Poulsen, Kevin Wednesday, November 07, :54 PM Singel, Ryan FW: [hush.com # ] Journalist's query
|
|
|
- Harry Skinner
- 5 years ago
- Views:
Transcription
1 Singel, Ryan From: Sent: To: Subject: Poulsen, Kevin Wednesday, November 07, :54 PM Singel, Ryan FW: [hush.com # ] Journalist's query -----Original Message----- From: Brian Smith Sent: Wednesday, November 07, :40 PM To: Poulsen, Kevin Subject: RE: [hush.com # ] Journalist's query Hi Kevin, Sorry, I've been really busy the past couple of days. However, I've collected some info from our internal counsel that hopefully will make things a bit clearer. Like any company doing this sort of thing for a long time, we've had to deal with quite a few requests from law enforcement. In these situations, we always require that a court order be issued, and that court order must be issued by the Supreme Court of British Columbia. For such an order to be issued in respect of a request where the alleged offenses have not occurred in Canada, a formal request must be made to the government of Canada under an applicable Mutual Legal Assistance Treaty by the country in which the requesting law enforcement agency is located. Assuming the government of Canada accepts the request, or if the alleged offense has occurred in Canada, an application is then made by the Department of Justice to the Supreme Court of British Columbia for an order that Hush be required to provide certain information. That application must be supported by Affidavit evidence such that the presiding Judge determines that an offense has occurred and that Hush has evidence of same. We receive many requests for information from law enforcement authorities, including subpoenas, but on being made aware of the requirements, a large percentage of them do not proceed. To date, we have not challenged a court order in court, as we have made it clear that the court orders that we would accept must follow our guidelines of requiring only actions that can be limited to the specific user accounts named in the court order. That is to say, any sort of requirement for broad data collection would not be acceptable. There's been some discussion about Hushmail in this context on the web lately, and I think it's a healthy thing. There are situations where Hushmail is an appropriate tool and situations where is not. It is useful for avoiding general Carnivore-type government surveillance, and protecting your data from hackers, but definitely not suitable for protecting your data if you are engaging in illegal activity that could result in a Canadian court order. That's also backed up by the fact that all Hushmail users agree to our terms of service, which state that Hushmail is not to be used for illegal activity. However, when using Hushmail, users can be assured that no access to data, including server logs, etc., will be granted without a specific court order. Yes, you are right about the fact that view source is not going to reveal anything about the compiled Java code. However, it does reveal the HTML in which the applet is embedded, and whether the applet is actually being used at all. Anyway, I meant that just as an example. The general point is that it is potentially detectable by the end-user, even though it is not practical to perform this operation every time. This means that in Java mode the level of trust the user must place in us is somewhat reduced, although not eliminated. The extra security given by the Java applet is not particularly relevant, in the practical sense, if an individual account is targeted. However, it makes it less necessary to take us at our word when we say we do not do any broad collection of private user data. The issues with applet verification were pointed out by Schneier back when Hushmail originally came out. 1
2 Regards, Brian On Wed, 07 Nov :44: "Poulsen, Kevin" wrote: Hi Brian, I want to make sure you didn't send me a reply to this message that I missed. I think we're going to write up something on this issue. K -----Original Message----- From: Poulsen, Kevin Sent: Monday, November 05, :16 AM To: 'Brian Smith' Subject: RE: [hush.com # ] Journalist's query Speaking generally, and not specifically about the affidavit I sent you, it seems like if Hushmail can be compelled by legal process to actively capture a private key, you could also be compelled to send a user a modified version of your Java applet that would send the user's private key to Hushmail or a law enforcment agency. Unless I'm missing something, "view source" wouldn't help a user against this type of attack, since the tinkering would be done in the compiled Java code. Are you free to say whether you've been obliged to do this, and if so, how often. And have you challenged in court an order compelling the collection and production of private keys? Kevin Poulsen senior editor -- wired news office: mobile: klp@wired.com -----Original Message----- From: Brian Smith [mailto:sbs@hushmail.com] Sent: Monday, November 05, :53 AM To: Poulsen, Kevin Subject: RE: [hush.com # ] Journalist's query Kevin, Yes, you are right. That's why in the matrix on that help page it shows "Not protected" for "Attacker controls webserver while you are accessing your ". That actually goes for Java and non-java, with the difference being that in Java mode, what the attacker does is potentially detectable by the user (via view source in the browser). For this reason a web-based service is never going to reach the rigorous level of security of an entirely client-based solution like GnuPG. However, the attack required to get encrypted messages from Hushmail is significantly more difficult than simply recovering messages from a server hard drive. Brian 2
3 On Mon, 05 Nov :13: "Poulsen, Kevin" wrote: Thanks again Brian for your quick response. I just want to make sure I understand this correctly. Is the case of the non-java user, it sounds the only option available to an attacker would require that someone reconfigure your servers to store the user's private key during the brief time that it's unencrypted. In other words, if an attacker gains access to your servers they still can't access the content of my -- until I next log in. Then everything I've received, or subsequently receive, is compromised. K -----Original Message----- From: Brian Smith [mailto:sbs@hushmail.com] Sent: Monday, November 05, :38 AM To: Poulsen, Kevin Subject: RE: [hush.com # ] Journalist's query Hi Kevin, I can't comment specifically on the affidavit, but I can clear up your questions about the architecture. The only way to decrypt encrypted Hushmail messages stored on our servers is with the private keys associated with the senders and recipients of those messages, and the only way to access those private keys is with the associated passphrases. Since early 2006, Hushmail can run in a couple of different configurations, which provide different balances of usability and security. One uses a Java applet, one does not. These links give a pretty full explanation of the different levels of security between the two version: i t y/java/index.html The key point, though, is that in the non-java configuration, private key and passphrase operations are performed on the server- side. This requires that users place a higher level of trust in our servers as a trade off for the better usability they get from not having to install Java and load an applet. 3
4 This might clarify things a bit when you are considering what actions we might be required to take under a court order. Again, I stress that our requirement in complying with a court order is that we not take actions that would affect users other than those specifically named in the order. BTW, if you have an older Hushmail account yourself, it may not have the non-java option available. If that's the case, I can switch that on for you. Regards, Brian On Thu, 01 Nov :59: "Poulsen, Kevin" <Kevin_Poulsen@wired.com wrote: Hi Brian, Thanks for your reply on this. I have a related question. This law enforcement affidavit (below) in a steroid sales case indicates that the police obtained, not just the IP addresses of users, but the actual content of mail sent to and from three separate Hushmail accounts. I understand that you have to comply with legal process, but I thought that Hushmail's architecture made it impossible for anybody, including your company, to access s' contents. Is that wrong? e. prod_ affiliate.25.pdf K Kevin Poulsen senior editor -- wired news office: mobile: klp@wired.com -----Original Message----- From: Brian Smith [mailto:sbs@hushmail.com] Sent: Wednesday, September 19, :10 PM To: Poulsen, Kevin Subject: [hush.com # ] Journalist's query Hi Kevin, Our policy is that we only release user information under court order from a court of British Columbia. 4
5 ( When a US agency requires information, they have to work in co- operation with Canadian authorities. While I'm not legal counsel, I believe that most of this is handled through the Mutual Legal Assistance (MLAT) process. From our perspective, the end result is always a Canadian court order. We comply fully with Canadian court orders, so long as they apply to specifically identified accounts as opposed to broad data collection. If you need any more info, let me know. Brian Smith CTO Hush Communications Corporation sbs@hushmail.com (604) ext 222 On Wed Sep 19 00:09: , klp@wired.com wrote: Hi Hushmail. I'm working on a story about Max Butler, a hacker who was recently indicted for a bunch of credit card related stuff in the U.S. It turns out U.S. law enforcment traced Butler through his Hushmail account. A U.S. Secret Service affidavit says "Secret Service has obtained Internet Protocol (IP) connection logs for the account, digits@hush.com. On multiple occasions, the account was accessed from a computer assigned the IP addresses ," etc. I'm just wondering what steps the Secret Service goes to in order to get information like that, given that you're located in Canada. Thanks in advance! Kevin Poulsen senior editor - wired news office: mobile: klp@wired.com 5
Happy to chat about this, however the final authority id Management however he would probably seek our advice on the content anyway.
 From: Subject: Date: Dann, Nicole RE: FOI release [DLM=Sensitive] Tuesday, 2 February 2016 3:17:28 PM Hi Nicole, I left a voice message. I would not be at all comfortable letting the file out with all
From: Subject: Date: Dann, Nicole RE: FOI release [DLM=Sensitive] Tuesday, 2 February 2016 3:17:28 PM Hi Nicole, I left a voice message. I would not be at all comfortable letting the file out with all
October Dear Clients of Exceptional Bear: Re: security issues
 October 2013 Dear Clients of Exceptional Bear: Re: security issues For security reasons, I am asking all clients to open a free Hushmail account. Although Hushmail is encrypted and password protected,
October 2013 Dear Clients of Exceptional Bear: Re: security issues For security reasons, I am asking all clients to open a free Hushmail account. Although Hushmail is encrypted and password protected,
PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between
 MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
MITOCW Lecture 10A [MUSIC PLAYING] PROFESSOR: Last time, we took a look at an explicit control evaluator for Lisp, and that bridged the gap between all these high-level languages like Lisp and the query
Register FAQ Calendar Today's Posts Search
 Custom Search Highly Liquid Forum > Current Products > UMR2 Casio SK-5 MIDI Retrofit Guide User Name User Name Password Remember Me? Log in Register FAQ Calendar Today's Posts Search Page 1 of 2 1 2 >
Custom Search Highly Liquid Forum > Current Products > UMR2 Casio SK-5 MIDI Retrofit Guide User Name User Name Password Remember Me? Log in Register FAQ Calendar Today's Posts Search Page 1 of 2 1 2 >
Introduction to JavaScript and the Web
 Introduction to JavaScript and the Web In this introductory chapter, we'll take a look at what JavaScript is, what it can do for you, and what you need to be able to use it. With these foundations in place,
Introduction to JavaScript and the Web In this introductory chapter, we'll take a look at what JavaScript is, what it can do for you, and what you need to be able to use it. With these foundations in place,
KIK s GUIDE FOR LAW ENFORCEMENT
 Thanks for checking out our law enforcement guide. We take the safety of our users very seriously, and we hope this guide will be a useful tool for you. It includes information about our app; the features
Thanks for checking out our law enforcement guide. We take the safety of our users very seriously, and we hope this guide will be a useful tool for you. It includes information about our app; the features
P1_L3 Operating Systems Security Page 1
 P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
P1_L3 Operating Systems Security Page 1 that is done by the operating system. systems. The operating system plays a really critical role in protecting resources in a computer system. Resources such as
The Activist Guide to Secure Communication on the Internet. Introduction
 The Activist Guide to Secure Communication on the Internet Posted by: The Militant Posted on: September 3rd 2008 Updated on: September 8th 2008 Introduction 1 - Secure Internet Access 1.1 - Internet Cafes
The Activist Guide to Secure Communication on the Internet Posted by: The Militant Posted on: September 3rd 2008 Updated on: September 8th 2008 Introduction 1 - Secure Internet Access 1.1 - Internet Cafes
Introducing the Employment Law Exams
 A webinar presented by the Office of the Registrar Introducing the Employment Law Exams for the CHRP and the CHRL July 18, 2016 1. If you wrote the CKE1 this past June and passed, are you required to write
A webinar presented by the Office of the Registrar Introducing the Employment Law Exams for the CHRP and the CHRL July 18, 2016 1. If you wrote the CKE1 this past June and passed, are you required to write
Hello, and welcome to another episode of. Getting the Most Out of IBM U2. This is Kenny Brunel, and
 Hello, and welcome to another episode of Getting the Most Out of IBM U2. This is Kenny Brunel, and I'm your host for today's episode which introduces wintegrate version 6.1. First of all, I've got a guest
Hello, and welcome to another episode of Getting the Most Out of IBM U2. This is Kenny Brunel, and I'm your host for today's episode which introduces wintegrate version 6.1. First of all, I've got a guest
Security seminar topics Aleksei Gorny
 Security seminar topics 2010 Aleksei Gorny Usability of security Overview Bad security/usability balancing choices prevail in software design. Blame the user for being stupid! Misunderstanding of the economic
Security seminar topics 2010 Aleksei Gorny Usability of security Overview Bad security/usability balancing choices prevail in software design. Blame the user for being stupid! Misunderstanding of the economic
MITOCW watch?v=flgjisf3l78
 MITOCW watch?v=flgjisf3l78 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=flgjisf3l78 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
ECE646 Fall Lab 1: Pretty Good Privacy. Instruction
 ECE646 Fall 2012 Lab 1: Pretty Good Privacy Instruction PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY: 1. You are expected to address all questions listed in this document in your final report. 2. All
ECE646 Fall 2012 Lab 1: Pretty Good Privacy Instruction PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY: 1. You are expected to address all questions listed in this document in your final report. 2. All
Tim moves to accept, Chris Z seconds. No objections or comments.
 Minutes for PKCS 11 TC weekly concall 5-Feb-2014 1 Opening remarks (co-chairs) 2 Roll call taken by Bob Griffin. Quorum achieved. 3 Review / approval of the agenda Proposed Agenda: 1 Opening remarks (co-chairs)
Minutes for PKCS 11 TC weekly concall 5-Feb-2014 1 Opening remarks (co-chairs) 2 Roll call taken by Bob Griffin. Quorum achieved. 3 Review / approval of the agenda Proposed Agenda: 1 Opening remarks (co-chairs)
Post Experiment Interview Questions
 Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Privacy & Cookie Statement
 Privacy & Cookie Statement Version: 8 May 2018 Since day 1, WeTransfer has cared a great deal about privacy and respecting our users. We have always had a lean data policy: no sign up, no install, no retargeting.
Privacy & Cookie Statement Version: 8 May 2018 Since day 1, WeTransfer has cared a great deal about privacy and respecting our users. We have always had a lean data policy: no sign up, no install, no retargeting.
Intro. So, let s start your first SMS marketing legalese class!
 Disclaimer This guide was created for educational purposes only. It should not be taken as legal advice. The laws and national regulations are complicated and applied to businesses and individuals in different
Disclaimer This guide was created for educational purposes only. It should not be taken as legal advice. The laws and national regulations are complicated and applied to businesses and individuals in different
Technology Safety Quick Tips
 Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Instructor (Mehran Sahami):
 Programming Methodology-Lecture26 Instructor (Mehran Sahami): All right. Welcome back to what kind of day is it going to be in 106a? Anyone want to fun-filled and exciting. It always is. Thanks for playing
Programming Methodology-Lecture26 Instructor (Mehran Sahami): All right. Welcome back to what kind of day is it going to be in 106a? Anyone want to fun-filled and exciting. It always is. Thanks for playing
SUPERIOR COURT OF THE DISTRICT OF COLUMBIA CRIMINAL DIVISION FELONY BRANCH
 SUPERIOR COURT OF THE DISTRICT OF COLUMBIA CRIMINAL DIVISION FELONY BRANCH In the Matter of the Search of www.disruptj20.org ) Special Proceeding No. 17 CSW 3438 that Is Stored at Premises Owned, Maintained,
SUPERIOR COURT OF THE DISTRICT OF COLUMBIA CRIMINAL DIVISION FELONY BRANCH In the Matter of the Search of www.disruptj20.org ) Special Proceeding No. 17 CSW 3438 that Is Stored at Premises Owned, Maintained,
Long Filename Specification
 Long Filename Specification by vindaci fourth release First Release: November 18th, 1996 Last Update: January 6th, 1998 (Document readability update) Compatibility Long filename (here on forth referred
Long Filename Specification by vindaci fourth release First Release: November 18th, 1996 Last Update: January 6th, 1998 (Document readability update) Compatibility Long filename (here on forth referred
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Brief to the House of Commons Standing Committee on Industry, Science and Technology on the review of Canada s Anti-Spam Legislation.
 Brief to the House of Commons Standing Committee on Industry, Science and Technology on the review of Canada s Anti-Spam Legislation October 5, 2017 1. Introduction The Email Sender and Provider Coalition
Brief to the House of Commons Standing Committee on Industry, Science and Technology on the review of Canada s Anti-Spam Legislation October 5, 2017 1. Introduction The Email Sender and Provider Coalition
How To Construct A Keyword Strategy?
 Introduction The moment you think about marketing these days the first thing that pops up in your mind is to go online. Why is there a heck about marketing your business online? Why is it so drastically
Introduction The moment you think about marketing these days the first thing that pops up in your mind is to go online. Why is there a heck about marketing your business online? Why is it so drastically
Skill 1: Multiplying Polynomials
 CS103 Spring 2018 Mathematical Prerequisites Although CS103 is primarily a math class, this course does not require any higher math as a prerequisite. The most advanced level of mathematics you'll need
CS103 Spring 2018 Mathematical Prerequisites Although CS103 is primarily a math class, this course does not require any higher math as a prerequisite. The most advanced level of mathematics you'll need
The Center for Affiliated Learning ( the CAL ) Privacy Policy
 The Center for Affiliated Learning ( the CAL ) Privacy Policy Welcome to the Center for Affiliated Learning ( the CAL ) an education and training platform owned and operated by Affiliates Risk Management
The Center for Affiliated Learning ( the CAL ) Privacy Policy Welcome to the Center for Affiliated Learning ( the CAL ) an education and training platform owned and operated by Affiliates Risk Management
Full Court Press: Getting the Press to Write About your App!
 Full Court Press: Getting the Press to Write About your App! Todd Bernhard Contributing Editor iphone Life Magazine Todd@ToddBernhard.com Unique Perspective Independent app developer Writer, iphone Life
Full Court Press: Getting the Press to Write About your App! Todd Bernhard Contributing Editor iphone Life Magazine Todd@ToddBernhard.com Unique Perspective Independent app developer Writer, iphone Life
Meet our Example Buyer Persona Adele Revella, CEO
 Meet our Example Buyer Persona Adele Revella, CEO 685 SPRING STREET, NO. 200 FRIDAY HARBOR, WA 98250 W WW.BUYERPERSONA.COM You need to hear your buyer s story Take me back to the day when you first started
Meet our Example Buyer Persona Adele Revella, CEO 685 SPRING STREET, NO. 200 FRIDAY HARBOR, WA 98250 W WW.BUYERPERSONA.COM You need to hear your buyer s story Take me back to the day when you first started
The Stack, Free Store, and Global Namespace
 Pointers This tutorial is my attempt at clarifying pointers for anyone still confused about them. Pointers are notoriously hard to grasp, so I thought I'd take a shot at explaining them. The more information
Pointers This tutorial is my attempt at clarifying pointers for anyone still confused about them. Pointers are notoriously hard to grasp, so I thought I'd take a shot at explaining them. The more information
Digital Marketing Manager, Marketing Manager, Agency Owner. Bachelors in Marketing, Advertising, Communications, or equivalent experience
 Persona name Amanda Industry, geographic or other segments B2B Roles Digital Marketing Manager, Marketing Manager, Agency Owner Reports to VP Marketing or Agency Owner Education Bachelors in Marketing,
Persona name Amanda Industry, geographic or other segments B2B Roles Digital Marketing Manager, Marketing Manager, Agency Owner Reports to VP Marketing or Agency Owner Education Bachelors in Marketing,
Who am I? I m a python developer who has been working on OpenStack since I currently work for Aptira, who do OpenStack, SDN, and orchestration
 Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
mid=81#15143
 Posted by joehillen - 06 Aug 2012 22:10 I'm having a terrible time trying to find the Lightworks source code. I was under the impression that Lightworks was open source. Usually that means that it's possible
Posted by joehillen - 06 Aug 2012 22:10 I'm having a terrible time trying to find the Lightworks source code. I was under the impression that Lightworks was open source. Usually that means that it's possible
CODE MAROON TEST SEPT. 30, 2011 SURVEY RESULTS
 CODE MAROON TEST SEPT. 30, 2011 SURVEY RESULTS SMS (text) Message 1. Respondents were asked if they received the Code Maroon test by SMS (text) message. The responses indicate that 93% of the respondents
CODE MAROON TEST SEPT. 30, 2011 SURVEY RESULTS SMS (text) Message 1. Respondents were asked if they received the Code Maroon test by SMS (text) message. The responses indicate that 93% of the respondents
REALTORS LEGAL ALERT
 C ONNECTICUT ASSOCIATION OF REALTORS, INC. SUITE 1101, 111 FOUNDERS PLAZA EAST HARTFORD, CONNECTICUT 06108 PHONE:800-335-4862 WORLD WIDE WEB WWW.CTREALTOR.COM REALTORS LEGAL ALERT ELECTRONIC SIGNATURES
C ONNECTICUT ASSOCIATION OF REALTORS, INC. SUITE 1101, 111 FOUNDERS PLAZA EAST HARTFORD, CONNECTICUT 06108 PHONE:800-335-4862 WORLD WIDE WEB WWW.CTREALTOR.COM REALTORS LEGAL ALERT ELECTRONIC SIGNATURES
CSE143 Notes for Monday, 4/25/11
 CSE143 Notes for Monday, 4/25/11 I began a new topic: recursion. We have seen how to write code using loops, which a technique called iteration. Recursion an alternative to iteration that equally powerful.
CSE143 Notes for Monday, 4/25/11 I began a new topic: recursion. We have seen how to write code using loops, which a technique called iteration. Recursion an alternative to iteration that equally powerful.
Good afternoon and thank you for being at the webinar on accessible PowerPoint presentations. This is Dr. Zayira Jordan web accessibility coordinator
 Good afternoon and thank you for being at the webinar on accessible PowerPoint presentations. This is Dr. Zayira Jordan web accessibility coordinator at Iowa State and this is the topic for this week s
Good afternoon and thank you for being at the webinar on accessible PowerPoint presentations. This is Dr. Zayira Jordan web accessibility coordinator at Iowa State and this is the topic for this week s
It s still very important that you take some steps to help keep up security when you re online:
 PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
PRIVACY & SECURITY The protection and privacy of your personal information is a priority to us. Privacy & Security The protection and privacy of your personal information is a priority to us. This means
Bellevue job Don C Burdick to: Ted A Carlson
 Bellevue job C Burdick to: Ted A Carlson 08/16/2011 09:34 PM I talked to Lorna and she didn't consider the Bellevue job a conflict of interest from the cities perspective. I will be following up with a
Bellevue job C Burdick to: Ted A Carlson 08/16/2011 09:34 PM I talked to Lorna and she didn't consider the Bellevue job a conflict of interest from the cities perspective. I will be following up with a
Case 1:18-cr TSE Document 2 Filed 06/20/18 Page 1 of 9 PageID# 2 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF VIRGINIA
 Case 1:18-cr-00308-TSE Document 2 Filed 06/20/18 Page 1 of 9 PageID# 2 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF VIRGINIA Alexandria Division i 20 2018 1:1 UNITED STATES OF AMERICA
Case 1:18-cr-00308-TSE Document 2 Filed 06/20/18 Page 1 of 9 PageID# 2 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF VIRGINIA Alexandria Division i 20 2018 1:1 UNITED STATES OF AMERICA
Module 6. Campaign Layering
 Module 6 Email Campaign Layering Slide 1 Hello everyone, it is Andy Mackow and in today s training, I am going to teach you a deeper level of writing your email campaign. I and I am calling this Email
Module 6 Email Campaign Layering Slide 1 Hello everyone, it is Andy Mackow and in today s training, I am going to teach you a deeper level of writing your email campaign. I and I am calling this Email
Lesson 4: Who Goes There?
 Lesson 4: Who Goes There? In this lesson we will write a program that asks for your name and a password, and prints a secret message if you give the right password. While doing this we will learn: 1. What
Lesson 4: Who Goes There? In this lesson we will write a program that asks for your name and a password, and prints a secret message if you give the right password. While doing this we will learn: 1. What
MITOCW watch?v=qota76ga_fy
 MITOCW watch?v=qota76ga_fy The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
MITOCW watch?v=qota76ga_fy The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality educational resources for free. To
4 having been first duly sworn, testified as follows: 6 Q. (BY MS. REYNA) Good afternoon, Officer. 7 Could you please introduce yourself to our jury?
 197 Eric Johnson - June 2, 2014 Cross-Examination by Mr. Davis 1 may have a seat, sir. 2 THE WITNESS: Thank you. 3 MARK WILSON, 4 having been first duly sworn, testified as follows: 5 DIRECT EXAMINATION
197 Eric Johnson - June 2, 2014 Cross-Examination by Mr. Davis 1 may have a seat, sir. 2 THE WITNESS: Thank you. 3 MARK WILSON, 4 having been first duly sworn, testified as follows: 5 DIRECT EXAMINATION
Windows Script Host Fundamentals
 O N E Windows Script Host Fundamentals 1 The Windows Script Host, or WSH for short, is one of the most powerful and useful parts of the Windows operating system. Strangely enough, it is also one of least
O N E Windows Script Host Fundamentals 1 The Windows Script Host, or WSH for short, is one of the most powerful and useful parts of the Windows operating system. Strangely enough, it is also one of least
CS103 Handout 50 Fall 2018 November 30, 2018 Problem Set 9
 CS103 Handout 50 Fall 2018 November 30, 2018 Problem Set 9 What problems are beyond our capacity to solve? Why are they so hard? And why is anything that we've discussed this quarter at all practically
CS103 Handout 50 Fall 2018 November 30, 2018 Problem Set 9 What problems are beyond our capacity to solve? Why are they so hard? And why is anything that we've discussed this quarter at all practically
How to Write a Proper Business Letter
 1.866.754.6477 www.ultimateestateplanner.com How to Write a Proper Business Letter By Kristina Schneider, Executive Assistant Writing a business letter seems somewhat common knowledge or perhaps common
1.866.754.6477 www.ultimateestateplanner.com How to Write a Proper Business Letter By Kristina Schneider, Executive Assistant Writing a business letter seems somewhat common knowledge or perhaps common
Obtained by Judicial Watch, Inc. via FOIA
 Obtained by Judicial Watch, Inc. via FOIA From: Sent: To: Subject: Judson Victoria A Friday, May 18, 2012 6:58 PM Munroe David; Cook Janine Re: EO Coordinator on (c)(4) questions Sorry- I had not reached
Obtained by Judicial Watch, Inc. via FOIA From: Sent: To: Subject: Judson Victoria A Friday, May 18, 2012 6:58 PM Munroe David; Cook Janine Re: EO Coordinator on (c)(4) questions Sorry- I had not reached
A Double Edged Sword. December 10, Originally published March 15, 1996 in Web Review magazine.
 A Double Edged Sword December 10, 2009 Originally published March 15, 1996 in Web Review magazine. Architecturally speaking, frames are one of the most intriguing HTML extensions around. Unfortunately,
A Double Edged Sword December 10, 2009 Originally published March 15, 1996 in Web Review magazine. Architecturally speaking, frames are one of the most intriguing HTML extensions around. Unfortunately,
A PROGRAM IS A SEQUENCE of instructions that a computer can execute to
 A PROGRAM IS A SEQUENCE of instructions that a computer can execute to perform some task. A simple enough idea, but for the computer to make any use of the instructions, they must be written in a form
A PROGRAM IS A SEQUENCE of instructions that a computer can execute to perform some task. A simple enough idea, but for the computer to make any use of the instructions, they must be written in a form
It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek
 Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry.
Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry.
e180 Privacy Policy July 2018
 e180 Privacy Policy July 2018 We are e180, the creators of Braindate. We care deeply about protecting your personal information, so we ve outlined everything you need to know about it here. Last modified:
e180 Privacy Policy July 2018 We are e180, the creators of Braindate. We care deeply about protecting your personal information, so we ve outlined everything you need to know about it here. Last modified:
Balanced BST and AVL Trees
 Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Last time on this topic: Introduced AVL trees Discussed
Carlos Moreno cmoreno @ uwaterloo.ca EIT-4103 https://ece.uwaterloo.ca/~cmoreno/ece250 Standard reminder to set phones to silent/vibrate mode, please! Last time on this topic: Introduced AVL trees Discussed
Double Your Affiliate Commissions with this VERY Simple Strategy
 Double Your Affiliate Commissions with this VERY Simple Email Strategy If you aren't resending your emails to the unopens you are missing out on one of the easiest and most readily available sources of
Double Your Affiliate Commissions with this VERY Simple Email Strategy If you aren't resending your emails to the unopens you are missing out on one of the easiest and most readily available sources of
IACA Discussion List Guidelines, Use and Subscription Management
 IACA Discussion List Guidelines, Use and Subscription Management Instructions... 2 Posting Guidelines... 2 Managing your Subscription... 3 Frequently Asked Questions... 4 I sent a request to iacalist@iaca.net
IACA Discussion List Guidelines, Use and Subscription Management Instructions... 2 Posting Guidelines... 2 Managing your Subscription... 3 Frequently Asked Questions... 4 I sent a request to iacalist@iaca.net
Defining Done in User Stories
 This article originally appeared on Artima Developer on Wednesday, January 6, 2010. To access it online, visit: http://www.artima.com/articl es/defining_done.html Defining Done in User Stories By Victor
This article originally appeared on Artima Developer on Wednesday, January 6, 2010. To access it online, visit: http://www.artima.com/articl es/defining_done.html Defining Done in User Stories By Victor
User's Manual. Intego ChatBarrier X3 User's Manual Page 1
 User's Manual Intego ChatBarrier X3 User's Manual Page 1 Intego ChatBarrier X3 for Macintosh 2004 Intego, Inc. All Rights Reserved Intego, Inc. 500 N Capital of Texas Hwy, Ste 8-150 Austin, Texas 78746
User's Manual Intego ChatBarrier X3 User's Manual Page 1 Intego ChatBarrier X3 for Macintosh 2004 Intego, Inc. All Rights Reserved Intego, Inc. 500 N Capital of Texas Hwy, Ste 8-150 Austin, Texas 78746
2007 chee kong ow yong (www.ckowyong.com) all rights reserved. VPS Guide for MT4. (version 1.0) by ckowyong.com, 30 september 2007.
 VPS Guide for MT4 (version 1.0) by ckowyong.com, 30 september 2007 Page 1 of 25 Introduction This guide aims to help you configure a Windows Virtual Private Server(from now on refered to as a VPS) for
VPS Guide for MT4 (version 1.0) by ckowyong.com, 30 september 2007 Page 1 of 25 Introduction This guide aims to help you configure a Windows Virtual Private Server(from now on refered to as a VPS) for
What's New. Version 9.2 release. Campground Master Contents 1. Contents. A couple quick reminders:
 Campground Master Contents 1 Contents A couple quick reminders: Make Backups! It's so sad when we hear from someone whose computer has crashed and they have no backup of their data to restore from. It's
Campground Master Contents 1 Contents A couple quick reminders: Make Backups! It's so sad when we hear from someone whose computer has crashed and they have no backup of their data to restore from. It's
STAUNING Credit Application Internet Sales Process with /Voic Templates to Non-Responsive Prospects 2018 Edition
 STAUNING Credit Application Internet Sales Process with Email/Voicemail Templates to Non-Responsive Prospects 2018 Edition Contents 30-DAY CREDIT APPLICATION INTERNET SALES PROCESS... 2 DAY 1 AUTO-RESPONSE
STAUNING Credit Application Internet Sales Process with Email/Voicemail Templates to Non-Responsive Prospects 2018 Edition Contents 30-DAY CREDIT APPLICATION INTERNET SALES PROCESS... 2 DAY 1 AUTO-RESPONSE
OOoCon Marketing OpenOffice.org. by Nick Richards On rendezvous. Right here, right now.
 OOoCon 2003 Marketing OpenOffice.org by Nick Richards nedrichards@openoffice.org http://nedrichards.com On rendezvous. Right here, right now. 1 About Nick Who am I? Why Are We Here Why OpenOffice.org Marketing?
OOoCon 2003 Marketing OpenOffice.org by Nick Richards nedrichards@openoffice.org http://nedrichards.com On rendezvous. Right here, right now. 1 About Nick Who am I? Why Are We Here Why OpenOffice.org Marketing?
CS144 Final Review. Dec 4th, 2009 Tom Wiltzius
 CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
BassAce Midi Synth old forum topics 1 of 6. here are some (minor) errors i found on the bassace documentation.
 BassAce Midi Synth old forum topics 1 of 6 Date: Wed, 26 Feb 2003 11:56:53 From: male man Subject: bassace errors here are some (minor) errors i found on the bassace documentation. -R16 listed under 1k
BassAce Midi Synth old forum topics 1 of 6 Date: Wed, 26 Feb 2003 11:56:53 From: male man Subject: bassace errors here are some (minor) errors i found on the bassace documentation. -R16 listed under 1k
ECA Trusted Agent Handbook
 Revision 8.0 September 4, 2015 Introduction This Trusted Agent Handbook provides instructions for individuals authorized to perform personal presence identity verification of subscribers enrolling for
Revision 8.0 September 4, 2015 Introduction This Trusted Agent Handbook provides instructions for individuals authorized to perform personal presence identity verification of subscribers enrolling for
Table of Contents. Part 1 Postcard Marketing Today Brief History of Real Estate Postcards Postcard Marketing Today...
 Table of Contents Part 1 Postcard Marketing Today... 2 Brief History of Real Estate Postcards... 3 Postcard Marketing Today... 4 Pyramid of Postcard Success... 6 Part 2 Achieving Postcard Success... 11
Table of Contents Part 1 Postcard Marketing Today... 2 Brief History of Real Estate Postcards... 3 Postcard Marketing Today... 4 Pyramid of Postcard Success... 6 Part 2 Achieving Postcard Success... 11
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
Guide to Installing Fldigi and Flmsg with Red Cross Templates
 Guide to Installing Fldigi and Flmsg with Red Cross Templates Unless you already have the latest versions of fldigi and flmsg on your computer, you need to uninstall the old versions. We will then install
Guide to Installing Fldigi and Flmsg with Red Cross Templates Unless you already have the latest versions of fldigi and flmsg on your computer, you need to uninstall the old versions. We will then install
IACA Discussion List. About the IACA Discussion List. Guidelines, use and subscription management
 IACA Discussion List Guidelines, use and subscription management About the IACA Discussion List The IACA discussion list (IACA List) is a free resource for all active IACA members. This resource allows
IACA Discussion List Guidelines, use and subscription management About the IACA Discussion List The IACA discussion list (IACA List) is a free resource for all active IACA members. This resource allows
DEPOSITION OF DOT THOMAS by Brian Korte
 DEPOSITION OF DOT THOMAS by Brian Korte Page: 1 IN THE CIRCUIT COURT OF THE 15TH JUDICIAL CIRCUIT IN AND FOR PALM BEACH COUNTY, FLORIDA CASE NO.: 2010 CA 002567 (AW) PNC MORTGAGE, A DIVISION OF PNC BANK,
DEPOSITION OF DOT THOMAS by Brian Korte Page: 1 IN THE CIRCUIT COURT OF THE 15TH JUDICIAL CIRCUIT IN AND FOR PALM BEACH COUNTY, FLORIDA CASE NO.: 2010 CA 002567 (AW) PNC MORTGAGE, A DIVISION OF PNC BANK,
2016 All Rights Reserved
 2016 All Rights Reserved Table of Contents Chapter 1: The Truth About Safelists What is a Safelist Safelist myths busted Chapter 2: Getting Started What to look for before you join a Safelist Best Safelists
2016 All Rights Reserved Table of Contents Chapter 1: The Truth About Safelists What is a Safelist Safelist myths busted Chapter 2: Getting Started What to look for before you join a Safelist Best Safelists
The following content is provided under a Creative Commons license. Your support
 MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
MITOCW Lecture 23 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free. To make a
ECE646 Fall Lab 1: Pretty Good Privacy. Instruction
 ECE646 Fall 2015 Lab 1: Pretty Good Privacy Instruction PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY: 1. You are expected to address all questions listed in this document in your final report. 2. All
ECE646 Fall 2015 Lab 1: Pretty Good Privacy Instruction PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY: 1. You are expected to address all questions listed in this document in your final report. 2. All
Manual Updating To Ios 7 Ipad 3 Not Working
 Manual Updating To Ios 7 Ipad 3 Not Working Apple has just released the long-awaited ios 8.3 update with support for new Siri iphone 6, iphone 6 Plus, iphone 5s, iphone 5c, iphone 5 and iphone 4s, ipad
Manual Updating To Ios 7 Ipad 3 Not Working Apple has just released the long-awaited ios 8.3 update with support for new Siri iphone 6, iphone 6 Plus, iphone 5s, iphone 5c, iphone 5 and iphone 4s, ipad
Notes to Accompany Debugging Lecture. Jamie Blustein
 Notes to Accompany Debugging Lecture Jamie Blustein 28 April 2002 Introduction This lecture was originally written for Turbo Pascal, then updated for the rst ANSI C standard, then object-free C++. It does
Notes to Accompany Debugging Lecture Jamie Blustein 28 April 2002 Introduction This lecture was originally written for Turbo Pascal, then updated for the rst ANSI C standard, then object-free C++. It does
Michael Phelps Foundation: Privacy Policy
 Effective November 7, 2018 Michael Phelps Foundation: Privacy Policy General Understanding of Our Privacy Policy The Michael Phelps Foundation ( the Foundation, We, Us, or Our ) understands and respects
Effective November 7, 2018 Michael Phelps Foundation: Privacy Policy General Understanding of Our Privacy Policy The Michael Phelps Foundation ( the Foundation, We, Us, or Our ) understands and respects
Q2 How many attorneys practice at the firm, organization, agency or department, or other entity you listed above?
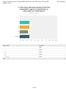 Q How many attorneys practice at the firm, organization, agency or department, or other entity you listed above? Answered: 7 Skipped: - 5-9 or more % % % % % 5% 6% 7% 8% 9% % - 5-9 or more.% 5.9% 7 5.9%
Q How many attorneys practice at the firm, organization, agency or department, or other entity you listed above? Answered: 7 Skipped: - 5-9 or more % % % % % 5% 6% 7% 8% 9% % - 5-9 or more.% 5.9% 7 5.9%
Sending s With Sendmail - Part 2
 CODECALL Programming Tutorials Linux Tutorials, Guides and Tips Sending Emails With Sendmail - Part 2 Started by, Aug 31 2009 04:55 PM form, Posted 31 August 2009-04:55 PM Ok, so now that you know how
CODECALL Programming Tutorials Linux Tutorials, Guides and Tips Sending Emails With Sendmail - Part 2 Started by, Aug 31 2009 04:55 PM form, Posted 31 August 2009-04:55 PM Ok, so now that you know how
MITOCW watch?v=yarwp7tntl4
 MITOCW watch?v=yarwp7tntl4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free.
MITOCW watch?v=yarwp7tntl4 The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high quality, educational resources for free.
How Do I Lock My Iphone 4 Screen While On A Call
 How Do I Lock My Iphone 4 Screen While On A Call You can also schedule a time or choose who you'll allow calls. With Do Not Disturb, you can silence calls, alerts, and notifications that you get while
How Do I Lock My Iphone 4 Screen While On A Call You can also schedule a time or choose who you'll allow calls. With Do Not Disturb, you can silence calls, alerts, and notifications that you get while
PRIVACY POLICY Let us summarize this for you...
 PRIVACY POLICY Let us summarize this for you... We promise to never sell your personal information. This site collects usage information to provide a better web experience for our users. If you purchase
PRIVACY POLICY Let us summarize this for you... We promise to never sell your personal information. This site collects usage information to provide a better web experience for our users. If you purchase
On 26 Jul 2011, at 19:15, Rory McCune wrote:
 On Tue, Jul 26, 2011 at 11:03 PM, Eoin
On Tue, Jul 26, 2011 at 11:03 PM, Eoin
Office Properties Income Trust Privacy Notice Last Updated: February 1, 2019
 General Office Properties Income Trust Privacy Notice Last Updated: February 1, 2019 Office Properties Income Trust ( OPI ) is committed to your right to privacy and to keeping your personal information
General Office Properties Income Trust Privacy Notice Last Updated: February 1, 2019 Office Properties Income Trust ( OPI ) is committed to your right to privacy and to keeping your personal information
Information Security Incident Response Plan
 Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
Information Security Incident Response Plan Purpose It is the objective of the university to maintain secure systems and data. In order to comply with federal, state, and local law and contractual obligations,
H O W T O I N S T R U C T Y O U R NEW USERS GUIDE TO INSTRUCTING PROCESS SERVER
 H O W T O I N S T R U C T Y O U R NEW USERS GUIDE TO INSTRUCTING YOUR PROCESS SERVER PROCESS SERVER The Process Serving Industry Despite being an integral part of the litigation process, the process serving
H O W T O I N S T R U C T Y O U R NEW USERS GUIDE TO INSTRUCTING YOUR PROCESS SERVER PROCESS SERVER The Process Serving Industry Despite being an integral part of the litigation process, the process serving
Network Working Group Request for Comments: 1984 Category: Informational August 1996
 Network Working Group IAB Request for Comments: 1984 IESG Category: Informational August 1996 IAB and IESG Statement on Cryptographic Technology and the Internet Status of This Memo This memo provides
Network Working Group IAB Request for Comments: 1984 IESG Category: Informational August 1996 IAB and IESG Statement on Cryptographic Technology and the Internet Status of This Memo This memo provides
Register FAQ Calendar Today's Posts Search
 Custom Search Highly Liquid Forum > Current Products > UMR2 Yamaha VSS-30 MIDI Retrofit Guide User Name User Name Password Remember Me? Log in Register FAQ Calendar Today's Posts Search Page 1 of 2 1 2
Custom Search Highly Liquid Forum > Current Products > UMR2 Yamaha VSS-30 MIDI Retrofit Guide User Name User Name Password Remember Me? Log in Register FAQ Calendar Today's Posts Search Page 1 of 2 1 2
Register FAQ Calendar Today's Posts Search
 Custom Search Highly Liquid Forum > Current Products > UMR2 Casio SK-1 MIDI Retrofit Guide User Name User Name Password Remember Me? Log in Register FAQ Calendar Today's Posts Search Page 1 of 3 1 2 3
Custom Search Highly Liquid Forum > Current Products > UMR2 Casio SK-1 MIDI Retrofit Guide User Name User Name Password Remember Me? Log in Register FAQ Calendar Today's Posts Search Page 1 of 3 1 2 3
ECE596C: Handout #9. Authentication Using Shared Secrets. Electrical and Computer Engineering, University of Arizona, Loukas Lazos
 ECE596C: Handout #9 Authentication Using Shared Secrets Electrical and Computer Engineering, University of Arizona, Loukas Lazos Abstract. In this lecture we introduce the concept of authentication and
ECE596C: Handout #9 Authentication Using Shared Secrets Electrical and Computer Engineering, University of Arizona, Loukas Lazos Abstract. In this lecture we introduce the concept of authentication and
On Mon, Sep 28, 2015 at 5:01 PM, Sams, Savannah wrote:
 From: To: Cc: Subject: Date: Adlerstein, David Sams, Savannah Gorman, Amanda; Oates, Ehren Re: FOIA request Franklin County Commissioner Monday, September 28, 2015 5:45:45 PM Savannah: I have gone to the
From: To: Cc: Subject: Date: Adlerstein, David Sams, Savannah Gorman, Amanda; Oates, Ehren Re: FOIA request Franklin County Commissioner Monday, September 28, 2015 5:45:45 PM Savannah: I have gone to the
I just left you a long-winded message about this issue. Can you please call me after you read the below ? Thank you.
 Zamora, Olga From: Sent: To: Subject: Attachments: Wednesday, April 27, 2016 3:51 PM Zamora, Olga Fwd: Illegal Tree Removal After-the-Fact Permit Dispute Deadline - Ohio Street WP_20160415_09_27_48_Pro.jpg
Zamora, Olga From: Sent: To: Subject: Attachments: Wednesday, April 27, 2016 3:51 PM Zamora, Olga Fwd: Illegal Tree Removal After-the-Fact Permit Dispute Deadline - Ohio Street WP_20160415_09_27_48_Pro.jpg
Tips from the experts: How to waste a lot of time on this assignment
 Com S 227 Spring 2018 Assignment 1 100 points Due Date: Friday, September 14, 11:59 pm (midnight) Late deadline (25% penalty): Monday, September 17, 11:59 pm General information This assignment is to be
Com S 227 Spring 2018 Assignment 1 100 points Due Date: Friday, September 14, 11:59 pm (midnight) Late deadline (25% penalty): Monday, September 17, 11:59 pm General information This assignment is to be
1 LOGGING IN REQUEST A SUB (from the calendar) REQUEST A SUB (from Line Listing) ACCEPTING AN INVITATION TO BE A SUB...
 SHORELINE SENIOR MEN S TENNIS USER GUIDE FOR MYTENNISGROUP.COM Copyright 2013 by Richard Yanowitz on behalf of the Shoreline (CT) Senior Men s Tennis Group This document walks you through the basics of
SHORELINE SENIOR MEN S TENNIS USER GUIDE FOR MYTENNISGROUP.COM Copyright 2013 by Richard Yanowitz on behalf of the Shoreline (CT) Senior Men s Tennis Group This document walks you through the basics of
Monette Garcia AT&T Senior Sales Executive - Fiber Solutions Wireless: Beech Ave McAllen, TX 78501
 1 of 8 2/10/2016 1:16 PM Zimbra sandra.montalvo@co.hidalgo.tx.us Fwd: Message from "RNP0026739EDEC6" From : Martha Salazar Subject : Fwd: Message from "RNP0026739EDEC6"
1 of 8 2/10/2016 1:16 PM Zimbra sandra.montalvo@co.hidalgo.tx.us Fwd: Message from "RNP0026739EDEC6" From : Martha Salazar Subject : Fwd: Message from "RNP0026739EDEC6"
WHITE PAPER. Authentication and Encryption Design
 WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
(Photos and Instructions Based on Microsoft Outlook 2007, Gmail, Yahoo! Mail, and Hotmail)
 Specific instructions on how to compose a professional e-mail using send and reply options, basic e-mail components, appropriate wording, content, tone, and examples of what not to do. (Photos and Instructions
Specific instructions on how to compose a professional e-mail using send and reply options, basic e-mail components, appropriate wording, content, tone, and examples of what not to do. (Photos and Instructions
etiquette rules for effective replies
 Page 1 of 7 Home Email Software Books Links Contact policy Search This site explains how to send effective email replies. It discusses why email etiquette is necessary, lists email etiquette rules, and
Page 1 of 7 Home Email Software Books Links Contact policy Search This site explains how to send effective email replies. It discusses why email etiquette is necessary, lists email etiquette rules, and
Why you should never ask favors from a graphic designer:
 Why you should never ask favors from a graphic designer: Story goes : Shannon (the secretary) has lost her cat and has asked David (the graphic designer) to help with a lost poster. This is their email
Why you should never ask favors from a graphic designer: Story goes : Shannon (the secretary) has lost her cat and has asked David (the graphic designer) to help with a lost poster. This is their email
How to Improve Your Campaign Conversion Rates
 How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
How to Improve Your Email Campaign Conversion Rates Chris Williams Author of 7 Figure Business Models How to Exponentially Increase Conversion Rates I'm going to teach you my system for optimizing an email
Hi Bob, I got this from my colleagues near the end of last week and unfortunately lost track of it in my inbox to send you.
 Robert Cook-Deegan To: "Rodriguez, Laura (NIH/NHGRI) [E]" Cc: Rachel Ankeny , Kathryn Maxson Reply-To: bob.cd@duke.edu
Robert Cook-Deegan To: "Rodriguez, Laura (NIH/NHGRI) [E]" Cc: Rachel Ankeny , Kathryn Maxson Reply-To: bob.cd@duke.edu
Cryptography and Network Security. Prof. D. Mukhopadhyay. Department of Computer Science and Engineering. Indian Institute of Technology, Kharagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 38 A Tutorial on Network Protocols
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 38 A Tutorial on Network Protocols
Part 1: Information Security for City Governments; Defining e-discovery
 Integrating Security Incident Response and e-discovery Transcript Part 1: Information Security for City Governments; Defining e-discovery Julia Allen: Welcome to CERT's Podcast Series: Security for Business
Integrating Security Incident Response and e-discovery Transcript Part 1: Information Security for City Governments; Defining e-discovery Julia Allen: Welcome to CERT's Podcast Series: Security for Business
