CCIE Service Provider v3.0 Lab Workbook. Copyright Information. Copyright Internetwork Expert, Inc. All rights reserved.
|
|
|
- Amberly Fowler
- 5 years ago
- Views:
Transcription
1 Copyright Information Copyright Internetwork Expert, Inc. All rights reserved. The following publication, CCIE Service Provider v3.0 Lab Workbook, was developed by Internetwork Expert, Inc. All rights reserved. No part of this publication may be reproduced or distributed in any form or by any means without the prior written permission of Internetwork Expert, Inc. Cisco, Cisco Systems, CCIE, and Cisco Certified Internetwork Expert, are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain countries. All other products and company names are the trademarks, registered trademarks, and service marks of the respective owners. Throughout this manual, Internetwork Expert, Inc. has used its best efforts to distinguish proprietary trademarks from descriptive names by following the capitalization styles used by the manufacturer. 1
2 Disclaimer The following publication, CCIE Service Provider v3.0 Lab Workbook, is designed to assist candidates in the preparation for Cisco Systems CCIE Service Provider Lab Exam. While every effort has been made to ensure that all material is as complete and accurate as possible, the enclosed material is presented on an as is basis. Neither the authors nor Internetwork Expert, Inc. assume any liability or responsibility to any person or entity with respect to loss or damages incurred from the information contained in this workbook. This workbook was developed by Internetwork Expert, Inc. and is an original work of the aforementioned authors. Any similarities between material presented in this workbook and actual CCIE lab material is completely coincidental. 2
3 R01 XR2 Fa0/0 POS0/7/0/ / /24 Fa1/0 POS0/6/0/0 R02 R03 R06 Fa0/0.619 XR1 Gig0/1/0/0.519 Fa0/0.23 Fa0/0.36 Gig0/1/0/ / / / /24 Fa0/0.46 Fa0/0.34 Fa0/ /24 Fa0/ / / / /24 R04 Fa0/0.45 R05 Fa0/0.519 CCIE Service Provider Version 3.0 Lab Workbook Base IPv4 Diagram INE Inc.
4 2.13 IS-IS BFD Configure BFD for IS-IS between R5 and XR1 so that if these is a failure of the link between them they begin reconvergence in less than one second. Configuration R5: interface FastEthernet0/0.519 bfd interval 250 min_rx 250 multiplier 3 isis bfd XR1: router isis 1 interface GigabitEthernet0/1/0/0.519 bfd minimum-interval 250 bfd multiplier 3 bfd fast-detect ipv4 Verification R5 and XR1 are BFD adjacenct via IS-IS, and are configured to detect a failure in 750ms. R05#show bfd neighbors detail NeighAddr LD/RD RH/RS State Int / Up Up Fa0/0.519 Session state is UP and using echo function with 250 ms interval. OurAddr: Local Diag: 0, Demand mode: 0, Poll bit: 0 MinTxInt: , MinRxInt: , Multiplier: 3 Received MinRxInt: , Received Multiplier: 3 Holddown (hits): 0(0), Hello (hits): 2000(544) Rx Count: 522, Rx Interval (ms) min/max/avg: 1/2004/1824 last: 856 ms ago Tx Count: 545, Tx Interval (ms) min/max/avg: 1/2000/1745 last: 1872 ms ago Elapsed time watermarks: 0 0 (last: 0) Registered protocols: CEF ISIS Uptime: 00:15:51 Last packet: Version: 1 - Diagnostic: 0 State bit: Up - Demand bit: 0 Poll bit: 0 - Final bit: 0 Multiplier: 3 - Length: 24 My Discr.: Your Discr.: 1 Min tx interval: Min rx interval: Min Echo interval:
5 RP/0/0/CPU0:XR1#show bfd ipv4 session detail Sat Mar 3 03:50: UTC I/f: GigabitEthernet0/1/0/0.519, Location: 0/1/CPU0, dest: , src: State: UP for 0d:0h:16m:3s, number of times UP: 1 Received parameters: Version: 1, desired tx interval: 1 s, required rx interval: 1 s Required echo rx interval: 250 ms, multiplier: 3, diag: None My discr: 1, your discr: , state UP, D/F/P/C/A: 0/0/0/0/0 Transmitted parameters: Version: 1, desired tx interval: 2 s, required rx interval: 2 s Required echo rx interval: 1 ms, multiplier: 3, diag: None My discr: , your discr: 1, state UP, D/F/P/C/A: 0/0/0/1/0 Timer Values: Local negotiated async tx interval: 2 s Remote negotiated async tx interval: 2 s Desired echo tx interval: 250 ms, local negotiated echo tx interval: 250 ms Echo detection time: 750 ms(250 ms*3), async detection time: 6 s(2 s*3) Local Stats: Intervals between async packets: Tx: Number of intervals=100, min=1669 ms, max=2001 ms, avg=1837 ms Last packet transmitted 351 ms ago Rx: Number of intervals=100, min=1507 ms, max=1996 ms, avg=1730 ms Last packet received 858 ms ago Intervals between echo packets: Tx: Number of intervals=100, min=251 ms, max=251 ms, avg=251 ms Last packet transmitted 22 ms ago Rx: Number of intervals=100, min=249 ms, max=252 ms, avg=251 ms Last packet received 21 ms ago Latency of echo packets (time between tx and rx): Number of packets: 100, min=0 us, max=2 ms, avg=540 us Session owner information: Client Desired interval Multiplier isis ms 3 69
6 R5 s interface is disabled at time index 03:56: XR1 detects this failure within 1 second at time index 03:56: Note that the carrier-delay 0 command is used on R5 so that there is no delay between when the interface is shutdown and when the link up/down message is generated. This allows us to see in real time that XR1 reacts to the change of the link status in less than 1 second. R05#config t Enter configuration commands, one per line. End with CNTL/Z. R05(config)#service timestamp log datetime msec R05(config)#int f0/0 R05(config-if)#carrier-delay 0 R05(config-if)#shut R05(config-if)# Mar 3 03:56:03.957: %LINK-5-CHANGED: Interface FastEthernet0/0, changed state to administratively down Mar 3 03:56:04.957: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to down RP/0/0/CPU0:XR1# LC/0/1/CPU0:Mar 3 03:56: : bfd_agent[121]: %L2-BFD-6-SESSION_STATE_DOWN : BFD session to neighbor on interface GigabitEthernet0/1/0/0.519 has gone down. Reason: Echo function failed 70
7 2.16 IS-IS Route Leaking Configure IS-IS Route Leaking from Level 1 to Level 2 on the L1/L2 routers as follows: o R3 should advertise the L2 prefix /32 to its L1 routers. o R4 should advertise the L2 prefix /32 to its L1 routers. o XR1 should advertise the /32 and /32 prefixes to its L1 routers. Configure IS-IS Route Leaking from Level 2 to Level 1 on the L1/L2 routers as follows: o R3 should not advertise the L1 prefix /32 to its L2 routers. o R4 should not advertise the L1 prefix /32 to its L2 routers. Configuration R3: router isis redistribute isis ip level-1 into level-2 distribute-list 101 redistribute isis ip level-2 into level-1 distribute-list 100 access-list 100 permit ip host host access-list 101 deny ip host host access-list 101 permit ip any any R4: router isis redistribute isis ip level-1 into level-2 distribute-list 101 redistribute isis ip level-2 into level-1 distribute-list 100 access-list 100 permit ip host host access-list 101 deny ip host host access-list 101 permit ip any any XR1: route-policy ISIS_ROUTE_LEAKING if destination in ( /32, /32) then pass endif end-policy router isis 1 address-family ipv4 unicast propagate level 2 into level 1 route-policy ISIS_ROUTE_LEAKING end 85
8 Verification Previously R1 and R2 only knew their own L1 routes as well as a default route to the L1/L2 routes. Now the specific routes /32 and /32 are advertised via R3 and R4 respectively. R02#show ip route isis Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP + - replicated route, % - next hop override Gateway of last resort is to network i*l /0 [115/10] via , 03:41:01, FastEthernet0/0.24 [115/10] via , 03:41:01, FastEthernet0/ /32 is subnetted, 1 subnets i L [115/10] via , 03:41:54, FastEthernet1/ /32 is subnetted, 1 subnets i ia [115/158] via , 00:14:38, FastEthernet0/ /32 is subnetted, 1 subnets i ia [115/148] via , 00:11:21, FastEthernet0/0.24 Due to the longest match routing principle, traffic going to /32 will always prefer R3 as the exit point, while traffic going to /32 will always prefer R4. R01#traceroute Type escape sequence to abort. Tracing the route to msec 0 msec 0 msec msec 4 msec 0 msec msec 4 msec 0 msec msec * 0 msec R01#traceroute Type escape sequence to abort. Tracing the route to msec 0 msec 4 msec msec 0 msec 4 msec msec * 0 msec 86
9 In the case that one of these exit points are down, traffic will fall back to the least specific match of /0 that is installed due to the Attached (ATT) bit being set in the IS-IS LSDB. R01#show ip route Routing entry for /32 Known via "isis", distance 115, metric 158, type inter area Redistributing via isis Last update from on FastEthernet0/0, 00:00:01 ago Routing Descriptor Blocks: * , from , 00:00:01 ago, via FastEthernet0/0 Route metric is 158, traffic share count is 1 R01#traceroute Type escape sequence to abort. Tracing the route to msec 0 msec 4 msec msec 0 msec 0 msec msec * 0 msec R02#config t Enter configuration commands, one per line. End with CNTL/Z. R02(config)#int f0/0.24 R02(config-subif)#shut R02(config-subif)# R01#show ip route % Network not in table R01#traceroute Type escape sequence to abort. Tracing the route to msec 0 msec 4 msec msec 0 msec 0 msec msec Route leaking can also be used to filter routes as the are converted from L1 to L2. Previously R6 has equal longest matches to /32 and /32 via R3 and R4. After route leaking filtering is applied, R6 has only one possible path to each of these destinations. R06#show ip route Routing entry for /32 Known via "isis", distance 115, metric 30, type level-2 Redistributing via isis Last update from on FastEthernet0/0.36, 00:17:55 ago Routing Descriptor Blocks: * , from , 00:17:55 ago, via FastEthernet0/0.36 Route metric is 30, traffic share count is 1 87
10 R06#show ip route Routing entry for /32 Known via "isis", distance 115, metric 20, type level-2 Redistributing via isis Last update from on FastEthernet0/0.46, 00:01:12 ago Routing Descriptor Blocks: * , from , 00:01:12 ago, via FastEthernet0/0.46 Route metric is 20, traffic share count is 1 Unlike L2 to L1 route leaking, which allows traffic engineering based on longest match, but still allows for fallback to a default route, filtering of L1 to L2 origination via route leaking does not allow for redundancy. For example in this case that R3 loses its link to the L1 domain, the /32 prefix becomes unreachable because R4 is configured to deny origination of this prefix from L1 into L2. R06#show ip route Routing entry for /32 Known via "isis", distance 115, metric 30, type level-2 Redistributing via isis Last update from on FastEthernet0/0.36, 00:20:02 ago Routing Descriptor Blocks: * , from , 00:20:02 ago, via FastEthernet0/0.36 Route metric is 30, traffic share count is 1 R06#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms R06# R03#config t Enter configuration commands, one per line. End with CNTL/Z. R03(config)#int f0/0.23 R03(config-subif)#shut R03(config-subif)# R06#show ip route % Network not in table R06#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:... Success rate is 0 percent (0/5) 88
11 Route leaking in IOS XR uses the same logic as regular IOS, however the matching of prefixes occurs through the usage of the Routing Policy Language (RPL). RP/0/0/CPU0:XR1#show rpl Sat Mar 3 02:55: UTC route-policy ISIS_ROUTE_LEAKING if destination in ( /32, /32) then pass endif end-policy RP/0/0/CPU0:XR1#show run router isis Sat Mar 3 02:55: UTC router isis 1 net address-family ipv4 unicast propagate level 2 into level 1 route-policy ISIS_ROUTE_LEAKING <snip> The result of this configuration is that XR2 learns the specific routes of /32 and /32 via XR1. RP/0/3/CPU0:XR2#show route isis Sat Mar 3 02:54: UTC i*l /0 [115/10] via , 03:52:07, POS0/7/0/0 i ia /32 [115/30] via , 00:13:51, POS0/7/0/0 i ia /32 [115/30] via , 00:13:51, POS0/7/0/0 89
12 To make this configuration more modular, the RPL policy could have called an external prefixset, similar to a prefix-list in regular IOS, that could be used to match the prefixes in question to be leaked. A configuration such as this could be written as follows: RP/0/0/CPU0:XR1#show rpl Sat Mar 3 02:59: UTC prefix-set ISIS_ROUTES /32, /32 end-set route-policy ISIS_ROUTE_LEAKING if destination in ISIS_ROUTES then pass endif end-policy RP/0/0/CPU0:XR1#show run router isis Sat Mar 3 02:59: UTC router isis 1 net address-family ipv4 unicast propagate level 2 into level 1 route-policy ISIS_ROUTE_LEAKING <snip> 90
13 2.18 Multi Topology IS-IS Configure IS-IS to run in Multi Topology mode on all devices. Change the IS-IS metric on the path from R2 to R3 to R6 to XR1 and back so that IPv4 traffic between R1 and XR2 prefers to use R4 and R5 in the transit path. Change the IS-IS metric on the path from R2 to R4 to R5 to XR1 and back so that IPv6 traffic between R1 and XR2 prefers to use R3 and R6 in the transit path. Configuration R01: router isis metric-style wide address-family ipv6 multi-topology R02: interface FastEthernet0/0.23 isis metric 20 interface FastEthernet0/0.24 isis ipv6 metric 20 router isis metric-style wide address-family ipv6 multi-topology R03: interface FastEthernet0/0.36 isis metric 20 router isis metric-style wide address-family ipv6 multi-topology R04: interface FastEthernet0/0.24 isis ipv6 metric 20 interface FastEthernet0/0.45 isis ipv6 metric 20 router isis metric-style wide address-family ipv6 multi-topology 103
14 R05: interface FastEthernet0/0.45 isis ipv6 metric 20 interface FastEthernet0/0.519 isis ipv6 metric 20 router isis metric-style wide address-family ipv6 multi-topology R06: interface FastEthernet0/0.36 isis metric 20 interface FastEthernet0/0.619 isis metric 20 router isis metric-style wide address-family ipv6 multi-topology XR1: router isis 1 address-family ipv4 unicast metric-style wide address-family ipv6 unicast metric-style wide no single-topology interface GigabitEthernet0/1/0/0.519 address-family ipv6 unicast metric 20 interface GigabitEthernet0/1/0/0.619 address-family ipv4 unicast metric 20 XR2: router isis 1 address-family ipv4 unicast metric-style wide address-family ipv6 unicast metric-style wide no single-topology 104
15 Verification In Multi Topology IS-IS, separate protocol stacks maintain separate database structures and use separate SPF runs, which means that one topology is independent of another. Mutli Topology IS-IS is most useful in practical IPv4 to IPv6 migration scenarios, where IPv6 is slowly introduced to the already existing IPv4 core. During migration the IPv4 and IPv6 topologies are kept separate from a database calculation point of view inside of IS-IS. Once the migration is complete and IPv4 and IPv6 run on a 1:1 basis with each other, Single Topology IS-IS can be enabled, which means that both IPv4 and IPv6 topology share the same database and SPF run. Note that this design is only possible if IPv4 runs on all interfaces that IPv6 runs on and vice-versa, otherwise database inconsistencies can occur which can result in loss of reachability in the network. Prior to making any changes to the previous example, R1 s IPv4 and IPv6 traffic follow the same path to reach XR2. R01#traceroute Type escape sequence to abort. Tracing the route to msec 0 msec 0 msec msec 4 msec 0 msec msec 4 msec 0 msec msec 0 msec 4 msec msec * 4 msec R01#traceroute 2000::20:20:20:20 Type escape sequence to abort. Tracing the route to 2000::20:20:20: :10:1:2::2 8 msec 0 msec 0 msec :20:2:3::3 8 msec 4 msec 0 msec :20:3:6::6 8 msec 12 msec 0 msec :20:6:19::19 4 msec 4 msec 0 msec ::20:20:20:20 8 msec 4 msec 4 msec 105
16 After the Multi Topology and metric changes, IPv4 traffic follows the path along the bottom of the topology through R4 and R5, while IPv6 traffic follows the path along the top of the topology through R3 and R6. R01#traceroute Type escape sequence to abort. Tracing the route to msec 0 msec 0 msec msec 4 msec 0 msec msec 4 msec 0 msec msec 4 msec 4 msec msec * 4 msec R01#traceroute 2000::20:20:20:20 Type escape sequence to abort. Tracing the route to 2000::20:20:20: :10:1:2::2 0 msec 0 msec 0 msec :20:2:3::3 4 msec 0 msec 0 msec :20:3:6::6 4 msec 0 msec 0 msec :20:6:19::19 4 msec 4 msec 0 msec ::20:20:20:20 0 msec 4 msec 0 msec RP/0/3/CPU0:XR2#traceroute Sat Mar 3 14:44: UTC Type escape sequence to abort. Tracing the route to msec 4 msec 2 msec msec 2 msec 2 msec msec 2 msec 2 msec msec 3 msec 2 msec msec * 3 msec RP/0/3/CPU0:XR2#traceroute 2000::1:1:1:1 Sat Mar 3 14:45: UTC Type escape sequence to abort. Tracing the route to 2000::1:1:1: :10:19:20::19 7 msec 4 msec 2 msec :20:6:19::6 2 msec 3 msec 3 msec :20:3:6::3 3 msec 3 msec 3 msec :20:2:3::2 4 msec 4 msec 2 msec :10:1:2::1 4 msec 5 msec 10 msec 106
17 When we look at the detailed view of the IS-IS database we can see that the IPv6 information is encoded as MT for Multi Topology, and that separate IPv4 and IPv6 metrics can exist. Note that Wide Metric Style is required in order to encode the Multi Topology information in the database. RP/0/3/CPU0:XR2#show isis database detail Sat Mar 3 14:46: UTC IS-IS 1 (Level-2) Link State Database LSPID LSP Seq Num LSP Checksum LSP Holdtime ATT/P/OL R x x313d 696 0/0/0 Area Address: MT: Standard (IPv4 Unicast) MT: IPv6 Unicast 0/0/0 NLPID: 0xcc NLPID: 0x8e Hostname: R01 IP Address: IPv6 Address: 2000::1:1:1:1 Metric: 10 IS-Extended R02.03 Metric: 10 MT (IPv6 Unicast) IS-Extended R02.03 Metric: 0 IP-Extended /32 Metric: 10 IP-Extended /24 Metric: 10 MT (IPv6 Unicast) IPv6 2000:10:1:2::/64 Metric: 0 MT (IPv6 Unicast) IPv6 2000::1:1:1:1/128 R x x66a /0/0 Area Address: MT: Standard (IPv4 Unicast) MT: IPv6 Unicast 0/0/0 NLPID: 0xcc NLPID: 0x8e Hostname: R02 IP Address: IPv6 Address: 2000::2:2:2:2 Metric: 10 IS-Extended R02.03 Metric: 10 IS-Extended R02.02 Metric: 20 IS-Extended R03.01 Metric: 20 MT (IPv6 Unicast) IS-Extended R02.02 Metric: 10 MT (IPv6 Unicast) IS-Extended R02.03 Metric: 10 MT (IPv6 Unicast) IS-Extended R03.01 Metric: 0 IP-Extended /32 Metric: 10 IP-Extended /24 Metric: 20 IP-Extended /24 Metric: 10 IP-Extended /24 Metric: 10 MT (IPv6 Unicast) IPv6 2000:20:2:3::/64 Metric: 20 MT (IPv6 Unicast) IPv6 2000:20:2:4::/64 Metric: 10 MT (IPv6 Unicast) IPv6 2000:10:1:2::/64 Metric: 0 MT (IPv6 Unicast) IPv6 2000::2:2:2:2/128 R x f 0x /0/0 Metric: 0 IS-Extended R02.00 Metric: 0 IS-Extended R04.00 R x x /0/0 Metric: 0 IS-Extended R02.00 Metric: 0 IS-Extended R01.00 <snip> 107
18 Note Load the Base OSPF and LDP Initial Configurations prior to starting this section. 4.2 MPLS L3 VPN with Static Routing Configure a VRF on R2 and XR1 as follows: o VRF Name: VPN_A o Route Distinguisher: 100:1 o Route Target Import: 100:1 o Route Target Export: 100:1 o Assign the VRF to the links connecting to R1 and XR2 respectively. Configure routing for the VRF as follows: o R1 should have a default route pointing towards R2. o R2 should have a static route for /32 pointing towards R1. o XR1 should have a static route for /32 pointing towards XR2. o XR2 should have a default route pointing towards XR1. Configure BGP on R2 and XR1 as follows: o Use BGP AS 100. o R2 and XR1 should be ibgp peers for the VPNv4 Address Family. o Use their Loopback0 interfaces as the source of the BGP session. o Advertise the static routes towards R1 and XR2 into BGP on R2 and XR1 respectively. Once complete R1 and XR2 should have reachability to each others Loopback0 interfaces when sourcing traffic from their own Loopback0 interfaces. 144
19 Configuration R1: ip route R2: vrf definition VPN_A rd 100:1 route-target export 100:1 route-target import 100:1 address-family ipv4 exit-address-family interface FastEthernet1/0 vrf forwarding VPN_A ip address router bgp 100 no bgp default ipv4-unicast neighbor remote-as 100 address-family vpnv4 neighbor activate neighbor send-community extended exit-address-family address-family ipv4 vrf VPN_A network mask exit-address-family ip route vrf VPN_A
20 XR1: vrf VPN_A address-family ipv4 unicast import route-target 100:1 export route-target 100:1 interface POS0/6/0/0 vrf VPN_A ipv4 address router static vrf VPN_A address-family ipv4 unicast / router bgp 100 address-family vpnv4 unicast neighbor remote-as 100 update-source Loopback0 address-family vpnv4 unicast vrf VPN_A rd 100:1 address-family ipv4 unicast network /32 XR2: router static address-family ipv4 unicast /
21 Verification show vrf detail is useful to quickly verify configured VRFs names, RDs, RT import and export policy, and assigned links. R02#show vrf detail VRF VPN_A (VRF Id = 1); default RD 100:1; default VPNID <not set> Interfaces: Fa1/0 Address family ipv4 (Table ID = 1 (0x1)): Export VPN route-target communities RT:100:1 Import VPN route-target communities RT:100:1 No import route-map No export route-map VRF label distribution protocol: not configured VRF label allocation mode: per-prefix Address family ipv6 not active. RP/0/0/CPU0:XR1#show vrf VPN_A detail Tue Mar 6 19:43: UTC VRF VPN_A; RD 100:1; VPN ID not set Description not set Interfaces: POS0/6/0/0 Address family IPV4 Unicast Import VPN route-target communities: RT:100:1 Export VPN route-target communities: RT:100:1 No import route policy No export route policy Address family IPV6 Unicast No import VPN route-target communities No export VPN route-target communities No import route policy No export route policy 147
22 Note that in IOS XR, once an interface is removed from the global routing table and assigned to a VRF table, it no longer appears in the show ip interface brief output, as seen below. Instead, interfaces can be verified with the command show ipv4 vrf all interface brief. RP/0/0/CPU0:XR1#show ip interface brief Tue Mar 6 20:26: UTC Interface IP-Address Status Protocol Loopback Up Up MgmtEth0/0/CPU0/0 unassigned Up Up MgmtEth0/0/CPU0/1 unassigned Up Up MgmtEth0/0/CPU0/2 unassigned Up Up GigabitEthernet0/1/0/0 unassigned Up Up GigabitEthernet0/1/0/ Up Up GigabitEthernet0/1/0/ Up Up GigabitEthernet0/1/0/1 unassigned Up Up GigabitEthernet0/1/0/2 unassigned Up Up GigabitEthernet0/1/0/3 unassigned Up Up RP/0/0/CPU0:XR1#show ipv4 vrf all interface brief Tue Mar 6 20:26: UTC Interface IP-Address Status Protocol Vrf-Name Loopback Up Up default MgmtEth0/0/CPU0/0 unassigned Up Up default MgmtEth0/0/CPU0/1 unassigned Up Up default MgmtEth0/0/CPU0/2 unassigned Up Up default GigabitEthernet0/1/0/0 unassigned Up Up default GigabitEthernet0/1/0/ Up Up default GigabitEthernet0/1/0/ Up Up default GigabitEthernet0/1/0/1 unassigned Up Up default GigabitEthernet0/1/0/2 unassigned Up Up default GigabitEthernet0/1/0/3 unassigned Up Up default POS0/6/0/ Up Up VPN_A 148
23 In this example, the CE routers R1 and XR2 simply have default routes pointing to the PE routers R2 and XR1, resulting in one of the simplest MPLS L3VPN designs. From the CE routers perspective these are just normal static routes in the global routing table. R01#show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP + - replicated route, % - next hop override Gateway of last resort is to network S* /0 [1/0] via /32 is subnetted, 1 subnets C is directly connected, Loopback /8 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, FastEthernet0/0 L /32 is directly connected, FastEthernet0/0 RP/0/3/CPU0:XR2#show route ipv4 Tue Mar 6 20:28: UTC Codes: C - connected, S - static, R - RIP, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - ISIS, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, su - IS-IS summary null, * - candidate default U - per-user static route, o - ODR, L - local, G - DAGR A - access/subscriber Gateway of last resort is to network S* /0 [1/0] via , 00:55:16 C /24 is directly connected, 01:24:13, POS0/7/0/0 L /32 is directly connected, 01:24:13, POS0/7/0/0 L /32 is directly connected, 01:24:14, Loopback0 149
24 From the PE routers R2 and XR1 s perspective, their static routes to the customers exist in the VRF table. R02#show ip route vrf VPN_A static Routing Table: VPN_A Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP + - replicated route, % - next hop override Gateway of last resort is not set /32 is subnetted, 1 subnets S [1/0] via RP/0/0/CPU0:XR1#show route vrf VPN_A ipv4 static Tue Mar 6 20:30: UTC S /32 [1/0] via , 00:53:58 R2 and XR1 then advertise these static routes into the VPNv4 BGP topology. In this case it is done with the network statement, but it could also be done with redistribution. R02#show bgp vpnv4 unicast all BGP table version is 4, local router ID is Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external Origin codes: i - IGP, e - EGP,? - incomplete Network Next Hop Metric LocPrf Weight Path Route Distinguisher: 100:1 (default for vrf VPN_A) *> / i *>i / i 150
25 RP/0/0/CPU0:XR1#show bgp vpnv4 unicast Tue Mar 6 20:31: UTC BGP router identifier , local AS number 100 BGP generic scan interval 60 secs BGP table state: Active Table ID: 0x0 BGP main routing table version 5 BGP scan interval 60 secs Status codes: s suppressed, d damped, h history, * valid, > best i - internal, r RIB-failure, S stale Origin codes: i - IGP, e - EGP,? - incomplete Network Next Hop Metric LocPrf Weight Path Route Distinguisher: 100:1 (default for vrf VPN_A) *>i / i *> / i Processed 2 prefixes, 2 paths Note that R2 and XR1 use the Loopback0 interfaces of each other as the next-hop value for the VPNv4 learned routes, since this is the update-source of the ibgp session. In addition to the next-hop value, the VPN label derived from VPNv4 BGP can be seen in the below output. This is the label value that the PE routers use to find the final customer route in the VRF. R02#show bgp vpnv4 unicast all /32 BGP routing table entry for 100:1: /32, version 4 Paths: (1 available, best #1, table VPN_A) Not advertised to any peer Local (metric 4) from ( ) Origin IGP, metric 0, localpref 100, valid, internal, best Extended Community: RT:100:1 mpls labels in/out nolabel/16003 RP/0/0/CPU0:XR1#show bgp vrf VPN_A ipv4 unicast /32 Tue Mar 6 20:33: UTC BGP routing table entry for /32, Route Distinguisher: 100:1 Versions: Process brib/rib SendTblVer Speaker 5 5 Last Modified: Mar 6 19:37: for 00:56:34 Paths: (1 available, best #1) Not advertised to any peer Path #1: Received by speaker 0 Local (metric 4) from ( ) Received Label 16 Origin IGP, metric 0, localpref 100, valid, internal, best, import-candidate, imported Extended community: RT:100:1 151
26 R2 and XR1 then combine this VPN label with the transport label used to reach each others Loopback0 interfaces. In this case the transport label is derived from OSPF + LDP. The transport label is used to tell the MPLS core what the exit PE is out of the network. R02#show ip route Routing entry for /32 Known via "ospf 1", distance 110, metric 4, type intra area Last update from on FastEthernet0/0.24, 01:10:13 ago Routing Descriptor Blocks: * , from , 01:10:13 ago, via FastEthernet0/0.24 Route metric is 4, traffic share count is , from , 01:10:13 ago, via FastEthernet0/0.23 Route metric is 4, traffic share count is 1 R02#show mpls forwarding-table Local Outgoing Prefix Bytes Label Outgoing Next Hop Label Label or Tunnel Id Switched interface /32 0 Fa0/ /32 0 Fa0/ RP/0/0/CPU0:XR1#show route ipv Tue Mar 6 20:36: UTC Routing entry for /32 Known via "ospf 1", distance 110, metric 4, type intra area Installed Mar 6 19:06: for 01:29:35 Routing Descriptor Blocks , from , via GigabitEthernet0/1/0/0.519 Route metric is , from , via GigabitEthernet0/1/0/0.619 Route metric is 4 No advertising protos. RP/0/0/CPU0:XR1#show mpls forwarding prefix /32 Tue Mar 6 20:36: UTC Local Outgoing Prefix Outgoing Next Hop Bytes Label Label or ID Interface Switched /32 Gi0/1/0/ /32 Gi0/1/0/
27 The two of these together, the VPN label and the transport label, make up the full label stack that is imposed when the PE routers receive traffic from the CE. This can be verified in the CEF table on the PE routers. The below cef table output of R2 indicates that the VPN label is 16003, and the transport label is either 21 or 22, depending which interface the traffic is CEF switched to. R02#show ip cef vrf VPN_A detail /32, epoch 0, flags rib defined all labels recursive via label nexthop FastEthernet0/0.23 label 21 nexthop FastEthernet0/0.24 label 22 The full label stack can also be verified in the data plane through the debug mpls packet output. Note that the transport label changes on a hop-by-hop basis, but the VPN label remains the same end-to-end. R3 is the Penultimate hop for R2, so the top label 17 is being removed for packets going to R2. Likewise on the other side R6 is the Penultimate hop for XR1, as the transport label 22 is being popped for traffic going towards XR1. R01#ping source repeat 1 Type escape sequence to abort. Sending 1, 100-byte ICMP Echos to , timeout is 2 seconds: Packet sent with a source address of Success rate is 100 percent (1/1), round-trip min/avg/max = 4/4/4 ms R03#debug mpls packet Packet debugging is on MPLS turbo: Fa0/0.23: rx: Len 126 Stack { } { } - ipv4 data MPLS turbo: Fa0/0.36: tx: Len 126 Stack { } { } - ipv4 data MPLS turbo: Fa0/0.36: rx: Len 126 Stack { } { } - ipv4 data MPLS turbo: Fa0/0.23: tx: Len 122 Stack { } - ipv4 data R03#show mpls forwarding-table Local Outgoing Prefix Bytes Label Outgoing Next Hop Label Label or Tunnel Id Switched interface / Fa0/ R03#show mpls forwarding-table Local Outgoing Prefix Bytes Label Outgoing Next Hop Label Label or Tunnel Id Switched interface 17 Pop Label / Fa0/
28 R06#debug mpls packet Packet debugging is on MPLS turbo: Fa0/0.36: rx: Len 126 Stack { } { } - ipv4 data MPLS turbo: Fa0/0.619: tx: Len 122 Stack { } - ipv4 data MPLS turbo: Fa0/0.619: rx: Len 126 Stack { } { } - ipv4 data MPLS turbo: Fa0/0.36: tx: Len 126 Stack { } { } - ipv4 data R06#show mpls forwarding-table Local Outgoing Prefix Bytes Label Outgoing Next Hop Label Label or Tunnel Id Switched interface 22 Pop Label / Fa0/ R06#show mpls forwarding-table Local Outgoing Prefix Bytes Label Outgoing Next Hop Label Label or Tunnel Id Switched interface / Fa0/ /32 0 Fa0/ The final result is that even though the devices in the core, i.e. R3, R4, R5, & R6, do not have routes for the customer VRF VPN_A, they are able to transport label switched packets that go between the PE routers of R2 and XR1. R03#show ip route % Network not in table R03#show ip route % Subnet not in table R04#show ip route % Network not in table R04#show ip route % Subnet not in table R05#show ip route % Network not in table R05#show ip route % Subnet not in table R06#show ip route % Network not in table R06#show ip route % Subnet not in table RP/0/3/CPU0:XR2#ping source Tue Mar 6 20:48: UTC Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/5 ms 154
29 Note Load the Base OSPF and LDP Initial Configurations prior to starting this section. 4.5 MPLS L3 VPN with BGP Configure a VRF on R2 and XR1 as follows: o VRF Name: VPN_A o Route Distinguisher: 100:1 o Route Target Import: 100:1 o Route Target Export: 100:1 o Assign the VRF to the links connecting to R1 and XR2 respectively. Configure BGP on R2 and XR1 as follows: o Use BGP AS 100. o R2 and XR1 should be ibgp peers for the VPNv4 Address Family. o Use their Loopback0 interfaces as the source of the BGP session. Configure BGP on R1 and XR2 as follows: o Use BGP AS 1. o R1 and R2 should peer EBGP. o XR1 and XR2 should peer EBGP. o Advertise the Loopback0 interfaces of R1 and XR2 into BGP. Once complete R1 and XR2 should have reachability to each others Loopback0 interfaces when sourcing traffic from their Loopback0 networks. 173
30 Configuration R1: router bgp 1 network mask neighbor remote-as 100 R2: vrf definition VPN_A rd 100:1 route-target export 100:1 route-target import 100:1 address-family ipv4 exit-address-family interface FastEthernet1/0 vrf forwarding VPN_A ip address router bgp 100 no bgp default ipv4-unicast neighbor remote-as 100 address-family vpnv4 neighbor activate neighbor send-community extended exit-address-family address-family ipv4 vrf VPN_A neighbor remote-as 1 neighbor as-override exit-address-family 174
31 XR1: vrf VPN_A address-family ipv4 unicast import route-target 100:1 export route-target 100:1 interface POS0/6/0/0 vrf VPN_A ipv4 address route-policy PASS pass end-policy router bgp 100 address-family vpnv4 unicast neighbor remote-as 100 update-source Loopback0 address-family vpnv4 unicast vrf VPN_A rd 100:1 address-family ipv4 unicast neighbor remote-as 1 address-family ipv4 unicast route-policy PASS in route-policy PASS out as-override XR2: route-policy PASS pass end-policy router bgp 1 address-family ipv4 unicast network /32 neighbor remote-as 100 address-family ipv4 unicast route-policy PASS in route-policy PASS out 175
32 Verification BGP as the PE-CE routing protocol uses one global BGP process, with the VRF specific peers defined under the address-family ipv4 vrf in regular IOS, and under the vrf BGP submode in IOS XR. Two things should be noted about this specific configuration. The first is that since the IOS XR routers are EBGP neighbors with each other, a Routing Policy is required in order to define which prefixes are allowed to be advertised and received. This is a fairly obvious requirement of IOS XR s configuration, because if the peering is committed without the RPL policy applied, a log message appears saying that the configuration is not functional without RPL. This can be seen as follows. RP/0/3/CPU0:XR2#show run router bgp Tue Mar 6 22:42: UTC router bgp 1 address-family ipv4 unicast network /32 neighbor remote-as 100 address-family ipv4 unicast route-policy PASS in route-policy PASS out RP/0/3/CPU0:XR2#config t Tue Mar 6 22:42: UTC RP/0/3/CPU0:XR2(config)#no router bgp 1 RP/0/3/CPU0:XR2(config)#commit RP/0/3/CPU0:Mar 6 22:42: : config[65736]: %MGBL-CONFIG-6-DB_COMMIT : Configuration committed by user 'cisco@admin'. Use 'show configuration commit changes ' to view the changes. RP/0/3/CPU0:XR2(config)#router bgp 1 RP/0/3/CPU0:XR2(config-bgp)# address-family ipv4 unicast RP/0/3/CPU0:XR2(config-bgp-af)# network /32 RP/0/3/CPU0:XR2(config-bgp-af)# RP/0/3/CPU0:XR2(config-bgp-af)# neighbor RP/0/3/CPU0:XR2(config-bgp-nbr)# remote-as 100 RP/0/3/CPU0:XR2(config-bgp-nbr)# address-family ipv4 unicast RP/0/3/CPU0:XR2(config-bgp-nbr-af)#commit RP/0/3/CPU0:Mar 6 22:42: : config[65736]: %MGBL-CONFIG-6-DB_COMMIT : Configuration committed by user 'cisco@admin'. Use 'show configuration commit changes ' to view the changes. RP/0/3/CPU0:XR2(config-bgp-nbr-af)#end RP/0/3/CPU0:Mar 6 22:42: : config[65736]: %MGBL-SYS-5-CONFIG_I : Configured from console by cisco@admin RP/0/3/CPU0:XR2#RP/0/3/CPU0:Mar 6 22:42: : bgp[139]: %ROUTING-BGP-5- ADJCHANGE : neighbor Up (VRF: default) RP/0/3/CPU0:Mar 6 22:42: : bgp[139]: %ROUTING-BGP-6-NBR_NOPOLICY : No inbound IPv4 Unicast policy is configured for ebgp neighbor No IPv4 Unicast prefixes will be accepted from the neighbor until inbound policy is configured. RP/0/3/CPU0:Mar 6 22:42: : bgp[139]: %ROUTING-BGP-6-NBR_NOPOLICY : No outbound IPv4 Unicast policy is configured for ebgp neighbor No IPv4 Unicast prefixes will be sent to the neighbor until outbound policy is configured. 176
33 If you were to miss this log message, for example if logging is disabled, you would also see it when you verify the BGP peering status with the neighbor as follows. RP/0/3/CPU0:XR2#show bgp ipv4 unicast summary Tue Mar 6 22:43: UTC BGP router identifier , local AS number 1 BGP generic scan interval 60 secs BGP table state: Active Table ID: 0xe BGP main routing table version 2 BGP scan interval 60 secs BGP is operating in STANDALONE mode. Process RcvTblVer brib/rib LabelVer ImportVer SendTblVer StandbyVer Speaker Some configured ebgp neighbors (under default or non-default vrfs) do not have both inbound and outbound policies configured for IPv4 Unicast address family. These neighbors will default to sending and/or receiving no routes and are marked with '' in the output below. Use the 'show bgp neighbor <nbr_address>' command for details. Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd :00:55 0 RP/0/3/CPU0:XR2# The second portion of this config that should be noted is the as-override keyword used on the PE s peering sessions towards the CEs. In cases where multiple customer sites are using the same BGP AS number, the default BGP filtering rule to not allow prefixes with the router s own AS number in the AS-Path will prevent prefixes from being exchanged between sites. The asoverride feature prevents prefixes from being filtered by editing the AS-Path information to remove the customer s Autonomous System. Without AS Override, prefixes are denied from being received, as seen in the following output. R2 removes the AS Override feature configured to its CE router, R1. R02#config t Enter configuration commands, one per line. End with CNTL/Z. R02(config)#router bgp 100 R02(config-router)#address-family ipv4 vrf VPN_A R02(config-router-af)#no neighbor as-override R02(config-router-af)#end R02#clear ip bgp * out R02# When new UPDATE messages are received in on R1 from R2 they contain the AS 1 in the path, which means that R1 cannot accept them. 177
34 R01#debug ip bgp updates BGP updates debugging is on for address family: IPv4 Unicast BGP(0): rcv UPDATE about /32 -- withdrawn BGP(0): rcv UPDATE w/ attr: nexthop , origin i, originator , merged path 100 1, AS_PATH, community, extended community, SSA attribute BGPSSA ssacount is 0 BGP(0): rcv UPDATE about /32 -- DENIED due to: AS-PATH contains our own AS; BGP: TX IPv4 Unicast Net global /32 Changed. BGP(0): no valid path for /32 BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL Attempting to install. BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL No bestpath. BGP: topo global:ipv4 Unicast:base Remove_fwdroute for /32 BGP: TX IPv4 Unicast Net global /32 RIB done. <snip> Even though R2 is still advertising /32 to R1, R1 cannot install it. R02#show bgp vpnv4 unicast vrf VPN_A neighbors advertised-routes BGP table version is 7, local router ID is Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external Origin codes: i - IGP, e - EGP,? - incomplete Network Next Hop Metric LocPrf Weight Path Route Distinguisher: 100:1 (default for vrf VPN_A) *>i / i Total number of prefixes 1 R01#show ip bgp BGP table version is 6, local router ID is Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external Origin codes: i - IGP, e - EGP,? - incomplete Network Next Hop Metric LocPrf Weight Path *> / i 178
35 Another alternative solution to this problem would be to configure the CE routers to allow prefixes that have their own AS in the path, such as the following. R01#debug ip bgp update BGP updates debugging is on for address family: IPv4 Unicast R01#config t Enter configuration commands, one per line. End with CNTL/Z. R01(config)#router bgp 1 R01(config-router)#neighbor allowas-in 1 R01(config-router)#end R01# %SYS-5-CONFIG_I: Configured from console by console BGP(0): rcvd UPDATE w/ attr: nexthop , origin i, merged path 100 1, AS_PATH BGP(0): rcvd /32 BGP: TX IPv4 Unicast Net global /32 Changed. BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL Attempting to install. BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL Built route type: 1024, flags: , tag: 64, metric: 0 paths: 1. BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL Path 1, type: DEF, gw: , idb: N/A, topo_id: 0, src: , lbl: , flags: 0. BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL Installing 1 paths, multipath limit 1 (from 1). BGP: net global:ipv4 Unicast:base /32 RIB-INSTALL Install successful. <snip> Even though the prefix /32 contains R1 s own AS number in the path, the allowasin command permits an exception for this. R01#show ip bgp BGP table version is 11, local router ID is Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external Origin codes: i - IGP, e - EGP,? - incomplete Network Next Hop Metric LocPrf Weight Path *> / i *> / i R01#show ip bgp BGP routing table entry for /32, version 11 Paths: (1 available, best #1, table default) Not advertised to any peer from ( ) Origin IGP, localpref 100, valid, external, best 179
36 The final result should be that R1 and XR2 have reachability to each others Loopbacks, but only when sourcing traffic from the Loopbacks, as the transit links from the PE-CEs have not been advertised. R01#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:... Success rate is 0 percent (0/5) R01#ping source Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Packet sent with a source address of Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 ms 180
Segment Routing On Demand Next Hop for L3/L3VPN
 Segment Routing On Demand Next Hop for L3/L3VPN When redistributing routing information across domains, provisioning of multi-domain services (L2VPN & L3VPN) has its own complexity and scalability issues.
Segment Routing On Demand Next Hop for L3/L3VPN When redistributing routing information across domains, provisioning of multi-domain services (L2VPN & L3VPN) has its own complexity and scalability issues.
Layer3 VPN with OSPF Protocol between CE-PE
 MPLS Layer3 VPN with OSPF Protocol between CE-PE Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made
MPLS Layer3 VPN with OSPF Protocol between CE-PE Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made
BGP Best External. Finding Feature Information
 The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
LAB1: BGP IPv4. BGP: Initial Config. Disclaimer
 Page1 LAB1: BGP IPv4 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB1: BGP IPv4 Disclaimer This Configuration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Configuring IPv6 Provider Edge over MPLS (6PE)
 Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
AS 100 AS 300. Lab -1 Private Communities - II .1 S1/2. Task 1. On R1: / / /24. Configure the above topology.
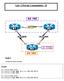 Lab -1 Private Communities - II AS 100.1 R1 S1/2 12.1.1.0/24 S1/1.2 R2 S1/3 S1/3 13.1.1.0/24 23.1.1.0/24 S1/1.3 R3 S1/2 Lo0 6.6.6.0/24 Lo1 7.7.7.0/24 AS 300 Task 1 Configure the above topology. On R1:
Lab -1 Private Communities - II AS 100.1 R1 S1/2 12.1.1.0/24 S1/1.2 R2 S1/3 S1/3 13.1.1.0/24 23.1.1.0/24 S1/1.3 R3 S1/2 Lo0 6.6.6.0/24 Lo1 7.7.7.0/24 AS 300 Task 1 Configure the above topology. On R1:
Layer3 VPN with RIP protocol between CE-PE
 MPLS Layer3 VPN with IP protocol between E-PE Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to
MPLS Layer3 VPN with IP protocol between E-PE Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to
IOS-XR EVPN Distributed Anycast IRB Gateway, L2/L3VPN Service with MPLS Data Plane
 IOS-XR EVPN Distributed Anycast IRB Gateway, L2/L3VPN Service with MPLS Data Plane Table of Content: 1. Overview... 2 2. Transport... 3 3. Services EVPN IRB L2/l3VPN Multipoint... 4 3.1. VRF/IRB Configuration...
IOS-XR EVPN Distributed Anycast IRB Gateway, L2/L3VPN Service with MPLS Data Plane Table of Content: 1. Overview... 2 2. Transport... 3 3. Services EVPN IRB L2/l3VPN Multipoint... 4 3.1. VRF/IRB Configuration...
Step 1: IP Configuration: On R1: On R2: On R3: R1(config)#int s1/2 R1(config-if)#ip addr R1(config-if)#no shu
 Step 1: IP Configuration: n R1: R1(config)#int s1/2 R1(config-if)#ip addr 12.1.1.1 255.255.255.0 R1(config-if)#no shu R1(config-if)#int lo0 R1(config-if)#ip addr 1.1.1.1 255.0.0.0 R1(config-if)#int lo1
Step 1: IP Configuration: n R1: R1(config)#int s1/2 R1(config-if)#ip addr 12.1.1.1 255.255.255.0 R1(config-if)#no shu R1(config-if)#int lo0 R1(config-if)#ip addr 1.1.1.1 255.0.0.0 R1(config-if)#int lo1
Adapted from the Synchronization example in g/case/studies/icsbgp4.html
 Adapted from the Synchronization example in http://www.cisco.com/en/us/docs/internetworkin g/case/studies/icsbgp4.html When an AS provides transit service to other ASs when there are non-bgp routers in
Adapted from the Synchronization example in http://www.cisco.com/en/us/docs/internetworkin g/case/studies/icsbgp4.html When an AS provides transit service to other ASs when there are non-bgp routers in
BGP Commands on Cisco ASR 9000 Series Router
 This module describes the commands used to configure and monitor Border Gateway Protocol (BGP) on Cisco ASR 9000 Series Aggregation Services Routers using Cisco IOS XR software. The commands in this module
This module describes the commands used to configure and monitor Border Gateway Protocol (BGP) on Cisco ASR 9000 Series Aggregation Services Routers using Cisco IOS XR software. The commands in this module
address-family ipv4 vrf vrf-name - Selects a per-vrf instance of a routing protocol.
 LAB 1: Initial MPLS VPN Setup LAB 2: Running OSPF between PE and CE Routers LAB 3: Running BGP between PE and CE Routers LAB 4: Overlapping VPNs LAB 1: Initial MPLS VPN Setup Introduction: Introduction
LAB 1: Initial MPLS VPN Setup LAB 2: Running OSPF between PE and CE Routers LAB 3: Running BGP between PE and CE Routers LAB 4: Overlapping VPNs LAB 1: Initial MPLS VPN Setup Introduction: Introduction
SDN Workshop. Contact: WSDN01_v0.1
 SDN Workshop Contact: training@apnic.net WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS - Lab SDN Workshop WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS Configuration 3 Configuration Example
SDN Workshop Contact: training@apnic.net WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS - Lab SDN Workshop WSDN01_v0.1 Issue Date: [Date] Revision: [xx] BGP-LS Configuration 3 Configuration Example
Internetwork Expert s CCNP Bootcamp. Border Gateway Protocol (BGP) What Is BGP?
 Internetwork Expert s CCNP Bootcamp Border Gateway Protocol (BGP) http:// What Is BGP? Border Gateway Protocol Version 4 Standards based RFC 4271 A Border Gateway Protocol 4 (BGP-4) Exterior Gateway Protocol
Internetwork Expert s CCNP Bootcamp Border Gateway Protocol (BGP) http:// What Is BGP? Border Gateway Protocol Version 4 Standards based RFC 4271 A Border Gateway Protocol 4 (BGP-4) Exterior Gateway Protocol
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
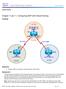 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
LAB5: OSPF IPv4. OSPF: Stub. Disclaimer
 Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
BGP Table Version. Contents. Introduction. Network Diagram. Best Path
 BGP Table Version Document ID: 116511 Contributed by Luc De Ghein, Cisco TAC Engineer. Sep 30, 2013 Contents Introduction Network Diagram Best Path Types of Table Versions Initial Table Version Number
BGP Table Version Document ID: 116511 Contributed by Luc De Ghein, Cisco TAC Engineer. Sep 30, 2013 Contents Introduction Network Diagram Best Path Types of Table Versions Initial Table Version Number
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Deploy MPLS L3 VPN. APNIC Technical Workshop October 23 to 25, Selangor, Malaysia Hosted by:
 Deploy MPLS L3 VPN APNIC Technical Workshop October 23 to 25, 2017. Selangor, Malaysia Hosted by: Issue Date: [201609] Revision: [01] Acknowledgement Cisco Systems Course Outline MPLS L3 VPN Models L3
Deploy MPLS L3 VPN APNIC Technical Workshop October 23 to 25, 2017. Selangor, Malaysia Hosted by: Issue Date: [201609] Revision: [01] Acknowledgement Cisco Systems Course Outline MPLS L3 VPN Models L3
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
MPLS VPN C H A P T E R S U P P L E M E N T. BGP Advertising IPv4 Prefixes with a Label
 7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
Implementing DCI VXLAN Layer 3 Gateway
 This chapter module provides conceptual and configuration information for Data Center Interconnect (DCI) VXLAN Layer 3 Gateway on Cisco ASR 9000 Series Router. Release Modification Release 5.3.2 This feature
This chapter module provides conceptual and configuration information for Data Center Interconnect (DCI) VXLAN Layer 3 Gateway on Cisco ASR 9000 Series Router. Release Modification Release 5.3.2 This feature
CCIE Service Provider Sample Lab. Part 1 of 7
 CCIE Service Provider Sample Lab Part 1 of 7 SP Sample Lab Main Topology R13 S2/1.135.13/24 Backbone Carrier SP AS 1002 S2/1 PPP E0/1.69.6/24 R6 Customer Carrier SP ABC Site 5 AS 612 E1/0 ISIS.126.6/24
CCIE Service Provider Sample Lab Part 1 of 7 SP Sample Lab Main Topology R13 S2/1.135.13/24 Backbone Carrier SP AS 1002 S2/1 PPP E0/1.69.6/24 R6 Customer Carrier SP ABC Site 5 AS 612 E1/0 ISIS.126.6/24
MPLS for R&S CCIE Candidates
 MPLS for R&S CCIE Candidates Johnny Bass CCIE #6458 2 About the Presenter Johnny Bass Networking industry since the late 1980s CCIE R&S #6458 CCSI 97168 Cisco 360 R&S Master Instructor Course director
MPLS for R&S CCIE Candidates Johnny Bass CCIE #6458 2 About the Presenter Johnny Bass Networking industry since the late 1980s CCIE R&S #6458 CCSI 97168 Cisco 360 R&S Master Instructor Course director
LAB8: OSPF IPv4. OSPF: Virtual Link. Disclaimer
 Page1 AB8: OSPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB8: OSPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Easy Virtual Network Configuration Example
 Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Chapter 7 Lab 7-2, Using the AS_PATH Attribute
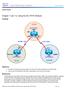 Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Failover with EIGRP Using VRF Configuration Example
 Failover with EIGRP Using VRF onfiguration Example ocument I: 113446 ontents Introduction Prerequisites Hardware and Software Versions onventions onfigure Network iagram onfigurations Verify Show ommands
Failover with EIGRP Using VRF onfiguration Example ocument I: 113446 ontents Introduction Prerequisites Hardware and Software Versions onventions onfigure Network iagram onfigurations Verify Show ommands
Module 6 Implementing BGP
 Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration
 Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration Topology Objectives Configure IPv6 addressing. Configure and verify RIPng on R1 and R2. Configure IPv6 static routes between R2 and R3.
Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration Topology Objectives Configure IPv6 addressing. Configure and verify RIPng on R1 and R2. Configure IPv6 static routes between R2 and R3.
IOS Implementation of the ibgp PE CE Feature
 IOS Implementation of the ibgp PE CE Feature Document ID: 117567 Contributed by Luc De Ghein, Cisco TAC Engineer. Apr 04, 2014 Contents Introduction Background Information Implement ibgp PE CE BGP Customer
IOS Implementation of the ibgp PE CE Feature Document ID: 117567 Contributed by Luc De Ghein, Cisco TAC Engineer. Apr 04, 2014 Contents Introduction Background Information Implement ibgp PE CE BGP Customer
GRE Tunnel with VRF Configuration Example
 GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
MPLS VPN--Inter-AS Option AB
 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
Border Gateway Protocol (BGP) Optimal Route Reflection
 Border Gateway Protocol (BGP) Optimal Route Reflection Contents Introduction Background Information Network Diagram Theory IOS-XR Implementation Configure Configuration Example MPLS Traffic-Engineering
Border Gateway Protocol (BGP) Optimal Route Reflection Contents Introduction Background Information Network Diagram Theory IOS-XR Implementation Configure Configuration Example MPLS Traffic-Engineering
MPLS VPN Multipath Support for Inter-AS VPNs
 The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
ibgp Multipath Load Sharing
 ibgp Multipath Load haring Feature History Release 12.2(2)T 12.2(14) Modification This feature was introduced. This feature was integrated into. This feature module describes the ibgp Multipath Load haring
ibgp Multipath Load haring Feature History Release 12.2(2)T 12.2(14) Modification This feature was introduced. This feature was integrated into. This feature module describes the ibgp Multipath Load haring
Troubleshooting LSP Failure in MPLS VPN
 Troubleshooting LSP Failure in MPLS VPN Document ID: 23565 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Router Configurations Problem Cause of the LSP Failure
Troubleshooting LSP Failure in MPLS VPN Document ID: 23565 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Router Configurations Problem Cause of the LSP Failure
Multiprotocol BGP Extensions for IP Multicast Commands
 Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Building the Routing Table. Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles
 Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Contents. Introduction. Prerequisites. Requirements
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Inheritence with EIGRP Named mode Route Replication with EIGRP name mode Routing Context
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Inheritence with EIGRP Named mode Route Replication with EIGRP name mode Routing Context
MPLS VPN Inter-AS Option AB
 First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
BGP Event-Based VPN Import
 The feature introduces a modification to the existing Border Gateway Protocol (BGP) path import process. The enhanced BGP path import is driven by events; when a BGP path changes, all of its imported copies
The feature introduces a modification to the existing Border Gateway Protocol (BGP) path import process. The enhanced BGP path import is driven by events; when a BGP path changes, all of its imported copies
Implement Static Routes for IPv6 Configuration Example
 Implement Static Routes for IPv6 Configuration Example Document ID: 113361 Contents Introduction Prerequisites Components Used Conventions Configure Network Diagram Configurations Verify Related Information
Implement Static Routes for IPv6 Configuration Example Document ID: 113361 Contents Introduction Prerequisites Components Used Conventions Configure Network Diagram Configurations Verify Related Information
IPv6 Tunnel through an IPv4 Network
 IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
INTRODUCTION TO CISCO IOS XR
 INTRODUCTION TO CISCO IOS XR Technical Workbook February 2014 This workbook provides a brief introductory tour to Cisco s IOS XR operating system as a supplement to the Cisco Configuration Guides found
INTRODUCTION TO CISCO IOS XR Technical Workbook February 2014 This workbook provides a brief introductory tour to Cisco s IOS XR operating system as a supplement to the Cisco Configuration Guides found
The information in this document is based on Cisco IOS Software Release 15.4 version.
 Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Relevant Configuration Verify Test case 1 Test case 2 Test case 3 Troubleshoot Introduction
Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Relevant Configuration Verify Test case 1 Test case 2 Test case 3 Troubleshoot Introduction
RealCiscoLAB.com. Chapter 2 Lab 2-2, EIGRP Load Balancing. Topology. Objectives. Background. CCNPv6 ROUTE
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 2 Lab 2-2, EIGRP Load Balancing Topology Objectives Background Review a basic EIGRP configuration. Explore the EIGRP topology table. Identify successors, feasible
RealCiscoLAB.com CCNPv6 ROUTE Chapter 2 Lab 2-2, EIGRP Load Balancing Topology Objectives Background Review a basic EIGRP configuration. Explore the EIGRP topology table. Identify successors, feasible
Multiprotocol Label Switching Virtual Private Network
 Anas Al-Selwi Multiprotocol Label Switching Virtual Private Network Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology Thesis 08 May 2013 Abstract Author(s)
Anas Al-Selwi Multiprotocol Label Switching Virtual Private Network Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology Thesis 08 May 2013 Abstract Author(s)
CCIE R&S Techtorial MPLS
 CCIE R&S Techtorial MPLS Ing. Tomáš Kelemen Partner Systems Engineer CCIE #24395 Ing. Peter Mesjar Systems Engineer CCIE #17428 2011 Cisco Systems, Inc. All rights reserved. 1 Agenda Introduction to MPLS
CCIE R&S Techtorial MPLS Ing. Tomáš Kelemen Partner Systems Engineer CCIE #24395 Ing. Peter Mesjar Systems Engineer CCIE #17428 2011 Cisco Systems, Inc. All rights reserved. 1 Agenda Introduction to MPLS
scope scope {global vrf vrf-name} no scope {global vrf vrf-name} Syntax Description
 Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
Chapter 5: Maintaining and Troubleshooting Routing Solutions
 Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Troubleshooting Network Layer Connectivity 2 Routing and Routing Data Structures
Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Troubleshooting Network Layer Connectivity 2 Routing and Routing Data Structures
MPLS VPN Carrier Supporting Carrier IPv4 BGP Label Distribution
 MPLS VPN Carrier Supporting Carrier IPv4 BGP Label Distribution This feature lets you configure your carrier supporting carrier network to enable Border Gateway Protocol (BGP) to transport routes and Multiprotocol
MPLS VPN Carrier Supporting Carrier IPv4 BGP Label Distribution This feature lets you configure your carrier supporting carrier network to enable Border Gateway Protocol (BGP) to transport routes and Multiprotocol
Contents. BGP commands 1
 Contents BGP commands 1 address-family ipv4 1 address-family ipv6 2 address-family link-state 3 advertise-rib-active 4 aggregate 5 balance 7 balance as-path-neglect 9 bestroute as-path-neglect 10 bestroute
Contents BGP commands 1 address-family ipv4 1 address-family ipv6 2 address-family link-state 3 advertise-rib-active 4 aggregate 5 balance 7 balance as-path-neglect 9 bestroute as-path-neglect 10 bestroute
Lab 5-3 Redistribution Between EIGRP and IS-IS
 Lab 5-3 Redistribution Between EIGRP and IS-IS Learning Objectives Review basic configuration of EIGRP and IS-IS Redistribute into EIGRP Redistribute into IS-IS Use a standard access list to select routes
Lab 5-3 Redistribution Between EIGRP and IS-IS Learning Objectives Review basic configuration of EIGRP and IS-IS Redistribute into EIGRP Redistribute into IS-IS Use a standard access list to select routes
You cannot configure prefix-sids on transit links at this time. Support for this feature may be introduced in later code versions.
 8.1 Segment Routing Segment Routing (SR) is a relatively new technology pioneered by Cisco that is meant to reduce state in MPLS core networks. One can use SR to replace LDP and RSVP-TE wholesale provided
8.1 Segment Routing Segment Routing (SR) is a relatively new technology pioneered by Cisco that is meant to reduce state in MPLS core networks. One can use SR to replace LDP and RSVP-TE wholesale provided
Chapter 3 Lab 3-2, Multi-Area OSPFv2 and OSPFv3 with Stub Area
 Chapter 3 Topology Objectives Configure multi-area OSPFv2 for IPv4. Configure multi-area OSPFv3 for IPv6 Verify multi-area behavior. Configure stub and totally stubby areas for OSPFv2. Configure stub and
Chapter 3 Topology Objectives Configure multi-area OSPFv2 for IPv4. Configure multi-area OSPFv3 for IPv6 Verify multi-area behavior. Configure stub and totally stubby areas for OSPFv2. Configure stub and
LAB8: Named EIGRP IPv4
 Page1 AB8: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB8: Named EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Route Leaking in MPLS/VPN Networks
 Route Leaking in MPLS/VPN Networks Document ID: 47807 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Route Leaking from a Global Routing Table into a VRF and Route
Route Leaking in MPLS/VPN Networks Document ID: 47807 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Route Leaking from a Global Routing Table into a VRF and Route
Page1. Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M), Version 15.2(4)M1, DEVELOPMENT TEST SOFTWARE
 BGP Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to ensure that all material is as complete
BGP Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made to ensure that all material is as complete
BGP Event-Based VPN Import
 BGP Event-Based VPN Import Last Updated: April 13, 2012 The BGP Event-Based VPN Import feature introduces a modification to the existing Border Gateway Protocol (BGP) path import process. The enhanced
BGP Event-Based VPN Import Last Updated: April 13, 2012 The BGP Event-Based VPN Import feature introduces a modification to the existing Border Gateway Protocol (BGP) path import process. The enhanced
MPLS VPN Route Target Rewrite
 The feature allows the replacement of route targets on incoming and outgoing Border Gateway Protocol (BGP) updates Typically, Autonomous System Border Routers (ASBRs) perform the replacement of route targets
The feature allows the replacement of route targets on incoming and outgoing Border Gateway Protocol (BGP) updates Typically, Autonomous System Border Routers (ASBRs) perform the replacement of route targets
CCIE Service Provider Sample Lab. Part 2 of 7
 CCIE Service Provider Sample Lab Part 2 of 7 SP Sample Lab Main Topology R13 S2/1.135.13/24 Backbone Carrier SP AS 1002 S2/1 PPP E0/1.69.6/24 R6 Customer Carrier SP ABC Site 5 AS 612 E1/0 ISIS.126.6/24
CCIE Service Provider Sample Lab Part 2 of 7 SP Sample Lab Main Topology R13 S2/1.135.13/24 Backbone Carrier SP AS 1002 S2/1 PPP E0/1.69.6/24 R6 Customer Carrier SP ABC Site 5 AS 612 E1/0 ISIS.126.6/24
MPLS VPN Carrier Supporting Carrier IPv4 BGP Label Distribution
 MPLS VPN Carrier Supporting Carrier IPv4 BGP Label Distribution This feature enables you to configure your carrier supporting carrier network to enable Border Gateway Protocol (BGP) to transport routes
MPLS VPN Carrier Supporting Carrier IPv4 BGP Label Distribution This feature enables you to configure your carrier supporting carrier network to enable Border Gateway Protocol (BGP) to transport routes
FlexVPN HA Dual Hub Configuration Example
 FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
IP NAT Troubleshooting. Solutions. Luke Bibby, CCIE #45527
 IP NAT Troubleshooting Solutions Luke Bibby, CCIE #45527 Quick Overview of Scenario Solutions Scenario #1 R2 s E0/0 should be NAT inside not NAT outside ACL 100 is configured incorrectly NAT policy missing
IP NAT Troubleshooting Solutions Luke Bibby, CCIE #45527 Quick Overview of Scenario Solutions Scenario #1 R2 s E0/0 should be NAT inside not NAT outside ACL 100 is configured incorrectly NAT policy missing
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF
 Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Configure Segment Routing for IS-IS Protocol
 Integrated Intermediate System-to-Intermediate System (IS-IS), Internet Protocol Version 4 (IPv4), is a standards-based Interior Gateway Protocol (IGP). The Cisco IOS XR software implements the IP routing
Integrated Intermediate System-to-Intermediate System (IS-IS), Internet Protocol Version 4 (IPv4), is a standards-based Interior Gateway Protocol (IGP). The Cisco IOS XR software implements the IP routing
LAB11: EIGRP IPv4. EIGRP: Stub. Disclaimer
 Page1 AB11: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB11: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Configuration and Management of Networks 2012
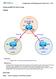 Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Configuring a BGP Route Server
 BGP route server is a feature designed for internet exchange (IX) operators that provides an alternative to full ebgp mesh peering among the service providers who have a presence at the IX. The route server
BGP route server is a feature designed for internet exchange (IX) operators that provides an alternative to full ebgp mesh peering among the service providers who have a presence at the IX. The route server
BGP Route Reflector Commands
 This chapter provides details of the commands used for configuring Border Gateway Protocol (BGP) Route Reflector (RR). address-family (BGP), on page 2 keychain, on page 5 neighbor (BGP), on page 7 remote-as
This chapter provides details of the commands used for configuring Border Gateway Protocol (BGP) Route Reflector (RR). address-family (BGP), on page 2 keychain, on page 5 neighbor (BGP), on page 7 remote-as
Configuration and Management of Networks
 Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
CertifyMe. CertifyMe
 CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
Configuring IPv6 VPN Provider Edge over MPLS (6VPE)
 Configuring IPv6 VPN Provider Edge over MPLS (6VPE) Finding Feature Information, page 1 Configuring 6VPE, page 1 Finding Feature Information Your software release may not support all the features documented
Configuring IPv6 VPN Provider Edge over MPLS (6VPE) Finding Feature Information, page 1 Configuring 6VPE, page 1 Finding Feature Information Your software release may not support all the features documented
Configuring Multicast VPN Inter-AS Support
 Configuring Multicast VPN Inter-AS Support Last Updated: December 23, 2011 The Multicast VPN Inter-AS Support feature enables Multicast Distribution Trees (MDTs) used for Multicast VPNs (MVPNs) to span
Configuring Multicast VPN Inter-AS Support Last Updated: December 23, 2011 The Multicast VPN Inter-AS Support feature enables Multicast Distribution Trees (MDTs) used for Multicast VPNs (MVPNs) to span
Troubleshooting Routing Solutions
 Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Chapter 5 Objectives Diagnose network layer connectivity problems using
Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Chapter 5 Objectives Diagnose network layer connectivity problems using
May 14, 2006 Nairobi, Kenya
 AfNOG MPLS Lab May 14, 2006 Nairobi, Kenya Page 1 of 30 Table of Contents Assignment...3 Topology...3 Connection information...3 IP Addressing...4 Initial Configuration...4 Lab Modules...5 Module 1: Basic
AfNOG MPLS Lab May 14, 2006 Nairobi, Kenya Page 1 of 30 Table of Contents Assignment...3 Topology...3 Connection information...3 IP Addressing...4 Initial Configuration...4 Lab Modules...5 Module 1: Basic
Implementing MPLS VPNs over IP Tunnels
 The MPLS VPNs over IP Tunnels feature lets you deploy Layer 3 Virtual Private Network (L3VPN) services, over an IP core network, using L2TPv3 multipoint tunneling instead of MPLS. This allows L2TPv3 tunnels
The MPLS VPNs over IP Tunnels feature lets you deploy Layer 3 Virtual Private Network (L3VPN) services, over an IP core network, using L2TPv3 multipoint tunneling instead of MPLS. This allows L2TPv3 tunnels
CCIE ROUTING & SWITCHING v5.0 LAB EXAM CONFIGURATION SECTION -H3 Lead2pass.
 CCIE ROUTING & SWITCHING v5.0 LAB EXAM CONFIGURATION SECTION -H3 H3 Topology Diagrams Collection SECTION 1 Layer 2 Technologies Section 1.1: LAN Access Section 1.2: LAN Distribution Section 1.3: LAN Resiliency:
CCIE ROUTING & SWITCHING v5.0 LAB EXAM CONFIGURATION SECTION -H3 H3 Topology Diagrams Collection SECTION 1 Layer 2 Technologies Section 1.1: LAN Access Section 1.2: LAN Distribution Section 1.3: LAN Resiliency:
RealCiscoLAB.com. Chapter 6 Lab 6-2, Using the AS_PATH Attribute. Topology. Objectives. Background. CCNPv6 ROUTE
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
Highly Available Wide Area Network Design
 Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com CCIE #6508 (R&S/SP/Security) BRKRST-2042 Agenda Introduction Cisco IOS and IP Routing Convergence Techniques
Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com CCIE #6508 (R&S/SP/Security) BRKRST-2042 Agenda Introduction Cisco IOS and IP Routing Convergence Techniques
ECMP Load Balancing. MPLS: Layer 3 VPNs Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) 1
 Equal-cost multi-path routing (ECMP) is a routing strategy where next-hop packet forwarding to a single destination can occur over multiple "best paths" which tie for top place in routing metric calculations.
Equal-cost multi-path routing (ECMP) is a routing strategy where next-hop packet forwarding to a single destination can occur over multiple "best paths" which tie for top place in routing metric calculations.
BGP FlowSpec Route-reflector Support
 The BGP (Border Gateway Protocol) Flowspec (Flow Specification) Route Reflector feature enables service providers to control traffic flows in their network. This helps in filtering traffic and helps in
The BGP (Border Gateway Protocol) Flowspec (Flow Specification) Route Reflector feature enables service providers to control traffic flows in their network. This helps in filtering traffic and helps in
IPv6 Switching: Provider Edge Router over MPLS
 Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
Multiprotocol Label Switching (MPLS) is deployed by many service providers in their IPv4 networks. Service providers want to introduce IPv6 services to their customers, but changes to their existing IPv4
BGP Cost Community. Prerequisites for the BGP Cost Community Feature
 The feature introduces the cost extended community attribute. The cost community is a non-transitive extended community attribute that is passed to internal BGP (ibgp) and confederation peers but not to
The feature introduces the cost extended community attribute. The cost community is a non-transitive extended community attribute that is passed to internal BGP (ibgp) and confederation peers but not to
BGP Nonstop Routing was made a default feature.
 Border Gateway Protocol (BGP) is an Exterior Gateway Protocol (EGP) that allows you to create loop-free interdomain routing between autonomous systems. An autonomous system is a set of routers under a
Border Gateway Protocol (BGP) is an Exterior Gateway Protocol (EGP) that allows you to create loop-free interdomain routing between autonomous systems. An autonomous system is a set of routers under a
BGP Support for Next-Hop Address Tracking
 The feature is enabled by default when a supporting Cisco software image is installed. BGP next-hop address tracking is event driven. BGP prefixes are automatically tracked as peering sessions are established.
The feature is enabled by default when a supporting Cisco software image is installed. BGP next-hop address tracking is event driven. BGP prefixes are automatically tracked as peering sessions are established.
BGP Commands: M through N
 match additional-paths advertise-set, on page 3 match as-path, on page 6 match community, on page 8 match extcommunity, on page 10 match local-preference, on page 12 match policy-list, on page 14 match
match additional-paths advertise-set, on page 3 match as-path, on page 6 match community, on page 8 match extcommunity, on page 10 match local-preference, on page 12 match policy-list, on page 14 match
Lab- Configuring Basic Single-Area OSPFv2
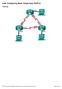 Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
RealCiscoLAB.com. Chapter 6 Lab 6-1, Configuring BGP with Default Routing. Configure BGP to exchange routing information with two ISPs.
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-1, Configuring BGP with Default Routing Topology Objectives Background Configure BGP to exchange routing information with two ISPs. The International Travel
RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-1, Configuring BGP with Default Routing Topology Objectives Background Configure BGP to exchange routing information with two ISPs. The International Travel
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Configuring Easy Virtual Network Shared Services
 Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
BGP Persistence. Restrictions for BGP Persistence. Information About BGP Persistence
 BGP persistence enables the router to retain routes that it has learnt from the configured neighbor even when the neighbor session is down. BGP persistence is also referred as long lived graceful restart
BGP persistence enables the router to retain routes that it has learnt from the configured neighbor even when the neighbor session is down. BGP persistence is also referred as long lived graceful restart
Rev External BGP
 Rev. 00.. External BGP c c n a c o o k b o o k. c o m C O N C E P T S AS (Autonomous System) A network under a single administrative control, like a single company or a single ISP. ASN (AS Number) used
Rev. 00.. External BGP c c n a c o o k b o o k. c o m C O N C E P T S AS (Autonomous System) A network under a single administrative control, like a single company or a single ISP. ASN (AS Number) used
CCIE Service Provider v3.0 Sample Lab
 CCIE Service Provider v3.0 Sample Lab Part 6/7 Vincent Jun Ling Zhou CCIE Service Provider Product Manager Cisco Systems SP Sample Lab Main Topology R13 S2/1.135.13/24 Backbone Carrier SP AS 1002 S2/1
CCIE Service Provider v3.0 Sample Lab Part 6/7 Vincent Jun Ling Zhou CCIE Service Provider Product Manager Cisco Systems SP Sample Lab Main Topology R13 S2/1.135.13/24 Backbone Carrier SP AS 1002 S2/1
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP
 MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
MPLS VPN Half-Duplex VRF
 The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
MPLS VPN Inter-AS with ASBRs Exchanging VPN-IPv4 Addresses
 MPLS VPN Inter-AS with ASBRs Exchanging VPN-IPv4 Addresses The Multiprotocol Label Switching (MPLS) VPN Inter-AS with Autonomous System Boundary Routers (ASBRs) Exchanging VPN-IPv4 Addresses feature allows
MPLS VPN Inter-AS with ASBRs Exchanging VPN-IPv4 Addresses The Multiprotocol Label Switching (MPLS) VPN Inter-AS with Autonomous System Boundary Routers (ASBRs) Exchanging VPN-IPv4 Addresses feature allows
BGP Support for Next-Hop Address Tracking
 BGP Support for Next-Hop Address Tracking Last Updated: November 26, 2012 The BGP Support for Next-Hop Address Tracking feature is enabled by default when a supporting Cisco software image is installed.
BGP Support for Next-Hop Address Tracking Last Updated: November 26, 2012 The BGP Support for Next-Hop Address Tracking feature is enabled by default when a supporting Cisco software image is installed.
