ColdFusion Foundations: POP3. Mosh Teitelbaum evoch, LLC
|
|
|
- Loraine Webster
- 6 years ago
- Views:
Transcription
1 ColdFusion Foundations: POP3 Mosh Teitelbaum evoch, LLC
2 POP3: Post Office Protocol Version 3 Purpose To allow a workstation to retrieve mail - RFC 1939 What is POP3? A protocol that defines how clients communicate with servers to retrieve messages. What does POP3 do? It allows messages to be retrieved from the server. It does not support transmission of messages by clients.
3 POP3 Involves Clients and Servers Internet File System Database Server POP3 Client POP3 Server Message Store
4 POP3 Communication Process 1. Session Initiation - Client establishes 2-way connection to server (port 110) which responds with welcome message 2. AUTHORIZATION State - Client sends identification and server responds with another message, acquires access to the user s mail store and enters the TRANSACTION state. 3. TRANSACTION State Client initiates one or more transactions. 4. UPDATE State - Client initiates termination of connection and server updates mail store, sends a farewell message and terminates the connection.
5 POP3 Commands and Responses All client-server communication involves: Commands Clients send commands to provide information and instructions to the server Commands are usually 3-4 characters and are case-insensitive Responses Servers respond with a status indicator and a keyword possibly followed by more information. Status indicators are +OK (positive) or ERR (negative) Single line responses end with a single CRLF Multiple line responses end with a line consisting solely of a period and a CRLF
6 POP3 Commands Command Description QUIT Initiates session termination STAT Requests a drop listing indicating number of messages and size of the mail store LIST [msg] Requests a scan listing for specified or all message(s) indicating message number and size of the message RETR msg Retrieves specified message DELE msg Marks specified message as deleted NOOP No operation RSET Resets initial state by unmarking deleted messages TOP msg n Retrieves specified message s headers and top n lines of body UIDL [msg] Requests a unique-id listing for specified or all message(s) indicating message number and unique ID of the message USER name Specifies username for USER/PASS authentication PASS password Specifies password for USER/PASS authentication APOP name digest Specifies MD5-based authentication credentials
7 POP3 Authorization State The Authorization state begins upon transmission of the 1-line welcome message: +OK POP3 server ready Client must identify and authenticate itself: USER/PASS Plaintext authentication APOP MD5 digest encryption AUTH Alternate authentication mechanism (RFC 1734) If authentication fails, client can try again or may terminate the session via the QUIT command If authentication is successful, server enters Transaction state
8 USER/PASS Authentication Plaintext authentication via username and password Simplest form of authentication but also the least secure +OK POP3 server ready USER +OK PASS cfugdemo123 +OK 0 messages 0 octets +OK POP3 server ready USER cfugdemo@evoch.com +OK cfugdemo@evoch.com PASS hack -ERR Unknown user or incorrect password
9 APOP Authentication Authentication via username and MD5 hashed password Server indicates APOP support by sending timestamp in welcome message +OK POP3 server ready Wed, 18 Aug :37: Digest is the password appended to the timestamp (including angle brackets) which is then run through the MD5 algorithm +OK POP3 server ready Wed, 18 Aug :05: APOP 786b5c12203b391c9a903b515ce65a12 +OK 0 messages 0 octets
10 AUTH Authentication Specified in RFC 1734, POP3 AUTHentication Command, to allow use of IMAP4 authentication mechanisms in POP3 Client-specified authentication mechanism allowing for much more secure means of authentication +OK POP3 server ready AUTH KERBEROS_V4 + AmFYig== BAcAQU5EUkVXLkNNVS5FRFUAOCAsho84kLN3/IJmrMG+25a4DT +nzimjjntnhjutxaa+o0kpkfhecafs9a3cl5oebe/ydhjuwyfd WwuQ1MWiy6IesKvjL5rL9WjXUb9MwT9bpObYLGOKi1Qh + or//eoaadzi= DiAF5A4gA+oOIALuBkAAmw== +OK Kerberos V4 authentication successful
11 POP3 Transaction State The Transaction state begins when the client successfully authenticates and the server gains exclusive access to the mail store After gaining access, server assigns a message-number to each message which is good for the duration of the session Client may repeatedly issue any number of commands Each client command is followed by a server response After client issues the QUIT command, server enters UPDATE state.
12 STAT Command The STAT command requests a drop listing of the server indicating number of messages and the size of the mail store Drop listings consist of a positive response code, a space, the number of messages, a space and the size of the maildrop STAT +OK
13 LIST Command The LIST command requests a scan listing indicating message number and size of specified or all message(s) Drop listings consist of the message number, a space and the size of the message LIST +OK 2 messages 2068 octets LIST 2 +OK
14 RETR Command The RETR command retrieves the specified message RETR 1 +OK 1015 octets From: "Mosh Teitelbaum" <mosh.teitelbaum@evoch.com> To: <cfugdemo@evoch.com> Subject: Test Message #1 Date: Wed, 18 Aug :58: [... more headers...] RETR 3 -ERR No such message
15 DELE Command The DELE command marks the specified message for deletion The message is deleted from the current client session but is not actually removed from the message store until the UPDATE state Messages marked as deleted can be undeleted via RSET DELE 1 +OK Message deleted
16 NOOP Command The NOOP command doesn t change anything Usually used to maintain an idle state without having the server terminate the connection from lack of activity NOOP +OK
17 RSET Command The RSET command resets the session (i.e, undeletes all messages marked for deletion) RSET +OK
18 QUIT Command The QUIT command terminates the session If issued in the Authorization state, server does not enter UPDATE state. If issued in the Transaction state, server enters UPDATE state. QUIT +OK POP3 server closing connection
19 TOP Command The optional TOP command retrieves the headers and first n lines of the specified message TOP 2 3 +OK 1053 octets From: "Mosh Teitelbaum" <mosh.teitelbaum@evoch.com> To: <cfugdemo@evoch.com> Subject: Test Message #1 Date: Wed, 18 Aug :58: [... more headers...] 1st line 2nd line 3rd line.
20 UIDL Command The optional UIDL command requests a unique-id listing indicating current message number and permanent unique ID Unique-id listings consist of the message number, a space and the unique ID of the message UIDL +OK E5E E640. UIDL 2 +OK E640
21 POP3 Update State The Update state begins when the client issues the QUIT command from within the Transaction state In the Update state, the server deletes marked messages from the mail store, releases its exclusive access to the mail store, sends a farewell message to the client and terminates the connection
22 <CFPOP> Retrieves and/or deletes messages from a POP mail server. Retrieved messages are placed in specified query. Most common attributes are below: Attribute Server, Port Username, Password Action Name messagenumber uid attachmentpath Description Optional. Specifies server and port to connect to. Optional. Specifies username and password to use for authentication Optional. getheaderonly (default) getall delete Required for getheaderonly and getall. Name of the query object that contains the retrieved message info Comma-delimited list of message numbers. Ignored if uid is specified. Comma-delimited list of Unique Ids. New in CFMX. Optional. Directory in which attachments should be saved
23 <CFPOP> Query Columns For actions getheaderonly and getall, the query specified via the NAME attribute has the following columns: Column Date, From, ReplyTo, Subject, CC, To MessageNumber UID Body, TextBody, HtmlBody header Attachments, AttachmentFiles Description Standard header values The message s MessageID The message s UniqueID First, text/plain, and text/html message parts, respectively. getall only. The message s header part. getall only. Tab delimited lists of the attachment names and locations (full path). getall only.
24 <CFPOP> Date Format Date values returned via <CFPOP> are in UTC/GMT format Thu, 19 Aug :22: To convert to a standard ColdFusion date value in local time use: <CFSCRIPT> function gettimestamp(httptimestring) { // Build Time Stamp var tsparts = ListToArray(httpTimeString, " "); var timestamp = "{ts '" & tsparts[4] & "-" & DateFormat("#tsParts[3]#/1/1970", "mm") & "-" & tsparts[2] & " " & tsparts[5] & "'}"; // Convert to local time timestamp = DateConvert("utc2Local", timestamp); // Return timestamp return timestamp; } </CFSCRIPT>
25 <CFPOP> Example: Get Message Headers <CFPOP ACTION="getHeaderOnly" NAME="getHeaders" SERVER="server" PORT="port" USER="username" PASSWORD="password">
26 <CFPOP> Example: Get Message <CFPOP ACTION="getAll" NAME="getMessage" SERVER="server" PORT="port" USER="username" PASSWORD="password" UID=" E640" ATTACHMENTPATH="C:\Attachments\">
27 <CFPOP> Example: Delete Message <CFPOP ACTION="delete" SERVER="server" PORT="port" USER="username" PASSWORD="password" UID=" E640">
28 POP Resources RFCs from rfc1939.txt Post Office Protocol - Version 3 rfc2384.txt POP URL Scheme rfc2449.txt POP3 Extension Mechanism rfc1734.txt POP3 AUTHentication command rfc2195.txt IMAP/POP AUTHorize Extension for Simple Challenge/Response rfc3206.txt The SYS and AUTH POP Response Codes rfc2595.txt Using TLS with IMAP, POP3 and ACAP rfc1321.txt MD5 Algorithm rfc1521.txt MIME (Multipurpose Internet Mail Extensions) Part One: Mechanisms for Specifying and Describing the Format of Internet Message Bodies rfc2045.txt - Multipurpose Internet Mail Extensions (MIME) Part One: Format of Internet Message Bodies
29 Closing Questions? Contact Info Mosh Teitelbaum evoch, LLC
Network Working Group. Category: Standards Track December 1994
 Network Working Group J. Myers Request for Comments: 1734 Carnegie Mellon Category: Standards Track December 1994 Status of this Memo POP3 AUTHentication command This document specifies an Internet standards
Network Working Group J. Myers Request for Comments: 1734 Carnegie Mellon Category: Standards Track December 1994 Status of this Memo POP3 AUTHentication command This document specifies an Internet standards
Network Working Group. Obsoletes: 1225 June 1993
 Network Working Group M. Rose Request for Comments: 1460 Dover Beach Consulting, Inc. Obsoletes: 1225 June 1993 Post Office Protocol - Version 3 Status of this Memo This RFC specifies an IAB standards
Network Working Group M. Rose Request for Comments: 1460 Dover Beach Consulting, Inc. Obsoletes: 1225 June 1993 Post Office Protocol - Version 3 Status of this Memo This RFC specifies an IAB standards
Network Working Group. Obsoletes: RFC 1081 May 1991
 Network Working Group M. Rose Request for Comments: 1225 Performance Systems International Obsoletes: RFC 1081 May 1991 Status of this Memo Post Office Protocol - Version 3 This memo suggests a simple
Network Working Group M. Rose Request for Comments: 1225 Performance Systems International Obsoletes: RFC 1081 May 1991 Status of this Memo Post Office Protocol - Version 3 This memo suggests a simple
Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 4: General Characteristics of Internet Protocols; the Email Protocol February 10, 2004 Arthur Goldberg Computer Science Department New York University
Internet and Intranet Protocols and Applications Lecture 4: General Characteristics of Internet Protocols; the Email Protocol February 10, 2004 Arthur Goldberg Computer Science Department New York University
SMTP. George Porter CSE 124 February 12, 2015
 SMTP George Porter CSE 124 February 12, 2015 Homework 2 out Announcements Project 2 checkpoint due Tuesday Traditional Applications Two of the most popular The World Wide Web and Email. Broadly speaking,
SMTP George Porter CSE 124 February 12, 2015 Homework 2 out Announcements Project 2 checkpoint due Tuesday Traditional Applications Two of the most popular The World Wide Web and Email. Broadly speaking,
Category: Standards Track December 1994
 Network Working Group M. Crispin Request for Comments: 1730 University of Washington Category: Standards Track December 1994 INTERNET MESSAGE ACCESS PROTOCOL - VERSION 4 Status of this Memo This document
Network Working Group M. Crispin Request for Comments: 1730 University of Washington Category: Standards Track December 1994 INTERNET MESSAGE ACCESS PROTOCOL - VERSION 4 Status of this Memo This document
Request for Comments: Obsoletes: 2095 September IMAP/POP AUTHorize Extension for Simple Challenge/Response
 Network Working Group Request for Comments: 2195 Category: Standards Track Obsoletes: 2095 J. Klensin R. Catoe P. Krumviede MCI September 1997 IMAP/POP AUTHorize Extension for Simple Challenge/Response
Network Working Group Request for Comments: 2195 Category: Standards Track Obsoletes: 2095 J. Klensin R. Catoe P. Krumviede MCI September 1997 IMAP/POP AUTHorize Extension for Simple Challenge/Response
Internet Technology. 03r. Application layer protocols: . Paul Krzyzanowski. Rutgers University. Spring 2016
 Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
Obsoletes: 1730 December 1996 Category: Standards Track. INTERNET MESSAGE ACCESS PROTOCOL - VERSION 4rev1
 Network Working Group M. Crispin Request for Comments: 2060 University of Washington Obsoletes: 1730 December 1996 Category: Standards Track Status of this Memo INTERNET MESSAGE ACCESS PROTOCOL - VERSION
Network Working Group M. Crispin Request for Comments: 2060 University of Washington Obsoletes: 1730 December 1996 Category: Standards Track Status of this Memo INTERNET MESSAGE ACCESS PROTOCOL - VERSION
Application-layer Protocols and Internet Services
 Application-layer Protocols and Internet Services Computer Networks Lecture 8 http://goo.gl/pze5o8 Terminal Emulation 2 Purpose of Telnet Service Supports remote terminal connected via network connection
Application-layer Protocols and Internet Services Computer Networks Lecture 8 http://goo.gl/pze5o8 Terminal Emulation 2 Purpose of Telnet Service Supports remote terminal connected via network connection
Request for Comments: 918 October 1984
 Network Working Group Request for Comments: 918 J. K. Reynolds ISI October 1984 POST OFFICE PROTOCOL Status of this Memo This RFC suggests a simple method for workstations to dynamically access mail from
Network Working Group Request for Comments: 918 J. K. Reynolds ISI October 1984 POST OFFICE PROTOCOL Status of this Memo This RFC suggests a simple method for workstations to dynamically access mail from
Network Applications Electronic Mail
 Network Applications Electronic Mail The OSI way to do this is specified in X.400 (84 & 88) Overall Architecture UA P3 UA MS P7 P1 MTS At the core of the X.400 Message Handling System (MHS) is the Message
Network Applications Electronic Mail The OSI way to do this is specified in X.400 (84 & 88) Overall Architecture UA P3 UA MS P7 P1 MTS At the core of the X.400 Message Handling System (MHS) is the Message
Network Working Group. Document: draft-myers-auth-sasl-02.txt July Simple Authentication and Session Layer. Status of this Memo
 HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 10:23:23 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Tue, 02 Jul 1996 22:21:00 GMT ETag: "361c4c-5e2c-31d9a0cc" Accept-Ranges: bytes Content-Length: 24108 Connection:
HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 10:23:23 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Tue, 02 Jul 1996 22:21:00 GMT ETag: "361c4c-5e2c-31d9a0cc" Accept-Ranges: bytes Content-Length: 24108 Connection:
Electronic Mail. Prof. Indranil Sen Gupta. Professor, Dept. of Computer Science & Engineering Indian Institute of Technology Kharagpur
 Electronic Mail Prof. Indranil Sen Gupta Professor, Dept. of Computer Science & Engineering Indian Institute of Technology Kharagpur 1 Introduction Most heavily used application on the Internet. Simple
Electronic Mail Prof. Indranil Sen Gupta Professor, Dept. of Computer Science & Engineering Indian Institute of Technology Kharagpur 1 Introduction Most heavily used application on the Internet. Simple
Network Working Group. Document: draft-myers-auth-sasl-05.txt September Simple Authentication and Security Layer. Status of this Memo
 HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 10:23:28 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Tue, 01 Oct 1996 22:19:00 GMT ETag: "361f1a-67f0-325198d4" Accept-Ranges: bytes Content-Length: 26608 Connection:
HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 10:23:28 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Tue, 01 Oct 1996 22:19:00 GMT ETag: "361f1a-67f0-325198d4" Accept-Ranges: bytes Content-Length: 26608 Connection:
CIS 505: Software Systems
 CIS 505: Software Systems Spring 2018 Assignment 2: Email servers MS1 due February 16, 2018, at 10:00pm EST MS2+3 due March 1, 2018, at 10:00pm EST 1 Overview For this assignment, you will build two simple
CIS 505: Software Systems Spring 2018 Assignment 2: Email servers MS1 due February 16, 2018, at 10:00pm EST MS2+3 due March 1, 2018, at 10:00pm EST 1 Overview For this assignment, you will build two simple
CN Assignment I. 1. With an example explain how cookies are used in e-commerce application to improve the performance.
 CN Assignment I 1. With an example explain how cookies are used in e-commerce application to improve the performance. In an e-commerce application, when the user sends a login form to the server, the server
CN Assignment I 1. With an example explain how cookies are used in e-commerce application to improve the performance. In an e-commerce application, when the user sends a login form to the server, the server
Network Working Group. Category: Standards Track October Simple Authentication and Security Layer (SASL)
 Network Working Group J. Myers Request for Comments: 2222 Netscape Communications Category: Standards Track October 1997 Status of this Memo Simple Authentication and Security Layer (SASL) This document
Network Working Group J. Myers Request for Comments: 2222 Netscape Communications Category: Standards Track October 1997 Status of this Memo Simple Authentication and Security Layer (SASL) This document
Applications & Application-Layer Protocols: FTP and (SMTP & POP)
 COMP 431 Internet Services & Protocols Applications & Application-Layer Protocols: FTP and E ( & POP) Jasleen Kaur February 7, 2019 Application-Layer Protocols Outline Example client/ systems and their
COMP 431 Internet Services & Protocols Applications & Application-Layer Protocols: FTP and E ( & POP) Jasleen Kaur February 7, 2019 Application-Layer Protocols Outline Example client/ systems and their
TFTP and FTP Basics BUPT/QMUL
 TFTP and FTP Basics BUPT/QMUL 2017-04-24 Agenda File transfer and access TFTP (Trivial File Transfer Protocol) FTP (File Transfer Protocol) NFS (Network File System) 2 File Transfer And Access 3 File Transfer
TFTP and FTP Basics BUPT/QMUL 2017-04-24 Agenda File transfer and access TFTP (Trivial File Transfer Protocol) FTP (File Transfer Protocol) NFS (Network File System) 2 File Transfer And Access 3 File Transfer
Part 4: Message delivery protocols (POP and IMAP) Network News (Usenet News)
 4-1 *:96 Overheads Part 4: Message delivery protocols (POP and IMAP) Network News (Usenet News) More about this course about Internet application protocols can be found at URL: http://www.dsv.su.se/~jpalme/internet-course/int-app-prot-kurs.html
4-1 *:96 Overheads Part 4: Message delivery protocols (POP and IMAP) Network News (Usenet News) More about this course about Internet application protocols can be found at URL: http://www.dsv.su.se/~jpalme/internet-course/int-app-prot-kurs.html
NATO UNCLASSIFIED STANAG 5066: ANNEX F Subnetwork Client Definitions F-1
 Annex F. Subnetwork Client Definitions (information only) This Annex defines interactions with the subnetwork for a set of clients types (i.e., subnetwork clients) to which the HF subnet defined in the
Annex F. Subnetwork Client Definitions (information only) This Annex defines interactions with the subnetwork for a set of clients types (i.e., subnetwork clients) to which the HF subnet defined in the
Set Up with Microsoft Outlook 2013 using POP3
 Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Internet Engineering Task Force (IETF) Category: Experimental. February 2010
 Internet Engineering Task Force (IETF) Request for Comments: 5721 Category: Experimental ISSN: 2070-1721 R. Gellens QUALCOMM Incorporated C. Newman Sun Microsystems February 2010 POP3 Support for UTF-8
Internet Engineering Task Force (IETF) Request for Comments: 5721 Category: Experimental ISSN: 2070-1721 R. Gellens QUALCOMM Incorporated C. Newman Sun Microsystems February 2010 POP3 Support for UTF-8
Category: Standards Track July The Post Office Protocol (POP3) Simple Authentication and Security Layer (SASL) Authentication Mechanism
 Network Working Group R. Siemborski Request for Comments: 5034 Google, Inc. Obsoletes: 1734 A. Menon-Sen Updates: 2449 Oryx Mail Systems GmbH Category: Standards Track July 2007 The Post Office Protocol
Network Working Group R. Siemborski Request for Comments: 5034 Google, Inc. Obsoletes: 1734 A. Menon-Sen Updates: 2449 Oryx Mail Systems GmbH Category: Standards Track July 2007 The Post Office Protocol
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
CSCE 463/612 Networks and Distributed Processing Spring 2018
 CSCE 463/612 Networks and Distributed Processing Spring 2018 Application Layer II Dmitri Loguinov Texas A&M University February 6, 2018 Original slides copyright 1996-2004 J.F Kurose and K.W. Ross 1 Chapter
CSCE 463/612 Networks and Distributed Processing Spring 2018 Application Layer II Dmitri Loguinov Texas A&M University February 6, 2018 Original slides copyright 1996-2004 J.F Kurose and K.W. Ross 1 Chapter
WWW: the http protocol
 Internet apps: their protocols and transport protocols Application e-mail remote terminal access Web file transfer streaming multimedia remote file Internet telephony Application layer protocol smtp [RFC
Internet apps: their protocols and transport protocols Application e-mail remote terminal access Web file transfer streaming multimedia remote file Internet telephony Application layer protocol smtp [RFC
Integrating a directory server
 Integrating a directory server Knox Manage provides a directory service that integrates a client's directory server through a Lightweight Directory Access Protocol (LDAP)-based Active Directory service
Integrating a directory server Knox Manage provides a directory service that integrates a client's directory server through a Lightweight Directory Access Protocol (LDAP)-based Active Directory service
Application: Electronic Mail
 Content Application: Electronic Mail Linda Wu Email system model protocol MIME extensions Mail access protocols (CMPT 471 2003-3) Reference: chapter 27 Notes-19 CMPT 471 2003-3 2 Email System Model Client-
Content Application: Electronic Mail Linda Wu Email system model protocol MIME extensions Mail access protocols (CMPT 471 2003-3) Reference: chapter 27 Notes-19 CMPT 471 2003-3 2 Email System Model Client-
Configuring Request Authentication and Authorization
 CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
RADIUS Configuration. Overview. Introduction to RADIUS. Client/Server Model
 Table of Contents RADIUS Configuration 1 Overview 1 Introduction to RADIUS 1 Client/Server Model 1 Security and Authentication Mechanisms 2 Basic Message Exchange Process of RADIUS 2 RADIUS Packet Format
Table of Contents RADIUS Configuration 1 Overview 1 Introduction to RADIUS 1 Client/Server Model 1 Security and Authentication Mechanisms 2 Basic Message Exchange Process of RADIUS 2 RADIUS Packet Format
Lecture 7 Application Layer. Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it
 Lecture 7 Application Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Application-layer protocols Application: communicating, distributed processes running in network hosts
Lecture 7 Application Layer Antonio Cianfrani DIET Department Networking Group netlab.uniroma1.it Application-layer protocols Application: communicating, distributed processes running in network hosts
[MS-STANXIMAP]: Exchange Internet Message Access Protocol (IMAP) Standards Compliance
![[MS-STANXIMAP]: Exchange Internet Message Access Protocol (IMAP) Standards Compliance [MS-STANXIMAP]: Exchange Internet Message Access Protocol (IMAP) Standards Compliance](/thumbs/77/75606149.jpg) [MS-STANXIMAP]: Exchange Internet Message Access Protocol (IMAP) Standards Compliance Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes
[MS-STANXIMAP]: Exchange Internet Message Access Protocol (IMAP) Standards Compliance Intellectual Property Rights Notice for Open Specifications Documentation Technical Documentation. Microsoft publishes
Adding your IMAP Mail Account in Outlook 2013 on Windows
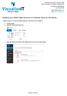 Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Appendix. Web Command Error Codes. Web Command Error Codes
 Appendix Web Command s Error codes marked with * are received in responses from the FTP server, and then returned as the result of FTP command execution. -501 Incorrect parameter type -502 Error getting
Appendix Web Command s Error codes marked with * are received in responses from the FTP server, and then returned as the result of FTP command execution. -501 Incorrect parameter type -502 Error getting
Network Working Group Request for Comments: 2595 Category: Standards Track June 1999
 Network Working Group C. Newman Request for Comments: 2595 Innosoft Category: Standards Track June 1999 Using TLS with IMAP, POP3 and ACAP Status of this Memo This document specifies an Internet standards
Network Working Group C. Newman Request for Comments: 2595 Innosoft Category: Standards Track June 1999 Using TLS with IMAP, POP3 and ACAP Status of this Memo This document specifies an Internet standards
Lecture 6: Application Layer Web proxies, , and SMTP
 Lecture 6: Application Layer Web proxies, Email, and SMTP COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016,
Lecture 6: Application Layer Web proxies, Email, and SMTP COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016,
Service User Manual. Outlook By SYSCOM (USA) May 2nd, Version 1.0. Outlook 2013 Ver.1.0
 Outlook 2013 By SYSCOM (USA) May 2nd, 2016 Version 1.0 1 Contents 1. How to Setup POP3/SMTP Setup for Outlook 2013... 3 2. How to Setup IMAP for Outlook 2013... 14 3. How to Manage Spam Filter... 25 2
Outlook 2013 By SYSCOM (USA) May 2nd, 2016 Version 1.0 1 Contents 1. How to Setup POP3/SMTP Setup for Outlook 2013... 3 2. How to Setup IMAP for Outlook 2013... 14 3. How to Manage Spam Filter... 25 2
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 15 Create an Identity Rule, page 15 Manage a Realm, page 20 Manage an Identity
Chapter 2 Application Layer
 Chapter 2 Application Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Chapter 2 Application Layer A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
. indigoo.com INTRODUCTION TO MAIL TRANSFER PROTOCOLS FOR THE INTERNET. Peter R. Egli INDIGOO.COM. 1/35 Rev Peter R.
 EMAIL INTRODUCTION TO MAIL TRANSFER PROTOCOLS FOR THE INTERNET Peter R. Egli INDIGOO.COM 1/35 Contents 1. EMail Electronic Mail RFC821/RFC822 2. Email Elements 3. Email Message 4. Email Transfer with SMTP
EMAIL INTRODUCTION TO MAIL TRANSFER PROTOCOLS FOR THE INTERNET Peter R. Egli INDIGOO.COM 1/35 Contents 1. EMail Electronic Mail RFC821/RFC822 2. Email Elements 3. Email Message 4. Email Transfer with SMTP
Gatesms.eu Mobile Solutions for Business
 TECHNICAL SPECIFICATIONS XML Web API GATESMS.EU, version 1.1 Prepared by: Gatesms.eu Contents Document version history...3 Security...3 General requirements...3 HTTP transmission security mechanism...3
TECHNICAL SPECIFICATIONS XML Web API GATESMS.EU, version 1.1 Prepared by: Gatesms.eu Contents Document version history...3 Security...3 General requirements...3 HTTP transmission security mechanism...3
Table of Contents. Why doesn t the phone pass 802.1X authentication?... 16
 Table of Contents ABOUT 802.1X... 3 YEALINK PHONES COMPATIBLE WITH 802.1X... 3 CONFIGURING 802.1X SETTINGS... 4 Configuring 802.1X using Configuration Files... 4 Configuring 802.1X via Web User Interface...
Table of Contents ABOUT 802.1X... 3 YEALINK PHONES COMPATIBLE WITH 802.1X... 3 CONFIGURING 802.1X SETTINGS... 4 Configuring 802.1X using Configuration Files... 4 Configuring 802.1X via Web User Interface...
What is ? TCP/IP Standard Applications for Electronic Mail. Agenda. History
 What is E-Mail? TCP/IP Standard Applications for Electronic Mail Email, SMTP, POP, IMAP, MIME E-Mail (or "email") is the most widely used Internet application Note: email was one of TCP/IP's keys to success:
What is E-Mail? TCP/IP Standard Applications for Electronic Mail Email, SMTP, POP, IMAP, MIME E-Mail (or "email") is the most widely used Internet application Note: email was one of TCP/IP's keys to success:
Computer Networks. Wenzhong Li. Nanjing University
 Computer Networks Wenzhong Li Nanjing University 1 Chapter 8. Internet Applications Internet Applications Overview Domain Name Service (DNS) Electronic Mail File Transfer Protocol (FTP) WWW and HTTP Content
Computer Networks Wenzhong Li Nanjing University 1 Chapter 8. Internet Applications Internet Applications Overview Domain Name Service (DNS) Electronic Mail File Transfer Protocol (FTP) WWW and HTTP Content
How do I configure my LPL client to use SSL for incoming mail?
 How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
Category: Standards Track August POP URL Scheme. Status of this Memo
 Network Working Group R. Gellens Request for Comments: 2384 QUALCOMM, Incorporated Category: Standards Track August 1998 Status of this Memo POP URL Scheme This document specifies an Internet standards
Network Working Group R. Gellens Request for Comments: 2384 QUALCOMM, Incorporated Category: Standards Track August 1998 Status of this Memo POP URL Scheme This document specifies an Internet standards
Synology MailPlus Server Administrator's Guide. Based on MailPlus Server 1.4.0
 Synology MailPlus Server Administrator's Guide Based on MailPlus Server 1.4.0 Table of Contents Chapter 1: Introduction Chapter 2: Getting Started with MailPlus Server Connect Synology NAS to the Internet
Synology MailPlus Server Administrator's Guide Based on MailPlus Server 1.4.0 Table of Contents Chapter 1: Introduction Chapter 2: Getting Started with MailPlus Server Connect Synology NAS to the Internet
Network Working Group Internet Draft: Using TLS with IMAP, POP3 and ACAP Document: draft-newman-tls-imappop-08.txt February 1999
 Network Working Group C. Newman Internet Draft: Using TLS with IMAP, POP3 and ACAP Innosoft Document: draft-newman-tls-imappop-08.txt February 1999 Using TLS with IMAP, POP3 and ACAP Status of this memo
Network Working Group C. Newman Internet Draft: Using TLS with IMAP, POP3 and ACAP Innosoft Document: draft-newman-tls-imappop-08.txt February 1999 Using TLS with IMAP, POP3 and ACAP Status of this memo
Basics BUPT/QMUL
 Email Basics BUPT/QMUL 2017-05-08 Agenda Brief introduction to email Components of email system Email Standards Summary 2 Brief Introduction To Email 3 What is Email? Electronic Mail (email, e-mail) Provides
Email Basics BUPT/QMUL 2017-05-08 Agenda Brief introduction to email Components of email system Email Standards Summary 2 Brief Introduction To Email 3 What is Email? Electronic Mail (email, e-mail) Provides
PPP Configuration Options
 PPP Configuration Options 1 PPP Configuration Options PPP can be configured to support various functions including: Authentication using either PAP or CHAP Compression using either Stacker or Predictor
PPP Configuration Options 1 PPP Configuration Options PPP can be configured to support various functions including: Authentication using either PAP or CHAP Compression using either Stacker or Predictor
Basics BUPT/QMUL
 Email Basics BUPT/QMUL 2014-04-28 Agenda Brief introduction to email Components of email system Email Standards Summary 2 Brief Introduction To Email 3 What is Email? Electronic Mail (email, e-mail) Provides
Email Basics BUPT/QMUL 2014-04-28 Agenda Brief introduction to email Components of email system Email Standards Summary 2 Brief Introduction To Email 3 What is Email? Electronic Mail (email, e-mail) Provides
Network Working Group Internet Draft: Using TLS with IMAP4, POP3 and ACAP Document: draft-newman-tls-imappop-06.txt January 1999
 Network Working Group C. Newman Internet Draft: Using TLS with IMAP4, POP3 and ACAP Innosoft Document: draft-newman-tls-imappop-06.txt January 1999 Using TLS with IMAP4, POP3 and ACAP Status of this memo
Network Working Group C. Newman Internet Draft: Using TLS with IMAP4, POP3 and ACAP Innosoft Document: draft-newman-tls-imappop-06.txt January 1999 Using TLS with IMAP4, POP3 and ACAP Status of this memo
Agenda. What is ? Brief Introduction To . History Of . Components Of System. Basics
 Agenda Email Basics BUPT/QMUL 2012-04-09 Brief introduction to email Components of email system Email Standards Summary Refer to Chapter 27, textbook 2 Brief Introduction To Email 3 What is Email? Electronic
Agenda Email Basics BUPT/QMUL 2012-04-09 Brief introduction to email Components of email system Email Standards Summary Refer to Chapter 27, textbook 2 Brief Introduction To Email 3 What is Email? Electronic
Request for Comments: 3206 Category: Standards Track February 2002
 Network Working Group R. Gellens Request for Comments: 3206 QUALCOMM Category: Standards Track February 2002 Status of this Memo The SYS and AUTH POP Response Codes This document specifies an Internet
Network Working Group R. Gellens Request for Comments: 3206 QUALCOMM Category: Standards Track February 2002 Status of this Memo The SYS and AUTH POP Response Codes This document specifies an Internet
CSCE 813 Internet Security Secure Services I
 CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
Outlook 2013 settings for workflow.rocks server
 Outlook 2013 settings for workflow.rocks email server February, 2016 For all questions regarding this document, please email support@thetaxworkflow.com Table of Contents Set up your email account... 3
Outlook 2013 settings for workflow.rocks email server February, 2016 For all questions regarding this document, please email support@thetaxworkflow.com Table of Contents Set up your email account... 3
Realms and Identity Policies
 The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 14 Create an Identity Rule, page 15 Manage a Realm, page 17 Manage an Identity
The following topics describe realms and identity policies: About, page 1 Create a Realm, page 8 Create an Identity Policy, page 14 Create an Identity Rule, page 15 Manage a Realm, page 17 Manage an Identity
Electronic mail, usually called , consists of simple text messages a piece of text sent to a recipient via the internet.
 1 Electronic Mail Electronic mail, usually called e-mail, consists of simple text messages a piece of text sent to a recipient via the internet. E-mail Clients To read e-mail, we use an e-mail client,
1 Electronic Mail Electronic mail, usually called e-mail, consists of simple text messages a piece of text sent to a recipient via the internet. E-mail Clients To read e-mail, we use an e-mail client,
Network Services, VU 2.0
 Network Services, VU 2.0 Email (SMTP, POP3, IMAP) News Dipl.-Ing. Johann Oberleiter Institute for Informationsystems, Distributed Systems Group Agenda Mail general info SMTP (Simple Mail Transfer Protocol)
Network Services, VU 2.0 Email (SMTP, POP3, IMAP) News Dipl.-Ing. Johann Oberleiter Institute for Informationsystems, Distributed Systems Group Agenda Mail general info SMTP (Simple Mail Transfer Protocol)
GroupWise Software Developer Kit IMAP Support. February 2018
 GroupWise Software Developer Kit IMAP Support February 2018 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
GroupWise Software Developer Kit IMAP Support February 2018 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
Fig (1) sending and receiving s
 Electronic Mail Protocols (SMTP, POP, IMAP) It is important to (1) distinguish the user interface (i.e., your mail reader) from the underlying message transfer protocols (such as SMTP, POP or IMAP), and
Electronic Mail Protocols (SMTP, POP, IMAP) It is important to (1) distinguish the user interface (i.e., your mail reader) from the underlying message transfer protocols (such as SMTP, POP or IMAP), and
Network Working Group. Category: Standards Track March 2001
 Network Working Group M. Rose Request For Comments: 3080 Invisible Worlds, Inc. Category: Standards Track March 2001 Status of this Memo The Blocks Extensible Exchange Protocol Core This document specifies
Network Working Group M. Rose Request For Comments: 3080 Invisible Worlds, Inc. Category: Standards Track March 2001 Status of this Memo The Blocks Extensible Exchange Protocol Core This document specifies
MIME and the Web. draft-masinter-mime-web-info-01.txt I-D by Larry Masinter Presented by Alexey Melnikov
 MIME and the Web draft-masinter-mime-web-info-01.txt I-D by Larry Masinter Presented by Alexey Melnikov History Multipurpose Internet Mail Extensions (MIME) RFC 2045, RFC 2046, MIME was originally invented
MIME and the Web draft-masinter-mime-web-info-01.txt I-D by Larry Masinter Presented by Alexey Melnikov History Multipurpose Internet Mail Extensions (MIME) RFC 2045, RFC 2046, MIME was originally invented
TMail Temporary Multi Domain System. API Documentation. TMail Temporary Multi Domain System. By Harshit Peer
 API Documentation By Harshit Peer List of Domains URL https://yourdomain.com/actions.php?action=getdomains&apikey=yourkey Parameters Key action apikey Value getdomains Key which you may have set in your
API Documentation By Harshit Peer List of Domains URL https://yourdomain.com/actions.php?action=getdomains&apikey=yourkey Parameters Key action apikey Value getdomains Key which you may have set in your
1 Setting Up GroupWise to Work with
 1 Setting Up GroupWise to Work with POP3 Mailboxes Overview If you use domain mail forwarding, incoming Internet e-mail for your organization can be handled by a program called the POP Forwarding Agent
1 Setting Up GroupWise to Work with POP3 Mailboxes Overview If you use domain mail forwarding, incoming Internet e-mail for your organization can be handled by a program called the POP Forwarding Agent
CYBERSECURITY CHALLENGES FOR YOUR CLASSROOM:
 SELECTED STADIUM CYBERSECURITY CHALLENGES FOR YOUR CLASSROOM: META, FTP, DNS, HTTP, TELNET, AND SSH AUTH Meta from 2015 Fall Season NCL puzzle: http://www.nationalcyberleague.org/2016/spring/solutions_files/ncl-2015-meta.jpg
SELECTED STADIUM CYBERSECURITY CHALLENGES FOR YOUR CLASSROOM: META, FTP, DNS, HTTP, TELNET, AND SSH AUTH Meta from 2015 Fall Season NCL puzzle: http://www.nationalcyberleague.org/2016/spring/solutions_files/ncl-2015-meta.jpg
21.1 FTP. Connections
 21.1 FTP File Transfer Protocol (FTP) is the standard mechanism provided by TCP/IP for copying a file from one host to another. Although transferring files from one system to another seems simple and straightforward,
21.1 FTP File Transfer Protocol (FTP) is the standard mechanism provided by TCP/IP for copying a file from one host to another. Although transferring files from one system to another seems simple and straightforward,
The following instructions will document how to set up an IMAP account using Lanair s hosted service.
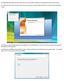 The following instructions will document how to set up an IMAP email account using Lanair s hosted email service. 1.) When you first start up outlook, and if there is no account currently associated with
The following instructions will document how to set up an IMAP email account using Lanair s hosted email service. 1.) When you first start up outlook, and if there is no account currently associated with
CFX_POP3 - Tag Reference May build 263.
 CFX_POP3 - Tag Reference 26 - May - 2005 build 263 http://www.newmediadevelopment.net 2 CFX_POP3 Tag Reference CFX_POP3 - Introduction... 1 CFX_POP3 Syntax... 2 SERVER... 3 PORT... 3 USERNAME... 3 PASSWORD...
CFX_POP3 - Tag Reference 26 - May - 2005 build 263 http://www.newmediadevelopment.net 2 CFX_POP3 Tag Reference CFX_POP3 - Introduction... 1 CFX_POP3 Syntax... 2 SERVER... 3 PORT... 3 USERNAME... 3 PASSWORD...
Employing VisNetic MailServer Security Features
 Employing VisNetic MailServer Security Features VisNetic MailServer p o w e r f u l email server VisNetic MailServer Security Features VisNetic MailServer includes a sophisticated and broad array of security
Employing VisNetic MailServer Security Features VisNetic MailServer p o w e r f u l email server VisNetic MailServer Security Features VisNetic MailServer includes a sophisticated and broad array of security
Configuring 802.1X Settings on the WAP351
 Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Internet Technology 2/10/2016
 Internet Technology 03r. Application layer protocols: email Email: (Simple Mail Transfer Protocol) Paul Krzyzanowski Rutgers University Spring 2016 1 2 Simple Mail Transfer Protocol () Protocol defined
Internet Technology 03r. Application layer protocols: email Email: (Simple Mail Transfer Protocol) Paul Krzyzanowski Rutgers University Spring 2016 1 2 Simple Mail Transfer Protocol () Protocol defined
Operation Manual AAA RADIUS HWTACACS H3C S5500-EI Series Ethernet Switches. Table of Contents
 Table of Contents Table of Contents... 1-1 1.1 AAA/RADIUS/HWTACACS Over... 1-1 1.1.1 Introduction to AAA... 1-1 1.1.2 Introduction to RADIUS... 1-3 1.1.3 Introduction to HWTACACS... 1-9 1.1.4 Protocols
Table of Contents Table of Contents... 1-1 1.1 AAA/RADIUS/HWTACACS Over... 1-1 1.1.1 Introduction to AAA... 1-1 1.1.2 Introduction to RADIUS... 1-3 1.1.3 Introduction to HWTACACS... 1-9 1.1.4 Protocols
Configuring a Virtual-Domain Server with LDAP
 This document provides a recipe for configuring a Mirapoint server to perform LDAP authentication, message routing, and email access proxying. Configuration requires two activities: LDAP Database User
This document provides a recipe for configuring a Mirapoint server to perform LDAP authentication, message routing, and email access proxying. Configuration requires two activities: LDAP Database User
WEBppliance for Windows User Administrator's Help
 WEBppliance for Windows User Administrator's Help September 23, 2003 Contents About This Document...3 How to use this Help system...4 Getting started...6 What to do first... 6 Viewing your account settings...
WEBppliance for Windows User Administrator's Help September 23, 2003 Contents About This Document...3 How to use this Help system...4 Getting started...6 What to do first... 6 Viewing your account settings...
COMMUNICATING WITH THE LOXONE MINISERVER. Loxone Config
 COMMUNICATING WITH THE LOXONE MINISERVER Loxone Config In order to modernize our interface, we improved our Miniserver, allowing it to communicate with WebSocket clients that conform to the RFC6455. This
COMMUNICATING WITH THE LOXONE MINISERVER Loxone Config In order to modernize our interface, we improved our Miniserver, allowing it to communicate with WebSocket clients that conform to the RFC6455. This
Network Working Group Request for Comments: 1339 U. of Illinois at Urbana-Champaign June 1992
 Network Working Group Request for Comments: 1339 S. Dorner P. Resnick U. of Illinois at Urbana-Champaign June 1992 Remote Mail Checking Protocol Status of this Memo This memo defines an Experimental Protocol
Network Working Group Request for Comments: 1339 S. Dorner P. Resnick U. of Illinois at Urbana-Champaign June 1992 Remote Mail Checking Protocol Status of this Memo This memo defines an Experimental Protocol
Chapter 2 part B: outline
 Chapter 2 part B: outline 2.3 FTP 2.4 electronic, POP3, IMAP 2.5 DNS Application Layer 2-1 FTP: the file transfer protocol at host FTP interface FTP client local file system file transfer FTP remote file
Chapter 2 part B: outline 2.3 FTP 2.4 electronic, POP3, IMAP 2.5 DNS Application Layer 2-1 FTP: the file transfer protocol at host FTP interface FTP client local file system file transfer FTP remote file
Cryptography and Network Security
 Cryptography and Network Security Third Edition by William Stallings Lecture slides by Lawrie Brown Chapter 14 Authentication Applications We cannot enter into alliance with neighbouring princes until
Cryptography and Network Security Third Edition by William Stallings Lecture slides by Lawrie Brown Chapter 14 Authentication Applications We cannot enter into alliance with neighbouring princes until
Black Box DCX3000 / DCX1000 Using the API
 Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
Black Box DCX3000 / DCX1000 Using the API updated 2/22/2017 This document will give you a brief overview of how to access the DCX3000 / DCX1000 API and how you can interact with it using an online tool.
CS 43: Computer Networks. 12: and SMTP September 28, 2018
 CS 43: Computer Networks 12: Email and SMTP September 28, 2018 A. HTTP Mail s communicate using B. IMAP C. POP D. SMTP Lecture 12 - Slide 2 Mail s typically A. send messages directly from the sending s
CS 43: Computer Networks 12: Email and SMTP September 28, 2018 A. HTTP Mail s communicate using B. IMAP C. POP D. SMTP Lecture 12 - Slide 2 Mail s typically A. send messages directly from the sending s
April 24, 1998 Expires in six months. SMTP Service Extension for Secure SMTP over TLS. Status of this memo
 HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 00:24:41 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Mon, 27 Apr 1998 14:31:00 GMT ETag: "2e9b64-31dd-354496a4" Accept-Ranges: bytes Content-Length: 12765 Connection:
HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 00:24:41 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Mon, 27 Apr 1998 14:31:00 GMT ETag: "2e9b64-31dd-354496a4" Accept-Ranges: bytes Content-Length: 12765 Connection:
CS408: Black-box Testing
 CS408: Black-box Testing (due 9/25 Midnight) Contents 1 Project Description 1 2 Setup the ftp server 1 3 Connect to the ftp server 2 3.1 Control connection.......................... 2 3.2 Data connection...........................
CS408: Black-box Testing (due 9/25 Midnight) Contents 1 Project Description 1 2 Setup the ftp server 1 3 Connect to the ftp server 2 3.1 Control connection.......................... 2 3.2 Data connection...........................
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide
 STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
Text-Based Protocols. Many common protocols based on sending text messages. Built atop the TCP stream protocol. Lines terminated with \r\n.
 Text-Based Protocols Many common protocols based on sending text messages. Built atop the TCP stream protocol. Lines terminated with \r\n. Traditional Web Apps Ch. 4 + The line convention essentially breaks
Text-Based Protocols Many common protocols based on sending text messages. Built atop the TCP stream protocol. Lines terminated with \r\n. Traditional Web Apps Ch. 4 + The line convention essentially breaks
About 802.1X... 3 Yealink IP Phones Compatible with 802.1X... 3 Configuring 802.1X Settings... 5 Configuring 802.1X using configuration files...
 About 802.1X... 3 Yealink IP Phones Compatible with 802.1X... 3 Configuring 802.1X Settings... 5 Configuring 802.1X using configuration files...5 Configuring 802.1X via web user interface...8 Configuring
About 802.1X... 3 Yealink IP Phones Compatible with 802.1X... 3 Configuring 802.1X Settings... 5 Configuring 802.1X using configuration files...5 Configuring 802.1X via web user interface...8 Configuring
The table below lists the protocols supported by Yealink SIP IP phones with different versions.
 Table of Contents About 802.1X... 3 Yealink IP Phones Compatible with 802.1X... 3 Configuring 802.1X Settings... 5 Configuring 802.1X Using Configuration Files... 6 Configuring 802.1X via Web User Interface...
Table of Contents About 802.1X... 3 Yealink IP Phones Compatible with 802.1X... 3 Configuring 802.1X Settings... 5 Configuring 802.1X Using Configuration Files... 6 Configuring 802.1X via Web User Interface...
SETUP FOR OUTLOOK (Updated October, 2018)
 EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
EMAIL SETUP FOR OUTLOOK (Updated October, 2018) This tutorial will show you how to set up your email in Outlook using IMAP or POP. It also explains how to configure Outlook for MAC. Click on your version
Distributed Systems. Ordering of events. Atomicity. State. Competition for resources. Selecting a co-ordinator. Architectures. Distributed clocks
 By 'geographic region' IP Addresses Giving things unique identifiers Handed out by a server? URLs DNS By 'vendor' MAC addresses stateless systems State stateful systems The Web Email Ditributed Games Peer
By 'geographic region' IP Addresses Giving things unique identifiers Handed out by a server? URLs DNS By 'vendor' MAC addresses stateless systems State stateful systems The Web Email Ditributed Games Peer
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
Configuring Health Monitoring
 CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
ESMTP Support for Cisco IOS Firewall
 ESMTP Support for Cisco IOS Firewall Finding Feature Information ESMTP Support for Cisco IOS Firewall Last Updated: June 14, 2011 The ESMTP Support for Cisco IOS Firewall feature enhances the Cisco IOS
ESMTP Support for Cisco IOS Firewall Finding Feature Information ESMTP Support for Cisco IOS Firewall Last Updated: June 14, 2011 The ESMTP Support for Cisco IOS Firewall feature enhances the Cisco IOS
Note: CONTENTS. 1. Outlook Express (IMAP) 2. Microsoft Outlook (IMAP) 3. Eudora (IMAP) 4. Thunderbird (IMAP) 5. Outlook Express (POP)
 CONTENTS 1. Outlook Express (IMAP) 2. Microsoft Outlook (IMAP) 3. Eudora (IMAP) 4. Thunderbird (IMAP) 5. Outlook Express (POP) Note: Prior to configuring, please ensure that your ID is enabled for POP/IMAP.
CONTENTS 1. Outlook Express (IMAP) 2. Microsoft Outlook (IMAP) 3. Eudora (IMAP) 4. Thunderbird (IMAP) 5. Outlook Express (POP) Note: Prior to configuring, please ensure that your ID is enabled for POP/IMAP.
Internet Protocol Stack! Principles of Network Applications! Some Network Apps" (and Their Protocols)! Application-Layer Protocols! Our goals:!
 Internet Protocol Stack! Principles of Network Applications! application: supporting network applications!! HTTP,, FTP, etc.! transport: endhost-endhost data transfer!! TCP, UDP! network: routing of datagrams
Internet Protocol Stack! Principles of Network Applications! application: supporting network applications!! HTTP,, FTP, etc.! transport: endhost-endhost data transfer!! TCP, UDP! network: routing of datagrams
Computer Networking. Chapter #1. Dr. Abdulrhaman Alameer
 Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Configuration examples for the D-Link NetDefend Firewall series DFL-260/860
 Configuration examples for the D-Link NetDefend Firewall series DFL-260/860 Scenario: How to configure User Authentication for multiple groups Last update: 2008-04-29 Overview In this document, the notation
Configuration examples for the D-Link NetDefend Firewall series DFL-260/860 Scenario: How to configure User Authentication for multiple groups Last update: 2008-04-29 Overview In this document, the notation
Radius, LDAP, Radius, Kerberos used in Authenticating Users
 CSCD 303 Lecture 5 Fall 2018 Radius, LDAP, Radius, Kerberos used in Authenticating Users Kerberos Authentication and Authorization Previously Said that identification, authentication and authorization
CSCD 303 Lecture 5 Fall 2018 Radius, LDAP, Radius, Kerberos used in Authenticating Users Kerberos Authentication and Authorization Previously Said that identification, authentication and authorization
