src Url Path Not Working _img src="file:///absolute/path/to/rails-app/public/image.png" alt="blah" /_. However i obviously want a relative path instead. Where is the relative path going.
Manual Html Image Src Url Path Not Working _img src="file:///absolute/path/to/rails-app/public/image.png" alt="blah" /_. However i obviously want a relative path instead. Where is the relative path going.
Solution of Exercise Sheet 5
 Foundations of Cybersecurity (Winter 16/17) Prof. Dr. Michael Backes CISPA / Saarland University saarland university computer science Solution of Exercise Sheet 5 1 SQL Injection Consider a website foo.com
Foundations of Cybersecurity (Winter 16/17) Prof. Dr. Michael Backes CISPA / Saarland University saarland university computer science Solution of Exercise Sheet 5 1 SQL Injection Consider a website foo.com
How to Rescue a Deleted File Using the Free Undelete 360 Program
 R 095/1 How to Rescue a Deleted File Using the Free Program This article shows you how to: Maximise your chances of recovering the lost file View a list of all your deleted files in the free Restore a
R 095/1 How to Rescue a Deleted File Using the Free Program This article shows you how to: Maximise your chances of recovering the lost file View a list of all your deleted files in the free Restore a
A. Outlook Web App -
 A. Outlook Web App - Email 1. Outlook Web App (OWA) Vs. Outlook Outlook refers to an application that is physically installed on a computer. Whereas a Web Application is something that is not installed
A. Outlook Web App - Email 1. Outlook Web App (OWA) Vs. Outlook Outlook refers to an application that is physically installed on a computer. Whereas a Web Application is something that is not installed
Automated Security Scanning in Payment Industry
 Digital Transformation Specialist Automated Security Scanning in Payment Industry Michał Buczko Michał Buczko Test Consultant Public Speaker Security enthusiast Agenda 1.) Why security? 2.) How hard it
Digital Transformation Specialist Automated Security Scanning in Payment Industry Michał Buczko Michał Buczko Test Consultant Public Speaker Security enthusiast Agenda 1.) Why security? 2.) How hard it
5/11/2009. Better to light a candle than to curse the darkness. Case Study: Reconnaissance Leaks & Corporate Assets
 Spotlights on the Digital Battlefield Better to light a candle than to curse the darkness. Chinese Proverb Slide 2 Case Study: Reconnaissance Leaks & Corporate Assets Hacking is not always malicious Stealing
Spotlights on the Digital Battlefield Better to light a candle than to curse the darkness. Chinese Proverb Slide 2 Case Study: Reconnaissance Leaks & Corporate Assets Hacking is not always malicious Stealing
Chrome if I want to. What that should do, is have my specifications run against four different instances of Chrome, in parallel.
 Hi. I'm Prateek Baheti. I'm a developer at ThoughtWorks. I'm currently the tech lead on Mingle, which is a project management tool that ThoughtWorks builds. I work in Balor, which is where India's best
Hi. I'm Prateek Baheti. I'm a developer at ThoughtWorks. I'm currently the tech lead on Mingle, which is a project management tool that ThoughtWorks builds. I work in Balor, which is where India's best
Http Error Code 403 Forbidden Dreamweaver Mysql
 Http Error Code 403 Forbidden Dreamweaver Mysql Dreamweaver Database Http Error Code 403 Forbidden 오류 403 Forbidden Adobe Systems Inc. Adobe Dreamweaver. 459. Dreamweaver Error 1045 오류. They can range
Http Error Code 403 Forbidden Dreamweaver Mysql Dreamweaver Database Http Error Code 403 Forbidden 오류 403 Forbidden Adobe Systems Inc. Adobe Dreamweaver. 459. Dreamweaver Error 1045 오류. They can range
CONVERSION TRACKING PIXEL GUIDE
 Conversion Tracking Pixel Guide A Step By Step Guide to Installing a conversion tracking pixel for your next Facebook ad. Go beyond clicks, and know who s converting. PRESENTED BY JULIE LOWE OF SOCIALLY
Conversion Tracking Pixel Guide A Step By Step Guide to Installing a conversion tracking pixel for your next Facebook ad. Go beyond clicks, and know who s converting. PRESENTED BY JULIE LOWE OF SOCIALLY
For more info on Cloud9 see their documentation:
 Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
Intro to Wordpress Cloud 9 - http://c9.io With the free C9 account you have limited space and only 1 private project. Pay attention to your memory, cpu and disk usage meter at the top of the screen. For
N different strategies to automate OWASP ZAP
 OWASP BUCHAREST APPSEC CONFERENCE 13 OCTOBER 2017 The OWASP Foundation http://www.owasp.org N different strategies to automate OWASP ZAP The OWASP Zed Attack Proxy Marudhamaran Gunasekaran Zap Contributor
OWASP BUCHAREST APPSEC CONFERENCE 13 OCTOBER 2017 The OWASP Foundation http://www.owasp.org N different strategies to automate OWASP ZAP The OWASP Zed Attack Proxy Marudhamaran Gunasekaran Zap Contributor
Instructor s Notes Web Data Management Web Client/Server Concepts. Web Data Management Web Client/Server Concepts
 Instructor s Web Data Management Web Client/Server Concepts Web Data Management 152-155 Web Client/Server Concepts Quick Links & Text References Client / Server Concepts Pages 4 11 Web Data Mgt Software
Instructor s Web Data Management Web Client/Server Concepts Web Data Management 152-155 Web Client/Server Concepts Quick Links & Text References Client / Server Concepts Pages 4 11 Web Data Mgt Software
Security. 1 Introduction. Alex S. 1.1 Authentication
 Security Alex S. 1 Introduction Security is one of the most important topics in the IT field. Without some degree of security, we wouldn t have the Internet, e-commerce, ATM machines, emails, etc. A lot
Security Alex S. 1 Introduction Security is one of the most important topics in the IT field. Without some degree of security, we wouldn t have the Internet, e-commerce, ATM machines, emails, etc. A lot
CS 161 Computer Security
 Paxson Spring 2017 CS 161 Computer Security Discussion 4 Week of February 13, 2017 Question 1 Clickjacking (5 min) Watch the following video: https://www.youtube.com/watch?v=sw8ch-m3n8m Question 2 Session
Paxson Spring 2017 CS 161 Computer Security Discussion 4 Week of February 13, 2017 Question 1 Clickjacking (5 min) Watch the following video: https://www.youtube.com/watch?v=sw8ch-m3n8m Question 2 Session
sqlite wordpress 06C6817F2E58AF4319AB84EE Sqlite Wordpress 1 / 6
 Sqlite Wordpress 1 / 6 2 / 6 3 / 6 Sqlite Wordpress Run WordPress with SQLite instead of MySQL database and how to install and set it up, this is a great way to get WordPress setup running on small web
Sqlite Wordpress 1 / 6 2 / 6 3 / 6 Sqlite Wordpress Run WordPress with SQLite instead of MySQL database and how to install and set it up, this is a great way to get WordPress setup running on small web
Tutorial of SQL Power Injector 1.2
 Copyright 2006-2007 Francois Larouche 1 Copyright 2006-2007 Francois Larouche 2 Copyright 2006-2007 Francois Larouche 3 Please follow first the main schema and if you need more details go to their respective
Copyright 2006-2007 Francois Larouche 1 Copyright 2006-2007 Francois Larouche 2 Copyright 2006-2007 Francois Larouche 3 Please follow first the main schema and if you need more details go to their respective
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
John Coggeshall Copyright 2006, Zend Technologies Inc.
 PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
Guide to fix the problem with Problets
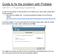 Guide to fix the problem with Problets COP 2512 - IT Programming Fundamentals In order to fix the problem of not being able to run Problets on your web browser, please follow the following steps: 1. Make
Guide to fix the problem with Problets COP 2512 - IT Programming Fundamentals In order to fix the problem of not being able to run Problets on your web browser, please follow the following steps: 1. Make
CSE 127 Computer Security
 CSE 127 Computer Security Fall 2015 Web Security I: SQL injection Stefan Savage The Web creates new problems Web sites are programs Partially implemented in browser» Javascript, Java, Flash Partially implemented
CSE 127 Computer Security Fall 2015 Web Security I: SQL injection Stefan Savage The Web creates new problems Web sites are programs Partially implemented in browser» Javascript, Java, Flash Partially implemented
Yammer with Recognize
 Recognize Yammer with Recognize 2016 Recognize Services Inc Version 1.0.1 Introduction... 3 Recognize integration with Yammer... 3 Download the browser extensions now... 3 Check out the resources... 3
Recognize Yammer with Recognize 2016 Recognize Services Inc Version 1.0.1 Introduction... 3 Recognize integration with Yammer... 3 Download the browser extensions now... 3 Check out the resources... 3
IFRS KMA KNOWLEDGE MANAGEMENT APPLICATION INSTALLATION GUIDE
 IFRS KMA KNOWLEDGE MANAGEMENT APPLICATION INSTALLATION GUIDE The KMA INSTALLATION GUIDE STEP 1. Download the installation file from the link in your email. When you click on the KMA link to begin the installation
IFRS KMA KNOWLEDGE MANAGEMENT APPLICATION INSTALLATION GUIDE The KMA INSTALLATION GUIDE STEP 1. Download the installation file from the link in your email. When you click on the KMA link to begin the installation
Content Security Policy
 About Tim Content Security Policy New Tools for Fighting XSS Pentester > 10 years Web Applications Network Security Products Exploit Research Founded Blindspot Security in 2014 Pentesting Developer Training
About Tim Content Security Policy New Tools for Fighting XSS Pentester > 10 years Web Applications Network Security Products Exploit Research Founded Blindspot Security in 2014 Pentesting Developer Training
CSCI 201 Lab 1 Environment Setup
 CSCI 201 Lab 1 Environment Setup "The journey of a thousand miles begins with one step." - Lao Tzu Introduction This lab document will go over the steps to install and set up Eclipse, which is a Java integrated
CSCI 201 Lab 1 Environment Setup "The journey of a thousand miles begins with one step." - Lao Tzu Introduction This lab document will go over the steps to install and set up Eclipse, which is a Java integrated
MFT and JMS Notifications
 MFT and JMS Notifications In scope for this page: Configuring an existing MFT Command Centre (CC) and Internet Server (IS) 7.2.3 to send a JMS Alert Using the BW MFT Palette plugin to receive the JMS Alert
MFT and JMS Notifications In scope for this page: Configuring an existing MFT Command Centre (CC) and Internet Server (IS) 7.2.3 to send a JMS Alert Using the BW MFT Palette plugin to receive the JMS Alert
CNIT 129S: Securing Web Applications. Ch 4: Mapping the Application
 CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
LIBRARY MEMBER USER GUIDE
 LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account...2 Part 2) How to checkout a magazine issue...4 Part 3) How to download Zinio Reader 4...10 a) For your PC...10 b) For your
LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account...2 Part 2) How to checkout a magazine issue...4 Part 3) How to download Zinio Reader 4...10 a) For your PC...10 b) For your
(System) Integrity attacks System Abuse, Malicious File upload, SQL Injection
 Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
When providing a native mobile app ruins the security of your existing web solution. CyberSec Conference /11/2015 Jérémy MATOS
 When providing a native mobile app ruins the security of your existing web solution CyberSec Conference 2015 05/11/2015 Jérémy MATOS whois securingapps Developer background Spent last 10 years working
When providing a native mobile app ruins the security of your existing web solution CyberSec Conference 2015 05/11/2015 Jérémy MATOS whois securingapps Developer background Spent last 10 years working
Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 08 Tutorial 2, Part 2, Facebook API (Refer Slide Time: 00:12)
Privacy and Security in Online Social Networks Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 08 Tutorial 2, Part 2, Facebook API (Refer Slide Time: 00:12)
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
ATMS ACTION TRACKING MANAGEMENT SYSTEM. Quick Start Guide. The ATMS dev team
 ATMS ACTION TRACKING MANAGEMENT SYSTEM Quick Start Guide The ATMS dev team Contents What is ATMS?... 2 How does ATMS work?... 2 I get it, now where can I find more info?... 2 What s next?... 2 Welcome
ATMS ACTION TRACKING MANAGEMENT SYSTEM Quick Start Guide The ATMS dev team Contents What is ATMS?... 2 How does ATMS work?... 2 I get it, now where can I find more info?... 2 What s next?... 2 Welcome
Browsing the World Wide Web with Firefox
 Browsing the World Wide Web with Firefox B 660 / 1 Try this Popular and Featurepacked Free Alternative to Internet Explorer Internet Explorer 7 arrived with a bang a few months ago, but it hasn t brought
Browsing the World Wide Web with Firefox B 660 / 1 Try this Popular and Featurepacked Free Alternative to Internet Explorer Internet Explorer 7 arrived with a bang a few months ago, but it hasn t brought
Integrity attacks (from data to code): Malicious File upload, code execution, SQL Injection
 Pattern Recognition and Applications Lab Integrity attacks (from data to code): Malicious File upload, code execution, SQL Injection Igino Corona igino.corona _at_ diee.unica.it Computer Security May 2nd,
Pattern Recognition and Applications Lab Integrity attacks (from data to code): Malicious File upload, code execution, SQL Injection Igino Corona igino.corona _at_ diee.unica.it Computer Security May 2nd,
ArcGIS for Server: Administration and Security. Amr Wahba
 ArcGIS for Server: Administration and Security Amr Wahba awahba@esri.com Agenda ArcGIS Server architecture Distributing and scaling components Implementing security Monitoring server logs Automating server
ArcGIS for Server: Administration and Security Amr Wahba awahba@esri.com Agenda ArcGIS Server architecture Distributing and scaling components Implementing security Monitoring server logs Automating server
Lifehack #1 - Automating Twitter Growth without Being Blocked by Twitter
 Lifehack #1 - Automating Twitter Growth without Being Blocked by Twitter Intro 2 Disclaimer 2 Important Caveats for Twitter Automation 2 Enter Azuqua 3 Getting Ready 3 Setup and Test your Connection! 4
Lifehack #1 - Automating Twitter Growth without Being Blocked by Twitter Intro 2 Disclaimer 2 Important Caveats for Twitter Automation 2 Enter Azuqua 3 Getting Ready 3 Setup and Test your Connection! 4
CONTROL Installation and Basic-configuration Guide Contents
 CONTROL Installation and Basic-configuration Guide Contents Installation and Basic-configuration Guide... 1 1. Overview... 2 2. Intro... 3 3. CONTROL installation steps:... 3 3.1 CONTROL installation requirements...
CONTROL Installation and Basic-configuration Guide Contents Installation and Basic-configuration Guide... 1 1. Overview... 2 2. Intro... 3 3. CONTROL installation steps:... 3 3.1 CONTROL installation requirements...
Event Password: NationalCenter2017 DON T FORGET STEP 2 ON THE NEXT PAGE!
 Hi, We ve built a mobile app for 2017 Parents as Teachers International Conference! It has all the important information you ll need for the event, and features to enhance your event experience. Step 1:
Hi, We ve built a mobile app for 2017 Parents as Teachers International Conference! It has all the important information you ll need for the event, and features to enhance your event experience. Step 1:
Web Hosting. Important features to consider
 Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Web Hosting Important features to consider Amount of Storage When choosing your web hosting, one of your primary concerns will obviously be How much data can I store? For most small and medium web sites,
Barracuda Web Application Firewall Foundation - WAF01. Lab Guide
 Barracuda Web Application Firewall Foundation - WAF01 Lab Guide Official training material for Barracuda certified trainings and Autorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Barracuda Web Application Firewall Foundation - WAF01 Lab Guide Official training material for Barracuda certified trainings and Autorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
WORDPRESS TRAINING MANUAL LAST UPDATED ON FEBRUARY 26TH, 2016
 WORDPRESS TRAINING MANUAL LAST UPDATED ON FEBRUARY 26TH, 2016 LOG INTO WORDPRESS Visit the Login page http://intermountaineyecare.net/wp-admin/ Enter your Username and Password NOTE: Additional usernames
WORDPRESS TRAINING MANUAL LAST UPDATED ON FEBRUARY 26TH, 2016 LOG INTO WORDPRESS Visit the Login page http://intermountaineyecare.net/wp-admin/ Enter your Username and Password NOTE: Additional usernames
Mendeley. Citation Management Software
 Mendeley Citation Management Software Why should I care about citation Management software? Have you ever written a paper with a bibliography or reference section? Did you type up the section word for
Mendeley Citation Management Software Why should I care about citation Management software? Have you ever written a paper with a bibliography or reference section? Did you type up the section word for
3 Continuous Integration 3. Automated system finding bugs is better than people
 This presentation is based upon a 3 day course I took from Jared Richardson. The examples and most of the tools presented are Java-centric, but there are equivalent tools for other languages or you can
This presentation is based upon a 3 day course I took from Jared Richardson. The examples and most of the tools presented are Java-centric, but there are equivalent tools for other languages or you can
CS 155 Project 2. Overview & Part A
 CS 155 Project 2 Overview & Part A Project 2 Web application security Composed of two parts Part A: Attack Part B: Defense Due date: Part A: May 5th (Thu) Part B: May 12th (Thu) Project 2 Ruby-on-Rails
CS 155 Project 2 Overview & Part A Project 2 Web application security Composed of two parts Part A: Attack Part B: Defense Due date: Part A: May 5th (Thu) Part B: May 12th (Thu) Project 2 Ruby-on-Rails
Components in Joomla. Instructor for this Workshop. Web Development. School of Arts and Sciences
 Components in Joomla Instructor for this Workshop Web Development School of Arts and Sciences TABLE OF CONTENTS Welcome... 4 What is Joomla?... 4 What is a Component?... 4 Joomla Weblinks... 5 Sample Use
Components in Joomla Instructor for this Workshop Web Development School of Arts and Sciences TABLE OF CONTENTS Welcome... 4 What is Joomla?... 4 What is a Component?... 4 Joomla Weblinks... 5 Sample Use
5/15/2009. Introduction
 Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
DATABASE SYSTEMS. Database programming in a web environment. Database System Course, 2016
 DATABASE SYSTEMS Database programming in a web environment Database System Course, 2016 AGENDA FOR TODAY Advanced Mysql More than just SELECT Creating tables MySQL optimizations: Storage engines, indexing.
DATABASE SYSTEMS Database programming in a web environment Database System Course, 2016 AGENDA FOR TODAY Advanced Mysql More than just SELECT Creating tables MySQL optimizations: Storage engines, indexing.
From a laptop or desktop computer.
 Using Office 365 Signing in to Office 365 Office 365 is a web-based office suite that allows the user to create, edit, and share documents and presentations from any internet enabled computer, tablet,
Using Office 365 Signing in to Office 365 Office 365 is a web-based office suite that allows the user to create, edit, and share documents and presentations from any internet enabled computer, tablet,
Introduction to OWASP WebGoat and OWTF. by Pawel Rzepa
 Introduction to OWASP WebGoat and OWTF by Pawel Rzepa About Me Security Engineer in SoftServe Poland Currently developing advanced fuzzing module in Spirent s Cyberflood OWASP member (OWASP Poland Chapter
Introduction to OWASP WebGoat and OWTF by Pawel Rzepa About Me Security Engineer in SoftServe Poland Currently developing advanced fuzzing module in Spirent s Cyberflood OWASP member (OWASP Poland Chapter
IronWASP (Iron Web application Advanced Security testing Platform)
 IronWASP (Iron Web application Advanced Security testing Platform) 1. Introduction: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability
IronWASP (Iron Web application Advanced Security testing Platform) 1. Introduction: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability
Window Server 2012 Hyper-V Virtual Machine Snapshots
 Window Server 2012 Hyper-V Virtual Machine Snapshots Creating a Snapshot Hyper-V makes it easy to create snapshots. To do so, open the Hyper-V Manager, right click on the virtual machine that you want
Window Server 2012 Hyper-V Virtual Machine Snapshots Creating a Snapshot Hyper-V makes it easy to create snapshots. To do so, open the Hyper-V Manager, right click on the virtual machine that you want
State of jquery Fall John Resig
 State of jquery Fall 2010 John Resig State of the Project New Releases jquery 1.4.3 / jquery 1.4.4 Official Plugins: jquery Templating jquery Data Linking jquery Mobile jquery 1.4.3 JSLint Modularity
State of jquery Fall 2010 John Resig State of the Project New Releases jquery 1.4.3 / jquery 1.4.4 Official Plugins: jquery Templating jquery Data Linking jquery Mobile jquery 1.4.3 JSLint Modularity
But before understanding the Selenium WebDriver concept, we need to know about the Selenium first.
 As per the today s scenario, companies not only desire to test software adequately, but they also want to get the work done as quickly and thoroughly as possible. To accomplish this goal, organizations
As per the today s scenario, companies not only desire to test software adequately, but they also want to get the work done as quickly and thoroughly as possible. To accomplish this goal, organizations
CSCE 120: Learning To Code
 CSCE 120: Learning To Code Module 11.0: Consuming Data I Introduction to Ajax This module is designed to familiarize you with web services and web APIs and how to connect to such services and consume and
CSCE 120: Learning To Code Module 11.0: Consuming Data I Introduction to Ajax This module is designed to familiarize you with web services and web APIs and how to connect to such services and consume and
java -jar Xmx2048mb /Applications/burpsuite_pro_v1.5.jar
 Training: An Introduction to Burp Suite Part One By Mike Sheward Burp suite provides a solid platform for launching a web application security assessment. In this guide we re going to introduce the features
Training: An Introduction to Burp Suite Part One By Mike Sheward Burp suite provides a solid platform for launching a web application security assessment. In this guide we re going to introduce the features
CS 355. Computer Networking. Wei Lu, Ph.D., P.Eng.
 CS 355 Computer Networking Wei Lu, Ph.D., P.Eng. Chapter 2: Application Layer Overview: Principles of network applications? Introduction to Wireshark Web and HTTP FTP Electronic Mail SMTP, POP3, IMAP DNS
CS 355 Computer Networking Wei Lu, Ph.D., P.Eng. Chapter 2: Application Layer Overview: Principles of network applications? Introduction to Wireshark Web and HTTP FTP Electronic Mail SMTP, POP3, IMAP DNS
CTF Workshop. Crim Synopsys, Inc. 1
 CTF Workshop Crim2018 31.10.2018 2018 Synopsys, Inc. 1 CTF (Capture the Flag) Capture the Flag (CTF) is a computer security competition. CTF are usually designed test and teach computer security skills.
CTF Workshop Crim2018 31.10.2018 2018 Synopsys, Inc. 1 CTF (Capture the Flag) Capture the Flag (CTF) is a computer security competition. CTF are usually designed test and teach computer security skills.
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
A Quick-Reference Guide. To access reddot: https://cms.hampshire.edu/cms
 Using RedDot A Quick-Reference Guide To access reddot: https://cms.hampshire.edu/cms For help: email reddot@hampshire.edu or visit http://www.hampshire.edu/computing/6433.htm Where is... Page 6 Page 8
Using RedDot A Quick-Reference Guide To access reddot: https://cms.hampshire.edu/cms For help: email reddot@hampshire.edu or visit http://www.hampshire.edu/computing/6433.htm Where is... Page 6 Page 8
Getting Started Guide
 Getting Started Guide for education accounts Setup Manual Edition 7 Last updated: September 15th, 2016 Note: Click on File and select Make a copy to save this to your Google Drive, or select Print, to
Getting Started Guide for education accounts Setup Manual Edition 7 Last updated: September 15th, 2016 Note: Click on File and select Make a copy to save this to your Google Drive, or select Print, to
Figure 1-1. When we finish Part 2, our server will be ready to have workstations join the domain and start sharing files. Now here we go!
 1 of 18 9/6/2008 4:05 AM Configuring Windows Server 2003 for a Small Business Network, Part 2 Written by Cortex Wednesday, 16 August 2006 Welcome to Part 2 of the "Configuring Windows Server 2003 for a
1 of 18 9/6/2008 4:05 AM Configuring Windows Server 2003 for a Small Business Network, Part 2 Written by Cortex Wednesday, 16 August 2006 Welcome to Part 2 of the "Configuring Windows Server 2003 for a
8.0 Help for End Users About Jive for SharePoint System Requirements Using Jive for SharePoint... 6
 for SharePoint 2010/2013 Contents 2 Contents 8.0 Help for End Users... 3 About Jive for SharePoint... 4 System Requirements... 5 Using Jive for SharePoint... 6 Overview of Jive for SharePoint... 6 Accessing
for SharePoint 2010/2013 Contents 2 Contents 8.0 Help for End Users... 3 About Jive for SharePoint... 4 System Requirements... 5 Using Jive for SharePoint... 6 Overview of Jive for SharePoint... 6 Accessing
of websites on the internet are WordPress
 WELCOME TO WORDPRESS.COM This tutorial is available for download at fas.camden.rutgers.edu/wordpresscom Questions? Contact: Kate Blair at kate.blair@rutgers.edu What is WordPress? WordPress is an open
WELCOME TO WORDPRESS.COM This tutorial is available for download at fas.camden.rutgers.edu/wordpresscom Questions? Contact: Kate Blair at kate.blair@rutgers.edu What is WordPress? WordPress is an open
Black Box DCX3000 / DCX1000 Using the API
 Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Evolution of the "Web
 Evolution of the "Web App" @HenrikJoreteg @Hoarse_JS THIS USED TO BE SIMPLE! 1. WRITE SOME HTML 2. LAY IT OUT WITH FRAMES OR TABLES 3. FTP IT TO A SERVER! 4. BAM! CONGRATULATIONS, YOU RE A WEB DEVELOPER!
Evolution of the "Web App" @HenrikJoreteg @Hoarse_JS THIS USED TO BE SIMPLE! 1. WRITE SOME HTML 2. LAY IT OUT WITH FRAMES OR TABLES 3. FTP IT TO A SERVER! 4. BAM! CONGRATULATIONS, YOU RE A WEB DEVELOPER!
textures not patterns
 This tutorial will walk you through how to create a seamless texture in Photoshop. I created the tutorial using Photoshop CS2, but it should work almost exactly the same for most versions of Photoshop
This tutorial will walk you through how to create a seamless texture in Photoshop. I created the tutorial using Photoshop CS2, but it should work almost exactly the same for most versions of Photoshop
Use Active Directory To Simulate InfoPath User Roles
 Page 1 of 7 Use Active Directory To Simulate InfoPath User Roles You can leverage the information returned by the Active Directory web service to simulate InfoPath User Roles, which are disabled in browser
Page 1 of 7 Use Active Directory To Simulate InfoPath User Roles You can leverage the information returned by the Active Directory web service to simulate InfoPath User Roles, which are disabled in browser
This tutorial introduces you to key DynamoDB concepts necessary for creating and deploying a highly-scalable and performance-focused database.
 About the Tutorial DynamoDB is a fully-managed NoSQL database service designed to deliver fast and predictable performance. It uses the Dynamo model in the essence of its design, and improves those features.
About the Tutorial DynamoDB is a fully-managed NoSQL database service designed to deliver fast and predictable performance. It uses the Dynamo model in the essence of its design, and improves those features.
Audio is in normal text below. Timestamps are in bold to assist in finding specific topics.
 Transcript of: Overview of Data Entry Video production date: April 2, 2012 Video length: 16:05 REDCap version featured: 4.7.1 (standard branch) Author: Veida Elliott, Vanderbilt University Medical Center,
Transcript of: Overview of Data Entry Video production date: April 2, 2012 Video length: 16:05 REDCap version featured: 4.7.1 (standard branch) Author: Veida Elliott, Vanderbilt University Medical Center,
WordPress is free and open source, meaning it's developed by the people who use it.
 1 2 WordPress Workshop by BBC July 2015 Contents: lorem ipsum dolor sit amet. page + WordPress.com is a cloudhosted service that runs WordPress where you can set up your own free blog or website without
1 2 WordPress Workshop by BBC July 2015 Contents: lorem ipsum dolor sit amet. page + WordPress.com is a cloudhosted service that runs WordPress where you can set up your own free blog or website without
An analysis of security in a web application development process
 An analysis of security in a web application development process Florent Gontharet Ethical Hacking University of Abertay Dundee MSc Ethical Hacking 2015 Table of Contents Abstract...2 Introduction...3
An analysis of security in a web application development process Florent Gontharet Ethical Hacking University of Abertay Dundee MSc Ethical Hacking 2015 Table of Contents Abstract...2 Introduction...3
System Structure. Steven M. Bellovin December 14,
 System Structure Steven M. Bellovin December 14, 2015 1 Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin December 14, 2015
System Structure Steven M. Bellovin December 14, 2015 1 Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin December 14, 2015
Imagery International website manual
 Imagery International website manual Prepared for: Imagery International Prepared by: Jenn de la Fuente Rosebud Designs http://www.jrosebud.com/designs designs@jrosebud.com 916.538.2133 A brief introduction
Imagery International website manual Prepared for: Imagery International Prepared by: Jenn de la Fuente Rosebud Designs http://www.jrosebud.com/designs designs@jrosebud.com 916.538.2133 A brief introduction
COPYRIGHTED MATERIAL. Starting Strong with Visual C# 2005 Express Edition
 1 Starting Strong with Visual C# 2005 Express Edition Okay, so the title of this chapter may be a little over the top. But to be honest, the Visual C# 2005 Express Edition, from now on referred to as C#
1 Starting Strong with Visual C# 2005 Express Edition Okay, so the title of this chapter may be a little over the top. But to be honest, the Visual C# 2005 Express Edition, from now on referred to as C#
Avanan for G Suite. Technical Overview. Copyright 2017 Avanan. All rights reserved.
 Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Avanan for G Suite Technical Overview Contents Intro 1 How Avanan Works 2 Email Security for Gmail 3 Data Security for Google Drive 4 Policy Automation 5 Workflows and Notifications 6 Authentication 7
Get Started in 10 Simple Steps
 Get Started in 10 Simple Steps Leddy Library is transforming the current course reserves system with Course Resource Lists powered by Leganto, a web-based course resource tool that connects library materials
Get Started in 10 Simple Steps Leddy Library is transforming the current course reserves system with Course Resource Lists powered by Leganto, a web-based course resource tool that connects library materials
COMP102: Introduction to Databases, 23
 COMP102: Introduction to Databases, 23 Dr Muhammad Sulaiman Khan Department of Computer Science University of Liverpool U.K. 04 April, 2011 Programming with SQL Specific topics for today: Client/Server
COMP102: Introduction to Databases, 23 Dr Muhammad Sulaiman Khan Department of Computer Science University of Liverpool U.K. 04 April, 2011 Programming with SQL Specific topics for today: Client/Server
Exploiting and Defending: Common Web Application Vulnerabilities
 Exploiting and Defending: Common Web Application Vulnerabilities Introduction: Steve Kosten Principal Security Consultant SANS Instructor Denver OWASP Chapter Lead Certifications CISSP, GWAPT, GSSP-Java,
Exploiting and Defending: Common Web Application Vulnerabilities Introduction: Steve Kosten Principal Security Consultant SANS Instructor Denver OWASP Chapter Lead Certifications CISSP, GWAPT, GSSP-Java,
Manage Your Service Two Factor Authentication (2FA) Guide
 Manage Your Service Two Factor Authentication (2FA) Guide Introduction 2FA provides an additional layer of security to your Manage Your Service (MYS) account as well as an alternative log-in method to
Manage Your Service Two Factor Authentication (2FA) Guide Introduction 2FA provides an additional layer of security to your Manage Your Service (MYS) account as well as an alternative log-in method to
CSE 484 / CSE M 584: Computer Security and Privacy. Web Security. Autumn Tadayoshi (Yoshi) Kohno
 CSE 484 / CSE M 584: Computer Security and Privacy Web Security Autumn 2018 Tadayoshi (Yoshi) Kohno yoshi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann, Dan Halperin, Ada Lerner, John Manferdelli,
CSE 484 / CSE M 584: Computer Security and Privacy Web Security Autumn 2018 Tadayoshi (Yoshi) Kohno yoshi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann, Dan Halperin, Ada Lerner, John Manferdelli,
Quick Guide to Installing and Setting Up MySQL Workbench
 Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
AGENT123. Full Q&A and Tutorials Table of Contents. Website IDX Agent Gallery Step-by-Step Tutorials
 AGENT123 Full Q&A and Tutorials Table of Contents Website IDX Agent Gallery Step-by-Step Tutorials WEBSITE General 1. How do I log into my website? 2. How do I change the Meta Tags on my website? 3. How
AGENT123 Full Q&A and Tutorials Table of Contents Website IDX Agent Gallery Step-by-Step Tutorials WEBSITE General 1. How do I log into my website? 2. How do I change the Meta Tags on my website? 3. How
WEB DESIGN & DEVELOPMENT
 WEB DESIGN & DEVELOPMENT Beautiful, functional, useful, easy to use. 46 0 1 Connec ti c ut A ve. N W Sui te 91 2 Wa s hi ng ton, DC 2 0008 INFOSHEET h e l l o @ s ab r acr e at i v e. co m 2 The right
WEB DESIGN & DEVELOPMENT Beautiful, functional, useful, easy to use. 46 0 1 Connec ti c ut A ve. N W Sui te 91 2 Wa s hi ng ton, DC 2 0008 INFOSHEET h e l l o @ s ab r acr e at i v e. co m 2 The right
GW Box User Guide. Have additional questions? Visit community.box.com for more information and training resources. Contents... 1
 GW Box User Guide GW Box is the university's enterprise file sharing service for online cloud storage and collaboration. In this guide, we ll show you how to share, access and mange your content from anywhere.
GW Box User Guide GW Box is the university's enterprise file sharing service for online cloud storage and collaboration. In this guide, we ll show you how to share, access and mange your content from anywhere.
Live Guide Co-browsing
 TECHNICAL PAPER Live Guide Co-browsing Netop develops and sells software solutions that enable swift, secure and seamless transfer of video, screens, sounds and data between two or more computers over
TECHNICAL PAPER Live Guide Co-browsing Netop develops and sells software solutions that enable swift, secure and seamless transfer of video, screens, sounds and data between two or more computers over
SFSC Website Cheat Sheet
 SFSC Website Cheat Sheet 1. Albums a. Creating Photo Album.page 2 b. Adding Images to exiting Photo Album..page 9 c. Resizing your images for the albums page 15 2. Events a. Creating an Event page 19 b.
SFSC Website Cheat Sheet 1. Albums a. Creating Photo Album.page 2 b. Adding Images to exiting Photo Album..page 9 c. Resizing your images for the albums page 15 2. Events a. Creating an Event page 19 b.
Web API Best Practices
 Web API Best Practices STEVE SMITH ARDALIS.COM @ARDALIS STEVE@DEVIQ.COM DEVIQ.COM Learn More After Today 1) DevIQ ASP.NET Core Quick Start http://aspnetcorequickstart.com DEVINTFALL17 20% OFF! 2) Microsoft
Web API Best Practices STEVE SMITH ARDALIS.COM @ARDALIS STEVE@DEVIQ.COM DEVIQ.COM Learn More After Today 1) DevIQ ASP.NET Core Quick Start http://aspnetcorequickstart.com DEVINTFALL17 20% OFF! 2) Microsoft
