It Cannot Get Away: An Approach to Enhance Security of User Account in Online Social Networks
|
|
|
- Cecil McDonald
- 5 years ago
- Views:
Transcription
1 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April It Cannot Get Away: An Approach to Enhance Security of User Account in Online Social Networks Abdulrahman Muthana Thamar University, Thamar, Yemen Abdul Azim Abd Ghani Universiti Putra Malaysia, Serdang, Selangor, Malaysia Rmlan Mahmod Universiti Putra Malaysia, Serdang, Selangor, Malaysia Summary The rapid development of internet technologies, lead to the growth of Online Social Networks (OSNs). Facebook, Twitter, Google Plus, MySpace, Orkut are well-known examples of online social networks. Although, existence of OSN networks makes the communication easier than ever, it introduces various types of security issues like identity impersonate, privacy-related issues due to losing user account. Online Social Networks (OSNs) provide various security schemes to protect user account, however in many situations such schemes are not adequate and the owners of the accounts find themselves unable to regain control of their accounts. This paper proposes a simple yet reliable security approach that allows users to protect their accounts in online social networks OSNs from unauthorized access. The proposed approach will improve the Quality of Service (QoS) by enhancing the existing security schemes and will considerably mitigate the effects of unauthorized access in online social networks OSNs. Key words: Online Social Networks (OSNs), Recovery Token, Security, Quality of Service (QoS), Authentication 1. Introduction The rapid development of internet technologies makes the connection among people much easier through Online Social Networks (OSNs). The web 2.0 technology developments led to forming a kind of communication named as Online Social Networks (OSNs) [1], which allow people to create accounts, setup profiles and share information available on their profile with other users. Facebook, Twitter, Google Plus, MySpace, Orkut are wellknown examples of online social networks. (OSNs).The active users of some Online Social Networks (OSNs) such as Facebook, and twitter almost crossed more than one billion [2] [3]. The main example of social networking websites is Facebook, which was founded on February 2004 and operated by Facebook community [4]. Facebook attracted many users in all around the world and crossed over one billion active users during the month of September 2012, and more than half of whom use on mobile devices [4]. To open an account in Facebook one needs a registration, which can be done with an id. The user of Facebook can share information through messages, comments or simply posts information on the wall of the user. Facebook also allows user to post pictures and videos and do chat with the other friends on Facebook. Facebook has various useful privacy settings and allows its users to set their own privacy policy, which enables the users to control information of their profile and the information shared by them. As other Online Social Networks (OSNs), number of security issues do exist [12]. Facebook security scheme still has certain limitations regarding preventing losing user account. While Facebook provides full privacy policy to the information on the user account, it fails to provide a full protection to user account. It seems that more efforts still required to improve Quality of Service (QoS) provided to its users through enhancing the security scheme. In this paper, we firstly introduce threats to user account in OSN networks. Then we describe Facebook existing security model as well as point out the limitations in Facebook security model. Finally, we propose a new approach to improve the Quality of Service (QoS) by enhancing the existing security schemes in which a specialuse password is introduced. In addition, we make a comparison between Facebook security model and the new enhancement, and analyze the security of the enhancement. Motivation. The proposed approach addresses the problem of losing ownership of online social network (OSN) user account and inability to access the user account due to hacking. The proposed approach helps users to regain control of their accounts from attackers. Contributions. We propose an approach to improve (QoS) in (OSNs) networks by enhancing their security schemes; (2) we introduce the notion of recovery password; (3) our approach shows how security schemes in (OSNs) can be enhanced with no or little overhead; (4) we show the feasibility of our approach to protect users accounts from unauthorized access in online social networks (OSNs). Outline. The remainder of this paper is organized as follows: section 2 gives a summary of the related work. Section 3 lists threats to user account in OSN networks. Existing Security model in Facebook, the most popular OSN, is described in Section 4. Our approach is described in Section 5 showing the implementation and security analysis and Section 6 concludes. Manuscript received April 5, 2015 Manuscript revised April 20, 2015
2 2 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April Related Work Several studies have discussed the security issues related to Online Social Networks (OSNs). The survey paper in [12] highlighted different security issues in OSNs. The research in [5] suggested that users can set privacy policy to their profile object and control the privacy of information on the account. This can be done by dividing their total number of friends into various groups and set privacy options to each group based on the priority. Grouping of friends was carried out based on clustering technology. The research in [5] focused mainly on user-to-user interactions in social networks only. With the growth of using third party applications with online social networking websites, the third party applications request the right to access the information from the users in those websites. The research in [1] presented a framework to control the access of third party application to user information. The framework is based on enabling the user to specify the data attributes to be shared with the application and at the same time be able to specify the degree of specificity of the shared attributes. Other related work has analyzed both privacy risks associated with information disclosure in social networks, and proposed a framework for deriving a privacy score to inform the user of the potential risks to their privacy created by their activities and activities with other users within the social network [6]. However the previous researches [1,5,6, 7] concentrated on how to give more security to the data available on user profile. All these privacy and security mechanisms provide protection only to the profile data of the user but not to the entire user account. The most close work to ours is [11], in which they attempted to enhance the security scheme in Facebook when the user account is temporarily locked. They suggested that Facebook should not verify the originality of the user by verifying the birthdate or identifying the photos of friends. They argue that, most of users especially very important persons (VIP) users do not wish to provide real birthdate in their homepages and put dummy birthdates instead. And after long time of not accessing their accounts it is unlikely that they can remember what birthdate information they provided to Facebook. They advised not to use photos of friend in the originality verification procedure because in many situations it is difficult for the owners of the accounts to recognize properly the correct photos and as a result losing their accounts permanently. They proposed security approach for verifying the originality of users based on and mobile phone device instead, however, their approach does not guarantee the security of user account. Their approach only deals with the issue of losing access to the account which is temporarily locked provided that that and mobile phone are intact. They ignore the events when mobile phone and/or account have been stolen or compromised. unlike [11] our approach is comprehensive and can prevent losing access to user account due to hacking. Our approach enables Facebook to verify the originality of account owner in a simple manner. 3. Threats to OSN User Account There exists number of threats on the authenticity means used in OSNs account including , mobile phone, login password. Therefore, these threats pose a risk on the ability of the user to access his or her account in OSNs networks and reduce the means available to the user to regain control of the account. It should be noted that being user is unable to prove authenticity due to failing of one or some of authenticity means does not necessarily lead to losing access to the account. However, failing of user to fulfill all authentication requests would render the user account inaccessible. Some of threats are: The user forgot username or account password The user forgot birthdate registered in his profile The user could not recognize photos of friends Mobile phone device was stolen and exploited by hacker for hacking user account Mobile phone number was temporarily or permanently blocked by network operator Mobile phone number changed because of travelling abroad The user cannot use the last device from which he/she logged in The user forgot the recovery The user forgot recovery login password The recovery was hacked 4. Facebook Security Model The most popular Online Social Networks (OSNs) Facebook allows users to create personal profile, post photos, videos, share information and send message to friends. Facebook has various useful privacy settings, which enable the users to control information of their profile and the information shared by them. However, number of security issues do exist [12]. Facebook security scheme still has limitations regarding preventing losing user account. While Facebook provides full privacy policy to the information on the user account, it fails to provide a full protection to user account. It seems that more efforts still required in order to enhance user account security and
3 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April protect it from unauthorized access. In the following we discuss the main processes in Facebook security model. Forgot password Identify the account Change general and security settings More Security Features Forgot password. When user forgets the password and clicks on "Forgot password", Facebook website will prompt the user to enter , mobile phone, username, or full name (Fig. 1). Trusted Contacts (Fig. 2). These features still have limitations. Fig. 2 More Security Features. Fig. 1 Forgot Password Screen. The issues that may arise are: - entered might be already attacked by an attacker, or blocked by Service Provider ESP for some reason, thus the user will not be able to receive reset password message. -Mobile phone number might be changed by the user or blocked by network operator. Furthermore, not all users do register mobile numbers in Facebook account. -Most of users do not care of username (Facebook URL) and, thus they do not remember username. -many users tend to use dummy names in Facebook account, and thus they may not be able to remember full name. Identify your account. If the user could not identify the account and failed to provide correct or username, Facebook website may prompt him to find a friend, who can help by looking at contact or URL. This idea may not succeed since most of users hide their contact information. Change general and security settings. Facebook allows user to change information in user account profile including password, s, mobile phone, and username provided that the password is given. This flexibility has a risk as it allows an attacker to change the account authenticity information by providing password only. This hardens the task of the owner to regain control of the account. More Security Features. Facebook offers more features to securing user account including Login Approvals and Login Approvals uses mobile phone as an extra authentication factor to prove user originality. Facebook allows users to turn "Login Approvals" ON and OFF, provided that password is given. Having the password, an attacker can change mobile phone number and/or turns Login Approvals OFF. Trusted Contacts cannot be always a reliable mechanism and it is not clear how to regain control of account if the user did not turn this feature ON previously. In the following we will show the limitations of Facebook security model to handle user account locking and hacking. 4.1 Account is locked If user account was locked, Facebook prompts the user to authenticate the user originality in the following ways. Provide your birthday. Identify the photos of friends. Try logging into Facebook from a device you have logged in before. Work in [11] highlighted the limitations of Facebook security model to deal with account locking. Please refer to [11] for more details. 4.2 Account is Hacked This section shows how Facebook may hinder legitimate users to regain control of their accounts that have been compromised by attackers. The point can be illustrated clearly with the following scenario. If user account was hacked by an attacker, the user will try to regain control of the account through "Forgot Password" procedure. Facebook website then prompts the user to prove the user authenticity (Fig. 3) using: registered in Facebook account, or
4 4 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April 2015 Mobile device number registered with Facebook account, or Username or, Full name Allowing the user to choose any method to prove user originality. Let us now discuss each option available to the user. the account. Some issues may prevent the user to access the account though this method: Mobile number has been temporarily or permanently blocked by Network operator, or The user has changed mobile number due to travelling abroad, or Mobile number entered by the user has been already changed in Facebook user account profile by an attacker. Case 3- Validation Through Username. Most of users do not care of username (Facebook URL) and, thus they do not remember username. Moreover, it is possible for attacker to change username in user profile. Case 4- Validation Through Full name. Many users tend to use dummy names in Facebook account, and thus they may not be able to remember full name 5. The Approach Fig. 3 Identify User. Case 1- Validation Through . If the user decided to regain control of the account through the , then Facebook website will prompt the user to provide the registered in Facebook account. If the correct was entered, Facebook will send a reset password to the provided enabling the user to reset the password and access the account. It seems an easy but the following examples show that it is possible for the account owner to lose the access to the account due to inability to prove the authenticity through . The user could not remember the correct , or The entered by user was correct but has already been blocked by Service Provider ESP, or The entered by user was correct but has already been hacked by an attacker, or The entered by user was correct but has already been changed in Facebook user profile by an attacker. As a result, the user will not be able to receive reset password message through , and thus cannot access Facebook user account. Case 2- Validation Through Mobile Phone. The user may select mobile phone to prove authenticity to Facebook website, which in turn will prompt the user to provide mobile phone number registered in Facebook account. The Facebook sends SMS verification message or makes a call to the entered mobile number enabling the user to access This section presents the proposed security approach to protect the user account in online social networks from unauthorized access. Sections 5.1 and 5.2 give an overview of the proposed approach and present its implementation respectively. The implementation of the proposed security approach is discussed in the context of Facebook, however the proposed approach is applicable to other OSN websites. Finally, Section 5.3 analyzes the security of the proposed approach. 5.1 An Overview Our approach aims to prevent losing access to user account in online social networks (OSNs) by enhancing existing security models in OSNs. For that end, our approach suggests that OSNs networks should allow each user to be having two passwords instead of one password. The first password (ordinary password) which is used to login to user account while the second one (additional password) is used only in exceptional cases. The proposed additional password is called Recovery Token, which is randomly generated by OSN website while opening an account. Recovery Token serves two purposes. On the user side, Recovery Token serves as an important recovery tool in the hand of account owner used in emergency cases to regain account control. And on the OSN website, Recovery Token serves as trusted identity authentication tool to prove the originality of the user. Having said that, we know Recovery Token cannot be used in normal login process but would be exclusively dedicated to recover user account and used in other processes that affect account ownership. In order to prevent losing access to user account, Recovery Token scheme should be given the highest priority above
5 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April all other authentication methods to access user account. Several facts support this assumption: First, the task assigned to Recovery Token to recover the account makes it very important to the account owner, and thus it is assumed that the owner would give more attention to Recovery Token and keep it in safe place. It would be much difficult for an attacker to know the Recovery Token as it is stored in safe place, and thus cannot impersonate the identity of the account owner; Second, as the Recovery Token is randomly generated by OSN website, it would be much harder for an attacker to guess it, even if the attacker has a knowledge about the user and his logic in creating passwords; Third, as the Recovery Token is infrequently used, utilized only for special purposes and kept away from prying eyes, the possibility of an attacker to steal it through key loggers and other spyware is very small. 5.2 Implementation We present the implementation of the proposed approach focusing on the newly introduced password (Recovery Token). Number of processes can be performed on Recovery Token during Facebook user account life cycle. The discussion first highlights the requirements of the Recovery Token. Recovery Token Requirements. To ensure the reliability of the proposed mechanism, Recovery Token must be random, unpredictable, and cannot be sub sequentially reliable reproduced [8]. It should not be shared and must be kept securely in safe place. Recovery Token should be given the highest priority over all other user authenticity proving mechanisms to recovering access to the account Opening User Account When internet user wishes to register and open an account in Facebook, Recovery Token is generated as a part of opening account process. Generation Recovery Token. After completing account registration process and the correctness of the provided information is verified, Facebook process generates the Recovery Token and prompts the user to keep the Recovery Token in safe place and to use it only for recovery purpose Normal Access to User Account During the life cycle of Facebook user account, the account owner may need to perform number of processes including: Recovery Token replacement, Recovery Token reporting, and obtaining new Recovery Token. Replacing Recovery Token. If user suspected a leakage of Recovery Token, he or she may request new Recovery Token and replacing the existing one. To get a new token, OSN website (eg., Facebook) prompts the user to provide current Recovery Token and then to prove user authenticity through and mobile phone as well. Report of Missing Recovery Token. The user may forget the Recovery Token. Losing Recovery Token should not increase opportunities of compromising user account unless it falls in the hands of an attacker. But losing the Recovery Token will reduce the opportunities of recovering the account in absence of other verification mechanisms ( , mobile phone, etc.). If our fear comes true and the user lost and misplaced the invaluable token, there should be existing a mechanism to handle this case. The user can report lost Recovery Token to OSN website and obtains new Recovery Token under certain conditions. Obtaining new Recovery Token. After reported of lost Token, the user may go into a process to obtain a new token for the account. because Recovery Token is crucial to regain control of user account, special attention must be paid into this process. The online social network OSN website prompts the user to: 1. prove the authenticity through ; and 2. prove the authenticity through mobile device; and 3. enter the first password used by user when the account was opened; or 4. try logging into Facebook from a device the user has logged in before registered , mobile device and password have been changed. Points 3 and 4 are precaution steps to prevent attackers from impersonating the identity of legitimate uses Inability to Access User Account The Recovery Token plays an important role when user loses access to the account. Recovering User Account. Number of threats (Section 3) may pose a risk on Facebook user account rendering it inaccessible (Sections 4.1 and 4.2). The worst case occurs when user fails to access both Facebook account and authenticity verification factors including and mobile. In this case Recovery Token becomes the only available option for user to recover the account. 5.3 Security Analysis We analyze the resilience of our approach against a number of attacks. We show that hacking one or all authentication factors cannot prevent the owner to use Recovery Token regain the control of account. Furthermore, we show that an attacker cannot carry out impersonation attacks. We will compare our security approach with Facebook security model. -Hacking Used in Facebook Account. Facebook security model allows users to regain account control
6 6 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April 2015 through or mobile phone. Let us consider the following two scenarios. An attacker hacked the registered in Facebook account and attempts to compromise Facebook account impersonating user identity. The attacker follows 'forgot the password' procedure and enters the to receive the reset password message from Facebook website. Once the attacker receives the new password, the account is compromised and the attacker can take control of the account and change information in user profile. Our solution can mitigate this impersonation attack and allows the user to regain the control of the account through the Recovery Token. -Compromising Mobile Phone Used in Facebook Account. If an attacker gets a possibility to access user mobile phone and tries to login to user account. Following "forgot the password' procedure the attacker enters the mobile phone number impersonate user identity and receives the access code from Facebook website. Once the attacker receives the access code, the account is compromised and the attacker takes the control of the account. Our solution can protect user account from such impersonation attack and allows the user to regain the control of the account through the Recovery Token. It should be noted that, the Recovery Token serves as another protection layer for user account. On the other side, using the Recovery Token would make it easy for the account owner to bypass traditional verification process and regain the control of the account. -Unauthorized Changes to Profile Settings. Facebook allows users to change information in their account profile including: password, , mobile phone, username provided that the password is given. Facebook also allows users to change security features like Login Approvals and trusted contacts. This way, it would be very easy for an attacker to change the account authentication information if the attacker already got the password by key loggers, spyware or any other means. On the other side, it would be very hard to the account owner to regain account control if information has been illegally changed by an attacker. Our solution can protect user account from unauthorized changes attack by allowing OSN user to regain the control of the account, and thus discards all unauthorized changes have been made to user profile. The user can provide the Recovery Token and regain the control of the account. -Losing account under the threat of force. In certain circumstances, the user may be forced to hand over account password to an adversary under the threat of force. After taking the control of user account, the attacker may change the login password as well as information in user account profile. In Facebook existing security model the user will lose access to the account and becomes unable to regain control of the account. Unlike Facebook security model, our solution can help the legitimate user to regain the control of the account with help of Recovery Token. -Losing account because of untrusted employee. A company manager may authorize an employee to administer Facebook account in the name of company. Having the administrative privileges, the employee can change information in company Facebook account. In case it could not retrieve the password from the employee for any reason, the company will lose the access to the account. Unlike Facebook security model, our solution can help the legitimate user to regain the control of the account with help of Recovery Token. -Hacking Facebook User Account. In Facebook existing security model, when an attacker compromises user account and changes profile information used in authentication process, it would be very difficult for the owner to regain control of the account. And it would be almost impossible for the owner to regain the control of the account if the used with Facebook account was hacked and the mobile phone number was changed, for example. No matter how the account owner loses the access to the account, by using Recovery Token the owner can regain the control of the account even if all authentication means are compromised. 6. Conclusion In this paper, we propose an approach that allows users to protect their accounts in online social networks OSNs from unauthorized access. Our approach mitigates the security risks resulting from unauthorized access by introducing an additional protection layer, Recovery Token. The proposed approach does not dedicated infrastructure and poses no overhead. The approach improves the Quality of Service (QoS) by enhancing the existing security schemes and provides users with an adequate assurance of account protection. The advantages of our solution are analyzed in the context of Facebook as an example. We believe the proposed approach is applicable and can be generalized to enhance security schemes in all other online social networks as well as Service Providers (ESPs) websites like Gmail, Yahoo, Hotmail, etc. Further research should investigate techniques to improve the resistance of OSNs networks that implement Recovery Token to impersonation attacks. 7. References [1] Mohamed Shehab a, Anna Squicciarini b, Gail-Joon Ahn c, Irini Kokkinou Access control for online social networks third party applications Elsevier- Computers
7 IJCSNS International Journal of Computer Science and Network Security, VOL.15 No.4, April [2] [3] [4] [5] [6] [7] [8] [9] [10] [11] [12] & Security 31 (2012) Facebook, Facebook Statistics, March < Twitter, Twitter Numbers, March < Facebook, Gorrell P. Cheek, Mohamed Shehab "Policy-by- Example for Online Social Networks" SACMATO 12, JUNE 20-22, 2012 NEWARK, NEW JERSY, USA, ACM, YEAR Liu Kun, Terzi Evimaria. A framework for computing the privacy scores of users in online social networks. In: ICDM 2009, the ninth IEEE international conference on data mining, pp.288e297; December H. Kim, J. Tang, R. Anderson, Social authentication: harder than it looks, in: Proceedings of the 2012 Cryptography and Data Security Conference, M. Gjoka, M. Kurant, C.T. Butts, A. Markopoulou, Walking in Facebook: a case study of unbiased sampling of osns, in: Proceedings of IEEE INFOCOM 10, San Diego, CA, A.S. Yuksel, M. E. Yuksel, and A. H. Zaim. An approach for protecting privacy on social networks. In Proceedings of 5th International Conference on Systems and Networks Communications, Washington, DC, USA, IEEE Computer Society. A. Acquisti and J. Grossklags. Privacy and rationality in individual decision making. IEEE Security and Privacy, 3(1):26{33}, M. Milton Joe, Dr. B. Ramakrishnan, Dr. R.S. Shaji Prevention of Losing User Account by Enhancing Security Module: A Facebook Case, Journal of Emerging Technologies in Web Intelligence, Vol. 5, No. 3, August 2013, Page No: M. Milton Joe, Dr. B. Ramakrishnan "A Survey of Various Security Issues in Online Social Networks", International Journal of Computer Networks and Applications Vol. 1, No. 1, November - December (2014), Page No: Abdul Azim Abdul Ghani received his M.S. degrees in Computer Science from University of Miami, Florida, U.S.A in 1984 and Ph.D. in Computer Science from University of Strathclyde, Scotland, U.K in His research areas include software engineering, software metric, software quality, software testing. He is now a professor in Department of Software Engineering and Information System, Faculty of Computer Science and Information Technology, Universiti Putra Malaysia. Ramlan Mahmod holds a PhD from University of Bradford, United Kingdom. Currently, he is now Professor and the Dean of Faculty of Computer Science and Information Technology, Universiti Putra Malaysia, His research area are artificial intelligence and Information Security. Abdulraman Muthana received his B.Sc in Computer Science from Mosul University, Iraq, M.Sc in Computer Applications from Bangalore University, India and PhD in Information Security from University Putra Malaysia in. His research areas include information security, smartphone security, network security, software security. He is now an Assistant Professor in Faculty of Computer Science and Information Systems, Thamar University, Yemen.
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Hygiene Guide. Politicians and Political Parties
 Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
Cyber Hygiene Guide Politicians and Political Parties Canadian Election Integrity Initiative Design by ccm.design Cover Image by Songquan Deng Helping to Safeguard the Integrity of the Electoral Process
ACCESS CONTROL IN A SOCIAL NETWORKING ENVIRONMENT
 ACCESS CONTROL IN A SOCIAL NETWORKING ENVIRONMENT A Project Report Presented to The faculty of Department of Computer Science San Jose State University In Partial fulfillment of the Requirements for the
ACCESS CONTROL IN A SOCIAL NETWORKING ENVIRONMENT A Project Report Presented to The faculty of Department of Computer Science San Jose State University In Partial fulfillment of the Requirements for the
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
International Journal of Electrical and Computer Engineering 4: Application of Neural Network in User Authentication for Smart Home System
 Application of Neural Network in User Authentication for Smart Home System A. Joseph, D.B.L. Bong, and D.A.A. Mat Abstract Security has been an important issue and concern in the smart home systems. Smart
Application of Neural Network in User Authentication for Smart Home System A. Joseph, D.B.L. Bong, and D.A.A. Mat Abstract Security has been an important issue and concern in the smart home systems. Smart
Detecting Insider Attacks on Databases using Blockchains
 Detecting Insider Attacks on Databases using Blockchains Shubham Sharma, Rahul Gupta, Shubham Sahai Srivastava and Sandeep K. Shukla Department of Computer Science and Engineering Indian Institute of Technology,
Detecting Insider Attacks on Databases using Blockchains Shubham Sharma, Rahul Gupta, Shubham Sahai Srivastava and Sandeep K. Shukla Department of Computer Science and Engineering Indian Institute of Technology,
A Remote Biometric Authentication Protocol for Online Banking
 International Journal of Electrical Energy, Vol. 1, No. 4, December 2013 A Remote Biometric Authentication Protocol for Online Banking Anongporn Salaiwarakul Department of Computer Science and Information
International Journal of Electrical Energy, Vol. 1, No. 4, December 2013 A Remote Biometric Authentication Protocol for Online Banking Anongporn Salaiwarakul Department of Computer Science and Information
Department of Defense Public Affairs Guidance for Official Use of Social Media
 Department of Defense Public Affairs Guidance for Official Use of Social Media References: (a) DoD Instruction 8550.01, DoD Internet Services and Internet-Based Capabilities, September 11, 2012 (b) DoD
Department of Defense Public Affairs Guidance for Official Use of Social Media References: (a) DoD Instruction 8550.01, DoD Internet Services and Internet-Based Capabilities, September 11, 2012 (b) DoD
Threats & Vulnerabilities in Online Social Networks
 Threats & Vulnerabilities in Online Social Networks Lei Jin LERSAIS Lab @ School of Information Sciences University of Pittsburgh 03-26-2015 201 Topics Focus is the new vulnerabilities that exist in online
Threats & Vulnerabilities in Online Social Networks Lei Jin LERSAIS Lab @ School of Information Sciences University of Pittsburgh 03-26-2015 201 Topics Focus is the new vulnerabilities that exist in online
How. Biometrics. Expand the Reach of Mobile Banking ENTER
 How Biometrics Expand the Reach of Mobile Banking ENTER Table of Contents 01 The Mobile Banking Opportunity 02 What s Suppressing Mobile Adoption? 03 Onboarding Challenges: Proving One s Identity 04 Authentication
How Biometrics Expand the Reach of Mobile Banking ENTER Table of Contents 01 The Mobile Banking Opportunity 02 What s Suppressing Mobile Adoption? 03 Onboarding Challenges: Proving One s Identity 04 Authentication
Developing an End-to-End Secure Chat Application
 108 IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.11, November 2017 Developing an End-to-End Secure Chat Application Noor Sabah, Jamal M. Kadhim and Ban N. Dhannoon Department
108 IJCSNS International Journal of Computer Science and Network Security, VOL.17 No.11, November 2017 Developing an End-to-End Secure Chat Application Noor Sabah, Jamal M. Kadhim and Ban N. Dhannoon Department
AUTHENTICATION AND LOOKUP FOR NETWORK SERVICES
 Vol.5, No.1, pp. 81-90, 2014 doi: 10.7903/ijecs.1040 AUTHENTICATION AND LOOKUP FOR NETWORK SERVICES Daniel J. Buehrer National Chung Cheng University 168 University Rd., Min-Hsiung Township, Chiayi County,
Vol.5, No.1, pp. 81-90, 2014 doi: 10.7903/ijecs.1040 AUTHENTICATION AND LOOKUP FOR NETWORK SERVICES Daniel J. Buehrer National Chung Cheng University 168 University Rd., Min-Hsiung Township, Chiayi County,
Trusted Profile Identification and Validation Model
 International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 7, Issue 1 (May 2013), PP. 01-05 Himanshu Gupta 1, A Arokiaraj Jovith 2 1, 2 Dept.
International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 7, Issue 1 (May 2013), PP. 01-05 Himanshu Gupta 1, A Arokiaraj Jovith 2 1, 2 Dept.
CHI Easy Access: Register From on the CHI Network
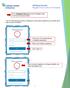 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
6 Vulnerabilities of the Retail Payment Ecosystem
 6 Vulnerabilities of the Retail Payment Ecosystem FINANCIAL INSTITUTION PAYMENT GATEWAY DATABASES POINT OF SALE POINT OF INTERACTION SOFTWARE VENDOR Table of Contents 4 7 8 11 12 14 16 18 Intercepting
6 Vulnerabilities of the Retail Payment Ecosystem FINANCIAL INSTITUTION PAYMENT GATEWAY DATABASES POINT OF SALE POINT OF INTERACTION SOFTWARE VENDOR Table of Contents 4 7 8 11 12 14 16 18 Intercepting
Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor Security
 Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
SECURED PASSWORD MANAGEMENT TECHNIQUE USING ONE-TIME PASSWORD PROTOCOL IN SMARTPHONE
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 3, March 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 3, March 2014,
Incident Response Lessons From the Front Lines. Session 276, March 8, 2018 Nolan Garrett, CISO, Children s Hospital Los Angeles
 Incident Response Lessons From the Front Lines Session 276, March 8, 2018 Nolan Garrett, CISO, Children s Hospital Los Angeles 1 Conflict of Interest Nolan Garrett Has no real or apparent conflicts of
Incident Response Lessons From the Front Lines Session 276, March 8, 2018 Nolan Garrett, CISO, Children s Hospital Los Angeles 1 Conflict of Interest Nolan Garrett Has no real or apparent conflicts of
Nigori: Storing Secrets in the Cloud. Ben Laurie
 Nigori: Storing Secrets in the Cloud Ben Laurie (benl@google.com) April 23, 2013 1 Introduction Secure login is something we would clearly like, but achieving it practically for the majority users turns
Nigori: Storing Secrets in the Cloud Ben Laurie (benl@google.com) April 23, 2013 1 Introduction Secure login is something we would clearly like, but achieving it practically for the majority users turns
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Adobe Sign and 21 CFR Part 11
 Adobe Sign and 21 CFR Part 11 Today, organizations of all sizes are transforming manual paper-based processes into end-to-end digital experiences speeding signature processes by 500% with legal, trusted
Adobe Sign and 21 CFR Part 11 Today, organizations of all sizes are transforming manual paper-based processes into end-to-end digital experiences speeding signature processes by 500% with legal, trusted
How to Secure SSH with Google Two-Factor Authentication
 How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
How to Secure SSH with Google Two-Factor Authentication WELL, SINCE IT IS QUITE COMPLEX TO SET UP, WE VE DECIDED TO DEDICATE A WHOLE BLOG TO THAT PARTICULAR STEP! A few weeks ago we took a look at how
Cybersecurity in 2016 and Lessons learned
 Cybersecurity in 2016 and Lessons learned Dr. Yu Cai Associate Professor Program Chair, Computer Network & System Administration School of Technology Michigan Technological University cai@mtu.edu A Quick
Cybersecurity in 2016 and Lessons learned Dr. Yu Cai Associate Professor Program Chair, Computer Network & System Administration School of Technology Michigan Technological University cai@mtu.edu A Quick
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Manually Create Phishing Page For Facebook 2014
 Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Progressive Authentication in ios
 Progressive Authentication in ios Genghis Chau, Denis Plotnikov, Edwin Zhang December 12 th, 2014 1 Overview In today s increasingly mobile-centric world, more people are beginning to use their smartphones
Progressive Authentication in ios Genghis Chau, Denis Plotnikov, Edwin Zhang December 12 th, 2014 1 Overview In today s increasingly mobile-centric world, more people are beginning to use their smartphones
ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0
 ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0 August 2017 Date Version Description August 2017 1.0 Initial Draft 1. Single Sign On... 2 2. To register for SSO on the Global ID webpage...
ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0 August 2017 Date Version Description August 2017 1.0 Initial Draft 1. Single Sign On... 2 2. To register for SSO on the Global ID webpage...
Abstract. main advantage with cloud computing is that, the risk of infrastructure maintenance reduces a
 Abstract Cloud computing is the key technology widely used across most of the organizations. The main advantage with cloud computing is that, the risk of infrastructure maintenance reduces a lot. Most
Abstract Cloud computing is the key technology widely used across most of the organizations. The main advantage with cloud computing is that, the risk of infrastructure maintenance reduces a lot. Most
ADP Security Management Services
 ADP Security Management Services Getting Started Guide for Security Administrators Updated August 2017 Contents Getting Started with Security Management Service... 5 Setting Up Your Organization... 5 Setting
ADP Security Management Services Getting Started Guide for Security Administrators Updated August 2017 Contents Getting Started with Security Management Service... 5 Setting Up Your Organization... 5 Setting
Secure access to your enterprise. Enforce risk-based conditional access in real time
 Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
Secure access to your enterprise Enforce risk-based conditional access in real time FOREWORD The intelligent cloud has created an opportunity to do security better Traditional security perimeters no longer
KT-4 Keychain Token Welcome Guide
 SafeNet Authentication Service KT-4 Keychain Token Welcome Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document
SafeNet Authentication Service KT-4 Keychain Token Welcome Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document
Hacking Demonstration. Dr John McCarthy Ph.D. BSc (Hons) MBCS
 Hacking Demonstration Dr John McCarthy Ph.D. BSc (Hons) MBCS Demonstration Deploying effective cyber security is one of the 21 st century s greatest challenges for business. The threats facing businesses
Hacking Demonstration Dr John McCarthy Ph.D. BSc (Hons) MBCS Demonstration Deploying effective cyber security is one of the 21 st century s greatest challenges for business. The threats facing businesses
Survey Guide: Businesses Should Begin Preparing for the Death of the Password
 Survey Guide: Businesses Should Begin Preparing for the Death of the Password Survey Guide: Businesses Should Begin Preparing for the Death of the Password The way digital enterprises connect with their
Survey Guide: Businesses Should Begin Preparing for the Death of the Password Survey Guide: Businesses Should Begin Preparing for the Death of the Password The way digital enterprises connect with their
A Smart Card Based Authentication Protocol for Strong Passwords
 A Smart Card Based Authentication Protocol for Strong Passwords Chin-Chen Chang 1,2 and Hao-Chuan Tsai 2 1 Department of Computer Science and Information Engineering, Feng Chia University, Taichung, Taiwan,
A Smart Card Based Authentication Protocol for Strong Passwords Chin-Chen Chang 1,2 and Hao-Chuan Tsai 2 1 Department of Computer Science and Information Engineering, Feng Chia University, Taichung, Taiwan,
Prof. Christos Xenakis
 From Real-world Identities to Privacy-preserving and Attribute-based CREDentials for Device-centric Access Control Device-Centric Authentication for Future Internet Prof. Christos Xenakis H2020 Clustering
From Real-world Identities to Privacy-preserving and Attribute-based CREDentials for Device-centric Access Control Device-Centric Authentication for Future Internet Prof. Christos Xenakis H2020 Clustering
Prof. Christos Xenakis
 From Real-world Identities to Privacy-preserving and Attribute-based CREDentials for Device-centric Access Control Device-Centric Authentication for Future Internet Prof. Christos Xenakis SAINT Workshop
From Real-world Identities to Privacy-preserving and Attribute-based CREDentials for Device-centric Access Control Device-Centric Authentication for Future Internet Prof. Christos Xenakis SAINT Workshop
IMPROVING DATA SECURITY USING ATTRIBUTE BASED BROADCAST ENCRYPTION IN CLOUD COMPUTING
 IMPROVING DATA SECURITY USING ATTRIBUTE BASED BROADCAST ENCRYPTION IN CLOUD COMPUTING 1 K.Kamalakannan, 2 Mrs.Hemlathadhevi Abstract -- Personal health record (PHR) is an patient-centric model of health
IMPROVING DATA SECURITY USING ATTRIBUTE BASED BROADCAST ENCRYPTION IN CLOUD COMPUTING 1 K.Kamalakannan, 2 Mrs.Hemlathadhevi Abstract -- Personal health record (PHR) is an patient-centric model of health
Innovative Graphical Passwords using Sequencing and Shuffling Together
 Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
Innovative Graphical Passwords using Sequencing and Shuffling Together Rashmi Wable 1, Dr.Suhas Raut 2 N.K. Orchid College of Engineering and Technology, Solapur ABSTRACT Graphical authentication technology
Facebook API Breach. Jake Williams Rendition Infosec
 Facebook API Breach Jake Williams (@MalwareJake) Rendition Infosec www.rsec.us @RenditionSec Facebook View As Facebook allows users/developers to see what a profile page looks like from another user s
Facebook API Breach Jake Williams (@MalwareJake) Rendition Infosec www.rsec.us @RenditionSec Facebook View As Facebook allows users/developers to see what a profile page looks like from another user s
Author: Group 03 Yuly Suvorov, Luke Harvey, Ben Holland, Jordan Cook, Michael Higdon. All Completed SRS2 Steps
 Software Requirements Document for Graffiti Author: Group 03 Yuly Suvorov, Luke Harvey, Ben Holland, Jordan Cook, Michael Higdon Version Date Author Change 0.1 09/13/ SM Initial Document 07 0.2 09/22/
Software Requirements Document for Graffiti Author: Group 03 Yuly Suvorov, Luke Harvey, Ben Holland, Jordan Cook, Michael Higdon Version Date Author Change 0.1 09/13/ SM Initial Document 07 0.2 09/22/
Making social interactions accessible in online social networks
 Information Services & Use 33 (2013) 113 117 113 DOI 10.3233/ISU-130702 IOS Press Making social interactions accessible in online social networks Fredrik Erlandsson a,, Roozbeh Nia a, Henric Johnson b
Information Services & Use 33 (2013) 113 117 113 DOI 10.3233/ISU-130702 IOS Press Making social interactions accessible in online social networks Fredrik Erlandsson a,, Roozbeh Nia a, Henric Johnson b
The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication
 White Paper The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication Table of contents Introduction... 2 Password protection alone is no longer enough...
White Paper The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication Table of contents Introduction... 2 Password protection alone is no longer enough...
Security and Privacy
 E-mail Security and Privacy Department of Computer Science Montclair State University Course : CMPT 320 Internet/Intranet Security Semester : Fall 2008 Student Instructor : Alex Chen : Dr. Stefan Robila
E-mail Security and Privacy Department of Computer Science Montclair State University Course : CMPT 320 Internet/Intranet Security Semester : Fall 2008 Student Instructor : Alex Chen : Dr. Stefan Robila
Texas Division How to Login and Register for My IT Support and ServiceNow
 Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT SUBSCRIBER S GUIDE VERSION 1.3 ECB-PUBLIC 15-April-2014 ESCB-PKI - Subscriber's Procedures v.1.3.docx Page 2 of 26 TABLE OF CONTENTS GLOSSARY AND ACRONYMS...
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT SUBSCRIBER S GUIDE VERSION 1.3 ECB-PUBLIC 15-April-2014 ESCB-PKI - Subscriber's Procedures v.1.3.docx Page 2 of 26 TABLE OF CONTENTS GLOSSARY AND ACRONYMS...
Privileged Account Security: A Balanced Approach to Securing Unix Environments
 Privileged Account Security: A Balanced Approach to Securing Unix Environments Table of Contents Introduction 3 Every User is a Privileged User 3 Privileged Account Security: A Balanced Approach 3 Privileged
Privileged Account Security: A Balanced Approach to Securing Unix Environments Table of Contents Introduction 3 Every User is a Privileged User 3 Privileged Account Security: A Balanced Approach 3 Privileged
CCloud for ios Devices
 CCloud for ios Devices User Guide Guide Version 3.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. CCloud for ios - Introduction... 3 1.1.Starting Comodo Cloud...
CCloud for ios Devices User Guide Guide Version 3.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. CCloud for ios - Introduction... 3 1.1.Starting Comodo Cloud...
Graphical password authentication using Pass faces
 RESEARCH ARTICLE OPEN ACCESS Graphical password authentication using Pass faces Ms Grinal Tuscano*, Aakriti Tulasyan**, Akshata Shetty**, Malvina Rumao**, Aishwarya Shetty ** *(Department of Information
RESEARCH ARTICLE OPEN ACCESS Graphical password authentication using Pass faces Ms Grinal Tuscano*, Aakriti Tulasyan**, Akshata Shetty**, Malvina Rumao**, Aishwarya Shetty ** *(Department of Information
Software Design Description Report
 2015 Software Design Description Report CodeBenders Haldun Yıldız 1819663 Onur Aydınay 1819002 Deniz Can Yüksel 1819697 Ali Şihab Akcan 1818871 TABLE OF CONTENTS 1 Overview... 3 1.1 Scope... 3 1.2 Purpose...
2015 Software Design Description Report CodeBenders Haldun Yıldız 1819663 Onur Aydınay 1819002 Deniz Can Yüksel 1819697 Ali Şihab Akcan 1818871 TABLE OF CONTENTS 1 Overview... 3 1.1 Scope... 3 1.2 Purpose...
SOCIAL NETWORKING'S EFFECT ON BUSINESS SECURITY CONTROLS
 SOCIAL NETWORKING'S EFFECT ON BUSINESS SECURITY CONTROLS Jon Hanny Director of Information Security and Assurance, Buckley Sandler LLP Gaurav Chikara Senior Security Engineer, Cooley LLP AGENDA Social
SOCIAL NETWORKING'S EFFECT ON BUSINESS SECURITY CONTROLS Jon Hanny Director of Information Security and Assurance, Buckley Sandler LLP Gaurav Chikara Senior Security Engineer, Cooley LLP AGENDA Social
PayThankYou LLC Privacy Policy
 PayThankYou LLC Privacy Policy Last Revised: August 7, 2017. The most current version of this Privacy Policy may be viewed at any time on the PayThankYou website. Summary This Privacy Policy covers the
PayThankYou LLC Privacy Policy Last Revised: August 7, 2017. The most current version of this Privacy Policy may be viewed at any time on the PayThankYou website. Summary This Privacy Policy covers the
ONE ID Identity and Access Management System
 ONE ID Identity and Access Management System Local Registration Authority User Guide Document Identifier: 2274 Version: 1.8 Page 1 Copyright Notice Copyright 2011, ehealth Ontario All rights reserved No
ONE ID Identity and Access Management System Local Registration Authority User Guide Document Identifier: 2274 Version: 1.8 Page 1 Copyright Notice Copyright 2011, ehealth Ontario All rights reserved No
Web Security Vulnerabilities: Challenges and Solutions
 Web Security Vulnerabilities: Challenges and Solutions A Tutorial Proposal for ACM SAC 2018 by Dr. Hossain Shahriar Department of Information Technology Kennesaw State University Kennesaw, GA 30144, USA
Web Security Vulnerabilities: Challenges and Solutions A Tutorial Proposal for ACM SAC 2018 by Dr. Hossain Shahriar Department of Information Technology Kennesaw State University Kennesaw, GA 30144, USA
Cyber Security. February 13, 2018 (webinar) February 15, 2018 (in-person)
 Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Cyber Security Presenters: - Brian Everest, Chief Technology Officer, Starport Managed Services - Susan Pawelek, Accountant, Compliance and Registrant Regulation February 13, 2018 (webinar) February 15,
Ubiquitous One-Time Password Service Using Generic Authentication Architecture
 Ubiquitous One-Time Password Service Using Generic Authentication Architecture Chunhua Chen 1, Chris J. Mitchell 2, and Shaohua Tang 3 1,3 School of Computer Science and Engineering South China University
Ubiquitous One-Time Password Service Using Generic Authentication Architecture Chunhua Chen 1, Chris J. Mitchell 2, and Shaohua Tang 3 1,3 School of Computer Science and Engineering South China University
SecureDoc Disk Encryption Cryptographic Engine
 SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
7. How do I obtain a Temporary ID? You will need to visit HL Bank or mail us the econnect form to apply for a Temporary ID.
 About HL Bank Connect 1. What is HL Bank Connect? HL Bank Connect provides you with the convenience of accessing your bank accounts and performing online banking transactions via the Internet. 2. What
About HL Bank Connect 1. What is HL Bank Connect? HL Bank Connect provides you with the convenience of accessing your bank accounts and performing online banking transactions via the Internet. 2. What
BASELINE GENERAL PRACTICE SECURITY CHECKLIST Guide
 BASELINE GENERAL PRACTICE SECURITY CHECKLIST Guide Last Updated 8 March 2016 Contents Introduction... 2 1 Key point of contact... 2 2 Third Part IT Specialists... 2 3 Acceptable use of Information...
BASELINE GENERAL PRACTICE SECURITY CHECKLIST Guide Last Updated 8 March 2016 Contents Introduction... 2 1 Key point of contact... 2 2 Third Part IT Specialists... 2 3 Acceptable use of Information...
Privacy Based Protection Mechanism for Location Data with an Accurate Service
 Privacy Based Protection Mechanism for Location Data with an Accurate Service K. Spatika #1 # Vellore Institute of Technology, India Abstract Location based service are suitable for the user based services.
Privacy Based Protection Mechanism for Location Data with an Accurate Service K. Spatika #1 # Vellore Institute of Technology, India Abstract Location based service are suitable for the user based services.
CEO EXPOSURE: PASSWORDS AND PWNAGE
 CEO EMAIL EXPOSURE: PASSWORDS AND PWNAGE Introduction Passwords have become the bane of our digital existence. We use so many different accounts and services that attempting to keep track of them all is
CEO EMAIL EXPOSURE: PASSWORDS AND PWNAGE Introduction Passwords have become the bane of our digital existence. We use so many different accounts and services that attempting to keep track of them all is
How Secured2 Uses Beyond Encryption Security to Protect Your Data
 Secured2 Beyond Encryption How Secured2 Uses Beyond Encryption Security to Protect Your Data Secured2 Beyond Encryption Whitepaper Document Date: 06.21.2017 Document Classification: Website Location: Document
Secured2 Beyond Encryption How Secured2 Uses Beyond Encryption Security to Protect Your Data Secured2 Beyond Encryption Whitepaper Document Date: 06.21.2017 Document Classification: Website Location: Document
UCRChatline - ios Mobile Application
 Team 16 Milestone 1 Project Documentation: Page 1 UCRChatline - ios Mobile Application Milestone 1 Documentation November 2014 Computer Science 180, Fall 2014 Professor Iulian Neamtiu, Instructor Aiping
Team 16 Milestone 1 Project Documentation: Page 1 UCRChatline - ios Mobile Application Milestone 1 Documentation November 2014 Computer Science 180, Fall 2014 Professor Iulian Neamtiu, Instructor Aiping
Chronos Fitness, Inc. dba Chronos Wearables, 1347 Green St. San Francisco CA 94109,
 Privacy Policy Of Chronos Wearables This Application collects some Personal Data from its Users. Data Controller and Owner Chronos Fitness, Inc. dba Chronos Wearables, 1347 Green St. San Francisco CA 94109,
Privacy Policy Of Chronos Wearables This Application collects some Personal Data from its Users. Data Controller and Owner Chronos Fitness, Inc. dba Chronos Wearables, 1347 Green St. San Francisco CA 94109,
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Pass, No Record: An Android Password Manager
 Pass, No Record: An Android Password Manager Alex Konradi, Samuel Yeom December 4, 2015 Abstract Pass, No Record is an Android password manager that allows users to securely retrieve passwords from a server
Pass, No Record: An Android Password Manager Alex Konradi, Samuel Yeom December 4, 2015 Abstract Pass, No Record is an Android password manager that allows users to securely retrieve passwords from a server
Table of Contents. Overview of the TEA Login Application Features Roles in Obtaining Application Access Approval Process...
 TEAL Help Table of Contents Overview of the TEA Login Application... 7 Features... 7 Roles in Obtaining Application Access... 7 Approval Process... 8 Processing an Application Request... 9 The Process
TEAL Help Table of Contents Overview of the TEA Login Application... 7 Features... 7 Roles in Obtaining Application Access... 7 Approval Process... 8 Processing an Application Request... 9 The Process
SecureTraveler User s Manual
 SecureTraveler User s Manual SecureTraveler is the DataTraveler II + Migo configuration utility program that allows corporate and home users to set up public and password-protected privacy zones on the
SecureTraveler User s Manual SecureTraveler is the DataTraveler II + Migo configuration utility program that allows corporate and home users to set up public and password-protected privacy zones on the
Hardware One-Time Password User Guide August 2018
 Hardware One-Time Password User Guide August 2018 Copyright 2017 Exostar LLC. All rights reserved 1 Version Impacts Date Owner Hardware One-Time Password User Guide Image updates August 2018 M. Williams
Hardware One-Time Password User Guide August 2018 Copyright 2017 Exostar LLC. All rights reserved 1 Version Impacts Date Owner Hardware One-Time Password User Guide Image updates August 2018 M. Williams
Defenses against Large Scale Online Password Guessing by Using Persuasive Cued Click Points
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 2, Issue. 4, April 2013,
Cyber security tips and self-assessment for business
 Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Cyber security tips and self-assessment for business Last year one in five New Zealand SMEs experienced a cyber-attack, so it s essential to be prepared. Our friends at Deloitte have put together this
Recovering Yahoo account
 Recovering Yahoo email account Submitted by Jess on Tue, 03/05/2013-02:36 It is undeniable that Yahoo Mail is one of the pioneering and widely used email service. It comes in two (2) versions: the free
Recovering Yahoo email account Submitted by Jess on Tue, 03/05/2013-02:36 It is undeniable that Yahoo Mail is one of the pioneering and widely used email service. It comes in two (2) versions: the free
Kingston SecureTraveler User Guide
 Kingston SecureTraveler User Guide Thank you for buying a Kingston DataTraveler Hi-Speed certified USB Flash drive. Kingston s DataTraveler products incorporate the latest in Hi-Speed USB 2.0 Flash memory
Kingston SecureTraveler User Guide Thank you for buying a Kingston DataTraveler Hi-Speed certified USB Flash drive. Kingston s DataTraveler products incorporate the latest in Hi-Speed USB 2.0 Flash memory
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE
 GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
A flexible biometrics remote user authentication scheme
 Computer Standards & Interfaces 27 (2004) 19 23 www.elsevier.com/locate/csi A flexible biometrics remote user authentication scheme Chu-Hsing Lin*, Yi-Yi Lai Department of Computer Science and Information
Computer Standards & Interfaces 27 (2004) 19 23 www.elsevier.com/locate/csi A flexible biometrics remote user authentication scheme Chu-Hsing Lin*, Yi-Yi Lai Department of Computer Science and Information
The State of Hacked Accounts
 October 2011 Overview The use of compromised (e.g. stolen credentials or hacked) accounts to send spam and scams has increased throughout 2011 to become a growing percentage of the unwanted email that
October 2011 Overview The use of compromised (e.g. stolen credentials or hacked) accounts to send spam and scams has increased throughout 2011 to become a growing percentage of the unwanted email that
Kenna Platform Security. A technical overview of the comprehensive security measures Kenna uses to protect your data
 Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme
 Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme Y.. Lee Department of Security Technology and Management WuFeng niversity, hiayi, 653, Taiwan yclee@wfu.edu.tw ABSTRAT Due
Smart-card-loss-attack and Improvement of Hsiang et al. s Authentication Scheme Y.. Lee Department of Security Technology and Management WuFeng niversity, hiayi, 653, Taiwan yclee@wfu.edu.tw ABSTRAT Due
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
Multi-factor Authentication Instructions
 What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
CIBC FirstCaribbean Mobile App. FREQUENTLY ASKED QUESTIONS (FAQs) Page 1 of 9
 CIBC FirstCaribbean Mobile App FREQUENTLY ASKED QUESTIONS (FAQs) 1. What is the CIBC FirstCaribbean Mobile App? A: The CIBC FirstCaribbean Mobile App allows you to complete everyday banking functions on
CIBC FirstCaribbean Mobile App FREQUENTLY ASKED QUESTIONS (FAQs) 1. What is the CIBC FirstCaribbean Mobile App? A: The CIBC FirstCaribbean Mobile App allows you to complete everyday banking functions on
Hardware One-Time Password User Guide November 2017
 Hardware One-Time Password User Guide November 2017 1 Table of Contents Table of Contents... 2 Purpose... 3 About One-Time Password Credentials... 3 How to Determine if You Need a Credential... 3 Acquisition
Hardware One-Time Password User Guide November 2017 1 Table of Contents Table of Contents... 2 Purpose... 3 About One-Time Password Credentials... 3 How to Determine if You Need a Credential... 3 Acquisition
Modern two-factor authentication: Easy. Affordable. Secure.
 Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Troubleshooting Tips
 Facts About the Durable Medical Equipment, Prosthetics, Orthotics, and Supplies (DMEPOS) Competitive Bidding Program Round 2 Recompete and the National Mail-Order Recompete Individual s Authorized Access
Facts About the Durable Medical Equipment, Prosthetics, Orthotics, and Supplies (DMEPOS) Competitive Bidding Program Round 2 Recompete and the National Mail-Order Recompete Individual s Authorized Access
10 Quick Tips to Mobile Security
 10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
lifeid Foundation FAQ v.1
 lifeid Foundation FAQ v.1 lifeid Foundation FAQ v.1 1 About the lifeid Foundation 2 1. What is the lifeid Foundation? 2 2. Who is on the lifeid Platform team? 2 3. What is the lifeid Foundation website
lifeid Foundation FAQ v.1 lifeid Foundation FAQ v.1 1 About the lifeid Foundation 2 1. What is the lifeid Foundation? 2 2. Who is on the lifeid Platform team? 2 3. What is the lifeid Foundation website
Algorithm To Ensure And Enforce Brute-Force Attack-Resilient Password In Routers
 Algorithm To Ensure And Enforce Brute-Force Attack-Resilient Password In Routers Mohammed Farik, ABM Shawkat Ali Abstract: Issues of weak login passwords arising from default passwords in wired and wireless
Algorithm To Ensure And Enforce Brute-Force Attack-Resilient Password In Routers Mohammed Farik, ABM Shawkat Ali Abstract: Issues of weak login passwords arising from default passwords in wired and wireless
CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE
 CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE The Customer: Top 10 Airline CREDENTIAL STUFFING KILLCHAIN A Top 10 Global Airline that earns over $15 Billion in annual revenue and serves
CASE STUDY TOP 10 AIRLINE SOLVES AUTOMATED ATTACKS ON WEB & MOBILE The Customer: Top 10 Airline CREDENTIAL STUFFING KILLCHAIN A Top 10 Global Airline that earns over $15 Billion in annual revenue and serves
SIMSme Management Cockpit Documentation
 Introduction SIMSme Management Cockpit Documentation Version 2.1 February 2018 Table of Contents 1 INTRODUCTION... 2 2 USERS... 3 3 LICENSES... 5 4 GROUPS... 7 5 CHANNELS... 8 6 DASHBOARD...10 7 APP SETTINGS...12
Introduction SIMSme Management Cockpit Documentation Version 2.1 February 2018 Table of Contents 1 INTRODUCTION... 2 2 USERS... 3 3 LICENSES... 5 4 GROUPS... 7 5 CHANNELS... 8 6 DASHBOARD...10 7 APP SETTINGS...12
TITLE SOCIAL MEDIA AND COLLABORATION POLICY
 DATE 9/20/2010 TITLE 408.01 SOCIAL MEDIA AND COLLABORATION POLICY ORG. AGENCY Department of Communications Approved AFT As more and more citizens in our community make the shift towards, or include the
DATE 9/20/2010 TITLE 408.01 SOCIAL MEDIA AND COLLABORATION POLICY ORG. AGENCY Department of Communications Approved AFT As more and more citizens in our community make the shift towards, or include the
Quick Heal AntiVirus Pro. Tough on malware, light on your PC.
 Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Employee Self Service Quick Reference Card
 Employee Self Service Quick Reference Card Contents Self Service Registration.... 2 Activate Your Email Address and Mobile Phone 7 Go Paperless After Registration 8 Forgot Username/Password 9 1 Self Service
Employee Self Service Quick Reference Card Contents Self Service Registration.... 2 Activate Your Email Address and Mobile Phone 7 Go Paperless After Registration 8 Forgot Username/Password 9 1 Self Service
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
International Journal of Computer Engineering and Applications, Volume XI, Issue III, March 17, ISSN
 International Journal of Computer Engineering and Applications, Volume XI, Issue III, March 17, www.ijcea.com ISSN 2321-3469 ENHANCING THE SECURITY OF SECONDARY AUTHENTICATION SYSTEM BASED ON EVENT LOGGER
International Journal of Computer Engineering and Applications, Volume XI, Issue III, March 17, www.ijcea.com ISSN 2321-3469 ENHANCING THE SECURITY OF SECONDARY AUTHENTICATION SYSTEM BASED ON EVENT LOGGER
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK REVIEW ON IMPLEMENTATION OF SECURITY MODEL FOR E-COMMERCE THROUGH AUTHENTICATION
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK REVIEW ON IMPLEMENTATION OF SECURITY MODEL FOR E-COMMERCE THROUGH AUTHENTICATION
2. Access Control. 1. Introduction
 PictureLock and Security Organizer Department of Computer Science and Engineering The Ohio State University Columbus, OH 43210 Abstract Traditional security measures require users
PictureLock and Security Organizer Department of Computer Science and Engineering The Ohio State University Columbus, OH 43210 Abstract Traditional security measures require users
Keep the Door Open for Users and Closed to Hackers
 Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Security Administrator Guide
 September 2017 Security Administrator Guide 2017 Arbitration Forums, Inc. All rights reserved. No parts of this work may be reproduced in any form or by any means graphic, electronic, or mechanical, including
September 2017 Security Administrator Guide 2017 Arbitration Forums, Inc. All rights reserved. No parts of this work may be reproduced in any form or by any means graphic, electronic, or mechanical, including
An Access Control Model for Collaborative Management of Shared Data in OSNS
 An Access Control Model for Collaborative Management of Shared Data in OSNS Ch. Aruna 1, G. Minni 2 1 M.Tech, Nimra College of Engineering & Technology, Vijayawada, A.P., India. 2 Asst. Professor, Dept.of
An Access Control Model for Collaborative Management of Shared Data in OSNS Ch. Aruna 1, G. Minni 2 1 M.Tech, Nimra College of Engineering & Technology, Vijayawada, A.P., India. 2 Asst. Professor, Dept.of
A Level-wise Priority Based Task Scheduling for Heterogeneous Systems
 International Journal of Information and Education Technology, Vol., No. 5, December A Level-wise Priority Based Task Scheduling for Heterogeneous Systems R. Eswari and S. Nickolas, Member IACSIT Abstract
International Journal of Information and Education Technology, Vol., No. 5, December A Level-wise Priority Based Task Scheduling for Heterogeneous Systems R. Eswari and S. Nickolas, Member IACSIT Abstract
